#RC Cluster
Explore tagged Tumblr posts
Text
aspd-culture-is
Being really sick of going into what’s supposed to be “safe spaces for mental health” and still having to fight for your life to get people to stop throwing around ableist terms and talking about “n*rc abuse” and making pwBPD into cutesy victims while demonizing the rest of us. And to be clear, that hurts pwBPD too - I’m not saying they have it good from people thinking that.
Like wtf is the point of being in these “safe spaces” at all if I’m gonna have to argue the same points I’d have to outside of them. This is why the words “mental health safe space” mean nothing to me unless they’re particular about bringing up all cluster b not just some.
Partially my fault for thinking it’d go any other way tbh.
Plain text (including uncensored ableist term) below the cut:
ASPD Culture Is
Being really sick of going into what’s supposed to be “safe spaces for mental health” and still having to fight for your life to get people to stop throwing around ableist terms and talking about “narc abuse” and making pwBPD into cutesy victims while demonizing the rest of us. And to be clear, that hurts pwBPD too - I’m not saying they have it good from people thinking that.
Like wtf is the point of being in these “safe spaces” at all if I’m gonna have to argue the same points I’d have to outside of them. This is why the words “mental health safe space” mean nothing to me unless they’re particular about bringing up all cluster b not just some.
Partially my fault for thinking it’d go any other way tbh.
33 notes
·
View notes
Text

RC Harris Waterworks No 3 Old Film Version.
Designed in the 1920s, constructed in the 1930s and opened in 1941, The R.C. Harris Water Treatment Plant is a cluster of three Art Deco style buildings at No 2701 Queen St E in Toronto Canada. The plant produces more than 950 million litres of clean water daily which is almost 45% of the cities tap water. The buildings were designated a Heritage Property by The City of Toronto in 1998.
Original photography using a Canon EOS T1i body with a Canon EF-S 17-85mm f/4-5.6 IS USM lens and Analog EFEX Pro 2 as a Lightroom plugin for the Old Film effect.
Brian Carson The Learning Curve Photography linktr.ee/thelearningcurvephotography
#toronto#canadian#photography#photographers on tumblr#original photographers#original photography#pws#lensblr#architecture photography#originalphotography#architecture
2 notes
·
View notes
Text

Here is a reference sheet for a spaceship, the Blue Dawn, an exploratory vessel. It started out as a stationary Bernal sphere inhabited by Akina until they was offered the chance to explore the cosmos, the bridge came with an AI to help the crew. At the time, it only had a single food production ring, with more being added as the crew grew and other species were discovered. Crew tend to go on space walks and draw on the hull, sometimes doing large scale artwork, eventually covering most of the hull with graffiti. The numbered components are these: 1. Whipple shield, it is silvery with a black spiral painted into it; 2. Bridge, installed on the habitat at the same time as the thrusters and fuel tank and later upgraded by the Pale Spires with a biological brain into which the ship's AI was downloaded, someone laser engraved their name into it; 3. Frontal sensor array, allows the Blue Dawn to «*see*» directly in front of it, it is heavily shielded and has redundant components; 4. Extendable sensor clusters, contain the more sensitive sensors and retract behind the shield when traveling at relativistic speeds; 5. Food production and alien accommodations, they possess advanced life support systems to house various alien species as comfortably as possible; 6. High gravity accommodations, for those who prefer higher gravity, installed before the other two rings around the original food production facility; 7. Bernal sphere, the original habitat, its interior is a cool and urban with high humidity and an average temperature of 40-45ºC and extensive gardens of home world fauna and flora, it also contains many fuel tanks which serve as radiation shielding; 8. Hangar ring, this is where shuttles, probes and drones are made, repaired and maintained; 9. External fuel tank, not much to say apart that it is internally divided to prevent sloshing and excessive fuel loss if punctured and it has a target painted on it; 10. Main thruster, powered by monopole catalysed fusion and baryon decay, it emits a prodigious amount of radiation; 11. RCS, same technology as the main thruster, but smaller and able to be aimed to some degree. !!Attention, the radiators have been omitted.
6 notes
·
View notes
Text
I'm going back to crocheting in a bit, but my biggest pet peeve is everyone clustering imperial clones and storm troopers as one thing which they are, in fact, not.
Storm troopers are TKs and DTs. Clone troopers are RC, CC, CT, ARC, and ARF. They are not the same.
#ooc :\\ hey panini head!!!#mobile :\\ jet🌺#[ Sb made a test of ppls knowledge of clones and called howzer a storm trooper which he is nOT ]
2 notes
·
View notes
Text
Community Health Nursing Flyer Flyer Proper health habits among middle aged people This information targets middle aged persons, ages 40-50 years. The information is to help improve on the health of middle aged persons by avoiding practices that cause obesity which would result into various health problems. Problems arising from obesity One problem associated with obesity is the increased risk of developing dementia at a later age in one's life. According to a study conducted in the Denese et al. 2009, people who are obese in their middle ages have a greater risk of developing dementias, an example being Alzheimer, later in life than those with normal weight. The Alzheimer disease is the most common form of dementia and develops differently among different individuals. Dementia, which is the gradual decline in cognitive ability, previously associated with old age. Another problem associated with obesity is depression in women. A study conducted by Simon et al. 2004, concluded that, in middle aged women, depression is strongly and constantly connected to obesity. The other problem associated with obesity in middle aged people is shorter life span. A study conducted by Simon et al. 2004, show adults who were obese at age 40 lived 6 to 7 years less than those who had normal weight. Other problems associated with obesity are diseases such as diabetes, knee arthritis and having high blood pressure. To curb the problem of obesity community participation is crucial. This is because the problem of obesity has some unique characteristics among different communities. Summary The target group for this flyer is the middle age group which is the group between ages 40 to 50 years. This is because this is the group most prone to obesity due to their economic status where they are the group who are most economically stable (Simon, Pronk, Martinson, Kessler, Beck, Wang, 2004). Distribution of flyers will be in grocery stores and offices. In grocery stores is the right place to reach people who are buying foodstuffs. People buying in grocery are the ones who might be aware of problems associated with obesity. People in offices are also prone to obesity due to their lack of exercise and also from their high tendency to eat junk foods (Simon et al., 2004). Those in attendance will give necessary information on the best ways of dealing with obesity. The information in books and articles is useless unless read and implemented, therefore, what is essential is to find out what various people have done in practice and has worked in dealing with obesity (Danese, Moffitt, Harrington, Milne, Polanczyk, Pariante & Caspi, 2009). Those in attendance will be able to share life experiences on the problem associated with obesity and thus help in identifying ways of dealing with this problem. There will be doctors available to help give their own views and medical solutions to those who are obese. Those in attendance will be able examine their health status. The utmost benefit will be to obese persons as they will be able to share and learn ways of dealing with obesity without affecting their health negatively (Danese et al., 2009). References Danese, A., Moffitt, T.E., Harrington, H., Milne, B.J., Polanczyk, G., Pariante, C.M., & Caspi, A. (2009). Adverse childhood experiences and adult risk factors for age-related disease: Depression, inflammation, and clustering of metabolic risk factors. Archives of Pediatric and Adolescent Medicine, 163(12), 1135-1143. Simon GE, Pronk NP, Martinson B, Kessler RC, Beck AL, Wang P. The association between work performance and physical activity, cardiorespiratory fitness, and obesity. J Occup Environ Med. 2004;46: 19 -- 25. https://www.paperdue.com/customer/paper/community-health-nursing-flyer-proper-health-83058#:~:text=Logout-,CommunityHealthNursingFlyerProperhealthhabits,-Length2pages Read the full article
0 notes
Text
The S2 Engine: building a better Hitbox



The S2 Engine is a leverless controller layout intended to allow you to play a wider variety of games with arcade style controls. A revision of the S2 Drive, which was designed with retro style games in mind, it combines WASD style directional controls with the spacebar style jump button popularized by the Hitbox.
The goal here was to keep a “home row” position for your hands, with the consideration that it's much faster and more comfortable to close your fingers than to extend them.
Two thumb buttons allow easy access to the trigger buttons, with oversized pinky buttons for auxiliary functions. This has the advantage of allowing both thumbs to access the jump button, with the thumb buttons replacing the hard to reach pinky column, making it easier to hit or hold with other buttons.
youtube
The layout gives you the advantages of a regular leverless layout for fighting games, with the benefit of more intuitive navigation in menus, 2D action games and even 3D space. Combined with a remappable controller firmware, it allows a wider range of applications than both traditional leverless and arcade stick layouts.
I have two recommended button mappings, one more in line with the traditional fightstick layout, and a more universal one suited to all kinds of games.

The first remaps the third column from R1 and R2 to both shoulder buttons, with L1 on the top and R1 on the bottom. This allows easier navigation through menu tabs, instead of the reversed left and right positions of the shoulder buttons on a traditional layout.
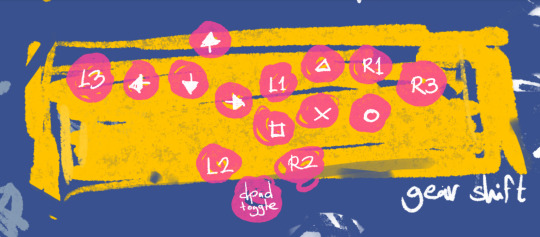
The second puts most of the face buttons on the same row, aligning them in a mirrored WASD position on the other side of the buttons, with the shoulder buttons flanking them. Square, cross, and circle are on the bottom row, with triangle above the cross button, and L1 and R1 to the side of the triangle button. Games commonly focus their main actions on the square, cross and circle buttons, so this allows you to access most of them at the same time without finger movement. The positioning of the L1 and R1 buttons allow more intuitive menu navigation, and directional actions.
Both trigger buttons are positioned on the thumb buttons to the side of the large jump button, with the up button duplicated in the WASD cluster, and the L3 and R3 flank the direction and action buttons.
LAYOUT DEMONSTRATIONS
Here's some example layouts as a demonstration.

For Street Fighter 6 this allows you to play with both classic and modern controls. On classic you get the usual 6 button layout on top, with the shortcuts for Drive Parry, Drive Impact or throw on the thumb or pinky buttons. You can even forego one of the up buttons to turn either into another macro. Personally, I use the right pinky for Drive Impact and the right thumb for parry, with throw and character specific functions on the remaining two.

On Modern this layout makes it easier to use the assist feature by mapping it to a thumb button, allowing the rest of your fingers to rest on top with the light, medium and heavy buttons, with some flexibility on where you'd like the special and shortcut buttons to be.

For Guilty Gear Strive I like to map the thumb buttons to dash and roman cancel, to get easy drift RC. I always found it hard to integrate the dash button in the main six button cluster, and this mimics the natural action of left trigger right trigger that I'm used to on controller.

For games with a block button the thumb buttons are a lifesaver. In Mortal Kombat, the top buttons handle the four attacks, throw and stance flip, while the thumb buttons allow me to hold block and call assists. MK always felt like it didn't have a good solution on a standard arcade layout. Either the attack buttons get stuck in the middle, or shoved to one side with the others requiring you to stretch to use all of them.

In Soulcalibur I keep the block button in the main cluster since I default to using the button combos instead of shortcuts, but I do like keeping the thumb buttons ready for stance macros and easy supers.

In Tekken 8 I use the the top 6 buttons for the standard 4 attacks and multibuttons shortcuts, with Rage on the thumb button, Heat on the right pinky and the left pinky for awkward button combinations.

How about something less conventional? Here's Gundam Versus. Typically you play this on an arcade stick since it only uses 8 directionals and a behind the back camera. The WASD cluster here makes it more natural and even lets you do moves like dashes and blocking (down to up) faster. Again, you can give up the larger UP button and use it for communication commands, or burst.

And here's Virtual-On. This makes it easier to hit the turbo modifiers and attack buttons together and perform fast jump cancels. You can even emulate the twin stick setup of the arcades with it. Which is also useful if you want to play some 8 way twin stick shooters.
If you're running GP2040CE you can even use it for 3D action games. A lot of action games don't rely on analog inputs, only differentiating between 8 directions and rarely needing to walk, and often allow you to get away with centering the camera behind the back with a button instead of messing with the right stick. Simply set the directions to the left analog stick, and set the bottom jump button to a dpad modifier so you can access those functions.
This works great in PS2 era action games like Nightshade, which requires you to quickly chain movement and attacks, or older Devil May Cry games, where it's much easier to perform precise inputs like enemy step attacks.

On my personal controllers, I've even added aux ports that allow me to plug in pedals, to go full pianist style, getting quicker reactions for shortcuts like Drive Impact, or adding modifiers to control the camera.
And of course, since it was designed with retro games in mind it works great for that, easily adapting to the six button layouts of the Genesis, Saturn and arcade games, and allowing you to play SNES games that rely on the shoulder buttons much easier.
HOW DO I BUILD ONE?
So how do you get this layout? For my part, I've mostly been creating prototypes for this layout by hand, with a power drill and step bit. But for my final build I went to Eternal Rival with my custom layout, and other case builders such as Jonyfraze, and AllFightSticks can also do custom layouts.
I originally finished this layout over a year ago, before Street Fighter 6, and those were kind of your only options for thumb buttons. Since then the leverless controller scene has blown up with different takes, and you've got quite a few options for something similar.

I personally like Mavercade's KeebBrawler-04MX, with its pill shaped buttons and split layout, but they also have a Keebfighter line with some similar layouts.

The Zenpad Duel has a split dual thumb button layout, and Attachon and Rush box have layouts with pinky and thumb buttons. Jonyfraze offers the 6GAWD for both leverless and fightstick builds. Hell, you could even go for something like a box style controller for Smash.

I'm less impressed with the offerings from companies like Haute42, which seem to just staple buttons onto the existing layout with no consideration for access or aesthetics, but they are an option for those looking for a cheap way to test a thumb button layout.
Whatever way you choose to go, it's undeniable that we're in an era of rapid controller innovation, with tons of different philosophies on how to build better controllers, and fresh ideas coming out all the time. The S2 Engine is what works best for me, but with so many options out there now, it'd be a waste to not experiment and find your personal favorite.
0 notes
Text
Mandiant Finds UNC5820 FortiManager For Data Exfiltration

Mandiant and Fortinet worked together in October 2024 to look into the widespread abuse of FortiManager appliances across more than fifty potentially compromised FortiManager devices in a range of businesses. A threat actor can use an unauthorized, threat actor-controlled FortiManager device to run arbitrary code or commands against susceptible FortiManager devices with the vulnerability, CVE-2024-47575 / FG-IR-24-423.
As early as June 27, 2024, Mandiant saw a new threat cluster that is currently monitor as UNC5820 taking advantage of the FortiManager vulnerability. The configuration information of the FortiGate devices controlled by the compromised FortiManager was staged and exfiltrated by UNC5820. Along with the users and their FortiOS256-hashed passwords, this data includes comprehensive configuration details for the controlled equipment. UNC5820 might utilize this information to target the enterprise environment, advance laterally to the controlled Fortinet devices, and further attack the FortiManager.
The precise requests that the threat actor made in order to take advantage of the FortiManager vulnerability were not yet documented in the data sources that Mandiant examined. Furthermore, as of this point in Google cloud study, there is no proof that UNC5820 used the configuration data it had acquired to migrate laterally and endanger the environment even more. It therefore don’t have enough information at the time of publication to evaluate actor location or motivation. Mandiant will update this blog’s attribution assessment as new information emerges from investigations.
A forensic investigation should be carried out right away by any organizations whose FortiManager may be exposed to the internet.
Exploitation Details
The first known instance of Mandiant being exploited was on June 27, 2024. Several FortiManager devices were connected to the default port TCP/541 on that day via the IP address 45[.]32[.]41[.]202. Around the same time, the file system stored the staging of different Fortinet configuration files in an archive called /tmp/.tm that was compressed using Gzip. The files and folders mentioned in below Table were included in this bundle.FilenameDescription/var/dm/RCSFolder containing configuration files of managed FortiGate devices/var/dm/RCS/revinfo.dbDatabase containing additional information of the managed FortiGate devices/var/fds/data/devices.txtContains a list of FortiGate serials and their corresponding IP addresses/var/pm2/global.dbGlobal database that contains object configurations, policy packages, and header and footer sensor configuration for IPS/var/old_fmversionContains current FortiManager version, build, and branch information
Mandiant noticed a second attempt at exploitation using the same symptoms on September 23, 2024. Outgoing network traffic happened soon after the archive was created in both exploitation scenarios. The size of the archive is marginally less than the number of bytes delivered to the corresponding destination IP addresses. The specifics of this action are listed in below Table .
The threat actor’s device was linked to the targeted FortiManager during the second exploitation attempt. Figure shows the timestamp at which the illegal FortiManager was introduced to the Global Objects database.
The threat actor’s unknown Fortinet device showed up in the FortiManager console after they had successfully exploited the FortiManager.
The files /fds/data/subs.dat and /fds/data/subs.dat.tmp contain additional indicators of the exploitation that include an associated disposable email address and a company name as listed in Figure .SerialNumber=FMG-VMTM23017412|AccountID= [email protected]|Company=Purity Supreme|UserID=1756868
Lack of Follow-On Malicious Activity
Mandiant examined rootfs.gz, the device’s initramfs (RAM disk) that is mounted to /bin. During the period of exploitation activity, did not discover any malicious files that had been produced or altered.
Affected clients who displayed comparable activities in their environments were alerted by Google Cloud. In order to help identify Fortinet device exploit attempts, Google Cloud Threat Intelligence also conducted retrohunts while creating detections for this activity and manually escalated Pre-Release Detection Rule notifications to impacted SecOps customers.
Apart from working with Mandiant, Fortinet made aggressive efforts to notify its clients in advance of their advise so that they may improve their security posture before it was widely made public.
Mitigation Strategies / Workaround
Restrict only authorized internal IP addresses from accessing the FortiManager admin portal.
Permitted FortiGate addresses should be the only ones allowed to connect to FortiManager.
Deny FortiManager access to unidentified FortiGate devices.
Available 7.2.5, 7.0.12, 7.4.3 and later (not functional workaround on 7.6.0). config system global set fgfm-deny-unknown enable end
Detection
YARA-L
IOCs mentioned in this blog post can be prioritized using Applied Threat Intelligence, and rules were released to the “Mandiant Intel Emerging Threats” rule pack (in the Windows Threats group) if you are a Google SecOps Enterprise+ customer.
Relevant Rules
Suspicious FortiManager Inbound and Outbound Connection
UNC5820 Fortinet Exploitation and File Download
UNC5820 Fortinet Exploitation and non-HTTPS Command and Control
UNC5820 Fortinet Exploitation and HTTPS Command and Control
Other SIEMs
Create searches for the following pertinent IOCs using Fortiguard logs. Specifically, if activated, the Malicious Fortinet Device ID need to deliver a high quality alert.
In the FortiManager logs, establish baselines and thresholds for distinct processes. Specifically, “Add device” and “Modify device” procedures can be infrequent enough for your company to issue a useful warning until this vulnerability is fixed.
In the FortiManager logs, baseline and establish thresholds for the changes field. When the word “Unregistered” appears in the changes field, take into account a higher sensitivity.
Every day, count the Fortigate devices and notify you when a device name that hasn’t been seen in the logs is detected.
Indicators of Compromise (IOCs)
Registered users can access a Google Threat Intelligence Collection of IOCs.
Read more on govindhtech.com
#MandiantFinds#UNC5820FortiManager#GoogleSecOps#Googlecloud#DataExfiltration#ThreatIntelligence#AdditionalKeywords#Workaround#MitigationStrategie#MaliciousActivity#technology#technews#news#govindhtech
0 notes
Text
Top Bikes Under ₹3 Lakh: Featuring Traction Control for a Safer Ride

If you’re in the market for a new motorcycle, your budget plays a significant role in determining the right fit. Fortunately, in India, there are a wide range of bikes under ₹3 lakh that come loaded with modern features like traction control for added safety. In this guide, we’ll explore some of the best bikes under ₹3 lakh that deliver a perfect balance of power, performance, and safety.
1. TVS Apache RR 310
One of the best bikes under ₹3 lakh, the TVS Apache RR 310 is known for its sporty performance and premium features. It comes equipped with a 312cc engine producing 34 bhp, offering smooth performance for daily commutes and long rides. What makes the Apache RR 310 stand out is the rider modes that include traction control, ensuring stability even during high-speed rides.
Price: ₹2.99 Lakh Key Features:
312cc engine
Traction Control
SmartXonnect system with Bluetooth
Dual-channel ABS
2. KTM RC 390
The KTM RC 390 is one of the best bikes in India for under ₹3 lakh, offering a perfect mix of speed and safety. With a 373cc engine and 43 bhp, this bike is built for thrill-seekers who don’t want to compromise on safety. It features traction control, which is essential for maintaining balance and preventing wheel slippage during cornering or wet conditions.
Price: ₹3.16 Lakh (on-road, slightly above budget, but worth mentioning) Key Features:
373cc engine with 43 bhp
Traction Control System
Dual-channel ABS
TFT display with smartphone connectivity
3. Bajaj Dominar 400
The Bajaj Dominar 400 is a value-for-money option for those looking for a powerful touring bike under ₹3 lakh. Powered by a 373cc engine with 40 bhp, this bike is equipped with a traction control system, ensuring safer rides on long highways or unpredictable terrains.
Price: ₹2.29 Lakh Key Features:
373cc engine with 40 bhp
Dual-channel ABS
LED headlights
Traction control
4. Yamaha R15 V4
The Yamaha R15 V4 is another strong contender when it comes to finding the best bike under ₹3 lakh. With its 155cc engine and impressive performance, the R15 V4 is a popular choice among younger riders. Though it doesn’t offer traction control, its quick-shifter feature is a welcome addition, making it a standout in the 150cc category.
Price: ₹1.81 Lakh Key Features:
155cc liquid-cooled engine
Quick-shifter
Assist and slipper clutch
Fully digital instrument cluster
5. Honda CB300R
The Honda CB300R is a compact yet powerful street bike that sits comfortably under ₹3 lakh. Its 286cc engine delivers 30.7 bhp, making it one of the best bikes in India for urban commuting as well as weekend getaways. While it lacks traction control, the CB300R’s light body and nimble handling make it a joy to ride.
Price: ₹2.77 Lakh Key Features:
286cc engine
Lightweight and agile
Dual-channel ABS
Minimalist design
Conclusion
With a budget of ₹3 lakh, there are several excellent bikes available in India that combine performance, safety, and advanced features like traction control. Whether you’re a speed enthusiast or someone who values safety and comfort, these options are some of the best bikes in India under ₹3 lakh. For those seeking added stability and control, models like the KTM RC 390 and TVS Apache RR 310 are ideal choices. On the other hand, budget-conscious buyers looking for reliability can consider the Bajaj Dominar 400 or Yamaha R15 V4.
Explore more options and compare specifications to find the bike that suits your riding style and needs.
0 notes
Text
Meta Exposes Eight Firms Behind Spyware Attacks on iOS, Android, and Windows Devices
Meta Platforms’ Actions Against Surveillance-for-Hire Companies
Meta Platforms has taken action against eight surveillance-for-hire companies based in Italy, Spain, and the United Arab Emirates (U.A.E.), as per their Adversarial Threat Report for Q4 2023. The companies were reportedly involved in malicious activities, including the development of spyware aimed at iOS, Android, and Windows devices.
The malware developed by these companies had the ability to gather and access a wide range of device data, including information about the device itself, location data, photos, media, contacts, calendar entries, emails, SMS, and data from social media and messaging apps. The malware could also activate device microphones, cameras, and screenshot functions.
The companies implicated in these activities are Cy4Gate/ELT Group, RCS Labs, IPS Intelligence, Variston IT, TrueL IT, Protect Electronic Systems, Negg Group, and Mollitiam Industries. According to Meta Platforms, these companies also engaged in data scraping, social engineering, and phishing activities across a variety of platforms, including Facebook, Instagram, X (formerly Twitter), YouTube, Skype, GitHub, Reddit, Google, LinkedIn, Quora, Tumblr, VK, Flickr, TikTok, SnapChat, Gettr, Viber, Twitch, and Telegram.
Specific Malicious Activities
RCS Labs, owned by Cy4Gate, reportedly used a network of fake personas to trick users into providing their phone numbers and email addresses, and to click on fraudulent links for reconnaissance purposes. Facebook and Instagram accounts linked to Spanish spyware company Variston IT were used for exploit development and testing, including the sharing of malicious links. Reports suggest that Variston IT is in the process of shutting down its operations.
Meta Platforms also identified accounts used by Negg Group for testing spyware delivery, and by Mollitiam Industries, a Spanish company offering data collection services and spyware for Windows, macOS, and Android, for scraping public information.
Actions Against Coordinated Inauthentic Behavior (CIB)
Alongside these actions, Meta Platforms also removed over 2,000 accounts, Pages, and Groups from Facebook and Instagram due to Coordinated Inauthentic Behavior (CIB) originating from China, Myanmar, and Ukraine. The Chinese cluster targeted U.S. audiences with content criticizing U.S. foreign policy towards Taiwan and Israel and supporting Ukraine. The Myanmar network targeted local residents with articles praising the Burmese army and criticizing ethnic armed organizations and minority groups. The Ukrainian cluster used fake Pages and Groups to post content supporting Ukrainian politician Viktor Razvadovskyi and expressing support for the current government and criticism of the opposition in Kazakhstan.
Industry-wide Efforts to Curb Spyware Abuse
This action by Meta Platforms comes as part of a broader initiative involving a coalition of government and tech companies aiming to curb the abuse of commercial spyware for human rights abuses. As part of its countermeasures, Meta Platforms has introduced new features such as Control Flow Integrity (CFI) on Messenger for Android and VoIP memory isolation for WhatsApp to make exploitation more difficult and reduce the overall attack surface.
The Persistence of the Surveillance Industry
Despite these efforts, the surveillance industry continues to evolve and thrive in various forms. Last month, 404 Media, building on prior research from the Irish Council for Civil Liberties (ICCL) in November 2023, revealed a surveillance tool called Patternz. This tool utilizes real-time bidding (RTB) advertising data from popular apps like 9gag, Truecaller, and Kik to track mobile devices. The Israeli company behind Patternz, ISA, claims that the tool allows national security agencies to use real-time and historical user advertising data to detect, monitor, and predict user actions, security threats, and anomalies based on user behavior, location patterns, and mobile usage characteristics.
In addition, last week, Enea unveiled a previously unknown mobile network attack known as MMS Fingerprint.
The Use of Pegasus-maker NSO Group’s Alleged Techniques
According to some sources, the Pegasus-maker NSO Group is believed to have employed specific techniques, as stated in a contract they had with Ghana’s telecom regulator in 2015. The exact means used by the group are still somewhat unclear. However, Enea, a Swedish telecom security firm, has put forward a plausible theory.
The Role of Binary SMS in the Suspected Method
Enea suggests that the group likely used a unique form of SMS message known as binary SMS, specifically MM1_notification.REQ. This particular message informs the recipient’s device of an MMS (Multimedia Messaging Service) that is pending retrieval from the MMSC (Multimedia Messaging Service Center).
The Process of Fetching MMS
The process of fetching the MMS involves the utilization of MM1_retrieve.REQ and MM1_retrieve.RES. The former is an HTTP GET request directed to the URL address contained in the MM1_notification.REQ message.
The Significance of User Device Information
What makes this technique particularly interesting is the inclusion of user device information such as User-Agent (distinct from a web browser User-Agent string) and x-wap-profile in the GET request. This data essentially serves as a unique identifier for the device.
Understanding User-Agent and X-wap-profile
Enea explains that the User-Agent in this context is a string that typically identifies the device’s OS and model. The x-wap-profile, on the other hand, points to a User Agent Profile (UAProf) file that outlines the capabilities of a mobile handset.
Potential Exploitation of Device Information
This device information could potentially be used by a threat actor to deploy spyware. They could exploit specific vulnerabilities, customize their harmful payloads to suit the target device, or even design more efficient phishing campaigns. However, it’s important to note that there is currently no evidence to suggest this security loophole has been exploited in recent times.
https://www.infradapt.com/news/meta-exposes-eight-firms-behind-spyware-attacks-on-ios-android-and-windows-devices/
0 notes
Photo

In Memoriam of Sonatta Morales
Sonatta past away in april 2021. Here I remind her vintage creations.
Sonatta Morales:
Haircut - Lulu V black
Gown with Gloves - Exo
Other:
MIMT - Wooden Wall
GK - Spider Couture - Gold - Necklace (not available)
RC Cluster - Hanky (not available)
#Made in Mulberry#marketplace#Vintage#Sonatta Morales#Vintage gown#retro#20's style#SL#gaming#fashion#spider web necklace#rc cluster#bob hair#wooden interior#30's
6 notes
·
View notes
Photo


October 20th, 2017
#2017#mumei#self portrait#portrait#second life#secondlife#photoblog#journal#rc cluster#redd columbia#Salchicha County
1 note
·
View note
Photo

New Post has been published on https://threadsandtuneage.com/hot-dawg/?Tumblr
Hot Dawg!
https://i1.wp.com/threadsandtuneage.com/wp-content/uploads/2019/05/Hot-Dawg-by-Duchess-Flux.jpg?fit=2047%2C1159&ssl=1
#Access#Black Bantam#Blueberry#Collabor88#Death Row Designs#DRD#Eclipse#Equal10#Genus Project#Glam Affair#HEXtraordinary#Jian#Moon Amore#no match#Oxydate#Pure Poison#RC Cluster#Salon52#Second Life#secondlife#sl#Una#iheartslFeed#Salon 52#Second Life Events
1 note
·
View note
Photo

March 3rd: Briar Rose x Aurora
Today has a tiktok theme and whilst I can't do a SL tiktok to save my life, I did do a close approximation of the 'wipe it down' tiktok meme
Oh and I did a RL tiktok too
https://vm.tiktok.com/ZMe6pej3K
pose by me backdrop @ FOXCITY. Photo Booth - Rose Bathroom
sponge @ RC - complete nasty dishes set
hair @ truth - thelma earrings @ maxi gossamer - waldorf pearl and carved roses
top @ RKKN - stefania corset moss w/poet shirt
gown @ just Because - alicia gown
#iheartsl#iheartsl feed#second life#second life fashion#second life disneybound#disneybound#march disneybound challenge#foxcity#aurora#briar rose#sleeping beauty#RC cluster#truth#maxi gossamer#rkkn#just because
0 notes
Photo


Sometimes you must Sacrifice your heart to get that which you desire....
Fun fact, @lilithvinciolo was apparently wearing a bra on her screen, but not on mine...lol.
Prop: -RC- Ritual Altars
//Wearing//
Hair: #Foxy - Morgana
Mask: *BOOM* Bonnwi Mask
Necklace: *BOOM* Bonnwi Collier
Tattoo: THIS IS WRONG Pain Tattoo (Out now @ The Bodyfy Event)
Axe: [Bad Unicorn] Redrum Axe (Salem)
Skirt: Stories&Co. Arielle Skirt
Shoes:#EMPIRE - Chrysanthemum
-Flickr- -Facebook-
#secondlife#halloween#horror#spooky#this is wrong sl#foxy#rc cluster#boom#bad unicorn#stories&ci#empire#for fun
4 notes
·
View notes
Text




Rocket teaches Chip about the best way to forget about the problems in your life.
Suggest more spacey topics in the tags!
186 notes
·
View notes