#Security Vulnerabilities in JWT
Explore tagged Tumblr posts
Text
youtube
JWT Security Vulnerabilities | CyberSecurityTv
JSON Web Tokens (JWTs) are a widely used method for representing claims between two parties in a compact and self-contained way
#security vulnerabilities#sql injection#jwt#vulnerability management#zero day vulnerability#vulnerabilities#Addressing JWT (JSON Web Token) Security Vulnerabilities#Security Vulnerabilities in JWT#JWT (JSON Web Token) Implementations#Identifying and Resolving JWT (JSON Web Token)#JWT (JSON Web Token) Vulnerabilities#sql injection attack#jsonwebtoken#jwt token#JWT Security Vulnerabilities#CyberSecurityTv#Youtube
0 notes
Text
How to Protect Your Laravel App from JWT Attacks: A Complete Guide
Introduction: Understanding JWT Attacks in Laravel
JSON Web Tokens (JWT) have become a popular method for securely transmitting information between parties. However, like any other security feature, they are vulnerable to specific attacks if not properly implemented. Laravel, a powerful PHP framework, is widely used for building secure applications, but developers must ensure their JWT implementation is robust to avoid security breaches.

In this blog post, we will explore common JWT attacks in Laravel and how to protect your application from these vulnerabilities. We'll also demonstrate how you can use our Website Vulnerability Scanner to assess your application for potential vulnerabilities.
Common JWT Attacks in Laravel
JWT is widely used for authentication purposes, but several attacks can compromise its integrity. Some of the most common JWT attacks include:
JWT Signature Forgery: Attackers can forge JWT tokens by modifying the payload and signing them with weak or compromised secret keys.
JWT Token Brute-Force: Attackers can attempt to brute-force the secret key used to sign the JWT tokens.
JWT Token Replay: Attackers can capture and replay JWT tokens to gain unauthorized access to protected resources.
JWT Weak Algorithms: Using weak signing algorithms, such as HS256, can make it easier for attackers to manipulate the tokens.
Mitigating JWT Attacks in Laravel
1. Use Strong Signing Algorithms
Ensure that you use strong signing algorithms like RS256 or ES256 instead of weak algorithms like HS256. Laravel's jwt-auth package allows you to configure the algorithm used to sign JWT tokens.
Example:
// config/jwt.php 'algorithms' => [ 'RS256' => \Tymon\JWTAuth\Providers\JWT\Provider::class, ],
This configuration will ensure that the JWT is signed using the RSA algorithm, which is more secure than the default HS256 algorithm.
2. Implement Token Expiry and Refresh
A common issue with JWT tokens is that they often lack expiration. Ensure that your JWT tokens have an expiry time to reduce the impact of token theft.
Example:
// config/jwt.php 'ttl' => 3600, // Set token expiry time to 1 hour
In addition to setting expiry times, implement a refresh token mechanism to allow users to obtain a new JWT when their current token expires.
3. Validate Tokens Properly
Proper token validation is essential to ensure that JWT tokens are authentic and have not been tampered with. Use Laravel’s built-in functions to validate the JWT and ensure it is not expired.
Example:
use Tymon\JWTAuth\Facades\JWTAuth; public function authenticate(Request $request) { try { // Validate JWT token JWTAuth::parseToken()->authenticate(); } catch (\Tymon\JWTAuth\Exceptions\JWTException $e) { return response()->json(['error' => 'Token is invalid or expired'], 401); } }
This code will catch any JWT exceptions and return an appropriate error message to the user if the token is invalid or expired.
4. Secure JWT Storage
Always store JWT tokens in secure locations, such as in HTTP-only cookies or secure local storage. This minimizes the risk of token theft via XSS attacks.
Example (using HTTP-only cookies):
// Setting JWT token in HTTP-only cookie $response->cookie('token', $token, $expirationTime, '/', null, true, true);
Testing Your JWT Security with Our Free Website Security Checker
Ensuring that your Laravel application is free from vulnerabilities requires ongoing testing. Our free Website Security Scanner helps identify common vulnerabilities, including JWT-related issues, in your website or application.
To check your site for JWT-related vulnerabilities, simply visit our tool and input your URL. The tool will scan for issues like weak algorithms, insecure token storage, and expired tokens.

Screenshot of the free tools webpage where you can access security assessment tools.
Example of a Vulnerability Assessment Report
Once the scan is completed, you will receive a detailed vulnerability assessment report to check Website Vulnerability. Here's an example of what the report might look like after checking for JWT security vulnerabilities.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
By addressing these vulnerabilities, you can significantly reduce the risk of JWT-related attacks in your Laravel application.
Conclusion: Securing Your Laravel Application from JWT Attacks
Securing JWT tokens in your Laravel application is essential to protect user data and maintain the integrity of your authentication system. By following the steps outlined in this post, including using strong algorithms, implementing token expiry, and validating tokens properly, you can safeguard your app from common JWT attacks.
Additionally, make sure to regularly test your application for vulnerabilities using tools like our Website Security Checker. It’s a proactive approach that ensures your Laravel application remains secure against JWT attacks.
For more security tips and detailed guides, visit our Pentest Testing Corp.
2 notes
·
View notes
Text
"Beyond the Browser: The Ultimate Full Stack Journey"
In the ever-evolving digital landscape, a new kind of developer is rising above the traditional boundaries of front-end and back-end work—the full stack developer. This role has quickly transformed from a buzzword into a must-have skillset for anyone looking to truly master web development. But what lies beyond the browser? What does it take to embark on the ultimate full stack journey?
Let’s dive deeper into the path of becoming a well-rounded developer capable of building complex applications from the ground up.
What Is a Full Stack Developer?
At its core, a Best full stack development course with Java is someone who has proficiency in both the front-end (what users interact with) and the back-end (the server, database, and application logic) of web applications. These developers can create seamless, fully functional systems by connecting the visible parts of a website with the underlying infrastructure.
A full stack professional typically understands:
Front-end technologies: HTML, CSS, JavaScript, and frameworks like React or Vue.js
Back-end languages and frameworks: Node.js, Python with Django or Flask, Ruby on Rails, or PHP
Databases: MySQL, PostgreSQL, MongoDB, etc.
Version control systems: Git and GitHub for collaboration and tracking changes
Deployment and hosting platforms: AWS, Heroku, Netlify, and Docker for managing environments
But being a full stack developer is not just about knowing tools—it's about understanding how everything connects.
The Journey Beyond the Browser
The road to becoming a full stack expert doesn't stop at the front-end. It goes far deeper, encompassing areas like DevOps, architecture, security, and scalability. Here’s what the ultimate full stack journey looks like:
1. Mastering the Front-End
To start, you need to understand how to build intuitive and accessible user interfaces. This includes:
Writing clean, semantic HTML and efficient CSS
Creating dynamic interfaces with JavaScript and frameworks like Angular or React
Learning how to optimize for performance and responsiveness across devices
2. Diving Into the Back-End
Once comfortable with the client side, developers must tackle server-side logic:
Writing RESTful APIs
Handling data with relational and non-relational databases
Implementing authentication and authorization
Managing server-side rendering and state
3. Connecting the Dots
The next step is learning how to integrate the front-end and back-end into a cohesive application:
Setting up API routes and handling requests/responses
Synchronizing data between client and server
Using tools like Postman to test API endpoints
4. Embracing DevOps and Deployment
Beyond coding, deploying and maintaining applications is crucial:
Setting up CI/CD pipelines for automated testing and deployment
Using Docker and containerization for consistent development environments
Monitoring performance and logging with tools like New Relic or Datadog
5. Staying Secure and Scalable
Security and scalability cannot be ignored:
Understanding authentication methods like JWT and OAuth
Learning best practices to prevent vulnerabilities (e.g., SQL injection, XSS)
Scaling applications with microservices or serverless architecture
Why Full Stack Developers Are in High Demand
Companies are constantly on the lookout for professionals who can see the whole picture. Full stack developers bring flexibility and efficiency to teams, as they can handle multiple responsibilities across the software development lifecycle.
Benefits of Being a Full Stack Developer:
Increased job opportunities across startups and enterprises
Higher earning potential due to broad skillsets
Ability to work independently or as a team leader
Strong foundation for becoming a tech entrepreneur
Conclusion: Your Journey Starts Now
Becoming a Java full stack developer roadmap is more than just checking off a list of programming languages. It’s about building a mindset that sees the bigger picture—how design, functionality, and user experience come together in harmony.
Beyond the browser lies a world of code, creativity, and challenge. Those who venture on this path develop not only technical expertise but also the problem-solving skills and vision required to lead in today’s tech industry.
So whether you're just starting out or leveling up your skills, remember: the ultimate full stack journey is a marathon, not a sprint—but it’s one worth running.
0 notes
Text
Java Full Stack: An Easy Guide with Coding Brushup
In today's tech-driven world, the demand for versatile developers who can handle both front-end and back-end tasks is higher than ever. Java Full Stack Developers are at the forefront of this demand, combining the robustness of Java with a comprehensive understanding of web development.

What Is a Java Full Stack Developer?
A Java Full Stack Developer is proficient in both client-side and server-side development. They work with front-end technologies like HTML, CSS, JavaScript, and frameworks such as React or Angular, as well as back-end technologies including Java, Spring Boot, and Hibernate. This dual expertise allows them to build complete web applications from scratch.
Essential Skills for Java Full Stack Development
To excel as a Java Full Stack Developer, one must master a diverse set of skills:
Java Programming
Core Java forms the foundation of back-end development. Understanding object-oriented programming (OOP), multithreading, and data structures is crucial. Frameworks like Spring Boot and Hibernate further enhance backend capabilities.
Front-End Technologies
Proficiency in HTML, CSS, and JavaScript is essential for creating responsive and interactive user interfaces. Frameworks such as React or Angular are commonly used to streamline front-end development.
Database Management
A solid understanding of both SQL (e.g., MySQL, PostgreSQL) and NoSQL (e.g., MongoDB) databases is vital for efficient data storage and retrieval.
Version Control Systems
Tools like Git are indispensable for tracking code changes and collaborating with teams. Platforms such as GitHub or GitLab facilitate seamless version control.
RESTful APIs and Web Services
Developing and consuming RESTful APIs is crucial for enabling communication between the client and server. Understanding HTTP methods and status codes is part of this skill set.
DevOps Practices
Familiarity with DevOps tools like Jenkins, Docker, and Kubernetes aids in automating the development pipeline and ensuring smooth deployment processes.
Cloud Computing
Knowledge of cloud platforms such as AWS, Azure, or Google Cloud is increasingly important for deploying and managing applications in scalable environments.
Testing and Debugging
Proficiency in testing frameworks like JUnit for Java and tools like Selenium for automated testing ensures the reliability and quality of applications.
Security Best Practices
Implementing security measures like OAuth, JWT, and input validation protects applications from vulnerabilities such as SQL injection and cross-site scripting (XSS).
Continuous Learning
The tech landscape is ever-evolving. Staying updated with the latest frameworks, tools, and best practices is essential for long-term success.
Java Full Stack Developer Roadmap
Embarking on a career as a Java Full Stack Developer involves a structured learning path:
Master Core Java: Begin with the fundamentals of Java programming.
Learn Front-End Development: Dive into HTML, CSS, JavaScript, and frameworks like React or Angular.
Understand Back-End Development: Get hands-on with Spring Boot and Hibernate.
Explore Database Management: Learn SQL and NoSQL databases.
Get Acquainted with DevOps Tools: Understand CI/CD pipelines, Docker, and Kubernetes.
Practice Testing and Debugging: Utilize JUnit and Selenium for ensuring code quality.
Implement Security Measures: Apply best practices to safeguard applications.
Benefits of Becoming a Java Full Stack Developer
High Demand: Versatile developers are sought after across various industries.
Lucrative Salary: Competitive compensation packages.
Career Growth: Opportunities to advance into roles like Tech Lead or Architect.
Skill Diversification: Exposure to a wide range of technologies and tools.
Coding Brushup for Java Full Stack Development
For those looking to refresh their coding skills, consider the following resources:
Online Platforms: Websites like LeetCode, HackerRank, and Codecademy offer exercises and tutorials.
Project-Based Learning: Building small projects can reinforce concepts and improve problem-solving skills.
Peer Collaboration: Engaging with coding communities can provide support and feedback.
Full Stack Developer Course Overview
Enrolling in a comprehensive course can accelerate your learning journey. A typical syllabus includes:
-Core Java Programming
-Front-End Technologies: HTML, CSS, JavaScript, React/Angular
-Back-End Development: Spring Boot, Hibernate
-Database Management: MySQL, MongoDB
-Version Control: Git
-API Development: RESTful services
-DevOps Tools: Jenkins, Docker, Kubernetes
-Cloud Platforms: AWS, Azure
-Testing Frameworks: JUnit, Selenium
-Security Practices: OAuth, JWT
Conclusion Becoming a Java Full Stack Developer is a rewarding endeavor that opens doors to numerous opportunities in the tech industry. By mastering the necessary skills and engaging in continuous learning, you can position yourself as a valuable asset in the ever-evolving world of software development.
#Java Full Stack#Full Stack Developer course#Java programming#coding brushup#coding brushup for Java
0 notes
Text
Security Vulnerabilities in SAML, OAuth 2.0, OpenID Connect, and JWT
Single Sign-On (SSO) protocols are critical for enterprise security but have a history of severe vulnerabilities. This report provides a data-rich overview of known security flaws in four major SSO technologies – SAML, OAuth 2.0, OpenID Connect (OIDC), and JSON Web Tokens (JWT) – including both historical exploits and recent findings. We compare the frequency and impact of these vulnerabilities,…
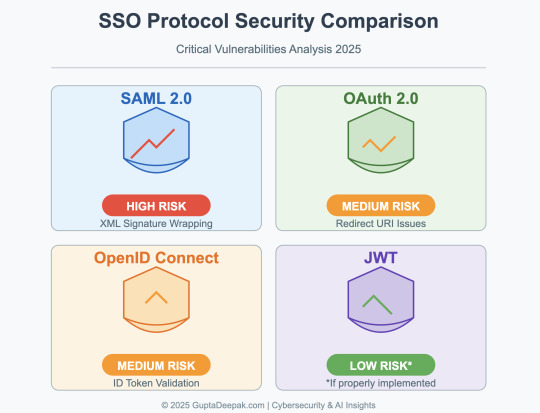
View On WordPress
#assistant professor#computer science#computer scientist#engineering#experimental roboticist#research scientist#university of denver
0 notes
Text
Secure API Development: Protecting Your Data in the Digital Age

Introduction: Why Secure API Development is Essential
In today's interconnected world, APIs are the backbone of modern software. They connect services, platforms, and users. However, with this connectivity comes risk. Cyberattacks, data breaches, and unauthorized access are growing threats. That's why secure API development has become a non-negotiable priority for developers and businesses.
In this comprehensive guide, we will explore what secure API development means, why it's more important than ever in 2025, how to implement security practices, the best tools for securing APIs, and answer common questions.
What is Secure API Development?
Secure API development is the process of designing, building, and managing APIs with a primary focus on data security, access control, and compliance. It involves a range of practices including:
Authentication & Authorization
Encryption of data in transit and at rest
Input validation
Rate limiting and throttling
Monitoring and logging
Why It Matters in 2025
API Attacks Are Increasing: APIs are a top target for attackers due to weak security implementations.
Strict Regulations: Laws like GDPR, HIPAA, and CCPA require secure data handling.
Brand Trust: A single breach can ruin consumer confidence.
Business Continuity: Secure APIs reduce downtime and financial loss.
IoT and Mobile Expansion: With billions of devices connected, secure APIs are vital.
Key Principles of Secure API Development
Least Privilege Access: Only grant access to what’s necessary.
Secure Authentication: Use OAuth 2.0, OpenID Connect, and strong token systems.
Data Encryption: Use HTTPS/TLS and encrypt sensitive data at rest.
Input Sanitization: Prevent injection attacks with proper input validation.
Rate Limiting: Protect APIs from abuse and DDoS attacks.
Monitoring & Logging: Track API usage and detect anomalies early.
Secure API Development Best Practices
PracticeDescriptionUse HTTPSAlways encrypt data in transit.Implement OAuth 2.0Modern standard for API authorization.Validate InputsAvoid SQL injection and XSS attacks.Token ExpirationUse short-lived tokens for sessions.CORS PoliciesRestrict cross-origin requests.API GatewayCentralize security and traffic management.LoggingLog all API calls with metadata for audits.
Tools for Secure API Development
Postman Security Suite: For testing vulnerabilities.
Swagger + OpenAPI: Document and test API access securely.
Kong Gateway: Secure API traffic and enforce policies.
Okta / Auth0: Authentication and authorization.
OWASP ZAP: For automated security testing.
DataDog: For monitoring API traffic and threats.
Common Threats in API Security
ThreatDescriptionBroken AuthenticationImproperly implemented login mechanisms.Excessive Data ExposureAPIs revealing more data than needed.Rate Limiting FailureAPIs can be abused without restrictions.Injection AttacksMalicious data sent to manipulate databases.Lack of LoggingNo trail of usage makes incident response hard.
How to Test for API Security
Penetration Testing: Simulate attacks to identify vulnerabilities.
Static Analysis: Analyze source code for security flaws.
Dynamic Testing: Test APIs during runtime.
Fuzz Testing: Send random data to uncover bugs.
Audit Trails: Review logs for unusual patterns.
Real-World Case Study: API Security in FinTech
A leading FinTech startup experienced a near-breach due to excessive data exposure in its open banking API. After adopting secure API practices:
Implemented OAuth 2.0 and JWT-based token system
Added rate limiting and IP whitelisting
Regularly audited logs and monitored API traffic
Result: No breaches since the update and a 40% increase in client trust and onboarding.
Review: Is Secure API Development Worth It?
Absolutely. In an era where APIs are integral to business, securing them is essential. The upfront investment in security reduces long-term costs and protects brand reputation.
Pros:
Reduced risk of data breaches
Regulatory compliance
Improved user trust
Lower long-term maintenance
Cons:
Increased initial development time
Need for continuous monitoring
Overall Rating: ⭐⭐⭐⭐⭐ (4.9/5)
FAQs: Secure API Development
Q1: Is HTTPS enough to secure an API? No. HTTPS is vital but not sufficient. You also need proper authentication, input validation, and access control.
Q2: What is OAuth 2.0? It’s a secure authorization protocol that allows users to grant apps access to their data without sharing passwords.
Q3: How often should I test my API security? Regularly—ideally during every release and after any major update.
Q4: Are open APIs less secure? Not necessarily. Open APIs can be secure if properly implemented with access control and monitoring.
Q5: Can rate limiting stop all attacks? It’s a useful defense but should be used in combination with other security measures.
Final Thoughts
Secure API development is no longer optional—it’s a fundamental requirement for digital businesses. From authentication to encryption, every step in your API design must consider security. Organizations that prioritize API security not only protect data but also build trust with users, stakeholders, and regulators.
Stay ahead in API security trends with more guides at diglip7.com. Invest in protection today for a safer tomorrow.
0 notes
Text
Enhancing Security in Backend Development: Best Practices for Developers
In today’s rapidly evolving digital environment, security in backend systems is paramount. As the backbone of web applications, the backend handles sensitive data processing, storage, and communication. Any vulnerabilities in this layer can lead to catastrophic breaches, affecting user trust and business integrity. This article highlights essential best practices to ensure your backend development meets the highest security standards.
1. Implement Strong Authentication and Authorization
One of the primary steps in securing backend development services is implementing robust authentication and authorization protocols. Password-based systems alone are no longer sufficient. Modern solutions like OAuth 2.0 and JSON Web Tokens (JWT) offer secure ways to manage user sessions. Multi-factor authentication (MFA) adds another layer of protection, requiring users to verify their identity using multiple methods, such as a password and a one-time code.
Authorization should be handled carefully to ensure users only access resources relevant to their role. By limiting privileges, you reduce the risk of sensitive data falling into the wrong hands. This practice is particularly crucial for applications that involve multiple user roles, such as administrators, managers, and end-users.
2. Encrypt Data in Transit and at Rest
Data encryption is a non-negotiable aspect of backend security. When data travels between servers and clients, it is vulnerable to interception. Implement HTTPS to secure this communication channel using SSL/TLS protocols. For data stored in databases, use encryption techniques that prevent unauthorized access. Even if an attacker gains access to the storage, encrypted data remains unreadable without the decryption keys.
Managing encryption keys securely is equally important. Store keys in hardware security modules (HSMs) or use services like AWS Key Management Service (KMS) to ensure they are well-protected. Regularly rotate keys to further reduce the risk of exposure.
3. Prevent SQL Injection and Other Injection Attacks
Injection attacks, particularly SQL injections, remain one of the most common threats to backend technologies for web development. Attackers exploit poorly sanitized input fields to execute malicious SQL queries. This can lead to unauthorized data access or even complete control of the database.
To mitigate this risk, always validate and sanitize user inputs. Use parameterized queries or prepared statements, which ensure that user-provided data cannot alter the intended database commands. Additionally, educate developers on the risks of injection attacks and implement static code analysis tools to identify vulnerabilities during the development process.
4. Employ Secure API Design
APIs are integral to backend development but can also serve as entry points for attackers if not secured properly. Authentication tokens, input validation, and rate limiting are essential to preventing unauthorized access and abuse. Moreover, all API endpoints should be designed with security-first principles.
For example, avoid exposing sensitive information in API responses. Error messages should be generic and not reveal the backend structure. Consider using tools like API gateways to enforce security policies, including data masking, IP whitelisting, and token validation.
5. Keep Dependencies Updated and Patched
Third-party libraries and frameworks streamline development but can introduce vulnerabilities if not updated regularly. Outdated software components are a common attack vector. Perform routine dependency checks and integrate automated vulnerability scanners like Snyk or Dependabot into your CI/CD pipeline.
Beyond updates, consider using tools to analyze your application for known vulnerabilities. For instance, dependency management tools can identify and notify you of outdated libraries, helping you stay ahead of potential risks.
6. Adopt Role-Based Access Control (RBAC)
Access management is a critical component of secure backend systems. Role-Based Access Control (RBAC) ensures users and applications have access only to what they need. Define roles clearly and assign permissions at a granular level. For example, a customer service representative may only access user profile data, while an admin might have permissions to modify backend configurations.
Implementing RBAC reduces the potential damage of a compromised user account. For added security, monitor access logs for unusual patterns, such as repeated failed login attempts or unauthorized access to restricted resources.
7. Harden Your Database Configurations
Databases are at the heart of backend systems, making them a prime target for attackers. Properly configuring your database is essential. Start by disabling unnecessary services and default accounts that could be exploited. Enforce strong password policies and ensure that sensitive data, such as passwords, is hashed using secure algorithms like bcrypt or Argon2.
Database permissions should also be restricted. Grant the least privilege necessary to applications interacting with the database. Regularly audit these permissions to identify and eliminate unnecessary access.
8. Monitor and Log Backend Activities
Real-time monitoring and logging are critical for detecting and responding to security threats. Implement tools like Logstash, Prometheus, and Kibana to track server activity and identify anomalies. Logs should include information about authentication attempts, database queries, and API usage.
However, ensure that logs themselves are secure. Store them in centralized, access-controlled environments and avoid exposing them to unauthorized users. Use log analysis tools to proactively identify patterns that may indicate an ongoing attack.
9. Mitigate Cross-Site Scripting (XSS) Risks
Cross-site scripting attacks can compromise your backend security through malicious scripts. To prevent XSS attacks, validate and sanitize all inputs received from the client side. Implement Content Security Policies (CSP) that restrict the types of scripts that can run within the application.
Another effective measure is to encode output data before rendering it in the user’s browser. For example, HTML encoding ensures that malicious scripts cannot execute, even if injected.
10. Secure Cloud Infrastructure
As businesses increasingly migrate to the cloud, backend developers must adapt to the unique challenges of cloud security. Use Identity and Access Management (IAM) features provided by cloud platforms like AWS, Google Cloud, and Azure to define precise permissions.
Enable encryption for all data stored in the cloud and use virtual private clouds (VPCs) to isolate your infrastructure from external threats. Regularly audit your cloud configuration to ensure compliance with security best practices.
11. Foster a Culture of Security
Security isn’t a one-time implementation — it’s an ongoing process. Regularly train your development team on emerging threats, secure coding practices, and compliance standards. Encourage developers to follow a security-first approach at every stage of development.
Conduct routine penetration tests and code audits to identify weaknesses. Establish a response plan to quickly address breaches or vulnerabilities. By fostering a security-conscious culture, your organization can stay ahead of evolving threats.
Thus, Backend security is an ongoing effort requiring vigilance, strategic planning, and adherence to best practices. Whether you’re managing APIs, databases, or cloud integrations, securing backend development services ensures the reliability and safety of your application.
0 notes
Text
Full Stack Web Development Coaching at Gritty Tech
Master Full Stack Development with Gritty Tech
If you're looking to build a high-demand career in web development, Gritty Tech's Full Stack Web Development Coaching is the ultimate solution. Designed for beginners, intermediates, and even experienced coders wanting to upskill, our program offers intensive, hands-on training. You will master both front-end and back-end development, preparing you to create complete web applications from scratch For More…
At Gritty Tech, we believe in practical learning. That means you'll not only absorb theory but also work on real-world projects, collaborate in teams, and build a strong portfolio that impresses employers.
Why Choose Gritty Tech for Full Stack Coaching?
Gritty Tech stands out because of our commitment to excellence, personalized mentorship, and career-oriented approach. Here's why you should choose us:
Expert Instructors: Our trainers are seasoned professionals from leading tech companies.
Project-Based Learning: You build real applications, not just toy examples.
Career Support: Resume workshops, interview preparation, and networking events.
Flexible Learning: Evening, weekend, and self-paced options are available.
Community: Join a vibrant community of developers and alumni.
What is Full Stack Web Development?
Full Stack Web Development refers to the creation of both the front-end (client-side) and back-end (server-side) portions of a web application. A full stack developer handles everything from designing user interfaces to managing servers and databases.
Front-End Development
Front-end development focuses on what users see and interact with. It involves technologies like:
HTML5 for structuring web content.
CSS3 for designing responsive and visually appealing layouts.
JavaScript for adding interactivity.
Frameworks like React, Angular, and Vue.js for building scalable web applications.
Back-End Development
Back-end development deals with the server-side, databases, and application logic. Key technologies include:
Node.js, Python (Django/Flask), Ruby on Rails, or Java (Spring Boot) for server-side programming.
Databases like MySQL, MongoDB, and PostgreSQL to store and retrieve data.
RESTful APIs and GraphQL for communication between client and server.
Full Stack Tools and DevOps
Version Control: Git and GitHub.
Deployment: AWS, Heroku, Netlify.
Containers: Docker.
CI/CD Pipelines: Jenkins, GitLab CI.
Gritty Tech Full Stack Coaching Curriculum
Our curriculum is carefully crafted to cover everything a full stack developer needs to know:
1. Introduction to Web Development
Understanding the internet and how web applications work.
Setting up your development environment.
Introduction to Git and GitHub.
2. Front-End Development Mastery
HTML & Semantic HTML: Best practices for accessibility.
CSS & Responsive Design: Media queries, Flexbox, Grid.
JavaScript Fundamentals: Variables, functions, objects, and DOM manipulation.
Modern JavaScript (ES6+): Arrow functions, promises, async/await.
Front-End Frameworks: Deep dive into React.js.
3. Back-End Development Essentials
Node.js & Express.js: Setting up a server, building APIs.
Database Management: CRUD operations with MongoDB.
Authentication & Authorization: JWT, OAuth.
API Integration: Consuming third-party APIs.
4. Advanced Topics
Microservices Architecture: Basics of building distributed systems.
GraphQL: Modern alternative to REST APIs.
Web Security: Preventing common vulnerabilities (XSS, CSRF, SQL Injection).
Performance Optimization: Caching, lazy loading, code splitting.
5. DevOps and Deployment
CI/CD Fundamentals: Automating deployments.
Cloud Services: Hosting apps on AWS, DigitalOcean.
Monitoring & Maintenance: Tools like New Relic and Datadog.
6. Soft Skills and Career Coaching
Resume writing for developers.
Building an impressive LinkedIn profile.
Preparing for technical interviews.
Negotiating job offers.
Real-World Projects You'll Build
At Gritty Tech, you won't just learn; you'll build. Here are some example projects:
E-commerce Website: A full stack shopping platform.
Social Media App: Create a mini version of Instagram.
Task Manager API: Backend API to handle user tasks with authentication.
Real-Time Chat Application: WebSocket-based chat system.
Each project is reviewed by mentors, and feedback is provided to ensure continuous improvement.
Personalized Mentorship and Live Sessions
Our coaching includes one-on-one mentorship to guide you through challenges. Weekly live sessions provide deeper dives into complex topics and allow real-time Q&A. Mentors assist with debugging, architectural decisions, and performance improvements.
Tools and Technologies You Will Master
Languages: HTML, CSS, JavaScript, Python, SQL.
Front-End Libraries/Frameworks: React, Bootstrap, TailwindCSS.
Back-End Technologies: Node.js, Express.js, MongoDB.
Version Control: Git, GitHub.
Deployment: Heroku, AWS, Vercel.
Other Tools: Postman, Figma (for UI design basics).
Student Success Stories
Thousands of students have successfully transitioned into tech roles through Gritty Tech. Some notable success stories:
Amit, from a sales job to Front-End Developer at a tech startup within 6 months.
Priya, a stay-at-home mom, built a portfolio and landed a full stack developer role.
Rahul, a mechanical engineer, became a software engineer at a Fortune 500 company.
Who Should Join This Coaching Program?
This coaching is ideal for:
Beginners with no coding experience.
Working professionals looking to switch careers.
Students wanting to learn industry-relevant skills.
Entrepreneurs building their tech startups.
If you are motivated to learn, dedicated to practice, and open to feedback, Gritty Tech is the right place for you.
Career Support at Gritty Tech
At Gritty Tech, our relationship doesn’t end when you finish the course. We help you land your first job through:
Mock interviews.
Technical assessments.
Building an impressive project portfolio.
Alumni referrals and job placement assistance.
Certifications
After completing the program, you will receive a Full Stack Web Developer Certification from Gritty Tech. This certification is highly respected in the tech industry and will boost your resume significantly.
Flexible Payment Plans
Gritty Tech offers affordable payment plans to make education accessible to everyone. Options include:
Monthly Installments.
Pay After Placement (Income Share Agreement).
Early Bird Discounts.
How to Enroll
Enrolling is easy! Visit Gritty Tech Website and sign up for the Full Stack Web Development Coaching program. Our admissions team will guide you through the next steps.
Frequently Asked Questions (FAQ)
How long does the Full Stack Web Development Coaching at Gritty Tech take?
The program typically spans 6 to 9 months depending on your chosen pace (full-time or part-time).
Do I need any prerequisites?
No prior coding experience is required. We start from the basics and gradually move to advanced topics.
What job roles can I apply for after completing the program?
You can apply for roles like:
Front-End Developer
Back-End Developer
Full Stack Developer
Web Application Developer
Software Engineer
Is there any placement guarantee?
While we don't offer "guaranteed placement," our career services team works tirelessly to help you land a job by providing job referrals, mock interviews, and resume building sessions.
Can I learn at my own pace?
Absolutely. We offer both live cohort-based batches and self-paced learning tracks.
Ready to kickstart your tech career? Join Gritty Tech's Full Stack Web Development Coaching today and transform your future. Visit grittytech.com to learn more and enroll!
0 notes
Text
Software Data Encryption and Protection Methods

In today's digital world, protecting sensitive information is more important than ever. Whether you're building a web app, mobile platform, or desktop software, data encryption and security should never be an afterthought. Here’s a breakdown of essential encryption techniques and protection methods developers should implement.
1. What Is Data Encryption?
Data encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext) to prevent unauthorized access. Only someone with the correct decryption key can read the encrypted data.
2. Types of Encryption
Symmetric Encryption: Uses one secret key for both encryption and decryption. Examples: AES (Advanced Encryption Standard), DES, Blowfish
Asymmetric Encryption: Uses a public key to encrypt and a private key to decrypt. Examples: RSA, ECC
3. Hashing vs Encryption
Hashing is different from encryption. It’s a one-way process used to verify data integrity (like passwords). You can’t “decrypt” a hash.
Common hashing algorithms: SHA-256, SHA-3, Bcrypt, Argon2
Use case: Store passwords using salted hashes, not plain text!
4. Data Protection Methods
Besides encryption, software should use other protective techniques to secure data:
Secure Transmission: Always use HTTPS (TLS) to encrypt data in transit.
Access Controls: Implement authentication and authorization mechanisms (OAuth, JWT).
Database Security: Use encrypted fields, SQL injection protection, and secure ORM practices.
Environment Security: Store secrets in environment variables or secure vaults (e.g., HashiCorp Vault, AWS Secrets Manager).
5. Best Practices for Developers
Never hardcode credentials or keys in your codebase.
Use well-tested encryption libraries instead of building your own.
Regularly update dependencies to patch known vulnerabilities.
Use 2FA (Two-Factor Authentication) for admin accounts and APIs.
Log access attempts and monitor for unusual activity.
6. Real-World Tools and Libraries
OpenSSL – Encryption and SSL/TLS implementation
PyCryptodome (Python), CryptoJS (JavaScript), Bouncy Castle (Java) – for app-level encryption
Let's Encrypt – Free SSL/TLS certificates for HTTPS
Conclusion
Strong encryption and data protection methods are crucial in preventing breaches and building user trust. By implementing these practices, developers can create more secure and reliable software. Remember — security is not a feature, it’s a responsibility.
0 notes
Text
API Vulnerabilities in Symfony: Common Risks & Fixes
Symfony is one of the most robust PHP frameworks used by enterprises and developers to build scalable and secure web applications. However, like any powerful framework, it’s not immune to security issues—especially when it comes to APIs. In this blog, we’ll explore common API vulnerabilities in Symfony, show real coding examples, and explain how to secure them effectively.

We'll also demonstrate how our Free Website Security Scanner helps identify these vulnerabilities before attackers do.
🚨 Common API Vulnerabilities in Symfony
Let’s dive into the key API vulnerabilities developers often overlook:
1. Improper Input Validation
Failure to sanitize input can lead to injection attacks.
❌ Vulnerable Code:
// src/Controller/ApiController.php public function getUser(Request $request) { $id = $request->query->get('id'); $user = $this->getDoctrine() ->getRepository(User::class) ->find("SELECT * FROM users WHERE id = $id"); return new JsonResponse($user); }
✅ Secure Code with Param Binding:
public function getUser(Request $request) { $id = (int)$request->query->get('id'); $user = $this->getDoctrine() ->getRepository(User::class) ->find($id); return new JsonResponse($user); }
Always validate and sanitize user input, especially IDs and query parameters.
2. Broken Authentication
APIs that don’t properly verify tokens or allow session hijacking are easy targets.
❌ Insecure Token Check:
if ($request->headers->get('Authorization') !== 'Bearer SECRET123') { throw new AccessDeniedHttpException('Unauthorized'); }
✅ Use Symfony’s Built-in Security:
# config/packages/security.yaml firewalls: api: pattern: ^/api/ stateless: true jwt: ~
Implement token validation using LexikJWTAuthenticationBundle to avoid manual and error-prone token checking.
3. Overexposed Data in JSON Responses
Sometimes API responses contain too much information, leading to data leakage.
❌ Unfiltered Response:
return $this->json($user); // Might include password hash or sensitive metadata
✅ Use Serialization Groups:
// src/Entity/User.php use Symfony\Component\Serializer\Annotation\Groups; class User { /** * @Groups("public") */ private $email; /** * @Groups("internal") */ private $password; } // In controller return $this->json($user, 200, [], ['groups' => 'public']);
Serialization groups help you filter sensitive fields based on context.
🛠️ How to Detect Symfony API Vulnerabilities for Free
📸 Screenshot of the Website Vulnerability Scanner tool homepage

Screenshot of the free tools webpage where you can access security assessment tools.
Manual code audits are helpful but time-consuming. You can use our free Website Security Checker to automatically scan for common security flaws including:
Open API endpoints
Broken authentication
Injection flaws
Insecure HTTP headers
🔎 Try it now: https://free.pentesttesting.com/
📸 Screenshot of an actual vulnerability report generated using the tool to check Website Vulnerability

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
✅ Our Web App Penetration Testing Services
For production apps and high-value APIs, we recommend deep testing beyond automated scans.
Our professional Web App Penetration Testing Services at Pentest Testing Corp. include:
Business logic testing
OWASP API Top 10 analysis
Manual exploitation & proof-of-concept
Detailed PDF reports
💼 Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
📚 More Articles from Pentest Testing Corp.
For in-depth cybersecurity tips and tutorials, check out our main blog:
🔗 https://www.pentesttesting.com/blog/
Recent articles:
Laravel API Security Best Practices
XSS Mitigation in React Apps
Threat Modeling for SaaS Platforms
📬 Stay Updated: Subscribe to Our Newsletter
Join cybersecurity enthusiasts and professionals who subscribe to our weekly threat updates, tools, and exclusive research:
🔔 Subscribe on LinkedIn: https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
💬 Final Thoughts
Symfony is powerful, but with great power comes great responsibility. Developers must understand API security vulnerabilities and patch them proactively. Use automated tools like ours for Website Security check, adopt secure coding practices, and consider penetration testing for maximum protection.
Happy Coding—and stay safe out there!
#cyber security#cybersecurity#data security#pentesting#security#coding#symfony#the security breach show#php#api
1 note
·
View note
Text
Security and Compliance in Cloud Computing: Best Practices for Risk Mitigation
As businesses rapidly adopt cloud computing, ensuring security and compliance is more critical than ever. Cyber threats, data breaches, and regulatory requirements demand that organizations implement robust security measures to protect sensitive data and maintain compliance.
In this blog, we’ll explore key security challenges in cloud computing, best practices for risk mitigation, and how Salzen helps businesses enhance their cloud security posture.
1. The Growing Importance of Cloud Security and Compliance
The shared responsibility model in cloud computing means that while cloud providers secure the infrastructure, businesses must safeguard data, applications, and user access.
Without proper security controls, organizations face:
🔹 Data breaches and cyberattacks 🔹 Regulatory fines for non-compliance 🔹 Operational disruptions due to security incidents
📌 Example: A global retailer suffered a $200M+ data breach due to misconfigured cloud storage, exposing millions of customer records.
2. Top Security Risks in Cloud Computing
🔹 1. Misconfigurations and Unauthorized Access
🔸 Misconfigured cloud storage, APIs, and identity settings are a leading cause of data leaks. 🔸 Lack of multi-factor authentication (MFA) can allow unauthorized access.
✅ Mitigation: ✔ Regular security audits to detect misconfigurations ✔ Enforce least privilege access and use MFA for all accounts
🔹 2. Compliance Violations and Data Sovereignty Issues
🔸 Businesses handling financial, healthcare, or personal data must comply with GDPR, HIPAA, SOC 2, and PCI DSS. 🔸 Storing data in the wrong geographic region can violate data sovereignty laws.
✅ Mitigation: ✔ Use automated compliance monitoring to ensure regulatory adherence ✔ Choose cloud regions that align with legal requirements
📌 Example: A fintech company avoided $1M in regulatory fines by implementing real-time compliance monitoring.
🔹 3. Insecure APIs and Weak Encryption
🔸 Unsecured APIs are a common attack vector for cybercriminals. 🔸 Poor encryption standards put sensitive data at risk.
✅ Mitigation: ✔ Implement API security best practices, including OAuth, JWT, and rate limiting ✔ Use end-to-end encryption for data in transit and at rest
📌 Example: A healthcare firm prevented API breaches by enforcing zero-trust authentication for all API endpoints.
3. Best Practices for Cloud Security and Compliance
🔹 1. Implement Zero Trust Security
The Zero Trust model assumes that no one inside or outside the network is automatically trusted.
✔ Enforce strict identity verification for all users and devices ✔ Use micro-segmentation to limit lateral movement in case of a breach
🔹 2. Automate Security and Compliance Monitoring
Manual security checks are inefficient and prone to human error. Automating security monitoring helps detect threats in real time.
✔ Deploy SIEM (Security Information and Event Management) tools like Splunk, Datadog, or AWS Security Hub ✔ Use compliance-as-code to continuously audit configurations
📌 Example: A global SaaS company reduced compliance violations by 75% using automated compliance scanning.
🔹 3. Secure CI/CD Pipelines
CI/CD pipelines introduce security risks if not properly secured.
✔ Implement automated security testing in CI/CD workflows ✔ Scan for vulnerabilities in containerized applications before deployment
📌 Example: A DevOps team prevented production breaches by integrating SAST and DAST security checks in CI/CD pipelines.
4. How Salzen Helps Secure Your Cloud Environment
At Salzen, we enable businesses to enhance cloud security and compliance through:
🔐 Automated security assessments to detect vulnerabilities early 🛡 Cloud-native security solutions for proactive threat detection 📊 Compliance management tools to ensure regulatory adherence
🔹 Ready to strengthen your cloud security? Let Salzen help you implement best-in-class security and compliance solutions! 🚀
0 notes
Text
How AI and Machine Learning Are Transforming API Testing

APIs are the backbone of modern software, enabling seamless communication between applications, services, and platforms. However, as APIs grow in complexity, so do the challenges of testing them. Traditional API testing approaches often struggle to keep up with rapid development cycles, frequent updates, and dynamic environments. Enter AI and Machine Learning (ML)—game changers that are revolutionizing API testing by introducing intelligence, adaptability, and predictive capabilities into the process.
This article explores how AI and ML are reshaping API testing, providing deeper insights into automation, anomaly detection, self-healing tests, and the future of API quality assurance.
The Shortcomings of Traditional API Testing
Before diving into AI’s impact, it’s important to understand the limitations of traditional API testing methods:
Manual Test Case Writing – Time-consuming and error-prone.
Static Test Scripts – Break easily with frequent API updates.
Slow Defect Identification – Reactive rather than proactive.
Limited Scalability – Cannot efficiently handle large-scale testing needs.
These challenges highlight the need for AI-powered solutions that introduce intelligence, efficiency, and adaptability into API testing.
How AI and Machine Learning Are Revolutionizing API Testing
1. AI-Driven Test Case Generation – Smarter, Faster, and More Accurate
AI can analyze API documentation, past test data, and traffic patterns to auto-generate optimized test cases. This reduces manual effort and ensures comprehensive test coverage, even for complex API structures.
Example: Tools like Postman AI can generate test scripts by analyzing API request/response pairs, eliminating the need for manual scripting.
2. Self-Healing Test Automation – Say Goodbye to Script Maintenance
APIs are frequently updated, leading to broken test scripts. AI-driven self-healing automation detects these changes and dynamically updates the test scripts to maintain functionality.
How it Works:
AI identifies changes in API responses and structure.
It automatically updates impacted test cases.
The system learns from past test failures to improve resilience.
3. Predictive Analytics and Anomaly Detection – Finding Bugs Before They Occur
Machine learning algorithms analyze historical API performance data to detect anomalies, predict failures, and identify vulnerabilities before they impact users.
Key Benefits:
Detects outliers in API response times.
Identifies security threats like unexpected API payload manipulations.
Predicts performance degradation based on usage trends.
4. AI-Powered API Security Testing – Proactive Threat Detection
With the rise of API-based cyberattacks, traditional security testing is no longer sufficient. AI-driven security testing continuously monitors API traffic and detects suspicious activities in real-time.
Security AI can:
Identify authentication vulnerabilities (e.g., weak API keys, JWT token leaks).
Detect malicious API calls using behavior-based threat detection.
Simulate sophisticated cyberattacks (e.g., SQL injections, API fuzzing) to assess resilience.
5. Autonomous Load and Performance Testing – Real-World Traffic Simulation
AI enhances API performance testing by analyzing real-world usage patterns and dynamically adjusting test scenarios to reflect actual user behavior.
Example: AI-powered tools can analyze peak traffic patterns and predict potential bottlenecks before they occur, ensuring APIs can handle extreme loads effectively.
6. AI-Assisted API Documentation Testing – Ensuring Accuracy and Consistency
AI can compare API documentation against actual API responses to ensure consistency, detect outdated documentation, and even auto-generate missing documentation.
Tools like:
Swagger Inspector (for API spec validation)
Apicurio (for AI-assisted API design and documentation validation)
Conclusion
AI and Machine Learning are redefining API testing by making it brighter, faster, and more efficient. From automated test generation to self-healing automation and proactive security testing, AI-powered tools enable seamless, reliable, and future-ready API validation.
Enhance Your API Testing with Testrig Technologies
At Testrig Technologies, we specialize in AI-driven API testing services that ensure faster, more reliable, and cost-effective API validation.
Our expertise in intelligent automation and machine learning-based testing can help businesses achieve superior API quality.
Contact us today to transform your API Automation testing strategy with AI!
0 notes
Text
Prevent JWT Attacks in Laravel with Secure Coding Practices
Introduction: What is JWT and Why Should You Care? JSON Web Tokens (JWT) are a popular method for securely transmitting information between parties as a JSON object. They are widely used for authentication and authorization in web applications, especially in frameworks like Laravel. While JWT offers many advantages, improper implementation can lead to serious security vulnerabilities, such…

View On WordPress
0 notes
Text
How Symfony Software Development Enhances Web Performance and Security?

In today’s digital era, businesses need web applications that are not only feature-rich but also high-performing and secure. Symfony, a leading PHP framework, has become a preferred choice for web application development due to its robust architecture, performance optimization features, and advanced security mechanisms. Let’s explore how Symfony software development enhances web performance and security.
Performance Optimization with Symfony
1. Efficient Caching Mechanism
Symfony’s built-in caching system ensures that web applications load faster and use fewer server resources. It supports multiple caching methods such as HTTP caching, application caching, and OPcache integration, reducing redundant computations and improving response times.
2. Code Reusability and Modularity
Symfony is designed around reusable components and a modular architecture. This reduces the need for redundant code, making the application lightweight and improving execution speed. Developers can integrate only the necessary components, ensuring optimized performance.
3. Autoloading and Dependency Injection
Symfony uses an efficient autoloading system that eliminates the need to manually include files. Additionally, its powerful dependency injection container reduces memory consumption, allowing applications to run faster with fewer resources.
4. Database Optimization
Symfony’s Doctrine ORM (Object-Relational Mapping) optimizes database queries by reducing unnecessary calls and enabling query caching. This ensures faster data retrieval and better database performance.
5. Built-in Debugging and Profiling Tools
Symfony’s debugging tools, such as the Web Debug Toolbar and Profiler, help developers identify performance bottlenecks. By optimizing slow queries and refining application logic, Symfony ensures enhanced application speed and efficiency.
Enhancing Security with Symfony
1. Secure Authentication and Authorization
Symfony offers a built-in security system that provides robust authentication and authorization mechanisms. It supports multi-factor authentication, OAuth, JWT, and LDAP integrations, ensuring secure user access and preventing unauthorized logins.
2. Protection Against Common Web Threats
Symfony is designed to protect applications from common security threats, including:
Cross-Site Scripting (XSS): It automatically escapes output to prevent malicious script injections.
Cross-Site Request Forgery (CSRF): Symfony includes built-in CSRF protection to safeguard forms from unauthorized requests.
SQL Injection Prevention: By using Doctrine ORM, Symfony prevents direct SQL injections by implementing parameterized queries.
3. Secure Data Encryption
Symfony supports data encryption mechanisms such as bcrypt and Argon2 hashing for password storage. It also enables secure transmission of sensitive data using SSL/TLS protocols.
4. Regular Security Updates and Community Support
Symfony has an active community and a dedicated security team that continuously monitors vulnerabilities and releases regular updates and patches. This ensures applications remain secure against evolving cyber threats.
Conclusion
Symfony software development is an excellent choice for businesses looking to build high-performing and secure web applications. With its powerful caching mechanisms, optimized database queries, and security-focused architecture, Symfony ensures enhanced web performance and protection against cyber threats. By leveraging Symfony’s capabilities, businesses can deliver fast, scalable, and secure web applications, ensuring a seamless user experience.
0 notes
Text
Provide insights into securing Java web and desktop applications.

Securing Java web and desktop applications requires a combination of best practices, security libraries, and frameworks to prevent vulnerabilities like SQL injection, XSS, CSRF, and unauthorized access. Here’s a deep dive into key security measures:
1. Secure Authentication and Authorization
Use Strong Authentication Mechanisms
Implement OAuth 2.0, OpenID Connect, or SAML for authentication.
Use Spring Security for web applications.
Enforce multi-factor authentication (MFA) for added security.
Example (Spring Security Basic Authentication in Java Web App)java@Configuration @EnableWebSecurity public class SecurityConfig { @Bean public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception { http .authorizeHttpRequests(auth -> auth .requestMatchers("/admin/**").hasRole("ADMIN") .anyRequest().authenticated()) .httpBasic(); return http.build(); } }Implement Role-Based Access Control (RBAC)
Define roles and permissions for users.
Use JWT (JSON Web Tokens) for securing APIs.
Example (Securing API using JWT in Spring Boot)javapublic class JwtUtil { private static final String SECRET_KEY = "secureKey"; public String generateToken(String username) { return Jwts.builder() .setSubject(username) .setIssuedAt(new Date()) .setExpiration(new Date(System.currentTimeMillis() + 1000 * 60 * 60)) .signWith(SignatureAlgorithm.HS256, SECRET_KEY) .compact(); } }
2. Secure Data Storage and Transmission
Use Secure Communication (HTTPS & TLS)
Use TLS 1.2+ for encrypting data in transit.
Enforce HSTS (HTTP Strict Transport Security).
Encrypt Sensitive Data
Store passwords using bcrypt, PBKDF2, or Argon2.
Use AES-256 for encrypting sensitive data.
Example (Hashing Passwords in Java)javaimport org.mindrot.jbcrypt.BCrypt;public class PasswordSecurity { public static String hashPassword(String password) { return BCrypt.hashpw(password, BCrypt.gensalt(12)); } public static boolean verifyPassword(String password, String hashedPassword) { return BCrypt.checkpw(password, hashedPassword); } }
Use Secure Database Connections
Use parameterized queries to prevent SQL injection.
Disable database user permissions that are not required.
Example (Using Prepared Statements in JDBC)javaPreparedStatement stmt = connection.prepareStatement("SELECT * FROM users WHERE username = ?"); stmt.setString(1, username); ResultSet rs = stmt.executeQuery();
3. Protect Against Common Web Vulnerabilities
Prevent SQL Injection
Always use ORM frameworks (Hibernate, JPA) to manage queries securely.
Mitigate Cross-Site Scripting (XSS)
Escape user input in web views using OWASP Java Encoder.
Use Content Security Policy (CSP) headers.
Prevent Cross-Site Request Forgery (CSRF)
Use CSRF tokens in forms.
Enable CSRF protection in Spring Security.
Example (Enabling CSRF Protection in Spring Security)javahttp.csrf().csrfTokenRepository(CookieCsrfTokenRepository.withHttpOnlyFalse());
4. Secure File Uploads and Deserialization
Validate File Uploads
Restrict allowed file types (e.g., only images, PDFs).
Use virus scanning (e.g., ClamAV).
Example (Checking File Type in Java)javaif (!file.getContentType().equals("application/pdf")) { throw new SecurityException("Invalid file type"); }
Avoid Untrusted Deserialization
Use whitelisting for allowed classes.
Prefer JSON over Java serialization.
Example (Disable Unsafe Object Deserialization in Java)javaObjectInputStream ois = new ObjectInputStream(inputStream) { @Override protected Class<?> resolveClass(ObjectStreamClass desc) throws IOException, ClassNotFoundException { throw new InvalidClassException("Deserialization is not allowed"); } };
5. Secure Desktop Java Applications
Use Code Signing
Sign JAR files using Java Keytool to prevent tampering.
shjarsigner -keystore mykeystore.jks -signedjar SecureApp.jar MyApp.jar myaliasRestrict JavaFX/Swing Application Permissions
Use Java Security Manager (deprecated but useful for legacy apps).
Restrict access to file system, network, and system properties.
Encrypt Local Data Storage
Use AES encryption for storing local files.
Example (Encrypting Files with AES in Java)javaCipher cipher = Cipher.getInstance("AES"); cipher.init(Cipher.ENCRYPT_MODE, new SecretKeySpec(key, "AES")); byte[] encrypted = cipher.doFinal(data);
6. Logging and Monitoring for Security
Use Secure Logging Frameworks
Use logback or SLF4J.
Avoid logging sensitive data like passwords.
Monitor for Anomalies
Implement Intrusion Detection Systems (IDS).
Use audit trails and security alerts.
7. Best Practices for Securing Java Applications
✅ Keep dependencies up to date (Use OWASP Dependency Check). ✅ Run security scans (SAST, DAST) using SonarQube, Checkmarx. ✅ Apply the principle of least privilege for database and API access. ✅ Enforce strong password policies (min length, special characters). ✅ Use API Gateway and rate limiting for public-facing APIs.
Conclusion
Securing Java web and desktop applications requires multi-layered security across authentication, data protection, and vulnerability mitigation. By following best practices like strong encryption, secure coding techniques, and continuous monitoring, developers can protect applications against cyber threats.
WEBSITE: https://www.ficusoft.in/core-java-training-in-chennai/
0 notes
Text
A Deep Dive into Modern Backend Development for Web Application
Creating seamless and dynamic web experiences often comes down to what happens behind the scenes. While front-end design captures initial attention, the backend is where much of the magic unfolds — handling data, security, and server logic. This article explores the core concepts of modern backend development, examines how evolving practices can fuel growth, and offers insights on selecting the right tools and partners.
1. Why the Backend Matters
Imagine a beautifully designed website that struggles with slow loading times or frequent errors. Such issues are typically rooted in the server’s logic or the infrastructure behind it. A robust backend ensures consistent performance, efficient data management, and top-tier security — elements that collectively shape user satisfaction.
Moreover, well-designed backend systems are better equipped to handle sudden traffic spikes without sacrificing load times. As online platforms scale, the backend must keep pace, adapting to increased user demands and integrating new features with minimal disruption. This flexibility helps businesses stay agile in competitive environments.
2. Core Components of Backend Development
Server
The engine running behind every web application. Whether you choose shared hosting, dedicated servers, or cloud-based virtual machines, servers host your application logic and data endpoints.
Database
From relational systems like MySQL and PostgreSQL to NoSQL options such as MongoDB, databases store and manage large volumes of information. Choosing the right type hinges on factors like data structure, scalability needs, and transaction speed requirements.
Application Logic
This code handles requests, processes data, and sends responses back to the front-end. Popular languages for writing application logic include Python, JavaScript (Node.js), Java, and C#.
API Layer
Application Programming Interfaces (APIs) form a communication bridge between the backend and other services or user interfaces. RESTful and GraphQL APIs are two popular frameworks enabling efficient data retrieval and interactions.
3. Emerging Trends in Backend Development
Cloud-Native Architectures
Cloud-native applications leverage containerization (Docker, Kubernetes) and microservices, making it easier to deploy incremental changes, scale specific components independently, and limit downtime. This modular approach ensures continuous delivery and faster testing cycles.
Serverless Computing
Platforms like AWS Lambda, Google Cloud Functions, and Azure Functions allow developers to run code without managing servers. By focusing on logic rather than infrastructure, teams can accelerate development, paying only for the computing resources they actually use.
Microservices
Rather than constructing one large, monolithic system, microservices break an application into smaller, independent units. Each service manages a specific function and communicates with others through lightweight protocols. This design simplifies debugging, accelerates deployment, and promotes autonomy among development teams.
Real-Time Communication
From chat apps to collaborative tools, real-time functionality is on the rise. Backend frameworks increasingly support WebSockets and event-driven architectures to push updates instantly, boosting interactivity and user satisfaction.
4. Balancing Performance and Security
The need for speed must not compromise data protection. Performance optimizations — like caching and query optimization — improve load times but must be paired with security measures. Popular practices include:
Encryption: Safeguarding data in transit with HTTPS and at rest using encryption algorithms.
Secure Authentication: Implementing robust user verification, perhaps with JWT (JSON Web Tokens) or OAuth 2.0, prevents unauthorized access.
Regular Audits: Scanning for vulnerabilities and patching them promptly to stay ahead of evolving threats.
Organizations that neglect security can face breaches, data loss, and reputational harm. Conversely, a well-fortified backend can boost customer trust and allow businesses to handle sensitive tasks — like payment processing — without fear.
5. Making the Right Technology Choices
Selecting the right backend technologies for web development hinges on various factors, including project size, performance targets, and existing infrastructure. Here are some examples:
Node.js (JavaScript): Known for event-driven, non-blocking I/O, making it excellent for real-time applications.
Python (Django, Flask): Valued for readability, a large ecosystem of libraries, and strong community support.
Ruby on Rails: Emphasizes convention over configuration, speeding up development for quick MVPs.
Java (Spring): Offers stability and scalability for enterprise solutions, along with robust tooling.
.NET (C#): Integrates deeply with Microsoft’s ecosystem, popular in enterprise settings requiring Windows-based solutions.
Evaluating the pros and cons of each language or framework is crucial. Some excel in rapid prototyping, while others shine in large-scale, enterprise-grade environments.
6. Customizing Your Approach
Off-the-shelf solutions can help businesses get started quickly but may lack flexibility for unique requirements. Customized backend development services often prove essential when dealing with complex workflows, specialized integrations, or a need for extensive scalability.
A tailored approach allows organizations to align every feature with operational goals. This can reduce technical debt — where one-size-fits-all solutions require extensive workarounds — and ensure that the final product supports long-term growth. However, custom builds do require sufficient expertise, planning, and budget to succeed.
7. The Role of DevOps
DevOps practices blend development and operations, boosting collaboration and streamlining deployment pipelines. Continuous Integration (CI) and Continuous Deployment (CD) are common components, automating tasks like testing, building, and rolling out updates. This not only reduces human error but also enables teams to push frequent, incremental enhancements without risking application stability.
Infrastructure as Code (IaC) is another DevOps strategy that uses configuration files to manage environments. This approach eliminates the guesswork of manual setups, ensuring consistent conditions across development, staging, and production servers.
8. Measuring Success and Ongoing Improvement
A robust backend setup isn’t a one-time project — it’s a continuous journey. Monitoring key performance indicators (KPIs) like uptime, response times, and error rates helps identify problems before they escalate. Logging tools (e.g., ELK stack) and application performance monitoring (APM) tools (e.g., New Relic, Datadog) offer deep insights into system performance, user behavior, and resource allocation.
Regular reviews of these metrics can inform incremental improvements, from refactoring inefficient code to scaling up cloud resources. This iterative process not only keeps your application running smoothly but also maintains alignment with evolving market demands.
Conclusion
From blazing-fast load times to rock-solid data integrity, a well-crafted backend paves the way for exceptional digital experiences. As businesses continue to evolve in competitive online spaces, adopting modern strategies and frameworks can yield remarkable benefits. Whether leveraging serverless architectures or working with microservices, organizations that prioritize performance, security, and scalability remain better positioned for future growth.
0 notes