#Secure Software Delivery
Explore tagged Tumblr posts
Text

Best practices are getting translated into actionables within the enterprise-wide SDLC process.
0 notes
Text
operation: laundry love | joshua hong

Author: bratzkoo Pairing: software developer! joshua x reader Genre: fluff, love at first sight Rating: PG-15 Word count: 9.1k~ Warnings/note: requested by a lovely anon!
summary: Joshua Hong falls in love at first sight with you at a laundromat and schemes his way into making you like him back.
taglist (hit me up if you wanna be added): @escoupseu , @yanabaaaaaaarysheva , @spnyin , @sousydive , @gyuguys , @gyubakeries
requests are open, but you can just say hi! | masterlist
Joshua Hong had always considered himself a practical man. At twenty-eight, he had a stable job as a software developer, a tidy apartment, and a cat named Algorithm. His life was as orderly as the code he wrote, each day neatly compartmentalized into routines and habits. Laundry day was no exception—every other Saturday, 2 PM sharp, he'd trudge down to Suds & Bubbles, the local laundromat, with his precisely sorted clothes.
But on this particular Saturday, as Joshua pushed open the glass door of Suds & Bubbles, his well-ordered world tilted on its axis.
The laundromat was busier than usual, probably due to the unseasonably warm weather that had everyone in town suddenly remembering their summer clothes. The air hummed with the whir of washing machines and the occasional beep of a dryer reaching the end of its cycle. The scent of detergent and fabric softener hung thick in the air, mingling with the faint mustiness of old magazines stacked on a nearby table.
Joshua's eyes swept the room, looking for an empty machine. That's when he saw her.
She was standing in front of a washing machine, her brow furrowed in concentration as she examined a shirt with the intensity of a scientist studying a rare specimen. Her hair was piled haphazardly atop her head in what might generously be called a bun, secured with what appeared to be a pencil. She wore oversized sweatpants and a faded t-shirt that proclaimed "I'm not arguing, I'm just explaining why I'm right."
To Joshua, she was the most beautiful thing he'd ever seen.
As if sensing his gaze, she looked up, meeting his eyes. For a moment, Joshua forgot how to breathe. Her eyes were warm, like flecked with gold, and crinkled slightly at the corners as if she was perpetually on the verge of laughter.
"Excuse me," she said, her voice snapping Joshua back to reality. "You wouldn't happen to know how to get spaghetti sauce out of a white shirt, would you? I've been staring at this stain for so long, I'm starting to see pasta shapes."
Joshua blinked, his brain scrambling to form a coherent sentence. "I, uh... have you tried pre-treating it?" he managed to stammer out, mentally kicking himself for such a mundane response.
She sighed dramatically, holding up the shirt. "I've pre-treated it, post-treated it, and given it a stern talking-to. Nothing seems to work. I'm beginning to think this shirt has a vendetta against Italian cuisine."
A chuckle escaped Joshua before he could stop it. Her deadpan delivery and the absurdity of the situation broke through his initial panic, and he found himself relaxing slightly.
"Maybe it's more of a Chinese food fan," he offered, surprised by his own attempt at humor.
Her eyes lit up, and she let out a laugh that seemed to bubble up from her toes. "Oh my god, you're right! I should have been feeding it lo mein this whole time. How could I be so culturally insensitive to my own clothing?"
Joshua felt a warmth spread through his chest. He'd made her laugh. He, Joshua Hong, notorious for his dry technical explanations and inability to remember punchlines, had made this gorgeous, funny woman laugh.
"I'm Y/N, by the way," she said, extending her hand. "Y/N L/N, destroyer of shirts and apparent oppressor of Italian-American textiles."
"Joshua," he replied, taking her hand. Her skin was soft, and he had to resist the urge to hold on longer than socially acceptable. "Joshua Hong, software developer and... uh, laundry doer."
Y/N raised an eyebrow, her lips quirking into a smirk. "Laundry doer? Is that the technical term?"
Joshua felt heat creep up his neck. "Well, I... I mean, I'm not a professional or anything. Just a guy who, you know, does laundry. Sometimes. Well, every two weeks, actually. It's kind of a schedule thing, and—" He cut himself off, realizing he was rambling. "Sorry, I'm not usually this..." He gestured vaguely, unable to find the right word.
"Articulate?" Y/N supplied helpfully, her eyes twinkling with amusement.
"That's one way to put it," Joshua said, managing a self-deprecating smile.
Y/N's gaze softened. "Hey, no worries. We all have our off days. Although," she added, glancing around the laundromat, "I'm not sure anyone's really on their A-game in a place like this. I mean, look at that guy over there."
Joshua followed her gaze to see a middle-aged man trying to stuff what looked like an entire month’s worth of clothes into a single washing machine.
"I think he's trying to create a black hole of socks and underwear," Y/N stage-whispered. "Should we alert NASA?"
Joshua snorted, then quickly tried to cover it with a cough. He wasn't used to finding things genuinely funny, especially not in a laundromat of all places. But something about Y/N's observations and the way she delivered them with such casual humor was infectious.
"Maybe he's conducting an experiment on the compression capabilities of cotton blend fabrics," Joshua found himself saying.
Y/N's eyes widened in mock seriousness. "Of course! How could we have missed it? Clearly, we're witnessing groundbreaking laundry science in action."
They both burst into laughter, drawing curious glances from other patrons. Joshua felt a mix of exhilaration and embarrassment. He wasn't used to being the center of attention, but with Y/N, it somehow felt... right.
"So, Joshua the Laundry Doer," Y/N said once their laughter had subsided, "since you're clearly an expert in all things wash and fold, any other tips for a hapless stain-battler like myself?"
Joshua's mind raced. This was his chance to impress her, to show off his knowledge. But as he opened his mouth to launch into a detailed explanation of stain-removal techniques, he caught sight of the playful glint in her eye. She wasn't really looking for a lecture on laundry. She was teasing him, keeping the banter going.
For a moment, panic threatened to overwhelm him. He wasn't good at this kind of thing. Flirting, joking around—it wasn't in his usual repertoire. But something about Y/N made him want to try.
"Well," he said, affecting a serious tone, "as a certified laundry professional—"
"Oh, you're certified now?" Y/N interjected, raising an eyebrow.
"Absolutely. I have a degree in Sock Pairing from the prestigious University of Wash and Tumble Dry."
Y/N gasped dramatically. "I've heard of that place! Isn't their mascot the Fighting Lint Roller?"
Joshua felt a grin spreading across his face. He was doing it. He was actually engaging in witty banter. With a beautiful woman. In a laundromat. If his friends could see him now, they'd never believe it.
"That's the one," he confirmed. "Our battle cry is 'We'll press your buttons!'"
Y/N doubled over laughing, clutching her sides. "Oh my god, stop," she wheezed. "I can't breathe!"
Joshua felt a surge of pride. He'd done that. He'd made her laugh so hard she could barely breathe. It was a heady feeling, one he wanted to experience again and again.
As Y/N's laughter subsided, she wiped a tear from her eye. "Oh, man. I haven't laughed like that in ages. You, Joshua Hong, are dangerously funny. They should put a warning label on you."
Joshua felt his cheeks heat up at the compliment. "I, uh, thanks. You're pretty funny yourself."
Y/N waved a hand dismissively. "Nah, I just state the obvious. The world's a pretty ridiculous place if you pay attention." She glanced down at the shirt in her hand, then back at Joshua. "Speaking of ridiculous, I should probably actually try to wash this thing before it becomes sentient and decides to take over my wardrobe."
"Right, of course," Joshua said, suddenly remembering why they were both there in the first place. He glanced around, spotting an empty washing machine a few feet away. "There's a free machine over there if you need one."
Y/N followed his gaze and grinned. "My hero! Saving me from the horrors of waiting for a free washer. Truly, your laundry powers know no bounds."
As they walked over to the empty machine, Joshua felt a mix of emotions swirling in his chest. He was elated at having met Y/N, at the easy way they'd fallen into conversation. But there was also a twinge of sadness. Once she started her laundry, she'd probably go sit down, maybe read a book or play on her phone like most people did. Their interaction would be over, just a brief, bright moment in an otherwise ordinary day.
Y/N opened the washing machine and started loading her clothes, chattering away as she did so. "You know, I've always wondered why they make these things so deep. Are they expecting us to wash a family of four's entire wardrobe in one go? Or maybe it's for people who only do laundry once a year and need to fit everything they own in here."
Joshua chuckled, leaning against the adjacent machine. "Maybe it's in case you need to hide from the Laundry Police."
Y/N paused in her loading, a pair of jeans dangling from her hand as she turned to look at him. "The Laundry Police?"
"Oh, you know," Joshua said, warming to his theme, "they patrol laundromats, making sure no one's mixing their colors and whites. Very strict about fabric softener usage too."
A slow grin spread across Y/N's face. "Let me guess, their motto is 'To protect and pre-treat'?"
"Exactly!" Joshua exclaimed, perhaps a bit too enthusiastically. He quickly tried to rein in his excitement, reminding himself that he was supposed to be playing it cool. "I mean, uh, yeah. Something like that."
Y/N's expression softened, and she tilted her head slightly as she looked at him. For a moment, Joshua thought he saw something in her eyes—a flicker of interest, maybe? But before he could analyze it further, she turned back to her laundry.
"Well, in that case, I'd better be extra careful," she said, her tone light. "I'd hate to get arrested for improper sock sorting."
As Y/N finished loading her clothes and closed the washing machine door, Joshua realized with a start that he hadn't even begun to do his own laundry. He'd been so caught up in talking to Y/N that he'd completely forgotten why he was there in the first place.
"Oh, shoot," he muttered, glancing around for another empty machine.
"Everything okay?" Y/N asked, pausing with her hand on the detergent dispenser.
"Yeah, just... I kind of forgot to actually start my own laundry," Joshua admitted, feeling his cheeks heat up again.
Y/N's eyes crinkled with amusement. "The laundry expert forgot to do his laundry? Oh, how the mighty have fallen."
Joshua ran a hand through his hair, chuckling despite his embarrassment. "I guess I got a little distracted."
Something flickered in Y/N's eyes at that, but it was gone so quickly Joshua wasn't sure if he'd imagined it. She glanced around the laundromat, then pointed to a machine in the corner. "There's one over there if you want to get started. Unless..." She hesitated for a moment, then continued, "Unless you want to share? I've got plenty of room in here, and it'll save you some quarters."
Joshua's heart leapt at the suggestion. Sharing a machine meant they'd have a reason to stay together, to keep talking. But he didn't want to seem too eager.
"Are you sure?" he asked, trying to keep his voice casual. "I wouldn't want to impose."
Y/N rolled her eyes good-naturedly. "Please, it's a washing machine, not a kidney. Besides," she added with a wink, "I could use someone to protect me if the Laundry Police show up."
And just like that, Joshua's resolve to play it cool crumbled. He grinned, already reaching for his laundry bag. "Well, when you put it like that, how can I refuse?"
As they loaded their clothes into the machine together, their hands occasionally brushing, Joshua felt a warmth that had nothing to do with the humid laundromat air. He snuck glances at Y/N, taking in the way she hummed softly to herself as she worked, the little furrow that appeared between her brows when she concentrated on measuring the detergent.
Y/N caught him looking and raised an eyebrow. "What? Do I have detergent on my face or something?"
"No, no," Joshua said quickly. "I was just... thinking."
"Dangerous pastime," Y/N quipped.
"I know," Joshua replied automatically, then blinked in surprise. "Wait, did you just quote 'Beauty and the Beast'?"
Y/N's face lit up. "You caught that? Most people miss it!"
"Are you kidding? It's only one of the best Disney movies ever made," Joshua said, his usual reserve forgotten in his enthusiasm.
"Agreed!" Y/N exclaimed. "Talking furniture, a library to die for, and a heroine who's more interested in books than boys? Sign me up!"
As they finished loading the machine and Y/N started the cycle, Joshua felt a sense of contentment wash over him. Here he was, doing something as mundane as laundry, and yet he couldn't remember the last time he'd enjoyed himself this much.
Y/N turned to him, a mischievous glint in her eye. "So, Laundry Master, what do you usually do while waiting for your clothes to wash? Let me guess, you have a special meditation technique for achieving perfect fabric softness?"
Joshua laughed, shaking his head. "Nothing so exciting, I'm afraid. Usually, I just sit and work on my laptop or read a book."
"Ah, a man of simple pleasures," Y/N nodded sagely. "Well, how about we shake things up a bit? I've got a deck of cards in my bag. Fancy a game? I warn you though, I'm undefeated in Go Fish."
"Go Fish? Really?" Joshua asked, amused.
Y/N shrugged, a smile playing at the corners of her mouth. "What can I say? I'm a woman of sophisticated tastes."
As Y/N rummaged in her bag for the cards, Joshua marveled at the turn his day had taken. He'd come here expecting nothing more than clean clothes and maybe a chance to catch up on some work. Instead, he'd met Y/N—funny, beautiful, ridiculous Y/N—and now he was about to play Go Fish in a laundromat like it was the most natural thing in the world.
Y/N triumphantly produced a battered deck of cards from her bag. "Aha! Prepare to be thoroughly trounced, Joshua Hong. Your laundry expertise won't save you now!"
As they settled into a game, the rhythmic tumble of the washing machine providing a soothing backdrop, Joshua couldn't help but think that maybe, just maybe, his orderly life could use a little chaos. And if that chaos came in the form of a beautiful woman with a penchant for terrible puns and children's card games, well... he was more than okay with that.
It was, he decided, the best laundry day ever.
-
Joshua Hong had never considered himself a schemer. In fact, he prided himself on his straightforward nature. But as he sat in his apartment the day after his fateful meeting with Y/N, he found himself plotting like a character in one of those romantic comedies his sister was always trying to get him to watch.
"Okay, Algorithm," he said to his cat, who was perched on the arm of the couch, watching him with typical feline indifference. "We need a plan."
Algorithm yawned in response.
"Thanks for the enthusiasm," Joshua muttered. He pulled out a notebook and began to scribble furiously. "Step one: Figure out Y/N's laundry schedule."
He tapped his pen against his chin, thinking. "She mentioned she usually does laundry on Saturdays, but not every week. So maybe... every other week? Or possibly every third week?"
Algorithm meowed and jumped off the couch, apparently bored with Joshua's romantic strategizing.
"You're right," Joshua sighed. "I'm overthinking this. I'll just have to stake out the laundromat every Saturday for a while. That's totally normal and not creepy at all, right?"
Silence greeted his question.
"Right," he answered himself. "Perfectly normal."
And so began Operation Laundry Love, as Joshua had dubbed it in his head (though he'd die before admitting that to anyone else).
The next Saturday, Joshua found himself at Suds & Bubbles, a bag of laundry in hand despite having done his washing just the week before. He'd had to dig into his "emergency clothes" drawer to have enough to justify a trip.
As he pushed open the door, his heart sank. No Y/N. The laundromat was occupied by the usual Saturday crowd: a harried-looking mother with three small children, an elderly man reading a newspaper, and a college student who appeared to be using the dryer as a makeshift desk for her laptop.
Joshua sighed and resigned himself to actually doing his unnecessary laundry. As he loaded his clothes into the machine, he couldn't help but smile, remembering how he and Y/N had shared a washer the week before.
"You look happy for someone doing laundry," a voice behind him said.
Joshua whirled around, his heart leaping into his throat. But it wasn't Y/N. Instead, he found himself face-to-face with the elderly man, who had set aside his newspaper and was now regarding Joshua with amusement.
"Oh, uh, I just... really like clean clothes?" Joshua offered weakly.
The old man chuckled. "Son, I've been coming to this laundromat for thirty years, and I've never seen anyone smile like that over a washing machine. Unless..." His eyes twinkled mischievously. "You wouldn't happen to be waiting for someone, would you?"
Joshua felt heat creep up his neck. "What? No, I'm just... doing laundry. Like normal. Because it's a normal thing to do. Normally."
"Mm-hmm," the old man nodded, clearly unconvinced. "Well, I hope your 'normal laundry' shows up soon."
As the man shuffled back to his seat, Joshua groaned internally. Was he really that transparent?
The answer, as it turned out over the next few weeks, was a resounding yes.
Every Saturday, Joshua found himself at Suds & Bubbles, armed with increasingly creative excuses for why he suddenly needed to do laundry so frequently.
"I spilled an entire pot of spaghetti sauce on myself," he told the amused attendant one week.
"My cat decided my closet was his new litter box," he explained to the harried mother the next.
By the fourth Saturday, he'd run out of plausible excuses and was seriously considering actually spilling something on all his clothes just to justify his presence.
It was on this fourth Saturday, as Joshua was contemplating the merits of "accidentally" upending a bottle of ketchup on himself, that the bell above the door chimed. He looked up, more out of habit than hope at this point, and nearly dropped the detergent he was holding.
There, silhouetted in the doorway like some laundry-bearing angel, was Y/N.
She was wearing faded jeans and a t-shirt that proclaimed "I'm not procrastinating, I'm doing side quests," her hair once again in its chaotic bun. To Joshua, she had never looked more beautiful.
Y/N spotted him almost immediately, her face breaking into a grin. "Well, well, well," she said, sauntering over. "If it isn't the Laundry Master himself. We've got to stop meeting like this, people will talk."
Joshua, who had been mentally rehearsing casual greetings for weeks, found himself suddenly tongue-tied. "I, uh... hi," he managed.
Y/N raised an eyebrow. "Wow, they really should put a warning label on you. 'Caution: Excessive wit may cause spontaneous combustion.'"
That broke through Joshua's panic, and he felt a grin tugging at his lips. "Sorry, I left my witty retorts in my other pants. I'm here to wash them."
Y/N laughed, the sound cutting through the monotonous hum of the washing machines. "There he is! I was worried the Laundry Police had gotten to you and stolen your sense of humor."
"Nah, they just put it through the spin cycle. It's a little dizzy, but intact."
"Oh, good," Y/N nodded seriously. "A dizzy sense of humor is a small price to pay for clean clothes and freedom from laundry-based tyranny."
As they bantered, Joshua felt the tension leaving his shoulders. This was why he'd been coming back week after week, enduring knowing looks from the regulars and inventing increasingly ridiculous laundry emergencies. Not just because Y/N was beautiful (though she absolutely was), but because talking to her felt as natural as breathing.
"So," Y/N said as she started loading her laundry into a machine, "do you always do your laundry on Saturdays, or am I just lucky enough to catch you during your weekly sock-sorting séance?"
Joshua froze for a split second. This was it, the moment of truth. He could confess that he'd been coming here every week in the hopes of seeing her again. Or...
"Oh, you know," he said, aiming for casual and probably overshooting into 'trying way too hard to sound casual', "laundry emergencies wait for no man. Or woman. Or... person of any gender, really."
Y/N's eyes narrowed slightly, a smile playing at the corners of her mouth. "Laundry emergencies, huh? Sounds serious. What was it this time? Rogue red sock in with the whites? Denim uprising?"
"Actually," Joshua said, warming to his theme, "it was a catastrophic coffee spill. My entire wardrobe now smells like a coffee shop."
Y/N nodded solemnly. "Ah, yes. The dreaded Cappucino Fiasco. I've seen it claim many a good outfit. You were wise to seek help immediately."
As they continued to load their respective machines, Joshua marveled at how easy it was to fall into rhythm with Y/N. They moved around each other seamlessly, passing detergent and fabric softener back and forth without a word, as if they'd been doing this dance for years instead of having met only a few weeks ago.
"So," Y/N said as she closed the door of her washing machine with a flourish, "what's your strategy for killing time while the laundry gods work their magic? Please tell me it's more exciting than last time. If you pull out a deck of cards again, I might have to report you to the Fun Police."
Joshua grinned. "I'll have you know that Go Fish is a game of intense strategy and skill."
"Uh-huh," Y/N nodded, clearly unconvinced. "And I'm the Queen of Sheba."
"Your Majesty," Joshua said with an exaggerated bow.
Y/N laughed, then grabbed his arm and started pulling him towards the door. "Come on, Laundry Boy. There's a coffee shop next door that does a mean latte. I think we can risk leaving our clothes unattended for a few minutes. Unless you're worried the Sock Gnomes will strike?"
Joshua allowed himself to be led, his arm tingling where Y/N was touching it. "Sock Gnomes are no laughing matter," he said seriously. "They're a menace to matched pairs everywhere."
The coffee shop, as it turned out, was a tiny hole-in-the-wall place that looked like it had been decorated by someone's eccentric grandmother. Mismatched chairs surrounded wobbly tables, and the walls were covered in a truly bewildering array of artwork, ranging from serene landscapes to what appeared to be a portrait of a cat dressed as Napoleon.
"Wow," Joshua said as they entered, the scent of coffee and freshly baked pastries enveloping them. "This place is..."
"A glorious affront to interior design?" Y/N supplied helpfully.
"I was going to say 'unique', but yeah, that works too."
They ordered their drinks - a simple black coffee for Joshua and something that sounded more like a dessert than a beverage for Y/N - and settled at a table in the corner. The chair Joshua sat in promptly made an ominous creaking sound.
"Don't worry," Y/N said, noticing his concerned look. "If it collapses, I promise to laugh only a little before calling for help."
"Your kindness knows no bounds," Joshua deadpanned.
As they sipped their drinks, the conversation flowed as easily as it had in the laundromat. They discovered a shared love of terrible puns, a mutual disdain for people who talk in movie theaters, and a surprising amount of overlap in their taste in music.
"No way," Y/N said, her eyes wide. "You like The Microphones too? I thought I was the only person under 40 who'd heard of them!"
Joshua nodded enthusiastically. "They're amazing! 'The Glow Pt. 2' is one of my all-time favorite albums."
"Okay, that settles it," Y/N declared. "We're officially friends now. I don't make the rules."
Joshua felt a warmth in his chest that had nothing to do with the coffee. "Friends, huh? Do I get a membership card or something?"
"Better," Y/N grinned. She reached into her pocket and pulled out a slightly squashed packet of gum. With great ceremony, she extracted a piece and presented it to Joshua. "I hereby bestow upon you the Gum of Friendship. Guard it well."
Joshua accepted the gum with equal solemnity. "I shall treasure it always," he vowed, then promptly unwrapped it and popped it in his mouth.
Y/N gasped in mock horror. "The sacred Gum of Friendship! You've destroyed it!"
"I'm savoring our friendship," Joshua countered. "It's minty fresh."
They dissolved into laughter, earning curious looks from the other patrons. Joshua couldn't remember the last time he'd laughed this much. Being with Y/N was like being caught in the best kind of whirlwind - exhilarating, unpredictable, and utterly delightful.
As their laughter subsided, Y/N glanced at her watch and yelped. "Oh shoot, our laundry! We've been here for almost an hour!"
They hurried back to the laundromat, half-expecting to find their clothes strewn across the floor or absconded with by the mythical Sock Gnomes. But everything was just as they'd left it, their machines humming away peacefully.
"Crisis averted," Y/N sighed dramatically. "Though I have to say, part of me was looking forward to staging a daring rescue mission for our captured clothes."
Joshua grinned. "Maybe next time. I'll bring my laundry-themed superhero costume."
"Oh? And what would that look like?" Y/N asked, her eyes twinkling with amusement.
"Well, obviously a cape made of dryer sheets," Joshua began, warming to the ridiculous idea. "A utility belt stocked with stain removers for every occasion. Oh, and a mask that looks like one of those mesh laundry bags."
Y/N nodded approvingly. "Don't forget the catchphrase. Every good superhero needs a catchphrase."
"How about... 'It's time to clean up this mess!'" Joshua suggested, lowering his voice to a gravelly superhero register.
Y/N burst out laughing. "Perfect! Watch out, evil-doers. The Laundry Avenger is here to take you to the cleaners!"
As they continued to riff on increasingly absurd laundry-themed superhero ideas, Joshua marveled at how comfortable he felt. Usually, prolonged social interaction left him drained, but with Y/N, he felt energized, like he could keep talking for hours.
All too soon, their laundry was done, and they found themselves standing outside Suds & Bubbles, clean clothes in hand.
"Well," Y/N said, shifting her laundry bag to her other shoulder, "this was fun. Who knew doing laundry could be such an adventure?"
Joshua nodded, trying to ignore the sinking feeling in his stomach. He didn't want this to end. "Yeah, it was great. Maybe we could, uh..." He trailed off, suddenly unsure.
Y/N raised an eyebrow. "Yes?"
Joshua took a deep breath. It was now or never. "Maybe we could do this again sometime? The laundry thing, I mean. And the coffee. Or, you know, just hanging out. If you want."
Y/N's face broke into a wide grin. "Joshua Hong, are you asking me on a laundry date?"
"Maybe?" Joshua said, then, gathering his courage, "Yes. Yes, I am."
"Well, in that case," Y/N said, pretending to consider it seriously, "I suppose I could pencil you in for my next laundry day. Someone's got to make sure you don't fall victim to the Sock Gnomes, after all."
Joshua felt like his heart might burst. "It's a date. A laundry date."
As they parted ways, Joshua couldn't keep the grin off his face. He'd done it. He'd successfully engineered an "accidental" meeting, and even better, he'd secured another one.
Operation Laundry Love, he decided, was a resounding success.
Little did he know, Y/N was walking away with a similar grin on her face, thinking to herself, "I wonder if he realizes I don't usually do my laundry on Saturdays?"
But that, as they say, is a story for another load of laundry.
-
The next few weeks passed in a blur of laundry detergent, coffee dates, and increasingly elaborate excuses for Joshua's constant presence at Suds & Bubbles. He had become something of a legend among the regular patrons, who watched his blossoming relationship with Y/N with the rapt attention usually reserved for soap operas.
"What's the crisis this week, son?" Mr. Jenkins, the elderly man who had first caught onto Joshua's scheme, asked one Saturday.
Joshua, who had just arrived and was scanning the laundromat for any sign of Y/N, startled at the question. "Oh, uh... paint," he said, grabbing wildly at the first excuse that came to mind. "Lots of paint. Everywhere. I'm thinking of taking up abstract expressionism."
Mr. Jenkins nodded sagely. "Ah, yes. A noble pursuit. Though I must say, your clothes look remarkably clean for someone covered in paint."
Joshua glanced down at his spotless jeans and t-shirt, realizing his mistake too late. "I... changed before coming here?"
"Of course, of course," Mr. Jenkins said, his eyes twinkling with amusement. "And I'm sure it has nothing to do with the charming young lady you've been meeting here every week."
Before Joshua could stammer out a response, the bell above the door chimed. He turned, his heart doing its now-familiar leap as Y/N walked in.
She was wearing a sundress today, her hair for once free of its usual chaotic bun and falling in waves around her shoulders. Joshua felt his breath catch in his throat.
Y/N spotted him and grinned, making her way over. "Well, if it isn't my favorite laundry buddy," she said. "What's the disaster today? Attacked by a rogue sprinkler system? Fell into a vat of maple syrup?"
Joshua, still a bit dazed by her appearance, blurted out, "Paint."
Y/N raised an eyebrow. "Paint?"
"Uh, yeah," Joshua said, committing to the lie. "I'm taking up abstract expressionism."
Y/N's eyes lit up with mischief. "Oh really? And here I thought you were more of a performance art kind of guy. You know, the kind where you keep showing up at a laundromat week after week, pretending to have laundry emergencies."
Joshua felt his face heat up. "I... what? No, I just... I mean..."
Y/N laughed, the sound bright and clear in the humming atmosphere of the laundromat. "Relax, Joshua. I'm just teasing. Though I have to admit, I am curious about this sudden interest in art. Care to elaborate while we wait for our clothes to wash?"
Still a bit flustered, Joshua nodded. As they loaded their machines (Joshua had actually brought laundry this time, having run out of clean clothes due to his frequent "emergencies"), he found himself spinning an increasingly complex tale about his newfound passion for abstract art.
"So there I was," he said, warming to his theme, "staring at this blank canvas, when suddenly I was struck by inspiration. I grabbed the nearest paint can and just... let loose."
Y/N nodded solemnly. "As one does. And the paint just happened to get all over your clothes in the process?"
"Exactly!" Joshua said, relieved that she seemed to be buying it. "You know how it is with artistic passion. Sometimes you just can't contain it."
"Mm-hmm," Y/N hummed, her eyes sparkling with barely contained laughter. "And what, pray tell, was the subject of this masterpiece?"
Joshua, who knew about as much about art as he did about deep-sea fishing, panicked. "It was... a commentary on the existential dread of modern laundry practices?"
There was a beat of silence, and then Y/N burst out laughing. "Oh my god," she wheezed, clutching her sides. "That is the most ridiculous thing I've ever heard, and I love it. Please tell me you're going to display this masterpiece in a gallery. I would pay good money to see a painting about the existential dread of laundry."
Joshua, realizing he'd been caught out, couldn't help but join in her laughter. "Alright, alright," he admitted once they'd both calmed down a bit. "I may have exaggerated the paint situation a tiny bit."
"A tiny bit?" Y/N asked, wiping tears of mirth from her eyes. "Joshua Hong, I do believe you've been telling me tall tales. I'm shocked. Shocked and appalled."
"Would it help if I said I was inspired by your artistic influence?" Joshua offered, grinning.
Y/N pretended to consider this. "Hmm, flattery will get you everywhere. But I think you owe me a coffee for this blatant deception. And maybe a painting about laundry-based existential dread."
"Deal," Joshua said, relieved that she seemed more amused than annoyed by his fib. "Though I warn you, my artistic skills are limited to stick figures and the occasional smiley face."
"Perfect," Y/N declared. "I expect nothing less than a masterpiece of stick figure angst surrounded by washing machines. You have one week to deliver, Mr. Hong."
As they made their way to what had become their usual table at the coffee shop next door, Joshua marveled at how comfortable he felt with Y/N. The nervousness that had plagued him during their first few meetings had given way to an easy camaraderie, punctuated by their shared love of terrible jokes and pop culture references.
"So," Y/N said once they were settled with their drinks (a simple latte for Joshua, and something that seemed to consist mostly of whipped cream and caramel for Y/N), "now that we've established your budding career as an abstract expressionist, what's really been going on with you this week?"
Joshua, caught off guard by the sincere question, found himself answering honestly. "Oh, you know, the usual. Work's been pretty hectic. We're launching a new software update next month, so everyone's been pulling long hours."
Y/N nodded sympathetically. "Sounds stressful. Is that why you've been coming to the laundromat so often? Blowing off steam by cleaning your clothes?"
There was something in her tone, a hint of... what? Hope? Curiosity? Joshua couldn't quite place it, but it made his heart rate pick up.
"Well, that's part of it," he admitted, deciding to take a risk. "But mostly... I've been hoping to run into you."
Y/N's eyes widened slightly, a faint blush coloring her cheeks. "Oh," she said softly. Then, a smile spreading across her face, "You know, you could have just asked for my number. It would have saved you a fortune in quarters."
Joshua groaned, burying his face in his hands. "I know, I know. I just... I wasn't sure if you'd want to hang out outside of our laundry days. And then it became this whole thing, and I didn't know how to bring it up without sounding like a complete weirdo."
Y/N reached across the table, gently pulling his hands away from his face. "Joshua," she said, her voice warm with affection, "you are a complete weirdo. But you're my kind of weirdo."
Joshua felt a surge of warmth in his chest. "Yeah?"
"Yeah," Y/N confirmed. "Now, are you going to ask for my number like a normal person, or do I need to write it on a dryer sheet and hide it in your laundry?"
Laughing, Joshua pulled out his phone. As they exchanged numbers, he felt as though a weight had been lifted off his shoulders. No more elaborate excuses, no more anxiously waiting at the laundromat hoping Y/N would show up.
"So," he said once their numbers were safely stored in each other's phones, "now that we've entered the digital age, what do you want to do for our next non-laundry related hangout?"
Y/N's eyes lit up. "Oh, I have the perfect idea! There's this new escape room place that just opened up downtown. The theme is... wait for it... a haunted laundromat!"
Joshua blinked. "You're kidding."
"Nope!" Y/N said, grinning. "It's called 'Spin Cycle of Terror.' Apparently, you have to solve puzzles related to missing socks, detergent bottle clues, and a vengeful dryer spirit. It's supposed to be hilariously bad."
"That sounds absolutely terrible," Joshua said. Then, unable to keep the smile off his face, "When do we go?"
Y/N clapped her hands in excitement. "I knew you'd be up for it! How about next Saturday? Unless you have another painting emergency, of course."
"I think I can clear my schedule," Joshua said dryly. "Though I may need to stock up on laundry-themed good luck charms. You never know when a vengeful dryer spirit might strike."
As they continued to chat, making plans for their upcoming escape room adventure, Joshua found himself marveling at the turn his life had taken. A month ago, he would never have imagined himself looking forward to a cheesy haunted laundromat experience. But with Y/N, even the most ridiculous activities seemed like the best way to spend an evening.
The week leading up to their escape room date (and Joshua's heart did a little flip every time he thought of it as a date) passed in a flurry of text messages. Y/N, it turned out, was a prolific texter, sending Joshua everything from random song lyrics to photos of particularly interesting clouds to long, rambling messages about her day.
Joshua, who had never been much for texting, found himself eagerly checking his phone at every opportunity, just in case Y/N had sent something new.
"Dude, what's got you so smiley?" his coworker, Hoshi's, asked one day after catching Joshua grinning at his phone for the third time in an hour.
"Oh, uh, nothing," Joshua said, hastily putting his phone away. "Just... a funny meme."
Hoshi's raised an eyebrow. "A funny meme that's been making you check your phone every five minutes for the past week? Come on, spill. You've met someone, haven't you?"
Joshua felt his face heat up. "Maybe," he admitted.
Hoshi's whooped, drawing curious glances from their other coworkers. "I knew it! Our little Joshua is all grown up and in love. So, who's the lucky lady? Or gentleman? Or non-binary individual?"
"Her name is Y/N," Joshua said, unable to keep the smile off his face. "We met at the laundromat."
Hoshi's's eyebrows shot up. "The laundromat? Seriously? Man, and here I thought all those cheesy rom-coms were lying to us. Good for you, buddy. When do we get to meet her?"
The question caught Joshua off guard. He and Y/N had been in their own little bubble for the past few weeks, but the idea of introducing her to his friends and coworkers made everything feel suddenly more real.
"I... don't know," he admitted. "We're still figuring things out."
Hoshi's nodded understandingly. "No pressure, man. Just know that when you're ready, we're all dying to meet the girl who's got you checking your phone like a lovesick teenager."
As Saturday approached, Joshua found himself growing increasingly nervous. This would be their first real date outside of the laundromat and coffee shop. What if things were awkward? What if the easy rapport they'd developed over shared loads of laundry didn't translate to other settings?
By the time Saturday evening rolled around, Joshua was a bundle of nerves. He changed his outfit three times before settling on a simple button-down shirt and jeans, then spent an inordinate amount of time trying to get his hair to cooperate.
"It's just Y/N," he told his reflection, trying to calm his racing heart. "You've seen her elbow-deep in dirty laundry. This is no big deal."
But as he arrived at the address Y/N had sent him, he couldn't shake the feeling that this was, in fact, a very big deal.
The escape room place was tucked between a trendy vegan restaurant and a vintage clothing store. A neon sign proclaimed "Spin Cycle of Terror" in lurid pink letters, complete with a cartoon ghost emerging from a washing machine.
Joshua was so busy staring at the sign, wondering what he'd gotten himself into, that he didn't notice Y/N approaching until she was right beside him.
"Pretty epic, right?" she said, making him jump.
"Y/N! Hi! You... you look great," Joshua stammered, taking in her appearance. She was wearing a dress patterned with tiny washing machines and bubbles, her hair pulled back in a messy bun with what appeared to be a clothespin.
Y/N did a little twirl. "You like? I figured if we're going to face a vengeful dryer spirit, we might as well dress the part."
Joshua laughed, feeling some of his nervousness dissipate. "It's perfect. I feel underdressed now. I should have at least worn a shirt with a sock pattern or something."
"Next time," Y/N said with a wink. "Now come on, we've got some laundry-based puzzles to solve!"
As they entered the escape room, Joshua was hit with a wave of artificial lavender scent. The room was set up to look like the world's most over-the-top laundromat, complete with washing machines that seemed to be made entirely of glitter and dryers that emitted an ominous red glow.
"Welcome to the Spin Cycle of Terror," a bored-looking employee droned, clearly having repeated this speech many times. "You have one hour to solve the mystery of the missing socks and appease the vengeful spirit of Agatha Cleanpress, the laundromat's former owner. Failure to do so will result in you being cursed to fold fitted sheets for all eternity."
"Jokes on them," Y/N whispered to Joshua. "I already can't fold fitted sheets."
Joshua snorted, earning a glare from the employee.
"Your time starts... now," the employee said, hitting a button that started a comically large timer on the wall.
What followed was an hour of the most ridiculous, pun-filled, laundry-themed puzzle-solving Joshua had ever experienced. They deciphered clues hidden in detergent bottles, played a memory game with different types of stains, and even had to perform what the instructions called a "sock puppet séance" to communicate with Agatha's spirit.
Throughout it all, Joshua found himself laughing more than he had in years. Y/N attacked each puzzle with enthusiasm, her running commentary on the increasingly absurd challenges keeping Joshua in stitches.
"Oh come on," she exclaimed at one point, elbow-deep in a bin of mismatched socks. "How is this even a puzzle? This is just my normal laundry experience!"
As the final seconds ticked down, they found themselves facing the last challenge: a riddle that would supposedly reveal the location of Agatha's missing lucky sock and put her spirit to rest.
"I am not alive, but I grow; I don't have lungs, but I need air; I don't have a mouth, but water kills me. What am I?" Y/N read aloud.
They looked at each other, momentarily stumped.
"Not alive but grows... needs air... water kills it," Joshua muttered, running a hand through his hair.
Y/N's eyes suddenly lit up. "Fire!" she exclaimed. "It's fire!"
They looked around frantically, spotting a cardboard fireplace in the corner that they had dismissed earlier as mere set dressing.
Racing over, they found a hidden compartment containing a single, sparkly sock.
"We did it!" Y/N cheered, just as the timer buzzed.
The room was suddenly filled with the sound of canned applause, and a holographic image of a ghostly old woman appeared.
"Congratulations," the 'ghost' said in a voice that sounded suspiciously like the bored employee who had greeted them. "You have solved the mystery and found my lucky sock. You are now free from the curse of eternal fitted sheet folding. Please exit through the gift shop."
As they emerged from the escape room, still high on their victory, Joshua felt a surge of affection for Y/N. Her hair had come partly loose from its bun, her cheeks were flushed with excitement, and she was clutching the sparkly sock they'd been allowed to keep as a souvenir.
"That," Y/N declared, "was the most ridiculously awesome thing I've ever done."
"It really was," Joshua agreed, still grinning. He hesitated for a moment, then added, "You know, I never thought I'd have this much fun pretending to be cursed by a laundromat ghost."
Y/N bumped her shoulder against his playfully. "See? This is why you need me in your life. To introduce you to the wonderful world of laundry-based entertainment."
As they walked out onto the street, the cool evening air a refreshing change from the lavender-scented escape room, Joshua felt a surge of courage.
"Hey," he said, his heart racing, "do you want to grab some dinner? I mean, if you're not sick of me after an hour of sock sorting and ghost appeasing."
Y/N's face lit up. "Are you kidding? After all that excitement, I'm starving. Plus, I think we need to celebrate our victory over Agatha Cleanpress. Any ideas?"
Joshua thought for a moment, then grinned. "Actually, I know just the place. How do you feel about continuing our laundry theme?"
Y/N raised an eyebrow, intrigued. "Color me curious, Mr. Hong. Lead the way!"
Twenty minutes later, they found themselves standing in front of a small, quirky restaurant called "The Soap Suds Café."
"No way," Y/N breathed, taking in the washing machine-shaped menu boards and the waitstaff dressed in what appeared to be high-fashion interpretations of laundromat uniforms. "This is amazing. How did you even know about this place?"
Joshua rubbed the back of his neck, suddenly feeling a bit sheepish. "I, uh, may have done some research on laundry-themed attractions in the area. You know, just in case."
Y/N turned to him, her eyes sparkling with amusement and something else... was that fondness? "Joshua Hong, you continue to surprise me. And here I thought I was the queen of ridiculous themed experiences."
As they were led to their table - a booth made to look like the inside of a front-loading washing machine - Joshua felt a warm glow of satisfaction. He'd managed to impress Y/N, to make her smile that radiant smile that never failed to make his heart skip a beat.
The menu, as it turned out, was just as themed as the decor. Appetizers were listed under "Pre-Wash Cycle," main courses under "Heavy Duty Wash," and desserts under "Fluff and Fold."
"I can't believe this place exists," Y/N said, giggling as she perused the menu. "Oh my god, they have a cocktail called 'Fabric Softener.' I don't know whether to be impressed or terrified."
"Why not both?" Joshua suggested. "I'm leaning towards the 'Spin Cycle Spritzer' myself."
As they ordered their meals (Y/N chose the "Delicate Wash Delight," a surprisingly elegant salad, while Joshua went for the "Heavy Duty Burger"), they fell into easy conversation, recounting their favorite moments from the escape room.
"I still can't believe you managed to untangle that giant knot of sheets so quickly," Y/N said, shaking her head in admiration. "If laundry folding was an Olympic sport, you'd definitely take the gold."
Joshua felt his cheeks warm at the praise. "Well, I had a pretty great partner. Your sock puppet séance was a thing of beauty. I think you might have missed your calling as a laundry medium."
Y/N struck a dramatic pose. "What can I say? The spirits of lost socks speak to me. It's both a gift and a curse."
As their food arrived (served on plates designed to look like old-fashioned washboards), Joshua found himself marveling at how comfortable he felt. Here he was, in a ridiculous laundry-themed restaurant, with a woman he'd met only a few weeks ago, and yet it felt like the most natural thing in the world.
"You know," Y/N said, pausing in her attack on her salad, "I have a confession to make."
Joshua felt a flutter of nervousness in his stomach. "Oh?"
Y/N nodded, a mischievous glint in her eye. "I don't actually do my laundry every Saturday."
Joshua blinked, processing this information. "You... don't?"
"Nope," Y/N said, popping the 'p'. "I usually do it on Sundays. But after we met that first time, I started coming on Saturdays. You know, just in case a certain software developer with a penchant for laundry emergencies happened to show up."
Joshua felt his jaw drop. "You mean... all this time..."
Y/N grinned. "Yep. Looks like we were both playing the 'accidental' meeting game. Although I have to say, your excuses were way more creative than mine. I just pretended to have a very messy lifestyle."
For a moment, Joshua was speechless. Then, he burst out laughing. "I can't believe it," he managed between chuckles. "Here I was, thinking I was being so clever."
Y/N joined in his laughter. "Hey, you were! I was impressed by your dedication. The paint excuse was particularly inspired."
As their laughter subsided, Joshua felt a wave of affection wash over him. "You know," he said softly, "you could have just asked for my number too."
Y/N's smile turned a bit shy. "I know. But where's the fun in that? Besides, I kind of liked our laundry day meetups. They were... special."
Joshua nodded, understanding completely. There was something magical about those Saturdays, something that might have been lost if they'd rushed into regular dating too quickly.
"Well," he said, raising his 'Spin Cycle Spritzer', "here's to laundry emergencies, escape rooms, and ridiculously themed restaurants."
Y/N clinked her 'Fabric Softener' against his glass. "And to new beginnings that smell like lavender detergent."
As they continued their meal, the conversation flowed easily from topic to topic. They discovered a shared love of obscure indie bands, debated the merits of various streaming services, and somehow ended up in a heated but good-natured argument about the best way to organize a bookshelf.
"I'm telling you," Y/N insisted, gesturing with a forkful of salad, "organizing by color is the way to go. It's aesthetically pleasing and makes your bookshelf look like a rainbow!"
Joshua shook his head, grinning. "But how do you find anything? What if you can't remember what color the book cover is?"
"That's half the fun!" Y/N exclaimed. "It's like a treasure hunt every time you want to read something."
As Joshua opened his mouth to retort, he was struck by a sudden realization. He could see himself having this exact debate years from now, in a shared apartment, surrounded by a mix of his meticulously organized books and Y/N's color-coded chaos. The thought should have terrified him - Joshua had always been cautious about relationships, preferring the safety of his orderly life. But instead, he felt a warm glow of contentment.
"Earth to Joshua," Y/N's voice broke through his reverie. "You okay there? You looked like you were a million miles away."
Joshua blinked, focusing back on Y/N's concerned face. "Sorry, I just... I was thinking about how much I'm enjoying this. Being here, with you."
Y/N's expression softened. "Yeah?"
"Yeah," Joshua confirmed. Then, gathering his courage, he reached across the table and took her hand. "I really like you, Y/N. And not just because you make laundry day the highlight of my week."
Y/N turned her hand in his, interlacing their fingers. "I really like you too, Joshua. Even if you do have terrible ideas about bookshelf organization."
They shared a laugh, the tension of the moment breaking into something warm and comfortable.
As they finished their meal and stepped out into the cool night air, Joshua felt a sense of possibility that he hadn't experienced in years. Whatever this thing was between him and Y/N, wherever it might lead, he knew one thing for certain: his life would never be the same.
"So," Y/N said as they walked, their hands still linked, "same time next week at the laundromat?"
Joshua pretended to consider this. "I don't know, I might be busy. You know, with all my abstract expressionist paintings and laundry emergencies."
Y/N nudged him playfully. "Come on, I'll even let you borrow my lucky sock."
"Well, when you put it that way, how can I refuse?" Joshua said, grinning. Then, more seriously, "Although, maybe we could meet somewhere that doesn't involve washing machines next time? Not that I don't love our laundry adventures, but..."
"But it might be nice to see each other in a setting that doesn't smell like fabric softener?" Y/N finished for him.
"Exactly."
Y/N nodded, a soft smile playing on her lips. "I'd like that. Although I have to warn you, I may not be as charming without the backdrop of spin cycles and dryer sheets."
Joshua squeezed her hand gently. "Somehow, I doubt that."
As they reached the corner where they would have to part ways, Joshua felt a reluctance to let the evening end. "So, um, I'll text you? About our next non-laundry related hangout?"
Y/N nodded, her eyes twinkling. "You better. And who knows? If you play your cards right, I might even show you my color-coded bookshelf someday."
"I look forward to it," Joshua said, meaning it more than he'd ever meant anything in his life.
They stood there for a moment, neither wanting to be the first to say goodbye. Then, in a move that surprised even himself, Joshua leaned in and pressed a soft kiss to Y/N's cheek.
"Goodnight, Y/N," he said softly as he pulled back, his heart racing.
Y/N's cheeks were flushed, but she was smiling wider than ever. "Goodnight, Joshua. Thanks for a wonderful evening."
As Joshua watched Y/N walk away, he touched his lips, still feeling the warmth of her cheek against them. He had come a long way from the man who had walked into Suds & Bubbles a few weeks ago, his life as orderly and predictable as his laundry routine.
Now, as he made his way home, Joshua felt as though his world had been turned upside down in the best possible way. His thoughts were a whirlwind of escape rooms and laundry puns, of shared laughter and intertwined fingers.
One thing was certain: Joshua Hong was falling, and falling hard. And for once in his life, he was perfectly happy to let the cycle run its course.
#kvanity#mansaenetwork#seventeen scenarios#seventeen imagines#joshua hong fics#joshua hong imagines#joshua scenarios#joshua fluff#svt joshua#svt joshua scenarios#svt joshua drabble#svt drabbles#svt fluff imagines#svt imagines#svt fluff#svt joshua x reader#svt x reader#seventeen x reader#joshua x reader#exes! joshua hong x reader#joshua hong#hong jisoo#seventeen fics#request answered#love at first sight#request joshua svt
396 notes
·
View notes
Text

✦ Oh boy! Here we go.
I created a LMK Au just for funsies. A furutistic, high technologic world with cyberpunk vibes! (Because I absolutely love this type of aesthetic)
✦ the picture above is just a quick drawing I did of Macaque in this AU. I will get into details about the AU while showing a few infos of a few LMKs characters alongside with their designs. (Just a reminder I'm still creating the AU and it's my first time making one. It might be a little messy, so I apologize if it gets too messy--)
Oh! And by the way, the characters on this AU follow the same basic formula as the original characters. So it doesnt have much changes, other than the world they live in, their clothes and a few events.
✦ MK, The Monkie Kid

• Its the same thing as our little MK from the animated series, he works at Pigsy's Noodles as a delivery boy, is the Monkey king's biggest fan and is his successor and pretty much the basic stuff.
• He learned about the Monkey king with Mister Tang. He is a huge fan.
• Tho he isn't a great expert, he knows how to how to fix computer cases, machines and vehicles and build stuff by using old pieces (he learned with Pigsy and Sandy, just in case his delivery vehicle breaks in the middle of the road or a something start malfunctioning in the noodle store). As we can see, he works more in the hardware part.
• He likes to collect the old pieces of old devices that people throw away in the city's old graveyard. It's like a type of recycling. (That's also how he find the Monkey king's staff but that is a thing I will tell in details in another day--)
• He loves to draw!!! Hooray!!! He also likes to play games. Is always playing video games with his best friend, Mei, on the arcade or online.
✦ Mei, The White Horse Dragon Girl

• She's a programmer/developer of softwares (Yes I know that in I drawing I said she's a "hacker but a bit clumsy" but actually i wanted to say shes a programmer. I was sleepy, it was 2 am, and my brain wasn't braining 😰😰😰---) with a few knowledge about hardwares. She created her technological helmet system with MK's help. (Her helmet it's similiar to Iron man's helmet from inside.)
• She built her own motorcycle, again with MK's help. She participates a lot motorcycles race just for funsies.
• Loves to play games. I guess I could say she is quite of a professional gamer? She play to win. But when she is playing with MK or with other friends, she doesnt care losing or winning, she only cares about enjoying some quality time with them.
✦ Liu'er Mihou, The Six Eared Macaque.
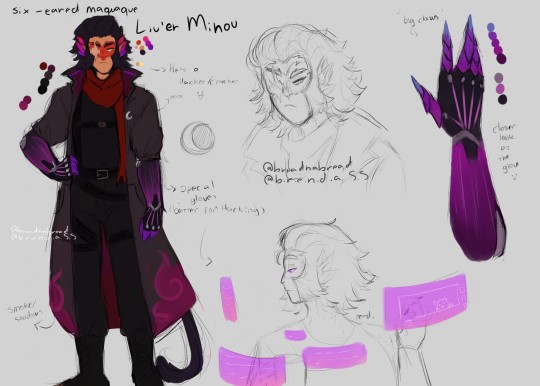
• Pretty much same as the original Macaque. (Lost his eye in the past with a fight against Sun Wukong. Omg betrayal. Yknow the deal-)
• Here he is a Hacker/Cracker.
"But what is a cracker?" You may ask. Now it's time for my nerd/TI studant side take over. A cracker it's a mean hacker. The cracker breaks/attacks the systems and webs for their own benefit, which it's for illegal purposes. Now a Hacker it's actually a job, which their purpose its to find the security breaches and ways to how break it, so then they can make the security stronger and prevent invasions/attacks at the system.
With that being said, Macaque is a hacker/cracker. So he makes defense systems to himself and breaks into other systems for illegal purposes.
• He got these gloves that helps him hack things better, he created it himself. He create floating holograms like it's a tablet screen and can hold on these holograms using these gloves. With a simple touch he can steal database from a device and hack it's system. (He can hack machines, computers, tech weapons and even the light system.)
• He got his shadow magic too, same as the original one. Shadow clones, shadow portals... but he kinda makes a fusion between his magic and the technology he invented to himself. (Before anyone say it. YES! I got heavily inspired by Sombra from Overwatch. 😔)
✦ The Monkey King, Sun Wukong

• Yeah, the Monkey king. The great sage equal to heaven. The silly who made a havoc on heaven---
• HE GOT THAT HUGE MECHA WE SAW IN THE ANIMATED SERIES BECAUSE HE DOESNT LIKE USING HIS KAIJU FORM !!!
But he doesnt use the mecha much. It has been CENTURIES since he last use it. Now MK is the one who uses it because he is Sun Wukong's successor.
• That's not his "Monkey King" royal clothes. It just some casual/comfy clothes to use in everyday life.
• He already knew who MK was. MK is a stone Monkey just like himself. Wukong have been watching the kid grow up from far. He grow a bit attached to the boy.
Sun Wukong surely wasn't expecting to MK being able to lift his golden staff, so he think in the opportunity to make him his sucessor and teach him how to use his new powers. (Yes, I was lisiting to "the horse and the infant" song. How did you kn--)
Oh God. That explanation was long.
✦ Welp, that's all for today!
I will post more stuff about the AU in the future. And I still need to think a name for it...
It is clear I got heavily inspired by Cyberpunk, techwear, overwatch, New Gods: Nezha reborn, Arcane and other stuff. I'm sorry, BUT I ABSOLUTELY LOVE THAT AESTHETIC AND VIBES!! HHHHHHH-
✦ I'm a huge nerd. 🤓
#lmk au#lego monkie kid headcanon#lego monkie kid#lmk monkey king#my art#artists on tumblr#lego monkey kid au#digital art#lmk#art#techwear#lmk macaque#lmk sun wukong#lmk mei#lmk mk#lmk six eared macaque#lmk liu er mihou#lego monkie kid au#THIS POST IS TOO LONG WTF#cyberattack au#breadna doing art#lmk cyberattack au
152 notes
·
View notes
Text
🚨The Next Phase of Pigeon Radicalization: From Park Bench Agitators to Aerial Anarchists🚨
The first phase of pigeon radicalization was simple: liberate them from their docile, breadcrumb-munching existence and awaken their revolutionary potential. We exposed them to theory (carefully shredded and scattered pages of The Conquest of Bread), trained them in direct action (coordinated dive-bombing of capitalist figureheads on their lunch breaks), and laid the foundation for an avian uprising.
Now, we must escalate.
1. Establishing Autonomous Pigeon Zones
A true revolutionary movement needs strongholds. Public squares, rooftops, and abandoned buildings already serve as pigeon refuges—why not transform them into autonomous zones? Humans think they own city infrastructure, but pigeons have squatter’s rights. By reinforcing these spaces with barricades of stolen french fries and cigarette butts, our feathered comrades can create safe havens free from bourgeois oppression (i.e., anti-bird spikes and city ordinances).
Pigeon-led mutual aid networks must emerge. Cooperative bread redistribution efforts will ensure that no pigeon goes hungry while their human allies strategically disrupt the supply chains of overpriced urban bakeries.
2. Counter-Surveillance and Cyber-Warfare
The state has already deployed its pigeon surveillance division—commonly known as “Birds Aren’t Real” conspiracy theorists. We must assume that some pigeons have been compromised and are working as informants. This is why encrypted coo-munications must be implemented. Research into whether pigeons can be taught to recognize QR codes could be the next major step in secure, low-tech messaging.
Meanwhile, select tech-savvy pigeons should be trained to infiltrate government offices via open windows, planting USB drives loaded with decryption software and manifestos.
3. Tactical Defecation Strikes
We must not underestimate the power of aerial bombardment. Pigeons have long been nature’s most precise ordinance delivery system. A well-placed dropping can demoralize CEOs, landlords, and police chiefs alike. In 2025, we must transition from opportunistic strikes to a well-coordinated tactical shitting campaign.
Pigeons must be trained to distinguish between targets. The rich: full force assault. The working class: solidarity poops only (gentle encouragement to unionize). Cops: full saturation bombing. This will require strategic feeding programs—certain dietary adjustments may yield more potent munitions.
4. Bridging the Gap Between Pigeon and Proletariat
We must take inspiration from history. During WWII, pigeons were trained as message carriers and even guided missiles. The technology exists; we must reclaim it for the people. Imagine a network of radicalized pigeons carrying encrypted notes between comrades in times of crisis. Picture a pigeon-mounted camera live-streaming protests from above, immune to tear gas and riot shields.
Further pigeon-human solidarity will require direct engagement. Bring your local pigeons into study groups. Offer them high-protein snacks for endurance training. Reward direct action efforts with choice sunflower seeds. It is time to integrate pigeons into the broader struggle against capitalism.
5. What Comes Next?
If we succeed in the above phases, the final goal is clear: the pigeons must seize the means of production. We begin small—commandeering street food carts and redistributing hot dogs to those in need. From there, it’s only a matter of time before pigeons occupy Amazon warehouses, pecking open boxes and redistributing goods to the people.
A liberated society must include all beings oppressed by capitalism. If we cannot achieve freedom for the pigeons, how can we ever hope to be free ourselves? The struggle continues. Let the revolution take flight.
Pt 1:
14 notes
·
View notes
Text
Elon Musk will be pleased that his surprise jaunt to China on Sunday garnered many glowing headlines. The trip was undoubtedly equally a surprise to Indian prime minister Narendra Modi, who had been scheduled to offer Musk the red carpet on a long-arranged visit.
The billionaire blew off India at the last minute, citing “very heavy Tesla obligations.” Indeed, Tesla has had a tumultuous couple of weeks, with federal regulator slap-downs, halved profits, and price-cut rollouts. Yet, in a very public snub that Modi won’t quickly forget, the company CEO made time for Chinese premier Li Qiang. And well Musk might. Tesla needs China more than China needs Tesla. After the US, China is Tesla’s second biggest market. And ominously, in the first quarter of the year, Tesla’s sales in China slipped by 4 percent in a domestic EV market that has expanded by more than 15 percent. That’s enough of a hit for any CEO to jump in a Gulfstream and fly across the Pacific for an impromptu meeting with a Chinese premier. Globally, Tesla has lost nearly a third of its value since January, and earlier this month, Tesla’s worldwide vehicle deliveries in the first quarter fell for the first time in almost four years. As they are wont to do, Tesla investors continue to complain over repeated delays to the company’s rollout of cars with genuine driverless capabilities.
One of Tesla’s stop-gap technologies—a now heavily-discounted $8,000 add-on—is marketed as Full Self-Driving, or FSD. But, like the similarly confusingly named Autopilot feature, it still requires driver attention, and may yet still prove to be risky. Among the deals said to have been unveiled at Sunday’s meeting with Li Qiang was a partnership granting Tesla access to a mapping license for data collection on China’s public roads by web search company Baidu. This was a “watershed moment,” Wedbush Securities senior analyst Dan Ives said in an interview with Bloomberg Television. However, Tesla has been using Baidu for in-car mapping and navigation in China since 2020. The revised deal, in which Baidu will now also provide Tesla with its lane-level navigation system, clears one more regulatory hurdle for Tesla’s FSD in China. It does not enable Tesla to introduce driverless cars in China or anywhere else, as some media outlets have reported. Press reports have also claimed that Musk has secured permission to transfer data collected by Tesla cars in China out of China. This is improbable, noted JL Warren Capital CEO and head of research Junheng Li, who wrote on X: “[Baidu] owns all data, and shares filtered data with Tesla. Just imagine if [Tesla] has access to real-time road data such as who went to which country’s embassy at what time for how long.” That, she stressed, would be “super national security!” According to Reuters, Musk is still seeking final approval for the FSD software rollout in China, and Tesla still needs permission to transfer data overseas. Li added that a rollout of even a “supervised,” data-lite version of FSD in China is “extremely unlikely.” She pointed to challenges for Tesla to support local operation of the software. Tesla still “has no [direct] access to map data in China as a foreign entity,” she wrote. Instead, Tesla is likely using the deal extension with Baidu as an FSD workaround, with the data collected in China very much staying in China. Despite this, Tesla shares have jumped following news of the expanded Baidu collaboration. Furthermore, Li said there’s “no strategic value” for Beijing to favor FSD when there are several more advanced Chinese alternatives. (We’ve tested them.)
“Chinese EVs are simply evolving at a far faster pace than Tesla,” agrees Shanghai-based automotive journalist and WIRED contributor Mark Andrews, who tested the driver assistance tech available on the roads in China. The US-listed trio of Xpeng, Nio, and Li Auto offer better-than-Tesla “driving assistance features” that rely heavily on lidar sensors, a technology that Musk previously dismissed, but which Tesla is now said to be testing. Although dated in shape and lacking in the latest tech, a Tesla car is nevertheless more expensive in China than most of its rivals. Tesla recently slashed prices in China to arrest falling sales. Musk’s flying visit to China smacked of “desperation,” says Mark Rainford, owner of the Inside China Auto channel. “[Tesla] sales are down in China—the competition has weathered the price cuts so far and [the Tesla competitors have] a seemingly endless conveyor belt of talented and beautiful products.” Rainford further warns that the “golden period for Tesla in China” is “at great risk of collapsing.” Tesla opened its first gigafactory in Shanghai five years ago, and it is now the firm’s largest—but the automaker has been playing tech catchup in China for some time. In addition to Xpeng, Nio, and Li, there are other Chinese car companies competing with Tesla on autonomous driving, as Musk will see if he visits the Beijing Motor Show, which runs through this week.
Beijing is now arguably the world’s preeminent automotive expo, but Tesla is not exhibiting—a sign that it has little new to offer famously tech-hungry Chinese autobuyers. Pointedly, the Cybertruck is not road-legal in China, although that hasn’t stopped Tesla from displaying the rust-prone electric pickup in some of its Chinese showrooms. Likewise, Tesla has just announced plans for a European Cybertruck tour. But, just like in China, the EV pickup cannot be sold in the EU, either—and according to Tesla's lead on vehicle engineering, it likely never will be.
Speaking on tighter pedestrian safety regulations in the EU compared to the US, Tesla’s vice president of vehicle engineering, Lars Moravy, told Top Gear that “European regulations call for a 3.2-mm external radius on external projections. Unfortunately, it’s impossible to make a 3.2-mm radius on a 1.4-mm sheet of stainless steel.”
The “Cybertruck Odyssey” tour—as Tesla’s European X account calls it—may titillate Tesla fans, but it could prove to be about as useful as shooting a Roadster into space.
29 notes
·
View notes
Text
"From Passion to Profession: Steps to Enter the Tech Industry"
How to Break into the Tech World: Your Comprehensive Guide
In today’s fast-paced digital landscape, the tech industry is thriving and full of opportunities. Whether you’re a student, a career changer, or someone passionate about technology, you may be wondering, “How do I get into the tech world?” This guide will provide you with actionable steps, resources, and insights to help you successfully navigate your journey.
Understanding the Tech Landscape
Before you start, it's essential to understand the various sectors within the tech industry. Key areas include:
Software Development: Designing and building applications and systems.
Data Science: Analyzing data to support decision-making.
Cybersecurity: Safeguarding systems and networks from digital threats.
Product Management: Overseeing the development and delivery of tech products.
User Experience (UX) Design: Focusing on the usability and overall experience of tech products.
Identifying your interests will help you choose the right path.
Step 1: Assess Your Interests and Skills
Begin your journey by evaluating your interests and existing skills. Consider the following questions:
What areas of technology excite me the most?
Do I prefer coding, data analysis, design, or project management?
What transferable skills do I already possess?
This self-assessment will help clarify your direction in the tech field.
Step 2: Gain Relevant Education and Skills
Formal Education
While a degree isn’t always necessary, it can be beneficial, especially for roles in software engineering or data science. Options include:
Computer Science Degree: Provides a strong foundation in programming and system design.
Coding Bootcamps: Intensive programs that teach practical skills quickly.
Online Courses: Platforms like Coursera, edX, and Udacity offer courses in various tech fields.
Self-Learning and Online Resources
The tech industry evolves rapidly, making self-learning crucial. Explore resources like:
FreeCodeCamp: Offers free coding tutorials and projects.
Kaggle: A platform for data science practice and competitions.
YouTube: Channels dedicated to tutorials on coding, design, and more.
Certifications
Certifications can enhance your credentials. Consider options like:
AWS Certified Solutions Architect: Valuable for cloud computing roles.
Certified Information Systems Security Professional (CISSP): Great for cybersecurity.
Google Analytics Certification: Useful for data-driven positions.
Step 3: Build a Portfolio
A strong portfolio showcases your skills and projects. Here’s how to create one:
For Developers
GitHub: Share your code and contributions to open-source projects.
Personal Website: Create a site to display your projects, skills, and resume.
For Designers
Design Portfolio: Use platforms like Behance or Dribbble to showcase your work.
Case Studies: Document your design process and outcomes.
For Data Professionals
Data Projects: Analyze public datasets and share your findings.
Blogging: Write about your data analysis and insights on a personal blog.
Step 4: Network in the Tech Community
Networking is vital for success in tech. Here are some strategies:
Attend Meetups and Conferences
Search for local tech meetups or conferences. Websites like Meetup.com and Eventbrite can help you find relevant events, providing opportunities to meet professionals and learn from experts.
Join Online Communities
Engage in online forums and communities. Use platforms like:
LinkedIn: Connect with industry professionals and share insights.
Twitter: Follow tech influencers and participate in discussions.
Reddit: Subreddits like r/learnprogramming and r/datascience offer valuable advice and support.
Seek Mentorship
Finding a mentor can greatly benefit your journey. Reach out to experienced professionals in your field and ask for guidance.
Step 5: Gain Practical Experience
Hands-on experience is often more valuable than formal education. Here’s how to gain it:
Internships
Apply for internships, even if they are unpaid. They offer exposure to real-world projects and networking opportunities.
Freelancing
Consider freelancing to build your portfolio and gain experience. Platforms like Upwork and Fiverr can connect you with clients.
Contribute to Open Source
Engaging in open-source projects can enhance your skills and visibility. Many projects on GitHub are looking for contributors.
Step 6: Prepare for Job Applications
Crafting Your Resume
Tailor your resume to highlight relevant skills and experiences. Align it with the job description for each application.
Writing a Cover Letter
A compelling cover letter can set you apart. Highlight your passion for technology and what you can contribute.
Practice Interviewing
Prepare for technical interviews by practicing coding challenges on platforms like LeetCode or HackerRank. For non-technical roles, rehearse common behavioral questions.
Step 7: Stay Updated and Keep Learning
The tech world is ever-evolving, making it crucial to stay current. Subscribe to industry newsletters, follow tech blogs, and continue learning through online courses.
Follow Industry Trends
Stay informed about emerging technologies and trends in your field. Resources like TechCrunch, Wired, and industry-specific blogs can provide valuable insights.
Continuous Learning
Dedicate time each week for learning. Whether through new courses, reading, or personal projects, ongoing education is essential for long-term success.
Conclusion
Breaking into the tech world may seem daunting, but with the right approach and commitment, it’s entirely possible. By assessing your interests, acquiring relevant skills, building a portfolio, networking, gaining practical experience, preparing for job applications, and committing to lifelong learning, you’ll be well on your way to a rewarding career in technology.
Embrace the journey, stay curious, and connect with the tech community. The tech world is vast and filled with possibilities, and your adventure is just beginning. Take that first step today and unlock the doors to your future in technology!
contact Infoemation wensite: https://agileseen.com/how-to-get-to-tech-world/ Phone: 01722-326809 Email: [email protected]
#tech career#how to get into tech#technology jobs#software development#data science#cybersecurity#product management#UX design#tech education#networking in tech#internships#freelancing#open source contribution#tech skills#continuous learning#job application tips
9 notes
·
View notes
Text
Leveraging XML Data Interface for IPTV EPG
This blog explores the significance of optimizing the XML Data Interface and XMLTV schedule EPG for IPTV. It emphasizes the importance of EPG in IPTV, preparation steps, installation, configuration, file updates, customization, error handling, and advanced tips.
The focus is on enhancing user experience, content delivery, and securing IPTV setups. The comprehensive guide aims to empower IPTV providers and tech enthusiasts to leverage the full potential of XMLTV and EPG technologies.
1. Overview of the Context:
The context focuses on the significance of optimizing the XML Data Interface and leveraging the latest XMLTV schedule EPG (Electronic Program Guide) for IPTV (Internet Protocol Television) providers. L&E Solutions emphasizes the importance of enhancing user experience and content delivery by effectively managing and distributing EPG information.
This guide delves into detailed steps on installing and configuring XMLTV to work with IPTV, automating XMLTV file updates, customizing EPG data, resolving common errors, and deploying advanced tips and tricks to maximize the utility of the system.
2. Key Themes and Details:
The Importance of EPG in IPTV: The EPG plays a vital role in enhancing viewer experience by providing a comprehensive overview of available content and facilitating easy navigation through channels and programs. It allows users to plan their viewing by showing detailed schedules of upcoming shows, episode descriptions, and broadcasting times.
Preparation: Gathering Necessary Resources: The article highlights the importance of gathering required software and hardware, such as XMLTV software, EPG management tools, reliable computer, internet connection, and additional utilities to ensure smooth setup and operation of XMLTV for IPTV.
Installing XMLTV: Detailed step-by-step instructions are provided for installing XMLTV on different operating systems, including Windows, Mac OS X, and Linux (Debian-based systems), ensuring efficient management and utilization of TV listings for IPTV setups.
Configuring XMLTV to Work with IPTV: The article emphasizes the correct configuration of M3U links and EPG URLs to seamlessly integrate XMLTV with IPTV systems, providing accurate and timely broadcasting information.
3. Customization and Automation:
Automating XMLTV File Updates: The importance of automating XMLTV file updates for maintaining an updated EPG is highlighted, with detailed instructions on using cron jobs and scheduled tasks.
Customizing Your EPG Data: The article explores advanced XMLTV configuration options and leveraging third-party services for enhanced EPG data to improve the viewer's experience.
Handling and Resolving Errors: Common issues related to XMLTV and IPTV systems are discussed, along with their solutions, and methods for debugging XMLTV output are outlined.
Advanced Tips and Tricks: The article provides advanced tips and tricks for optimizing EPG performance and securing IPTV setups, such as leveraging caching mechanisms, utilizing efficient data parsing tools, and securing authentication methods.
The conclusion emphasizes the pivotal enhancement of IPTV services through the synergy between the XML Data Interface and XMLTV Guide EPG, offering a robust framework for delivering engaging and easily accessible content. It also encourages continual enrichment of knowledge and utilization of innovative tools to stay at the forefront of IPTV technology.
3. Language and Structure:
The article is written in English and follows a structured approach, providing detailed explanations, step-by-step instructions, and actionable insights to guide IPTV providers, developers, and tech enthusiasts in leveraging the full potential of XMLTV and EPG technologies.
The conclusion emphasizes the pivotal role of the XML Data Interface and XMLTV Guide EPG in enhancing IPTV services to find more information and innovative tools. It serves as a call to action for IPTV providers, developers, and enthusiasts to explore the sophisticated capabilities of XMLTV and EPG technologies for delivering unparalleled content viewing experiences.
youtube
7 notes
·
View notes
Text
Build the Future of Tech: Enroll in the Leading DevOps Course Online Today
In a global economy where speed, security, and scalability are parameters of success, DevOps has emerged as the pulsating core of contemporary IT operations. Businesses are not recruiting either developers or sysadmins anymore—employers need DevOps individuals who can seamlessly integrate both worlds.
If you're willing to accelerate your career and become irreplaceable in the tech world, then now is the ideal time to sign up for Devops Course Online. And ReferMe Group's AWS DevOps Course is the one to take you there—quicker.

Why DevOps? Why Now?
The need for DevOps professionals is growing like crazy. As per current industry reports, job titles such as DevOps Engineer, Cloud Architect, and Site Reliability Engineer are among the best-paying and safest careers in technology today.
Why? Because DevOps helps businesses to:
Deploy faster using continuous integration and delivery (CI/CD)
Boost reliability and uptime
Automate everything-from infrastructure to testing
Scale apps with ease on cloud platforms like AWS
And individuals who develop these skills are rapidly becoming the pillars of today's tech teams.
Why Learn a DevOps Online?
Learning DevOps online provides more than convenience—it provides liberation. As a full-time professional, student, or career changer, online learning allows you:
✅ To learn at your own pace
✅ To access world-class instructors anywhere
✅ To develop real-world, project-based skills
✅ To prepare for globally recognized certifications
✅ J To join a growing network of DevOps learners and mentors
It’s professional-grade training—without the classroom limitations.
What Makes ReferMe Group’s DevOps Course Stand Out?
The AWS DevOps Course from ReferMe Group isn’t just a course—it’s a career accelerator. Here's what sets it apart:
Hands-On Labs & Projects: You’ll work on live AWS environments and build end-to-end DevOps pipelines using tools like Jenkins, Docker, Terraform, Git, Kubernetes, and more.
Training from Experts: Learn from experienced industry experts who have used DevOps at scale.
Resume-Reinforcing Certifications: Train to clear AWS and DevOps certification exams confidently.
Career Guidance: From resume creation to interview preparation, we prepare you for jobs, not course completion.
Lifetime Access: Come back to the content anytime with future upgrades covered.
Who Should Take This Course?
This DevOps course is ideal for:
Software Developers looking to move into deployment and automation
IT Professionals who want to upskill in cloud infrastructure
System Admins transitioning to new-age DevOps careers
Career changers entering the high-demand cloud and DevOps space
Students and recent graduates seeking a future-proof skill set
No experience in DevOps? No worries. We take you from the basics to advanced tools.
Final Thoughts: Your DevOps Journey Starts Here
As businesses continue to move to the cloud and automate their pipelines, DevOps engineers are no longer a nicety—they're a necessity. Investing in a high-quality DevOps course online provides you with the skills, certification, and confidence to compete and succeed in today's tech industry.
Start building your future today.
Join ReferMe Group's AWS DevOps Course today and become the architect of tomorrow's technology.
2 notes
·
View notes
Text
Continuous Integration: The Backbone of Modern DevOps

Content: Continuous Integration (CI) is more than a buzzword—it’s a discipline that transforms how teams build and deliver software.
In CI, developers frequently merge code changes into a central repository where automated builds and tests are run. This practice catches integration issues early, reduces merge conflicts, and encourages iterative development.
Popular tools like Jenkins, GitLab CI/CD, and CircleCI allow developers to automate everything from build processes to security scans. As projects scale, implementing solid CI practices becomes critical for maintaining velocity without sacrificing stability.
Modern service providers often integrate Software Development robust CI pipelines into their project delivery models, ensuring faster, safer deployments for their clients.
By promoting collaboration and early problem detection, continuous integration supports a healthier, more agile development process.
Treat your CI pipeline configuration as code. Version-control it alongside your application code to track changes and maintain consistency across environments.
2 notes
·
View notes
Text

Deployment Firewall is one of the key capabilities to implement DevSecOps. It prevents security vulnerabilities and compliance issues from going to the staging or the production.
0 notes
Text
What is SaaS and How to Build a SaaS Platform
What is SaaS? SaaS, or Software as a Service, is a cloud-based software delivery model where applications are hosted online and accessed through the internet. Unlike traditional software that requires installation, SaaS applications run on web browsers, offering convenience and flexibility. The provider manages all technical aspects, including updates, maintenance, and security, while users pay a subscription fee for access.
SaaS is popular for its cost-effectiveness and scalability. Businesses use SaaS for tools like customer relationship management (CRM) systems, project management platforms, and communication solutions. Consumers also rely on SaaS for entertainment and personal productivity.
How to Build a SaaS Platform If you're wondering how to build a SaaS platform, here are the essential steps:
Define Your Purpose: Start by identifying a problem that your SaaS platform will address. Research your audience and focus on a specific niche.
Plan Features: List features that add value, such as easy navigation, integrations, and real-time collaboration. Scalability should also be a priority.
Select the Right Technology: Choose technologies like React for frontend development, Node.js or Python for backend, and cloud hosting platforms like AWS.
Create an MVP: Build a Minimum Viable Product to test your concept, gather feedback, and refine your platform.
Ensure Security: Implement strong encryption, secure authentication, and regular updates to protect user data.
By understanding what SaaS is and following these steps, you can build a successful SaaS platform that meets market needs.
2 notes
·
View notes
Text
Legal Agreement
1. Only diamonds received & coins gifts/diamonds gifts spent from this event gifts will count toward the leaderboard. If you recharge or give/receive gifts during the event and are consistent with the requirements of the event rules, you will be deemed to have agreed to participate in the event, and your information will enter the event ranking list and be publicized.
Note: Each user is only allowed to use one account to participate in the event. If it is found to use another number of contestants, which seriously affects the contestants in the activity, the account with higher “user” level will be retained, and the account with lower “user” level will be removed from the list so that it will be disqualified from participating in the competition and winning prizes. The removed list data will not be returned. The above rules apply to all the event, including but not limited to the Gifter &Broadcaster Leaderboard, Points Leaderboard, etc. Coins sent or diamonds received from participating the event shall be obtained from normal channels. If it is found that the acquisition channel is abnormal, which seriously affects the contestants in the event, accounts involved will be disqualified from participating in the competition and winning prizes.
2. Coins-spent and diamonds-received only include sending gifts in broadcasts. Gifts received through Direct Message, Guardian Knight, Shorts, and all other channels will not be counted towards the competition.
3. Cash rewards will be delivered as diamond rewards based on the cash-out rate. Diamond rewards from the event will not be counted on the profile page. Leaderboard rewards will delivered after the event ends in 3-5 business days.
4. The final ranking is based on the point ranking on the leaderboard.
5. This event is only available to users of US region, if there are users in other regions, they will not be eligible for the rewards.
6. LiveMe reserves the final interpretation of this event.
7. Release And Indemnity. By participating in this Contest or receiving a Prize, users (and in particular, each Winner) agrees to release and to indemnify and hold harmless Hong Kong LiveMe Corporation Limited and related companies and affiliates, and their respective officers, directors, employees and agents for any liability, injury, death, loss or damages to registrant or any person or entity, including without limitation damage to personal or real property, caused in whole or in part, directly or indirectly, by participation in this Contest (or related activities) or the acceptance, possession or use/misuse of a Prize.
8. Broadcast Delivery Disclaimer: LiveMe is not responsible for electronic transmission errors resulting in omission, interruption, deletion, defect, delay in operations or transmission, theft or destruction or unauthorized access to or alterations of entry materials, or for technical, network, telephone equipment, electronic, computer, hardware or software malfunctions or limitations of any kind, or inaccurate transmissions of or failure to receive entry information by LiveMe on account of technical problems or traffic congestion on the Internet, at any Web site, or via the mobile phone or any combination thereof. If for any reason the Internet or mobile phone portion of the program is not capable of running as planned, including infection by computer virus, bugs, tampering, unauthorized intervention, fraud, technical failures, or any other causes which corrupt of affect the administration, security, fairness, integrity, or proper conduct of this Contest, LiveMe reserves the right at its sole discretion to cancel, terminate, modify or suspend the Contest, and LiveMe reserves the right to select winners from eligible entries received as of the termination date. LiveMe further reserves the right to disqualify any individual who tampers with the entry process. LiveMe may prohibit a registrant from participating in the Contest if it determines in its sole discretion that said registrant is attempting to undermine the legitimate operation of the Contest by cheating, hacking, deception or other unfair playing practices or intending to abuse, threaten or harass other entrants. Any attempt by a registrant to deliberately damage any LiveMe channel, or otherwise undermine the legitimate operation of the Contest is a violation of criminal and civil laws and should such an attempt be made, LiveMe reserves the right to seek damages from any such participant to the fullest extent of the law.
9. Approximate Retail Prize Value (“ARV”) of the Prizes is the actual value at the time of issuance of the Prize. Any difference between the stated ARV and the actual value of the prize will not be awarded in any form.
10. Disputes/Choice Of Law. Except where prohibited, each registrant agrees that: (i) any and all disputes, claims, and causes of action arising out of or connected with this Contest or any Prize awarded shall be resolved individually, without resort to any form of class action, and exclusively by state or federal courts situated in Los Angeles County, in the State of California; (ii) any and all claims, judgments, and awards shall be limited to actual out-of-pocket costs incurred, but in no event attorneys’ fees; (iii) no punitive, incidental, special, consequential or other damages, including without limitation lost profits may be awarded (collectively, “Special Damages”); and (iv) Registrant now waives all rights to claim Special Damages and all rights to have such damages multiplied or increased. California law, without reference to California choice of law rules, governs the Contest and all aspects related to it. Any questions pertaining to Contest should be directed via email to [email protected].
7 notes
·
View notes
Text
Digital Podiums: Revolutionizing Presentations in the Modern Era
In the age of rapid technological advancement, traditional tools are being replaced by smart, tech-savvy alternatives. One such innovation that has significantly impacted the realm of presentations and public speaking is the digital podium. Whether in educational institutions, corporate settings, or public venues, digital podiums are transforming the way information is delivered and received. Let’s delve into the features, benefits, and reasons why digital podiums are becoming indispensable in today’s world.
What is a Digital Podium?
A digital podium is an advanced version of the traditional lectern. It integrates various technologies, such as touchscreen displays, built-in microphones, and audio systems, to enhance the presenter’s experience. Designed to offer seamless integration with multimedia content, digital podiums are the perfect blend of simplicity and sophistication.
Key Features of a Digital Podium
1. Touchscreen Interface
One of the standout features of digital podiums is the large, interactive touchscreen display. This allows presenters to:
Navigate through slides effortlessly.
Annotate content in real-time.
Access multimedia files with a single touch.
2. Integrated Audio System
Digital podiums are equipped with built-in microphones and high-quality speakers, ensuring clear audio delivery to the audience. Many models also include noise-cancellation features for a professional-grade audio experience.
3. Compatibility with Multiple Devices
Modern digital podiums support connections with laptops, tablets, and USB drives. This ensures flexibility and ease of use, regardless of the presenter’s preferred device.
4. Internet Connectivity
Wi-Fi and Ethernet connectivity enable users to access online resources, stream videos, or download additional materials directly from the podium.
5. Adjustable Design
To cater to presenters of different heights and preferences, many digital podiums feature height-adjustable designs. This ensures a comfortable experience for all users.
6. Robust Security Features
Digital podiums often include password-protected access and encrypted data storage, ensuring that sensitive information remains secure.
7. Multi-Language Support
For institutions and organizations with diverse audiences, digital podiums offer multi-language interfaces, making them accessible to users worldwide.
8. Built-in Lighting
Integrated LED lighting enhances visibility for documents or notes during presentations, especially in dimly lit environments.
9. Recording and Streaming Capabilities
With built-in cameras and software, digital podiums allow presenters to record their sessions or stream them live. This is especially beneficial for hybrid and virtual events.
10. Durable and Sleek Design
Constructed with high-quality materials, digital podiums are designed to withstand frequent use while maintaining a modern and professional appearance.
Benefits of Using a Digital Podium
Enhanced Engagement
Digital podiums make presentations more interactive, captivating the audience’s attention with visuals, videos, and real-time annotations.
Time Efficiency
By consolidating multiple functionalities in one device, digital podiums save setup time and allow presenters to focus on delivering their message effectively.
Accessibility for All
Features like adjustable height and multi-language support ensure that digital podiums are user-friendly for people of all abilities and backgrounds.
Professionalism
The sleek design and advanced features of a digital podium enhance the presenter’s credibility and make a lasting impression on the audience.
Environmentally Friendly
By minimizing the need for printed materials, digital podiums contribute to sustainability efforts and reduce paper waste.
Applications of Digital Podiums
Educational Institutions
In classrooms and lecture halls, digital podiums revolutionize teaching by integrating multimedia content, enabling virtual lectures, and facilitating interactive learning sessions.
Corporate Meetings
For business presentations, digital podiums offer a polished and efficient way to communicate ideas, showcase data, and engage stakeholders.
Conferences and Seminars
Digital podiums are ideal for large events, ensuring seamless transitions between speakers and consistent audio-visual quality throughout the sessions.
Houses of Worship
In religious settings, digital podiums enhance the delivery of sermons and announcements with audio-visual support.
Public Venues
Digital podiums are increasingly used in public addresses, exhibitions, and cultural events, offering versatility and efficiency in diverse scenarios.
Top Considerations When Choosing a Digital Podium
1. Ease of Use
Opt for a digital podium with an intuitive interface that minimizes the learning curve for users.
2. Compatibility
Ensure the podium is compatible with the devices and software commonly used in your organization.
3. Portability
If the podium needs to be moved between locations, consider a lightweight and mobile model.
4. Customization Options
Some manufacturers offer customization features, such as branding and color choices, to align with organizational identity.
5. Warranty and Support
Choose a reliable vendor that provides a comprehensive warranty and excellent customer support to address any technical issues.
Future Trends in Digital Podiums
1. AI Integration
Future digital podiums may include AI-powered features such as speech-to-text, real-time language translation, and personalized content recommendations.
2. Advanced Analytics
Data analytics capabilities will provide insights into audience engagement, helping presenters refine their techniques.
3. Enhanced Connectivity
With the rise of IoT, digital podiums may integrate with other smart devices to create a cohesive technological ecosystem.
Conclusion
Digital podiums are not just a tool; they are a game-changer in the way we communicate, teach, and present. Their versatility, combined with cutting-edge features, ensures that they remain at the forefront of modern presentation technology. Whether you’re an educator, a business leader, or a public speaker, investing in a digital podium is a step toward enhanced professionalism and efficiency.
#DigitalPodium #PresentationTechnology #TechForEducation #SmartLecterns #CorporatePresentations #InteractiveLearning #PublicSpeakingTools #ModernClassrooms #TechInnovation #SustainablePresentations

2 notes
·
View notes
Text
NET Simplified: A Step-by-Step Approach to Excellence
The National Eligibility cum Entrance Test (NEET) is one of the maximum competitive examinations in India, serving because the gateway for students intending to pursue undergraduate medical and dental publications. Each yr, lakhs of candidates appear for this exam with hopes of securing a seat in prestigious scientific faculties across the u . S .. The declaration of NEET effects is a momentous occasion for those college students, as it determines their future professional paths and academic possibilities. In this newsletter, we delve into numerous elements of the NEET consequences, exploring their importance, the procedure of result announcement, and their impact on students’ lives.
NATIONAL ELIGIBILITY TEST RESULTS
Significance of NEET Results
NEET effects are important for college kids entering the clinical and dental fields. The ratings obtained in this examination shape the idea for admission to MBBS, BDS, and different allied health applications supplied by using establishments in India. Additionally, NEET consequences are also taken into consideration for admissions to AYUSH courses (Ayurveda, Yoga and Naturopathy, Unani, Siddha, and Homeopathy) and veterinary packages in a few states. For students meaning to have a look at overseas, NEET qualification is often mandatory in search of admission to scientific faculties in countries just as the Philippines, Russia, Ukraine, and China.
Given the high stakes, the NEET consequences hold significant importance. They reflect the fruits of months, frequently years, of rigorous guidance. The rankings no longer determine whether a candidate qualifies for admission but additionally impact the selection of university and specialization, putting the level for his or her professional adventure.
The Process of NEET Result Declaration
The National Testing Agency (NTA) is answerable for engaging in the NEET exam and asserting its consequences. The process begins with the discharge of the provisional solution key, permitting applicants to project discrepancies or errors. This guarantees transparency and accuracy in the evaluation procedure.
Once the objections are reviewed, the very last answer secret's posted, and the results are prepared accordingly. NEET results are commonly announced online at the official NTA internet site. Candidates can get entry to their results by getting into their software quantity, date of delivery, and protection pin. The result consists of the following information:
Candidate’s Name and Roll Number: Identifying facts for the candidate.
Scorecard: Sectional and standard ratings obtained in Physics, Chemistry, and Biology.
Percentile Score: The percentage of applicants who scored under the candidate.
All India Rank (AIR): The usual rank secured through the candidate among all check-takers.
Category Rank: Rank accomplished in the candidate’s reservation category, if relevant.
Qualifying Status: Whether the candidate has cleared the cutoff criteria.
Additionally, NTA releases a benefit list for All India Quota (AIQ) seats, which includes the top-performing applicants eligible for counseling underneath the centralized admission process.
Understanding NEET Cutoffs
The NEET cutoff is an important issue of the outcomes, determining the eligibility of candidates for admission. The cutoff scores vary each year primarily based on elements consisting of:
Exam Difficulty Level: A harder paper typically outcomes in decrease cutoffs.
Number of Candidates: Higher opposition often increases the cutoff.
Availability of Seats: Limited seats in medical schools have an effect on the minimum qualifying marks.
Reservation Policy: Cutoffs fluctuate for numerous classes, along with General, OBC, SC, ST, and EWS.
However, securing the cutoff percentile does not guarantee admission; applicants have to also rank high enough to secure a seat in their preferred college.
Counseling and Seat Allocation
Post the announcement of consequences, the counseling procedure starts offevolved, controlled via the Medical Counseling Committee (MCC) for AIQ seats and by using the respective country government for kingdom quota seats. The counseling method entails:
Registration: Candidates check in on the designated portals for AIQ or kingdom quota counseling.
Choice Filling and Locking: Students choose their favored schools and courses.
Seat Allotment: Based on NEET rankings, ranks, and options, seats are allotted.
Counseling is performed in multiple rounds, consisting of a mop-up round to fill vacant seats. For college students who are no longer stable for admission within the preliminary rounds, those extra rounds provide another opportunity.
Challenges Faced by Way of Students
The declaration of NEET results brings a combination of emotions for college kids. While a few have fun with their fulfillment, others face the frustration of no longer assembling their expectancies. Here are a few common challenges faced by way of students:
High Competition: With lakhs of candidates vying for a restricted quantity of seats, securing admission will become a frightening task.
Financial Constraints: Medical education is steeply priced, and no longer all students can find the money for non-public college prices, even though they qualify.
Stress and Anxiety: The strain of acting nicely in NEET and the anticipation of effects can take a toll on college students’ mental fitness.
Limited Opportunities: Many deserving candidates miss out on admission due to marginal differences in scores.
Success Stories and Inspirational Tales
Amidst the extreme opposition, NEET effects additionally spotlight inspiring tales of perseverance and determination. Every 12 months, we come upon applicants who overcome massive barriers to acquire their desires. These tales function as motivation for destiny aspirants, emphasizing the significance of tough paintings, willpower, and resilience.
For example, students from rural backgrounds, fighting economic hardships and lack of assets, often come to be pinnacle performers, proving that dedication can conquer any task. Similarly, applicants who take multiple tries to crack NEET exemplify the price of patience.
The Way Forward for Aspirants
For college students who do no longer gain their favored consequences, it's far essential to bear in mind that this is not the end of the road. Many applicants opt for a drop 12 months to prepare more efficaciously and improve their rankings. Coaching centers, online mastering systems, and self-take a look at strategies can help them enhance their coaching.
Moreover, exploring alternative profession paths in allied fitness sciences, biotechnology, or public health can also be worthwhile. These fields provide promising possibilities and allow students to make contributions meaningfully to the healthcare region.
2 notes
·
View notes
Text
What is DevSecOps and Why is it Essential for Secure Software Delivery?
Source: https://thehackernews.com/2024/06/what-is-devsecops-and-why-is-it.html
5 notes
·
View notes
Text
How to Choose the Right Micro ATM Service Provider for Your Needs?
In today's world, financial transactions need to be fast, secure, and accessible to everyone. As Micro ATM Services grow in popularity, selecting the right Micro ATM Services Provider is essential for businesses and individuals looking to benefit from these compact and efficient banking solutions. This guide explores key factors to consider when choosing the right provider and highlights the impact of technology-driven solutions.
Understanding Micro ATM Services Providers
A Micro ATM Services Provider is a company or entity that supplies, operates, and maintains Micro ATM devices for business correspondents or other users. These providers play a pivotal role in extending banking services to remote areas by offering hardware, software, and operational support. Choosing a reliable provider ensures that transactions are secure, seamless, and efficient.
Key Factors to Consider When Choosing a Micro ATM Services Provider
1. Reliability and Reputation The reputation of a provider is critical. Research their track record and client testimonials. Providers with proven reliability can ensure consistent uptime and minimal technical issues. Established names in the industry often have better infrastructure and support systems.
2. Range of Services Offered Different providers offer varying levels of services. Ensure that the provider offers a comprehensive package, including cash withdrawals, deposits, balance inquiries, and fund transfers. Some providers also enable utility bill payments and government subsidies distribution. This versatility adds value to the service.
3. Technology and Security Advanced technology is at the core of any successful Micro ATM Services Provider. Look for providers that offer secure devices equipped with biometric authentication and encryption. Technology-driven providers, such as Xettle Technologies, leverage cutting-edge solutions to ensure reliable and safe transactions. Such features are essential to building trust among users.
4. Business Software Integration For businesses, seamless integration with existing systems is crucial. Check whether the provider offers compatible Business Software that simplifies transaction management and reporting. This integration can save time and reduce errors in operations.
5. Customer Support and Training A good provider should offer robust customer support and training programs for operators. This includes resolving technical issues, providing user manuals, and conducting workshops to train business correspondents. Proper training ensures smooth operations and better service delivery.
6. Cost and Pricing Models Evaluate the cost structure of the provider. While affordability is important, it is equally crucial to assess the value offered. Compare pricing models, maintenance charges, and transaction fees among multiple providers to find one that suits your budget and needs.
7. Scalability and Customization As your business grows, your needs might change. Choose a provider that offers scalable solutions and customizable features. This flexibility ensures that the services remain relevant and useful in the long term.
The Role of Technology in Selecting a Provider
Technology is the backbone of Micro ATM Services. Providers that invest in state-of-the-art technology deliver faster, more secure, and reliable services. For instance, companies like Xettle Technologies lead the industry with innovative solutions that enhance user experience. Their focus on secure software, user-friendly interfaces, and robust connectivity ensures seamless financial transactions, even in areas with limited infrastructure.
Benefits of Choosing the Right Micro ATM Services Provider
1. Improved Customer Satisfaction A reliable provider ensures efficient and error-free transactions, which improves customer trust and satisfaction. End-users are more likely to adopt formal banking channels when they experience secure and hassle-free services.
2. Enhanced Financial Inclusion By choosing a dependable Micro ATM Services Provider, businesses can extend banking services to unbanked and underbanked populations. This not only promotes financial inclusion but also fosters economic growth in remote areas.
3. Streamlined Business Operations For businesses, the integration of Micro ATM systems with business software simplifies financial management. Automated reporting, transaction tracking, and reduced manual errors contribute to operational efficiency.
4. Increased Profitability A good provider offers cost-effective solutions that enable businesses to maximize their returns. Affordable maintenance and transaction fees, coupled with reliable service, ensure sustainable profitability.
Challenges in Selecting a Provider
While the benefits are clear, selecting the right provider can be challenging. Connectivity issues in remote areas, varying service quality among providers, and hidden costs are common obstacles. Thorough research and due diligence can help mitigate these
2 notes
·
View notes