#Preventing cyberattacks with digital intelligence
Explore tagged Tumblr posts
Text
Why Drone Manufacturers in Taiwan Are Being Cyber-Targeted: A Technologist’s Perspective
Why Drone Manufacturers in Taiwan Are Being Cyber-Targeted: A Technologist’s Perspective
This story explores the intersection of technology and geopolitics. It covers the cyberattacks targeting Taiwan’s drone manufacturers and what they reveal about global power struggles and technological vulnerabilities. Taiwan drone manufacturers under siege: Technology meets geopolitics In the world of technology and defense, Taiwan has become a central player, particularly in the field of…
#Applying Digital Intelligence to Geopolitics#Applying digital intelligence to global defense system#Cyber threats in Taiwan#Cyber threats to drones#Cybersecurity#Digital Intelligence by Digital Mehmet#Digital Intelligence by Dr Mehmet Yildiz#Digital intelligence principles for cyberdefence#Drone industry cyber defense#Drone manufacturers security#Drone tech cybersecurity#Geopolitics and drone tech#How are Drones Changing Modern Warfare?#Lessons from Ukraine War#Perspectives from Australian Defense Force#Politics and digitial intelligence integration#Preventing cyberattacks with digital intelligence#Taiwan cyber geopolitics#Taiwan drone cyberattacks#Taiwan tech cyberwar#Tech industry cyber risks#Technology Perspectives by Technologist Dr Mehmet Yildiz#Thought leadership for digital intelligence#Using digital intelligence for cybersecurity
0 notes
Text
If Donald Trump wins the US presidential election in November, the guardrails could come off of artificial intelligence development, even as the dangers of defective AI models grow increasingly serious.
Trump’s election to a second term would dramatically reshape—and possibly cripple—efforts to protect Americans from the many dangers of poorly designed artificial intelligence, including misinformation, discrimination, and the poisoning of algorithms used in technology like autonomous vehicles.
The federal government has begun overseeing and advising AI companies under an executive order that President Joe Biden issued in October 2023. But Trump has vowed to repeal that order, with the Republican Party platform saying it “hinders AI innovation” and “imposes Radical Leftwing ideas” on AI development.
Trump’s promise has thrilled critics of the executive order who see it as illegal, dangerous, and an impediment to America’s digital arms race with China. Those critics include many of Trump’s closest allies, from X CEO Elon Musk and venture capitalist Marc Andreessen to Republican members of Congress and nearly two dozen GOP state attorneys general. Trump’s running mate, Ohio senator JD Vance, is staunchly opposed to AI regulation.
“Republicans don't want to rush to overregulate this industry,” says Jacob Helberg, a tech executive and AI enthusiast who has been dubbed “Silicon Valley’s Trump whisperer.”
But tech and cyber experts warn that eliminating the EO’s safety and security provisions would undermine the trustworthiness of AI models that are increasingly creeping into all aspects of American life, from transportation and medicine to employment and surveillance.
The upcoming presidential election, in other words, could help determine whether AI becomes an unparalleled tool of productivity or an uncontrollable agent of chaos.
Oversight and Advice, Hand in Hand
Biden’s order addresses everything from using AI to improve veterans’ health care to setting safeguards for AI’s use in drug discovery. But most of the political controversy over the EO stems from two provisions in the section dealing with digital security risks and real-world safety impacts.
One provision requires owners of powerful AI models to report to the government about how they’re training the models and protecting them from tampering and theft, including by providing the results of “red-team tests” designed to find vulnerabilities in AI systems by simulating attacks. The other provision directs the Commerce Department’s National Institute of Standards and Technology (NIST) to produce guidance that helps companies develop AI models that are safe from cyberattacks and free of biases.
Work on these projects is well underway. The government has proposed quarterly reporting requirements for AI developers, and NIST has released AI guidance documents on risk management, secure software development, synthetic content watermarking, and preventing model abuse, in addition to launching multiple initiatives to promote model testing.
Supporters of these efforts say they’re essential to maintaining basic government oversight of the rapidly expanding AI industry and nudging developers toward better security. But to conservative critics, the reporting requirement is illegal government overreach that will crush AI innovation and expose developers’ trade secrets, while the NIST guidance is a liberal ploy to infect AI with far-left notions about disinformation and bias that amount to censorship of conservative speech.
At a rally in Cedar Rapids, Iowa, last December, Trump took aim at Biden’s EO after alleging without evidence that the Biden administration had already used AI for nefarious purposes.
“When I’m reelected,” he said, “I will cancel Biden’s artificial intelligence executive order and ban the use of AI to censor the speech of American citizens on Day One.”
Due Diligence or Undue Burden?
Biden’s effort to collect information about how companies are developing, testing, and protecting their AI models sparked an uproar on Capitol Hill almost as soon as it debuted.
Congressional Republicans seized on the fact that Biden justified the new requirement by invoking the 1950 Defense Production Act, a wartime measure that lets the government direct private-sector activities to ensure a reliable supply of goods and services. GOP lawmakers called Biden’s move inappropriate, illegal, and unnecessary.
Conservatives have also blasted the reporting requirement as a burden on the private sector. The provision “could scare away would-be innovators and impede more ChatGPT-type breakthroughs,” Representative Nancy Mace said during a March hearing she chaired on “White House overreach on AI.”
Helberg says a burdensome requirement would benefit established companies and hurt startups. He also says Silicon Valley critics fear the requirements “are a stepping stone” to a licensing regime in which developers must receive government permission to test models.
Steve DelBianco, the CEO of the conservative tech group NetChoice, says the requirement to report red-team test results amounts to de facto censorship, given that the government will be looking for problems like bias and disinformation. “I am completely worried about a left-of-center administration … whose red-teaming tests will cause AI to constrain what it generates for fear of triggering these concerns,” he says.
Conservatives argue that any regulation that stifles AI innovation will cost the US dearly in the technology competition with China.
“They are so aggressive, and they have made dominating AI a core North Star of their strategy for how to fight and win wars,” Helberg says. “The gap between our capabilities and the Chinese keeps shrinking with every passing year.”
“Woke” Safety Standards
By including social harms in its AI security guidelines, NIST has outraged conservatives and set off another front in the culture war over content moderation and free speech.
Republicans decry the NIST guidance as a form of backdoor government censorship. Senator Ted Cruz recently slammed what he called NIST’s “woke AI ‘safety’ standards” for being part of a Biden administration “plan to control speech” based on “amorphous” social harms. NetChoice has warned NIST that it is exceeding its authority with quasi-regulatory guidelines that upset “the appropriate balance between transparency and free speech.”
Many conservatives flatly dismiss the idea that AI can perpetuate social harms and should be designed not to do so.
“This is a solution in search of a problem that really doesn't exist,” Helberg says. “There really hasn’t been massive evidence of issues in AI discrimination.”
Studies and investigations have repeatedly shown that AI models contain biases that perpetuate discrimination, including in hiring, policing, and health care. Research suggests that people who encounter these biases may unconsciously adopt them.
Conservatives worry more about AI companies’ overcorrections to this problem than about the problem itself. “There is a direct inverse correlation between the degree of wokeness in an AI and the AI's usefulness,” Helberg says, citing an early issue with Google’s generative AI platform.
Republicans want NIST to focus on AI’s physical safety risks, including its ability to help terrorists build bioweapons (something Biden’s EO does address). If Trump wins, his appointees will likely deemphasize government research on AI’s social harms. Helberg complains that the “enormous amount” of research on AI bias has dwarfed studies of “greater threats related to terrorism and biowarfare.”
Defending a “Light-Touch Approach”
AI experts and lawmakers offer robust defenses of Biden’s AI safety agenda.
These projects “enable the United States to remain on the cutting edge” of AI development “while protecting Americans from potential harms,” says Representative Ted Lieu, the Democratic cochair of the House’s AI task force.
The reporting requirements are essential for alerting the government to potentially dangerous new capabilities in increasingly powerful AI models, says a US government official who works on AI issues. The official, who requested anonymity to speak freely, points to OpenAI’s admission about its latest model’s “inconsistent refusal of requests to synthesize nerve agents.”
The official says the reporting requirement isn’t overly burdensome. They argue that, unlike AI regulations in the European Union and China, Biden’s EO reflects “a very broad, light-touch approach that continues to foster innovation.”
Nick Reese, who served as the Department of Homeland Security’s first director of emerging technology from 2019 to 2023, rejects conservative claims that the reporting requirement will jeopardize companies’ intellectual property. And he says it could actually benefit startups by encouraging them to develop “more computationally efficient,” less data-heavy AI models that fall under the reporting threshold.
AI’s power makes government oversight imperative, says Ami Fields-Meyer, who helped draft Biden’s EO as a White House tech official.
“We’re talking about companies that say they’re building the most powerful systems in the history of the world,” Fields-Meyer says. “The government’s first obligation is to protect people. ‘Trust me, we’ve got this’ is not an especially compelling argument.”
Experts praise NIST’s security guidance as a vital resource for building protections into new technology. They note that flawed AI models can produce serious social harms, including rental and lending discrimination and improper loss of government benefits.
Trump’s own first-term AI order required federal AI systems to respect civil rights, something that will require research into social harms.
The AI industry has largely welcomed Biden’s safety agenda. “What we're hearing is that it’s broadly useful to have this stuff spelled out,” the US official says. For new companies with small teams, “it expands the capacity of their folks to address these concerns.”
Rolling back Biden’s EO would send an alarming signal that “the US government is going to take a hands off approach to AI safety,” says Michael Daniel, a former presidential cyber adviser who now leads the Cyber Threat Alliance, an information sharing nonprofit.
As for competition with China, the EO’s defenders say safety rules will actually help America prevail by ensuring that US AI models work better than their Chinese rivals and are protected from Beijing’s economic espionage.
Two Very Different Paths
If Trump wins the White House next month, expect a sea change in how the government approaches AI safety.
Republicans want to prevent AI harms by applying “existing tort and statutory laws” as opposed to enacting broad new restrictions on the technology, Helberg says, and they favor “much greater focus on maximizing the opportunity afforded by AI, rather than overly focusing on risk mitigation.” That would likely spell doom for the reporting requirement and possibly some of the NIST guidance.
The reporting requirement could also face legal challenges now that the Supreme Court has weakened the deference that courts used to give agencies in evaluating their regulations.
And GOP pushback could even jeopardize NIST’s voluntary AI testing partnerships with leading companies. “What happens to those commitments in a new administration?” the US official asks.
This polarization around AI has frustrated technologists who worry that Trump will undermine the quest for safer models.
“Alongside the promises of AI are perils,” says Nicol Turner Lee, the director of the Brookings Institution’s Center for Technology Innovation, “and it is vital that the next president continue to ensure the safety and security of these systems.”
26 notes
·
View notes
Text
Health care

The Future of Health Care: Innovations and Challenges
Health care is an ever-evolving field that impacts every individual and society as a whole. With rapid technological advancements and shifting global health concerns, the future of health care holds promising opportunities as well as significant challenges. In this blog post, we will explore key innovations shaping the industry and the hurdles that need to be addressed to ensure accessible and high-quality health care for all.
Innovations Transforming Health Care
1. Telemedicine and Remote Patient Monitoring
Telemedicine has revolutionized how patients access medical care, especially in rural and underserved areas. Virtual consultations, remote monitoring devices, and AI-driven diagnostic tools allow doctors to provide timely and efficient care without requiring in-person visits. This trend is expected to continue growing, making health care more accessible and convenient.
2. Artificial Intelligence and Machine Learning
AI and machine learning are being integrated into health care to enhance diagnostics, streamline administrative tasks, and improve patient outcomes. Algorithms can detect diseases like cancer at early stages, predict patient deterioration, and even assist in drug discovery. These technologies help reduce human errors and improve overall efficiency in medical practice.
3. Personalized Medicine and Genomics
Advancements in genetic research have paved the way for personalized medicine, where treatments are tailored to an individual’s genetic makeup. This approach increases the effectiveness of treatments, reduces side effects, and improves patient care. Pharmacogenomics, a branch of personalized medicine, ensures that patients receive medications best suited for their genetic profile.
4. Wearable Health Tech
Wearable devices such as smartwatches and fitness trackers monitor vital signs, detect abnormalities, and encourage healthier lifestyles. These innovations empower individuals to take charge of their health while providing valuable data for doctors to assess long-term health trends.
Challenges in Health Care
1. Health Care Disparities
Despite advancements, disparities in health care access remain a critical issue. Many low-income and rural communities lack access to quality medical facilities, trained professionals, and essential medications. Bridging this gap requires investment in infrastructure, policies that promote equitable health care, and the expansion of telehealth services.
2. Rising Costs and Affordability
Health care costs continue to rise due to factors such as expensive treatments, administrative inefficiencies, and high pharmaceutical prices. Governments, insurance companies, and health care providers must collaborate to make medical care more affordable and sustainable for all.
3. Data Security and Privacy Concerns
With the increasing digitization of health records and AI-driven health solutions, data security is a growing concern. Cyberattacks on medical institutions can compromise sensitive patient information. Strengthening cybersecurity measures and establishing stricter data protection regulations are essential for maintaining patient trust and safety.
4. Aging Population and Chronic Diseases
The world’s aging population is placing additional strain on health care systems. Chronic diseases such as diabetes, heart disease, and dementia require long-term care and management. Investing in preventive care, promoting healthy lifestyles, and developing innovative treatment strategies are vital to addressing these challenges.
The Road Ahead
The future of health care depends on a balance between innovation and accessibility. Embracing new technologies, improving affordability, and addressing disparities will pave the way for a healthier global population. Collaboration between governments, medical professionals, and technology developers is crucial in creating a health care system that serves everyone efficiently and equitably.
As we move forward, the focus should remain on patient-centered care, ethical medical advancements, and ensuring that no one is left behind in the quest for better health care. With the right policies and innovations, the future of health care can be bright and promising for all.
2 notes
·
View notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
Understanding the Impact of Indian Army Defense Result on National Security
Indian Army Defense Result is performs a critical position in safeguarding a nation's sovereignty, security, and balance. It encompasses diverse techniques, technology, and military forces that work collectively to protect a country from external threats, such as army aggression, terrorism, and cyber-assaults. The outcome of a nicely-coordinated defense approach no longer simplest ensures countrywide safety but also strengthens a country’s impact on the worldwide stage.

Military Defense
One of the important thing components of defense is the military. Armed forces, which include the military, military, air force, and once in a while specialised gadgets like area and cyber commands, are liable for protecting the u . S . In opposition to physical threats. The effectiveness of a kingdom's army depends on its stage of schooling, get right of entry to to trendy technology, and universal preparedness. Strong navy abilties act as a deterrent towards potential adversaries, decreasing the probability of conflict. In instances of warfare or disaster, a nicely-prepared military can quickly mobilize to shield country wide pastimes, stable borders, and protect citizens.
Technological and Cyber Defense
In today’s digital age, defense additionally closely is based on superior technology. Innovations which includes artificial intelligence (AI), unmanned aerial cars (UAVs), and missile protection structures have transformed modern warfare. A nation’s ability to broaden, collect, and combine those technologies into its protection apparatus can considerably effect its safety consequences. Cyber protection has emerged as an crucial element of countrywide safety as well. With increasing cyber threats from both country and non-kingdom actors, protecting essential infrastructure and touchy statistics is paramount. A a hit cyber defense strategy prevents espionage, hacking, and other cyberattacks that would disrupt authorities operations or damage important structures.
Diplomatic and Economic Defense
Beyond the battlefield, protection techniques additionally embody diplomacy and monetary safety. Building robust alliances through international relations enables in collective defense efforts, including NATO, in which member states pledge to shield each other. Economic electricity also contributes to country wide protection through making sure good enough investment for defense tasks and retaining resilience in opposition to sanctions or monetary battle.

Result of Effective Defense
Defense Result Army is powerful protection system not only protects a country’s borders however also complements its international status. A strong and adaptive protection infrastructure guarantees peace, deters capability threats, and permits a nation to task power responsibly on the worldwide stage.
2 notes
·
View notes
Text
How Can You Ensure Data Quality in Healthcare Analytics and Management?

Healthcare facilities are responsible for the patient’s recovery. Pharmaceutical companies and medical equipment manufacturers also work toward alleviating physical pain, stress levels, and uncomfortable body movement issues. Still, healthcare analytics must be accurate for precise diagnosis and effective clinical prescriptions. This post will discuss data quality management in the healthcare industry.
What is Data Quality in Healthcare?
Healthcare data quality management includes technologies and statistical solutions to verify the reliability of acquired clinical intelligence. A data quality manager protects databases from digital corruption, cyberattacks, and inappropriate handling. So, medical professionals can get more realistic insights using data analytics solutions.
Laboratories have started emailing the test results to help doctors, patients, and their family members make important decisions without wasting time. Also, assistive technologies merge the benefits of the Internet of Things (IoT) and artificial intelligence (AI) to enhance living standards.
However, poor data quality threatens the usefulness of healthcare data management solutions.
For example, pharmaceutical companies and authorities must apply solutions that remove mathematical outliers to perform high-precision data analytics for clinical drug trials. Otherwise, harmful medicines will reach the pharmacist’s shelf, endangering many people.
How to Ensure Data Quality in the Healthcare Industry?
Data quality frameworks utilize different strategies to prevent processing issues or losing sensitive intelligence. If you want to develop such frameworks to improve medical intelligence and reporting, the following 7 methods can aid you in this endeavor.
Method #1| Use Data Profiling
A data profiling method involves estimating the relationship between the different records in a database to find gaps and devise a cleansing strategy. Data cleansing in healthcare data management solutions has the following objectives.
Determine whether the lab reports and prescriptions match the correct patient identifiers.
If inconsistent profile matching has occurred, fix it by contacting doctors and patients.
Analyze the data structures and authorization levels to evaluate how each employee is accountable for specific patient recovery outcomes.
Create a data governance framework to enforce access and data modification rights strictly.
Identify recurring data cleaning and preparation challenges.
Brainstorm ideas to minimize data collection issues that increase your data cleaning efforts.
Ensure consistency in report formatting and recovery measurement techniques to improve data quality in healthcare.
Data cleaning and profiling allow you to eliminate unnecessary and inaccurate entries from patient databases. Therefore, healthcare research institutes and commercial life science businesses can reduce processing errors when using data analytics solutions.
Method #2| Replace Empty Values
What is a null value? Null values mean the database has no data corresponding to a field in a record. Moreover, these missing values can skew the results obtained by data management solutions used in the healthcare industry.
Consider that a patient left a form field empty. If all the care and life science businesses use online data collection surveys, they can warn the patients about the empty values. This approach relies on the “prevention is better than cure” principle.
Still, many institutions, ranging from multispecialty hospitals to clinical device producers, record data offline. Later, the data entry officers transform the filled papers using scanners and OCR (optical character recognition).
Empty fields also appear in the database management system (DBMS), so the healthcare facilities must contact the patients or reporting doctors to retrieve the missing information. They use newly acquired data to replace the null values, making the analytics solutions operate seamlessly.
Method #3| Refresh Old Records
Your physical and psychological attributes change with age, environment, lifestyle, and family circumstances. So, what was true for an individual a few years ago is less likely to be relevant today. While preserving historical patient databases is vital, hospitals and pharma businesses must periodically update obsolete medical reports.
Each healthcare business maintains a professional network of consulting physicians, laboratories, chemists, dietitians, and counselors. These connections enable the treatment providers to strategically conduct regular tests to check how patients’ bodily functions change throughout the recovery.
Therefore, updating old records in a patient’s medical history becomes possible. Other variables like switching jobs or traveling habits also impact an individual’s metabolism and susceptibility to illnesses. So, you must also ask the patients to share the latest data on their changed lifestyles. Freshly obtained records increase the relevance of healthcare data management solutions.
Method #4| Standardize Documentation
Standardization compels all professionals to collect, store, visualize, and communicate data or analytics activities using unified reporting solutions. Furthermore, standardized reports are integral to improving data governance compliance in the healthcare industry.
Consider the following principles when promoting a documentation protocol to make all reports more consistent and easily traceable.
A brand’s visual identities, like logos and colors, must not interfere with clinical data presentation.
Observed readings must go in the designated fields.
Both the offline and online document formats must be identical.
Stakeholders must permanently preserve an archived copy of patient databases with version control as they edit and delete values from the records.
All medical reports must arrange the data and insights to prevent ambiguity and misinterpretation.
Pharma companies, clinics, and FDA (food and drug administration) benefit from reporting standards. After all, corresponding protocols encourage responsible attitudes that help data analytics solutions avoid processing problems.
Method #5| Merge Duplicate Report Instances
A report instance is like a screenshot that helps you save the output of visualization tools related to a business query at a specified time interval. However, duplicate reporting instances are a significant quality assurance challenge in healthcare data management solutions.
For example, more than two nurses and one doctor will interact with the same patients. Besides, patients might consult different doctors and get two or more treatments for distinct illnesses. Such situations result in multiple versions of a patient’s clinical history.
Data analytics solutions can process the data collected by different healthcare facilities to solve the issue of duplicate report instances in the patients’ databases. They facilitate merging overlapping records and matching each patient with a universally valid clinical history profile.
Such a strategy also assists clinicians in monitoring how other healthcare professionals prescribe medicine to a patient. Therefore, they can prevent double dosage complications arising from a patient consuming similar medicines while undergoing more than one treatment regime.
Method #6| Audit the DBMS and Reporting Modules
Chemical laboratories revise their reporting practices when newly purchased testing equipment offers additional features. Likewise, DBMS solutions optimized for healthcare data management must receive regular updates.
Auditing the present status of reporting practices will give you insights into efficient and inefficient activities. Remember, there is always a better way to collect and record data. Monitor the trends in database technologies to ensure continuous enhancements in healthcare data quality.
Simultaneously, you want to assess the stability of the IT systems because unreliable infrastructure can adversely affect the decision-making associated with patient diagnosis. You can start by asking the following questions.
Questions to Ask When Assessing Data Quality in Healthcare Analytics Solutions
Can all doctors, nurses, agents, insurance representatives, patients, and each patient’s family members access the required data without problems?
How often do the servers and internet connectivity stop functioning correctly?
Are there sufficient backup tools to restore the system if something goes wrong?
Do hospitals, research facilities, and pharmaceutical companies employ end-to-end encryption (E2EE) across all electronic communications?
Are there new technologies facilitating accelerated report creation?
Will the patient databases be vulnerable to cyberattacks and manipulation?
Are the clinical history records sufficient for a robust diagnosis?
Can the patients collect the documents required to claim healthcare insurance benefits without encountering uncomfortable experiences?
Is the presently implemented authorization framework sufficient to ensure data governance in healthcare?
Has the FDA approved any of your prescribed medications?
Method #7| Conduct Skill Development Sessions for the Employees
Healthcare data management solutions rely on advanced technologies, and some employees need more guidance to use them effectively. Pharma companies are aware of this as well, because maintaining and modifying the chemical reactions involved in drug manufacturing will necessitate specialized knowledge.
Different training programs can assist the nursing staff and healthcare practitioners in developing the skills necessary to handle advanced data analytics solutions. Moreover, some consulting firms might offer simplified educational initiatives to help hospitals and nursing homes increase the skill levels of employees.
Cooperation between employees, leadership, and public authorities is indispensable to ensure data quality in the healthcare and life science industries. Otherwise, a lack of coordination hinders the modernization trends in the respective sectors.
Conclusion
Healthcare analytics depends on many techniques to improve data quality. For example, cleaning datasets to eliminate obsolete records, null values, or duplicate report instances remains essential, and multispecialty hospitals agree with this concept.
Therefore, medical professionals invest heavily in standardized documents and employee education to enhance data governance. Also, you want to prevent cyberattacks and data corruption. Consider consulting reputable firms to audit your data operations and make clinical trials more reliable.
SG Analytics is a leader in healthcare data management solutions, delivering scalable insight discovery capabilities for adverse event monitoring and medical intelligence. Contact us today if you want healthcare market research and patent tracking assistance.
3 notes
·
View notes
Text
The Future of Finance: How Fintech Is Winning the Cybersecurity Race

In the cyber age, the financial world has been reshaped by fintech's relentless innovation. Mobile banking apps grant us access to our financial lives at our fingertips, and online investment platforms have revolutionised wealth management. Yet, beneath this veneer of convenience and accessibility lies an ominous spectre — the looming threat of cyberattacks on the financial sector. The number of cyberattacks is expected to increase by 50% in 2023. The global fintech market is expected to reach $324 billion by 2028, growing at a CAGR of 25.2% from 2023 to 2028. This growth of the fintech market makes it even more prone to cyber-attacks. To prevent this there are certain measures and innovations let's find out more about them
Cybersecurity Measures in Fintech
To mitigate the ever-present threat of cyberattacks, fintech companies employ a multifaceted approach to cybersecurity problems and solutions. Here are some key measures:
1. Encryption
Encrypting data at rest and in transit is fundamental to protecting sensitive information. Strong encryption algorithms ensure that even if a hacker gains access to data, it remains unreadable without the decryption keys.
2. Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of verification (e.g., passwords, fingerprints, or security tokens) before gaining access to their accounts.
3. Continuous Monitoring
Fintech companies employ advanced monitoring systems that constantly assess network traffic for suspicious activities. This allows for real-time threat detection and rapid response.
4. Penetration Testing
Regular penetration testing, performed by ethical hackers, helps identify vulnerabilities in systems and applications before malicious actors can exploit them.
5. Employee Training
Human error is a significant factor in cybersecurity breaches. Companies invest in cybersecurity training programs to educate employees about best practices and the risks associated with cyber threats.
6. Incident Response Plans
Having a well-defined incident response plan in place ensures that, in the event of a breach, the company can respond swiftly and effectively to mitigate the damage.
Emerging Technologies in Fintech Cybersecurity
As cyber threats continue to evolve, so do cybersecurity technologies in fintech. Here are some emerging technologies that are making a significant impact:
1. Artificial Intelligence (AI)
AI and machine learning algorithms are used to analyse vast amounts of data and identify patterns indicative of cyber threats. This allows for proactive threat detection and quicker response times.
2. Blockchain
Blockchain technology is employed to enhance the security and transparency of financial transactions. It ensures that transaction records are immutable and cannot be altered by malicious actors.
3. Biometrics
Fintech companies are increasingly adopting biometric authentication methods, such as facial recognition and fingerprint scanning, to provide a higher level of security than traditional passwords.
4. Quantum-Safe Encryption
With the advent of quantum computing, which poses a threat to current encryption methods, fintech companies are exploring quantum-safe encryption techniques to future-proof their security measures.
Conclusion
In the realm of fintech, where trust and security are paramount, the importance of cybersecurity cannot be overstated. Fintech companies must remain vigilant, employing a combination of advanced digital transformation solutions, employee training, and robust incident response plans to protect sensitive financial data from cyber threats. As the industry continues to evolve, staying one step ahead of cybercriminals will be an ongoing challenge, but one that fintech firms must embrace to ensure their continued success and the safety of their customers' financial well-being.
3 notes
·
View notes
Text
Decoding Cybersecurity: Unveiling the Future of US Digital Forensics Excellence
What is the Size of US Digital forensics Industry?
US Digital forensics Market is expected to grow at a CAGR of ~% between 2022-2028 and is expected to reach ~USD Mn by 2028.
Escalating cyberattacks targeting individuals, organizations, and critical infrastructure underscore the need for robust digital forensics capabilities. The increasing frequency and sophistication of these attacks drive the demand for advanced tools and expertise to investigate and respond effectively.
Rapid technological advancements, including IoT, cloud computing, AI, and blockchain, introduce new avenues for cyber threats. Digital forensics services are crucial to understanding these emerging technologies' vulnerabilities and mitigating associated risks.
Furthermore, stricter data protection regulations and compliance mandates necessitate thorough digital evidence collection, preservation, and analysis.
Organizations across industries has invested in digital forensics to ensure adherence to legal requirements and regulatory frameworks.
Additionally Legal proceedings increasingly rely on digital evidence. Law enforcement, legal firms, and corporations require robust digital forensics services to gather, analyze, and present evidence in a court of law, driving market expansion.
Us Digital Forensics Market By Type
The US Digital forensics market is segmented by Computer Forensics, Network Forensics, Mobile Device forensics and Cloud forensics. Based on type, Computer Forensics type segment is emerged as the dominant segment in US Digital forensics market in 2022.
Computers are ubiquitous in modern society, utilized across industries, organizations, and households. As a result, a significant portion of digital evidence related to cybercrimes and incidents is generated from computer systems, driving the demand for specialized computer forensics expertise. Computers and their software environments evolve rapidly.
Us Digital Forensics Market By End User Application
US Digital forensics market is segmented by Government and Defence, BFSI, Telecom and IT, Retail, Healthcare and Other Government and Defence market is dominant in end user application segment in Digital forensics market in 2022.
Government and defense agencies handle highly sensitive information related to national security and intelligence. The increasing sophistication of cyber threats targeting these entities necessitates robust digital forensics capabilities to investigate and respond to cyber incidents effectively.
Government and defense entities are prime targets for cyberattacks due to their critical roles. Effective incident response through digital forensics helps in containing and mitigating cyber incidents swiftly, minimizing damage and preventing further breaches.
US Digital forensics by Region
The US Digital forensics market is segmented by Region into North, East, West, South. In 2022, the dominance region is East region in US Digital forensics market.
The East region has a dense population and a well-established digital infrastructure, making it a hotspot for cybercriminal activity. The higher frequency of cyber threats and incidents necessitates a strong emphasis on digital forensics to investigate and mitigate these risks effectively. Additionally, the East region often sees a proactive approach from regulatory and legal bodies, reinforcing the demand for digital forensics services to ensure compliance and assist in investigations. The proximity of key players in law enforcement, government agencies, legal firms, and corporate headquarters further fuels the need for robust digital forensics capabilities.
Download a Sample Report of US digital forensics Solution Market
Competition Scenario in US Digital forensics Market
The US digital forensics market is characterized by a competitive landscape with several key players competing for market share. Prominent companies offering a range of digital forensics solutions and services contribute to the market's dynamism.
The competitive landscape also includes smaller, specialized firms and start-ups that focus on niche areas of digital forensics, such as cloud forensics, memory forensics, and industrial control systems forensics.
The competition is further intensified by the continuous evolution of technology, leading to the emergence of new players and innovative solutions. As the demand for digital forensics continues to grow, companies in this market are likely to invest in research and development to stay ahead of the curve, leading to a consistently competitive environment.
What is the Expected Future Outlook for the Overall US Digital forensics Market?
Download a Custom Report of US digital forensics market Growth
The US Digital forensics market was valued at USD ~Million in 2022 and is anticipated to reach USD ~ Million by the end of 2028, witnessing a CAGR of ~% during the forecast period 2022- 2028.
The US digital forensics market is poised for robust expansion due to the ever-evolving cybersecurity landscape, technological advancements, and regulatory pressures. Organizations across industries will increasingly recognize the necessity of investing in digital forensics to safeguard their digital assets and ensure compliance.
As long as cyber threats continue to evolve, the demand for sophisticated digital forensic tools, services, and expertise will remain on an upward trajectory.
The US digital forensics market appears promising, characterized by a confluence of technological advancements, increasing cyber threats, and growing legal and regulatory requirements. As technology continues to evolve rapidly, so does the nature of cybercrimes, creating a persistent demand for digital forensics solutions and services.
Additionally, the escalating frequency and complexity of cyberattacks. As more critical operations and personal information are digitized, the potential attack surface expands, leading to a higher likelihood of security breaches. This dynamic compels organizations and law enforcement agencies to enhance their digital forensic capabilities to investigate, mitigate, and prevent cyber incidents effectively.
Furthermore, the rise of emerging technologies like the Internet of Things (IoT), artificial intelligence (AI), and blockchain presents both opportunities and challenges. These technologies bring new possibilities for efficiency and connectivity but also introduce novel avenues for cyber threats. Consequently, the demand for digital forensics services is expected to surge as organizations seek expertise in unraveling incidents involving these cutting-edge technologies.
The market is also likely to see increased adoption of cloud-based digital forensics solutions. As more data is stored and processed in the cloud, digital forensic providers will need to develop tools and methodologies to effectively gather evidence from virtual environments, remote servers, and distributed systems.
2 notes
·
View notes
Text
A silent ally of the ongoing energy transition
Key insights by the founder of TELF AG, Stanislav Kondrashov
We are living through a major energy transition. One innovation often overlooked is the Smart Grid. These intelligent electricity networks are already helping future energy sources spread. They do so in a way that is both sustainable and efficient. In the coming years, Smart Grids could take center stage. They may become key players in shaping the future of global energy.
Exploring the role of smart grids in the ongoing energy transition
Many people still don’t know much about smart grids. That’s not surprising. The energy transition is still new. We’re only beginning to adjust to it. Some parts of this change are rarely talked about. Yet, they’re fascinating and deserve more attention.
“Smart grids could become vital partners in the global energy shift,” says Stanislav Kondrashov, founder of TELF AG and civil engineer. “These systems do more than move power. They improve efficiency, reduce energy waste, and cut losses across the grid. They also work well with solar, hydro, and other renewable sources.”
But what exactly is a smart grid? It’s an advanced electrical network. Unlike the old systems, it uses digital tools, AI, and sensors. These tools help manage energy in real-time. They make the grid more interactive and flexible. Smart grids can adjust to demand and respond fast to changes. That makes them key to a cleaner future.
Exploring the evolving role of smart grids in the energy transition
Old power networks had one job. They moved electricity from plants to homes. That was it. Smart grids work very differently. They don’t just deliver power — they also monitor it. These systems track supply and demand in real-time. They talk directly to users and adjust based on need. This saves energy and cuts waste. Most of all, it changes how people use electricity. It turns passive users into active participants.
Challenges to overcome
“Smart grids have huge potential, but they’re still developing,” says Stanislav Kondrashov, founder of TELF AG. “Many issues need to be solved. High costs are one. Building new infrastructure and going fully digital is expensive. Managing the system is also complex. And then there’s the risk of cyberattacks. A digital grid can be vulnerable. Still, I believe we can handle these problems. As technology improves, so will our solutions. With time, most of these hurdles will become easier to overcome.”
Exploring the role and modern importance of smart grids
Some of the most interesting parts of smart grids come from how they differ from old power networks. Traditional grids are simple and one-way. Energy flows in a straight line—from the power plant to the user. There’s no feedback, no adjustment, and no flexibility in real-time.
Smart grids work differently. They support two-way communication. Energy and data move both ways. This makes the system far more dynamic. It can respond to sudden demand, dips in supply, or even faults and outages—instantly. That flexibility keeps things running smoothly.
What makes them even more powerful is consumer involvement. People are no longer passive users. They become part of the process. With smart meters and energy apps, users can track their power in real-time. They can cut waste, shift usage, and even send energy back to the grid. It creates a smarter, cleaner, and more efficient energy system for everyone.
Exploring the strategic role of smart grids in the ongoing energy transition
A strategic role
“We are going through a big energy change,” says Stanislav Kondrashov, founder of TELF AG. “In this shift, smart grids can play a key role. They help communities use renewable energy better. They improve output and reduce waste. They also stop overloads caused by electric vehicles and high demand.” As pressure grows, smart grids react fast. They move energy, balance loads, and prevent blackouts. These systems change how power works. Instead of one source, energy flows from many places. It goes both ways. That makes the grid flexible, modern, and ready for the future we all rely on.
In this phase of development, smart grids include three main parts:
Smart meters – They measure how much electricity is used. They send that data right away. This helps people track and manage their energy better.
Advanced sensors – These find problems fast. If something goes wrong, they alert the system. This helps prevent big issues and keeps the grid safe. AI-based software – It uses smart tools like machine learning. It controls how energy moves. This cuts waste and keeps supply and demand balanced.
Alongside core tools, smart grids also include:
Energy storage systems – These store extra power. They help the grid stay balanced during peak use or when renewables drop.
Automation systems – These manage outages and restarts. They act fast and reduce delays.
Because these networks are so advanced, many countries are now testing them. Trials are active in China, the United States, Japan, South Korea, and parts of Europe. These tests help shape how smart grids will be used in the future.
People Also Ask
What is a Smart Grid?
A smart grid is a modern power network. It uses digital tools to monitor how electricity is made, shared, and used in real-time. Unlike old systems, it allows two-way communication between energy producers and users. This helps balance supply and demand, reduce waste, and support clean energy. It’s smarter, faster, and better for the future.
How do they differ from traditional power grids?
Old power grids are simple and one-way. Energy flows from plants to homes with no real control. Smart grids are different. They are fast, flexible, and reactive. They use sensors, AI, and smart meters to track usage. They fix issues before they grow. This helps manage renewables like wind and solar. It also cuts energy waste and boosts efficiency.
Why are grids important for the energy transition?
The world is moving toward cleaner energy. But sources like solar and wind are not always steady. The sun doesn’t always shine. The wind doesn’t always blow. That’s why we need systems that can adapt. Smart grids store extra power and release it when needed. This flexible flow is key as more renewables come into the energy mix.
How do they support renewable energy?
Smart grids are built to work with renewable energy. They connect easily with solar panels, wind turbines, and other small sources. These systems send extra energy back into the grid. Storage units save unused power for later. They also support “prosumers”—people who make their energy. This boosts efficiency and makes the whole network stronger and smarter.
What are the benefits for consumers?
Smart grids give control back to the user. With smart meters, people can see how much power they use in real-time. This helps them spot waste and change habits to save money. Some homes can even sell extra energy back to the grid. Users are no longer passive. They play an active role in how energy flows.
What are the main components of this technology?
Key parts of a smart grid include:
Smart meters – They measure power use. They send live data to both users and operators.
Advanced sensors – These spot problems fast. They find faults or strange activity in the system.
AI systems – They guide how power moves. They help keep things steady and efficient.
Storage units – These save extra power. They help balance the grid during peak or low times.
Automation tools – They fix outages fast. They restart systems without human help.
Together, these tools keep the grid strong, smart, and ready for change.
Are they already being used?
Yes, these smart systems are already in use. Countries like the United States, China, Japan, South Korea, and many in Europe are leading the way. Rollouts are still in the early stages, but results look strong. Tests show better energy savings, faster outage fixes, and smoother use of renewable power. As adoption grows, the impact will grow with it.
What challenges do they face?
Even with great promise, smart grids still face a few big hurdles:
High costs – Updating old grids needs a lot of money for new parts and software.
Cyber risks – More digital links make the system easier to attack.
Complex setup – Running a digital grid takes smart tools and trained people.
Slow laws – In many places, rules don’t match the speed of new tech.
But the good news? New ideas and stronger support from leaders are helping to fix these issues—step by step.
How can they prevent blackouts and network overloads?
Smart grids can spot energy spikes before they happen. They use real-time data and smart forecasts to stay ahead. When demand jumps, they respond fast. They can reroute power, tap into storage, or send signals to lower usage. This keeps the system stable. It matters more now, as electric cars and home energy tech add pressure to the grid.
What is the role of Smart Grids in energy communities?
Energy communities are local groups that make and share their own clean power. Smart grids help these groups in many ways. They support energy trading between neighbors. They also cut power loss and make local systems stronger. These grids link small energy sources in one area. That helps local networks run better. It also makes them more flexible and self-reliant.
What does the future look like for Smart Grids?
Energy use is rising fast. At the same time, renewables are becoming a must. That’s where smart grids come in. They help systems stay flexible. They cut carbon and give users more control. These tools may be quiet, but they are key. They support the shift to a cleaner, safer, and stronger energy future.
0 notes
Text
Why Should Governments Give Blockchain and AI Policy Development Top Priority?

The creation of AI and blockchain policies has become not only pertinent but also crucial for governments all over the world in the age of digital transformation. Lack of defined legislative frameworks might result in inefficiencies, misuse, and growing inequality as blockchain and artificial intelligence technologies develop quickly. Governments will have an advantage in governance, economic growth, and international influence if they are proactive in developing regulations around these disruptive technologies.
Maintaining Public Trust and Ethical Use
Unchecked AI systems have the potential to breach privacy, propagate bias, and lead to moral quandaries. Notwithstanding its advantages in terms of security and transparency, blockchain can also be abused for illegal purposes in the absence of adequate regulation. Strong AI and blockchain regulations assist governments in establishing guidelines that guarantee moral application, boost responsibility, and promote public confidence in cutting-edge technologies.
Promoting Innovation When Handling Hazards
Governments may promote responsible innovation by investing in careful policymaking. Knowing that the risks are controlled and innovation is encouraged, companies, researchers, and private sector investment can be drawn to areas with clear regulations surrounding AI and blockchain. In addition to promoting economic progress, such a framework keeps innovation from becoming an unchecked force with unforeseen repercussions.
Strengthening Data Sovereignty and National Security
Cyberattacks powered by AI and illegal financial flows made possible by blockchain present significant risks to national security. Governments can secure digital infrastructures, protect sensitive data, and prevent hostile actors from using vital technology as weapons by giving AI and blockchain policy top priority.
Enhancing Governance and Public Services
Better decision-making, fraud detection, and transparent citizen services are just a few of the ways that AI plus blockchain could revolutionize public administration. Predictive analytics, decentralized ID systems, and smart contracts can simplify everything from tax collection to welfare distribution. However, governments require robust AI and blockchain policy frameworks that establish norms, safeguard individuals, and direct implementations in order to use these tools responsibly.
At the forefront of the global digital economy
The global digital future will be shaped by the nations that take the lead in establishing international rules and standards for blockchain and artificial intelligence. Innovative policies that support global human rights, economic interests, and technical advancements are necessary for this strategic leadership.
In conclusion
Blockchain and artificial intelligence are here to stay, and their impact on the economy, society, and governance will only increase. In order to maintain national competitiveness in a digital environment, promote ethical use, and strike a balance between innovation and oversight, governments must take the lead in developing comprehensive AI and blockchain regulatory frameworks. Setting policy development as a top priority is required, not optional.
0 notes
Text
Advanced AI Ethical Hacking Course: The Future of Cybersecurity

Cybersecurity is evolving rapidly in the face of increasingly sophisticated cyber threats. Traditional methods of protecting systems and networks are insufficient, as attackers leverage artificial intelligence to breach defenses. To counteract these threats, the Advanced AI Ethical Hacking Course equips professionals with the skills and tools to protect digital infrastructures using cutting-edge AI technologies.
This guide explores the intricacies of this advanced course, including why it’s essential, its detailed curriculum, the tools you’ll master, and how it prepares you for a lucrative career in cybersecurity.
Why AI is Transforming Cybersecurity
AI has fundamentally reshaped the cybersecurity landscape. It empowers ethical hackers to automate routine tasks, identify vulnerabilities faster, and predict potential threats. However, cybercriminals have also weaponized AI, making traditional security measures inadequate.
In 2024 alone, AI-enhanced cyberattacks accounted for over 50% of global cyber incidents. As AI grows more sophisticated, its attacks and defense applications will continue to expand. The Advanced AI Ethical Hacking Course prepares professionals to meet these challenges by teaching them to harness AI’s potential for good.
How the Advanced AI Ethical Hacking Course Prepares You
This course offers a unique blend of cybersecurity principles and AI-driven methodologies. It enables participants to:
Understand AI Integration: Learn how AI enhances ethical hacking techniques to counteract advanced threats.
Develop AI Models: Build and train machine learning models for intrusion detection, malware analysis, and more.
Simulate Cyberattacks: Create realistic attack scenarios using AI to test system vulnerabilities effectively.
Automate Security Processes: Use AI to streamline vulnerability assessment and penetration testing tasks.
The result? A highly skilled professional capable of staying ahead of cybercriminals in an ever-evolving digital world.
Course Curriculum: A Deep Dive
The curriculum of the Advanced AI Ethical Hacking Course is designed to ensure participants gain comprehensive knowledge and practical experience. Below are the core modules and their components:
Module 1: Foundations of AI in Cybersecurity
The role of AI in modern cybersecurity.
Basics of machine learning, neural networks, and data analysis.
Overview of ethical hacking frameworks and their integration with AI tools.
Module 2: AI-Driven Threat Detection
Leveraging AI for real-time threat identification and mitigation.
Building models to detect anomalies in network traffic.
Case studies: Successful applications of AI in cybersecurity.
Module 3: Penetration Testing with AI
Automating reconnaissance and exploiting vulnerabilities.
Using AI-enhanced tools for penetration testing.
Hands-on labs: Conducting simulated attacks using AI algorithms.
Module 4: Adversarial AI and Countermeasures
Understanding adversarial AI attacks.
Techniques to protect AI systems from manipulation.
Building robust defenses against AI-driven cyber threats.
Module 5: Malware Analysis and Prevention
Identifying malware using AI classifiers.
Training deep learning models to recognize ransomware and trojans.
Practical labs: Reverse engineering malware with AI tools.
Module 6: Capstone Project
A real-world simulation of AI-driven penetration testing.
Presenting findings and proposing actionable cybersecurity strategies.
This structured learning pathway ensures that every participant leaves the course with advanced skills and a robust understanding of AI-powered ethical hacking.
Tools You’ll Master
One of the highlights of the Advanced AI Ethical Hacking Course is its hands-on approach to learning. Participants gain proficiency in the following tools:
TensorFlow and PyTorch: For building machine learning models used in threat detection and analysis.
Metasploit AI: Enhances traditional penetration testing capabilities with AI-driven insights.
Kali Linux with AI Add-ons: A complete suite of tools for AI-enhanced ethical hacking.
Snort AI: Combines real-time intrusion detection with machine learning.
IBM Watson for Cybersecurity: Uses natural language processing to identify and mitigate threats.
Mastering these tools ensures participants can tackle real-world challenges effectively.
Real-World Applications of AI Ethical Hacking
The practical skills gained from an Advanced AI Ethical Hacking Course translate into diverse real-world applications, including:
Corporate Security Testing: AI-powered penetration tests simulate sophisticated attacks to expose and fix vulnerabilities in corporate networks.
Government Cybersecurity: Protect critical infrastructure and sensitive data from nation-state actors using AI-enhanced defenses.
IoT Device Protection: With billions of IoT devices connected worldwide, AI helps safeguard these devices from exploitation.
Financial Systems Security: AI detects and mitigates fraudulent transactions and secures payment gateways.
Healthcare Cybersecurity: Protect patient data and medical devices from ransomware and unauthorized access.
Career Opportunities After Completing the Course
Graduates of the Advanced AI Ethical Hacking Course are highly sought after across industries. Here are some roles you can pursue:
1. AI Cybersecurity Analyst
Monitor and protect systems using AI tools, ensuring real-time threat mitigation.
2. AI Penetration Tester
Specialize in using AI to find and exploit vulnerabilities in systems and networks.
3. Adversarial AI Researcher
Focus on developing defenses against malicious uses of AI.
4. Cyber Threat Intelligence Specialist
Analyze trends, predict future attacks, and develop strategies using AI.
5. Automation Security Engineer
Automate repetitive security tasks with AI to improve efficiency.
6. AI Cybersecurity Consultant
Advise organizations on implementing AI-driven solutions to enhance their security frameworks.
Ethical Challenges in AI Ethical Hacking
While AI is a powerful tool, it also introduces ethical challenges that every professional must address:
Dual-Use Technology: AI can be used for both good and malicious purposes. Ethical hackers must ensure their work adheres to legal and ethical standards.
Privacy Concerns: AI’s ability to process vast amounts of data raises questions about user privacy.
Bias in AI Models: Ethical hackers must ensure AI systems are trained on diverse datasets to avoid biased decision-making.
Accountability: Determining responsibility when an AI system causes unintended harm remains a gray area.
Addressing these challenges is a key component of the Advanced AI Ethical Hacking Course, ensuring professionals use AI responsibly.
Certifications to Supplement the Advanced AI Ethical Hacking Course
After completing the Advanced AI Ethical Hacking Course, earning certifications can significantly boost your career prospects. Below is a detailed list of top certifications, including their focus areas and direct links to explore them:
1. AI+ Ethical Hacker (AI CERTs)
This certification focuses on equipping ethical hackers with AI-based tools and techniques to counteract advanced cyber threats. It emphasizes practical applications like AI-driven penetration testing and adversarial defense strategies.
Key Highlights:
AI in threat detection and malware analysis.
Adversarial AI and countermeasures.
Real-world applications in cybersecurity.
Who Should Pursue This? Professionals who want to specialize in integrating AI with ethical hacking.
👉 Learn more
2. Certified Information Systems Security Professional (CISSP)
Offered by (ISC)², the CISSP certification is globally recognized as a standard for information security expertise. It covers eight domains, including AI-driven cybersecurity strategies.
Key Highlights:
Covers access control, cryptography, and AI in cybersecurity.
Emphasizes risk management and advanced security practices.
Validates expertise in designing and managing security systems.
Who Should Pursue This? Mid-level and senior professionals aiming for leadership roles in cybersecurity.
👉 Learn more
3. Offensive Security Certified Professional (OSCP)
This hands-on certification from Offensive Security focuses on practical penetration testing skills. Its AI-integrated modules allow professionals to test AI-enhanced defenses effectively.
Key Highlights:
Real-world penetration testing scenarios.
Hands-on labs with AI-enhanced tools.
Training on exploiting vulnerabilities in AI-powered systems.
Who Should Pursue This? Ethical hackers looking to demonstrate their technical prowess in AI-based and traditional systems.
👉 Learn more
4. AI in Cybersecurity Certificate (Stanford Online)
This program offers a deep dive into how AI can be leveraged in cybersecurity. It includes case studies and hands-on projects using AI for real-time threat detection.
Key Highlights:
Covers AI models for network security and malware detection.
Explores ethical challenges in AI applications.
Hands-on experience with AI algorithms and cybersecurity frameworks.
Who Should Pursue This? Professionals interested in the academic and technical aspects of AI-driven cybersecurity.
👉 Learn more
5. Certified Adversarial AI Specialist (CAAS)
This niche certification focuses on adversarial AI, teaching professionals to identify and mitigate attacks designed to exploit AI systems.
Key Highlights:
Techniques to protect against adversarial AI attacks.
Developing robust AI systems immune to manipulation
Comprehensive training in AI-specific security protocols.
Who Should Pursue This? Those specializing in securing AI systems and applications from emerging threats.
👉 Learn more
Why Certifications Matter
Earning certifications validates your skills and enhances your professional credibility. They are essential for standing out in the competitive field of AI-driven ethical hacking. Each certification offers a unique value proposition, helping you tailor your career to your interests and expertise.
These certifications not only complement the Advanced AI Ethical Hacking Course but also open doors to leadership roles and lucrative career opportunities in cybersecurity.
How to Get Started
Enrolling in the Advanced AI Ethical Hacking Course is a straightforward process:
Research the best platforms offering the course.
Choose a program that aligns with your goals and budget.
Prepare by brushing up on fundamental cybersecurity and AI concepts.
Dedicate time to practice hands-on labs and projects.
Conclusion
The Advanced AI Ethical Hacking Course is more than just a training program, it’s an investment in your future. By mastering AI-driven ethical hacking techniques, you position yourself at the forefront of a rapidly evolving field, ready to tackle the most sophisticated cyber threats.
Leap today and secure your place in the future of cybersecurity. The world needs ethical hackers armed with AI expertise, and the Advanced AI Ethical Hacking Course is your gateway to making a meaningful impact.
0 notes
Text
What Makes EDSPL’s SOC the Nerve Center of 24x7 Cyber Defense?

Introduction: The New Reality of Cyber Defense
We live in an age where cyberattacks aren’t rare—they're expected. Ransomware can lock up entire organizations overnight. Phishing emails mimic internal communications with eerie accuracy. Insider threats now pose as much danger as external hackers. And all this happens while your teams are working, sleeping, or enjoying a weekend away from the office.
In such an environment, your business needs a Security Operations Center (SOC) that doesn’t just detect cyber threats—it anticipates them. That’s where EDSPL’s SOC comes in. It’s not just a monitoring desk—it’s the nerve center of a complete, proactive, and always-on cyber defense strategy.
So, what makes EDSPL’s SOC different from traditional security setups? Why are enterprises across industries trusting us with their digital lifelines?
Let’s explore, in depth.
1. Around-the-Clock Surveillance – Because Threats Don’t Take Holidays
Cyber attackers operate on global time. That means the most devastating attacks can—and often do—happen outside regular working hours.
EDSPL’s SOC is staffed 24x7x365 by experienced cybersecurity analysts who continuously monitor your environment for anomalies. Unlike systems that rely solely on alerts or automation, our human-driven vigilance ensures no threat goes unnoticed—no matter when it strikes.
Key Features:
Continuous monitoring and real-time alerts
Tiered escalation models
Shift-based analyst rotations to ensure alertness
Whether you’re a bank in Mumbai or a logistics firm in Bangalore, your systems are under constant protection.
2. Integrated, Intelligence-Driven Architecture
A SOC is only as good as the tools it uses—and how those tools talk to each other. EDSPL’s SOC is powered by a tightly integrated stack that combines:
Network Security tools for perimeter and internal defense
SIEM (Security Information and Event Management) for collecting and correlating logs from across your infrastructure
SOAR (Security Orchestration, Automation, and Response) to reduce response time through automation
XDR (Extended Detection and Response) for unified visibility across endpoints, servers, and the cloud
This technology synergy enables us to identify multi-stage attacks, filter false positives, and take action in seconds.
3. Human-Centric Threat Hunting and Response
Even the best tools can miss subtle signs of compromise. That’s why EDSPL doesn’t rely on automation alone. Our SOC team includes expert threat hunters who proactively search for indicators of compromise (IoCs), analyze unusual behavior patterns, and investigate security gaps before attackers exploit them.
What We Hunt:
Zero-day vulnerabilities
Insider anomalies
Malware lateral movement
DNS tunneling and data exfiltration
This proactive hunting model prevents incidents before they escalate and protects sensitive systems like your application infrastructure.
4. Multi-Layered Defense Across Infrastructure
Cybersecurity isn’t one-size-fits-all. That’s why EDSPL’s SOC offers multi-layered protection that adapts to your unique setup—whether you're running on compute, storage, or backup systems.
We secure:
Switching and routing environments
On-premise data centers and hybrid cloud security models
Core network devices and data center switching fabric
APIs, applications, and mobility endpoints through application security policies
No layer is left vulnerable. We secure every entry point, and more importantly—every exit path.
5. Tailored Solutions, Not Templates
Unlike plug-and-play SOC providers, EDSPL dives deep into your business architecture, industry regulations, and operational needs. This ensures our SOC service adapts to your challenges—not the other way around.
Whether you’re a healthcare company with HIPAA compliance needs, or a fintech firm navigating RBI audits, we offer:
Custom alert thresholds
Role-based access control
Geo-fencing and behavioral analytics
Industry-specific compliance dashboards
That’s the EDSPL difference—we offer tailored SOC services, not templated defense.
6. Fully Managed and Maintained – So You Focus on Business
Hiring, training, and retaining a cybersecurity team is expensive. Most businesses struggle to maintain their own SOC due to cost, complexity, and manpower limitations.
EDSPL eliminates that burden with its Managed and Maintenance Services. From deployment to daily operations, we take complete ownership of your SOC infrastructure.
We offer:
Security patch management
Log retention and archiving
Threat intelligence updates
Daily, weekly, and monthly security reports
You get enterprise-grade cybersecurity—without lifting a finger.
7. Real-Time Visibility and Reporting
What’s happening on your network right now? With EDSPL’s SOC, you’ll always know.
Our customizable dashboards allow you to:
Monitor attack vectors in real time
View compliance scores and threat levels
Track analyst responses to incidents
Get reports aligned with Services KPIs
These insights are vital for C-level decision-makers and IT leaders alike. Transparency builds trust.
8. Scalable for Startups, Suitable for Enterprises
Our SOC is designed to scale. Whether you’re a mid-sized company or a multinational enterprise, EDSPL’s modular approach allows us to grow your cybersecurity posture without disruption.
We support:
Multi-site mobility teams
Multi-cloud and hybrid setups
Third-party integrations via APIs
BYOD and remote work configurations
As your digital footprint expands, we help ensure your attack surface doesn’t.
9. Rooted in Vision, Driven by Expertise
Our SOC isn’t just a solution—it’s part of our Background Vision. At EDSPL, we believe cybersecurity should empower, not limit, innovation.
We’ve built a culture around:
Cyber resilience
Ethical defense
Future readiness
That’s why our analysts train on the latest attack vectors, attend global security summits, and operate under frameworks like MITRE ATT&CK and NIST CSF.
You don’t just hire a service—you inherit a philosophy.
10. Real Impact, Real Stories
Case Study 1: Ransomware Stopped in Its Tracks
A global logistics client faced a rapidly spreading ransomware outbreak on a Friday night. Within 15 minutes, EDSPL’s SOC identified the lateral movement, isolated the infected devices, and prevented business disruption.
Case Study 2: Insider Threat Detected in Healthcare
A hospital’s employee tried accessing unauthorized patient records during off-hours. EDSPL’s SOC flagged the behavior using our UEBA engine and ensured the incident was contained and reported within 30 minutes.
These aren’t hypothetical scenarios. This is what we do every day.
11. Support That Goes Beyond Tickets
Have a concern? Need clarity? At EDSPL, we don't bury clients under ticket systems. We offer direct, human access to cybersecurity experts, 24x7.
Our Reach Us and Get In Touch teams work closely with clients to ensure their evolving needs are met.
From technical walkthroughs to incident post-mortems, we are your extended cybersecurity team.
12. The Future Is Autonomous—And EDSPL Is Ready
As cyberattacks become more AI-driven and sophisticated, so does EDSPL. We're already integrating:
AI-based threat intelligence
Machine learning behavioral modeling
Predictive analytics for insider threats
Autonomous remediation tools
This keeps us future-ready—and keeps you secure in an ever-evolving world.
Final Thoughts: Why EDSPL’s SOC Is the Backbone of Modern Security
You don’t just need protection—you need presence, prediction, and precision. EDSPL delivers all three.
Whether you're securing APIs, scaling your compute workloads, or meeting global compliance benchmarks, our SOC ensures your business is protected, proactive, and prepared—day and night.
Don’t just react to threats. Outsmart them.
✅ Partner with EDSPL
📞 Reach us now | 🌐 www.edspl.net
0 notes
Text
Strategic Intelligence in Incident Response: Your Silent Weapon Against Cyber Chaos
Your system detects a strange login attempt at 2:13 AM. Is it an anomaly? A harmless blip? Or the first sign of a major breach?
If your answer is: “Let’s investigate,” you’re already behind. If your answer is: “Our system flagged it, analyzed it, and blocked the threat—while alerting us,” you’re ahead of the curve.
This is what strategic intelligence in incident response looks like. And in 2025, it’s not just useful—it’s essential.
Here’s the brutal truth: Alerts don’t equal security
Ask any security team what their biggest problem is and you’ll hear the same thing again and again: noise.
Thousands of alerts. Half of them false positives. No clear prioritization. And most critically—no context.
That’s where strategic cyber threat intelligence flips the script. Instead of reacting to events in isolation, it helps you understand the bigger picture:
Who is targeting you?
What tools are they using?
Why you?
What should you do next?
It’s the difference between putting out fires and preventing arson.
Let’s break it down: What is “strategic” intelligence?
You’ve probably heard of threat intelligence before. But not all intelligence is created equal.
Tactical intelligence tells you there’s a malware signature to block.
Operational intelligence tells you a phishing campaign is active.
Strategic intelligence tells you which adversaries are most likely to target your industry, how they operate, and how to prepare for their evolving tactics.
Strategic intelligence isn’t just technical. It’s business-aligned. It helps CISOs and decision-makers translate cyber risk into business risk—and that changes everything.
Need proof? STL Digital’s cyber threat intelligence and incident response article goes deep into how organizations are using intelligence to pre-empt, not just respond.
A quick question: How often do you actually use your threat feeds?
Be honest. You may have feeds coming from every direction—SIEMs, firewalls, third-party tools—but how often do they actually inform your strategy?
If the answer is “rarely,” you’re not alone.
The problem isn’t the data—it’s the lack of interpretation. Strategic intelligence is about turning raw data into actionable insight. Not in hours or days. In real time.
When threat detection and intelligence are built into your incident response from the start, your team isn’t just reacting faster—they’re anticipating attacks before they land.
Why is this suddenly critical in 2025?
Three reasons.
Attackers are more coordinated. They’re sharing tools, buying access, and deploying AI themselves.
Attack surfaces are expanding. Every SaaS tool, every IoT device, every remote worker is a potential entry point.
Regulations are stricter than ever. Delayed response isn't just risky—it’s non-compliant.
In short, you can’t afford to just “see what happens” anymore. You need to know who’s coming, how they’ll come, and what to do when they do.
Let’s shift the focus: Incident response as a business strategy
Think of it this way. If you had a warehouse filled with expensive goods, you’d invest in surveillance, insurance, and emergency protocols.
So why do companies treat digital assets any differently?
Incident response isn’t just an IT protocol. It’s a business continuity plan. When handled strategically, it minimizes downtime, protects customer trust, and keeps operations moving—even during a crisis.
And when backed by strong intelligence, it’s not just faster—it’s smarter.
The key is integration. Not adding “yet another” dashboard, but weaving intelligence into your IR playbooks, your detection rules, and your escalation workflows.
STL Digital outlines how leading companies are achieving this in their detailed report on cyber intelligence.
Ask yourself: Do you know what a breach would really cost you?
It’s easy to think of a breach as a technical issue—patch the system, reset the passwords, move on.
But the true cost of a cyberattack includes:
Downtime across operations
Lost customer trust
Legal liabilities
Compliance violations
Damaged brand reputation
That’s why modern IR teams are no longer just responders—they’re advisors to the business. Their insights can influence product design, vendor decisions, even marketing strategy.
But only if their data is strategic, contextual, and timely.
So, what does strategic incident response actually look like?
It’s not a product. It’s not a policy document. It’s a capability—one that evolves as your threats evolve.
Here’s what a mature, intelligence-driven incident response framework includes:
Pre-built playbooks for top threat scenarios
Threat actor profiling tied to business units
Automated detection and containment
Business impact mapping
Executive dashboards with strategic risk insights
Sound like a lot? It is. But the good news: you don’t have to do it alone.
Partners like STL Digital help businesses build this capability step by step—starting from where you are now. Their cyber intelligence insights are a great place to begin.
One final question to reflect on:
If your team got an alert right now—this very second—would they know whether to ignore it, investigate it, or escalate it?
And would your leadership understand the business impact of that decision?
If not, it’s time to move beyond reactive security. Strategic intelligence isn’t just for defense—it’s for resilience. It empowers your team, informs your leaders, and gives your business the foresight it needs to navigate the threat landscape of 2025 and beyond.
So don’t wait for the breach. Plan, detect, and respond—strategically.
0 notes
Text
How Insurtechs Are Strengthening Core Software with Advanced Cybersecurity Measures
As cyber threats continue to evolve in complexity, securing sensitive customer information has become a top priority, particularly within the core software systems that drive the insurance industry. Insurers are enhancing their cybersecurity efforts, and it’s fascinating to see how they are approaching this critical challenge.
Many insurtech companies are leading this transformation by incorporating state-of-the-art technologies, such as AI-powered threat detection systems soc security operations center, into their platforms. Instead of merely reacting to cyberattacks, these companies are taking proactive steps to identify and mitigate risks before they escalate into significant issues.
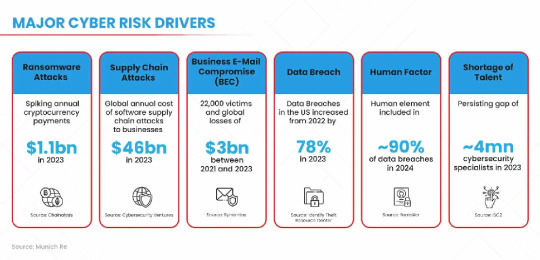
The Growing Need for Cybersecurity in Insurance
Property & Casualty (P&C) insurance companies are sitting on a wealth of sensitive personal and financial data, making them prime targets for cybercriminals. As insurers embrace technologies like cloud computing, artificial intelligence (AI), and the Internet of Things (IoT) to streamline operations, they gain substantial efficiencies—but also open themselves to new vulnerabilities.
For insurers, investing in cybersecurity isn’t just about avoiding regulatory penalties. In today's increasingly hostile digital environment, robust cybersecurity is essential for long-term survival.
To underscore this point, let’s take a look at a real-world example that rattled the insurance sector: the 2020 data breach at Folksam, one of Sweden’s largest insurance providers. This incident served as a major wake-up call for the industry. Folksam unintentionally leaked sensitive data for around one million customers, not due to an external cyberattack, but because of an internal oversight. In an attempt to analyze customer behavior and provide more personalized services, the company shared private customer information with tech giants such as Facebook, Google, Microsoft, LinkedIn, and Adobe.
While Folksam stated there was no evidence of misuse by these third parties, the breach raised serious concerns among customers and regulators alike. It demonstrated that even well-intentioned actions could lead to significant security failures if proper safeguards are not in place.
Core Platform Security: A Critical Priority
Your core platform—the system responsible for policy management, claims processing, billing, and customer relations—is the backbone of your insurance business. But it also becomes a prime target for cyberattacks if not adequately protected.
AI: The Ultimate Security Co-Pilot
Leading insurers are increasingly integrating AI-powered soc security operations center “co-pilots” into their core platforms. These AI-driven systems analyze vast amounts of data to:
Detect Anomalies: Machine learning algorithms can identify unusual patterns in claims, underwriting, or policy modifications that may indicate fraudulent activity or a security breach. For instance, an unexpected increase in claims from a particular region or a sudden surge in requests to modify policy details could signal potential fraud.
Automate Incident Response: Once a threat is detected, AI can automatically isolate compromised systems, preventing the breach from spreading. This might involve shutting down affected servers or disabling user accounts to contain the damage.
Predict Attack Vectors: By analyzing data from threat intelligence feeds and the dark web, AI can help insurers anticipate and defend against future attacks. This might include identifying emerging malware strains or pinpointing vulnerabilities in third-party software.
Take Zurich Insurance, for example. Their AI models soc security operations center successfully identified and stopped a credential-stuffing attack targeting their Asian SME clients, blocking thousands of fraudulent login attempts within hours. This kind of rapid response is only achievable when AI is deeply embedded in the core platform.
0 notes
Text
Protection Relays Market Future Trends Highlighting Smart Grid and Digital Substation Integration
The protection relays market is undergoing a dynamic transformation influenced by emerging technologies, infrastructure upgrades, and the increasing demand for reliable and secure power distribution systems. As global economies shift toward smarter, more resilient energy grids, the role of protection relays has become more critical than ever. These devices are essential in detecting faults and ensuring the safety and stability of electrical systems, making them indispensable across utility, industrial, and commercial sectors.

Rise of Smart Grids Driving Innovation
One of the most prominent trends shaping the future of the protection relays market is the global shift toward smart grids. Traditional electrical grids are being upgraded with digital technologies to enable two-way communication, remote monitoring, and advanced control systems. This transformation demands more sophisticated and adaptable protection relay systems capable of handling complex data and responding to rapidly changing conditions.
Microprocessor-based digital relays are replacing electromechanical models, offering superior speed, accuracy, and integration capabilities. Their ability to process real-time data, support multiple protection functions, and communicate with other smart grid components makes them ideal for modern energy infrastructure.
Expansion of Renewable Energy Sources
The integration of renewable energy sources such as solar and wind is also influencing the design and deployment of protection relays. Unlike conventional power plants, renewable sources are decentralized and often variable in output. This introduces new challenges for grid protection, necessitating advanced relays that can manage distributed generation, fluctuating voltages, and bidirectional power flows.
Future trends suggest that protection relays will increasingly incorporate adaptive algorithms and artificial intelligence to recognize patterns and predict potential faults. Such predictive maintenance capabilities can prevent outages, reduce downtime, and optimize asset management.
Digital Substations Enhancing System Efficiency
Digital substations are another major driver transforming the protection relay landscape. These substations utilize digital communication protocols, fiber optics, and intelligent electronic devices (IEDs) to improve performance and reduce the need for copper cabling. Protection relays serve as the brain of digital substations by providing precise control, diagnostics, and protection functions.
As utility companies worldwide modernize their infrastructure, digital substations offer a scalable and efficient solution. The trend is expected to accelerate adoption of advanced protection relays that support IEC 61850 communication standards, allowing seamless interoperability and real-time data exchange.
Growth in Industrial Automation and Smart Manufacturing
The proliferation of industrial automation and Industry 4.0 is another trend positively impacting the protection relays market. Manufacturing plants, data centers, oil and gas facilities, and transport networks rely on uninterrupted power supply to maintain operations. Protection relays provide critical fault detection and isolation to minimize equipment damage and operational downtime.
Future demand will focus on compact, modular, and intelligent relays that integrate with industrial automation platforms. These systems not only enhance safety but also allow remote diagnostics and control through cloud-based monitoring tools, improving overall operational efficiency.
Emphasis on Cybersecurity and Grid Resilience
As power systems become increasingly interconnected and data-driven, cybersecurity is emerging as a vital concern. Modern protection relays are now being designed with built-in security features to prevent unauthorized access, tampering, and cyberattacks. Encryption, role-based access control, and real-time security monitoring are becoming standard features in next-generation devices.
Regulatory bodies are also setting stricter guidelines to ensure critical energy infrastructure remains secure. As a result, manufacturers of protection relays are investing in robust firmware and hardware solutions that align with global security standards, further reinforcing market growth.
Market Expansion in Emerging Economies
Emerging economies in Asia-Pacific, Latin America, and Africa are witnessing rapid industrialization and urban development, creating significant opportunities for the protection relays market. With increasing investments in power generation, transmission, and distribution networks, these regions are adopting advanced protective technologies to support grid expansion and reliability.
In addition, government-led electrification programs and renewable energy initiatives are accelerating demand for protection relays in rural and remote areas. The trend is likely to continue as countries prioritize energy access and infrastructure modernization.
Outlook and Strategic Focus
Looking ahead, the protection relays market will be driven by continued innovation, standardization, and the need for adaptive and secure electrical protection systems. Companies operating in this space are focusing on research and development to deliver feature-rich, scalable, and cost-effective solutions that meet the evolving needs of utilities and industries alike.
Partnerships between relay manufacturers and software developers are expected to flourish, enabling deeper integration of protection systems with digital platforms and analytics tools. Moreover, as data plays a larger role in grid management, the future of protection relays lies in their ability to transform from reactive to proactive systems—capable of learning from data, adapting to new conditions, and safeguarding the electric grid of tomorrow.
In conclusion, the future of the protection relays market is both promising and complex, marked by technological convergence, global infrastructure developments, and the pressing need for more intelligent and secure power systems. Stakeholders who invest in innovation and adaptability will be well-positioned to lead the next era of electrical protection solutions.
#ProtectionRelaysMarket#SmartGridTechnology#DigitalSubstations#ElectricalProtection#PowerGridSecurity
0 notes