#EnterpriseSecurity
Text
#ManagedSecurityServices#CyberSecurity#SecuritySolutions#ITSecurity#DataProtection#NetworkSecurity#ThreatManagement#SecurityAsAService#MSSP#RiskManagement#CyberDefense#CloudSecurity#EnterpriseSecurity#Infosec#SecurityTrends#ManagedSecurity#SecurityInnovation#TechSecurity#CyberThreats#SecurityMonitoring
0 notes
Text
Box: The Ultimate Cloud Content Management Platform

Click here- Box: The Ultimate Cloud Content Management Platform
Box is a leading cloud content management platform designed to help businesses securely store, share, and collaborate on files online. Founded in 2005, Box has become an essential tool for companies of all sizes, offering a secure and user-friendly environment for managing content across teams.

Key Features:
Secure File Storage and Sharing: Box provides robust security features, including data encryption, access controls, and compliance certifications, ensuring sensitive information is protected.
Collaboration Tools: With real-time collaboration features, Box allows teams to work together on documents, leave comments, and track changes, streamlining workflows and enhancing productivity.
Integration with Popular Apps: Box integrates seamlessly with popular business tools like Microsoft Office 365, Google Workspace, Slack, and Salesforce, allowing users to work within their preferred applications.
Automated Workflows: Box’s automation tools help streamline repetitive tasks, improve efficiency, and reduce manual work, making it easier for teams to focus on high-value activities.
Advanced Analytics: Box offers insights into how content is being used across the organization, helping businesses make data-driven decisions to optimize their content strategy.
Why Choose Box?
Box is more than just a file storage solution; it's a comprehensive content management platform that empowers businesses to work smarter. Its focus on security, compliance, and collaboration makes it a top choice for organizations looking to manage their content in the cloud.
#BoxPlatform#CloudStorage#ContentManagement#FileSharing#TeamCollaboration#SecureCloud#CloudSolutions#DigitalWorkspace#WorkflowAutomation#EnterpriseSecurity#BoxCommunity#BusinessProductivity#DataSecurity#FileManagement#CloudIntegration
1 note
·
View note
Text

Kensington VeriMark™ Desktop Fingerprint Key
🔒 Secure Your Workspace with the Kensington VeriMark™ Desktop Fingerprint Key! 🔒
Elevate your security with cutting-edge biometric technology. The VeriMark™ Desktop Fingerprint Key offers business-class security with FIDO U2F and FIDO2 WebAuthn compatibility, plus seamless integration with Windows Hello. Perfect for enterprise PC deployment and compatible with Microsoft services like Office365, Outlook, and more. Protect your data effortlessly!
#Kensington#VeriMark#FingerprintSecurity#EnterpriseSecurity#BiometricTechnology#WindowsHello#SecureWorkspace luckyfalcon#kensington#kenya#southafrica#dubai#middleeast
0 notes
Text
#RemoteBrowserIsolation#CyberSecurity#WebSecurity#DigitalSafety#ThreatPrevention#DataProtection#BrowserSecurity#ITSecurity#CyberDefense#SecureBrowsing#NetworkProtection#SecuritySolutions#VirtualIsolation#EnterpriseSecurity#RemoteWorkSecurity
0 notes
Text
Lucas Nolan - Google Targets Microsoft’s Enterprise Security Weaknesses, Pitches Its Services to Government:
CyberSafetyReviewBoard #CSRB #Google #Microsoft #SingleSource #Cracking #Vulnerabilities #EnterpriseSecurity #NetworkSecurity #InformationTechnology #ComputerScience
#cybersafetyreviewboard#csrb#google#microsoft#singlesource#cracking#vulnerabilities#enterprisesecurity#networksecurity#informationtechnology#computerscience
0 notes
Link
https://bit.ly/3Rmzron - 🔒 Mallox, a persistent ransomware threat first identified in 2021, continues to exploit enterprises, particularly through vulnerabilities in MS-SQL. Operating under a Ransomware-as-a-Service (RaaS) model, Mallox targets unpatched systems and uses brute force attacks to gain access. This activity underscores the ongoing risk posed by ransomware to business data security. #MalloxCyberThreat #RansomwareAlert 🌐 Mallox gains initial access through exploitation of MS-SQL and ODBC interfaces, targeting specific vulnerabilities. The group focuses on vulnerabilities like CVE-2019-1068 in Microsoft SQL Server and CVE-2020-0618 in Microsoft SQL Server Reporting Services, alongside brute force attacks. This strategy highlights the importance of regular system updates and strong security configurations. #CyberSecurity #VulnerabilityManagement 💻 Post-compromise, Mallox actors utilize PowerShell commands to download and execute ransomware payloads. They employ scripts to terminate processes that could hinder encryption routines, reflecting a sophisticated approach to system compromise. Understanding these tactics is crucial for defenders to effectively protect their networks. #MalwareAnalysis #NetworkDefense 🔐 Recent Mallox payloads, labeled "Mallox.Resurrection," display consistent core functionalities, indicating a successful, unaltered formula. These payloads exempt certain file types and processes from encryption and modify system recovery settings, making it difficult for administrators to restore affected systems. #RansomwareTactics #DigitalProtection 📝 Mallox threats often conclude with encrypted files receiving the .mallox extension and a ransom note demanding payment for decryption. Failure to comply results in threats of public data exposure on Mallox's data leak site. This tactic emphasizes the critical need for robust backup strategies and incident response planning. #DataSecurity #CyberRiskManagement In conclusion, Mallox's ongoing ransomware activities, exploiting MS-SQL vulnerabilities and employing sophisticated encryption techniques, serve as a reminder for enterprises to prioritize cybersecurity and stay vigilant against evolving threats.
#MalloxCyberThreat#RansomwareAlert#CyberSecurity#VulnerabilityManagement#MalwareAnalysis#NetworkDefense#RansomwareTactics#DigitalProtection#DataSecurity#CyberRiskManagement#CyberResilience#EnterpriseSecurity
0 notes
Text
Secure Access Service Edge (SASE) Market Strategic Analysis: Enabling Secure Transformation
The global secure access service edge market size is expected to reach USD 11.29 billion by 2028, registering a CAGR of 36.4% from 2021 to 2028, according to a new study conducted by Grand View Research, Inc. The existing networking technologies are complex and difficult to manage but easy for cybercriminals to intrude. The growing preference for remote working practices, increase in traffic across public clouds, and the rising dependence on data centers are further adding to the data security risks. At this juncture, the growing demand for ensuring secure access to data and networks is driving the need for advanced network approaches and technologies. The subsequent need for a unified and simplified approach to strengthen network security has resulted in the emergence of SASE.
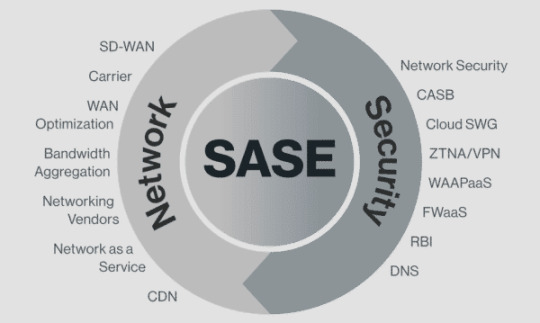
Secure Access Service Edge Market Report Highlights
The platform segment accounted for over 70% of the overall revenue share in 2020 as the growing preference for remote working continued to drive the demand for a unified security solution that can offer the capabilities of several network security services
The demand for SASE was higher among IT & telecom enterprises in 2020 as the need to filter contents across edges and ensure efficient security framework management continued to drive the adoption of SASE among IT & telecom organizations
North America dominated the global market in 2020 and is expected to remain dominant over the forecast period
Aggressive IT spending, effective implementation of security standards, and the continued rollout of the digital workforce by organizations across the U.S. and Canada are some of the factors that are expected to drive the regional market
For More Details or Sample Copy please visit link @: Secure Access Service Edge Market Report
SASE architecture comprises the capabilities of network security services, such as Zero Trust, FWaaS, and CASB, and software-defined WAN capabilities, combined in a unified platform to help organizations in ensuring easy and secure access to data and networks. SASE architecture simplifies the IT infrastructure and frees organizations from the burden of managing and periodically updating multiple security systems. SASE architecture also allows organizations to save on the costs incurred on procuring multiple security solutions and helps them in the quick implementation of data protection policies. All such benefits are driving the popularity of SASE frameworks among enterprises.
The COVID-19 pandemic and the subsequent restrictions on the movement of people imposed by various governments across the world have prompted organizations to switch to a remote working model. However, the remote working model has also triggered challenges related to managing the productivity of a flexible workforce and security governance. Organizations are also exposed to higher levels of cybersecurity risks than ever. As a result, organizations are looking forward to implementing robust security frameworks. The growing need to establish effective security frameworks while ensuring convenient access to information for employees using an integrated approach is expected to drive the adoption of SASE frameworks.
#SASE#NetworkSecurity#EdgeSecurity#Cybersecurity#CloudSecurity#SecureConnectivity#EnterpriseSecurity#CyberDefense#EdgeComputing#InfoSec#ITInfrastructure#NetworkArchitecture#SASESolutions#DataProtection#CyberThreats#SecureNetworking
0 notes
Text
The Cost-Effective Approach to Cybersecurity for SMBs - Part 2
While large enterprises have dedicated resources like Security Operations Centers (SOC), SMBs undergo a different trajectory compared to their large enterprise counterparts to attain a mature security posture.
To summarize, ensure your cybersecurity provides you complete visibility, interoperability, scalability, hunting & early detection capabilities, analytics & incident reporting, low latency, and on-demand access to experts. You can take cost-effective approaches explained in this blog
1 note
·
View note
Text
Cloudtv italia

#Cloudtv italia software
#Cloudtv italia tv
By delivering a combined set of content, you can cater to a wider audience on your OTT platform, giving them the option of switching between live or on-demand video. Opt for a cloud playout solution provider that lets you host both VoD and live stream content based on your event calendar prepared in advance.
#Cloudtv italia tv
While there are a lot of advanced features a cloud playout solution can offer you, here are some of the basic requirements you would be needing from your playout solution partner to launch your cloud TV channel: If you want to explore more on the features of a cloud playout software, read our blog- Features of a Best-in-Class Cloud Playout Solutionįeatures an Online TV Playout Platform Should have The simplest of all options- you can opt for a readymade cloud playout platform like Muvi Playout to launch your online TV channel without any coding hassles.Although this option is expensive, you have the advantage of getting a custom-made content delivery platform tailored according to your needs
#Cloudtv italia software
If you have the budget, you could hire a professional developer to build the cloud playout software for you.
Of course for this job, you would need to have a complete technical know-how on the subject
You can build your playout software by coding in-house.
So, to start your online TV channel, you have three options: Let’s assume you have some amazing TV content that you want to stream on your website, but do not have the playout software you would require to schedule and stream it on your video streaming website. Just follow the below-mentioned steps and you will be ready to launch your internet TV channel in no time:Ĭhoosing your Online Cloud TV Playout Platform Starting your online cloud TV channel is simple, once you narrow down on a professional cloud playout solution equipped with futuristic features and functionalities to help you reach your business goals. How Can I Start My Online Cloud TV Channel? Broadcasters are now venturing into cloud playout- driven software solutions to launch online TV channels across multiple platforms to reach the Gen Z audience. Josh Hilliker, Intel's Director of Cloud Solutions, takes a look at the benefits and tradeoffs of different types of processors used in cloud computing and why it's important to evaluate business workloads and existing hardware when choosing the optimal cloud solution." Ĭq_tms.video_thumbnail = "/content/dam/Compared to their predecessor, online cloud TV channels are now becoming more popular amongst broadcasters owing to their cost-effectiveness, scalability, and more flexible and technology-friendly infrastructure. Wa_cq_url: "/content/= "Find the Right Processor for Your Workloads" Ĭq_tms.video_long_desc = "You may have been led to believe that hardware is irrelevant in the cloud. Wa_audience: "emtaudience:business/btssbusinesstechnologysolutionspecialist,emtaudience:business/itoperationsspecialist,emtaudience:business/srbusinessdecisionmaker", Wa_english_title: "Intel® Cloud TV: Processors in the Cloud", Wa_industry_type: "emtindustry:accommodationandfoodservices,emtindustry:agriculture,emtindustry:defenseandspace,emtindustry:education,emtindustry:energy,emtindustry:financialservices,emtindustry:government,emtindustry:healthcareandwellbeing,emtindustry:manufacturing,emtindustry:media,emtindustry:retail,emtindustry:telecommunications,emtindustry:transportation", Wa_emtsubject: "emtsubject:intelsecurity/enterprisesecurity/networksecurity,emtsubject:itinformationtechnology/cloudcomputing/cloudplatforms,emtsubject:itinformationtechnology/cloudcomputing/multicloud,emtsubject:design/hardwaredesign,emtsubject:itinformationtechnology/cloudcomputing/cloudstorage,emtsubject:itinformationtechnology/cloudcomputing/hybridcloud,emtsubject:itinformationtechnology/cloudcomputing/cloudservers,emtsubject:itinformationtechnology/cloudcomputing/cloudsecurity", Wa_emtindustry: "emtindustry:transportation,emtindustry:government,emtindustry:manufacturing,emtindustry:healthcareandwellbeing,emtindustry:accommodationandfoodservices,emtindustry:telecommunications,emtindustry:energy,emtindustry:financialservices,emtindustry:agriculture,emtindustry:media,emtindustry:retail,emtindustry:education,emtindustry:defenseandspace", Wa_emtcontenttype: "emtcontenttype:salesandmarketingmaterials/marketingtools/topicoverviews", Wa_uetcontentformat: "uetcontentformat:videos/videoseries",

0 notes
Text
How to Secure Your Business from Ransomware Attacks

Throughout the most recent couple of years, there has been an emotional expansion in ransomware assaults against associations. Last year alone, an expected 184 million ransomware assaults (statista 2019) have been accounted for. It is regularly connected with monetary liabilities as payoff requested by assailants, ordinarily through intense to-follow electronic installments. Without sufficient calamity recuperation and reinforcement plans, numerous organizations are compelled to pay the payoff. The Cybercrime Magazine Cybersecurity like gamification solutions, enterprise security, finance solutions and logistics solutions Ventures had anticipated that the worldwide expense of ransomware will surpass $5 billion out of 2017, which is multiple times higher than the expense in 2015. At that equivalent time, the quantity of ransomware variations has likewise grown thirty-overlay (Proofpoint, Q4 2016 and Year in Review, December 2016). A new ransomware assault on American city Baltimore's administration PC frameworks is assessed to associate with 18 M USD. Survivors of ransomware now length from huge size association to independent picture takers. Not all associations are openly uncovering the assaults. What we hear in the news is only a glimpse of something larger.
Once ransomware contaminates a machine, it encodes all information in the machine and requests installment. Generally, the installment is asked through well known cryptographic forms of money. What is drawing the cybercriminals to play out these ransomware assaults is the simple chance to bring in speedy cash.
There is no immediate fix for ransomware assaults. Layered protection Cybersecurity like gamification solutions, enterprise security, finance solutions and logistics solutions is the best way to forestall these assaults. Controls are needed from a specialized and non-specialized point of view. The main variable influencing Cybersecurity is unseemly planning. A large portion of the associations getting impacted by Ransomware had a relaxed "this won't influence us" mentality.
This article sums up the danger relief steps to stay away from ransomware assaults.
1. Forestall phishing assaults
Guarantee that worker preparing strategy is set up and representatives are prepared to perceive phishing assaults.
Perform various sorts of reproduced phishing assaults in the association to screen the representatives who succumb to it.
Carry out a spam channel
Guarantee an outsider is performing mimicked phishing assaults in specific spans.
2. Guarantee frameworks are refreshed and fixes are applied
Guarantee fix the board strategy is executed and all frameworks, applications and working frameworks are refreshed
Ensure a weakness the executives program is carried out in the association followed by weakness appraisal at incessant spans.
Guarantee that total redressal of all weaknesses are recognized.
Ensure an outsider is performing VAPT (weakness appraisal and entrance testing) and Red Teaming exercises in specific stretches.
3. Reinforcement Policy
Guarantee a distinct reinforcement strategy is carried out and followed. Reinforcement of the frameworks are vital to recuperate from ransomware assaults.
Store reinforcements in a different gadget or distributed storage relying upon the affectability of the information. The reinforcements ought to be kept in a different area from the organization. For independent venture associations distributed storage can be a trustworthy savvy choice. Cloud , tape drives and outside hard plates are a portion of the choices. Guarantee that reinforcements are confirmed consistently and the capacity to recuperate information should be estimated by a customary reinforcement recuperation work out
4. Guarantee powerful preventive controls are executed
Preventive controls endeavor to forestall episodes before they happen. Ensure antivirus introduced and refreshed routinely. Concentrated antivirus the executives is essential to distinguish machines that are not refreshed or have missing antivirus programming.
Guarantee firewalls are introduced and strategies are overseen such that no Insecure guidelines are executed. Perform standard arrangement audits to comprehend the pointless openness to the frameworks or the edge gadget itself.
Guarantee an Intrusion Prevention System (IPS) is executed and arranged viably. IPS can distinguish known correspondence methods utilized by Ransomwares.
5. What to do when a framework is tainted
Eliminate the tainted framework from the organization. Detach all Wired and Wireless organizations. Debilitate Bluetooth. Disengage remote shared gadgets assuming any.
Separate the frameworks that are associated with a similar organization as the tainted framework. A few frameworks not been totally scrambled by ransomware gives a choice to recuperation.
Quickly illuminate the neighborhood Cyber Police.
Try to change all framework passwords subsequent to eliminating the ransomware.
#cybersecurity#logistics solutions#gamification solutions#finance solutions#enterprise solutions#enterprisesecurity#HeraSoft
1 note
·
View note
Text
#SAML#SAMLAuthentication#IdentityManagement#SingleSignOn#SSO#AuthenticationSolutions#SecurityStandards#IdentitySecurity#CyberSecurity#AccessManagement#AuthenticationTechnology#SAMLIntegration#DigitalIdentity#EnterpriseSecurity#SecureAccess
0 notes
Text
The Reason Why Small Enterprise Never Recover Post Cyberattacks
Critical cyberattacks can also impact your brand and will make you lose confidence in your business. Many businesses gives up because their income has dropped in addition to the cost of cyberattacks.

A cyberattack can paralyze critical infrastructure and businesses and create negative pressure. In other cases, this can lead to litigation between you and your company.
Every organization have some kind of Internet security breach in the last twelve months. The problem is so strong that about 80% of all social security numbers have been hacked at least once.
The Reason Why Small Enterprise Never Recover Post Cyberattacks
0 notes
Link
0 notes
Photo

Why Is Cyber Security For Business Important?
Know the importance of cyber security and why we need cyber secuirty for business. Read more to know about the Cyber Security
Know More: https://goo.gl/ytrJRM
0 notes
Link
https://bit.ly/47rZAsw - 🖥️ In a recent malvertising campaign, a threat actor replicated the legitimate Windows news portal https://bit.ly/47sScNi to distribute a malicious installer for CPU-Z. This method targets enthusiasts and system administrators who frequent such sites for computer reviews and software downloads. The fake site deceives users into downloading malware, highlighting the sophistication of modern cyber threats. #Malvertising #CyberSecurity #InfoStealer 🕵️♂️ Google ads are being exploited in this campaign, with threat actors using cloaking techniques to evade detection. Unsuspecting victims are presented with seemingly legitimate ads, leading to malicious websites when clicked. This practice underscores the ongoing challenge of detecting and preventing malvertising. #GoogleAds #OnlineSafety #DigitalThreats 🔗 Upon clicking the ad, users are redirected to a domain that mimics the Windows news site, complete with a download page for CPU-Z. However, the URL in the address bar reveals it's not the authentic site. This tactic is part of a broader strategy targeting other utilities like Notepad++, Citrix, and VNC Viewer. #Phishing #CyberFraud #InternetSafety 🔏 The payload from this campaign is a digitally signed MSIX installer containing a malicious PowerShell script and a loader known as FakeBat. This approach increases the likelihood of the malware appearing legitimate to the operating system and antivirus software. Malwarebytes is actively blocking these malvertising domains and has detected the final infostealer payload. #MalwareProtection #DigitalSecurity #FakeBat 🚨 The choice of mimicking a popular software download portal like Windows Report indicates a strategic move by threat actors to exploit the trust users place in such sites. In an enterprise environment, it's recommended to verify file checksums and compare SHA256 hash sums with those on the vendor's official website to ensure software integrity.
#Malvertising#CyberSecurity#InfoStealer#GoogleAds#OnlineSafety#DigitalThreats#Phishing#CyberFraud#InternetSafety#MalwareProtection#DigitalSecurity#FakeBat#EnterpriseSecurity#SoftwareSafety#TechAdvice
0 notes
Video
instagram
#AI is now reading better than humans >>> MT @TopCyberNews and @wef via @MikeQuindazzi cc : @darshan_h_sheth >>> #IoT #NLP #CloudComputing #BigData #RPA #DataScience #artificialintelligence #deeplearning #robot #data #computervision #industry40 #deepmind #enterprisesecurity #machinelearning #cybernews #digitalmarketingprocess #iamdarshan #influncer #twitterclarets #mpgvip #emg #twittersmarter #4ir https://www.instagram.com/p/B7O18KRnQbg/?igshid=1pevfgyy2djmg
#ai#iot#nlp#cloudcomputing#bigdata#rpa#datascience#artificialintelligence#deeplearning#robot#data#computervision#industry40#deepmind#enterprisesecurity#machinelearning#cybernews#digitalmarketingprocess#iamdarshan#influncer#twitterclarets#mpgvip#emg#twittersmarter#4ir
0 notes