#Robot TCP Setup
Explore tagged Tumblr posts
Text
Precision Starts Here: Understanding Tool Center Point Calibration with Dynalog-US
In the world of advanced manufacturing and robotics, precision isn’t just a luxury—it’s a necessity. Whether you're in aerospace, automotive, or industrial automation, the smallest deviation in your robot’s tool position can lead to major quality issues and costly downtime. That’s where Tool Center Point Calibration (TCP Calibration) comes in, and Dynalog-US is leading the way with innovative solutions that make calibration faster, easier, and more accurate than ever.

What is Tool Center Point Calibration?
Tool Center Point Calibration is the process of determining the exact location of the tip of a robotic tool in 3D space. In simple terms, it’s figuring out where the “business end” of your robot is at all times. Without accurate TCP data, a robot might think it’s applying a weld or picking a part in one place, but in reality, it’s slightly off. That tiny error? It adds up—fast.
Whether you're using a welding torch, gripper, or inspection probe, accurate TCP is critical for consistent performance. TCP calibration ensures your robot can move precisely and predictably, even when switching between tools or performing multi-step operations.
Why Is It Important?
Imagine a car manufacturer where hundreds of robots are working in sync on a single vehicle. If even one of those robots has a miscalibrated tool, it can cause alignment issues, reduce weld quality, or cause collisions with other equipment. TCP calibration ensures that each movement is as precise as the software thinks it is.
In high-precision industries like aerospace, this isn’t just about efficiency—it’s about safety. That’s why leading manufacturers trust calibration experts like Dynalog-US to deliver pinpoint accuracy in every operation.
How Dynalog-US Elevates TCP Calibration
Dynalog has been at the forefront of robotic accuracy for over two decades. Their cutting-edge systems are designed to not only calibrate robots and tools but also verify their accuracy in real-time. With a strong foundation in metrology and automation, Dynalog brings deep expertise to the table—helping companies around the globe fine-tune their robotic systems to perform at peak precision.
Their Tool Center Point Calibration systems are built with one goal in mind: making high-accuracy calibration fast, simple, and repeatable.
Here’s how Dynalog’s approach makes a difference:
1. Fast and Reliable Calibration Process
Dynalog’s TCP calibration kits can be used on nearly any industrial robot, from FANUC to KUKA, ABB, or Universal Robots. The process is streamlined to minimize downtime. In just a few minutes, the robot tool tip can be precisely located with minimal human intervention.
This saves time on the shop floor and ensures consistent calibration every time.
2. High Precision Measurement Tools
Dynalog uses advanced measurement devices and software algorithms that calculate the exact position of the tool center point to sub-millimeter accuracy. This level of precision ensures better repeatability and long-term reliability—critical for production environments where consistency is king.
3. Seamless Integration with Robotic Systems
Whether you're implementing a new robotic cell or fine-tuning an existing one, Dynalog's systems integrate smoothly with major robot brands and programming environments. Their software outputs compatible TCP data that can be directly fed into your robot’s controller—reducing human error and speeding up deployment.
4. Verification and Documentation
Unlike traditional calibration tools, Dynalog doesn’t just stop at the calibration step. Their systems include built-in verification, so you can be confident your robot is operating within acceptable tolerances. You also get detailed reports and logs, which are crucial for traceability, audits, and quality assurance.
Real-World Applications of TCP Calibration
Tool Center Point Calibration is critical in a wide variety of industries:
Automotive: For robotic welding, sealant application, and part handling
Aerospace: For precision drilling, fastening, and composite manufacturing
Medical Device Manufacturing: Where micro-level accuracy is required
Electronics: For robotic assembly of circuit boards and small components
Inspection and Metrology: For robots equipped with sensors and scanners
In all of these industries, TCP calibration isn’t optional—it’s essential for maintaining high-quality standards and reducing waste.
Why Choose Dynalog?
When you partner with Dynalog-US, you’re not just buying a calibration tool—you’re gaining a precision partner. Their team understands the complexity of robotic systems and brings a proven track record of delivering turnkey calibration solutions.
✅ Trusted by Fortune 500 manufacturers
✅ Compatible with all major robot brands
✅ Backed by expert support and training
✅ Customizable to fit your exact application
With Dynalog, your robotic processes will be more accurate, efficient, and reliable—giving you the competitive edge you need in today’s fast-paced manufacturing world.
Final Thoughts
Tool Center Point Calibration might sound technical, but the concept is simple: get your robot's tool where it needs to be—every time. And with Dynalog-US, that process becomes faster, smarter, and more dependable.
Whether you're scaling up your automation efforts or fine-tuning existing workflows, TCP calibration is a foundational step toward operational excellence. Dynalog helps you get it right from the start.
Discover more about TCP calibration and robotic accuracy at www.dynalog-us.com and take the first step toward precision-driven automation.
#Tool Center Point Calibration#TCP Calibration#Robot Tool Calibration#Robotic Accuracy#Dynalog Tool Calibration#Robot TCP Setup#Tool Tip Calibration#Industrial Robot Calibration
0 notes
Text
ARMxy Based SBC Controller BL340 for Production Line OEE Monitoring

Case Details
Introduction to OEE
OEE (Overall Equipment Effectiveness) is a key performance indicator (KPI) in manufacturing that measures how effectively a production line or equipment is utilized. It combines three critical factors:
Availability (percentage of scheduled production time when the equipment is operational).
Performance (actual production speed relative to maximum theoretical speed).
Quality (ratio of defect-free products to total products produced).
The formula for OEE is:OEE=Availability×Performance×Quality
Aiming for an OEE value ≥85% is considered "world-class" in manufacturing. By monitoring OEE, companies can identify bottlenecks, reduce downtime, and improve product quality.
I. Hardware Configuration for OEE Monitoring
Data Acquisition Layer
Equipment Status Monitoring:
Use X-series I/O boards (e.g., X23/X26) to connect DI (Digital Input) signals for tracking equipment start/stop states and downtime statistics; utilize DO (Digital Output) to control alarm lights.
Deploy Y-series I/O boards (e.g., Y95/Y96) with pulse counters to collect real-time cycle times (e.g., motor RPM) for performance rate calculations.
Quality Inspection:
Connect sensors (e.g., pressure sensors, optical detectors) via Y-series AI/AO boards (e.g., Y31/Y33) to acquire defect rate data.
Networking:
Use 3x 10/100M Ethernet ports to interface with PLCs or SCADA systems for production plan synchronization; optional 4G/WiFi modules (via Mini PCIe slot) enable cloud data transmission.
Edge Computing Capabilities
Real-Time Local Processing:
Leverage the quad-core ARM Cortex-A53 CPU (1.4 GHz) to compute OEE metrics locally.
Ensure low-latency processing with the Linux-RT real-time OS (kernel v4.9.170).
Storage Expansion:
Store historical data on SD cards or 16GB eMMC for offline analysis.
II. Software System Integration
Protocol Compatibility
Built-in BLIoTLink software supports Modbus TCP/RTU, OPC UA, MQTT, etc., enabling seamless integration with PLCs (e.g., Siemens S7-1200), SCADA (e.g., Ignition), and MES systems.
Example: Validate data accuracy by combining Modbus TCP readings from PLCs with local pulse counts.
Visualization & Alerts
Develop OEE dashboards using Qt-5.12.5 or Node-RED:
Display real-time equipment status (running/idle/fault), OEE values, and historical trends.
Configure threshold alerts (e.g., trigger emails/SMS if OEE < 80%).
Example: Use Node-RED to aggregate OEE data → MQTT → ThingsBoard platform → dashboard visualization.
Cloud & Analytics
Deploy Python scripts via Docker to connect with AWS IoT Core or Alibaba Cloud:
Store long-term OEE data and apply machine learning to identify downtime causes (e.g., vibration anomalies linked to mold wear).
Example: Predict equipment failures using TensorFlow Lite models to boost availability via proactive maintenance.
III. Deployment Case Studies
Automotive Welding Line:
BL340B model (1 X board + 2 Y boards) connects to welding robot PLCs. Y95 board collects welding cycle pulses; X23 monitors emergency stop signals.
Results: 15% increase in availability (predictive maintenance reduces unplanned downtime); 99.2% quality rate.
Food Packaging Line:
BL342A model (3 Ethernet ports + HDMI) integrates USB cameras for visual inspection, directly displaying defect counts and quality rates on factory screens.
IV. Key Advantages & Scalability
Flexibility:
Expand with Y-series AI/AO boards (e.g., Y43/Y46) for high-precision sensors or Y51/Y52 boards for PT100 temperature probes.
Robustness:
Operates in harsh environments (-40°C to 85°C, IP30 rating); hardware watchdog ensures automatic recovery from faults.
Cost-Effective Upgrades:
Retrofit legacy equipment via RS485/Ethernet interfaces, avoiding full PLC replacement.
V. Implementation Steps
Hardware Setup:
Select BL340B (2 Y-slots) + SOM341 (16GB+2GB) for optimal processing power.
Install X23 (4DI/4DO) and Y95 (pulse counter + PWM) boards.
Software Configuration:
Deploy BLIoTLink for Modbus TCP PLC integration; build OEE logic with Node-RED.
System Validation:
Verify real-time data acquisition (<100ms latency); calibrate sensor accuracy (e.g., ±0.5%).
With the ARMxy Based SBC Controller BL340 manufacturers can rapidly establish a cost-effective, reliable OEE monitoring system, transitioning from "experience-driven" to "data-driven" smart manufacturing.
0 notes
Text
PiSquare: RP2040 & ESP-12E-based board for all Raspberry Pi HATs
PiSquare is a compact, wireless communication board designed for Raspberry Pi that enables you to wirelessly connect and communicate with multiple Raspberry Pi HATs including SPI, I2C, and SPI HATs. It is based on two powerful components:
⦁ The RP2040 microcontroller (the same chip used in the Raspberry Pi Pico). ⦁ The ESP-12E Wi-Fi module for seamless wireless communication.
By using socket programming, PiSquare can wirelessly interact with Raspberry Pi HATs through TCP/IP communication, allowing you to connect as many devices as you need, without worrying about physical stacking or GPIO conflicts.
Key Specifications:
⦁ Microcontroller: Raspberry Pi RP2040
Core Architecture: Dual-core ARM Cortex-M0+ microcontroller
Clock Speed: Up to 133 MHz
Flash Memory: 2MB onboard QSPI Flash (for program storage)
RAM: 264KB SRAM
GPIO Pins: 26 multi-function GPIO pins with support for PWM, SPI, I2C, UART, and other peripherals
⦁ Wi-Fi Connectivity: ESP-12E
Wi-Fi Standard: 802.11 b/g/n
Wireless Frequency: 2.4 GHz
Wi-Fi Chipset: ESP8266 (with 4MB of onboard Flash)
Data Rate: Up to 72.2 Mbps (with 802.11n support)
Communication Interface: UART (Universal Asynchronous Receiver Transmitter)
⦁ Wireless Communication via Socket Programming
Protocol: TCP/IP (Transmission Control Protocol/Internet Protocol) via socket programming
Connection Type: Full-duplex, bi-directional communication
Network Type: Local Area Network (LAN) or Wi-Fi based network for device communication
Number of Supported Devices: Configurable for communication with multiple (n) Raspberry Pi HATs over Wi-Fi without the need for physical stacking
Socket Layer: Raw socket-based communication for sending and receiving data over the network
⦁ HAT Compatibility
Supported Protocols: SPI (Serial Peripheral Interface): Full-duplex, synchronous communication for connecting peripherals
I2C (Inter-Integrated Circuit): Multi-master, multi-slave communication for sensors, actuators, and peripheral devices
GPIO-based HATs: Supports a variety of devices and sensors with GPIO pin control
Pin Multiplexing: Flexible I/O pin assignment allowing for easy configuration of multiple communication protocols simultaneously
Addressing: Supports unique addressing for SPI and I2C devices to avoid conflicts
⦁ Power Supply
Voltage: 5V DC ±5% (typical operating voltage range)
Power Consumption: Low-power operation suitable for remote or battery-powered applications
Regulation: Onboard linear voltage regulator to provide stable power for the microcontroller and Wi-Fi module
⦁ Form Factor
Dimensions: 65mm x 30mm x 20mm (compact design suitable for integration into small devices)
Mounting: Compatible with standard Raspberry Pi connectors (via external interface) without the need for physical GPIO stacking
⦁ I/O and Expansion
Interface: UART, SPI, I2C (for communication with external peripherals)
GPIO: 26 GPIO pins for signal input/output, including support for digital, analog, PWM, and interrupts
Use Cases
Here are a few ways PiSquare can revolutionize your Raspberry Pi projects:
Multi-HAT Robotics: Easily connect multiple HATs for motor control, sensor arrays, and communication modules in a wireless setup.
IoT Projects: PiSquare can communicate with several sensor HATs in remote locations, sending data back to a central Raspberry Pi for processing or cloud storage.
Home Automation: Connect a variety of home automation HATs wirelessly, creating a smart home system that’s efficient and scalable.
Distributed Sensor Networks: Set up multiple sensors across a large area without worrying about physical connections or pin conflicts.
The Pisquare RP2040 with the onboard ESP-12E Wi-Fi module is a powerful and compact solution for anyone looking to build wireless IoT projects. Its support for multiple HATs, including SPI and I2C, makes it versatile enough to handle a wide variety of peripherals, while its ability to implement socket programming provides you with the flexibility to create robust networked applications.
Whether you're creating a smart home system, an industrial IoT device, or a robotics project, the Pisquare by SB Components can be the perfect foundation for your next creation.
#technology#raspberry pi#innovation#tech#techinnovation#programming#tech projects#projects#artificial intelligence#technews
0 notes
Text
Nmap: My Experience with This Powerful Network Scanning Tool

Many IT and cybersecurity experts use the powerful network scanning tool Nmap. Nmap is a powerful network scanning tool that I've found very useful in my job as an IT worker. It lets me scan networks quickly and easily, which helps me find live hosts, open ports, and working services. This post will discuss what I've learned and done with Nmap and show you how it can be used in the real world. What is Nmap? I found the open-source command-line tool Nmap, which is short for Network Mapper, invaluable for network port and IP address scanning. Although Linux is its main platform, its adaptability spans several others. Nmap helps me to quickly find installed programs and provide a whole picture of the network. As a network administrator, Nmap lets me find all the devices running on my network, uncover open ports and services, and spot possible weaknesses. Gordon Lyon, sometimes known as Fyodor, developed the program to streamline mapping a whole network and identify its open ports and services. Featuring in films like The Matrix and the TV series Mr. Robot, Nmap has become somewhat well-known throughout the years and even entered popular culture. Why Did I Apply For Nmap? Many other security experts find Nmap preferred for several more convincing reasons than other network scanning software. First, Nmap lets you quickly and effectively map networks without requiring advanced instructions or setups. It enables you to create complicated scripts using the Nmap Scripting Engine (NSE) and supports basic commands such as determining whether a host is up. Nmap Features I Most Find Beneficial Nmap fast identifies any device on a network—including servers, routers, switches, and mobile devices. Managing single or numerous networks makes this function quite helpful. Nmap can even reasonably detect application versions and find services running on a system, including DNS and web servers. This talent enables me to see current weaknesses. Nmap can offer a comprehensive operating system that runs on device information, including particular OS versions. This element is vital when developing further methods of penetration testing. Using Nmap to use current scripts from the Nmap Scripting Engine, I search systems during security audits for vulnerabilities. This talent helps me to spot and fix security flaws. Nmap also provides Zenmap, a graphical user interface designed to enable visual mappings of a network. This interface helps reporting and increases usability, therefore facilitating the presentation of complex network structures and vulnerabilities to stakeholders. How To Install Nmap? The particular requirements of the work will determine the several uses for Nmap. These are some broad Nmap use guidelines: Download and set up Nmap from the official website - https://nmap.org/download.html. Check for the executable file that is being downloaded in your system and then run it. Enter the command for the scan you wish to do with extra targets or settings. For a TCP SYN scan, for instance, "nmap -s "; for OS detection, "nmap -O ." Enter to run the scan. Nmap will show operating services, open ports, and a list of live hosts together with scan findings. Top Functions Of Nmap With Codes Network Mapping Network mapping is Nmap's primary purpose; it lets me scan the network and look for connected devices, including PCs, servers, routers, and switches. I find information on online devices, open ports, and network connections by running the basic Nmap command focused on an IP address or range. Zenmap allows one to depict this information graphically. Additionally captured by Nmap are media access control (MAC) addresses, which enable device manufacturer identification. For example, I could run to find out which devices are linked to my network only running: Code: nmap 192.168.1.0/24 Network Packet Manipulation Nmap can change the contents of network messages. I can catch, filter, reroute, or send data packets with these tools. The Nping tool stands out because it can test firewall rules, stress test networks, and fix problems. As an example, if I want to see how strong my network is, I could use Code: nping --tcp -p 80 192.168.1.10 Scripting The coding features of Nmap are what make it so powerful. I can automate complicated scanning jobs and find security holes with the Nmap Scripting Engine (NSE). To find weaknesses, for example, I might use Code: nmap --script vuln 192.168.1.10 Fundamental Nmap Commands I often run through these fundamental commands: On a host, find open ports by: nmap To obtain OS details and service versions: Nmap -A To find whether a firewall is turned on. nmap -sA To examine a particular port in scanning nmap -p Nmap's rich documentation offers many choices and examples for more complex scanning and scripting. Looking for Alternatives to Nmap As a security tester, I've looked into many tools that can be used instead of Nmap. There are several open-source tools for security testing, and each one is good at a different part of it: Zap: great program scanner. John the Ripper: A strong brute force password hacker. Wireshark: It is a flexible packet sniffer. These tools are handy, but they usually only cover specific areas of security testing. On the other hand, Nmap is the best because it can scan whole networks. Even paid penetration testing tools like Rapid7's Metasploit or Burp Suite have difficulty entirely replacing Nmap. These paid tools have features and interfaces that are easy for anyone to use and can do various security jobs. However, Nmap is still used by many security teams, including mine, because it can run scripts and meet special user needs. Nmap gets most of its money from OEM licensing, meaning companies buy and use it for their goods. Many paid pen-testing tools either use parts of Nmap code in their programs or run Nmap locally and then use their programs to read the results. Sometimes, companies that buy commercial tools might use Nmap behind the scenes. Most of the time, the extra cost is worth it because these commercial tools are so easy to use that even IT security staff with little experience can do jobs that would be hard to do with Nmap alone. Also, these tools make it easier to write professional reports faster, which is a big plus. It's also possible for companies to use skilled penetration testing services instead of their tools. It's essential to keep in mind, though, that some security testing firms may use the open-source Nmap tool directly. Most businesses are honest about how they work, but some, like Nmap Online, which has a name that could be confusing, use images and domain names that look a lot like those on the official Nmap.org website, which could lead to confusion. Even though there are other options, I find that Nmap's many features and adaptability make it an essential part of my security testing kit. In Summary In my toolkit for cybersecurity, Nmap is quite a helpful instrument. Although mastery requires time and effort, the great powers it provides make it well worth it. Nmap offers a complete collection of tools to help you safeguard and comprehend your network regardless of your knowledge about network security—that of a security professional, network administrator, or just curious learner. FAQs What is Nmap, and for what purposes can one utilize it? For Network Mapper, Nmap is an open-source network security audit and discovery tool. It lets users scan networks looking for running services, open ports, live hosts, and operating systems. IT managers and cybersecurity experts extensively use Nmap for chores, including network inventory, host or service uptime monitoring, and timetable management of service upgrades. How might I install Nmap on several OS systems? Installing Nmap differs somewhat based on your operating system: Linux: Run sudo apt-get install nmap to install Nmap on variants such as Debian or Ubuntu. While the installation command may vary for other distributions, it is usually found in the default repositories. Windows: Download the installer from the official Nmap website, then run the executable file to install. macOS: Take advantage of Homebrew or another package manager. The installation command is brew install nmap. Zenmap: You can download the Zenmap graphical user interface (GUI) variant for a more aesthetically pleasing experience for all operating systems. Can one legally use Nmap for network scanning? While using Nmap is legal, the legality relies on your usage. A perfectly lawful and popular security audit and management method is scanning your network or one under clear authority. Using Nmap to scan devices or networks without permission is unethical and illegal. Always be sure you have the required rights before doing any scans since unauthorized scanning could result in serious legal penalties. Read the full article
0 notes
Text
Tool Center Point (TCP) Calibration: Why It’s Crucial for Robotic Accuracy
In the world of industrial robotics, precision and accuracy are paramount. Whether in automotive manufacturing, electronics assembly, or aerospace engineering, the ability of a robot to accurately position and manipulate tools directly impacts production quality, efficiency, and overall operational success. One of the most critical processes for ensuring this level of precision is Tool Center Point (TCP) Calibration. For companies that rely on robotic automation, Dynalog Inc. offers industry-leading solutions for TCP calibration, helping businesses achieve optimal robot performance.

In this comprehensive guide, we'll explore the importance of TCP calibration, how it works, and why partnering with Dynalog Inc. for TCP calibration solutions can significantly enhance your robotic operations.
What Is Tool Center Point (TCP) Calibration?
Tool Center Point (TCP) Calibration refers to the process of identifying the exact position of a robot's tool in relation to its coordinate system. In simple terms, the TCP is the point at which a robot’s tool (such as a gripper, welding tip, or spray nozzle) makes contact with a workpiece or performs a specific action.
For a robot to execute its tasks accurately, it must "know" the exact location of the TCP in 3D space. If the TCP is not properly calibrated, even minor deviations can result in:
Inaccurate positioning
Poor product quality
Increased cycle times
Tool wear and damage
Reduced overall efficiency
TCP calibration ensures that the robot’s internal coordinate system aligns perfectly with the physical position of the tool, allowing for highly precise and repeatable movements.
Why TCP Calibration Is Essential for Robotic Operations
1. Improved Accuracy and Repeatability
Robots are designed to repeat complex movements with high precision. However, if the TCP is not accurately defined, even small discrepancies can lead to misalignment and inconsistent results. Proper TCP calibration helps ensure that the robot performs each task with consistent accuracy, reducing the margin of error and improving production quality.
2. Enhanced Process Efficiency
When the TCP is correctly calibrated, robots require fewer corrections and adjustments during operation. This leads to faster cycle times, reduced downtime, and overall higher operational efficiency. A robot that knows exactly where its tool is positioned will perform faster and more accurately, improving the output rate.
3. Reduced Tool Wear and Maintenance Costs
Incorrect TCP calibration can cause excessive tool wear, as the robot may apply incorrect forces or angles during operation. Over time, this can lead to premature tool failure and increased maintenance costs. Proper calibration ensures that the robot applies the right amount of pressure and movement, extending the lifespan of tools and reducing maintenance expenses.
4. Increased Product Quality
Precision is crucial in industries like automotive, aerospace, and electronics manufacturing, where even minor deviations can compromise product integrity. Accurate TCP calibration allows the robot to execute detailed movements with minimal variation, ensuring that every product meets strict quality standards.
How TCP Calibration Works
TCP calibration involves defining the exact position and orientation of the tool relative to the robot's base coordinate system. The process typically includes the following steps:
1. Initial Tool Setup
The robot is equipped with the desired tool, such as a gripper, welding torch, or sensor. The tool must be securely attached to prevent any movement during calibration.
2. Measurement of Tool Position
A calibration device, such as a laser tracker or a measurement probe, is used to measure the tool’s position in multiple orientations. The robot will move the tool through various predefined positions, and the calibration device records the precise coordinates.
3. Data Processing and Calculation
The recorded data is processed using specialized software (such as Dynalog's DynaCal), which calculates the exact position and orientation of the tool. This involves solving complex kinematic equations to define the TCP’s coordinates.
4. Updating the Robot’s Control System
Once the TCP coordinates are determined, the data is uploaded to the robot’s control system. The robot then uses this information to adjust its internal programming, ensuring that the TCP aligns with the robot’s coordinate system.
5. Validation and Testing
After the calibration process, the robot is tested to confirm that the TCP is correctly aligned. This may involve executing sample tasks or conducting accuracy tests to verify that the robot’s movements match the programmed positions.
Challenges in TCP Calibration and How Dynalog Solves Them
1. Complex Tool Shapes and Configurations
Calibrating a simple gripper is relatively straightforward, but complex tools with multiple contact points or irregular shapes present greater challenges. Dynalog’s advanced calibration solutions can handle even the most complex tool geometries, ensuring accurate results regardless of tool design.
2. Thermal Expansion and Tool Wear
Tools can shift or expand due to heat and wear over time, causing deviations in the TCP. Dynalog’s calibration systems are designed to compensate for these variations, maintaining accuracy even under challenging operating conditions.
3. High-Speed Operations
In high-speed manufacturing environments, even millisecond-level inaccuracies can affect product quality. Dynalog’s TCP calibration systems provide real-time adjustments, ensuring that the robot maintains precision at high speeds.
Why Choose Dynalog for TCP Calibration?
Dynalog Inc. is a global leader in robotic calibration and performance analysis. With decades of experience in robotic automation, Dynalog has developed state-of-the-art TCP calibration solutions that deliver unmatched accuracy and reliability. Here’s why Dynalog stands out:
✅ Advanced Calibration Technology
Dynalog’s proprietary DynaCal software and measurement devices provide precise and real-time calibration data, ensuring that the robot’s TCP is always aligned with the coordinate system.
✅ Industry Expertise
With clients in automotive, aerospace, electronics, and other precision industries, Dynalog understands the unique challenges of robotic automation and tailors calibration solutions to meet specific operational needs.
✅ Comprehensive Support and Training
Dynalog offers full-service support, including on-site calibration, troubleshooting, and operator training. Their expert team ensures that your robots are always performing at peak efficiency.
✅ Custom Solutions
No two manufacturing environments are identical. Dynalog customizes TCP calibration systems to match the specific requirements of your production line, ensuring seamless integration and optimal performance.
Benefits of Accurate TCP Calibration with Dynalog
Partnering with Dynalog for TCP calibration provides numerous benefits, including:
Higher production efficiency and faster cycle times
Improved product consistency and quality
Reduced maintenance and tool replacement costs
Increased robot lifespan and reliability
Enhanced operational flexibility and scalability
Conclusion
Tool Center Point (TCP) Calibration is a critical process for any robotic automation system. Without proper calibration, even the most advanced robots can suffer from inaccuracies and operational inefficiencies. Dynalog Inc. offers cutting-edge TCP calibration solutions that enhance robotic performance, reduce costs, and improve product quality.
If you’re looking to optimize your robotic operations, Dynalog’s TCP calibration systems are the key to achieving unmatched precision and efficiency. Contact Dynalog today to learn how their solutions can transform your production line and take your automation to the next level.
#TCPCalibration#ToolCenterPoint#RobotCalibration#Dynalog#RoboticAutomation#IndustrialRobotics#PrecisionEngineering#ManufacturingEfficiency#RobotAccuracy#AutomationSolutions
0 notes
Text
ARMxy Based SBC Controller BL340 for Production Line OEE Monitoring

Case Details
Introduction to OEE
OEE (Overall Equipment Effectiveness) is a key performance indicator (KPI) in manufacturing that measures how effectively a production line or equipment is utilized. It combines three critical factors:
Availability (percentage of scheduled production time when the equipment is operational).
Performance (actual production speed relative to maximum theoretical speed).
Quality (ratio of defect-free products to total products produced).
The formula for OEE is:OEE=Availability×Performance×Quality
Aiming for an OEE value ≥85% is considered "world-class" in manufacturing. By monitoring OEE, companies can identify bottlenecks, reduce downtime, and improve product quality.
I. Hardware Configuration for OEE Monitoring
Data Acquisition Layer
Equipment Status Monitoring:
Use X-series I/O boards (e.g., X23/X26) to connect DI (Digital Input) signals for tracking equipment start/stop states and downtime statistics; utilize DO (Digital Output) to control alarm lights.
Deploy Y-series I/O boards (e.g., Y95/Y96) with pulse counters to collect real-time cycle times (e.g., motor RPM) for performance rate calculations.
Quality Inspection:
Connect sensors (e.g., pressure sensors, optical detectors) via Y-series AI/AO boards (e.g., Y31/Y33) to acquire defect rate data.
Networking:
Use 3x 10/100M Ethernet ports to interface with PLCs or SCADA systems for production plan synchronization; optional 4G/WiFi modules (via Mini PCIe slot) enable cloud data transmission.
Edge Computing Capabilities
Real-Time Local Processing:
Leverage the quad-core ARM Cortex-A53 CPU (1.4 GHz) to compute OEE metrics locally.
Ensure low-latency processing with the Linux-RT real-time OS (kernel v4.9.170).
Storage Expansion:
Store historical data on SD cards or 16GB eMMC for offline analysis.
II. Software System Integration
Protocol Compatibility
Built-in BLIoTLink software supports Modbus TCP/RTU, OPC UA, MQTT, etc., enabling seamless integration with PLCs (e.g., Siemens S7-1200), SCADA (e.g., Ignition), and MES systems.
Example: Validate data accuracy by combining Modbus TCP readings from PLCs with local pulse counts.
Visualization & Alerts
Develop OEE dashboards using Qt-5.12.5 or Node-RED:
Display real-time equipment status (running/idle/fault), OEE values, and historical trends.
Configure threshold alerts (e.g., trigger emails/SMS if OEE < 80%).
Example: Use Node-RED to aggregate OEE data → MQTT → ThingsBoard platform → dashboard visualization.
Cloud & Analytics
Deploy Python scripts via Docker to connect with AWS IoT Core or Alibaba Cloud:
Store long-term OEE data and apply machine learning to identify downtime causes (e.g., vibration anomalies linked to mold wear).
Example: Predict equipment failures using TensorFlow Lite models to boost availability via proactive maintenance.
III. Deployment Case Studies
Automotive Welding Line:
BL340B model (1 X board + 2 Y boards) connects to welding robot PLCs. Y95 board collects welding cycle pulses; X23 monitors emergency stop signals.
Results: 15% increase in availability (predictive maintenance reduces unplanned downtime); 99.2% quality rate.
Food Packaging Line:
BL342A model (3 Ethernet ports + HDMI) integrates USB cameras for visual inspection, directly displaying defect counts and quality rates on factory screens.
IV. Key Advantages & Scalability
Flexibility:
Expand with Y-series AI/AO boards (e.g., Y43/Y46) for high-precision sensors or Y51/Y52 boards for PT100 temperature probes.
Robustness:
Operates in harsh environments (-40°C to 85°C, IP30 rating); hardware watchdog ensures automatic recovery from faults.
Cost-Effective Upgrades:
Retrofit legacy equipment via RS485/Ethernet interfaces, avoiding full PLC replacement.
V. Implementation Steps
Hardware Setup:
Select BL340B (2 Y-slots) + SOM341 (16GB+2GB) for optimal processing power.
Install X23 (4DI/4DO) and Y95 (pulse counter + PWM) boards.
Software Configuration:
Deploy BLIoTLink for Modbus TCP PLC integration; build OEE logic with Node-RED.
System Validation:
Verify real-time data acquisition (<100ms latency); calibrate sensor accuracy (e.g., ±0.5%).
With the ARMxy Based SBC Controller BL340 manufacturers can rapidly establish a cost-effective, reliable OEE monitoring system, transitioning from "experience-driven" to "data-driven" smart manufacturing.
0 notes
Text
Tera Term Software Download For Windows

Download - Software and applications | ABB.
Best Terminal Emulator? - Cisco.
Download free Tera Term 4.106.
Download Tera Term 4.106 for Windows - F.
Terminal Software - SourceForge.
Troubleshooting RS-232 Connectivity Issues.
Get TERA | Xbox.
Miscellaneous Software Products - Arbiter Systems, Inc.
Freeware Vt100 Emulation Downloads - WinSite.
RealTerm: Serial/TCP Terminal download | SourceF.
Robot Arm Download Center – Rotrics.
Tera Term Pro 2.3 Free Download - Free Software Downloads.
CoolTerm - Download.
Product Support Downloads - Click2Enter.
Download - Software and applications | ABB.
OldV provides free software downloads for old versions of programs, drivers and games. So why not downgrade to the version you love?.... because newer is not always bett. Jul 08, 2010 · You can download Tera Term 4.106 from our software library for free. Our antivirus analysis shows that this download is virus free. The following versions: 5.0, 4.82 and 4.9 are the most frequently downloaded ones by the program users. Also the program is known as "Tera Term Pro", "Tera Term Scso", "Tera Term SSH". 61,303 downloads Updated: September 27, 2021 Donationware / GPLv3. 3.6 / 5 24. Review Free Download... Windows 10 32/64 bit Windows Server 2012 Windows 2008 R2 Windows 8 32/64 bit.
Best Terminal Emulator? - Cisco.
Tera Term Pro Web Builds. Tera Term Pro 2.3; Tera Term Pro 1.4 Windows3.1;... Windows; Mac; Linux; Games; Android; Follow OldV ; Old Version. OldV provides free software downloads for old versions of programs, drivers and games. So why not downgrade to the version you love?.... because newer is not always better!.
Download free Tera Term 4.106.
Tera Term on your Windows PC. Then run Tera Term. Use the serial setup and set the serial port parameters to 115.200 bps (baud rate), 8 data bits, none parity, one stop bit and none handshaking (115.200, N, 8, 1). Please note: Tera Term works also very well as a Telnet client or SSH client program for the eSOM/2586 Linux. That is all. Tera Term is free software terminal emulator which supports: TCP/IP (telnet, ssh, raw), serial, and named-pipe connections. VT100 emulation and selected VT200/300/400/500 emulation. Tera Term, free download. Tera Term 4.71: Tera Term is the terminal emulator for Microsoft Windows, that supports serial port, telnet and SSH connections. Among many other features it also has built in Macro scripting language.
Download Tera Term 4.106 for Windows - F.
Sep 22, 2021 · Tera Term is a freeware for Microsoft Windows PCs that lets you communicate with remote systems through TCP/IP and serial connections. TT is a complete terminal application that boasts many features: local echo, etc. The comprehensive program is impressively lightweight. and the simple user interface makes using Tera Term relatively easy.
Terminal Software - SourceForge.
Lightweight.. 101 alternatives to PuTTY. PuTTY is a free and open-source terminal emulator, serial console and network file transfer application. It supports several network protocols, including SCP, SSH, Telnet, rlogin, and raw socket connection. It can also connect to a serial port. Most users think PuTTY is a great alternative to Tera Term.
Troubleshooting RS-232 Connectivity Issues.
Download for Windows; Download for Linux 64bit; Download for Linux 32bit; When you have issues with running or using HTerm check the FAQ if there is already a solution. For bugs or feature requests write me at Older versions. 0.8.5: Download for Windows, Linux 32bit, Linux 64bit. With that small public service announcement out of the way, here are some of the best HyperTerminal alternatives for Windows 10. Tera Term. TeraTerm is a completely free and Open Source (FOSS) terminal emulator that comes in at a very small size. It's not just a generic terminal, but can emulate specific models of physical terminals, making it easy for people who know those terminals to keep.
Get TERA | Xbox.
Tera Term, free download. Tera Term 4.71: Tera Term is the terminal emulator for Microsoft Windows, that supports serial port, telnet and SSH connections. Among many other features it also has built in Macro scripting language. Projeto Descrição. Tera Term is Tera Term Pro 2.3 succession version and is being officially recognized by the original author. Tera Term is open source free software terminal emulator supporting UTF-8 protocol. Now TTSSH supports SSH2 protocol (Original version supports SSH1).
Miscellaneous Software Products - Arbiter Systems, Inc.
TERA – Fantasy, MMORPG, Strategy and Skill! Get ready for the action-packed challenge of your life in TERA! Your adventures in this breathtaking universe will push the very boundaries of the genre. With its True Action Combat system, you need to aim and dodge to cast spells, land your attacks and avoid taking damage. Tera Term X11. Here are a number of highest rated Tera Term X11 pictures on internet. We identified it from honorable source. Its submitted by handing out in the best field. We acknowledge this nice of Tera Term X11 graphic could possibly be the most trending subject taking into consideration we allocation it in google help or facebook. Jul 11, 2020 · Download the Tera Term installer file from the link above. Save the downloaded file to your computer. Double-click on the downloaded Tera Term installer file. Now, a smart screen might appear and ask for a confirmation. Click “Yes” to confirm.
Freeware Vt100 Emulation Downloads - WinSite.
Version 0.63. WinSCP is a free open-source SFTP and FTP client for Windows. Its main function is to secure file transfer between a local and a remote computer. Beyond this, WinSCP offers scripting and basic file manager functionality. Version 5.5.5. Tera Term Pro is a free open-source, software implemented, terminal emulator program.
RealTerm: Serial/TCP Terminal download | SourceF.
4.83. Free Download. Download Now! Tera Term 4.83 (S server) Microsoft Office 2010 Service... Express your ideas, solve problems, and connect... Macromedia Flash 8 8.0 Macromedia Flash 8 Professional. Cool Edit Pro 2.1.3097.0 Advanced multi track sound editing program. Internet Explorer 10 10 Microsoft’s latest version of Internet. RealTerm: Serial/TCP Terminal. Serial terminal program for engineering. Ideal for development, reverse engineering, debugging, datalogging and capture, and automatic test. The website is a comprehensive manual for Realterm. It has an comprehensive ActiveX/COM automation support so it can be used a serial component by other programs.
Robot Arm Download Center – Rotrics.
Download Vt100 Emulation Software. Tera Term (Pro) Tera Term (Pro) is a free software terminal emulator (communication program) for MS-Windows. It supports VT100 emulation, telnet connection, serial port connection, and so on. Source code (C, C++) available (315. Windows XP HyperTerminal? I don't want or need a free one full of adware. I work at a place were men don't dance with there computers in skinny jeans. I work with old equipment that still operates reliably, my 16 year old laptop just can't do it anymore, and the new windows computers can't do much at all right out of the box. Aug 05, 2009 · Tera Term Pro is a free RS232 software terminal emulator. (communication program) for MS-Windows. It supports VT100 emulation, telnet connection, serial port connection, ethernet and so on. They also offer Tera Term ver. 1.4 for Windows 3.1 for anyone using or needing a RS232 Communications program for older versions of Windows.
Tera Term Pro 2.3 Free Download - Free Software Downloads.
File info. (TeraTerm) 2007.9.30 (Ver 4.54) - added support for selecting a current screen buffer. Also, added `select screen' new menu under edit menu. - added support for showing the device description of COM port on the connection dialog. - added support of telnet keep-alive. TeraTerm will send TELNET NOP command to host when no commucation. Tera Term (Pro) is a free software terminal emulator (communication program) for MS-Windows. It supports VT100 emulation, telnet connection, serial port connection, and so on.
CoolTerm - Download.
Tera Term Pro 2.3 Download at Download32.. Download File (942.0 KB) All Software Windows Mac Palm OS Linux Windows 7 Windows 8 Windows Mobile Windows Phone iOS Android Windows CE Windows Server Pocket PC BlackBerry Tablets OS/2 Handheld Symbian OpenVMS Unix. Oct 16, 2016 · Tera Term (Pro) is a free software terminal emulator (communication program) for MS-Windows. It supports VT100 emulation, telnet connection, serial port connection, and so on..
Product Support Downloads - Click2Enter.
Tera Term 4.83Free Download Secure Tera TermDownload Options Download Now! Popular Downloads ACR911.1.0.15 Macromedia Flash 88.0 Macromedia Flash 8 Professional. Microsoft Office 2010Service... Express your ideas, solve problems, and connect... Cool Edit Pro2.1.3097.0 Advanced multi track sound editing program. Tera Term (Pro) is a free software terminal emulator (communication program) for MS-Windows. It supports VT100 emulation, telnet connection, serial port connection, and so on. Source code (C, C++) available (315..

0 notes
Text
Messung Group: Multiple technology solutions under one roof

Messung is a diversified conglomerate with expertise that spans industries and applications. Messung offers a diverse portfolio of best-in-class products, solutions, and services enabling a wide range of industrial verticals to optimize operations and maximize productivity. The Group’s know-how and offerings keep growing, keeping pace with global trends, market dynamics and new technologies.
Messung in Industrial Automation & Control
In 1981, Messung innovated India's first indigenous PLC - Meprolog-H. From that pioneering start, Messung has grown to become a market leader in industrial automation; a PLC manufacturer who continuously adds to their ever-expanding portfolio of technology solutions. Their solutions cover:
Process Automation: In verticals such as Oil & Gas, Sugar, Power, Pulp & Paper, Water & Sewage Treatment, Messung customises high-end process automation & control solutions in India that meet the highest technical demands for speed, quality, operational reliability, system availability and more.
Servo & Motion Control Automation: In industries such as Plastic Technology, Robotics & Handling Systems, Food & Packaging, Printing & Paper, Textile Machinery, Energy, Machine Tools for cutting & forming, Messung delivers fully integrated solutions incorporating their own Nx-ERA programmable logic controllers and XM-PRO remote I/O modules; motion control systems and drive products from Sigmatek, Austria VFDs from Fuji Electric, Japan; HMIs and much more.
General Purpose Automation: Messung offers smart, compact, economical solutions for automation of varied equipment such as special purpose Machines, Utility applications, Material Handling and machineries of general usage. Messung's technology enables high-performance machines that are information-enabled and easy to integrate.
Messung in Building & Infrastructure Automation & Control
For all types of buildings, from hospitals to shopping malls, IT and industrial establishments, corporate buildings, and power stations – Messung offers solutions under four broad categories:
IBMS: With products from Distech Controls, Canada, Messung’s IOT-enabled BMS solution provides control and supervision of HVAC, Security, CCTV, Intrusion Alarm and Fire systems, including diesel genset, water pumping systems, and other third-party systems, which are now mandatory in all modern buildings.
IOT: The Internet of Things (IOT) allows exchange of information and data, and enables 24x7 monitoring and remote control of equipment, systems, buildings and plants. Customised dashboards provide data on different criteria while advanced analytics help to improve efficiency, response, operation, preventive maintenance, etc.
EMS: Messung offers integrated energy management systems designed to store energy parameters, analyse consumptions, identify areas of wastage, reduce energy consumption, predict electrical system performance and optimise energy usage to reduce cost in a premise.
Lighting Management Systems: Messung provides a complete solution based on advanced technology, service and support from a single source - for Airports, Transportation, Retail, Hospitality, Offices and Residential properties. All products are based on open standards like KNX, DALI, BACnet, Modbus, SNMP, TCP/IP, etc.
Messung in Home, Office & Hotel Automation & Control
To transform interiors into luxurious spaces, enhancing comfort and safety while reducing energy consumption, contact Messung. They offer a wide range of industry-best automation products and customised solutions for:
Home Automation: Messung partners with Zennio, Spain, to provide KNX-based solutions to control all your home appliances, lights, fans, TVs, ACs, curtains & blinds, video door phones, CCTV cameras, media devices, garden sprinklers, etc.
Office Automation: Messung helps in automating existing office procedures, and providing control over an increasingly complex network of devices, for greater convenience, comfort and efficiency. Their partner: Crestron, USA.
Hotel Automation: Guests can control multiple functions including lighting, air conditioning, drapes and audio/video systems using smart, automated bedside consoles and interfaces. Integration of guest rooms with the hotel's property management system enable better monitoring and control.
Messung in Electrical Engineering
Messung provides reliable, intelligent and world-class solutions for Power Monitoring and Distribution in three broad segments:
Distribution & Control: Messung provides smart power distribution control panels with Wohner’s special Busbar systems as per IEC 61439 standards. Messung offers total low voltage power distribution control systems that are Industry 4.0-compatible, Cloud-based solutions to provide “Any time Anywhere” supervisory & control features.
Control Panels: For a wide arena of applications like water and waste water treatment plants, sugar machinery, plastic extrusion, printing, pharmaceutical, automotive assembly and testing lines, electro plating, boilers, material handling, furnaces, mechanical and hydraulic press, in different industry verticals.
Energy Management: Customised energy management solutions to help enterprises optimise power usage, improve power protection and increase productivity by reducing downtime, safety risks and electricity bills.
Incorporating best-in-class Class A power quality analysers, digital energy meters etc. from Janitza and advanced online UPS, Active Harmonic Filters and Servo Stabilizers from Fuji Electric Consul Neowatt, Messung enhances productivity and the reliability of your critical electrical assets in industrial, data centre and commercial applications.
Messung in Workplace Technology
Messung’s rich industrial experience has made them aware of the health hazards, safety risks and challenges of the industrial workplace. Messung is committed to find and deliver meaningful ergonomic solutions.
For Test & Measuring, Messung provides complete setups for R&D labs, calibration centres, training and didactic centres, electronic assembly & testing, spread across the Indian electronic industry. The ergonomic industrial furniture with ESD protection, and intelligent test & measurement solutions are designed to improve efficiency while offering user comfort.
Messung offers a world-class range of indigenous ESD workstations, ESD chairs, ESD storage trolleys, etc. for ESD workplaces; and workstation chairs, lab table, lab chairs, industrial work tables, workshop tables, stainless steel table, etc. for general workplaces.
Last but not least, there are Class 100/ISO 5 cleanroom chairs and stools from Uchida, Japan, for Special Category Cleanrooms, Chemical Laboratories, Inspection & Quality Control Rooms in Chemical, Bio-tech, Pharma, Food & Beverages industries.
Conclusion
Whether you are looking for complex industrial automation solutions or lab chairs for your R&D team, the latest power distribution/monitoring devices or sophisticated hotel automation, a new testing lab set-up as per stringent standards or a lighting management system to save electricity and costs – Messung is your go-to partner for technological excellence with customised service.
0 notes
Photo

After a full year and a half of improvements and fine tuning, firmware v2.0 is finally officially released. Changes include improvement in sinusoidal commutation (e.g. auto sensor setup, linearity correction, ...), expanded connectivity (e.g. CANOpen DS402, Modbus TCP, ...), higher resolution PID, STO support, improved Sensorless operation, optimized protection and more. See our website for more information (link in bio) . . . . #roboteq #robotics #tech #engineering #motorcontrollers https://www.instagram.com/p/B1FL7CUhQ1a/?igshid=psad0548w8ua
0 notes
Text
Vulnerability Assessment With Nessus Home - Part 1
Part One of a Two-Part series
Introduction
If you work in the field of Information Technology, you have probably heard of Vulnerability Assessment (VA). VA is a process of identifying security vulnerabilities in a system. It is recommended that you conduct a VA against your organization's network every quarter, and if your organization follows certain policy and standards, such as PCI DSS, VA is a requirement. However, organizations should not be the only ones conducting VAs against their network; average home users should also conduct vulnerability assessment against their network. In this blog, I will guide you through the process of performing a VA against your network using Nessus Home.
What Is Nessus?
Nessus is a vulnerability scanner developed by Tenable and there are two versions of it: Nessus Home and Nessus Professional. Basically, the major differences between the two are that you can only scan up to 16 IP addresses per scanner, and you won’t be able to perform compliance checks and content audits with Nessus Home. Most average users will not have more than 16 systems, and there is no need to run compliance checks or content audits on your home systems.
Vulnerability assessments are typically done by running authenticated scans, which means the scanner will authenticate against the systems its scanning. The scan will then come back with much more detailed information about a system. With Nessus, you can perform authenticated scans against different operating systems such as Windows, Linux, and Mac OS via different methods such as SMB, SSH, SNMP, Telnet, etc.
Installing and Setting Up Nessus
For demonstration purposes, I will walk you through the process of installing and setting up Nessus and performing an authenticated scan against Windows 10.
To use Nessus, you need to obtain an activation code on Tenable's website, which is (https://www.tenable.com/products/nessus-home). Use your name and email address, and the code will be sent to your email.

Registering for an Activation Code

Emailed Activation Code
Once you receive your code, go to this page (https://www.tenable.com/downloads/nessus) and download Nessus. Choose the appropriate package. In my case, I'm going to download the package for Windows 10 (64-bit).

Downloading Nessus
Install Nessus. During the installation, Nessus will install a tool called WinPcap, which will allow Nessus to capture live network traffic. Check Automatically start the WinPcap driver at boot time option and install WinPcap.

Nessus installer

Nessus Setup Wizard

Select the start the WinPcap driver at boot option
Nessus runs on TCP Port 8834 on your local machine. To access the web console, open a browser and navigate to https://localhost:8834. Once the installation is complete, your default browser will open, and it will ask you to connect via SSL. Click Connect via SSL and your browser will display a warning saying that the certificate cannot be trusted. This is normal since Nessus uses a self-signed certificate. Proceed by clicking Go on to the webpage (Different browsers will have different wording, but they will give you an option to accept the risk and proceed).

Welcome to Nessus!

Certificate Warning, Select Go on to the webpage
Create your account. Make sure you use a strong password! Once you create an account, you will be asked to enter your activation code that was sent to your email. After you enter the code and click Continue, Nessus will start to set up the plugins and other files that it needs to perform a scan. This process will take a while so take a break and come back in an hour or so. After the setup is complete, you’ll be greeted by the web console.
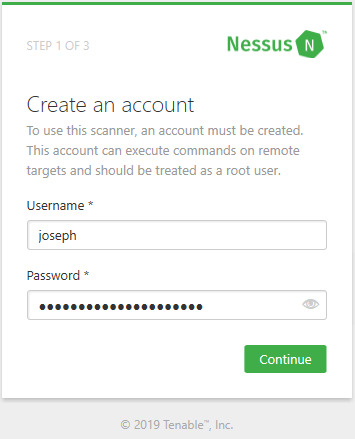
Creating a Nessus account

Registering the scanner

Initializing Nessus

Nessus using Localhost and Port 8834
You can create a new scan by clicking New Scan on the upper right corner. You’ll see that certain templates aren’t available until you upgrade to Nessus Professional, but you still have access to templates such as Advanced Scan, Basic Network Scan, Host Discovery, Malware Scan, Spectre and Meltdown, and WannaCry Ransomware. It is straight forward to use these templates; you give it the IP addresses you want to scan, and credentials if you want to perform the recommended authenticated scan. Setting up a scan and properly performing an authenticated scan will be covered in Part II.

Listing of Scan Templates for Nessus
Useful Tips and Tricks
Now, I would like to share how some tips and tricks that I’ve acquired using Nessus for about a year. This is a personal preference, so you do not have to follow my suggestions. It will involve tweaking some settings and if you don’t want to, that’s fine. It won’t affect the performance of the Nessus scans.
By default, Nessus will automatically start and run in the background on boot on Windows. I don’t like how it’s running when I don’t need it (On Linux, Nessus does not start automatically by default and you need to start it manually, which is what I prefer!). In order to prevent Nessus starting on boot, open Services and find Tenable Nessus on the list. You will see that it is set to Automatic. To change this, right click on it and set Startup type to Manual. Nessus won’t start on boot anymore and you’ll have to manually start/stop it. To do so, open a Command Promptor PowerShell and type net stop/start “Tenable Nessus”.

Windows Services

Configuring Nessus to manual start using Windows Services

Net Start/Stop of Nessus
According to Tenable, they release more than 100 plugins weekly. This means that you will have to update Nessus frequently in order to use those new plugins. If there is an update available, Nessus will let you know when you log into the GUI. However, I prefer updating it from the command line. To do this, open a Command Prompt or PowerShell as an administrator and navigate to C:\Program Files\Tenable\Nessus directory. Once you are there, type .\nessuscli.exe update –all (.\ is not needed if you are doing this from the Command Prompt). Nessus will download the updates from nessus.org. Make sure to restart Nessus after you update it.
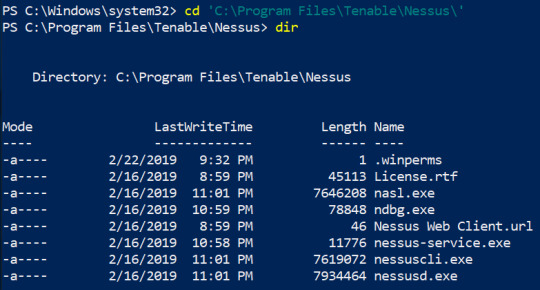
Nessus Directory

Nessus Update from command line
Lastly, Nessus rates the findings with its severity levels: Critical, High, Medium, Low, and Informational. Prior to Nessus v8, it listed the findings by severity but now it “groups” certain findings. I find this feature not very helpful and annoying, so I disabled it right away. To do so, click on Settings next to Scans, go to Advanced, and type groups. This will return two settings: Use Mixed Vulnerability Groups and Use Vulnerability Groups. Set the values to No. You are welcome.

Nessus Groups

Nessus Advanced Settings
Conclusion
Nessus Home is a great vulnerability scanner that everyone should be using, not just cybersecurity professionals. In this blog, I’ve demonstrated installing and setting up Nessus on Windows. In Part II, I will demonstrate how to set up an authenticated scan and tweak some settings on Windows to allow Nessus to perform an authenticated scan.

Author Bio
Joseph Choi is a Cybersecurity Analyst with Alpine Security. He holds several security-related certifications, including Certified Ethical Hacker (CEH), EC-Council Certified Security Analyst (ECSA), CyberSec First Responder (CFR), Security+, and Network+. Joseph is a graduate from Truman State University with a B.S. in Business Administration.
Joseph's cybersecurity experience began at Alpine and includes penetration tests, vulnerability assessments, and wireless penetration tests. He was born and raised in South Korea until the age of 10 when he moved to Mexico. It wasn't until 2007 that his family moved to the States where he completed his high school and college education. He is a fan of Mr. Robot, and in his spare time he enjoys spending time with his girlfriend, taking long walks around the park, and going to the gym.
0 notes
Text
10 Excellent Tools You Must Apply In Web Performance Testing
Web Performance Testing Tools – Looking to test the heap pressure limit and execution of your web applications? Here are ten of the best web execution testing devices to guarantee that your application performs even in outrageous pressure and pinnacle traffic conditions.
This rundown incorporates authorized just as open source web performance testing apparatuses, yet you can discover free preliminary forms of most authorized instruments. Attempt your hand with these preliminary forms before you settle on your official conclusion. We should investigate them
Web Performance Testing Tools
WebLOAD
WebLOAD is a heap and web execution testing apparatus for web applications that empowers pressure and burden testing utilizing Adobe Flex, Ajax, HTML5, Oracle Forms, Microsoft .NET and different advancements. You can create load from on-premises machines or from the cloud.
The device is entirely simple to utilize, and it highlights programmed relationship, DOM-based account and playback, and different highlights. In view of JavaScript, the instrument underpins extensive scale testing with intricate and overwhelming client load conditions.
The instrument produces an unmistakable investigation of a web application's exhibition and usefulness, and it has a committed, solid customer base. It has additionally won a few honors. All the more essentially, it has a quite alluring evaluating and authorizing model.
WebLOAD has a broad scope of highlights and backings different web advancements, enabling you to perform load testing and copy gigantic client loads. You can rapidly manufacture tests, produce load and dissect the outcomes with a rich arrangement of reports that distinguishes explicit execution issues.
The heap situation is produced in JavaScript so you can make upgrades according to your necessities. The standard language is upgraded with inbuilt burden testing strategies and articles that offer HTTP usefulness, DOM usefulness, load techniques and the sky is the limit from there. The device additionally incorporates robotized relationship to discover and supplant session IDs, time and other powerful qualities.
Apache JMeter
An open source load testing device, Apache JMeter is additionally based on a Java stage. In spite of the fact that it is considered for the most part as a web exhibition testing apparatus, you can likewise coordinate it with the test plan. You can make load test and utilitarian test designs too. The apparatus can be stacked into a system or server so as to evaluate its execution under different working conditions.
Apache JMeter was first presented for web application testing, however today it is utilized for various different purposes too. It is especially valuable to test the execution of Java objects, Perl Scripts and Servlets and different assets.
The instrument can likewise test the execution of static assets, web dynamic dialects like ASP.NET, Java, and PHP, databases, questions, FTP servers and substantially more. It can mimic a substantial burden on server gatherings, singular servers, items or systems to evaluate its quality and execution under various sorts of burdens. You can utilize the JMeter to produce a graphical examination of your web application's execution or to test your server, article or content conduct under substantial simultaneous burden.
Apache JMeter can load and test the execution of a few sorts of servers/conventions:
· Web-HTTP, HTTPS
· FTP
· Cleanser/REST
· LDAP
· Database by means of JDBC
· Message-situated middleware through JMS
· MongoDB
· SMTP, POP3, and IMAP email
· Local directions and shell contents
· TCP
Different highlights of this instrument include:
100 percent Java virtue

Convenientce
A full multithreading system for simultaneous inspecting by different strings and examining of different capacities at the same time by string gatherings
· A GUI structure that empowers quicker investigating and test plan creation
· Storing and disconnected examination
· Test outcomes replaying
· Pluggable samplers for further testing capacities
· Pluggable clocks for a wide decision of burden insights
· Information representation and examination modules for personalization and extensibility
· Capacities to give dynamic test information or information control
· Scriptable samplers in JSR223-perfect and BSF-good dialects
HP LoadRunner
Hewlett Packard's LoadRunner is an available web exhibition testing apparatus that can comprehend and decide the execution of a framework under burden. A key favorable position of this instrument is that it can deal with and create a huge number of clients at the same time. It empowers you to assemble all execution related and foundation-based data.
LoadRunner comprises of different separate instruments: Virtual User Generator, Load Generator and Analysis, and Controller. It works by making a situation that contains the content that will be executed. The quantity of virtual clients required is additionally created, alongside different essentials for running the test and producing the normal outcomes. The quantity of virtual clients to be created could go from a couple of hundred to a couple of thousand.
The situation could be manual or objective arranged, in which the instrument naturally produces the situations dependent on recently determined objectives by the analyzer. The arrangement of activities to be performed are recorded onto the virtual client content. A heap generator is then used to run the clients, producing the essential dimension of burden on the framework. The procedures to be estimated are spoken to as exchanges. When the heap is created, the framework conduct is checked and broke down.
· Prescribed courses
· Web Services in Java Course
· Online Certification Course in Game Development in C++
· Online Certification Training in Ethical Hacking
· Preparing on Vegas Pro 13
· Judicious Web Performance Tester
The Rational Performance Tester from IBM is a computerized web act testing apparatus for web and server-based applications in which there is an info and yield process. The instrument produces a demo of the first exchange procedure, assembling and dissecting factual data to build proficiency. Any server or site spillage can be promptly distinguished and corrected, and it tends to be utilized to make a blunder free, viable distributed computing administration.
The device can recognize the nearness and underlying driver of bottlenecks in framework execution. It consolidates a few conveniences includes alongside point by point examination, streamlining test creation, lead age, and information accumulation procedures to guarantee that their web applications can suit the required client loads.

NeoLoad
NeoLoad by France-based Netosys is a Java-based web execution testing instrument that can be utilized for estimating and dissecting a site's act. It can likewise be utilized to dissect further strides to be taken dependent on the execution of the site and final product of the tests. This, thusly, improves and enhance the execution of your web application.
The instrument works by expanding the traffic on your site and after that breaking down the execution of the application under substantial burden. You get the chance to comprehend the limit of the application and what number of clients it can deal with at the same time. Written in Java, NeoLoad is accessible in French and English. It reenacts client action in web and portable applications too, and screens the foundation conduct. You can look over cloud-based burden generators for the execution test.
NeoLoad can be utilized for robotizing the total Web 2.0 suite, which incorporates Flex, Silver Light, Web Services, Web and Multimedia. The client can decide the quantity of burden generators that are required and the LGs from LAN. They can likewise reenact 2G-4G and WiFi versatile systems with varieties in flag qualities.
The device can be coordinated with outsider devices like Dynatrace, App Dynamics, Introscope and Site Scorpion for a profound jump investigation on servers. In any case, SLA setup isn't accessible on this instrument for breaking down the outcomes. At last, it is an exhibition testing answer for portable and web applications that can be utilized for running cloud-based tests. In the event that you or your execution group needs a device that can investigate and co-relate test results with crude information, NeoLoad would be an extraordinary decision. The instrument is perfect on working frameworks Solaris, Linux and Windows.
LoadUI
The following open source pressure test and web execution testing device in this rundown is LoadUI, once more to gauge the execution of a web application. The device works really well when it is coordinated with the soapUI practical testing instrument. It is a standout amongst the most intelligent and adaptable testing apparatuses as well, enabling you to make, refresh and design your tests while the application is tried. It gives a visual guide too for the client with a simplified component.
LoadUI is a long way from a static act apparatus. It offers propelled report creating and investigation producing highlights that let you inspect the genuine execution of the web application by including new information even as the application is being tried. You don't need to restart the device each time that you change or alter the application. LoadUI gets refreshed naturally in the interface. It is a cross-stage instrument, so it should work for any major working framework. It is additionally accessible for nothing, given that it is open framework.

WAPT
This specific web execution testing instrument can be utilized for intranet applications and sites. WAPT is short for Web Performance Testing Tool, and it goes about as a scale or breaking down device for estimating the yield and execution of a web application and related interface.
The apparatuses help measure the execution of any web-related interface, web administration or web application. You can utilize this apparatus to test the application execution in various situations and burden conditions.
The apparatus gives point by point data on the virtual clients and its yield to the clients amid burden testing. It is considered by numerous individuals to be a standout amongst the best and most practical apparatuses for investigating the execution of web administrations.
The WAPT instrument can likewise test the similarity of a web application with working frameworks and programs. It tends to be utilized for testing the similarity with Windows applications in specific cases.
0 notes
Text
Interview For Cybersecurity
Following are often posed inquiries in interviews for freshers just as experienced network protection confirmation competitors.
1) What is cybersecurity?
cybersecurity alludes to the insurance of equipment, programming, and information from assailants. The main role of network safety is to ensure against cyberattacks like getting to, changing, or obliterating touchy data.
2) What are the components of online protection?
Significant components of online protection are:
Data security
Organization security
Operational security
Application security
End-client schooling
Business congruity arranging
3) What are the benefits of network protection?
Advantages of network safety are as per the following:
It secures the business against ransomware, malware, social designing, and phishing.
It secures end-clients.
It gives great security for both information just as organizations.
Increment recuperation time after a break.
Online protection forestalls unapproved clients.
4) Define Cryptography.
It is a method used to shield data from outsiders called foes. Cryptography permits the sender and beneficiary of a message to peruse its subtleties.
5) Differentiate among IDS and IPS.
Interruption Detection System (IDS) recognizes interruptions. The director must be cautious while forestalling the interruption. In the Intrusion Prevention System (IPS), the framework discovers the interruption and forestall it.
6) What is CIA?
Secrecy, Integrity, and Availability (CIA) is a famous model which is intended to foster a security strategy. CIA model comprises of three ideas:
Classification: Ensure the touchy information is gotten to simply by an approved client.
Trustworthiness: Integrity implies the data is in the correct configuration.
Accessibility: Ensure the information and assets are accessible for clients who need them.
7) What is a Firewall?
It is a security framework intended for the organization. A firewall is defined on the limits of any framework or organization which screens and controls network traffic. Firewalls are for the most part used to shield the framework or organization from malware, worms, and infections. Firewalls can likewise forestall content sifting and far off access.
8) Explain Traceroute
It is a device that shows the parcel way. It records every one of the focuses that the bundle goes through. Traceroute is utilized for the most part when the parcel doesn't arrive at the objective. Traceroute is utilized to check where the association breaks or stops or to distinguish the disappointment.
9) Differentiate among HIDS and NIDS.
Parameter HIDS NIDS
Usage HIDS is utilized to recognize the intrusions. NIDS is utilized for the organization.
What does it do? It screens dubious framework exercises and traffic of a particular device. It screens the traffic of all gadget on the organization.
10) Explain SSL
SSL represents Secure Sockets Layer. It is an innovation making encoded associations between a web worker and an internet browser. It is utilized to ensure the data in online exchanges and advanced installments to keep up information security.
11) What do you mean by information spillage?
Information spillage is an unapproved move of information to the rest of the world. Information spillage happens through email, optical media, PCs, and USB keys.
12) Explain the beast power assault. How to forestall it?
It is an experimentation strategy to discover the correct secret phrase or PIN. Programmers monotonously attempt every one of the mixes of accreditations. As a rule, animal power assaults are robotized where the product consequently works to login with qualifications. There are approaches to forestall Brute Force assaults. They are:
Setting secret key length.
Increment secret key intricacy.
Put forth line on login disappointments.
13) What is port examining?
It is the strategy for distinguishing open ports and administration accessible on a particular host. Programmers utilize port filtering strategy to discover data for malignant purposes.
14) Name the various layers of the OSI model.
Seven distinct layers of OSI models are as per the following:
Actual Layer
Information Link Layer
Organization Layer
Transport Layer
Meeting Layer
Show Layer
Application Layer
15) What is a VPN?
VPN represents Virtual Private Network. It is an organization association technique for making a scrambled and safe association. This technique shields information from impedance, sneaking around, control.
16) What are dark cap programmers?
Dark cap programmers are individuals who have a decent information on penetrating organization security. These programmers can create malware for individual monetary profit or other malignant reasons. They break into a protected organization to change, take, or obliterate information with the goal that the organization can not be utilized by approved organization clients.
17) What are white cap programmers?
White cap programmers or security expert are represented considerable authority in entrance testing. They ensure the data arrangement of an association.
18) What are dark cap programmers?
Dark cap programmers are PC programmer who in some cases abuse moral norms, however they don't have pernicious aim.
19) How to reset a secret key secured BIOS setup?
There are different approaches to reset BIOS secret key. Some of them are as per the following:
Eliminate CMOS battery.
By using the product.
By using a motherboard jumper.
By using MS-DOS.
20) What is MITM assault?
A MITM or Man-in-the-Middle is a kind of assault where an aggressor captures correspondence between two people. The fundamental aim of MITM is to get to classified data.
21) Define ARP and its functioning cycle.
It is a convention utilized for discovering MAC address related with IPv4 address. This convention fill in as an interface between the OSI organization and OSI connect layer.
22) Explain botnet.
It's various web associated gadgets like workers, cell phones, IoT gadgets, and PCs that are tainted and constrained by malware.
23) What is the fundamental distinction among SSL and TLS?
The fundamental distinction between these two is that SSL confirms the character of the sender. SSL assists you with following the individual you are conveying to. TLS offers a safe channel between two customers.
24) What is the contraction of CSRF?
CSRF represents Cross-Site Request Forgery.
25) What is 2FA? How to carry out it for a public site?
TFA represents Two Factor Authentication. It is a security cycle to recognize the individual who is getting to an online record. The client is allowed admittance solely after introducing proof to the confirmation gadget.
26) Explain the contrast among topsy-turvy and symmetric encryption.
Symmetric encryption requires a similar key for encryption and unscrambling. Then again, hilter kilter encryption needs various keys for encryption and unscrambling.
27) What is the full type of XSS?
XSS represents cross-site prearranging.
28) Explain WAF
WAF represents Web Application Firewall. WAF is utilized to secure the application by separating and observing approaching and active traffic between web application and the web.
29) What is hacking?
Hacking is a cycle of discovering shortcoming in PC or private organizations to misuse its shortcomings and get entrance.
For instance, utilizing secret key breaking method to access a framework.
30) Who are programmers?
A Hacker is an individual who finds and adventures the shortcoming in PC frameworks, cell phones, tablets, or organizations to obtain entrance. Programmers are very much experienced software engineers with information on PC security.
31) What is network sniffing?
Organization sniffing is an instrument utilized for dissecting information bundles sent over an organization. This should be possible by the specific programming project or equipment hardware. Sniffing can be utilized to:
Catch touchy information like secret word.
Snoop on visit messages
Screen information bundle over an organization
32) What is the significance of DNS observing?
Yong areas are handily tainted with pernicious programming. You need to utilize DNS observing devices to distinguish malware.
33) Define the way toward salting. What is the utilization of salting?
Salting is that interaction to expand the length of passwords by utilizing unique characters. To utilize salting, it is vital to know the whole system of salting. The utilization of salting is to shield passwords. It likewise forestalls aggressors testing known words across the framework.
For instance, Hash("QxLUF1bgIAdeQX") is added to every single secret key to ensure your secret key. It is called as salt.
34) What is SSH?
SSH represents Secure Socket Shell or Secure Shell. It is a utility suite that gives framework executives secure approach to get to the information on an organization.
35) Is SSL convention enough for network security?
SSL checks the sender's character, yet it doesn't give security once the information is moved to the worker. It is great to utilize worker side encryption and hashing to secure the worker against an information break.
36) What is discovery trying and white box testing?
Discovery testing: It is a product testing strategy in which the inward construction or program code is covered up.
White box testing: A product testing strategy in which inner construction or program is known by analyzer.
37) Explain weaknesses in network security.
Weaknesses allude to the flimsy part in programming code which can be abused by a danger entertainer. They are most generally found in an application like SaaS (Software as an assistance) programming.
38) Explain TCP Three-way handshake.
It is a cycle utilized in an organization to make an association between a nearby host and worker. This technique requires the customer and worker to arrange synchronization and affirmation parcels prior to beginning correspondence.
39) Define the term remaining danger. What are three different ways to manage hazard?
It is a danger that adjusts hazard openness subsequent to finding and dispensing with dangers.
Three different ways to manage hazard are:
Decrease it
Keep away from it
Acknowledge it.
40) Define Exfiltration.
Information exfiltration alludes to the unapproved move of information from a PC framework. This transmission might be manual and done by anybody having physical a
0 notes
Text
Top Ten metal fabrication Related Trends To Keep In View.
RJB Steel Ltd is a specialist welding and steel fabrication company based in Woodchurch http://woodchurchinfo.com/directory/ pic.twitter.com/iMxAo7kliL — Woodchurch Info (@WoodchurchInfo) December 6, 2017
Although the electrode-positive part of the Air Conditioner cycle helps eliminate the oxide layer that accumulates on aluminum, you may wish to use a devoted stainless-steel brush to manually cleanse the material prior to welding. Using this brush for other functions will certainly introduce international pollutants to the weld joint and also endanger the weld's structural integrity. An oxide layer begins to form promptly after cleaning, so it is likewise required to rebrush an item that sits for a prolonged amount of time without being bonded. A few of the devices used are the scissors or bench shears which are really great specifically if you have cumbersome materials that are hard to cut with the normal devices. Although the tools will look the very same, you ought to separate the many blades that are used for different purposes. Easy Plugin for AdSense. Subdue this ad port. Punching the materials generally needs to be performed with a punching maker. Typically, a hole is pierced with the steels.
With their maximized processes, design requirements can be maximized at full size. Production amounts can in some way influence the typical costing. Therefore, one is required to obtain quotes from several possible producers. To obtain started, it could be a great idea to obtain comments from various other customers. There are no better sources of details aside from those who have used solutions from particular suppliers. Hunters might search for honest online reviews or simply browse for people to interview personally. Yes, the process is called "nesting," as well as utilizing it efficiently permits Cobra to maintain production expenses affordable while additionally decreasing product prices. What kinds of quality control programs are adhered to? We provide superb high quality for our customers. We mainly make use of arbitrary sampling as well as testing based on statistical sampling to make certain top quality. In turn, this is mainly based upon the size of the metal marking manufacturing run. Component precision is examined at the beginning as well as end of each change or item run. Exactly what is the thinnest scale product you will produce? We will certainly make a part to 24 gauge (.024 ). That is in charge of the cost of tool maintenance? Cobra pays of routine tool maintenance. What is Cobra's minimum order? High levels of skill as well as precision and also complete knowledge of steel working are vital requirements, to satisfy clients' needs. Custom manufacture processes are accomplished to customers' demands and specifications. There are numerous processes performed which are fancy and also extensive in details according to each job. Puncturing with all materials is feasible using latest modern technologies such as laser cutting makers, water jet reducing devices and also turret punching machines. Steel marking, robotic welding are some of the processes made use of for steel fabrication techniques. The paper takes a look at welding procedure patterns in the building and construction of structures, bridges, pipes and other engineering items necessary for framework in city environments. Performance gains in arc welding are reviewed, and also the raising use of laser cutting as well as welding, as well as laser-arc hybrid welding, particularly in Europe, is talked about and also described. Some friction technologies are already commonly embraced, yet they might make even more influence with further growth. The last 50 years have actually seen big improvements in efficiency for many arc welding procedures and also arc welding still produces the mass of welding outcome in engineering building and construction today. Increasingly, high power laser, hybridlaser-arc, electron beam of light (EB) and rubbing welding methods are starting to showcase in the manufacture of large range frameworks in numerous countries, and usage is expected to expand. EOAT: End Of Arm Tooling. This is everything bolted to the end of the tool plate. An instance is a transformer bolted to the tool plate but not really completion effect. The transformer only supports the operation of completion effector. Manipulator: The robot arm (every little thing other than the EOAT). TCP: Tool Center Point. This is the point (coordinates) that we program in connection with. Positioning Axes: The other joints (4, 5, 6). These joints are constantly rotary.
Going Into G-Code Commands
Call Your Panels
Making pure uranium dioxide (UO2) from inbound UF6 or UO3
Stress Die Setup
Light weight aluminum fascia
The Router Coordinate System
Just what is metal stamping? Stamping is a term used to refer to different press forming operations including: creating, embossing, blanking, pressing, and forming metals making use of stress right into the surface of a metal, typically a strip or sheet. The procedures most frequently related to stamping are blanking, piercing, creating, and also illustration. These procedures are made with devoted tooling also called tough tooling. Tough tooling is utilized to earn high quantity components of one arrangement of a component style. This is yet one more kind of steel manufacture tools made use of in order to make the task of people less complicated. Searching for those with foot pedals and also emergency situation stops is highly positive for the business. Programmable axes could assist manage blade voids, stroke length, back determine and shearing times. At times, the shears are additionally commendable for its capacity to move spheres and load steel sheets. It likewise possesses a complete defense guard system. Shears are made use of in order to provide quiet as well as smooth operation while cutting or producing metal parts. There are different usages of these steels. Metal develops an essential part for numerous things that we make use of in our day to day life. The metals need to be made into wanted shapes. Manufacture of steels primarily implies the cutting, welding as well as bending of metals in the wanted form for use in commercial as well as domestic function. The reducing includes procedure like sawing, sculpting as well as shearing. The flexing is done by hammering manually or by press brakes. The fabrication of metals is made using most advanced treatments. There are numerous uses of these steels. Making new welds "hard as steel" takes effort. Commonly clients ask that the customized or fixed mold and mildew location have a firmness of 32-36 Rc. The mold material initially should be assessed to identify the correct electrode dimension and also filler steel to match the tool steel composition, so the specific heat treatment approach could be determined. NORTH SIDE STEEL WORK Certifying firmness of the steel figures out the materials to be made use of in addition to the toughening up contours to be utilized with the materials that are being welded. It does not need to be the primary choosing element, but it can be valuable when the firm is near to you. It can assist to lower costs, although always consider the overall expenses as opposed to deciding based on location alone. The quality of the completing is an essential factor to consider. You will certainly desire a construction that can complete it to your exact specifications, and also the company might do this on its premises, or it may subcontract it. Nonetheless, some suitable device must be repaired inside the device for it to punch efficiently. Afterwards, the continuing to be sheet is clipped as necessary. This indicates eliminating any excess product from it hence offering it the requisite size. The various other task involved in producing steels is referred to as shaping. This entails a selection of forming operations that are generally described as bending or folding. Devices such as presses and also those of its kind are utilized in this process. Relocating Y steps laterally. Sometimes it is essential to extremely precisely find a part on the router table. You can do this utilizing the measure tool. Usually this is stored in slot 9 of the carousel. If not you'll locate it in the device cabinet near the router. Go into the G-Code to load the device: M6T9 and also press the Green Go switch. The device is loaded from slot 9. The measurement procedure includes running the probe to touch the challenge gauge as well as reviewing the coordinate data from the screen. Prototek is below to help our designers style and also draw components that are simple for us to deal with keeping the distribution as well as cost to a minimum. Please check out below or call our Engineering Team with any type of questions you may have, you could likewise Chat straight with them utilizing the following link, please go into the Chat room and after that enter our Engineering Chat Room. Described right here are suggested methods for making use of the SolidWorks CAD software program ´ s sheet metal performance for SolidWorks.
Undertaking Six Sigma certification is not a basic job, as every possibility for an issue need to be energetically accounted for and outlined on a pareto layout to locate effectiveness and high quality enhancing routines to be carried out right into on a daily basis processes. Each worker will have to comprehend just what it means to attain Six Sigma, as quality and also effectiveness has always been Prototek's specific niche. Prototek Sheet Metal Manufacturing began in October of 1987 specializing in rapid prototyping as well as brief run manufacturing of sheet steel and CNC machined parts for the hi-tech industries. Their facility is a new 40,000 sq. ft. Therefore, if you are seeking the aluminium fabricators, see to it that you are hiring a person who is extremely experienced. You need to make certain that the individual has been in the area for a substantial number of years. Only then, he will have the ability to recognize the called for approaches as well as gadgets required for the task. After all, the aluminium construction needed special interest as well as just a skilled producer will have the ability to discover that out.
0 notes
Text
This Is Why This Year Will Be The Year Of metal fabrication.
This relates to any type of steel item as well as specialist companies will certainly not wait to offer their advice and also skills, so that you wind up a satisfied consumer. The look for blacksmiths can begin online, given that several firms advertise their services online. This method, you could find out more about just what they have to offer, browse through established tasks and see whether they can assist in the requests you have. Steel manufactures Glasgow will look wonderful when they are produced as well as put together in the right one, making certain they are secure and also secure in the exact same time. Are you interested in including steel fabrications Glasgow to your residence or service? Despite the tasks you have to accomplish, you can count on these blacksmiths Glasgow. On top of that, our customer support team is focused on answering any questions our customers may have regarding ship days, revision changes, as well as order standing, assuring they are satisfied every action of the method. RFQ that are sent out to [email protected] or submitted directly via one of our internet sites will receive a quote within a day. Prototek Manufacturing can collaborate with several data consisting of dxf, stp, action, iges, pdf, Pro-E, Solidworks, Autocad and also Inventor files. They are generated utilizing a balanced out surface. The technique begins by finding the closest factor externally to the axis of each side. The vector in between the axis as well as the closest factor is copied over to the corners of the side as well as lengthened. These vectors are then converged with the surface area. This is done for each side of the polygon. The verts are attached by lines which form all-time lows of the planar tabs. A stainless-steel balustrade is versatile. Steel balustrades never ever pinch your pocket. Such a balustrade is such an addition which would give you significant benefits in lieu of a meager amount of money. The extensive accessibility of stainless steel makes it an extremely budget-friendly manufacturing material. Apart from the cost effective purchase benefit, it also gives you remedy for installation cost as it is additionally much less. A stainless steel balustrade is flexible. Wide array of choices in regards to form, dimension, makes as well as looks is readily available. Although the complete charge for these services is in fact really low when contrasted to embalming and typical interments, it could still be substantial for those who get on a spending plan. With a layaway plan, you could make certain that your family is not swamped with funeral service expenditures after you die. People frequently believe that they will certainly not have a chance to claim farewell to their liked ones when making use of these services. Actually, nonetheless, the real cremation process does not start up until the funeral has actually been held. They are given top quality training for completing this task. Like every various other job sheet metal fabrication too needs experience and also you need knowledgeable specialists. When you do sheet metal manufacture with seasoned professionals you obtain the very best outcomes. There are many sheet steel manufacture business that you may get perplexed to pick one from a long listing. It is important to do some research study on this problem before you take the decision. Prototek presently has 65 staff members and also has actually increased right into a one quit shop for all machining and sheet steel demands. They are house to state of the art welding and flexing divisions, as well as plating rooms, setting up division, and far more. Prototek's particular niche has actually constantly been a strong commitment to on-time shipments of top quality products. They produce from 3D strong models or CAD (computer system assisted style) documents, as well as keep a big, constant supply of essential materials, sheetmetal stock, machinable plastics and steel, and PEM equipment. Prototek is presently ISO 9001:2008 certified as well as ITAR and DFAR compliant. Manufacture of steels includes several procedures of manufacture like welding, folding, cutting, punching, shearing, marking and a lot more. All these procedures are made use of to transform the forms of metals and also make various items that work in industrials works like functioning machines smoothly as well as usage of parts in it. Metal fabrication has been provided for ages to use metal in various forms. With the improvement in scientific research and innovation this technique has customized.
Base X: 1102.51
Metal Fabrication Robots Market Vendors landscape
Inexpensive Sourcing
Japanese JIS
It contains movable reducing blade as well as crank drive to appropriately cutting sheet steels. site link Afterwards the laser light is pushed transversely the outside of metal sheets so about cut right into Computer Numeric Control lasers pieces. Computer System Numerical Control Punch Press is then utilized in reducing steel sheets into various shapes or dimensions such that of a hexagon, square or circle . Water jets making usage of high water stress that varies from 20,000 as much as 60,000 with the purpose of effectively cutting steels. What Do Steel Fabricators (http://www.trucutfabricators.com/metal-fabrication-lynchburg-va-244260/) Do? Author: Andrew Cooper Steel is a incredibly long lasting as well as multi-functional metallic alloy of iron, carbon and little quantities of sulphur, phosphorus, silicon, manganese as well as oxygen. Carbon is actually a setting agent that offers steel is hardness and durability. Author: gaga Background: Structural Steel Elements Structural steel is usually believed of as the "skeletal system" of multi-story building, in that it supplies the structure whereupon outside, flooring and wall cladding systems are affixed. When it concerns selecting lively colour and also boundary dramatization you truly can't go incorrect and also whatever size your garden there's always area for a few even more. Publisher: Blair E DePaul University, located in Chicago, has made a huge relocation for its vehicle parking garage illumination. Energy efficient LED light bulbs have actually changed the metal halide light bulbs that originally occupied the outlets in the garage. Author: Blair E The University of Alabama has actually replaced the 400 watt metal halide light bulbs in their Gymnastics Practice Gym with MaxLite HighMax high wattage 200 watt portable fluorescent light bulbs. The increase in power performance has actually reduced their lights expense by fifty percent! Forming a fold or sharp factor from an undefined elevated location similar to this is called acumination. The color in this picture is the outcome of annealing. Home heating copper triggers the metal to create oxides on it's surface. These oxides are untidy as well as frustrating as well as need to be eliminated, unless they are intended to be part of the sculpture's coating. Copper is usually cleaned up with something acidic or by mechanically rubbing the surface area. I clean up copper with a weak sulfuric acid as well as water mix, yet have likewise utilized vinegar or lemon juice with suitable results, although it is significantly slower. You get this movement type using the KUKA|prc Lin Movement part. You utilize the right-click menu on this part to pick the interpolation settings. The robotic overviews the TCP at a defined rate along a circular path throughout factor. The round course is specified by a start point, complementary factor and also end factor. You obtain this movement kind by utilizing the KUKA|prc Cir Movement part. You utilize the right-click menu on this element to choose the interpolation setups. The robotic will move along the placements in a smooth spline movement. Author: Koz Huseyin Buying a HDTV for the home is among the best things you can do for your residence amusement demands. Think about the exceptional picture quality. Consider the ability to enjoy in hd. There is a great deal to HDTV innovation, however there is 3 things you should know. Publisher: Flynna Sarah Molina For other individuals, purchasing a home is the main goal why they work. Once they begin earning money, several of them desire to spend for the purpose of purchasing a house. Home is always in addition to everyone's priority. In the event you loved this informative article and you would love to receive more details relating to metal gates (Going In this article) generously visit our own website.
0 notes
Text
Ctronics Bullet Wifi Ip Camera Hd 720p 30m Ir 3.6mm Lens Onvif 2.0 36 Leds Night Vision Indoor&outdoor 16G Brand SD Card Built-in CTIPC-245C720PWS
Ctronics Bullet Wifi Ip Camera Hd 720p 30m Ir 3.6mm Lens Onvif 2.0 36 Leds Night Vision Indoor&outdoor 16G Brand SD Card Built-in CTIPC-245C720PWS
Do not miss this chance to get this product on most reasonably priced value.
Pros:
1280×720 HD Wi-fi WiFi out of doors IP digital camera,30m IR vary,indoor&out of doors Weatherproof to IP66 Ranking with Full Steel Casing and Sunshield.
Free iPhone, iPad, Android apps providing simple setup and viewing – no want for a PC or complicated set up. Simply 2 Steps WiFi Setup (2.four GHz community required,5.Zero GHz WIFI router would not assist). Free PC and Mac Dwell view obtainable too(MAC want to put in Quicktime).
ONVIF 2.Zero appropriate,works with multi manufacturers NVR,Ctronics, Hikvision, Dahua,and so forth.SD card slot for simple storage.
Robotically file on movement to Micro SD card (Takes as much as 128GB playing cards.16G branded SD Card built-in)Observe:Solely assist fats32 format, for different format SD card,should be formated by this digital camera.
Free on the spot push alerts to your cell/pill when movement is detected. Playback recordings from cell phone or PC everytime you need to test again in your property in addition to view Dwell video anytime.
Get this Ctronics Bullet Wifi Ip Digital camera Hd 720p 30m Ir Three.6mm Lens Onvif 2.Zero 36 Leds Night time Imaginative and prescient Indoor&out of doors 16G Model SD Card Constructed-in CTIPC-245C720PWS
Observe: Please obtain the Hiplayer to play the video from SD card by this hyperlink: http://ift.tt/2jjIf1e
Picture Sensor: 1/four” OV9732 coloration CMOS WXGA (1 megapixel) HD sensor Show Decision: 1280*720 Pixels Lens: Three.6mm (F:1.four ) Min. Illumination: Zero.5Lux (0LUX on) Picture Compression: H.264 Gentle Frequency: 50Hz, 60Hz Picture Decision: 720p(1280*720),VGA(640*480),CIF(352*288) Picture body price: 25fps(50Hz), 30fps(60Hz),Down adjustable View: H.264 twin streaming Picture modify: The brightness, distinction, saturation, chromaticity, is adjustable White stability: Automated, Indoor, out of doors , is adjustable Infrared mode: Automated , guide (on/off) Night time visibility: Φ5mm 36 IR LEDs, Night time visibility as much as 30 metres Ethernet: One 10/100Mbps RJ-45 Supported Protocol: TCP/IP、UDP/IP、HTTP、SMTP、FTP、DHCP、DDNS、UPNP Wi-fi Commonplace: WIFI(IEEE802.11b/g/n) Information Price: 802.11b: 11Mbps(Max.) 802.11g: 54Mbps(Max.) 802.11n: 150Mbps(Max.) Assist IP handle: static IP handle, dynamic IP handle Alarm detection: The movement detecting, detection threshold Settings Alarm inform: Assist Electronic mail、FTP and so forth alarm inform means POWER Interface: DC 12V1.0A (EU,US,AU adapter or different sorts optionally available) Ethernet: One 10/100Mbps RJ-45 Wi-fi Interface: WIFI antenna CE FC, Restricted 1 years guarantee
Bundle: 1*1 720P IR bullet digital camera 1*CD with software program 1*energy adaptor 1*guide
It’s all the time higher to purchase Ctronics Bullet Wifi Ip Digital camera Hd 720p 30m Ir Three.6mm Lens Onvif 2.Zero 36 Leds Night time Imaginative and prescient Indoor&out of doors 16G Model SD Card Constructed-in CTIPC-245C720PWS from the the chief on this eCommerce trade. They’ve proved their skill in delivering high quality service after shopping for implausible merchandise from them.
The post Ctronics Bullet Wifi Ip Camera Hd 720p 30m Ir 3.6mm Lens Onvif 2.0 36 Leds Night Vision Indoor&outdoor 16G Brand SD Card Built-in CTIPC-245C720PWS appeared first on IPCAMVOX.
from Ctronics Bullet Wifi Ip Camera Hd 720p 30m Ir 3.6mm Lens Onvif 2.0 36 Leds Night Vision Indoor&outdoor 16G Brand SD Card Built-in CTIPC-245C720PWS
0 notes