#PrivacyGuide
Explore tagged Tumblr posts
Text
Surf the Web Anonymously! What is Tor? A Deep Dive into The Onion Router

0 notes
Text
Here are some articles / guides for the anarchist that is seeking online privacy or perhaps anonymity.
I would recommend reading the EFF's Surveilance Self Defence guides for an understanding on how to holistically defend your privacy.
A good general guide is the PrivacyGuides website.
And I would heavily recommend both the Hitchhiker's Guide to Online Anonymity and the Anarsec website to anyone that does anything the state might class as illicit online.
Digital surveillance is a huge and terrifying thing that anyone should be legitimately worried about. However, it is crucial that you do not just add random "privacy" tools to be more secure. More often than not, these just de-anonymize you from the stream of users not using them (looking at you PrivacyBadger).
3 notes
·
View notes
Text
Aight, I'm pissed enough at Y*utube's aggressive ad bullshit (this reddit comment summarizes it pretty well) and it's one of the few G**gle services that we're stuck stuck with, that I'm gonna make my own post on current workarounds as of 10/12/2023, with info on methods that I know of for both desktop and mobile. They may not be the best workarounds, but they are what I'm currently using or trust from what I've heard (and I haven't had any other posts like this come across my dash, so maybe this is needed). We fight to the bitter end, comrades.
This post is specifically for if you must be logged in to use Youtube. Your greatest defense would be to use Youtube while logged out. From what I can tell, they basically can't do anything to you if you are.
Please note that I am absolutely no web or code expert, I don't understand the inner workings of the G**gle all seeing eye and how they catch you on this shit, I don't know if it's account based or IP based, I just barely figured out how to buy and use my own domain like three weeks ago, so there are likely things in this post I will suggest that people will correct me on. If for some reason this post gets big and starts circulating (unlikely), please check reblogs and replies for additional information (and make sure it's ACCURATE if you can). Knowledge is your friend.
With that plea to the void out of the way:
Desktop:
Some folks are using browsers with built in ad blockers such as Brave (with varying results; the comments are worth a read by everyone regardless if you use Brave) to circumvent the ad block policy, but that's Chromium shit! We don't do that in this house! I guess you can if you really want to (PrivacyGuides apparently gives it the seal of approval) but if you like your online privacy, I personally really do suggest sticking with Firefox.
"But Dyl, they're catching us on Firefox even with Ublock Origin."
Yes, but the Ublock team is working their asses off to keep up with every. single. ID. change. Y*utube makes to try to break their workarounds. If it's not currently working for you, click on that link right there and follow that guide. This war of the ads will probably continue for a while, so my advice for the foreseeable future is this:
Always perform the four steps listed in the above link any time you've been away from Y*utube for a while (even just a couple hours),
and double check the Y*utube ID VS Ublock's current ID as stated in the linked comment at the start of this post.
After verifying there's an ID update and Ublock is caught up, reset your filters every single time you get on after a several hour break (after backing up your personal filters and trusted sites, if you have any of those customized). Why so often? Because that's just about how often Y*utube's updating their popup ID to catch you with your ad blocker. The Ublock team is staying on top of it fairly well considering the insane frequency, but they may not always get to it for a few hours (hence checking the ID).
After rebooting your Ublock, check a few videos without being logged in first so as not to put your account at risk. Do so in incognito if it's easiest for you. EDIT: If you aren't logged in, YT won't give a shit if you have an ad blocker-- or so I've heard.
"That sounds like a hassle. Don't the filters in this post work?"
They may have at one point! But that post was made all the way back at the end of June 2023, and most recent replies in the post are stating it's not working for them anymore. Thus, I'd just constantly reset your Ublock for the time being until a better solution is implemented. Besides, once you know what you're doing, resetting Ublock takes a grand total of, oh I dunno, a minute? On that note, with YT's constant updates, I have no idea how Brave is faring/keeping up in comparison. And besides from using either Brave or Firefox+Ublock, I don't know of any other desktop solutions.
Furthermore-- and this applies to both desktop and mobile, but I'm bringing it up now-- if you really value your Y*utube channel and don't want it to lose access to watching videos-- or worse-- it may work to make a Y*utube account that's dispensable as your new default. I just used my spam email, honestly. It's literally no skin off my nose if that account suddenly can't watch Y*utube anymore. Then, save the browsing on your main account for when you can afford to have your adblock off (or just don't watch videos from that account anymore). It seems if you've already got the warning once, you're basically on G**gle's watchlist with that account now-- so if you've gotten it on your main, better safe than sorry.
Mobile:
There are a couple things I know of that you can do here. My first suggestion, and the one I just set up, is Revanced (aka the Revanced Manager, and it works in tangent with a MicroG fork (I absolutely do not have the vocabulary to explain what MicroG is/does, just know you can't log in to YT Revanced without it)). This Reddit post is the one I think will make the most sense to everyone for installation, but I would use it in conjunction with the official guide for dummies, not as a replacement for it.
TL;DR, Revanced is an open source APK patcher (or in gamer speak, a mod) that provides patches for numerous applications (T*mblr included, hint hint). Note the term "patches." Yes, you do need to download an APK of your app of choice (on non-rooted devices), but technically what Revanced does is create its own "build" of the app by combining the APK and the patches, and since they're not the ones distributing the APK, I believe that technically keeps them out of G**gle's death laser. PLEASE note that Revanced does NOT distribute its own APKs: if you're trying to save yourself hassle and find something claiming to be an already patched Revanced APK, be it for Y*utube, Reddit, etc, assume it's a virus even if it's not. Always get your APK from apkmirror with your own fingers and manually patch it in with Revanced.
I know the guide looks scary, but believe me: Revanced used to be WAY harder to install, as in, you had to go through a virtual machine on your phone harder. At the current moment, Revanced is Android only. Sorry Apple users :/
If logging in to an account is of no consequence to you and you could not care less, Newpipe is another good third party YT choice from what I've heard; I don't know if it has all of the same features as Revanced YT, but at the very least, yes, it should block ads. It seems to also be compatible with Soundcloud and Bandcamp of all things at a glance, so if those are common applications for you, Newpipe might even be a better option for you over Revanced. Alas, yet again, this app is not compatible with Apple-- and as this is the last third party YT app I have to offer, I don't know if there are any third party YT apps that are Apple compatible. However...
If installing a scary new non-playstore app isn't up your alley, Brave seems to have a mobile app as well; you'd be watching Y*utube in your browser instead of the Y*utube app, but hey, I was watching Y*utube in Firefox mobile with Ublock until I put on my big kid pants with Revanced, so it's absolutely doable. Again, I must reiterate, I don't know how Brave is faring with these changes.
That's all I've got, but just to reiterate: I'm not an expert. I only know bare bones web/code stuff, my understanding on some of these things may be slightly off or wrong, these are just the methods I know of that work to circumvent YT ads. Your mileage may vary on a number of factors, including but not limited to, your understanding of/ability to learn how to download and use non-playstore apps, any breaking updates YT makes to further enforce their tyranny, how G**gle keeps track of ad blockers in browsers, and how long ago this post was made vs when you're seeing it.
It's war out there, soldier; good luck.
#important#psa#ad blocking#should i tag this with more relevant tags? yes#am i not going to because i fear this post actually circulating? also yes#if it 'escapes' containment it's more like it's going to be dragged out#dylawa rambles
6 notes
·
View notes
Note
A correction on your post about piracy and Firefox extension recommendations: all recommended extensions on that post except uBlock Origin is either worthless due to a more capable feature in uBO/Firefox or actively negates your privacy. Here's a list of extensions to use instead: https://github.com/arkenfox/user.js/wiki/4.1-Extensions
In addition, you want as little extensions as possible for privacy reasons. Also depending on your country of residency, you need a VPN to avoid getting into trouble with your internet service provider. The recommended ones are Mullvard, Firefox, and ProtonVPN. I believe there's 1 more but I don't remember which. All other VPNs not listed above can and will compromise your privacy such as Shark VPN, Nord VPN, etc.
To learn more about piracy, check out r/piracy, r/freemediaheckyeah, r/crackwatch, etc
To learn more about privacy, check out r/privacy, r/privacyguides, r/cybersecurity101, etc.
👍
184 notes
·
View notes
Text
it has always been important, but it is even more important during times like these - times with a steep rise in fascism and other far right ideologies along with an uptick in extremely conservative policy making - that everyone takes the chance to become more computer literate.
learn how to protect your data and your privacy. i dont care how much you are sure you know, but go back to basics and learn about the fundementals of internet safety (what not to share online, how to spot phishing schemes, ad blockers, etc). and while you're at it learn about data privacy in more depth.
learn about use cases. learn about VPNs. learn about self-hosting. learn about the decentralized web. learn about online federation/the fediverse. learn about FLOSS (free, libre, open source software). learn about encryption (especially e2ee). learn about which browser is best for you to use. learn how to harden firefox. learn about tor. learn about browsers in general, and cookies, and fingerprinting. learn about log policies. learn how to check if a service had been audited and by who. the list goes on.
even if you don't plan on using all of these things, i cannot stress enough how important it is to know at least basic info about them and how they work. it could genuinely be the difference between life and death for you and your loved ones, especially if you or them are in marginalized groups targeted by this latest wave of conservative policies. it is also imperative to learn about these if you are planning to be an activist on any serious level.
if you don't really know what any of this is, then it can be intimidating. if you don't know where to start, i suggest r/privacy and r/privacyguides. they have excellent compilations of resources for various levels of privacy needs.
stay safe.
#yes yes somewhat hypocritical to preach about privacy while using tumblr regularly#but still#ky speaks
0 notes
Text
another useful resource if you want to really go ham with privacy is privacyguides which has info on how to model what you're trying to protect (threat modelling), what steps you should take, and tools that will help you achieve that beyond just adblockers
i hate seeing people now making fun of those who care about privacy online. i've seen people saying things like "well they already have your data. what are companies going to do with it" and it's like, that's not the point. it's that companies /shouldn't/ be able to have my data and sell it. am i aware they probably already have my data? yes, absolutely. but i'm still going to try and keep them from monetizing it any further, why are we defending companies selling data they shouldn't have to begin with though?
80K notes
·
View notes
Text
Changes in Technology: Communication & Ethics
Hi this is Sophie, and Ill be discussing how changes in technology have impacted the way in which people communicate, through use of the internet, and the ethical considerations around the use of technology, including internet privacy and acting responsibly.
Technology has become a frequently used new medium for communicating with each other. It is estimated that over half of the global population use the internet, ‘generating about 2.5 quintilian bytes of data’ (Tesfay et al., 2018, p. 15). Communication previously consisted of mainly face to face communication, and now texting, social media, telecommunication, the internet and digital images and media are communication methods of the digital age we rely on. This has also changed the skill set required for and quality of communication. One point worth making is that we can no longer rely on body language, tone of voice, and facial expressions for digital communication, and therefore our verbal skills need to be better than ever before (TED, 2016). We need to enhance our verbal skills to communicate in the digital age, as we frequently use texting, emails and social media to communicate on a day to day basis and this consists almost entirely of this. I personally think messaging and social media cannot facilitate social connection and communication of the same quality that face to face communication facilitates, however there are advantages of being able to communicate in a wireless setting. Personal Learning Networks (PLN) are the online networks of people that share and communicate information via the internet (Hiltz & Turoff, 2002). Due to the internet, users are able to get in contact, connect with and learn from people all over the world (Hiltz & Turoff, 2002). Particularly useful for students, PLNs allow people to transfer knowledge and collaborate in an online environment, with people in a community broader than the local setting, therefore broadening communication opportunities.
In terms of ethics, Marsoof’s (2011) research refers to the Declaration of Human Rights in stating that people have rights to their own privacy, which includes their privacy on the internet. It needs to be recognized that there are rights to free speech as well as rights to privacy, and so this has caused conflict. Legislation is being constantly updated to try and achieve a balance between the two rights and preventing the sharing of personally sensitive information (Marsoof, 2011). Another ethical consideration is that we have a responsibility in ensuring what we post, message and watch on the internet is legally and morally right, for example, not participating in online bullying or watching pornography, to ensure the safety of ourselves and others.
Technology has become a big part of our daily lives, enabling us to communicate in new ways and with people across the country and globe. However, it is important to abide by law and be ethical when using the internet, in terms of internet privacy and responsible use of the internet.
References
Hiltz, S. R., & Turoff, M. (2002). What makes learning networks effective?. Communications of the ACM, 45(4), 56-59.
Marsoof, A. (2011). Online Social Networking and the Right to Privacy: The Conflicting Rights of Privacy and Expression. International Journal of Law and Information Technology, 19(2), https://doi.org/10.1093/ijlit/eaq018
TED. (2016, June 21). Communication in the 21st Century: Is It What You Say, Not How You Say It? | Vivian Ta [Video]. Youtube. https://www.youtube.com/watch?v=laDnZ_FWyhM
Tesfay, W. B., Hofmann, P., Nakamura, T., Kiyomoto, S., & Serna, J. (2018, March). PrivacyGuide: Towards an Implementation of the EU GDPR on Internet Privacy Policy Evaluation. In Proceedings of the Fourth ACM International Workshop on Security and Privacy Analytics (pp. 15-21). https://doi.org/10.1145/3180445.3180447
0 notes
Text
Tweeted
PrivacyGuide: Towards an implementation of the EU #GDPR on Internet #privacy policy evaluation https://t.co/bcpClTaxYW via @kdnuggets
— SQL Joker (@sql_joker) May 3, 2018
0 notes
Text
New top story on Hacker News: PrivacyGuide: Towards an Implementation of EU GDPR on Privacy Policy Evaluation
New top story on Hacker News: PrivacyGuide: Towards an Implementation of EU GDPR on Privacy Policy Evaluation
PrivacyGuide: Towards an Implementation of EU GDPR on Privacy Policy Evaluation 17 by denzil_correa | 0 comments on Hacker News.
https://ClusterAssets.tk
View On WordPress
0 notes
Text
Here's the info from that article (with a lot of heavy editorializing from me):
Don't call or text; you want to leave as minimal a traceable digital footprint as possible and cellphones are extremely traceable. The Trump admin is committed to collecting metadata from journalists who receive leaks and that includes call history and who sent text messages; even if the message gets deleted there is a record of it with the carrier that can be subpoenaed.
If you are going to email, do so from a burner account created for the purpose of leaking/whistleblowing. (my advice: use a service like protonmail that allows you to encrypt messages and doesn't collect any data beyond what is absolutely necessary for an email system to function; email is inherently insecure you have to treat it as insecure, but a burner account at a privacy-focused company like proton that facilitates sending encrypted messages is the best option for email; here's some information about how to use protonmail as privately as possible) When setting up your burner email, do not use your phone number for 2FA or include any accurate biographical information during the account setup. Set up the account while using a traffic anonymizer like Tor. Here's a PDF about what Tor is and how it works and here's the Tor project's manual explaining how to install and configure the browser for privacy. (The article advises to use Tor or a VPN but that raises the question of whether you trust your VPN provider; if you are going to use a VPN use one of the ones recommended by privacyguides; I know fuck all about VPNs but I know I wouldn't trust most VPN providers in this context).
Don't reach out to the person you're leaking to on social media. I feel like this should be obvious, but it may not be - don't reach out through meta or X or tumblr, these are not anonymous platforms and they can and will be compelled to share messages sent to journalists or data sent from your account. Don't follow the people you're leaking to (unless you already happened to be following them), don't interact with their posts. Do not make any kind of visible connection between you and the person you are leaking to.
Be careful about using encrypted messaging platforms. I personally wouldn't trust telegram or whatsapp, and I haven't heard of Session until now, but generally speaking Signal is one of your safest bets for sending messages. Signal collects the smallest amount of user data it can, and while it does require a phone number to sign up, the phone number doesn't have to stay connected to your username. If you don't already have a signal account, create one NOW because one of the things that they do track and can be compelled to disclose is when an account was created. If an account is linked to you and it was created shortly before a leak, that's suspicious. Create an account now and have it handy for when you need it. IF you are using signal, be aware that people can still screencap your messages; don't share personally identifying data via signal chats.
Have good opsec about how you collect the data that you're going to leak. For example, don't email yourself a copy of the data from your work email account, take photos of the data on a non-work phone and then strip the metadata. If you require login access to get the info you're looking to leak, figure out if there's a way that you can make the leak more ambiguous about the access by making sure there's time between your access and the leak, or that the time of your access isn't included in the information that is leaked. Take a lot of time to think about how someone might track a leak back to you and take steps to mitigate that.
Don't save copies of the data that you've leaked; once you've passed the message on to people who can get it out there, destroy any copies that you had.
GlobaLeaks and SecureDrop are tools to securely share leaks with organizations that will publicize the information you're sharing while protecting you to the best of their ability. Do not access those sites through your normal browser when you are preparing to leak data, only access them through Tor.
Be cautious about who you leak to. (Look I love the team at It Could Happen Here but you don't share a leak with a podcaster you share a leak with a group like Distributed Denial of Secrets). Focus on groups that have a history of securely sharing leaked info and on outlets that might have some legal protection from sharing information about you. The Intercept and DDoSecrets are the two that spring to mind immediately for me. (In fact I got the screenshot at the top of this thread because I went searching for this intercept article to paste on to a reply to another post but then this happened so here we are). Both of those links have their tips for leakers, btw.
It isn't stated elsewhere here so I'll add it at the end: if you are using Tor, don't log in to personal accounts that are associated with your real name or your private data. If you create burner accounts, don't use them to communicate with accounts associated with your real name or private data.
Also don't tell people - partners, parents, friends, etc. - that you're going to leak something.
And, I cannot emphasize this enough, do not tell me or any other tumblr user if you have data you are thinking about leaking or a hack you think you've pulled off. Don't talk about doing crime on the internet and definitely don't talk to me about it. Don't send an anonymous ask, don't send a private message. "The hacker or hacker-adjacent person I parasocially know from tumblr" is not a safe recipient for your leak and tumblr is not a secure or anonymous platform EVER.
buds, this is the wrong article to put under an email gate.
9K notes
·
View notes
Link
PrivacyGuide: Towards an Implementation of EU GDPR on Privacy Policy Evaluation 7 by denzil_correa |
0 notes
Link
PrivacyGuide: Towards an implementation of the EU GDPR on Internet privacy policy evaluation Tesfay et al., IWSPA’18 (Note: the above link takes you to the ACM Digital Library, where the pape… https://ift.tt/2vjIOOQ
0 notes
Text
and just in case anyone is wondering: for any correspondence that requires privacy like this, there are NO mainstream programs/services that are secure and private in the necessary ways to do so. zip, zilch, zero, nada. not discord, not messenger, not telegram, not text. the answer is no.
please look into the suggestions above. make sure you are using a program that its transparent (open source is a good start even if it's not a 100% guarantee), has a no log policy (for identifying data, messages, etc), and furthermore couldn't log your messages and hand them over to pigs even if they wanted to (E2EE is key and the creators/hosts/etc of the program should not have that key). make sure login is secure but private. as mentioned, don't use your phone number or other identifying info. use a long and secure password. if you think its long enough, make it a bit longer (and memorize it, do nooot save it to your phone). make sure that you can delete messages and even the entire program at a moments notice, and once it's gone it's completely gone. this isn't everything but it's a damn good start.
if you are looking into privacy oriented and secure communication alternatives (like if you want to inform youself more about the programs suggested above), read their official sites thoroughly, AND go search or ask on r/privacy or r/privacyguides on reddit. they are absolute goldmines of information.
if you want to find more alternatives, look for suggestions on alternativeto.net (and do research on those as well).
stay safe.
Do not use Discord to seek an abortion. Discord willingly hands out user data to the cops.
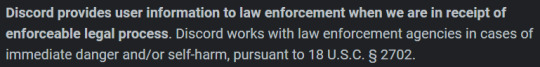
Use Signal to communicate for seeking an abortion, they use double ended encryption
60K notes
·
View notes