#What is bitlocker recovery ?
Explore tagged Tumblr posts
Text
For those who are not aware: Bitlocker is encryption software, it encrypts your computer and makes it impossible to access the information on the computer unless you have the key.
It should be standard practice for IT companies to document the bitlocker keys as they are configuring bitlocker on a computer; generally you would do this by creating a record in your client management software for that specific device and putting the key in the record. Sometimes software can be used to extract that information in the event that it's necessary, but even if there's theoretically a way to extract the key, it should be documented somewhere *other* than on the encrypted computer.
This is something that a lot of IT people fuck up on kind of a lot (we've definitely had problems with missing bitlocker keys and I'm quite happy that the people who didn't document those keys aren't my coworkers anymore).
So what do you do if you want to use encryption software and you're NOT an IT company using a remote management tool that might be able to snag the keys?
When you are setting up encryption, put the encryption key in your password manager. Put it in your password manager. Document the important information that you cannot lose in your password manager. Your password manager is a good place to keep important things like your device encryption key, which you do not want lost or stolen. (If you run your password manager locally on an encrypted computer, export the data every once in a while, save it as an encrypted file, and put the file on your backup drive; you are going to have a bad time if your computer that hosts the only copies of your passwords shits the bed so *make a backup*)
This is my tip for home users for any kind of important recovery codes or software product keys: Print out the key and put it in your underwear drawer. Keep it there with your backup drive. That way you've got your important (small) computer shit in one place that is NOT your computer and is not likely to get shifted around and lost (the way that papers in desks often get shifted around and lost).
2K notes
·
View notes
Text
Installing Linux (Mint) as a Non-Techy Person
I've wanted Linux for various reasons since college. I tried it once when I no longer had to worry about having specific programs for school, but it did not go well. It was a dedicated PC that was, I believe, poorly made. Anyway.
In the process of deGoogling and deWindows365'ing, I started to think about Linux again. Here is my experience.
Pre-Work: Take Stock
List out the programs you use regularly and those you need. Look up whether or not they work on Linux. For those that don't, look up alternatives.
If the alternative works on Windows/Mac, try it out first.
Make sure you have your files backed up somewhere.
Also, pick up a 5GB minimum USB drive.
Oh and make a system restore point (look it up in your Start menu) and back-up your files.
Step One: Choose a Distro
Dear god do Linux people like to talk about distros. Basically, from what all I've read, if you don't want to fuss a lot with your OS, you've got two options: Ubuntu and Linux Mint. Ubuntu is better known and run by a company called Canonical. Linux Mint is run by a small team and paid for via donations.
I chose Linux Mint. Some of the stuff I read about Ubuntu reminded me too much of my reasons for wanting to leave Windows, basically. Did I second-guess this a half-dozen times? Yes, yes I did.
The rest of this is true for Linux Mint Cinnamon only.
Step Two: Make your Flash Drive
Linux Mint has great instructions. For the most part they work.
Start here:
The trickiest part of creating the flash drive is verifying and authenticating it.
On the same page that you download the Linux .iso file there are two links. Right click+save as both of those files to your computer. I saved them and the .iso file all to my Downloads folder.
Then, once you get to the 'Verify your ISO image' page in their guide and you're on Windows like me, skip down to this link about verifying on Windows.
Once it is verified, you can go back to the Linux Mint guide. They'll direct you to download Etchr and use that to create your flash drive.
If this step is too tricky, then please reconsider Linux. Subsequent steps are both easier and trickier.
Step Three: Restart from your Flash Drive
This is the step where I nearly gave up. The guide is still great, except it doesn't mention certain security features that make installing Linux Mint impossible without extra steps.
(1) Look up your Bitlocker recovery key and have it handy.
I don't know if you'll need it like I did (I did not turn off Bitlocker at first), but better to be safe.
(2) Turn off Bitlocker.
(3) Restart. When on the title screen, press your Bios key. There might be more than one. On a Lenovo, pressing F1 several times gets you to the relevant menu. This is not the menu you'll need to install, though. Turn off "Secure Boot."
(4) Restart. This time press F12 (on a Lenovo). The HDD option, iirc, is your USB. Look it up on your phone to be sure.
Now you can return to the Linux Mint instructions.
Figuring this out via trial-and-error was not fun.
Step Four: Install Mint
Just follow the prompts. I chose to do the dual boot.
You will have to click through some scary messages about irrevocable changes. This is your last chance to change your mind.
I chose the dual boot because I may not have anticipated everything I'll need from Windows. My goal is to work primarily in Linux. Then, in a few months, if it is working, I'll look up the steps for making my machine Linux only.
Some Notes on Linux Mint
Some of the minor things I looked up ahead of time and other miscellany:
(1) HP Printers supposedly play nice with Linux. I have not tested this yet.
(2) Linux Mint can easily access your Windows files. I've read that this does not go both ways. I've not tested it yet.
(3) You can move the taskbar (panel in LM) to the left side of your screen.
(4) You are going to have to download your key programs again.
(5) The LM software manager has most programs, but not all. Some you'll have to download from websites. Follow instructions. If a file leads to a scary wall of strange text, close it and just do the Terminal instructions instead.
(6) The software manager also has fonts. I was able to get Fanwood (my favorite serif) and JetBrains (my favorite mono) easily.
In the end, be prepared for something to go wrong. Just trust that you are not the first person to ever experience the issue and look it up. If that doesn't help, you can always ask. The forums and reddit community both look active.
178 notes
·
View notes
Text
2024 CrowdStrike Incident
I just wanted to document my day today. Since I feel this is a pretty major historical event in the history of computing.
From my understanding, the update that CrowdStrike pushed occurred last night, but I wasn't made aware of it until this morning.
I heard the notification for Microsoft Teams go off on my work phone a couple of times while I was still in bed. I decided not to answer right away since employees are supposed to call me directly if there's a production issue. However, around 5:30 this morning, I got a call from one of my team leads telling me that a CrowdStrike update got pushed earlier that has now "BitLockered" a bunch of computers.
For context, my team uses the term "BitLockered" for any time a computer crashes and requires the BitLocker encryption key to recover.
In any case, I was asked if I could run over to our local distribution center right away to start mitigating the damage. I immediately got up, got dressed, grabbed my work laptop and bag and left. I skipped my morning coffee and shower so I could get there ASAP.
When I finally managed to get inside the building, I started taking a look around the front office and saw several computers stuck on the Windows Recovery Mode screen. Already starting to look like a bad sign. I started booting up my work laptop, which I thankfully did not leave turned over overnight, and headed upstairs to a bank of production computers. As soon as I got up there, I saw a sea of Windows Recovery Mode screens.
By this point my Microsoft Teams notifications started going off non-stop, and I started running the recommended fix on one of the computers. Basically I was trying to make sure I understood how to perform the fix. At this point, it became apparent we were going to have to touch every endpoint in our network at every facility.
Around 6:00AM, I got a call from a manager from a separate facility asking me about what was going on. This is someone that's constantly just called me instead of submitting a help desk ticket, and I've tried to be patient with. Today I had to be a bit more blunt and state that I couldn't drop what I was doing to come over and help, but that someone would be there later today to assist. This manager continued to try and call me throughout the day, but I had to keep telling him that I was not going to be available all day.
Around 6:30AM one of my co-workers made it to the distribution center to help. I ran the fix on his laptop and we started working to fix each computer one by one. A bit later I noticed my mom texted me that she heard about this in the news. So I looked up "CrowdStrike" on Google and found that not only were we affected by it, but many other major companies were.
As we started getting workstations back online, it became apparent that was only going to be half the battle, as this issue caused most of our servers to crash as well. But at this point, we figured it would be best to continue to get as many workstations back up and running one by one. But because the servers were down, I kept getting asked if I could restore a connection, which unfortunately we couldn't do until the server team could run the fixes on our servers.
Eventually I was asked to join a Zoom call so I could start providing other facilities with BitLocker keys so they could start running the fix on their own computers. Some machines we determined could be fixed by reverting to a restore point. Others we had find a way to manually remove the "C-00000291*.sys* file by booting the computer into Safe Mode with Networking. Those devices ended up costing us a bunch of time to get back up and running.
By the time 5:00PM rolled around, I asked if I could go home and continue to work from there. So I took the opportunity to go home, get myself cleaned up, and continue to work. By 8:30PM it seemed that things had died down to the point we could stop for the day. I'm sure we've got a few machines we still need to apply the fix to, but we managed to get our core business back up and running within the matter of a few hours.
So yeah, long story. But I just felt like documenting it, given that this is an event that's probably going to be pretty well remembered in the history books.
157 notes
·
View notes
Text
Awesome.
I turned on my laptop this morning to do my passport renewal, and it asks me for my Bitlocker Recovery Key.
Cool. That's fine. Probably did a firmware update so put it in.
Goes to a BSOD, says it will do an automatic repair, reboots.
STRAIGHT BACK INTO THE RECOVERY KEY SECTION!
Welp. Looks like I get to fix my laptop this week.
Just what I love doing with my copious amounts of free time.
2 notes
·
View notes
Text
I'd like to point out that even for "tech savvy" people, technology is becoming more and more inaccessible. Trying to navigate all the pre-installed bloatware to find what's necessary and what isn't is becoming nigh impossible for the average person, and googling it doesn't always help.
My laptop from 2016 died and I needed a new one. Tell me why of the 1TB of storage it has, about 150GB were taken up upon first start-up? And when you open control panel [which, not everyone even knows what that is anymore] to delete the bloatware, it doesn't show anything that takes up that much space.
Knowing how to make a clean install of windows isn't something most people know how to do, and even people who are at least slightly technologically aware, might be wary of messing with Windows for warranty/Windows key reasons or what not. The more predatory technology becomes, the more difficult it becomes even for people who try to stay on top of it. "Yeah, I can look up how to do it, and understand what it says, but there are so many ways it could go wrong, and I can't afford another device" is an absolutely valid fear, and if even someone who does know what the tech lingo means is unwilling to mess with it, how can the average user?
[No, I don't want to hear how it's easy because you can do it through an ISO, or because it's only the first install that can't be clean and afterwards the key is bound to your Microsoft account. The average, kinda-sorta-maybe tech literate person won't touch that because tech is expensive and not everyone can try it out on an old laptop that doesn't work anymore to make sure they know wtf they're doing. So they'll remove what they can, sigh, and live with the rest.]
My dad's laptop recently threw a BIOS error and loaded up with the requirement for a BitLocker key. His laptop, in fact, most peoples laptops, have no need for that kind of security, and most people won't know that their computer has it activated until it throws an error. If the error hadn't occurred while I was there, there is no way in hell he could have figured out how to find the key, because he wasn't even aware this key exists. I wasn't even aware my laptop had BitLocker activated until his showed that error, because its either not mentioned anywhere, or hidden in the multi-page agreements that you need to accept before being allowed access to "your" device.
And guess what? If this reaches anyone, somewhere out there is someone who considers themselves "tech savvy", who has just found out their new device has BitLocker activated, and they're trying to figure out how to find the BitLocker key because no one told them this exists or that they may want to know how to find it. (Go to aka.ms/myrecoverykey, sign in to the Microsoft account linked to the device, look for the key that corresponds to the first 8 letters/numbers of the Recovery key ID on the device)
And if you followed one of those helpful guides on how to force a local account onto your lovely new win11 device? I hope you also went and found a lovely guide on how to find your BitLocker key/how to de-encrypt your device, cuz guess what? You see that blue screen and your files are gone. (Well, there are ways around it but again, they're not exactly the easiest of methods, definitely not something the average user could manage)
Sure, it's a safety feature, but it's unnecessary for most and should be an opt-in, not a "find out when shit hits the fan"
The more predatory technology becomes, the harder it becomes to be technologically literate.
I was lucky, my first proper device was a Windows 7 that required some tech literacy but was for the most part user friendly, I didn't love the switch to Windows 10 because it became harder to to find the more complex settings, but I learned most of my tech skills on it, moving to Windows 11 and seeing the "simplified, user friendly, easy setup" interface that makes accessing things harder and actively hides settings from the user? It still grates my nerves. I still have issues with the audio settings of all things because for some stupid reason apps set to 0 still produce noise and the slider moves up by 1-5 points automatically. I've pinned the windows 10 volume mixer to my windows 11 devices task bar because I cannot tolerate the windows 11 one and its bs.
Technology becoming "user friendly and easy to navigate" has, in a lot of cases, actually made it harder to understand. I did not get taught what I know about technology at school. I learnt it on my own, because I grew up with tech that still allowed it.
Yes, schools should still be teaching the basics of technology, but at some point we need to realise that technology has become much more inaccessible too.
And that's only the software side of things. Why does all of my laptops RAM come soldered now? Why does opening my device up to clean it void the warranty? Why does the number of ports keep decreasing?
Anyway, this has gotten longer than I wanted, so I'm going to say this one more time and end it there.
Technology has become easier to use on the surface and harder to understand beyond that. Users are being kept away from "settings they may not understand", and it makes it significantly harder to learn as a result.
Me: oh yeah, if you think school photography is hard now, try imagining doing this with film.
The new girl: what's film?
Me: ... film. Like... film that goes in a film camera.
New girl: what's that mean?
Me: ... before cameras were digital.
New girl: how did you do it before digital?
Me:... with film? I haven't had enough coffee for this conversation
114K notes
·
View notes
Text
Maximize Your Control with Dedicated Windows Servers
When it comes to web hosting and managing digital resources, the need for control, reliability, and high performance is non-negotiable. This is where Dedicated Windows Servers step in, offering a premium solution for businesses, developers, and enterprises looking to elevate their web presence. Unlike shared hosting or virtual private servers (VPS), dedicated servers provide an exclusive environment, giving you full control over your resources and software configurations.
In this blog, we'll explore the benefits and reasons why dedicated Windows servers are the ideal choice for those seeking maximum control over their hosting environment.
What is a Dedicated Windows Server?
A Dedicated Windows Server refers to a physical server that is entirely dedicated to a single user or organization. This means that you don’t share resources like CPU, RAM, or bandwidth with other clients. Powered by the Windows operating system, these servers support a variety of enterprise-level applications, including SQL Server, Active Directory, and custom web hosting environments.
The Windows environment is known for its user-friendly interface and wide support for software, making it an excellent choice for businesses that rely on Microsoft-based applications and require a stable, familiar platform.
1. Full Control Over Your Server
One of the most significant advantages of using a dedicated Windows server is complete control. As the sole user of the server, you have administrative access to the entire machine. This means you can install and configure any software, change system settings, and implement custom solutions according to your needs.
With root access to the operating system, you can:
Install and update software without restrictions.
Set up complex configurations to meet business requirements.
Ensure maximum security by controlling firewall settings and access permissions.
Install custom scripts and tools that may not be available in shared hosting environments.
This level of flexibility is essential for businesses with specific software needs or those operating resource-intensive applications.
2. Enhanced Performance and Reliability
With a dedicated Windows server, performance is vastly improved compared to shared hosting or VPS. Since you're the only user, the server's resources are allocated entirely to your applications and websites, ensuring faster load times and better overall performance.
Key performance benefits include:
No Resource Sharing: Unlike shared hosting, where multiple users share the same server, a dedicated server's resources are all yours.
Better Uptime: Since the server is dedicated to your use, there's less likelihood of experiencing downtime caused by the actions of other users.
Scalability: Dedicated servers can be easily upgraded to accommodate growing needs, whether that involves adding more RAM, storage, or processing power.
This reliability is crucial for businesses that require constant uptime, such as e-commerce stores, large websites, and enterprise applications.
3. Improved Security and Customization
Security is one of the most critical factors for any business operating online. With a dedicated Windows server, you can take control of your security measures and implement custom security protocols. Unlike shared hosting, where security depends on the actions of other users, a dedicated server offers isolated resources, reducing the risk of cyber-attacks and data breaches.
You can customize security settings by:
Installing and configuring your own firewalls.
Using Windows Security features such as BitLocker and Windows Defender.
Creating isolated environments with virtual machines (VMs).
Enabling regular backups and disaster recovery plans.
Implementing SSL certificates for secure transactions.
These customizable options allow you to create a robust security framework suited to your business’s specific needs.
4. Dedicated Support and Expert Assistance
When you opt for a dedicated Windows server, you're not just paying for the hardware and software – you're also getting access to expert technical support. Most hosting providers offer 24/7 support with dedicated teams that understand the intricacies of Windows servers.
This means:
Quick Resolution of Issues: Any technical difficulties or issues are resolved faster with a team that understands your specific setup.
Proactive Monitoring: Many providers offer proactive server monitoring services to identify potential issues before they impact your operations.
Consultation and Optimization: Dedicated support staff can guide you through system optimization and help you get the most out of your server.
This hands-on support ensures you can maintain your server's performance, security, and stability with ease.
5. Cost-Effective for Large Operations
Although dedicated Windows servers are generally more expensive than shared hosting or VPS options, they can be incredibly cost-effective for larger operations or businesses with high resource demands. By consolidating multiple applications, websites, and services onto a single dedicated server, you can save money on multiple hosting solutions.
Additionally, with full control over your server, you can optimize costs by adjusting the configuration to your precise needs, avoiding unnecessary expenses for resources you don’t use.
Conclusion
A Dedicated Windows Server offers unmatched control, performance, and security, making it the ideal choice for businesses that require a customized, scalable, and reliable hosting environment. Whether you’re running mission-critical applications, handling sensitive data, or operating large-scale websites, the flexibility and power provided by a dedicated server can take your business to the next level.
If you’re ready to maximize your control and optimize your online presence, consider upgrading to a dedicated Windows server today. With the right configuration and support, you’ll experience an enhanced digital experience that positions your business for long-term success.
0 notes
Text
Improve The Dell Management Portal With Microsoft Intune

Boost Microsoft Intune’s Management Capabilities for Dell PCs. Find out how IT managers can minimize complexity, save time, and maximize resources using the Dell Management Portal.
Dell Management
Keeping an inventory of PCs across several locations, OEMs, and management software may be a challenging chore, especially with the growing complexity of the IT environment and evolving needs. IT managers often have to juggle a number of tools and procedures in order to keep control over the business. Let me introduce you to the Dell Management Portal, a cutting-edge tool that makes managing Dell client devices with Microsoft Intune easier. For IT managers, this cloud-based tool seeks to minimize complexity, save time, and maximize resources.
- Advertisement -
What is the Dell Management Portal?
The online Dell Management Portal helps IT administrators and enterprises manage, monitor, and support Dell hardware and software solutions. Dell network equipment, servers, storage systems, laptops, and desktops may be managed from one interface.
Features
The Dell Management Portal‘s salient characteristics comprise:
Device Monitoring: Keep an eye on the functionality, state, and health of your Dell devices in real time.
Updates for Firmware and Software: Make it easier to update drivers, system software, and firmware on various Dell devices.
Enable remote diagnostics, system setting, and troubleshooting from any location with remote management.
Automation Tools: Automate regular IT chores like as patch management, compliance checks, and backups.
Analytics and Reporting: Get access to thorough reports and insights on use patterns, system alarms, and hardware performance.
The gateway makes it simpler for businesses to manage large fleets of Dell devices by streamlining IT operations, decreasing downtime, and enhancing security.
The Dell Management Portal: What Sets It Apart?
Tools for Integrated Management
IT administrators may face serious difficulties as a result of different end user client device management programs not communicating with one another. This is made easier by the Dell Management Portal, which links Microsoft Intune and Dell PC Management Solutions to create an integrated ecosystem that improves control and reduces the amount of human labor needed.
Cloud-Based Adaptability
The cloud-based flexibility, ease of use, and forward-thinking benefits that contemporary IT settings need are provided with the Dell Management Portal. Workflows are streamlined by this connection, which also gives you more visibility and control over your Dell devices.
- Advertisement -
Entire Device Administration
It’s never been easier to manage Dell computers. IT administrators may get both the prior and current BIOS passwords as well as the BitLocker recovery keys using the Dell Management Portal. These are essential for maintenance procedures. Dell commercial devices from both the previous and current generations are compatible with this capability.
Management of Applications
IT managers may now manage assignments from inside Microsoft Intune and publish Dell corporate apps to their Intune environment via the Dell Management Portal. All programs are kept current and correctly allocated to the proper device groups thanks to this seamless interaction.
The functioning of the Dell Management Portal
Open a browser or Microsoft Intune first
IT managers will have the option to access the Dell Management Portal directly from a contemporary browser like Microsoft Edge, Mozilla Firefox, or Google Chrome, or via the Microsoft Intune Partner Portal (which will arrive in late September or early October). Just go to manage.dell.com.
Log in to the Dell Management Portal
A Tenant Global Administrator must first start the portal, log in using Entra credentials, and then accept the required rights via the Microsoft Authentication dialog box. Taking this step guarantees safe access to the Dell Management Portal‘s management features.
Take Control of Your Dell Software and Hardware
After connecting, IT managers have access to comprehensive end-user client device data, enabling them to manage Dell PCs. On Dell-managed PCs, they may examine both the most recent and older BIOS passwords as well as the BitLocker recovery keys.
Make Applications Public and Assign Them
Viewing the available Dell corporate apps, together with their descriptions, supported operating systems, and languages, is accessible to IT managers. The selected version of an application is instantly published to Microsoft Intune when you click “publish now.” The program may then be assigned by administrators to certain user or device groups, with the option to remove, require installation, or make it accessible.
The Dell Management Portal’s Advantages
Efficiency of Time and Resources
The Dell Management Portal facilitates easy Dell PC Management by allowing a smooth interface to Microsoft Intune. With only a few clicks, key apps may be loaded into Microsoft Intune for deployment. Accessing device information is simpler. This facilitates IT administrators’ access to important data.
Improved Control and Visibility
One consolidated view of all Dell devices controlled by Microsoft Intune is offered via the Dell Management Portal. IT managers may now access critical device information more quickly thanks to the improved visibility and management.
Enhanced Safety and Adherence
The BitLocker recovery key management and BIOS password retrieval functions of the Dell Management Portal improve security and compliance. IT managers can quickly get vital security data, guaranteeing that devices stay safe and adhere to company regulations.
Practical Uses
IT managers may benefit from the features that the Dell Management Portal provides, which range from installing drivers and setting up BIOS to keeping an eye on devices and controlling updates. It offers the features and tools required to guarantee the best possible device performance and efficiency, regardless of the size of your organization or fleet of devices.
In Summary
When used with Microsoft Intune, the Dell Management Portal is an extremely potent tool that enhances the management potential of Dell PCs. By providing complete device management, cloud-based flexibility, integrated management tools, and seamless application administration, it tackles the main issues encountered by IT administrators and offers a foundation for ongoing development within a well-known global ecosystem.
Read more on govindhtech.com
#DellManagementPortal#MicrosoftIntune#DellPC#Dellclientdevices#systemsoftware#cloud#dell#currentBIOS#GoogleChrome#Microsoft#pc#ManagementPortal#Hardware#Software#news#technology#technews#govindhtech
0 notes
Text
Force BitLocker Recovery: Perform BitLocker Recovery via the Self-Service Portal and Helpdesk
BitLocker recovery is the process in which access to a BitLocker-protected drive is restored in the event the drive doesn’t unlock using its default unlock mechanism. In this article, we shall discuss “Force BitLocker recovery: Perform BitLocker Recovery via the Self-Service Portal and Helpdesk”. Please see Perform BitLocker Recovery Password Rotation in Active Directory, what are the Reasons for…
#Bitlocker#Force BitLocker Recovery#HelpDesk Portal#MBAM#MBAM for Bitlocker Administration#Microsoft Windows#Perform BitLocker Recovery#Self-Service Portal#Windows#Windows 10#Windows 11#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2022#Windows Server 2025
0 notes
Text
If you have Windows 11 on your computer, drop what you're doing, back up your data and see if your Microsoft account has your BitLocker recovery key. NOW.
I will leave the reason why I'm issuing this advice as an exercise for the reader, though suffice it to say I am enraged.
1 note
·
View note
Text
at my old work, each employee was tasked with storing their own bitlocker encryption key this would have been no issue except from there only being one place that we were allowed to store it in and that was a password protected excel spreadsheet on sharepoint
the issue that occurred isn't the first one that would pop into most peoples minds - being that the password was lost and thus all bitlocker keys were lost, no the issue was a little simpler than that the spreadsheed, due to everyone needing to post their own keys to it, was editable by everyone in the company
I put my key in next to the serial number and recovery key ID for my laptop same as everyone else
my laptop bitlockered for whatever reason
I get one of my colleagues to open up the spreadsheet to get the key
someone at some point overwrote every key in the excel spreadsheet with their own key
"no problem at all" you may say "as sharepoint offers previous versions of documents, you could just restore an older version and get your key from that"
for what ever reason the only previous version of that document that had any key other than the one that had replaced every key in the spreadsheet was when it was first created -_-
we didn't have network storage to save files so the desktop was all I had and it was all gone - scripts, useful tidbits of information, etc all wiped forever
some was recoverable because I emailed a bunch to people because it was useful to have, but yeah
#and that's my bitlocker story in case people are sharing theirs#my current work doesn't have this issue as they programmatically store each one in a database when the computers get imaged#oh yeah my old work didn't image computers#they just bought them wherever was selling them cheapest and used whatever os they came with#they were a managed service provider#yeah#bitlocker
1 note
·
View note
Text
CrowdStrike has a new guidance hub for dealing with the Windows outage
Image: The Verge CrowdStrike has published a new “Remediation and Guidance Hub” that collects details related to its faulty update that crashed 8.5 million Windows computers across the globe on Friday. The page includes technical information on what caused the outage, what systems are affected, and CEO George Kurtz’s statement. It contains links to Bitlocker key recovery processes and to various…
0 notes
Text
CrowdStrike'd and BitLocker'd
With yesterday's CrowdStrike outage. I'm sure a number of you are probably wondering "what does BitLocker have to do with any of this?" Well, it all has to do with an added layer of security many organizations use to keep data from being stolen if a computers ends up in the hands of an "unauthorized user."
To start, let me briefly explain what the CrowdStrike driver issue did and what the fix for it is.
After the update was automatically installed to computers running the CrowdStrike Falcon Sensor, a faulty driver file caused the Windows kernel on those computers to crash and display a Blue Screen of Death. How Windows typically handles a crash like this is to create a crash log file, then perform a reboot. Since this driver would launch shortly after Windows finished booting, it would cause the operating system to crash and reboot again. When two crashes have occurred in sequence, Windows will automatically boot into Recovery Mode. Hence why we say several pictures of the Recovery Mode screen across social media yesterday.

Unfortunately, this update was automatically pushed out to around 8.5 million computers across several organizations, causing widespread chaos within the matter of a few hours. And the fix for this issue had to be performed by physically accessing each computer, which required those of us working in I.T. to have to run around several facilities, locate each affected computer, and apply the fix one by one.
The short and simple of the fix is either one of two options. You can either use the Recovery Mode that Windows was already booted into to navigate to Start-Up Setting, and launch Safe Mode. Once Windows boots into Safe Mode, the technician can navigate to C:\Windows\System32\Drivers\CrowdStrike, and delete the file C00000291-*.sys. After that the computer can be rebooted as normal, and the crashing will stop.
Or the technician can open System Restore from Recovery Mode. And, assuming there is a recovery point, restore the computer back to a good known working state.
Now, this may all seem simple enough. So why were so many organizations having trouble running this fix? That all has to do with BitLocker. As an added security measure, many organizations use BitLocker on their computers to perform a full hard disk encryption. This is done so that if a computer ends up being lost or stolen, and ends up in the hands of an "unauthorized user" they will not be able to access any of the data stored on the computer without a password to log into the computer, or the computer's BitLocker recovery key.
This presented a problem when trying to restore all of these affected computers, because when either trying to launch Safe Mode or System Restore, the user would be prompted for the BitLocker recovery key.
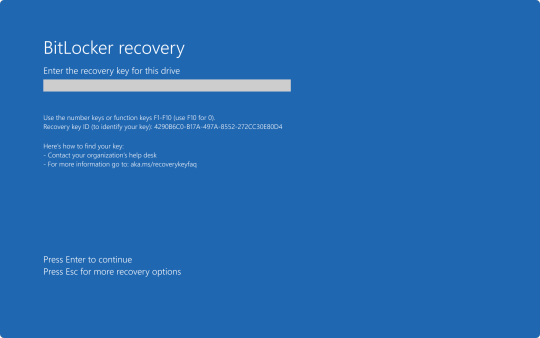
In my organization's case, we found we could save time by providing our end user the steps to perform one of the two fixes on their own to save time. But the problem we still continue to run into is the need for these BitLocker recovery keys. In my case, I've been fielding several calls where I've had end users walking from one computer to another while I provide them with the key as they walk through reverting back to a previous restore point.
Again, a pretty long story, but hopefully that can provide some context as to what's been happening over the past 48 hours.
30 notes
·
View notes
Text
Understanding the BitLocker Recovery Key: What It Is and How to Use It

Hey Tumblr friends! 🌟
If you've recently enabled BitLocker on your Windows device and suddenly find yourself staring at a prompt asking for a BitLocker recovery key, you might be wondering what this mysterious key is all about. Let’s dive into the essentials of the BitLocker recovery key, why you might need it, and how to find it when necessary.
What is a BitLocker Recovery Key?
A BitLocker recovery key is a 48-digit numerical password that acts as a backup method to unlock your encrypted drive. This key is generated when you first enable BitLocker on a drive and is crucial for situations where you can’t access your drive through the usual means.
Why Might You Need a BitLocker Recovery Key?
There are several reasons why you might be prompted to enter your BitLocker recovery key:
Forgotten Password: If you forget your BitLocker password, the recovery key is your only way to regain access.
Hardware Changes: Making significant changes to your computer’s hardware, like replacing the motherboard, can trigger the recovery key prompt.
Software Updates: Major updates to your operating system or BIOS might require you to enter the recovery key.
Security Concerns: If BitLocker detects potential security threats or unauthorized access attempts, it will ask for the recovery key.
Where to Find Your BitLocker Recovery Key
If you’re in a pinch and need to find your BitLocker recovery key, here are some common places to check:
Microsoft Account: If you linked BitLocker to your Microsoft account, you can find your key on the Microsoft BitLocker recovery key portal.
USB Drive: If you saved the recovery key to a USB drive, make sure to keep it somewhere safe and accessible.
Printout: Some folks print their recovery key and store it securely.
Azure Active Directory (AAD): If your device is connected to an organization’s AAD, your IT department might have a copy.
File: If you saved the recovery key as a file, it’s usually named something like BitLocker Recovery Key.txt.
What to Do if You Can’t Find Your Recovery Key
If you can’t locate your BitLocker recovery key, your options are unfortunately limited. Without the recovery key, accessing your encrypted data is not possible. This is a vital reminder to store your recovery key securely in multiple locations.
Best Practices for Managing Your BitLocker Recovery Key
Store Multiple Copies: Keep your recovery key in several places, such as your Microsoft account, a USB drive, a printout, and a secure digital file.
Secure Storage: Ensure your recovery key is stored in a safe location, like a safe or encrypted digital storage.
Keep Updated: Regularly update your recovery key and ensure it’s accessible, especially after significant system changes.
By following these best practices, you can avoid the potential frustration and data loss associated with being locked out of your BitLocker-encrypted drive.
For a more detailed guide on BitLocker and managing recovery keys, including step-by-step instructions and troubleshooting tips, check out this Comprehensive BitLocker Recovery Key Guide.
Hope this helps you stay secure and stress-free! If you have any more questions about BitLocker or need further assistance, feel free to drop a comment. 💬✨
Also read our related articals:
How Ad Blockers Might Trigger BSOD Blue Screen
Audio Troubleshooter: Resolve No Sound Issues On Dell Laptop
Laptop Not Connecting To WiFi? Fix Laptop WiFi Issues Today!
How To Fix ‘No Sound’ Issues On Your Laptop Or PC: A Comprehensive Guide
1 note
·
View note
Text
Fediverse thread, for anyone who wants reliable updates from someone who knows exactly what they're talking about and doesn't mind a bit of tech jargon or occasional wisecracking in the middle of the discussion
my own summary goes like so:
There were two separate incidents, one much worse than the other.
First Microsoft did a minor fucky upsy that caused a network outage in a bunch of the "Azure" brand data centers they manage.
This didn't take very long to fix.
It's only relevant because that CNN link makes it sound like the big problem is Microsoft's fault which is only true insofar as all the computers affected by the big problem run Windows and Microsoft has made design choices that make it impossible to automate recovery from the big problem.
The big problem is that, shortly after the Azure outage, Crowdstrike, which is an antivirus company, pushed a bad update to their virus definitions or something.
Nobody outside the company is sure what the file in question is supposed to do because its actual contents are total nonsense.
Crowdstrike is apparently the antivirus of choice for giant corporations all over the world that run their servers on Windows.
The bad update is really really bad.
How bad?
Well, just loading it onto a computer will make that computer crash. Immediately.
But it gets worse.
The computer will try to load it agaIn when it reboots.
And crash again.
Repeat forever.
They pushed this bad update to all their customers, all at once.
To fix it you have to boot the computer into Recovery Mode and delete the bad update by hand.
If the computer had BitLocker enabled you need the BitLocker recovery key to do this; the regular password won't work.
Official advice for what to do if you don't have the BitLocker recovery key is to keep rebooting the computer over and over again and hope that on one of the cycles it'll manage to download another Crowdstrike definitions update before crashing.
Baffled I haven't seen anyone talking about the crowdstrike thing on my dash. Maybe I need to follow more tech nerds.
6K notes
·
View notes
Text
Download iMyFone AnyRecover 5.3.1.15 Full Free Activated
May 17, 2024
iMyFone AnyRecover Crack + License Key {Latest}
iMyFone AnyRecover data recovery software Full Version helps you to recover emails, videos, documents, images and a variety of other data with its clever and superficial features.it is a best and easy Software developed to help users to recover lost or deleted files from a variety of storage systems. It supports recovery from hard drives, memory cards, USB flash drives, and other digital storage mediums. AnyRecover can be particularly useful in situations where data has been lost due to accidental deletion, formatting, device corruption, or computer virus attacks.
Additionally, iMyFone AnyRecover Activation Key can recover your valuable data from Windows, Mac (M1, M2 supported), SSD, external drive, camera, drone, dashcam, camcorder, video, music player, hard drive, USB, SD cards, etc. Overall, iMyFone AnyRecover 4.5.0 cracked is aims to provide a reliable solution for data recovery needs across various operating systems, including Windows and macOS. the software supports recovery from different file systems such as FAT, exFAT, NTFS, and more.
You Can Also Download: Undelete 360
Key Features iMyFone AnyRecover:
iMyFone AnyRecover data recovery Free Download software recover delete or lost data from iOS device, iTunes, iCloud.
this software Recover any iOS data like photos, contacts, WhatsApp, call history, videos, app data, etc.
You can Save iOS data lost by accidental deletion, factory resetting etc.
Preview detailed iOS files (both deleted and existing files) before recovery.
It Support all iOS devices and iOS versions including iOS 17, iPhone 14 and iPhone 15.
Your best data recovery specialist for Windows, Mac, iOS and Android.
This software Restore deleted files from Recycle Bin, HDD, SSD, USB, SD card, etc.
Also, Recover deleted document, pictures, videos, emails and other files in 1 click.
In addition, It Can recover files from popular cloud storage services like Dropbox and Google Drive.
Allows pause, save, and resume of recovery sessions for flexible data restoration.
Recovers data from BitLocker-encrypted drives with decryption.
What’s New in Version iMyFone AnyRecover 8.5.5?
This release Comes with Optimizes the recovery quality, especially the data recovery of FAT/FAT32/NTFS
file systems, so more data can be recovered.
This new version Optimizes the scanning process and shortens the recovery time.
iMyFone AnyRecover Registration Code Supports to scan the partitioned disks.
Additionally, it now Support to recover data from BitLocker encrypted disks.
It now Support devices with APFS and HFS+ file systems.
This supports Window 12 and macOS 11.0.
iMyFone AnyRecover Supports the Following File Types:
Documents: PPT/PPTX, PDF, DOC/DOCX, XLS/XLSX, and more.
Graphics: JPG, PNG, GIF, TIFF, BMP, PSD, and various camera raw formats like CRW, CR2, NEF, ORF.
Videos: AVI, MOV, MP4, MKV, WMV, and other popular video formats.
Audio Files: MP3, WAV, WMA, AAC, M4A, and other common audio formats.
Emails: File types from various email clients, including PST, EMLX.
Archives: ZIP, RAR, ISO,
System Requirements:
For Windows:
Operating System: Windows 11,10, 8.1, 8, 7, XP
CPU/Processor: 1GHz (32 bit or 64 bit) or higher
RAM: 256 MB or more of RAM (1024MB Recommended)
Hard Disk Space: At least 200 MB of free space
For macOS:
Operating System: macOS 10.10 and later (up to the latest macOS)
CPU/Processor: 1GHz Intel or higher
RAM: 512 MB or more
Hard Disk Space: At least 200 MB of free space
How to Install iMyFone AnyRecover Crack Free Download?
Click the link below to begin the iMyFone AnyRecover Data recovery Crack Free Download. This is a complete offline installer standalone setup for the Windows Operating System. This would be compatible with both 32 and 64-bit Windows.
0 notes
Text
How to introduce and actuate BitLocker on my gadget?
In the domain of network safety, safeguarding delicate information has become fundamental. BitLocker, a powerful encryption instrument created by Microsoft, fills in as a defend against unapproved admittance to your gadget and guarantees the classification of your information. In this thorough aide, we will walk you through the bit by bit course of introducing and enacting BitLocker on your gadget, normally alluded to as aka.ms/yourpc.
I. Figuring out BitLocker:
Prior to digging into the establishment cycle, it's critical to comprehend what BitLocker is and why it's a fundamental apparatus for getting your information. BitLocker is a full-plate encryption highlight included with Microsoft Windows working frameworks aka ms yourpc. It scrambles the whole plate to safeguard the information put away on it from unapproved access.
II. Framework Prerequisites:
Prior to continuing with the establishment, guarantee that your gadget meets the essential framework necessities. BitLocker is available on Windows 10 Pro, Enterprise, and Education editions, among others. Moreover, your gadget ought to have a Confided in Stage Module (TPM) rendition 1.2 or later for improved security.
III. Bit by bit Establishment Guide:
Presently, we should go through the bit by bit course of introducing BitLocker on your gadget.
Getting to the BitLocker Setup:
Open the Beginning menu and select "Settings."
Explore to "Update and Security" and snap on "Gadget encryption."
Really take a look at BitLocker Similarity:
Guarantee that your gadget meets the important prerequisites for BitLocker encryption.
Check to see if your device supports TPM versions earlier than 1.2.
Activate TPM (if required):
In the event that your gadget's TPM isn't empowered, access the Profiles/UEFI aka ms mfasetup firmware settings during the framework boot.
Enable the TPM settings wherever you find them. After making changes, exit.
Make use of BitLocker:
Get back to the "Gadget encryption" segment in the "Update and Security" settings.
On the off chance that your gadget is qualified, you'll track down the choice to "Turn on BitLocker." Click on it to start the establishment interaction.
Pick Encryption Technique:
Select by the same token "TPM as it were" or "TPM and PIN" in light of your inclination and security necessities.
Pick a Method for Unlocking Your Drive:
Choose whether to utilize a secret key, a savvy card, or both to open your drive.
Take a Backup of Your Recovery Key:
Save your BitLocker recuperation key in a solid area. In the event that you forget your password or run into other problems, you will need this key to unlock your drive.
Pick Encryption Mode:
Select the encryption mode - by the same token "Scramble utilized plate space as it were" or "Encode whole drive." The last option gives more complete assurance.
Start the encryption procedure:
To begin the BitLocker encryption process, select "Start encrypting" and then "Next."
IV. BitLocker activation with MS YourPC:
Since you have effectively introduced BitLocker, how about we investigate how to initiate it utilizing Otherwise known as MS YourPC.
Getting into AKA MS YourPC:
Navigate to the AKA MS YourPC portal using your browser.
Signing In:
Use the credentials from your Microsoft account to log in.
Gadget Approval:
Find the part for BitLocker gadget approval.
Follow the on-screen prompts to interface your gadget to your Microsoft account.
Two-Element Validation (2FA):
Add an extra layer of protection by enabling two-factor authentication.
Evaluating Gadget Status:
Actually look at the Also known as MS YourPC dashboard to guarantee that your gadget is effectively connected and approved.
Far off Administration:
Exploit Otherwise known as MS YourPC's distant administration highlights for BitLocker, permitting you to screen and deal with your gadget's encryption status from the entryway.
V. Best Practices and Investigating:
To expand the viability of BitLocker and aka ms myrecoverykey, think about the accompanying accepted procedures:
Make regular backups of your BitLocker recovery key in a number of safe places.
Update your operating system and device with the most recent security patches.
Test your recuperation key to guarantee it fills in true to form.
In the event that you experience any issues, allude to the BitLocker investigating documentation given by Microsoft or look for help from Otherwise known as MS YourPC support.
Conclusion:
Getting your gadget and information is a basic part of mindful registering. By introducing and initiating BitLocker on your gadget and utilizing the capacities of Also known as MS YourPC, you can essentially upgrade the security of your delicate data. Follow the bit by bit guide gave in this article to guarantee a smooth and secure establishment process. Make sure to remain informed about the most recent security practices and updates to keep up with the honesty of your scrambled information.
0 notes