#anonymous web browsing
Explore tagged Tumblr posts
Text
Fast Secure Proxy Browser: Browse Anonymously Without Limits

Have you ever tried to access a website, only to be met with a frustrating “This content is not available in your region” message? Or perhaps you've felt uneasy knowing your online activity might be tracked or exposed on public Wi-Fi. In today’s digital landscape, where privacy breaches and content restrictions are increasingly common, it’s no surprise that more users are turning to solutions that offer both security and speed.
That’s where a fast secure proxy browser comes in. It's more than just a digital detour — it’s your shield against surveillance, a bridge to open access, and a tool that puts you back in control of your browsing experience. But what exactly makes a proxy browser both fast and secure? And how can it help you browse anonymously without limits?
In this post, we’ll break down how a fast secure proxy browser works, explore why it matters, and guide you through choosing one that fits your needs. Whether you’re looking to protect your data, bypass geo-blocks, or simply surf without compromise, you’re in the right place. Let’s dive into the tools and tactics that make anonymous browsing not just possible—but effortless.
Understanding Proxy Browsers
Proxy browsers serve as intermediaries between your device and the internet. When you access a website through a proxy browser, your request is rerouted through a remote server. This server masks your IP address, effectively hiding your identity from websites, advertisers, and even government surveillance.
A proxy browser differs from a Virtual Private Network (VPN) in a few key ways. While both hide your IP and offer privacy, VPNs typically encrypt all internet traffic on your device, while proxy browsers work at the application level—usually within the browser itself. This makes proxy browsers lighter and often faster for everyday use.
Why does speed matter? Because privacy tools shouldn't slow you down. A fast proxy browser ensures you're not waiting forever for a webpage to load, all while keeping your identity secure. It also allows seamless streaming, gaming, and general browsing without buffering or lag.
With a secure proxy browser, you no longer need to worry about malicious entities tracking your every move. Your location stays hidden, your data remains encrypted, and your browsing history is safe from third parties.
Key Benefits of a Fast Secure Proxy Browser
Maintain Online Privacy and Hide Your IP
One of the biggest advantages of a fast secure proxy browser is the ability to mask your real IP address. By doing so, your digital footprint is hidden, and your activities can't easily be traced back to you.
Bypass Geo-Restrictions and Censorship
Tired of running into blocked websites? Proxy browsers help you bypass content restrictions imposed by governments, schools, or workplaces. Whether you're accessing streaming services, social media, or news outlets, you can do so freely.
Enjoy Fast Speeds Without Compromising Security
Many users avoid privacy tools due to slow speeds. Fast secure proxy browsers, however, use optimized routing and load-balancing techniques to ensure swift connections, even under heavy traffic.
Protect Data on Public Wi-Fi Networks
Public Wi-Fi is notorious for being a security risk. With a secure proxy browser, you can encrypt your traffic and ensure your data isn’t intercepted by hackers, snoopers, or malicious hotspots.
Essential Features to Look for in a Proxy Browser
End-to-End Encryption Capabilities
Ensure that the proxy browser you choose offers end-to-end encryption. This prevents any third party, including your ISP, from reading your data.
Zero-Log and No Tracking Policies
A true privacy-focused proxy browser won’t log your activity. Check for providers that openly commit to zero-log policies.
Multiple Server Locations for Flexibility
The more server locations available, the easier it is to access global content. It also allows you to switch locations if one is underperforming.
One-Click Access and User-Friendly Interface
Ease of use matters. Look for browsers that require no technical expertise and offer clean, intuitive dashboards for users of all levels.
Use Cases: Who Needs a Fast Secure Proxy Browser?
Journalists and Researchers in Restricted Regions
For those working in countries with limited internet freedom, proxy browsers offer a vital tool for uncensored information gathering.
Everyday Users Who Value Privacy
Even if you're not a whistleblower or journalist, your data matters. Proxy browsers help safeguard everyday browsing activities.
Students Accessing Blocked Educational Resources
Educational institutions sometimes block certain sites. Proxy browsers can help students bypass these restrictions to access learning materials.
Travelers Looking to Avoid Regional Content Blocks
Traveling abroad and can’t access your favorite streaming service? A proxy browser can make it seem like you're back home, unblocking content seamlessly.
How to Get Started with a Secure Proxy Browser
Choosing the Right Tool for Your Needs
Not all proxy browsers are created equal. Look for one that balances speed, privacy, and usability based on your unique needs.
Step-by-Step Setup and Configuration
Download the proxy browser from the official website.
Install and launch the application.
Select a server or location you want to browse from.
Enable encryption settings if available.
Start browsing anonymously.
Tips for Maximizing Speed and Performance
Choose servers closer to your actual location.
Avoid peak usage times when servers may be overloaded.
Clear your browser cache regularly.
Common Mistakes to Avoid
Using free proxies with poor security protocols
Forgetting to turn on encryption settings
Overlooking privacy policies and logging practices
Conclusion
In a world where digital privacy is increasingly under threat, a fast secure proxy browser isn't just a luxury—it's a necessity. From hiding your IP address to bypassing global content barriers, it empowers you to browse anonymously, safely, and without limits.
Whether you're a professional navigating sensitive research or a casual user who values their online freedom, the right proxy browser can redefine your web experience. Choose wisely, stay informed, and take control of your digital journey. Your path to a freer, more secure internet starts now.
FAQ’s
1. What makes a proxy browser fast and secure?It combines optimized server infrastructure with encryption protocols and minimal data logging, ensuring high-speed access and strong privacy.
2. Are proxy browsers legal to use?Yes, using a proxy browser is legal in most countries. However, it's important to comply with local laws regarding internet usage.
3. Can a proxy browser replace a VPN?For basic privacy and unblocking content, yes. But for full-device encryption and enhanced security, a VPN may still be preferable.
4. Do proxy browsers work on mobile devices?Many secure proxy browsers are available for Android and iOS, offering similar features as their desktop counterparts.
5. Are free proxy browsers safe? Not always. Many free services log your data or serve ads. It’s better to choose a reputable proxy browser with a transparent privacy policy.
#secure proxy browser#anonymous web browsing#bypass internet restrictions#online privacy tools#fast proxy service
0 notes
Text
Choosing the Right VPN Service: Key Features and Considerations
In an era where online privacy and security are paramount, selecting the right VPN (Virtual Private Network) service is crucial. With countless options available, it’s essential to understand what features to look for and what makes a VPN service reliable and effective. Here’s a comprehensive guide on how to choose a VPN service and the key elements a good VPN should offer. Security…

View On WordPress
#A#Access#Affordable Pricing Plans#Anonymity#Anonymous Browsing#Anonymous Internet Browsing Experience#Anonymous Web Browsing#Compatibility#Competitive and Transparent Pricing#Comprehensive Privacy Protection Features#Cross-Platform Compatibility#Customer Support#Data Protection#Encryption#Extensive Global Server Network#Global Server Network#High Speed#High-Speed Connection Options#High-Speed Connections#Internet Security#Intuitive User-Friendly Interface#Multi-Device Compatibility#No-Logs Policy#Privacy#Privacy and Security#Privacy Policy#reliability#Reliable Customer Support#Reliable Service#Responsive Customer Support Services
0 notes
Text
ONİONSİTES - DRAGON+ (2)

Onion sites, also known as.onion sites, are a unique type of website that can only be accessed through the Tor network. The Tor network, short for The Onion Router, provides a layer of anonymity and encryption for users accessing these sites, making them popular for those seeking privacy and security online. Unlike traditional websites that can be accessed through standard web browsers, onion sites list require special software, such as the Tor browser, to navigate. Individuals can create onion versions of regular websites or develop standalone onion sites for specific purposes. The exclusivity and privacy features of onion sites contribute to their appeal for various users, ranging from privacy advocates to individuals navigating the dark web for specific content.
There are several reasons why individuals choose to use onion sites, with privacy and anonymity being at the forefront. Onion sites offer a level of confidentiality that is not typically found on the surface web, making them attractive to individuals seeking to protect their identity and browsing habits. Moreover, best onion sites can provide access to content that may be restricted or censored in certain regions, allowing users to circumvent such limitations and access information freely. The encrypted nature of the Tor network adds an additional layer of security, reducing the risk of surveillance and tracking by third parties, including governments and internet service providers.
Common types of content found on onion sites range from forums and marketplaces to news outlets and secure communication platforms. While exploring onion sites, individuals may come across forums, chat rooms, file-sharing platforms, and other interactive spaces that facilitate communication and information exchange in a secure environment. The anonymity and encryption offered 2024 onion sites contribute to a unique online experience, enabling users to engage with content and communities that may not be easily accessible through conventional web browsers.
1K notes
·
View notes
Text
PSA for anyone with an Android phone. Delete your Meta apps (Facebook, Facebook Messenger, Instagram, WhatsApp, Threads). They are spying on you. Much worse than you thought they were. (June 7, 2025)
Gift link to a Washington Post article: https://wapo.st/45hNMeB
Quote from the article:
…apps from Meta and Yandex, a technology company that originated in Russia, circumvented privacy protections in Android devices in ways that allowed their apps to secretly track people as they browsed the web.
That should not have happened. Apps on your phone are walled off from accessing your activity on other apps, including web browser apps like Chrome. Meta and Yandex found work-arounds.
The techniques essentially were akin to malware, or malicious software that is surreptitiously planted on your phone or computer, Dolanjski said.
Google said the behaviors of Meta and Yandex “blatantly violate our security and privacy principles.”
Technical analysis from Ars Technica: https://arstechnica.com/security/2025/06/meta-and-yandex-are-de-anonymizing-android-users-web-browsing-identifiers/
Note: the WaPo article says that so far, there’s no evidence this is happening on iPhones, but that it would be theoretically possible. So you should probably delete your Meta apps on iPhone, too.
50 notes
·
View notes
Text
Friday, August 25th, 2023
🌟 New
On /search pages on the web, we moved the search bar from the sidebar to the center/main section of the page.
For folks in the aforementioned reblog header redesign experiment, we added avatars back to posts from group blogs when the option to show author portraits is enabled.
When blocking a blog via a submission in your inbox on the web, you can now block from both your secondary (if it was the recipient) and your primary blog.
On the web, we have made some improvements to localized number formatting across all supported languages.
On the web, logged out users browsing a blog view will sometimes be prompted to log in after scrolling for some time.
We are testing out showing the “You’re all caught up!” carousel to folks with “Best stuff first” enabled.
🛠 Fixed
On the web, we’ve made some improvements to the post header in compact posts (like when they’re displayed in a grid on the Explore page, for example). Long blog names, badges, and the follow button no longer break onto a new line in the middle of a word, and each element remains properly aligned in the header.
We fixed an issue that caused a bullet point to appear next to the Blogs menu item when using Safari.
We’ve made some headway in fixing various issues relating to undo/redo in the post editor on web. You should notice improved stability when using undo and redo in the editor.
On the web, we fixed an issue where avatars from anonymous asks were empty.
On the web, we fixed an issue affecting the HTML and Markdown modes in the post editor where select all would sometimes select text outside of the editor.
We fixed an issue affecting some users where starting a search with a hashtag (#) would return search results instead of results for that tag.
🚧 Ongoing
We are hard at work updating our docs. If you see anything confusing or out-of-date, please send some feedback!
🌱 Upcoming
Nothing to share today.
Experiencing an issue? File a Support Request and we’ll get back to you as soon as we can!
Want to share your feedback about something? Check out our Work in Progress blog and start a discussion with the community.
501 notes
·
View notes
Text
If you still hold any notion that Google Chrome’s “Incognito mode” is a good way to protect your privacy online, now’s a good time to stop.
Google has agreed to delete “billions of data records” the company collected while users browsed the web using Incognito mode, according to documents filed in federal court in San Francisco on Monday. The agreement, part of a settlement in a class action lawsuit filed in 2020, caps off years of disclosures about Google’s practices that shed light on how much data the tech giant siphons from its users—even when they’re in private-browsing mode.
Under the terms of the settlement, Google must further update the Incognito mode “splash page” that appears anytime you open an Incognito mode Chrome window after previously updating it in January. The Incognito splash page will explicitly state that Google collects data from third-party websites “regardless of which browsing or browser mode you use,” and stipulate that “third-party sites and apps that integrate our services may still share information with Google,” among other changes. Details about Google’s private-browsing data collection must also appear in the company’s privacy policy.
Additionally, some of the data that Google previously collected on Incognito users will be deleted. This includes “private-browsing data” that is “older than nine months” from the date that Google signed the term sheet of the settlement last December, as well as private-browsing data collected throughout December 2023. Certain documents in the case referring to Google's data collection methods remain sealed, however, making it difficult to assess how thorough the deletion process will be.
Google spokesperson Jose Castaneda says in a statement that the company “is happy to delete old technical data that was never associated with an individual and was never used for any form of personalization.” Castaneda also noted that the company will now pay “zero” dollars as part of the settlement after earlier facing a $5 billion penalty.
Other steps Google must take will include continuing to “block third-party cookies within Incognito mode for five years,” partially redacting IP addresses to prevent re-identification of anonymized user data, and removing certain header information that can currently be used to identify users with Incognito mode active.
The data-deletion portion of the settlement agreement follows preemptive changes to Google’s Incognito mode data collection and the ways it describes what Incognito mode does. For nearly four years, Google has been phasing out third-party cookies, which the company says it plans to completely block by the end of 2024. Google also updated Chrome’s Incognito mode “splash page” in January with weaker language to signify that using Incognito is not “private,” but merely “more private” than not using it.
The settlement's relief is strictly “injunctive,” meaning its central purpose is to put an end to Google activities that the plaintiffs claim are unlawful. The settlement does not rule out any future claims—The Wall Street Journal reports that the plaintiffs’ attorneys had filed at least 50 such lawsuits in California on Monday—though the plaintiffs note that monetary relief in privacy cases is far more difficult to obtain. The important thing, the plaintiffs’ lawyers argue, is effecting changes at Google now that will provide the greatest, immediate benefit to the largest number of users.
Critics of Incognito, a staple of the Chrome browser since 2008, say that, at best, the protections it offers fall flat in the face of the sophisticated commercial surveillance bearing down on most users today; at worst, they say, the feature fills people with a false sense of security, helping companies like Google passively monitor millions of users who've been duped into thinking they're browsing alone.
76 notes
·
View notes
Text
/r9k/Elsa Ten Years Later: A Retrospective
Ten years ago today, on July 22, 2014, r9kElsa is Suffering was completed.
If you're reading this, you probably already know the gravity of that event. Let's talk about it anyway :)
r9kElsa is Suffering was one of the earliest fan fiction works written for Frozen, its first chapter published only a few weeks after the movie's release, and was decidedly the most influential.
It was the first widely-read modern-alternate-universe take on Elsa's and Anna's characters, and the way it painted their relationship into a reluctant and tragic romance almost singlehandedly inspired the wider Elsanna ship.
Despite its legacy, it's not the most practiced prose, nor is the plot meticulously planned.
So why did it leave such a mark on its audience? And how was it conceived?
Come with me back to 2013 and we'll find out.
A History
Frozen was released on November 27, 2013, to unexpected critical acclaim and unprecedented box office success.
The internet was quickly buzzing with thoughts about it. A hundred communities in the far-flung reaches of a simpler Web gathered in their respective forums to articulate what the movie meant to them.
Within a few days, a few thoughts began to coalesce in many different places at once: these characters are important to us. They're relatable. They're inspiring.
And, in some strange new way, the scattered diaspora found that the message had spoken to their hearts: love is stronger than fear. There is hope.
The first Frozen fan fiction to gain any traction was "Songs of Ice and Snow", published on November 23 by a lucky author with the privilege of seeing a pre-screening of the movie. It would go on to reach almost 140,000 words over the next several months, and explored the characters in their canon environment, written to take place immediately after the events of the movie.
Soon though, another fic was written with a bold twist: For the First Time was published on December 3, and suggested something previously unexplored: a romantic angle to the sisters' relationship. Niche artists and shitposters had already asserted the notion, but this very early work fleshed out the idea into something surprisingly charming. If love is an open door, then For the First Time opened it just a crack, and readers everywhere were tempted by the glow from beyond.
One specific forum that was quick to latch on to the hard-to-swallow concept was /frz/, a thread on 4chan's /co/ dedicated to Frozen. The trolling effortlessly began to morph into ironic, then tongue-in-cheek, and finally occasionally genuine consideration of what this romance would mean. The trolling never stopped, of course; but in the margins, there was a growing understanding and even affection for this relationship. Why?
Like so much well-loved fiction, it was because people saw themselves in it.
In Elsa, some saw a shut-in who just didn't want to be ostracized anymore. Some saw a dutiful figure who couldn't allow herself to be happy.
In Anna, some saw a socially awkward romantic, starving for affection and acceptance. Others saw an endlessly forgiving empath.
And in both, they saw someone who might understand them.
And in that moment, they fell victim to the fantasy: that two people could be so different and yet could love each other so unreservedly. That two people could understand each other's failings and doubts and grief, that they could be so wounded by each other, and at the end of it all, still sacrifice everything for the other.
In a world of cynicism and transactional relationships, it turns out that these sisters bound by blood scratch an itch: a need to be accepted despite all our flaws. And in some corners of the internet, there grew an quiet desire to be loved like that.
It was in this context that an anonymous /co/ reader, usually only browsing the board for DC comics, began to engage with /frz/. She hadn't ever written fiction before, but at the moment unemployed, was sucked in by the concepts being set forth. She wrote a first chapter that was an exceptional attention grabber, starting with the line "She heard the crossbow bolt thud into her shoulder before she felt it." Many readers will recognize that opening line immediately from Frozen Fractals. The first chapter was initially published in a pastebin for /frz/ to read, on December 6, with promises of violence, cuteness, and sex. Despite very little initial response, the anon is fully engrossed in her work, and posts the next few chapters in the following two days.
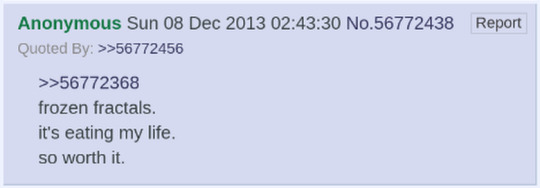
Over the next couple weeks, Frozen Fractals becomes the foremost image of the romantic portrayal of the sisters. The writing style is unpracticed, the character choices sometimes stretch disbelief, and the story is occasionally brutal; and yet, the work is outstanding.
The critical response is enormously positive, even reaching the point of other fiction authors in /frz/ asking the author -- having at this point earned the nickname "Fractals" or "Frac" -- for writing tips and constructive criticism. Additionally though, there are some constructive criticisms offered back, which undoubtedly aided Frac's later work.
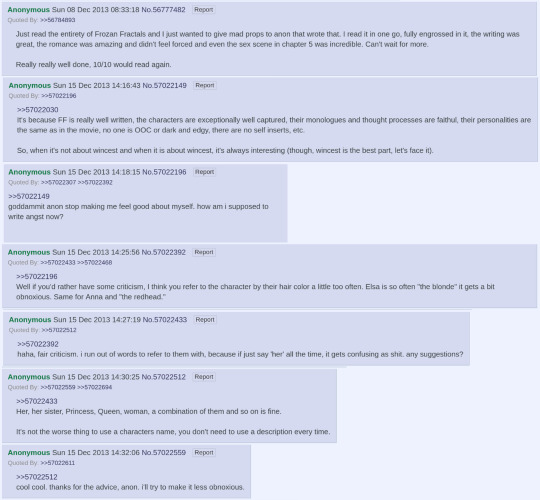
During this same period, the image of Elsa being a broken, self-doubting recluse, while Anna waits determinedly for her to open her door to the world, begins to take a more distinct shape in the /frz/ threads.
Anons start to see Elsa as one of them.
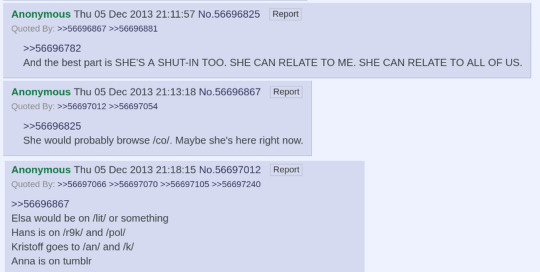
And so it began, slowly at first. But over the next couple weeks, this idea started taking center stage in threads.

And then, the first greentext from the character of /r9k/Elsa:
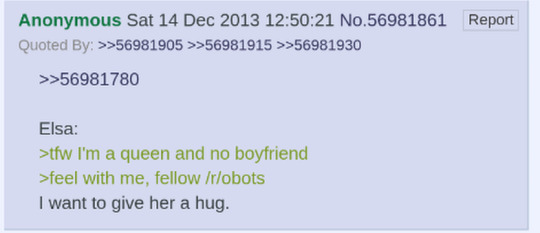
There grew a consensus, a common understanding of who this persona was.
It was initially tongue-in-cheek. But later, like Elsa's monster, it was often the person that we most fear to be.
And the storm raged on.
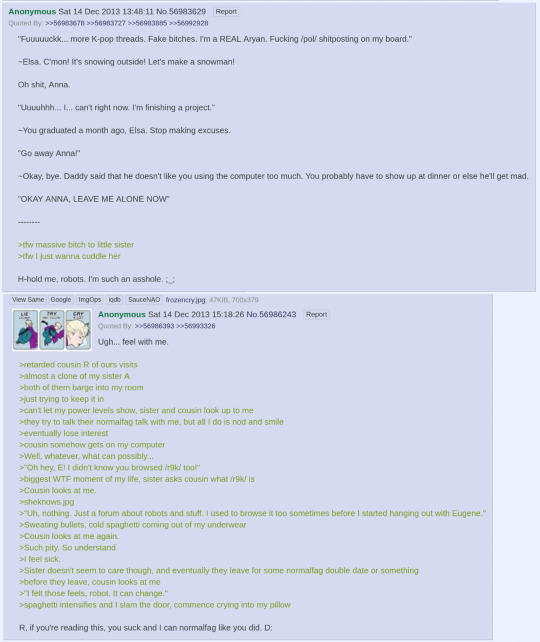
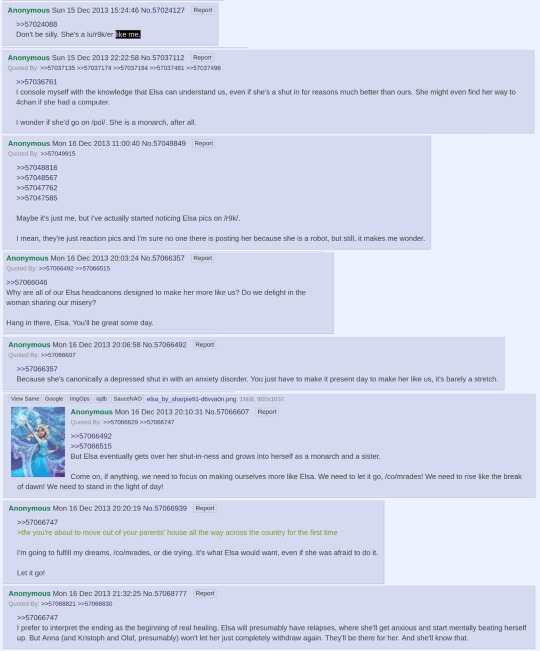
Then, the next day, a turning point is reached: a greentext that realizes the core of the character. These 12 lines precipitated years of community fixation and the story that would come of her.
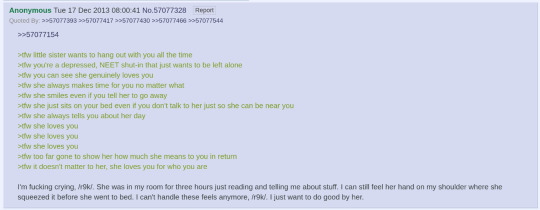
And the rest is history.
Over the next few days, an onslaught of r9kElsa greentexts are posted. For a short while, threads are overwhelmed with discussion of the character. People can't stop talking about it.
Some suggest temporarily banning it from threads so as to stop derailing every discussion.
Despite the proposed ban, some discussion continues behind spoiler tags. Frac is wrapping up Frozen Fractals and becoming increasingly engrossed in the character.
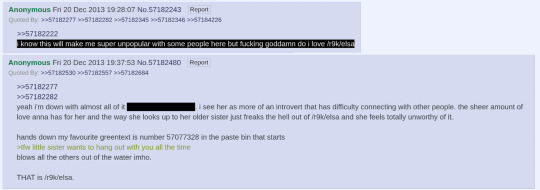
Then, finally, on the Winter Solstice 2013, Elsa's first birthday, tfw She Loves You is posted on Fictionpress.
Frac posts it under an alias in an ultimately-doomed effort to fly under the radar.
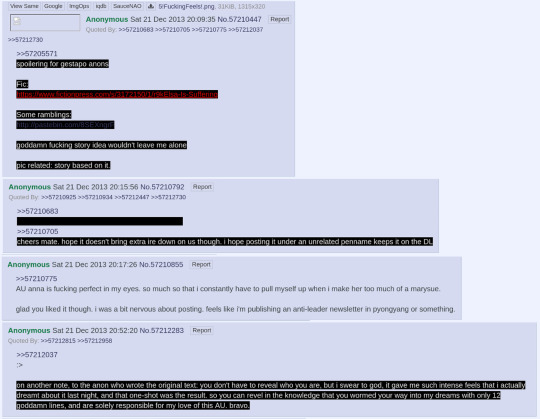
Over the next few days, up to and through Christmas 2013, Frac cannot stop writing. She writes ELEVEN CHAPTERS in four days. The rest of /frz/ is caught up in the r9k storm right along with her.
And then, there's a pause. A couple days go by without update. Finally, a few days later, chapter 12 Drawfriend is posted, and Frac seems a little burned out. Anons ask her what's up.
She realizes that her story is beginning to diverge from the greentexts that /frz/ has written. What started as a collection of one-shots based on scattershot 4chan replies is beginning to feel more important than that. None of the offered greentexts are hitting the spot like they used to. Somehow, the characters need more.
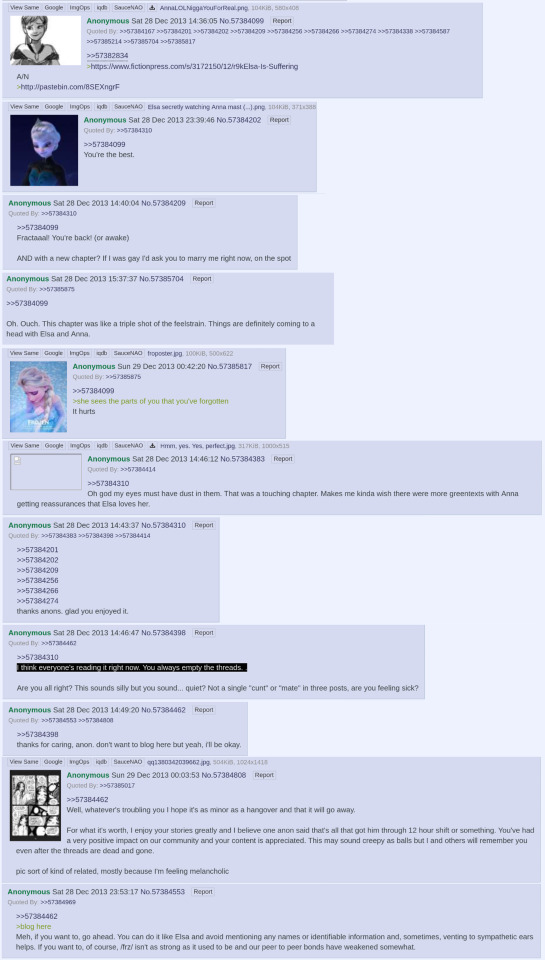
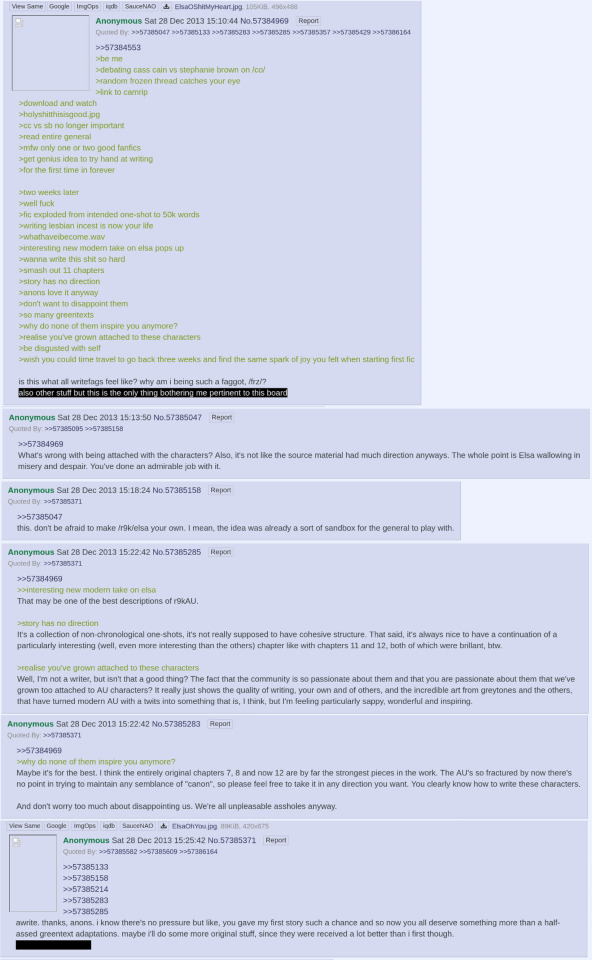
From this moment onward, Frac takes a new direction. Only a couple chapters after this point (16 and 21) are based on greentexts, and even those are loosely adapted. Instead, the fic ceases to be a collection of one-shots and starts forming into a true story, the story that everyone now knows and loves.
She posts the next chapter the same night. Chapter 13 Past is in the Past is a unique installment in the series, going back in time to detail the moment Elsa believes that she fell for Anna. It briefly scales back the angst and drama, and gives a cute slice-of-life of a simpler time for the characters. Some consider it the most human chapter in the story.
From this point on, the story progresses in a remarkable way. In case you haven't read it, I'll avoid too many major spoilers here. But as you can imagine, certain chapters (like 20: Implode-Explode) prompted clamorous reactions from the /frz/ threads.
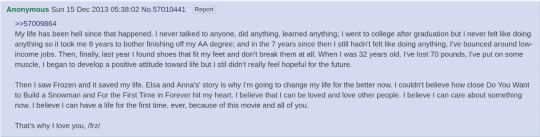
After a few more weeks, other sites start taking notice of what's happening here. Tumblr picks up on the fic and begins rallying behind it. Artists begin painting r9kElsa portraits. It's when r9k starts wrapping up that r/Elsanna is founded and starts gaining traffic.
Other well-known stories also start being published once r9k hits its stride. During a very short period between mid-January and early February 2014, you see Extra! Extra!, A Formal Arrangement, Feel, Don't Conceal, Drum Major, You Are, A Snowflake in Spring, Winter Girl, the Cake Fic, and others published for the first time. Almost every modern-AU fic can trace its characterizations at least partially back to r9k. In some cases, e.g. Tessellate, much more than partially!
A Reason
If you read any post or thread from any Elsanna community in 2014, you'll find one thing repeated over and over: r9kElsa is Suffering brought me here. The story is the most common elevator pitch for the ship, because especially at that time, it meant something more to people than just sexy cartoon girls (though it undoubtedly meant that too).
In a world of isolation, where many traditional sources of community have been whittled away, people are desperate for hope.
This is the core of why Frozen succeeded so tremendously.
It came at exactly the right cultural moment, when both adults and teenagers the world over were feeling more alone than any prior point in history; and it showed that there's a reason to open your door. Even when you're feeling like there's no way out, like no one could ever see past your faults and doubts, you can remember that there IS hope. It's not in Prince Charming or a genie in a bottle. You can have hope in knowing that there are other people, broken in their own ways, who WILL love you for you. Unreservedly.
Frozen has been criticized for its resolution being too easy. "Love," they say, "what a shallow fix for everything!"
They are wrong. Love is an anomaly of nature. It breaks every rule. It is supernatural and spiritual and it is real life magic. And realizing that you can always choose to love the fixer-upper beside you is the surest way to thaw your own frozen heart.
r9kElsa is Suffering has likewise been criticized for its ending. Readers wanted to see something sexy, thrilling, or at least certain. Instead, they got something ambiguous and thoughtful.
Personally, the last two chapters are my favorites of the whole story.
We see a broken family trying to piece itself together. We see a father reckoning with his abject failure, and seeking a new way of living with his family. Any parent would feel overwhelmed, angry, afraid in that situation. He doesn't want to be consumed by fear and frustration. He just wants to love his daughters. And he does. Even after everything, he does.
And critically, he trusts Elsa to make the right decisions, even when he himself doesn't know what they are anymore.
And then, ultimately, in the final chapter, we read a beautiful mirror of the first. Elsa is in her room, but the curtains aren't shut anymore. Sunlight streams in through the window. Anna enters freely, their tension long released by their figurative walls having been dismantled.
In an often-overlooked moment of clarity, Elsa ceases to be consumed by her preferred method of isolation, her computer. Whereas in the first chapter, she can't look Anna in the eye, and only stares at her ever-illuminated computer screen; now, she does something new. She turns off her monitor and momentarily contemplates her reflection in the black mirror. Who is the woman she sees staring back at her?
She would be unrecognizable from the girl who sat in that chair six months before.
Finally, in the last moment, Elsa is faced with making the "right decision".
Unburdened by fear or requirement, she is prompted for the first time to determine honestly what the right thing is, for herself, for Anna, for their family.
She hesitates. What is right? Is it right to push Anna away?
She decides. She loves Anna, and she's never going to erect a wall between them again.
Her father asked her to remember what's important. Anna is what's important to her. All of the rules, all of the shame, all of the worries -- they don't matter.
You love her, and she loves you. That's all that matters.
Dear reader: today, now ten years older, remember what matters to you. Love the people in your life. Love boldly and selflessly and unreservedly, and frozen hearts will begin to thaw.
- tfwyouloveher
---
A/N: many thanks to the people and resources that made this retrospective achievable
frac, also known as @kate---kane and anonelsa, who so many of us have to thank (or curse?) for our years spent in this community
desuarchive.org and archived.moe make this digital archaeology possible
/frz/ will hate me for posting their activity across the web but I don't mind :)
there is a wealth of fascinating and entertaining material in the /frz/ threads of these archives. I spent weeks reading through old threads long considered lost for this post
neiromaru and @spooths are among the top connoiseurs of frozen fanfiction, and their ancient lists made this research much easier
the various archivists on r/elsanna and elsewhere who saved so many important pieces of fic history before they were deleted
the dropbox and mega archives were instrumental
enormous thanks to my editor, who ended up rewriting most of this post, but who wished to remain anonymous. seems unexpectedly appropriate :)
49 notes
·
View notes
Text
Tfw you're browsing a random tumblr and get an important phone call you were only half expecting and your mouth has to do Important Grownup Things while your brain is fumbling through the information catalogue and suddenly this little blog is your lifeline to sanity, this window to a better life where you're not on the phone, a crack in the prison wall that you're glued to, huffing the sweet air of freedom and frantically peeking at the posts you can't focus on.
You're making intelligent Listening noises and writing down things without knowing what they are, just that the psychotic and merciless telephone caller has deemed them worthwhile information that you need to know, and you're staring at a minimalist pastel blog theme with an animated avatar and a doodle of a cat is your safety net, the lines of the pencil drawing forming a web that you dangle above, knowing the second the call ends your brain will fall into its waiting embrace and burrow into the nest of pages of hand-drawn cats in tomato costumes and little bow ties.
Like a stranger grabbing your hand as you dangle off a cliff, this anonymous blogger suddenly holds your world in their invisible hands, a promise that you will survive this and live to see another cat. An unbreakable bond between two strangers, never acknowledged or forgotten.
#and then the call ends and you like a handful of posts and leave#already forgetting the life debt you swore to them in a haze of hysteria#you do not follow their blog and have already forgotten them#poem#poetry
9 notes
·
View notes
Text
Word of the day: Innominate
(adj) having no name, nameless; anonymous; not named, classified.
Remaining innominate on the Internet is the most important safety tip for browsing the world wide web.
3 notes
·
View notes
Text
While the Tor project has tried to assure users that the network is safe, the team is calling for more information. Doubts are spreading about who really controls the network's servers.
The Tor network, used for communications and accessing the dark web, is a gold standard for online anonymity, as it bounces encrypted data through a labyrinth of servers worldwide. However, according to a new investigation by public broadcasters in Germany, its users might not be so anonymous after all.
Law enforcement agencies themselves operate servers on Tor and have developed a “timing analysis” technique to cancel out anonymity provided by the network, research conducted by the ARD political magazine Panorama and STRG_F (funk/NDR) reveals. This was once thought to be impossible.
The Tor project responded by saying that previous Onion service deanonymization attempts were possible because they relied on an old version of the long-retired application Ricochet. However, the organization does not have the documents related to the case and is calling for more information from its users.
“Like many of you, we are still left with more questions than answers – but one thing is clear: Tor users can continue to use Tor Browser to access the web securely and anonymously. And the Tor Network is healthy,” the Tor project team said in a blog post.
“For the great majority of users worldwide that need to protect their privacy while browsing the internet, Tor is still the best solution for them.”
10 notes
·
View notes
Text
ONİONSİTES - DRAGON+

Onion sites, also known as Tor sites, are a unique type of website that can only be accessed through the Tor network. The term "onion site" specifically refers to websites that are exclusively accessible via Tor, distinguishing them from traditional websites that can be reached through standard web browsers. These sites utilize a special-use top-level domain name.onion, which designates them as anonymous onion services previously known as "hidden services". The Tor network, short for The Onion Router, is a free and open-source platform that enables users to browse the internet anonymously and access content not typically available through conventional means.
The functionality of onion sites is based on the encryption and routing protocols of the Tor network. When a user attempts to access an onion site, their connection is routed through a series of volunteer-operated servers, or nodes, to conceal their identity and location. This process helps to protect the privacy and anonymity of both the user and the site they are visiting. Onion web list offer enhanced security and privacy compared to traditional websites, making them attractive to individuals seeking to safeguard their online activities from surveillance, censorship, or tracking.
What are onion sites presents both benefits and risks for users navigating the dark web. Understanding the potential advantages and drawbacks is essential for making informed decisions about online activities. Some key points to consider include: Benefits:
- Enhanced privacy and anonymity
- Access to content not available on the clear web
- Protection against surveillance and tracking Risks:
- Exposure to illegal or harmful content
- Potential security vulnerabilities
- Increased likelihood of encountering malicious actors
By weighing these factors and exercising caution while browsing onion sites, users can leverage the unique capabilities of the Tor network while minimizing potential risks to their online security and well-being.
1K notes
·
View notes
Text
Facebook, Messenger, and Instagram circumvent user anonymity.
2 notes
·
View notes
Text
In today’s digital world, our smartphones are more than just devices—they're personal storage units for our lives. From treasured photos and confidential videos to sensitive contacts, private notes, and login credentials, we rely on our phones to keep it all safe. But what happens when that privacy is compromised? Whether it’s by someone snooping through your phone or a hacker trying to gain access remotely, your personal information could be at serious risk.
If you’ve been wondering how to protect your personal information from hackers, one tool that stands out for everyday users is SafeCalc. It combines powerful privacy features with a smart disguise—appearing as a simple calculator app on your phone. Let’s take a closer look at how this clever little app can protect your digital life without drawing any attention.
Hidden Photo and Video Vault
Most people store photos and videos that are deeply personal. These could be family moments, travel memories, or even private clips not meant for public eyes. SafeCalc offers a hidden vault that locks away your media files securely. Only you can access them using a private code, and because the app is masked as a calculator, no one would ever suspect it contains sensitive content.
Whether you're worried about someone borrowing your phone or concerned about data theft, keeping personal media secure is a solid first step in defending against privacy invasion.
Keep Your Contacts Truly Private
Some contacts are best kept confidential—close friends, work-related connections, or other sensitive relationships. SafeCalc includes a hidden contacts feature that stores important phone numbers away from your default contact list. This means even if someone is casually browsing your phone, these contacts won’t show up.
In cases where you might be dealing with business competitors, concerned about digital tracking, or just value your privacy, separating your personal contacts from public ones is a smart approach.
Secure Notes and Private Thoughts
We often jot down thoughts, ideas, reminders, or personal plans in our phone’s notes app. Sometimes these notes include access information or deeply personal content like journals or affirmations. SafeCalc features a secure notes locker that helps you keep this information under digital lock and key.
Unlike standard notes apps, the locker is encrypted and discreet. No icons, no flashy design—just a calculator on the surface and a secure storage zone underneath.
Smarter Management of Login Details
One of the most common habits that puts people at risk of hacking is using the same login details across multiple sites or apps. Remembering all your different usernames and access codes can be overwhelming, which leads many to cut corners. SafeCalc offers a protected area where you can store your login information, safely encrypted and easy to retrieve when needed.
This is especially helpful for people managing several online accounts, including work platforms, streaming services, and banking apps. Instead of using insecure options like writing them down or reusing old combinations, you can store them safely using a tool like SafeCalc.
Private and Secure Web Browsing
Your browsing history can reveal a lot about you—what you're searching for, where you're going online, and what kind of content you're consuming. SafeCalc includes a private browser that allows you to explore the internet without leaving behind traces like history logs or cookies.
This is ideal for those who value anonymity online, are researching sensitive topics, or simply want a more secure way to browse. It’s a practical solution for staying safe from trackers and minimizing the risk of phishing or targeted hacking attempts.
Built-In Backup and Restore Features
Even if you’ve locked everything away securely, there’s still the possibility of losing your phone or experiencing a technical failure. That’s why SafeCalc includes backup and restore capabilities. All your hidden content—photos, notes, contacts, and login data—can be saved securely and recovered when needed.
This feature offers peace of mind, especially for users who depend on their device as their primary storage. Backing up personal content is one of the most effective ways to safeguard against both hackers and accidental loss.
Why Use SafeCalc for Personal Security?
Unlike typical vault apps that are clearly labeled and attract curiosity, SafeCalc blends in perfectly. It functions like a normal calculator, making it an ideal choice for anyone who wants protection without drawing attention. The app is also designed with simplicity in mind—no complex settings or technical steps, just effective privacy in a user-friendly format.
It combines the power of multiple security apps into one: a photo and video vault, a hidden contact list, a secure notes locker, a login manager, and a private browser—all housed in an app that looks like a basic calculator.
For users looking for a discreet and effective way to safeguard their digital life, SafeCalc has become a trusted companion. Whether you’re worried about hackers, nosy friends, or just want more control over your personal data, it offers a comprehensive solution that fits right in your pocket.
2 notes
·
View notes
Text
Do you know about Queering the Map?

Hey y'all! I wanna highlight a queer platform I've been really interested in recently, one that has gained popularity in the last couple months especially. You might recognize this heartbreaking and intimate excerpt from Gaza that's been circulating social media platforms in the last couple months:
I’ve always imagined you and me sitting out in the sun, hand and hand, free at last. We spoke of all the places we would go if we could. Yet you are gone now. If I had known that bombs raining down on us would take you from me, I would have gladly told the world how I adored you more than anything. I’m sorry I was a coward.
The post comes from queeringthemap.com which, according to their Instagram, "is a community-generated counter mapping platform for digitally archiving LGBTQ2IA+ experience in relation to physical space."
Basically, Queering the Map allows you to post your own queer memories from anywhere in the world, completely anonymous. Wanna mark where you and your girlfriend had your first date? Drop a pin. Wanna place yourself in the middle of the ocean as a metaphor for unrequited love? Drop a pin. Wanna reflect on being the only queer person in your town? Drop a pin.
There is no limit to what users can post - or what they can see. Every post that users have ever created is still on the site, serving as make-shift digital archive for queer memories. Posts are public to any user who visits the website, allowing people to browse the digital globe and the queer experiences people have shared.
Founded by Canadian artist Lucas LaRochelle in 2017, Queering the Map has connected countless LGBTQ2IA+ people from around the world. Some like to share their own memories, others find hope in reading others' posts, and some share the posts to other platforms for rhetorical purposes.
Take the excerpt above from Gaza, for example. It first began to circulate the web (to my knowledge) roughly a year ago, and then again in June after it was featured in a NYT article. Then, in October, Instagram, Twitter, Tik Tok, and Tumblr users began sharing the screenshotted post to show solidarity with Palestinians - especially queer Palestinians. The Dyke Project used this excerpt and others from Gaza to display on bus advertising systems. Something about Queering the Map captivated attention in a unique way - something about it made people feel like it was the right place to turn in moments and feelings of tragedy and horror.
Other times, people share posts that simply spoke to them. Illustrator Aude Nasr brought some posts to life, helping us picture the moments people were trying to document. I've posted some of Nasr's art here.



I encourage you all to check out queeringthemap.com at some point, if not to post for yourself but to just see the beautiful, lively, and complicated memories someone, somewhere, wanted you to see. And to my queer siblings everywhere: I am constantly amazed by our desire to connect with each other, to defy borders and time, and to write our stories down.
Quick userguide:
Entering the website, users find themselves in a zoomed in location on the map. The water is blue, but the land is pink with dotted lines indicating borders between states or regions, and straight lines between countries. Using their mouse, one can scroll to zoom in or out. Memories are marked on the pink map by black location tags, which you can click on to view the specific memory a user shared for that location, or simply run your mouse over it for a smaller box to show the text. Zooming out too far, a user might see a black blob, no pink space in sight as so many memories have been posted to a particular region.
Were you familiar with Queering the Map before this post? What about before the last couple of months? What Queering the Map entry speaks to you? What does queer memory making mean to you?
Here's some posts I've been thinking about lately.
It gets better. When I first got here I was so unsure of myself and if I would be accepted. Now, I know I am loved, I am more sure and I have been accepted and embraced unlike ever before. Roll Pride baby!
came out to my daughter here while driving her to school, 6 years later and 6000km away she came out to me .
Came out to my folks. It didn’t go too well.
Was with the cutest guy I’d ever met
I’m from rafah and she’s from deir al balah, she got married later and i left gaza strip, to this day i think of you, to this day i wish to be back to sleep with you in the same bed, i want you to call for my name again, i wish if i can be with you again my heart. بحبك وبالرغم من الي صار دايما في بالي.
Idk how long I will live so I just want this to be my memory here before I die. I am not going to leave my home, come what may. My biggest regret is not kissing this one guy. He died two days back. We had told how much we like each other and I was too shy to kiss last time. He died in the bombing. I think a big part of me died too. And soon I will be dead. To younus, i will kiss you in heaven.
First kiss 16 years ago
One day, this sea will not divide us.
i hope your family knows i will love you until the day i die. i hope we meet in every life, no matter how many times you break my heart. Wo ai ni
故事从这里开始 : ) Un día te olvidaré, no importa que sea tan difícil. Me lo creo.
31 notes
·
View notes