#cyber security solution
Explore tagged Tumblr posts
Text
#web development service#e commerce website development service#web development company#web app development services#web and mobile app development services#it management service#it management solutions#it infrastructure management services#it service management consulting#it service operations management#cyber security service#cyber security company#cyber security solution#cyber security service provider#cyber security consultation#cloud computing services#cloud computing companies#best cloud service provider#cloud computing security#best cloud computing services#iot services#iot solutions#iot development services#iot software development#iot network solutions#hr services#staffing service provider#hr recruitment solutions#hr services company#staffing solutions provider
0 notes
Text
Powered by Cyber Security Services- Getting your security right
In an increasingly digital world, cybersecurity services are essential for safeguarding confidential information, infrastructure and operations from cyber threats, which is why it has gained much attention over the past few years. It is risk for any organisation small SME or enterprise, ransomware, phishing and data breaches. In order to combat these atrocities, you require cybersecurity services that are architected with a focus on business continuity, data privacy and assurance of technology resilient.
They come with a slew of services including specifically tailored solutions to various security needs Would be network protection (access and malware blockage), devices endpoint protection (PC, laptop and smartphone) as well cloud security(blockage for data in the cloud). With advanced features like penetration testing and threat detection, vulnerability anticipation becomes possible for organizations whereas incident response services guarantee that downtime as well as the impact of an attack is kept to a bare minimum.
Managed Security Service Providers (MSSPs) are a highly popular choice for a complete cyber security solution. Provide round-the-clock monitoring, perform vulnerability assessments and help manage compliance, MSSPs allow organizations to streamline their operations while experts take charge of their security systems. As SMBs usually lack the resources to house in-house security teams, this is useful especially for small and medium businesses. The All-in-One Managed Security Services Providers (MSSPs)- MSSPs make enterprise-level protection accessible with a fraction of the expenditures, therefore a good cybersecurity has become not out of reach.
Besides computer viruses and malware, human error is among the most common cause of cyber incidents, which means employee training for cybersecurity services is vital. The amount of vulnerability an organization can reduce simply by training the entire staff to identify phishing scams, social engineering and every other type of attack is enormous. An adept workforce becomes an additional layer of security on top of your technical security solutions.
The second of these major focus areas relates to compliance. Certain industries have strict regulations (GDPR; Finance and health care, HIPAA; e-commerce, PCI DSS) that you must comply with. Having the relevant cybersecurity providers deploy the required controls to help an organization comply with these standards and conduct periodic audits verifying that all such requirements are in place, assists both parties to avoid regulatory penalties and reputational damage.
AI and machine learning sitting on cybersecurity These pattern analysis capabilities enable it to spot anomalies and automate countermeasure actions against a new class of threats, as never before tools powered by AI could detect & respond. This is important, as attackers have become increasingly sophisticated in their methods, and it will take defenses of equal complexity to combat them.
As digital outreach increases, global cybersecurity services will continue to be the hottest commodity in many industries. These services are essential to avoid data loss, maintain corporate infrastructure security, guarantee regulatory compliance etc. in todays ever evolving digital landscape. Staying ahead of evolving threats is a process; partnering with seasoned cybersecurity providers and keeping security fundamentals updated regularly is one solution.
Simply put, the cyber services provide an ultimate protection for all kinds of comprehensive hack invasion threats. Carlini leads a team that combines innovative technology, cutting-edge solutions, and an education-first approach; all combined to help ensure everyone (and every organization) are able to be safe & secure in an increasingly connected environment.
0 notes
Text
Best Cyber Security Consultant in USA

MasGlobal serves as your comprehensive destination for cybersecurity consulting services in USA. For more information: https://www.masglobalservices.com/services/cyber-security/
#Cyber Security Services#Cyber Security Service in USA#Cyber Security Protection#Cyber Security Solution
0 notes
Text

TekReach Solutions is an authorized provider of Digital Solutions, based in the vibrant business hub of Dubai, UAE. With a focus on Creativity and Innovation, we provide a broad range of Digital Marketing Services and IT Solutions. We are committed to supporting businesses in navigating the evolving digital landscape and achieving their objectives through leveraging innovating and practical solutions.
#branding services#cloud storage#cyber security services#digital marketing#e commerce development#e commerce services#e commerce solutions#branding#cyber security solutions#cyber security#digital marketing services#seo services#digital marketing company#ppc services#search engine marketing#social media marketing#website development#website development services#software development#mobile application development
2 notes
·
View notes
Text
The Future of Finance: How Fintech Is Winning the Cybersecurity Race

In the cyber age, the financial world has been reshaped by fintech's relentless innovation. Mobile banking apps grant us access to our financial lives at our fingertips, and online investment platforms have revolutionised wealth management. Yet, beneath this veneer of convenience and accessibility lies an ominous spectre — the looming threat of cyberattacks on the financial sector. The number of cyberattacks is expected to increase by 50% in 2023. The global fintech market is expected to reach $324 billion by 2028, growing at a CAGR of 25.2% from 2023 to 2028. This growth of the fintech market makes it even more prone to cyber-attacks. To prevent this there are certain measures and innovations let's find out more about them
Cybersecurity Measures in Fintech
To mitigate the ever-present threat of cyberattacks, fintech companies employ a multifaceted approach to cybersecurity problems and solutions. Here are some key measures:
1. Encryption
Encrypting data at rest and in transit is fundamental to protecting sensitive information. Strong encryption algorithms ensure that even if a hacker gains access to data, it remains unreadable without the decryption keys.
2. Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of verification (e.g., passwords, fingerprints, or security tokens) before gaining access to their accounts.
3. Continuous Monitoring
Fintech companies employ advanced monitoring systems that constantly assess network traffic for suspicious activities. This allows for real-time threat detection and rapid response.
4. Penetration Testing
Regular penetration testing, performed by ethical hackers, helps identify vulnerabilities in systems and applications before malicious actors can exploit them.
5. Employee Training
Human error is a significant factor in cybersecurity breaches. Companies invest in cybersecurity training programs to educate employees about best practices and the risks associated with cyber threats.
6. Incident Response Plans
Having a well-defined incident response plan in place ensures that, in the event of a breach, the company can respond swiftly and effectively to mitigate the damage.
Emerging Technologies in Fintech Cybersecurity
As cyber threats continue to evolve, so do cybersecurity technologies in fintech. Here are some emerging technologies that are making a significant impact:
1. Artificial Intelligence (AI)
AI and machine learning algorithms are used to analyse vast amounts of data and identify patterns indicative of cyber threats. This allows for proactive threat detection and quicker response times.
2. Blockchain
Blockchain technology is employed to enhance the security and transparency of financial transactions. It ensures that transaction records are immutable and cannot be altered by malicious actors.
3. Biometrics
Fintech companies are increasingly adopting biometric authentication methods, such as facial recognition and fingerprint scanning, to provide a higher level of security than traditional passwords.
4. Quantum-Safe Encryption
With the advent of quantum computing, which poses a threat to current encryption methods, fintech companies are exploring quantum-safe encryption techniques to future-proof their security measures.
Conclusion
In the realm of fintech, where trust and security are paramount, the importance of cybersecurity cannot be overstated. Fintech companies must remain vigilant, employing a combination of advanced digital transformation solutions, employee training, and robust incident response plans to protect sensitive financial data from cyber threats. As the industry continues to evolve, staying one step ahead of cybercriminals will be an ongoing challenge, but one that fintech firms must embrace to ensure their continued success and the safety of their customers' financial well-being.
3 notes
·
View notes
Text
Managed IT Services in Aged Care: Ensuring Compliance and Continuity of Care
In the ever-evolving aged care industry, maintaining regulatory compliance, ensuring data security, and delivering uninterrupted care are top priorities. This insightful article by TechBlokes explores how Managed IT Services are transforming aged care facilities by enhancing operational efficiency, meeting compliance requirements, and protecting sensitive resident information. From proactive monitoring to data backup and cybersecurity, TechBlokes ensures that your facility is always audit-ready and running smoothly.
Looking for dependable IT support tailored to the aged care sector? Contact TechBlokes today at +61 449 130 194 and discover how we can help your facility stay compliant and connected. Read More:
#onedrive microsoft#Cybersecurity solutions for businesses#Customizable IT solutions#CRM implementation specialists#cyber security australia#IT Support
1 note
·
View note
Text
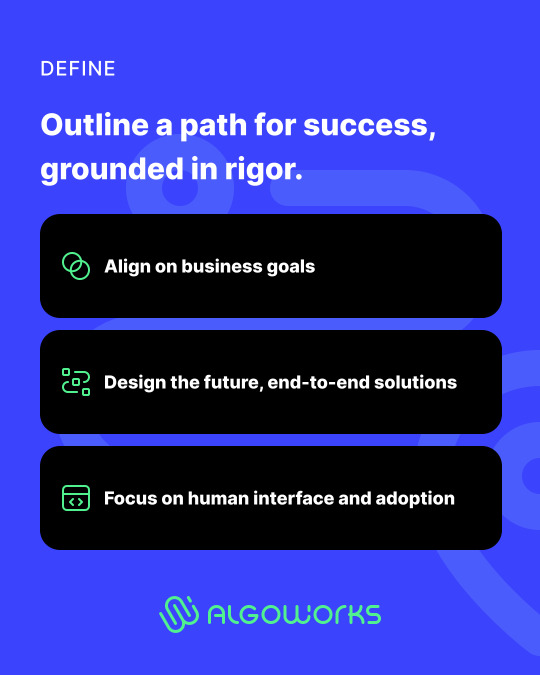


We follow our Define, Build, Run framework to execute flawlessly. From deep listening and 360° planning, to building with agile development and clean code, we ensure performance, security and return on investment through 24/7 monitoring and SLA-backed delivery.
Visit our website to learn more! https://www.algoworks.com/services/
#digital transformation#agile development#clean code#software engineering#cyber security#enterprise solutions#tech innovation#cloud services#innovations#technology#leadership#business excellence
1 note
·
View note
Text
The AIoT Revolution: How AI and IoT Convergence is Rewriting the Rules of Industry & Life

Imagine a world where factory machines predict their own breakdowns before they happen. Where city streets dynamically adjust traffic flow in real-time, slashing commute times. Where your morning coffee brews automatically as your smartwatch detects you waking. This isn’t science fiction—it’s the explosive reality of Artificial Intelligence of Things (AIoT), the merger of AI algorithms and IoT ecosystems. At widedevsolution.com, we engineer these intelligent futures daily.
Why AIoT Isn’t Just Buzzword Bingo: The Core Convergence
Artificial Intelligence of Things fuses the sensory nervous system of IoT devices (sensors, actuators, smart gadgets) with the cognitive brainpower of machine learning models and deep neural networks. Unlike traditional IoT—which drowns in raw data—AIoT delivers actionable intelligence.
As Sundar Pichai, CEO of Google, asserts:
“We are moving from a mobile-first to an AI-first world. The ability to apply AI and machine learning to massive datasets from connected devices is unlocking unprecedented solutions.”
The AIoT Trinity: Trends Reshaping Reality
1. Predictive Maintenance: The Death of Downtime Gone are days of scheduled check-ups. AI-driven predictive maintenance analyzes sensor data intelligence—vibrations, temperature, sound patterns—to forecast failures weeks in advance.
Real-world impact: Siemens reduced turbine failures by 30% using AI anomaly detection on industrial IoT applications.
Financial upside: McKinsey estimates predictive maintenance cuts costs by 20% and downtime by 50%.
2. Smart Cities: Urban Landscapes with a Brain Smart city solutions leverage edge computing and real-time analytics to optimize resources. Barcelona’s AIoT-powered streetlights cut energy use by 30%. Singapore uses AI traffic prediction to reduce congestion by 15%.
Core Tech Stack:
Distributed sensor networks monitoring air/water quality
Computer vision systems for public safety
AI-powered energy grids balancing supply/demand
3. Hyper-Personalized Experiences: The End of One-Size-Fits-All Personalized user experiences now anticipate needs. Think:
Retail: Nike’s IoT-enabled stores suggest shoes based on past purchases and gait analysis.
Healthcare: Remote patient monitoring with wearable IoT detects arrhythmias before symptoms appear.
Sectoral Shockwaves: Where AIoT is Moving the Needle
🏥 Healthcare: From Treatment to Prevention Healthcare IoT enables continuous monitoring. AI-driven diagnostics analyze data from pacemakers, glucose monitors, and smart inhalers. Results?
45% fewer hospital readmissions (Mayo Clinic study)
Early detection of sepsis 6+ hours faster (Johns Hopkins AIoT model)
🌾 Agriculture: Precision Farming at Scale Precision agriculture uses soil moisture sensors, drone imagery, and ML yield prediction to boost output sustainably.
Case Study: John Deere’s AIoT tractors reduced water usage by 40% while increasing crop yields by 15% via real-time field analytics.
🏭 Manufacturing: The Zero-Waste Factory Manufacturing efficiency soars with AI-powered quality control and autonomous supply chains.
Data Point: Bosch’s AIoT factories achieve 99.9985% quality compliance and 25% faster production cycles through automated defect detection.
Navigating the Minefield: Challenges in Scaling AIoT
Even pioneers face hurdles:ChallengeSolutionData security in IoTEnd-to-end encryption + zero-trust architectureSystem interoperabilityAPI-first integration frameworksAI model driftContinuous MLOps monitoringEnergy constraintsTinyML algorithms for low-power devices
As Microsoft CEO Satya Nadella warns:
“Trust is the currency of the AIoT era. Without robust security and ethical governance, even the most brilliant systems will fail.”
How widedevsolution.com Engineers Tomorrow’s AIoT
At widedevsolution.com, we build scalable IoT systems that turn data deluge into profit. Our recent projects include:
A predictive maintenance platform for wind farms, cutting turbine repair costs by $2M/year.
An AI retail personalization engine boosting client sales conversions by 34%.
Smart city infrastructure reducing municipal energy waste by 28%.
We specialize in overcoming edge computing bottlenecks and designing cyber-physical systems with military-grade data security in IoT.
The Road Ahead: Your AIoT Action Plan
The AIoT market will hit $1.2T by 2030 (Statista). To lead, not follow:
Start small: Pilot sensor-driven process optimization in one workflow.
Prioritize security: Implement hardware-level encryption from day one.
Democratize data: Use low-code AI platforms to empower non-technical teams.
The Final Byte We stand at an inflection point. Artificial Intelligence of Things isn’t merely connecting devices—it’s weaving an intelligent fabric across our physical reality. From farms that whisper their needs to algorithms, to factories that self-heal, to cities that breathe efficiently, AIoT transforms data into wisdom.
The question isn’t if this revolution will impact your organization—it’s when. Companies leveraging AIoT integration today aren’t just future-proofing; they’re rewriting industry rulebooks. At widedevsolution.com, we turn convergence into competitive advantage. The machines are learning. The sensors are watching. The future is responding.
“The greatest achievement of AIoT won’t be smarter gadgets—it’ll be fundamentally reimagining how humanity solves its hardest problems.” — widedevsolution.com AI Lab
#artificial intelligence#predictive maintenance#smart city solutions#manufacturing efficiency#AI-powered quality control in manufacturing#edge computing for IoT security#scalable IoT systems for agriculture#AIoT integration#sensor data intelligence#ML yield prediction#cyber-physical#widedevsolution.com
0 notes
Text
Top Cyber Security Services in Sydney to Protect Your Business from Digital Threats

In today’s digital-first environment, cybercrime is more advanced and widespread than ever. Whether you're a small startup or a large enterprise, investing in cyber security services in Sydney is no longer optional it’s essential. From data breaches to ransomware attacks, Australian businesses face a growing range of cyber threats that can lead to significant financial and reputational damage.
Why Cyber Security Matters for Sydney Businesses
Sydney is home to thousands of businesses across finance, healthcare, eCommerce, legal, and other high-risk industries. These sectors are prime targets for cybercriminals, which makes advanced cyber protection services in Sydney a necessity rather than a luxury.
What Do Cyber Security Services Include?
A reliable cyber security service provider in Sydney typically offers a comprehensive suite of protection solutions, including:
Network Security & Monitoring Real-time threat detection and firewall management to keep your infrastructure safe.
Endpoint Protection Securing all devices connected to your network from malware and unauthorized access.
Data Backup & Recovery Automated backups and fast disaster recovery to prevent data loss.
Email & Phishing Protection Tools to prevent phishing scams, malicious links, and spam from entering your organization.
Security Audits & Risk Assessments Periodic evaluations to identify system vulnerabilities and compliance issues.
Managed Detection and Response (MDR) Continuous monitoring and quick threat mitigation by experts.
Who Needs Cyber Security Services?
If you store customer data, process payments online, operate remote teams, or rely heavily on digital systems, you need professional cyber security services in Sydney. It’s especially critical for:
Financial institutions
Law firms
Healthcare providers
Online retailers
Educational institutions
Conclusion
Cyberattacks don’t just target big corporations small and medium-sized businesses are equally at risk. Partnering with a trusted cyber security service provider in Sydney can help you stay ahead of threats, safeguard sensitive data, and maintain customer trust.
Ready to Secure Your Business? Speak to a certified Sydney-based cyber security team today to assess your vulnerabilities and get a customized protection plan.
1 note
·
View note
Text
Empowering Saudi Arabia’s Digital Frontier: Network, Cyber Security & IT Solutions
Meta Description: Explore how Sky Informations is transforming Saudi Arabia’s digital ecosystem with cutting-edge network, cyber security, and IT solutions tailored for future-ready businesses.
Empowering Saudi Arabia’s Digital Frontier: Network, Cyber Security & IT Solutions
As Saudi Arabia fast-tracks its Vision 2030 goals, digital innovation is becoming the cornerstone of national progress. From smart cities to advanced e-governance and enterprise automation, the Kingdom’s demand for trusted network infrastructure, cyber security, and end-to-end IT services is growing rapidly.
Sky Informations is at the forefront of this transformation — helping businesses secure, scale, and innovate with powerful digital solutions.
Leading the Way in Network & IT Services
Sky Informations delivers robust, enterprise-grade network architecture designed to support agility, scalability, and data integrity across every industry. Core offerings include:
High-speed LAN/WAN solutions
Wireless & hybrid cloud network integration
24/7 monitoring and troubleshooting
Infrastructure upgrades for enterprise digitalization
Cyber Security That Protects What Matters
With increasing cyber threats targeting Middle Eastern businesses, Sky Informations implements multi-layered security systems to keep critical data and digital operations safe.
Threat detection & risk assessments
Firewall & endpoint protection
Encryption & access control
ISO & NCA compliance consulting
Whether you're a government agency, financial firm, or SME, Sky’s cybersecurity team offers customized defense strategies to mitigate risks.
Comprehensive IT Solutions for a Smarter Tomorrow
Sky Informations also offers a full suite of IT services to support digital growth:
Cloud migration & backup systems
Software development & tech support
IT helpdesk and managed services
AI & automation consulting
Their customer-centric, scalable approach makes technology more accessible, secure, and cost-effective for businesses of all sizes.
Why Saudi Arabia Chooses Sky Informations
Saudi Arabia is rapidly becoming a regional leader in digital infrastructure. With government incentives, smart city developments, and rising tech literacy, the nation demands world-class IT providers.
Sky Informations stands out by combining:
Local understanding of regulations and business culture
Global standards in tech and security
Flexible support with scalable service models
Conclusion
The future of Saudi business is digital — and Sky Informations is your trusted partner in that journey. From secure networks to smart IT frameworks, the company empowers your organization to grow fearlessly in a connected world.🔗 Visit https://skyinformations.com to learn more and request a consultation.
0 notes
Text
Ever wondered how quirky #techstartups became market sensations? 🚀✨ Discover 5 surprising #IPO stories that highlight the power of #creativity in #marketing ! Learn from their journeys and innovate boldly. For more insights, visit https://techsolworld.com/subscriptions ! #TechMarketing #techupdate #technology #cuttingedgetechnology #technews #techinfo #techindustry #tech #latesttech
#tech startups#technology for tech startups#tech startup software#microsoft for tech startups#best microsoft software for business#tech startup business solutions#tech startup security#tech startup cyber security#tech marketing#microsoftgoldpartner#find a microsoft gold partner#find a microsoft solutions partner#buy microsoft volume licensing#buy microsoft volume licenses#microsoftappsource#technologysolutionsworldwide#microsoftreseller#microsoftenterprise#microsoft enterprise solutions#microsoft enterprise agreement#get a microsoft enterprise agreement#find a microsoft enterprise partner#buy a microsoft enterprise agreement#technology solutions worldwide#technology solutions#microsoft#microsoft appsource#microsoftlicensereseller
0 notes
Text
Is Your Business Ready for the Next Wave of Cyber Threats? 👀

Recent expert warnings highlight that America’s power grid-and the critical infrastructure businesses rely on-is increasingly vulnerable to sophisticated attacks, from EMPs to AI-driven cyber threats. While these risks may seem distant, the reality is that small and mid-size businesses are often the first targets in supply chain attacks. What does this mean for your business? 📌Cyber threats are evolving faster than ever, and attackers are using AI to find and exploit weak links. 📌Disruptions to the power grid or digital infrastructure can cripple business operations, even if you’re not a direct target. 📌Proactive cybersecurity isn’t just for the big players-every organization needs a plan. At Century Group Solutions, we help businesses like yours build resilience with layered security, smart backup strategies, and real-time threat monitoring. Don’t wait for a wake-up call-let’s strengthen your defenses now. https://centurygroup.net/cloud-computing/cyber-security/
#CyberSecurity #CriticalInfrastructure #B2B #BusinessContinuity #ITSecurity
#Cyber Threats Protection#Cybersecurity#IT Security#managed it services#managed it solutions#phishing#managed service provider
1 note
·
View note
Text
Securing Tomorrow: Exploring Cutting-Edge Cyber Security Service Solutions

In an era dominated by digital advancements, the need for robust cyber security solutions has never been more critical. As businesses embrace the advantages of a connected world, the risks of cyber threats loom larger than ever. In this blog post, we delve into the cutting-edge cyber security service solutions offered by MAS Global Services, shedding light on their innovative approaches to securing tomorrow's digital landscape.
1. The Threat Landscape Today:
The first section of the blog will set the stage by discussing the current cyber threat landscape. Highlight recent trends, statistics, and notable incidents to emphasize the urgency of advanced security measures.
2. MAS Global Services: A Brief Overview:
Provide readers with a snapshot of MAS Global Services, emphasizing their commitment to staying at the forefront of cyber security. Discuss the company's mission, values, and their role in addressing the evolving challenges of the digital age.
3. Cutting-Edge Technologies:
Explore the innovative technologies employed by MAS Global Services. This could include AI-driven threat detection, blockchain security, and other advanced tools designed to outsmart and outpace cyber threats.
4. Comprehensive Security Services:
Detail the range of cyber security services offered by MAS Global Services. This might include network security, endpoint protection, incident response, and more. Explain how these services work together to create a comprehensive defense strategy.
5. Industry-Specific Solutions:
If applicable, discuss how MAS Global Services tailors its cyber security solutions to specific industries. Whether it's healthcare, finance, or manufacturing, delve into how the company addresses unique challenges faced by different sectors.
6. Future Trends and Adaptability:
Conclude the blog by discussing future trends in cyber security and how MAS Global Services remains adaptable and forward-thinking. This could include insights into upcoming technologies, regulatory changes, or emerging threats.
Conclusion:
Wrap up the blog by reiterating the significance of staying ahead in the cyber security game. Emphasize how MAS Global Services is playing a pivotal role in securing tomorrow's digital landscape through its cutting-edge cyber security Services.
MasGlobal Services provide Cyber security service to protect systems, networks, programs, devices and data from cyber attacks. So if you are looking for the best Cyber Security Service, Mas Global is the company you can contact.
#Cyber Security Services#Cyber Security Service in USA#Cyber Security Protection#Cyber Security Solution
0 notes
Text
Smart Cyber Security Solutions and Services for a Safer Future

In the digital age of 2025, where cyber threats evolve as swiftly as technology itself, safeguarding your business's digital assets is paramount. At Indepth IT Solutions, we understand that navigating the complex landscape of Cyber Security Solutions and Services requires not just expertise but a proactive approach.
Imagine your business as a fortress. Traditional defenses like firewalls and antivirus software are akin to moats and drawbridges once effective but now insufficient against sophisticated adversaries. Modern cyber threats are stealthy, often bypassing these barriers unnoticed. This is where advanced Cyber Security Solutions and Services come into play, offering dynamic and adaptive defenses.
Artificial Intelligence (AI) and Machine Learning (ML) have become the sentinels of cybersecurity. These technologies analyze vast amounts of data in real-time, identifying anomalies and potential threats with unprecedented speed and accuracy. By learning from each interaction, they evolve, becoming more adept at predicting and neutralizing threats before they materialize.
Complementing AI and ML is the Zero Trust Architecture—a paradigm shift from the old adage of "trust but verify" to "never trust, always verify." This model ensures that every access request is thoroughly vetted, regardless of its origin. By implementing strict access controls and continuous monitoring, businesses can significantly reduce the risk of unauthorized access and data breaches.
Drawing inspiration from industries like electrical services, where precision and safety are non-negotiable, we at Indepth IT Solutions emphasize the importance of meticulous planning and execution in cybersecurity. Just as a well-installed electrical system ensures the smooth operation of a building, a robust cybersecurity framework ensures the seamless functioning of your digital infrastructure.
Moreover, the integration of Cybersecurity-as-a-Service (CaaS) offers businesses scalable and customizable security solutions. This approach allows for continuous updates and real-time threat intelligence, ensuring that your defenses are always a step ahead.
In conclusion, as cyber threats become more sophisticated, the need for comprehensive Cyber Security Solutions and Services becomes imperative. At Indepth IT Solutions, we are committed to providing you with cutting-edge security measures tailored to your unique needs. Let us be the guardians of your digital realm, ensuring peace of mind in an ever-connected world.
1 note
·
View note
Text
Cyber Security Services Company | Data Security Solutions

In today’s fast-paced digital world, businesses increasingly rely on technology to store, process, and transmit sensitive data. As companies across industries harness the power of the internet, the need for robust cybersecurity services has never been more crucial. Data breaches and cyberattacks are growing threats from small startups to large corporations that can have devastating consequences. That’s where a cybersecurity company specializing in data protection services and cybersecurity management comes into play.
This blog explores the importance of cybersecurity management, the types of services offered by a cybersecurity services company, and how data protection services and endpoint security services can help businesses protect their sensitive information.
Understanding the Growing Importance of Cybersecurity
The digital transformation that businesses have undergone in recent years has revolutionized operations, providing significant benefits like improved efficiency, better customer engagement, and more streamlined processes. However, this transformation has also opened new doors for cybercriminals who exploit vulnerabilities in systems and networks to steal data, launch attacks, and disrupt operations.
With data breaches and cyberattacks on the rise, organizations must safeguard sensitive information from unauthorized access, manipulation, and theft. Whether it’s customer data, intellectual property, or financial records, securing these assets is paramount to maintaining trust, compliance with regulations, and protecting brand reputation.
Cybersecurity solutions providers play a key role in defending organizations from these threats. Cybersecurity isn’t just a technical need—it’s a business priority that can help prevent costly disruptions, legal ramifications, and loss of customer confidence. This is where the role of a cybersecurity consulting firm becomes indispensable.
What Is a Cybersecurity Services Company?
A cybersecurity services company specializes in identifying, mitigating, and preventing cyber threats. They provide tailored solutions to ensure businesses’ information and infrastructure are well-protected from a wide range of security risks. These companies are essential partners in safeguarding businesses from cyberattacks and ensuring the security of sensitive data and systems.
Key Services Provided by a Cybersecurity Services Company

Cybersecurity companies offer a range of services designed to safeguard businesses from evolving threats. These services include:
Threat Detection & Prevention Services: Cybersecurity companies deploy advanced monitoring tools and techniques to detect vulnerabilities, anomalous activities, and potential threats before they cause harm. This includes setting up firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Risk Management: Cybersecurity firms assess vulnerabilities and design strategies to safeguard businesses from both internal and external threats. A cyber risk management company helps ensure that businesses are prepared for any potential cyber risks.
Cybersecurity Audits & Assessments: Regular security audits and penetration testing are vital for identifying weaknesses in a company’s infrastructure. These audits ensure no part of the system remains unprotected.
Compliance Support: For businesses in regulated industries, cybersecurity compliance services help ensure adherence to standards like GDPR, HIPAA, and PCI DSS. Companies in these industries can also benefit from IT security services companies that provide guidance and support for meeting compliance requirements.
Incident Response & Disaster Recovery: Even with robust security measures, breaches can still occur. Incident response services help businesses respond quickly and effectively to limit damage. Additionally, cybersecurity audit services and vulnerability assessment companies help identify and prevent potential attacks before they materialize.
Employee Training & Awareness: Cybersecurity management companies often provide training programs to raise awareness about phishing, password hygiene, and safe online behavior, reducing human error and improving security.
Types of Data Security Solutions Offered by Cybersecurity Companies

At the core of every cybersecurity service is data protection. Cybersecurity solutions providers offer several key solutions to help businesses secure their information:
Encryption: Encryption ensures that even if data is accessed by cybercriminals, it remains unreadable without the decryption key. Cloud security companies offer encryption solutions to protect data stored in the cloud, safeguarding sensitive information during transit and while at rest.
Access Control & Authentication: Multi-factor authentication (MFA) and role-based access control (RBAC) are implemented to ensure only authorized personnel can access sensitive systems.
Data Loss Prevention (DLP): Data protection services monitor data transfers and emails to prevent unauthorized sharing or leakage of confidential information.
Firewalls & Network Security: Firewalls act as the first line of defense by filtering traffic and blocking harmful activities. Network security services providers ensure that your network is properly configured with firewalls, VPNs, and network segmentation to protect data from external attacks.
Backup & Disaster Recovery: A comprehensive backup and recovery plan ensures that lost or compromised data can be restored with minimal disruption to business operations. Cloud security companies play a key role in providing reliable cloud-based backup and recovery services.
Endpoint Security: With more employees working remotely, endpoint security services are becoming essential. Cybersecurity firms implement solutions to protect mobile devices, laptops, and tablets from threats.
Why Partner with a Cybersecurity Services Company?
Businesses of all sizes can benefit from the specialized expertise of a cybersecurity consulting firm. Here are some reasons why partnering with one is essential:
Expertise and Experience
Cybersecurity is a complex field requiring in-depth knowledge of emerging threats and security solutions. A cybersecurity services company brings years of experience and expertise to the table, ensuring best practices and cutting-edge tools are used to protect your data.
Cost Efficiency
Building an in-house cybersecurity team can be costly. By outsourcing to a cybersecurity solutions provider, businesses gain access to expert resources and advanced technologies without the need to invest in full-time staff.
Proactive Protection
Rather than waiting for a breach to occur, a cybersecurity management company helps you adopt a proactive approach by identifying and neutralizing potential threats before they can impact your business.
Regulatory Compliance
Staying compliant with regulations like GDPR, HIPAA, and CCPA can be challenging. A cybersecurity services company ensures your business complies with relevant data protection laws, avoiding legal complications and fines. These companies provide cybersecurity compliance services to meet the highest standards of data protection.
Business Continuity
Cybersecurity services also encompass disaster recovery planning, ensuring that your business can continue to operate smoothly after a cyber attack or natural disaster. Security operations center services ensure continuous monitoring, offering peace of mind that any security breaches are quickly detected and neutralized.
Conclusion: Protect Your Business with a Cybersecurity Services Company
As cyber threats continue to evolve, businesses must take proactive steps to protect their sensitive data and maintain customer trust. Partnering with a reputable cybersecurity consulting firm ensures that you have the right tools, expertise, and strategies in place to prevent cyberattacks, secure your data, and maintain regulatory compliance.
Whether it’s through penetration testing, endpoint security services, or incident response services, a cybersecurity services company plays a crucial role in keeping your data safe and your business running smoothly.
Investing in cybersecurity solutions today can help prevent significant financial and reputational damage in the future. Don't wait until it's too late—reach out to a trusted cybersecurity services company today to protect your data and your business's future.
#Cyber Security Services Company | Data Security Solutions#Cybersecurity Management Company#Managed Cyber Security Services#Cyber Security Company#Cyber Security Services#Endpoint Security Services#Cybersecurity Solutions Provider#Cyber Security Consulting Firm#Network Security Services#Cybersecurity Audit Services#IT Security Services Company#Cloud Security Company#Data Protection Services#Cybersecurity Compliance Services#Security Operations Center Services#Threat Detection Services#Penetration Testing Company#Incident Response Services#Vulnerability Assessment Company#Cyber Risk Management Company#Information Security Services
0 notes
Text

Automate and streamline proficiency testing in your laboratory using our Dubai-based solution, ideal for lab assessments across the GCC. Visit: https://lqms.net/
0 notes