#computer_virus
Explore tagged Tumblr posts
Text
pip install computer_virus
pip install malware --upgrade
8 notes
·
View notes
Text
دليلك الشامل لمعرفة: فيروسات الحاسوب
طرق انتقال الفيروس الي الحاسوب ( الطرق الاكثر وضوحاً ):
المواقع الاباحية
الدخول علي الروابط الاعلانية المشبوهة
توصيل ذاكرة تخزينية علي حاسوبك
الدخول علي رابط مرسل في رسالة بريدية لك
تحميل البرامج والالعاب من مواقع غير موثوقة
المصدر: https://techgena.com/computer-virus/
0 notes
Photo

Save your system from malware attack. Hire expert to make your system virus free before it is too late. iTech Xpress offers comprehensive security services including virus removal. With all of the recent news about the moneypak virus and the extortion and the debacle over the risks that Windows XP opened up, the need for computer security has never been more necessary. Here save our number: (626) 777-4747 Website: https://itechxpressinc.com/virus-malware-removal/
0 notes
Photo

Computer virus by Geek4lyf https://www.reddit.com/r/ProgrammerHumor/comments/9y49jk/computer_virus/?utm_source=ifttt
15 notes
·
View notes
Text
Week07 - “Something Awesome” Final Update
In this final update for my “Something Awesome” project I will be going over three different ways (Macros, DDE, Fake Website) of attacking the target through phishing emails. Within these I will give a brief description of the exploit, an example of the exploit being used in the real-world, and my own “less malicious” version of the exploit showing how it could be used.
Macros
A macro is a series of commands and instructions that you group together as a single command to accomplish a task automatically. They are often used to automate frequently used tasks. However macros can also be used maliciously and is a common (yet easy to avoid) way of transmitting malware via phishing scams. The key to successful macro scams is in the social engineering aspect of the phish.
Real-world example:
The Melissa Virus (https://en.wikipedia.org/wiki/Melissa_(computer_virus))
The phishing email came with a message like: “Here is that document you asked for, don't show it to anybody else." Once opened, the virus replicated itself and sent the same email out to the top 50 people in the recipient's Outlook e-mail address book. While it did not destroy files or other resources, Melissa disabled email systems due to the ripple effect of spam email, including Microsoft who shut down incoming e-mail until the virus was reigned in.
Here is the virus code for anyone interested: https://packetstormsecurity.com/files/12131/melissa.macro.virus.txt.html
Writing my own macro based “malware”:
1. Create a new macro in the macro menu inside word
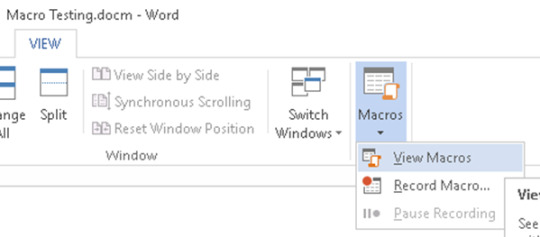
2. Write your macro
runs when document is opened
executes calc.exe
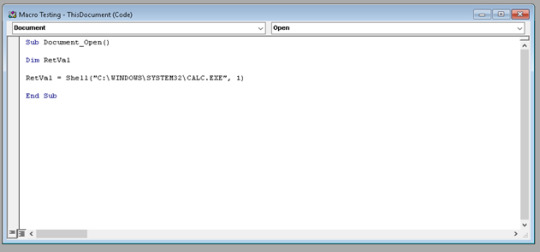
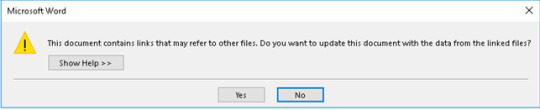
3. When someone opens a document with macros they will get this warning (relies on effective social engineering in the phishing email to deceive the target into clicking “Yes”).
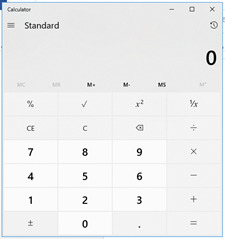
4. Windows Calculator is opened by macro.
DDE
Microsoft’s Dynamic Data Exchange (DDE) is a protocol designed to allow the transportation of data between MS Office applications. DDE allows the execution of embedded code once a victim opens such a file, without the authorisation request associated with macros (won’t get picked up by anti-virus).
Note: this exploit was rendered somewhat useless when Microsoft released a patch following the exploit https://docs.microsoft.com/en-us/openspecs/office_standards/ms-oi29500/4fe6d033-f0d4-4d73-ac81-a7128522c5ff
However not all versions of Word received the update and users can still re-enable DDE. Since many people still rely on legacy applications, an attacker may still be able to exploit DDE in Word (also in Excel and Outlook).
Real-world Example:
Both these examples highlight how DDE has been used to maliciously phish in the real world. However it also shows how easy it is to avoid being infected by DDE exploits, as you have to click through at least 2 warning screens before anything malicious can occur like macros (though many people do click through warnings without reading them).
https://isc.sans.edu/forums/diary/Necurs+Botnet+malspam+pushes+Locky+using+DDE+attack/22946/?source=post_page---------------------------
https://isc.sans.edu/forums/diary/Hancitor+malspam+uses+DDE+attack/22936/?source=post_page---------------------------
Writing my own DDE Exploit:
1. Insert field
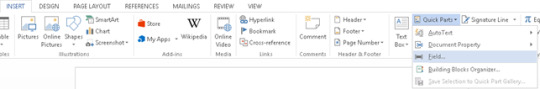
...
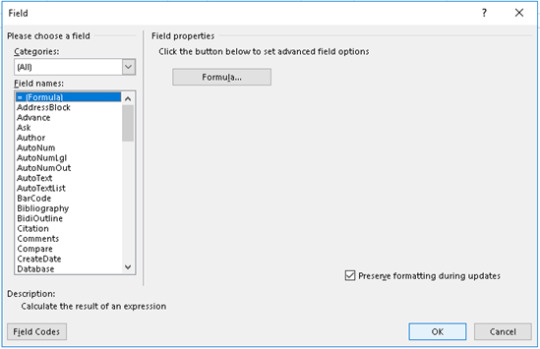
2. Write desired code
This executes calc.exe again
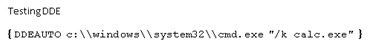
3. Target gets two prompts (again good social engineering is needed)
Second prompt would scare off many targets but can be hidden as shown here: https://twitter.com/ryhanson/status/917820530975223809?lang=en
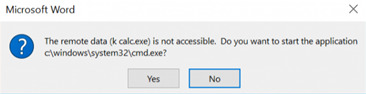
4. Calculator is launched

Fake login page
Fake login pages are a classic example of how hackers steal their targets data and is a very common phishing method. The hacker will either attach an html document or will make their own website with a spoofed url similar to the real login page.
Real world example:
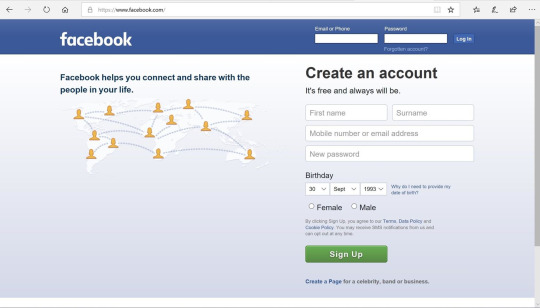
A bit of an outdated example as Facebook has since changed the format of their login page slightly but I think it effectively shows how this method can trick people.
Real login:
Fake login (taken from http://ankitsingh24.blogspot.com/2017/04/phishing-hack-fbamezonflipcart-phishing.html):
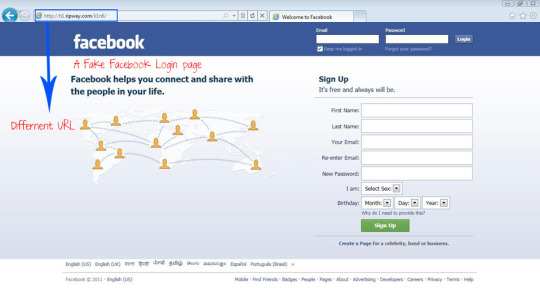
We see here that unless the target was very familiar with the layout of the Facebook login page or looked at the url (but who does that??) they would likely be tricked due to how legit the fake page looks.
Recreating my own fake login page:
For this exploit I will be recreating the old Google login page so that I can hypothetically steal the login details of Google users by sending them to my phony sign in page via a phishing email. Through this I may also be able to access many other accounts owned by the target as most people use the same password across platforms.
Here is the actual Google login page:
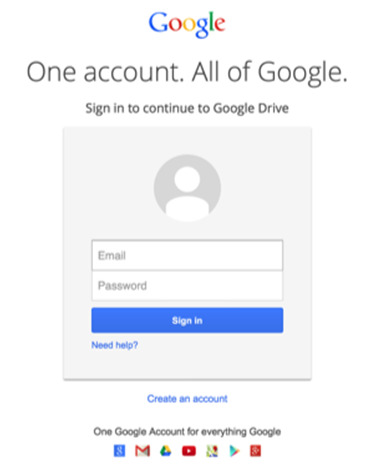
And here is my recreation:
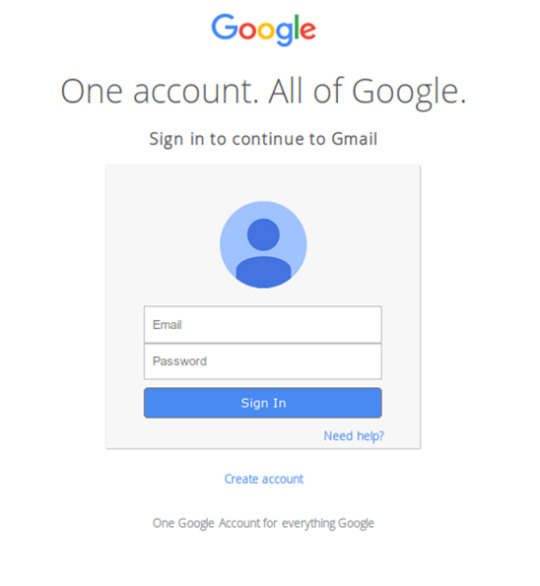
It looks a little shabby and less refined than the actual Google login page (and doesn’t actually do anything) but I’m not a professional software engineer so there’s that. Either way most people are so used to not getting hacked that they would blindly enter their details anyway (if the phishing email was good). Once they’ve done this I can reroute it to my server and use this to maliciously access their account.
If anyone is interested here is the html and css for the site:
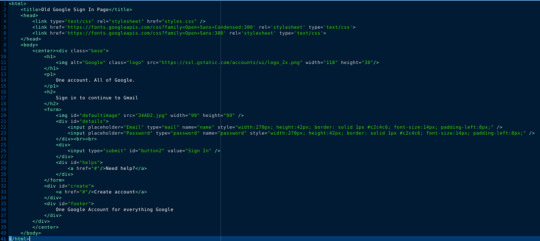
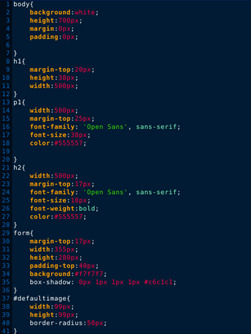
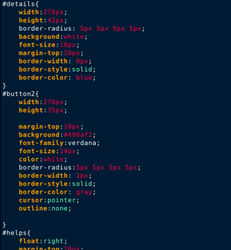
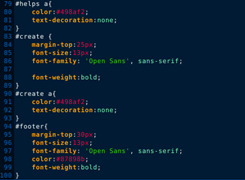
0 notes
Note
what is a cavity virus
“..Some viruses can infect files without increasing their sizes or damaging the files. They accomplish this by overwriting unused areas of executable files. These are called cavity viruses. For example, the CIH virus, or Chernobyl Virus, infects Portable Executable files. Because those files have many empty gaps, the virus, which was 1 KB in length, did not add to the size of the file.”
https://en.m.wikipedia.org/wiki/Computer_virus
1 note
·
View note
Text
Malware Analysis - Draft 1
Rationale We are increasingly reliant on technology which not only includes personal computers and networked servers but network infrastructure (i.e. routers and switches), smart phones, tablets and the increasing use of IoT (Internet of Things) devices (smart devices). People in the form of organised crime groups, political hackers, terrorists, individual hackers and potentially government agencies may want to gain control of your device for their own benefit and without your permission. The reasons can be anything from stealing money, identity fraud, trying to change the outcome of elections, gaining control of infrastructure, tracking your movements, steal data, disrupt governments, steal business information. We need to analyse malware to understand how it works in order to fix security issues in the legitimate software we use. ….
Malware What is malware? Malware is any program or file that intentionally designed to harm, infiltrate, or damage a computer, server or computer network. This software can disable or disrupt the operation of a system, allowing hackers to gain access to confidential and sensitive information and to spy on the computer and the owner of the computer itself. Malware is specifically made to be hidden so that they can remain inside a system for a certain period of time without the knowledge of the system owner. Usually, they disguise themselves into a clean program; even some of the latest malware has the ability to avoid detection of antivirus (1. Wikipedia, 2019).
Types of malware Virus A type of malicious software that, when executed, replicates itself by modifying other computer programs and inserting its own code. When this replication succeeds, the affected areas are then said to be "infected" with a computer virus. Viruses usually try to modify/corrupt data or files on the host, waste system resources. (2. Wikipedia, 2019) Worm A worm is a program that replicates itself in the computer system and transfers itself through the network. The work itself may not have a payload. If it does have a payload it could be in the form of ransomware that can encrypt files or gain access to password.
Spyware Adware Trojan Trojans can allow the attacker to access the personal, bank account and password details. They can also carry a payload which can delete files and cause a ransomware attack or even take control of the whole device. Trojans do not generally try to replicate themselves like worms and viruses. Rootkit Ransomware Keylogger Backdoor
Malware Analysis Is the process of dissecting the software to understand how it works so you can identify it, see how it works and work out ways of defeating it. This project will be using basic static analysis and basic dynamic analysis. Basic Static Analysis This refers to the process of analysing the structure and if possible the code of the software. This allows us to determine what functions it can perform. This involves reverse engineering the binary using tools such as IDA and Binary Ninja.
Basic Dynamic Analysis This refers to analysing the malware after it has been executed. It allows the observation of actions performed and functionality of the software. Dynamic analysis is performed after static analysis.
Risks There are risk in trying to analyse malware as it may escape the lab environment. Some malware can identify that they are in a virtual environment and can act differently so it can be more difficult to analyse.
Malware to Analyse
...
Tools 1. Virtual Box VM 2. Windows 10 O/S 3. IDA Reverse Engineering software 4. Wireshark 5. Process Explorer
Method (for Dynamic Analysis) Setup environment 1. Set up a clean virtual machine with no malware running on it 2. Transfer malware to the virtual machine 3. Conduct analysis 4. Reinstall clean snapshot of virtual environment
References
1. https://en.wikipedia.org/wiki/Malware, accessed on 23/06/2019.
2. https://en.wikipedia.org/wiki/Computer_virus, access on 23/06/2019.
3. https://en.wikipedia.org/wiki/Computer_worm, accessed on 23/06/2019.
4. https://en.wikipedia.org/wiki/Trojan_horse_(computing), access on 23/06/2019.
0 notes
Text
Questions and Answers
1. What is a Computer Virus?
According to Wikipedia, a Computer Virus is “a type of malicious software that, when executed, replicates itself by modifying other computer programs and inserting its own code. When this replication succeeds, the affected areas are then said to be "infected" with a computer virus.”
2. What is Virus Protection?
Virus Protection is, according to webopedia, “software designed to prevent viruses, worms and Trojan horses from getting onto a computer as well as remove any malicious software code that has already infected a computer.”
3. What is a Firewall?
As suggested by techopedia, “a firewall is software used to maintain the security of a private network. Firewalls block unauthorized access to or from private networks and are often employed to prevent unauthorized Web users or illicit software from gaining access to private networks connected to the Internet. A firewall may be implemented using hardware, software, or a combination of both.”
4. Why do you need a Firewall?
You need firewall because as adaware talks about, being on the web, we are all targets for an attack. Firewell helps to protect our identity and our assets while we use the web. It keeps us safe and out of hackers court and allows us to know what is going on when we are using the internet.
5. What is spyware? Spyware is according to malware bytes, “it’s actually a generic term for malicious software that infects your PC or mobile device and gathers information about you, your browsing and Internet usage habits, as well as other data.” It is usually on your computer without your realization that its there.
6. And why would you need spyware protection? You need spyware protection for the same reasons you need firewall, namely that when you are on the web you are a target and open to the threat of viruses, hacking, or malicious software embedding itself on your drives. If this happens you could be at risk to loose parts of your identity, personal information, finances or property. Thus, it is better to get spyware protection to be one step ahead of the bad guys.
Sources 1. https://en.wikipedia.org/wiki/Computer_virus 2. https://www.webopedia.com/TERM/V/virus_protection.html 3. https://www.techopedia.com/definition/5355/firewall 4. https://www.adaware.com/faq/firewalls 5. https://www.malwarebytes.com/spyware/
0 notes
Photo

Computer Virus via /r/funny https://www.reddit.com/r/funny/comments/9xnu58/computer_virus/?utm_source=ifttt
0 notes
Text
EXHIBITION VIDEO INFLUENCE
‘a piece of code that is capable of copying itself and typically has a detrimental effect, such as corrupting the system or destroying data.’
‘A computer virus is a type of malicious software program ("malware") that, when executed, replicates by reproducing itself (copying its own source code) or infecting other computer programs by modifying them. Infecting computer programs can include as well, data files, or the "boot" sector of the hard drive. When this replication succeeds, the affected areas are then said to be "infected" with a computer virus.The term "virus" is also commonly, but erroneously, used to refer to other types of malware. "Malware" encompasses computer viruses along with many other forms of malicious software, such as computer "worms", ransomware, trojan horses, keyloggers, rootkits, spyware, adware, malicious Browser Helper Object (BHOs) and other malicious software. The majority of active malware threats are actually trojan horse programs or computer worms rather than computer viruses. The term computer virus, coined by Fred Cohen in 1985, is a misnomer.Viruses often perform some type of harmful activity on infected host computers, such as acquisition of hard disk space or central processing unit (CPU) time, accessing private information (e.g., credit card numbers), corrupting data, displaying political or humorous messages on the user's screen, spamming their e-mail contacts, logging their keystrokes, or even rendering the computer useless. However, not all viruses carry a destructive "payload" and attempt to hide themselves—the defining characteristic of viruses is that they are self-replicating computer programs which install themselves without user consent.Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to gain access to their hosts' computers and computing resources. The vast majority of viruses target systems running Microsoft Windows,employing a variety of mechanisms to infect new hosts,[9] and often using complex anti-detection/stealth strategies to evade antivirus software. Motives for creating viruses can include seeking profit (e.g., with ransomware), desire to send a political message, personal amusement, to demonstrate that a vulnerability exists in software, for sabotage and denial of service, or simply because they wish to explore cybersecurity issues, artificial life and evolutionary algorithms. Computer viruses currently cause billions of dollars' worth of economic damage each year, due to causing system failure, wasting computer resources, corrupting data, increasing maintenance costs, etc. In response, free, open-source antivirus tools have been developed, and an industry of antivirus software has cropped up, selling or freely distributing virus protection to users of various operating systems. As of 2005, even though no currently existing antivirus software was able to uncover all computer viruses (especially new ones), computer security researchers are actively searching for new ways to enable antivirus solutions to more effectively detect emerging viruses, before they have already become widely distributed.’
https://en.wikipedia.org/wiki/Computer_virus (02/04/2017)
0 notes