#jwt token
Explore tagged Tumblr posts
Text
youtube
JWT Security Vulnerabilities | CyberSecurityTv
JSON Web Tokens (JWTs) are a widely used method for representing claims between two parties in a compact and self-contained way
#security vulnerabilities#sql injection#jwt#vulnerability management#zero day vulnerability#vulnerabilities#Addressing JWT (JSON Web Token) Security Vulnerabilities#Security Vulnerabilities in JWT#JWT (JSON Web Token) Implementations#Identifying and Resolving JWT (JSON Web Token)#JWT (JSON Web Token) Vulnerabilities#sql injection attack#jsonwebtoken#jwt token#JWT Security Vulnerabilities#CyberSecurityTv#Youtube
0 notes
Text
Spring Security - Trabajando con tokens
En esta ocasión, vamos a ver como podemos incorporar los tokens, y hacer que Spring Security nos controle igualmente la seguridad de nuestra Api Continue reading Untitled

View On WordPress
0 notes
Text
Django REST Framework: Authentication and Permissions
Secure Your Django API: Authentication and Permissions with DRF
Introduction Django REST Framework (DRF) is a powerful toolkit for building Web APIs in Django. One of its key features is the ability to handle authentication and permissions, ensuring that your API endpoints are secure and accessible only to authorized users. This article will guide you through setting up authentication and permissions in DRF, including examples and…
#custom permissions#Django API security#Django JWT integration#Django REST Framework#DRF authentication#Python web development#token-based authentication
0 notes
Text
JWT Explained in Depth | CyberSecurityTv
youtube
In this comprehensive video on CyberSecurityTv, They dive deep into the world of JWT (JSON Web Tokens), unraveling its intricacies and shedding light on its significance in the realm of cybersecurity. Join and explore the inner workings, use cases, and security considerations of JWTs. Whether you're a cybersecurity enthusiast or a developer, this video will equip you with a thorough understanding of JWTs.
#JWT#JSONWebTokens#Cybersecurity#Authentication#Authorization#WebSecurity#Tokenization#CyberSecurityTv#TokenSecurity#DigitalSecurity#DataProtection#Youtube
0 notes
Photo

Another great infographic from ByteByteGo that crams a lot of detail into a single page.
This one illustrates the difference between session tokens and JSON web tokens (JWT) and then goes on to show how JWTs are the backbone of modern single sign on (SSO) and OAuth flows.
(via https://substack-post-media.s3.amazonaws.com/public/images/041727d8-aaba-4c1d-8b74-b2c26e2e05e2_1446x1890.png (1446×1890))
1 note
·
View note
Text
How To Generate JWT Token
Welcome To the Article About How To Generate JWT Token (JSON Web Token)! In this article, we will discuss the concept of the JWT token, the benefits of using it, how to generate it, and the security considerations that come with it. We will also explore how to use JWT token authentication in your applications. By the end of this blog, you will have a better understanding of JWT token and how to…

View On WordPress
#generate a JSON Web Token#Generate jwt Token#How to generate a JSON Web Token#How To Generate jwt Token#how to generate jwt token in python#how to generate jwt token online
0 notes
Text
how i discovered akuma homura was in magia record
so magia record's twitter posted a link to an anniversary website said to contain hints at who its anniversary unit will be

throughout this website there were a few codes in base64, parts of a JWT token. as well, a series of numbers at the bottom.

when you go to the secret page of the site, it announces to you that you've found more hints. going back to the main section and sharing the contest-entrance tweet will get you an image with one of forty codes that correspond with one of those numbers. this is the one i got!

when you put all forty together, eventually, you'll get yourself a code. it is as follows:
O4W7TwhxYieUU8FFDPWv4FpkKnqmzRtl6TE9ps4dGWA
going back to the website, there's another sub-page called settoken, where you need to insert all the data you've found scrounging the site.

hitting set and going back to the secret page will bring you here.


the shield's ascii art is,
also, a png in text form, and when converted, you get a tiny image of akuma homura's insignia.


and this is where the story ends. thank god. i cant wait to waste a million dollars rolling for akuhomu
#magia record#madoka magica#puella magi madoka magica#pmmm#magireco#homura akemi#akuma homura#homucifer#akemi homura#angel analysis
268 notes
·
View notes
Text
As someone whose work heavily involves making computer systems talk to one another I've come to the conclusion that robot girls are perfectly capable of being stupid but it wont be anything like "She's bad at math </3" as a chatgpt joke or whatever it'll be some shit like "The JWT Bearer Token she uses to retrieve information from the robot girl information exchange returned a code 500 and she's going uuuuuuuuuhhhhhhhhhhhhhhhhhhhh as the connection retries until it inevitably times out"
25 notes
·
View notes
Text
How to Protect Your Laravel App from JWT Attacks: A Complete Guide
Introduction: Understanding JWT Attacks in Laravel
JSON Web Tokens (JWT) have become a popular method for securely transmitting information between parties. However, like any other security feature, they are vulnerable to specific attacks if not properly implemented. Laravel, a powerful PHP framework, is widely used for building secure applications, but developers must ensure their JWT implementation is robust to avoid security breaches.

In this blog post, we will explore common JWT attacks in Laravel and how to protect your application from these vulnerabilities. We'll also demonstrate how you can use our Website Vulnerability Scanner to assess your application for potential vulnerabilities.
Common JWT Attacks in Laravel
JWT is widely used for authentication purposes, but several attacks can compromise its integrity. Some of the most common JWT attacks include:
JWT Signature Forgery: Attackers can forge JWT tokens by modifying the payload and signing them with weak or compromised secret keys.
JWT Token Brute-Force: Attackers can attempt to brute-force the secret key used to sign the JWT tokens.
JWT Token Replay: Attackers can capture and replay JWT tokens to gain unauthorized access to protected resources.
JWT Weak Algorithms: Using weak signing algorithms, such as HS256, can make it easier for attackers to manipulate the tokens.
Mitigating JWT Attacks in Laravel
1. Use Strong Signing Algorithms
Ensure that you use strong signing algorithms like RS256 or ES256 instead of weak algorithms like HS256. Laravel's jwt-auth package allows you to configure the algorithm used to sign JWT tokens.
Example:
// config/jwt.php 'algorithms' => [ 'RS256' => \Tymon\JWTAuth\Providers\JWT\Provider::class, ],
This configuration will ensure that the JWT is signed using the RSA algorithm, which is more secure than the default HS256 algorithm.
2. Implement Token Expiry and Refresh
A common issue with JWT tokens is that they often lack expiration. Ensure that your JWT tokens have an expiry time to reduce the impact of token theft.
Example:
// config/jwt.php 'ttl' => 3600, // Set token expiry time to 1 hour
In addition to setting expiry times, implement a refresh token mechanism to allow users to obtain a new JWT when their current token expires.
3. Validate Tokens Properly
Proper token validation is essential to ensure that JWT tokens are authentic and have not been tampered with. Use Laravel’s built-in functions to validate the JWT and ensure it is not expired.
Example:
use Tymon\JWTAuth\Facades\JWTAuth; public function authenticate(Request $request) { try { // Validate JWT token JWTAuth::parseToken()->authenticate(); } catch (\Tymon\JWTAuth\Exceptions\JWTException $e) { return response()->json(['error' => 'Token is invalid or expired'], 401); } }
This code will catch any JWT exceptions and return an appropriate error message to the user if the token is invalid or expired.
4. Secure JWT Storage
Always store JWT tokens in secure locations, such as in HTTP-only cookies or secure local storage. This minimizes the risk of token theft via XSS attacks.
Example (using HTTP-only cookies):
// Setting JWT token in HTTP-only cookie $response->cookie('token', $token, $expirationTime, '/', null, true, true);
Testing Your JWT Security with Our Free Website Security Checker
Ensuring that your Laravel application is free from vulnerabilities requires ongoing testing. Our free Website Security Scanner helps identify common vulnerabilities, including JWT-related issues, in your website or application.
To check your site for JWT-related vulnerabilities, simply visit our tool and input your URL. The tool will scan for issues like weak algorithms, insecure token storage, and expired tokens.

Screenshot of the free tools webpage where you can access security assessment tools.
Example of a Vulnerability Assessment Report
Once the scan is completed, you will receive a detailed vulnerability assessment report to check Website Vulnerability. Here's an example of what the report might look like after checking for JWT security vulnerabilities.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
By addressing these vulnerabilities, you can significantly reduce the risk of JWT-related attacks in your Laravel application.
Conclusion: Securing Your Laravel Application from JWT Attacks
Securing JWT tokens in your Laravel application is essential to protect user data and maintain the integrity of your authentication system. By following the steps outlined in this post, including using strong algorithms, implementing token expiry, and validating tokens properly, you can safeguard your app from common JWT attacks.
Additionally, make sure to regularly test your application for vulnerabilities using tools like our Website Security Checker. It’s a proactive approach that ensures your Laravel application remains secure against JWT attacks.
For more security tips and detailed guides, visit our Pentest Testing Corp.
2 notes
·
View notes
Text
Base64 URL Encoder and Decoder with UTF-8 support - base64url
Base64url is a lightweight, straightforward TypeScript library that encodes and decodes Base64 URLs for JavaScript strings with comprehensive UTF-8 support. It can be useful for developers working with JSON Web Tokens (JWTs) or those involved in encoding JavaScript strings to UTF-8 for binary formats. How to use it: 1. Download the package and import the following modules into your…
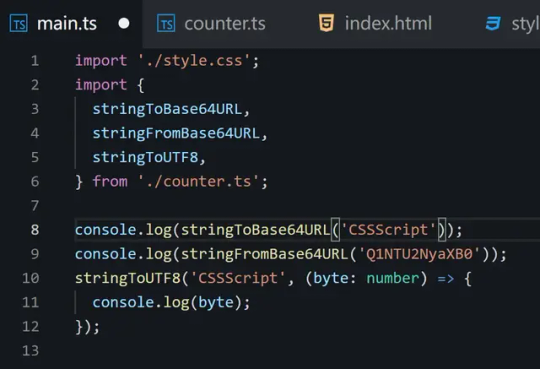
View On WordPress
4 notes
·
View notes
Text
Advanced Techniques in Full-Stack Development

Certainly, let's delve deeper into more advanced techniques and concepts in full-stack development:
1. Server-Side Rendering (SSR) and Static Site Generation (SSG):
SSR: Rendering web pages on the server side to improve performance and SEO by delivering fully rendered pages to the client.
SSG: Generating static HTML files at build time, enhancing speed, and reducing the server load.
2. WebAssembly:
WebAssembly (Wasm): A binary instruction format for a stack-based virtual machine. It allows high-performance execution of code on web browsers, enabling languages like C, C++, and Rust to run in web applications.
3. Progressive Web Apps (PWAs) Enhancements:
Background Sync: Allowing PWAs to sync data in the background even when the app is closed.
Web Push Notifications: Implementing push notifications to engage users even when they are not actively using the application.
4. State Management:
Redux and MobX: Advanced state management libraries in React applications for managing complex application states efficiently.
Reactive Programming: Utilizing RxJS or other reactive programming libraries to handle asynchronous data streams and events in real-time applications.
5. WebSockets and WebRTC:
WebSockets: Enabling real-time, bidirectional communication between clients and servers for applications requiring constant data updates.
WebRTC: Facilitating real-time communication, such as video chat, directly between web browsers without the need for plugins or additional software.
6. Caching Strategies:
Content Delivery Networks (CDN): Leveraging CDNs to cache and distribute content globally, improving website loading speeds for users worldwide.
Service Workers: Using service workers to cache assets and data, providing offline access and improving performance for returning visitors.
7. GraphQL Subscriptions:
GraphQL Subscriptions: Enabling real-time updates in GraphQL APIs by allowing clients to subscribe to specific events and receive push notifications when data changes.
8. Authentication and Authorization:
OAuth 2.0 and OpenID Connect: Implementing secure authentication and authorization protocols for user login and access control.
JSON Web Tokens (JWT): Utilizing JWTs to securely transmit information between parties, ensuring data integrity and authenticity.
9. Content Management Systems (CMS) Integration:
Headless CMS: Integrating headless CMS like Contentful or Strapi, allowing content creators to manage content independently from the application's front end.
10. Automated Performance Optimization:
Lighthouse and Web Vitals: Utilizing tools like Lighthouse and Google's Web Vitals to measure and optimize web performance, focusing on key user-centric metrics like loading speed and interactivity.
11. Machine Learning and AI Integration:
TensorFlow.js and ONNX.js: Integrating machine learning models directly into web applications for tasks like image recognition, language processing, and recommendation systems.
12. Cross-Platform Development with Electron:
Electron: Building cross-platform desktop applications using web technologies (HTML, CSS, JavaScript), allowing developers to create desktop apps for Windows, macOS, and Linux.
13. Advanced Database Techniques:
Database Sharding: Implementing database sharding techniques to distribute large databases across multiple servers, improving scalability and performance.
Full-Text Search and Indexing: Implementing full-text search capabilities and optimized indexing for efficient searching and data retrieval.
14. Chaos Engineering:
Chaos Engineering: Introducing controlled experiments to identify weaknesses and potential failures in the system, ensuring the application's resilience and reliability.
15. Serverless Architectures with AWS Lambda or Azure Functions:
Serverless Architectures: Building applications as a collection of small, single-purpose functions that run in a serverless environment, providing automatic scaling and cost efficiency.
16. Data Pipelines and ETL (Extract, Transform, Load) Processes:
Data Pipelines: Creating automated data pipelines for processing and transforming large volumes of data, integrating various data sources and ensuring data consistency.
17. Responsive Design and Accessibility:
Responsive Design: Implementing advanced responsive design techniques for seamless user experiences across a variety of devices and screen sizes.
Accessibility: Ensuring web applications are accessible to all users, including those with disabilities, by following WCAG guidelines and ARIA practices.
full stack development training in Pune
2 notes
·
View notes
Text
You can learn NodeJS easily, Here's all you need:
1.Introduction to Node.js
• JavaScript Runtime for Server-Side Development
• Non-Blocking I/0
2.Setting Up Node.js
• Installing Node.js and NPM
• Package.json Configuration
• Node Version Manager (NVM)
3.Node.js Modules
• CommonJS Modules (require, module.exports)
• ES6 Modules (import, export)
• Built-in Modules (e.g., fs, http, events)
4.Core Concepts
• Event Loop
• Callbacks and Asynchronous Programming
• Streams and Buffers
5.Core Modules
• fs (File Svstem)
• http and https (HTTP Modules)
• events (Event Emitter)
• util (Utilities)
• os (Operating System)
• path (Path Module)
6.NPM (Node Package Manager)
• Installing Packages
• Creating and Managing package.json
• Semantic Versioning
• NPM Scripts
7.Asynchronous Programming in Node.js
• Callbacks
• Promises
• Async/Await
• Error-First Callbacks
8.Express.js Framework
• Routing
• Middleware
• Templating Engines (Pug, EJS)
• RESTful APIs
• Error Handling Middleware
9.Working with Databases
• Connecting to Databases (MongoDB, MySQL)
• Mongoose (for MongoDB)
• Sequelize (for MySQL)
• Database Migrations and Seeders
10.Authentication and Authorization
• JSON Web Tokens (JWT)
• Passport.js Middleware
• OAuth and OAuth2
11.Security
• Helmet.js (Security Middleware)
• Input Validation and Sanitization
• Secure Headers
• Cross-Origin Resource Sharing (CORS)
12.Testing and Debugging
• Unit Testing (Mocha, Chai)
• Debugging Tools (Node Inspector)
• Load Testing (Artillery, Apache Bench)
13.API Documentation
• Swagger
• API Blueprint
• Postman Documentation
14.Real-Time Applications
• WebSockets (Socket.io)
• Server-Sent Events (SSE)
• WebRTC for Video Calls
15.Performance Optimization
• Caching Strategies (in-memory, Redis)
• Load Balancing (Nginx, HAProxy)
• Profiling and Optimization Tools (Node Clinic, New Relic)
16.Deployment and Hosting
• Deploying Node.js Apps (PM2, Forever)
• Hosting Platforms (AWS, Heroku, DigitalOcean)
• Continuous Integration and Deployment-(Jenkins, Travis CI)
17.RESTful API Design
• Best Practices
• API Versioning
• HATEOAS (Hypermedia as the Engine-of Application State)
18.Middleware and Custom Modules
• Creating Custom Middleware
• Organizing Code into Modules
• Publish and Use Private NPM Packages
19.Logging
• Winston Logger
• Morgan Middleware
• Log Rotation Strategies
20.Streaming and Buffers
• Readable and Writable Streams
• Buffers
• Transform Streams
21.Error Handling and Monitoring
• Sentry and Error Tracking
• Health Checks and Monitoring Endpoints
22.Microservices Architecture
• Principles of Microservices
• Communication Patterns (REST, gRPC)
• Service Discovery and Load Balancing in Microservices
1 note
·
View note
Link
OAuth or JWT? Everything Developers Need to Know in 2025
In contemporary software development, authorization and authentication are essential elements. OAuth and JWT (JSON Web Tokens) are two of the most widely used protocols and standards available to developers today. Despite their frequent usage together, they have distinct functions and cannot be substituted for one another. This article gives a thorough side-by-side analysis of OAuth and JWT, explaining how each functions, when to use it, and why it’s important for contemporary application security...
Learn more here:
https://www.nilebits.com/blog/2025/05/oauth-jwt-everything-need-know-2025/
0 notes
Text
0 notes
Text
Securing API Integrations: Best Practices for Contact Form Data Transmission
In today’s digital ecosystem, contact forms are more than just entry points for customer inquiries—they’re gateways to critical data that drive business operations. Whether the information is funneled into a CRM, ticketing system, or email marketing platform, the underlying mechanism that powers this is API integration. But with increasing cyber threats and stricter data regulations, securing the transmission of contact form data through APIs has never been more important.
This blog delves into the best practices for ensuring your contact form data is transmitted securely via API integrations, covering encryption, authentication, compliance, and more.

Why Securing Contact Form Data Matters
Contact forms often collect personally identifiable information (PII), such as:
Names
Email addresses
Phone numbers
Company names
Inquiry messages
Unsecured transmission of this data can lead to breaches, phishing attacks, or unauthorized access—exposing businesses to legal consequences and reputational damage. Secure API integration mitigates these risks and ensures data integrity, privacy, and compliance with laws like GDPR, HIPAA, and CCPA.
Common Threats to API-Based Data Transmission
Before diving into the best practices, it's important to understand the threats you’re defending against:
Man-in-the-middle (MITM) attacks – where data is intercepted between the contact form and the API.
Unauthorized access – due to poor authentication or exposed API keys.
Injection attacks – through unsanitized input, enabling attackers to manipulate API calls.
Data leakage – from insecure storage or logging mechanisms.
Replay attacks – where a malicious user resends legitimate API requests to gain unauthorized access or cause disruptions.
Best Practices for Securing API Integrations with Contact Forms
1. Use HTTPS with SSL/TLS Encryption
The first and most critical step is to ensure all communication between the form, your server, and any third-party APIs happens over HTTPS. HTTPS encrypts the data in transit, making it nearly impossible for attackers to intercept and read sensitive information.
Pro tip: Use strong TLS configurations and ensure your SSL certificate is up to date.
2. Implement Strong Authentication and Authorization
APIs must be protected by robust authentication mechanisms. Relying solely on static API keys can be risky if they’re not stored securely or become exposed.
Best practices include:
OAuth 2.0 – A widely accepted protocol for secure delegated access.
JWT (JSON Web Tokens) – Allows secure transmission of claims between parties.
IP whitelisting – Restrict API access to known IP addresses.
Role-based access control (RBAC) – Ensure only authorized applications and users have access.
3. Validate and Sanitize Input Data
Never trust data coming from a user-facing contact form. Always validate and sanitize inputs before processing or transmitting them to an API to prevent injection attacks.
Validation examples:
Use regex patterns to validate email formats.
Limit message length to prevent buffer overflows.
Sanitize inputs by removing or escaping special characters.
4. Rate Limiting and Throttling
Implement API rate limiting to protect your integration from abuse. Bots or attackers may try to flood your endpoints with traffic, potentially leading to denial-of-service (DoS) attacks or data scraping.
Suggested limits:
Max 60 requests per minute per IP
Max 1000 requests per day per user
Use appropriate HTTP response headers like 429 Too Many Requests to inform clients of limits.
5. Encrypt Data at Rest and in Transit
While HTTPS encrypts data in transit, you should also encrypt sensitive data at rest if you're storing it temporarily before pushing it to an API.
Encryption standards to consider:
AES-256 for data at rest
TLS 1.2 or higher for data in transit
Never store unencrypted form submissions on disk, in logs, or database tables.
6. Use Web Application Firewalls (WAFs)
A WAF helps filter out malicious requests to your contact form and API endpoints. They block suspicious IPs, detect bots, and protect against common OWASP Top 10 threats.
Features to look for:
SQL injection protection
Cross-site scripting (XSS) filters
Geo-blocking for unknown regions
Cloudflare, AWS WAF, and Sucuri are popular options.
7. Secure API Keys and Secrets
API credentials should never be hardcoded into frontend code or exposed in browser-accessible scripts. Instead:
Store secrets in server-side environment variables.
Use secret management tools like HashiCorp Vault or AWS Secrets Manager.
Rotate keys periodically and revoke unused credentials.
8. Enable Logging and Monitoring
Real-time monitoring can alert you to anomalies like spikes in traffic or repeated failed API calls, indicating an attack or integration issue.
What to log:
Timestamped request metadata
Status codes and error responses
Authentication failures
Ensure logs themselves do not store sensitive information, and secure them with proper access control.
9. Implement CSRF and CAPTCHA Protection
To prevent bots and malicious actors from abusing your contact form, use:
CSRF tokens to verify that a submission originated from your site.
CAPTCHAs or reCAPTCHA to block automated submissions.
This reduces the risk of your API being bombarded with spam or test payloads.
10. Follow the Principle of Least Privilege
Only allow the contact form integration to access what it absolutely needs. If the form only needs to create a lead in a CRM, don’t give it permission to delete or modify records.
This principle minimizes potential damage if credentials are compromised.
11. Secure Third-Party Services
If your contact form integrates with external APIs (e.g., HubSpot, Mailchimp, Salesforce), ensure these services:
Use HTTPS exclusively
Provide granular API scopes
Offer audit trails
Comply with regulations like GDPR and SOC 2
Always vet vendors for their security posture before integration.
12. Test for Vulnerabilities Regularly
Conduct regular penetration testing and vulnerability scans to uncover weak spots in your form and API integration. Include both automated tools and manual ethical hacking.
Tools to try:
OWASP ZAP
Burp Suite
Postman Security Testing
Fix any discovered vulnerabilities immediately and document the fixes.
13. Comply with Data Protection Regulations
Different regions have specific laws about how user data should be collected, stored, and transmitted. For example:
GDPR (EU): Requires explicit user consent and secure handling of PII.
CCPA (California): Grants users the right to know and delete their data.
HIPAA (US): Regulates health-related data.
Make sure your API-based contact form integration complies with relevant laws, especially if collecting data from users in regulated industries.
14. Include a Clear Privacy Policy
Your contact form should link to a privacy policy explaining:
What data is collected
How it will be used
Where it will be transmitted
How long it will be stored
This not only ensures compliance but also builds trust with users.
15. Fail Gracefully and Securely
Even with all protections, failures can occur. Ensure your contact form and API integration handle errors securely:
Don’t expose stack traces or internal server information in error responses.
Avoid leaking API credentials in logs or responses.
Inform the user of a failure without revealing system details.
Use secure error handling to maintain a good user experience while protecting your backend.
Conclusion
Securing API integrations for contact form data transmission is not optional—it’s a necessity in a world where data breaches are commonplace and user privacy is paramount. From implementing HTTPS and strong authentication to input validation and compliance, each layer of protection contributes to a robust, secure system.
Organizations that proactively secure their contact form integrations not only protect themselves from cyber threats but also enhance their credibility and user trust. By adopting these best practices, you're not just guarding data—you're safeguarding your brand.
0 notes