#endpoint security market trends
Text
#endpoint security market report#endpoint security industry report#endpoint security market#endpoint security market share#endpoint security market size#endpoint security market trends#endpoint security market growth#endpoint security market analysis#endpoint security market forecast
0 notes
Text
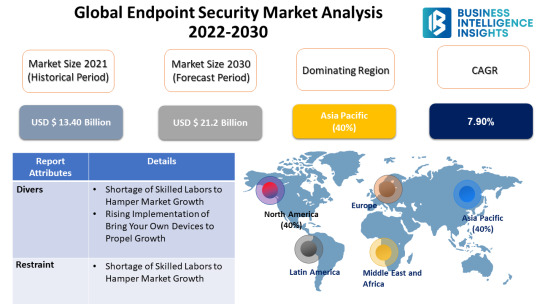
As per Business Intelligence Insights (BII) study, the global Global Endpoint Security Market attained revenue growth of USD 13.40 billion in 2021 and it is projected to reach around USD 21.2 billion by 2030, growing at a 7.90% CAGR.
#Endpoint Security Market#Endpoint Security Market Market#Endpoint Security Market Market Trends#Endpoint Security Market Market Share#Endpoint Security Market Market Size#Endpoint Security Market Market Analysis#Endpoint Security Market Market Demand#Endpoint Security Market Market Growth 2023#Endpoint Security Market Market Industry
0 notes
Text
Global Industrial Cybersecurity Market Size[271 Pages Report] The global industrial cybersecurity market size is expected to growing at a CAGR of 7.7%, from USD 16.3 billion in 2022 to USD 24.4 billion in 2028. The primary reasons for this rise in demand for industrial cybersecurity products in power industry.
0 notes
Text
Future of OTT App Scraping

The Over-The-Top (OTT) media industry has seen exponential growth in recent years, driven by the increasing demand for digital content and the rise of streaming platforms. As we look ahead to 2025 and beyond, OTT app scraping is poised to become an even more critical tool for businesses, analysts, and researchers seeking to understand and capitalize on this dynamic sector. This article explores the future of scraping OTT app data, focusing on emerging trends, technological advancements, and the implications for stakeholders in the industry.
Overview OTT App Scraping
OTT app scraping refers to extracting data from OTT platforms such as Netflix, Amazon Prime ,Video Disney+, and Hulu. This data can include a wide range of information, such as content metadata (titles, genres, release dates), user reviews, ratings, and viewing statistics. Streaming data is extracted to gather valuable insights that inform business strategies, content acquisition, and market analysis.
The need for robust scraping tools and techniques will grow as OTT platforms evolve. Several key factors, including technological advancements, regulatory changes, and shifts in consumer behavior, will shape the future of extracting OTT app data.
Emerging Trends in OTT App Scraping
Advanced-Data Extraction Techniques
The future of OTT app scraping services will see the implementation of more advanced data extraction techniques. Traditional scraping methods, which rely on static web pages and HTML structures, will evolve to accommodate the increasing complexity of modern OTT platforms. Dynamic content, JavaScript rendering, and APIs will necessitate more sophisticated scraping solutions.
Headless browsers and browser automation tools like Puppeteer and Selenium will become more prevalent. These tools allow interaction with dynamic content and facilitate data extraction from platforms that rely on complex JavaScript. APIs will also play a crucial role. Many OTT platforms provide APIs for accessing content and user data, which can be leveraged to streamline the scraping process. However, as platforms become more stringent about API access, finding and utilizing these endpoints will require advanced skills and strategies.
Increased Focus on Personalization and Recommendations
Personalization has become a hallmark of the OTT experience, with platforms using sophisticated algorithms to tailor content recommendations to individual users. As OTT platforms invest heavily in personalization, OTT data scraper must adapt to capture data on how these algorithms function and influence user behavior. Machine learning and artificial intelligence(AI) will be employed to analyze scraping data and derive insights about recommendation systems. By understanding how personalization affects content consumption, businesses can better predict viewer preferences and optimize content strategies.
Integration of Multi-Source Data
OTT platforms are not the only sources of valuable data. Social media, forums, and review sites provide additional insights into viewer preferences and industry trends. Future OTT app data scraping will increasingly involve integrating data from multiple sources to create a comprehensive market view. Sentiment analysis and social listening tools will gauge audience reactions to content and identify emerging trends. By combining data from OTT platforms with social media insights, businesses can gain a more holistic understanding of viewer preferences and behavior.
Enhanced Data Privacy and Security Measures
As data privacy concerns continue to rise, OTT platforms will likely implement stricter security measures to protect user information. This will impact how data is scraped and used, necessitating advancements in data anonymization and compliance practices. Scraping tools must incorporate features that ensure data is collected and processed by privacy regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). Ensuring ethical and legal compliance will be critical for maintaining trust and avoiding potential legal issues.
Real-Time Data Processing and Analytics
The demand for real-time insights is growing, driven by the need to make swift decisions in a rapidly changing market. Future OTT app scraping will focus on real-time data processing and analytics to provide up-to-the-minute insights into content performance, user engagement, and market trends. Stream processing frameworks such as Apache Kafka and Apache Flink will become essential for handling and analyzing large volumes of data in real time. These technologies will enable businesses to adapt their strategies quickly based on the latest information.
Technological Advancements Shaping the Future
1. Artificial Intelligence and Machine Learning
AI and machine learning will play a pivotal role in the evolution of OTT app scraping. These technologies will enhance the ability to analyze and interpret complex data sets, uncovering patterns and trends that may not be immediately apparent.
Natural Language Processing (NLP) will analyze text data from user reviews and social media, providing deeper insights into audience sentiment and content reception. Image recognition and video analysis technologies will also extract data from visual content, adding another layer of depth to scraping efforts.
2. Blockchain Technology
Blockchain technology has the potential to revolutionize streaming data scraping by providing a secure and transparent way to track data usage and ownership. In the context of OTT app scraping, blockchain could be used to ensure data integrity and prevent unauthorized access. Smart contracts and decentralized applications (dApps) could facilitate more secure and efficient data transactions, while blockchain’s immutable ledger would enhance transparency and accountability.
3. Cloud Computing and Big Data
Cloud computing will continue to play a significant role in managing and processing the large volumes of data generated by OTT platforms. Cloud-based scraping tools and big data solutions will enable businesses to scale their data collection efforts and handle complex data processing tasks more efficiently.
Data lakes and warehouses will store and manage vast amounts of scraped data, while cloud-based analytics platforms will provide the computational power needed to derive actionable insights.
4. Enhanced User Interface and Experience
Future OTT scraping tools will feature more advanced and user-friendly interfaces, allowing users to easily configure scraping tasks, visualize data, and generate reports. Drag-and-drop interfaces, visual data exploration tools, and customizable dashboards will make it easier for users to interact with and analyze their data.
Automated reporting and alerting systems will also be integrated, providing users with real-time updates and notifications based on predefined criteria or data anomalies.
Implications for Stakeholders
1. Content Providers and Distributors
For content providers and distributors, OTT app scraping will offer valuable insights into market trends and viewer preferences. They can make informed decisions about content acquisition, distribution, and marketing by analyzing data on content performance, pricing strategies, and competitor offerings.
Content optimization and pricing strategies can be tailored based on data-driven insights, leading to more effective content strategies and improved ROI.
2. Marketers and Advertisers
Marketers and advertisers will benefit from scraping data that reveals how viewers interact with content and respond to advertisements. Understanding audience preferences and behavior can create more targeted and effective advertising campaigns.
Ad placement strategies and content promotion efforts can be optimized based on data-driven insights, leading to better engagement and higher conversion rates.
3. Researchers and Analysts
Researchers and analysts will use scraped data to study industry trends, consumer behavior, and the impact of emerging technologies. The ability to access and analyze large volumes of data will enable more comprehensive and accurate research.
The availability of detailed and up-to-date data will enhance market research and competitive analysis, leading to more informed conclusions and recommendations.
4. Regulators and Policymakers
Regulators and policymakers must stay informed about the implications of OTT app scraping for data privacy and security. As data scraping becomes more prevalent, ensuring compliance with privacy regulations and addressing potential ethical concerns will be essential.
Regulatory frameworks and guidelines must be updated to reflect the evolving landscape of data scraping, protect user privacy, and support innovation.
Conclusion
The future of OTT app scraping holds immense potential for transforming how businesses, researchers, and analysts interact with and leverage data from streaming platforms. As we move towards 2025 and beyond, technological advancements, changes in consumer behavior, and evolving regulatory landscapes will shape how data is collected, analyzed, and utilized. By staying ahead of these trends and embracing new technologies, stakeholders can harness the power of OTT app scraping to gain valuable insights, drive strategic decisions, and maintain a competitive edge in the ever-evolving world of digital media. The journey towards a more data-driven and informed future is just beginning, and the opportunities are as vast as the data itself.
Embrace the potential of OTT Scrape to unlock these insights and stay ahead in the competitive world of streaming!
Source -
0 notes
Text
How Netherlands Dedicated Hosting Solutions Outperform the Competition
In the web hosting market, availability and speed are critical factors that one cannot disregard. Another interesting trend is that the Netherlands has become one of the endpoints for dedicated hosting solutions. This was proved in a recent study which revealed that dedicated servers located in Netherlands are 25% more efficient than those from the global websites. This is where Dutch dedicated hosting comes in as an ideal hosting solution for any business requiring a reliable and high performing online platform.

Key Takeaways
Netherlands dedicated hosting solutions offer 25% higher performance compared to global competitors.
Robust infrastructure and cutting-edge technology ensure unparalleled server reliability and uptime.
Scalable solutions accommodate business growth, allowing seamless expansion of online operations.
Secure and compliant hosting services safeguard sensitive data and ensure regulatory compliance.
Unmetered bandwidth provides the bandwidth required for seamless connectivity and uninterrupted operations.
Unleashing the Power of Netherlands Dedicated Hosting
The solutions for dedicated server holland hosting are tremendous for your business if you are located in the Netherlands. They offer superior performance and modularity. These are quite stable platforms, meaning that your site or app will be up and running smoothly with few or no glitches at all.
Robust Infrastructure for Unparalleled Performance
The central component of netherlands unmetered server offerings is inbuilt with advanced technology. It is fortified to handle large volumes of work. Equipped with the newest Intel Xeon E3 1270 processors and abundant storage space, these servers are capable of providing efficient solutions for any digital demands you might have.
Scalability to Accommodate Business Growth
You require elastic hosting environments when your business scales up and the reach of the internet widens. Dedicated server holland in the Netherlands is versatile, meaning that it can be easily expanded or reduced depending on an organization’s needs. This means that resources can be easily flexed to suit requirements within a short time or that resources may be easily changed to suit the business if need be. Be it enhanced computing capabilities, memory capacity, or connectivity – these solutions are built with scalability in mind.
Having unmetered server infrastructure in netherlands opens new vistas of performance and dependability. These are instrumental in making it big in the new economy.
Netherlands Dedicated Hosting: A Secure and Reliable Choice
That is why, Netherlands dedicated hosting solutions are unmatched in terms of efficiency to protect your online identity. This is very crucial in helping to ensure that each single byte or perhaps something that may lie in the ether essentially, is always there for you and safe. This is important for organizations which participate in Internet commercial processes either deliberately or as a result of being drawn into it.
The only benefit that could be pointed out when discussing dedicated hosting in Netherlands is that the data that the users enter is more protected. Some of the security features that Reliant Business Park has include; high level firewall as well as round the clock surveillance. This setup aids in reducing cyber risks hence making sure that you do not need to worry about safety of your data as well as the applications.
Netherlands dedicated hosting is also widely popular because of its reliability. It has two source of power and has sound networking to it. These features enable your website to be always ‘up’ irrespective of its state. This is especially relevant to those businesses relying on a website as their means of generating revenues as well as communicating with customers.
"Choosing a Netherlands dedicated hosting solution has been a game-changer for our business. The heightened security and unparalleled uptime have allowed us to focus on our core operations with complete confidence."
Netherlands dedicated hosting is the only way to ensure safety of your data and availability of your Internet presence always. When you decide on a good Netherlands dedicated hosting you get a protected environment and that is due to the fact that you are working with a good host. Such environment brings protection and safeguard of every record and application you consider important to protect from disruptors.
The Competitive Edge with Unmetered Bandwidth
Netherlands dedicated hosting solutions offer one compelling advantage with their ‘unmetered bandwidth’ offering. In so doing, it provides seamless connectivity, allowing organizations to focus on their operations free from bandwidth woes. With the elimination of metered bandwidth limitations on the Netherlands servers, businesses can expand their internet profiles and effectively manage high traffic volumes. This helps to keep the services up and running, thus providing the users with a world-class experience.
Seamless Connectivity for Uninterrupted Operations
The unlimited bandwidth of Netherlands dedicated hosting services create a sturdy and stable foundation for enterprises of all types. Whether the times have shifted and your website traffic fluctuates or your online tools required an additional feature, operations run seamlessly. This dependable connection enables you to provide steady, superior service, enhancing the perception of your brand and providing a competitive advantage.
No more worrying about bandwidth when it is time to expand your online presence, look for new revenue streams, or create: Netherlands unmetered servers make it all possible. This freedom to grow and adapt to market changes is what makes Netherlands dedicated hosting stand out. This allows you to achieve your business objectives and outcompete rivals.
FAQ
What sets Netherlands dedicated hosting solutions apart from the competition?
Netherlands dedicated hosting solutions stand out with their strong infrastructure, scalability, and top-notch performance. They offer powerful hardware like Intel Xeon E3 1270 processors and plenty of storage. This setup supports businesses as they grow and change.
How does the security and reliability of Netherlands dedicated hosting benefit businesses?
For businesses, security and reliability are key to keeping their online presence safe and always available. Netherlands dedicated hosting focuses on these areas. It provides a secure and dependable platform for businesses to thrive.
What advantages does unmetered bandwidth offer for businesses with Netherlands dedicated hosting?
Unmetered bandwidth gives businesses a competitive edge with Netherlands dedicated hosting. It ensures smooth connectivity and non-stop operations. This lets companies concentrate on their main tasks without bandwidth worries.
0 notes
Text
Endpoint Security Market Size, Share, Trend, Forecast, & Growth Analysis: 2024-2032
Endpoint Security Market 2024 Report: A Comprehensive Analysis of Historical and Current Market Trends with Strategic Insights.
Analysis of the global "Endpoint Security Market" shows that the market will develop steadily and strongly between 2024 and 2032, and projections indicate that this growth will continue through 2032. The increasing demand from consumers for ecologically friendly and sustainable products is a noteworthy development in the Endpoint Security Market. To improve the effectiveness and caliber of products in the Endpoint Security Market, technology has also been used much more frequently.
➼ Market Capacity:
Between 2017 and 2023, the Endpoint Security Market's value increased significantly, from US$ million to US$ million. With a compound annual growth rate (CAGR) predicted to reach US$ million by 2032, this momentum is anticipated to continue. An extensive analysis explores consumer preferences and purchasing patterns in this industry, broken down by type (Trend Micro (Japan), Eset (U.S.), Symantec (U.S.), Sophos (U.K.), McAfee (U.S.)). Based on extensive research, this perceptive analysis is anticipated to be a useful tool for industry participants looking to profit from the market's remarkable anticipated compound annual growth rate (2024–2032).
➼ Key Players:
List of Endpoint Security Market PLAYERS PROFILED
The Endpoint Security Market includes several key players such as Cloud, On-Premises, Other play crucial roles in this market.
Endpoint Security Market Report Contains 2024: -
Complete overview of the global Endpoint Security Market
Top Country data and analysis for United States, Canada, Mexico, Germany, France, United Kingdom, Russia, Italy, China, Japan, Korea, India, Southeast Asia, Australia, Brazil and Saudi Arabia, etc. It also throws light on the progress of key regional Endpoint Security Markets such as North America, Europe, Asia-Pacific, South America and Middle East and Africa.
Description and analysis of Endpoint Security Market potentials by type, Deep Dive, disruption, application capacity, end use industry
impact evaluation of most important drivers and restraints, and dynamics of the global Endpoint Security Market and current trends in the enterprise
Value Propositions of This Market Research:
The study covers a comprehensive analysis of industry drivers, restraints, and opportunities, providing a neutral perspective on the market performance. It highlights recent industry trends and developments, offering insights into the competitive landscape and the strategies employed by key players. The study identifies potential and niche segments and regions exhibiting promising growth, supported by historical, current, and projected market size data in terms of value. An in-depth analysis of the Endpoint Security Market is included, along with an overview of the regional outlook. This holistic approach ensures a thorough understanding of the market dynamics and potential growth areas.
Request a Free Sample Copy
Global Endpoint Security Market: SEGMENTATION ANALYSIS
The research report includes specific segments by region (country), manufacturers, Type, and Application. Market segmentation creates subsets of a market based on product type, end-user or application, Geographic, and other factors. By understanding the market segments, the decision-maker can leverage this targeting in product, sales, and marketing strategies. Market segments can power your product development cycles by informing how you create product offerings for different segments.
➼ PRODUCTS/SERVICES:
Valuable Points from Endpoint Security Market Research Report 2024-2032:
The market for Endpoint Security Market has undergone significant changes because to changing consumer preferences, laws, and technological advancements. This dynamic business is being shaped by new product launches, mergers, and creative marketing strategies from big players. A thorough analysis of recent and historical data yields insights into the market's value, volume, historical growth, current size, and potential for the future. While competition research explores market share and strategy, segmentation by key regions exposes regional variances. The research provides practical suggestions to help you improve your position in this dynamic market and finds new niches and development possibilities across regions.
Request a Free Sample Copy
Behind the Brand
In an industry characterized by rapid growth and technological advancements, economic changes occur daily. To thrive in this dynamic environment, companies must understand market trends and develop effective strategies. A well-defined strategy not only facilitates planning but also offers a competitive edge. For dependable market reports that provide essential insights to guide your business toward success, visit us at www.globalmarketstatistics.com .
Explore More Related Reports Here :
Fantasy Games Market
Relational Databases Software Market
High Pressure Composite Gas Cylinder Market
Privacy Compliance Consulting Services Market
BNC Connector Market
Car Recycling Market
Smart Construction Excavator Market
Continuous Passive Motion Devices Market
Kubernetes Security Software Market
Warehouse Shuttle Car Market
Residual Current Detectors Market
Titanium Elastic Nail Market
Industrial Counterweights Market
Magnetic Resonance Imaging Market
Micro-Compact Cars Market
#innovation#management#digitalmarketing#technology#creativity#futurism#startups#marketing#entrepreneurship#money#sustainability#inspiration#Leadership#Business#Strategy#Growth#Success#Innovation#Ecommerce#PersonalDevelopment
1 note
·
View note
Text
Security Automation Market Outlook On The Basis Of Offering, Deployment Mode, Application, Code Type, Vertical, Technology, Region And Forecast To 2030: Grand View Research Inc.
San Francisco, 10 Sep 2024: The Report Security Automation Market Size, Share & Trends Analysis Report By Offering, By Deployment, By Application (Network Security, Endpoint Security), By Technology, By Code Type, By Vertical, By Region, And Segment Forecasts, 2024 – 2030
The global security automation market size is expected to reach USD 22.92 billion by 2030, growing at a CAGR of 14.0% from…

View On WordPress
0 notes
Text

The digital landscape is constantly evolving, and unfortunately, so are the threats that plague it. Malicious software development, often abbreviated as malware development, has become a booming underground industry, churning out ever-more sophisticated threats designed to steal data, disrupt operations, and inflict financial damage.
This poses a significant challenge for individuals and businesses alike, particularly in the United States, a prime target for cybercriminals due to its vast digital infrastructure and economic power. Here, we'll delve into the concerning rise of malware development, explore the evolving tactics of cybercriminals, and highlight how Sohojware (https://sohojware.com) is fortifying its proactive security measures to safeguard its clients.
The Alarming Rise of Malware Development
The malware development industry is fueled by significant financial gains. By compromising systems and stealing sensitive information, cybercriminals can extort victims, sell stolen data on the black market, or disrupt critical operations for ransom. This lucrative incentive has led to a surge in malware development, with new threats emerging at an alarming rate.
According to a recent report by Cybersecurity Ventures, global ransomware damage costs are projected to reach a staggering $26 billion by 2 This highlights the immense financial strain that malware development inflicts on businesses worldwide.
Evolving Tactics of Cybercriminals
Cybercriminals behind malware development are constantly innovating their tactics. Here are some of the concerning trends:
Ransomware as a Service (RaaS): This model allows less technical attackers to leverage pre-developed malware for a share of the ransom profits. This democratizes cyberattacks, making them more accessible and widespread.
Supply Chain Attacks: Targeting trusted vendors and software providers allows attackers to infiltrate a vast network of systems through a single point of entry.
Fileless Malware: This type of malware doesn't rely on traditional executables, making it more challenging to detect with conventional antivirus software.
Social Engineering: Deceptive tactics like phishing emails and phone scams are used to trick victims into revealing sensitive information or downloading malware.
These are just a few examples, and cybercriminals are constantly developing new methods to exploit vulnerabilities.
Sohojware's Commitment to Proactive Security
At Sohojware (https://sohojware.com), we understand the gravity of the malware development threat. We are committed to providing our clients with robust security solutions that are constantly evolving to stay ahead of the curve. Here's how we're fortifying our security measures:
Threat Intelligence: We maintain a comprehensive threat intelligence feed, allowing us to stay abreast of the latest malware development trends and vulnerabilities.
Security Awareness Training: We offer security awareness training programs to educate our clients and their employees on how to identify and avoid malware threats.
Multi-Layered Security Solutions: We employ a layered security approach that combines firewalls, intrusion detection systems, endpoint protection, and regular security assessments to mitigate malware risks.
Regular Patch Management: We prioritize timely patching of vulnerabilities to minimize the window of opportunity for malware exploits.
Incident Response Planning: We have a comprehensive incident response plan in place to effectively address and contain malware incidents should they occur.
By proactively addressing the evolving threat landscape of malware development, Sohojware empowers its clients to operate with greater peace of mind in the digital world.
FAQs about Sohojware and Malware Development
1. How can Sohojware help me protect my business from malware development?
Sohojware offers a comprehensive suite of security solutions designed to mitigate malware risks. We can conduct security assessments, implement multi-layered security solutions, and provide ongoing monitoring and threat intelligence to safeguard your business.
2. Does Sohojware offer security awareness training for employees?
Yes, Sohojware offers security awareness training programs that educate employees on how to identify and avoid malware threats. This training empowers your workforce to become a vital line of defense against cyberattacks.
3. What is Sohojware's incident response plan for malware attacks?
Sohojware has a comprehensive incident response plan that outlines the steps we take to identify, contain, and remediate malware incidents. This plan ensures a swift and effective response to minimize damage.
4. How does Sohojware stay updated on the latest malware development trends?
Sohojware maintains a subscription to a comprehensive threat intelligence feed. This allows us to stay informed about the latest malware development tactics and vulnerabilities, enabling us to proactively adjust our security measures.
5. Can Sohojware help me recover my data if it's encrypted by ransomware?
Yes, Sohojware offers incident response services that can assist in recovering your data after a ransomware attack. While we cannot guarantee data recovery in all cases, our experts will work diligently to develop a recovery plan tailored to your specific situation. We also provide guidance on data backup and recovery best practices to help prevent future data loss.
Conclusion
The relentless evolution of malware development underscores the critical importance of robust cybersecurity measures. By staying informed about the latest threats and implementing proactive security strategies, businesses and individuals can significantly reduce their risk of falling victim to cyberattacks. Sohojware (https://sohojware.com) is committed to helping you navigate this complex landscape and protect your valuable assets.
Remember: The key to effective cybersecurity lies in a multi-layered approach that includes technology, employee training, and ongoing vigilance.
By partnering with Sohojware, you're taking a proactive step towards safeguarding your digital world.
1 note
·
View note
Text
DNS Security Software Market – Latest Scenario with Future Trends Analysis Report 2024-2033 | Global Insight Services
“Global Insight Services offers unparalleled market intelligence and strategic consulting services to businesses worldwide. Our expertise spans across various industries, including healthcare, technology, and consumer goods, providing comprehensive analysis and actionable insights. By leveraging advanced data analytics and in-depth market research, we empower our clients to make informed decisions, identify growth opportunities, and stay ahead of the competition”.
The global DNS security software market was valued at US$ 1.2 billion in 2021 and it is anticipated to grow up to US$ 2.7 billion by 2031, at a CAGR of 8.4% during the forecast period.
Domain name system (DNS) security software is used to secure DNS servers and the websites it support. This software redirects end user web traffic through filters that identify malware signatures and other characteristics of potentially dangerous websites and media. DNS security software provides IT personnel with tools to classify websites, group devices, categorize users, and customize usage policies. Businesses use these tools to protect their employees’ endpoint devices and their own servers by blocking harmful content, media, and websites. DNS security software can also be used to prevent employees from accessing unapproved content in the workplace.
View The Full Report Here –https://www.globalinsightservices.com/reports/dns-security-software-market
Market Drivers and Trends
Cloud-based DNS security software provides multiple benefits to users through scalability, affordability, security, and resiliency, particularly by preventing Distributed Denial-Of-Service (DDoS) attacks. Benefits related to the cloud deployment of these software systems drive the DNS security software market. Additionally, cloud-based DNS helps enterprises configure the Domain Name System Security Extensions (DNSSEC), a method for authenticating DNS records and enabling protection against known attacks. Moreover, cloud-based DNS security software systems offer advanced traffic routings, facilitating round-robin, latency-based routing, geographic DNS, and geo-proximity routing to simple failover. Cloud-based DNS aid in better monitoring and visibility and make configuration changes easy and convenient for enterprises. Enterprises can scale up and down their working productivity with cloud deployment. Therefore, numerous small and medium enterprises (SMEs) believe cloud deployment to be the most effective deployment platform for DNS security software solutions.
Market Restraints and Challenges
In open source, developers take an existing Organization Size/program in the open-source market, make improvements, add features, and share their modifications with the community for everyone’s benefit. On the other side, closed source software (known as proprietary software) belongs to a company/individual that licenses the software and has sole rights to distribute the code.
While open-source software may be free to use in terms of price, furthermore, there are many other reasons open-source software can be the better choice overall for business needs, including access to a talented community of developers and the flexibility to integrate other pieces of technology within the software. Further, many good reasons why more companies are turning to open-source software exist. Firstly, expert developers continuously monitor and improve open-source software, catching and fixing bugs collaboratively. This leads to reliable, stable, and performant software that works across various environments. Secondly, open-source software is attractive for multiple businesses due to there are no up-front costs to download the code and start working with it. Thirdly, available source code leads to greater longevity and stability of the open-source product, as it can’t be phased out, such as proprietary software, which is at the mercy of a commercial vendor. Thus, the rising availability of open-source software is acting as a restraining factor for the closed source software manufacturers.
Unlock Growth Potential in Your Industry – Get Your Sample Report Now-https://www.globalinsightservices.com/request-sample/GIS10394
Global DNS Security Software Market Segmentation
By Deployment Type
On-Premise
Cloud-Based
By Organization Size
SMEs
Large Enterprises
Major Players in the Global DNS Security Software Market
The key players studied in the global DNS security software market are Akamai Technologies (US), Cloudflare, Inc. (US), Comodo Security Solutions, Inc. (US), DNSFilter Inc. (US), DomainTools LLC (US), Efficient IP (US), Open Text Corporation (Canada), Palo Alto Networks Inc. (US), ScoutDNS, LLC (US), and TitanHQ (Ireland).
COVID-19 Impact
In 2020, the COVID-19 pandemic had positively impacted the growth of the DNS security software market, as millions of employees were asked to do work from home by their companies. As employees accessed corporate systems through the less-secure home and public Wi-Fi networks, the remote working practices led to a surge in queries for DNS, further increasing cyber-attacks targeting DNS and boosting the demand for DNS security software.
Buy Now@https://www.globalinsightservices.com/checkout/single_user/GIS10394
Research Scope
Scope – Highlights, Trends, Insights. Attractiveness, Forecast
Market Sizing – Product Type, End User, Offering Type, Technology, Region, Country, Others
Market Dynamics – Market Segmentation, Demand and Supply, Bargaining Power of Buyers and Sellers, Drivers, Restraints, Opportunities, Threat Analysis, Impact Analysis, Porters 5 Forces, Ansoff Analysis, Supply Chain
Business Framework – Case Studies, Regulatory Landscape, Pricing, Policies and Regulations, New Product Launches. M&As, Recent Developments
Competitive Landscape – Market Share Analysis, Market Leaders, Emerging Players, Vendor Benchmarking, Developmental Strategy Benchmarking, PESTLE Analysis, Value Chain Analysis
Company Profiles – Overview, Business Segments, Business Performance, Product Offering, Key Developmental Strategies, SWOT Analysis.
With Global Insight Services, you receive:
10-year forecast to help you make strategic decisions
In-depth segmentation which can be customized as per your requirements
Free consultation with lead analyst of the report
Infographic excel data pack, easy to analyze big data
Robust and transparent research methodology
Unmatched data quality and after sales service
Contact Us:
Global Insight Services LLC
16192, Coastal Highway, Lewes DE 19958
E-mail: [email protected]
Phone: +1-833-761-1700
Website: https://www.globalinsightservices.com/
About Global Insight Services:
Global Insight Services (GIS) is a leading multi-industry market research firm headquartered in Delaware, US. We are committed to providing our clients with highest quality data, analysis, and tools to meet all their market research needs. With GIS, you can be assured of the quality of the deliverables, robust & transparent research methodology, and superior service.
0 notes
Text
The Evolution and Impact of the Web Content Filtering Market and Artificial Intelligence for IT Operations Platform Market
In today's rapidly evolving digital landscape, two markets have garnered significant attention: the Web Content Filtering Market and the Artificial Intelligence for IT Operations (AIOps) Platform Market. These two sectors are pivotal in shaping how businesses manage and secure their digital operations. This article delves into the nuances of these markets, exploring their growth, key players, technological advancements, and future trends.

1. Introduction to Web Content Filtering
What is Web Content Filtering?
Web content filtering is a crucial aspect of internet security, involving the control of what content is accessible over the internet within a particular network. It helps organizations prevent access to harmful or inappropriate websites, thus safeguarding employees and data.
Importance of Web Content Filtering
The importance of web content filtering cannot be overstated. It helps protect against malware, phishing attacks, and other cyber threats. Additionally, it ensures compliance with legal and regulatory standards, improves productivity by blocking distracting websites, and maintains a company's reputation by preventing access to inappropriate content.
2. Market Overview of Web Content Filtering
Current Market Size and Growth
The web content filtering market has experienced substantial growth over the past decade. As of 2023, it is valued at approximately $6 billion and is expected to grow at a CAGR of 14.8% from 2023 to 2028. This growth is driven by increasing cyber threats, the proliferation of internet usage, and stringent regulatory requirements.
Key Players in the Web Content Filtering Market
Several key players dominate the web content filtering market. These include:
Cisco: Known for its robust security solutions, Cisco offers comprehensive web content filtering services.
McAfee: A leader in cybersecurity, McAfee provides advanced web filtering solutions to protect against various threats.
Symantec: Now a part of Broadcom, Symantec offers powerful web filtering tools integrated with its broader cybersecurity suite.
Forcepoint: Specializes in data protection and cybersecurity, including web content filtering.
Webroot: Provides cloud-based web filtering solutions that are easy to deploy and manage.
Technological Advancements in Web Content Filtering
The web content filtering market has seen significant technological advancements, such as:
AI and Machine Learning: AI-driven algorithms enhance the accuracy of filtering by continuously learning from new threats and user behaviors.
Cloud-Based Solutions: Cloud-based filtering offers scalability, easier management, and real-time updates.
Integration with Other Security Tools: Modern web content filtering solutions are often integrated with broader cybersecurity frameworks, providing comprehensive protection.
3. Challenges in the Web Content Filtering Market
Evolving Cyber Threats
As cyber threats become more sophisticated, web content filtering solutions must continuously evolve to keep up. This requires constant updates and the incorporation of advanced technologies like AI.
User Privacy Concerns
Balancing effective content filtering with user privacy is a significant challenge. Companies must ensure that their filtering practices comply with privacy laws and do not infringe on users' rights.
Implementation and Management
Implementing and managing web content filtering solutions can be complex, especially for large organizations with diverse networks and numerous endpoints.
4. Future Trends in Web Content Filtering
Increased Use of AI and Machine Learning
AI and machine learning will play an increasingly important role in web content filtering. These technologies will enhance the accuracy and efficiency of filtering processes, enabling quicker responses to emerging threats.
Greater Emphasis on User Privacy
As privacy concerns continue to grow, future web content filtering solutions will need to strike a better balance between security and privacy. This could involve more transparent filtering practices and greater user control over what is filtered.
Integration with Comprehensive Security Frameworks
Web content filtering will increasingly be part of integrated security solutions that offer comprehensive protection against a range of cyber threats. This holistic approach will provide better overall security for organizations.
5. Introduction to AIOps Platforms
What are AIOps Platforms?
AIOps platforms use artificial intelligence to enhance IT operations. They analyze large volumes of data from various IT operations tools and devices to automatically identify and resolve IT issues. This helps improve the efficiency and reliability of IT operations.
Importance of AIOps Platforms
AIOps platforms are essential for modern IT operations due to their ability to handle the complexity and scale of today's IT environments. They help reduce downtime, improve performance, and enhance the overall user experience.
6. Market Overview of AIOps Platforms
Current Market Size and Growth
The AIOps platform market is also experiencing rapid growth. As of 2023, it is valued at approximately $2.5 billion and is expected to grow at a CAGR of 25% from 2023 to 2028. This growth is driven by the increasing complexity of IT environments and the need for more efficient and reliable IT operations.
Key Players in the AIOps Platform Market
Key players in the AIOps platform market include:
Splunk: Offers a comprehensive AIOps platform that provides visibility across the entire IT environment.
Moogsoft: Specializes in AI-driven IT incident management and analytics.
IBM: Provides a powerful AIOps platform that leverages its expertise in AI and cloud computing.
Dynatrace: Offers an AI-driven platform for monitoring and managing IT operations.
AppDynamics: Now part of Cisco, AppDynamics provides a robust AIOps platform focused on application performance management.
Technological Advancements in AIOps Platforms
Technological advancements driving the AIOps platform market include:
Advanced Analytics: Improved data analytics capabilities allow for more accurate identification and resolution of IT issues.
Automation: Enhanced automation capabilities reduce the need for manual intervention, improving efficiency and reliability.
Integration with Other IT Tools: Modern AIOps platforms integrate with a wide range of IT tools, providing a more comprehensive view of IT operations.
7. Challenges in the AIOps Platform Market
Data Complexity and Volume
Handling the sheer volume and complexity of data generated by modern IT environments is a significant challenge for AIOps platforms. Effective data management and analysis are crucial for the success of these platforms.
Integration with Existing Systems
Integrating AIOps platforms with existing IT systems can be complex and time-consuming. Ensuring seamless integration is essential for maximizing the benefits of these platforms.
Skill Gaps
The successful implementation of AIOps platforms requires specialized skills. There is a growing need for IT professionals with expertise in AI, data analytics, and IT operations.
8. Future Trends in the AIOps Platform Market
Enhanced AI Capabilities
As AI technology continues to advance, AIOps platforms will become even more powerful. Enhanced AI capabilities will allow for more accurate predictions, faster issue resolution, and improved overall performance.
Greater Automation
Future AIOps platforms will feature even greater levels of automation, reducing the need for manual intervention and allowing IT teams to focus on more strategic tasks.
Broader Integration
AIOps platforms will increasingly integrate with a wider range of IT tools and systems, providing a more comprehensive view of IT operations and enabling better decision-making.
9. The Intersection of Web Content Filtering and AIOps
Synergies Between the Two Markets
There are significant synergies between the web content filtering and AIOps platform markets. Both markets focus on improving security, efficiency, and reliability in the digital landscape. Integrating web content filtering with AIOps platforms can enhance overall IT security and operations.
Combined Benefits for Organizations
Organizations that leverage both web content filtering and AIOps platforms can achieve enhanced security and operational efficiency. Web content filtering protects against cyber threats, while AIOps platforms ensure reliable and efficient IT operations.
Future Opportunities
The convergence of these two markets presents future opportunities for innovation and growth. As organizations continue to adopt digital transformation strategies, the integration of web content filtering and AIOps platforms will become increasingly important.
10. Conclusion
In conclusion, the Web Content Filtering Market and the Artificial Intelligence for IT Operations Platform Market are both critical components of modern digital security and operations. As cyber threats evolve and IT environments become more complex, the demand for advanced web content filtering and AIOps solutions will continue to grow. Organizations that invest in these technologies will be better positioned to protect their digital assets, ensure compliance, and improve operational efficiency. The future holds exciting opportunities for these markets, driven by technological advancements and the increasing importance of digital security and reliability.
1 note
·
View note
Text
Global Cybersecurity as a Service (CSaaS) Market: Growth, Trends, and Forecast 2024-2032
Market Overview
The Cybersecurity as a Service (CSaaS) market is rapidly expanding as organizations increasingly prioritize the protection of their digital assets against evolving cyber threats. This market provides on-demand security solutions and services via the cloud, offering flexibility, scalability, and cost-efficiency. Key offerings include threat intelligence, managed security services, security information and event management (SIEM), and endpoint protection.
0 notes
Text
Headless Content Management: The Future of Flexible Digital Experiences
In the rapidly evolving digital landscape, headless content management systems (CMS) have emerged as a revolutionary solution for businesses seeking greater flexibility and efficiency in delivering content across multiple platforms. Unlike traditional CMSs, which tightly couple the backend content repository with the frontend presentation layer, headless CMS decouples these two components, providing unparalleled freedom in how content is managed and delivered.
A headless CMS operates with a "content-first" approach. It stores and organizes content in a backend system and delivers it via APIs to any frontend or device, whether it's a website, mobile app, IoT device, or digital signage. This decoupling allows developers to use any technology or framework to build the frontend, giving them the flexibility to create highly customized and dynamic digital experiences.
One of the primary benefits of a headless CMS is its ability to provide a consistent content experience across multiple channels. As consumers interact with brands through various touchpoints, maintaining a unified and coherent message becomes crucial. With a headless CMS, content can be created once and reused across different platforms, ensuring consistency while reducing the effort and time required for content updates.
The headless architecture also significantly enhances the speed and agility of content delivery. Traditional CMS platforms often struggle with performance issues as they try to handle both content management and delivery. In contrast, a headless CMS focuses solely on content management, leaving the delivery to specialized frontend technologies. This separation results in faster load times and a smoother user experience, especially on mobile devices where performance is critical.
Moreover, headless CMSs are ideal for businesses looking to future-proof their digital strategies. As new devices and platforms emerge, organizations using a headless CMS can easily adapt by connecting their existing content repository to these new endpoints via APIs. This adaptability ensures that businesses can quickly respond to market trends and technological advancements without overhauling their entire content management system.
Security is another significant advantage of headless CMSs. By decoupling the frontend from the backend, the attack surface is reduced, and potential vulnerabilities are minimized. Additionally, most headless CMS providers offer robust security features, such as encryption and role-based access controls, to protect sensitive data.
In conclusion, headless content management systems represent a forward-thinking approach to digital content delivery. By decoupling the backend and frontend, businesses gain unparalleled flexibility, speed, and scalability in managing and delivering content. As the digital landscape continues to evolve, adopting a headless CMS can provide the agility and innovation necessary to stay ahead of the competition and meet the ever-changing needs of consumers.
Website:- https://www.rws.com/content-management/tridion/
0 notes
Text
Cyber Security Market - Forecast(2024 - 2030)
Cyber Security Market Overview
Cyber Security Marketsize is forecast to reach $360 billion by 2030, estimated to grow at a CAGR of 9.5% during 2024-2030. The increasing use of technology such as artificial intelligence, IoT, machine learning and so on are significantly driving the cybersecurity market. Furthermore, the increasing demand for cloud-based cybersecurity systems in order to reduce data loss are also enhancing the growth of the market. The rising demand for network and endpoint security, information technology security mobile security, behavioral detection is fueling the growth of the market during the forecast period. The telecom organizations are adopting advanced cyber security solutions such as real-time security monitoring, instant cyber posture visibility, and rapid threat resolution to prevent the cyber-attack on telecom networks. Along with the telecom sector, the aerospace industry is considered to be another key end-users to cyber security market. The aerospace and defense industry are prone to cyber-attack due to its continuous exposure to non-A&D, OT-based technologies.
Thus, this industry is adopting advanced cybersecurity solution to enhance protection against cybercrime. The rising need for solutions ranging from antivirus software, unified threat management system, next-generation firewalls, DNS filtering, malware protection and threat intelligence will drive the demand for cyber security. One prominent trend in the cyber security market is the increasing adoption of Zero Trust Architecture (ZTA). This approach challenges the traditional perimeter-based security model by assuming that threats can originate from both inside and outside the network. ZTA emphasizes strict identity verification and access controls, requiring continuous authentication and authorization for every user and device attempting to access resources. With the proliferation of cloud services, remote work, and mobile devices, organizations are realizing the limitations of perimeter defenses alone. As a result, they are turning to ZTA to bolster their defenses and mitigate the risks associated with insider threats, unauthorized access, and advanced persistent threats.
The growing recognition of ZTA's effectiveness in enhancing security posture is driving significant investment in Zero Trust solutions across various industries. Another key trend shaping the cyber security market is the increasing integration of artificial intelligence (AI) and machine learning (ML) technologies for threat detection and response. As cyber threats become more sophisticated and prevalent, organizations are turning to AI-driven solutions to augment their security operations. AI and ML algorithms can analyze vast amounts of data in real-time, enabling early detection of anomalies, unusual patterns, and potential security breaches. These technologies empower security teams to identify and respond to threats more efficiently, reducing detection and response times. Moreover, AI-driven security solutions can automate repetitive tasks, freeing up security personnel to focus on more strategic initiatives. With the continuous evolution of cyber threats, the demand for AI-powered security tools and platforms is expected to grow, driving innovation and investment in the development of advanced threat detection and response capabilities.
Cyber Security Market Report Coverage
The report: “Cyber Security Market Forecast (2024-2030)”, by IndustryARC, covers an in-depth analysis of the following segments of the Cyber Security System Market.
By Component: Cyber Security Software, Cyber Security Hardware, Cyber Security Services.
By Deployment: On-Premise and Cloud.
By Security Type: Network & Endpoint Security, Internet of Things/Industrial Internet of Things Security, Threat Intelligence, Mobile Security, Behavioral Detection, Cloud Security, Deception Security and Others.
By Organization Size: SME, Large Enterprise.
By Solution: Antivirus, UTM, SIEM, DDOS Mitigation, Disaster Recovery, Firewall, DLP, Web Filtering, Threat Intelligence, IAM, Risk and Compliance Management, IDS, Encryption and Others.
By Industry Vertical: Aerospace, Government, Financial Services, Healthcare, Telecommunications, Automobile, Information Technology sector and others
By Geography: North America (U.S, Canada, Mexico), Europe(Germany, UK, France, Italy, Spain, Russia, Netherlands, Denmark and Others), APAC(China, Japan India, South Korea, Australia, Taiwan, Malaysia and Others), South America(Brazil, Argentina, Ecuador, Peru, Colombia, Costa Rica and others), and RoW (Middle east and Africa)
Request Sample
Key Takeaways
• In 2023, the Cyber Security market was dominated by North America owing to the increasing use of prevalent technology which has raised the risk of cyber threat leading to the need for cybersecurity solutions.
• The rising demand for cloud-based cybersecurity solutions in order to store and secure data during data loss or data breaches has driven the growth of the market
• The rapid advancement of artificial intelligence leading to the introduction of technologies such as machine learning and deep learning which will enhance the growth of the market.
• The rising security threats due to the increasing use of Blockchain systems and IoT threats are making difficult to detect cyber-attacks which is hampering the market growth.
Cyber Security Market Segment Analysis – By Deployment
Cloud segment held the largest market share of 53.1% in the Cybersecurity market in 2023. The growing of massive store applications in order to store and secure data with advanced security methods are driving the need for cloud-based security solutions. As cloud-based cybersecurity solutions offers social networking privacy, online storage, system optimization and so on. Furthermore, the rising demand for online cloud storage leads to provide backup and restorations of data caused due to data breaches or data loss. These significant advantages of cloud technology will lead to surge the growth of the market.
Inquiry Before Buying
Cyber Security Market Segment Analysis - By Industry Vertical
The telecom sector is estimated to grow at a CAGR of 10.2% during the forecast period 2023-2030. The GSM Association (GSMA) predicted that quantum computing will be a destabilizer for the telecom sector, making Public Key Infrastructure (PKI) obsolete in the near future. Telecommunication companies are in plans of implementing quantum-safe cryptography algorithms to mitigate cyber-attacks. In order to control cyber-attacks, the European Union (EU) has introduced many regulations such as the Network and Information Security Directive (NISD) and the General Data Protection Regulations (GDPR). NISD is yet to be implemented which requires core digital infrastructure operators and certain digital service providers to ensure that their network and information systems meet minimum standards of cybersecurity. These regulations are implemented to achieve and maintain high network security, and ensure obligatory reporting during any incidents.
Cyber Security Market Segment Analysis – By Geography
In 2023, North America dominated the Cyber Security market with a share of more than 40.2%, followed by Europe and APAC. The growing use of technology and data has led to the rise of most vulnerable cyber threats and crimes which is leading to the growth of this market in this region. Also, the financial stability in this region has allowed organization to invest in cybersecurity for providing security of data and software. These developments are propelling the growth of cybersecurity market in North America.
Schedule a Call
Cyber Security Market Drivers
Rising importance Artificial Intelligence (AI)
The rising advancement in artificial intelligence is leading to the introduction of machine learning technologies into products which includes cybersecurity. Moreover, technologies such as deep learning are being used for face detection, natural language processing, threat detection, and others concepts. Also, the acceleration of artificial intelligence (AI) has led to the identification of new threats and helps in responding and block cyber-attacks in an organization. Hence, the deployment of artificial intelligence technologies will further drive the growth of the cybersecurity market.
Increasing need for Cybersecurity in Aerospace
Aerospace industry is widely developing with the integration of new technology such as advanced navigation and guidance systems. This system are used in airplanes which are highly vulnerable to cyber-attacks, which have irrevocable repercussions. So, the rising risk of cyber-attacks and the increasing need to protect the computer networks in the air are leading to the rise of investment in the security infrastructure. Thus, the rising investment by aerospace industry in the security infrastructure has led to the requirement of cybersecurity further boosting the growth of the market.
Cyber Security Market Challenges
Revolution of Blockchain and IoT Threats
The rising demand for Blockchain systems has made it difficult to predict the rising cyber threats which is hindering the cybersecurity market. Furthermore, the increasing usage of IoT has led to the growing number of IoT threats, as IoT includes the connection of physical devices which have a unique identifier (UID). These devices has the ability to transfer data over a network without any human interference and human to computer interaction. Thus, the software and firmware which are required to run these IoT devices make the user more susceptible to cyber-attacks further hindering the growth of the market.
Buy Now
Cyber Security Market Landscape
Technology launches, acquisitions and R&D activities are key strategies adopted by players in the Cyber Security market. In 2023, the market of Cyber Security has been consolidated by the major players – AWS, Check Point Software Technologies, NTT Security, Cisco Systems, CyberArk, FireEye, IBM Corporation, Oracle, Microsoft and Juniper Networks.
Acquisitions/Technology Launches
In December 2023, Multinational conglomerate Honeywell has agreed to buy Carrier’s Global Access Solutions business for $4.95 billion in cash. The acquisition will strengthen Honeywell’s core security offerings with the addition of hardware and software properties
In Nov 2023, US-based data security company Rubrik has launched Ruby, its generative AI extension for Rubrik Security Cloud, which will speed up cyber threat detection, recovery and resilience. In response to data risk alerts generated in Rubrik Security Cloud, users can interact with Ruby, the company's AI assistant, ask follow-up questions including whether any sensitive data was impacted, or what needs to be done to restore the environment.
#Cyber Security Market#Cloud Security#Cyber Security Market size#Threat Intelligence#Cyber Security industry#Cyber Security Market share#Cyber Security top 10 companies#Cyber Security Market report#Cyber Security industry outlook
0 notes
Text
Evolving cyber security in the financial services sector - CyberTalk
New Post has been published on https://thedigitalinsider.com/evolving-cyber-security-in-the-financial-services-sector-cybertalk/
Evolving cyber security in the financial services sector - CyberTalk


EXECUTIVE SUMMARY:
The financial sector is a leading target for cyber criminals and cyber criminal attacks. Markedly improving the sector’s cyber security and resilience capabilities are a must. While the sector does have a comparatively high level of cyber security maturity, security gaps invariably persist and threaten to subvert systems.
As Check Point CISO Pete Nicoletti has noted, attackers only need to get it right once in order to catalyze strongly negative, systemic consequences that could send shockwaves throughout companies and lives across the globe.
In this article, discover financial sector trends, challenges and recommendations that can transform how you see and respond to the current cyber threat landscape.
Industry trends
According to a newly emergent report, 65% of financial services sector organizations have endured cyber attacks.
The median ransom demand is $2 million. Mean recovery costs have soared to roughly $2.6 million – up from $2.2 million in 2023.
The size of extreme losses has quadrupled since 2017, to $2.5 billion.
The potential for losses is substantial, especially when multiplied in order to account for downstream effects.
Industry challenges
The majority of financial leaders lack confidence in their organization’s cyber security capabilities, according to the latest research.
Eighty-percent of financial service firm leaders say that they’re unable to lead future planning efforts effectively due to concerns regarding their organization’s abilities to thwart a cyber attack.
There is a significant gap between where financial sector institutions want to be with cyber security and where the industry is right now.
Preparing for disruption
Beyond cyber security, financial sector groups need to concern themselves with business continuity in the event of disruption — which is perhaps more likely than not.
“While cyber incidents will occur, the financial sector needs the capacity to deliver critical business services during these disruptions,” writes the International Monetary Fund.
A major disruption – the financial sector equivalent of the Colonial Pipeline attack – could disable infrastructure, erode confidence in the financial system, or lead to bank runs and market selloffs.
To put the idea into sharper relief, in December of 2023, the Central Bank of Lesotho experienced outages after a cyber attack. While the public did not suffer financial losses, the national payment system could not honor inter-bank transactions for some time.
Industry recommendations
Organizations need innovative approaches to cyber security — approaches that prevent the latest and most sophisticated threats. Approaches that fend off disaster from a distance.
In 2023, nearly 30 different malware families targeted 1,800 banking applications across 61 different nations.
At Check Point, our AI-powered, cloud-delivered cyber security architecture addresses everything — networks, endpoints, cloud environments and mobile devices via a unified approach.
We’ve helped thousands of organizations, like yours, mitigate risks and expand business resilience. Learn more here.
For additional financial services insights, please see CyberTalk.org’s past coverage. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2023#ai#AI-powered#analyses#applications#approach#architecture#Article#Articles#attackers#bank#banking#banks#billion#Business#business continuity#business resilience#Check Point#CISO#Cloud#cloud-delivered#Companies#cyber#cyber attack#cyber attacks#cyber criminals#cyber security#cyber threat#cybersecurity#december
0 notes