#bytecode analysis
Explore tagged Tumblr posts
Text
🚀 Unlock your Python potential! Dive into our latest guide on mastering bytecode analysis with the dis module. Perfect for all coding levels! #Python #DisModule #CodingTips
#bytecode#bytecode analysis#coding#developer guide#dis module#programming#Python#python optimization
0 notes
Note
do you happen to know which facial expression is the “autizm” one from classic hd? i cannot stop thinking about this lately of all things they could have called it they went for “autizm”. thanks in advance! :)
Thanks for sending me on this quest! It's been a few years since the discovery of Autizm, and in this time the Pathologic community has developed advanced tools for its analysis. Namely, Gorkhon Script Editor allows the viewing of bytecode scripts, which are where LifeStudio:HEAD facial animations are controlled. With GSE, pathologicdialogue, and somevideoguy's string unpacker, I was at last able to find dialogue lines that, with 100% certainty, cause the Autizm facial expression for each character.


For Grace and Murky, Autizm is a pretty similar expression: they look directly forward. Grace stays still, while Murky raises and lowers her head slightly. However, Grace's Autizm is distinguished by being on a 15-second loop (Murky's and Peter's both last 10 seconds.)

On the other hand, Peter's Autizm expression has almost no eye contact - he looks away and up, occasionally glancing at the player.
There's more to discuss about the process of tracking these down... I'm tempted to do a quick video about it in the near future, schedule permitting. (Look under the cut for the example dialogue lines that you can find to see Autizm for yourself.) In conclusion,

Grace: bachelor day 2 - I don't know. The dead told me to remind you that you will be spoken for by those whom you save, that's all. Is it true that you're going to leave us soon? (509475) [no requirements]
Murky: bachelor day 6 - The mara's hiding today. Everyone's hunting her. And she's hunting you. She thinks that if she kills you, everyone will just let her go. Tee-hee... (512811) [requires that Grace has told you to ask Murky where Clara is to draw her blood]
Peter: bachelor day 2 - Can't you see what I've managed to build here? Where else would I be allowed to do something like this? Everything that I have ever called my purpose has been brought to life in this town. For now, I have no reason to leave it. I haven't finished my observations yet. I'm this close to figuring it out... (507443) [requires Andrey to have agreed to flee the town]
#pathologic#grace#murky#peter stamatin#grace pathologic#murky pathologic#datamining#asks#zinovia#LifeStudio:HEAD
87 notes
·
View notes
Text
Introduction to JavaScript Compilers
JavaScript is one of the most widely used programming languages, powering web applications, servers, and even mobile apps. But how does JavaScript code transform from human-readable text into executable instructions? The answer lies in the JavaScript compiler.
A JavaScript compiler translates high-level JavaScript code into optimized machine code or bytecode, improving performance and efficiency. In this article, we’ll explore how JavaScript compilers work, their key components, and their role in modern web development.
What Is a JavaScript Compiler?
A compiler is a software tool that converts source code written in a high-level programming language (like JavaScript) into a lower-level representation (such as machine code or bytecode). Unlike interpreters, which execute code line by line, compilers process the entire codebase at once, optimizing it for better performance.
JavaScript engines like V8 (Chrome), SpiderMonkey (Firefox), and JavaScriptCore (Safari) use Just-In-Time (JIT) compilation to execute JavaScript efficiently.
How Does a JavaScript Compiler Work?
The JavaScript compilation process involves several stages:
1. Parsing (Lexical Analysis & Syntax Tree Generation)
The compiler first breaks down the code into tokens (keywords, variables, operators).
It then constructs an Abstract Syntax Tree (AST), a structured representation of the code’s logic.
2. Compilation (Bytecode or Machine Code Generation)
Modern JavaScript engines use JIT compilation, which combines interpretation and compilation.
The engine converts the AST into bytecode (an intermediate low-level code) or directly into machine code for execution.
3. Optimization (Inlining, Dead Code Elimination, etc.)
The compiler applies optimizations like:
Inline Caching: Speeds up property access.
Hidden Classes: Optimizes object property access.
Dead Code Elimination: Removes unused code.
4. Execution
The optimized code runs in the browser or Node.js environment.
1 note
·
View note
Text
Unlocking Insights: Text Analytics in NLP with Azure - Ansi ByteCode LLP
Discover how Text Analytics in NLP with Azure. Learn tokenization, sentiment analysis, entity recognition to analyze text efficiently. Please visit:- https://ansibytecode.com/text-analytics-in-nlp-with-azure/
0 notes
Text
R Compiler vs. Interpreter
In programming languages, a compiler translates the entire source code into machine code before execution, making programs run faster, while an interpreter executes code line by line, allowing real-time feedback but often at the cost of speed.
Understanding Compilation and Interpretation
Compiler:
Interpreter:
How R Works: Interpreter vs. Compiler
R is primarily an interpreted language, meaning that when a command is entered, it is executed immediately without requiring prior compilation. This makes it highly suitable for data analysis, statistical computing, and visualization, where real-time feedback is essential.
However, R also has Just-In-Time (JIT) Compilation, which allows parts of the code (such as functions and loops) to be compiled into bytecode before execution. This improves performance while retaining the flexibility of an interpreted language.
Conclusion
While R remains an interpreted language in most cases, its support for JIT compilation through the compiler package helps optimize performance where needed. This hybrid approach allows R to maintain its interactivity while benefiting from compilation efficiency in performance-intensive applications.
For Free Online Tutorials Visit-https://www.tpointtech.com/
For Compiler Visit-https://www.tpointtech.com/compiler/python
0 notes
Text
Understanding the Java Virtual Machine (JVM): Internals and Optimization

Introduction
Briefly introduce the JVM and its role in running Java applications.
Highlight why understanding JVM internals is crucial for developers.
Mention key aspects like performance, memory management, and optimizations.
1. JVM Architecture: An Overview
Explain how JVM acts as an abstraction layer between Java code and the underlying hardware.
Key components:
Class Loader: Loads bytecode into memory.
Runtime Memory Areas: Heap, Stack, Method Area, etc.
Execution Engine: Converts bytecode into native code.
Garbage Collector (GC): Manages memory automatically.
2. JVM Memory Management
Heap vs. Stack Memory: What each is used for.
Method Area & Runtime Constant Pool: Storage for metadata and constants.
Garbage Collection (GC) Mechanisms:
Serial, Parallel, CMS, G1, and ZGC collectors.
When and how GC runs.
Tuning GC for performance (using JVM options like -XX:+UseG1GC).
3. Just-In-Time (JIT) Compilation
How JIT compiles frequently used bytecode into native machine code for performance.
Difference between:
Interpreter Mode (slower execution but quick startup).
JIT Compilation (optimizes hot code paths).
JVM optimizations like:
Method Inlining
Loop Unrolling
Escape Analysis
4. JVM Optimization Techniques
Tuning JVM with Command-line Flags
-Xms and -Xmx for memory allocation.
-XX:+PrintGCDetails for monitoring GC.
Profiling and Monitoring Tools
JVisualVM, JConsole, Java Flight Recorder.
Code-level Optimizations
Reducing object creation to avoid excessive GC.
Using efficient data structures (ArrayList vs. LinkedList).
Avoiding memory leaks (proper use of WeakReferences, ThreadLocal).
5. JVM Performance Best Practices
Selecting the right GC algorithm for different workloads.
Analyzing JVM logs to detect performance bottlenecks.
Using Ahead-of-Time (AOT) Compilation (like GraalVM) for even faster execution.
Conclusion
Summarize key takeaways: JVM architecture, memory management, JIT compilation, and optimizations.
Emphasize the importance of tuning JVM settings for different applications.
WEBSITE: https://www.ficusoft.in/core-java-training-in-chennai/
0 notes
Text

In It has become commonplace in software engineering to refer to testing in a shift-left fashion in recent years. How does that work? This refers to conducting more software testing during the software development phase to reduce defects and save the business money.
The term shift-left testing refers to increased involvement by quality assurance (QA) engineers during the development phase to detect bugs as early as possible, before software engineers have handed the code over to QA for further testing. The most common method is to develop and execute more automated testing of the UIs and APIs.
A software developer should, however, perform a few basic and essential software testing steps before showing someone else their work, whether it is for shift-left testing, formal testing, ad hoc testing, code merging and integration, or just calling a colleague over for a quick look. Its goal is to detect obvious errors that jump out immediately during this basic testing. You would otherwise have to describe the problem to the developer, who would then have to reproduce, debug, and solve it before trying again.
Each software engineer should perform these essential software testing steps before showing their work to others.
1. Basic functionality testing Begin by making sure that every button on every screen works. You also need to ensure that you can enter simple text into each field without crashing the software. You don't have to try out all the different combinations of clicks and characters, or edge conditions, because that's what your testers do—and they're really good at that. The goal here is this: don't let other people touch your work if it's going to crash as soon as they enter their own name into the username field. If the feature is designed to be accessed by way of an API, you need to run tests to make sure that the basic API functionality works before submitting it for more intensive testing. If your basic functionality testing detects something that doesn't work, that's fine. Just tell them that it doesn't work, that you're aware of it, and that they shouldn't bother trying it. You can fix it later, just don't leave any surprises in there.
2. Code review One more sets of eyes taking a gander at the source code can reveal a great deal of issues. Assuming that your coding system requires peer audit, play out this step before you hand the code over for testing. However, make sure to do your essential usefulness testing before the code survey.
3. Static code analysis There are devices that can perform investigation on source code or bytecode without executing it. These static code examination apparatuses can search for some shortcomings in the source code, for example, security weaknesses and potential simultaneousness issues. Utilize static code examination apparatuses to implement coding guidelines, and arrange those devices to run naturally as a feature of the form.
4. Unit testing Engineers will compose unit tests to ensure that the unit (be it a technique, class, or part) is filling in true to form and test across a scope of substantial and invalid data sources. In a consistent reconciliation climate, unit tests ought to run each time you commit a change to the source code store, and you ought to run them on your improvement machine too. A few groups have inclusion objectives for their unit tests and will bomb a form on the off chance that the unit tests aren't sufficiently broad.
Engineers likewise work with mock articles and virtualized administrations to ensure their units can be tried freely. Assuming your unit tests fall flat, fix them prior to letting another person utilize your code. If under any circumstance you can't fix them at this moment, let the other individual in on what has fizzled, so it won't come as a shock when they run over the issue.
5. Single-client execution testing A few groups have burden and execution testing heated into their ceaseless mix cycle and run load tests when code is checked in. This is especially valid for back-end code. In any case, designers ought to likewise be taking a gander at single-client execution toward the front and ensuring the product is responsive when they are just utilizing the framework. On the off chance that it requires in excess of a couple of moments to show a site page taken from a neighborhood or copied (and in this manner responsive) web server, figure out what client-side code is pumping the brakes and fix it before you let another person see it.
#software testing training#automation testing training in ahmedabad#selenium training in ahmedabad#unicodetechnologies
0 notes
Text
UNC5812: Russian Group “Civil Defense” Malware Campaign

Russian Hybrid Espionage and Influence Campaign Seek to Deliver Anti-Mobilization Narratives and Compromised Ukrainian Military Recruits
In September 2024, the Google Threat Intelligence Group which is made up of Mandiant and Google’s Threat Analysis Group (TAG) discovered UNC5812, a suspected Russian hybrid espionage and influence campaign that used the Telegram persona “Civil Defense” to distribute malware for Windows and Android. According to their claims, “Civil Defense” offers free software applications that let prospective conscripts see and share crowdsourced locations of Ukrainian military recruiters.
These apps provide the victim with a decoy mapping application it track as SUNSPINNER combined with an OS system-specific commodity malware version if they are installed with Google Play Protect turned off. UNC5812 is actively involved in influence activity, disseminating narratives, and requesting content aimed at undermining support for Ukraine’s mobilization efforts, in addition to using its website and Telegram channel to distribute malware.
Targeting Telegram Users
Both the website civildefense[.]com.ua and the actor-controlled Telegram channel @civildefense_com_ua are used by UNC5812 to distribute malware. In April 2024, the related website was registered; however, the Telegram channel was not established until early September 2024, which it believes marks the full operationalization of UNC5812’s campaign. It estimates that UNC5812 is probably buying promoted posts in reputable, well-established Ukrainian-language Telegram channels to direct potential victims to these actor-controlled sites.
A reputable missile alerts Telegram channel with over 80,000 followers was seen advertising the “Civil Defense” website and channel to its members on September 18, 2024.
As recently as October 8th, another Ukrainian-language news outlet promoted Civil Defense’s articles, suggesting the campaign is likely still actively looking for new Ukrainian-language groups for focused interaction.
Channels that have pushed “Civil Defense” posts highlight the opportunity to contact their administrations about sponsorship opportunities. It believes that to expand the operation’s scope, UNC5812 is most likely approaching the appropriate legal channels through this vector.
The campaign’s ultimate goal is to direct victims to the “Civil Defense” website, which is under UNC5812’s control and promotes a number of software applications for various operating systems. These apps download different commodity malware families when they are installed.
The website provides a PHP downloader for Windows users called Pronsis Loader, which is publicly recorded and compiled into Java Virtual Machine (JVM) bytecode using the open source JPHP project. When Prosnis Loader is run, it starts a complicated malware delivery chain that eventually delivers SUNSPINNER and PURESTEALER, a commodity information stealer.
The malicious APK file aims to install a version of the commercially available Android backdoor CRAXSRAT on Android users. This payload was seen in a variety of forms, including one that had SUNSPINNER in addition to the CRAXSRAT payload.
Although support for macOS and iPhones is also advertised on the Civil Defense website, at the time of study, only Windows and Android payloads were accessible.
Notably, the Civil Defense website also uses an unusual kind of social engineering to allay user concerns about APK delivery outside of the App Store and provide justification for the high level of permissions needed to install CRAXSRAT.
In an attempt to “protect the anonymity and security” of its users, the website’s FAQ offers a strained defense for the Android application‘s hosting outside of the App Store, pointing users to a set of video instructions that go along with it.
After the malware is successfully installed, the Ukrainian-language video instructions show victims how to manually allow all permissions and disable Google Play Protect, a program that checks apps for malicious functionality when they are installed on Android devices.
Image credit to Google Cloud
Operation of Anti-Mobilization Influence
UNC5812 is participating in influence operations to thwart Ukraine’s broader mobilization and military recruitment initiatives in addition to its attempts to spread malware and obtain access to the devices of possible military recruits. Videos of “unfair actions from territorial recruitment centers,” which it believes likely to be meant for follow-on exposure to support UNC5812’s anti-mobilization narratives and disparage the Ukrainian military, are actively sought out on the group’s Telegram channel by users and subscribers. An attacker-controlled https://t[.]me/UAcivildefenseUA account is used to establish a chat thread when the “Send Material” (Ukrainian: Нaдіслати матеріал) button is clicked.
Additionally, there are anti-mobilization images and content in Ukrainian on the Civil Defense website, including a news section highlighting alleged instances of unfair mobilization tactics.
Cross-posted anti-mobilization propaganda on the group’s Telegram channel and website seems to come from larger pro-Russian social media networks. In at least one case, the Russian Embassy posted a video on South Africa’s X account a day after UNC5812 shared it.
Malware Analysis
From the group’s website, civildefense[.]com[.]ua, UNC5812 runs two distinct malware delivery chains for Android and Windows devices. The parallel release of a decoy mapping program known as SUNSPINNER, which shows users a map that represents the alleged locations of Ukrainian military recruits from an actor-controlled command-and-control (C2) server, is a commonality among these several delivery chains.
SUNSPINNER
The fake graphical user interface (GUI) program SUNSPINNER (MD5: 4ca65a7efe2e4502e2031548ae588cb8) was created with the Flutter framework and compiled for both the Windows and Android operating systems. The application’s GUI renders the map markers that SUNSPINNER requests fromhttp://h315225216.nichost[.]ru/itmo2020/Student/map_markers/mainurl.json, followed by a request for map markers from https://fu-laravel.onrender[.]com/api/markers that are then rendered on the app’s GUI.
According to the features listed on the Civil Defense website, SUNSPINNER can show crowdsourced markers that include the locations of Ukrainian military recruiters, and users can even add their own markers. Nevertheless, the presented map does not seem to contain any authentic user inputs, even though it has the minimal functionality needed for people to register and add markers. The same user added every marker found in the JSON file extracted from SUNSPINNER’s C2 infrastructure on the same day.
Pronsis Loader to PURESTEALER in Windows
CivilDefense.exe (MD5: 7ef871a86d076dac67c2036d1bb24c39), the Windows payload obtained from the Civil Defense website, is a customized version of Pronsis Loader, a newly identified commodity malware that is largely being used by threat actors with financial motivations.
The second-stage downloader “civildefensestarter.exe” (MD5: d36d303d2954cb4309d34c613747ce58) and the decoy SUNSPINNER binary are both retrieved by Pronsis Loader. This starts a multi-stage delivery chain that uses a series of self-extracting archives and finally runs PURESTEALER on the victim device. The open-source JPHP project is used to compile the PHP-written second-stage downloader into Java Virtual Machine (JVM) bytecode, which is subsequently created as a Windows executable file. The CivilDefense installer runs this file automatically.
PURESTEALER is the last payload (MD5: b3cf993d918c2c61c7138b4b8a98b6bf), a highly disguised commodity infostealer built in.NET, is intended to steal cryptocurrency wallets, chat apps, email clients, and browser data like passwords and cookies. “Pure Coder Team” is the company that sells PURESTEALER. Monthly subscriptions cost $150, while lifetime licenses cost $699.
CraxsRAT Android
A variation of the commercially available Android backdoor CRAXSRAT is the Android Package (APK) file “CivilDefensse.apk” (MD5: 31cdae71f21e1fad7581b5f305a9d185) that was downloaded from the Civil Defense website. File management, SMS management, contact and credential harvesting, and a number of location, audio, and keystroke monitoring features are all features that CRAXSRAT offers that are common to a conventional Android backdoor. It is also sold on underground forums, just like PURESTEALER.
At the time of investigation, the Android sample that was being circulated merely showed a splash screen with the “Civil Defense” logo. Nevertheless, it was discovered that the identical SUNSPINNER decoy application was present in another identified sample (MD5: aab597cdc5bc02f6c9d0d36ddeb7e624) as it was in the Windows delivery chain. This version downloads the CRAXSRAT payload from http://h315225216.nichost[.]ru/itmo2020/Student/map_markers/CivilDefense.apk after requesting the user’s Android REQUEST_INSTALL_PACKAGES permission.
Safeguarding Users
Google also keeps an eye out for Android spyware, and it implements and maintains Google Play Protect’s safeguards both inside and outside of Google Play, scanning devices for potentially dangerous apps from any source. Notably, the Civil Defense website of UNC5812 had social engineering content and comprehensive video instructions that directly instructed the intended user to disable Google Play Protect and manually activate the Android permissions needed for CRAXSRAT to operate. By alerting users before they access risky websites, Safe Browsing also protects Chrome users on Android. Google Play is protected by app scanning infrastructure, which also enables Verify Apps to further secure consumers who install apps from sources other than Google Play.
The national authorities of Ukraine have also been informed of its discoveries, and they have taken steps to limit the campaign’s reach by preventing the actor-controlled “Civil Defense” website from being resolved nationwide.
In brief
Following modifications to Ukraine’s national mobilization rules in 2024, Russian threat actors have increased their operational involvement in Ukraine, as seen by UNC5812’s hybrid espionage and information operation targeting prospective Ukrainian military recruits. The introduction of Ukraine’s national digital military ID, which is designed to handle the information of people due for military duty and increase recruitment, has specifically led to an increase in the targeting of prospective military recruits. It also continues to see consistent efforts by pro-Russian influence actors to spread messaging that undermines Ukraine’s mobilization drive and sows popular mistrust in the officials conducting it, in line with studies from EUvsDisinfo.
From a tradecraft standpoint, UNC5812‘s campaign exemplifies Russia’s focus on using its cyber capabilities to achieve cognitive effect and emphasizes the significant role messaging apps continue to play in the spread of malware and other cyber aspects of Russia’s war in Ukraine. It concludes that Telegram will very certainly continue to be a major conduit for cyber-enabled activity for a variety of Russian-affiliated espionage and influence operations as long as it remains a vital information source during the conflict.
Read more on Govindhtech.com
#UNC5812#civildefense#cicildefensewebsite#google#googlecloud#CRAXSRAT#CraxsRATAndroid#PURESTEALER#PronsisLoader#SUNSPINNER#govindhtech#news#TechNews#Technology#technologynews#technologytrends
0 notes
Text
What is Java Programming Language?
Java is a widely-used, high-level programming language that has become a cornerstone in the world of software development. Created by Sun Microsystems in 1995, Java is known for its versatility, platform independence, and object-oriented approach. This article explores the key features, history, and applications of Java, highlighting why it remains a popular choice among developers today. If you’re interested in enhancing your skills, Java training in Pune offers excellent opportunities for hands-on learning.
History of Java
Java was originally developed by James Gosling and his team at Sun Microsystems, initially as a project called “Green Project.” The primary aim was to create a language that could run on various devices, including embedded systems. The first public release, Java 1.0, was introduced in 1995, and since then, Java has evolved through several versions, with each iteration introducing new features and enhancements. In 2010, Oracle Corporation acquired Sun Microsystems and took over the development and maintenance of Java.
Key Features of Java
1. Platform Independence
One of Java’s most significant advantages is its platform independence, achieved through the Java Virtual Machine (JVM). Java programs are compiled into bytecode, which can run on any device equipped with a JVM, allowing developers to write code once and run it anywhere (WORA principle). This makes Java highly versatile for building cross-platform applications, a valuable skill that can be gained through Java training in Pune.
2. Object-Oriented Programming (OOP)
Java is inherently an object-oriented language, meaning it emphasizes concepts such as encapsulation, inheritance, and polymorphism. This allows for modular and reusable code, making it easier to develop and maintain complex applications.
3. Automatic Memory Management
Java includes an automatic garbage collection system, which helps manage memory by automatically freeing up space occupied by objects that are no longer in use. This reduces memory leaks and improves application performance.
4. Rich Standard Library
Java offers a vast standard library that provides pre-written classes and methods for various tasks, including data manipulation, networking, GUI development, and more. This extensive library simplifies the development process and reduces the need for writing code from scratch.
5. Multithreading Support
Java supports multithreading, enabling developers to write programs that can perform multiple tasks simultaneously. This is particularly useful for applications that require high performance, such as real-time systems and games.
6. Robustness and Security
Java is designed to be robust and secure, with strong memory management and exception handling features. The language’s syntax helps eliminate common programming errors, and its security features allow for the development of safe applications, particularly important in networked environments.
Applications of Java
Java’s versatility has led to its widespread use across various domains, including:
1. Web Development
Java is commonly used in server-side web development through frameworks like Spring and JavaServer Faces (JSF). Its ability to handle high traffic and complex transactions makes it ideal for building robust web applications.
2. Mobile Development
Android, the world’s most popular mobile operating system, is primarily built using Java. Developers use Java to create Android applications, taking advantage of its extensive libraries and community support.
3. Enterprise Applications
Many large-scale enterprise applications are developed using Java due to its scalability, reliability, and security features. Frameworks like Java EE (Enterprise Edition) facilitate the development of complex business solutions.
4. Scientific and Research Applications
Java is often used in scientific computing and research due to its portability and powerful libraries for numerical computing and data analysis.
5. Game Development
While not as common as C++ in game development, Java is still used to create games, particularly for Android and desktop platforms. Libraries like LibGDX provide tools for developing 2D and 3D games.
Conclusion
Java programming language stands out as a powerful, versatile, and reliable tool for developers worldwide. Its rich features, platform independence, and robust community support have made it a preferred choice for a wide range of applications, from web and mobile development to enterprise solutions and scientific research. If you’re looking to boost your career in this field, Java training in Pune can provide you with the necessary skills and hands-on experience to excel. As technology continues to evolve, Java remains a crucial player in the software development landscape, ensuring its relevance for years to come. Whether you are a beginner or an experienced programmer, learning Java can provide you with valuable skills that are highly sought after in the tech industry.
0 notes
Text
Spring Boot vs Quarkus: A Comparative Analysis for Modern Java Development

Liberating industry with Java
Java has been a great asset for developers in elevating the industry to higher standards. Java has a lot of built-in libraries and frameworks, which makes it easy for developers to build an application and website. It is a set of built-in codes used by developers for building applications on the web. These frameworks possess functions and classes that control hardware, input processes, and communication with the system applications. The main purpose of preferring Java frameworks in development is that they provide a consistent design pattern and structure for creating applications. Moreover, this improves the code maintainability. This code consistency makes it easy for the developers to understand and change the code, neglecting bugs and errors. In Java, multiple frameworks are used, such as SpringBoot, Quarkus, MicroNaut, etc. In this blog, we will learn more about the differences between SpringBoot and Quarkus. Also, we will drive through the advantages of using it in the development process.
Boosting development with SpringBoot and Quarkus:
SpringBoot is an open-source framework that supports Java, Groovy, Kotlin, and JIT compilation, which makes it very much easier to create, configure, and run microservice web applications. It is a part of the Spring framework that allows developers to utilize the Spring framework features. This makes it easy for the developers to expand and construct spring applications. It reduces the code length and also increases the production speed. This is possible due to the automated configuration of the application built on the Java annotations.
Quarkus is also an open-source Java framework that supports Scala, Java, and Kotlin. The major purpose of preferring Quarkus is to simplify the development and deployment process of Java applications in containers like Kubernetes and Docker. It is also used for developing microservice Java applications with a minimal consumption of resources. It is very easy to use and necessarily less demanding on hardware resources to run applications.
Unbinding the differences between SpringBoot and Quarkus
Quarkus will be performing better because of its Kubernetes native framework, which is designed particularly to run in a containerized environment. Moreover, it uses an Ahead-of-time (AOT) compiler for pre-compiling the Java bytecode into native code. This results in faster start-up time and lower usage of memory. But, on the other hand, SpringBoot is a traditional Java framework that uses the Java Virtual Machine (JVM) to run applications. SpringBoot can also run on the containerized environment but it doesn’t have the same performance level optimization as Quarkus.
The greatest difference between Quarkus and SpringBoot is the size of the frameworks. SpringBoot is a well-established and feature-rich framework, but it comes with vast dependencies, which increases the application size. On the other hand, Quarkus is a new framework that has a much smaller runtime footprint when compared with SpringBoot. It also has a feature for optimizing the size of the application. SpringBoot has been in the industry for a long period of time, it has a larger community and a vast ecosystem of libraries and plugins. Quarkus is a relatively new framework in the industry, but it is attracting a lot of developers to its side. The community of Quarkus is small when it is compared with SpringBoot.
Conclusion
From this blog, we can understand the impact of Java and its crucial role in the development of applications. SpringBoot and Quarkus has made quite an impact in developing applications and websites in an unique way. Both of these frameworks have been a great asset for most developers to create an interactive application. Preferring the perfect Java application development company also plays an important role in a company’s growth.
Pattem Digital, a leading Java app development company that helps in meeting the current business needs and demands. Our talented team of developers guides our clients throughout the project. We work on the latest technologies and provide the best results meeting the current market trends.
0 notes
Text
Why Python? Exploring the Language's Core Aims and Benefits
Introduction
Python, a versatile and widely-admired programming language, stands out for its simplicity, readability, and vast array of applications. Understanding the core aims and philosophy behind Python is crucial for grasping its significance and widespread adoption. In this comprehensive guide, we will delve into Python's main objectives and explore how they contribute to its popularity and versatility.

With the helpful support from the Learn Python Course in Hyderabad, learning Python becomes more enjoyable regardless of your experience level or reasons for transitioning from another programming language.
Simplicity and Clarity
Python's primary objective is to provide a programming language that is easy to read, write, and comprehend. Guido van Rossum, the mastermind behind Python, envisioned a language with a clean and straightforward syntax. This emphasis on simplicity is evident in Python's minimalistic design and intuitive structure. By prioritizing readability, Python enables developers to express complex ideas with clarity and brevity, making it an ideal choice for both beginners and seasoned programmers.
Versatility and Adaptability
Another key aim of Python is versatility. Python supports multiple programming paradigms, including procedural, object-oriented, and functional programming. This versatility allows developers to tackle a wide range of tasks, from web development and data analysis to artificial intelligence and scientific computing. With its extensive standard library and a vast ecosystem of third-party packages, Python provides the tools and resources needed to address diverse challenges across various domains.
High-Level Abstraction
Python aims to be a high-level language, abstracting away the complexities of low-level hardware operations. This abstraction enables developers to focus on solving problems without getting bogged down in the intricacies of memory management or bytecode manipulation. By providing a high-level interface, Python facilitates rapid application development and simplifies the process of translating ideas into code.
Accessibility and Inclusivity
Python strives to be accessible and inclusive, welcoming developers from all backgrounds and skill levels. Its beginner-friendly syntax and extensive documentation make it an ideal choice for educational purposes. Many educational institutions use Python as the introductory programming language due to its simplicity and versatility. Additionally, Python's supportive community and collaborative development model ensure that resources and assistance are readily available to newcomers.
Enrolling in the Best Python Certification Online can help people realise Python's full potential and gain a deeper understanding of its complexities.

Community-Driven Development
Python's development is guided by a vibrant and collaborative community. The Python Software Foundation (PSF) oversees the development of the language, fostering an environment of openness and inclusivity. The community-driven approach encourages contributions from developers worldwide, leading to continuous improvement and innovation. Whether through code contributions, educational initiatives, or community events, Python's community plays a pivotal role in shaping the language's evolution.
Continuous Learning and Growth
Python's journey is one of continuous learning and growth. The language evolves through a collaborative process, with developers proposing and discussing new features and enhancements through the Python Enhancement Proposal (PEP) system. Staying updated with the latest trends and best practices is essential for developers, and Python's vast ecosystem of resources provides ample opportunities for ongoing learning and skill development.
Conclusion
In conclusion, Python's core aims revolve around simplicity, versatility, accessibility, and community-driven development. By prioritizing readability, abstraction, and inclusivity, Python has become one of the most popular and widely-used programming languages today. Whether you're a beginner learning to code or an experienced developer building complex systems, Python's aims align with providing a powerful, efficient, and enjoyable programming experience.
0 notes
Text
know Python.
A Look into the Python Programming Language
Introduction
Python has become a dominant force in the world of programming. This versatile language is lauded for its readability, extensive libraries, and vast applications. This article delves into the history of Python, explores the reasons why it's a valuable skill to learn, and examines its impact on the world today and tomorrow.
History
Guido van Rossum, a Dutch programmer, designed Python in the late 1980s. His goal was to create a language that was both powerful and easy to learn, emphasizing code readability. Inspired by the humor group Monty Python, he named the language after them. Python's first official release came in 1991, and it has grown steadily in popularity ever since.

Why Learn Python?
There are numerous reasons why Python is a great language to pick up. Here are a few key points:
Readability: Python's syntax is clear and concise, resembling natural language. This makes it easier to learn and maintain code compared to languages with complex syntax.
Versatility: Python is a general-purpose language, meaning it can be used for a wide range of tasks. From web development and data science to machine learning and automation, Python excels in numerous domains.
Extensive Libraries: The Python ecosystem boasts a vast collection of libraries and frameworks. These pre-written tools provide users with functionalities for specific tasks, saving development time.
Large Community: Python has a vibrant and supportive online community. This means there's an abundance of resources and help available for learners and experienced programmers alike.
Python's Global Reach
Python's influence extends far and wide. Here are some examples of how countries around the world are leveraging Python's power:
The United States: Tech giants like Google, Facebook, and Netflix utilize Python for various purposes, including web development, data analysis, and machine learning.
India: Python is a popular choice for software development and data science in India, a country experiencing a major tech boom.
China: China's tech sector is also embracing Python, particularly in areas like artificial intelligence and scientific computing.
The Future of Python
With its adaptability and ease of use, Python is well-positioned for a prominent role in the future of technology. Here are some potential areas where Python might play a key role:
Artificial Intelligence (AI): Python's established libraries like TensorFlow and PyTorch make it a go-to language for developing AI applications.
Data Science and Machine Learning: Python's data manipulation and analysis capabilities will continue to be crucial for these rapidly evolving fields.
Internet of Things (IoT): As more devices become interconnected, Python's potential for scripting and automating tasks within IoT systems will be increasingly valuable.
Recent Advancements with Python
Python has been instrumental in the development of several cutting-edge technologies. A few notable examples include:
Self-Driving Cars: Python plays a role in developing the control systems and machine learning algorithms used in self-driving cars.
Facial Recognition Software: Python libraries are used to create and train facial recognition systems.
Natural Language Processing (NLP): Python is a popular choice for developing NLP applications, such as chatbots and machine translation tools.

Working Structure
Source Code:
You write Python code in plain text files with the .py extension. This code is human-readable, resembling natural language for easy understanding and modification.
Compilation (Bytecode):
Unlike some languages that directly translate to machine code, Python utilizes an intermediate step. The Python compiler converts your source code into bytecode, a lower-level representation. Bytecode files typically have the .pyc or .pyo extension.
Python Virtual Machine (PVM):
The bytecode can't be directly executed by your computer's hardware. The Python Virtual Machine (PVM) acts as an interpreter, reading and executing the bytecode instructions. The PVM manages memory allocation and provides an environment for your code to run.
Libraries and Modules:
Python boasts a rich collection of pre-written code called libraries and modules. These modules contain functions, classes, and variables that provide functionalities for various tasks. You can import these modules into your code to leverage their capabilities, saving development time.
Execution:
When you run a Python script, the interpreter reads the bytecode line by line. It executes the instructions, interacting with libraries and modules as needed. The output of your code is then displayed on the console or used within the program itself.
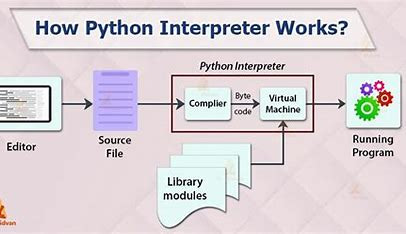
Conclusion
Python's impact on the technological landscape is undeniable. Its readability, vast ecosystem of libraries, and diverse applications make it a language well worth learning. As technology continues to evolve, Python is sure to remain a powerful tool that shapes the future.

0 notes
Text
“Understanding Compiler Variants: An In-Depth Analysis of Various Compiler Types”
Java depends on dedicated programs to convert human-readable code into machine-understandable language. This transformation results in bytecode, a series of 0s and 1s that computers can interpret. The widely acknowledged primary Java compiler, javac, is particularly familiar to newcomers in the field. With the aid of these compilers, we can run Java programs on a variety of platforms, including Windows, Linux, and macOS. While there is flexibility in selecting a compiler, having knowledge about the availability of different compiler options can be advantageous.

Java Compiler:
• Compilers act as an intermediary between human-readable language and machine-interpretable code.
• When dealing with Java, the compiler processes the .java file, converting each class into a matching .class file that remains independent of any particular Operating System.
• As a result, Java is recognized as a platform-agnostic language. The javac compiler is tasked with converting our Java code into machine language, which is commonly referred to as bytecode.
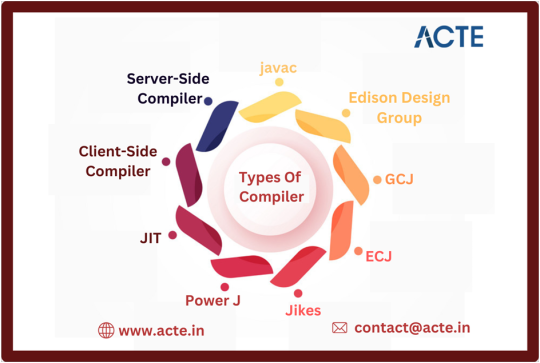
1. Javac:
· Javac stands as the standard Java compiler, primarily serving the purpose of translating Java source code into bytecode.
· It plays a pivotal role in the Java development process, enabling the execution of Java programs across various platforms.
· Javac commonly integrates with popular Integrated Development Environments (IDEs) such as Eclipse and IntelliJ IDEA.
2. Edison Design Group:
· The Edison Design Group (EDG) compiler is renowned for its preprocessing and parsing capabilities.
· It aids in optimizing code and enhancing overall software performance.
· Although it may not be as extensively integrated into IDEs as Javac, it remains a valuable tool for specific tasks related to code refinement and enhancement.
3. GCJ:
· The GNU Compiler for Java (GCJ) is a versatile compiler that not only handles Java source code but also supports other programming languages like C, C++, Fortran, and Pascal.
· While its support is confined to UNIX, GCJ serves as a useful option for developers seeking a free and multi-purpose compiler for their projects.
4. ECJ:
· The Eclipse Compiler for Java (ECJ) is seamlessly integrated with the Eclipse IDE, providing developers with a comprehensive environment for Java development.
· ECJ stands out for its distinctive approach to identifying and managing compile-time errors, allowing for quicker debugging and development cycles within the Eclipse IDE.
5. Jikes:
· Jikes, an open-source Java compiler developed at IBM, is renowned for its high-performance capabilities, especially in managing extensive projects.
· However, it lacks support for newer Java versions, making it more suitable for legacy systems operating on older versions of the Java Development Kit (JDK).
6. Power J:
· Power J is a compiler created at Sybase, now under the ownership of SAP.
· Tailored for the Windows platform, it provides developers with an efficient means to compile and execute Java code within specific development environments.
7. JIT:
· The Just-In-Time (JIT) compiler constitutes an integral component of the Java Runtime Environment (JRE), responsible for optimizing Java application performance during runtime.
· It dynamically compiles segments of bytecode into native machine code, resulting in improved execution speed and overall performance.
8. Client-Side Compilers:
· The client-side compiler (C1) concentrates on reducing the startup time of applications operating under limited resources.
· By specifically optimizing the code for client-side environments, this compiler ensures that Java applications can launch swiftly and operate efficiently, even on systems with restricted capabilities.
9. Server-Side Java Compilers:
· Server-side compilers (C2) are specifically engineered for enterprise-level applications, offering advanced optimization techniques and algorithms to enhance the performance of Java applications operating within server environments.
· These compilers facilitate the execution of intricate operations and ensure that server-side applications can effectively manage substantial workloads.
If you are looking to bolster your Java expertise, you can take advantage of the comprehensive Java learning programs offered by ACTE Technologies. Achieving mastery in Java demands consistent dedication to learning, regular practice, and unwavering commitment. ACTE Technologies provides an array of Java learning courses, complete with certifications and support for job placements, enabling you to acquire proficiency in Java. By maintaining a persistent learning routine, you can develop a strong grasp of Java and leverage its capabilities to create a wide range of applications and projects. Should you have any more questions or require further discussion on related topics, please feel free to get in touch. Your interest and support are greatly valued and inspire me to share additional valuable insights on Java.
0 notes
Text
Unlocking Insights: Text Analytics in NLP with Azure - Ansi ByteCode LLP
Discover how Text Analytics in NLP with Azure. Learn tokenization, sentiment analysis, entity recognition to analyze text efficiently. Please visit:- https://ansibytecode.com/text-analytics-in-nlp-with-azure/
0 notes
Text
Java Virtual Machine
Learn Java Certification Course, Java Virtual Machine (JVM) is a crucial component of the Java ecosystem, responsible for executing Java bytecode. Understanding how Java code is executed by the JVM is essential for optimizing performance and troubleshooting issues.
Compilation and Bytecode: Java source code is first compiled into platform-independent bytecode by the Java Compiler (javac). This bytecode is a set of instructions that the JVM can understand.
Class Loading: When you run a Java application, the JVM loads classes as needed. The class loader loads classes from the classpath and verifies their bytecode for security.
Just-In-Time (JIT) Compilation: The JVM employs a JIT compiler to convert bytecode into native machine code for the specific hardware it's running on. This step improves execution speed by avoiding interpretation of bytecode.
Execution: The JVM executes the native machine code. During execution, it manages memory, garbage collection, and thread synchronization, ensuring the program's integrity and security.
HotSpot Optimization: The JVM continuously optimizes code for better performance using techniques like inlining, loop unrolling, and escape analysis. It identifies "hot spots" or frequently executed code and applies optimizations selectively.
Garbage Collection: JVM handles memory management, automatically freeing memory occupied by objects that are no longer referenced. Different garbage collection algorithms (e.g., G1, CMS) can be selected based on application requirements.
Exception Handling: The JVM manages exceptions and provides a mechanism for developers to handle them through try-catch blocks.
Native Interface: Java applications can interact with native code through the Java Native Interface (JNI). The JVM facilitates this interaction by allowing Java code to call native methods written in languages like C/C++.
Monitoring and Profiling: JVM provides tools like JVisualVM and tools provided by vendors like JProfiler for monitoring and profiling Java applications, helping developers identify bottlenecks and optimize performance.
Understanding how the JVM executes Java code is essential for diagnosing and resolving performance bottlenecks, memory issues, and other runtime problems. Profiling tools, JVM tuning, and knowledge of JVM internals are valuable skills for Java developers aiming to create efficient and reliable applications.
0 notes
Text
PHP Tools to Use in 2023

As technology evolves, so do the tools that support it. PHP, a popular scripting language, continues to be a cornerstone of web development. With each passing year, new tools emerge to enhance PHP development processes. In this guide, we delve into the essential PHP tools to use in 2023, providing developers with insights to streamline their coding journey. PHP Tools to Use in 2023 The year 2023 brings a host of innovative PHP tools that cater to developers' needs. These tools enhance productivity, code quality, and collaboration, making PHP development more efficient than ever. Here's a curated list of PHP tools that deserve your attention: 1. Laravel Framework Description: Laravel remains a powerful PHP framework known for its elegant syntax and robust features. It simplifies common tasks like routing, caching, and authentication, enabling developers to focus on building outstanding applications. Usage: Use Laravel to create web applications quickly and efficiently while benefiting from its expressive syntax and comprehensive documentation. 2. Symfony Components Description: Symfony offers a collection of reusable PHP components that simplify complex tasks in web development. From HTTP handling to form creation, Symfony components provide a foundation for building scalable applications. Usage: Integrate Symfony components into your projects to streamline development and leverage pre-built solutions for various tasks. 3. Xdebug Description: Debugging is an essential aspect of coding. Xdebug is a powerful tool that helps developers identify and fix issues by providing detailed insights into code execution, variable values, and stack traces. Usage: Integrate Xdebug into your development environment to enhance the debugging process and save time in identifying and resolving errors. 4. Composer Description: Dependency management is crucial for PHP projects. Composer is a package manager that simplifies the process of installing, updating, and managing external libraries and dependencies. Usage: Utilize Composer to manage dependencies efficiently and ensure your projects are well-organized and up-to-date. 5. PHPStan Description: Code quality is paramount. PHPStan is a static analysis tool that scans your codebase for potential issues, type errors, and bugs, allowing you to catch problems early in the development cycle. Usage: Incorporate PHPStan into your workflow to improve code quality, minimize errors, and ensure robust application performance. Exploring PHP Tools for Specific Needs While the tools mentioned above cover a broad spectrum of PHP development, specific needs require specialized solutions. Let's explore some additional PHP tools tailored to particular tasks: 1. Database Management: phpMyAdmin Description: phpMyAdmin is a popular tool for managing MySQL databases through a user-friendly web interface. It simplifies tasks like database creation, querying, and data manipulation. Usage: Employ phpMyAdmin to efficiently manage your MySQL databases and execute SQL queries without the need for complex command-line operations. 2. Code Versioning: Git and GitHub Description: Git, coupled with platforms like GitHub, enables efficient code versioning and collaboration among developers. It helps track changes, merge code, and manage project histories. Usage: Embrace Git and GitHub to foster collaboration, track code changes, and maintain a comprehensive history of your project's development. 3. Performance Optimization: PHP OPcache Description: PHP OPcache is a built-in caching engine that improves the performance of PHP applications by storing precompiled script bytecode in memory, reducing the need for repetitive compilation. Usage: Enable PHP OPcache to enhance the speed and efficiency of your PHP applications, resulting in faster response times and reduced server load. FAQs About PHP Tools in 2023 Q: What is PHP used for?A: PHP is a scripting language primarily used for web development to create dynamic and interactive web pages. Q: Are these tools suitable for beginners?A: Yes, many of these tools offer comprehensive documentation and user-friendly interfaces, making them accessible to developers of all levels. Q: Can I use these tools on different operating systems?A: Yes, most PHP tools are cross-platform and can be used on various operating systems, including Windows, macOS, and Linux. Q: Are these tools free to use?A: Many of the tools mentioned are open-source and available for free. However, some may offer premium features or support packages. Q: Do I need to use all of these tools?A: The selection of tools depends on your specific project requirements. Choose the tools that align with your development needs. Q: How do I stay updated with the latest PHP tools?A: Follow official websites, communities, and forums related to PHP development to stay informed about the latest tools and updates. Conclusion: Elevate Your PHP Development with Cutting-Edge Tools In the realm of PHP development, the tools you choose significantly impact your efficiency, code quality, and overall development experience. By embracing the top PHP tools of 2023, you position yourself to create exceptional applications, streamline workflows, and collaborate seamlessly with other developers. Stay ahead of the curve by integrating these tools into your development toolkit and witness the transformation in your PHP coding journey. Read the full article
0 notes