#Cyber Security Solutions and Services
Explore tagged Tumblr posts
Text
Smart Cyber Security Solutions and Services for a Safer Future

In the digital age of 2025, where cyber threats evolve as swiftly as technology itself, safeguarding your business's digital assets is paramount. At Indepth IT Solutions, we understand that navigating the complex landscape of Cyber Security Solutions and Services requires not just expertise but a proactive approach.
Imagine your business as a fortress. Traditional defenses like firewalls and antivirus software are akin to moats and drawbridges once effective but now insufficient against sophisticated adversaries. Modern cyber threats are stealthy, often bypassing these barriers unnoticed. This is where advanced Cyber Security Solutions and Services come into play, offering dynamic and adaptive defenses.
Artificial Intelligence (AI) and Machine Learning (ML) have become the sentinels of cybersecurity. These technologies analyze vast amounts of data in real-time, identifying anomalies and potential threats with unprecedented speed and accuracy. By learning from each interaction, they evolve, becoming more adept at predicting and neutralizing threats before they materialize.
Complementing AI and ML is the Zero Trust Architecture—a paradigm shift from the old adage of "trust but verify" to "never trust, always verify." This model ensures that every access request is thoroughly vetted, regardless of its origin. By implementing strict access controls and continuous monitoring, businesses can significantly reduce the risk of unauthorized access and data breaches.
Drawing inspiration from industries like electrical services, where precision and safety are non-negotiable, we at Indepth IT Solutions emphasize the importance of meticulous planning and execution in cybersecurity. Just as a well-installed electrical system ensures the smooth operation of a building, a robust cybersecurity framework ensures the seamless functioning of your digital infrastructure.
Moreover, the integration of Cybersecurity-as-a-Service (CaaS) offers businesses scalable and customizable security solutions. This approach allows for continuous updates and real-time threat intelligence, ensuring that your defenses are always a step ahead.
In conclusion, as cyber threats become more sophisticated, the need for comprehensive Cyber Security Solutions and Services becomes imperative. At Indepth IT Solutions, we are committed to providing you with cutting-edge security measures tailored to your unique needs. Let us be the guardians of your digital realm, ensuring peace of mind in an ever-connected world.
1 note
·
View note
Text

TekReach Solutions is an authorized provider of Digital Solutions, based in the vibrant business hub of Dubai, UAE. With a focus on Creativity and Innovation, we provide a broad range of Digital Marketing Services and IT Solutions. We are committed to supporting businesses in navigating the evolving digital landscape and achieving their objectives through leveraging innovating and practical solutions.
#branding services#cloud storage#cyber security services#digital marketing#e commerce development#e commerce services#e commerce solutions#branding#cyber security solutions#cyber security#digital marketing services#seo services#digital marketing company#ppc services#search engine marketing#social media marketing#website development#website development services#software development#mobile application development
2 notes
·
View notes
Text
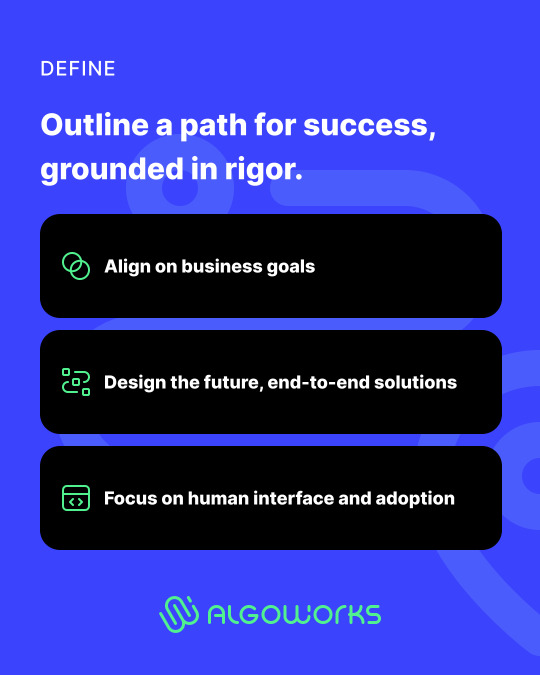


We follow our Define, Build, Run framework to execute flawlessly. From deep listening and 360° planning, to building with agile development and clean code, we ensure performance, security and return on investment through 24/7 monitoring and SLA-backed delivery.
Visit our website to learn more! https://www.algoworks.com/services/
#digital transformation#agile development#clean code#software engineering#cyber security#enterprise solutions#tech innovation#cloud services#innovations#technology#leadership#business excellence
1 note
·
View note
Text
Top Cyber Security Services in Sydney to Protect Your Business from Digital Threats

In today’s digital-first environment, cybercrime is more advanced and widespread than ever. Whether you're a small startup or a large enterprise, investing in cyber security services in Sydney is no longer optional it’s essential. From data breaches to ransomware attacks, Australian businesses face a growing range of cyber threats that can lead to significant financial and reputational damage.
Why Cyber Security Matters for Sydney Businesses
Sydney is home to thousands of businesses across finance, healthcare, eCommerce, legal, and other high-risk industries. These sectors are prime targets for cybercriminals, which makes advanced cyber protection services in Sydney a necessity rather than a luxury.
What Do Cyber Security Services Include?
A reliable cyber security service provider in Sydney typically offers a comprehensive suite of protection solutions, including:
Network Security & Monitoring Real-time threat detection and firewall management to keep your infrastructure safe.
Endpoint Protection Securing all devices connected to your network from malware and unauthorized access.
Data Backup & Recovery Automated backups and fast disaster recovery to prevent data loss.
Email & Phishing Protection Tools to prevent phishing scams, malicious links, and spam from entering your organization.
Security Audits & Risk Assessments Periodic evaluations to identify system vulnerabilities and compliance issues.
Managed Detection and Response (MDR) Continuous monitoring and quick threat mitigation by experts.
Who Needs Cyber Security Services?
If you store customer data, process payments online, operate remote teams, or rely heavily on digital systems, you need professional cyber security services in Sydney. It’s especially critical for:
Financial institutions
Law firms
Healthcare providers
Online retailers
Educational institutions
Conclusion
Cyberattacks don’t just target big corporations small and medium-sized businesses are equally at risk. Partnering with a trusted cyber security service provider in Sydney can help you stay ahead of threats, safeguard sensitive data, and maintain customer trust.
Ready to Secure Your Business? Speak to a certified Sydney-based cyber security team today to assess your vulnerabilities and get a customized protection plan.
1 note
·
View note
Text
Empowering Saudi Arabia’s Digital Frontier: Network, Cyber Security & IT Solutions
Meta Description: Explore how Sky Informations is transforming Saudi Arabia’s digital ecosystem with cutting-edge network, cyber security, and IT solutions tailored for future-ready businesses.
Empowering Saudi Arabia’s Digital Frontier: Network, Cyber Security & IT Solutions
As Saudi Arabia fast-tracks its Vision 2030 goals, digital innovation is becoming the cornerstone of national progress. From smart cities to advanced e-governance and enterprise automation, the Kingdom’s demand for trusted network infrastructure, cyber security, and end-to-end IT services is growing rapidly.
Sky Informations is at the forefront of this transformation — helping businesses secure, scale, and innovate with powerful digital solutions.
Leading the Way in Network & IT Services
Sky Informations delivers robust, enterprise-grade network architecture designed to support agility, scalability, and data integrity across every industry. Core offerings include:
High-speed LAN/WAN solutions
Wireless & hybrid cloud network integration
24/7 monitoring and troubleshooting
Infrastructure upgrades for enterprise digitalization
Cyber Security That Protects What Matters
With increasing cyber threats targeting Middle Eastern businesses, Sky Informations implements multi-layered security systems to keep critical data and digital operations safe.
Threat detection & risk assessments
Firewall & endpoint protection
Encryption & access control
ISO & NCA compliance consulting
Whether you're a government agency, financial firm, or SME, Sky’s cybersecurity team offers customized defense strategies to mitigate risks.
Comprehensive IT Solutions for a Smarter Tomorrow
Sky Informations also offers a full suite of IT services to support digital growth:
Cloud migration & backup systems
Software development & tech support
IT helpdesk and managed services
AI & automation consulting
Their customer-centric, scalable approach makes technology more accessible, secure, and cost-effective for businesses of all sizes.
Why Saudi Arabia Chooses Sky Informations
Saudi Arabia is rapidly becoming a regional leader in digital infrastructure. With government incentives, smart city developments, and rising tech literacy, the nation demands world-class IT providers.
Sky Informations stands out by combining:
Local understanding of regulations and business culture
Global standards in tech and security
Flexible support with scalable service models
Conclusion
The future of Saudi business is digital — and Sky Informations is your trusted partner in that journey. From secure networks to smart IT frameworks, the company empowers your organization to grow fearlessly in a connected world.🔗 Visit https://skyinformations.com to learn more and request a consultation.
0 notes
Text
Is Your Business Ready for the Next Wave of Cyber Threats? 👀

Recent expert warnings highlight that America’s power grid-and the critical infrastructure businesses rely on-is increasingly vulnerable to sophisticated attacks, from EMPs to AI-driven cyber threats. While these risks may seem distant, the reality is that small and mid-size businesses are often the first targets in supply chain attacks. What does this mean for your business? 📌Cyber threats are evolving faster than ever, and attackers are using AI to find and exploit weak links. 📌Disruptions to the power grid or digital infrastructure can cripple business operations, even if you’re not a direct target. 📌Proactive cybersecurity isn’t just for the big players-every organization needs a plan. At Century Group Solutions, we help businesses like yours build resilience with layered security, smart backup strategies, and real-time threat monitoring. Don’t wait for a wake-up call-let’s strengthen your defenses now. https://centurygroup.net/cloud-computing/cyber-security/
#CyberSecurity #CriticalInfrastructure #B2B #BusinessContinuity #ITSecurity
#Cyber Threats Protection#Cybersecurity#IT Security#managed it services#managed it solutions#phishing#managed service provider
1 note
·
View note
Text
Cyber Security Services Company | Data Security Solutions

In today’s fast-paced digital world, businesses increasingly rely on technology to store, process, and transmit sensitive data. As companies across industries harness the power of the internet, the need for robust cybersecurity services has never been more crucial. Data breaches and cyberattacks are growing threats from small startups to large corporations that can have devastating consequences. That’s where a cybersecurity company specializing in data protection services and cybersecurity management comes into play.
This blog explores the importance of cybersecurity management, the types of services offered by a cybersecurity services company, and how data protection services and endpoint security services can help businesses protect their sensitive information.
Understanding the Growing Importance of Cybersecurity
The digital transformation that businesses have undergone in recent years has revolutionized operations, providing significant benefits like improved efficiency, better customer engagement, and more streamlined processes. However, this transformation has also opened new doors for cybercriminals who exploit vulnerabilities in systems and networks to steal data, launch attacks, and disrupt operations.
With data breaches and cyberattacks on the rise, organizations must safeguard sensitive information from unauthorized access, manipulation, and theft. Whether it’s customer data, intellectual property, or financial records, securing these assets is paramount to maintaining trust, compliance with regulations, and protecting brand reputation.
Cybersecurity solutions providers play a key role in defending organizations from these threats. Cybersecurity isn’t just a technical need—it’s a business priority that can help prevent costly disruptions, legal ramifications, and loss of customer confidence. This is where the role of a cybersecurity consulting firm becomes indispensable.
What Is a Cybersecurity Services Company?
A cybersecurity services company specializes in identifying, mitigating, and preventing cyber threats. They provide tailored solutions to ensure businesses’ information and infrastructure are well-protected from a wide range of security risks. These companies are essential partners in safeguarding businesses from cyberattacks and ensuring the security of sensitive data and systems.
Key Services Provided by a Cybersecurity Services Company

Cybersecurity companies offer a range of services designed to safeguard businesses from evolving threats. These services include:
Threat Detection & Prevention Services: Cybersecurity companies deploy advanced monitoring tools and techniques to detect vulnerabilities, anomalous activities, and potential threats before they cause harm. This includes setting up firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Risk Management: Cybersecurity firms assess vulnerabilities and design strategies to safeguard businesses from both internal and external threats. A cyber risk management company helps ensure that businesses are prepared for any potential cyber risks.
Cybersecurity Audits & Assessments: Regular security audits and penetration testing are vital for identifying weaknesses in a company’s infrastructure. These audits ensure no part of the system remains unprotected.
Compliance Support: For businesses in regulated industries, cybersecurity compliance services help ensure adherence to standards like GDPR, HIPAA, and PCI DSS. Companies in these industries can also benefit from IT security services companies that provide guidance and support for meeting compliance requirements.
Incident Response & Disaster Recovery: Even with robust security measures, breaches can still occur. Incident response services help businesses respond quickly and effectively to limit damage. Additionally, cybersecurity audit services and vulnerability assessment companies help identify and prevent potential attacks before they materialize.
Employee Training & Awareness: Cybersecurity management companies often provide training programs to raise awareness about phishing, password hygiene, and safe online behavior, reducing human error and improving security.
Types of Data Security Solutions Offered by Cybersecurity Companies

At the core of every cybersecurity service is data protection. Cybersecurity solutions providers offer several key solutions to help businesses secure their information:
Encryption: Encryption ensures that even if data is accessed by cybercriminals, it remains unreadable without the decryption key. Cloud security companies offer encryption solutions to protect data stored in the cloud, safeguarding sensitive information during transit and while at rest.
Access Control & Authentication: Multi-factor authentication (MFA) and role-based access control (RBAC) are implemented to ensure only authorized personnel can access sensitive systems.
Data Loss Prevention (DLP): Data protection services monitor data transfers and emails to prevent unauthorized sharing or leakage of confidential information.
Firewalls & Network Security: Firewalls act as the first line of defense by filtering traffic and blocking harmful activities. Network security services providers ensure that your network is properly configured with firewalls, VPNs, and network segmentation to protect data from external attacks.
Backup & Disaster Recovery: A comprehensive backup and recovery plan ensures that lost or compromised data can be restored with minimal disruption to business operations. Cloud security companies play a key role in providing reliable cloud-based backup and recovery services.
Endpoint Security: With more employees working remotely, endpoint security services are becoming essential. Cybersecurity firms implement solutions to protect mobile devices, laptops, and tablets from threats.
Why Partner with a Cybersecurity Services Company?
Businesses of all sizes can benefit from the specialized expertise of a cybersecurity consulting firm. Here are some reasons why partnering with one is essential:
Expertise and Experience
Cybersecurity is a complex field requiring in-depth knowledge of emerging threats and security solutions. A cybersecurity services company brings years of experience and expertise to the table, ensuring best practices and cutting-edge tools are used to protect your data.
Cost Efficiency
Building an in-house cybersecurity team can be costly. By outsourcing to a cybersecurity solutions provider, businesses gain access to expert resources and advanced technologies without the need to invest in full-time staff.
Proactive Protection
Rather than waiting for a breach to occur, a cybersecurity management company helps you adopt a proactive approach by identifying and neutralizing potential threats before they can impact your business.
Regulatory Compliance
Staying compliant with regulations like GDPR, HIPAA, and CCPA can be challenging. A cybersecurity services company ensures your business complies with relevant data protection laws, avoiding legal complications and fines. These companies provide cybersecurity compliance services to meet the highest standards of data protection.
Business Continuity
Cybersecurity services also encompass disaster recovery planning, ensuring that your business can continue to operate smoothly after a cyber attack or natural disaster. Security operations center services ensure continuous monitoring, offering peace of mind that any security breaches are quickly detected and neutralized.
Conclusion: Protect Your Business with a Cybersecurity Services Company
As cyber threats continue to evolve, businesses must take proactive steps to protect their sensitive data and maintain customer trust. Partnering with a reputable cybersecurity consulting firm ensures that you have the right tools, expertise, and strategies in place to prevent cyberattacks, secure your data, and maintain regulatory compliance.
Whether it’s through penetration testing, endpoint security services, or incident response services, a cybersecurity services company plays a crucial role in keeping your data safe and your business running smoothly.
Investing in cybersecurity solutions today can help prevent significant financial and reputational damage in the future. Don't wait until it's too late—reach out to a trusted cybersecurity services company today to protect your data and your business's future.
#Cyber Security Services Company | Data Security Solutions#Cybersecurity Management Company#Managed Cyber Security Services#Cyber Security Company#Cyber Security Services#Endpoint Security Services#Cybersecurity Solutions Provider#Cyber Security Consulting Firm#Network Security Services#Cybersecurity Audit Services#IT Security Services Company#Cloud Security Company#Data Protection Services#Cybersecurity Compliance Services#Security Operations Center Services#Threat Detection Services#Penetration Testing Company#Incident Response Services#Vulnerability Assessment Company#Cyber Risk Management Company#Information Security Services
0 notes
Text

Best Employee Monitoring Solution | Kriptone | Kntrol
#best employee time tracking software#Real-time monitoring software#it security services company#Data loss prevention solutions#Endpoint security#IT cyber security services#Data loss protection#Web Tracking
1 note
·
View note
Text

The Role of Managed IT Services in Cybersecurity & Cloud-Managed IT Services
Let’s be honest—cyber threats aren’t just the stuff of action movies. Your business isn't fighting off rogue hackers in hoodies from dimly lit basements (or maybe it is, who knows?). In reality, cyber threats are stealthier, smarter, and more relentless than ever.
Enter Managed IT Services—your digital bodyguards, working behind the scenes to keep your data safe. And when it comes to cloud-managed IT? It’s like giving your business a VIP pass to efficiency, scalability, and airtight security.
Let’s break it down—with the technical muscle to back it up.
1. The Role of Managed IT Services in Cybersecurity: Protecting Your Digital Assets
Cyber threats like ransomware, phishing, and insider attacks are relentless. Managed IT Services act as your 24/7 security command center, blending cutting-edge tools and frameworks to outsmart threats.
1.1 Advanced Security Operations Center (SOC): The Nerve Center
SIEM (Security Information and Event Management): Aggregates logs from firewalls, cloud apps, and endpoints to detect anomalies in real time. For example, SIEM tools like Splunk or LogRhythm correlate login attempts across systems to flag brute-force attacks.
SOAR (Security Orchestration, Automation, and Response): Automates threat containment, slashing response times. Imagine automatically isolating a compromised server before ransomware spreads.
XDR (Extended Detection and Response): Unified visibility across networks, endpoints, and cloud environments. XDR platforms like CrowdStrike Falcon uncover hidden threats in multi-cloud setups.
Threat Intelligence Feeds: Constantly updated feeds track new malware variants, vulnerabilities, and cybercrime tactics, allowing preemptive defense strategies.
1.2 Zero Trust Architecture (ZTA): No More Blind Trust
Micro-Segmentation: Limits lateral movement by isolating network segments. For instance, separating finance data from general employee access.
MFA & IAM: Multi-factor authentication and role-based access ensure only verified users get in. Tools like Okta enforce least-privilege access.
EDR (Endpoint Detection and Response): Monitors endpoints for behavioral anomalies, such as unusual file encryption patterns signaling ransomware.
Continuous Authentication: AI-driven authentication models assess user behavior dynamically, reducing risks of credential-based attacks.
1.3 AI-Driven Threat Detection: Outsmarting Attackers
UEBA (User and Entity Behavior Analytics): Uses machine learning to flag suspicious activity (e.g., Dave in accounting suddenly accessing sensitive files at 3 AM).
Predictive Analytics: Anticipates attack vectors using historical data. For example, identifying phishing campaigns targeting your industry.
Deep Learning-Based Malware Detection: Identifies previously unknown threats by analyzing patterns and behaviors rather than signatures.
1.4 Compliance Frameworks: Building a Regulatory Fortress
Managed IT Services align with frameworks like:
NIST Cybersecurity Framework (CSF): Risk-based strategies for identifying, protecting, and recovering from threats.
MITRE ATT&CK: Simulates real-world attacks to harden defenses. Red team exercises mimic APT groups like Lazarus.
CIS Controls: Automates audits for critical safeguards like data encryption and access controls.
ISO 27001 & GDPR Compliance: Ensures global security standards are met.
Case Study: A healthcare client reduced HIPAA violation risks by 80% through encrypted EHR systems and quarterly audits.
2. Cloud-Managed IT Services: Efficiency Meets Enterprise-Grade Security
Imagine an IT team that never sleeps, scales on demand, and cuts costs—all while securing your data. That’s cloud-managed IT.
2.1 Cloud Security Posture Management (CSPM)
Scans for misconfigured storage buckets (e.g., exposed AWS S3 instances). Tools like Palo Alto Prisma Cloud auto-remediate gaps.
Monitors IAM permissions to prevent overprivileged access. For example, revoking admin rights for temporary contractors.
Automated Compliance Audits: Ensures cloud environments align with regulatory policies.
2.2 Secure Access Service Edge (SASE)
Integrates Zero Trust with cloud-delivered security:
CASB (Cloud Access Security Broker): Secures SaaS apps like Office 365.
SWG (Secure Web Gateway): Blocks malicious URLs in real time.
FWaaS (Firewall as a Service): Replaces legacy hardware with scalable cloud firewalls.
ZTNA (Zero Trust Network Access): Prevents unauthorized access through software-defined perimeters.
2.3 Disaster Recovery as a Service (DRaaS)
Immutable Backups: Unalterable backups ensure data integrity. Veeam and Rubrik prevent ransomware from corrupting backups.
Multi-Region Failover: Keeps businesses running during outages. A retail client maintained uptime during an AWS outage by failing over to Azure.
Automated Recovery Testing: Regular tests ensure recovery strategies remain effective.
2.4 Cost Savings & Flexibility
Pay-as-you-go: Only pay for the cloud resources you use. Startups save 40% compared to on-premise setups.
Infrastructure as Code (IaC): Automates deployments using Terraform or AWS CloudFormation, reducing human error.
Statistic: Gartner predicts 60% of enterprises will use cloud-managed services by 2025 for cost and agility benefits.
Resource Optimization Strategies: AI-driven cloud cost optimization minimizes wasteful spending.
3. Incident Response and Disaster Recovery: When Seconds Matter
3.1 Automated Incident Response
Prebuilt Playbooks: For ransomware, isolate infected devices and trigger backups. For DDoS, reroute traffic via CDNs like Cloudflare.
Threat Containment: Automated network isolation of compromised assets. A financial firm contained a breach in 12 minutes vs. 4 hours manually.
AI-Based Incident Prediction: Uses past incidents to anticipate and mitigate future threats proactively.
3.2 Next-Gen Firewalls (NGFW)
Deep Packet Inspection (DPI): Uncovers hidden malware in encrypted traffic.
Behavioral Analytics: Detects zero-day exploits by analyzing traffic patterns.
Deception Technology: Uses decoy systems to detect attackers before they reach critical systems.
3.3 Digital Forensics and Threat Hunting
Malware Analysis: Reverse-engineers ransomware to identify kill switches.
Proactive Hunting: Combines AI alerts with human expertise. One MSP uncovered a dormant APT group during a routine hunt.
Blockchain-Based Security Logging: Ensures forensic logs remain immutable and tamper-proof.
4. Choosing the Right Managed IT Service Provider
4.1 Key Evaluation Criteria
Expertise in Frameworks: Look for NIST, ISO 27001, or CIS certifications.
24/7 Support: Ensure SOC teams operate in shifts for round-the-clock coverage.
Industry Experience: Healthcare providers need HIPAA experts; fintechs require PCI DSS mastery.
Customization Capabilities: Managed IT should be tailored to unique business needs.
4.2 In-House vs. Managed Services: A Cost Comparison
Mid-Sized Business Example:
In-House: $200k/year for salaries, tools, and training.
Managed Services: $90k/year with predictable pricing and no overhead.
5. Conclusion: Future-Proof Your Business
Cyber threats evolve, but so do Managed IT Services. With AI, Zero Trust, and cloud agility, businesses can stay ahead of attackers.
At Hardwin Software Solutions, we merge 24/7 SOC vigilance, compliance expertise, and scalable cloud solutions to shield your business.
📞 Contact us today—because cybercriminals don’t wait, and neither should you.
FAQs :
1. How long does it take to onboard Managed IT Services, and when will we see results?
Onboarding: Typically 2–4 weeks, depending on infrastructure complexity. This includes risk assessments, tool integration (e.g., SIEM, XDR), and policy alignment.
Results: Proactive threat detection begins immediately, but full optimization (e.g., AI-driven threat modeling, Zero Trust implementation) takes 60–90 days.
2. Can Managed IT Services integrate with our legacy systems, or do we need a full infrastructure overhaul?
Yes! Managed IT providers use hybrid frameworks to secure legacy systems:
API-based integrations for outdated software.
Network segmentation to isolate legacy systems from modern attack surfaces.
Virtual patching to shield unpatched legacy apps from exploits.
3. How do you defend against AI-powered cyberattacks, like deepfake phishing or adaptive malware?
We counter AI-driven threats with:
Behavioral AI models: Detect anomalies in communication patterns (e.g., deepfake voice calls).
Adversarial Machine Learning: Trains defense systems to recognize AI-generated attack patterns.
Threat Hunting Teams: Human experts validate AI alerts to avoid false positives.
4. Do you offer industry-specific compliance solutions beyond HIPAA and GDPR (e.g., CMMC for defense contractors)?
Absolutely. We tailor compliance to your sector:
CMMC for defense contractors.
PCI DSS for payment processors.
FERPA for education.
Custom audits and controls to meet frameworks like NERC CIP (energy) or ISO 27701 (privacy).
5. How do you measure the ROI of Managed IT Services for stakeholders?
We quantify ROI through:
MTTD/MTTR Reductions: Track mean time to detect/respond to incidents (e.g., 30% faster threat neutralization).
Downtime Costs: Calculate savings from preventing outages (e.g., $10K/minute saved for e-commerce).
Compliance Penalty Avoidance: Estimate fines dodged via audit-ready systems.
Productivity Metrics: Reduced IT ticket volume (e.g., 50% fewer disruptions).
0 notes
Text
Cybersecurity Solutions for a Safer Digital World
At Spearhead Technology, we understand that cyber threats are evolving rapidly, making robust cybersecurity a necessity for businesses of all sizes. Our cutting-edge cybersecurity solutions are designed to safeguard your data, networks, and digital assets from malicious attacks, ensuring business continuity and compliance.
Our Cybersecurity Services
1. Threat Detection & Prevention
We employ AI-powered threat intelligence to identify vulnerabilities and mitigate risks before they escalate into full-scale attacks. Our proactive approach ensures real-time protection against malware, ransomware, phishing, and other cyber threats.
2. Network Security
From firewalls to intrusion detection systems, we provide a multi-layered defense strategy to secure your network against unauthorized access and cyber intrusions.
3. Cloud Security
With businesses rapidly migrating to the cloud, we ensure that your cloud environments—whether AWS, Azure, or Google Cloud—are fortified against data breaches, insider threats, and compliance risks.
4. Endpoint Protection
Every connected device is a potential entry point for hackers. Our advanced endpoint security solutions protect laptops, mobile devices, and IoT systems from cyber threats.
5. Security Compliance & Risk Management
Navigating complex regulatory requirements can be challenging. We help businesses comply with industry standards such as GDPR, HIPAA, and NIST while minimizing cybersecurity risks.
6. Incident Response & Recovery
In the event of a cyberattack, our rapid incident response team ensures minimal downtime. We provide comprehensive forensic analysis, threat containment, and recovery solutions to restore normal operations quickly.
Why Choose Spearhead Technology?
Cutting-Edge Security Solutions— We leverage the latest advancements in cybersecurity technology to keep you ahead of emerging threats. 24/7 Monitoring & Support – Our dedicated cybersecurity team provides round-the-clock monitoring and rapid response to potential threats. Customized Protection Plans—We tailor cybersecurity strategies to fit your unique business needs and industry regulations. Proven Expertise—With years of experience in the cybersecurity field, we are trusted by businesses across various sectors.
Secure Your Business Today
Don’t wait for a cyberattack to expose vulnerabilities in your systems. Protect your business with Spearhead Technology’s cybersecurity solutions. Contact us today for a consultation!
0 notes
Text
Empowering Businesses with Due Diligence, Cyber Forensics, and Server Management: Synovatic Cyber Solutions
Synovatic Cyber Solutions is a leading provider of comprehensive cybersecurity and IT management services, specializing in Due Diligence, Cyber Forensics, and Server Management. With a commitment to empowering businesses through technology, Synovatic ensures operational resilience and data security.

Due Diligence Services
In today's fast-paced business environment, Due Diligence is essential for evaluating potential investments, partnerships, and acquisitions. Synovatic Cyber Solutions conducts thorough assessments to uncover financial, operational, and cybersecurity risks. By providing detailed insights into a company's digital infrastructure, regulatory compliance, and data security posture, Synovatic helps clients make informed decisions and avoid costly pitfalls. Businesses rely on Synovatic’s expertise to mitigate hidden vulnerabilities, ensuring that mergers and acquisitions proceed smoothly and securely.
Advanced Cyber Forensics
Cyber threats are evolving faster than ever, making Cyber Forensics an indispensable service for organizations aiming to protect their digital assets. Synovatic Cyber Solutions excels in investigating, analyzing, and mitigating cyber incidents. Whether it's a data breach, malware attack, or insider threat, Synovatic's forensic experts swiftly trace the source, gather critical evidence, and provide actionable recommendations. This ensures businesses recover faster while minimizing legal and financial repercussions. Synovatic’s Cyber Forensics services are designed to not only address immediate threats but also strengthen long-term cybersecurity defenses.
Reliable Server Management
For any modern business, robust Server Management is the backbone of IT infrastructure. Synovatic Cyber Solutions offers end-to-end server management services to ensure maximum uptime, security, and performance. From regular monitoring and maintenance to software updates and emergency troubleshooting, Synovatic’s team ensures servers run smoothly and efficiently. By optimizing server performance and preventing potential failures, businesses can focus on their core operations without worrying about downtime or data loss.
Why Choose Synovatic Cyber Solutions?
Synovatic Cyber Solutions combines cutting-edge technology with industry expertise to deliver tailored solutions for Due Diligence, Cyber Forensics, and Server Management. Their client-focused approach ensures that each service is customized to meet the unique needs of the business, enhancing operational efficiency and cybersecurity resilience. With a track record of success across various industries, Synovatic remains a trusted partner for businesses seeking reliable and forward-thinking IT solutions.
Discover how Synovatic Cyber Solutions can protect your business and drive growth through expert Due Diligence, advanced Cyber Forensics, and top-notch Server Management services. Visit synovatic.org to learn more and take your business’s cybersecurity to the next level.
0 notes
Text
Website: https://www.turacolabs.com/
Address: 31a Charnham Street, Hungerford, Berkshire, RG17 0EJ, United Kingdom
Turaco Labs specializes in eCommerce cybersecurity, offering ThreatView, a state-of-the-art cyber threat detection and PCI DSS compliance monitoring solution. Their services focus on protecting online businesses from malware, digital skimmers, loaders, and data theft. With a free security scan, breach protection warranty, and forensic-level monitoring, they provide a proactive defense system for online stores using platforms such as Magento, WordPress, OpenCart, and Joomla. Their ThreatView solution ensures continuous monitoring, detects the latest cybersecurity threats, and helps eCommerce merchants comply with PCI DSS standards.
LinkedIn: https://www.linkedin.com/company/turaco-labs-threatview/
Keywords: eCommerce cyber security website malware scan scan website for malware PCI compliance monitoring free website security scan website security monitoring website compliance audit security services website website malware scanning tools eCommerce security solutions eCommerce fraud prevention ecommerce fraud prevention companies prevent ecommerce fraud website malware scanner PCI compliance services pci compliance service provider pci compliance consulting services cybersecurity services for small businesses Magecart protection Google Tag Manager malware hacked website recovery eCommerce security best practices website security services malware removal from weebly website website malware removal website malware removal service how do i remove malware from my website how to remove malware from website how to remove malware from wordpress website malware removal for websites malware removal website remove malware from website best website malware removal how to remove virus from website website protection services best website protection service website malware protection services ecommerce fraud protection services
#eCommerce cyber security#website malware scan#scan website for malware#PCI compliance monitoring#free website security scan#website security monitoring#website compliance audit#security services website#website malware scanning tools#eCommerce security solutions#eCommerce fraud prevention#ecommerce fraud prevention companies#prevent ecommerce fraud#website malware scanner
1 note
·
View note
Text

At Pepoint Solution, we provide a full suite of IT services, from web and app development to digital marketing, AI solutions, and cybersecurity.
#cyber security#cyber sigilism#cyberart#ethicalhacking#cyber security services#cyber security companies#cyber security solutions#data protection
1 note
·
View note
Text
Managed IT, Computer Networking, Cyber Security Support, Cloud IT Services and More in Levittown, King of Prussia, Abington, Cheltenham, PA, Trenton, Hamilton, NJ, and the Surrounding Areas
Alpha IT Solutions: IT with a Personal Touch
Our team at Alpha IT Solutions aims to provide a full range of IT and Cyber security services to protect your business from today and tomorrow's challenges. We provide computer network operational and security services with a strong emphasis in the financial industry. We handle computer networking, IT service management, networking security, and preventative services including computer network security and risk audits, assessments, and evaluations.
We take care of IT cloud security and managed IT. Please speak with an IT consultant about tech support options and cloud IT services. Find out how we address cyber security support by calling us at (215) 550-1222.
#Smart Home#Network Solutions#Home Automation#disaster recovery#cyber security#Computer Service#Business Continuity
0 notes
Text
#web development service#e commerce website development service#web development company#web app development services#web and mobile app development services#it management service#it management solutions#it infrastructure management services#it service management consulting#it service operations management#cyber security service#cyber security company#cyber security solution#cyber security service provider#cyber security consultation#cloud computing services#cloud computing companies#best cloud service provider#cloud computing security#best cloud computing services#iot services#iot solutions#iot development services#iot software development#iot network solutions#hr services#staffing service provider#hr recruitment solutions#hr services company#staffing solutions provider
0 notes
Text
Microsoft 365 Business Apps deliver versatile tools to help organizations streamline operations and improve productivity. When combined with IT managed services in Lanham, Maryland, businesses gain support for seamless Microsoft 365 integration and reliable day-to-day management. Core apps like Outlook, Word, and Excel keep essential tasks organized, while cloud services make document sharing, scheduling, and collaboration more accessible and secure.
0 notes