#Vendor and Third-Party Management Software
Explore tagged Tumblr posts
Text
Microsoft pinky swears that THIS TIME they’ll make security a priority

One June 20, I'm live onstage in LOS ANGELES for a recording of the GO FACT YOURSELF podcast. On June 21, I'm doing an ONLINE READING for the LOCUS AWARDS at 16hPT. On June 22, I'll be in OAKLAND, CA for a panel and a keynote at the LOCUS AWARDS.

As the old saying goes, "When someone tells you who they are and you get fooled again, shame on you." That goes double for Microsoft, especially when it comes to security promises.
Microsoft is, was, always has been, and always will be a rotten company. At every turn, throughout their history, they have learned the wrong lessons, over and over again.
That starts from the very earliest days, when the company was still called "Micro-Soft." Young Bill Gates was given a sweetheart deal to supply the operating system for IBM's PC, thanks to his mother's connection. The nepo-baby enlisted his pal, Paul Allen (whom he'd later rip off for billions) and together, they bought someone else's OS (and took credit for creating it – AKA, the "Musk gambit").
Microsoft then proceeded to make a fortune by monopolizing the OS market through illegal, collusive arrangements with the PC clone industry – an industry that only existed because they could source third-party PC ROMs from Phoenix:
https://www.eff.org/deeplinks/2019/08/ibm-pc-compatible-how-adversarial-interoperability-saved-pcs-monopolization
Bill Gates didn't become one of the richest people on earth simply by emerging from a lucky orifice; he also owed his success to vigorous antitrust enforcement. The IBM PC was the company's first major initiative after it was targeted by the DOJ for a 12-year antitrust enforcement action. IBM tapped its vast monopoly profits to fight the DOJ, spending more on outside counsel to fight the DOJ antitrust division than the DOJ spent on all its antitrust lawyers, every year, for 12 years.
IBM's delaying tactic paid off. When Reagan took the White House, he let IBM off the hook. But the company was still seriously scarred by its ordeal, and when the PC project kicked off, the company kept the OS separate from the hardware (one of the DOJ's major issues with IBM's previous behavior was its vertical monopoly on hardware and software). IBM didn't hire Gates and Allen to provide it with DOS because it was incapable of writing a PC operating system: they did it to keep the DOJ from kicking down their door again.
The post-antitrust, gunshy IBM kept delivering dividends for Microsoft. When IBM turned a blind eye to the cloned PC-ROM and allowed companies like Compaq, Dell and Gateway to compete directly with Big Blue, this produced a whole cohort of customers for Microsoft – customers Microsoft could play off on each other, ensuring that every PC sold generated income for Microsoft, creating a wide moat around the OS business that kept other OS vendors out of the market. Why invest in making an OS when every hardware company already had an exclusive arrangement with Microsoft?
The IBM PC story teaches us two things: stronger antitrust enforcement spurs innovation and opens markets for scrappy startups to grow to big, important firms; as do weaker IP protections.
Microsoft learned the opposite: monopolies are wildly profitable; expansive IP protects monopolies; you can violate antitrust laws so long as you have enough monopoly profits rolling in to outspend the government until a Republican bootlicker takes the White House (Microsoft's antitrust ordeal ended after GW Bush stole the 2000 election and dropped the charges against them). Microsoft embodies the idea that you either die a rebel hero or live long enough to become the evil emperor you dethroned.
From the first, Microsoft has pursued three goals:
Get too big to fail;
Get too big to jail;
Get too big to care.
It has succeeded on all three counts. Much of Microsoft's enduring power comes from succeeded IBM as the company that mediocre IT managers can safely buy from without being blamed for the poor quality of Microsoft's products: "Nobody ever got fired for buying Microsoft" is 2024's answer to "Nobody ever got fired for buying IBM."
Microsoft's secret sauce is impunity. The PC companies that bundle Windows with their hardware are held blameless for the glaring defects in Windows. The IT managers who buy company-wide Windows licenses are likewise insulated from the rage of the workers who have to use Windows and other Microsoft products.
Microsoft doesn't have to care if you hate it because, for the most part, it's not selling to you. It's selling to a few decision-makers who can be wined and dined and flattered. And since we all have to use its products, developers have to target its platform if they want to sell us their software.
This rarified position has afforded Microsoft enormous freedom to roll out harebrained "features" that made things briefly attractive for some group of developers it was hoping to tempt into its sticky-trap. Remember when it put a Turing-complete scripting environment into Microsoft Office and unleashed a plague of macro viruses that wiped out years worth of work for entire businesses?
https://web.archive.org/web/20060325224147/http://www3.ca.com/securityadvisor/newsinfo/collateral.aspx?cid=33338
It wasn't just Office; Microsoft's operating systems have harbored festering swamps of godawful defects that were weaponized by trolls, script kiddies, and nation-states:
https://en.wikipedia.org/wiki/EternalBlue
Microsoft blamed everyone except themselves for these defects, claiming that their poor code quality was no worse than others, insisting that the bulging arsenal of Windows-specific malware was the result of being the juiciest target and thus the subject of the most malicious attention.
Even if you take them at their word here, that's still no excuse. Microsoft didn't slip and accidentally become an operating system monopolist. They relentlessly, deliberately, illegally pursued the goal of extinguishing every OS except their own. It's completely foreseeable that this dominance would make their products the subject of continuous attacks.
There's an implicit bargain that every monopolist makes: allow me to dominate my market and I will be a benevolent dictator who spends his windfall profits on maintaining product quality and security. Indeed, if we permit "wasteful competition" to erode the margins of operating system vendors, who will have a surplus sufficient to meet the security investment demands of the digital world?
But monopolists always violate this bargain. When faced with the decision to either invest in quality and security, or hand billions of dollars to their shareholders, they'll always take the latter. Why wouldn't they? Once they have a monopoly, they don't have to worry about losing customers to a competitor, so why invest in customer satisfaction? That's how Google can piss away $80b on a stock buyback and fire 12,000 technical employees at the same time as its flagship search product (with a 90% market-share) is turning into an unusable pile of shit:
https://pluralistic.net/2024/02/21/im-feeling-unlucky/#not-up-to-the-task
Microsoft reneged on this bargain from day one, and they never stopped. When the company moved Office to the cloud, it added an "analytics" suite that lets bosses spy on and stack-rank their employees ("Sorry, fella, Office365 says you're the slowest typist in the company, so you're fired"). Microsoft will also sell you internal data on the Office365 usage of your industry competitors (they'll sell your data to your competitors, too, natch). But most of all, Microsoft harvest, analyzes and sells this data for its own purposes:
https://pluralistic.net/2020/11/25/the-peoples-amazon/#clippys-revenge
Leave aside how creepy, gross and exploitative this is – it's also incredibly reckless. Microsoft is creating a two-way conduit into the majority of the world's businesses that insider threats, security services and hackers can exploit to spy on and wreck Microsoft's customers' business. You don't get more "too big to care" than this.
Or at least, not until now. Microsoft recently announced a product called "Recall" that would record every keystroke, click and screen element, nominally in the name of helping you figure out what you've done and either do it again, or go back and fix it. The problem here is that anyone who gains access to your system – your boss, a spy, a cop, a Microsoft insider, a stalker, an abusive partner or a hacker – now has access to everything, on a platter. Naturally, this system – which Microsoft billed as ultra-secure – was wildly insecure and after a series of blockbuster exploits, the company was forced to hit pause on the rollout:
https://arstechnica.com/gadgets/2024/06/microsoft-delays-data-scraping-recall-feature-again-commits-to-public-beta-test/
For years, Microsoft waged a war on the single most important security practice in software development: transparency. This is the company that branded the GPL Free Software license a "virus" and called open source "a cancer." The company argued that allowing public scrutiny of code would be a disaster because bad guys would spot and weaponize defects.
This is "security through obscurity" and it's an idea that was discredited nearly 500 years ago with the advent of the scientific method. The crux of that method: we are so good at bullshiting ourselves into thinking that our experiment was successful that the only way to make sure we know anything is to tell our enemies what we think we've proved so they can try to tear us down.
Or, as Bruce Schneier puts it: "Anyone can design a security system that you yourself can't think of a way of breaking. That doesn't mean it works, it just means that it works against people stupider than you."
And yet, Microsoft – whose made more widely and consequentially exploited software than anyone else in the history of the human race – claimed that free and open code was insecure, and spent millions on deceptive PR campaigns intended to discredit the scientific method in favor of a kind of software alchemy, in which every coder toils in secret, assuring themselves that drinking mercury is the secret to eternal life.
Access to source code isn't sufficient to make software secure – nothing about access to code guarantees that anyone will review that code and repair its defects. Indeed, there've been some high profile examples of "supply chain attacks" in the free/open source software world:
https://www.securityweek.com/supply-chain-attack-major-linux-distributions-impacted-by-xz-utils-backdoor/
But there's no good argument that this code would have been more secure if it had been harder for the good guys to spot its bugs. When it comes to secure code, transparency is an essential, but it's not a sufficency.
The architects of that campaign are genuinely awful people, and yet they're revered as heroes by Microsoft's current leadership. There's Steve "Linux Is Cancer" Ballmer, star of Propublica's IRS Files, where he is shown to be the king of "tax loss harvesting":
https://pluralistic.net/2023/04/24/tax-loss-harvesting/#mego
And also the most prominent example of the disgusting tax cheats practiced by rich sports-team owners:
https://pluralistic.net/2021/07/08/tuyul-apps/#economic-substance-doctrine
Microsoft may give lip service to open source these days (mostly through buying, stripmining and enclosing Github) but Ballmer's legacy lives on within the company, through its wildly illegal tax-evasion tactics:
https://pluralistic.net/2023/10/13/pour-encoragez-les-autres/#micros-tilde-one
But Ballmer is an angel compared to his boss, Bill Gates, last seen some paragraphs above, stealing the credit for MS DOS from Tim Paterson and billions of dollars from his co-founder Paul Allen. Gates is an odious creep who made billions through corrupt tech industry practices, then used them to wield influence over the world's politics and policy. The Gates Foundation (and Gates personally) invented vaccine apartheid, helped kill access to AIDS vaccines in Sub-Saharan Africa, then repeated the trick to keep covid vaccines out of reach of the Global South:
https://pluralistic.net/2021/04/13/public-interest-pharma/#gates-foundation
The Gates Foundation wants us to think of it as malaria-fighting heroes, but they're also the leaders of the war against public education, and have been key to the replacement of public schools with charter schools, where the poorest kids in America serve as experimental subjects for the failed pet theories of billionaire dilettantes:
https://www.ineteconomics.org/perspectives/blog/millionaire-driven-education-reform-has-failed-heres-what-works
(On a personal level, Gates is also a serial sexual abuser who harassed multiple subordinates into having sexual affairs with him:)
https://www.nytimes.com/2022/01/13/technology/microsoft-sexual-harassment-policy-review.html
The management culture of Microsoft started rotten and never improved. It's a company with corruption and monopoly in its blood, a firm that would always rather build market power to insulate itself from the consequences of making defective products than actually make good products. This is true of every division, from cloud computing:
https://pluralistic.net/2022/09/28/other-peoples-computers/#clouded-over
To gaming:
https://pluralistic.net/2023/04/27/convicted-monopolist/#microsquish
No one should ever trust Microsoft to do anything that benefits anyone except Microsoft. One of the low points in the otherwise wonderful surge of tech worker labor organizing was when the Communications Workers of America endorsed Microsoft's acquisition of Activision because Microsoft promised not to union-bust Activision employees. They lied:
https://80.lv/articles/qa-workers-contracted-by-microsoft-say-they-were-fired-for-trying-to-unionize/
Repeatedly:
https://www.reuters.com/technology/activision-fired-staff-using-strong-language-about-remote-work-policy-union-2023-03-01/
Why wouldn't they lie? They've never faced any consequences for lying in the past. Remember: the secret to Microsoft's billions is impunity.
Which brings me to Solarwinds. Solarwinds is an enterprise management tool that allows IT managers to see, patch and control the computers they oversee. Foreign spies hacked Solarwinds and accessed a variety of US federal agencies, including National Nuclear Security Administration (who oversee nuclear weapons stockpiles), the NIH, and the Treasury Department.
When the Solarwinds story broke, Microsoft strenuously denied that the Solarwinds hack relied on exploiting defects in Microsoft software. They said this to everyone: the press, the Pentagon, and Congress.
This was a lie. As Renee Dudley and Doris Burke reported for Propublica, the Solarwinds attack relied on defects in the SAML authentication system that Microsoft's own senior security staff had identified and repeatedly warned management about. Microsoft's leadership ignored these warnings, buried the research, prohibited anyone from warning Microsoft customers, and sidelined Andrew Harris, the researcher who discovered the defect:
https://www.propublica.org/article/microsoft-solarwinds-golden-saml-data-breach-russian-hackers
The single most consequential cyberattack on the US government was only possible because Microsoft decided not to fix a profound and dangerous bug in its code, and declined to warn anyone who relied on this defective software.
Yesterday, Microsoft president Brad Smith testified about this to Congress, and promised that the company would henceforth prioritize security over gimmicks like AI:
https://arstechnica.com/tech-policy/2024/06/microsoft-in-damage-control-mode-says-it-will-prioritize-security-over-ai/
Despite all the reasons to mistrust this promise, the company is hoping Congress will believe it. More importantly, it's hoping that the Pentagon will believe it, because the Pentagon is about to award billions in free no-bid military contract profits to Microsoft:
https://www.axios.com/2024/05/17/pentagon-weighs-microsoft-licensing-upgrades
You know what? I bet they'll sell this lie. It won't be the first time they've convinced Serious People in charge of billions of dollars and/or lives to ignore that all-important maxim, "When someone tells you who they are and you get fooled again, shame on you."

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/06/14/patch-tuesday/#fool-me-twice-we-dont-get-fooled-again
#pluralistic#microsoft#infosec#visual basic#ai#corruption#too big to care#patch tuesday#solar winds#monopolists bargain#eternal blue#transparency#open source#floss#oss#apts
278 notes
·
View notes
Text
Elon Musk’s so-called Department of Government Efficiency (DOGE) has plans to stage a “hackathon” next week in Washington, DC. The goal is to create a single “mega API”—a bridge that lets software systems talk to one another—for accessing IRS data, sources tell WIRED. The agency is expected to partner with a third-party vendor to manage certain aspects of the data project. Palantir, a software company cofounded by billionaire and Musk associate Peter Thiel, has been brought up consistently by DOGE representatives as a possible candidate, sources tell WIRED.
Two top DOGE operatives at the IRS, Sam Corcos and Gavin Kliger, are helping to orchestrate the hackathon, sources tell WIRED. Corcos is a health-tech CEO with ties to Musk’s SpaceX. Kliger attended UC Berkeley until 2020 and worked at the AI company Databricks before joining DOGE as a special adviser to the director at the Office of Personnel Management (OPM). Corcos is also a special adviser to Treasury Secretary Scott Bessent.
Since joining Musk’s DOGE, Corcos has told IRS workers that he wants to pause all engineering work and cancel current attempts to modernize the agency’s systems, according to sources with direct knowledge who spoke with WIRED. He has also spoken about some aspects of these cuts publicly: "We've so far stopped work and cut about $1.5 billion from the modernization budget. Mostly projects that were going to continue to put us down the death spiral of complexity in our code base," Corcos told Laura Ingraham on Fox News in March.
Corcos has discussed plans for DOGE to build “one new API to rule them all,” making IRS data more easily accessible for cloud platforms, sources say. APIs, or application programming interfaces, enable different applications to exchange data, and could be used to move IRS data into the cloud. The cloud platform could become the “read center of all IRS systems,” a source with direct knowledge tells WIRED, meaning anyone with access could view and possibly manipulate all IRS data in one place.
Over the last few weeks, DOGE has requested the names of the IRS’s best engineers from agency staffers. Next week, DOGE and IRS leadership are expected to host dozens of engineers in DC so they can begin “ripping up the old systems” and building the API, an IRS engineering source tells WIRED. The goal is to have this task completed within 30 days. Sources say there have been multiple discussions about involving third-party cloud and software providers like Palantir in the implementation.
Corcos and DOGE indicated to IRS employees that they intended to first apply the API to the agency’s mainframes and then move on to every other internal system. Initiating a plan like this would likely touch all data within the IRS, including taxpayer names, addresses, social security numbers, as well as tax return and employment data. Currently, the IRS runs on dozens of disparate systems housed in on-premises data centers and in the cloud that are purposefully compartmentalized. Accessing these systems requires special permissions and workers are typically only granted access on a need-to-know basis.
A “mega API” could potentially allow someone with access to export all IRS data to the systems of their choosing, including private entities. If that person also had access to other interoperable datasets at separate government agencies, they could compare them against IRS data for their own purposes.
“Schematizing this data and understanding it would take years,” an IRS source tells WIRED. “Just even thinking through the data would take a long time, because these people have no experience, not only in government, but in the IRS or with taxes or anything else.” (“There is a lot of stuff that I don't know that I am learning now,” Corcos tells Ingraham in the Fox interview. “I know a lot about software systems, that's why I was brought in.")
These systems have all gone through a tedious approval process to ensure the security of taxpayer data. Whatever may replace them would likely still need to be properly vetted, sources tell WIRED.
"It's basically an open door controlled by Musk for all American's most sensitive information with none of the rules that normally secure that data," an IRS worker alleges to WIRED.
The data consolidation effort aligns with President Donald Trump’s executive order from March 20, which directed agencies to eliminate information silos. While the order was purportedly aimed at fighting fraud and waste, it also could threaten privacy by consolidating personal data housed on different systems into a central repository, WIRED previously reported.
In a statement provided to WIRED on Saturday, a Treasury spokesperson said the department “is pleased to have gathered a team of long-time IRS engineers who have been identified as the most talented technical personnel. Through this coalition, they will streamline IRS systems to create the most efficient service for the American taxpayer. This week the team will be participating in the IRS Roadmapping Kickoff, a seminar of various strategy sessions, as they work diligently to create efficient systems. This new leadership and direction will maximize their capabilities and serve as the tech-enabled force multiplier that the IRS has needed for decades.”
Palantir, Sam Corcos, and Gavin Kliger did not immediately respond to requests for comment.
In February, a memo was drafted to provide Kliger with access to personal taxpayer data at the IRS, The Washington Post reported. Kliger was ultimately provided read-only access to anonymized tax data, similar to what academics use for research. Weeks later, Corcos arrived, demanding detailed taxpayer and vendor information as a means of combating fraud, according to the Post.
“The IRS has some pretty legacy infrastructure. It's actually very similar to what banks have been using. It's old mainframes running COBOL and Assembly and the challenge has been, how do we migrate that to a modern system?” Corcos told Ingraham in the same Fox News interview. Corcos said he plans to continue his work at IRS for a total of six months.
DOGE has already slashed and burned modernization projects at other agencies, replacing them with smaller teams and tighter timelines. At the Social Security Administration, DOGE representatives are planning to move all of the agency’s data off of legacy programming languages like COBOL and into something like Java, WIRED reported last week.
Last Friday, DOGE suddenly placed around 50 IRS technologists on administrative leave. On Thursday, even more technologists were cut, including the director of cybersecurity architecture and implementation, deputy chief information security officer, and acting director of security risk management. IRS’s chief technology officer, Kaschit Pandya, is one of the few technology officials left at the agency, sources say.
DOGE originally expected the API project to take a year, multiple IRS sources say, but that timeline has shortened dramatically down to a few weeks. “That is not only not technically possible, that's also not a reasonable idea, that will cripple the IRS,” an IRS employee source tells WIRED. “It will also potentially endanger filing season next year, because obviously all these other systems they’re pulling people away from are important.”
(Corcos also made it clear to IRS employees that he wanted to kill the agency’s Direct File program, the IRS’s recently released free tax-filing service.)
DOGE’s focus on obtaining and moving sensitive IRS data to a central viewing platform has spooked privacy and civil liberties experts.
“It’s hard to imagine more sensitive data than the financial information the IRS holds,” Evan Greer, director of Fight for the Future, a digital civil rights organization, tells WIRED.
Palantir received the highest FedRAMP approval this past December for its entire product suite, including Palantir Federal Cloud Service (PFCS) which provides a cloud environment for federal agencies to implement the company’s software platforms, like Gotham and Foundry. FedRAMP stands for Federal Risk and Authorization Management Program and assesses cloud products for security risks before governmental use.
“We love disruption and whatever is good for America will be good for Americans and very good for Palantir,” Palantir CEO Alex Karp said in a February earnings call. “Disruption at the end of the day exposes things that aren't working. There will be ups and downs. This is a revolution, some people are going to get their heads cut off.”
15 notes
·
View notes
Text
So this is what the Biden administration spent it's last week in office doing. It's important to know this isn't unusual activity for them. But this is all just in one week:
"Out With a Bang: Enforcers Go After John Deere, Private Equity Billionaires
https://www.thebignewsletter.com/p/out-with-a-bang-enforcers-go-after
At least for a few more days, laws are not suggestions. In the end days of strong enforcement, a flurry of litigation is met with a direct lawsuit by billionaires against Biden's Antitrust chief.
Matt Stoller
Jan 16, 2025
It’s less than a week until this era of antitrust ends. And while much of the news has been focused elsewhere, enforcers have engaged in a flurry of action, which will by legal necessity continue into the next administration. One case in particular angered some of the most powerful people on Wall Street, the partners of a $600 billion private equity firm called Kohlberg Kravis Roberts (KKR).
But before getting to that suit, here’s a partial list of some of the actions enforcers have taken in the last two weeks.
The Federal Trade Commission
Filed a monopolization claim against agricultural machine maker John Deere for generating $6 billion by prohibiting farmers from being able to repair their own equipment, a suit which Wired magazine calls a “tipping point” for the right to repair movement.
Released another report on pharmacy benefit managers, including that of UnitedHealth Group, showing that these companies inflated prices for specialty pharmaceuticals by more than $7 billion.
Sued Greystar, a large corporate landlord, for deceiving renters with falsely advertised low rents and not including mandatory junk fees in the price.
Issued a policy statement that gig workers can’t be prosecuted for antitrust violations when they try to organize, and along with the Antitrust Division, updated guidance on labor and antitrust.
Put out a series of orders prohibiting data brokers from selling sensitive location information.
Finalized changes to a rule barring third party targeted advertising to children without an explicit opt-in.
The Consumer Financial Protection Bureau
Went to court against Capital One for cheating consumers out of $2 billion by deceiving them on savings accounts and interest rates.
Fined cash app purveyor Block $175 million for fostering fraud on its platform and then refusing to offer customer support to affected consumers.
Proposed a rule to prohibit take-it-or-leave-it contracts from financial institutions that allow firms to de-bank users over how they express themselves or whether they seek redress for fraud.
Issued a report with recommendations on how states can update their laws to protect against junk fees and privacy abuses.
Sued credit reporting agency Experian for refusing to investigate consumer disputes and errors on credit reports.
Finalized a rule to remove medical debt from credit scores.
The Antitrust Division
Sued to block a merger of two leading business travel firms, American Express Global Business Travel Group and CWT Holdings.
Filed a complaint against seven giant corporate landlords for rent-fixing, using the software and consulting firm RealPage.
Got four guilty pleas in a bid-rigging conspiracy by IT vendors against the U.S. government, a guilty plea from an asphalt vendor company President, and convicted five defendants in a price-fixing scam on roofing contracts.
Issued a policy statement that non-disclosure agreements that deter individuals from reporting antitrust crimes are void, and that employers “using NDAs to obstruct or impede an investigation may also constitute separate federal criminal violations.”
Filed two amicus briefs with the FTC, one supporting Epic Games in its remedy against Google over app store monopolization, and the other supporting Elon Musk in his antitrust claims against OpenAI, Microsoft, and Reid Hoffman.
And honorary mention goes to the Department of Transportation for suing Southwest and fining Frontier for ‘chronically delayed flights.’"
It's worth reading the entire piece because the Biden people have also gone after KKR which is one of the biggest and most well-connected private equity firms. Remember when suddenly last year all the rich people who used to donate to both parties stopped giving money to Democrats? The billionaires coup against Biden was because of anti trust enforcement.
IF YOU'RE THINKING "GOSH I NEVER HEARD ABOUT ANY OF THIS BEFORE" I HOPE YOU CAN PUT TOGETHER THAT THE NEWS AND SOCIAL MEDIA PLATFORMS ARE ALL OWNED BY BILLIONAIRES WHO ARE VERY ANGRY ABOUT ALL OF THIS AND MAYBE THAT'S WHY YOU NEVER SAW ANYONE TALK ABOUT THE HUGE RESURGENCE OF ANTI TRUST WORK DONE BY BIDEN FOR THE LAST FOUR YEARS.
And no, Trump cannot magically make this all go away. The lawsuits will have to be played out and many of them have state level components that mean the feds can't just shut them down.
X
11 notes
·
View notes
Text
Charting the Course to SAP HANA Cloud
The push towards SAP HANA cloud shift stems from the need for agility and responsiveness in a dynamic business climate. The cloud promises reduced infrastructure expenses, robust data analytics, and the nimbleness to address changing needs quickly. However, for many companies, transitioning from on-premise SAP HANA to the cloud involves navigating concerns around data security, performance, and potentially relinquishing control of business-critical ERP systems.
SAP HANA Enterprise Cloud: A Tailored Offering
In light of these challenges, SAP presented the SAP HANA Enterprise Cloud (HEC), a private cloud service designed expressly for mission-critical workloads. HEC advertises no compromise on performance, integration, security, failover, or disaster recovery. It spotlights versatility, strong customer support, and end-to-end coverage - from strategic planning to application management. This offering intends to provide the cloud’s agility and innovation under SAP’s direct guidance and expertise.
Actual Delivery of HANA Enterprise Cloud
Despite SAP’s messaging, the HEC’s delivery involves a consortium of third-party providers, including HPE, IBM, CenturyLink, Dimension Data, and Virtustream. SAP collaborates with these partners, who bid on projects often awarded to the lowest bidder, to leverage specialized capabilities while upholding SAP’s standards.
Weighing the Pros and Cons
Partnering with competent vendors ensures clients receive secure, best-practice SAP hosting and support. HEC’s comprehensive solution integrates licensing, infrastructure, and support with touted scalability and integration.
However, several customer challenges emerge. Firstly, leveraging SAP’s brand for cloud hosting and SAP managed services risks diminishing anticipated cost savings. Secondly, the lack of direct engagement with third-party providers raises concerns about entrusting critical ERP operations to unseen partners. This dynamic obscures visibility and control over SAP HANA migration and management.
Furthermore, the absence of a direct relationship between SAP HANA users and cloud suppliers may complicate support, especially for urgent issues warranting rapid response. While SAP’s ecosystem aims to guarantee quality and security, intermediation can hinder the timely resolution of critical situations, affecting system uptime and operations.
SAP HANA Cloud: A Strategic Decision
As SAP systems become increasingly vital, migrating SAP HANA is not simply a technical or operational choice but a strategic one. SAP HANA transcends a database or software suite – it constitutes a competitive advantage that, when optimized, can spur tremendous innovation and success. This migration necessitates meticulous planning, execution, and governance to ensure the transition empowers rather than compromises SAP HANA’s strategic value.
In this context, selecting the ideal cloud model and service providers represents critical decisions. Companies must scrutinize partners beyond cost, evaluating track records, SAP skills, security protocols, and the aptitude to deliver personalized, responsive service.
The Future SAP HANA Cloud Trajectory
As we advance into 2024, the SAP DATA Cloud Analytics landscape continues evolving. Innovations in cloud technology, security, and service creation provide new prospects for migration planning. Firms must stay updated on cloud service advancements, SAP’s strategic direction, and cloud shift best practices to navigate this transition successfully.
To accomplish this, companies should:
Collaborate cross-functionally to align SAP HANA cloud plans with broader business goals and technology roadmaps.
Ensure chosen cloud environments and suppliers meet rigorous data security, privacy, and regulatory standards.
Assess infrastructure ability to support SAP HANA performance requirements and scale amid fluctuating demands.
Institute clear governance and support structures for effective issue resolution throughout and post-migration.
Transitioning SAP HANA to the cloud is complex but ultimately rewarding, unlocking efficiency, agility, and innovation when executed deliberately. By weighing the strategic, operational, and technical dynamics, businesses can drive this migration smoothly, fully capturing SAP HANA’s power to fuel future prosperity.
2 notes
·
View notes
Text
How to Choose the best ERP for Engineering Industry?
Introduction:
In the ever-evolving landscape of the engineering industry, staying ahead of the competition requires streamlined processes, real-time decision-making, and efficient resource management. This is where Enterprise Resource Planning (ERP) systems come into play. As a leading ERP solution provider, Shantitechnology (STERP) understands the critical role that ERP plays in the success of manufacturing enterprises. In this blog, we will guide you through the essential considerations for selecting the best ERP for the engineering industry, focusing on ERP for manufacturing industry, ERP system for manufacturing industry, ERP solution provider, ERP software for manufacturing industry, and the best ERP for manufacturing industry.

Understanding the Unique Needs of the Engineering Industry:
Before delving into the selection process, it's crucial to recognize the unique requirements of the engineering and manufacturing sector. The complexity of operations, intricate supply chains, and the need for precise production planning make the engineering industry distinct. A robust ERP for manufacturing industry should address these challenges seamlessly.
Key Considerations for Choosing ERP for Manufacturing Industry:
Comprehensive Functionality:
Look for ERP systems that offer comprehensive functionality tailored to the engineering industry. This includes modules for production planning, materials management, quality control, and supply chain management. The best ERP for manufacturing industry should integrate all these aspects to provide a holistic solution.
Scalability:
As your engineering business grows, so should your ERP system. Opt for an ERP solution that is scalable, allowing you to add functionalities and users as needed. This ensures that your ERP system can adapt to the changing needs of your manufacturing processes.
Real-time Data Integration:
The ability to access real-time data is crucial for making informed decisions. Choose an ERP system that facilitates seamless integration with various data sources within your organization. This ensures that decision-makers have access to up-to-date information for accurate analysis and planning.
Customization Options:
Every manufacturing business is unique, and your ERP system should reflect that. A flexible ERP solution allows for customization to align with your specific processes and workflows. This adaptability ensures that the ERP system enhances efficiency without imposing rigid structures.
User-Friendly Interface:
An intuitive and user-friendly interface is vital for successful ERP implementation. Ensure that the ERP software for manufacturing industry you choose has an interface that is easy to navigate, minimizing the learning curve for your staff and maximizing productivity.
Mobile Accessibility:
In today's fast-paced business environment, having access to your ERP system on the go is essential. Look for ERP solutions that offer mobile accessibility, enabling key stakeholders to make decisions and monitor operations remotely.
Integration with Third-party Applications:
A best-in-class ERP system should be able to integrate seamlessly with other third-party applications. This ensures that your engineering business can leverage the latest technologies and tools without disrupting existing processes.
Compliance and Security:
Compliance with industry regulations and data security are non-negotiable aspects of ERP for manufacturing industry. Ensure that the ERP solution provider adheres to the necessary standards and provides robust security features to safeguard sensitive information.
Cost Considerations:
While the aim is to invest in the best ERP for manufacturing industry, it's essential to consider the total cost of ownership. Evaluate the upfront costs, ongoing maintenance fees, and potential hidden expenses to make an informed decision that aligns with your budget.
Vendor Support and Training:
A reliable ERP solution provider should offer comprehensive support and training programs. Evaluate the level of support provided during the implementation phase and inquire about ongoing support options. Adequate training ensures that your team can maximize the benefits of the ERP system.
Choosing the Best ERP System for Manufacturing Industry – A Case for STERP:
Now that we've outlined the key considerations, let's explore how Shantitechnology (STERP) excels in providing the best ERP for manufacturing industry.
Comprehensive Functionality:
STERP offers a comprehensive suite of ERP solutions specifically designed for the engineering and manufacturing sector. From production planning to quality control, our ERP system covers all aspects of your operations, ensuring a seamless workflow.
Scalability:
STERP understands that the engineering industry is dynamic, with businesses experiencing growth and changes. Our ERP solution is highly scalable, allowing you to add modules and users as your business expands.
Real-time Data Integration:
With STERP's ERP system, real-time data integration is at the core. Our solution enables you to access accurate and up-to-date information, empowering your decision-makers to respond swiftly to changing market demands.
Customization Options:
STERP recognizes that each manufacturing business has its unique processes. Our ERP solution provides robust customization options, allowing you to tailor the system to match your specific workflows and requirements.
User-Friendly Interface:
STERP places a strong emphasis on user experience. Our ERP system features an intuitive and user-friendly interface, ensuring that your team can quickly adapt to the new system, minimizing downtime and maximizing productivity.
Mobile Accessibility:
In a world where business operations extend beyond the office walls, STERP's ERP system offers mobile accessibility. Stay connected and in control, whether you're on the shop floor or attending a business meeting.
Integration with Third-party Applications:
STERP's ERP system is designed to integrate seamlessly with a wide range of third-party applications. This flexibility allows your business to stay at the forefront of technological advancements without disrupting your existing processes.
Compliance and Security:
STERP is committed to compliance with industry regulations and prioritizes the security of your data. Our ERP system incorporates robust security features to ensure the confidentiality and integrity of your sensitive information.
Cost Considerations:
STERP believes in transparency when it comes to costs. Our pricing model is designed to provide value for your investment, with no hidden fees. We work with you to ensure that the total cost of ownership aligns with your budgetary constraints.
Vendor Support and Training:
STERP stands by your side throughout the implementation process and beyond. Our dedicated support team is ready to assist, and our training programs are designed to equip your team with the knowledge and skills needed to make the most of our ERP system.
Conclusion:
Choosing the best ERP for manufacturing industry is a strategic decision that can significantly impact the efficiency and competitiveness of your engineering business. By considering factors such as comprehensive functionality, scalability, real-time data integration, customization options, user-friendly interface, mobile accessibility, integration capabilities, compliance, security, cost, and vendor support, you can make an informed choice.
As a trusted ERP solution provider, Shantitechnology (STERP) offers a tailored ERP system that addresses the unique needs of the engineering industry. Our commitment to excellence, coupled with a focus on innovation and customer satisfaction, positions STERP as the ideal partner for your ERP journey. Invest in the best ERP for manufacturing industry – choose STERP and empower your engineering business for success in the digital era.
#best ERP for manufacturing industry#ERP software for manufacturing industry#ERP solution provider#ERP system for manufacturing industry#ERP for manufacturing industry
6 notes
·
View notes
Text
Ensuring Data Security in Online Market Research while using AI to Collect Data
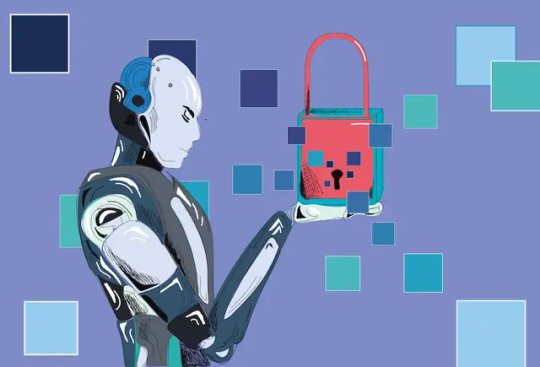
In the realm of Online market research, the integration of Artificial Intelligence (AI) has revolutionized data collection processes, offering unparalleled efficiency and insights. However, alongside these advancements, ensuring robust data security measures is paramount to safeguarding sensitive information.
Encryption Protocols: Implementing robust encryption protocols is the first line of defense in protecting data integrity. Utilizing industry-standard encryption algorithms ensures that data remains encrypted both in transit and at rest, mitigating the risk of unauthorized access.
Access Controls: Implementing strict access controls ensures that only authorized personnel can access sensitive data. Role-based access controls (RBAC) limit access to data based on predefined roles and responsibilities, minimizing the potential for data breaches.
Anonymization and Pseudonymization: Employing techniques such as anonymization and pseudonymization reduces the risk of exposing personally identifiable information (PII). By replacing identifiable information with artificial identifiers, researchers can analyze data while preserving individual privacy.
Data Minimization: Adhering to the principle of data minimization involves collecting only the necessary data required for research purposes. By reducing the volume of sensitive information stored, organizations can minimize the potential impact of a data breach.
Secure Data Transmission: Utilizing secure communication channels, such as encrypted connections (e.g., SSL/TLS), ensures that data transmitted between clients and servers remains confidential. Secure socket layers provide end-to-end encryption, safeguarding against eavesdropping and tampering.
Regular Security Audits: Conducting regular security audits and assessments helps identify vulnerabilities and areas for improvement within existing security frameworks. By proactively addressing security gaps, organizations can enhance their resilience to potential threats.
Compliance with Regulations: Adhering to relevant data protection regulations such as GDPR, CCPA, and HIPAA ensures legal compliance and fosters trust among participants. Compliance frameworks outline specific requirements for data handling, storage, and processing, guiding organizations in implementing robust security measures.
Continuous Monitoring and Response: Implementing real-time monitoring systems allows organizations to detect and respond to security incidents promptly. Automated alerting mechanisms notify administrators of suspicious activities, enabling swift intervention to mitigate potential risks.
Employee Training and Awareness: Educating employees about data security best practices and the importance of safeguarding sensitive information is critical in maintaining a secure environment. Training programs raise awareness about common security threats and equip staff with the knowledge to identify and respond appropriately to potential risks.
Vendor Due Diligence: When outsourcing data collection or processing tasks to third-party vendors, conducting thorough due diligence is essential. Assessing vendor security practices and ensuring compliance with data protection standards mitigate the risk of data breaches arising from external sources.
By implementing these comprehensive strategies, organizations can uphold the integrity and confidentiality of data collected through AI-powered online market research. Prioritizing data security not only fosters trust with participants but also mitigates the risk of reputational damage and regulatory non-compliance.
Also read:
The Right Approach to Designing & Conducting Online Surveys
Know more: Online Community Management Software
panel management platform
Online Project Management Platform
#market research#onlineresearch#samplemanagement#panelmanagement#communitypanel#datacollection#datainsights
2 notes
·
View notes
Text
What is Quick Payable?
Quick Payable is a user-friendly application available on Salesforce's app exchange platform. It is designed to simplify and streamline the accounts payable process for businesses. Here are the key features and benefits of Quick Payable:
1. Efficient Bill Management:
- Quick Payable allows businesses to easily manage bills from multiple vendors.
- The intuitive interface makes it easy to organize and track invoices.
- Businesses can ensure timely payments and avoid penalties or late fees.
2. Automated Invoice Data Capture:
- Quick Payable leverages advanced software to automate invoice data capture.
- This eliminates the need for manual data entry, saving time and reducing errors.
- The system intelligently extracts relevant information from invoices, such as invoice numbers, due dates, and amounts.
3. Streamlined Approval Process:
- With Quick Payable, businesses can customize their approval workflow.
- Approvers can be assigned based on vendor configurations, ensuring the right people review and authorize invoices.
- This streamlines the approval process, reducing bottlenecks and delays in the payment cycle.
4. Complete Expense Visibility:
- Quick Payable provides rich dashboards and reports, offering complete visibility of expenses.
- Businesses can track and analyze spending patterns, identify unnecessary costs, and optimize their spending.
- This level of insight empowers businesses to make informed financial decisions and improve overall financial management.
5. Effortless Data Export:
- Quick Payable allows for seamless data export to third-party ERP systems.
- Businesses can integrate their accounts payable information with existing financial software.
- This eliminates the need for manual transfers and ensures data consistency across different platforms.
6. Enhanced Efficiency and Error Reduction:
- By utilizing Quick Payable, businesses can improve the efficiency of their accounts payable processes.
- The app automates repetitive tasks, freeing up valuable time for the finance team.
- With fewer errors and delays, businesses can focus on strategic financial planning and ensure accurate financial records.
In summary, Quick Payable is a powerful tool that simplifies and streamlines the accounts payable process for businesses. With features like efficient bill management, automated invoice data capture, and streamlined approval processes, businesses can improve their financial management capabilities. The complete expense visibility and effortless data export features further enhance efficiency and reduce errors. Embrace Quick Payable to optimize your accounts payable processes and take control of your financial management.
2 notes
·
View notes
Text
5 IT Cost Saving Strategies for Your Enterprise Infrastructure
Managing enterprise IT infrastructure is a balancing act between performance, reliability, and cost. As technology evolves rapidly, so do expenses. To stay competitive and efficient, IT managers must find smart ways to reduce costs without compromising service quality or security. Below are five proven IT cost-saving strategies that can make a meaningful impact on your enterprise infrastructure.
1. Extend the Life of Existing Hardware
Rather than defaulting to frequent hardware refresh cycles, enterprises can often extend the life of servers, storage devices, and networking hardware through proper maintenance and strategic upgrades. Partnering with a third-party maintenance provider for post-warranty support can reduce costs by 30-70% compared to OEM contracts.
💡 Tip: Use asset lifecycle management tools to monitor hardware health and optimize replacement timing based on performance, not just age.
2. Leverage Cloud and Hybrid Infrastructure
Moving specific workloads to the cloud—or adopting a hybrid cloud model—can reduce the cost of owning and maintaining physical infrastructure. Cloud services provide flexibility and scalability, allowing you to pay only for what you use.
💡 Tip: Use cloud cost optimization tools to avoid waste, identify underutilized instances, and right-size your resources.
3. Optimize Software Licensing
Licensing costs can quietly eat into IT budgets. Regular audits of software usage can help identify unused or underutilized licenses, especially with large suites or per-user subscription models.
💡 Tip: Consider switching to open-source or lower-cost alternatives for certain tools, and negotiate volume discounts or enterprise agreements with vendors.
4. Consolidate and Virtualize Resources
Server consolidation through virtualization reduces the need for physical hardware, power, and cooling. It also simplifies management, backup, and disaster recovery planning.
💡 Tip: Evaluate opportunities for workload consolidation across departments and assess whether underused servers can be decommissioned or repurposed.
5. Implement Preventive Maintenance and Monitoring
Downtime is costly. By implementing proactive monitoring tools and a preventive maintenance strategy, you can catch performance issues before they lead to outages or data loss—saving both money and reputation.
💡 Tip: Schedule regular health checks for your servers and storage systems, and set up alerts for threshold-based issues like CPU spikes or disk failure warnings.
Final Thoughts
Cost optimization isn’t about cutting corners—it’s about making smarter, data-driven decisions. With the right strategies, enterprises can lower IT infrastructure costs while improving agility, performance, and reliability. Evaluate your current infrastructure and consider where these strategies can have the most immediate impact.

0 notes
Text
Why Outsourcing Accounts Payable Is a Smart Move for Growing Businesses
In the dynamic world of business, where time and resources are increasingly scarce, companies—especially growing businesses—must focus on their core competencies to scale effectively. One of the most impactful ways to streamline operations and improve financial efficiency is by outsourcing accounts payable (AP).
Accounts payable is a crucial component of any company's financial structure. It involves the management of outgoing payments to vendors and suppliers. As businesses grow, the volume and complexity of transactions increase, often putting a strain on internal resources. This is where outsourcing can be a game-changer.
In this blog, we'll explore why outsourcing accounts payable is a smart move for growing businesses, diving deep into the benefits, potential challenges, and best practices.
What Is Accounts Payable Outsourcing?
Outsourcing accounts payable refers to delegating the task of managing vendor invoices, payment processing, reconciliation, and reporting to a third-party service provider. These firms specialize in financial operations and typically use a combination of human expertise and technology to deliver efficient AP solutions.
Whether it's a startup scaling rapidly or an SME trying to reduce operational overhead, AP outsourcing offers a strategic solution.
Key Benefits of Outsourcing Accounts Payable
1. Cost Efficiency
One of the most compelling reasons to outsource AP is the cost savings. Hiring, training, and retaining skilled accounting professionals is expensive. Add to that the infrastructure costs—software licenses, hardware, office space—and the bill quickly adds up.
Outsourcing offers access to a team of experts without the overhead. According to various financial studies, businesses can save 30-50% in operational costs by outsourcing their AP functions.
2. Improved Accuracy and Compliance
Manual processing is prone to errors: duplicate payments, missed deadlines, or incorrect data entry. These mistakes not only affect cash flow but also damage vendor relationships and expose the company to compliance risks.
Outsourcing partners use advanced AP automation tools that improve accuracy, ensure regulatory compliance (like GST, TDS, or VAT filings), and maintain detailed audit trails. This is especially critical for growing companies that may not have an internal compliance expert.
3. Scalability and Flexibility
As your business grows, so does the volume of invoices and payments. Handling this growth with a small in-house team can be chaotic and error-prone. An outsourced partner, however, can scale their services based on your needs—be it seasonal spikes or long-term expansion.
This scalability ensures you’re never understaffed or overpaying for underutilized services.
4. Access to Expertise and Technology
Outsourcing firms are often at the forefront of financial technology, offering cloud-based platforms, automation tools, and AI-driven insights that growing businesses may not afford independently.
You gain immediate access to:
E-invoicing and OCR scanning
Real-time dashboards
Automated three-way matching (PO, invoice, receipt)
Fraud detection algorithms
These technologies not only streamline operations but also offer valuable insights into spending patterns and vendor performance.
5. Faster Processing and Timely Payments
Late payments can result in penalties, missed discounts, and strained vendor relationships. Outsourced teams operate with defined SLAs (Service Level Agreements) ensuring that payments are processed promptly and systematically.
Some vendors even offer 24/7 service availability, ensuring that invoice processing doesn’t stop—regardless of time zones or holidays.
6. Enhanced Focus on Core Business
For growing companies, leadership should be focused on strategy, innovation, and customer experience—not bogged down with invoice approvals and reconciliations.
By outsourcing AP, businesses free up internal teams to concentrate on growth-driving activities. It reduces the burden on finance departments and enables better collaboration across other functions like procurement and operations.
7. Reduced Risk of Fraud
Accounts payable fraud is a growing concern for companies of all sizes. Insider threats, duplicate payments, or fictitious vendors can go unnoticed in a busy, under-resourced team.
Outsourcing firms implement strict internal controls, such as:
Segregation of duties
Multi-level invoice approvals
Secure data handling protocols
These systems significantly reduce the risk of fraud and protect your financial assets.
When Should You Consider Outsourcing?
Outsourcing AP is not a one-size-fits-all decision. Here are key indicators that it might be time:
Your AP volume has grown beyond your team's capacity
You're experiencing frequent payment errors or delays
You lack real-time visibility into outstanding liabilities
Internal AP costs are rising disproportionately
You want to modernize your finance function without heavy investment
If any of these resonate, it's a clear sign your business could benefit from a professional AP outsourcing partner.
Common Concerns and How to Address Them
Despite its advantages, some business leaders hesitate to outsource due to the following concerns:
1. Loss of Control
Concern: “Will I lose visibility or control over my finances?”
Solution: Reputable providers offer transparent dashboards, regular reports, and customized workflows that keep you in the driver’s seat. In fact, you may gain more control through better visibility and tracking.
2. Data Security Risks
Concern: “Is my financial data safe?”
Solution: Leading firms are compliant with ISO, GDPR, and SOC standards, ensuring secure data handling, storage, and transfer. Always vet your outsourcing partner's cybersecurity policies.
3. Quality of Service
Concern: “Will they understand my business well enough?”
Solution: Look for providers with industry-specific experience and check references. A well-chosen partner will take time to understand your vendor network, business cycles, and approval structures.
Best Practices for a Successful AP Outsourcing Strategy
To ensure a smooth transition and maximum ROI, follow these best practices:
Choose the Right Partner: Vet their industry expertise, technological capabilities, client testimonials, and service model.
Define Clear SLAs: Establish expectations around invoice turnaround times, reporting frequency, and accuracy rates.
Maintain Communication: Set up regular check-ins and access to a dedicated account manager.
Integrate Systems: Ensure that the AP system integrates well with your ERP, accounting software, or procurement tools.
Monitor KPIs: Track metrics like DPO (Days Payable Outstanding), invoice processing time, error rate, and early payment discounts captured.
Real-Life Example: A Growing Tech Startup
Take the case of a 3-year-old SaaS startup that recently secured Series A funding. With its vendor base expanding globally, the in-house finance team struggled to manage over 500 invoices monthly.
After outsourcing their AP function to a third-party specialist:
Invoice turnaround time dropped from 7 days to 2 days
Vendor satisfaction scores improved
They saved 40% on finance operation costs
Leadership could reallocate resources to support customer success and R&D
This is a prime example of how outsourcing AP creates operational and strategic advantages for growth-focused businesses.
Conclusion
Outsourcing accounts payable is not just a cost-cutting tactic—it's a strategic move that helps growing businesses scale faster, operate more efficiently, and stay financially healthy.
In a world where agility and smart resource allocation are key to survival and success, delegating AP to a trusted partner allows companies to sharpen their competitive edge while maintaining strong financial governance.
If you're a growing business looking to enhance your financial processes, it may be time to consider outsourcing your accounts payable—because doing everything in-house is no longer the only smart choice.
1 note
·
View note
Text
How Outsourcing Prior Authorization Can Boost Revenue and Efficiency
In today’s fast-paced healthcare environment, medical practices are under constant pressure to streamline operations, ensure regulatory compliance, and maximize revenue. One area that significantly impacts both cash flow and operational efficiency is prior authorization (PA). The process, while essential for payer compliance, is time-consuming, resource-intensive, and often riddled with errors. That’s where outsourcing prior authorization services emerges as a game-changer.
Let’s explore how outsourcing this critical function can help your practice reduce overhead, improve approval turnaround times, minimize claim denials, and ultimately enhance both revenue and efficiency.
What Is Prior Authorization and Why Is It a Challenge?
Prior authorization is the process of obtaining approval from a health insurance company before a prescribed treatment, procedure, or medication is provided. Although its purpose is to control costs and ensure appropriate care, it often results in administrative bottlenecks.
Common challenges include:
Long approval wait times
Increased claim denials due to errors or missed documentation
High administrative costs
Poor communication between providers and payers
Reduced time for patient care
According to the American Medical Association, physicians and staff spend an average of 13 hours per week on prior authorization tasks per physician. This directly impacts staff productivity and can delay necessary treatments for patients.
The Shift Toward Outsourcing Prior Authorization
Medical practices, hospitals, and specialty clinics are increasingly turning to third-party experts or virtual medical assistants to manage prior authorization tasks. These specialized vendors use advanced technology, experienced staff, and real-time tracking systems to handle authorizations more efficiently than in-house teams.
Let’s break down the key ways outsourcing can boost both revenue and operational efficiency.
1. Faster Authorization Turnaround
Outsourcing companies specialize in prior authorization workflows and have established payer-specific processes that accelerate approvals. Their familiarity with payer guidelines, medical necessity criteria, and documentation requirements means fewer errors and quicker response times.
Benefits:
Improved cash flow through faster claim submission
Enhanced patient satisfaction due to fewer treatment delays
Reduced time chasing payer approvals
2. Reduced Administrative Costs
Hiring and training in-house staff for prior authorizations can be expensive. From salary and benefits to ongoing training and overhead, the costs add up quickly. By outsourcing, practices can reduce or even eliminate many of these fixed costs.
Cost savings include:
Lower staffing expenses
No investment in PA software or technology
Scalability without extra hiring during peak volumes
3. Minimized Claim Denials and Rework
Claim denials due to prior authorization errors can result in significant revenue leakage. Outsourcing partners are well-versed in payer requirements and use automated tools and checklists to ensure complete and accurate submissions.
Impact on revenue:
Fewer denials and appeals
Increased first-pass resolution rates
Reduced write-offs and accounts receivable backlogs
4. More Time for Patient Care
By offloading prior authorization responsibilities to a dedicated team, your in-house clinical and administrative staff can focus more on patient care and other mission-critical tasks. This enhances the overall patient experience and reduces staff burnout.
Efficiency gains:
Streamlined front-desk operations
Faster scheduling and check-ins
Higher staff morale and retention
5. 24/7 Availability and Scalability
Many outsourcing companies offer 24/7 support, especially those with virtual PA teams. This ensures that authorizations are being processed even outside of regular office hours, reducing delays and handling urgent requests more efficiently.
Scalable support:
Manage seasonal or specialty-based volume spikes
Rapid deployment during payer changes or software transitions
Continuous workflow regardless of internal staff shortages
6. Improved Compliance and Documentation
Outsourced PA vendors are trained in HIPAA compliance and ensure that every authorization request is documented according to federal and state guidelines. They also provide audit-ready reports and logs, minimizing legal risks and supporting better practice management.
Compliance benefits:
Lower risk of HIPAA violations
Ready documentation for audits
Better tracking of payer correspondence
7. Better Insights Through Analytics
Top-tier prior authorization service providers offer real-time dashboards, detailed reports, and analytics that help practices identify bottlenecks and improve workflows. These insights allow for data-driven decisions to further optimize performance.
Sample metrics tracked:
Approval turnaround time
Denial reasons
Most frequently delayed services
Payer performance trends
Use Case: Specialty Practices Reaping the Rewards
Specialty care providers like cardiology, radiology, oncology, and orthopedics deal with complex authorizations daily. In these settings, outsourcing has shown even more dramatic results due to:
Higher volume of PA requests
More extensive documentation
Specific payer requirements for procedures and medications
Outsourcing allows specialty practices to avoid treatment delays, reduce revenue loss, and deliver high-quality patient care without getting bogged down by paperwork.
Choosing the Right Prior Authorization Partner
Not all outsourcing providers are created equal. To see true revenue and efficiency gains, look for vendors that offer:
Experience with your specific specialty or payer mix
A HIPAA-compliant platform and trained staff
Transparent pricing models
Real-time communication and tracking
Integration with your EHR/EMR or PM system
Conclusion: A Smart Move for Forward-Thinking Practices
Outsourcing prior authorization is no longer just a cost-cutting strategy—it’s a revenue and efficiency booster that helps your practice remain competitive, agile, and patient-focused. Whether you’re a small primary care clinic or a large specialty group, the benefits are clear: faster approvals, fewer denials, reduced admin work, and better financial outcomes.By trusting experts to handle the administrative burden of authorizations, your team can focus on what truly matters—delivering exceptional patient care and growing your practice.
#priorauthorization#medical coding services#medicalbillingservices#healthcarercmservices#prior authorization services
0 notes
Text
Empowering Hospitality with Next‑Gen Software in 2025 and Beyond
The pace of change in hospitality technology has accelerated—today’s systems aren’t just tools, but catalysts for exceptional guest experiences, operational agility, and long-term profitability. Whether you're managing a chain of resorts or a boutique city inn, here’s a comprehensive look at the software pillars that every forward-thinking hotel needs to thrive in 2025 and beyond.
1. A Unified, Cloud-Native Property Management System (PMS)
At the core of any modern hotel operation lies the PMS. But the bar for today’s PMS is higher: it must be:
In short, the PMS must act as the central nervous system of your operations—comprehensive, interconnected, and secure.
2. Channel Management & Real-Time Distribution
With inventory spread across OTAs, direct booking channels, GDS systems, and third-party agents, maintaining up-to-the-minute availability and pricing is paramount. A channel management tool helps by:
By ensuring your digital storefront is cohesive and responsive, your property can increase visibility without compromising accuracy.
3. Integrated Point-of-Sale Systems
Hospitality isn’t limited to room nights—restaurants, bars, spas, mini-bars, and event venues all contribute to your bottom line. A modern POS must:
By bridging POS and PMS, hotels ensure billing accuracy, operational efficiency, and improved guest satisfaction.
4. AI‑Powered Revenue & Pricing Intelligence
In an era defined by data, your pricing strategy must be fluid and nuanced. AI-driven revenue platforms:
Rather than relying on manual rate adjustments, hotels in 2025 need automated, responsive systems.
5. Contactless & Mobile Guest Tools
Guest preferences have evolved: convenience is no longer optional—it’s expected. Leading technologies include:
These innovations do more than reduce friction—they empower staff to focus on human moments.
6. Deep CRM & Guest Personalization
Once a guest checks in, intelligent CRM systems begin collecting data—preferences, spending behavior, past visits—to:
The goal: each guest feels known, valued, and treated as more than a reservation.
7. Smart Housekeeping & Maintenance Management
Operational efficiency begins behind the scenes. Technology helps with:
Systems like hotelkit—a SaaS module for housekeeping and facilities—are gaining traction, especially in international hotel groups.
8. Analytics, BI & Operational Dashboards
Modern systems ingest data from all departments to surface insights, such as:
Analytics become the threads tying together revenue, operations, and guest satisfaction—fueling better decisions daily.
9. Security, Privacy & Compliance
Handling guest IDs, payments, and preferences requires stringent data governance:
With rising cyber risks, software must be trustworthy and resilient—always.
10. Ecosystem Compatibility & Open APIs
Your tech stack should avoid vendor lock-in:
An interoperable ecosystem means flexibility: assemble best‑in‑class tools, adapt over time, and pivot as guest trends shift.
Emerging Tech & Trends to Watch
Why This Matters: Tangible Impact
Implementing a Winning Tech Strategy
Conclusion
In 2025, hospitality software is far more than operational support—it’s a strategic asset. The right combination of modern PMS, intelligent revenue engines, seamless integration, guest-centric tools, CRM, analytics, and security provides a foundation not just to operate, but to differentiate and lead.
By embracing cloud-first, AI-enhanced, mobile-enabled, and interoperable platforms, hotel operators can create intuitive experiences for guests, efficient workflows for staff, and a revenue engine that reacts instantly to market dynamics.
Bold, connected, data-informed, and guest-centric: that’s the shape of hospitality excellence in 2025—and it starts with investing in the right software ecosystem.
0 notes
Text
Top 5 Best ERP Software Solutions in 2025 to Streamline Your Business
In today’s fast-evolving digital landscape, managing operations manually or using scattered tools is no longer efficient. Modern businesses require a centralized system that integrates all departments, including accounting, sales, inventory, and HR. That’s where ERP (Enterprise Resource Planning) software plays a vital role.
But with countless platforms available, how do you identify the best ERP software for your business? This guide highlights the top ERP solutions in 2025 and helps you make an informed decision based on your needs.
What is ERP Software?
ERP software is an all-in-one business management solution designed to automate, streamline, and integrate core business processes. By providing real-time data access across departments, ERP systems improve collaboration, reduce operational costs, and enhance decision-making.
Key Features of Top ERP Systems
The best ERP software includes:
Modular design – Choose and scale features as your business grows.
Real-time analytics – Gain valuable insights for faster decision-making.
Cloud or on-premise deployment – Flexible hosting options.
Integration-ready – Connects with third-party applications.
Industry-specific modules – Tailored features for different sectors.
Best ERP Software in 2025
1. Odoo ERP
A leading open-source ERP platform known for its flexibility and affordability. Odoo offers fully integrated modules for CRM, accounting, inventory, manufacturing, HR, and more.
Ideal for: SMEs looking for customizable and scalable ERP solutions Why choose: User-friendly interface, strong community support, modular design
2. SAP Business One
A robust ERP software designed for growing businesses. It handles everything from financial management and procurement to operations and analytics.
3. Oracle NetSuite
A cloud-based ERP system offering advanced capabilities for global businesses, including CRM, finance, e-commerce, and supply chain management.
4. Microsoft Dynamics 365
A comprehensive platform combining ERP and CRM functionalities with deep integration into Microsoft’s ecosystem.
5. TallyPrime
Popular in India for its ease of use and GST compliance, TallyPrime is a simple yet powerful ERP solution focused on accounting and business management.
How to Select the Best ERP Software for Your Business
Consider the following before making your decision:
Business size and industry type
Budget and implementation timeline
Required features and scalability
Local support and vendor expertise
Integration with your current systems
Why Choose Banibro IT Solution?
At Banibro IT Solution, we specialize in helping businesses find and implement the best ERP software to suit their unique needs. As a trusted Odoo implementation partner, we provide end-to-end ERP consulting, customization, and support to ensure a seamless digital transformation.
Whether you need a scalable ERP for manufacturing, a retail-ready solution, or cloud ERP for a growing business, our experts will guide you every step of the way.
Final Thoughts
The right ERP software can dramatically improve your efficiency, accuracy, and growth potential. By partnering with the right ERP implementation firm, you ensure that your investment yields long-term results.
✅ Ready to Upgrade Your Business Operations?
Let Banibro IT Solution help you choose and implement the best ERP software for your business. 📞 Contact us today for a Free ERP Consultation
0 notes
Text
Cybersecurity Threats to Watch Out For in 2025

The digital landscape is like a double-edged sword: offering new ways of connectivity and new vistas of innovation, while on the other side harboring a constantly mutating set of threats and increasingly complex attacks. As we approach 2025, we also see cybersecurity threats growing in complexity and reach. Thus, looking into these emerging threats should not merely be an interest for IT professionals, but something each person and organization involved in the online world should be aware of.
In the hands of cybercriminals, new technologies like Artificial Intelligence (AI) and Machine Learning (ML) are used to launch increasingly sophisticated and hence difficult to resist attacks. Learning what the top security issues of 2025 will be is the first in laying out necessary defenses.
Why Vigilance is Crucial in 2025
AI-Powered Attacks: Threat actors are using AI to make phishing smarter, malware more evasive and brute-force attacks faster.
Expanded Attack Surface: More devices (IoT), cloud services, and remote work setups mean more entry points for cybercriminals.
Sophisticated Social-Engineering: Attacks are becoming highly personalized and convincing, thereby being harder to detect.
Data Is Gold: Both individual and corporate data remains the Lucifer for theft, extortion, and manipulation.Lucifer prime target
Here are the top Cybersecurity Threats to Watch Out For in 2025:
1. AI-Powered Phishing and Social Engineering
The generic scam emails will be a thing of the past. In 2025, AI will revolutionize extremely sophisticated and bespoke phishing campaigns. The vast data lakes will be churned by AI to create messages that resemble trusted contacts, sound more convincing, and adapt in real-time, creating an impasse for the human end users in separating legitimate from malicious.
What to do: Promote enhanced employee awareness through AI-based phishing simulation, employ strong email filters, and intensify the mantra of "verify, don't trust."
2. Evolving Ransomware 3.0 (Data Exfiltration & Double Extortion)
Ransomware isn't just about encrypting data anymore. Attackers will increasingly focus on exfiltrating sensitive data before encryption. This "double extortion" tactic means they demand payment not only to decrypt your data but also to prevent its public release or sale on the dark web.
What to do: Implement robust data backup and recovery plans (following the 3-2-1 rule), deploy advanced endpoint detection and response (EDR) solutions, and strengthen network segmentation.
3. Supply Chain Attacks on the Rise
Targeting a single, vulnerable link in a software or service supply chain allows attackers to compromise multiple organizations downstream. As seen with past major breaches, this method offers a high return on investment for cybercriminals, and their sophistication will only grow.
What to do: Implement stringent vendor risk management, conduct regular security audits of third-party suppliers, and ensure software integrity checks.
4. IoT and Edge Device Vulnerabilities
The proliferation of Internet of Things (IoT) devices (smart homes, industrial sensors, medical devices) creates a massive, often insecure, attack surface. Many IoT devices lack strong security features, making them easy targets for botnets, data theft, or even physical disruption.
What to do: Secure all IoT devices with strong, unique passwords, segment IoT networks, and ensure regular firmware updates. Implement strong network security protocols.
5. Deepfakes and AI-Generated Misinformation
Advancements in AI make it possible to create highly realistic fake audio, video, and images (deepfakes). These can be used for sophisticated spear-phishing attacks, corporate espionage, market manipulation, or even to spread widespread disinformation campaigns, eroding trust and causing financial damage.
What to do: Implement robust identity verification protocols, train employees to be highly skeptical of unsolicited requests (especially via video/audio calls), and rely on verified sources for information.
6. Cloud Security Misconfigurations
While cloud providers offer robust security, misconfigurations by users remain a leading cause of data breaches. As more data and applications migrate to the cloud, improperly configured storage buckets, identity and access management (IAM) policies, or network settings will continue to be prime targets.
What to do: Adopt cloud security best practices, implement continuous monitoring tools, and conduct regular audits of cloud configurations.
Fortifying Your Digital Defenses
So, putting in a multi-layer defense model would do in order to be an active response to those cybersecurity threats in 2025. From the perspective of the individual, this encompasses strong passwords, MFA, software updates on a regular basis, and a little basic cybersecurity awareness. Organizations, on the other hand, would look at investing in good security infrastructure, ongoing employee training, threat intelligence, and possibly, ethical hacking exercises.
Cybersecurity Training in Ahmedabad could be your next area of interest in order to keep updating yourself and your team on fighting the said contemporary threats. The future is digital; securing it is the prerogative of every individual.
Contact us
Location: Bopal & Iskcon-Ambli in Ahmedabad, Gujarat
Call now on +91 9825618292
Visit Our Website: http://tccicomputercoaching.com/
0 notes
Text
IoT Device Management Market Poised for Massive Expansion Through 2031

The global IoT Device Management Market stood at US$ 1.58 billion in 2020 and is projected to reach a market valuation of US$ 10.42 billion by the end of 2031, expanding at a robust CAGR of 18.7% during the forecast period. The proliferation of IoT-connected devices across industries such as healthcare, manufacturing, transportation, and smart homes is driving the need for centralized device management solutions. As enterprises increasingly rely on remote operations and automation, IoT device management services are emerging as essential tools for ensuring system performance, data integrity, and network security.
Market Drivers & Trends
Several key factors are propelling the growth of the IoT device management market:
Security and Data Protection Needs: With rising cyber threats and concerns over privacy, organizations are investing in robust device management platforms that ensure secure device authentication, firmware updates, and data encryption.
Adoption of 5G Technology: The deployment of 5G networks is enabling higher device density and real-time communication, making IoT management solutions even more vital for maintaining network efficiency.
Industrial Automation and Industry 4.0: The shift towards smart factories and digitally connected operations is increasing demand for IoT platforms that offer seamless integration, monitoring, and analytics capabilities.
Hybrid Cloud Adoption: Enterprises are leaning towards hybrid cloud environments to balance cost, scalability, and performance. This trend is directly influencing the deployment strategies for IoT device management solutions.
Latest Market Trends
AI and Machine Learning Integration: Emerging IoT platforms now include AI/ML algorithms for predictive maintenance, anomaly detection, and intelligent automation.
Increased Use of Edge Computing: As real-time responsiveness becomes critical, edge computing is being integrated with IoT management systems to process data closer to the source.
Unified Platforms: Vendors are offering unified IoT platforms that combine device management, data analytics, and security, streamlining operations and reducing overhead.
Key Players and Industry Leaders
The market features intense competition with several prominent global players innovating to expand their footprints:
Amazon Web Services Inc.
ARM Holdings
Robert Bosch GmbH
IBM Corporation
Microsoft Corporation
Oracle Corporation
SAP SE
Altair SmartWorks
GE Digital
Upswift
PTC
These players are investing in research and development to offer secure, scalable, and easy-to-integrate solutions. Key focus areas include enhanced APIs, cloud-based infrastructure, and interoperability with third-party systems.
Download Sample PDF Copy: https://www.transparencymarketresearch.com/sample/sample.php?flag=S&rep_id=27224
Recent Developments
Telefonica & PTC Partnership (2020): Telefonica collaborated with PTC to leverage ThingWorx for delivering integrated IoT applications and analytics.
GE’s IIoT Company Formation (2018): GE announced the creation of an independent Industrial IoT software entity with US$ 1.2 billion in revenue.
Siemens, IBM, and Red Hat Collaboration (2021): The trio launched a hybrid cloud initiative to unlock real-time value from industrial IoT data.
These strategic alliances reflect a broader trend toward cloud-first and interoperable IoT device management ecosystems.
Market Opportunities
Emerging Economies and Smart City Projects: Rapid digitalization in Asia Pacific, the Middle East, and Latin America offers new opportunities for IoT solution providers.
Healthcare Sector Boom: The increased use of connected health monitors and wearable medical devices is creating demand for secure, real-time device management platforms.
Standardization and Interoperability: Efforts to develop universal IoT standards will improve device compatibility and accelerate market adoption.
Future Outlook
Looking ahead, the IoT device management market is expected to witness exponential growth as industries transition to data-driven decision-making and remote asset monitoring. Innovations in AI, edge computing, and 5G connectivity will redefine how businesses manage and secure their IoT infrastructure. The integration of blockchain for enhanced security and transparency is also anticipated to disrupt the industry. Vendors that prioritize interoperability, scalability, and user experience will likely lead the market through the next decade.
Market Segmentation
The IoT device management market is segmented as follows:
By Deployment:
Public Cloud
Private Cloud
Hybrid Cloud
By Application:
Smart Manufacturing
Smart Home
Smart Utilities
Smart Retail
Connected Health
Smart Transportation
By Solution:
Security Solution
Data Management
Remote Monitoring
Network Bandwidth Management
These segments allow for customized deployment based on industry needs and enterprise scale.
Regional Insights
North America dominates the global IoT device management market, attributed to its advanced IT infrastructure, high adoption of connected technologies, and significant investments in R&D. Companies in this region are focusing on enhancing real-time data management tools and security platforms.
Europe follows as a strong market due to stringent data privacy laws (like GDPR), pushing vendors to build more secure and compliant solutions.
Asia Pacific is emerging rapidly with smart city projects, manufacturing innovation, and growing IoT penetration in countries like China, India, and Japan.
Middle East & Africa and South America are gradually adopting IoT technologies, especially in utilities, transportation, and public sector automation.
Why Buy This Report?
Comprehensive Market Intelligence: Covers all major trends, challenges, opportunities, and forecast data
In-depth Segment Analysis: By application, deployment, solution, and geography
Competitor Landscape: Market share analysis, product strategies, and SWOT profiling of leading players
Quantitative & Qualitative Insights: Provides strategic recommendations based on current market dynamics and future projections
Customizable Data: Includes electronic (PDF) and Excel formats for easy analysis and integration into business presentations or strategies
Frequently Asked Questions (FAQs)
1. What is the expected CAGR of the IoT Device Management Market from 2021 to 2031? The market is expected to grow at a CAGR of 18.7% during this period.
2. What factors are driving the growth of the market? Key drivers include rising data security concerns, adoption of 5G networks, increasing IoT penetration, and demand for real-time monitoring.
3. Which region leads the global IoT device management market? North America currently leads the global market, followed by Europe and Asia Pacific.
4. Who are the major players in the market? Some of the leading players are Amazon Web Services, IBM Corporation, Microsoft, Oracle, Bosch, PTC, and SAP SE.
5. What are the major application areas of IoT device management? The key applications include smart manufacturing, smart homes, connected health, and smart utilities.
6. What are the challenges faced by the market? Major challenges include privacy risks, infrastructure limitations, real-time data complexities, and lack of standardization.
0 notes
Text
Privileged Access Management Market Driven by AI and Cloud Trends in 2032 Outlook
Privileged Access Management Market was valued at USD 2.69 billion in 2023 and is expected to reach USD 17.42 billion by 2032, growing at a CAGR of 23.13% from 2024-2032.
Privileged Access Management Market is undergoing rapid expansion as organizations face mounting cybersecurity threats targeting privileged credentials. With data breaches becoming more sophisticated, enterprises across critical sectors—including finance, healthcare, and government—are prioritizing PAM solutions to secure administrative access and enforce least-privilege policies.
U.S. Market Shows Aggressive Adoption in Response to Rising Cyber Threats
Privileged Access Management Market is increasingly recognized as a core component of modern cybersecurity frameworks. Companies are investing in PAM tools to enhance visibility, automate session monitoring, and mitigate internal risks. The demand is especially strong in compliance-heavy regions, where regulators emphasize secure access to sensitive systems.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6666
Market Keyplayers:
Fortinet (FortiPAM, FortiAuthenticator)
BeyondTrust (Password Safe, Privilege Management for Windows & Mac)
CyberArk (Privileged Access Manager, Endpoint Privilege Manager)
Broadcom (Symantec PAM, Symantec PAM Gateway)
Imprivata (OneSign, Privileged Access Management)
Optiv Security (Privileged Access Management Services, Identity & Access Management Solutions)
Okta (Okta Privileged Access, Okta Identity Governance)
IBM (Security Verify Privilege Vault, Security Identity Governance & Intelligence)
Micro Focus (OpenText) (NetIQ Privileged Account Manager, NetIQ Identity Governance)
ManageEngine (Zoho) (PAM360, Password Manager Pro)
HashiCorp (Vault, Boundary)
One Identity (Safeguard for Privileged Sessions, Safeguard for Privileged Passwords)
ARCON (Privileged Access Management, Session Monitoring & Recording)
Netwrix (Privileged Access Management, Auditor for Active Directory)
Delinea (Secret Server, Privilege Manager)
Wallix (Bastion, AdminBastion)
Saviynt (Saviynt for Privileged Access, Identity Governance Cloud)
Senhasegura (PAM Core, DevOps Secret Manager)
KronTech (Single Connect, Dynamic Password Controller)
miniOrange (PAM Solution, Identity Broker)
EmpowerID (Privileged Access Manager, Identity Governance Platform)
StrongDM (Infrastructure Access Platform, Admin UI)
CyberSolve (PAM Advisory, Identity & Access Consulting Services)
Opal Security (Access Review Automation, Just-in-Time Access)
Foxpass (PAM Solution, LDAP-as-a-Service)
Secureden (PAM Software, Remote Access Management)
RevBits (Privileged Access Management, Endpoint Security)
Silverfort (Unified Identity Protection, Secure Access for PAM)
IDM Technologies (IDM Privileged Access, Identity Governance Suite)
Market Analysis
The Privileged Access Management (PAM) market is being shaped by an urgent need to defend against identity-based attacks and insider threats. As businesses adopt hybrid cloud infrastructures and remote access models, managing privileged credentials becomes a top priority. Organizations are shifting from traditional perimeter security to identity-first security strategies that include PAM as a foundational layer. In the U.S., regulatory mandates like SOX, HIPAA, and FISMA are driving PAM implementation across enterprises, while in Europe, GDPR compliance and industry-specific norms continue to fuel adoption.
Market Trends
Growing demand for cloud-native and hybrid PAM solutions
Integration of AI and machine learning for threat detection and access analytics
Increased automation of access provisioning and de-provisioning
Rise in just-in-time (JIT) access and zero standing privileges
Expansion of PAM to DevOps and third-party vendor environments
Enhanced auditing and reporting features to meet compliance
Privileged session recording and real-time behavior analytics
Market Scope
The Privileged Access Management Market is not limited to large enterprises—it is increasingly essential for mid-sized businesses managing critical assets and data. With digital transformation accelerating, PAM is becoming a non-negotiable part of cybersecurity roadmaps.
Secure access to critical systems across cloud and on-prem
Real-time monitoring and auditing of privileged sessions
Identity-centric security aligned with zero-trust models
Vendor and third-party access governance
Scalable solutions for enterprises of all sizes
Policy enforcement and credential vaulting
Forecast Outlook
The future of the PAM market is marked by aggressive innovation, strategic investments, and global standardization. With threat actors constantly evolving, businesses are embracing dynamic, identity-focused security architectures. PAM solutions are expected to integrate more deeply with endpoint protection, identity governance, and broader zero-trust ecosystems. The market's trajectory points toward smarter, automated, and user-centric systems that deliver both protection and operational efficiency.
Access Complete Report: https://www.snsinsider.com/reports/privileged-access-management-market-6666
Conclusion
The Privileged Access Management Market is no longer a niche solution—it’s a strategic imperative. As U.S. and European enterprises adapt to a hyper-connected, threat-prone environment, PAM stands at the forefront of cyber resilience. With increasing attacks on administrative access, organizations that prioritize PAM will not only meet regulatory standards but will also build trust, reduce risk, and enable secure digital transformation.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A experiences robust growth in Cloud Access Security Broker Market driven by data security priorities
U.S.A sees rising adoption of Voice Biometrics Market Size across banking and government sectors
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
ISO 27001 Certification in E-Commerce: Why It's Crucial for Bahrain's Online Market

Introduction: Bahrain's e-commerce industry has been on a tear over the last few years. From digital service providers to online retail sites, the business is booming — as are the risks.
In a time when a breach of data can ruin trust in an instant, information security has become the linchpin of e-commerce success. That's where ISO/IEC 27001 certification comes in.
For Bahraini online companies, ISO 27001 is not merely a matter of cybersecurity; it is a matter of gaining customer trust, safeguarding digital property, and adhering to local and global standards. If you have an e-commerce website, payment gateway, or digital logistics system — this certification can be your differentiator.
What Is ISO 27001?
ISO/IEC 27001 is the global standard for Information Security Management Systems (ISMS). It provides a systematic framework to determine, control, and minimize security threats in your business processes.
While you and many companies concentrate on firewalls and antivirus software, ISO 27001 addresses the issue in a more comprehensive, intelligent way. It assists you in controlling:
Data access rights and user permissions
Vulnerabilities to cyberattacks
Customer privacy and confidentiality
Legal and regulatory risks
System availability and dependability
Rather than responding to violations, ISO 27001 prevents them from occurring in the first place.
Why is ISO 27001 Crucial for E-Commerce in Bahrain?
1. Customer Trust Is Everything
Customers in e-commerce exchange confidential information — from bank details to home addresses and shopping history. One leak or hack can destroy your reputation forever.
With ISO 27001, you demonstrate to customers that:
You're serious about their data
You adhere to global best practices
Their personal and financial data is secure
This confidence translates to increased sales, increased retention, and increased word-of-mouth.
2. Cybersecurity Threats Are on the Rise
From phishing sites to ransomware, cybercriminals are attacking online shops more than ever before. Bahrain's move toward digital services also raises local exposure.
ISO 27001 assists you in determining and securing your vulnerabilities prior to attackers. It encompasses not only tech, but also human mistake — such as bad password behavior or unprotected third-party integrations.
3. Regulatory Compliance Is Increasingly Tight
The Personal Data Protection Law (PDPL) in Bahrain and international regulations such as GDPR mandate companies to treat data responsibly.
ISO 27001 assists you in:
Remaining compliant with privacy legislation
Steering clear of enormous fines
Recording and auditing your data handling policies
If you handle foreign customers or partners, certification simplifies overseas data compliance.
4. Encourages Business Partnerships and Expansion
If you are looking to partner with payment processors, logistics firms, or online banks, ISO 27001 provides you with a stamp of credibility.
It demonstrates that your company is dependable, secure, and in compliance with global standards — making it simpler to secure strategic partnerships or attract investment.
E-Commerce Risk Domains Addressed by ISO 27001
This is how ISO 27001 directly relates to e-commerce sites:
E-Commerce Sector
ISO 27001 Implementation
Payment Processing
Secure transaction practices, encryption, fraud management
Customer Data Management
Regulated access, storage security, data classification
Website and App Security
Anti-SQL injection, XSS, DDoS attack protection
Staff Access Controls
Role-based access, password policy
Cloud Hosting
Third-party risk management, backup and availability
Vendor Integrations
Secure APIs and contracts, SLA protections
Email & Marketing
Anti-spam, opt-in/opt-out compliance, email fraud checks
Even one vulnerability might result in a breach. ISO 27001 covers all of them under one umbrella.
Real-World Example: ISO 27001 for a Bahrain-Based Online Retailer
Suppose a Bahrain-based online retail startup sells clothing and electronics throughout the GCC.
Before ISO 27001:
Customer accounts were exposed because of weak password policies
There was no formal process in place for processing data requests or complaints
Third-party plugins within the site were not current
A minor phishing attack briefly took down the site
Following ISO 27001:
Access rights were designated and enforced
Customer information was encrypted and backed up
Periodic risk assessments enabled patching vulnerabilities early on
A well-defined incident response strategy enabled quick recovery by the business from any breach attempt
Result: Customers felt safer, repeat purchases increased, and the company expanded confidently into Saudi Arabia.
Who Should Consider ISO 27001 in Bahrain’s E-Commerce Sector?
Whether you’re a startup or an established platform, ISO 27001 is applicable to:
Online retail stores
B2B e-commerce platforms
Subscription-based service portals
E-wallets and digital payment solutions
Delivery and logistics apps
Online booking and reservation sites
Platforms handling user-generated content or transactions
If your company gathers, maintains, or processes sensitive data, then you must seriously think about ISO 27001 certification.
How to Get ISO 27001 Certified in Bahrain
The certification process usually involves:
Initial Risk Assessment Determine your existing security stance and information assets.
ISMS Development Develop policies and procedures to secure those assets depending on risk levels.
Training and Implementation Train your staff to operate the new system — from management to IT and customer service.
Internal Audit Verify everything is in working order and address any loopholes.
External Certification Audit A certification organization audits your system and grants the ISO 27001 certificate (for 3 years).
Annual Surveillance Keep your system current with audits and improvements.
What Are the Benefits for E-Commerce Businesses?
Increased customer confidence
Less risk of data breaches
Improved compliance with PDPL and global laws
Simplified business partnerships and exports
Improved internal processes and staff accountability
Less downtime due to cyber incidents
All of this ultimately means increased sales, fewer issues, and long-term growth.
How Maxicert Bahrain Can Help
Maxicert provides ISO 27001 consultation and certification services specialized for the e-commerce and digital sectors in Bahrain.
We assist you from initial to final with:
Risk-based gap analysis
Tailor-made policies and documentation
Employee training specific for online businesses
ISMS implementation and sensitization
Co-ordination with Bahrain-approved certifying bodies
Irrespective of whether you're starting a new e-commerce portal or enhancing an existing portal, we make the process of certification easy and cost-effective.
Conclusion:
Bahrain's online marketplace is speedy, intelligent, and full of promise. But it's also constantly at risk from cyber threats and increasing compliance requirements.
ISO 27001 is more than a badge — it's your security play book.
It assists you in establishing a safe, trusted online business that expands without fear. Whether you sell garments, electronics, or services — ISO 27001 is the message that you care about your customers, your brand, and your future.
Frequently Asked Questions (FAQ)
Q1: Is ISO 27001 compulsory for online stores in Bahrain? Not yet, but it's strongly advised — particularly if you process customer information or provide payment services.
Q2: Can small e-commerce companies get ISO 27001? Yes. The system can be scaled to fit your size and scope. Even two-man start-ups can take advantage.
Q3: How long does certification take? Usually 2 to 4 months, depending on your preparedness and team size.
Q4: Is ISO 27001 superior to simply employing cybersecurity software? Yes — because it addresses people, processes, and policies, not solely tech tools.
Q5: Does ISO 27001 assist with GDPR compliance? Definitely. It lays down a framework for privacy protection, breach notification, and data subject rights — which assists with both local and overseas privacy.
0 notes