#endpoint security market share
Text
#endpoint security market report#endpoint security industry report#endpoint security market#endpoint security market share#endpoint security market size#endpoint security market trends#endpoint security market growth#endpoint security market analysis#endpoint security market forecast
0 notes
Text
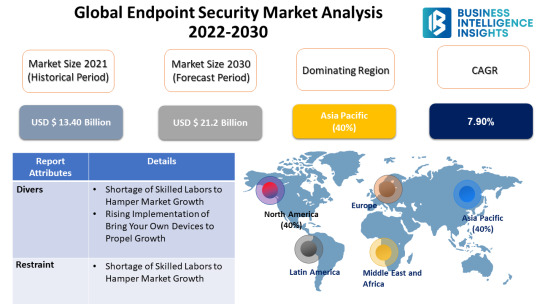
As per Business Intelligence Insights (BII) study, the global Global Endpoint Security Market attained revenue growth of USD 13.40 billion in 2021 and it is projected to reach around USD 21.2 billion by 2030, growing at a 7.90% CAGR.
#Endpoint Security Market#Endpoint Security Market Market#Endpoint Security Market Market Trends#Endpoint Security Market Market Share#Endpoint Security Market Market Size#Endpoint Security Market Market Analysis#Endpoint Security Market Market Demand#Endpoint Security Market Market Growth 2023#Endpoint Security Market Market Industry
0 notes
Text
Global Industrial Cybersecurity Market Size[271 Pages Report] The global industrial cybersecurity market size is expected to growing at a CAGR of 7.7%, from USD 16.3 billion in 2022 to USD 24.4 billion in 2028. The primary reasons for this rise in demand for industrial cybersecurity products in power industry.
0 notes
Text
Endpoint Security Market Size, Share, Trend, Forecast, & Growth Analysis: 2024-2032
Endpoint Security Market 2024 Report: A Comprehensive Analysis of Historical and Current Market Trends with Strategic Insights.
Analysis of the global "Endpoint Security Market" shows that the market will develop steadily and strongly between 2024 and 2032, and projections indicate that this growth will continue through 2032. The increasing demand from consumers for ecologically friendly and sustainable products is a noteworthy development in the Endpoint Security Market. To improve the effectiveness and caliber of products in the Endpoint Security Market, technology has also been used much more frequently.
➼ Market Capacity:
Between 2017 and 2023, the Endpoint Security Market's value increased significantly, from US$ million to US$ million. With a compound annual growth rate (CAGR) predicted to reach US$ million by 2032, this momentum is anticipated to continue. An extensive analysis explores consumer preferences and purchasing patterns in this industry, broken down by type (Trend Micro (Japan), Eset (U.S.), Symantec (U.S.), Sophos (U.K.), McAfee (U.S.)). Based on extensive research, this perceptive analysis is anticipated to be a useful tool for industry participants looking to profit from the market's remarkable anticipated compound annual growth rate (2024–2032).
➼ Key Players:
List of Endpoint Security Market PLAYERS PROFILED
The Endpoint Security Market includes several key players such as Cloud, On-Premises, Other play crucial roles in this market.
Endpoint Security Market Report Contains 2024: -
Complete overview of the global Endpoint Security Market
Top Country data and analysis for United States, Canada, Mexico, Germany, France, United Kingdom, Russia, Italy, China, Japan, Korea, India, Southeast Asia, Australia, Brazil and Saudi Arabia, etc. It also throws light on the progress of key regional Endpoint Security Markets such as North America, Europe, Asia-Pacific, South America and Middle East and Africa.
Description and analysis of Endpoint Security Market potentials by type, Deep Dive, disruption, application capacity, end use industry
impact evaluation of most important drivers and restraints, and dynamics of the global Endpoint Security Market and current trends in the enterprise
Value Propositions of This Market Research:
The study covers a comprehensive analysis of industry drivers, restraints, and opportunities, providing a neutral perspective on the market performance. It highlights recent industry trends and developments, offering insights into the competitive landscape and the strategies employed by key players. The study identifies potential and niche segments and regions exhibiting promising growth, supported by historical, current, and projected market size data in terms of value. An in-depth analysis of the Endpoint Security Market is included, along with an overview of the regional outlook. This holistic approach ensures a thorough understanding of the market dynamics and potential growth areas.
Request a Free Sample Copy
Global Endpoint Security Market: SEGMENTATION ANALYSIS
The research report includes specific segments by region (country), manufacturers, Type, and Application. Market segmentation creates subsets of a market based on product type, end-user or application, Geographic, and other factors. By understanding the market segments, the decision-maker can leverage this targeting in product, sales, and marketing strategies. Market segments can power your product development cycles by informing how you create product offerings for different segments.
➼ PRODUCTS/SERVICES:
Valuable Points from Endpoint Security Market Research Report 2024-2032:
The market for Endpoint Security Market has undergone significant changes because to changing consumer preferences, laws, and technological advancements. This dynamic business is being shaped by new product launches, mergers, and creative marketing strategies from big players. A thorough analysis of recent and historical data yields insights into the market's value, volume, historical growth, current size, and potential for the future. While competition research explores market share and strategy, segmentation by key regions exposes regional variances. The research provides practical suggestions to help you improve your position in this dynamic market and finds new niches and development possibilities across regions.
Request a Free Sample Copy
Behind the Brand
In an industry characterized by rapid growth and technological advancements, economic changes occur daily. To thrive in this dynamic environment, companies must understand market trends and develop effective strategies. A well-defined strategy not only facilitates planning but also offers a competitive edge. For dependable market reports that provide essential insights to guide your business toward success, visit us at www.globalmarketstatistics.com .
Explore More Related Reports Here :
Fantasy Games Market
Relational Databases Software Market
High Pressure Composite Gas Cylinder Market
Privacy Compliance Consulting Services Market
BNC Connector Market
Car Recycling Market
Smart Construction Excavator Market
Continuous Passive Motion Devices Market
Kubernetes Security Software Market
Warehouse Shuttle Car Market
Residual Current Detectors Market
Titanium Elastic Nail Market
Industrial Counterweights Market
Magnetic Resonance Imaging Market
Micro-Compact Cars Market
#innovation#management#digitalmarketing#technology#creativity#futurism#startups#marketing#entrepreneurship#money#sustainability#inspiration#Leadership#Business#Strategy#Growth#Success#Innovation#Ecommerce#PersonalDevelopment
1 note
·
View note
Text
Security Automation Market Outlook On The Basis Of Offering, Deployment Mode, Application, Code Type, Vertical, Technology, Region And Forecast To 2030: Grand View Research Inc.
San Francisco, 10 Sep 2024: The Report Security Automation Market Size, Share & Trends Analysis Report By Offering, By Deployment, By Application (Network Security, Endpoint Security), By Technology, By Code Type, By Vertical, By Region, And Segment Forecasts, 2024 – 2030
The global security automation market size is expected to reach USD 22.92 billion by 2030, growing at a CAGR of 14.0% from…

View On WordPress
0 notes
Text
0 notes
Text
Competitive Landscape: Analyzing Zscaler's Key Rivals
Zscaler Inc. is a leading provider of cloud security solutions, offering businesses a comprehensive platform to secure their digital transformation. With its Zero Trust Exchange architecture, Zscaler has revolutionized the way enterprises approach cybersecurity, particularly in a cloud-first world. This article provides an in-depth analysis of Zscaler's competitive landscape, highlighting the key players in the market and how Zscaler's innovative approach positions it against its competitors.
Overview of the Cloud Security Market
The cloud security market is rapidly growing, driven by the increasing adoption of cloud services and the need for robust security solutions to protect against evolving cyber threats. As organizations continue to migrate their operations to the cloud, the demand for secure access solutions, data protection, and threat intelligence has surged. In this competitive landscape, Zscaler stands out with its unique Zero Trust approach, which eliminates the need for traditional network security architectures.
Key Competitors in the Cloud Security Space
Zscaler operates in a highly competitive market, with several established players vying for market share. Some of the key competitors include:
Palo Alto Networks: A global leader in cybersecurity, Palo Alto Networks offers a broad portfolio of security solutions, including firewalls, cloud security, and endpoint protection. The company’s Prisma Access platform is a direct competitor to Zscaler, offering secure access to applications and data from anywhere.
Cisco Systems: Cisco is a well-known player in the network and cybersecurity space, offering a range of products, including secure access solutions, firewalls, and threat intelligence. Cisco's Umbrella platform competes with Zscaler's offerings, providing cloud-delivered security to protect users both on and off the corporate network.
Fortinet: Fortinet is another significant competitor, known for its integrated and automated cybersecurity solutions. Fortinet's Security Fabric platform is designed to secure all points of the digital attack surface, and its Secure SD-WAN solution competes with Zscaler's cloud security platform.
Akamai Technologies: Akamai is a key player in the content delivery and cloud security markets. Its Zero Trust Enterprise Security platform is a direct competitor to Zscaler, offering secure access to applications without the need for traditional VPNs or firewalls.
Zscaler's Competitive Advantages
Zscaler’s primary competitive advantage lies in its Zero Trust Exchange architecture, which provides a holistic approach to securing users, applications, and data in the cloud. Unlike traditional security solutions that rely on network perimeter defenses, Zscaler’s platform is designed to secure access based on the principles of Zero Trust, where no user or device is trusted by default.
Scalability and Global Reach: Zscaler’s cloud-native architecture allows it to scale rapidly and efficiently, providing seamless security for enterprises of all sizes. With data centers located across the globe, Zscaler ensures low latency and high availability, which is crucial for global enterprises.
Integration and Ecosystem: Zscaler offers robust integrations with leading cloud service providers such as AWS, Microsoft Azure, and Google Cloud Platform. This allows organizations to seamlessly integrate Zscaler’s security solutions into their existing cloud environments, enhancing their overall security posture.
Innovation and R&D: Zscaler continually invests in research and development, staying ahead of emerging threats and ensuring its platform remains at the cutting edge of cybersecurity. The company’s focus on AI and machine learning has enabled it to develop advanced threat detection and response capabilities, further strengthening its competitive position.
Challenges and Market Dynamics
While Zscaler has established itself as a leader in cloud security, it faces several challenges that could impact its market position:
Intense Competition: The cloud security market is highly competitive, with major players continuously innovating and expanding their product offerings. Zscaler must remain agile and responsive to market changes to maintain its competitive edge.
Customer Acquisition and Retention: As the market becomes more crowded, acquiring and retaining customers becomes increasingly challenging. Zscaler’s ability to demonstrate clear ROI and the value of its Zero Trust approach will be crucial in winning and keeping customers.
Regulatory Compliance: As data privacy regulations evolve globally, Zscaler must ensure its solutions comply with regional and international standards. Failure to meet these requirements could result in penalties or loss of business opportunities.
Conclusion
Zscaler Inc. is a formidable player in the cloud security market, with a strong competitive position built on its innovative Zero Trust Exchange architecture. While it faces stiff competition from established cybersecurity companies like Palo Alto Networks, Cisco Systems, and Fortinet, Zscaler’s focus on Zero Trust, scalability, and continuous innovation sets it apart in the industry. However, the company must navigate challenges such as intense competition and regulatory compliance to sustain its growth and market leadership.
0 notes
Text

The digital landscape is constantly evolving, and unfortunately, so are the threats that plague it. Malicious software development, often abbreviated as malware development, has become a booming underground industry, churning out ever-more sophisticated threats designed to steal data, disrupt operations, and inflict financial damage.
This poses a significant challenge for individuals and businesses alike, particularly in the United States, a prime target for cybercriminals due to its vast digital infrastructure and economic power. Here, we'll delve into the concerning rise of malware development, explore the evolving tactics of cybercriminals, and highlight how Sohojware (https://sohojware.com) is fortifying its proactive security measures to safeguard its clients.
The Alarming Rise of Malware Development
The malware development industry is fueled by significant financial gains. By compromising systems and stealing sensitive information, cybercriminals can extort victims, sell stolen data on the black market, or disrupt critical operations for ransom. This lucrative incentive has led to a surge in malware development, with new threats emerging at an alarming rate.
According to a recent report by Cybersecurity Ventures, global ransomware damage costs are projected to reach a staggering $26 billion by 2 This highlights the immense financial strain that malware development inflicts on businesses worldwide.
Evolving Tactics of Cybercriminals
Cybercriminals behind malware development are constantly innovating their tactics. Here are some of the concerning trends:
Ransomware as a Service (RaaS): This model allows less technical attackers to leverage pre-developed malware for a share of the ransom profits. This democratizes cyberattacks, making them more accessible and widespread.
Supply Chain Attacks: Targeting trusted vendors and software providers allows attackers to infiltrate a vast network of systems through a single point of entry.
Fileless Malware: This type of malware doesn't rely on traditional executables, making it more challenging to detect with conventional antivirus software.
Social Engineering: Deceptive tactics like phishing emails and phone scams are used to trick victims into revealing sensitive information or downloading malware.
These are just a few examples, and cybercriminals are constantly developing new methods to exploit vulnerabilities.
Sohojware's Commitment to Proactive Security
At Sohojware (https://sohojware.com), we understand the gravity of the malware development threat. We are committed to providing our clients with robust security solutions that are constantly evolving to stay ahead of the curve. Here's how we're fortifying our security measures:
Threat Intelligence: We maintain a comprehensive threat intelligence feed, allowing us to stay abreast of the latest malware development trends and vulnerabilities.
Security Awareness Training: We offer security awareness training programs to educate our clients and their employees on how to identify and avoid malware threats.
Multi-Layered Security Solutions: We employ a layered security approach that combines firewalls, intrusion detection systems, endpoint protection, and regular security assessments to mitigate malware risks.
Regular Patch Management: We prioritize timely patching of vulnerabilities to minimize the window of opportunity for malware exploits.
Incident Response Planning: We have a comprehensive incident response plan in place to effectively address and contain malware incidents should they occur.
By proactively addressing the evolving threat landscape of malware development, Sohojware empowers its clients to operate with greater peace of mind in the digital world.
FAQs about Sohojware and Malware Development
1. How can Sohojware help me protect my business from malware development?
Sohojware offers a comprehensive suite of security solutions designed to mitigate malware risks. We can conduct security assessments, implement multi-layered security solutions, and provide ongoing monitoring and threat intelligence to safeguard your business.
2. Does Sohojware offer security awareness training for employees?
Yes, Sohojware offers security awareness training programs that educate employees on how to identify and avoid malware threats. This training empowers your workforce to become a vital line of defense against cyberattacks.
3. What is Sohojware's incident response plan for malware attacks?
Sohojware has a comprehensive incident response plan that outlines the steps we take to identify, contain, and remediate malware incidents. This plan ensures a swift and effective response to minimize damage.
4. How does Sohojware stay updated on the latest malware development trends?
Sohojware maintains a subscription to a comprehensive threat intelligence feed. This allows us to stay informed about the latest malware development tactics and vulnerabilities, enabling us to proactively adjust our security measures.
5. Can Sohojware help me recover my data if it's encrypted by ransomware?
Yes, Sohojware offers incident response services that can assist in recovering your data after a ransomware attack. While we cannot guarantee data recovery in all cases, our experts will work diligently to develop a recovery plan tailored to your specific situation. We also provide guidance on data backup and recovery best practices to help prevent future data loss.
Conclusion
The relentless evolution of malware development underscores the critical importance of robust cybersecurity measures. By staying informed about the latest threats and implementing proactive security strategies, businesses and individuals can significantly reduce their risk of falling victim to cyberattacks. Sohojware (https://sohojware.com) is committed to helping you navigate this complex landscape and protect your valuable assets.
Remember: The key to effective cybersecurity lies in a multi-layered approach that includes technology, employee training, and ongoing vigilance.
By partnering with Sohojware, you're taking a proactive step towards safeguarding your digital world.
1 note
·
View note
Text
The worldwide Mobile Threat Defense Market will expand at a compound annual growth rate (CAGR) of 26.50%. From USD 2154.8 million in 2022, the market is projected to be worth USD 14129.6 million by 2030.In the rapidly evolving digital landscape, mobile devices have become indispensable tools for communication, business, and personal use. With the increasing reliance on smartphones and tablets, the need for robust security solutions to protect these devices from cyber threats has surged. The Mobile Threat Defence (MTD) market has emerged as a critical component in safeguarding mobile ecosystems from a wide array of threats. This article delves into the current state of the Mobile Threat Defence market, its drivers, challenges, and future prospects.
Browse the full report at https://www.credenceresearch.com/report/mobile-threat-defence-market
Market Overview
The Mobile Threat Defence market encompasses a range of security solutions designed to protect mobile devices from threats such as malware, phishing attacks, data breaches, and other cyber risks. MTD solutions provide comprehensive protection by leveraging advanced technologies such as machine learning, artificial intelligence, and real-time threat intelligence. According to recent market research, the MTD market is experiencing significant growth, driven by the increasing prevalence of mobile devices and the escalating sophistication of cyber threats.
Key Drivers of Market Growth
1. Rising Mobile Device Adoption: The proliferation of smartphones and tablets across various sectors, including enterprises, healthcare, finance, and government, has heightened the need for effective mobile security solutions. As organizations continue to embrace mobile technologies for enhanced productivity and connectivity, the demand for MTD solutions has grown correspondingly.
2. Increasing Cyber Threats: Mobile devices are increasingly targeted by cybercriminals due to their widespread use and the sensitive information they store. Threats such as mobile malware, phishing attacks, and insecure app downloads pose significant risks to both individual users and organizations. The growing frequency and sophistication of these threats have driven the need for advanced MTD solutions.
3. Regulatory Compliance: Governments and regulatory bodies worldwide are implementing stringent data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). These regulations mandate organizations to protect sensitive data, including that stored on mobile devices, thereby boosting the demand for MTD solutions to ensure compliance.
4. Shift to Remote Work: The COVID-19 pandemic has accelerated the adoption of remote work, leading to an increase in the use of personal and company-issued mobile devices for work-related tasks. This shift has expanded the attack surface for cyber threats, further emphasizing the need for robust mobile security measures.
Market Challenges
Despite the growth prospects, the Mobile Threat Defence market faces several challenges:
1. Complexity of Threat Landscape: The rapidly evolving nature of cyber threats makes it challenging for MTD solutions to keep pace. Attackers continually develop new tactics and techniques, requiring MTD providers to continuously innovate and adapt their solutions.
2. Integration Issues: Integrating MTD solutions with existing IT infrastructure and security systems can be complex. Ensuring seamless interoperability between MTD solutions and other security tools, such as endpoint protection and network security systems, is crucial for comprehensive protection.
3. Cost Considerations: For many organizations, especially small and medium-sized enterprises (SMEs), the cost of implementing advanced MTD solutions can be a significant barrier. Balancing the need for robust security with budget constraints remains a challenge for these organizations.
Future Outlook
The future of the Mobile Threat Defence market appears promising, with several trends shaping its trajectory:
1. Advancements in AI and Machine Learning: The integration of artificial intelligence (AI) and machine learning (ML) into MTD solutions is expected to enhance threat detection and response capabilities. AI-powered solutions can analyze vast amounts of data to identify patterns and anomalies, providing more accurate and timely protection against emerging threats.
2. Growth of 5G Technology: The rollout of 5G networks will drive increased data speeds and connectivity, potentially creating new security challenges. MTD solutions will need to evolve to address the security implications of 5G technology and ensure robust protection for devices connected to these networks.
3. Enhanced Focus on Privacy: As concerns about data privacy continue to grow, there will be an increased emphasis on solutions that not only protect against threats but also ensure the confidentiality and integrity of user data. MTD providers will need to prioritize privacy features and compliance with data protection regulations.
4. Collaboration and Integration: Future MTD solutions are likely to focus on greater integration and collaboration with other security technologies and platforms. This holistic approach will enable more effective threat management and provide a unified security framework for organizations.
Key Players
Cisco Systems
SAP SE
Broadcom, Inc.
VMware
Citrix Systems
Kaspersky Labs
Ivanti
Micro Focus
ZOHO
SolarWinds
Zimperium
Matrix42
Sophos
BlackberryEsper
Segmentation
By Security Threat Type:
Malware Protection
Phishing Protection
Data Loss Prevention (DLP)
Network Security
App Security
Device Security
By Deployment Model:
Cloud-based
On-Premises
Hybrid
By Organization Size:
Small and Medium-sized Enterprises (SMEs)
Large Enterprises
By End Users:
Enterprises
Government and Public Sector
Individuals and Consumers
BY Operating System:
Android
iOS
Multi-OS Compatibility
By Industry Verticals:
Financial Services
Healthcare
Retail
Telecommunications
Government and Defense
Energy and Utilities
Other Verticals
By Regulatory Compliance and Standards:
GDPR Compliance
HIPAA Compliance
Industry-specific Compliance
By Region
North America
US
Canada
Mexico
Europe
Germany
France
UK
Italy
Spain
Rest of Europe
Asia Pacific
China
Japan
India
South Korea
South-east Asia
Rest of Asia Pacific
Latin America
Brazil
Argentina
Rest of Latin America
Middle East & Africa
GCC Countries
South Africa
Rest of Middle East and Africa
Browse the full report at https://www.credenceresearch.com/report/mobile-threat-defence-market
About Us:
Credence Research is committed to employee well-being and productivity. Following the COVID-19 pandemic, we have implemented a permanent work-from-home policy for all employees.
Contact:
Credence Research
Please contact us at +91 6232 49 3207
Email: [email protected]
Website: www.credenceresearch.com
0 notes
Text
Seamlessly integrate with thousands of endpoints with Jitterbit

Workflow automation for every business
Jitterbit has awesome flexibilities to help businesses automate workflows by role, by solution and by use cases. Digital transformation to increase efficiency requires re-engineering of workflows. Jitterbit is very user friendly in defining workflows, be it for IT / HR / Customer Service / Marketing. Jitterbit is a low-code, iPaaS, EDI integrator. Various key use cases like Purchasing Workflow, Expense Management, Lead to Order, Order Fulfilment etc. are some common examples of workflow automation using Jitterbit.
Connect your SaaS, on-premise, and cloud apps
Whether you have SaaS products, on-premise, or cloud applications, Jitterbit can integrate different systems with ease. With easy-to-use, drag-and-drop, pre-built connectors, it’s effortless to streamline workflows and automate processes end to end. Jitterbit offers quicker, smarter and better RoI as an iPaaS when integration is concerned. Jitterbit has thousands of pre-built connectors and integrations is easy with a variety of systems like leading ERPs, CRMs, HRIS/HCMs, eCommerce products etc.
OdiTek’s Cloud Integration Services with Jitterbit
Oditek Solutions offers integration services on Jitterbit iPaaS, that can help businesses automate their workflows and business processes. Our team on Jitterbit middleware helps in data integration, data hub development, workflow automation, and API design, and we can help you unlock the full potential of Jitterbit for your business. With Jitterbit, users can create triggers and actions to automate various processes, from simple tasks like creating a new customer record to complex workflows that involve multiple apps and data sources.
Key Jitterbit Advantages
Efficient Integrations
Connect SaaS, on-premise & legacy apps with a single iPaaS solution. Automate workflows with an intuitive visual interface, access 400+ pre-built, certified recipes, process templates, & connectors.
Manage & Scale Easily
Control and monitor your integrations and processes anywhere, anytime. Get full visibility across the enterprise with a centralized dashboard. Perform full API lifecycle management tasks
Build Business Apps Superfast
Create with ease in a low code, “drag-and-drop” visual application builder. User-facing, business applications built from the integrations already created utilizing Harmony.
Highly Secure iPaaS
Harmony low-code integration platform ensures safe and secure integration processes by complying with GDPR, ISO 27001, SOC 1 and SOC 2, and HIPAA.
Seamlessly manage Trading Partners
Manage electronic data interchange (EDI) trading partners, create connections, and monitor transactions in one location.
Super easy creating integrations
Create integration workflows with a drag-and-drop interface for low-code integration. Jitterbit is intuitive and easy to use iPaaS.
Our Service Offering
Consulting Services
Uninterrupted Workflow
Optimizing the data integration
Access of Automation 360 Control Room
Automation of data transfer
Efficient API & EDI management
Architecting Services
Assessing system & challenges.
Identifying Integration patterns
On-prem/cloud app deployment
Capacity planning & assessment
System & app architecture review
Implementing Services
Testing and debugging of integrations
Automated deployment & support
App alerts configuration & fine-tuning
Configuration and customization
Compatibility with existing systems
Development Services
Reusable components, connectors
Custom APIs and integrations
Real-time data orchestration
Developing Custom connectors
Transforming data across formats
Designing Services
Business requirements analysis
Custom workflow design
Data mapping and transformation
Error handling & monitoring tools
Secure data transfer as per norms
Managed Services
Reduced costs & increased agility
Proactive & preventive Monitoring
Legacy and Disparate Data optimization
Easy collaboration via shared IT assets
Anypoint Platform environment
Platform Support & Services
24×7 support and monitoring
Performance tuning of applications
Automation & process improvements
Providing weekly & monthly reports
Root cause analysis & effective solution
Maintenance & Operation
Maintenance & timely updating tickets
Security audits for performance growth
Security and privacy compliance concerns
Customized maintenance contracts
Continuous Remote and desktop support
Planning & Testing Services
Defining timelines & resources
Assessing & analysing current state
Unit testing & system testing
Identifying and troubleshooting the issues
Post-deployment monitoring and testing
To know more about our service offerings
Click Here
Jitterbit’s Key Differentiators
A Master of ETL
Jitterbit’s powerful ETL tools and data integration solutions provide an intuitive, easy-to-use interface that simplifies data integration. Jitterbit helps reduce development costs, increase efficiencies, and eliminate risk. Whether you are using ETL processes for Data Warehousing, Business Intelligence or legacy systems integration initiatives, Jitterbit is designed to handle even the most complex tasks.
1234
OdiTek’s Jitterbit Expertise
Oditek offers cloud integration services for businesses in various industries. Our experienced team integrates, designs and implements Jitterbit-based solutions to seamlessly connect data sources. With Jitterbit’s iPaaS, we automate integration projects and configure pre-built connectors to ensure smooth data flows across applications and data stores.
Seamless Integration
Jitterbit offers unique integration capabilities and code-free structure link cloud, on-premise, and big data endpoints in real time across APIs, databases, and apps
Save Integration Costs
Enterprises can accelerate integration development by 70% and simplify tasks for tech specialists with Jitterbit’s AI-powered design feature, resulting in increased ROI
Reduce Ramp-Time
Cloud-based and AI-powered platforms provide real-time automation and enable monitoring and measuring of employee experience for improved productivity
Efficient Administration Console
Jitterbit’s intuitive web-based interface of the platform, empowers a Jitterbit developer to manage user tasks remotely with ease.
Discover the Expertise of Our Jitterbit Integration Specialists
To know more about Jitterbit check our website OdiTek
1 note
·
View note
Text
Next - Gen cyber security

Introduction
Welcome and Orientation
Overview of the Next-Gen Cyber Security Skills course in Bangalore
Introduction to instructors and fellow participants
Setting goals and expectations for the course
Module 1: Foundations of Cyber Security
Understanding Cyber Security
Definition and importance of cyber security in today’s world
Current landscape and emerging threats
Cyber Security Terminology
Key terms and concepts crucial for the Bangalore cyber security course
Overview of common attack vectors and defenses
Cyber Security Frameworks and Standards
NIST Cybersecurity Framework
ISO/IEC 27001
CIS Controls and their relevance to Bangalore’s cyber security environment
Module 2: Network Security
Network Security Fundamentals
Basic networking concepts vital for Bangalore cyber security professionals
Understanding firewalls, VPNs, and IDS/IPS
Securing Network Infrastructure
Techniques for network segmentation and isolation
Secure network design and architecture
Wireless Network Security
Wireless security protocols (WPA3, WPA2)
Securing wireless access points in a Bangalore context
Module 3: Application Security
Introduction to Application Security
Common vulnerabilities (OWASP Top Ten)
Secure coding practices essential for Bangalore developers
Web Application Security
Addressing Cross-Site Scripting (XSS) and SQL Injection
Integrating secure development lifecycle (SDLC) practices
Mobile Application Security
Addressing mobile-specific threats and vulnerabilities
Best practices for securing mobile apps in the Bangalore market
Module 4: Endpoint Security
Endpoint Protection
Anti-virus and anti-malware solutions
Endpoint Detection and Response (EDR) tools
Securing Operating Systems
Hardening Windows and Linux systems
Effective patch management and software updates
BYOD and IoT Security
Managing Bring Your Own Device (BYOD) policies in Bangalore
Securing Internet of Things (IoT) devices
Module 5: Identity and Access Management (IAM)
Fundamentals of IAM
Authentication vs. Authorization
Identity lifecycle management and its application in Bangalore businesses
Access Control Mechanisms
Role-Based Access Control (RBAC)
Implementing Multi-Factor Authentication (MFA)
Identity Management Solutions
Single Sign-On (SSO) and Federation
Identity as a Service (IDaaS) platforms and their relevance
Module 6: Cloud Security
Cloud Security Basics
Understanding cloud service models (IaaS, PaaS, SaaS)
Shared responsibility model for cloud security
Securing Cloud Environments
Best practices for AWS, Azure, and Google Cloud in Bangalore
Cloud security posture management
Cloud Compliance and Governance
Regulatory requirements and compliance standards applicable in Bangalore
Data protection and privacy in the cloud
Module 7: Threat Intelligence and Incident Response
Cyber Threat Intelligence
Gathering and analyzing threat data
Using threat intelligence platforms effectively
Incident Response Planning
Developing an incident response plan
Incident detection and analysis
Handling Security Incidents
Containment, eradication, and recovery strategies
Post-incident activities and lessons learned
Module 8: Security Operations and Monitoring
Security Operations Center (SOC)
Roles and responsibilities of SOC teams
Setting up and managing a SOC in Bangalore
Monitoring and Logging
Importance of logging and monitoring
Using SIEM (Security Information and Event Management) tools
Threat Hunting
Proactive threat hunting techniques
Leveraging advanced analytics and AI for threat detection
Module 9: Compliance and Legal Aspects
Understanding Cyber Security Regulations
Key regulations (GDPR, CCPA, HIPAA, etc.)
Compliance requirements for organizations in Bangalore
Legal Considerations in Cyber Security
Data breach laws and notification requirements
Intellectual property and cyber crime laws
Auditing and Assessment
Conducting security audits and assessments
Preparing for compliance audits
Module 10: Capstone Project and Certification
Capstone Project
Real-world scenario-based project
Applying learned skills to solve complex problems
Exam Preparation
Review of key concepts and practice exams
Tips and strategies for passing the certification exam
Certification and Next Steps
Receiving course completion certificate
Exploring advanced certifications and career paths
Conclusion and Course Wrap-Up
Final Q&A Session
Addressing any remaining questions
Sharing additional resources and tools
Networking and Alumni Community
Joining the course alumni network
Continued learning and professional development opportunities in Bangalore
This Next-Gen Cyber Security course in Bangalore will equip you with the knowledge and skills needed to excel in the evolving field of cyber security
0 notes
Text
DNS Security Software Market – Latest Scenario with Future Trends Analysis Report 2024-2033 | Global Insight Services
“Global Insight Services offers unparalleled market intelligence and strategic consulting services to businesses worldwide. Our expertise spans across various industries, including healthcare, technology, and consumer goods, providing comprehensive analysis and actionable insights. By leveraging advanced data analytics and in-depth market research, we empower our clients to make informed decisions, identify growth opportunities, and stay ahead of the competition”.
The global DNS security software market was valued at US$ 1.2 billion in 2021 and it is anticipated to grow up to US$ 2.7 billion by 2031, at a CAGR of 8.4% during the forecast period.
Domain name system (DNS) security software is used to secure DNS servers and the websites it support. This software redirects end user web traffic through filters that identify malware signatures and other characteristics of potentially dangerous websites and media. DNS security software provides IT personnel with tools to classify websites, group devices, categorize users, and customize usage policies. Businesses use these tools to protect their employees’ endpoint devices and their own servers by blocking harmful content, media, and websites. DNS security software can also be used to prevent employees from accessing unapproved content in the workplace.
View The Full Report Here –https://www.globalinsightservices.com/reports/dns-security-software-market
Market Drivers and Trends
Cloud-based DNS security software provides multiple benefits to users through scalability, affordability, security, and resiliency, particularly by preventing Distributed Denial-Of-Service (DDoS) attacks. Benefits related to the cloud deployment of these software systems drive the DNS security software market. Additionally, cloud-based DNS helps enterprises configure the Domain Name System Security Extensions (DNSSEC), a method for authenticating DNS records and enabling protection against known attacks. Moreover, cloud-based DNS security software systems offer advanced traffic routings, facilitating round-robin, latency-based routing, geographic DNS, and geo-proximity routing to simple failover. Cloud-based DNS aid in better monitoring and visibility and make configuration changes easy and convenient for enterprises. Enterprises can scale up and down their working productivity with cloud deployment. Therefore, numerous small and medium enterprises (SMEs) believe cloud deployment to be the most effective deployment platform for DNS security software solutions.
Market Restraints and Challenges
In open source, developers take an existing Organization Size/program in the open-source market, make improvements, add features, and share their modifications with the community for everyone’s benefit. On the other side, closed source software (known as proprietary software) belongs to a company/individual that licenses the software and has sole rights to distribute the code.
While open-source software may be free to use in terms of price, furthermore, there are many other reasons open-source software can be the better choice overall for business needs, including access to a talented community of developers and the flexibility to integrate other pieces of technology within the software. Further, many good reasons why more companies are turning to open-source software exist. Firstly, expert developers continuously monitor and improve open-source software, catching and fixing bugs collaboratively. This leads to reliable, stable, and performant software that works across various environments. Secondly, open-source software is attractive for multiple businesses due to there are no up-front costs to download the code and start working with it. Thirdly, available source code leads to greater longevity and stability of the open-source product, as it can’t be phased out, such as proprietary software, which is at the mercy of a commercial vendor. Thus, the rising availability of open-source software is acting as a restraining factor for the closed source software manufacturers.
Unlock Growth Potential in Your Industry – Get Your Sample Report Now-https://www.globalinsightservices.com/request-sample/GIS10394
Global DNS Security Software Market Segmentation
By Deployment Type
On-Premise
Cloud-Based
By Organization Size
SMEs
Large Enterprises
Major Players in the Global DNS Security Software Market
The key players studied in the global DNS security software market are Akamai Technologies (US), Cloudflare, Inc. (US), Comodo Security Solutions, Inc. (US), DNSFilter Inc. (US), DomainTools LLC (US), Efficient IP (US), Open Text Corporation (Canada), Palo Alto Networks Inc. (US), ScoutDNS, LLC (US), and TitanHQ (Ireland).
COVID-19 Impact
In 2020, the COVID-19 pandemic had positively impacted the growth of the DNS security software market, as millions of employees were asked to do work from home by their companies. As employees accessed corporate systems through the less-secure home and public Wi-Fi networks, the remote working practices led to a surge in queries for DNS, further increasing cyber-attacks targeting DNS and boosting the demand for DNS security software.
Buy Now@https://www.globalinsightservices.com/checkout/single_user/GIS10394
Research Scope
Scope – Highlights, Trends, Insights. Attractiveness, Forecast
Market Sizing – Product Type, End User, Offering Type, Technology, Region, Country, Others
Market Dynamics – Market Segmentation, Demand and Supply, Bargaining Power of Buyers and Sellers, Drivers, Restraints, Opportunities, Threat Analysis, Impact Analysis, Porters 5 Forces, Ansoff Analysis, Supply Chain
Business Framework – Case Studies, Regulatory Landscape, Pricing, Policies and Regulations, New Product Launches. M&As, Recent Developments
Competitive Landscape – Market Share Analysis, Market Leaders, Emerging Players, Vendor Benchmarking, Developmental Strategy Benchmarking, PESTLE Analysis, Value Chain Analysis
Company Profiles – Overview, Business Segments, Business Performance, Product Offering, Key Developmental Strategies, SWOT Analysis.
With Global Insight Services, you receive:
10-year forecast to help you make strategic decisions
In-depth segmentation which can be customized as per your requirements
Free consultation with lead analyst of the report
Infographic excel data pack, easy to analyze big data
Robust and transparent research methodology
Unmatched data quality and after sales service
Contact Us:
Global Insight Services LLC
16192, Coastal Highway, Lewes DE 19958
E-mail: [email protected]
Phone: +1-833-761-1700
Website: https://www.globalinsightservices.com/
About Global Insight Services:
Global Insight Services (GIS) is a leading multi-industry market research firm headquartered in Delaware, US. We are committed to providing our clients with highest quality data, analysis, and tools to meet all their market research needs. With GIS, you can be assured of the quality of the deliverables, robust & transparent research methodology, and superior service.
0 notes
Text

Security challenges in Hybrid Work (Infographic)
Data breach - 58
Unsecured Endpoint devices - 52
Lack of Wi-Fi security in-home location - 25
More data access points - 64
Compliance and privacy risks - 17
The concept of hybrid work is pandemic induced. Before the pandemic, most of the workforce used to go to the office, whereas during the pandemic, the same number (over 95%, give or take) worked out of their homes or remote locations. But now, as we emerge out of that period comes a situation where we see a balance of people working in-office while the rest is working out of their homes. This has never happened in the past, and precisely so, the challenges that come with it are also unprecedented.
New and emerging ways of securing the enterprise have come up with data, applications or devices not confined to the data center. They had to since the perimeter expanded. Two frameworks which have created a lot of buzz are SASE and Zero Trust.
With the cloud and the internet being the bedrock of all that is happening, the concept of network security has to transform. But a more considerable challenge is identifying the best solution portfolio (or security framework) that fits your enterprise's needs. It's a conundrum created because of the plethora of offerings in the market.
When we speak about SASE and Zero Trust, there are questions on which of the two frameworks better suits an organization's requirements. We think a better approach is to see them working in tandem and not against each other. SASE brings together cloud-based security aspects like CASB and SWG with WAN capabilities. Zero Trust is an integral part of this framework, where its chief purpose is to manage access control.
Given SASE is a relatively new framework, and vendors and end-users alike are trying to see the best fitment in their scheme of things, given the de facto position of the market, we see it gaining mind share in the future. know more...
0 notes
Text
How Does the Power of Crypto Exchange API Integration Level Up Your Venture in 2024?
Introduction
In the ever-evolving landscape of cryptocurrency, businesses must stay ahead of the curve to remain competitive. One of the most transformative tools available today is Crypto Exchange API Integration. This technology not only simplifies processes but also offers a myriad of benefits that can elevate your venture to new heights. In this article, we will delve into how leveraging the power of Crypto Exchange API Integration can propel your business forward in 2024.
What is Crypto Exchange API Integration?
Understanding APIs
Before we dive into the specifics of Crypto Exchange API Integration, it's essential to understand what an API (Application Programming Interface) is. In simple terms, an API is a set of rules and protocols that allow different software applications to communicate with each other. APIs enable seamless data exchange and functionality sharing, which is crucial in today's interconnected digital world.
The Role of Crypto Exchange APIs
Crypto Exchange APIs are specialized APIs that facilitate interaction with cryptocurrency exchanges. They provide developers with the tools needed to access real-time market data, execute trades, manage accounts, and more. By integrating these APIs into your business operations, you can automate and streamline various processes, enhancing efficiency and performance.
Benefits of Crypto Exchange API Integration
Enhanced Efficiency and Automation
One of the most significant advantages of Crypto Exchange API Integration is the ability to automate repetitive tasks. This automation can include everything from executing trades based on predefined criteria to generating detailed reports. By reducing manual intervention, you not only save time but also minimize the risk of human error.
Access to Real-Time Data
In the fast-paced world of cryptocurrency, having access to real-time data is paramount. Crypto Exchange APIs provide up-to-the-minute information on market prices, trading volumes, and other critical metrics. This data allows you to make informed decisions quickly, giving you a competitive edge.
Improved Trading Strategies
With real-time data at your fingertips, you can develop and implement more effective trading strategies. Whether you're involved in day trading, arbitrage, or long-term investments, having accurate and timely information is crucial. Crypto Exchange APIs enable you to execute trades faster and more efficiently, maximizing your potential returns.
Scalability and Flexibility
As your business grows, so do your needs. Crypto Exchange API Integration offers the scalability and flexibility required to adapt to changing demands. Whether you need to support more users, integrate additional exchanges, or expand your service offerings, APIs make it easy to scale your operations without significant overhauls.
Key Features of Crypto Exchange APIs
Market Data Endpoints
Market data endpoints are a fundamental feature of Crypto Exchange APIs. They provide access to various types of market data, including current prices, historical data, and market depth. This information is essential for analyzing market trends and making informed trading decisions.
Trading Endpoints
Trading endpoints allow you to execute trades directly through the API. This includes placing buy and sell orders, canceling orders, and retrieving order statuses. By integrating these endpoints, you can automate your trading strategies and respond to market changes swiftly.
Account Management
Managing your accounts efficiently is crucial for any cryptocurrency venture. Crypto Exchange APIs offer account management features such as balance retrieval, transaction history, and deposit/withdrawal functions. These features help you maintain accurate records and streamline your financial operations.
Security and Authentication
Security is a top priority when dealing with cryptocurrencies. Crypto Exchange APIs incorporate robust security measures, including API key authentication, IP whitelisting, and encryption. These features ensure that your data and transactions are protected from unauthorized access and cyber threats.
Use Cases of Crypto Exchange API Integration
Cryptocurrency Trading Platforms
For cryptocurrency trading platforms, API Integration is a game-changer. It allows platforms to offer a seamless trading experience, providing users with real-time data, efficient order execution, and robust account management. By leveraging APIs, trading platforms can attract more users and enhance their overall service offerings.
Financial Services
Financial institutions are increasingly incorporating Crypto Exchange API Integration to offer cryptocurrency-related services. This includes crypto trading, portfolio management, and financial analysis tools. By integrating APIs, financial services can diversify their offerings and cater to the growing demand for cryptocurrency investments.
E-Commerce Platforms
E-commerce platforms can benefit from Crypto Exchange API Integration by enabling cryptocurrency payments. This integration allows businesses to accept various cryptocurrencies as payment methods, expanding their customer base and providing a modern, secure payment option.
Blockchain Projects
Blockchain projects often require access to real-time data and efficient transaction processing. Crypto Exchange APIs provide the necessary tools to support these requirements, enabling blockchain projects to operate smoothly and effectively.
Steps to Integrate Crypto Exchange APIs
Identify Your Requirements
The first step in integrating Crypto Exchange APIs is to identify your specific requirements. Determine what functionalities you need, such as market data access, trading capabilities, or account management. Understanding your needs will help you choose the right API and streamline the integration process.
Choose the Right API
There are numerous Crypto Exchange APIs available, each with its unique features and capabilities. Research and compare different APIs to find the one that best suits your requirements. Consider factors such as data accuracy, reliability, security, and ease of use.
Set Up API Keys and Authentication
Once you've chosen an API, you'll need to set up API keys and authentication mechanisms. This process typically involves creating an account with the API provider, generating API keys, and configuring security settings. Ensure that you follow best practices for API security to protect your data and transactions.
Implement the Integration
With your API keys and authentication in place, you can begin implementing the integration. This involves coding the necessary functions to interact with the API, such as retrieving market data, executing trades, and managing accounts. Test the integration thoroughly to ensure it works correctly and efficiently.
Monitor and Maintain
After the integration is complete, it's essential to continuously monitor and maintain it. Keep an eye on the performance of your API integration, address any issues that arise, and update the integration as needed. Regular maintenance ensures that your integration remains reliable and effective.
Best Practices for Crypto Exchange API Integration
Prioritize Security
Security should be a top priority when integrating Crypto Exchange APIs. Use strong authentication methods, encrypt sensitive data, and implement regular security audits. Protecting your data and transactions is crucial to maintaining trust and credibility with your users.
Optimize for Performance
Ensure that your API integration is optimized for performance. This includes minimizing latency, efficiently handling large volumes of data, and ensuring fast response times. A high-performing integration enhances the user experience and improves overall efficiency.
Stay Updated
The world of cryptocurrency is constantly evolving, and so are Crypto Exchange APIs. Stay updated with the latest API versions, features, and best practices. Regularly updating your integration ensures that you leverage the most advanced and secure functionalities available.
Provide Comprehensive Documentation
Comprehensive documentation is essential for a smooth integration process. Ensure that your developers have access to detailed API documentation, including endpoint descriptions, request/response formats, and usage examples. Good documentation reduces the learning curve and speeds up the integration process.
Test Thoroughly
Thorough testing is crucial to the success of your API integration. Test all functionalities extensively to ensure they work as expected. Identify and address any bugs or issues before going live. Testing ensures a reliable and smooth integration experience for your users.
Challenges and Solutions in Crypto Exchange API Integration
Handling High Volumes of Data
Challenge: Cryptocurrency markets generate massive amounts of data, which can be challenging to handle.
Solution: Implement efficient data processing techniques and use scalable infrastructure to manage high data volumes. Consider using cloud-based solutions to ensure scalability and reliability.
Ensuring Data Accuracy
Challenge: Inaccurate data can lead to poor trading decisions and financial losses.
Solution: Choose reputable API providers known for their data accuracy. Implement validation checks to ensure the data you receive is reliable and up-to-date.
Managing Security Risks
Challenge: Security risks, such as hacking and unauthorized access, are significant concerns in cryptocurrency.
Solution: Prioritize security measures, including strong authentication, encryption, and regular security audits. Stay informed about the latest security threats and best practices.
Integrating with Multiple Exchanges
Challenge: Integrating with multiple exchanges can be complex and time-consuming.
Solution: Use multi-exchange APIs that provide a unified interface for interacting with various exchanges. This approach simplifies the integration process and reduces development time.
Future Trends in Crypto Exchange API Integration
Advanced Analytics and AI
The future of Crypto Exchange API Integration will likely see increased use of advanced analytics and artificial intelligence (AI). These technologies can provide deeper insights into market trends, enhance trading strategies, and improve overall decision-making processes.
Increased Regulatory Compliance
As the cryptocurrency industry matures, regulatory compliance will become more critical. Future Crypto Exchange APIs will likely incorporate features to help businesses comply with regulations, such as KYC (Know Your Customer) and AML (Anti-Money Laundering) requirements.
Enhanced Security Measures
Security will continue to be a top priority. Future Crypto Exchange APIs will likely offer enhanced security measures, such as biometric authentication, advanced encryption techniques, and real-time threat detection. These features will help protect businesses and users from evolving cyber threats.
Greater Integration with DeFi
Decentralized Finance (DeFi) is rapidly gaining traction in the cryptocurrency world. Future Crypto Exchange APIs will likely offer greater integration with DeFi platforms, enabling businesses to tap into this growing market and offer innovative financial products and services.
Conclusion
Crypto Exchange API Integration is a powerful tool that can significantly enhance your venture in 2024. From improving efficiency and automation to providing real-time data and enhancing security, the benefits are substantial. By integrating these APIs, you can stay ahead of the competition, adapt to changing market demands, and provide superior services to your users. Embrace the power of Crypto Exchange API Integration and level up your venture today.
🙋Contact us for more details:
📞Call us: +91-9650020493
📧Email us: [email protected]
🌐Website: https://takshitsolutions.com/exchange-software-development
#Crypto Exchange APIs#decentralizedfinance#cryptocurrency exchange#cryptocurrency#blockchain#takshitsolutions#technology#softwaredevelopment#blockchaintechnology#crypto#ethereum#defi#investment#digitalcurrency#website development
0 notes
Text
Why Digital Risk Protection is Essential for Modern Enterprises
Top Digital Risk Protection Software Solutions for your Business
Digital Risk Protection (DRP) solutions detect and manage cybersecurity risks to an organization's digital assets, which include accounts, domains, apps, and cloud infrastructure. This involves keeping an eye on your digital channels for any cyber-threats like phishing attempts or ransomware. The systems can detect, track, and analyze threats in conjunction with threat intelligence and incident response technologies, alerting security professionals to potential problems before they happen.
DRP tools are critical for security teams to prevent advanced cyber-attacks that seek to abuse the digital channels we all use to gather data, extort corporations, and propagate hazardous malware, such as ransomware. These digital risk protection services market typically include protection against brand impersonation and social engineering assaults, threat content monitoring, dark web scanning, automated hazardous content cleanup, account takeover prevention, and even app management capabilities.
In this blog, we'll look at the top cloud-based digital risk prevention solutions for businesses. We'll provide an overview of each product, as well as pricing information and editorial comments, to assist you in selecting the best digital risk prevention solution for your organization.
What is Digital Risk Protection?
Digital risk protection (DRP) refers to technologies and strategies that help secure an organization's infrastructure by determining the true extent of its digital footprint and improving the security of its external digital assets. DRP solutions enable businesses to proactively detect and manage risks to their data, digital and physical assets, personnel, and overall brand reputation by continuously monitoring numerous channels on the open, deep, and dark web.
Download the sample report of Market Share: https://quadrant-solutions.com/download-form/market-research/market-forecast-digital-risk-protection-2022-2027-worldwide-2747
A digital risk protection system can be self-managed, which means that a corporation installs digital risk protection software and manages risk factors itself. Alternatively, there are digital risk protection services, which allow the firm to delegate the implementation of its DRP strategy to a third-party managed service. In addition to automatic technologies, a digital risk protection services market will employ a team of analysts to manually monitor a variety of data sources, including social media applications, blog and forum posts, DNS records, and the deep and dark web, for all risk factors associated with your firm.
Best Digital Risk Protection Tools
BlueVoyant Sky: DRP
BlueVoyant, a network security firm formed in 2017, provides a cloud-native, unified platform for internal and external cyber defenses. They provide an end-to-end digital risk prevention solution that detects and mitigates dangers to your digital assets by utilizing threat intelligence and comprehensive data sets.
CrowdStrike Falcon Intelligence
CrowdStrike is a market-leading cybersecurity service that offers cloud-based threat intelligence and endpoint protection (EPP) solutions to safeguard cloud workloads and data. CrowdStrike's Falcon Intelligence technology uses real-time threat intelligence to detect signs of an attack. This, combined with human analysis, gives actionable insights that enable security teams to quickly detect and resolve vulnerabilities, as well as avoid data breaches.
Digital Shadows SearchLight
Digital Shadows is a threat intelligence company that identifies and mitigates external threats to protect digital assets. Digital Shadows' SearchLight product is a dedicated threat intelligence platform that enables security teams to quickly assess and respond to threats. Along with this, Digital Shadows provides tailored consulting and intelligence services for white glove support and deployment. ReliaQuest, a security operations company, bought Digital Shadows in June 2022.
PhishLabs Digital Risk Protection
Fortra (previously HelpSystems) offers a broad range of cybersecurity solutions, such as data security, email security managed services, and threat intelligence. In 2021, Fortra purchased PhishLabs, a renowned provider of cyber threat intelligence and digital asset security. Fortra's PhishLabs Digital Risk Protection Solution provides targeted threat information and rapid attack response.
Proofpoint Digital Risk Protection
Proofpoint Digital Risk Protection enables businesses to defend their brands and customers against harmful activity on websites, social media platforms, and the dark web. It serves as a comprehensive security solution for all digital channels via which clients connect with your band. Proofpoint is well-known for its market-leading email security services, which are powered by a worldwide threat intelligence network that includes email, social media, and mobile channels. The intelligence network is driven by data from over 100 million email inboxes, 200 million social media accounts, and 7 million mobile applications.
Download the sample report of Market Forecast: https://quadrant-solutions.com/download-form/market-research/market-forecast-digital-risk-protection-2022-2027-worldwide-2747
How To Choose The Right Digital Risk Protection Solution?
Finding the best DRP solution for your company can be a challenging task. There are various aspects to consider, including price. However, we would recommend keeping the following three crucial elements in mind while selecting a digital risk prevention solution:
Coverage: Ensure the solution protects all digital applications vital to your firm and has the necessary features to prevent digital hazards.
Compliance: Different sectors have unique compliance challenges. It's critical to determine which solutions will assist you achieve your specific regulatory needs.
Deployment Options: DRP solutions can be deployed in multiple ways. Many of the solutions on this list are cloud-based, integrating across digital assets, but companies can also choose hybrid or managed deployment choices.
Talk To Analyst: https://quadrant-solutions.com/talk-to-analyst
When exploring Digital Risk Protection (DRP), selecting the right tools hinges on a multitude of critical considerations. Assessing your platform's requirements, scalability prerequisites, and budgetary constraints form the core of this decision-making process. Yet, insights derived from Market Intelligence (MI) reports play a pivotal role in navigating this landscape. These Digital Risk Protection Market Share, 2022-2027, Worldwide and Market Forecast: Digital Risk Protection, 2022-2027, Worldwide reports offer an all-encompassing analysis of available digital risk protection services market tools, delving into their strengths, weaknesses, and applicability across various digital experience needs. While each tool may tout its prowess, the true distinctions emerge in factors such as implementation simplicity, scalability potential, and seamless integration with existing infrastructure. Leveraging MI reports enriches decision-making by providing nuanced insights and aligning benchmarks with industry standards, facilitating a more informed and precise selection of the optimal DRP tool tailored to your specific business requisites.
Conclusion
Digital Risk Protection (DRP) tools help keep our online places safe from cyber threats like hacking or phishing. In this blog, we talked about some great DRP tools that can watch over your digital world and stop dangers before they happen. When choosing the right tool, think about what your business needs, how much it can spend, and how well the tool fits with what you already use. Using these tools means you can work and play online more safely.
0 notes
Text
Same Day Agra Tour By Gatimaan Express Train By Taj Mirror Company

Taj Mirror Company's Same Day Agra Tour by Gatimaan Express Train is an efficient and entertaining method to see Agra's major monuments in a single day. This tour is ideal for those looking for a quick but comprehensive overview of Agra's ancient gems.
Same Day Agra Tour by Gatimaan Express Train Your adventure begins in the early morning with a simple pick-up from your Delhi hotel and transfer to Hazrat Nizamuddin railway station. You'll board the Gatimaan Express, India's quickest train, for a comfortable and rapid travel to Agra, which takes around 1 hour and 40 minutes.
Upon arriving in Agra, you will be met by a professional tour guide who will accompany you throughout the day. The first visit is the beautiful Taj Mahal, a UNESCO World Heritage Site and one of the New Seven Wonders of the World. Built by Emperor Shah Jahan in commemoration of his beloved wife Mumtaz Mahal, this architectural marvel is known for its gorgeous white marble and delicate inlay work.
Following the visit to the Taj Mahal, the group continues to Agra Fort, another UNESCO World Heritage site. This enormous stronghold, built of red sandstone, was the primary palace of the Mughal rulers and is rich in history and architectural splendor. Your guide will share fascinating details about the fort's history and significance.
A delicious meal at a reputed local restaurant will give you a taste of authentic Indian fare. Following lunch, the group continues to the Tomb of Itimad-ud-Daulah, also known as the "Baby Taj." This magnificent mausoleum is renowned for its elaborate marble lattice screens and meticulous craftsmanship.
The tour concludes with some free time for shopping or exploring local markets before being transferred back to the train station. You will board the Gatimaan Express for your return trip to Delhi, where a driver will be ready to drive you back to your accommodation.
Taj Mirror Company's Same Day Agra Tour by Gatimaan Express Train is a seamless and fascinating experience that combines comfort and convenience with a thorough exploration of Agra's most iconic attractions. It's an excellent alternative for individuals who wish to experience the beauty and history of the Taj Mahal and other important attractions in one day.
ALSO READ-
CrowdStrike is a renowned cybersecurity firm that specializes in endpoint protection, threat intelligence, and cyberattack response services. CrowdStrike, founded in 2011 by George Kurtz, Dmitri Alperovitch, and Gregg Marston, has quickly established itself as a powerful force in the cybersecurity market. The corporation is based in Sunnyvale, California.
CrowdStrike's core product, the Falcon platform, uses AI and ML to detect and respond to threats in real time. The technology gives extensive visibility into endpoint activity, enabling enterprises to quickly detect and remediate any security breaches. Falcon's cloud-native architecture provides scalability and ease of deployment, making it a popular choice for businesses of all sizes.
CrowdStrike's role in detecting high-profile intrusions, such as the 2016 Democratic National Committee (DNC) hack, is one of its most notable accomplishments. The company's competence in threat intelligence and incident response has made it a reliable partner for both government agencies and private-sector businesses.
CrowdStrike's business strategy is subscription-based, with several service tiers to meet different corporate demands. This concept has been successful, as the company's revenue has grown rapidly and its customer base has expanded abroad. CrowdStrike went public in 2019, reinforcing its market position.
The company's commitment to innovation is demonstrated by continual updates to the Falcon platform and the incorporation of new technologies to battle increasing cyber threats. CrowdStrike's focus on proactive threat hunting, along with its comprehensive threat intelligence capabilities, enables enterprises to stay ahead of adversaries.
To summarize, CrowdStrike has evolved as a cybersecurity leader thanks to its cutting-edge technologies, strategic threat intelligence, and effective incident response. Its Falcon platform continues to set industry standards, equipping enterprises with the capabilities they need to defend against complex cyber threats.
0 notes