#Pulse topology
Video
PULSE TOPOLOGY - Durham Lumiere festival by John Wolfe
Via Flickr:
By RAFAEL LOZANO-HEMMER
#RAFAEL LOZANO-HEMMER#Pulse topology#art#light#Durham#UK#Festival#North#Art festival#exhibition#Durham Cathedral#Cathedral#Cathedrals#Lightbulb#lightbulbs#chiaroscuro#Darkness#people#crowd#crowds#display#sculpture#Gathering#lights#churches#heartbeat#pulse#topology#painting#nikon
4 notes
·
View notes
Text
IT'S LORE TIIIIIIMEEEEE
SO
This is my theory on the Numberjacks' (and meanies', kind of?) creation and anatomy. To begin with, I'll talk about how I think they were created.

The Brain Gain Machine is quite obviously not fully machine. It can move, talk and a lot of weird green goop is involved??? Which I don't think would be there if it was completely machine. So I think it is a cyborg. And it originally looked something like this.
I think it is parasite-esque, using the sofa as some kind of shell. My lore theory/AU(?) says that there were 2-3 of these, the others being destroyed and this one being damaged, so it was modified to be a cyborg. Since the Numberjacks and Meanies are somewhat alien, I think they all share a godlike creator that sent the Brain Gains to Earth to then later send signals to them (via the 'cables' on top of it) that 'spawned' the characters. The other Brain Gains would have been the ones that created the Meanies.

Numberjack birth I guess?
Since they are literally maths, the Numberjacks are just physical forms given to mathematical concepts/structures. Since they are created by the Brain Gain Machine, they do not need to reproduce (hence not having reproductive organs).
'But if the Numberjacks are maths given physical forms, what about the Meanies?' You might ask. Well, since they are more complex, with more specific abilities of their own, they are physical forms given to concepts, for example, topology (in Shape Japer's case).
Now on to the anatomy of the characters.
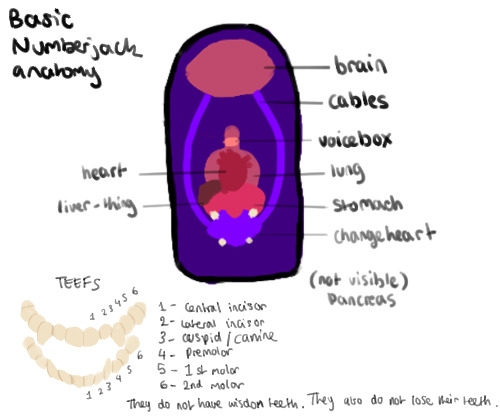
Their organs are somewhat similar to that of humans, but do not have all of the same ones. Since, as I've said before, they are just maths given a physical form, they do not grow or change in any way naturally. (The younger characters would be pretty small if that was the case.) However, since they are still living beings, they need to eat to survive. It'd also be pretty obvious if they did need to use the bathroom because Zero, One and possibly Two would be wearing nappies/diapers.
I think they'd also have an organ that I will call:

a Changeheart.
Which would be of similar size to that of their regular heart, except it gives them them a mild ability to change how things are mathematically described (and since the way things are described can't be changed, the thing being described has to change itself). The reason this would work is because I think the godlike being I mentioned earlier would be the Mathematical Universe Hypothesis given form, and the hypothesis is that our external reality is a mathematical structure. (You can tell I did a lot of research on this lol)
'Waste' products from their stomach are burned as fuel by this organ.
The changeheart gives out pulses (presumably bioelectric? Idk I'm not that good at science) containing the change that needs to be made to the surrounding area's structure. The Brain Gain Machine picks up on these pulses, concentrates them and sends them to a specific location to be used by another person with a changeheart.
The reason it has the same green goopy stuff as Brain Gain is because the Brain Gain itself has a changeheart, just a really big and more complex one.
Now on to human forms! Since I feel like it should be explained for various reasons.

Since they are 'aliens', they would not be born with a humanoid form. I think several other characters other than the Puzzler and the Numbertaker have humanoid forms since it has been implied that they have done things that only humans would be able to do (mostly shown in the audio stories). They may have one opportunity to visualize and shift into a human form that will be that form for as long as they live (which is forever). Since visualizing a human form means knowing what a human looks like, they would've only seen humans as they are usually, which also means their human forms would not have... you know. And anyway since they are all technically biologically agender they couldn't do that.

me right now
Oh gosh that was a lot. If you've made it this far, thank you so much for reading! I hope you found it interesting.
If you have any questions about this or want to know more about, for example, the Meanies' anatomies, feel free to ask in the ask box thingy!
17 notes
·
View notes
Photo

Rafael Lozano-Hemmer
Pulse Topology
2021, 3,000 LED filament lightbulbs, DMX controllers, custom-made photoplethysmography sensors, computers
Covers any area between 1,000 and 5,000 square feet
20 notes
·
View notes
Link
Skyrmions are scientifically interesting from two perspectives: On the one hand, magnetic skyrmions are envisioned as information carriers in future information technology. On the other hand, skyrmions in thin magnetic films may act as an ideal test bed to study the dynamics of topologically non-trivial magnetic quasi-particles. However, to make progress in this field, reliable generation of the magnetic skyrmion at controlled positions is required. A team of researchers, led by the Max Born Institute, has now achieved full nanometer-scale control of the skyrmion generation by two independent approaches employing He+-ion irradiation or using backside reflective masks.
#nanotechnology#data storage#computing#engineering#technology#innovation#informationtechnology#informationsystems#advanced materials
3 notes
·
View notes
Text
Interesting Papers for Week 30, 2022
Optimism and pessimism in optimised replay. Antonov, G., Gagne, C., Eldar, E., & Dayan, P. (2022). PLOS Computational Biology, 18(1), e1009634.
Increased associative interference under high cognitive load. Baror, S., & Bar, M. (2022). Scientific Reports, 12, 1766.
Retinal horizontal cells use different synaptic sites for global feedforward and local feedback signaling. Behrens, C., Yadav, S. C., Korympidou, M. M., Zhang, Y., Haverkamp, S., Irsen, S., … Schubert, T. (2022). Current Biology, 32(3), 545-558.e5.
Traveling waves in the prefrontal cortex during working memory. Bhattacharya, S., Brincat, S. L., Lundqvist, M., & Miller, E. K. (2022). PLOS Computational Biology, 18(1), e1009827.
Foraging as sampling without replacement: A Bayesian statistical model for estimating biases in target selection. Clarke, A. D. F., Hunt, A. R., & Hughes, A. E. (2022). PLOS Computational Biology, 18(1), e1009813.
Toroidal topology of population activity in grid cells. Gardner, R. J., Hermansen, E., Pachitariu, M., Burak, Y., Baas, N. A., Dunn, B. A., … Moser, E. I. (2022). Nature, 602(7895), 123–128.
Preparatory attention incorporates contextual expectations. Gayet, S., & Peelen, M. V. (2022). Current Biology, 32(3), 687-692.e6.
Serotonin neurons modulate learning rate through uncertainty. Grossman, C. D., Bari, B. A., & Cohen, J. Y. (2022). Current Biology, 32(3), 586-599.e7.
Increasing neural network robustness improves match to macaque V1 eigenspectrum, spatial frequency preference and predictivity. Kong, N. C. L., Margalit, E., Gardner, J. L., & Norcia, A. M. (2022). PLOS Computational Biology, 18(1), e1009739.
Asymmetries around the visual field: From retina to cortex to behavior. Kupers, E. R., Benson, N. C., Carrasco, M., & Winawer, J. (2022). PLOS Computational Biology, 18(1), e1009771.
Subicular neurons represent multiple variables of a hippocampal-dependent task by using theta rhythm. Lee, S.-M., Seol, J.-M., & Lee, I. (2022). PLOS Biology, 20(1), e3001546.
Hierarchical timescales in the neocortex: Mathematical mechanism and biological insights. Li, S., & Wang, X.-J. (2022). Proceedings of the National Academy of Sciences, 119(6), e2110274119.
Connectomic features underlying diverse synaptic connection strengths and subcellular computation. Liu, T. X., Davoudian, P. A., Lizbinski, K. M., & Jeanne, J. M. (2022). Current Biology, 32(3), 559-569.e5.
Pupil diameter is not an accurate real-time readout of locus coeruleus activity. Megemont, M., McBurney-Lin, J., & Yang, H. (2022). eLife, 11, e70510.
A lexical approach for identifying behavioural action sequences. Reddy, G., Desban, L., Tanaka, H., Roussel, J., Mirat, O., & Wyart, C. (2022). PLOS Computational Biology, 18(1), e1009672.
High-value decisions are fast and accurate, inconsistent with diminishing value sensitivity. Shevlin, B. R. K., Smith, S. M., Hausfeld, J., & Krajbich, I. (2022). Proceedings of the National Academy of Sciences, 119(6), e2101508119.
Sparse connectivity for MAP inference in linear models using sister mitral cells. Tootoonian, S., Schaefer, A. T., & Latham, P. E. (2022). PLOS Computational Biology, 18(1), e1009808.
An initial ‘snapshot’ of sensory information biases the likelihood and speed of subsequent changes of mind. Turner, W., Feuerriegel, D., Hester, R., & Bode, S. (2022). PLOS Computational Biology, 18(1), e1009738.
Probing subthreshold dynamics of hippocampal neurons by pulsed optogenetics. Valero, M., Zutshi, I., Yoon, E., & Buzsáki, G. (2022). Science, 375(6580), 570–574.
A behavioural correlate of the synaptic eligibility trace in the nucleus accumbens. Yamaguchi, K., Maeda, Y., Sawada, T., Iino, Y., Tajiri, M., Nakazato, R., … Yagishita, S. (2022). Scientific Reports, 12, 1921.
#science#Neuroscience#computational neuroscience#Brain science#research#cognition#cognitive science#neurons#neural networks#neural computation#neurobiology#psychophysics#scientific publications
6 notes
·
View notes
Text
CORE REACTOR II VE PSU with VENTO PWM FAN from XPG

Adata XPG CORE REACTOR II review
XPG, a rapidly expanding supplier of systems, parts, and accessories for gamers, pros in esports, and tech enthusiasts, has introduced a number of products aimed at the discerning, low-cost gamer. XPG has introduced a new range of entry-level Gold efficiency power supply units and ARGB PWM fans in an effort to meet the demands of PC builders of all skill levels. It’s now easier than ever to upgrade your system with the new XPG CORE REACTOR II VE and XPG VENTO PWM fans.
VE CORE REACTOR II
Finding the right balance between performance and cost is never easy, but XPG prioritises the needs of its customers above all else. Despite being marketed as a Value Edition product, the CORE REACTOR II VE’s specifications are anything but low-cost. This power supply uses XPG’s unique PSU topology, which is inspired by the design of the award-winning CORE REACTOR II, to achieve performance that exceeds Intel ATX 3.1 requirements. With its DC-DC circuit design, gold efficiency, and dedicated 12V-2×6 connector, this power supply unit is ideal for all of your modern gaming needs. The XPG CORE REACTOR II VE, available in 650W, 750W, and 850W models, is the ideal base for a current generation build.
VENTO PWM HOUSE
The stock fans from XPG have been upgraded to support pulse width modulation, or PWM. From high-end devices to the entry-level end of their portfolio, XPG is expanding its compatible offerings in response to the growing demand for software support in all things PC DIY. Without going over budget, you can easily meet all of your fan needs with the new VENTO 120 ARGB PWM and VENTO R 120 ARGB PWM. You can precisely customise your airflow to meet the requirements of your build and gaming environment by combining regular and reverse VENTO 120 ARGB PWM fans.
It only takes a few clicks to synchronise the RGB lighting on all of your fans thanks to daisy-chain compatibility. When connecting all of your Vento ARGB PWM fans to the XPG VENTO PWM you can precisely control the lighting and fan performance by using the RGB software from any popular motherboard brand or by using XPG’s own PRIME ecosystem management software.
PULL EVERYTHING TOGETHER
These new XPG products work best with the cases they were designed to go with, even though they can be used with a wide variety of chassis options from almost every brand on the market. With its bezel-less tempered glass front and side panels, something like the iF design award-winning and media acclaimed XPG INVADER X mid-tower chassis would be the ideal way to display the vibrant synchronised lighting of your new VENTO 120 R ARGB PWM fans. In the meanwhile, handling the cables from your CORE REACTOR II VE is simple thanks to the built-in wiring channel and pre-installed cable straps.
XPG is enabling more gamers and creators to create setups they can be proud of, both inside and out, and they can do so with money left over to actually buy some games by expanding their entry level product offerings.
VE CORE COMPETENCE CORE REACTOR II
Your system is empowered by the effective power delivery of XPG CORE REACTOR II VE. It sports a dedicated 12V-2×6 connector for the newest graphics cards and is compliant with Intel’s most recent ATX 3.1 design guidelines. This device has a DC-DC circuit design for improved consistency, stability, and performance. It also has outstanding ripple control and hold-up time that exceeds Intel’s specifications. Its eight industrial protections strengthen its robustness and protect your system as well as the unit.
Compatible with ATX 3.1
The seamless integration of XPG CORE REACTOR II VE with ATX 3.1 standards improves both performance and dependability. It delivers advanced power delivery and efficiency, and its dedicated 12V-2×6 connector guarantees optimal compatibility with the most recent graphics card requirements.
12V-2×6 Connector
By ensuring direct and effective power delivery to crucial components, the included 12V-2×6 connector maximises system performance and stability. For the demanding needs of your system, this connector ensures consistent and reliable power by minimising voltage drops and optimising efficiency.
DC-DC Circuit Architecture
The DC-DC circuit design of the XPG CORE REACTOR II VE optimises efficiency and dependability by converting power directly to the necessary output voltage. This increases hardware lifespan, lowers heat generation, and improves system stability.
Minimal Ripple Noise Architecture
The low ripple noise design of the XPG CORE REACTOR II VE exceeds Intel’s specifications, with ripple levels of less than 40 mV at +5V and +3.3V and less than 60 mV at +12V. This guarantees consistent power supply, reduces electrical interference, improves system efficiency, and offers a smooth computing environment.
15 milliseconds of hold time
The XPG CORE REACTOR II VE has an outstanding hold-up time, exceeding Intel’s specifications with a continuous power delivery time of more than 15 milliseconds. This makes it the ideal option for high-performance computing setups because it guarantees dependable operation even in demanding circumstances.
With the help of eight industrial-grade protections, XPG CORE REACTOR II VE
protecting your system from short circuits, overcurrent, undervoltage, and more. Even in the wake of electrical anomalies, you can depend on continuous performance with peace of mind thanks to this all-inclusive protection suite.
140 mm in length
The 140mm length of the XPG CORE REACTOR II VE is compact, maximising space efficiency without sacrificing performance. Its compact design makes it simple to integrate into different PC configurations and chassis while providing unwavering power and dependability.
XPG VENTO 120 ARGB PWM
Featuring a 4-Pin PWM connector, ARGB lighting effects, and a rifle bearing for long-lasting durability and quiet operation, the XPG VENTO 120 ARGB PWM cooling fan is built for maximum performance and style. Its ability to daisy-chain, along with its high static pressure and auto-restart function, guarantee ideal cooling effectiveness. It is compatible with all major ARGB management software and provides an infinite number of configuration choices. With the help of the XPG VENTO 120 ARGB PWM fan, improve your cooling setup.
4-Pin PWM Socket
Precise control over the fan’s speed is possible with the XPG VENTO 120 ARGB PWM, which adapts dynamically to variations in system temperature. This minimises noise and power consumption while ensuring optimal cooling performance catered to your PC’s needs.
Daisy Chain Capable
The XPG VENTO 120 ARGB PWM fan offers dazzling lighting effects across multiple units for an enhanced cooling experience without clutter, and its daisy-chain feature and ARGB lighting effect synchronisation make installation simpler.
Bearing Rifle
Using a rifle bearing, the XPG VENTO 120 ARGB PWM fan ensures long-lasting, dependable performance in addition to low noise levels.
Cooling Efficiency
With its outstanding cooling efficiency of 50.27 10% CFM airflow and 1.5mm H2O static pressure, the XPG VENTO 120 ARGB PWM fan is a great choice. You can anticipate ideal temperature control even during long gaming sessions.
Mechanism of Auto-Restart
The fan has an auto-restart feature that protects against possible malfunctions brought on by problems with rotation. This feature not only guarantees continuous cooling but also guards against damage to the fan and related electrical equipment. It guarantees safety and dependable operation in the majority of situations by guarding against any electrical damage to the rotational motor.
Compatibility of ARGB Software
The majority of motherboard brands‘ ARGB software is seamlessly compatible with the XPG VENTO 120 ARGB PWM fan. Because of its compatibility, you can easily integrate the fan into your current setup and synchronise its beautiful ARGB lighting effects with the other parts of your system. With the unmatched versatility of the XPG VENTO 120 ARGB PWM fan, you can design a visually appealing and cohesive space that suits your tastes.
Contents of the Package
You can choose between a single pack or a triple pack of the XPG VENTO 120 ARGB fan, depending on your exact cooling requirements. We provide solutions for improving airflow in individual systems as well as upgrading multiple setups at once. With the XPG VENTO 120 ARGB cooling fan’s ease of use and adaptability, you can improve the cooling of your PC.
About XTREME PERFORMANCE GEAR, or XPG
ADATA founded XPG to offer high-quality gear to gamers, techies, and esports pros. Adata work closely with esports and gaming communities to understand their needs and create high-performance products. They design all their products for maximum performance, stability, and dependability. Their products range from complete systems to peripherals, systems, and components. They also create products with incredibly cool designs, for which they have won numerous important international awards, including Good Design and iF Design. Besides their products, they support and sponsor esports teams and events worldwide to provide the best xtreme gaming experiences.
Read more on Govindhtech.com
0 notes
Text
Tying Knots Inside Lasers - Technology Org
New Post has been published on https://thedigitalinsider.com/tying-knots-inside-lasers-technology-org/
Tying Knots Inside Lasers - Technology Org
What do you picture in your mind’s eye when you hear the word “laser“? A light saber? A cat toy? The sensor at the supermarket reading barcodes as fast as the eye can blink?
These are all lasers, but there are so many more in so many sizes and colors with capabilities that have yet to be tapped or even imagined. Assistant Professor of Electrical Engineering and Applied Physics Alireza Marandi is in the business of dreaming up these lasers and creating them in the lab.
Marandi’s latest investigation involves mode-locked lasers, which emit light in steady pulses rather than in a single continuous beam. These pulses can be extremely short, counted in picoseconds (trillionths of a second) or femtoseconds (quadrillionths of a second), and can carry ultrahigh powers in such short times. Pulses from mode-locked lasers have been used in many applications, such as eye surgery, by providing narrowly targeted cutting power without creating the undue heat that a continuous laser beam would cause.
Mode-locking involves locking the amplitudes and phases of the light waves that traverse a laser’s resonant cavity. When mode-locking is achieved, these resonant waves act in concert, typically forming a steadily pulsing pattern. Marandi’s team adds topological robustness to a mode-locked laser by introducing specific couplings among the resonant light pulses in the laser cavity.
The resulting topological temporal mode-locking creates laser pulse patterns that can tolerate imperfections and disorders arising from manufacturing or environmental noise sources.
“This fundamental research could potentially have many applications,” Marandi says. “By realizing topological behaviors in mode-locked lasers, we are essentially creating a knot that can make the laser’s behavior more robust against noise. If the laser is ordinarily mode-locked and you shake it, everything goes crazy. But if the laser pulses are knotted together, you can shake the system, and nothing chaotic will happen, at least for a certain range of shakings.”
Topologically protected mode-locked lasers can create better frequency combs used in communication, sensing, and computing applications. “The output of a mode-locked laser in the frequency domain is a frequency comb, that is, many equidistant narrow spectral peaks,” Marandi explains. “Frequency combs are typically prone to noise sources and environmental instabilities. By utilizing the topological behaviors in a mode-locked laser, the resulting frequency comb can protect against some noise sources.”
In the future, Marandi hopes to utilize the rich physics of this new type of laser to access regimes of nonlinear topological physics that are not accessible with other experimental platforms as well as developing advanced types of sensors and computing hardware.
Written by Cynthia Eller
Source: Caltech
You can offer your link to a page which is relevant to the topic of this post.
#applications#Behavior#Business#caltech#colors#communication#computing#computing hardware#continuous#cutting#disorders#engineering#Environmental#experimental#eye#frequency combs#Fundamental#Fundamental physics news#Future#Hardware#Heat#it#laser#lasers#Light#Link#Manufacturing#mind#multiple laser beams#noise
0 notes
Text
The unconscious does have a spatial
geometric topological position but it also is dynamic operative and has a temporal structure as well it's not just spatial that's why all this emphasis in psychoanalysis on the where can be misleading where it was so on and so forth the spatiality of the unconscious this
other place is completely important it's very relevant crucially missed though often in those conversations is the way that the unconscious was a temporal structure it moves also according to time in fact the movement of the unconscious
when it pops up and when it goes away is by way of temporal pulsation these are pulses in time openings in time at the level of symptomatic expression slip and the like but allow for the unconscious define expression and then also the transference which will be the opposite which would be a closure transference is important because it shows you where there is an opening for the unconscious although
that opening is presently closed so you see at the level of the unconscious a structure
that's not just linguistic but also edge-like that's going to be important as well to
remember so even readings of unconscious the level of structure can oftentimes go astray
it's not just that the unconscious is structured like a language it's that it also has an edge-like structure that's going to become important in this essay position of the unconscious but it also has a key operation there's an operationality of the unconscious and its move is by temporal pulsation
you have openings that are oftentimes caused by trauma the Primal scene as an incision or a cut that
produces an opening and opening through which further down the road symptomatic Expressions can pop up it's the causeway for symptoms but it also has closings the trauma is also what allows for repression a closing of sorts and further down the road transference which as you heard me just say is also a closing of sorts if you've read seminar 11 you know I'm not straying far from this text this is
Lacan breaking down basically how the structure of repression and return of the repressed works
you're cruising along you have a traumatic experience a signifier of that experience is repressed it goes into this newly founded place called The unconscious where it then mixes up with other signifiers and then later on in a
different scenario circumstance you have a return of the repressed because that signifier now connects to another signifier in your environment and pow the trauma and that symptomatic pow are
openings temporal pulsations pulsations in the
lived experience of the individual moments of seizure or rupture openings in time openings for something other than just the elapse of time
something more retrospective more insightful psychoanalytic animesis is what I'm
talking about here the re-subjectivization of one's past to transform it into one's history
-Samuel McCormick
0 notes
Text
https://www.linkedin.com/pulse/structural-topology-optimization-software-market-foreseen-shaikh-ztpfe?trackingId=hDnG6NbwMVQTwDxHacvlqw%3D%3D&lipi=urn%3Ali%3Apage%3Ad_flagship3_profile_view_base_recent_activity_content_view%3BdYjTZdQNQh6%2BiQ5SpQLm4A%3D%3D
0 notes
Text
Bluetooth in Hospitals:How BLE AoA Help Streamline Hospital Asset and Personnel Management
Hospitals are usually large and complex institution organizations faces with ineffective running issues. The most typical one is to managing a large number of medical staff, patients, and equipment, especially in personnel scheduling, resource allocation and safety monitoring.
Challenges Faced by Traditional Hospitals
Inflexible personnel scheduling: In the hospital setting, it's crucial to schedule medical staff flexibly to accommodate varying departmental, ward, and work requirements. However, traditional personnel scheduling techniques frequently prove low-efficiency and prone to error.
Inefficient medical equipment management: Resource waste are frequently caused by the lack of information about the distribution and usage of medical equipment in a timely manner.
Security challenges in hospital environments: Lost equipment and missing patients are always possible security hazards inside the hospital. Obviously, traditional monitoring methods have their limitations and are unable to provide real-time perception and early warning.
Benefits of Using Bluetooth Positioning in Hospitals
The Bluetooth-based hospital personnel and equipment positioning solution represents an innovative approach to meeting the demands of modern smart hospital management. This solution enables real-time tracking and monitoring of staff and equipment within the hospital by harnessing advanced technologies such as BLE AoA positioning technology, wireless connectivity, and data analysis.

Source: bluetooth.com
Why Bluetooth in Hospitals?
Pervasive Role in Various Medical Wearables and Medical Equipment
Bluetooth technology has been extensively used in medical wearables such as fitness trackers, glucose monitors, pulse oximeters, and more. It has taken over the consumer electronic device market for years, and is able to integrate with many popular IoT operating systems including Android, Windows, iOS, etc., making BLE embedded applications functions optimally in devices using these OSs. Meanwhile, Bluetooth technology is progressively replacing wired alternatives in recovery rooms, operating rooms, and intensive care units (ICUs). Know more BLE advantages over Zigbee here.
Frequency Hopping to Mitigate Radio Interference
The stability of wireless radio-frequency technology may worry hospitals. Having too many devices broadcast data on heavily trafficked channels can produce radio interference and distorted signals, which may cause healthcare facilities to pause.
However, Bluetooth employs adaptive frequency hopping (AFH) to lessen such an effect in surroundings. BLE devices can use AFH to determine which channels are in use and employ hop sequencing to avoid accessing these occupied channels. Due to the significant reduction in radio impedance, Bluetooth packets are able to pass through even the difficult interference sources, making it is the perfect addition to any wireless infrastructure.
Low Energy Consumption to Prolong Device Battery Life
Bluetooth Low Energy (LE) is a technology marketed as Bluetooth Smart and integrated into version 4.0 of the Core Specification was completed in early 2010. It is designed for very low power operation, transmitting data over 40 channels in the 2.4GHz unlicensed ISM frequency band.
Bluetooth LE supports a variety of communication topologies, ranging from point-to-point to broadcast and mesh, making it possible to build dependable, extensive device networks. In order to meet the growing need for highly accurate indoor location services, Bluetooth LE is also commonly employed as a device positioning technology.
A wide range of medical devices like such as blood glucose monitors use BLE technology to improve patient condition monitoring and care. Thanks to the power efficiency of Bluetooth LE, these devices can operate for years on small, coin-cell batteries.
BLE technology is used in a wide variety of medical equipment, including blood glucose monitors, to enhance patient status monitoring and treatment by transmitting data via BLE gateways. These gadgets can run for years on tiny coin-cell batteries because of Bluetooth LE's power economy.
Large-Scale Device Networking to Enhance Healthcare Efficiency
Hospitals can quickly create large-scale device networks with BLE mesh technology and use the automated system to manage and keep an eye on tens, hundreds, or thousands of staff, patients and devices. This will aid healthcare facilities in reducing costs, improving patient care, and increasing operational effectiveness.
As an illustration, hospitals may think about deploying a BLE-based remote patient monitoring solution to track patients vital signs at any time, anyplace. Facilities may also track patients' whereabouts within hospitals, which could benefit emergency services by enabling nurses to locate lost patients more quickly.
How Does Bluetooth AoA Work to Help Optimize Hospital Management?
To enable Bluetooth Angle of Arrival (AoA) positioning within a medical facility, you first need to install Bluetooth AoA locators (some people also call them positioning base stations) on the ceiling or walls of the hospital building. These locators are capable of transmitting Bluetooth signals into the surrounding environment and receiving signals from Bluetooth-tagged devices.
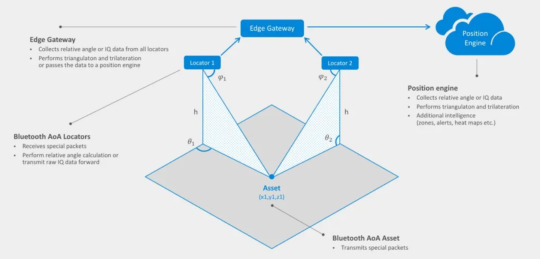
In the process of signal transmission between the locator and the Bluetooth tag, a critical technology comes into play, known as the Angle of Arrival (AoA) based on the Bluetooth 5.1 Direction Finding function. It is a kind of algorithm calculating the time difference received by different antennas.
That is, when the Bluetooth chip activates the carrier amplitude and phase transmission and reception values of the Bluetooth radio frequency end, the signal is calculated using the I/Q value (phase value) according to different antenna array designs. By analyzing the signals received at two distinct endpoints with varying orientations, the algorithm accurately determines the location of the transmitting endpoint.
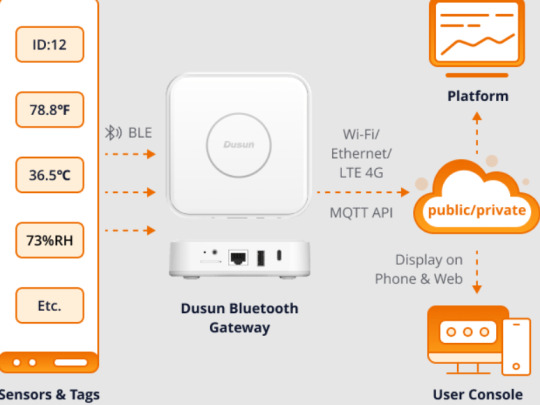
Hospital can also develop a specialized application for medical staff and install it on mobile devices, such as smartphones, tablets or handheld devices. With this app in place, hospital management staff gain the convenience of real-time monitoring and management capabilities accessible anytime and from anywhere.
Final Words
While Bluetooth Angle of Arrival (AoA) positioning has the qualities of high accuracy, high concurrency, low power consumption, low cost, and high interoperability, it is not flawless. Technically speaking, Bluetooth AoA is susceptible to signal reflection interference, antenna array errors, and the complexities stemming from environmental and antenna directional disturbances. On the other hand, the development time of Bluetooth AoA high-precision positioning is short, which strongly tests the technical strength of Bluetooth AoA positioning platform suppliers.
However, in the field of medical and health care, Bluetooth AoA positioning proves to be an invaluable solution for a range of scenarios, including hospital indoor navigation, medical and security personnel scheduling, high-value medical equipment tracking, managing special patient cases, and preventing maternal and infant abduction, etc. This technology has demonstrated its capacity to significantly enhance hospital management efficiency in these healthcare settings.
0 notes
Text
The Expressiveness of the Body and the Divergence of Greek and Chinese Medicine, Shigehisa Kuriyama (1999)
“physicians of the empiricist school insisted on the distance separating the anatomical definition of the pulse and the actual experience of the fingers.”
“How do pulse and palpitation differ?”
“Basic to this divorce was the new perception of the body defined by dissection.”
“transform…from a vague occasional oddity into a vital sign”
“systematic anatomy”
“The earliest evidence of systematic anatomy appears in the animal dissections of Aristotle”
“Phlebes, moreover, stretched the length of the body in routes that cannot be directly matched with anatomical blood vessels.”
“Praxagoras also took an interest in both dissection and pulsation.”
“physicians of the empiricist school insisted on the distance separating the anatomical definition of the pulse and the actual experience of the fingers. What our fingers feel, the empiricists contended, is merely the sensation of being struck.”
“no necessity dictates the pulsetaker’s approach. There are other ways to cradle meaning at the wrist.”
“roughly mirrored the spatial organization of the body”
“All approaches took for granted that the meaning of what the fingers felt, depended on where they felt.”
“its grammar was topological”
“Greek diagnosticians evinced little interest in, or even awareness of, the differing feel of the pulse in distant parts.” [in different parts, different places]
“one inspects the wrist because the pulse there can be felt clearly”
“he conjures of the image of their frantic panting”
“No major blood vessel matches these meanderings from ankle to eye.”
“how and why treating one site on the body solved [involved] suffering in other, distant parts”
1 note
·
View note
Text
STMicroelectronics releases 100V industrial-grade STripFET F8 transistor with 40% higher figure of merit

【Lansheng Technology Information】On May 24, STMicroelectronics' STL120N10F8 N-channel 100V power MOSFET has extremely low gate-drain charge (QGD) and on-resistance RDS(on), and the figure of merit (FoM) 40% higher than the previous generation of similar products.
The new MOSFET from STMicroelectronics utilizes ST's STPOWER STripFET F8 advanced technology and introduces an oxide-filled trench process, which combines extremely low conduction loss and low gate charge to achieve high-efficiency switching performance. As a result, the STL120N10F8 has a maximum on-resistance RDS(on) of 4.xn--6m-fcc (at VGS = 10V) and operates efficiently up to 600kHz.
STripFET F8 technology also ensures that the output capacitance value can mitigate the drain-source voltage spike, minimizing charge and discharge energy waste. In addition, the body-drain diode of this MOSFET has a higher softness characteristic. These improvements reduce electromagnetic emissions, simplify compliance testing of the final system, and ensure electromagnetic compatibility (EMC) compliance with applicable product standards.
The STL120N10F8 has excellent energy efficiency and low electromagnetic radiation, which can enhance the power conversion performance of hard-switching and soft-switching topologies. In addition, it is the first STPOWER 100V STripFET F8 MOSFET to fully meet industrial specifications, making it ideal for motor control, power supplies and converters for telecom and computer systems, LED and low-voltage lighting, as well as consumer appliances and battery-operated equipment.
STMicroelectronics' new MOSFETs also have other advantages, including a small difference in gate threshold voltage (VGS(th)), which is useful in high-current applications and simplifies the parallel design of multiple power switches. The robustness of the new product is very strong, able to withstand 800A short-circuit pulse current impact for 10µs.
Lansheng Technology Limited, which is a spot stock distributor of many well-known brands, we have price advantage of the first-hand spot channel, and have technical supports.
Our main brands: STMicroelectronics, Toshiba, Microchip, Vishay, Marvell, ON Semiconductor, AOS, DIODES, Murata, Samsung, Hyundai/Hynix, Xilinx, Micron, Infinone, Texas Instruments, ADI, Maxim Integrated, NXP, etc
To learn more about our products, services, and capabilities, please visit our website at http://www.lanshengic.com
0 notes
Text
Operating a Dark Fiber Network: Use Cases, Complexity, Cost vs. Lit Fiber

Are you afraid of the dark? There’s no need because Lightyear’s here to shine a light on dark- fiber network connectivity.
If you’re investigating high-speed fiber options and looking for greater bandwidth and lower latency to improve the performance of your applications and services, then dark fiber or lit fiber could be the silver bullet. In this post, we’ll help you think through considerations on when to go with dark fiber.
What Is Dark Fiber?
Fiber-optic cables carry pulses of light which communicate data. So, if you’re procuring a dark-fiber line, you’re basically looking to rent an unused (or “dark”) set of fiber lines, without any of the additional transmitters usually included. To use technical parlance (according to the OSI model used to describe telecoms infrastructure), dark fiber is an unlit, layer-1 service.
Lit fiber is an adjacent service to dark fiber. With a lit-fiber service, the customer rents a dedicated fiber line, along with all the transmission equipment, from the service provider (billing for lit fiber services is also slightly different, with the cost increasing depending on tiered bandwidth usage).
At this point, you might be wondering why there’s all this fiber lying around unused, anyway? Surely, it’s expensive to lay this stuff in the first place?
It’s a valid question, and there are two main reasons.
Technological improvements. When the Incumbent Local Exchange Carriers (ILECs) first started laying down fiber, back in the late 80s/early 90s, a single fiber channel could transmit data at around 2.5 Gbps. Then the lab geeks figured out they could use Dense Wavelength Division Multiplexing (DWDM) to send multiple data streams down a single channel. Multiple streams = more bandwidth. How much more? Well, you can squeeze 32 Tbs down one channel now, which is about 12,800 times more data. So, modern fiber-optic usage leaves plenty of spare fiber for everyone.
Long-term planners laid extra capacity to save on future costs. Labor and project management makes up much of the cost of a fiber install. Those crazy 20th century ILECs figured they’d save a few bucks and installed additional fiber, far more than their requirements at the time – not anticipating the huge efficiencies DWDM would bring.
So, what’s the net result of these two factors? Depending on your geographic location, there could be plenty of dark fiber going unused that your service provider would be more than happy to lease to you.
Who Uses Dark Fiber?
Lots of folk. We’ve seen dark fiber deployed in many ways by a range of businesses who tend to have the following things in common.
Multiple, well-established static locations
A qualified team of in-house transport technicians capable of lighting a fiber network
A strong need for a secure, low latency network, with scalable network connections
These are some common users of dark-fiber networks.
Wireless Internet Service Providers (WISPs). Cellular providers often use a dark-fiber network to connect their cell towers to the data center. They’ll install and manage their own Dense Wavelength Division Multiplexing (DWDM) equipment, configured either as a point-to-point service or as an any-to-any topology, to best suit local requirements.
Municipalities. Critical infrastructure such as police stations, fire departments, and hospitals needs to be connected with as much security, reliability, and permanence as possible, making dark-fiber networks a great fit for public services.
Schools and colleges. Large, multi-campus institutions like to connect their locations securely, and enjoy the level of control a dark-fiber network provides.
Connecting two data centers. More of a business need than a use case or typical user – we’re often contacted by companies that, for one reason or another, want dark fiber to run between their data centers. Again, as a secure, predictable low-latency solution, it’s a useful addition to a wide area network (WAN).
Where Can I Get Dark Fiber?
The nearer your location to a major city, the greater the chance that dark-fiber services are available to you. There are fiber lines running between the major cities, too.Outside of major cities and their connective infrastructure, it becomes trickier for carriers to make a business case for fiber installations. As we mentioned previously, the CapEx and project management costs make it harder to recoup fiber network investment from major population centers.
Even if your location is close to a major fiber line, it’s by no means a given that you can tap directly into their line to build your dark-fiber network. Connections to a fiber line are made via splice points – and most carriers have no desire to create additional splices on the line.
Once you know where the splice points are, you can work out whether a service provider is able to offer you a fiber buildout to your locations. Think of splice points as highway onramps – even though your house might be underneath the flyover, you could still have several miles to drive before you can merge onto the highway.
To determine whether a service provider is able to offer you dark fiber, you’d work with the same set of culprits you’d deal with for lit fiber service (Zayo, Crown Castle, Lumen, and the like) and go through similar bidding processes (sounds fun, right?).
What Kind of Contracts Are Available for Dark Fiber?
If you find a carrier that owns fiber between the locations you’re looking to connect, the most common kind of dark-fiber agreement is an Indefeasible Right of Use (IRU) lease. These are usually long-term leases – typically between 20 and 30 years.
If that’s more of a bind than you’re looking for, it’s worth investigating whether potential vendors would be willing to offer an International Private Leased Circuit (IPLC). As the name suggests, IPLCs are designed for international networks, and offer shorter terms – some IPLCs even offer monthly rolling contracts.
One disadvantage of IPLCs, however, is the prohibition of subletting – you can’t rent the dark fiber out as if it was your own, which removes the possibility of offsetting the costs of your network.
If you’re looking for a lit-fiber deal, with leased fiber transmitters providing DWDM services, a term length of between three and five years is more commonplace. The costs involved for the provider are subject to change over time, so it makes more financial sense for them to ensure they can adjust equipment rental costs at more regular intervals.
Which Should I Choose – Dark Fiber or Lit Fiber?
When it comes to performance metrics, there’s little difference between these two dedicated internet services. The factors to be considered are scalability, security, and cost.
Scalability. Dark fiber isn’t infinitely scalable, due to the physics involved and the mounting cost of equipment, but it's not that far off! Also, any upgrades you carry out on your existing bandwidth capabilities are entirely your own business – no need to contact the carrier, and there are no additional monthly costs.
Lit fiber upgrades will require some negotiation with the service provider, who is likely to charge you a tiered rate according to your bandwidth requirements.
Security. Neither dark fiber nor lit fiber services provide any visibility into traffic through that part of the network – any security provision must take place after the fiber hands off to the customer premises equipment (CPE).
Cost. When comparing like-for-like network locations and provision, lit-fiber services are generally more expensive. The provider is obviously going to charge more for their leased equipment and technicians than you’d pay if you were procuring these things in-house.
However, the relatively lower cost of dark fiber is only available for customers with considerable connectivity needs – you’ll need to have fairly hefty throughput requirements to justify the outlay, although there’s often wildly unpredictable regional variations in how much providers charge for dark fiber. To run a dark fiber network, you'll need to invest in hardware as well as smart hands to run your network and deal with issues, so there is a breakeven bandwidth point where this makes sense.
Subletting fibers on your dark-fiber network can be a handy way to offset the expense of this long-term investment – although this comes with its own set of legal and contractual hassles and responsibilities with which not every business is prepared to engage.
There are several other variables to consider when gauging dark-fiber costs. These include distance from the fiber splice point, and the links used to reach the fiber line, as well as the distance between your connected locations.
This last cost can quickly mount up, depending on the range of your transmitters – should your transmitter only be effective for up to 500 miles, and your locations are several thousand miles apart, then you’ll need to install and maintain repeaters every 500 miles, increasing your project management and labor costs.
While this list of pros and cons will help you get a sense of what both these services can offer, it might not be so simple to apply this knowledge to the complexities of your business and connectivity procurement needs.
The Lightyear telecom operating system is designed to solve problems like these. With ease, you can configure a dark fiber or lit fiber network and compare options digitally, or arrange a real-time meeting to discuss your options with an experienced industry professional.
0 notes
Text
youtube
Pulse Topology by Rafael Lozano-Hemmer
Artist Page
“Pulse Topology” is composed of thousands of light bulbs suspended at different heights that create a series of crests and valleys—an intimate landscape that visitors are invited to traverse. Each light bulb glimmers to the pulse of a different participant, which contributes to a connective arrangement. Custom-made pulse sensors record visitor heartbeats; when a new participant interacts with the installation, their pulse is added to the canopy of recordings above them, with the newest recording replacing the oldest.
Forming a platform for self-representation, in “Pulse Topology” individual heartbeats come together to form an immersive chorus of light and sound. Translating an interior force to an exterior form, the piece makes tangible the otherwise invisible register of the heartbeat, which glows and then fades in the spirit of a memento mori.
1 note
·
View note
Text
Physical Layer in OSI Model
What is the Physical Layer in OSI Model?
Regarding network security and hardware support, the physical layer in OSI model is the basic level for the whole network. It identifies the equipment, including the wires, devices, frequencies, and pulses, required to connect between computers. The information is stored in bits and is transferred between devices through the nodes in this physical layer.
Now that you understand the answer to questions like What is the physical layer in the OSI model? you will also have to look at the significance it holds in the security of the whole network. The physical layer is required for network hardware visibility. The existing breed of software solutions often ignores Layer 1 in the OSI model. The lack of identifiability of the layer 1 devices may cause rogue devices to get implanted in the hardware and pose a security threat to the whole network. The physical layer identifies the devices and eliminates such bad actors. The layer also consists of a separate security procedure to ensure network safety.
Functions of OSI Model in Physical Layer
1. Representation of Bits
The physical layer in OSI model (Layer 1) takes the responsibility of transmitting individual bits from one node to another via a physical medium. It specifies the procedure for encoding bits, such as how many volts should represent a 0 bit and a 1 bit in the case of electrical signals.
2. Data Rate
The data rate is maintained by the function of Physical Layer in OSI model. The number of bits sent per second is referred to as the data rate. It is determined by a variety of factors, including:
Bandwidth: The physical constraint of the underlying media.
Encoding: The number of levels used for signaling.
Error rate: Incorrect information reception due to noise.
3. Synchronization
The function of physical layer in OSI model includes bit synchronization. The sender and receiver are bit-synchronized. This is accomplished by including a clock. This clock is in charge of both the sender and the receiver. Synchronization is achieved at the bit level in this manner.
4. Interface
The transmission interface between devices and the transmission medium is defined by the physical layer in OSI model. PPP, ATM, and Ethernet are the three most commonly used frames on the physical interface. When considering the standards, it is common, but not required, that the physical layer be divided into two:
Physical Medium (PM) layer: The physical layer’s lowest sublayer.
Transmission Convergence (TC) layer: The high sublayer of the physical layer.
5. Line Configuration
The function of physical layer in OSI models includes connecting devices to the medium or line configuration. Line configuration, also known as a connection, is the method by which two or more devices are connected to a link. A dedicated link connects two devices in a point-to-point configuration. A device can be a computer, a printer, or any device capable to send and receive data.
6. Topologies
The physical layer in OSI model specifies how different computing devices in a network should be connected to one another. A network topology is a configuration by which computer systems or network devices are linked to one another. Topologies can define both the physical and logical aspects of a network. Mesh, Star, Ring, and Bus topologies are required for device connectivity.
7. Transmission Modes
The physical layer in OSI model specifies the transmission direction between two devices. Transmission mode refers to the method that is used to transfer data from a device to another device. The physical layer in the OSI model primarily determines the direction of data travel required to reach the receiver system or node. Transmission modes are classified into three types:
Simplex mode
Half-duplex mode
Full-duplex mode
Modes of Transmission Medium:
Well, now we know ‘what is the physical layer in the OSI model?’. However, what are the common modes of data transmission?
How data is transferred between two interconnected devices, the direction of transfer and the time when this transfer happens all pertain to the mode or medium of transmission.
Here are the 3 common modes of transmission:
Simplex mode: Here, data is transmitted from one point to another only in one direction. The data flows only from one device in a single direction and the other device simply receives the data that is coming from this direction. Take the example of a computer in which the input devices like the keyboard can only send a signal to the monitor, which receives the data and displays the output.
Half-duplex mode: Here, the two devices involved in the data communication process can send as well as receive data. This happens only one at a time and not both at the same time. What this means is that while there is a bi-directional flow of data, data does not flow from both devices simultaneously. Take the example of a walkie talkie where signals are being sent as well as received by the same device, but both sending and receiving doesn’t happen at the same time.
Full-duplex mode: Here, the communication between two devices happens bi-directionally and both devices can send data or receive data at the same time. Two channels exist for this purpose as both sending and receiving can happen simultaneously. The most common example that you will see of a full-duplex mode is a mobile phone, where you can talk to someone and hear them at the same time.
What are the Layers in the OSI Model?
An OSI model is made up of seven distinct layers that are typically described from top to bottom. The 7 layers in the OSI model are: application, presentation, session, transport, network, data link, and physical. These layers represent what happens within a networking system visually. Understanding the OSI model can assist in determining the source of networking issues, developing applications, and better understanding which networking products work with which layers. Each layer of the OSI Model is responsible for a specific function and communicates with the layers above and below it. DDoS attacks target specific network layers; application layer attacks target layer 7, and protocol layer attacks target layers 3 and 4.
1. Physical Layer
In the Open System Interconnection (OSI) Model, the Physical Layer is the lowest layer. The physical layer in OSI model is in charge of transmitting data from one computer to another. It is not concerned with the data of these bits but rather with the establishment of a physical connection to the network. It interacts with actual hardware as well as signaling mechanisms.
2. Data Link Layer
The second layer of the OSI model is the data link layer. It is also known as layer 2. The data link layer controls the delivery of messages from node to node. The main goal of this layer is to ensure error-free data transfer from one node to another across the physical layer. The data link layer conceals the underlying hardware details and represents itself as the communication medium to the upper layer.
3. Network Layer
In the physical layer in OSI model, the network layer is the third layer. It serves two primary purposes. The “network layer” of the Internet communications process is where these connections are made by sending data packets back and forth between different networks. Furthermore, the network layer defines an addressing scheme in order to uniquely identify each device on the internetwork.
4. Transport
Layer 4 of the OSI Model, known as the transport layer, provides transparent data transfer between end users while also providing reliable data transfer services to the upper layers. The transport layer is in charge of delivering an entire message from a source device application program to a destination device application program.
5. Session
The Session Layer is the layer of the ISO Open Systems Interconnection (OSI) model that governs computer dialogues (connections). It is in charge of establishing, maintaining, synchronizing, and terminating sessions between end-user applications. It makes use of the transport layer’s services, allowing applications to establish and maintain sessions as well as synchronize them.
6. Presentation
The sixth layer in the Open System Interconnection (OSI) model is the Presentation Layer. It ensures that the message is delivered to the upper layer in a consistent format. It is concerned with the syntax and semantics of the messages. The data received from the Application Layer is extracted and manipulated in this layer so that it can be transmitted over the network.
Conclusion
The physical layer in OSI model of the interconnectivity of devices has helped secure and seamless data transfer over devices and keeps the application services connected. It is all possible because of the seven layers that it consists of. The ground layer, the physical layer, provides all the hardware connections to the network and ensures that the next processes can occur without error. So the function of the physical layer in the OSI model is pretty significant, making it important for security and efficiency reasons.
0 notes
Text
The Physical Layer in OSI Model Explained
What is Physical Layer in OSI Model?
Regarding network security and hardware support, the physical layer in OSI model is the basic level for the whole network. It identifies the equipment, including the wires, devices, frequencies, and pulses, required to connect between computers. The information is stored in bits and is transferred between devices through the nodes in this physical layer.
As you understand what the physical layer in OSI model is, you will also have to look at the significance it holds in the security of the whole network. The physical layer is required for network hardware visibility. The existing breed of software solutions often ignores Layer 1 in the OSI model. The lack of identifiability of the layer 1 devices may cause rogue devices to get implanted in the hardware and pose a security threat to the whole network. The physical layer identifies the devices and eliminates such bad actors. The layer also consists of a separate security procedure to ensure network safety.
How does Physical Layer in OSI Model Work?
Mesh Topology: It is a highly secure device connection where every device is connected through links to every other device in the network. A dedicated point-to-point connection is present, which is complex to form.
Star Topology: In this kind of device connection, all the devices are connected with a dedicated point-to-point connection to a central hub. It is easy to install but has no fault tolerance.
Bus Topology: Here, all the devices are connected with a single backbone cable which is less costly and easily re-installable.
There are several other ways, too, through which the physical layer in OSI model works, such as the end-to-end configuration.
What are the Functions of the Physical Layer in OSI Model?
1. Representation of Bits
The physical layer in OSI model (Layer 1) takes the responsibility of transmitting individual bits from one node to another via a physical medium. It specifies the procedure for encoding bits, such as how many volts should represent a 0 bit and a 1 bit in the case of electrical signals.
2. Data Rate
The data rate is maintained by the function of Physical Layer in OSI model. The number of bits sent per second is referred to as the data rate. It is determined by a variety of factors, including:
Bandwidth: The physical constraint of the underlying media.
Encoding: The number of levels used for signaling.
Error rate: Incorrect information reception due to noise.
3. Synchronization
The function of physical layer in OSI model includes bit synchronization. The sender and receiver are bit-synchronized. This is accomplished by including a clock. This clock is in charge of both the sender and the receiver. Synchronization is achieved at the bit level in this manner.
1 note
·
View note