#Scanner - Advanced Auditing and Professional Ethics
Explore tagged Tumblr posts
Text
Best Tools & Software You Will Learn in an Ethical Hacking Course in CRAFT Dehradun

In today’s digital world, cybersecurity threats are on the rise, making ethical hacking a crucial skill for IT professionals. If you're looking for a top-rated Ethical Hacking Course in Dehradun, CRAFT Empowering Careers offers a hands-on program covering all the essential tools and software used by ethical hackers. Join now and kickstart your journey in cybersecurity!
Why Learn Ethical Hacking?
Ethical hackers play a key role in securing networks, applications, and data from cyber threats. Learning ethical hacking opens doors to exciting career opportunities in cybersecurity, penetration testing, and network security. By enrolling in our Ethical Hacking Course in Dehradun, you'll gain real-world experience with industry-standard tools and techniques.
Essential Tools & Software Covered in the Course
At CRAFT Empowering Careers, our ethical hacking course includes practical training on some of the most powerful tools used in cybersecurity.
1. Kali Linux – The Ultimate Penetration Testing OS
Pre-installed with top security tools like Nmap, Metasploit, and Wireshark.
Used by professionals for ethical hacking and penetration testing.
2. Metasploit Framework – Mastering Exploits
A must-have tool for penetration testers.
Helps in identifying vulnerabilities and launching simulated cyberattacks.
3. Wireshark – The Best Network Analysis Tool
Monitors and captures network traffic to detect unauthorized activities.
Essential for network security assessments.
4. Nmap (Network Mapper) – Scanning & Auditing Networks
Helps in network discovery, identifying open ports, and running security audits.
Used by professionals to map out network vulnerabilities.
5. Burp Suite – Web Application Security Testing
An advanced tool for detecting vulnerabilities like SQL injection and cross-site scripting (XSS).
Essential for web security professionals.
6. Aircrack-ng – Wireless Security Assessment
Tests the security of Wi-Fi networks.
Helps in cracking WEP and WPA-PSK encryption for security analysis.
7. SQLmap – Automated SQL Injection Detection
Detects and exploits SQL injection vulnerabilities in databases.
A must-have tool for database security testing.
8. John the Ripper – Password Cracking Made Easy
Helps test the strength of passwords.
Supports various encryption techniques and algorithms.
9. Nikto – Web Server Security Scanner
Scans web servers for outdated software, misconfigurations, and vulnerabilities.
Ensures website security against cyber threats.
10. Maltego – Cyber Intelligence & Investigation Tool
Used for information gathering and mapping relationships between entities.
Helps cybersecurity professionals in reconnaissance and intelligence gathering.
Enroll in the Best Ethical Hacking Course in Dehradun
At CRAFT Empowering Careers, we provide practical training with real-world hacking scenarios to help you master cybersecurity skills. Our course is designed for beginners and professionals looking to build a strong foundation in ethical hacking.
Key Features of Our Ethical Hacking Course:
✔ Hands-on training with real-world tools.
✔ Expert guidance from cybersecurity professionals.
✔ Certification upon course completion.
✔ 100% placement assistance for career growth.
Enroll Now and take the first step toward a rewarding cybersecurity career!
Conclusion
Cybersecurity is a booming field, and ethical hackers are in high demand. By mastering tools like Kali Linux, Metasploit, Wireshark, and more, you can boost your cybersecurity skills and land high-paying jobs in the IT sector. Join the Ethical Hacking Course in Dehradun at CRAFT Empowering Careers and start your journey today!
For more details, visit: CRAFT Empowering Careers Ethical Hacking Course
0 notes
Text
Is 70 Days enough to Clear the CA Final Group 1 from Scratch ?

The Chartered Accountancy (CA) Final is one of the most challenging exams in the field of finance and accounting. Clearing CA Final Group 1 requires not only a solid understanding of complex concepts but also the ability to apply them in various scenarios. If you’re starting from scratch with just 70 days to prepare, the task might seem daunting, but it is not impossible. With the right strategy, focus, and discipline, you can significantly improve your chances of success. One valuable resource to consider during your preparation is using Scanner CA Final books. These books can help you identify important topics and frequently asked questions, providing a targeted approach to your study plan.
1. Understand the Syllabus and Prioritize
The first step is to thoroughly understand the syllabus for CA Final Group 1. The group covers four key subjects:
Financial Reporting
Strategic Financial Management (SFM)
Advanced Auditing and Professional Ethics
Corporate and Economic Laws
Given the vastness of the syllabus, it's essential to prioritize topics based on their weightage in the exam. Focus on high-scoring areas first, ensuring that you cover essential topics that are likely to appear in the exam. Create a study plan that allocates sufficient time to each subject, with more time dedicated to complex topics.
2. Create a Detailed Study Plan
A well-structured study plan is crucial when you have limited time. Break down the 70 days into weeks and further into days, assigning specific topics and chapters to each day. Ensure that your plan includes time for revision and practice exams. A suggested plan might look like this:
Focus: Core Subjects Overview
Day 1-2: Review Subject 1 - Read through main topics and key chapters.
Day 3-4: Practice questions from the CA Final scanner for Subject 1.
Day 5-6: Review Subject 2 - Focus on important chapters and concepts.
Day 7: Practice questions from the CA Final scanner for Subject 2.
Weeks 3-4:
Focus: Deep Dive into Subjects
Day 8-10: Study Subject 1 in detail - Major topics and past papers.
Day 11-13: Practice questions from the CA Final scanner for Subject 1.
Day 14: Revision of Subject 1.
Day 15-17: Study Subject 2 in detail - Major topics and past papers.
Day 18-20: Practice questions from the CA Final scanner for Subject 2.
Day 21: Revision of Subject 2.
Weeks 5-6:
Focus: New Subjects and Integration
Day 22-24: Study Subject 3 - Main topics and key areas.
Day 25-27: Practice questions from the CA Final scanner for Subject 3.
Day 28: Revision of Subject 3.
Day 29-31: Study Subject 4 - Major topics and focus areas.
Day 32-34: Practice questions from the CA Final scanner for Subject 4.
Day 35: Revision of Subject 4.
Weeks 7-8:
Focus: Mock Exams and Revision
Day 36-38: Take mock exams for Subjects 1 and 2.
Day 39-40: Review and analyze mock exam results for Subjects 1 and 2.
Day 41-43: Take mock exams for Subjects 3 and 4.
Day 44-45: Review and analyze mock exam results for Subjects 3 and 4.
Weeks 9-10:
Focus: Final Revision and Exam Strategy
Day 46-48: Revise all subjects with a focus on weaker areas.
Day 49-51: Final practice with CA Final scanner questions for all subjects.
Day 52-53: Take full-length mock exams and analyze results.
Day 54-56: Adjust study focus based on mock exam results.
Weeks 11-10:
Focus: Final Preparation
Day 57-59: Intensive revision of key topics and weak areas.
Day 60-62: Review important formulas, concepts, and CA Final scanner summaries.
Day 63-65: Take final mock exams to gauge preparedness.
Day 66-68: Review mock exam results and refine strategy.
Day 69-70: Relax and ensure you’re well-rested for the exam day.
3. Focus on Conceptual Clarity
Starting from scratch means you need to build your foundation quickly. Focus on understanding the concepts rather than rote memorization. CA exams test your ability to apply knowledge, so ensure that you grasp the underlying principles of each topic. Use study materials, reference books, online resources, and CA Final scanner to aid your understanding. If you come across any difficult concepts, don’t hesitate to seek help from peers, mentors, or online forums.
4. Practice, Practice, Practice
Practicing problems and case studies is crucial to reinforce your learning with the right study material for CA. Dedicate time each day to solve problems, especially in subjects like Financial Reporting and SFM. For auditing and law, practice writing answers to theoretical questions, focusing on structuring your answers clearly and concisely. Additionally, take timed mock tests using comprehensive study CA to simulate the exam environment and improve your time management skills.
5. Maintain Discipline and Stay Positive
With only 70 days at your disposal, discipline is key. Stick to your study plan religiously, avoid distractions, and maintain a consistent study routine. It’s easy to get overwhelmed, but staying positive and confident in your abilities is essential. Utilize recommended books for the CA exam
to ensure you cover all necessary material. Take short breaks to recharge, but ensure they don't derail your focus.
6. Revise Regularly
Revision is critical in the final weeks leading up to the CA entrance exam. Make sure you revisit important topics from your CA entrance exam books multiple times and practice recalling information without looking at your notes. Summarize key points from these books and create quick reference sheets for last-minute revision.
Conclusion
While 70 days is a tight timeline to prepare for CA Final Group 1 from scratch, it’s not an impossible task. Success will depend on how effectively you manage your time, the clarity of your concepts, and the amount of practice you put in. By following a disciplined approach and staying focused on your goal, you can maximize your chances of clearing the exam. Remember, perseverance and determination are just as important as your study strategy. Good luck!
#ca entrance exam books#study material for ca#scanner ca foundation books#books for ca exam#ca intermediate scanner#scanner ca intermediate books
0 notes
Text
Is 70 Days enough to Clear the CA Final Group 1 from Scratch ?

The Chartered Accountancy (CA) Final is one of the most challenging exams in the field of finance and accounting. Clearing CA Final Group 1 requires not only a solid understanding of complex concepts but also the ability to apply them in various scenarios. If you’re starting from scratch with just 70 days to prepare, the task might seem daunting, but it is not impossible. With the right strategy, focus, and discipline, you can significantly improve your chances of success. One valuable resource to consider during your preparation is using Scanner CA Final books. These books can help you identify important topics and frequently asked questions, providing a targeted approach to your study plan.
1. Understand the Syllabus and Prioritize
The first step is to thoroughly understand the syllabus for CA Final Group 1. The group covers four key subjects:
Financial Reporting
Strategic Financial Management (SFM)
Advanced Auditing and Professional Ethics
Corporate and Economic Laws
Given the vastness of the syllabus, it's essential to prioritize topics based on their weightage in the exam. Focus on high-scoring areas first, ensuring that you cover essential topics that are likely to appear in the exam. Create a study plan that allocates sufficient time to each subject, with more time dedicated to complex topics.
2. Create a Detailed Study Plan
A well-structured study plan is crucial when you have limited time. Break down the 70 days into weeks and further into days, assigning specific topics and chapters to each day. Ensure that your plan includes time for revision and practice exams. A suggested plan might look like this:
Focus: Core Subjects Overview
Day 1-2: Review Subject 1 - Read through main topics and key chapters.
Day 3-4: Practice questions from the CA Final scanner for Subject 1.
Day 5-6: Review Subject 2 - Focus on important chapters and concepts.
Day 7: Practice questions from the CA Final scanner for Subject 2.
Weeks 3-4:
Focus: Deep Dive into Subjects
Day 8-10: Study Subject 1 in detail - Major topics and past papers.
Day 11-13: Practice questions from the CA Final scanner for Subject 1.
Day 14: Revision of Subject 1.
Day 15-17: Study Subject 2 in detail - Major topics and past papers.
Day 18-20: Practice questions from the CA Final scanner for Subject 2.
Day 21: Revision of Subject 2.
Weeks 5-6:
Focus: New Subjects and Integration
Day 22-24: Study Subject 3 - Main topics and key areas.
Day 25-27: Practice questions from the CA Final scanner for Subject 3.
Day 28: Revision of Subject 3.
Day 29-31: Study Subject 4 - Major topics and focus areas.
Day 32-34: Practice questions from the CA Final scanner for Subject 4.
Day 35: Revision of Subject 4.
Weeks 7-8:
Focus: Mock Exams and Revision
Day 36-38: Take mock exams for Subjects 1 and 2.
Day 39-40: Review and analyze mock exam results for Subjects 1 and 2.
Day 41-43: Take mock exams for Subjects 3 and 4.
Day 44-45: Review and analyze mock exam results for Subjects 3 and 4.
Weeks 9-10:
Focus: Final Revision and Exam Strategy
Day 46-48: Revise all subjects with a focus on weaker areas.
Day 49-51: Final practice with CA Final scanner questions for all subjects.
Day 52-53: Take full-length mock exams and analyze results.
Day 54-56: Adjust study focus based on mock exam results.
Weeks 11-10:
Focus: Final Preparation
Day 57-59: Intensive revision of key topics and weak areas.
Day 60-62: Review important formulas, concepts, and CA Final scanner summaries.
Day 63-65: Take final mock exams to gauge preparedness.
Day 66-68: Review mock exam results and refine strategy.
Day 69-70: Relax and ensure you’re well-rested for the exam day.
3. Focus on Conceptual Clarity
Starting from scratch means you need to build your foundation quickly. Focus on understanding the concepts rather than rote memorization. CA exams test your ability to apply knowledge, so ensure that you grasp the underlying principles of each topic. Use study materials, reference books, online resources, and CA Final scanner to aid your understanding. If you come across any difficult concepts, don’t hesitate to seek help from peers, mentors, or online forums.
4. Practice, Practice, Practice
Practicing problems and case studies is crucial to reinforce your learning with the right study material for CA. Dedicate time each day to solve problems, especially in subjects like Financial Reporting and SFM. For auditing and law, practice writing answers to theoretical questions, focusing on structuring your answers clearly and concisely. Additionally, take timed mock tests using comprehensive study CA to simulate the exam environment and improve your time management skills.
5. Maintain Discipline and Stay Positive
With only 70 days at your disposal, discipline is key. Stick to your study plan religiously, avoid distractions, and maintain a consistent study routine. It’s easy to get overwhelmed, but staying positive and confident in your abilities is essential. Utilize recommended books for the CA exam
to ensure you cover all necessary material. Take short breaks to recharge, but ensure they don't derail your focus.
6. Revise Regularly
Revision is critical in the final weeks leading up to the CA entrance exam. Make sure you revisit important topics from your CA entrance exam books multiple times and practice recalling information without looking at your notes. Summarize key points from these books and create quick reference sheets for last-minute revision.
Conclusion
While 70 days is a tight timeline to prepare for CA Final Group 1 from scratch, it’s not an impossible task. Success will depend on how effectively you manage your time, the clarity of your concepts, and the amount of practice you put in. By following a disciplined approach and staying focused on your goal, you can maximize your chances of clearing the exam. Remember, perseverance and determination are just as important as your study strategy. Good luck!
#scanner ca intermediate books#books for ca exam#study material for ca#Scanner CA Final books#CA Final Scanner
0 notes
Text
How to Tackle the Most Challenging CA Final Subjects

The CA Final exams are the last hurdle in the journey to becoming a Chartered Accountant. These exams test a candidate's knowledge, analytical skills, and practical application of various accounting principles. However, some subjects pose more challenges than others. This blog will guide you on how to tackle the most challenging CA Final subjects effectively.
1. Financial Reporting (FR)
Financial Reporting is often considered one of the most challenging subjects due to its vast syllabus and the complexity of accounting standards. Here's how to tackle it:
Conceptual Clarity: Ensure that you have a strong grasp of accounting standards and concepts. Refer to Scanner CA Final Books for a comprehensive understanding.
Practice Problems: Regular practice is crucial. Solve questions from past exam papers and CA Final Scanner to familiarize yourself with the types of questions asked.
Revision Notes: Create concise notes for each standard. These notes will be handy during the revision period.
2. Strategic Financial Management (SFM)
Strategic Financial Management involves complex calculations and strategic decision-making. To master this subject:
Understand Concepts: Before jumping into problem-solving, ensure you understand the underlying financial concepts.
Formula Memorization: Create a formula sheet and revise it regularly.
Use Scanners: Utilize CA Final Books to practice a variety of problems. This will help you identify patterns and frequently asked questions.
3. Advanced Auditing and Professional Ethics (Auditing)
Auditing is another tough subject due to its theoretical nature and the need for critical thinking. To excel in Auditing:
Reading and Writing: Regularly read the study material and practice writing answers to improve retention.
Case Studies: Focus on case studies and practical questions. The CA Intermediate Scanner can be particularly helpful for this.
Ethics and Standards: Pay special attention to professional ethics and auditing standards, as these are crucial for scoring well.
4. Corporate and Economic Laws
Corporate and Economic Laws is a subject that requires detailed reading and understanding of various laws and regulations. Here’s how to handle it:
Regular Reading: Make it a habit to read the law regularly. Summarize key points in your own words.
Refer to Scanners: Use CA Entrance Exam Books to practice questions and understand the pattern of questions asked in exams.
Flowcharts and Diagrams: Create flowcharts and diagrams to remember complex legal provisions and their applications.
5. Direct Tax Laws and International Taxation
Direct Tax Laws is a vast and dynamic subject with frequent updates. To manage this subject:
Stay Updated: Regularly update yourself with the latest amendments and notifications.
Conceptual Understanding: Focus on understanding the concepts rather than rote learning.
Practice with Scanners: Use books for CA Exam to practice a wide range of questions and enhance your problem-solving skills.
6. Indirect Tax Laws
Indirect Tax Laws, including GST, can be quite challenging due to its practical application and frequent changes. To tackle this subject:
Detailed Study: Study each section of GST in detail to cover the foundational aspects.
Practical Problems: Solve practical problems from CA Foundation Scanner to build a strong base.
Regular Revision: Regularly revise the key provisions and practice writing answers to practical questions.
Conclusion
Tackling the most challenging CA Final subjects requires a strategic approach combining thorough understanding, effective time management, and consistent practice. Focus on conceptual clarity and utilize a mix of study materials, including ICAI modules, reference books, and practice manuals. Regularly solve past exam papers and take mock tests to gauge your preparation. Seek guidance from mentors and join study groups for collaborative learning. Stay organized with a well-structured study plan, prioritize difficult topics, and allocate sufficient time for revision. Maintaining a balanced routine with breaks and stress management techniques is crucial for optimal performance.
#Scanner CA Final Books#CA foundation scanner#CA intermediate scanner#CA final scanner#CA Final Books#Books for CA Exam#CA Entrance Exam books
0 notes
Text
Complete Guide to CA After 12th

It can be exciting and difficult to start your road toward becoming a Chartered Accountant (CA) as soon as you finish your 12th grade. You will find all the information you need about the CA course in this all-inclusive guide, which includes eligibility requirements, for your CA Exam preparation.
Eligibility Criteria
To pursue a CA course after 12th, you need to meet the following eligibility criteria:
Educational Qualification: You must have completed your 12th grade from a recognized board.
Minimum Marks: There is no minimum percentage required in the 12th grade to register for the CA Foundation Course.
Course Structure
The CA course is structured in three levels:
CA Foundation: This is the entry-level exam.
CA Intermediate: This level requires deeper knowledge and understanding.
CA Final: This is the last stage before you become a certified Chartered Accountant.
CA Foundation
The CA Foundation Course is the first step in the CA journey. It covers four subjects:
Principles and Practice of Accounting
Business Laws and Business Correspondence and Reporting
Business Mathematics, Logical Reasoning, and Statistics
Business Economics and Business and Commercial Knowledge
To excel in these subjects, it's crucial to refer to the right CA Foundation Books.These books provide a solid foundation and help in understanding the basic concepts.
CA Intermediate
After passing the CA Foundation, the next step is the CA Intermediate Course, which comprises two groups with four papers each:
Group I:
Accounting
Corporate and Other Laws
Cost and Management Accounting
Taxation
Group II:
Advanced Accounting
Auditing and Assurance
Enterprise Information Systems & Strategic Management
Financial Management & Economics for Finance
Using the best CA Intermediate Books is essential to grasp the complex topics covered in this level. These books not only provide in-depth knowledge but also include practical problems to enhance your understanding.
CA Final
The CA Final Course is the ultimate stage. It consists of two groups, each containing four papers:
Group I:
Financial Reporting
Strategic Financial Management
Advanced Auditing and Professional Ethics
Corporate and Economic Laws
Group II:
Strategic Cost Management and Performance Evaluation
Elective Paper (Choose one from Risk Management, Financial Services & Capital Markets, International Taxation, Economic Laws, Global Financial Reporting Standards, Multidisciplinary Case Study)
Direct Tax Laws and International Taxation
Indirect Tax Laws
To succeed in the CA Final, it’s critical to use comprehensive CA Final Books and Study Material For CA. These resources provide detailed explanations, practical problems, and case studies.
Essential Study Materials
Study Material For CA
ICAI provides official study materials for all levels. These materials are meticulously designed to cover the entire syllabus comprehensively. They are essential for understanding the core concepts and for exam preparation.
Scanner CA Books
Scanner CA Books are invaluable for exam preparation. They compile previous years’ question papers along with suggested answers. Scanners help you understand the exam pattern, important topics, and the type of questions frequently asked.
Conclusion
Becoming a Chartered Accountant after the 12th grade is a structured yet challenging journey. With the right approach, dedication, and the best study materials like CA Entrance Exam Books, you can navigate through each level successfully. Remember, consistency and hard work are the keys to achieving your goal of becoming a CA. Good luck!
#books for ca exam#scanner for ca intermediate books#ca entrance exam#ca entrance exam books#ca foundation books#ca intermediate books#study material for ca#ca final books
0 notes
Text
Best Ways to Prevent Internal Theft in Your Business

Internal theft can have significant consequences for businesses, leading to financial losses, damaged trust, and decreased morale among employees. Implementing effective measures to prevent internal theft is essential for safeguarding your business's assets and reputation. Here are some of the best ways to prevent internal theft in your business:
1. Conduct Background Checks: Start by conducting thorough background checks on all employees before hiring them, especially for positions with access to sensitive information or financial resources. Look for any red flags, such as past criminal records or discrepancies in employment history, that could indicate a potential risk for theft.
2. Implement Strict Access Controls: Limit access to sensitive areas, such as storage rooms, cash registers, and accounting systems, to authorized personnel only. Use key cards, passwords, or biometric scanners to restrict access and monitor who enters these areas. Regularly review and update access permissions to ensure they align with employees' roles and responsibilities.
3. Establish Clear Policies and Procedures: Develop comprehensive insurance and procedures outlining acceptable behavior, ethical standards, and consequences for theft or misconduct. Clearly communicate these policies to all employees during onboarding and provide regular training sessions to reinforce them. Encourage employees to report any suspicious behavior or incidents of theft promptly.
4. Implement Regular Audits and Inventory Controls: Conduct regular audits of financial records, inventory, and cash transactions to identify any discrepancies or irregularities. Use surveillance cameras and inventory tracking systems to monitor inventory movement and identify potential theft patterns. Perform surprise audits occasionally to deter employees from engaging in fraudulent activities.
5. Foster a Positive Work Environment: Cultivate a positive work culture based on trust, transparency, and open communication. Recognize and reward employees for their honesty, integrity, and contributions to the company's success. Encourage employees to take ownership of their work and provide opportunities for professional growth and advancement.
6. Lead by Example: Demonstrate ethical behavior and integrity in your own actions as a leader within the organization. Lead by example by following established policies and procedures, treating employees fairly and respectfully, and upholding high ethical standards. Set a positive tone for the workplace culture and hold yourself and others accountable for adhering to company policies.
By implementing these proactive measures, businesses can significantly reduce the risk of internal theft and create a more secure and trustworthy work environment for employees and customers alike. For more information, feel free to contact Cove today.
0 notes
Text
How to Contact a Professional Hacker

Introduction
In today's digital age, cybersecurity is of paramount importance. With the rise of cyber threats, it has become crucial for individuals and businesses to protect their sensitive information from malicious hackers. However, there may be instances when you need to contact a professional hacker for ethical reasons, such as testing the security of your systems or recovering lost data. In this article, we will explore how to contact a hacker for legitimate purposes and answer some common questions related to this topic.
What is a Professional Hacker?
A professional hacker, also known as an ethical hacker or a white-hat hacker, is an individual who possesses advanced computer skills and expertise in identifying and exploiting vulnerabilities in computer systems, networks, or applications. Unlike malicious hackers (black-hat hackers), ethical hackers use their skills for lawful and beneficial purposes, helping organizations and individuals strengthen their cybersecurity measures.
Understanding Ethical Hacking
Ethical hacking is the practice of simulating cyber-attacks on systems, networks, or applications to assess their security strengths and weaknesses. The goal of ethical hacking is to identify and rectify potential vulnerabilities before malicious hackers can exploit them. Organizations often hire ethical hackers to conduct penetration testing, vulnerability assessments, and security audits to ensure their data remains secure.
How Much Do You Pay an Ethical Hacker?
The remuneration of an ethical hacker can vary depending on factors such as experience, skill level, and the complexity of the job. Generally, ethical hackers are well-compensated for their expertise due to the critical nature of their work. They may be paid on a project basis or hired as full-time employees by cybersecurity firms or organizations with a dedicated cybersecurity team.
What Tools Do Professional Hackers Use to Hack?
Professional hackers use an array of specialized tools and software to carry out ethical hacking activities. These tools include network scanners, password crackers, vulnerability scanners, and forensic analysis tools. Each tool serves a specific purpose, enabling ethical hackers to assess and secure various aspects of a computer system.
Who Is the Highest Paid Hacker?
The world of ethical hacking is highly competitive, and some ethical hackers have gained immense recognition for their contributions to cybersecurity. The highest-paid hacker, however, is often difficult to determine as it depends on various factors such as their clientele, reputation, and the scale of their work. Many ethical hackers who work for top cybersecurity firms or collaborate with government agencies tend to command higher salaries.
Is It Possible to Trace a Hacker?
Tracing a hacker can be a challenging task, but it is not impossible. Ethical hackers, forensic experts, and law enforcement agencies use advanced techniques to trace the origins of cyber-attacks. The process involves analyzing network logs, tracking IP addresses, and studying the attack patterns to identify the hacker's location or origin. However, sophisticated hackers can employ various methods to obfuscate their tracks, making it more difficult to trace them.
How Can We Help You?
If you require the assistance of a professional hacker for ethical reasons, we offer various services to meet your needs.
Speak with Sales
Our sales team can guide you through the process of engaging an ethical hacker for security testing, vulnerability assessments, or any other cybersecurity service you require.
Report a Vulnerability
If you have identified a security vulnerability in your system or software, our ethical hackers can help you assess its impact and recommend appropriate measures to address it.
Start, Locate, or Configure a Program
Whether you need to initiate a cybersecurity program, locate vulnerabilities, or configure security settings, our team of professional hackers is equipped to assist you at every step.
Conclusion
In conclusion, contacting a professional hacker for ethical purposes is a responsible and proactive approach to strengthen your digital defenses. Ethical hackers play a vital role in safeguarding sensitive information and ensuring the resilience of computer systems. By understanding their role, the tools they use, and the services they offer, you can make informed decisions to enhance your cybersecurity posture.
FAQs
Can I hire an ethical hacker to hack into someone's personal accounts? No, hiring an ethical hacker for unauthorized activities, such as accessing someone's personal accounts without their consent, is illegal and unethical. Ethical hacking should always be conducted with proper authorization and for legitimate purposes.
Is ethical hacking legal? Yes, ethical hacking is legal when conducted with proper authorization or within the scope of a contract. Ethical hackers must abide by the law and adhere to the terms agreed upon by both parties.
Can I become an ethical hacker without a technical background? While a technical background can be beneficial, it is not a strict requirement to become an ethical hacker. With dedication, learning resources, and hands-on practice, individuals from diverse backgrounds can acquire the necessary skills to become successful ethical hackers.
How long does it take to become a proficient ethical hacker? The time it takes to become proficient in ethical hacking can vary depending on one's prior knowledge and learning pace. With consistent effort and practice, some individuals can gain proficiency within a few months, while others may take a year or more.
Is ethical hacking a promising career option? Yes, ethical hacking is a promising and in-demand career option, given the increasing need for robust cybersecurity measures. Ethical hackers are valued by organizations seeking to protect their data and infrastructure from cyber threats, making it a rewarding career choice for those interested in the field of cybersecurity.
#find a hacker#contact a hacker#finding a hacker#ethical hacking#phone hacking#phone hacking service
0 notes
Link
Scanner - Advanced Auditing and Professional Ethics (New Syllabus)

Scanner - Advanced Auditing and Professional Ethics (New Syllabus) by Pankaj Garg
Key Highlights:
Strictly as per New Syllabus of ICAI
820+ Questions and Case Studies with complete answers
Coverage of Questions from RTPs and MTPs of ICAI
Point-wise answers for easy learning
Chapter-wise marks distribution for Past Exams
Inclusion of ICAI Examiner Comments with Past Exam Questions
#Scanner - Advanced Auditing and Professional Ethics#Advanced Auditing and Professional Ethics#AdvancedAuditingAndProfessionalEthics#Scanner#ForCAFinal#QuestionsWithCompleteAnswers#PointWise#Answers#EasyLearning#ICAIExaminer#PastExamQuestions#CAFinalBooks#AcademicBooks#ProfessionalBooks#OnlineBookstore#BuyBooksOnline#CMAFinal#CAFinal
1 note
·
View note
Text
How to succeed in the CA Final Exams with the help of the right CA Final Books
If you're studying to become a certified Chartered Accountant, passing the CA Final exams is a crucial step towards success. One key element of effective studying is access to quality books and materials that can help you prepare for the rigorous exam. In this article, we'll explore some of the top recommended CA Final books that can give you an extra edge as you work to master these challenging exams.
Importance of Choosing the Right Study Materials
Choosing the right CA Final study materials is crucial for success on the CA Final exams. Quality study materials can provide you with a better grasp of concepts and topics, more examples to practise and understand, and improve your overall preparation level. Using engaging textbooks, practice manuals, revisionary material, and question banks from reputable sources are key components in securing passing marks. Remember that it's not only about putting in time and effort; using the right tools to aid your studies is just as essential.
As a CA Final student, you must prioritise selecting the right study materials to effectively prepare for the exams. Reading from high-quality textbooks and practice manuals can help you develop a deeper understanding of complex concepts, especially those that may be challenging to comprehend. Reputable sources generally offer engaging content that keeps students interested in the material, which is also essential for effective learning. Furthermore, using question banks and revisionary material from trusted experts can assist with improving your overall exam preparation level by providing examples and increasing your confidence with the topics at hand. Keep in mind that utilising superior study materials is just as crucial as dedicating sufficient time and effort to studying.
Overview of the CA Final Exam
The CA Final Exam is the last level of the Chartered Accountancy (CA) course, and is considered one of the toughest exams in India. It consists of two groups, with a total of eight papers. Group I covers financial reporting, strategic financial management, advanced auditing and professional ethics, and corporate and economic laws. Group II covers advanced management accounting, information systems control and audit, direct tax laws, and indirect tax laws. Passing both groups is necessary to become a qualified CA. The exam requires extensive knowledge on a variety of financial and taxation topics, as well as critical analysis skills to solve complex problems.
To prepare for the CA Final Exam, it is important to choose the right study materials. Many students prefer to use reference books or study materials provided by recognized coaching institutes, as these tend to cover all the important topics in detail. Some of the most popular CA Final books include Scanner for Financial Reporting, Advanced Auditing and Professional Ethics by Shuchita Prakashan, Munish Bhandari's Handbook on Corporate and Allied Laws, and Tulsian's Advanced Taxation. It is also a good idea to attempt mock test papers and previous year question papers to get an idea of the exam pattern and improve time management skills. While studying for this exam may seem daunting, with proper planning and dedication, individuals can successfully pass this critical milestone towards becoming a Chartered Accountant.
How to Choose the Best Study Material for You
Choosing the right study material is crucial when preparing for the CA Final exams. With so many options available, it can be overwhelming to decide which ones to use. To start, consider your learning style - do you prefer visual aids or extensive problem-solving? Research and compare different books, guides, and online resources that align with your preferred learning method. Additionally, seek out reviews or recommendations from other students who have successfully passed the CA Final exams. Keep in mind that quality study materials may be an investment, but they can make all the difference in your success on exam day.
When selecting study materials for the CA Final exams, it’s important to find ones that fit your individual preferences and needs. Some students prefer textbooks with detailed explanations and examples, while others may find video lectures more effective at retaining information. Consider which format you excel in and try to find study material that matches those strengths. It may also be helpful to look for review books or online resources that offer practice problems and mock exams, allowing you to test your knowledge and evaluate your progress leading up to exam day. Remember that investing time and money in quality study materials can pay off when it is time to take the exam.
Tips for Studying Effectively with CA Final Books
Proper utilisation of CA Final books and study materials can significantly improve your chances of success in the exam. Firstly, create a study plan and follow it consistently. Allocate proper time for each subject and chapter according to your strengths and weaknesses. Limit your distractions during study time and focus solely on understanding the concepts. Use colours, markers, or sticky notes to highlight important information for easy recall later on. Make sure to also take frequent breaks to prevent burnout and maintain productivity. Lastly, practise previous years’ question papers regularly to identify areas where you need improvement and get familiar with the exam pattern. Remember - studying effectively is about quality over quantity!
Studying for the CA Final exam can be daunting, but with the right approach and tools, it doesn’t have to be overwhelming. The key to success is the proper utilisation of CA Final books and study materials. Creating a study plan and following it consistently is essential. Allocate proper time for each subject and chapter according to your strengths and weaknesses. This will help you stay on track and ensure that you cover all the necessary topics before the exam.
Conclusion
In conclusion, passing the CA Final exams requires dedication, hard work, and access to quality study materials. By following a structured study plan, utilising recommended books and materials, avoiding distractions during study time, and engaging in regular practice with past papers, you can set yourself up for success. Remember that success is not just about putting in long hours; it’s about studying effectively and focusing on quality over quantity. With these tips and tricks in mind, you can increase your chances of passing the CA Final exams with flying colours!
Choosing the right CA Final study materials is critical to success in any exam, and this also rings true for the CA Final exams. Several books are available in the market to help students prepare for these exams, offering a range of topics and levels of detail. While it can be overwhelming to choose from among so many options, it’s advisable to stick with respected authors and publications that successful CA Final candidates have recommended. With a solid understanding of the topics covered in these books, coupled with a structured study plan and plenty of practice, you’ll be well on your way to passing the CA Final exams with flying colours!
#caexambook
#caentranceexambook
#cafoundationexambook
0 notes
Text
Ca Entrance Exam Books | CUET Books | CS | CMA | Scanneradda
Scanner is one of the most trusted brands in India for publishing competitive books like CA, CUET, and CMA. We are glad to say that Scanner publishes more than 200 books for CA, CMA, CUET, CS and many more other competitive exams. Now let’s have a look on some of the best Scanner Entrance Exam Books: CA: In India, the Chartered Accountant (CA) entrance exam is conducted by the Institute of Chartered Accountants of India (ICAI). The CA exam is a professional certification for accountants in India, and employers highly regard it in the country. To become a Chartered Accountant in India, students must first qualify for the three levels of the Chartered Accountancy Exam and they can study from CA Entrance Exam Books for that. The three levels are CA Foundation, CA Intermediate and CA Final. CA Foundation Exam:The Chartered Accountant (CA) Foundation Exam is the first level of the CA exam in India, which is conducted by the Institute of Chartered Accountants of India (ICAI). The CA exam is a professional certification for accountants in India, and employers highly regard it in the country. It is an objective-type test that covers the fundamentals of accounting, mercantile laws, general economics, and quantitative aptitude. CA Foundation exam is designed for candidates who have completed their 10+2 education or its equivalent. Students can go through our CA Foundation Books to get the best results in their CA Foundation Entrance Exam. CA Intermediate Exam: The Chartered Accountant (CA) Intermediate Exam, is the second level of the CA exam in India, which is conducted by the Institute of Chartered Accountants of India (ICAI). The CA Intermediate Exam consists of two groups, each containing four papers. The exam covers subjects such as accounting, law, cost accounting and financial management and taxation. Our CA Intermediate Books are available online and offline as well. CA Final Exam: CA Final Exam is the third and final level of the CA exam in India, conducted by the Institute of Chartered Accountants of India (ICAI). The CA Final Exam consists of two groups, each containing four papers. The exam covers advanced subjects such as financial reporting, strategic financial management, advanced auditing and professional ethics, and corporate and allied laws. Students can go to our website and check CA Final Books for all subjects. Candidates who have passed the CA Intermediate Exam are eligible to give the CA Final Exam and have completed the required number of hours of practical training, known as "Articleship."
0 notes
Text
CA Final Group 1 Books for November 2022 Exam!!
“The harder you work the better you get”
It is a matter of pride to be a Chartered Accountant in India. There are three stages of the exam: CA Foundation, CA Intermediate, and CA Final.
CA Final is the final level of the course. One has to clear this level to become a chartered accountant. Two groups—Group I and Group II—make up the final course. Four core papers make up Group I, whereas three core papers and one elective paper make up Group II. Before taking the CA Final exams, students must select one of the six Elective Paper alternatives. Any candidate who wants to succeed in the exam must go through the CA Final Group 1 books .
Before taking the CA final test, he or she must sign up for a 3-year articleship training programme under a licenced Chartered Accountant. The student must additionally complete a four-week Advanced Integrated Course in Information Technology and Soft Skills during their final two years of training (AICITSS). In the final six months of the articleship training, the CA final test may be taken. A student can enroll as a member of ICAI and receive the designation of CA after completing the articled training and passing both Final Course groups with a minimum of 40% in each subject and 50% overall.
There are many good CA Final Books that any diligent aspirants can prefer. There are four papers in the group 1 exam and their books are listed below respectively:
Green Edition Scanner ( Study Material Based Attempt-Wise Questions with Suggested Answers and Much More)
Applicable For November 2022 Attempt (As per latest updated syllabus of ICAI)
CA Final Group 1: Paper 1- Financial Reporting
Features:
Graph showing marks, categories wise in each chapter in various attempts
Examination Trends Analysis- 5 Attempts
Analytical Classification of every chapter
Marks of each question/part question
List of similarly asked questions
Contents establishing correlation between study material and Chapters in Scanner
Complete Questions with solutions
Complete Test Series

Green Edition Scanner ( Study Material Based Attempt-Wise Questions with Suggested Answers and Much More)
Applicable For November 2022 Attempt (As per latest updated syllabus of ICAI)
CA Final Group 1: Paper 2- Strategic Financial Management
Features:
Graph showing marks, categories wise in each chapter in various attempts
Examination Trends Analysis- 5 Attempts
Analytical Classification of every chapter
Marks of each question/part question
List of similarly asked questions
Contents establishing correlation between study material and Chapters in Scanner
Complete Questions with solutions
Complete Test Series

Green Edition Scanner ( Study Material Based Attempt-Wise Questions with Suggested Answers and Much More)
Applicable For November 2022 Attempt (As per latest updated syllabus of ICAI)
CA Final Group 1: Paper 3- Advanced Auditing & Professional Ethics
Features:
Graph showing marks, categories wise in each chapter in various attempts
Examination Trends Analysis- 5 Attempts
Analytical Classification of every chapter
Marks of each question/part question
List of similarly asked questions
Contents establishing correlation between study material and Chapters in Scanner
Complete Questions with solutions
Complete Test Series

Green Edition Scanner ( Study Material Based Attempt-Wise Questions with Suggested Answers and Much More)
Applicable For November 2022 Attempt (As per latest updated syllabus of ICAI)
CA Final Group 1: Paper 4- Corporate and Economic Laws
Features:
Graph showing marks, categories wise in each chapter in various attempts
Examination Trends Analysis- 5 Attempts
Analytical Classification of every chapter
Marks of each question/part question
List of similarly asked questions
Contents establishing correlation between study material and Chapters in Scanner
Complete Questions with solutions
Complete Test Series

Conclusion:
Nowadays Chartered accountancy is one of the most popular career choices in India after 12th. The professional accounting organisation in India, The Institute of Chartered Accountants of India, is in-charge of managing the CA test programme. The CA test has three levels, and passing each level is required to become a CA.
The first is the CA Foundation, then CA Intermediate, which has two levels and the last is the CA Final. It has two levels as well. One must be conversant with the necessary material and the ICAI-required exam format in order to pass this exam. There are four papers in the CA Final group 1 exam. One can qualify it with the help of CA Entrance Exam books .These books are suggested for anyone preparing for the CA Final Group 1 Exam under ICAI standards. A hardworking candidate always needs the best to read and understand. These books are quite easy to understand and very authentic.
All the very best for the CA Final Exam!!!
0 notes
Text
15 Best Hacking Apps For Android - Top Hacking Apps For Android | Convert Your Android To A Hacking Machine

Disclaimer
Hacking Apps or any hacking related content are not promoted by us directly or indirectly for illegal purposes or misuse. The content of the post is only for educational purposes. We only want you guys to get aware of these concepts around the world, not for misusage.
Introduction
Android is the world's most popular operating system and 99% of peoples using android services including Hackers, Pentesters, and lot more. In this tutorial, I will give you an android hacking application that turns your device into a hacking machine. Few of them are work in the rooted phone and others are in the non-rooted device. Penetration testing and Hacking are made for the computer but by using this application you can perform penetration testing in your android phone and hacking too.
Best 15 Android Hacking Apps

SpoofApp

SpoofApp is a Caller ID Spoofing, Voice Changing and Call Recording mobile app for your iPhone, BlackBerry, and Android phone. It’s a decent mobile app to help protect your privacy on the phone. However, it has been banned from the Play Store for allegedly conflicting with The Truth in Caller ID Act of 2009. Download APK Now Andosid

The DOS tool for Android Phones allows security professionals to simulate a DOS attack (an HTTP post flood attack to be exact) and of course a DDoS on a web server, from mobile phones. Download APK Now Faceniff

It allows you to sniff and intercept web session profiles over the WiFi that your mobile is connected to. It is possible to hijack sessions only when WiFi is not using EAP, but it should work over any private networks. Download APK Now Nmapper

(Network Mapper) is a security scanner originally written by Gordon Lyon used to discover hosts and services on a computer network, thus creating a “map” of the network. To accomplish its goal, Nmapper sends specially crafted packets to the target host and then analyses the responses. Download APK Now Zanti

ZANTI is a comprehensive network diagnostics toolkit that enables complex audits and penetration tests at the push of a button. It provides cloud-based reporting that walks you through simple guidelines to ensure network safety. Download APK Now SSHDroid

SSHDroid is an SSH server implementation for Android. This application will let you connect to your device from a PC and execute commands (like “terminal” and “ADB shell”) or edit files (through SFTP, WinSCP, Cyberduck, etc). Download APK Now WiFi Analyser

Turns your android phone into a Wi-Fi analyzer. Shows the Wi-Fi channels around you. It helps you to find a less crowded channel for your wireless router. Download APK Now You May Also Check Out This Post: What is meant by Hacking ? What is Hacker - 3 Types of Hacker, detailed overview for Beginners Network Discovery

Discover hosts and scan their ports in your Wifi network. A great tool for testing your network security. Download APK Now ConnectBot

ConnectBot is a powerful open-source Secure Shell (SSH) client. It can manage simultaneous SSH sessions, create secure tunnels, and copy/paste between other applications. This client allows you to connect to Secure Shell servers that typically run on UNIX-based servers. Download APK Now Dsploit

Android network analysis and penetration suite offering the most complete and advanced professional toolkit to perform network security assessments on a mobile device. Download APK Now Hackode

The hacker’s Toolbox is an application for penetration tester, Ethical hackers, IT administrator, and Cybersecurity professional to perform different tasks like reconnaissance, scanning performing exploits, etc. Download APK Now Androrat

Remote Administration Tool for Android. Androrat is a client/server application developed in Java Android for the client-side and in Java/Swing for the Server. Download APK Now APKInspector

APKinspector is a powerful GUI tool for analysts to analyze Android applications. The goal of this project is to aide analysts and reverse engineers to visualize compiled Android packages and their corresponding DEX code. Download APK Now Burp Suite

Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities. Droid Sheep

DroidSheep can be easily used by anybody who has an Android device and only the provider of the web service can protect the users. So Anybody can test the security of his account by himself and can decide whether to keep on using the web service. Download APK Now
How To Use These Apps
These are the top Android Hacking Apps but the question is how to use them? Most of the apps work in the non-rooted phone and others are work in rooted phones. Still, we are working on a full-fledged video, in which we will explain all of the above android hacking apps in detail. As soon as the video gets completed we will post it over here. Till then enjoy the post.
Conclusion
It's pretty easy nowadays to convert your current android smartphone into a portable hacking machine. So we have disclosed some of the android hacking apps that might help you, people, to learn the basics of hacking. For the latest tech-related updates, follow TechAliens on Twitter, Facebook, and our Instagram page. Hopefully, the next update will be more exciting. Read the full article
0 notes
Text
Vulnerability Assessment With Nessus Home - Part 1
Part One of a Two-Part series
Introduction
If you work in the field of Information Technology, you have probably heard of Vulnerability Assessment (VA). VA is a process of identifying security vulnerabilities in a system. It is recommended that you conduct a VA against your organization's network every quarter, and if your organization follows certain policy and standards, such as PCI DSS, VA is a requirement. However, organizations should not be the only ones conducting VAs against their network; average home users should also conduct vulnerability assessment against their network. In this blog, I will guide you through the process of performing a VA against your network using Nessus Home.
What Is Nessus?
Nessus is a vulnerability scanner developed by Tenable and there are two versions of it: Nessus Home and Nessus Professional. Basically, the major differences between the two are that you can only scan up to 16 IP addresses per scanner, and you won’t be able to perform compliance checks and content audits with Nessus Home. Most average users will not have more than 16 systems, and there is no need to run compliance checks or content audits on your home systems.
Vulnerability assessments are typically done by running authenticated scans, which means the scanner will authenticate against the systems its scanning. The scan will then come back with much more detailed information about a system. With Nessus, you can perform authenticated scans against different operating systems such as Windows, Linux, and Mac OS via different methods such as SMB, SSH, SNMP, Telnet, etc.
Installing and Setting Up Nessus
For demonstration purposes, I will walk you through the process of installing and setting up Nessus and performing an authenticated scan against Windows 10.
To use Nessus, you need to obtain an activation code on Tenable's website, which is (https://www.tenable.com/products/nessus-home). Use your name and email address, and the code will be sent to your email.

Registering for an Activation Code

Emailed Activation Code
Once you receive your code, go to this page (https://www.tenable.com/downloads/nessus) and download Nessus. Choose the appropriate package. In my case, I'm going to download the package for Windows 10 (64-bit).

Downloading Nessus
Install Nessus. During the installation, Nessus will install a tool called WinPcap, which will allow Nessus to capture live network traffic. Check Automatically start the WinPcap driver at boot time option and install WinPcap.

Nessus installer

Nessus Setup Wizard

Select the start the WinPcap driver at boot option
Nessus runs on TCP Port 8834 on your local machine. To access the web console, open a browser and navigate to https://localhost:8834. Once the installation is complete, your default browser will open, and it will ask you to connect via SSL. Click Connect via SSL and your browser will display a warning saying that the certificate cannot be trusted. This is normal since Nessus uses a self-signed certificate. Proceed by clicking Go on to the webpage (Different browsers will have different wording, but they will give you an option to accept the risk and proceed).

Welcome to Nessus!

Certificate Warning, Select Go on to the webpage
Create your account. Make sure you use a strong password! Once you create an account, you will be asked to enter your activation code that was sent to your email. After you enter the code and click Continue, Nessus will start to set up the plugins and other files that it needs to perform a scan. This process will take a while so take a break and come back in an hour or so. After the setup is complete, you’ll be greeted by the web console.
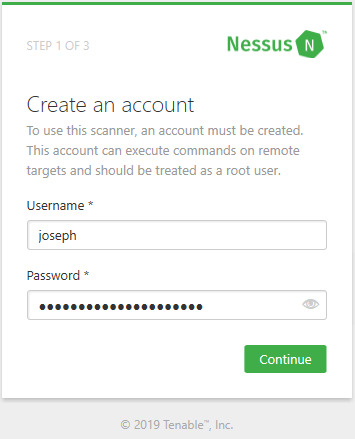
Creating a Nessus account

Registering the scanner

Initializing Nessus

Nessus using Localhost and Port 8834
You can create a new scan by clicking New Scan on the upper right corner. You’ll see that certain templates aren’t available until you upgrade to Nessus Professional, but you still have access to templates such as Advanced Scan, Basic Network Scan, Host Discovery, Malware Scan, Spectre and Meltdown, and WannaCry Ransomware. It is straight forward to use these templates; you give it the IP addresses you want to scan, and credentials if you want to perform the recommended authenticated scan. Setting up a scan and properly performing an authenticated scan will be covered in Part II.

Listing of Scan Templates for Nessus
Useful Tips and Tricks
Now, I would like to share how some tips and tricks that I’ve acquired using Nessus for about a year. This is a personal preference, so you do not have to follow my suggestions. It will involve tweaking some settings and if you don’t want to, that’s fine. It won’t affect the performance of the Nessus scans.
By default, Nessus will automatically start and run in the background on boot on Windows. I don’t like how it’s running when I don’t need it (On Linux, Nessus does not start automatically by default and you need to start it manually, which is what I prefer!). In order to prevent Nessus starting on boot, open Services and find Tenable Nessus on the list. You will see that it is set to Automatic. To change this, right click on it and set Startup type to Manual. Nessus won’t start on boot anymore and you’ll have to manually start/stop it. To do so, open a Command Promptor PowerShell and type net stop/start “Tenable Nessus”.

Windows Services

Configuring Nessus to manual start using Windows Services

Net Start/Stop of Nessus
According to Tenable, they release more than 100 plugins weekly. This means that you will have to update Nessus frequently in order to use those new plugins. If there is an update available, Nessus will let you know when you log into the GUI. However, I prefer updating it from the command line. To do this, open a Command Prompt or PowerShell as an administrator and navigate to C:\Program Files\Tenable\Nessus directory. Once you are there, type .\nessuscli.exe update –all (.\ is not needed if you are doing this from the Command Prompt). Nessus will download the updates from nessus.org. Make sure to restart Nessus after you update it.
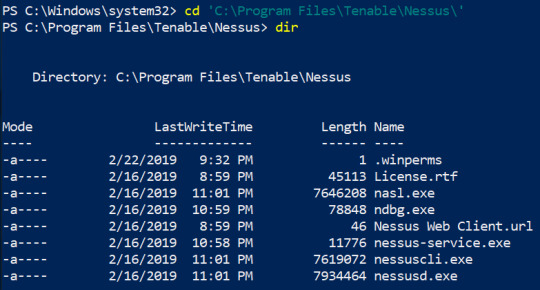
Nessus Directory

Nessus Update from command line
Lastly, Nessus rates the findings with its severity levels: Critical, High, Medium, Low, and Informational. Prior to Nessus v8, it listed the findings by severity but now it “groups” certain findings. I find this feature not very helpful and annoying, so I disabled it right away. To do so, click on Settings next to Scans, go to Advanced, and type groups. This will return two settings: Use Mixed Vulnerability Groups and Use Vulnerability Groups. Set the values to No. You are welcome.

Nessus Groups

Nessus Advanced Settings
Conclusion
Nessus Home is a great vulnerability scanner that everyone should be using, not just cybersecurity professionals. In this blog, I’ve demonstrated installing and setting up Nessus on Windows. In Part II, I will demonstrate how to set up an authenticated scan and tweak some settings on Windows to allow Nessus to perform an authenticated scan.

Author Bio
Joseph Choi is a Cybersecurity Analyst with Alpine Security. He holds several security-related certifications, including Certified Ethical Hacker (CEH), EC-Council Certified Security Analyst (ECSA), CyberSec First Responder (CFR), Security+, and Network+. Joseph is a graduate from Truman State University with a B.S. in Business Administration.
Joseph's cybersecurity experience began at Alpine and includes penetration tests, vulnerability assessments, and wireless penetration tests. He was born and raised in South Korea until the age of 10 when he moved to Mexico. It wasn't until 2007 that his family moved to the States where he completed his high school and college education. He is a fan of Mr. Robot, and in his spare time he enjoys spending time with his girlfriend, taking long walks around the park, and going to the gym.
0 notes
Text
Top 20 hacking tools for Windows, Linux and Mac OS X [2020 Edition]
New Post has been published on https://techneptune.com/windows/top-20-hacking-tools-for-windows-linux-and-mac-os-x-2020-edition/
Top 20 hacking tools for Windows, Linux and Mac OS X [2020 Edition]
Top 20 hacking tools for Windows, Linux and Mac OS X [2020 Edition]
Hacking is of two types: ethical and unethical. Hackers used unethical hacking techniques to make money quickly. But, there are many users who want to learn how to hack the right way. Security research, WiFi protocols, etc. are included in the range of ethical hacking.
So if you are willing to learn ethical hacking then you need to use some tools. These tools would help you facilitate many complicated things in the field of security. Here we have compiled a list of the best hacking tools with their descriptions and features.
Top 20 hacking tools for Windows, Linux and Mac OS X
Therefore, in this article, we are going to share a list of the best hacking tools for Windows, Linux and Mac OS X. Most of the tools listed in the article were available for free. We have written the article for educational purposes; please do not use these tools for evil purposes.
1. Metasploit
Metasploit
Instead of calling Metasploit a collection of exploit tools, I’ll call it an infrastructure that you can use to create your custom tools. This free tool is one of the most frequent cybersecurity tools that allow you to locate vulnerabilities on different platforms. Metasploit is supported by more than 200,000 users and collaborators who help you obtain information and discover the weaknesses of your system.
2. Nmap
Nmap
Well Nmap is available for all major platforms including Windows, Linux and OS X. I think you have all heard of it, Nmap (Network Mapper) is a free open source utility for network scanning or security audit. It was designed to scan large networks, and works well against single hosts. It can be used to discover computers and services on a computer network, thereby creating a “map” of the network.
3. Acunetix WVS
Acunetix WVS
It is available for Windows XP and higher. Acunetix is a web vulnerability scanner (WVS) that scans and discovers flaws on a website that could prove fatal. This multithreaded tool crawls a website and discovers malicious cross-site scripts, SQL injection, and other vulnerabilities. This quick and easy-to-use tool scans WordPress websites for over 1200 WordPress vulnerabilities.
4. Wireshark
Wireshark
This free and open source tool was originally called Ethereal. Wireshark also comes in a command line version called TShark. This GTK + based network protocol scanner runs easily on Linux, Windows, and OS X. Wireshark is a GTK + based network protocol scanner or sniffer, allowing you to interactively capture and explore the content of frameworks. net. The goal of the project is to create a commercial grade parser for Unix and provide the missing Wireshark features in closed source crawlers.
5. oclHashcat
oclHashcat
This useful hacking tool can be downloaded in different versions for Linux, OSX and Windows. If password cracking is something you do on a daily basis, you may be familiar with the free Hashcat password cracking tool. While Hashcat is a CPU-based password cracking tool, oclHashcat is its advanced version that uses the power of its GPU. You can also take the tool as a WiFi password cracker.
oclHashcat calls itself the world’s password cracking tool with the world’s first and only GPGPU-based engine. To use the tool, NVIDIA users require ForceWare 346.59 or later, and AMD users require Catalyst 15.7 or later.
6. Nessus Vulnerability Scanner
Nessus Vulnerability Scanner
It is compatible with a variety of platforms, including Windows 7 and 8, Mac OS X, and popular Linux distributions such as Debian, Ubuntu, Kali Linux, etc. This free 2020 hacking tool works with the help of a client-server framework. Developed by Tenable Network Security, the tool is one of the most popular vulnerability scanners we have. Nessus has different purposes for different types of users: Nessus Home, Nessus Professional, Nessus Manager, and Nessus Cloud.
7. Maltego
Maltego
This tool is available for Windows, Mac and Linux. Maltego is an open source forensic platform that offers rigorous mining and information gathering to paint a picture of the cyber threats around you. Maltego stands out for showing the complexity and severity of failure points in its infrastructure and the surrounding environment.
8. Social Engineer Toolkit
Social Engineer Toolkit
In addition to Linux, the Social-Engineer Toolkit is partially compatible with Mac OS X and Windows. Also featured in Mr. Robot, the TrustedSec Social Engineer Toolkit is an advanced framework for simulating multiple types of social engineering attacks, such as credentialing, phishing attacks, and more.
9. Nessus Remote Security Scanner
Nessus Remote Security Scanner
It was recently closed source, but is still essentially free. It works with a client-server framework. Nessus is the most popular Remote Security Scanner vulnerability scanner used in over 75,000 organizations worldwide. Many of the world’s largest organizations are achieving significant cost savings by using Nessus to audit business-critical devices and business applications.
10. Kismet
Kismet
It is an 802.11 layer2 wireless network detector, sniffer and intrusion detection system. Kismet will work with any kismet wireless card that supports raw monitoring mode (rfmon) and can detect 802.11b, 802.11a, and 802.11g traffic. A good wireless tool as long as your card supports rfmon.
11. John The Ripper
John The Ripper
It is free and open source software, distributed mainly in the form of source code. It is the software tool to crack passwords. It is one of the most popular password breaking and testing programs, as it combines multiple password crackers in one package, automatically detects password hash types, and includes a customizable cracker.
12. Unicornscan
Unicornscan
Well, Unicornscan is an attempt by a user distributed TCP / IP stack for information gathering and mapping. Its objective is to provide a researcher with a superior interface to introduce a stimulus and measure a response from a device or network with TCP / IP. Some of its features include stateless asynchronous TCP scanning with all variations of TCP flags, stateless asynchronous TCP banner capture and active / passive remote operating system, application and component identification through response analysis.
13. Netsparker
Netsparker
It is an easy-to-use web application security scanner that uses advanced evidence-based vulnerability scanning technology and has built-in penetration testing and reporting tools. Netsparker automatically exploits the identified vulnerabilities in a secure, read-only manner and also produces a proof of exploitation.
14. Burp Suite
Burp Suite
Well, Burp Suite is an integrated platform for testing web application security. It is also one of the best hacker programs available on the internet right now. Its various tools work perfectly to support the entire testing process, from initial mapping and analysis of an application’s attack surface to finding and exploiting security vulnerabilities.
15. Superscan 4
Superscan 4
Well, this is another popular hacking software for PC that is used to scan ports in Windows. This is a free connection based port scanning tool that is designed to detect open TCP and UDP ports on a destination computer. In simple words, you can take SuperScan is a powerful TCP port scanner, pinger and resolver.
16. Aircrack
Aircrack
It is the best WiFi hacker for Windows 10, consisting of a detector, a packet tracker, a WEP and WPA / WPA2-PSK cracker and a scan tool. In AirCrack you will find many tools that can be used for tasks such as monitoring, attack, leak test and cracks. Without a doubt, this is one of the best networking tools you can use. Therefore, it is one of the best WiFi hacking tools.
17. w3af
w3af
If you are looking for a free and open source web application security scanner then w3af is the best for you. Hackers and security researchers widely use the tool. The w3aF or web application audit and attack framework is used to obtain security vulnerability information that can be used more in penetration testing jobs.
18. OWASP Zed
OWASP Zed
Well, the Zed Attack Proxy is one of the best and most popular OWASP projects that has reached the new height. OWASP Zed is a pencil hacking and testing tool that is very efficient and easy to use. OWASP Zed provides many tools and resources that enable security researchers to find security holes and vulnerabilities.
19. Nikto Website Vulnerability Scanner
Nikto website vulnerability scanner
It is widely used by pentesters. Nikto is an open source web server scanner that is capable of scanning and detecting vulnerabilities on any web server. The tool also searches for outdated versions of more than 1,300 servers. Not only that, but the Nikto website vulnerability scanner also looks for server configuration issues.
20. SuperScan
SuperScan
Es uno de los mejores y gratuitos programas de escaneo de puertos basados en conexión disponibles para el sistema operativo Windows. La herramienta es lo suficientemente capaz de detectar los puertos TCP y UDP que están abiertos en la computadora de destino. Además de eso, SuperScan también se puede utilizar para ejecutar consultas básicas como whois, traceroute, ping, etc. Por lo tanto, SuperScan es otra mejor herramienta de piratería que puede considerar.
¿Puedo hackear cuentas en línea con estas herramientas?
Estas herramientas estaban destinadas a fines de seguridad y se pueden utilizar para encontrar lagunas. No promovemos el pirateo de cuentas y puede provocar problemas legales.
¿Son seguras estas herramientas?
Si está descargando las herramientas de fuentes confiables, entonces estaría del lado seguro.
¿Puedo escanear mi red WiFi con estas herramientas?
Para escanear la red WiFi, uno necesita usar un escáner WiFi. Hay pocos escáneres WiFi enumerados en el artículo que le proporcionarían detalles completos sobre la red.
Entonces, arriba están las mejores herramientas de piratería ética para PC. Si te gusta esta publicación, no olvides compartirla con tus amigos. Si tiene algún problema, no dude en hablar con nosotros en la sección de comentarios a continuación.
0 notes
Text
Kali Linux – Assuring Security by Penetration Testing
Kali Linux – Assuring Security by Penetration Testing: Master the art of penetration testing with Kali Linux Download Introduction Kali Linux is a penetration testing and security auditing platform with advanced tools to identify, detect, and exploit any vulnerabilities uncovered in the target network environment. Applying an appropriate testing methodology equipped with well-defined business objectives and a scheduled test plan will result in the robust penetration testing of your network. Kali Linux – Assuring Security by Penetration Testing is a fully focused, structured book that provides guidance on developing practical penetration testing skills by demonstrating the cutting-edge hacker tools and techniques in a coherent step-by-step strategy. It offers all the essential lab preparation and testing procedures to reflect realworld attack scenarios from your business perspective in today's digital age. This book reveals the industry's best approach for logical and systematic penetration testing process. This book starts with lab preparation and testing procedures, explaining the basic installation and configuration setup, discussing different types of penetration testing, uncovering open security testing methodologies, and proposing the Kali Linux specific testing process. We shall discuss a number of security assessment tools necessary to conduct penetration testing in their respective categories (target scoping, information gathering, discovery, enumeration, vulnerability mapping, social engineering, exploitation, privilege escalation, maintaining access, and reporting), following the formal testing methodology. Each of these tools is illustrated with real-world examples to highlight their practical usage and proven configuration techniques. We have also provided extra weaponry treasures and key resources that may be crucial to any professional penetration testers. This book will serve as a single professional, practical, and expert guide to develop necessary penetration testing skills from scratch. You will be trained to make the best use of Kali Linux either in a real-world environment or in an experimental test bed. What this book covers Chapter 1, Beginning with Kali Linux, introduces you to Kali Linux, a Live DVD Linux distribution specially developed to help in the penetration testing process. You will learn a brief history of Kali Linux and several categories of tools that Kali Linux has. Next, you will also learn how to get, use, configure, and update Kali Linux as well as how to configure several important network services (HTTP, MySQL, and SSH) in Kali Linux. You will also learn how to install and configure a vulnerable virtual machine image for your testing environment and several ways that can be used to install additional tools in Kali Linux. Chapter 2, Penetration Testing Methodology, discusses the basic concepts, rules, practices, methods, and procedures that constitute a defined process for a penetration testing program. You will learn about making a clear distinction between two well-known types of penetration testing, black box and white box. The differences between vulnerability assessment and penetration testing will also be analyzed. You will also learn about several security testing methodologies and their core business functions, features, and benefits. These include OSSTMM, ISSAF, OWASP, and WASC-TC. Thereafter, you will learn about a general penetration Kali Linux testing process incorporated with 10 consecutive steps to conduct a penetration testing assignment from an ethical standpoint. Chapter 3, Target Scoping, covers a scope process to provide necessary guidelines on normalizing the test requirements. A scope process will introduce and describe each factor that builds a practical roadmap towards test execution. This process integrates several key elements, such as gathering client requirements, preparing a test plan, profiling test boundaries, defining business objectives, and project management and scheduling. You will learn to acquire and manage the information about the target's test environment. Chapter 4, Information Gathering, introduces you to the information gathering phase. You will learn how to use public resources to collect information about the target environment. Next, you learn how to analyze DNS information and collect network routing information. Finally, you will learn how to utilize search engines to get information of the target domain, e-mail addresses, and document metadata from the target environment. Chapter 5, Target Discovery, introduces you to the target discovery process. You will learn the purpose of target discovery and the tools that can be used to identify target machines. At the end of this chapter, you will also learn about the tools that can be used to perform OS fingerprinting on the target machines. Chapter 6, Enumerating Target, introduces you to target enumeration and its purpose. You will learn a brief theory on port scanning and several tools that can be used to do port scanning. You will also learn about various options available to be used by the Nmap port scanner tool. Also, you will learn about how to find SMB, SNMP, and VPN available in the target machine in the last part of the chapter. Chapter 7, Vulnerability Mapping, discusses two generic types of vulnerabilities: local and remote. You will get insights on vulnerability taxonomy, pointing to industry standards that can be used to classify any vulnerability according to its unifying commonality pattern. Additionally, you will learn a number of security tools that can assist you in finding and analyzing the security vulnerabilities present in a target environment. These include OpenVAS, Cisco, Fuzzing, SMB, SNMP, and web application analysis tools. Chapter 8, Social Engineering, covers some core principles and practices adopted by professional social engineers to manipulate humans into divulging information or performing an act. You will learn some of the basic psychological principles that formulate the goals and vision of a social engineer. You will also learn about the attack process and methods of social engineering followed by real-world examples. In the end, you will be given hands-on exercise using the social engineering tools that can assist you in evaluating the target's human infrastructure. Chapter 9, Target Exploitation, highlights the practices and tools that can be used to conduct a real-world exploitation. The chapter will explain what areas of vulnerability research are crucial in order to understand, examine, and test the vulnerability. Additionally, it will also point out several exploit repositories that should keep you informed about the publicly available exploits and when to use them. You will also learn to use one of the infamous exploitation toolkits from a target evaluation perspective. Moreover, you will discover the steps for writing a simple exploit module for the Metasploit framework. Chapter 10, Privilege Escalation, introduces you to privilege escalation as well as network sniffing and spoofing. You will learn how to escalate your gained privilege using a local exploit. You will also learn the tools required to attack a password via the offline or online technique. You will also learn about several tools that can be used to spoof the network traffic. In the last part of this chapter, you will discover several tools that can be used to do a network sniffing attack. Chapter 11, Maintaining Access, introduces you to the operating system and web backdoors. You will learn about several backdoors that are available and how to use them. You will also learn about several network tunneling tools that can be used to create covert communication between the attacker and the victim machine. Chapter 12, Documentation and Reporting, covers the penetration testing directives for documentation, report preparation, and presentation. These directives draw a systematic, structured, and consistent way to develop the test report. Furthermore, you will learn about the process of results verification, types of reports, presentation guidelines, and the post-testing procedures. Appendix A, Supplementary Tools, describes several additional tools that can be used for the penetration testing job. Appendix B, Key Resources, explains various key resources to help you become more skillful in the penetration testing field.. What you need for this book All the necessary requirements for the installation, configuration, and use of Kali Linux have been discussed in Chapter 1, Beginning with Kali Linux. Who this book is for If you are an IT security professional or a network administrator who has a basic knowledge of Unix/Linux operating systems, including an awareness of information security factors, and you want to use Kali Linux for penetration testing, this book is for you Via TimoBook
0 notes
Link
Advanced Auditing & Professional Ethics - CA Final (New Syllabus)

Advanced Auditing & Professional Ethics CA-Final (New Syllabus) by Pankaj Garg
Key Highlights:
Strictly as per New Syllabus of ICAI
Coverage of Companies (Amendment) Act 2017
Coverage of Revised SA 299 and Revised SA 720
850+Questions and Case Studies with Hints for self practice (For detailed answer, refer 2nd edition of scanner for new syllabus)
Questions are covered alongwith every topic for easy understanding
Coverage of All Past Exam Questions till May 2018 Exam
Coverage of Questions from RTPs and MTPs of ICAI
Chapter-wise marks distribution for Past Exams for each Chapter
Coverage of Relevant Illustrations of AS,Ind AS and Schedule III
#Advanced Auditing & Professional Ethics#Advanced Auditing & Professional Ethics (CA Final) New Syllabus#November2018Exam#AdvancedAuditing#ForCAFinal#Auditing#ProfessionalEthics#AdvancedAuditingAndProfessionalEthics#ForCAFinalStudents#CAFinalBooks#CompaniesAct2017#AcademicBooks#ProfessionalBooks#OnlineBookstore#BuyBooksOnline
0 notes