#Scrape Data from Apple App Store
Explore tagged Tumblr posts
Text
by the way Congrats IbisPaint. Somehow, you managed to piss off BOTH SIDES of the AI debate. (elaboration in tags)
#for context: ibispaint apparently added some ai scaping feature (which could be turned off thankfully!)#however they removed it after backlash#...which led to the pro-ai crowd to get angry#and just recently ibispaint added an “AI disturb” feature which prevents artists from having their data scraped#however you have to have a premium account to even turn it on#(And honestly I think they only added it as a way to say “Sowwy :C” after the initial update)#so yeah#i'd change apps but the thing is most of the other apps are either difficult to use or just straight up suck#(and a good chunk of art apps are on apple stores only- i use an android)#ibispaint#ai debate#ai discourse
2 notes
·
View notes
Text
How to Scrape Data from Apple App Store?

Apple Store provides a limited API; however, iWeb Data Scraping’s App Store Scraper will assist you in scraping data from that at scale.
App Store Scraper — iWeb Data Scraping
Scrape App Store and iTunes for millions of movies, podcasts, apps, and more. Crawling media types with ISBN, author, images, title, language, description, and other information it offers. You can stipulate filters, search terms, custom URLs, and more.
App Store scraper

As Apple Store doesn’t offer a valid and good API, this data scraper will help you scrape data from that.
Our App Store data scraper offers the given features:
Scrape App Store or iTunes URLs : Get any App Store or iTunes URLs from a detail page.
Scrape by filters : Country, keyword, or media type. You could customize the results
Scrape media types : Scrape all media types which you want to get from Apple Store
Scrape publishers : You can collect intelligence from rivals by collecting data from them
Search any keywords : You could search any keywords you would need to have to get results
Search by several ids : If you want to extract multiple media or competitors, you can save them at once.
Features
Our App Store Scraper helps with the given features:
Scrape a media type
Scrape App Store or iTunes URLs
Scrape oppose publishers
Search by filters
Search keywords
Search various IDs
Figure Unit Consumption
The actor augmented to run quickly and extract many listings as possible. If the actor doesn’t slab very often it’ll extract 100 listings within 2 minutes having ~0.01–0.02 compute units. So, it leads all the listing information requests.

In the Program Run
In the run, an actor would output messages to tell you what is happening. Every message always has a shorter label requiring which page from the given list is presently specified. While items get loaded from a page, you need to see messages about the event having loaded item counts and total item count for every page.
If you offer incorrect inputs to an actor, this will directly stop with the failure position and output explanation about what is getting wrong.
App Store Transfer
During this run, an actor stores the results in a dataset. Every item is a specific item in a dataset.
You could organize results in a language (Node JS/NPM, Python, PHP).
Extracted Apps Store Media

Conclusion
Like all other actors, many new features are on a roadmap, and we are always open to new ideas! You can always contact us for feedback, feature requests, or new ideas that might be exciting to implement. You can get iWeb Data Scraping for your web scraping service and mobile app scraping service requirements.
Know more : https://www.iwebdatascraping.com/how-to-scrape-data-from-apple-app-store.php
#Extracted Apps Store Media#Scrape Data from Apple App Store#App Store Scraper#Scrape App Store data#Scrape App Store and iTunes#web scraping service#mobile app scraping service
0 notes
Text
Apple's complicity in Chinese state oppression

Bruce Schneier coined “feudal security” to describe the dominant Big Tech security model, in which you surrender your autonomy by moving into a warlord’s fortress (Google, Apple, Facebook, etc) and in return get protection from the bandits that roam the badlands without.
The historian Stephen Morillo pointed out that this is more like “manorialism” than “feudalism.” As I wrote in January, digital manorialism works well (if the warlord wants the same thing as you) but fails badly (if they decide to sell you out).
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
Google wants to kill third party cookies to protect you from randos doing tracking and targeting — but it wants to retain the ability to nonconsensually track and target you on its own:
https://www.eff.org/deeplinks/2021/04/fighting-floc-and-fighting-monopoly-are-fully-compatible
Facebook promises to defend you from the next Cambridge Analytica, but it threatens to sue academics who scrape its political ads to see whether it’s really living up to its promises to fight paid political disinformation:
https://pluralistic.net/2021/04/05/zucks-oily-rags/#into-the-breach
Apple has rolled out the most significant consumer privacy tech in decades, changing the defaults on Ios products so that if you don’t give your explicit consent, no one is allowed to track you (surprise: no one gave consent!).
https://www.eff.org/deeplinks/2020/12/facebooks-laughable-campaign-against-apple-really-against-users-and-small
Apple is 100% committed to protecting its users from commercial surveillance. But it’s also 100% committed to accessing the Chinese market and maintaining its Chinese manufacturing. Warlord Apple will defend you from ad-tech bandits, but not the People’s Liberation Army.
That’s why Apple valiantly, laudably fought the FBI’s demands to back-door its OS to gain access to the San Bernardino shooters’ Iphones, but rolled over when the Chinese government ordered it to remove all working VPNs from the App Store.
https://www.cnet.com/news/apple-removes-vpn-apps-from-china-app-store/
It’s why Apple took good, brave stands on human rights in the US, fighting gender and racial discrimination in important ways but continues to manufacture devices with Chinese contractors like Foxconn, one of the most egregious human-rights manufacturers in the world.
Now, in an explosive NY Times investigation, Jack Nicas, Raymond Zhong and Daisuke Wakabayashi accuse Apple of giving the Chinese state effectively unfettered access to user-data, directly contradicting the claims of Apple CEO Tim Cook.
https://www.nytimes.com/2021/05/17/technology/apple-china-censorship-data.html
The Times reporters say that this data isn’t just used to invade Chinese users’ privacy, but also to fine-tune Chinese state censorship, helping guide government operatives’ choices about which apps to censor and how.
This has resulted in the removal of “tens of thousands of apps… foreign news outlets, gay dating services and encrypted messaging apps…tools for organizing pro-democracy protests and skirting internet restrictions, as well as apps about the Dalai Lama.”
This is true of all firms doing business in China. The choice to do business there is the choice to be complicit in ghastly human rights abuses. But there are two ways in which Apple’s participation is different.
First, there is its carefully cultivated “Cult of Mac” identity that paints it as an “ethical” company whose paternalistic controls are part of a commitment to serving its users.
This has created a vast cyber-militia of Apple fans who consider themselves members of an oppressed religious minority and who lash out at anyone who crticizes the company as a “hater” (see, for example, the replies to this thread on Twitter).
And second, Apple arrogates to itself more control over its users and their devices than its rivals, asserting the right to block Apple device owners from making their own choices about which software to run, where to get their devices repaired, and even which parts to use.
Apple has distorted copyright, patent, trademark and import law to accomplish this control.
There’s an the army of defenders who’ll simp for Apple on this.
They oscillating between claims it’s all for the good of Apple customers, and claims that people who own Apple devices but don’t want to use them according to Apple’s corporate dictates “shouldn’t have bought Apple products.”
The Apple version of the No True Scotsman fallacy is the most creepily cultish thing that Apple’s self-appointed street-team do, especially in light of these latest China revelations.
Apple acts on behalf of its customers when that means acting on its own behalf. Apple — like the other warlords — cares ultimately about its shareholders, and if its shareholders’ interests diverge from its customers, the shareholders will always win.
That’s true of every tech firm, but only Apple has built an “ecosystem” — a great walled fortress that keeps the bandits out when Apple wants to, but once Apple lets them in, it keeps Apple’s customers from escaping.
26 notes
·
View notes
Text
What is Wikicamps Data Scraping Services?
Our Wikicamp travel mobile app scraping API will make it possible to scrape the information from the unstructured app.
About Wikicamps
Wikicamps is Australia’s largest database of campgrounds, caravan parks, backpacker hostels, points of interest, dump stations, visitor details, water taps, toilets, showers, and many more. It also helps to search for various destinations using Google Maps, Apple, or offline maps, navigation, and routing.
The scraping Wikicamps data will assist in downloading the offline content to a device with high-quality vectored Maps that will help you reach any destinations.
It becomes very easy to plan a trip using Wikicamps Trip Planner. You can create unlimited trips, also add various destinations, notes, and custom map pins.
How Can You Scrape Wikicamps Data?
Although there are several methods for Web Scraping Services wikicamps data, the most suitable solution for recurrent and large-scale requirements is to use a Data as a Service (DaaS) provider. DaaS service providers can give you all the relevant data based on your requirements because they have the necessary destinations, technological experience, and scalability benefits. It's also possible that the cost will be less than an in-home crawling arrangement.
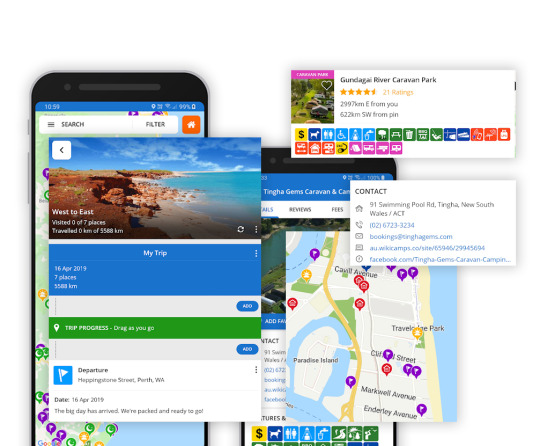
List Of Website
Here is the list of data fields that we can scrape from Wikicamps:
Map Information
Site List
Email Id
Destinations
Contact Details
City
Email Address
How does it Work?
When a customer requests data for the Wikicamps Travel Mobile app scraping using API, the API crawls the Wikicamps in real-time and stores the data directly in the user database solely in JSON format. As a result, the request (Input) and response (Output) for the Wikicamps Travel Mobile app scraping API will only be in JSON format.
1 note
·
View note
Text
As to that fanfic app, this is what I got from AO3
Thanks for asking about this app. We checked with the OTW Legal team and our coders, and have some information to pass on. "The OTW does not own the works posted on the Archive – they are all owned by their respective authors. For that reason, although the OTW can (and does) rely on trademark law to make sure that people don’t make confusing apps that would make people think the OTW or AO3 is associated with them, there’s nothing we can do about apps or services that contain works owned by AO3 users. That is up to the authors themselves, who own the copyrights in their fanworks. "Many sites have procedures (known as DMCA takedown procedures) that allow copyright owners such as fan-authors to request that their works be removed. The Fanfic Pocket Archive Library may have such procedures. Regardless of whether those procedures exist, copyright owners can always demand that their works be removed from places they are not authorized, and as a matter of copyright law, sites should comply with such demands. "The Apple App store also has procedures for reporting apps that infringe copyright: https://www.apple.com/legal/internet-services/itunes/appstorenotices/#?lang=en The Google Play store has similar: https://support.google.com/legal/troubleshooter/1114905 " To be clear, to the best of our knowledge, the app is not wholesale scraping and storing data - they're displaying content from the Archive in a very heavily modified format. Because the app's subscription fee can be explained as "to support the app's code base" and not for the content itself, it is within legal bounds. Our only suggestions are for the creators of the works to issue DCMA takedowns to the app developer, and to the appropriate app store if they find the developer response unsatisfactory.
because I looked and I don’t seem to have any stories on the app, there isn’t anything more I can do. Everyone needs to check to see if one of their stories is on it, then follow through. Sorry!
31 notes
·
View notes
Text
NEWS ON FANFIC POCKET LIBRARY!
Okay, I sent an email to A03 about this, to see if anything can be done. They can’t do anything... as all works are the rights of the authors. This is the email I recieved.
Hi: Thanks for asking about the Fanfiction Pocket Archive Library app. We checked with the OTW Legal team and our coders, and have some information to pass on. "The OTW does not own the works posted on the Archive – they are all owned by their respective authors. For that reason, although the OTW can (and does) rely on trademark law to make sure that people don’t make confusing apps that would make people think the OTW or AO3 is associated with them, there’s nothing we can do about apps or services that contain works owned by AO3 users. That is up to the authors themselves, who own the copyrights in their fanworks. "Many sites have procedures (known as DMCA takedown procedures) that allow copyright owners such as fan-authors to request that their works be removed. The Fanfic Pocket Archive Library may have such procedures. Regardless of whether those procedures exist, copyright owners can always demand that their works be removed from places they are not authorized, and as a matter of copyright law, sites should comply with such demands. "The Apple App store also has procedures for reporting apps that infringe copyright: https://www.apple.com/legal/internet-services/itunes/appstorenotices/#?lang=en The Google Play store has similar: https://support.google.com/legal/troubleshooter/1114905 " To be clear, to the best of our knowledge, the app is not wholesale scraping and storing data - they're displaying content from the Archive in a very heavily modified format. The app functions as a very heavily modified site skin, with a few extra functions provided with your data within the app. Because the app's subscription fee may be explained as "to support the app's code base" and not for the content itself, it is within bounds. Our only suggestions are for the creators of the works to issue DMCA takedowns to the app developer, and to the appropriate app store if they find the developer response unsatisfactory. We are also receiving reports about apps from a developer called Woodsign. We don't have a comment regarding these apps at this time.
So... simply... We as the Author’s of these works need to make a stand against the app, they are breaking our copyright rights. if your fic is on there you can demand and legally have them remove it as it is your property. If you are on A03 and have fics on there lease report the app for copyright. If we can at least get the Google pay people to look at it and start asking the important questions about copyright, then we have a chance for it to be removed.
Man, this is a fight I would never be in, but here we are. Please spread this around. Report Fanfic Pocket Library for breaking copyright, we have a chance in this!
16 notes
·
View notes
Text
Hi:
Thanks for asking about the Fanfiction Pocket Archive Library app.
Unfortunately, whenever anything is posted on the internet, there is always a risk of it being copied. It is not possible to block or prevent others from copying your work. If you want to try and reduce the chances of this happening in the future, you may want to consider locking your works to Archive users only. Doing so won't prevent all copying, but may make it less likely to happen. We checked with the OTW Legal team and our coders, and have some information to pass on.
"The OTW does not own the works posted on the Archive – they are all owned by their respective authors. For that reason, although the OTW can (and does) rely on trademark law to make sure that people don’t make confusing apps that would make people think the OTW or AO3 is associated with them, there’s nothing we can do about apps or services that contain works owned by AO3 users. That is up to the authors themselves, who own the copyrights in their fanworks.
"Many sites have procedures (known as DMCA takedown procedures) that allow copyright owners such as fan-authors to request that their works be removed. The Fanfic Pocket Archive Library may have such procedures. Regardless of whether those procedures exist, copyright owners can always demand that their works be removed from places they are not authorized, and as a matter of copyright law, sites should comply with such demands.
"The Apple App store also has procedures for reporting apps that infringe copyright: https://www.apple.com/legal/internet-services/itunes/appstorenotices/#?lang=en The Google Play store has similar: https://support.google.com/legal/troubleshooter/1114905" Our Legal team wrote a post with some helpful information in a similar situation some time ago, see https://archiveofourown.org/admin_posts/2692 (Scroll down to “What Can Fans Do if Their Fanworks Actually Are Hosted Elsewhere.”)
To be clear, to the best of our knowledge, the FPAL app is not wholesale scraping and storing data - they're displaying content from the Archive in a very heavily modified format. The app functions as a very heavily modified site skin, with a few extra functions provided with your data within the app. Because the app's subscription fee may be explained as "to support the app's code base" and not for the content itself, it is within bounds.
Our only suggestions are for the creators of the works to issue DMCA takedowns to the app developer, and to the appropriate app store if they find the developer response unsatisfactory.
If you have other questions about fanworks and copyright, feel free to contact the Organization for Transformative Works’ Legal team at [email protected]. Bella AO3 Policy & Abuse
10 notes
·
View notes
Text
What is Mobile Phishing?
Recent years have witnessed the increasing threat of phishing attacks on mobile platforms. In fact, mobile phishing is more dangerous due to the limitations of mobile phones and mobile user habits. Existing schemes designed for phishing attacks on computers/laptops cannot effectively address phishing attacks on mobile devices. Let’s talk more about mobile phishing attacks:

Phishing has moved to mobile
Most think “email” when they hear the word “phishing” but it is different on mobile. Mobile phishing extends beyond email to SMS, MMS, messaging platforms, and social media apps. Attacks are technically simple but novel in their approach. They seek to exploit human trust along social networks using personal context. For example, a parent would click without hesitation on a message saying their daughter has been in an accident at school.
Employees also find it easier to perform tasks on a mobile device than on a desktop. Depositing checks via mobile banking app, for example, is simple, fast, and convenient, and there are many other examples like this.
Ease and sophistication of attack
Part of the problem is the fact that it’s very easy for attackers to launch phishing attacks. Criminals can shop for and customize phishing toolkits. They can use tools that scrape genuine websites, grabbing fonts, images, and everything else they need in seconds to build quick replicas connected to an ever-changing portfolio of URLs.

“Vishing” you to give up your data
Another type of phishing fraudsters have been using is the one called “Vishing”, which is short for “Voice-mail phishing”. Some vishers will send you voice-mail messages saying they represent your bank, or some other financial institution, and urge you to call them back immediately or send them sensitive data to perform certain operations. Other vishers will skip the voice-mail part altogether. They will call you and persuade you to give up those details. Either way, your mobile security is run down.
Preventative Measures for Mobile Phishing
Only install apps from authorized sources
To avoid an unauthorized app getting a hold of your data, it’s best to only download apps from your smartphone’s authorized vendors. For Android phone owners, that’s the Google Play Store, while for iPhone and iPad owners, it’s Apple’s App Store.

Turn on caller ID or other services
Many carriers now offer a free service that highlights possible scam calls, like T-Mobile’s and MetroPCS’s “scam likely” service, and many phones now come with call-identifying capabilities built in. These abilities give a quick snapshot of whether the service thinks the call is legitimate, and allow you to report scam calls to a central database.
Final Words
There is no foolproof method to counter the attacks of hackers on your mobile phones. Organizations must set up advanced phishing protection services to safeguard against these kinds of attacks.
Source:
https://cybersecurity.att.com/blogs/security-essentials/mobile-phishing
https://www.bullguard.com/bullguard-security-center/mobile-security/mobile-threats/smishing-vishing-mobile-phishing.aspx
https://www.csoonline.com/article/3268109/the-rise-of-mobile-phishing-attacks-and-how-to-combat-them.html
https://www.digitaltrends.com/mobile/how-to-protect-yourself-from-cellphone-phishing-attacks/
1 note
·
View note
Text
How to Extract Data from Apple App Store?

We all are familiar with the Apple App store. Here, we will brief some information about it. The Apple App store is an online store where you can purchase and download software applications and mobile apps for Apple computers and devices. Initially, this app, known as an online app store for mobile devices, is generated by Apple’s iOS mobile Operating store, including iPad, iPhone, and iPad touch. But it has gained its expansion to Mac App Store for applications purchasing like Mac OS X personal computers.
The Apple App Store is a ground-breaking medium for downloading native iOS applications easily. You can easily purchase and download directly to the device. Moreover, it is also accessible via Apple’s iTunes software and then transferred to the iOS device. However, more than 500,000 apps are available on the Apple App Store. These apps majorly share the app store market.
It is a well-known platform exclusively meant for Apple users. In today’s era, everyone is inclined towards gadgets usage and highly depends on their functionalities to perform essential day-to-day services. To satisfy the need of millions of people across the globe, the app store possesses apps loaded with several functions. These apps are known to possess high-security features.
Web scrapers extract data from reviews and app details in the app store. This article will discuss simple steps to extract data from Apple App Store.
Why Scraping App Store
The app store contains various categories like TV, movies and streaming, lifestyle, travel and food, books and magazines, social networking, and lots more. These apps also possess information related to ratings, reviews, downloads number, etc. Customer sentiments and feedback is essential to enhance the app’s functioning. Manually reading thousands of feedback is a tedious task. Hence, by automating the 0065traction process, you can easily extract any information in real-time.
Benefits of Scraping App Store
Understanding customers’ requirements are the highest priority. Scraping reviews and analyzing them gives a better understanding of customers’ negative and positive feelings.
Scraping enables tracking what’s trending. It, however, analyzes trends and new updates. Based on that, it picks the trending keywords that might help boost the app’s reach.
It helps investigate the app’s popularity. By extracting information about trending and popular apps, developers can enhance the betterment of their apps.
Scraping and analyzing data boosts the rate of success of specific marketing strategies.
Tools and Steps Involved in Apple App Store Data Extraction
Here we are using Scrapy, a web-scraping Python tool that will accomplish the task perfectly.
Name of the app
Size in MB
Category
Compatibility
Languages
App Ratings (0-5)
Age Ratings
Price
Total Ratings
Data Cleaning and Pre-processing
After we scraped the raw data, we used multiple tools in Python to ensure that our data were cleaned and formatted. The primary tool for cleaning is the Panda library. Next, we encapsulated all pre-processing code in a function for more elegant data analysis.
Data Analysis
The first thing we analyzed was the app size (MB) distribution. Our objective was to understand the app size density installed in the App Store and their ranges. We observed that most applications are between 50 and 100 MB. The below image illustrates this:
The above image depicts that the gaming category has the highest rating category on the app store.
Lastly, we looked into the most-rated new apps and found that Twitter and Reddit lead the top 10.
Scrape App Store Reviews using Python
Using the Python package installer, first, install the app_store_scraper
For the demo, here we are using the random app. Let’s take an example of the Slack app.
Now convert the data into JSON format to make it more readable and structured. Use the following code to do this:
This final step converts the data frame into a comma-separated value format.
Save this Slack-app-review csv file into your folder, and you are ready to go.
Conclusion:
Thus, the ever-changing digital world generates a plethora of data daily. Millions and millions of apps hosts on the App Store, which has extensive market reach. Companies, however, require ratings and reviews data to modify and maintain their apps. With web scraping, you can easily understand users’ sentiment and by utilizing these understandings, companies can enhance their app functionalities. It also benefits companies to release new app updates and improve their marketing strategies.
CTA: For more information, contact Actowiz Solutions now! You can also reach us for all your mobile app scraping and web scraping services requirements.
0 notes
Text
Apple builds on privacy commitment by unveiling new education and awareness efforts on Data Privacy Day
Data Privacy Day is an important day for Apple, as it marks the company's commitment to privacy and security. On this day, Apple unveils new education and awareness efforts that not only help its customers understand the importance of data privacy and security but also inform them on how they can protect their own information. This blog post will discuss Apple's efforts to raise privacy awareness on Data Privacy Day, highlighting the various initiatives that the company has undertaken. We will also explore how these initiatives help protect customers from data breaches and other digital threats. Finally, we will explore what this means for data privacy in the future and how we can all help keep our personal information safe.

Protecting Users’ Privacy with Today at Apple
The website includes information about Apple’s privacy practices, as well as videos and other materials to help users better understand the importance of data privacy. In addition to the new website, Apple has also announced the launch of a new privacy education program to help teach users about the importance of protecting their data online. The program includes free online courses, webinars, and other materials that are designed to help users better understand data privacy and security. The portal will give users more control over their data, allowing them to view and edit their data as needed. Apple’s commitment to data privacy is clear, and these new initiatives demonstrate their dedication to helping users better protect their data. By providing education and resources, users can be better informed and take steps to protect their data online.
Building in Privacy from the Ground Up
How Apple Protects Customer DataApple Carefully Chooses the Developers that Work with its PlatformApple has a strict set of guidelines for those who want to work with its platform. They make sure to only work with developers who are committed to protecting data privacy and helping customers do the same. As part of this commitment, Apple has built an App Store Review Guidelines that emphasizes protecting customer data and preventing any harm from happening in the future. This also includes a no-UI-scraping policy, which is cautious about not allowing apps that rely on user input without their expressed permission. to be included in the App Store.This is a good thing for developers and users, because Apple is not going to allow any apps that don't respect user privacy or data protection. to be included. in the App Store.
The most important thing is to remember that Apple has tried to make user privacy the core of its business strategy, and that the app ecosystem could have been a lot different had it not. been for strict privacy policies.Most people are willing to give up a little privacy in exchange for convenience, but Apple is the Silicon Valley company that's trying to maintain a more level playing field between big tech and consumers. .To do so, Apple has made the iPhone a closed ecosystem by refusing to allow apps that are not on its App Store. While this is a contentious move, it's one that Google doesn't take: The company allows third-party companies like Facebook, Snapchat and Instagram to build apps for Android phones through its Google Play Store.If you use a phone that runs entirely on Apple software and services, you're stuck with whatever they decide to add or change.Apple's dominance in the smartphone industry makes it difficult for other tech companies to offer their products and services because of the closed ecosystem Apple has created. This commitment to transparency and control — and to privacy-protecting innovations across its technology — gives Apple users more choice and more control over their personal information. On Data Privacy Day and every day, teams across Apple are pushing this work forward. Learn more about Apple’s privacy features by visiting apple.com/privacy.

wristwatchstraps.co
0 notes
Text
Tech trustbusting's moment has arrived

When it's railroading time, you get railroads.
When the railroads turn into the personal satrapies of rail-barons, you get trustbusters.
A couple decades ago, it was online service time. We had the users, the telcoms systems, the computers, the modems, so we got platforms.
We had that, but we lacked something important: effective antimonopoly enforcement. Lax merger laws allowed companies with access to capital markets to buy out or neutralize all their competitors, so we got monopolies.
Right on schedule, we're getting digital trustbusters.
Now, some people aren't technically sophisticated, but they do understand a lot about competition law. That's how you get meat-and-taters antitrust proposals like Amy Klobuchar's CALERA, which address the structural problems with antitrust law.
https://pluralistic.net/2021/02/06/calera/#fuck-bork
Klobuchar's bill is hugely important. The reason we have monopolies is that we stopped enforcing anti-monopoly law 40 years ago. Monopoly isn't a tech problem, it's everywhere from sneakers to glass bottles to pro wrestling to candy to aerospace.
https://www.openmarketsinstitute.org/learn/monopoly-by-the-numbers
Klobuchar's CALERA doesn't just seek to apply antitrust law to tech – it also explicitly restores the pre-Reagan basis for fighting monopolies: we fight monopolies because they concentrate power and corrupt our politics. All monopolies are guilty unless proven otherwise.
But though industries all attained their monopolies through similar tactics – predatory acquisitions and mergers, vertical integration – they also each have their own technical characteristics that must inform our demonopolization tactics.
Take emergency care: monopolists love ERs because we don't choose which ER to use, nor when. You can't shop for an ER from the back of an ambulance. You don't know going in whether you're going to spend $1m or $1k. And you'll buy whatever services the ER tells you to buy.
Or power-grids: demand for electricity is both inelastic (you need power when you need power) and price-insensitive, and that inelasticity increases with demand: that is, when it's freezing or boiling out, everyone wants electricity.
Tech, of course, has its own technical characteristics. Chief among these is its flexibility. At a deep, theoretical level our digital tools and networks are capable of interoperating with one another in ways that no physical technologies can match.
Think of the Australian rail-system. In the mid-19th century, would-be rail-barons laid differing gauges in hopes of conquering the nation's logistics and transport. For 150+ years, engineers have tried to solve the "multi-gauge muddle" by designing multi-system railcars.
Hundreds of designs for cars that retract and extrude different wheelbases have been tried, and none ever caught on. Instead, Australia is tearing up and re-laying thousands of kilometers' worth of track. With physical tech, "compatibility" often means starting from scratch.
Not so with digital tech. If you are an OS company whose rival has locked up all office docs in a proprietary format, you don't have to convince all its customers to abandon their documents and start over. You just make a compatible program:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
With digital and physical tech, network effects drive high switching costs, but when it comes to digital, network effects are a double-edged sword.
With interoperability, a walled garden can easily become a feed-lot, where customers for a new service are neatly arrayed for competitors to come and harvest.
https://www.eff.org/deeplinks/2021/01/twitter-and-interoperability-some-thoughts-peanut-gallery
Good tech policy emphasizes interoperability when it comes to demonopolizing the digital world. Long before the US ACCESS Act and the EU Digital Markets Act, Mike Masnick published his seminal "Protocols, Not Platforms" paper.
https://www.eff.org/deeplinks/2021/01/twitter-and-interoperability-some-thoughts-peanut-gallery
And Daphne Keller's work on "Magic APIs" presaged the ACCESS Act's idea of forcing tech companies to expose the APIs they use internally so that competitors can plug into their services:
https://www.techdirt.com/articles/20200901/13524045226/if-lawmakers-dont-like-platforms-speech-rules-heres-what-they-can-do-about-it-spoiler-options-arent-great.shtml
(that paper is outstanding, BTW, with clear-eyed assessments of alternatives, like a digital fairness doctrine, "common carriage" rules, an "indecency" standard for content moderation – basically a checklist for "So you've got a plan to fix tech – did you think of ____?")
Masnick's "protocols" are a vision for a decentralized, better internet. Keller's Magic APIs describe a legal path to getting there. My own work on Competitive Compatibility (nee Adversarial Interoperability) describes how we'll STAY there.
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Because monopolies are good at subverting regulation, so any Magic API rule would be brittle – dependent on the tech companies not sabotaging those APIs by moving the important data-flows away from the mandatory APIs.
That's why we have to strip monopolists of the power to ask a court to block interoperators: take away the wildly distorted copyright, patent, terms of service and other legal doctrines that Big Tech ignored during its ascent, but now enforces against would-be competitors.
With both interop mandates and a legal right for new entrants to force interoperability through technical means, tech giants will face consequences if they subvert antimonopoly rules.
The choice becomes: either respect the intent of a mandate and preserve interop; or be plunged into a chaotic arms-race with competitors who switch to scraping, bots, and reverse-engineering.
All of this is incredibly wonkish, a highly specialized debate that involves highly technical propositions about how digital technology works today, how it used to work and how it might work – layered atop a similar, highly technical understanding of antitrust law.
The Venn overlap of "deep understanding of digital tech" and "deep understanding of antitrust debates" isn't so much a slice as it is a sphincter, and the debate has been equally narrow, but when it's railbaron time, you get trustbusters.
The tech monopoly/interop debate is going mainstream. Francis Fukuyama and his colleagues at the Stanford Working Group on Platform Scale have proposed an intervention similar to the ACCESS Act, where trusted third parties mediate between monopolists, new entrants and users.
The Stanford proposal calls them "middleware companies," but they're conceptually interchangeable with the idea of a "data fiduciary": companies that act as referees when a new co-op, startup or nonprofit wants to plug into a monopolist's service.
https://pairagraph.com/dialogue/4124f75013da40038c4cbff5ebdaaa51/3
This is clearly an idea whose time has come – it's present in the EU's DMA and the US Access Act, and latent in the UK CMA report:
https://www.gov.uk/cma-cases/online-platforms-and-digital-advertising-market-study#final-report
Importantly, it's an approach that recognizes the distinctive character of tech – taking account of the power of interop to break open walled gardens and unravel network effects.
What's especially interesting about this work is that it appears to have been developed in parallel to pre-existing work from Masnick and Keller (and me) – it's a case of convergence between the tech-policy world and the broader world of policy.
After all, while Masnick and Keller's work is well known inside of tech policy, that's just our obscure, nerdy corner of the policy world – now they're escaping that corner, becoming self-evident to people from traditional policy backgrounds.
https://review.chicagobooth.edu/economics/2020/article/capitalisn-t-francis-fukuyama-s-proposal-rein-big-tech
My hope is that the trend continues – that we see ideas about Competitive Compatibility/Adversarial Interop join the idea of API mandates, so that we produce durable anti-monopoly systems, not just anti-monopoly rules.
Most important, though, is restoring an appreciation for the importance of interoperability in preventing monopolies and promoting technological self-determination for communities and individuals.
Because such a sensibility can escape the legislative world and be enacted via fast-moving, easier-to-use policy tools. For example, we could (should!) make interop a feature of all government procurement rules.
No school district should buy devices for students without securing the right to sideload the apps they need on them – imagine buying 50,000 Ipads at public expense and then having Apple boot the app you rely on out of the App Store!
Likewise, no district should buy Google Classroom without securing a legally binding guarantee not to block interoperators who want to integrate other ed-tech services into the curriculum, with or without Google's cooperation.
Procurement and interop are as old as the Civil War, when the Union Army demanded firearms and ammo that had multiple manufacturers. As the state-level Net Neutrality rules (which bar governments from using non-neutral ISPs) showed us, procurement can shape markets.
Procurement is just for starters. Right now, tech companies caught breaking the law are handed down fines that are less than the profits their lawbreaking generated – instead, we could demand interop as part of any settlement.
One major barrier to interop is contract law: terms of service, EULAs, noncompetes, arbitration, etc. States wield enormous power over contracting terms: states can declare certain contractual language against public policy and thus unenforceable.
If, say, California were to pass a rule nullifying the mountain of abusive garbage that has become standard in digital "contracts," it would be in a position to export fair usage terms to the country in just the same way it exports robust emissions standards.
Antittrust is primarily a federal manner (that's why 40 years of federal antitrust malpractice has been such a disaster). But every level of government, down to your local school board, can make a meaningful difference in tech antitrust.
Digital technology's inescapable, marvellous, terrifying flexibility can be translated into so many unique, powerful weapons for transforming the industry and empowering communities to control their digital lives and seize the means of computation.
33 notes
·
View notes
Text
Meta Cracks Down on User Security Threats
Meta makes a few notable steps this week in the fight against security threats. Andrew Hutchinson writes in Social Media Today that Meta detected 400 applications that steal user data from Meta’s family of apps, namely a Facebook login. Users are lured by apps that claim to be a variety of functions- photo editors, games, business, etc- in which login information is mandated for access, then stolen by developers. Hutchinson comments that the apps look suspicious, but it is understandable that a novel feature could trick users to input information. Because these scam apps cover many categories, Apple and Google must be cautious of what’s approved for app stores.
Joseph DeAvila also covers Meta’s notification of these scams in The Wall Street Journal, noting that Google has now removed all suspicious Android apps, and Apple removed 45 IOS apps detected by Meta. DeAvila and Hutchinson highlight Meta’s recommendation for users to stay away from applications that require a Facebook login and to enable a 2-factor authentication.
In the same vein, Ivan Mehta writes in Tech Crunch that Apple and Google have removed The OG App, an Instagram client that removes ads, after Meta took action against it for its violation of Instagram policy and risk to user privacy. Mehta notes that Meta has been cracking down on any threats to user data, so the timely removal of unofficial API is no surprise. This is not the only company Meta has shut down this week, as Meta just settled a lawsuit against BrandTotal Ltd. and Unimania Inc. for data scraping operations. Sarah Perez and Zack Whittaker cover the suit in Tech Crunch. They write that the complaint started against the companies in 2020 has now been settled, and they are banned from scraping Meta user data or profiting off the data collected.
As Meta removes external offerings of alternative Meta app experiences, whether it be an ad-free timeline or anonymous story viewing, I wonder if Meta’s dedication to safety is paired with an intent to monopolize user interactions as it attempts to shift the technological world to the metaverse.
0 notes
Text
Apple IOS 10.2 Possesses Dozens New Emojis, And Even more.
Nintendo's upcoming new console will definitely be actually along with our team in less than a year, with the next-generation console - codenamed Nintendo NX - affirmed to become coming in March 2017. And in a bid to safeguard help from insurance carriers, medical facilities as well as other personal healthcare passions, the Us senate - with the White Home's benefit - eliminated the supposed public possibility, a government-run health insurance plan that would certainly have contended alongside exclusive anticipate Obamacare's insurance policy exchanges. The iphone 9.3 update contrasts along with what our team have actually seen prior to: iOS 9.1 included brand-new emojis, iOS 9.2 tweaked Apple Popular music and Apple Headlines and iOS 9.2.1 simply dealt with bugs. Yet the even more these choices with multiple girls accumulate, the more probable the male will permit his bodily recommends receive the best from him. You'll merely locate BUST choices in Windows Server versions; pc Microsoft window XP, Panorama, Microsoft window 7 editions only supply spanned, removed and also exemplified features as a result of licensing. If the rate trends breaks free throw line on a upward or descending style, you acquire the equivalent choice. This possibility makes it possible for home owners to pay simply on the enthusiasm of the home loan without making any type of payments to the concept. http://frumosi-razboinici.info will very recommend the People of New York (HONY) blog or even Instagram feed to receive a daily fix if you possess but to examine it out. Or even you can easily locate even more technological field study involving a wide array of trading methods that analyze essential headlines and market information to create PHONE CALL or even PUT techniques. Our experts may add 9 different options to this, and we 'd highly recommend important ones like WiFi, Bluetooth, Battery Life, Information Utilization, Notifications, or whatever you utilize or need to have usually. It does not deal with the entire display, and sometimes I can observe the edge of the protector running down each side from the screen, which distracts from the on-screen action. On other devices, such as the Huawei P9, the second SIM port likewise functions as a microSD slot, yet that is actually certainly not the scenario below - as pointed out, there is actually no expanding storage space possibility. Mommies - and fathers - which look at selection acquire no possibilities counseling and, instead of sufficient opportunity making an informed selection, numerous define being pressured as well as made to experience required to adoptive moms and dads they have actually been matched along with. These Forex trading robotics will truly assist you out when creating tough choices about buying and selling. At the beginning you can only leave it on Car, yet if you notice saw teeth along with the image in motion (certainly not those generated due to the edges from polygons), you can make an effort the possibility Bob ttf. Our experts have actually made use of the Flower Gold apple iphone Sixes Plus for a year with no true scrapes, and have not learnt through individuals complaining about the Gold or even Silver option. If pressing doesn't seem like your trait and space isn't an issue, stuffing a mid- or even full-sized tower packed with drives is a basic alternative. Essentially enabling proprietors to add all their beloved setups or choices they make use of one of the most usually to be presented listed here instead of digging by means of the whole entire Galaxy S7 settings menu. Those extra months are going to vary depending on the option cycle which this is a member. Due to the fact that modern technology possesses an influence on the cost sustained in the creation of movies and their streaming to customers, firms that have managed to use this well have actually realized better return thus raising competition. You can easily today pick the Hibernate alternative from the Start menu whenever you prefer to hide for returning to operate rapidly. Furthermore, bad news regarding Obamacare's health plan swaps-- where superiors seem readied to rise substantially for at least some clients as well as less insurance providers will definitely be delivering plans for following year-- has stimulated passion among Democrats as well as other supporters of the medical care legislation in extending health protection and also decreasing prices. Binary choice trades are performed on an on an hourly basis manners and also due to their simple backwards and forwards structure; they could be simply recognized even by beginners. Windows 8.1 offers you choices to establish what units and data are made use of by apps found in the Microsoft window Store. In the U.S. we could just view a few of the formal choices generally 3 shades, however our company will definitely view a stable of better and also differed shades available in other places. http://frumosi-razboinici.info from The big apple: Stories, is actually a compilation publication of the tales and also photographes accumulated through Brandon Stanton. This last option is used to keep your firewall program off icy up during the course of the download method. The dropdown component is actually a Selectable When an alternative is selected, the label and/or image of the control modifications to present the chosen choice. This isn't really as a lot from a complication as this sounds considering that today, with lashings from processor chip electrical power to spare, software-based BUST has ended up being the favoured possibility.
1 note
·
View note
Text
Extract Popular App From Apple Store Using Google Chrome
Using Extension of Chrome, you can extract Apple Store online or acquire details from popular applications – this blog will help you to show how to do it.

What is an App Store?
An App Store is one type of digital sharing stage maintained and developed by Apple INC and it is particularly used for mobile applications on its iOS & iPad OS operating systems. The App Store allows all the users to download and browse with Apple IOS development.
There are around about 218 Billion Mobile App Downloads in 2020. Users are spending around 143 Billion globally on Mobile Apps in 2020. Many users had spent over 4.64 Billion on mobile Apps in Quarter3 in 2020. Apple is having around 2.9 Million apps in App Store. The Most Downloaded app category in the Apple store is Game. There are around about 85 Billion users that are downloading from Apple Store.
Listing of Data Fields
At Web Screen Scraping, we extract the required data fields from Popular Apps from Apple App Store :
Application Name
Size of Application
Categories of Applications
Compatibility of Device
App Store Languages
Ratings of App
Ratings of Age
Total Number of Ratings
Price of Apps
Below is the defined image: -

Fundamentals
To Extract App Store you require these packages
Google Chrome Browser: - You require to download Chrome Browser first. The extension needs Chrome 49+
Web Extractor Chrome Extension: - You can download Web Extractor Extension from Chrome Website Store. Once you download the extension you will notice a spider sign in the browser.
Import iTunes Extractor
Utilizing Web extractor, you will be able to make a site that displays what information should be scraped & how a website must pass over. The system process is equally simple; you will be able to follow more or less of our Documentation & Web Extracting Extension tutorials if you want to learn more.
We have created an extractor you need to copy & paste into the extension.
Import Extractor
After installing the extension, you need to right-click wherever on the given webpage, go to the Develop Tools & ‘Inspect’ will come up. Tick on the given tab ‘Web Extractor’ and go click on ‘Import Sitemap’ and to the ‘Generate fresh site’ key option. Just paste the JSON underneath into the Site JSON box.
Run the Extractor
To start extracting, go to Sitemap and tick on ‘Extract’ from the dropdown. A new request of Chrome wants to present, the extension to grab & scroll the data. When the extractor is completed, the browser will send a notice & it will end automatically.
Conclusion
In conclusion, gaming is considered to be the best notable category amongst all the apps in the Apple store, specifying that this category is having the most money making-potential. While doing more research you need deeper examination into subdivisions of the games.
In conclusion, gaming is considered to be the best notable category amongst all the apps in the Apple store, specifying that this category is having the most money making-potential. While doing more research you need deeper examination into subdivisions of the games.
If you want to build anything wonderful from the Popular Apple App Store with the help of Web Screen Scraping let us know your requirements.
0 notes
Text
I reportrd to AO3. This is the message I received. Thanks for asking about the Fanfiction Pocket Archive Library app. We checked with the OTW Legal team and our coders, and have some information to pass on. "The OTW does not own the works posted on the Archive – they are all owned by their respective authors. For that reason, although the OTW can (and does) rely on trademark law to make sure that people don’t make confusing apps that would make people think the OTW or AO3 is associated with them, there’s nothing we can do about apps or services that contain works owned by AO3 users. That is up to the authors themselves, who own the copyrights in their fanworks. "Many sites have procedures (known as DMCA takedown procedures) that allow copyright owners such as fan-authors to request that their works be removed. The Fanfic Pocket Archive Library may have such procedures. Regardless of whether those procedures exist, copyright owners can always demand that their works be removed from places they are not authorized, and as a matter of copyright law, sites should comply with such demands. "The Apple App store also has procedures for reporting apps that infringe copyright: https://www.apple.com/legal/internet-services/itunes/appstorenotices/#?lang=en The Google Play store has similar: https://support.google.com/legal/troubleshooter/1114905 " To be clear, to the best of our knowledge, the app is not wholesale scraping and storing data - they're displaying content from the Archive in a very heavily modified format. The app functions as a very heavily modified site skin, with a few extra functions provided with your data within the app. Because the app's subscription fee may be explained as "to support the app's code base" and not for the content itself, it is within bounds. Our only suggestions are for the creators of the works to issue DMCA takedowns to the app developer, and to the appropriate app store if they find the developer response unsatisfactory. We are also receiving reports about apps from a developer called Woodsign. We don't have a comment regarding these apps at this time. Best, Jocelin AO3 Support
🚨ATTENTION🚨
All Writers Published on Ao3:
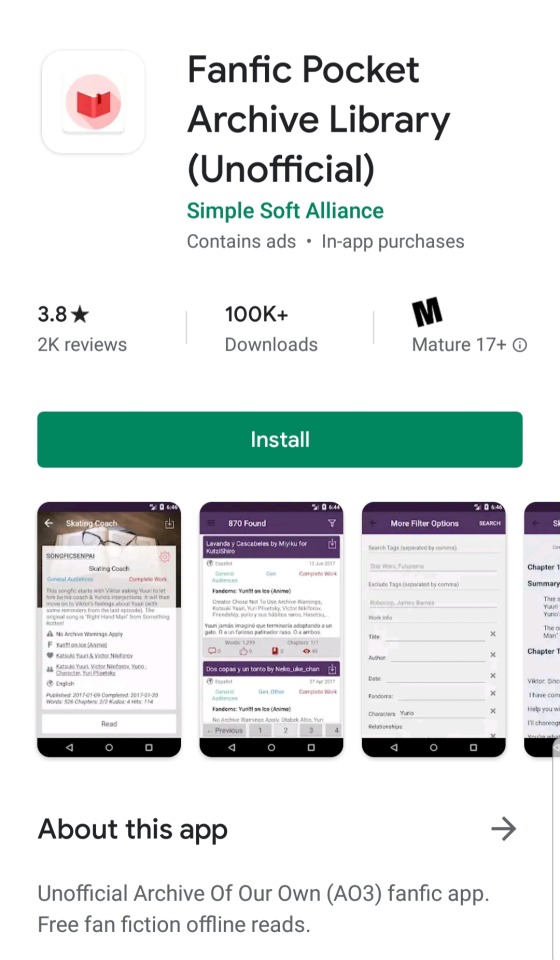
This app, "Fanfic Pocket Archive Library", is lifting all public content from Ao3 and making it available through a service they profit from.
Your work has been stolen and is being used to make money for a third party.
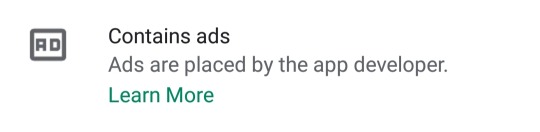
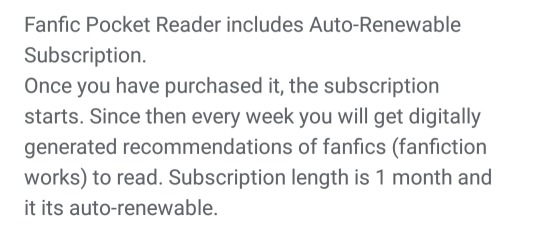
^above are the ways in which the app makes money off of Ao3 content. The developer is called Simple Soft Alliance. Here's the app's Terms and Conditions.
Any fanfiction that can be accessed without a password on Ao3 is already available in this app. Yours, mine, every fan creator's. Whether this is illegal I do not know, but it is certainly unethical and needs to be fought. Ao3 is a site of unparalleled integrity and shows the utmost respect to creators, so this content grab is an even bigger slap in the face for that reason.
🚨Please flag/report this app in your app store. 🚨
🚩Google Playstore link
🚩Apple Store link (download app, then go to report it here )
Feel free to contact Ao3 as well to alert them to this issue. Let's take em down, folks. In the meantime, you can put your Ao3 in private mode to prevent any more data theft.
Please reblog and tag your writer friends. Signal boost this.
49K notes
·
View notes