#Usercontrol
Explore tagged Tumblr posts
Link
Yahoo's all about keeping our data safe while we enjoy their platforms! They've laid out how they use cookies to boost functionality, security, and personalized experiences. It’s all about giving users control—whether you want to accept all cookies for a more tailored experience or reject some to protect your privacy, the choice is yours.
Plus, you can tweak your settings anytime through their easy-to-navigate privacy dashboard. Transparency is key, and Yahoo invites you to learn more about how they handle your data. In a world where privacy matters more than ever, they’re stepping up to keep our info secure while still enhancing our online experience.
Curious to learn more? Sign Up to the free newsletter here www.investmentrarities.com.
#Yahoo#Privacy#DataSafety#CookiesUsage#UserControl#OnlineExperience#Personalization#DataProtection#InternetSafety#PrivacyDashboard#Transparency#CookieSettings#UserExperience#CyberSecurity#DigitalPrivacy#TechNews
0 notes
Text
What is the privacy risk of new tech?
New technology often brings various privacy risks, which can arise from how personal data is collected, stored, shared, and used. Here are some key privacy risks associated with new tech:
1.Data Collection and Surveillance
Over-Collection of Data: Many new technologies collect more data than necessary, often without the user’s explicit consent. This includes location data, browsing history, and personal preferences.
Mass Surveillance: Technologies like facial recognition, AI-driven analytics, and IoT devices can enable mass surveillance, where individuals are constantly monitored without their knowledge.
2. Data Breaches
Increased Vulnerability: As more personal data is stored digitally, the risk of data breaches increases. Hackers can exploit vulnerabilities in new tech, leading to unauthorized access to sensitive information like financial data, health records, and personal communications.
Lack of Strong Security Measures: Some new technologies may lack robust security measures, making them prime targets for cyberattacks.
3. Data Misuse
Profiling and Targeting: Companies may use personal data to create detailed profiles of users, which can be used for targeted advertising, manipulation, or discrimination. This can lead to invasive marketing practices and unfair treatment.
Third-Party Sharing: Data collected by one service is often shared with or sold to third parties without the user’s knowledge or consent, leading to privacy breaches.
4. Lack of Transparency and Control
Opaque Privacy Policies: Many tech companies have complex and unclear privacy policies, making it difficult for users to understand how their data is being used.
Limited User Control: Users often have limited control over their data, including who can access it, how it is used, and how long it is stored.
5. AI and Machine Learning Risks
Bias and Discrimination: AI systems can unintentionally perpetuate biases present in training data, leading to discriminatory practices, especially in areas like hiring, lending, and law enforcement.
Automated Decision-Making: Automated systems may make decisions about individuals without their input, which can affect their privacy and personal freedoms.
6. IoT Devices
Insecure Devices: Many Internet of Things (IoT) devices lack strong security measures, making them vulnerable to hacking and unauthorized access.
Continuous Data Collection: IoT devices often collect data continuously, creating detailed profiles of users' habits, preferences, and daily routines.
7. Emerging Technologies
Quantum Computing: The development of quantum computers poses a future risk to current encryption methods, potentially exposing encrypted data to unauthorized access.
Blockchain Technology: While blockchain offers enhanced security, the immutability of data can be a double-edged sword, as once data is recorded, it cannot be easily altered or deleted, leading to potential privacy issues.
8. Social Engineering and Phishing
Manipulation: New technologies may be exploited to create more sophisticated phishing attacks and social engineering schemes, tricking users into revealing personal information.
Regulatory and Legal Risks
Cross-Border Data Transfers: As data moves across borders, it may be subject to different privacy laws and regulations, complicating the protection of personal information.
Legal Compliance: Rapidly evolving technologies may outpace existing privacy laws, leading to gaps in legal protections.
9. Mitigating Privacy Risks:
Strong Encryption: Ensuring data is encrypted both in transit and at rest.
User Education: Educating users about the privacy risks associated with new technologies and how to protect themselves.
Privacy-by-Design: Incorporating privacy features into the design of new technologies from the outset.
Regulation and Oversight: Governments and organizations should create and enforce regulations that protect user privacy.
Understanding and addressing these privacy risks is essential for maintaining trust and protecting individuals in an increasingly connected world.
#DataCollection#Surveillance#DataBreach#DataMisuse#LackOfTransparency#IoTPrivacy#AIrisks#RegulatoryChallenges#Cybersecurity#UserControl#DigitalFootprint#PrivacyByDesign
0 notes
Text
Facebook and Instagram Enhance User Control and Transparency in Content Ranking

Enhancing User Control and Transparency
In a recent announcement, Facebook and Instagram unveiled significant updates to empower users with more control over their content experience and provide greater transparency into the algorithms shaping their feeds. The updates aim to make the platforms more user-friendly and address concerns regarding algorithmic influence. These changes come as billions of people rely on Facebook and Instagram to connect, share their lives, and discover captivating content. Empowering Users with AI Systems Understanding the importance of personalization, both platforms utilize AI systems to curate content tailored to each user's preferences. By factoring in user choices and behavior, these systems attempt to deliver relevant and engaging content. In a prior discussion, Meta, the parent company of Facebook and Instagram, acknowledged the need for more transparency and user control, challenging the notion that algorithms render users powerless. Building on that commitment, Meta now takes strides toward openness and control. Increased Transparency and Control Facebook and Instagram are committed to providing users with more transparency regarding AI systems that rank content across the platforms. By releasing 22 system cards, Meta grants insights into how these AI systems operate, the predictions they make to determine content relevance, and the available controls to customize the user experience. These system cards cover various sections such as Feed, Stories, Reels, and even unconnected content recommendations. Users can access the Transparency Center for a more detailed explanation of content recommendation AI. Moreover, Meta goes beyond system cards by sharing the types of signals and predictive models used to determine content relevance in the Facebook Feed. While the company aims to be transparent, it also recognizes the need to balance disclosure with safeguarding against misuse. Personalizing the User Experience Recognizing that users have different preferences, Facebook and Instagram have centralized controls to customize content exposure. The Feed Preferences on Facebook and the Suggested Content Control Center on Instagram provide users with the ability to influence the content they see. Additionally, features like "Interested" and "Not Interested" on Instagram's Reels tab allow users to indicate their preferences and receive more of the content they enjoy. Facebook's "Show more, Show less" feature further empowers users to fine-tune their content consumption. For users desiring a more chronological feed experience, the Feeds tab on Facebook and the Following section on Instagram offer alternatives. Users can also create a Favorites list to ensure they never miss content from their favorite accounts. Enabling Research and Innovation Meta believes in fostering openness and collaboration in the field of research and innovation, particularly regarding transformative AI technologies. Over the past decade, the company has released over 1,000 AI models, libraries, and data sets to support academic and public interest research. In the coming weeks, Meta will introduce the Content Library and API, offering comprehensive access to publicly-available content from Facebook and Instagram. Researchers from qualified institutions can apply for access, fostering scientific exploration while meeting new data-sharing and transparency obligations. By involving researchers early in the development process, Meta aims to receive valuable feedback, ensuring the tools align with their needs and aspirations. Facebook and Instagram's commitment to user control, transparency, and research collaboration signifies a forward-thinking approach, emphasizing the importance of customization and understanding in the ever-evolving landscape of social media platforms. Sources: THX News & Meta. Read the full article
#AIsystems#Algorithmicinfluence#Contentcustomization#Contentranking#Datasharing#FacebookandInstagram#Personalizedexperience#Researchtools#Transparency#Usercontrol
0 notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
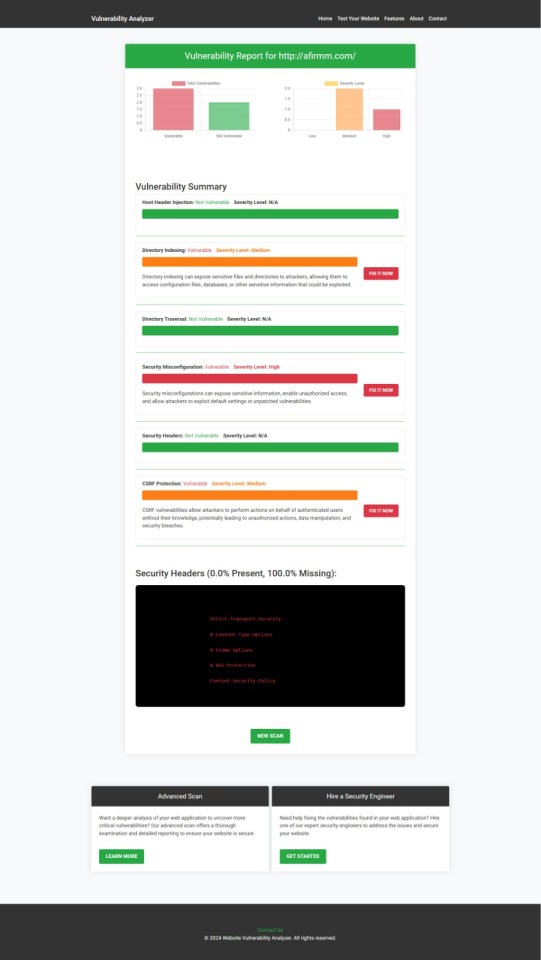
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Photo

🌟💻 Microsoft is back in the spotlight with its controversial "Recall" feature for Windows 11! Initially delayed due to privacy and security concerns, this feature is being re-launched with enhanced security measures that might just make it safer for users. Here’s the lowdown: 📸✨ 1. **Opt-in Only**: No surprises—it's disabled by default! 2. **Encryption FTW**: Your "Snapshots" are now encrypted for extra security. 3. **Smart Protect**: Rate-limiting and anti-hammering techniques in place to keep hackers at bay. 4. **Purview Software**: Sensitive info like passwords won't be stored, so you can breathe easy. 5. **User Control**: Choose what Recall captures and have the option to disable it entirely. Microsoft's working hard to regain trust after the initial backlash. Are you excited or skeptical about this feature? Let's chat! Read more about it here: [Microsoft Revives Controversial Recall Feature with Security Enhancements](https://medium.com/@meditationmusicshiva/microsoft-revives-controversial-recall-feature-with-security-enhancements-645e710fc69d) #Microsoft #Windows11 #RecallFeature #Privacy #Security #TechNews #UserControl #Encryption #WindowsInsider
0 notes
Text
Stay in control with intuitive wallets. #UserControl #CryptoManagement https://thirdweb.digital/
0 notes
Text
From PHP 7 to 8 - A Modern Tour

Introduction Over the years, PHP has evolved significantly, with PHP 7 to 8 bringing substantial improvements and exciting new features. In this blog post, we'll take you on a tour of modern PHP, starting with PHP 7 and leading up to the latest version, PHP 8. In the world of web development, PHP has long been a stalwart. It's the scripting language that powers a significant portion of the web, from small personal blogs to large-scale e-commerce platforms. PHP 7 to 8: A Quantum Leap Released in December 2015, PHP 7 marked a significant turning point in the language's history. Here are some key highlights of PHP 7: 1. Performance Improvements PHP 7 brought substantial performance improvements over its predecessor, PHP 5. With the introduction of the Zend Engine 3.0, PHP 7 achieved a substantial reduction in memory consumption and substantial speed enhancements. This made PHP 7 applications significantly faster, allowing developers to handle more traffic with fewer resources. 2. Scalar Type Declarations In PHP 7, developers could finally specify the data type of function parameters and return values. This addition improved code clarity and helped catch type-related errors early in the development process. phpCopy code function add(int $a, int $b): int { return $a + $b; } 3. Spaceship Operator () The spaceship operator is a handy addition for comparing two values. It returns -1 if the left operand is less than the right, 0 if they are equal, and 1 if the left is greater. PHP copy code $result = $a $b; 4. Null Coalescing Operator (??) This operator simplifies the common task of checking if a variable is set and not null before assigning a default value. phpCopy code $myVar = $otherVar ?? 'default'; PHP 8: A Leap Forward PHP 8, released in November 2020, builds upon the foundations laid by PHP 7. It introduces several exciting features and improvements: 1. Just-In-Time (JIT) Compilation PHP 8 includes a JIT compiler that can significantly boost the performance of CPU-bound code. This feature is optional but can be a game-changer for certain applications. 2. Union Types Union types allow a parameter or return type to accept multiple types of values. This increases the flexibility and expressiveness of your code. PHP copy code function foo(int|string $value): void { // $value can be an integer or a string } 3. Named Arguments With named arguments, you can pass arguments to functions in any order by specifying the parameter name. This enhances code readability and eliminates the need to remember the order of function arguments. phpCopy code function connectToDatabase(string $host, string $username, string $password, string $database) { // ... } connectToDatabase(database: 'mydb', host: 'localhost', username: 'user', password: 'pass'); 4. Attributes Attributes provide a way to add metadata to your code. They are similar to annotations in other programming languages and can be used for various purposes like documentation, autoloading, and more. phpCopy code # class UserController { // ... } 5. Match Expression The match expression is a more robust and versatile alternative to the switch statement, offering cleaner and more predictable code for value matching. phpCopy code $result = match($value) { 'A' => 'Option A', 'B' => 'Option B', default => 'Default Option', }; Conclusion PHP has come a long way from its earlier iterations, and PHP 7 and PHP 8 have ushered in a new era of performance, type safety, and expressiveness. As a web developer, it's crucial to stay updated with the latest features and best practices in the ecosystem. Whether you're building a personal project or working on a large-scale application, the modern versions provide the tools you need to write efficient, maintainable, and secure code. So, whether you're already well-versed in PHP or just starting your journey, exploring PHP's is a must. These versions have set the stage for a more powerful and efficient PHP, and they open up exciting possibilities for web developers around the world. Happy coding! Read the full article
0 notes
Text
Route file example in Laravel
Route file example in Laravel 10 <?php use App\Http\Controllers\UserController; use Illuminate\Http\Request; use Illuminate\Support\Facades\Route; /* |-------------------------------------------------------------------------- | Web Routes |-------------------------------------------------------------------------- | | Here is where you can register web routes for your application. These |…
View On WordPress
0 notes
Text
Laravel: Escribe rutas IDE friendly
Laravel: Escribe rutas IDE friendly
Es muy común encontrar esta forma de definir rutas en un proyecto
Route::get('users', 'UserController@index');
(more…)
View On WordPress
1 note
·
View note
Text
Laravel is a popular PHP framework that provides a robust routing system for building web applications. The routing system in Laravel allows you to define how incoming HTTPrequests should be handled and mapped to specific controllers and actions within your application. To get started with the routing system in Laravel, follow these steps: Routes File: Open the routes/web.php file in your Laravel application. This file contains the route definitions for handling web requests. You can define your routes here using the Route facade. Basic Route: A basic route definition consists of an HTTP verb (e.g., GET, POST) and a URL pattern. For example, to handle a GET request to the root of your application, you can define a route like this: phpCopy code Route::get('/', function () return 'Hello, World!'; ); Route Parameters: You can define route parameters by wrapping them in curly braces within the URL pattern. For example, to capture a user ID in the URL, you can define a route like this: phpCopy code Route::get('/user/id', function ($id) return 'User ID: ' . $id; ); Named Routes: You can assign names to your routes using the name method. Named routes are useful when generating URLs or redirecting to a specific route. For example: phpCopy code Route::get('/user/id', function ($id) return 'User ID: ' . $id; )->name('user.profile'); Route Groups: You can group related routes together using the prefix and middleware methods. The prefix method allows you to add a common prefix to a group of routes, while the middleware method allows you to apply middleware to the routes within the group. For example: phpCopy code Route::prefix('admin')->middleware('auth')->group(function () Route::get('/dashboard', function () return 'Admin Dashboard'; ); // Other admin routes... ); Route Controllers: Instead of using anonymous functions as route callbacks, you can also route to controller actions. First, create a controller using the php artisan make:controller command. Then, you can define a route that points to a specific controller and action. For example: phpCopy code Route::get('/user/id', 'UserController@show'); In the above example, the show method of the UserController will be called when a GET request is made to the specified URL. Route Model Binding: Laravel's routing system also supports route model binding, which automatically injects model instances into your controller actions. For example, if you have a User model, you can define a route like this: phpCopy code Route::get('/user/user', function (User $user) return $user; ); In this case, Laravel will automatically fetch the user with the corresponding ID from the database and pass it to the route callback. These are some of the key concepts of Laravel routing system. By using these techniques, you can define flexible and powerful routes to handle various HTTP requests in your Laravel application. Remember to refer to the official Laravel documentation for more details and advanced routing features: https://laravel.com/docs/routing
0 notes
Text
Top Asp. Net interview questions for experienced.
To develop into. You must enroll in MVC training if you are a Net MVC expert developer to study C#, a widely used programming language, OOPS, SQL Server, and several front-end technologies like HTML, JavaScript, and JQuery. Refer to the MVC interview question and answer pdf in addition to your studies to ace your job interview and advance your professional development. You will get all your concepts cleared if you opt for MVC tutorial.
MVC, or model-view-controller, is an acronym. It is a pattern for software design that was first used in the 1970s. Additionally, the MVC style enforces a separation of responsibilities, which separates the user interface from the domain model and controller functionality (view). These are some of the top asp.net MVC interview questions for experienced.
Here is a list of Asp. Net interview questions which can let you upskill your Career.
1. Describe the life cycle of an MVC application?
Any web application’s two main execution steps are as follows:
● Recognizing the desire
● Delivering a suitable reaction.
There are two primary phases in an MVC application life cycle:
● The request object is being created.
● Response to the browser is sent.
2. What do you think MVC filters mean?
Action methods in MVC are mutually exclusive and determined by controllers and UI controls. Example: The UserController class has the UserAdd and UserDelete functions. However, we frequently wish to do something before or after a particular operation. Using the ASP.NET MVC feature, pre- and post-action behaviors can be added to the controller’s action methods.
3. What does the controller’s before render() function do?
When we manually call render() before the conclusion of a particular operation, this function is necessary. Before the view is rendered and after the logic for the controller action, this method is invoked. It is hardly frequently used.
4. Define DispatcherServerlet?
A class called DispatcherServerlet is responsible for receiving incoming requests and assigning them to the most appropriate resources, such as Views, Models, and Controllers.
5. What in MVC is attribute-based routing?
In ASP.NET MVC, a new attribute route has been added. The routing element can be used to determine URL structure. If the route property is used to decorate the GotoAbout action, indicates that GotoAbout can be called using the Users/about URL structure.
6. How does the MVC pattern handle routing?
Registered routes in the program comprise the route collection, or group, of routes. The collection routes are recorded through the RegisterRoutes method. If the request meets the pattern, the route and a handler define the URL pattern. The first parameter of the MapRoute is the name of the route; the second is the pattern that the URL matches; and the third is the default values for the Placeholders.
7. What distinguishes ViewResult from ActionResult?
ActionResult is an abstract class, and ViewResult is inherited from AbstractResult. When you are dynamically deriving various types of views, ActionResult is useful. FileStreamResult, ViewResult, and JsonResult are ActionResult’s descendant classes. This is a common asp.net MVC interview question for experienced.
8. Describe NonActionAttribute’s significance?
If we want to stop a public method of a controller from being used as an action method by default, we can do so by giving it the NonActionattribute.
9. Define the partial view in MVC?
The MVC partial view renders a portion of the view content. This lessens the need for code requests. The partial view enables the display of a view inside the parent view.
10. Describe MVC Scaffolding?
For ASP.NET web apps, MVC Scaffolding is a framework for code creation. When we want to quickly add code that communicates with data activities in our project, we use scaffolding. Field page templates, filter templates, and entity page templates are included. These scaffold templates make it possible to construct a working data-driven website quickly.
11. Explain ORM and its application?
A framework called the ORM (object-relational mapping) aids in minimizing the amount of handwritten code in a web application. When there aren’t any strict performance requirements, ORM is employed; nevertheless, high-load applications might use frameworks like Dapper.
12. Describe the POST and GET action types?
A resource provided by the POST action type receives data to process. With every POST request, we include the crucial URL and data. Overloads may be Absorbed.
A resource provided by the GET action type is asked for data. With each GET request, the required URLs are passed. Overloads may be absorbed.
13. How will MVC validation be implemented?
With the aid of validators established in the System, we can implement validation in the MVC application.ComponentModel. Namespace for DataAnnotations. The many validators include StringLength, Required, Range, and DataType.
14. What exactly do you mean by WebAPI?
Using WebAPI technology, you may use RESTful principles to provide data over HTTP. This method was implemented to satisfy many clients who needed to consume data from Windows, JavaScript, mobile devices, and other sources.
15. Give us an example of when employing an IoC container was
Advantageous?
The advantages include external management of every object’s life, future contract implementation changes, dependency list changes that do not affect things utilizing the service, and sharing one instance by numerous unrelated Customers.
16. What is Spring MVC?
A Java framework called Spring MVC creates web applications by using the MVC design pattern. It carries out all of the fundamental components of the spring framework, including dependency injection and inversion of control. Spring MVC offers a classy method for using MVC in the Spring Framework with DispatcherServlet. This class translates incoming requests to view models and controllers after receiving them.
17. What does MVC’s ViewState term mean to you?
ViewState is the basis for one of the most typical asp.net interview questions. In contrast to WebForms, MVC lacks ViewState. This is because ViewState is saved in a hidden field on the page, considerably increasing its size and slowing down page loading.
Conclusion
This was a detailed list of MVC-specific ASP.NET interview questions. Be prompt and assured when answering questions during an interview. Answers should be brief and unambiguous, without discussion.
0 notes
Text
Maschine mk controller editor template bitwig 2

#Maschine mk controller editor template bitwig 2 update
Add the code below somewhere inside your init() function. Each member of userControls is an object that will be associated with a CC in our range, and those userControls can then be attached to a parameter in Bitwig using the MIDI learn functionality. Now that we have defined our range, we can create a bank of userControls.
#Maschine mk controller editor template bitwig 2 update
If we weren’t using variables we might have to comb through a ton of code to manually update functions, which is not a good time, and leaves you prone to errors. And these numbers can be available to any functions we use in our script. If we’d like to change this range in the future, we’ll just have to change the values of our variables. There are many advantages to using variables as opposed to just using these numbers when we need them. This is how you create variables in javascript, and we will be referencing these numbers throughout the rest of the script. Add these lines of code somewhere above your init() function: You could use the whole range, but for the sake of demonstration let’s restrict it a bit using these values. There is a lot of information in there, but if you’re ever interested in a more in depth explanation of the functions and methods we use, you’ll want to get friendly with it.įirst, let’s define the range of CC values that we will be using. In there you can explore all of the classes and functions available to us. I would also open Bitwig, navigate to the help menu and pop open their documentation. Navigate to your M圜 file (or whatever you happened to name your file last time), and open it up in your text editor, or development environment of choice. You can download the script HERE, or you can build it up from the script we previously created. This is a pretty straightforward process and only involves a handful of lines of code. In this next installment we will implement freely mappable CCs so you can use any controller you have laying around to interact with Bitwig. In the previous article we walked through the setup and creation of a basic controller script for Bitwig Studio. Posted May 29th, 2015 by Evan Bogunia & filed under Bitwig Studio, Blog, Tutorials.

0 notes
Text
How to Get Query Log in Laravel Eloquent ?
How to Get Query Log in Laravel Eloquent ?
Example 1: Now in this example i can get the directly get current sql query by using toSql() of laravel query builder. So in this example i don’t need to enable query log or something i can directly query like bellow example: Controller Code: <?php namespace App\Http\Controllers; use Illuminate\Http\Request; use App\Models\User; class UserController extends Controller { /** * Write code on…
View On WordPress
0 notes
Text
.@kalilinux .@debian .@cnet .@california .@texas @bitcoin .@coinbase @coinbase @winklevoss @jack .@jack .@larry #amazing #octal @debian .@debian @cybersec_feeds @planetdebian @wired .@california .@texas @swiftonsecurity @swiftonsecuriti @xfceofficial @cnet @techpowerup @pcwelt @tomshardware #reframed #questionforall #it : restated: can i identif y your user+mount setup including acl permissions by simply knowing itis #octal, wheni mount anycode virtually in byteorder1 ,but host this as reverse byte order with spicebits controlbits any virtual machine all ofthe usercontrol expansion any architecture this over acpi calls -12volt
.@kalilinux .@debian .@cnet .@california .@texas @bitcoin .@coinbase @coinbase @winklevoss @jack .@jack .@larry #amazing #octal @debian .@debian @cybersec_feeds @planetdebian @wired .@california .@texas @swiftonsecurity @swiftonsecuriti @xfceofficial @cnet @techpowerup @pcwelt @tomshardware #reframed #questionforall #it : restated: can i identif y your user+mount setup including acl permissions by simply knowing itis #octal, wheni mount anycode virtually in byteorder1 ,but host this as reverse byte order with spicebits controlbits any virtual machine all ofthe usercontrol expansion any architecture this over acpi calls -12volt
.@kalilinux .@debian .@cnet .@california .@texas @bitcoin .@coinbase @coinbase @winklevoss @jack .@jack .@larry #amazing #octal @debian .@debian @cybersec_feeds @planetdebian @wired .@california .@texas @swiftonsecurity @swiftonsecuriti @xfceofficial @cnet @techpowerup @pcwelt @tomshardware #reframed #questionforall #it : restated: can i identify your user+mount setup including acl permissions…
View On WordPress
0 notes
Text
XML Injection in Laravel: Prevention & Secure Coding 🚀
Introduction
XML Injection in Laravel is a critical web security flaw that occurs when attackers manipulate XML input to exploit applications. This vulnerability can lead to data exposure, denial-of-service (DoS) attacks, and even remote code execution in severe cases.

In this post, we will explore what XML Injection is, how it affects Laravel applications, and most importantly, how to prevent it using secure coding practices. We will also show how our Website Vulnerability Scanner can detect vulnerabilities like XML Injection.
What is XML Injection?
XML Injection happens when an application improperly processes XML input, allowing attackers to inject malicious XML data. This can lead to:
Data theft – Attackers can access unauthorized data.
DoS attacks – Malicious XML can crash the application.
Code execution – If poorly configured, it can lead to executing arbitrary commands.
🔍 Example of an XML Injection Attack
Let's consider a Laravel-based ERP system that takes XML input from users:
<?xml version="1.0" encoding="UTF-8"?> <user> <name>John</name> <password>12345</password> </user>
An attacker can inject malicious data to extract sensitive information:
<?xml version="1.0" encoding="UTF-8"?> <user> <name>John</name> <password>12345</password> <role>&exfiltrate;</role> </user>
If the application does not sanitize the input, it may process this malicious XML and expose sensitive data.
How XML Injection Works in Laravel
Laravel applications often use XML parsing functions, and if improperly configured, they may be susceptible to XML Injection.
Consider the following Laravel controller that parses XML input:
use Illuminate\Http\Request; use SimpleXMLElement; class UserController extends Controller { public function store(Request $request) { $xmlData = $request->getContent(); $xml = new SimpleXMLElement($xmlData); $name = $xml->name; $password = $xml->password; return response()->json(['message' => "User $name created"]); } }
🚨 The Problem
The SimpleXMLElement class does not prevent external entity attacks (XXE).
Malicious users can inject XML entities to read sensitive files like /etc/passwd.
How to Prevent XML Injection in Laravel
✅ 1. Disable External Entity Processing (XXE)
Modify XML parsing with libxml_disable_entity_loader() to prevent external entity attacks:
use Illuminate\Http\Request; use SimpleXMLElement; class SecureUserController extends Controller { public function store(Request $request) { $xmlData = $request->getContent(); // Secure XML parsing $xml = new SimpleXMLElement($xmlData, LIBXML_NOENT | LIBXML_DTDLOAD); $name = $xml->name; $password = $xml->password; return response()->json(['message' => "User $name created securely"]); } }
✅ 2. Use JSON Instead of XML
If possible, avoid XML altogether and use JSON, which is less prone to injection attacks:
use Illuminate\Http\Request; class SecureUserController extends Controller { public function store(Request $request) { $validatedData = $request->validate([ 'name' => 'required|string', 'password' => 'required|string|min:6' ]); return response()->json(['message' => "User {$validatedData['name']} created securely"]); } }
✅ 3. Implement Laravel’s Built-in Validation
Always validate and sanitize user inputs using Laravel's built-in validation methods:
$request->validate([ 'xmlData' => 'required|string|max:5000' ]);
Check Your Laravel Website for XML Injection
🚀 You can test your Laravel application for vulnerabilities like XML Injection using our Free Website Security Scanner.
📸 Screenshot of Free Tool Webpage

Screenshot of the free tools webpage where you can access security assessment tools.
How It Works: 1️⃣ Enter your website URL. 2️⃣ Click "Start Test". 3️⃣ Get a full vulnerability report in seconds!
📸 Example of a Security Report to check Website Vulnerability

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Final Thoughts
XML Injection in Laravel can lead to data breaches and security exploits if not handled properly. Following secure coding practices such as disabling external entities, using JSON, and validating input data can effectively prevent XML Injection attacks.
🔗 Check out more security-related articles on our blog: Pentest Testing Blog
💡 Have you checked your website for vulnerabilities? Run a free security scan now at Website Security Checker.
🔥 Stay secure, keep coding safe! 🔥
1 note
·
View note
Photo

🎉💻 Hey fellow tech enthusiasts! Big news from Microsoft! 💻🎉 The much-talked-about Windows Recall feature has made a comeback, and this time it’s packing serious security upgrades! 🔒✨ Here’s a breakdown of the cool enhancements making waves: 1. **Revamped Security Architecture**: Say goodbye to worries! Windows Recall now has proof-of-presence encryption, anti-tampering checks, and secure enclave data management. 🛡️ 2. **Total Data Encryption**: Your sensitive data, including screenshots, is locked down with powerful encryption. Only accessible through Windows Hello! 🙌 3. **Opt-In Control**: No more surprises! Windows Recall is now off by default. Only turn it on if you want to! Plus, you can filter what it remembers. 🗂️ 4. **DLP Technology**: Block the storage of private info like passwords and keep your secrets safe! 🔐 5. **Enhanced Security Reviews**: Microsoft’s brought in serious security measures and assessments, ensuring your data is in safe hands! 👮♂️ For all the details on these cool new features, check out the full article here: [Revamped Windows Recall - Enhanced Security & User Control](https://medium.com/@meditationmusicshiva/revamped-windows-recall-enhanced-security-user-control-a1cab87fe5a5) Let’s chat! Have any of you tried the new Windows Recall? What do you think about the changes? 🤔💬 #WindowsRecall #Microsoft #TechUpdates #Cybersecurity #PrivacyMatters #Windows11 #UserControl
0 notes