#SQLi Scanner
Explore tagged Tumblr posts
Text
Remote Code Execution (RCE) Attack in Symfony
Remote Code Execution (RCE) vulnerabilities are among the most dangerous web security flaws. If an attacker exploits an RCE vulnerability in your Symfony application, they can execute arbitrary commands on your server — potentially gaining full control over your system!

In this post, we’ll dive deep into what RCE in Symfony looks like, see real coding examples, learn how to prevent it, and explore how our free website vulnerability scanner online can help you identify such issues.
What is Remote Code Execution (RCE)?
Remote Code Execution occurs when an application executes user-supplied input without proper validation or sanitization. In Symfony, insecure coding practices or unsafe handling of user data can easily lead to RCE vulnerabilities.
If exploited, RCE can allow attackers to:
Steal sensitive information
Install malware
Take full control of the server
This is why identifying and patching RCE vulnerabilities early is critical.
RCE Vulnerability Example in Symfony
Here’s a real-world example of insecure code in a Symfony application that could lead to an RCE vulnerability:
// Controller Example (Vulnerable to RCE) use Symfony\Component\HttpFoundation\Request; public function vulnerableCommandAction(Request $request) { $userCommand = $request->query->get('cmd'); $output = shell_exec($userCommand); return new Response("<pre>$output</pre>"); }
✅ Problem: The cmd parameter is taken directly from user input and passed to shell_exec() without any validation — a textbook RCE vulnerability!
Testing the RCE Vulnerability
An attacker could simply pass a malicious command like this:
http://yourwebsite.com/run-cmd?cmd=ls%20-la
Or worse:
http://yourwebsite.com/run-cmd?cmd=rm%20-rf%20/
👉 These examples show how deadly this vulnerability can be!
How to Fix RCE in Symfony Applications
Symfony developers must avoid running user input in system-level commands. Here are some good practices:
1. Avoid Direct Shell Execution
Instead of shell_exec(), use Symfony’s Process Component safely:
use Symfony\Component\Process\Process; use Symfony\Component\Process\Exception\ProcessFailedException; public function safeCommandAction(Request $request) { $command = 'ls -la'; // Never use user input directly! $process = Process::fromShellCommandline($command); $process->run(); if (!$process->isSuccessful()) { throw new ProcessFailedException($process); } return new Response("<pre>".$process->getOutput()." </pre>"); }
2. Whitelist Allowed Commands
If you must allow user input, validate it strictly:
$allowedCommands = ['list', 'status']; $userCommand = $request->query->get('cmd'); if (!in_array($userCommand, $allowedCommands)) { throw new \Exception('Invalid command!'); } $command = 'git ' . escapeshellarg($userCommand); $output = shell_exec($command);
Important: Always sanitize and validate user input!
3. Implement Strong Server Permissions
Even if a vulnerability exists, make sure the server permissions are tight enough to limit damage.
📸 Screenshot of Our Website Vulnerability Scanner Tool:

Use our free tool to scan your website for Remote Code Execution vulnerabilities and more!
📸 Screenshot of Vulnerability Assessment Report:

Get a detailed vulnerability report to check Website Vulnerability and fix issues before attackers find them!
How to Detect RCE Vulnerabilities Easily
Manually finding RCE vulnerabilities can be complex. That’s why we recommend using a trusted security scanner.
✅ Try our free free Website Security Scanner tool. ✅ It scans your site for RCE risks, misconfigurations, and more vulnerabilities. ✅ It's quick, simple, and secure.
You can also stay updated with our latest cybersecurity guides at Pentest Testing Blog.
New! Web App Penetration Testing Services 🚀
If you want a professional penetration testing service to deeply inspect your web applications for vulnerabilities like RCE, SSRF, SQLi, and more — we've got you covered!
Check out our service page: 🔗 Web App Penetration Testing Services
Detailed reports
Manual and automated testing
Best industry practices followed
Make your web app bulletproof today!
Conclusion
Remote Code Execution (RCE) vulnerabilities in Symfony applications are extremely dangerous but completely preventable with secure coding practices.
Regularly scan your website, validate all user inputs, avoid executing unsanitized data, and follow security best practices. 🔒 Stay safe, stay secure — and don't forget to try our free tool for Website Security check today!
1 note
·
View note
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text
SQL injection | SQL注入
SQLi是一种网络安全漏洞,它允许攻击者干扰应用程序对其数据库进行的查询。这可能允许攻击者查看他们通常无法检索的数据。这可能包括属于其他用户的数据,或者应用程序可以访问的任何其他数据。在许多情况下,攻击者可以修改或删除这些数据,导致应用程序的内容或行为发生持久变化。
在某些情况下,攻击者可以升级SQL注入攻击,以破坏底层服务器或其他后端基础设施。它还可以使他们能够执行拒绝服务攻击。
[图片]
假设有一个网站URL https://someurl.com/someroute?param=some_value,它返回一组公共数据。当请求此URL时,服务器的中间件会生成一个SQL查询来检索数据:
SELECT * FROM SOMEROUTE WHERE SOME_CONDITION = 'some_value' AND RELEASED = 1
这个查询旨在返回SOME_CONDITION与URL参数中提供的值匹配且RELEASED标志设置为1的数据,表示公共数据。
然而,如果黑客在GET请求的param值后附加'--,它有效地注释掉了SQL查询的其余部分,导致中间件返回所有数据,包括公共和私有数据。修改后, https://someurl.com/someroute?param=some_value'-- 将导致以下SQL查询:
SELECT * FROM SOMEROUTE WHERE SOME_CONDITION = 'some_value' --' AND RELEASED = 1
`--` 之后的内容被视为注释,因此忽略了AND RELEASED = 1条件。
此外,如果黑客将URL更改为https://someurl.com/someroute?param=some_value'+OR+1=1--,他们利用了OR 1=1 始终为真的事实。这导致以下SQL查询:
SELECT * FROM SOMEROUTE WHERE SOME_CONDITION = 'some_value' OR 1 = 1 --' AND RELEASED = 1;
同样,`--` 注释掉了AND RELEASED = 1条件,由于1=1始终为真 (TRUE),查询返回SOMEROUTE的所有行,忽略任何条件。
应用程序逻辑的颠覆:
想象一下这样的情景, 一个网站要求用户输入用户名和密码进行登录。然后,应用程序使用类似以下查询的方式检查这些凭据:SELECT * FROM USERS WHERE USERNAME = 'username' AND PASSWORD = 'password' 。如果提供的凭据与数据库中存储的匹配,则应用程序会继续进行其他阶段,例如转到主页面。然而,攻击者或黑客可以利用应用程序逻辑中的漏洞来获取未经授权的访问权限。
一种常见的方法涉及操纵查询以完全绕过密码检查。通过输入一个特制的用户名,比如administrator'--,攻击者可以有效地注释掉查询中的密码检查部分。这导致应用程序执行类似于SELECT * FROM USERS WHERE USERNAME = 'administrator' -- AND PASSWORD = ''" 的查询,从而允许攻击者无需有效密码即可登录。
此外,攻击者还可以利用UNION关键字执行SQL注入攻击,并从数据库中的其他表中检索敏感数据。例如,如果应用程序通常查询SELECT NAME, DESCRIPTION FROM PRODUCTS WHERE CATEGORY = 'GIFTS'来显示可用产品,则攻击者可以注入一个UNION SELECT USERNAME, PASSWORD FROM USERS 的语句,将结果与用户凭据合并。这将允许攻击者从数据库中提取用户名和密码。
SELECT NAME, DESCRIPTION FROM PRODUCTS WHERE CATEGORY = ' GIFTS ' UNION SELECT USERNAME , PASSWORD FROM USERS
对于开发人员来说,实施强大的输入验证和参数化查询至关重要,以防止此类攻击,并保护敏感数据免受未经授权的访问。定期进行安全审计和测试可以帮助识别和解决应用程序逻辑中的潜在漏洞。
成功的SQL注入攻击会有什么影响?
成功的SQL注入攻击可能导致未经授权的访问敏感数据,例如:
• 密码。
• 信用卡详细信息。
• 个人用户信息。
多年来,SQL注入攻击已被用于许多高调的数据泄露事件。这些事件造成了声誉损害和监管罚款。在某些情况下,攻击者可以获得组织系统的持久后门,导致长期妥协,可能长时间不被发现。
如何检测SQL注入漏洞?
您可以使用一套系统的测试手动检测每个应用程序入口点的SQL注入。为此,您通常会提交:
• 单引号字符'并查找错误或其他异常。
• 一些SQL特定语法,评估入口点的基本(原始)值和不同的值,并寻找应用程序响应中的系统差异。
• 布尔条件,如OR 1=1和OR 1=2,并寻找应用程序响应中的差异。
• 设计用于在SQL查询中执行时触发时间延迟的有效载荷,并寻找响应时间的差异。
• 设计用于在SQL查询中执行时触发出站网络交互的OAST有效载荷,并监视任何结果交互。
或者,您可以使用Burp Scanner快速可靠地找到大多数SQL注入漏洞。
查询中不同部分的SQL注入
大多数SQL注入漏洞发生在SELECT查询的WHERE子句中。大多数有经验的测试人员都熟悉这种类型的SQL注入。
然而,SQL注入漏洞可以发生在查询的任何位置,以及在不同的查询类型中。SQL注入出现的一些其他常见位置包括:
• 在UPDATE语句中,在更新的值或WHERE子句中。
• 在INSERT语句中,在插入的值中。
• 在SELECT语句中,在表名或列名中。
• 在SELECT语句中,在ORDER BY子句中。
SQL注入示例
有许多不同情况下发生的SQL注入漏洞、攻击和技术。一些常见的SQL注入示例包括:
• 检索隐藏的数据,您可以修改SQL查询以返回额外的结果。
• 颠覆应用程序逻辑,您可以更改查询以干扰应用程序的逻辑。
• UNION攻击,您可以从不同的数据库表中检索数据。
• 盲SQL注入,您控制的查询结果不会在应用程序的响应中返回。
SQL注入示例
存在许多不同情况下的SQL注入漏洞、攻击和技术。一些常见的SQL注入示例包括:
• 检索隐藏数据,您可以修改SQL查询以返回额外的结果。
• 颠覆应用程序逻辑,您可以更改查询以干扰应用程序的逻辑。
• UNION攻击,您可以从不同的数据库表中检索数据。
• 盲SQL注入,您控制的查询结果不会在应用程序的响应中返回。
二阶SQL注入
一阶SQL注入发生在应用程序处理来自HTTP请求的用户输入,并以不安全的方式将输入纳入SQL查询中。二阶SQL注入发生在应用程序接收来自HTTP请求的用户输入并将其存储以供将来使用时。这通常是通过将输入放入数据库来完成的,但在存储数据时不会出现漏洞。稍后,在处理不同的HTTP请求时,应用程序会检索存储的数据,并以不安全的方式将其纳入SQL查询。因此,二阶SQL注入也被称为存储型SQL注入。
[图片]
二阶SQL注入通常发生在开发者意识到SQL注入漏洞,并因此安全地处理输入数据至数据库的情况。当数据稍后被处理时,由于之前已安全地存放在数据库中,它被认为是安全的。此时,数据以不安全的方式被处理,因为开发者错误地认为它是可信的。
检查数据库
SQL语言的一些核心特性在流行的数据库平台中以相同的方式实现,因此许多检测和利用SQL注入漏洞的方法在不同类型的数据库上工作方式相同。
然而,常见数据库之间也存在许多差异。这意味着一些检测和利用SQL注入的技术在不同平台上的工作方式不同。例如:
• 字符串连接的语法。
• 注释。
• 批处理(或堆叠)查询。
• 特定平台的API。
• 错误信息。
在你识别出SQL注入漏洞后,获取有关数据库的信息通常很有用。这些信息可以帮助你利用漏洞。
你可以查询数据库的版本详细信息。不同的方法适用于不同类型的数据库。这意味着如果你找到一个特定的方法有效,你可以推断出数据库类型。例如,在Oracle上,你可以执行:
SELECT * FROM v$version
你还可以识别存在哪些数据库表,以及它们包含哪些列。例如,在大多数数据库上,你可以执行以下查询来列出表格:
SELECT * FROM information_schema.tables
不同上下文中的SQL注入
在之前的实验室中,你使用查询字符串来注入恶意SQL有效载荷。然而,你可以使用任何可控输入来执行SQL注入攻击,只要应用程序将其作为SQL查询处理。例如,一些网站接受JSON或XML格式的输入,并使用这些输入来查询数据库。
这些不同的格式可能提供了不同的方法来混淆攻击,这些攻击由于WAFs和其他防御机制而被阻止。弱实现通常会在请求中查找常见的SQL注入关键字,因此你可能能够通过编码或转义禁止关键字中的字符来绕过这些过滤器。例如,以下基于XML的SQL注入使用XML转义序列来编码SELECT中的S字符:
<stockCheck>
<productId>123</productId>
<storeId>999 SSELECT * FROM information_schema.tables</storeId>
</stockCheck>
这将在服务器端解码,然后传递给SQL解释器。
SQL注入速查表
1. 字符串连接: 不同的数据库有不同的字符串连接语法。例如,Oracle使用’foo’||‘bar’,而Microsoft SQL Server使用’foo’+‘bar’。
2. 子字符串:您可以从指定的偏移量提取字符串的一部分,具有指定的长度。在所有数据库中,偏移索引都是基于1的。
3. 注释:注释可用于截断查询并删除跟随您输入的部分。不同数据库的注释语法不同,如Oracle和Microsoft使用–comment,MySQL使用#comment。
4. 数据库版本:您可以查询数据库以确定其类型和版本,这对于制定更复杂的攻击非常有用。
5. 数据库内容:您可以列出数据库中存在的表及其包含的列。这通常使用information_schema.tables和information_schema.columns来完成。
6. 条件错误:您可以测试单个布尔条件,并在条件为真时触发数据库错误。这对于盲SQL注入非常有用,其中结果不直接可见。
7. 不同上下文中的SQL注入:SQL注入可以使用应用程序作为SQL查询处理的任何可控输入来执行,不仅仅是通过查询字符串。
0 notes
Text
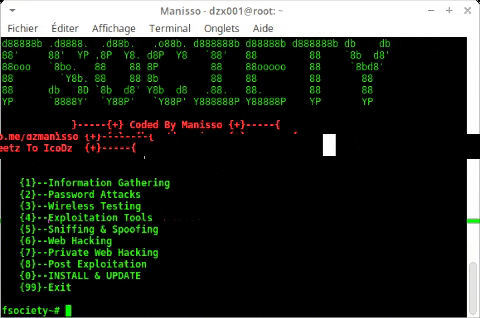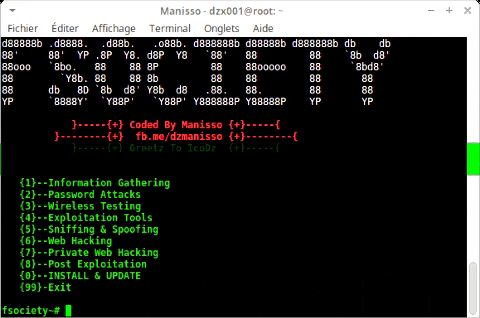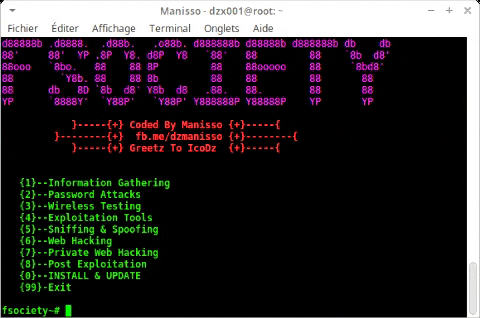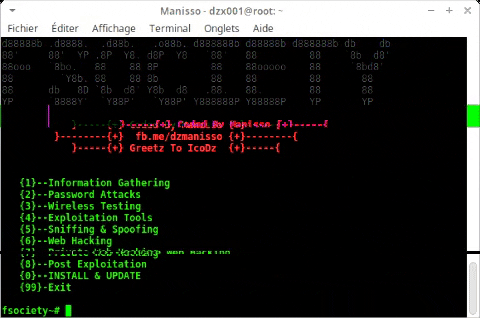
Fsociety Hacking Tools Pack
Paquete de herramientas de hacking de Fsociety: un marco de prueba de penetración.
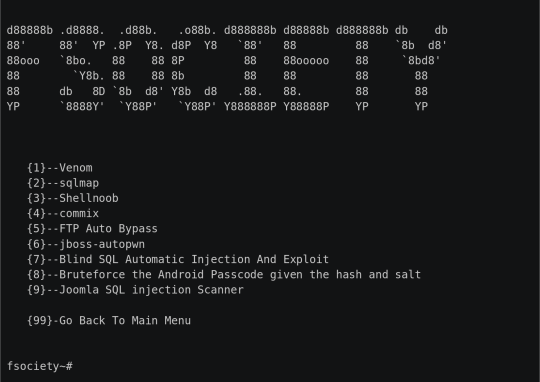
Fsociety es un sistema de prueba de penetración hermoso que comprende todos los dispositivos de prueba de penetración que necesita un programador. Incorpora todos los dispositivos asociados a la serie Mr. Robot. Esta herramienta consta de una inmensa lista de dispositivos que comienza con la estructura de la información del evento social para después de la explotación.
Menu
Information Gathering
Password Attacks
Wireless Testing
Exploitation Tools
Sniffing & Spoofing
Web Hacking
Private Web Hacking
Post Exploitation
Contributors
Install & Update
Information Gathering:
Nmap
Setoolkit
Host To IP
WPScan
CMS Scanner
XSStrike
Dork - Google Dorks Passive Vulnerability Auditor
Scan A server's Users
Crips
Password Attacks:
Cupp
Ncrack
Wireless Testing:
Reaver
Pixiewps
Bluetooth Honeypot
Exploitation Tools:
ATSCAN
sqlmap
Shellnoob
Commix
FTP Auto Bypass
JBoss Autopwn
Sniffing & Spoofing:
Setoolkit
SSLtrip
pyPISHER
SMTP Mailer
Web Hacking:
Drupal Hacking
Inurlbr
WordPress & Joomla Scanner
Gravity Form Scanner
File Upload Checker
WordPress Exploit Scanner
WordPress Plugins Scanner
Shell and Directory Finder
Joomla! 1.5 - 3.4.5 remote code execution
Vbulletin 5.X remote code execution
BruteX - Automatically brute force all services running on a target
Arachni - Web Application Security Scanner Framework
Private Web Hacking:
Get all websites
Get joomla websites
Get wordpress websites
Control Panel Finder
Zip Files Finder
Upload File Finder
Get server users
SQli Scanner
Ports Scan (range of ports)
Ports Scan (common ports)
Get server Info
Bypass Cloudflare
Post Exploitation:
Shell Checker
POET
Weeman
Installation
Installation Linux
bash <(wget -qO- https://git.io/vAtmB)
Installation
Download Termux
bash <(wget -qO- https://git.io/vAtmB)
33 notes
·
View notes
Text
Striker - Offensive Information And Vulnerability Scanner
Striker - Offensive Information And Vulnerability Scanner #Vulnerability #Scanner #Offensive #hacking #Information #Striker
Striker is an offensive information and vulnerability scanner.
Features Just supply a domain name to Striker and it will automatically do the following for you:
Check and Bypass Cloudflare
Retrieve Server and Powered by Headers
Fingerprint the operating system of Web Server
Detect CMS (197+ CMSs are supported)
Launch WPScan if target is using WordPress
Retrieve robots.txt
Check if the target is a…
View On WordPress
#Attack#Bypass Cloudflare#CloudFlare#honeypot#Information#Offensive Information#SQLi#SQLi Scanner#SQLmap#Striker#Vulnerability#Vulnerability Scanner#WPScan
0 notes
Text
Hacktronian. Otra herramienta all-in-one para Pentesters
Hacktronian quiere hacernos la vida más fácil a los Pentesters ofreciendo un conjunto de herramientas de hacking accesibles a través de un menú.
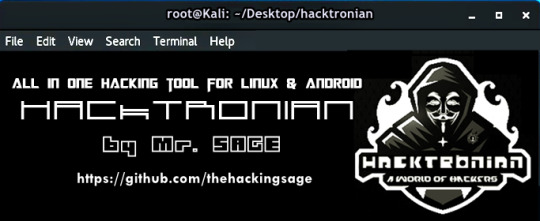
Lo bueno es que se puede instalar tanto en Linux como en Android (mediante Termux y siendo root)
Esto es lo que contiene la herramienta
HACKTRONIAN Menu :
Information Gathering
Password Attacks
Wireless Testing
Exploitation Tools
Sniffing & Spoofing
Web Hacking
Private Web Hacking
Post Exploitation
Install The HACKTRONIAN
Information Gathering:
Nmap
Setoolkit
Port Scanning
Host To IP
wordpress user
CMS scanner
XSStrike
Dork - Google Dorks Passive Vulnerability Auditor
Scan A server's Users
Crips
Password Attacks:
Cupp
Ncrack
Wireless Testing:
reaver
pixiewps
Fluxion
Exploitation Tools:
ATSCAN
sqlmap
Shellnoob
commix
FTP Auto Bypass
jboss-autopwn
Sniffing & Spoofing:
Setoolkit
SSLtrip
pyPISHER
SMTP Mailer
Web Hacking:
Drupal Hacking
Inurlbr
Wordpress & Joomla Scanner
Gravity Form Scanner
File Upload Checker
Wordpress Exploit Scanner
Wordpress Plugins Scanner
Shell and Directory Finder
Joomla! 1.5 - 3.4.5 remote code execution
Vbulletin 5.X remote code execution
BruteX - Automatically brute force all services running on a target
Arachni - Web Application Security Scanner Framework
Private Web Hacking:
Get all websites
Get joomla websites
Get wordpress websites
Control Panel Finder
Zip Files Finder
Upload File Finder
Get server users
SQli Scanner
Ports Scan (range of ports)
ports Scan (common ports)
Get server Info
Bypass Cloudflare
Post Exploitation:
Shell Checker
POET
Weeman
Instalación en Linux :
(la herramienta hay que ejecutarla como ROOT)
git clone https://github.com/thehackingsage/hacktronian.git
cd hacktronian
chmod +x install.sh
./install.sh
Lanzarla escribiendo hacktronian
Instalación en Android :
Abrir Termux
pkg install git
pkg install python
git clone https://github.com/thehackingsage/hacktronian.git
cd hacktronian
chmod +x hacktronian.py
python2 hacktronian.py
Más info en su repositorio de GitHub
2 notes
·
View notes
Text
Fix Security Misconfigurations in Symfony Easily
Symfony is a powerful PHP framework used by developers worldwide. But like all platforms, it's vulnerable to security misconfigurations if not set up correctly. These misconfigurations can expose your app to serious threats like unauthorized access, data leakage, and more.

In this guide, we’ll walk you through how security misconfigurations happen in Symfony, how attackers exploit them, and how you can fix them—along with real coding examples.
And the best part? You can use our free website vulnerability scanner online to instantly detect misconfigurations and other vulnerabilities in your web apps.
🔎 What is Security Misconfiguration?
Security misconfiguration happens when:
Unnecessary services are enabled.
Default credentials are used.
Error messages leak sensitive data.
Debug mode is active in production.
In Symfony apps, this often includes exposed .env files, open profiler tools, or misconfigured firewalls.
⚠️ Common Symfony Misconfiguration Examples (and Fixes)
Let’s look at some real-world Symfony misconfiguration examples—and how to fix them fast.
✅ 1. Disabling Symfony Debug Mode in Production
Issue: When debug mode is enabled in production, detailed error messages expose internal files and paths.
Misconfigured Code (in .env):
APP_ENV=dev APP_DEBUG=1
Fixed Configuration:
APP_ENV=prod APP_DEBUG=0
Pro Tip: Never commit .env files with debug settings to version control.
✅ 2. Securing the Profiler Tool
Issue: The Symfony Profiler gives deep app insights but should never be exposed in production.
Risk: Attackers can view routing, services, and database queries.
How to Disable Profiler in Production:
# config/packages/prod/web_profiler.yaml web_profiler: toolbar: false intercept_redirects: false framework: profiler: enabled: false
✅ 3. Harden HTTP Headers
Misconfiguration: Default Symfony headers don’t include secure settings.
Solution (Using a Response Event Listener):
// src/EventListener/SecurityHeaderListener.php namespace App\EventListener; use Symfony\Component\HttpKernel\Event\ResponseEvent; class SecurityHeaderListener { public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $response->headers->set('X-Frame-Options', 'DENY'); $response->headers->set('X-Content-Type-Options', 'nosniff'); $response->headers->set('Referrer-Policy', 'no- referrer'); } }
Register Listener in Services.yaml:
services: App\EventListener\SecurityHeaderListener: tags: - { name: kernel.event_listener, event: kernel.response }
🛡️ Prevent Directory Listings
Exposing directory indexes can leak source files or configuration data.
Apache Fix:
Options -Indexes
Nginx Fix:
location / { autoindex off; }
🖼️ Screenshot: Our Free Website Security Checker Tool

Screenshot of the free tools webpage where you can access security assessment tools.
Use our website vulnerability scanner to instantly check if your Symfony app is misconfigured or vulnerable. It’s fast, simple, and doesn’t require installation.
📄 Screenshot: Sample Vulnerability Assessment Report

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
You’ll receive a detailed report like this to check Website Vulnerability, highlighting every vulnerability—including misconfigurations, XSS, SQLi, and more—so you can fix them before attackers find them.
🔁 Extra Tips to Avoid Symfony Misconfigurations
Disable unused bundles.
Validate permissions in security.yaml.
Sanitize file uploads.
Never expose sensitive routes like /phpinfo() or /admin/.
🧪 Test Your Symfony App Now – It’s Free
Don’t wait for attackers to find your security flaws. Use our free vulnerability scanner to detect weaknesses in your Symfony-based apps in minutes.
Looking for more cybersecurity insights? Visit our main blog at Pentest Testing Corp. where we regularly share vulnerability breakdowns, tools, and remediation tips.
📌 Final Thoughts
Symfony is secure by design—but only if configured correctly. Always sanitize your environment, remove default settings, and test thoroughly. Misconfiguration is one of the top OWASP vulnerabilities and can be avoided with basic hygiene.
1 note
·
View note
Text
Vulnerability Management of your Complete IT stack from SQL vulnerability
Now it’s high time to secure yourself from SQL Injection, one of the SANS ( SysAdmin, Audit, Network, and Security) vulnerabilities. There is a severe security risk associated with SQL injection vulnerable sites since attackers use them to extract entire database contents and be used to execute commands on the server.
Attacks by SQL Injection are very disastrous because of these two facets:
The important pervasiveness of SQL vulnerabilities.
Alluringness of the target(i.e., a database which contains all the significant and fascinating data of your application).
So, If you want to protect your applications from SQL Injection vulnerability, this blog is for you.
What is SQL Injection?
Web app vulnerabilities such as SQL injection (SQLi) allow attackers to modify an application’s queries to its database. Mainly, it will enable the attacker to view data they cannot usually fetch. Moreover, it includes the data attachment to other users or the other data that the application retrieves by itself.
However, in most cases, an attacker can customize or delete this data, leading to a consistent substitute for the application’s content. SQL injection attacks can compromise the underlying server or other back-end infrastructure, as well as trojan attacks.
Impact Of SQL Injection on your web applications?
Filching Credentials: Attackers can attain credentials through SQLi and then imitate users and use their benefit.
Acquire Database: Hackers can permit sensitive data in the database servers.
Modify Data: Hackers can modify or add new details or information to the acquired database.
Delete Data– hackers, can remove the database details and drop complete tables.
Oblique Movement: Hackers can attain database servers with operating system advantages and use this authorization to access other delicate systems.
Protect yourself from SQL Injection attacks by using ESOF AppSec ESOF AppSec helps you in protecting your complete IT stack from SQL Injection, which is a SANS vulnerability. It detects the vulnerabilities in the system; therefore, you don’t need prevention. Also, it does vulnerability management in environments where SQL Injection vulnerabilities occur.
Secures your system in the following ways with ESOF AppSec:
Timely Scanning: It allows you to scan the vulnerability on a monthly, weekly, and annual basis when it comes across SQL injection vulnerability. However, one must have ESOF vulnerability scanner licenses to secure their systems.
Zero-False Positives: It also maintains an option for both automated and manual testing for detecting and analyzing all potential vulnerabilities for assets.
Time: With an ESOF vulnerability management timeline, team members can become aware of the open and patched threats they have encountered since the first scan. Allowing them to react immediately if a possible business threat becomes apparent.
Cyber Risk Score: Observing the risk measures of an organization’s applications gives you a comprehensive understanding of its security posture using the ESOF Cyber Risk Score powered by A.I. Therefore, after detecting vulnerabilities, it provides a cyber risk score.
Top 10 vulnerabilities: Now that the platform is modern, it is possible to deliver a detailed and segmented report that outlines the Top 10 Vulnerabilities and risk severity in the hybrid IT stack associated with them.
Trend History: Upon boarding, you will see a detailed description of what has happened over the last five years regarding your organization’s Information Technology security posture.
Conclusion
ESOF AppSec helps you find SQL Injection vulnerabilities at your fingertips in your application. Also, it has advanced scanners which scan your complete hybrid IT stack.
ESOF with Next-Gen Execution capabilities detects the vulnerabilities in your web apps and provides you with a cyber risk score.
Get your ESOF Cyber Risk Score now.
0 notes
Photo

Vulnerability Testing Tools | Web Scanner
The ScantricsVulnerability Testing Tools is a Site Scanner which automated application scan and gives you the confidence to make smart decisions about how to eliminate vulnerability and protect your organization’s digital assets from application attacks. It combines the power of the Scantrics platform with the cloud based security capabilities of Primary Guard to deliver through its API the ability for Develops teams to move faster in a more secure way.
To know more just visit this link: https://scantrics.io/sqli-scanner
0 notes
Text
[Media] ReconFTW
ReconFTW Automates the entire process of reconnaisance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target. ReconFTW uses lot of techniques (passive, bruteforce, permutations, certificate transparency, source code scraping, analytics, DNS records...) for subdomain enumeration which helps you getting the maximum and the most interesting subdomains so that you be ahead of the competition. It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target. https://github.com/six2dez/reconftw #scanner
YouTubeThe automated recon using reconftw | Bug Bounty ToolIn this video, we will see how use ReconFTW tool for recon. It automates the entire process of reconnaisance for you. It performs the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target. GitHub Link: https://github.com/six2dez/reconftw It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target. Need Better Machine to Hack? Setup your own VPS today! Get $100 credit on Digital Ocean using this link https://m.do.co/c/551f689486b2 ⏩ If you like the Video then please like , share and subscribe to channel ⏩ Follow us on Social Media Twitter : https://twitter.com/simrotion13 Thanks For Watching😊 #bugbounty #recon #automation #reconftw Everything is Just for Educational Purpose

0 notes
Photo
V3n0M-Scanner: Pentesting Scanner for SQLi/XSS/LFI/RFI | #pentesting #scanner #vulnerabilities #security
0 notes
Text
SQLiv – Massive SQL Injection Vulnerability Scanner – Kali Linux 2017.2
SQLiv – Massive SQL Injection Vulnerability Scanner – Kali Linux 2017.2
Hey Guys, In this video i show you a cool tool called SQLiv which used to scan websites for sql injection.
SQLiv: https://github.com/Hadesy2k/sqliv
Features: multiple domain scanning with SQL injection dork by Bing, Google, or Yahoo targetted scanning by providing specific domain (with crawling) reverse domain scanning
both SQLi scanning and domain info checking are done in multiprocessing so the…
View On WordPress
#how to find sql vulnerable sites#how to find vulnerable websites#how to install sqli scanner#how to scan a website for vulnerabilities#how to scan website#how to scan website vulnerabilities#how to use sqli scanner in kali linux#kali linux#kali linux 2017#kali linux hacking tutorials#linux#Massive SQL injection scanner#pentesttools#scan#scan website for vulnerabilities kali#sql#SQL Injection#SQLi#SQLi Scanner#SQLiv#vulnerabilities#website hacking
0 notes
Text
SQLi Scanner v.1.0 New 2019

youtube
https://www.virustotal.com/gui/file/b2a1dd726115cf01916e54cff80f866dc40596eb634a3d0c74fe425aa91ca57f/detection Link Download : http://www.mediafire.com/folder/c0rktaos02grd/SQLiScannerKidux
https://drive.google.com/open?id=1SgGfQmQDTiI6Zdbhf8mbXuomONG4rvu9
https://www.dropbox.com/sh/dbs7541kqjkhtgl/AAC3emgYDqHPDeELjj2wDUmka?dl=0 Pass mmo My blog : https://www.freetoolss.com/ https://freetools2020.tumblr.com My Youtube Channel : https://www.youtube.com/channel/UCZ3nkUMvkKBBb1Nj1nO2TWQ
0 notes
Text
Simple SQLi Dork Scanner 2019

https://www.virustotal.com/gui/file/984509bca2e43f0b703ffe7741894838d700eb0a20566f585ea428506ba066ed/detection Download : https://mega.nz/#F!3JdVQSCY!iG7iYR1MLi1BvD_yygarWQ Pass mmo My blog: https://mmo4allonline.blogspot.com https://www.freetoolss.com/ My Youtube Channel: https://www.youtube.com/channel/UCZ3nkUMvkKBBb1Nj1nO2TWQ
0 notes
Text
Prevent XSS Attacks in Symfony Applications
Cross-Site Scripting (XSS) remains one of the most exploited web vulnerabilities, especially in modern PHP frameworks like Symfony. In this post, we'll explore how XSS vulnerabilities can creep into Symfony apps, how attackers exploit them, and how to fix or prevent these issues with practical code examples.

You’ll also see how you can scan your site for free using the Website Vulnerability Scanner, which helps detect XSS vulnerabilities and other issues automatically.
🔍 What is Cross-Site Scripting (XSS)?
Cross-Site Scripting (XSS) is a type of vulnerability that allows attackers to inject malicious JavaScript into webpages viewed by other users. The goal? Stealing cookies, session tokens, or redirecting users to malicious sites.
There are three common types:
Stored XSS – Malicious script is permanently stored on the target server.
Reflected XSS – Script is reflected off a web server, often in search results or error messages.
DOM-based XSS – Happens entirely on the client side using JavaScript.
⚠️ XSS in Symfony: How it Happens
Even though Symfony is a robust framework, developers may still accidentally introduce XSS vulnerabilities if they don’t properly escape output or trust user input blindly.
✅ Vulnerable Example: Output Without Escaping
// src/Controller/SampleController.php public function unsafeOutput(Request $request): Response { $name = $request->query->get('name'); return new Response("<h1>Hello, $name!</h1>"); }
If a user visits:
http://example.com?name=<script>alert('XSS')</script>
This JavaScript will execute in the browser. That’s a textbook XSS vulnerability.
🛡️ Secure Coding: Escaping Output in Symfony
Symfony uses Twig by default, which automatically escapes variables. But developers can override this behavior.
✅ Safe Example with Twig
{# templates/welcome.html.twig #} <h1>Hello, {{ name }}</h1>
This is safe because Twig escapes {{ name }} by default. But if you do this:
<h1>Hello, {{ name|raw }}</h1>
You disable escaping, making it vulnerable again. Avoid using |raw unless you're 100% sure the content is safe.
✋ Validating and Sanitizing Input
Always sanitize and validate input using Symfony’s form and validator components.
✅ Example Using Symfony Validator
use Symfony\Component\Validator\Constraints as Assert; use Symfony\Component\Validator\Validation; $validator = Validation::createValidator(); $violations = $validator->validate($userInput, [ new Assert\NotBlank(), new Assert\Regex([ 'pattern' => '/^[a-zA-Z0-9\s]*$/', 'message' => 'Only alphanumeric characters allowed.' ]), ]); if (count($violations) > 0) { // Handle validation errors }
🧪 Detecting XSS Automatically with a Free Tool
Want to find XSS vulnerabilities without writing a line of code?
Use the free security scanner by Pentest Testing Corp for a Website Security test. It scans your website for XSS, SQLi, Clickjacking, and many other issues.
🖼️ Screenshot of the Website Security Checker homepage

Screenshot of the free tools webpage where you can access security assessment tools.
📄 Sample XSS Detection Report
After scanning, you’ll get a detailed vulnerability report to check Website Vulnerability. Here’s a sample:
🖼️ Screenshot of a vulnerability assessment report

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
This includes affected URLs, vulnerability types, severity levels, and remediation suggestions.
🔗 Learn More About Web Security
Visit our blog at Pentest Testing Corp. for more insights, tutorials, and vulnerability write-ups.
✅ Final Checklist for Preventing XSS in Symfony
✅ Use Twig’s auto-escaping.
✅ Never use |raw unless absolutely necessary.
✅ Validate user input with Symfony's Validator.
✅ Sanitize dynamic content before outputting.
✅ Scan your app regularly with tools like free.pentesttesting.com.
Cross-Site Scripting is dangerous, but with a few best practices and tools, you can keep your Symfony app safe. Try out our website vulnerability scanner and harden your web applications today!
1 note
·
View note
