#anonymous web proxy
Explore tagged Tumblr posts
Text
Fast Secure Proxy Browser: Browse Anonymously Without Limits

Have you ever tried to access a website, only to be met with a frustrating “This content is not available in your region” message? Or perhaps you've felt uneasy knowing your online activity might be tracked or exposed on public Wi-Fi. In today’s digital landscape, where privacy breaches and content restrictions are increasingly common, it’s no surprise that more users are turning to solutions that offer both security and speed.
That’s where a fast secure proxy browser comes in. It's more than just a digital detour — it’s your shield against surveillance, a bridge to open access, and a tool that puts you back in control of your browsing experience. But what exactly makes a proxy browser both fast and secure? And how can it help you browse anonymously without limits?
In this post, we’ll break down how a fast secure proxy browser works, explore why it matters, and guide you through choosing one that fits your needs. Whether you’re looking to protect your data, bypass geo-blocks, or simply surf without compromise, you’re in the right place. Let’s dive into the tools and tactics that make anonymous browsing not just possible—but effortless.
Understanding Proxy Browsers
Proxy browsers serve as intermediaries between your device and the internet. When you access a website through a proxy browser, your request is rerouted through a remote server. This server masks your IP address, effectively hiding your identity from websites, advertisers, and even government surveillance.
A proxy browser differs from a Virtual Private Network (VPN) in a few key ways. While both hide your IP and offer privacy, VPNs typically encrypt all internet traffic on your device, while proxy browsers work at the application level—usually within the browser itself. This makes proxy browsers lighter and often faster for everyday use.
Why does speed matter? Because privacy tools shouldn't slow you down. A fast proxy browser ensures you're not waiting forever for a webpage to load, all while keeping your identity secure. It also allows seamless streaming, gaming, and general browsing without buffering or lag.
With a secure proxy browser, you no longer need to worry about malicious entities tracking your every move. Your location stays hidden, your data remains encrypted, and your browsing history is safe from third parties.
Key Benefits of a Fast Secure Proxy Browser
Maintain Online Privacy and Hide Your IP
One of the biggest advantages of a fast secure proxy browser is the ability to mask your real IP address. By doing so, your digital footprint is hidden, and your activities can't easily be traced back to you.
Bypass Geo-Restrictions and Censorship
Tired of running into blocked websites? Proxy browsers help you bypass content restrictions imposed by governments, schools, or workplaces. Whether you're accessing streaming services, social media, or news outlets, you can do so freely.
Enjoy Fast Speeds Without Compromising Security
Many users avoid privacy tools due to slow speeds. Fast secure proxy browsers, however, use optimized routing and load-balancing techniques to ensure swift connections, even under heavy traffic.
Protect Data on Public Wi-Fi Networks
Public Wi-Fi is notorious for being a security risk. With a secure proxy browser, you can encrypt your traffic and ensure your data isn’t intercepted by hackers, snoopers, or malicious hotspots.
Essential Features to Look for in a Proxy Browser
End-to-End Encryption Capabilities
Ensure that the proxy browser you choose offers end-to-end encryption. This prevents any third party, including your ISP, from reading your data.
Zero-Log and No Tracking Policies
A true privacy-focused proxy browser won’t log your activity. Check for providers that openly commit to zero-log policies.
Multiple Server Locations for Flexibility
The more server locations available, the easier it is to access global content. It also allows you to switch locations if one is underperforming.
One-Click Access and User-Friendly Interface
Ease of use matters. Look for browsers that require no technical expertise and offer clean, intuitive dashboards for users of all levels.
Use Cases: Who Needs a Fast Secure Proxy Browser?
Journalists and Researchers in Restricted Regions
For those working in countries with limited internet freedom, proxy browsers offer a vital tool for uncensored information gathering.
Everyday Users Who Value Privacy
Even if you're not a whistleblower or journalist, your data matters. Proxy browsers help safeguard everyday browsing activities.
Students Accessing Blocked Educational Resources
Educational institutions sometimes block certain sites. Proxy browsers can help students bypass these restrictions to access learning materials.
Travelers Looking to Avoid Regional Content Blocks
Traveling abroad and can’t access your favorite streaming service? A proxy browser can make it seem like you're back home, unblocking content seamlessly.
How to Get Started with a Secure Proxy Browser
Choosing the Right Tool for Your Needs
Not all proxy browsers are created equal. Look for one that balances speed, privacy, and usability based on your unique needs.
Step-by-Step Setup and Configuration
Download the proxy browser from the official website.
Install and launch the application.
Select a server or location you want to browse from.
Enable encryption settings if available.
Start browsing anonymously.
Tips for Maximizing Speed and Performance
Choose servers closer to your actual location.
Avoid peak usage times when servers may be overloaded.
Clear your browser cache regularly.
Common Mistakes to Avoid
Using free proxies with poor security protocols
Forgetting to turn on encryption settings
Overlooking privacy policies and logging practices
Conclusion
In a world where digital privacy is increasingly under threat, a fast secure proxy browser isn't just a luxury—it's a necessity. From hiding your IP address to bypassing global content barriers, it empowers you to browse anonymously, safely, and without limits.
Whether you're a professional navigating sensitive research or a casual user who values their online freedom, the right proxy browser can redefine your web experience. Choose wisely, stay informed, and take control of your digital journey. Your path to a freer, more secure internet starts now.
FAQ’s
1. What makes a proxy browser fast and secure?It combines optimized server infrastructure with encryption protocols and minimal data logging, ensuring high-speed access and strong privacy.
2. Are proxy browsers legal to use?Yes, using a proxy browser is legal in most countries. However, it's important to comply with local laws regarding internet usage.
3. Can a proxy browser replace a VPN?For basic privacy and unblocking content, yes. But for full-device encryption and enhanced security, a VPN may still be preferable.
4. Do proxy browsers work on mobile devices?Many secure proxy browsers are available for Android and iOS, offering similar features as their desktop counterparts.
5. Are free proxy browsers safe? Not always. Many free services log your data or serve ads. It’s better to choose a reputable proxy browser with a transparent privacy policy.
#secure proxy browser#anonymous web browsing#bypass internet restrictions#online privacy tools#fast proxy service
0 notes
Note
I saw one of your posts if the creepypastas or proxies darling was famous. What type of celebrity like an old childhood favorite actor/actress for example would the proxies take? Would Ticci Toby take a celebrity who is an actor or an author for instance?
I feel like Toby would want a famous darling who starred in one of his favorite rom coms or was a voice actor of sorts. But, I could also see him Kidnapping a darling that he liked when he was younger, like an actor who was around his age. If it was an actor who Toby liked when he was younger, I can see Toby watching your stuff whenever he needed comfort, because your character was hilarious, you two were roughly the same age, and you were really pretty.
I can see Tim Kidnapping a darling who is more like a neighborhood or town/city celeb. He does not want to kidnap no international, well known celeb, nah, he wants the person that everyone either wants to date or be. They're not so famous where he can't hide them in plain site, but they're famous enough where he can brag to Toby and Brian about it.
Brian would kidnap a model. Brian loves photography and cinematography, so who better to have than a darling who models for a living. He doesn't need to find out your right angles or what poses to have you do because you already know. Don't want to take a picture for him in lingerie? Fine. Starve for a week straight. Still don't want to do it? OK, guess you want him to take all that beauty away. What will the public think when he anonymously post all of those photos onto the dark web, ans then he'll read to you every single rude and disgusting comment people at to say. This man will ruin you.
Ben would kidnap a streamer, hands down. Ben is the biggest nerd of century, loving all things video games and anime related. Before he kidnapped you he would binge your videos, making sure to pop into every single live stream from start to finish. Sometimes he thought about hacking into your stream just to mess with you, or to just come out of your TV in the middle of your live and just kidnap you then. But, Ben knew better. He'd much rather terrorize you in private and release the feed later rather than doing it in real time.
LJ would love the star of a circus. Maybe your think is fire breathing, or animal taming, or you share his love of clowns. The possibilities are endless. But he would love to have you be apart of his acts and schemes. If you love taking risks he'll definitely test just how far you're willing to go. He will have you leap through circles that are lit on fire. Or, he'll have you tightrope walk with heels, or maybe with weights of both your arms. And don't even think about refusing him.
Jeff is definitely taking a true crime Podcaster. You only peeped his interest because one day you made a video discussing his crimes and how he was still on the loose. This caused him to spiral into an endless amount of fantasizes.
45 notes
·
View notes
Text
so you've probably been warned against clicking strange links and to especially avoid revealing your personal information online, even in "private" accounts. But what about a "cute" spin-the-wheel link above a tumblr poll?? (like the post in the following screenshot)
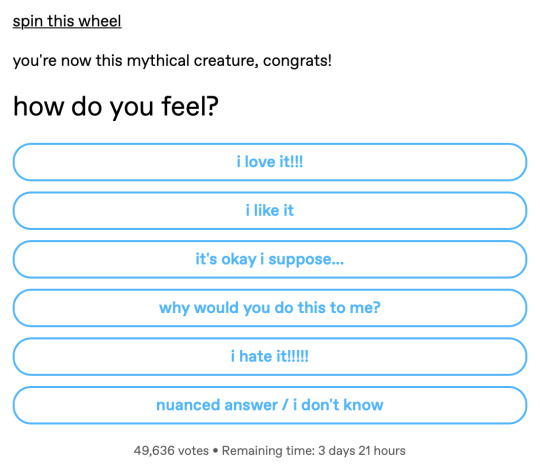
FYI: getting people to click an external link is a great strategy for gathering more details about a mostly anonymous user in a forum or tumblr or wherever. Here's some reasons why: 1. If you shared a unique link in a restricted forum or channel or community or chatroom or public fandom blog or at the end of a fic on ao3, you can be sure only the people of interest could click on it 2. That URL could lead to fucking anything of their choosing. Do they want to do an intensive browser fingerprint or get a log of IP addresses? Do they want to estimate the hardware specs of everyone's machines? Do they want to try loading other things on the page to test for adblockers or other blacklists? (an additional kind of profiling) 3. People LOVE to give away identifying information for the sake of a poll or cute name generator. Here are some questions I've seen recently and what information it can point to: - First anime? (fuzzy proxy for age and country) - First celebrity crush? (fuzzy proxy for age and country) - First album? (fuzzy proxy for age and country) - First name using first letter of last name, Last name using birthday month (do I need to spell this out? last name and birthday month) - What word do you use for [common item]? (region, language, culture, class) - Getting people to talk about astrology (you've all given away your birth month for free, wtf) Another fun fact about "Spin The Wheel" links: they can generate ad revenue for someone! Fun fact about Quizzes: they can help build deeper advertising profiles for linkbait sites like facebook or buzzfeed or the daily mail or tmz Another fun fact: besides the info the Spin The Wheel or Name Generator pages save direct to the server, the page can encode that information back into where the wheel stops or the name it gives you. That makes it easier to gather information because it's recorded 1st on the server (controlled by person fishing to unmask someone) 2nd back in the post notes or in the discord channel or wherever. And we all know how much people want to gab about the Fun poll or survey or quiz and reveal even more information. Another fun fact about Spin the Wheel or Name Generator or Quiz pages: You might be seeing a list of options nobody else saw that only appear for IP addresses from a certain region! And if you post your result (that would be mostly unique) it's an INSTANT indication that the person from [region] is logged in. (same goes for browser fingerprint - which device a certain person has) I remember a line from an article about digital detectives (I think it was feds tracking dark web stuff), it said they wait for YEARS for someone to post or log in just to confirm a person of interest was in a certain place at a certain time. You and I probably don't remember the information we leaked years and years ago in the notes of a post or on a retweet of some idiot, but any people who might want to figure you out probably have a huge spreadsheet with everything recorded. They can and do analyze and annotate it all, and can start to narrow down where you are, how old you are, your interests, hobbies, class background, devices you use etc. You might be thinking: "but I don't worry about federal agents or intelligence agencies, why do I care?" What if tomorrow your post goes viral, truly globally Viral? You can go from tumblr nobody to target for stalkers and/or hate crimes instantly. An even more serious example from this year: What if you've been advocating for years for people that are now scapegoat of the day for the fascists? What if a federal agent is tasked with creating a list of "those people" for surveillance? The less information you have unintentionally posted about yourself the better. A perhaps more personal and private example: what if you had to get away from a city or country or person or persons or family and didn't want them to follow you? People with a grudge will go to great lengths to get back at someone
#privacy online is bigger than direct reveals of the big details like dob or location#gotta be careful#some people make it their life's work to tease out key information without you ever noticing - they're experts#be cautious and wary out there#you don't know who's reading your posts or sharing your dms or charting your ip addresses#my blog#digital privacy
31 notes
·
View notes
Text
[Full Text] Emerging Media Companies, Tracking Cookies, and Data Privacy -- An open letter to Critical Role, Dropout, and fellow audience members
Summary / TL;DR
Both Critical Role (CR) and Dropout have begun exclusively using links provided by third-party digital marketing solution companies in their email newsletters.
Every link in each of the newsletters (even the unsubscribe link) goes through a third-party domain which is flagged as a tracking server by the uBlock Origin browser extension.
Third-party tracking cookies are strictly unnecessary and come with a wide array of risks, including non-consensual targeted advertising, targeted misinformation, doxxing, and the potential for abuse by law enforcement.
You are potentially putting your privacy at risk every time you click on any of the links in either of these newsletters.
IMO these advertising companies (and perhaps CR/Dropout by proxy) are likely breaking the law in the EU and California by violating the GDPR and CCPA respectively.
Even if Critical Role and Dropout are not directly selling or exploiting your personal data, they are still profiting off of it by contracting with, and receiving services from, companies who almost certainly are. The value of your personal data is priced into the cost of these services.
They should stop, and can do so without any loss of web functionality.
1/7. What is happening?
Critical Role and Dropout have begun exclusively using links provided by third-party digital marketing solution companies in their email newsletters.

[ID: A screenshot of the Dropout newsletter alongside the page’s HTML source which shows that the target destination for an anchor element in the email leads to d2xR2K04.na1.hubspotlinks.com. End ID.]

[ID: A screenshot of the CR newsletter alongside the page’s HTML source which shows that the target destination for an anchor element in the email leads to trk.klclick.com. End ID.]
The domains attached to these links are flagged as advertising trackers by the uBlock Origin browser extension.

[ID: Screenshot of a Firefox web browser. The page displays a large warning icon and reads “uBlock Origin has prevented the following page from loading [...] because of the following filter: `||hubspotlinks.com` found in Peter Lowe’s Ad and tracking server list. End ID.]

[ID: Screenshot of a Firefox web browser. The page displays a large warning icon and reads “uBlock Origin has prevented the following page from loading [...] because of the following filter: `||klclick1.com` found in Peter Lowe’s Ad and tracking server list. End ID.]
In both cases, every link in the newsletter goes through the flagged third-party domain, and the intended endpoint (Twitter, their store page, etc.) is completely obscured and inaccessible from within the email itself. Even the unsubscribe links feed through the tracking service.
You can test this yourself in your own email client by hovering your cursor over a link in the email without clicking it and watching to see what URL pops up. You may have noticed this yourself if you use uBlock Origin as an ad-blocker.
I don’t know for certain when this first started. It’s possible that this has been going on for a year or more at this point, or it may have started just a few months ago. Either way: it ought to stop.
2/7. What is a tracking cookie?
A tracking cookie is a unique, universally identifiable value placed on your machine by somebody with the intention of checking for that value later to identify you (or at least to identify your machine).
Tracking cookies are used by companies to create advertising behaviour profiles. These profiles are supposedly anonymous, but even if the marketing companies creating them are not lying about that (a tough sell for me personally, but your mileage may vary when it comes to corporations with 9-figure annual incomes), the data can often be de-anonymized.
If this happens, the data can be used to identify the associated user, potentially including their full name, email address, phone number, and physical address—all of which may then be associated with things like their shopping habits, hobbies, preferences, the identities of their friends and family, gender, political opinions, job history, credit score, sexuality, and even when they ovulate.
Now, it is important to note that not all cookies are tracking cookies. A cookie is just some data from a web page that persists on your machine and gets sent back to the server that put it there. Cookies in general are not necessarily malicious or harmful, and are often essential to certain web features functioning correctly (e.g. keeping the user logged in on their web browser after they close the tab). But the thing to keep in mind is that a domain has absolute control over the information that has been stored on your computer by that domain, so allowing cookies is a matter of trusting the specific domain that wants to put them there. You can look at the outgoing information being sent from your machine, but its purpose cannot be determined without knowing what is being done with it on the other side, and these marketing companies ought not to have the benefit of your doubt when they have already been flagged by privacy watchdogs.
3/7. What’s the harm?
Most urgently, as I touched on above: The main source of harm is from corporations profiting off of your private data without your informed consent. However, targeted advertising is actually the least potentially harmful outcome of tracking cookies.
1/6. Data brokers
A data broker is an individual or company that specializes in collecting personal data (such as personal income, ethnicity, political beliefs, geolocation data, etc.) and selling or licensing such information to third parties for a variety of uses, such as background checks conducted by employers and landlords, two universally benevolent groups of people.
There are varying regulations around the world limiting the collection of information on individuals, and the State of California passed a law attempting to address this problem in 2018, following in the footsteps of the EU’s GDPR, but in the jurisdiction of the United States there is no federal regulation protecting consumers from data brokers. In fact, due to the rising interest in federal regulation, data broker firms lobbied to the tune of $29 million in the year 2020 alone.
2/6. De-anonymization techniques
Data re-identification or de-anonymization is the practice of combining datasets (such as advertising profiles) and publicly available information (such as scraped data from social media profiles) in order to discover patterns that may reveal the identities of some or all members of a dataset otherwise intended to be anonymous.
Using the 1990 census, Professor Latanya Sweeney of the Practice of Government and Technology at the Harvard Kennedy School found that up to 87% of the U.S. population can be identified using a combination of their 5-digit zip code, gender, and date of birth. [Link to the paper.]
Individuals whose datasets are re-identified are at risk of having their private information sold to organizations without their knowledge or consent. Once an individual’s privacy has been breached as a result of re-identification, future breaches become much easier: as soon as a link is made between one piece of data and a person’s real identity, that person is no longer anonymous and is at far greater risk of having their data from other sources similarly compromised.
3/6. Doxxing
Once your data has been de-anonymized, you are significantly more vulnerable to all manner of malicious activity: from scam calls and emails to identity theft to doxxing. This is of particular concern for members of minority groups who may be targeted by hate-motivated attacks.
4/6. Potential for abuse by government and law enforcement
Excerpt from “How period tracking apps and data privacy fit into a post-Roe v. Wade climate” by Rina Torchinsky for NPR:
Millions of people use apps to help track their menstrual cycles. Flo, which bills itself as the most popular period and cycle tracking app, has amassed 43 million active users. Another app, Clue, claims 12 million monthly active users. The personal health data stored in these apps is among the most intimate types of information a person can share. And it can also be telling. The apps can show when their period stops and starts and when a pregnancy stops and starts. That has privacy experts on edge because this data—whether subpoenaed or sold to a third party—could be used to suggest that someone has had or is considering an abortion. ‘We're very concerned in a lot of advocacy spaces about what happens when private corporations or the government can gain access to deeply sensitive data about people’s lives and activities,’ says Lydia X. Z. Brown, a policy counsel with the Privacy and Data Project at the Center for Democracy and Technology. ‘Especially when that data could put people in vulnerable and marginalized communities at risk for actual harm.’
Obviously Critical Role and Dropout are not collecting any sort of data related to their users’ menstrual cycles, but the thing to keep in mind is that any data that is exposed to third parties can be sold and distributed without your knowledge or consent and then be used by disinterested—or outright malicious—actors to de-anonymize your data from other sources, included potentially highly compromising data such as that collected by these period-tracking apps. Data privacy violations have compounding dangers, and should be proactively addressed wherever possible. The more of your personal data exists in the hands of third parties, the more it is to be de-anonymized.
5/6. Targeted misinformation
Data brokers are often incredibly unscrupulous actors, and will sell your data to whomever can afford to buy it, no questions asked. The most high-profile case of the consequences of this is the Facebook—Cambridge Analytica data scandal, wherein the personal data of Facebook users were acquired by Cambridge Analytica Ltd. and compiled alongside information collected from other data brokers. By giving this third-party app permission to acquire their data back in 2015, Meta (then Facebook) also gave the app access to information on their users’ friend networks: this resulted in the data of some 87 million users being collected and exploited.
The data collected by Cambridge Analytica was widely used by political strategists to influence elections and, by and large, undermine democracy around the world: While its parent company SCL had been influencing elections in developing countries for decades, Cambridge Analytica focused more on the United Kingdom and the United States. CEO Alexander Nix said the organization was involved in 44 American political races in 2014. In 2016, they worked for Donald Trump’s presidential campaign as well as for Leave.EU, one of the organisations campaigning for the United Kingdom to leave the European Union.
6/6. The Crux: Right to Privacy Violations
Even if all of the above were not concerns, every internet user should object to being arbitrarily tracked on the basis of their right to privacy. Companies should not be entitled to create and profit from personality profiles about you just because you purchased unrelated products or services from them. This right to user privacy is the central motivation behind laws like the EU’s GDPR and California’s CCPA (see Section 6).
4/7. Refuting Common Responses
1/3. “Why are you so upset? This isn’t a big deal.”
Commenter: Oh, if you’re just talking about third party cookies, that’s not a big deal … Adding a cookie to store that ‘this user clicked on a marketing email from critical role’ is hardly [worth worrying about].
Me: I don’t think you understand what tracking cookies are. They are the digital equivalent of you going to a drive through and someone from the restaurant running out of the store and sticking a GPS monitor onto your car.
Commenter: Kind of. It’s more like slapping a bumper sticker on that says, in restaurant-ese, ‘Hi I’m [name] and I went to [restaurant] once!’
This is actually an accurate correction. My metaphor was admittedly overly simplistic, but the correction specifies only so far as is comfortable for the commenter. If we want to construct a metaphor that is as accurate as possible, it would go something like this:
You drive into the McDonald’s parking lot. As you are pulling in, unbeknownst to you, a Strange Man pops out of a nearby bush (that McDonald’s has allowed him to place here deliberately for this express purpose), and sticks an invisible bumper sticker onto the back of your car. The bumper sticker is a tracker that tells the Strange Man which road you took to drive to McDonald’s, what kind of car you drive, and what (if anything) you ordered from McDonald’s while you were inside. It might also tell him where you parked in the parking lot, what music you were listening to in your car on the way in, which items you looked at on the menu and for how long, if you went to the washroom, which washroom you went into, how long you were in the washroom, and the exact location of every step you took inside the building.
Now, as soon as you leave the McDonald’s, the bumper sticker goes silent and stops being able to report information. But, let’s say next week you decide to go to the Grocery Store, and (again, unbeknownst to you), the Strange Man also has a deal with the Grocery Store. So as you’re driving into the grocery store’s parking lot, he pops out of another bush and goes to put another bumper sticker onto your car. But as he’s doing so, he notices the bumper sticker he’s already placed there a week ago that only he can see (unless you’ve done the car-equivalent of clearing your browser cache), and goes “ah, it’s Consumer #1287499290! I’ll make sure to file all of this new data under my records for Consumer #1287499290!”
You get out of your car and start to walk into the Grocery Store, but before you open the door, the Strange Man whispers to the Grocery Store: “Hey, I know you’re really trying to push your cereal right now, want me to make it more likely that this person buys some cereal from you?” and of course the Grocery Store agrees—this was the whole reason they let him set up that weird parking lot bush in the first place.
So the Strange Man runs around the store rearranging shelves. He doesn’t know your name (all the data he collects is strictly anonymous after all!) but he does know that you chose the cutesy toy for your happy meal at McDonald’s, so he changes all of the cereal packaging labels in the store to be pastel-coloured and covered in fluffy bears and unicorns. And maybe you were already going to the Grocery Store to buy cereal, and maybe you’re actually very happy to buy some cereal in a package that seems to cater specifically to your interests, but wouldn’t you feel at least a little violated if you found out that this whole process occurred without your knowledge? Especially if you felt like you could trust the people who owned the Grocery Store? They’re not really your friend or anything, but maybe you thought that they were compassionate and responsible members of the community, and part of the reason that you shopped at their store was to support that kind of business.
2/3. “Everyone does it, get over it.”
Commenter: [The marketing company working with CR] is an industry standard at this point, particularly for small businesses. Major partner of Shopify, a fairly big player. If you don't have a software development team, using industry standard solutions like these is the easy, safe option.
This sounds reasonable, but it actually makes it worse, not better, that Critical Role and Dropout are doing this. All this excuse tells me is that most businesses using Shopify (or at least the majority of those that use its recommended newsletter service) have a bush for the Strange Man set up in their parking lot.
Contracting with these businesses is certainly the easy option, but it is decidedly not the safe one.
3/3. “They need to do it for marketing reasons.”
Commenter 1: Email marketing tools like [this] use tracking to measure open and click rates. I get why you don’t want to be tracked, but it’s very hard to run a sizeable email newsletter without any user data.
Commenter 2: I work in digital marketing … every single email you get from a company has something similar to this. Guaranteed. This looks totally standard.
I am a web programmer by trade. It is my full time job. Tracking the metrics that Critical Role and Dropout are most likely interested in does not require embedding third-party tracking cookies in their fans’ web browsers. If you feel comfortable taking my word on that, feel free to skip the next section. If you’re skeptical (or if you just want to learn a little bit about how the internet works) please read on.
5/7. Tracking cookies are never necessary
We live in a technocracy. We live in a world in which technology design dictates the rules we live by. We don’t know these people, we didn’t vote for them in office, there was no debate about their design. But yet, the rules that they determine by the design decisions they make—many of them somewhat arbitrary—end up dictating how we will live our lives. —Latanya Sweeney
1/3. Definitions
A website is a combination of 2 computer programs. One of the two programs runs on your computer (laptop/desktop/phone/etc.) and the other runs on another computer somewhere in the world. The program running on your computer is the client program. The program running on the other computer is the server program.
A message sent from the client to the server is a request. A message sent from the server to the client is a response.
Cookies are bits of data that the server sends to the client in a response that the client then sends back to the server as an attachment to its subsequent requests.
A session is a series of sequential interactions between a client and server. When either of the two programs stops running (e.g. when you close a browser tab), the session is ended and any future interactions will take place in a new session.
A URL is a Uniform Resource Locator. You may also sometimes see the initialism URI—in which the ‘I’ stands for Identifier—but they effectively refer to the same thing, which is the place to find a specific thing on the internet. For our purposes, a “link” and a URL mean the same thing.
2/3. What do Critical Role and Dropout want?
These media companies (in my best estimation) are contracting with the digital advertising companies in order to get one or more of the following things:
Customer identity verification (between sessions)
Marketing campaign analytics
Customer preference profiles
Customer behaviour profiles
3/3. How can they get these things without tracking cookies?
Accounts. Dropout has an account system already. As Beacon is a thing now I have to assume Critical Role does as well, therefore this is literally already something they can do without any additional parties getting involved.
URL Query Parameters. So you want to know which of your social media feeds is driving the most traffic to your storefront. You could contract a third-party advertising company to do this for you, but as we have seen this might not be the ideal option. Instead, when posting your links to said feeds, attach a little bit of extra text to the end of the URL link so: becomes or or even These extra bits of information at the end of a URL are query parameters, and act as a way for the client to specify some instructions for the server when sending a request. In effect, a URL with query parameters allows the client to say to the server “I want this thing under these conditions”. The benefit of this approach is, of course, that you actually know precisely what information is being collected (the stuff in the parameters) and precisely what is being done with it, and you’ve avoided exposing any of your user data to third parties.
Internal data collection. Optionally associate a user’s email address with their preferences on the site. Prompt them to do this whenever they purchase anything or do any action that might benefit from having some saved preference, informing them explicitly when you do so and giving them the opportunity to opt-out.
Internal data collection. The same as above, but let the user know you are also tracking their movements while on your site. You can directly track user behaviour down to every single mouse movement if you really want to—again, no need to get an outside party involved to snoop on your fans. But you shouldn’t do that because it’s a little creepy!
At the end of the day, it will of course be more work to set up and maintain these things, and thus it will inevitably be more expensive—but that discrepancy in expense represents profit that these companies are currently making on the basis of violating their fans’ right to privacy.
6/7. Breaking the Law
The data subject shall have the right to object, on grounds relating to his or her particular situation, at any time to processing of personal data concerning him or her [...] The controller shall no longer process the personal data unless the controller demonstrates compelling legitimate grounds for the processing which override the interests, rights and freedoms of the data subject or for the establishment, exercise or defence of legal claims. Where personal data are processed for direct marketing purposes, the data subject shall have the right to object at any time to processing of personal data concerning him or her for such marketing, which includes profiling to the extent that it is related to such direct marketing. Where the data subject objects to processing for direct marketing purposes, the personal data shall no longer be processed for such purposes. At the latest at the time of the first communication with the data subject, the right referred to in paragraphs 1 and 2 shall be explicitly brought to the attention of the data subject and shall be presented clearly and separately from any other information. — General Data Protection Regulation, Art. 21
Nobody wants to break the law and be caught. I am not accusing anyone of anything and this is just my personal speculation on publicly-available information. I am not a lawyer; I merely make computer go beep-boop. If you have any factual corrections for this or any other section in this document please leave a comment and I will update the text with a revision note. Before I try my hand at the legal-adjacent stuff, allow me to wade in with the tech stuff.
Cookies are sometimes good and sometimes bad. Cookies from someone you trust are usually good. Cookies from someone you don’t know are occasionally bad. But you can take proactive measures against bad cookies. You should always default to denying any cookies that go beyond the “essential” or “functional” categorizations on any website of which you are remotely suspicious. Deny as many cookies as possible. Pay attention to what the cookie pop-ups actually say and don’t just click on the highlighted button: it is usually “Accept All”, which means that tracking and advertising cookies are fair game from the moment you click that button onward. It is illegal for companies to arbitrarily provide you a worse service for opting out of being tracked (at least it is in the EU and California).
It is my opinion (and again, I am not a legal professional, just a web developer, so take this with a grain of salt) that the links included in the newsletter emails violate both of these laws. If a user of the email newsletter residing in California or the EU wishes to visit any of the links included in said email without being tracked, they have no way of doing so. None of the actual endpoints are available in the email, effectively forcing the user to go through the third-party domain and submit themselves to being tracked in order to utilize the service they have signed up for. Furthermore, it is impossible to unsubscribe directly from within the email without also submitting to the third-party tracking.

[ID: A screenshot of the unsubscribe button in the CR newsletter alongside the page HTML which shows that the target destination for the anchor element is a trk.klclick.com page. End ID.]
As a brief aside: Opening the links in a private/incognito window is a good idea, but will not completely prevent your actions from being tracked by the advertiser. My recommendation: install uBlock Origin to warn you of tracking domains (it is a completely free and open-source project available on most major web browsers), and do not click on any links in either of these newsletters until they change their practices.
Now, it may be the case that the newsletters are shipped differently to those residing in California or the EU (if you are from either of these regions please feel free to leave a comment on whether or not this is the case), but ask yourself: does that make this any better? Sure, maybe then Critical Role and Dropout (or rather, the advertising companies they contract with) aren’t technically breaking the law, but it shows that the only thing stopping them from exploiting your personal data is potential legal repercussions, rather than any sort of commitment to your right to privacy. But I expect that the emails are not, in fact, shipping any differently in jurisdictions with more advanced privacy legislation—it wouldn’t be the first time a major tech giant blatantly flaunted EU regulations.
Without an additional browser extension such as uBlock Origin, a user clicking on the links in these emails may not even be aware that they have interacted with the advertising agency at all, let alone what sort of information that agency now has pertaining to them, nor do they have any ability to opt out of this data collection.
For more information about your right to privacy—something that only those living in the EU or California currently have—you can read explanations of the legislations at the following links (take note that these links, and all of the links embedded in this paper, are anchored directly to the destinations they purport to be, and do not sneakily pass through an additional domain before redirecting you):
7/7. Conclusion
Never attribute to malice that which can be adequately explained by neglect, ignorance or incompetence. —Hanlon’s Razor
The important thing to make clear here is this: Even if Critical Role and Dropout are not directly selling or exploiting your personal data, they are still profiting off of it by contracting with, and receiving services from, companies whom I believe are. You may not believe me.
I do not believe that the management teams at Critical Role and Dropout are evil or malicious. Ignorance seems to be the most likely cause of this situation. Someone at some marketing company told them that this type of thing was helpful, necessary, and an industry standard, and they had no reason to doubt that person’s word. Maybe that person had no reason to doubt the word of the person who told them. Maybe there are a few people in that chain, maybe quite a few. I do not expect everyone running a company to be an expert in this stuff (hell, I’m nowhere close to being an expert in this stuff myself—I only happened to notice this at all because of a browser extension I just happened to have installed to block ads), but what I do expect is that they change their behaviour when the potential harms of their actions have been pointed out to them, which is why I have taken the time to write this.
PS. To the employees of Critical Role and Dropout
It is my understanding that these corporations were both founded with the intention of being socially responsible alongside turning a profit. By using services like the ones described above, you are, however unintentionally, profiting off of the personal datasets of your fans that are being compiled and exploited without their informed consent. You cannot say, implicitly or explicitly, “We’re not like those other evil companies! We care about more than just extracting as much money from our customers as possible!” while at the same time utilizing these services, and it is my hope that after reading this you will make the responsible choice and stop doing so.
Thank you for reading,
era
Originally Published: 23 May 2024
Last Updated: 28 May 2024
#critical role#dimension 20#dropout#dropout tv#brennan lee mulligan#sam reich#critical role campaign 3#cr3#midst podcast#candela obscura#make some noise#game changer#smarty pants#very important people#web security#data privacy#gdpr#ccpa#open letter
10 notes
·
View notes
Text
What is a Mobile Proxy? A Complete Guide for All Use Cases
Mobile proxies are a key asset for businesses managing tasks that depend on trusted, carrier-assigned IP addresses. Their ability to deliver authentic mobile network IPs makes them essential for operations like data extraction, market analysis, and managing multiple online accounts. In this guide, we’ll explain what is a mobile proxy, how it works, and why businesses rely on it for efficient, secure, and scalable online processes.
2 notes
·
View notes
Text
My experiences from shifting to a realistic creepypasta reality.
i'm gonna tell you guys about my shifting experience to a REALISTIC creepypasta reality. Remember that you have to at least be 14 or 16 to read this because there are very messed up and disgusting stuff in this post, and most things look like it came from a the boys episode so DON'T READ IT if you're too sensitive to this stuff.
And a reminder that english is not my first language
One day me and smile dog made a bet about something i don't remember much, but he lost and i made him dress like paw patrol for a week.
once I had a mission in an abandoned factory and I hadn't to kill anyone just rob an item there, but there was criminals in there and an innocent man, so I decided to save him, which was extremely hard for me but he ended running from me frightened because of me... and he ran to a avenue where a truck ran over him.
one day masky made me mad, so I sneaked into Toby's room and extracted his cum on the floor and put it in masky's coffee.
I had a crush on Dr smiley once so I decided to write him a letter confessing to him. but the letter ended up in Slenderman's hands and later he told me he felt the same.
During a phase of my childhood when I was 7 years old, I had a kitten, and one day my cat had disappeared and I had been very sad, so my mother had prepared a meat soup to cheer me up, and when I had finished eating she showed me a piece of my cat's head and said: "was it good?". And then she laughed.
When i was a normal human in my 14s i had an encounter with a zalgo's prophet on Omegle's and they said that they were coming to me, so i thought that if i acted weird in my webcam they wouldn't come. So i started to do wild animal noises and pissed myself.
The prophet or zalgo's proxy, didn't came to get me so it worked.
one day I was in my real form, when I saw a girl with black hair wearing a white sweatshirt that I thought was Jeff, so I started following her, until she turned to me and screamed: "WHAT DO YOU WANT FROM ME?" and threw pepper spray on my face.
I've already eaten a piece of Jack when he had an accident and was on the operating table, so they removed a piece of meat from his ribs that was very damaged and hanging and left it on a tray next to him. I was passing in the corridor and when I looked inside the operating room I saw the piece of meat on the tray and that Dr. smiley had gone out to get something, I sneaked in, took the piece and ate it and left the room.
I don't know what came over me, but at least it was good.
I found out that he regenerates, so this accident was no big deal.
One day I'd been bullied by everyone in the mansion, so i "accidentally" dropped some drug in the soup i was making and the people there ended up eating it, and everyone, except the ghosts, went high. And i got punished for it.
One day I made pasta (not a Creepypasta) as dinner and everyone who ate got sick and almost shit themselves. And again I've got punished and gone to the mansion's dungeon.
One day the proxy trio humiliated me in front of everyone, and i wanted revenge so i posted anonymously a hentai of them three in the mansion's web, and everyone who had phones saw it.
I dated Jack for a while there, and he started to like me to the point where he revealed his face to me. When he did that I realized he was so ugly that I almost cried when I kissed him. After about two weeks I broke up with him.
during my first Christmas in the mansion I saw offenderman using the Christmas turkey to do things u know what... but I was too shy to tell anyone, so during the dinner everyone ate the turkey, except me.
During a mission me and some proxies were discussing a plan and soon we got to a part that involved opening degrees, so I made a joke telling masky to open my legs 180 degrees and I got punished for it.
Note: proxies have a higher ranking than other creepys or lone rangers as they're called there, so you can't disrespect them at all
I already made at least 3 people go to a mental institution.
One day i got to knew about Jeff's and Liu's parents, so while Liu was very drunk i called him on a caller ID and i did my best mom impression voice to say: "it's me Liu, your mother, and I'm coming back for you." While playing hell background noises.
when i was 8 i hated clowns with all my forces but one day i had the bad luck to laughing jack find me. i hated him too much but i was good in not showing it, so one day I've set fire on him and Lucky that my mother found out about my "friend" and got rid of him.
my mother was a witch in that reality.
One say i fell out of my bedroom's window and broke a few bones, and i was brought to the medical office of the mansion and explained what happened to me to nurse and and she just said: "skill issue".
Of course, these are the funniest and light stuff that happened to me. Going to this reality just messed with me, and I'm still scared of some things, but my mental state is fine there's nothing to worry about me.
#creepypasta#shifting#reality shifting#dr smiley#eyeless jack#jeff the killer#masky#ticci toby#slenderman#zalgo#nurse ann#smile dog#homicidal liu#weird
41 notes
·
View notes
Text
What is an ISP Proxy?
An ISP Proxy is a type of proxy hosted in a data center but uses residential IP addresses. Through ISP proxies, you can take advantage of the speed of data center networks while benefiting from the good reputation of residential IPs.
If ISP proxies are a combination of data center and residential proxies in some way, we might want to first define these terms.
Data Center Proxies are designed with simplicity in mind. In most cases, traffic is forwarded from the proxy client to the data center, where the provider redirects your traffic to the destination. As a result, the traffic originates from one of the IP addresses in the data center, meaning multiple users often share the same IP address. For anyone trying to block their use, this can be a red flag. The main advantages of data center proxies are speed and network stability, as data center networks are very stable and offer gigabit speeds.
Residential Proxies rely on the ability of an Internet Service Provider (ISP) to assign IP addresses tied to specific locations. In other words, you get a legitimate and unique IP address that masks your actual location.
With ISP proxies, you get access to these legitimate and unique IP ranges, and hosting them in a data center provides an additional benefit. This makes ISP proxies particularly effective, offering the benefits of both residential proxy services (such as the ability to surf the web from anywhere and the good reputation of residential IPs) and data center proxy services (such as impressive speed).
---
Why Do You Need ISP Proxies?
As you can see, ISP proxies combine the undetectable features of residential proxies with the speed of data center proxies. ISP proxy providers achieve this by working with different ISPs to provide IP addresses instead of the user's IP address. This makes them especially useful for various tasks. Let’s take a look at some of them:
1. Web Scraping
ISP proxies are the best choice for web scraping. They provide fast, undetectable connections that allow you to scrape as much data as needed.
2. Bypass Rate Limiting Displayed as Residential Connections
To prevent attacks like Denial of Service (DoS), most websites and data centers implement rate limiting. This prevents a single IP address from making too many requests or downloading too much data from a single website. The direct consequence is that if you perform web scraping, you are likely to hit these limits.
However, ISP proxies offer a way to bypass rate limits; they use ISP IP addresses to trick the rate limiter code, making it appear as if the requests are coming from a different residential location.
3. Accessing Geo-Restricted Content
Like all proxies, ISP proxies allow you to change your location, making it appear as though you are accessing the internet from another country or region.
4. Bulk Purchasing of Limited Edition Products
E-commerce websites take proactive measures to prevent bots (automated scripts) from purchasing products on their platforms. One common technique is to blacklist IP addresses associated with compulsive purchasing behavior. ISP proxies can help you bypass these restrictions.
---
A Closer Look at ISP Proxies
As mentioned earlier, ISP proxies are hosted in data centers and provide internet service provider IP addresses to the destination. Since ISPs own large pools of public IP addresses, it is nearly impossible to trace the computer using the proxy.
While the main benefit is that they are ideal for web scraping, they also provide other features such as:
- Security: End-to-end encryption, firewalls, web filtering, auditing, and analysis.
- Performance: Web caching and high-speed internet from data centers to destinations.
The uniqueness of ISP proxies is that they are the only proxies that directly deal with ISPs to provide the best anonymous connection. While data center proxies are a good option for providing speed and privacy at a lower price, ISP proxies combine the ability to offer speed and anonymity, giving them a significant advantage.
---
Use Cases
The speed and undetectability of ISP proxies make them the preferred choice for large-scale network operations such as web scraping, SEO monitoring, social media monitoring, and ad verification. Let’s take a deeper look at each use case.
1. Web Scraping
Web scraping is the process of analyzing HTML code to extract the required data from websites.
While the concept is simple, large-scale web scraping requires proxy servers to change your location because many websites display different pages based on your location Additionally, to scrape large volumes of data within a reasonable timeframe, proxies need to be extremely fast. Because of these reasons, ISP proxies are considered the best choice for web scraping.
2. SEO Monitoring
SEO monitoring involves checking the performance of your website, content, articles, etc., in search engine results. However, search engine results are influenced by your location, and the cookies attached to your web browser can affect the displayed results. To bypass these issues, proxies are needed to anonymize your connection or simulate a user from another global location.
Moreover, SEO monitoring involves frequent access to the same webpage, which could lead to your IP address being blacklisted or subjected to rate limits. Therefore, it’s best to use proxies when performing SEO monitoring.
3. Social Media Monitoring
Similar to SEO monitoring, activities in social media monitoring can raise suspicion. As a result, you are forced to comply with the host's rules to avoid being blocked or banned from the platform. For example, managing multiple accounts with the same IP address would certainly raise red flags.
In such cases, ISP proxies can be particularly useful because they fool social network algorithms about your IP address, so you won’t be blocked in the end.
4. Ad Verification
As a marketer, you may want to verify that your advertising partners are delivering on their promises and that the statistics they provide are legitimate.
Ad verification involves scanning the web to check if the ads displayed on various websites match campaign standards, appear on the right sites, and reach the target audience. Since these scans need to cover millions of websites, ISP proxies are ideal to ensure that your ad verification process runs quickly and without being blocked due to excessive use of IP addresses.
---
Conclusion
ISP proxies combine the best of both worlds by offering the speed and stability of data center proxies along with the anonymity and legitimacy of residential proxies. This makes them the perfect tool for activities that require speed, anonymity, and high-volume operations, such as web scraping, SEO monitoring, social media management, and ad verification. By working with ISPs to provide legitimate and unique IP addresses, ISP proxies help users bypass restrictions, access geo-restricted content, and operate more efficiently online.
2 notes
·
View notes
Text
Last Monday of the Week 2023-09-18
Not getting a whole lot of "autumn" vibes from this thing
Listening: Many things, but the one that has been stuck in my head is once again from Siege Ubsessed! by Curta'n'Wall. A New Castle is Born. Do you want a song about. A castle? Yes, you do.
Bonus track: whatever the hell is going on in The Dark Ages
Reading: Finished Perhaps The Stars the other day. I am increasingly convinced that Neal Stephenson has the right idea on how to end most things. The end of Perhaps the Stars is good but it's less good than the rest of the series. The book is wild, so much happens, it's a dramatic change of pace from the prior books, both way more happens and it's far slower.
9A. I am mixed on 9A. As a narrator they do not feel like the 9A. To be fair, Mycroft also does not feel like he would be a great Anonymous either. Still.
Stephenson, yes. Stephenson's books end like an 80's pop song, they just hit a peak and then fade out before you can realize it's happened. An extremely effective way to fill you with what the fuck was that great.
I like the ideas in Terra Ignota immensely. I like the style and the world of Terra Ignota a great deal. I'm not actually sure if I like the prose in Terra Ignota that much.
I do appreciate how the final chapters serve as a sort of proxy for the thoughts you've probably been having while you read the series. The various peoples who have had to just endure the clashing hives get to stand up and go you guys realize an empire is not a good thing right.
Playing: Breath of the Wild, beat Vah Rudania, the Salamander beast. One left, plus maybe four or five more memories, and I do want to track down a couple more of the side quests before I hit the endgame but I feel like I'm probably not going to come back to this much after I beat Ganon.
Also beat the snow dragon Naydra fight which was a really good setpiece. You get the reveal that it's been corrupted by Ganon, which is a great oh shit moment when you think you might have to fight it. You don't but it's still a good mobility challenge. I have some video.
Watching: Nothing really.
Making: Getting back in the CAD saddle for printing things reminds me why I still keep Autodesk Fusion installed in Windows. FreeCAD is great but it has idiosyncrasies that make it less than ideal for even moderately complicated parts. Chief among these is that it is a CAD package with no first class concept of an assembly, anything involving multiple bodies is arduous as fuck.
As a result I am trying out Onshape, the cloud/web CAD package, because at least I can run that in Linux rather than rebooting. I'm going to try and see if I can spin up Fusion 360 (or maybe even SolidEdge for the first time in, god, almost a decade) in Wine/Proton/Whatever but Onshape is promising. Despite the cloud bullshit it handles pretty much like any other professional-ish CAD package.
Tools and Equipment: I have been shaving with a old fashioned safety razor for almost a year now. I had a cheap one from the grocery store but I bought that fancy precision machined aluminium one because I like the concept of a safety razor that barely exposes a blade at all. It has been good.
As a teenager my parents deemed me too ADHD to be allowed even a cartridge razor, and for years I fought with electric razors that left crappy finishes and couldn't get anywhere near what I'd call clean. When I was in University I was like "Man it cannot be that hard to use a cartridge razor" and sure enough it wasn't. The problem I have with cartridge razors is that they clog in seconds and keeping them clear is a pain in the ass. Cuts are even less likely with this fancy one but even with a plain old safety razor it's remarkably hard to injure yourself unless you really aren't paying attention.
Safety razors are marginally more dangerous than cartridge razors but you can clear shaved hair extremely easily which means they cut like a dream for a while and they aren't as frustrating to work with. The fact that blades cost like US¢25 a piece even for slightly fancier ones is a nice touch that makes me much less likely to keep using blades long after they're too blunt to serve.
12 notes
·
View notes
Text
Which Are the BEST 4 Proxy Providers in 2024?
Choosing the best proxy provider can significantly impact your online privacy, web scraping efficiency, and overall internet experience. In this review, we examine the top four proxy providers in 2024, focusing on their unique features, strengths, and tools to help you make an informed decision.
Oneproxy.pro: Premium Performance and Security
Oneproxy.pro offers top-tier proxy services with a focus on performance and security. Here’s an in-depth look at Oneproxy.pro:
Key Features:
High-Performance Proxies: Ensures high-speed and low-latency connections, perfect for data-intensive tasks like streaming and web scraping.
Security: Provides strong encryption to protect user data and ensure anonymity.
Comprehensive Support: Offers extensive customer support, including detailed setup guides and troubleshooting.
Flexible Plans: Provides flexible pricing plans to suit different user needs, from individuals to large enterprises.
Pros and Cons:
Pros
High-speed and secure
Excellent customer support
Cons
Premium pricing
Might be overkill for casual users
Oneproxy.pro is ideal for users requiring premium performance and high security.
Proxy5.net: Cost-Effective and Versatile
Proxy5.net is a favorite for its affordability and wide range of proxy options. Here’s a closer look at Proxy5.net:
Key Features:
Affordable Pricing: Known for some of the most cost-effective proxy packages available.
Multiple Proxy Types: Offers shared, private, and rotating proxies to meet various needs.
Global Coverage: Provides a wide range of IP addresses from numerous locations worldwide.
Customer Support: Includes reliable customer support for setup and troubleshooting.
Pros and Cons:
Pros
Budget-friendly
Extensive proxy options
Cons
Shared proxies may be slower
Limited advanced features support
Proxy5.net is an excellent choice for budget-conscious users needing versatile proxy options.
FineProxy.org: High-Speed, Reliable, and Affordable
FineProxy.org is well-regarded for delivering high-quality proxy services since 2011. Here’s why FineProxy.org remains a top pick:
Key Features:
Diverse Proxy Packages: Offers various proxy packages, including US, Europe, and World mix, with high-anonymous IP addresses.
High Speed and Minimal Latency: Provides high-speed data transfer with minimal latency, suitable for fast and stable connections.
Reliability: Guarantees a network uptime of 99.9%, ensuring continuous service availability.
Customer Support: Offers 24/7 technical support to address any issues or queries.
Free Trial: Allows users to test the service with a free trial period before purchasing.
Pricing:
Shared Proxies: 1000 proxies for $50
Private Proxies: $5 per proxy
Pros and Cons:
Pros
Affordable shared proxies
Excellent customer support
Cons
Expensive private proxies
Shared proxies may have fluctuating performance
Shared proxies may have fluctuating performance
FineProxy.org provides a balanced mix of affordability and performance, making it a strong contender for shared proxies.
ProxyElite.Info: Secure and User-Friendly
ProxyElite.Info is known for its high-security proxies and user-friendly interface. Here’s what you need to know about ProxyElite.Info:
Key Features:
High Security: Offers high levels of anonymity and security, suitable for bypassing geo-restrictions and protecting user privacy.
Variety of Proxies: Provides HTTP, HTTPS, and SOCKS proxies.
User-Friendly Interface: Known for its easy setup process and intuitive user dashboard.
Reliable Support: Maintains high service uptime and offers reliable customer support.
Pros and Cons:
Pros
High security
Easy to use
Cons
Can be more expensive
Limited free trial options
ProxyElite.Info is ideal for users who prioritize security and ease of use.
Comparison Table
To help you compare these providers at a glance, here’s a summary table:

Conclusion
Selecting the right proxy provider depends on your specific needs, whether it's speed, security, pricing, or customer support. Oneproxy.pro offers premium performance and security, making it ideal for high-demand users. Proxy5.net is perfect for those looking for cost-effective and versatile proxy solutions. FineProxy.org provides a balanced mix of affordability and performance, especially for shared proxies. ProxyElite.Info excels in security and user-friendliness, making it a great choice for those who prioritize privacy.
These top four proxy services in 2024 have proven to be reliable and effective, catering to a wide range of online requirements.
2 notes
·
View notes
Note
Earlier you and I (and this is how you'll know who I am) were talking in someone's comment section about the two hacktivist groups, Anonymous and User, the latter of whom I figured you were, and I couldn't answer you while there, so I've come here to tell you the difference between the two groups, though it also helps to look these people up.
Anonymous Let's start off with the group almost everyone knows about. Anonymous is the group most notable for the slogan "we do not forgive, we do not forget", which refers to its interest in the justice of the world, which, under its veil of literal ambiguity, it pushes for against those in power who wish to stall it. This veil extracts a sense of quantity out of its identity, as the vastness of anonymity, which is inspired by the 4chan presence of peoples whom an "anonymous" name have been applied, as well as the character V in V for Vendetta who shows that it can envelope all forces and functions as it refers to all figures unknown, is akin to an ocean, one which can blur the concept of whatever a perpetrator may be. They, using the ocean that is themselves as a self-enforcing unifying force, also take inspiration from the alter egos of vigilantes of stories of old, though things are not always black and white, as the herd mentality implied by this ocean can, like the ever-changing winds, lead Anonymous to also commit less than stellar acts, as the ocean is only as good as the droplets in it. They are the soul of the web, able to come forth into the world of life to manifest as shadows to enact vengeance upon those they deem wrongdoers.
User User is a group whose mental conception is similar to Anonymous but with key features. A vigilante presence that operates under the milieus whereupon violence and justice are not perceived as the primary key modus operandis, they, while not under a veil like Anonymous, operate under some sense of ambiguity, not which one can say stems from identity but rather imbued in the aura of their actions, which one can say extracts a sense of quantity as well, which are the Machiavellianism/resourcefulness to Anonymous' crackdown, the independently-thinking "trickster character" Loki to Anonymous' herd-thinking "vigilante" Thor. They, in a vain not unlike Anonymous, in a similar self-enforcing unified way via the self-applying implications of their rationale which they don't believe is wrongful so as long as they do it for good (which, like Anonymous, is not an inherent adjective for them, should circumstances guide them off like seismic forces to a more or less desirable direction), believe in a restoration of all that is appreciable in the world, but, defined by the above difference, adhere to a modus operandi that sees them affected by an ambiguity bestowed by the likes of proxies, maneuvers, and what might be called consequentialist actions, with their names having similarly group-oriented origins, with User coming from the hidden nature of an individual whose actions cloud themselves in concealed side-effort methods in order to achieve the end goal, such as, for example, the Ismali Muslims (who invented Assassin's Creed by the way) posing as important people using their voice to guide the right people in place before they could kill rival powers once all the circumstances were facing the right way, which as I read about your ten e-cepts at https://www.deviantart.com/triagonal/art/The-Ten-E-Cepts-written-based-on-one-s-experience-899257268 and https://www.tumblr.com/deviantartdramahub/725681730451800064/i-have-a-question-about?source=share was a thought that came to mind, though it could be interpreted as being of both groups, both in the great web and even the noosphere.
User, with its own slogan of also not forgetting but also encompassing rather than ever judging, is at times the ally of those who call themselves Anonymous and other times its rival and even foe, similar to the ninja and samurai, due to their different ethical-inspired approaches to issues plaguing the world, but they always share the same struggles.
I know, my friend, I know. And you know why.
"User" is also an acronym, at least if you ask some circles.
5 notes
·
View notes
Text
How to get image URLs
Hi all, your friendly mod Kate here! Every once in a while we get people who don't know how best to send images with their submissions, so hopefully this guide helps you out. It covers getting the url using a mouse, and has examples of what to avoid and why.
Since Google Forms don't allow anonymous image uploads, the image must already be on the web with a url that anyone can access. If you are using a search engine, be sure to go to the site your image is from before you do the next steps. If you do this just from a search results page, the url won't be quite right!
Getting the URL
The best way to get the url is to view it on web so you can right click on the image. From the menu, choose "Copy image address".
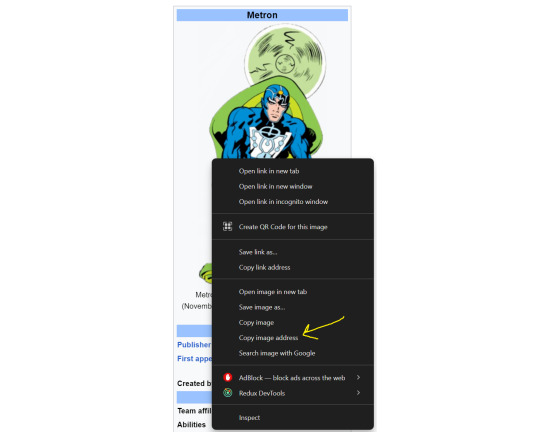
[ID: Screenshot from a wikipedia page of Metron with the right click menu open and an arrow pointing to "Copy image address". /END]
--
Alternatively you can choose "Open image in new tab", then copy the url from the browser's search bar.
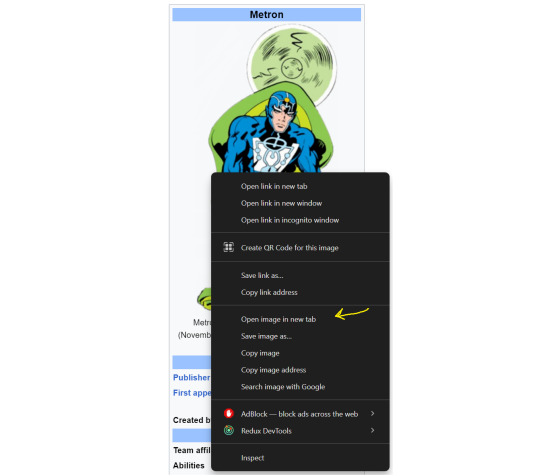
[ID: The same screenshot as above, but with the arrow pointing to "Open image in new tab". /END]

[ID: Cropped screenshot of the image opened in a new tab with an arrow pointing to the browser's url bar. /END]
--
Things to Avoid
When we get unusable image urls, there are three main reasons:
The image is not publicly accessible.
The url is not for an image.
The image is no longer available.
Examples of Issue #1
Images from Google Drive that don't have link sharing on
Images that you have to sign in to see
Examples of Issue #2
This link is to a Google search results page. I can't tell which image someone intended to use.
https://www.google.com/search?q=metron+dc+comics&rlz=1C1CHBF_enUS911US911&oq=metron+&gs_lcrp=EgZjaHJvbWUqDggAEEUYJxg7GIAEGIoFMg4IABBFGCcYOxiABBiKBTIGCAEQRRg7Mg4IAhBFGCcYOxiABBiKBTIGCAMQRRg8MgYIBBBFGEEyBggFEEUYPDIGCAYQRRhBMgYIBxBFGEGoAgCwAgE&sourceid=chrome&ie=UTF-8

[ID: Screenshot of a Google search results page for query "metron dc comics". /END]
This link is to the Google Image search results page. Once again, I don't know which one to use.
https://www.google.com/search?sca_esv=986cfd32cb66a37f&sca_upv=1&rlz=1C1CHBF_enUS911US911&sxsrf=ADLYWIIdCEk3PzdCJUoz7Ymo7teGL9YUIQ:1717103084714&q=metron+dc+comics&tbm=isch&source=lnms&prmd=isnvmbt&sa=X&sqi=2&ved=2ahUKEwjbwaC7o7aGAxUw4MkDHVzeB2YQ0pQJegQIEhAB&biw=1020&bih=1293&dpr=1.5
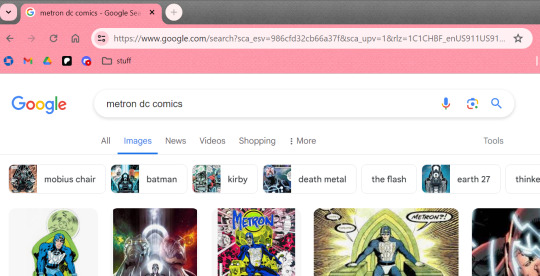
[ID: Screenshot of a Google Image search results page for query "metron dc comics". /END]
This link appears to be from a different search engine called Startpage, where a wiki image had been selected. This is a case where right clicking and choosing "Copy image link" or "Open image in new tab" is not going to work. It is better to go to the page where the image is actually from, and then getting the image url from there. Interestingly, you can see that part of the link contains something that looks similar to this https://vignette.wikia.nocookie.net/marvel_dc/images/a/a5/Dawnallen.jpg, which is a real image url, but it took me quite a while to figure that out, and I'm not going to be able to do that every time.
https://www.startpage.com/av/proxy-image?piurl=https%3A%2F%2Fvignette.wikia.nocookie.net%2Fmarvel_dc%2Fimages%2Fa%2Fa5%2FDawnallen.jpg%2Frevision%2Flatest%2Fscale-to-width-down%2F292%3Fcb%3D20141119200128&sp=1716665195T3f28a643c60d90c333200b2b00010330c9bd2d886952cfba77583da3e859b911
[ID: Screenshot of the browser showing a Startpage search bar that has a red alert message at the top that says, "We're sorry, the page yuo requested is not found. The URL may be misspelled or the page you're looking for is no longer-" the rest is cut off. /END]
--
Examples of Issue #3
This link was valid at the time it was submitted, but Discord links are temporary, so now the image is gone.
https://media.discordapp.net/attachments/927416037027221524/1154255413148143766/Batman_1940_Issue_148_-_Read_Batman_1940_Issue_148_comic_online_in_high_quality2.jpg?ex=6583ae9f&is=6571399f&hm=6faed65d8bb4b81826980470b397632d2ee00f7b6cffcc4320767bdaf7863cd4&
[ID: Screenshot of the browser with a white page that says "This content is no longer available." /END]
This link from Facebook has expired. The image probably still exists, but Facebook uses a CDN that makes temporary urls for content. These expire quickly.
https://scontent-sea1-1.xx.fbcdn.net/v/t1.6435-9/118003141_10157715190051242_806076112121497002_n.jpg?_nc_cat=102&ccb=1-7&_nc_sid=7f8c78&_nc_ohc=aGCMuhwSkFQAX-qpqh1&_nc_ht=scontent-sea1-1.xx&oh=00_AfCWUrtuC3X0qmogIEQMzOb5xdKOp9hwpxJjj4f3v5WQJA&oe=65CA7A60
[ID: Screenshot of the browser with a white page that says "URL signature expired". /END]
4 notes
·
View notes
Text
How To Set Up Socks5 Proxy List in Wingate.me?
What Is Private Proxy Wingate.me?

Wingate.me is a private proxy service that delivers secure managed internet access across your entire network and all your online activities. It caters to a range of requirements, from small networks to large enterprises. Known for its high-quality private proxies, particularly in the Russian region, Wingate.me has carved a niche for itself as a powerful online platform.
Supporting for Internet hosting ensures that the WinGate Proxy Server is compatible with all browsers, SSL, FTP, streaming audio and video, DirectPlay Internet gaming, etc. Socks5 proxy list wingate.me provides clients with a safe, anonymous, and unrestricted internet browsing experience. They shield users from data collection and facilitate access to otherwise blocked websites.
Types of Private Proxy Wingate.me
It offers a variety of private proxy types, including:
1. SOCKS4 proxy
A versatile proxy for web browsing, file sharing and online gaming, known for its speed and efficiency.
2. SOCKS5 proxy
These proxies support TCP and UDP traffic, making them ideal for online streaming, torrenting, and high-performance tasks.
3. IPv4 proxy
Stable and reliable proxy based on IPv4 protocol, compatible with most websites and services on the Internet.
4. Mix of SOCKS5 and IPv4 proxies
This option combines the advantages of both proxy types, providing flexibility for different tasks.
An Overview Of Wingate.me’s Socks5 Proxy List
Socks5 proxy list wingate.me provides an extensive list of Socks5 proxy servers, ensuring users have access to a broad range of functional and efficient proxies. The list, updated regularly, includes information such as the IP address, port number, country, and the last time the proxy was checked for functionality. This transparency empowers users to make informed decisions when selecting a proxy server.
Get 1GB Proxy Free Trial of Residential Proxies Now!
How To Set Up Wingate.me’s Socks5 Proxy?
Setting up a Socks5 proxy from Wingate.me is straightforward. After selecting a proxy from the list, users can configure their web browsers or applications to use the proxy by entering the provided IP address and port number in the relevant settings. Specific setup instructions may vary depending on the application or browser used. Here are detailed instructions:
Step 1 Installing Wingate Proxy Server
After downloading the latest package of WinGate Proxy Server, double-click its ‘.exe’ package to start the installation setup wizard of WinGate proxy server. After that, you will be greeted by its welcome page to get started with the installation on your devices. Click on the “Next” button to continue.
Get 1GB Proxy Free Trial of Residential Proxies Now!
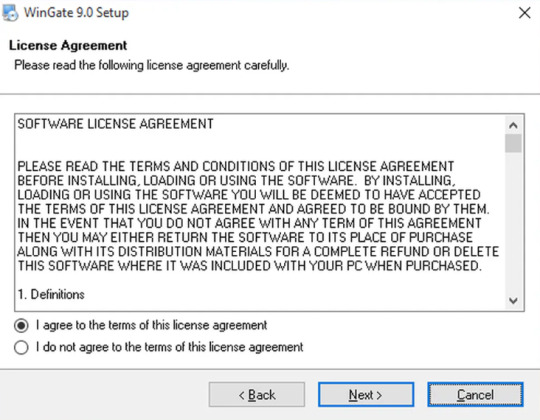
Step 2 License Agreement
You need to read and accept the license agreement before the installation and use of Wingate by choosing the right option as shown.
Step 3 Installation Folder
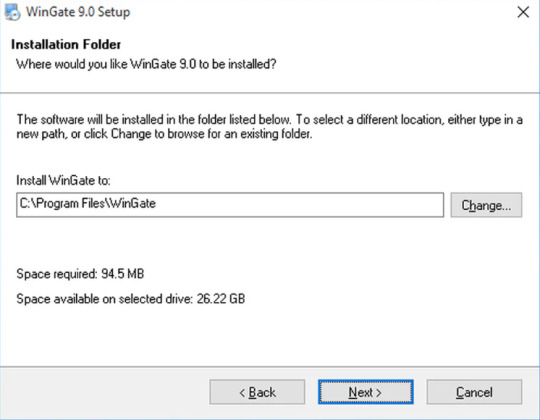
Choose the location on your system, where you like to place the WinGate installation setup.
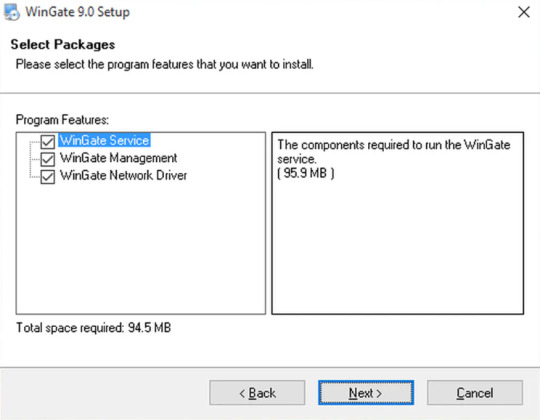
Step 4 Select Packages
You will be asked to choose the program features that you wish to install on your system.
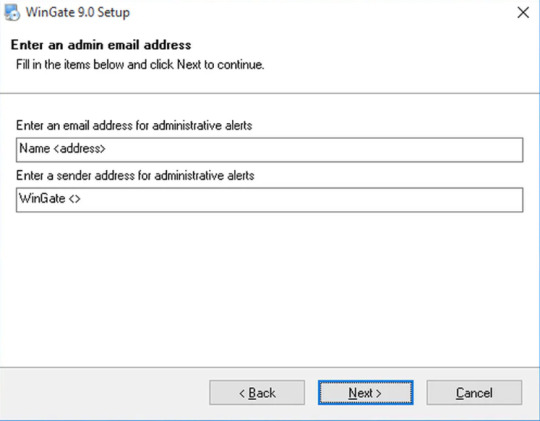
Step 5 Admin Email Address
You should provide your Administrative User Name and Email ID along with the Senders’ address for the administrative alerts.
Step 6 Ready to Install
If you click on the ‘Next’ button, your installation process will start processing files and other selecting configurations. After finishing the installation process of WinGate, click on the ‘Finish’ to exit the installer. Remember to click on the ‘Yes’ to go for system reboot and wait till it is back.

Step 7 Setting Up
After you finish the installation, you can set up Wingate.me’s Socks5 Proxy List now.
1. You will see a welcome page and a navigation menu on the left with available configuration options. Please focus on setting up the proxy. To do this, select “Services” from the navigation menu, then right-click on the empty space on the right and select Install Service.
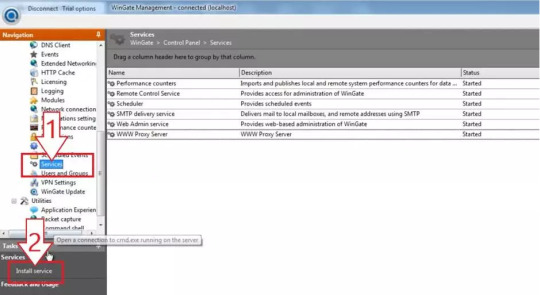
2. The service properties window will appear. Navigate to the Bindings tab. Remove all active bindings and click Add. Select “Any External Adapter” and click “OK” to save your configuration.
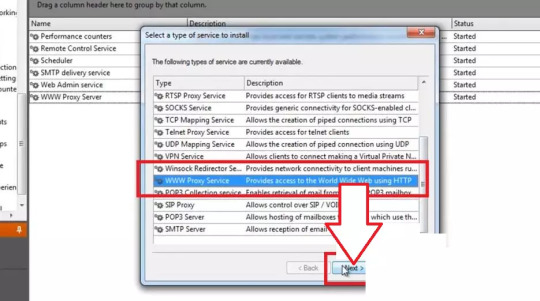
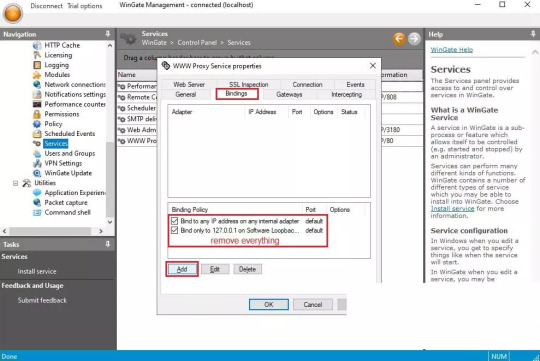
3. Now, go to the Connection tab. Check the box next to “Connect through upstream proxy.” Go to the IP Settings dashboard to configure your proxy. Note down the HTTP proxy host, proxy port, proxy username and proxy password of the private proxy you obtained from the website and import this data into WinGate.

By following these steps, you will successfully configure a private proxy using Wingate’s user-friendly interface. This ensures safe, anonymous and efficient internet browsing while protecting your online activity and data.
Get 1GB Proxy Free Trial of Residential Proxies Now!
Conclusion
Wingate.me’s Socks5 proxy list is a powerful tool for anyone seeking to navigate the digital world with anonymity, versatility, and global access. However, like any tool, it should be used responsibly and ethically. As we continue to sail through the data-driven era, tools like Wingate.me’s Socks5 proxy list will undoubtedly play a crucial role in shaping our digital experiences.
For more please read the original article which is from:
#socks5 proxy list wingate.me
#private proxy wingate.me
#buy wingate me private proxy
#proxy for email wingate.me
3 notes
·
View notes
Text
Mobile Proxies
A mobile proxy is a service that allows users to access the Internet from another location. This can be used to easily bypass geo-restrictions on content or circumvent censorship. When you search the Internet, you share your personal information, such as your IP address and other things that can be used against you in the future.
A mobile proxy server is an intermediary that prevents your personal information, including your IP address, from being transmitted through the websites and places you visit on the Internet.
It provides protection for your sensitive or personal information that could potentially be seen by anyone. If you are interested in such protection, consider one of these proxy servers Infatica.io
Using such a server, you can anonymously visit web pages on the Internet for research, testing and tracking, research competitors' ads, and more.
Proxy servers can help you keep your personal information safe and minimize the chance of you being seen by hackers, even if they are actively looking for your location. By hiding your IP address and replacing it with another from anywhere in the world, you can safely conduct business online and protect yourself from potential cybercrime.
2 notes
·
View notes
Quote
One of the paradoxes of Internet discussion groups is the level of intimacy that can be established while maintaining near-perfect anonymity. This unusual circumstance affords a risk-free opportunity for deceptions that may serve as a practice arena for individuals not yet bold enough to try their deceptions openly. Such online behavior can be easily viewed as a manifestation of factitious disorder. Instead of seeking care at numerous hospitals, these individuals can now gain new audiences merely by clicking from one support group to another. Under the pretense of illness, they can also join multiple groups simultaneously or establish different personae in a single group or one-on-one interactions.
Marc Feldman, from Playing Sick?: Untangling the Web of Munchausen Syndrome, Munchausen by Proxy, Malingering, and Factitious Disorder
2 notes
·
View notes
Text
Cybercriminals turn to “residential proxy” services to hide malicious traffic
For years, gray market services known as “bulletproof” hosts have been a key tool for cybercriminals looking to anonymously maintain web infrastructure with no questions asked. But as global law enforcement scrambles to crack down on digital threats, they have developed strategies for getting customer information from these hosts and have increasingly targeted the people behind the services with…
0 notes
Text
Static residential proxies are IP addresses assigned to devices by Internet Service Providers (ISPs) that are fixed or static, meaning they do not change. These IP addresses belong to actual residential devices, such as personal computers or smartphones, and are not associated with data centers or other types of proxy servers. Static residential proxies are often used for web scraping, data mining, and other activities that require a high degree of anonymity and the ability to bypass detection by websites or online services. Since the IP addresses are associated with residential devices, they are less likely to be flagged as suspicious or associated with automated activity. Static residential proxies are often more expensive than other types of proxies, such as data center proxies or rotating residential proxies, because they are more difficult to obtain and maintain. However, they are also considered more reliable and effective for certain use cases, such as accessing location-based content or conducting market research. How static residential proxies are used for web scraping? Static residential proxies are often used for web scraping because they provide a high degree of anonymity and can help bypass detection by websites or online services. Here's how static residential proxies can be used for web scraping: Collecting data: First, a web scraper uses a program to collect data from a website or online service. This can include data such as prices, product information, reviews, or other information. Sending requests: When a scraper sends a request to a website, the website can see the IP address of the device making the request. If the website detects that the requests are coming from a data center IP address or a high volume of requests are originating from a single IP address, it may block the requests or flag them as suspicious. By using a static residential proxy, the scraper can send requests using an IP address associated with a residential device, making the requests appear more natural and less suspicious. Rotating proxies: Scrapers may use multiple static residential proxies to avoid detection. They can rotate between these proxies after a certain number of requests or a certain amount of time to make it more difficult for websites to detect and block their activity. Overall, static residential proxies are a useful tool for web scraping because they provide a high level of anonymity and can help avoid detection by websites. However, it's important to use them responsibly and in compliance with the terms of service of the websites being scraped. How static residential proxies are used for data mining? Static residential proxies can also be used for data mining, which involves the process of extracting useful information from large data sets. Here's how static residential proxies can be used for data mining: Collecting data: Data mining involves collecting large amounts of data from various sources, such as websites, social media platforms, or databases. A scraper or a crawler is used to extract the data from these sources. Sending requests: When sending requests to extract data, the scraper or crawler may need to access multiple sources simultaneously, or may need to access the same source multiple times. This can be detected by the source's servers, and the activity may be flagged as suspicious or blocked altogether. By using a static residential proxy, the scraper or crawler can send requests using an IP address associated with a residential device, making the requests appear more natural and less suspicious. Maintaining data quality: Data mining often involves cleaning and organizing the collected data to ensure its quality and accuracy. Static residential proxies can help ensure that the data collected is reliable and not biased, by allowing access to different sources and avoiding detection. Overall, static residential proxies are a useful tool for data mining because they provide a high level of anonymity and can help avoid detection by data sources.
However, it's important to use them responsibly and in compliance with the terms of service of the data sources being accessed. How static residential proxies are used for high degree of anonymity? Static residential proxies are used for a high degree of anonymity because they provide IP addresses that are associated with residential devices, making them appear more natural and less suspicious than other types of proxies. Here are some ways static residential proxies can be used for a high degree of anonymity: IP address masking: By using a static residential proxy, the user can mask their actual IP address and appear to be accessing the internet from a different location. This can help protect their privacy and prevent websites or online services from tracking their online activities. Bypassing geo-restrictions: Static residential proxies can be used to access content that is geo-restricted, such as streaming services or websites that are only available in certain countries. By using a proxy with an IP address associated with the target location, the user can bypass these restrictions and access the content they want. Avoiding detection: Static residential proxies can help avoid detection by websites or online services that may block or restrict access based on suspicious activity. By using an IP address associated with a residential device, the user can appear more natural and less suspicious, making it more difficult for their activities to be detected. Overall, static residential proxies are a useful tool for achieving a high degree of anonymity online. However, it's important to use them responsibly and in compliance with the terms of service of the websites or online services being accessed. Why static residential proxies are difficult to obtain? Static residential proxies are difficult to obtain for several reasons: Limited availability: There are only a limited number of residential IP addresses available for use, as they are assigned by Internet Service Providers (ISPs) to residential devices. This means that there are only a limited number of static residential proxies available for use. High demand: Static residential proxies are in high demand because they provide a high degree of anonymity and are less likely to be detected by websites or online services. This means that there is often a high demand for static residential proxies, which can make them difficult to obtain. Cost: Static residential proxies are often more expensive than other types of proxies, such as data center proxies or rotating residential proxies, because they are more difficult to obtain and maintain. This can make them cost-prohibitive for some users. Overall, the limited availability, high demand, and cost of static residential proxies can make them difficult to obtain. However, there are providers that offer access to static residential proxies for a fee. It's important to choose a reputable provider and use them responsibly and in compliance with the terms of service of the websites or online services being accessed. How static residential proxies can be used for conducting market research? Static residential proxies can be used for conducting market research in several ways, including: Competitive analysis: By using static residential proxies, researchers can access the websites and online services of their competitors, and gather information about their products, pricing, and marketing strategies. This can help identify gaps in the market, as well as opportunities for growth and expansion. Survey research: Static residential proxies can be used to conduct online surveys, by allowing researchers to access and interact with different online communities and demographics. This can help gather valuable insights and data about consumer preferences, behavior, and trends. Social media analysis: Static residential proxies can be used to access social media platforms and gather data about consumer sentiment, preferences, and behavior.
This can help identify emerging trends, popular products and services, and areas for improvement. Overall, static residential proxies can be a valuable tool for conducting market research, by allowing researchers to access and gather data from different online sources and communities. However, it's important to use them responsibly and in compliance with the terms of service of the websites and online services being accessed. It's also important to ensure that the research is conducted ethically and that the privacy and rights of research participants are respected. What is rotating residential proxies? Rotating residential proxies are a type of proxy that allows users to access the internet through a pool of IP addresses that are constantly changing or rotating. These IP addresses are associated with residential devices, such as home computers or mobile devices, and are leased from an intermediary service provider that manages the proxy network. When a user makes a request through a rotating residential proxy, the request is routed through one of the available IP addresses in the pool. After a set period of time or after a certain number of requests, the proxy will rotate the IP address being used, so that the user appears to be accessing the internet from a different location each time. Rotating residential proxies are often used for web scraping, data mining, and other tasks that require a high volume of requests to be made without triggering security measures, such as IP blocking or rate limiting. By rotating IP addresses, the user can avoid being detected as a bot or automated program, and can more easily gather data from a wide range of sources. However, because the IP addresses used by rotating residential proxies are shared among multiple users, they may not provide the same level of anonymity or reliability as other types of proxies, such as dedicated or static residential proxies. It's important to choose a reputable provider and use rotating residential proxies responsibly and in compliance with the terms of service of the websites or online services being accessed. In conclusion, rotating and static residential proxies offer unique benefits for web scraping, data mining, and market research. While rotating residential proxies provide constantly changing IP addresses to avoid detection, static residential proxies provide a high degree of anonymity and reliability. Both types of proxies can be valuable tools for accessing and gathering data from the internet, but it's important to use them responsibly and in compliance with the terms of service of the websites or online services being accessed. Choosing a reputable provider and following ethical research practices will help ensure that the data gathered is accurate, useful, and obtained in a legal and ethical manner.
0 notes