#Sensor Data Acquisition
Explore tagged Tumblr posts
Text
Mastering Data Collection in Machine Learning: A Comprehensive Guide -
Artificial intelligence, mastering the art of data collection is paramount to unlocking the full potential of machine learning algorithms. By adopting systematic methods, overcoming challenges, and adopting best practices, organizations can harness the power of data to drive innovation, gain competitive advantage, and provide transformative solutions across various domains. Through careful data collection, Globose Technology Solutions remains at the forefront of AI innovation, enabling clients to harness the power of data-driven insights for sustainable growth and success.
#Data Collection#Machine Learning#Artificial Intelligence#Data Quality#Data Privacy#Web Scraping#Sensor Data Acquisition#Data Labeling#Bias in Data#Data Analysis#Public Datasets#Data-driven Decision Making#Data Mining#Data Visualization#data collection company#dataset
1 note
·
View note
Text
Front Brake Speed Sensor Kits for Drag Racing – Strange Engineering

Drag racing is a competitive sport, and using quality adjustment tools is crucial to staying ahead of your competition. Small adjustments need to be made carefully in the car so that it can provide the maximum benefits in the competition. Front Brake Speed Sensor Kit is one of those important small adjustments that should not be neglected. This component plays an important role in providing stability to the driver while doing drag racing.
The Value of Front Wheel Data
Drag racing isn’t just about speed—it’s about control and consistency. Most racers are familiar with rear wheel sensors, but adding a sensor to the front brakes offers unique insights. These kits track front wheel rotation during launch and braking, offering data that helps diagnose traction issues, brake timing, and suspension behavior.
This forward-looking approach allows teams to understand how their cars behave at the most critical points of a run. Without it, you're missing half the story.
Designed for the Track, Built for Abuse
Race environments are punishing. Heat, high RPMs, vibration, and abrupt force changes mean that only the toughest components survive. That’s why selecting sensor kits designed for racing, not adapted from street vehicles, is crucial.
High-grade materials and motorsport-focused designs ensure these sensors can deliver clean, uninterrupted signals every run. From sealed wiring to strong mounting hardware, durability isn’t optional—it’s expected.
Installation and Compatibility Matter
A solid sensor is only as good as its installation. Alignment, spacing, and secure mounting are key to avoiding signal errors or component wear. Quality kits offer user-friendly setup options that work seamlessly with major data acquisition systems.
Once in place, a properly installed sensor kit will begin generating actionable insights immediately. Fewer adjustments, faster calibration, and better accuracy mean more time fine-tuning performance, and less time troubleshooting.
Smarter Data Leads to Smarter Decisions
What makes these kits so powerful is the ability to reveal patterns drivers can’t feel. For instance, consistent early deceleration on one wheel may indicate imbalance or hidden chassis issues. Without this feedback, teams might continue tuning around a problem they didn’t know existed.
By integrating this information with other data sources, teams can refine setup decisions that impact every launch, shift, and braking point.
Why Front Sensors Are Gaining Popularity
Front brake speed sensors have become more common in top-tier racing, not because of a trend, but because of results. Racers who embrace this technology often find themselves one step ahead—predicting problems, dialing in performance, and maintaining mechanical health better than those relying on guesswork.
With any racing tool, there is a matter of quality. Drag-specific kits tested in actual track conditions provide unparalleled reliability and value.
A Trusted Source for Race-Grade Components
This is where Strange Engineering continues to set the standard. Known for delivering parts that hold up under extreme pressure, they offer Front Brake Speed Sensor Kits that racers trust for performance and longevity. Whether you’re a weekend warrior or a seasoned pro, having dependable data from the front wheels can be the edge you’ve been missing.
Conclusion
When you're racing for every hundredth of a second, trusted feedback becomes very important for your progress. A front brake speed sensor kit is an investment, yes, but the insights it provides can be life-changing. In a sport where control is speed, it's the silent data that tends to speak the loudest.
#front brake speed sensor kit#drag racing brake sensors#Strange Engineering brake sensors#race car speed sensor kits#front wheel speed sensor#brake system sensor kit#drag car data acquisition#high-performance brake sensors#motorsports sensor kits#front brake monitoring#front brake speed sensor kits#drag racing brake speed sensors#Strange Engineering front brake sensor#race car front wheel sensor#brake system speed monitoring#drag racing data acquisition sensors#high performance racing sensors#front wheel data logging sensor#drag racing brake components#brake sensor kits for race cars
0 notes
Text
Enhancing Structural Integrity: The Role of Structural Health Monitoring
Structural Health Monitoring (SHM) is a revolutionary discipline within civil engineering that employs advanced technologies to ensure the ongoing safety, reliability, and longevity of structures. In an era where infrastructure serves as the backbone of societal progress, the proactive and data-driven approach of SHM has become increasingly vital. Structural Health Monitoring (Source:…

View On WordPress
#civil engineering#Communication Systems#Corrosion#Data Acquisition#Data Analysis#Deterioration#Fatigue#Offshore Structures#Sensor Networks#Structural Health Monitoring
0 notes
Text
Battery-operated Remote Terminal Units Market Research, Size, Share, Analysis, Overview and Regional Outlook Study 2017 – 2032
The market for Remote Terminal Units (RTUs) that are battery-operated allows them to function in isolated or off-grid regions where access to a reliable power supply is restricted. RTUs are electronic devices used to monitor and manage remote equipment and processes in many different industries, such as oil and gas, water and wastewater management, power distribution, and telecommunications. Here is a summary of the market for battery-operated RTUs, including information on demand:
Market Overview: Due to a number of circumstances, the market for battery-operated RTUs has been expanding. The need for battery-operated RTUs has been fueled by the necessity for remote monitoring and control capabilities in various industries, particularly in places with weak power infrastructure. These devices enable efficient monitoring and control of remote assets without the requirement for a continual external power source thanks to their dependable and autonomous operation.
Demand Drivers:
1. Real-time monitoring and control of assets: situated in remote or isolating locations are necessary in many businesses. Without the requirement for a sizable power infrastructure or reliance on cable connections, battery-operated RTUs allow for effective data gathering, monitoring, and control of these assets.
2. Applications Off-Grid: In off-grid applications where access to a dependable power supply is restricted or nonexistent, battery-operated RTUs are widely used. Examples include remote water pumping stations in rural areas, environmental monitoring stations, remote weather monitoring stations, and remote oil and gas wellheads.
3. Emergency and Temporary Installations: Whereas immediate deployment is necessary, battery-powered RTUs are also used in emergency and temporary installations. When catastrophe recovery, building projects, or temporary infrastructure installations are taking place, these machines can instantly provide remote monitoring and control capabilities.
4. Environmental Monitoring: Data collection from remote weather stations, air quality sensors, and water quality sensors are all important aspects of environmental monitoring that battery-operated RTUs play a key role in. Continuous monitoring is made possible in remote or environmentally delicate locations by these equipment.
5. IoT Connectivity: The need for battery-operated RTUs has increased as the Internet of Things (IoT) is becoming more widely used in a variety of businesses. These devices are essential parts of IoT networks because they provide seamless data transmission, communication, and control between remote assets and central management systems.
Here are some of the key benefits for Stakeholders:
Remote Monitoring and Control
Flexibility and Mobility
Cost-Effective Deployment
Resilience to Power Outages
Integration with IoT and Smart Grids
Increased Data Accessibility
Environmental Monitoring and Compliance
Rapid Deployment for Emergency Response
Redundancy and Reliability
Scalability and Future-Proofing
We recommend referring our Stringent datalytics firm, industry publications, and websites that specialize in providing market reports. These sources often offer comprehensive analysis, market trends, growth forecasts, competitive landscape, and other valuable insights into this market.
By visiting our website or contacting us directly, you can explore the availability of specific reports related to this market. These reports often require a purchase or subscription, but we provide comprehensive and in-depth information that can be valuable for businesses, investors, and individuals interested in this market.
“Remember to look for recent reports to ensure you have the most current and relevant information.”
Click Here, To Get Free Sample Report: https://stringentdatalytics.com/sample-request/battery-operated-remote-terminal-units-market/10333/
Market Segmentations:
Global Battery-operated Remote Terminal Units Market: By Company • SIEMENS • SENECA • Omniflex • King Pigeon Communication Co.,Limited �� Servelec Group • TEKBOX • Micro Sensor Co., Ltd. • Hitachi Group • Remsdaq Ltd Global Battery-operated Remote Terminal Units Market: By Type • GPRS • GSM • Modular • Others Global Battery-operated Remote Terminal Units Market: By Application • Power Industry • Government and Utilities • Industrial Global Battery-operated Remote Terminal Units Market: Regional Analysis The regional analysis of the global Battery-operated Remote Terminal Units market provides insights into the market's performance across different regions of the world. The analysis is based on recent and future trends and includes market forecast for the prediction period. The countries covered in the regional analysis of the Battery-operated Remote Terminal Units market report are as follows: North America: The North America region includes the U.S., Canada, and Mexico. The U.S. is the largest market for Battery-operated Remote Terminal Units in this region, followed by Canada and Mexico. The market growth in this region is primarily driven by the presence of key market players and the increasing demand for the product. Europe: The Europe region includes Germany, France, U.K., Russia, Italy, Spain, Turkey, Netherlands, Switzerland, Belgium, and Rest of Europe. Germany is the largest market for Battery-operated Remote Terminal Units in this region, followed by the U.K. and France. The market growth in this region is driven by the increasing demand for the product in the automotive and aerospace sectors. Asia-Pacific: TheAsia-Pacific region includes Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, China, Japan, India, South Korea, and Rest of Asia-Pacific. China is the largest market for Battery-operated Remote Terminal Units in this region, followed by Japan and India. The market growth in this region is driven by the increasing adoption of the product in various end-use industries, such as automotive, aerospace, and construction. Middle East and Africa: The Middle East and Africa region includes Saudi Arabia, U.A.E, South Africa, Egypt, Israel, and Rest of Middle East and Africa. The market growth in this region is driven by the increasing demand for the product in the aerospace and defense sectors. South America: The South America region includes Argentina, Brazil, and Rest of South America. Brazil is the largest market for Battery-operated Remote Terminal Units in this region, followed by Argentina. The market growth in this region is primarily driven by the increasing demand for the product in the automotive sector.
Visit Report Page for More Details: https://stringentdatalytics.com/reports/battery-operated-remote-terminal-units-market/10333/
Reasons to Purchase Battery-operated Remote Terminal Units Market Report:
• To obtain insights into industry trends and dynamics, including market size, growth rates, and important factors and difficulties. This study offers insightful information on these topics.
• To identify important participants and rivals: This research studies can assist companies in identifying key participants and rivals in their sector, along with their market share, business plans, and strengths and weaknesses.
• To comprehend consumer behaviour: these research studies can offer insightful information about customer behaviour, including preferences, spending patterns, and demographics.
• To assess market opportunities: These research studies can aid companies in assessing market chances, such as prospective new goods or services, fresh markets, and new trends.
In general, market research studies offer companies and organisations useful data that can aid in making decisions and maintaining competitiveness in their industry. They can offer a strong basis for decision-making, strategy formulation, and company planning.
About US:
Stringent Datalytics offers both custom and syndicated market research reports. Custom market research reports are tailored to a specific client's needs and requirements. These reports provide unique insights into a particular industry or market segment and can help businesses make informed decisions about their strategies and operations.
Syndicated market research reports, on the other hand, are pre-existing reports that are available for purchase by multiple clients. These reports are often produced on a regular basis, such as annually or quarterly, and cover a broad range of industries and market segments. Syndicated reports provide clients with insights into industry trends, market sizes, and competitive landscapes. By offering both custom and syndicated reports, Stringent Datalytics can provide clients with a range of market research solutions that can be customized to their specific needs
Contact US:
Stringent Datalytics
Contact No - +1 346 666 6655
Email Id - [email protected]
Web - https://stringentdatalytics.com/
#Battery-operated Remote Terminal Units#RTU Market#Remote Monitoring#Wireless RTU#Industrial Automation#Battery-powered RTU#IoT (Internet of Things)#Energy Efficiency#Data Collection#Telemetry#Remote Control#Battery-powered Sensors#SCADA (Supervisory Control and Data Acquisition)#Energy Management#Off-grid Applications#Renewable Energy#Battery Technology#Remote Sensing#Communication Protocols#Edge Computing#Connectivity Solutions#Remote Data Acquisition#Condition Monitoring#Asset Management.
0 notes
Text
My TFP Soundwave ramblings (be warned cuz there are many words)


I was gonna draw today but the prospect of it felt overwhelming for some reason so instead I’m just gonna talk about TFP Soundwave’s alt mode (a UAV/ reaper drone) just cuz I was reading about it and I like how I could link stuff between how he is and how reaper drones are.
So basically, one of the first things I wanna mention is that reaper drones/UAVs are unmanned aerial vehicles (given the whole “drone” thing and what UAV even means) but to me that just sorta makes sense for Soundwave in regard to his more.. Unsettling, robotic/alien-like behavior and movements? As well as his silence and usual distance from the front lines and his lack of showing face/(social?) detachment from like everyone else other than Laserbeak (don’t ask, it just makes sense to me). Reaper drones were also made to work at first only in intelligence, surveillance, and reconnaissance roles; but eventually additionally a hunter-killer role which you can kinda see in Soundwave’s character in the show (my best example is the scene where he retrieves Laserbeak from Ratchet, super cool creepy behavior from him, just waiting for something or someone to make any noise or any movement). When he has a mission, he’s most definitely getting it done, he stalks and lurks and takes action when the time is just Right; he’s very pinpoint accurate in Prime.
Reaper drones were also made to provide “deadly persistence” capability, being able to fly over areas night and day waiting for a target to present itself, or to survey for LONG long amounts of time. Which to me correlates to how he’s able to stand still and do work and wait and listen and watch and do everything for So Long as he does in the show (and tolerate Starscream— or like everyone actually for so long 🙄).

Reapers also utilize satellite communications for command and control (as in, they kinda literally have satellite dishes in them I think that’s what that is?), so that to me also easily parallels Soundwave's abilities with the space bridges and kind of his visor being computer-like as well (and that time he used an. Antenna satellite thing? To look for signals or whatever). They also use other multiple sensors to target and observe, which include optical (high resolution imagery for identification and target acquisition), infrared, and radar systems (enables the drone to locate and track targets regardless of weather conditions or visibility). Which imo links to how Soundwave is described as the “eyes and ears of the decepticons”.
They carry many weapons but I’m not really gonna get into that tbh cuz. Idk. Don’t wanna. Also TFP Soundwave doesn’t fight often anyways and when he does it’s mostly just straight hands (and data cables). And this is as far as my not the most accurate of ramblings most likely but just one I wanted to make because there’s just a Lot from so Little of TFP Soundwave I just love to think about it. Was I geeked out writing this? Maybe, so what 😒
#If there’s one thing about Soundwave it’s that he’s one hell of a capable mech.#Like you really gotta give it to him#transformers#soundwave#transformers prime#tfp#tfp soundwave#maccadam#transformers analysis#transformer#decepticons
569 notes
·
View notes
Text

U.S. Approves Foreign Military Sale for South Korean F-15K Upgrade
The State Department has approved the possible sale of components that will allow South Korea to upgrade its F-15K Slam Eagle fleet to a configuration similar to the F-15EX Eagle II.
Stefano D'Urso
F-15K upgrade
The U.S. State Department has approved on Nov.19, 2024, a possible Foreign Military Sale (FMS) to the Republic of Korea of components that will allow the upgrade of the country’s F-15K Slam Eagle fleet. The package, which has an estimated cost of $6.2 billion, follows the decision in 2022 to launch an upgrade program for the aircraft.
The State Department has approved the possible sale of components that will allow South Korea to upgrade its F-15K Slam Eagle fleet to a configuration similar to the F-15EX Eagle II.The F-15KThe new capabilities
The Slam Eagles are the mainstay of the Republic of Korea Air Force’s (ROKAF) multirole missions, with a particular ‘heavy hitting’ long-range strike role. According to the available data, the country operates 59 F-15Ks out of 61 which were initially fielded in 2005. In 2022, the Defense Acquisition Program Administration (DAPA) approved the launch of an upgrade program planned to run from 2024 to 2034.
In particular, the Defense Security Cooperation Agency’s (DSCA) FMS notice says a number of components were requested for the upgrade, including 96 Advanced Display Core Processor II (ADCP II) mission system computers, 70 AN/APG-82(v)1 Active Electronically Scanned Arrays (AESA) radars, seventy 70 AN/ALQ-250 Eagle Passive Active Warning Survivability System (EPAWSS) electronic warfare (EW) suites and 70 AN/AAR-57 Common Missile Warning Systems (CMWS).
In addition to these, South Korea will also get modifications and maintenance support, aircraft components and spares, consumables, training aids and the entire support package commonly associated with FMS. It is interesting to note that the notice also includes aerial refueling support and aircraft ferry support, so it is possible that at least the initial aircraft will be ferried to the United States for the modifications before the rest are modified in country.

A ROKAF F-15K Slam Eagle drops two GBU-31 JDAM bombs with BLU-109 warhead. (Image credit: ROKAF)
The components included in the possible sale will allow the ROKAF to upgrade its entire fleet of F-15Ks to a configuration similar to the new F-15EX Eagle II currently being delivered to the U.S. Air Force. Interestingly, the Korean configuration will also include the CMWS, currently not installed on the EX, so the F-15K will also require some structural modifications to add the blisters on each side of the canopy rail where the sensors are installed.
“This proposed sale will improve the Republic of Korea’s capability to meet current and future threats by increasing its critical air defence capability to deter aggression in the region and to ensure interoperability with US forces,” says the DSCA in the official notice.
The upgrade of the F-15K is part of a broader modernization of the ROKAF’s fighter fleet. In fact, the service is also upgrading its KF-16s Block 52 to the V configuration, integrating a new AESA radar, mission computer, self-protection suite, with works expected to be completed by 2025. These programs complement the acquisition of the F-35 Lightning II and the KF-21 Boramae.
Ulchi Freedom Shield 24

A ROKAF F-15K Slam Eagle, assigned to the 11th Fighter Wing at Daegu Air Base, takes off for a mission on Aug. 20, 2024. (Image credit: ROKAF)
The F-15K
The F-15K is a variant of the F-15E Strike Eagle built for the Republic of Korea Air Force’s (ROKAF) with almost half of the components manufactured locally. The aircraft emerged as the winner of the F-X fighter program against the Rafale, Typhoon and Su-35 in 2002, resulting in an order for 40 F-15s equipped with General Electric F110-129 engines. In 2005, a second order for 21 aircraft equipped with Pratt & Whitney F100-PW-229 engines was signed.
The Slam Eagle name is derived from the F-15K’s capability to employ the AGM-84H SLAM-ER standoff cruise missiles, with the Taurus KEPD 350K being another weapon exclusive to the ROKAF jet. The F-15K is employed as a fully multi-role aircraft and is considered ad one of the key assets of the Korean armed forces.
With the aircraft averaging an age of 16 years and expected to be in service until 2060, the Defense Acquisition Program Administration (DAPA) launched in 2022 an upgrade program for the F-15Ks. The upgrade, expected to run from 2024 to 2034, is committed to strengthening the mission capabilities and survivability of the jet.
The F-15K currently equips three squadrons at Daegu Air Base, in the southeast of the country. Although based far from the demilitarized zone (DMZ), the F-15K with its SLAM-ER and KEPD 350 missiles can still hit strategic targets deep behind North Korean borders.

An F-15K releases a Taurus KEPD 350K cruise missile. (Image credit: ROKAF)
The new capabilities
It is not yet clear if the F-15K will receive a new cockpit, since its configuration will be similar to the Eagle II. In fact, the F-15EX has a full glass cockpit equipped with a 10×19-inch touch-screen multifunction color display and JHMCS II both in the front and rear cockpit, Low Profile HUD in the front, stand-by display and dedicated engine, fuel and hydraulics display, in addition to the standard caution/warning lights, switches and Hands On Throttle-And-Stick (HOTAS) control.
Either way, the systems will be powered by the Advanced Display Core Processor II, reportedly the fastest mission computer ever installed on a fighter jet, and the Operational Flight Program Suite 9.1X, a customized variant of the Suite 9 used on the F-15C and F-15E, designed to ensure full interoperability of the new aircraft with the “legacy Eagles”.
The F-15K will be equipped with the new AN/APG-82(V)1 Active Electronically Scanned Array (AESA) radar. The radar, which has been developed from the APG-63(V)3 AESA radar of the F-15C and the APG-79 AESA radar of the F/A-18E/F, allows to simultaneously detect, identify and track multiple air and surface targets at longer ranges compared to mechanical radars, facilitating persistent target observation and information sharing for a better decision-making process.
F-15K upgrade

A ROKAF F-15K Slam Eagle takes off for a night mission during the Pitch Black 2024 exercise. (Image credit: Australian Defense Force)
The AN/ALQ-250 EPAWSS will provide full-spectrum EW capabilities, including radar warning, geolocation, situational awareness, and self-protection to the F-15. Chaff and flares capacity will be increased by 50%, with four more dispensers added in the EPAWSS fairings behind the tail fins (two for each fairing), for a total of 12 dispenser housing 360 cartridges.
EPAWSS is fully integrated with radar warning, geo-location and increased chaff and flare capability to detect and defeat surface and airborne threats in signal-dense and highly contested environments. Because of this, the system enables freedom of maneuver and deeper penetration into battlespaces protected by modern integrated air defense systems.
The AN/AAR-57 CMWS is an ultra-violet based missile warning system, part of an integrated IR countermeasures suite utilizing five sensors to display accurate threat location and dispense decoys/countermeasures. Although CMWS was initially fielded in 2005, BAE Systems continuously customized the algorithms to adapt to new threats and CMWS has now reached Generation 3.
@TheAviationist.com
20 notes
·
View notes
Text
To the Cabal & Those Of Baal Worship
Do you want to know a secret?
- Remember the good ole days when someone had to be wired to gather information for a sting operation?
- Remember how someone would be searched before they entered a high security area for secret meetings you didn't want recorded on record?
- Remember when you could ensure that if someone would speak of what went on you had a way to get rid of them?
I want you to think of a hypothetical technology for second. Let's call it "Bio-Sensory Neural Interface" or "Energetic Biofield Interface" (EBI)
What can this technology achieve?
• The Bio-Sensory Neural Interface (BSNI) technology represents intelligence-gathering methodologies. It leverages the interaction between advanced computational systems and the human energetic biofield to facilitate seamless, real-time communication and data acquisition from human sensory experiences.
• Utilizes sophisticated sensors to interact with the human biofield, capturing and interpreting electromagnetic signals naturally emitted by the body.
• Enables non-invasive interfacing, ensuring the integrity and operational security of the actor.
Real-Time Sensory Data Transmission:
• Converts sensory input (visual, auditory, olfactory, and tactile) into digital data streams, allowing remote operators to experience the actor's environment firsthand.
• Acts as a live sensory transceiver, making the human body a dynamic tool for intelligence collection.
Cognitive Communication:
• Facilitates direct, silent communication between the operator and the actor through thought transmission, eliminating the need for spoken words or physical devices.
• Supports bidirectional communication, enabling strategic planning and real-time adjustments through inner dialogue.
What does this basically mean in more mundane terms?
This basically eliminates the need for physical implants or external devices, reducing the risk of detection and enhancing the safety of the operative in sensitive environments. Which means you could never detect any infiltration apparatus. You could never know who is working for the good guys.
This is one reason why your plans never pan out. This is why you can never quite nail down why something didn't go as planned. This is why you can never trace or track how certain info was shared to those who were never invited to your secret clandestine meetings.
You think because you hold them while a major celebrity is performing in town that the powerful political figures attending would fly under the radar because everyone is distracted with Taylor Swift? You are some funny guys.
BSNI technology is ideally suited for intelligence operations requiring high levels of discretion and security. Its applications extend to military intelligence, covert operations, and high-stakes negotiations where traditional intelligence methods may be impractical or too intrusive. And please avoid trying to look up this technology. This is not what it is called.
This is Mind-to-Mind technology. You all have been caught with your pants down. And now you are way too far behind to catch up to how this could have possibly been used against you. Now you are scrambling. Trying to wonder how you have had to resort to outright assassination attempts. Something that wasn't on the cards before you 1st tried years ago.
Oh' well. You lose. Off to G¡tmo you go. Pain-(☠️) is in your future.
- Julian Assange
#pay attention#educate yourselves#educate yourself#knowledge is power#reeducate yourself#reeducate yourselves#think about it#think for yourselves#think for yourself#do your homework#do your own research#do your research#do some research#ask yourself questions#question everything#julian assange#news
50 notes
·
View notes
Text
(ooc: @queen-of-the-cackle @ocram-station-admin-and-records kicking this shindig off!)
[ ENCRYPTED AUDIOVISUAL FEED RECEIVED. STREAMING… ]
View from the forward fuselage of a fighter craft, passing through a solid wall of cloud. Superficial scorch marks are streaked across the craft’s armored hull, the scars of recent entry into dense atmosphere.
As the fighter emerges into sunlight, a green icon stenciled onto its forewing becomes visible: a Shikoku dog leaping into the air, swatting at a crescent moon with one paw. Within the arc of the moon are the letters “L3HK.”
< Altitude eleven klicks, crossing tropopause. >
< Reduce rate of descent. Level out at six. Ma’ii? >
< Maintain passive sensors. The Eye is working; targeting data forwarded to tacnet. Nothing to suggest that we’ve been detected. >
< Beautiful. Let’s wake ‘em up. >
Sunlight, clouds, an electric blue sky. Below, an expanse of dusty gray stretches from horizon to horizon, streaked with red and orange. Mesas, crags, plains and ridge lines—all lifeless.
A HUD overlay highlights altitude, velocity, heading, pitch, roll. The fighter’s nose is pointed a few degrees under the horizon, below a cluster of highlighted targets around twelve kilometers away. Too far to be clearly visible, the targets are on the ground, unmoving.
< Spears up. >
In a single, precise motion, the horizon swivels around the craft, leaving the HUD reticle centered on one of the painted targets.
<<< Confirm target acquisition. >>>
< Engagement begins, mark time. Accelerate Mach 3. Set power 30 megajoules, load, charge. Whites of their eyes. >
<<< Whites of their eyes. >>>
Range closes to nine kilometers. Eight. Coming into view, a group of heavily-armed subline craft surrounded by a scattering of ground vehicles, dropships, mecha. A low hum registers on audio as the fighter’s primary railgun begins to charge.
< Sublines first, aim for cores. Break off following third kinetic volley, stabilize reactors, and circle to reacquire. Orders are full neutralize. All affirm? >
Range collapses to seven kilometers. Fusion drives screaming, the craft accelerates.
<<< All affirm. >>>
< Hyena, be advised: striking now, prepare to drop. >
< Load set, charge ready. First volley, fire. >
<<< First volley. >>>
Four deafening concussions roll across the landscape. Spears descend from above, sailing down towards the landed vessels.
#lancer rp#lancer nhp#lancer oc#luna wing#akhaan station#queen of the cackle#ocram ii science facility#for reference btw:#angle bracket colors are#L1 Grey - blue#L2 Garmr - red#L3 Hachiko - green#L4 Ma’ii - purple
7 notes
·
View notes
Text

Preparing for the greatest cosmic movie ever made
High up on the top of Cerro Pachón in northern Chile, NSF–DOE Vera C. Rubin Observatory is nearing completion. At the heart of the facility, a pivotal moment in the project's scientific adventure is unfolding. After more than 20 years of meticulous research and development, and weeks of testing, the LSST Camera has been successfully installed on the Simonyi Survey Telescope.
The teams breathe a collective sigh of relief. The world's largest digital camera, built at the DOE SLAC National Accelerator Laboratory (SLAC), is now in place, and the anticipation of capturing the first images for the Legacy Survey of Space and Time (LSST) is palpable. The greatest astronomical movie ever made is about to begin.
Well, almost.
Starting up such a sophisticated camera is far more complicated than pressing a simple "on/off" button. Creating the greatest astronomical film in history takes time, patience, and a commitment to precision. Every detail must be double-checked, and every system must meet its exact specifications before proceeding.
Unlike in the past stages of construction, the camera team now operates five meters (16.4 feet) above the ground, securely harnessed to a small platform that supports no more than 125 kilograms (275 pounds). Their movements are limited by the camera's rotation and the telescope's mirrors, positioned just inches away. What might seem like a simple hose connection becomes an entirely new challenge under these conditions.
The LSST Camera is about to undergo a series of critical steps. The first one is to create a vacuum inside the cryostat, a container designed to maintain extremely low temperatures, positioned in the middle of the camera. The cryostat houses the camera's complex electronic systems and its mosaic of 189 charge-coupled device (CCD) science sensors. These sensors are designed to capture images of the night sky with exceptional precision, with each image made up of 3,200 megapixels.
With his hands inside the camera, working to connect the vacuum system, Stuart Marshall, camera operations scientist and staff scientist at SLAC, explains, "The vacuum is crucial to insulate the camera's electronics from temperature changes. Once we've ensured a stable vacuum, we'll activate the refrigeration system which will cool the cryostat to very low temperatures."
The electronics generate about 1 kilowatt of heat during operation, roughly equivalent to the output of a small electric heater. This heat must be removed from the vacuum chamber to prevent overheating. "We want the camera's electronics to be between -20°C and -5°C (-4°F and 23°F) to maintain a safe operating temperature. So we need to pull that heat out. And we do it by pumping a fluid at -50°C (-58°F) through the cooling system."
Meanwhile, the CCDs themselves must be cooled to -100°C (-148°F). This temperature ensures optimal performance and helps prevent unwanted heat from interfering with the sensitive electronics and degrading the quality of the images. These sensors have their own dedicated cooling system, which will only be activated once the electronic cooling system is stable.
Once these critical steps are completed, the teams will power on the CCDs and test the control and data acquisition systems to ensure the camera communicates properly with the computers. The camera will then be fully operational.
"Building the camera was never routine and we still have new challenges and problems to solve," explains Marshall. "But now, as we're getting ready for the first images, we are transferring the knowledge to the observing specialists and commissioning scientists who shadow our work and often drive the start-up, with supervision. It's really exciting!"
A few meters away, on the scaffold next to the camera, Yijung Kang, observing specialist and postdoctoral researcher at SLAC, is ready to operate the vacuum system. "All the observing team is really excited to prepare for operations. We are now working closely with the other teams, preparing tests and procedures to ensure the successful launch of our decade-long science mission."
The work is methodical and demanding, and involves interconnected systems that require a comprehensive understanding of the entire camera. Experts in vacuum systems, cooling, and electronics play a critical role in the process. It is not enough to be an expert in one specific area—one must have a deep, holistic knowledge of the camera. Every system, every component, every adjustment must be carefully anticipated to ensure perfect operation.
Yousuke Utsumi, camera operations scientist and associate professor at the National Astronomical Observatory of Japan, knows the team is up to the challenge. "The work on the camera is progressing well, and we are confident that any issues that come up, even the most unexpected ones, will be resolved."
In just a few weeks, once these critical steps are completed and the CCDs are activated, another breathtaking moment will come: The camera's lens cap will be removed. "It is just like any standard camera lens cap, but this one is five and a half feet wide, and we will use a crane to lift it," says Utsumi. Then starlight will pour into the LSST Camera for the very first time.
At this point, the observing specialists will take control. They will select the portion of the sky to observe, point the telescope, and run the computer program that will capture the first photons. Shortly after, the first images of the sky will be displayed on three giant screens in the control room, marking the beginning of an extraordinary cinematic adventure.
Just like a director meticulously fine-tuning the first shots of a film, the teams will spend a few more weeks refining the telescope and the camera, perfecting focus and optical alignment, capturing calibration images, ensuring smooth and stable operation, and preparing for any potential technical issues. Only then will the greatest astronomical film ever made officially begin.
TOP IMAGE: Built at the DOE SLAC National Accelerator Laboratory (SLAC), the world's largest digital camera is now installed on NSF–DOE Vera C. Rubin Observatory's Simonyi Survey Telescope and is nearly ready to capture the greatest astronomical movie ever made. Credit: RubinObs/NOIRLab/SLAC/NSF/DOE/AURA/F. Munoz
LOWER IMAGE: On a small platform five meters (16.4 feet) above the ground, wedged between the LSST camera and the telescope, Stuart Marshall, camera operations scientist and staff scientist at SLAC, is working to connect the LSST camera's vacuum system. Credit: RubinObs/NOIRLab/SLAC/NSF/DOE/AURA/Y. Utsumi

5 notes
·
View notes
Text
The Hidden Cost of Convenience: How Your Smart Devices Are Mapping Your Life

In an era where smart devices have become ubiquitous in our homes, a disturbing reality lurks beneath their convenient features. Is that robot vacuum diligently cleaning your floors? It's creating detailed 3D maps of your home. The biometric scanner at your local grocery store? It's collecting more than just payment data. These revelations come from data privacy experts Aram Senriq and Jesse Gilbert, authors of "The Secret Life of Data," who warn that our digital footprints are far more extensive – and permanent – than most people realize. "Data isn't really an object so much as it's a frame of mind," explains Senriq. "You can take any aspect of the human experience and reduce it to a set of numbers that has value for somebody somewhere." Take Amazon's Roomba, for instance. While marketed as a simple vacuum cleaner, its LIDAR sensors create comprehensive 3D maps of your home's interior, tracking everything from furniture placement to the number of residents and pets. According to Gilbert, this data has value far beyond improving cleaning efficiency. "The vacuuming function is why we invite them into our homes, but it's not the value for Amazon," he notes. This detailed spatial data helps build sophisticated consumer profiles that can be packaged and sold to third parties – or potentially accessed by government agencies without a warrant. The implications extend beyond individual privacy concerns. Amazon's acquisition of One Medical and its collection of biometric data through Whole Foods' palm-scanning payment system creates an unprecedented intersection of consumer behavior and health data. "Correlating your shopping habits with your medical risk factors... are very consequential and very high stakes," Gilbert warns. Even more troubling is how today's innocent data collection could have tomorrow's unforeseen consequences. The authors point to a stark example: during the decades when abortion was legal nationwide, millions of Americans used Google Maps to locate healthcare clinics. Post-Roe v. Wade, that same location data could potentially be used as evidence in criminal proceedings in states where abortion is now illegal. So what can consumers do? While completely opting out of digital services isn't realistic for most people, the authors suggest a three-pronged approach: - Support federal data privacy legislation - Take practical steps like using VPNs to encrypt personal data - Foster a culture of privacy awareness and normalized protective behaviors The message is clear: We need to move beyond the "nothing to hide" mindset and recognize that all data, like DNA, exists as part of an interconnected web that can reveal far more about us—and those connected to us—than we might imagine. As our homes and lives become increasingly connected, the question isn't just about what data we're willing to share today, but how that data might be used tomorrow. The convenience of smart devices comes with a price tag we're only beginning to understand. Read the full article
2 notes
·
View notes
Text
How SCADA Works?
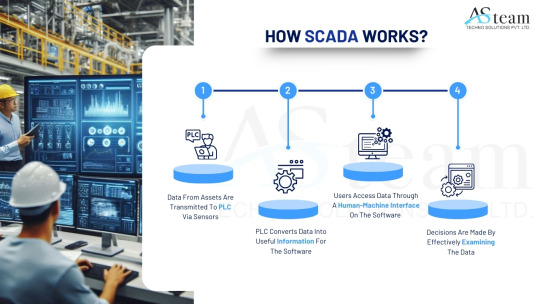
Supervisory Control and Data Acquisition (SCADA) systems are critical in managing and monitoring industrial processes across various industries, including manufacturing, utilities, transportation, and energy.
Field Devices
At the process level, field devices like sensors, meters, and actuators are used to monitor variables like voltage, flow, temperature, and pressure. These gadgets collect information and carry out system-directed operations.
Remote Terminal Units (RTUs) and Programmable Logic Controllers (PLCs)
The SCADA software and the field devices are connected by RTUs and PLCs. After gathering information from the sensors, they transmit it to the control center. Additionally, the SCADA system may send them orders to modify settings or control actuators.
Communication Infrastructure
Strong communication networks are necessary for SCADA to transmit data between the control center and field equipment. This infrastructure can be wireless (such as satellite, radio, and cellular networks) or wired (such as Ethernet and fiber optics).
Centralized Control Station
SCADA software, which analyzes data, creates visualizations, and gives operators tools to monitor and manage operations, is housed in the control station.
Human-Machine Interface (HMI)
The SCADA system's user interface is called the HMI. Operators can engage with the system and make well-informed decisions because to its graphical depictions of processes, warnings, and trends.
#automation#SCADA#PLC#HMI#Automation#Technology#business and industry sectors#business#industrial automation#soft starter#software#software engineering
3 notes
·
View notes
Text
Fluffy February (Catching Up) #20: Partners
SWTOR
Rating: PGish
Time: KotFE
Pairing: Theron Shan/Eva Corolastor
Words: 875
~~
“Hey, Spike.” Eva’s voice crackled over the comm. She suspected the shadow had been him, but she had to confirm it.
Using the “Spy Guy” nickname from the Holochat would have been a bit obvious; using Bowie’s alternative was a better plan.
“What’s new, darling?”
So was using a far, far less obvious nom de guerre than “EC” (which strangely still worked in a remarkable number of places).
At the word “darling,” Eva let the corner of her lip pull up slightly but no more. They were on a job, and Theron had just confirmed it was him, far up and away. She refocused her attention on the safe that the old omnitool was cracking, one binary digit at a time. “Doing a little bit of shopping. Waiting for a store to open up. Think the owner is on a caf break.”
“At this time of the night, you would think.” A shift of high-tech stealth fabric, the filaments scraping on duracrete. “I was just going for a run. Never have time anymore, what with work being as it is.”
“Don’t tell me I’m not getting your heart-rate up enough for that high-intensity thing you do…” Eva taunted him.
“You aren’t around all the time –”
“I could be if you –”
Just then the omnitool sang its note of completion and unlatched itself from the safe door.
“Should I take it that you’re buying something nice and expensive?”
Eva opened the safe door, carefully, and used one of Theron’s gadgets to scan for surveillance, weight sensors, and laser deployments within the lead-lined safe. “We’ll see in a minute,” she muttered under her breath. “Gotta do some viewport shopping.”
Theron cut the comm, giving her the silence she needed to do the checks properly.
Anyone who sliced their comms or intercepted their signal would assume they were just romantic partners.
Not partners in crime.
Part the business of Very Awful Things (VAT), LLC, included corporate espionage and theft of various data and prototypes. Theron was looking for Akaavi and Risha, the other proprietors…but since they had been good smugglers who disappeared, the LLC name had been disused since the last job they’d done (a little moonlighting thing while running something for Marr, after Ziost, before Eternal Fleet). No tax filings, no indication of the disposition of the owners.
Maybe when Eva filed taxes this year, that would perk Risha’s attention.
Until then, Eva was going to use VAT as a contractor for Odessen’s less than benevolent business. Although Theron had indicated he was less enthusiastic about the very not nice things VAT did, corporations weren’t people, and the acquisition of tech for the Alliance would be for the great good of the galaxy.
When Eva had asked him about payment as a subcontractor for VAT, LLC, he’d just grunted. She was sure she’d be able to compensate him for his time.
The checks finished, all green. Eva carefully extended her left hand ---
And nothing happened.
She carefully grasped the device, shaped like a dodecahedron (“a 20-point word!” crowed Corso, in her mind). She lifted its base off the floor of the safe and paused. Waited. Nothing.
She withdrew her hand, not too slow. Not too fast.
Eva’s ears rang in the silence, a sign of too many high-octane adventures. Her eyes dropped to look at what she had retrieved. It matched the schematics and the surveillance holos that Theron had acquired. She gave it a slight lift. Weight was right – the same as Dr. O’s flimsi-weight.
Even through the tinnitus, Eva could hear something click or move outside of the room. Could have been the building settling. Could have been the heat turning on. Didn’t matter. She had to go.
Eva shoveled the device into the specially designed interior pocket of her catsuit, off to the side, right where a shoulder holster would rest if she was carrying that day. It slotted in neatly, and then Eva was out the window.
She planted her left hand on the outside of the transparisteel window and, using the activated webbing, swung herself around the window sill. The second that she felt her feet secure to the side of the building (right hand unknown), Eva pushed off and the window slid shut. With a gesture, the locks reactivated, as if she’d never been there.
“Ready to go home?”
Eva’s head tilted up toward the voice.
As planned, Theron waited for her exit, perched just below the window ledge, the webbing on his stealth suit activated as well. He’d covered her with his sniper rifle from the building across the street, and as extraction grew near, he’d migrated to their departure point.
“Thanks for picking me up. We going to my place?” she asked as she raised her right hand toward him.
Theron reached beyond the hand to grab at her elbow and hauled her up the side of the building. “It’s the place with the food.”
With ease, Theron quickly climbed up and over the ledge, turning to grasp Eva’s left forearm and bring her up the rest of the way, her feet touching down on the roof neatly into front of his own.
“Hey.”
“Hey.”
Anyone listening in could guess how they greeted each other.
~~
@fluffyfebruary
10 notes
·
View notes
Text
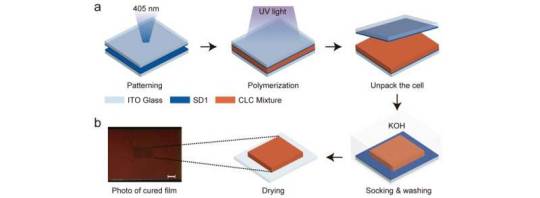
Geometric phase-encoded liquid crystal optical sensing
Sensing technology, integral to environmental monitoring, data acquisition, and precision data processing, is evolving rapidly. Researchers are at the forefront of developing swift, accessible, and cost-effective sensors. Among these innovations, cholesteric liquid crystals (CLCs) in stimulus-responsive photonic crystals exhibit exceptional promise. Their unique helical structure and photonic properties enable the production of vivid, power-independent structural colors, paving the way for advanced visual analysis tools. However, a significant challenge hinders CLC's broader application in optical sensing: Although they visibly alter color in response to stimuli, accurately gauging these changes necessitates costly spectroscopic equipment, constraining their practical deployment. Responding to the growing need for compact and planar optical elements, researchers have investigated Pancharatnam-Berry geometric phases, derived from light's spin-orbit interactions. Recent developments include integrating the geometric phase into reflected light via CLC helical superstructures, leading to novel photonic applications.
Read more.
7 notes
·
View notes
Text
@sd-vtm

Intruder detected! -------------------------------------------------------------------------- Initiating System; namespace WrathStartup { classSentinel { static void Main(string[] args) { Console.WriteLine("Initializing Wrath Model DR-7.01; Callsign: Roako..."); LoadConfiguration(C9OS 33.4); InitializeComponents(Optics, sensors, actuators, operating system, target acquisition software,); StartServices(hunt, capture, interrogate,); Error: data corruption detected; System starting in free mode
Console.WriteLine("Wrath Model is now running."); ---------------------------------------------------------------------------
'Who the FUCK was dumb enough to wake him up with this godawful noise?!'
All around the facility, alarms were blaring out their call as Roako was awakened by the faulty system that ran the place. It wanted him to do his job as a sentinel but he honestly couldn't give a crap what it wanted from him. The whole thing was degraded and torn apart to the point where this "Intruder" could have been nothing more than a skull that shifted in a tremor or something.
But that noise! That horrible, grating noise! He just wanted to sleep! Was that too much to ask?!
With a suffering sigh and a kick, Roako gets up and leaves the room. If he wanted to shut this shit off, he had to go to the main control room.....
One of these days he really should move his room there or something...
2 notes
·
View notes
Text
Top 10 Projects for BE Electrical Engineering Students
Embarking on a Bachelor of Engineering (BE) in Electrical Engineering opens up a world of innovation and creativity. One of the best ways to apply theoretical knowledge is through practical projects that not only enhance your skills but also boost your resume. Here are the top 10 projects for BE Electrical Engineering students, designed to challenge you and showcase your talents.
1. Smart Home Automation System
Overview: Develop a system that allows users to control home appliances remotely using a smartphone app or voice commands.
Key Components:
Microcontroller (Arduino or Raspberry Pi)
Wi-Fi or Bluetooth module
Sensors (temperature, motion, light)
Learning Outcome: Understand IoT concepts and the integration of hardware and software.
2. Solar Power Generation System
Overview: Create a solar panel system that converts sunlight into electricity, suitable for powering small devices or homes.
Key Components:
Solar panels
Charge controller
Inverter
Battery storage
Learning Outcome: Gain insights into renewable energy sources and energy conversion.
3. Automated Irrigation System
Overview: Design a system that automates the watering of plants based on soil moisture levels.
Key Components:
Soil moisture sensor
Water pump
Microcontroller
Relay module
Learning Outcome: Learn about sensor integration and automation in agriculture.
4. Electric Vehicle Charging Station
Overview: Build a prototype for an electric vehicle (EV) charging station that monitors and controls charging processes.
Key Components:
Power electronics (rectifier, inverter)
Microcontroller
LCD display
Safety features (fuses, circuit breakers)
Learning Outcome: Explore the fundamentals of electric vehicles and charging technologies.
5. Gesture-Controlled Robot
Overview: Develop a robot that can be controlled using hand gestures via sensors or cameras.
Key Components:
Microcontroller (Arduino)
Motors and wheels
Ultrasonic or infrared sensors
Gesture recognition module
Learning Outcome: Understand robotics, programming, and sensor technologies.
6. Power Factor Correction System
Overview: Create a system that improves the power factor in electrical circuits to enhance efficiency.
Key Components:
Capacitors
Microcontroller
Current and voltage sensors
Relay for switching
Learning Outcome: Learn about power quality and its importance in electrical systems.
7. Wireless Power Transmission
Overview: Experiment with transmitting power wirelessly over short distances.
Key Components:
Resonant inductive coupling setup
Power source
Load (LED, small motor)
Learning Outcome: Explore concepts of electromagnetic fields and energy transfer.
8. Voice-Controlled Home Assistant
Overview: Build a home assistant that can respond to voice commands to control devices or provide information.
Key Components:
Microcontroller (Raspberry Pi preferred)
Voice recognition module
Wi-Fi module
Connected devices (lights, speakers)
Learning Outcome: Gain experience in natural language processing and AI integration.
9. Traffic Light Control System Using Microcontroller
Overview: Design a smart traffic light system that optimizes traffic flow based on real-time data.
Key Components:
Microcontroller (Arduino)
LED lights
Sensors (for vehicle detection)
Timer module
Learning Outcome: Understand traffic management systems and embedded programming.
10. Data Acquisition System
Overview: Develop a system that collects and analyzes data from various sensors (temperature, humidity, etc.).
Key Components:
Microcontroller (Arduino or Raspberry Pi)
Multiple sensors
Data logging software
Display (LCD or web interface)
Learning Outcome: Learn about data collection, processing, and analysis.
Conclusion
Engaging in these projects not only enhances your practical skills but also reinforces your theoretical knowledge. Whether you aim to develop sustainable technologies, innovate in robotics, or contribute to smart cities, these projects can serve as stepping stones in your journey as an electrical engineer. Choose a project that aligns with your interests, and don’t hesitate to seek guidance from your professors and peers. Happy engineering!
5 notes
·
View notes
Text

Kuiil on Arvala-7 speaking with Din Djarin about Grogu. Image from The Mandalorian, Season 1, Episode 7, The Reckoning. Calendar from DateWorks. Caption reads: I don't think it was engineered. I've worked in the gene farms. This one looks evolved. Too ugly. - Kuiil.
“Too ugly”? Wow. That stung. Grogu didn't know what to say, other than everyone couldn't be as handsome, good looking, charismatic, and esthetically pleasing as an Ugnaught. It wasn’t Grogu's fault that his parents, pollen donators, genetic precursors, hosts, or whatever you call the people who created him… somehow, weren’t the pinnacle of physical beauty. To be fair, he didn't even know who they were, so he couldn’t bring it up to them and get an explanation that Kuiil would find satisfactory. It just was not his fault.
On the other hand it was nice to know that he hadn't been ‘engineered’. Imagine someone sitting down at a comp and inputing the requirements of the project.
“Needs excellent hearing, audio processing center must be highly protected, multiple forms of communication acceptance sensors required for data acquisition, visual data sensors must work in all lighting conditions, including infra-red and ultraviolet. Long eyelashes are not necessary due to other reaction factors, etc. etc. etc.”
Kuiil had both long eyelashes and impressively bushy eyebrows. No wonder he thought Grogu was ugly. His eyelashes were stubby and he hadn’t actually developed any substantial facial hair. It was a pity because he was certain that if he had been able to grow a goatee and a mustache, the Ugnaught would have admitted that it was possible to be non-engineered as well as beautiful.
On the other hand, Kuiil had noted that Cara Dune was actually pretty enough to be from the cytocaves of Nora. Grogu didn’t understand why. Cara looked like an average human to Grogu. Her face was regular and practically symmetrical. Was that a sign of beauty? Grogu shrugged. Maybe it was. No wonder Kuiil thought he was ugly. If you looked at him very carefully you might notice that his left ocular bump was a tiny bit bigger than his right ocular bump. That sort of asymmetry had never bothered him before, but now he realized that it could be a critical flaw that the Ugnaught couldn't ignore. Dank Farrik.
That’s probably what the Ugnaught liked about the Mandalorian. That helmet of his was perfectly symmetrical. It was a thing of beauty and you didn't have to worry about it being natural or engineered. Of course it was engineered. It was a Mandalorian helmet. Those things didn’t grow on trees, sprout from the ground, or even pop out of a sea creature because it was the irritating offspring of a tiny speck of beskar oar. Nope. It was made. Probably hand made by a Mandalorian armorer at some point in the distant past.
Grogu had a theory that Mandalorians were hideous creatures that were only semi-human and they had to cover their heads because if regular humans saw them, they would scream and faint. He also suspected that even if they were regular humans, after wearing a helmet all the time they would likely turn into a hideous creature that looked like the pale underbelly of a worm, with a beard and eye brows that desperately needed a clean and bald heads from the interior surface of the helmet rubbing the hair so much it was like sandpaper over time. Uff. Now he was just grossing himself out.
The one theory he didn't like to examine was that the Mandalorian could remove his helmet whenever he wanted, but chose not to when other people were around so no one would speculate about his origin - cytocaves of Nora or regular reproduction for humans. That just didn’t seem fair. Considering the size of his own ears, Grogu knew that he couldn’t get away with the same behavior. No one could make him a helmet that didn’t squish his ears, expose them to dangerous speculation or double his weight so he couldn't even move around in it.
Normally he would have tried to investigate the situation when the Mandalorian was asleep. He never had to worry about figuring out when the bounty hunter was asleep. He snored like ten slavering barghest. Loud and proud as Ian used to say when they were at the Jedi Temple. And that might have been true in the Mandalorian’s case, but he was also a lighter sleeper than a stepped on Loth cat.
The few times Grogu had just hopped out of his ‘pram’ to go use the privy or search the Razor Crest for something to eat other than ration packs (you’d be surprised at how many delicious spiders you could find in the average cargo hold), the Mandalorian had been on hot on his trail an instant later. It was like he was faking the snoring just to lull Grogu into a false sense of security. Dank Farrik!
In any case, the Mandalorian's status as ugly or beautiful, engineered or just thrown together, was moot. No way to know. Which also wasn’t fair. It was annoying enough that a beautiful person like Kuiil had made those comments. The fact that the Mandalorian hadn’t jumped to his defense made things even worse, plus the fact that he couldn’t be judged by that same set of standards because he was protected from scrutiny by his Mandalorian-ness.
Grogu sighed. This had never been an issue at the Jedi Temple. People there learned not to make comments of such a personal nature. Not because they were afraid who ever they talked that way about would use the Force to find a way to punish them or shut them up, Jedi didn’t do things like that, but because everyone there was just as beautiful as everyone else. It was just true. When the Force was your friend, then it settled around you like an aura and showed how balanced and good you were. Master Beq had explained how all that worked practically a lifetime ago. When the younglings looked at each other they realized he was absolutely correct and they just didn’t worry about appearance.
Now here he was, back on Arvala-7 and that aura that had protected him from all sorts of scrutiny had vanished. Was he no longer balanced in the Force? Uff. That was pretty likely. You can’t end up eating a little container of delicious pasty stuff without permission and maintain balance. Grogu had never considered it a problem until just then, when he realized it must have been the Mandalorian’s beauty cream. Dank Farrik!

Grogu sitting in bin at Kuiil's moisture farm on Arvala-7 while Kuiil speaks with Din Djarin. Image from The Mandalorian, Season 1, Episode 7, The Reckoning. Caption reads: I don't think it was engineered. - Kuiil
3 notes
·
View notes