#malwareanalysis
Explore tagged Tumblr posts
Text
Code Interpreter And GTI For Gemini Malware Analysis

Using Google Threat Intelligence and Code Interpreter to Empower Gemini for Malware Analysis
What is Code Interpreter?
A tool that converts human-readable code into commands that a computer can understand and carry out is called a code interpreter.
What is code obfuscation?
A method called “code obfuscation” makes it more difficult to understand or reverse engineer source code. It is frequently used to hide data in software programs and safeguard intellectual property.
Giving security experts up-to-date tools to help them fend off the newest attacks is one of Google Cloud‘s main goals. Moving toward a more autonomous, adaptive approach to threat intelligence automation is one aspect of that aim.
As part of its most recent developments in malware research, it is giving Gemini new tools to tackle obfuscation strategies and get real-time information on indicators of compromise (IOCs). While Google Threat Intelligence (GTI) function calling allows Gemini to query GTI for more context on URLs, IPs, and domains found within malware samples, the Code Interpreter extension allows Gemini to dynamically create and run code to help obfuscate specific strings or code sections. By improving its capacity to decipher obfuscated parts and obtain contextual information depending on the particulars of each sample, these tools represent a step toward making Gemini a more versatile malware analysis tool.
Building on this, Google previously examined important preprocessing procedures using Gemini 1.5 Pro, which allowed us to analyze large portions of decompiled code in a single pass by utilizing its large 2-million-token input window. To address specific obfuscation strategies, it included automatic binary unpacking using Mandiant Backscatter before the decompilation phase in Gemini 1.5 Flash, which significantly improved scalability. However, as any experienced malware researcher is aware, once the code is made public, the real difficulty frequently starts. Obfuscation techniques are commonly used by malware developers to hide important IOCs and underlying logic. Additionally, malware may download more dangerous code, which makes it difficult to completely comprehend how a particular sample behaves.
Obfuscation techniques and additional payloads pose special issues for large language models (LLMs). Without specific decoding techniques, LLMs frequently “hallucinate” when working with obfuscated strings like URLs, IPs, domains, or file names. Furthermore, LLMs are unable to access URLs that host extra payloads, for instance, which frequently leads to speculative conclusions regarding the behavior of the sample.
Code Interpreter and GTI function calling tools offer focused ways to assist with these difficulties. With the help of Code Interpreter, Gemini may independently write and run bespoke scripts as necessary. It can use its own discretion to decode obfuscated elements in a sample, including strings encoded using XOR-based methods. This feature improves Gemini’s capacity to uncover hidden logic without the need for human participation and reduces interpretation errors.
By obtaining contextualized data from Google Threat Intelligence on dubious external resources like URLs, IP addresses, or domains, GTI function calling broadens Gemini’s scope while offering validated insights free from conjecture. When combined, these tools enable Gemini to better manage externally hosted or obfuscated data, moving it closer to its objective of operating as an independent malware analysis agent.
Here’s a real-world example to show how these improvements expand Gemini’s potential. Here, we are examining a PowerShell script that hosts a second-stage payload via an obfuscated URL. Some of the most sophisticated publicly accessible LLM models, which include code generation and execution in their reasoning process, have already been used to analyze this specific sample. Each model “hallucinated,” producing whole fake URLs rather than correctly displaying the correct one, in spite of these capabilities.Image credit to Google Cloud
Gemini discovered that the script hides the download URL using an RC4-like XOR-based obfuscation method. Gemini recognizes this pattern and uses the Code Interpreter sandbox to automatically create and run a Python deobfuscation script, successfully exposing the external resource.
After obtaining the URL, Gemini queries Google Threat Intelligence for more context using GTI function calling. According to this study, the URL is associated with UNC5687, a threat cluster that is well-known for deploying a remote access tool in phishing attacks that pose as the Ukrainian Security Service.
As demonstrated, the incorporation of these tools has improved Gemini’s capacity to operate as a malware analyst that can modify its methodology to tackle obfuscation and obtain crucial information about IOCs. Gemini is better able to handle complex samples by integrating the Code Interpreter and GTI function calling, which allow it to contextualize external references and comprehend hidden aspects on its own.
Even while these are important developments, there are still a lot of obstacles to overcome, particularly in light of the wide variety of malware and threat situations. Google Cloud is dedicated to making consistent progress, and the next upgrades will further expand Gemini’s capabilities, bringing us one step closer to a threat intelligence automation strategy that is more independent and flexible.
Read more on govindhtech.com
#CodeInterpreter#GeminiMalwareAnalysis#GoogleThreatIntelligence#GoogleCloud#phishing#Gemini15Pro#Gemini15Flash#malwareanalysis#technology#technews#news#govindhtech
0 notes
Text
🔐 Stay one step ahead with Arrowscope IT Solutions!
From VAPT to forensics, our Cyber Security Servicesvare designed to protect your business from every angle. 🛡
Your digital safety is our top priority! Whether it’s infrastructure security, secure code reviews, or advanced threat simulations – we’ve got you covered.
👉 Explore our full range of services and safeguard your company against cyber threats.
#cybersecurity#dataprotection#vapt#malwareanalysis#pentesting#arrowscopeitsolutions#businesssecurity#techsafety#codextechnologie#security#threats#protectyourbusiness#cybersecurityexpert#cybersecurityawareness#cybersecurityagency
0 notes
Link
https://bit.ly/48AQn1a - 🔒 Avast has uncovered an admin-to-kernel exploit used by the Lazarus Group, exploiting a previously unknown zero-day vulnerability in Windows’ appid.sys driver. Microsoft patched the vulnerability, CVE-2024-21338, showcasing the ongoing cyber warfare between attackers and defenders. The exploit facilitated kernel-level access, allowing for direct manipulation of the system, including disabling security software and evading detection. #CyberSecurity #ZeroDay #MicrosoftPatch 👾 The Lazarus Group utilized this access for an updated version of the FudModule rootkit, increasing its stealth and functionality. This version includes new techniques for evading detection and disrupting security mechanisms, highlighting the group's sophisticated approach to cyber espionage and malware deployment. #MalwareAnalysis #Rootkit #CyberEspionage 💻 The exploit represents a significant step up from previous methods, allowing Lazarus to operate more quietly by avoiding the need to exploit known vulnerable drivers. This shift underscores the evolving landscape of cyber threats and the importance of advanced security measures. #CyberThreats #InfoSec #TechInnovation 🛡️ The discovery and analysis of the rootkit and its infection chain shed light on the complexities of modern cyber attacks and the importance of vigilance in the cybersecurity community. This ongoing battle emphasizes the need for continuous improvement in defense mechanisms against sophisticated threat actors.
#CyberSecurity#ZeroDay#MicrosoftPatch#MalwareAnalysis#Rootkit#CyberEspionage#CyberThreats#InfoSec#TechInnovation#CyberDefense#DigitalSecurity#TechCommunity
0 notes
Text
youtube
1 note
·
View note
Text
Strengthening Cyber Defense: The Role of Network Sandboxing
Network sandboxing is a pivotal component in modern cybersecurity strategies, offering organizations proactive defense against advanced cyber threats by creating isolated environments for analyzing suspicious files and activities.
This innovative technique involves the containment and execution of potentially malicious files within a controlled environment, enabling security teams to observe and assess their behavior without risking the integrity of the entire network. By subjecting these elements to scrutiny, network sandboxes effectively neutralize threats, including zero-day exploits and advanced malware, which traditional security measures may overlook. Furthermore, network sandboxing provides valuable insights into the behavior and intent of cyber threats, empowering security teams to develop more robust threat mitigation strategies and enhance overall cyber resilience. With the proliferation of sophisticated cyber attacks targeting organizations of all sizes and industries, network sandboxing emerges as a critical line of defense, enabling proactive threat detection and response to safeguard sensitive data and maintain the integrity of organizational networks. #NetworkSandboxing #CyberDefense #CyberSecurity #ThreatDetection #ZeroDayExploits #MalwareAnalysis #CyberResilience #NetworkSecurity #AdvancedThreats #DataProtection #CyberThreats #ITSecurity #Innovation #Technology #SecurityStrategy #DigitalTransformation
0 notes
Text
LiSa: Sandbox for Automated Linux Malware Analysis | #Malware #MalwareAnalysis #Sandbox #Linux
0 notes
Text
youtube
🔍 Stay one step ahead of cyber threats with Malware Analysis! 💻✨ Discover how this powerful technique is bolstering cybersecurity defenses and thwarting malicious attacks. 🛡️💪 Dive into the world of threat detection, forensic analysis, and proactive mitigation. Together, we can safeguard the digital realm! 🌐🔒 #malwareanalysis #Cybersecurity #ThreatDetection #StaySecure #DigitalDefense
0 notes
Text
Is AI eliminating jobs or work?

Evolution in human economic history experienced, technology has removed employment while increasing work and being a net job creator; the excess of job creation over destruction has been good. The same is the case with Artificial Intelligence in India. Artificial Intelligence or AI is a field of Data Science that trains machines to learn from inputs, adjust to inputted fields and criteria, and perform tasks of computational logic that match certain human cognitive levels. AI as a function has pervaded almost all industries and functions in India – from E-Commerce to BFSI and from Manufacturing to Agriculture – Data Science and Deep Learning are increasingly utilized to solve complex business challenges. AI is increasingly utilized across several B2B, B2C, and, even, C2C (Consumer-to-Consumer) channels. More than a replacement, it is being used as a complement to human skills to increase productivity and output.
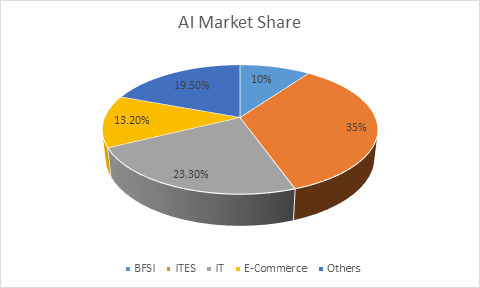
The current AI market share is around $8bn in India and is divided into IT and ITEs, E-Commerce and BFSI as the major users of AI, followed by others such as Healthcare, Agriculture etc. Over 1 lakh people are employed in this sector and this is one sector where employment is growing constantly. Employment created by AI is projected to reach 2 crore by 2025. No need to be over optimistic, but no need to be pessimistic either. Overall growth of AI market in India is predicted to be more than 10% per annum. And routine and codifiable jobs are expected to be eliminated by AI while jobs requiring IQ and EQ are expected to grow. However, considerable polarization in the employment market may arise at the higher and lower ends, necessitating special government initiatives to generate jobs in order to maintain social stability.
Please share your opinion with us.
#iccblogs#softwaredevelopment#datavisualization#automation#machinelearningalgorithms#coding#artificialintelligenceai#bigdata#cybersec#codinglife#malwareanalysis#security#cyberattack
2 notes
·
View notes
Text
FLARE Capa, Identifies Malware Capabilities Automatically

Capa is FLARE’s latest open-source malware analysis tool. Google Cloud platform lets the community encode, identify, and exchange malicious behaviors. It uses decades of reverse engineering knowledge to find out what a program performs, regardless of your background. This article explains capa, how to install and use it, and why you should utilize it in your triage routine now.
Problem
In investigations, skilled analysts can swiftly analyze and prioritize unfamiliar files. However, basic malware analysis skills are needed to determine whether a software is harmful, its participation in an assault, and its prospective capabilities. An skilled reverse engineer can typically restore a file’s full functionality and infer the author’s purpose.
Malware analysts can rapidly triage unfamiliar binaries to acquire first insights and guide analysis. However, less experienced analysts sometimes don’t know what to look for and struggle to spot the unexpected. Unfortunately, strings / FLOSS and PE viewers offer the least information, forcing users to mix and interpret data.
Malware Triage 01-01
Practical Malware Analysis Lab 01-01 illustrates this. Google Cloud want to know how the software works. The file’s strings and import table with relevant values are shown in Figure 1.Image credit to Google cloud
This data allows reverse engineers to deduce the program’s functionality from strings and imported API functions, but no more. Sample may generate mutex, start process, or interact via network to IP address 127.26.152.13. Winsock (WS2_32) imports suggest network capabilities, but their names are unavailable since they are imported by ordinal.
Dynamically evaluating this sample may validate or reject hypotheses and uncover new functionality. Sandbox reports and dynamic analysis tools only record code path activity. This excludes features activated following a successful C2 server connection. Google seldom advise malware analysis with an active Internet connection
We can see the following functionality with simple programming and Windows API knowledge. The malware:
Uses a mutex to limit execution to one
Created a TCP socket with variables 2 = AF_INET, 1 = SOCK_STREAM, and 6 = IPPROTO_TCP.
IP 127.26.152.13 on port 80
Transmits and gets data
Checks data against sleep and exec
Develops new method
Malware may do these actions, even if not all code paths execute on each run. Together, the results show that the virus is a backdoor that can execute any program provided by a hard-coded C2 server. This high-level conclusion helps us scope an investigation and determine how to react to the danger.
Automation of Capability Identification
Malware analysis is seldom simple. A binary with hundreds or thousands of functions might propagate intent artifacts. Reverse engineering has a high learning curve and needs knowledge of assembly language and operating system internals.
After enough effort, it is discern program capabilities from repeating API calls, strings, constants, and other aspects. It show using capa that several of its primary analytical results can be automated. The technology codifies expert knowledge and makes it accessible to the community in a flexible fashion. Capa detects characteristics and patterns like a person, producing high-level judgments that may guide further investigation. When capa detects unencrypted HTTP communication, you may need to investigate proxy logs or other network traces.
Introducing capa
The output from capa against its sample program virtually speaks for itself. Each left item in the main table describes a capability in this example. The right-hand namespace groups similar capabilities. capa defined all the program capabilities outlined in the preceding part well.
Capa frequently has unanticipated outcomes. Capa to always present the evidence required to determine a capability. The “create TCP socket” conclusion output from capa . Here, it can see where capa detected the necessary characteristics in the binary. While they wait for rule syntax, it may assume they’re a logic tree with low-level characteristics.
How it Works
Its two major components algorithmically triage unknown programs. First, a code analysis engine collects text, disassembly, and control flow from files. Second, a logic engine identifies rule-based feature pairings. When the logic engine matches, it reports the rule’s capability.
Extraction of Features
The code analysis engine finds program low-level characteristics. It can describe its work since all its characteristics, including strings and integers, are human-recognizable. These characteristics are usually file or disassembly-related.
File characteristics, like the PE file header, are retrieved from raw file data and structure. Skimming the file may reveal this. Other than strings and imported APIs, they include exported function and section names.
Advanced static analysis of a file extracts disassembly characteristics, which reconstructs control flow. Figure displays API calls, instruction mnemonics, integers, and string references in disassembly.Image credit to Google cloud
It applies its logic at the right level since sophisticated analysis can differentiate between functions and other scopes in a program. When unrelated APIs are utilized in distinct functions, capa rules may match them against each function separately, preventing confusion.
It is developed for flexible and extensible feature extraction. Integrating code analysis backends is simple. It standalone uses a vivisect analysis framework. The IDA Python backend lets you run it in IDA Pro. various code analysis engines may provide various feature sets and findings. The good news is that this seldom causes problems.
Capa Rules
A capa rule describes a program capability using an organized set of characteristics. If all needed characteristics are present, capa declares the program capable.
Its rules are YAML documents with metadata and logic assertions. Rule language includes counting and logical operators. The “create TCP socket” rule requires a basic block to include the numbers 6, 1, and 2 and calls to API methods socket or WSASocket. Basic blocks aggregate assembly code low-level, making them perfect for matching closely connected code segments. It enables function and file matching in addition to basic blocks. Function scope connects all features in a disassembled function, whereas file scope includes all file features.
Rule names define capabilities, whereas namespaces assign them to techniques or analytic categories. Its output capability table showed the name and namespace. Author and examples may be added to the metadata. To unit test and validate every rule, Google Cloud utilizes examples to reference files and offsets with known capabilities. Please maintain a copy of capa rules since they detail real-world malware activities. Meta information like capa’s support for the ATT&CK and Malware Behavior Catalog frameworks will be covered in a future article.
Installation
The offer standalone executables for Windows, Linux, and OSX to simplify capa use. It provide the Python tool’s source code on GitHub. The capa repository has updated installation instructions.
Latest FLARE-VM versions on GitHub feature capa.
Usage
Run capa and provide the input file to detect software capabilities:
Suspicious.exe
Capa supports shellcode and Windows PE (EXE, DLL, SYS). For instance, to analyze 32-bit shellcode, capa must be given the file format and architecture:
Capa sc32 shellcode.bin
It has two verbosity levels for detailed capability information. Use highly verbose to see where and why capa matched rules:
Suspicious.exe capa
Use the tag option to filter rule meta data to concentrate on certain rules:
Suspicious.exe capa -t “create TCP socket”
Show capa’s help to show all available options and simplify documentation:
$capa-h
Contributing
Google cloud believe capa benefits the community and welcome any contribution. Google cloud appreciate criticism, suggestions, and pull requests. Starting with the contributing document is ideal.
Rules underpin its identifying algorithm. It aims to make writing them entertaining and simple.
Utilize a second GitHub repository for its embedded rules to segregate work and conversations from its main code. Rule repository is a git submodule in its main repository.
Conclusion
FLARE’s latest malware analysis tool is revealed in this blog article. The open-source capa framework encodes, recognizes, and shares malware behaviors. Believe the community needs this tool to combat the number of malware it encounter during investigations, hunting, and triage. It uses decades of knowledge to explain a program, regardless of your background.
Apply it to your next malware study. The program is straightforward to use and useful for forensic analysts, incident responders, and reverse engineers.
Read more on govindhtech.com
#FLARECapa#IdentifiesMalware#GoogleCloud#CapabilitiesAutomatically#malwareanalysis#Sandbox#Malware#Introducingcapa#Python#Automation#MalwareTriage0101#technology#technews#news#govindhtech
0 notes
Photo

#Ellis #Threat Hunter #digitalart #digitaldrawing #digitalpainting #malwareanalysis #photoshop #conceptart #ukartists #polishartists #wacomart #wacomtablet #wacommobilestudiopro13 #wacom #Hunter #characterdesigns #characterdesign (w: London, United Kingdom) https://www.instagram.com/p/B0jOS97Hh6B/?igshid=48wx98pxfxfy
#ellis#threat#digitalart#digitaldrawing#digitalpainting#malwareanalysis#photoshop#conceptart#ukartists#polishartists#wacomart#wacomtablet#wacommobilestudiopro13#wacom#hunter#characterdesigns#characterdesign
1 note
·
View note
Photo

AI in Cybersecurity: Defense and Offense Strategies
#artificialintelligence#cybersecurity#DataPrivacy#deeplearning#DefenseStrategies#MachineLearning#MalwareAnalysis#NetworkSecurity#OffenseStrategies#ThreatDetection
0 notes
Link
https://bit.ly/3Rq0Dme - 🌐 The hospitality industry faces a new cyber threat: the "Inhospitality" malspam campaign, using social engineering to deploy password-stealing malware. Attackers lure hotel staff with emails about service complaints or information requests, leading to malicious payload links. #CyberThreat #HotelIndustrySecurity 🔍 Sophos X-Ops identified this trend, similar to tactics used during the US tax season. Attackers engage with hotel staff through emotionally charged scenarios, from lost items to accessibility needs, only sending malware links after initial contact. #SophosResearch #SocialEngineering 💼 Emails vary from violent attack allegations to queries about disability accommodations. Once staff respond, attackers reply with links claiming to contain relevant "documentation," which are actually malware in password-protected files. #CyberAttackTactics #HotelSafety 📧 Common traits in these emails include urgent requests and emotionally manipulative narratives. Examples range from lost cameras with sentimental value to issues in booking for disabled family members, all designed to elicit quick responses from hotel staff. #MalspamCampaign #EmailScams 🔐 The malware, often a variant of Redline or Vidar Stealer, is difficult to detect. It's hidden in large, password-protected files and often carries valid or counterfeit signatures to bypass security scans. #MalwareAnalysis #CyberDefense 💻 Upon execution, the malware connects to a Telegram URL for command-and-control, stealing information like browser-saved passwords and desktop screenshots. It doesn't establish persistence, running once to extract data before quitting. #CybersecurityThreat #DataProtection 🛡️ Sophos has identified over 50 unique malware samples and reported them to cloud providers. With low detection rates on Virustotal, Sophos has published indicators of compromise and ensures detection in their products.
#CyberThreat#HotelIndustrySecurity#SophosResearch#SocialEngineering#CyberAttackTactics#HotelSafety#MalspamCampaign#EmailScams#MalwareAnalysis#CyberDefense#CybersecurityThreat#DataProtection#SophosSecurity#CyberAwareness#engineering#hotels#staff#emails#requests#tactic#tax
1 note
·
View note
Photo

Alerta de actualización . . . . . #coding #computer #cyber #cybercrime #cybersecurity #digital #hacking #infosec #kalilinux #linux #maker #malware #malwareanalysis #marketing #networksecurity #opensource #phishing #programmer #programming #ransomware #raspberrypi #redteam #software #startup #sysadmin #thinkpad #vulnerability #webdev #webdeveloper #wifihacking (en İphone) https://www.instagram.com/p/CoihfpXuYF6/?igshid=NGJjMDIxMWI=
#coding#computer#cyber#cybercrime#cybersecurity#digital#hacking#infosec#kalilinux#linux#maker#malware#malwareanalysis#marketing#networksecurity#opensource#phishing#programmer#programming#ransomware#raspberrypi#redteam#software#startup#sysadmin#thinkpad#vulnerability#webdev#webdeveloper#wifihacking
0 notes
Photo

Herramientas gratuitas de análisis de correo electrónico de phishing: Análisis de encabezado de: 1 correo electrónico >> https://lnkd.in/gxaGmWcg 2-Verificación de reputación de URL/IP >> https://lnkd.in/gNqxtn4d https://urlscan.io/ https://lnkd.in/g7uWdC5q https://www.abuseipdb.com/ 3-Análisis de archivos/adjuntos Comprobación de hash de archivo >> https://lnkd.in/gNqxtn4d sandbox en línea >> https://any.run/ Sandbox en línea >> https://lnkd.in/gaRGY8kB 4-Registro Whois >> https://centralops.net/co/ 5-Herramienta de análisis de phishing >> https://www.phishtool.com/ #phishing #ransomware #phishingemails #malware #malwareanalysis #threatintelligence #computersecurity https://www.instagram.com/p/CnMlu-nOrDc/?igshid=NGJjMDIxMWI=
0 notes
Link
#vulnerability#CyberSecurity#SOC#IncidentResponse#SecurityAnalyst#ThreatIntelligence#MalwareAnalysis#phishing#OWASP#VAPT#SIEM#Hacking#Bugbounty#infosec#AppSec
0 notes
Photo
Freki: Open-Source Malware Analysis Platform | #Analysis #AntiMalware #MalwareAnalysis #Security
0 notes