#facebook hacking preventing
Explore tagged Tumblr posts
Text
The moral injury of having your work enshittified

This Monday (November 27), I'm appearing at the Toronto Metro Reference Library with Facebook whistleblower Frances Haugen.
On November 29, I'm at NYC's Strand Books with my novel The Lost Cause, a solarpunk tale of hope and danger that Rebecca Solnit called "completely delightful."

This week, I wrote about how the Great Enshittening – in which all the digital services we rely on become unusable, extractive piles of shit – did not result from the decay of the morals of tech company leadership, but rather, from the collapse of the forces that discipline corporate wrongdoing:
https://locusmag.com/2023/11/commentary-by-cory-doctorow-dont-be-evil/
The failure to enforce competition law allowed a few companies to buy out their rivals, or sell goods below cost until their rivals collapsed, or bribe key parts of their supply chain not to allow rivals to participate:
https://www.engadget.com/google-reportedly-pays-apple-36-percent-of-ad-search-revenues-from-safari-191730783.html
The resulting concentration of the tech sector meant that the surviving firms were stupendously wealthy, and cozy enough that they could agree on a common legislative agenda. That regulatory capture has allowed tech companies to violate labor, privacy and consumer protection laws by arguing that the law doesn't apply when you use an app to violate it:
https://pluralistic.net/2023/04/12/algorithmic-wage-discrimination/#fishers-of-men
But the regulatory capture isn't just about preventing regulation: it's also about creating regulation – laws that make it illegal to reverse-engineer, scrape, and otherwise mod, hack or reconfigure existing services to claw back value that has been taken away from users and business customers. This gives rise to Jay Freeman's perfectly named doctrine of "felony contempt of business-model," in which it is illegal to use your own property in ways that anger the shareholders of the company that sold it to you:
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Undisciplined by the threat of competition, regulation, or unilateral modification by users, companies are free to enshittify their products. But what does that actually look like? I say that enshittification is always precipitated by a lost argument.
It starts when someone around a board-room table proposes doing something that's bad for users but good for the company. If the company faces the discipline of competition, regulation or self-help measures, then the workers who are disgusted by this course of action can say, "I think doing this would be gross, and what's more, it's going to make the company poorer," and so they win the argument.
But when you take away that discipline, the argument gets reduced to, "Don't do this because it would make me ashamed to work here, even though it will make the company richer." Money talks, bullshit walks. Let the enshittification begin!
https://pluralistic.net/2023/11/22/who-wins-the-argument/#corporations-are-people-my-friend
But why do workers care at all? That's where phrases like "don't be evil" come into the picture. Until very recently, tech workers participated in one of history's tightest labor markets, in which multiple companies with gigantic war-chests bid on their labor. Even low-level employees routinely fielded calls from recruiters who dangled offers of higher salaries and larger stock grants if they would jump ship for a company's rival.
Employers built "campuses" filled with lavish perks: massages, sports facilities, daycare, gourmet cafeterias. They offered workers generous benefit packages, including exotic health benefits like having your eggs frozen so you could delay fertility while offsetting the risks normally associated with conceiving at a later age.
But all of this was a transparent ruse: the business-case for free meals, gyms, dry-cleaning, catering and massages was to keep workers at their laptops for 10, 12, or even 16 hours per day. That egg-freezing perk wasn't about helping workers plan their families: it was about thumbing the scales in favor of working through your entire twenties and thirties without taking any parental leave.
In other words, tech employers valued their employees as a means to an end: they wanted to get the best geeks on the payroll and then work them like government mules. The perks and pay weren't the result of comradeship between management and labor: they were the result of the discipline of competition for labor.
This wasn't really a secret, of course. Big Tech workers are split into two camps: blue badges (salaried employees) and green badges (contractors). Whenever there is a slack labor market for a specific job or skill, it is converted from a blue badge job to a green badge job. Green badges don't get the food or the massages or the kombucha. They don't get stock or daycare. They don't get to freeze their eggs. They also work long hours, but they are incentivized by the fear of poverty.
Tech giants went to great lengths to shield blue badges from green badges – at some Google campuses, these workforces actually used different entrances and worked in different facilities or on different floors. Sometimes, green badge working hours would be staggered so that the armies of ragged clickworkers would not be lined up to badge in when their social betters swanned off the luxury bus and into their airy adult kindergartens.
But Big Tech worked hard to convince those blue badges that they were truly valued. Companies hosted regular town halls where employees could ask impertinent questions of their CEOs. They maintained freewheeling internal social media sites where techies could rail against corporate foolishness and make Dilbert references.
And they came up with mottoes.
Apple told its employees it was a sound environmental steward that cared about privacy. Apple also deliberately turned old devices into e-waste by shredding them to ensure that they wouldn't be repaired and compete with new devices:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
And even as they were blocking Facebook's surveillance tools, they quietly built their own nonconsensual mass surveillance program and lied to customers about it:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Facebook told employees they were on a "mission to connect every person in the world," but instead deliberately sowed discontent among its users and trapped them in silos that meant that anyone who left Facebook lost all their friends:
https://www.eff.org/deeplinks/2021/08/facebooks-secret-war-switching-costs
And Google promised its employees that they would not "be evil" if they worked at Google. For many googlers, that mattered. They wanted to do something good with their lives, and they had a choice about who they would work for. What's more, they did make things that were good. At their high points, Google Maps, Google Mail, and of course, Google Search were incredible.
My own life was totally transformed by Maps: I have very poor spatial sense, need to actually stop and think to tell my right from my left, and I spent more of my life at least a little lost and often very lost. Google Maps is the cognitive prosthesis I needed to become someone who can go anywhere. I'm profoundly grateful to the people who built that service.
There's a name for phenomenon in which you care so much about your job that you endure poor conditions and abuse: it's called "vocational awe," as coined by Fobazi Ettarh:
https://www.inthelibrarywiththeleadpipe.org/2018/vocational-awe/
Ettarh uses the term to apply to traditionally low-waged workers like librarians, teachers and nurses. In our book Chokepoint Capitalism, Rebecca Giblin and I talked about how it applies to artists and other creative workers, too:
https://chokepointcapitalism.com/
But vocational awe is also omnipresent in tech. The grandiose claims to be on a mission to make the world a better place are not just puffery – they're a vital means of motivating workers who can easily quit their jobs and find a new one to put in 16-hour days. The massages and kombucha and egg-freezing are not framed as perks, but as logistical supports, provided so that techies on an important mission can pursue a shared social goal without being distracted by their balky, inconvenient meatsuits.
Steve Jobs was a master of instilling vocational awe. He was full of aphorisms like "we're here to make a dent in the universe, otherwise why even be here?" Or his infamous line to John Sculley, whom he lured away from Pepsi: "Do you want to sell sugar water for the rest of your life or come with me and change the world?"
Vocational awe cuts both ways. If your workforce actually believes in all that high-minded stuff, if they actually sacrifice their health, family lives and self-care to further the mission, they will defend it. That brings me back to enshittification, and the argument: "If we do this bad thing to the product I work on, it will make me hate myself."
The decline in market discipline for large tech companies has been accompanied by a decline in labor discipline, as the market for technical work grew less and less competitive. Since the dotcom collapse, the ability of tech giants to starve new entrants of market oxygen has shrunk techies' dreams.
Tech workers once dreamed of working for a big, unwieldy firm for a few years before setting out on their own to topple it with a startup. Then, the dream shrank: work for that big, clumsy firm for a few years, then do a fake startup that makes a fake product that is acquihired by your old employer, as an incredibly inefficient and roundabout way to get a raise and a bonus.
Then the dream shrank again: work for a big, ugly firm for life, but get those perks, the massages and the kombucha and the stock options and the gourmet cafeteria and the egg-freezing. Then it shrank again: work for Google for a while, but then get laid off along with 12,000 co-workers, just months after the company does a stock buyback that would cover all those salaries for the next 27 years:
https://pluralistic.net/2023/09/10/the-proletarianization-of-tech-workers/
Tech workers' power was fundamentally individual. In a tight labor market, tech workers could personally stand up to their bosses. They got "workplace democracy" by mouthing off at town hall meetings. They didn't have a union, and they thought they didn't need one. Of course, they did need one, because there were limits to individual power, even for the most in-demand workers, especially when it came to ghastly, long-running sexual abuse from high-ranking executives:
https://www.nytimes.com/2018/10/25/technology/google-sexual-harassment-andy-rubin.html
Today, atomized tech workers who are ordered to enshittify the products they take pride in are losing the argument. Workers who put in long hours, missed funerals and school plays and little league games and anniversaries and family vacations are being ordered to flush that sacrifice down the toilet to grind out a few basis points towards a KPI.
It's a form of moral injury, and it's palpable in the first-person accounts of former workers who've exited these large firms or the entire field. The viral "Reflecting on 18 years at Google," written by Ian Hixie, vibrates with it:
https://ln.hixie.ch/?start=1700627373
Hixie describes the sense of mission he brought to his job, the workplace democracy he experienced as employees' views were both solicited and heeded. He describes the positive contributions he was able to make to a commons of technical standards that rippled out beyond Google – and then, he says, "Google's culture eroded":
Decisions went from being made for the benefit of users, to the benefit of Google, to the benefit of whoever was making the decision.
In other words, techies started losing the argument. Layoffs weakened worker power – not just to defend their own interest, but to defend the users interests. Worker power is always about more than workers – think of how the 2019 LA teachers' strike won greenspace for every school, a ban on immigration sweeps of students' parents at the school gates and other community benefits:
https://pluralistic.net/2023/04/23/a-collective-bargain/
Hixie attributes the changes to a change in leadership, but I respectfully disagree. Hixie points to the original shareholder letter from the Google founders, in which they informed investors contemplating their IPO that they were retaining a controlling interest in the company's governance so that they could ignore their shareholders' priorities in favor of a vision of Google as a positive force in the world:
https://abc.xyz/investor/founders-letters/ipo-letter/
Hixie says that the leadership that succeeded the founders lost sight of this vision – but the whole point of that letter is that the founders never fully ceded control to subsequent executive teams. Yes, those executive teams were accountable to the shareholders, but the largest block of voting shares were retained by the founders.
I don't think the enshittification of Google was due to a change in leadership – I think it was due to a change in discipline, the discipline imposed by competition, regulation and the threat of self-help measures. Take ads: when Google had to contend with one-click adblocker installation, it had to constantly balance the risk of making users so fed up that they googled "how do I block ads?" and then never saw another ad ever again.
But once Google seized the majority of the mobile market, it was able to funnel users into apps, and reverse-engineering an app is a felony (felony contempt of business-model) under Section 1201 of the Digital Millennium Copyright Act. An app is just a web-page wrapped in enough IP to make it a crime to install an ad-blocker.
And as Google acquired control over the browser market, it was likewise able to reduce the self-help measures available to browser users who found ads sufficiently obnoxious to trigger googling "how do I block ads?" The apotheosis of this is the yearslong campaign to block adblockers in Chrome, which the company has sworn it will finally do this coming June:
https://www.tumblr.com/tevruden/734352367416410112/you-have-until-june-to-dump-chrome
My contention here is not that Google's enshittification was precipitated by a change in personnel via the promotion of managers who have shitty ideas. Google's enshittification was precipitated by a change in discipline, as the negative consequences of heeding those shitty ideas were abolished thanks to monopoly.
This is bad news for people like me, who rely on services like Google Maps as cognitive prostheses. Elizabeth Laraki, one of the original Google Maps designers, has published a scorching critique of the latest GMaps design:
https://twitter.com/elizlaraki/status/1727351922254852182
Laraki calls out numerous enshittificatory design-choices that have left Maps screens covered in "crud" – multiple revenue-maximizing elements that come at the expense of usability, shifting value from users to Google.
What Laraki doesn't say is that these UI elements are auctioned off to merchants, which means that the business that gives Google the most money gets the greatest prominence in Maps, even if it's not the best merchant. That's a recurring motif in enshittified tech platforms, most notoriously Amazon, which makes $31b/year auctioning off top search placement to companies whose products aren't relevant enough to your query to command that position on their own:
https://pluralistic.net/2023/04/25/greedflation/#commissar-bezos
Enshittification begets enshittification. To succeed on Amazon, you must divert funds from product quality to auction placement, which means that the top results are the worst products:
https://pluralistic.net/2023/11/06/attention-rents/#consumer-welfare-queens
The exception is searches for Apple products: Apple and Amazon have a cozy arrangement that means that searches for Apple products are a timewarp back to the pre-enshittification Amazon, when the company worried enough about losing your business to heed the employees who objected to sacrificing search quality as part of a merchant extortion racket:
https://www.businessinsider.com/amazon-gives-apple-special-treatment-while-others-suffer-junk-ads-2023-11
Not every tech worker is a tech bro, in other words. Many workers care deeply about making your life better. But the microeconomics of the boardroom in a monopolized tech sector rewards the worst people and continuously promotes them. Forget the Peter Principle: tech is ruled by the Sam Principle.
As OpenAI went through four CEOs in a single week, lots of commentators remarked on Sam Altman's rise and fall and rise, but I only found one commentator who really had Altman's number. Writing in Today in Tabs, Rusty Foster nailed Altman to the wall:
https://www.todayintabs.com/p/defective-accelerationism
Altman's history goes like this: first, he founded a useless startup that raised $30m, only to be acquired and shuttered. Then Altman got a job running Y Combinator, where he somehow failed at taking huge tranches of equity from "every Stanford dropout with an idea for software to replace something Mommy used to do." After that, he founded OpenAI, a company that he claims to believe presents an existential risk to the entire human risk – which he structured so incompetently that he was then forced out of it.
His reward for this string of farcical, mounting failures? He was put back in charge of the company he mis-structured despite his claimed belief that it will destroy the human race if not properly managed.
Altman's been around for a long time. He founded his startup in 2005. There've always been Sams – of both the Bankman-Fried varietal and the Altman genus – in tech. But they didn't get to run amok. They were disciplined by their competitors, regulators, users and workers. The collapse of competition led to an across-the-board collapse in all of those forms of discipline, revealing the executives for the mediocre sociopaths they always were, and exposing tech workers' vocational awe for the shabby trick it was from the start.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/11/25/moral-injury/#enshittification
#pluralistic#moral injury#enshittification#worker power#google#dont be evil#monopoly#sam altman#openai#vocational awe#making a dent in the universe
562 notes
·
View notes
Text
💫 Join the Fediverse! 💫
Greetings, fellow bloggers! We welcome you to join us in discovering, honoring, and promoting the potential future of social networking—commonly referred to as the "Fediverse."
The Fediverse, or Federation Universe, refers to a collective of online platforms that utilize the web protocol known as ActivityPub, which has set a standard of excellence in regards to both protecting and respecting users' online privacies.
There's a good chance in the past few years that you've caught wind of the fedi family's critically acclaimed Mastodon; however, there are many other unique platforms worth your consideration...
✨ Where To Begin?
Conveniently enough, from the minds of brilliant independent developers, there already likely exists a Fediverse equivalent to your favorite socials. Whether it's an opinion from the critics, or from the community alike—the following popular websites are commonly associated with one another:
Friendica 🐰 = Facebook Mastodon 🐘 = Twitter Pixelfed 🐼 = Instagram PeerTube 🐙 = YouTube Lemmy 🐭 = Reddit
It's worth mentioning, too, a few other sites and forks thereof that are worthy counterparts, which be: Pleroma 🦊 & Misskey 🐱, microblogs also similar to Twitter/Mastodon. Funkwhale 🐋 is a self-hosting audio streamer, which pays homage to the once-popular GrooveShark. For power users, Hubzilla 🐨 makes a great choice (alongside Friendica) when choosing macroblogging alternatives.
✨ To Be Clear...
To address the technicalities: aside from the "definitive" Fediverse clients, we will also be incorporating any platforms that utilize ActivityPub-adjacent protocols as well. These include, but are not limited to: diaspora*; AT Protocol (Bluesky 🦋); Nostr; OStatus; Matrix; Zot; etc. We will NOT be incorporating any decentralized sites that are either questionably or proven to be unethical. (AKA: Gab has been exiled.)
✨ Why Your Privacy Matters
You may ask yourself, as we once did, "Why does protecting my online privacy truly matter?" While it may seem innocent enough on the surface, would it change your mind that it's been officially shared by former corporate media employees that data is more valuable than money to these companies? Outside of the ethical concerns surrounding these concepts, there are many other reasons why protecting your data is critical, be it: security breaches which jeopardize your financial info and risk identity theft; continuing to feed algorithms which use psychological manipulation in attempts to sell you products; the risk of spyware hacking your webcams and microphones when you least expect it; amongst countless other possibilities that can and do happen to individuals on a constant basis. We wish it could all just be written off as a conspiracy... but, with a little research, you'll swiftly realize the validity of these claims are not to be ignored any longer. The solution? Taking the decentralized route.
✨ Our Mission For This Blog
Our mission for establishing this blog includes 3 core elements:
To serve as a hub which anybody can access in order to assist themselves in either: becoming a part of the Fediverse, gaining the resources/knowledge to convince others to do the very same, and providing updates on anything Fedi-related.
We are determined to do anything within our power to prevent what the future of the Internet could become if active social users continue tossing away their data, all while technologies are advancing at faster rates with each passing year. Basically we'd prefer not to live in a cyber-Dystopia at all costs.
Tumblr (Automattic) has expressed interest in switching their servers over to ActivityPub after Musk's acquisition of then-Twitter, and are officially in the transitional process of making this happen for all of us. We're hoping our collective efforts may at some point be recognized by @staff, which in turn will encourage their efforts and stand by their decision.
With that being stated, we hope you decide to follow us here, and decide to make the shift—as it is merely the beginning. We encourage you to send us any questions you may have, any personal suggestions, or corrections on any misinformation you may come across.
From the Tender Hearts of, ✨💞 @disease & @faggotfungus 💞✨
#JOIN THE FEDIVERSE#fediverse#decentralization#internet privacy#social media#social networks#FOSS#activitypub#mastodon#fedi#big data#degoogle#future technology#cybersecurity#technology#essential reading
37 notes
·
View notes
Note
On one hand, having a group chat of some sort to discuss hero-ing shenanigans seems useful. On the other, using Discord or even a text group chat seems like a pretty good way for some tech company to get their hands on a whole bunch of secret identities. Do superheroes have a proprietary app for this sort of thing? Or do they have another solution?
For the JLA and Titans-related heroes, Cyborg's hacking powers render this a total non-issue. On the client end, they use the same texting and messaging apps as everyone else, with a few added bits and bobbles of interface.
On the server end, software that Cyborg set up (took him about 5 minutes) casually intercepts every message they send before it reaches any servers corporations could extract data from, redirects to a private, secure instance of the same chat/texting software (getting Facebook's total source code without authorization is about 0.02 seconds of effort for him), also redirects anyone else in the same chatspace to the same private server, then filters all the messages for sensitive info (there's ways people can flag their own messages) before hacking back into the corporate servers to re-insert a record of some messages they would expect to see as if their own servers had handled everything, so even if admins try to investigate they won't be able to tell who's using the pirated chat instance to ban them.
It's all very complicated from a human perspective but it's all happening totally automatically in real time so it doesn't really matter. The end result is the Titans just have a regular old Discord server that, as far as Discord the company is concerned, doesn't exist, but they can still invite people to who are using regular Discord accounts or chat from their accounts on other normal servers, and other apps are all similarly seamless and convenient.
The Avengers have basically an ultra-high-end spy version of Signal (the app, not Batman's latest son). At first they were just using SHIELD messaging software but after not too long Stark made his own. But the way it's set up, not even Stark has access to all the messages that are sent to anyone besides him. During Civil War he tried to shut down the whole service so the other side couldn't use it, and failed. He just made it too secure and autonymous. Unless someone has the app open and is currently looking at what he wants to see, not even Cyborg could extract chatlogs from it.
The X-Men, X-Force, and X-Factor are basically left out in the cold and forced to use a combination of regular services (some encrypted like Signal) and, when available, and only for the people who agree to it, telepathic chatrooms.
Whoever is "hosting" a telepathic chatroom isn't consciously aware of the messages being subconsciously relayed in real time, but, there's nothing to stop them browsing if they get curious, and as soon as they need to focus and use their powers on anything else strenuous or with stakes, the whole thing shuts down. But the chatlogs being stored in the literal memories of the people in them, that only prevents new messages from being sent for a while (and from being able to literally visually see it), and if the telepathic chatrooms need a new "host" to run it, little is lost in the hand-off.
Of course all of that is just about text chat. Earpiece comms are fairly standard among superheroes, so a lot of communication happens over comms voice calls/recorded voice messages, and that's its own whole topic.
#BronzeRealms#superheroes on Discord#superhero texting#marvel#dc comics#marvel comics#dc universe#justice league#jla#dc titans#the avengers#marvel avengers#x men#dc cyborg#telepathy#the Kimmunicator is worth mentioning but I'll just leave it down here in tags since only a handful of heroes have one#x force#x factor#discord chat
4 notes
·
View notes
Text
Today morning (19.11.2024 08.01 ) I logged into 【tumblr】 in the morning(1st)
Today morning (19.11.2024 08.01 ) I logged into 【tumblr】 in the morning(1st) This is today's my 1st log into【tumblr】(Nearly this time(almost at the same time),I also login in facebook too.)
Yesterday evening,I am tired,Listening Czech language sleeping…………………… Today morning,At 05.45,2 alarm clocks ringing,But I didn't heard. This time,I using ordinary battery(Double Bell Alarm Clock),It ringing for about 50 minutes,But I sleeping too deep,Didn't heard it………………Not on purpose!!!! Beause recently,I doing many houseworks(preparation works)every day,Used up too many physical energy……………… When about 07.13,I got up,Sleeping for 1.5 hours more,Recovery many physical energy. Very Happy Very Happy!!!!
Recently,Too many houseworks,I am too tired,Can't heard the alarm clock ringing. Now,Today,I will recharge the 2 alarm clocks. Big capacity batteries are prepared,They will be take to Czech with alarm clocks. I didn't heard alarm clock,Not on purpose!!!!
Yeserday,I went out to doing some necessary preparing works,Used up many times. Since today,I will not go out doing these preparations,They are all done. Now,Before I go to Czech,Rest days are very less.I will doing many houseworks and preparations at home every day. Very Happy,Very Happy!!!! Very Happy Very Happy!!!!!! Very Very Happy Happy!!!!!!!!!! Happing~!!!!!!!!!!!,Happing~!!!!!!!!!!!!!!!!!!!!!……………………Happy Meowing~!!!!!!!!!!!!!!!!!!!!!…………………………
Recently several days,Because necessary houseworks(preparations…………) are too much every day,Affected my learning Czech language,I learning Very Slow every day,Not on purpose!!!! And,My IDs needs more test,And I using them(Facebook,Tumblr) more carefully,(Prevent the IDs are hacked or stealed.)And prevent being misunderstood………………I learning Czech language,Absolutely Serious,Absolutely Happy!!!! How to prove this simple fact(I learning Czech language,Absolutely Serious,Absolutely Happy!!!!)????………………Meow~!!!!!!…………………… Using websites,Too trouble some…………Meow~!!!!!!!!!!…………………………
Today morning,I continue doing necessary houseworks,Saving time for learning Czech language. Recently,I am learning Czech language 【B1 textbook】【Lesson 13】,Happy Happy!!!! I am preparing Czech language text materials. I am Very Happy!!!! The theme of 【Lesson 13】 is 【What we are and what we look like】. Very Meaningful And Very Happy!!!! I am Very Happy, Very Happy, Very Happy!!!! I am Very Happy learning Czech language!!!! I am Very Happy Very Happy Very Happy!!!!!! Learning Czech Language,The Happiest The Happiest!!!!!!!!!!
Today morning,I got up,Very Happy Very Happy!!!! I learning Czech language and doing necessary houseworks,Very Happy!!!! (Because Too Many Houseworks,Before I go to Czech,Recent several days,Almost have not time learning Czech language………………) I started doing houseworks,Saving time for learning Czech language,Very Happy!!!!!! Very Happy Very Happy!!!!!!(Happing~ Happing~!!!!!!!!!!………………Happy Meowing~!!!!!!!!!!!!!!!!!!!!!……………………)
Recently,Necessary houseworks are increasing,Affect my learning Czech language.Not on purpose!!!! But,Necessary houseworks and perparations are Very Happy!!!!(Note:Happing~,Happing~!!!!!!………………) I doing houseworks,Saving time for learning Czech language,Very Seriously,Very Happily!!!!
Today, where I live, the temperature is 11 degrees Celsius to 15 degrees Celsius, the outdoor temperature is 12 degrees Celsius, and the indoor temperature is 18.9 degrees Celsius. Today morning,I got up,Started learning Czech language,Happy Happy!!!!
This morning,I started doing houseworks,Saving time for learning Czech language,Very Happy!!!!!!
I Love Czech Language!!!! I Love Learning Czech Language!!!!!!Very Happy Vey Happy!!!!!!!!!!Very Very Happy Happy!!!!!!!!!!!…………Happing~,Happing~!!!!!!!!!!!!!!!!!!!!!…………………… Learning Czech Language, Very Seriously And Very Happily!!!!!!!,Very Happy Very Happy Very Happy!!!!!!!!!!………………Happing~ Happing~!!!!!!!!!!!!!!!!!!!!!……………………………………
Learning Czech Language,The Happiest The Happiest!!!!!!
Now,I started doing houseworks,Saving time for learning Czech language,Very Happy,Very Happy!!!! The Happnesses of my learning Czech language couldn't describe in any words,Because Too Happy!!!!!! Very Happy Very Happy Very Happy!!!!!!!!!!Happing~,Happing~!!!!!!!!!!!!!!!!!!!!!………………………………Happy Meowing~!!!!!!!!!!!!!!!!!!!!!………………………………………………………………(Note: As Happy As A Middle-Aged Big Good Meow,Happy Happy!!!!)………………………………………………
Bangjia Zheng I doing houseworks,Saving time for learning Czech Language,Very Happy Very Happy!!!!!!!!!!
19.11.2024 08.01
#Learning Czech Language#The Happiest The Happiest!!!!#I Love Czech Language!!!!#I Love Learning Czech Language!!!!!!#Very Happy Vey Happy!!!!!!!!!!#Very Very Happy Happy!!!!!!!!!!!…………#Very Happy#Very Happy Very Happy#Very Happy Very Happy Very Happy#Very Very Happy Happy#Very Very Very Happy Happy Happy#Sharing The Happinesses#Happy#Happy Happy#Happy Happy Happy#Bangjia Zheng#19.11.2024 08.01
5 notes
·
View notes
Text
How to Hire a Social Media Hacker Safely: A Complete Guide
In today’s tech-driven world, social media accounts are more than just a place for socializing—they are gateways to personal and business data. Whether you're locked out of your account, worried about digital privacy, or need to strengthen your security, hiring a hacker might seem like a quick fix. However, it's important to approach this cautiously. In this guide, we'll explain how to safely and legally hire a social media hacker, what to look for, and the risks involved.
1. Why Hire a Social Media Hacker?
There are a variety of reasons why you might consider hiring a hacker for your social media needs. Some of the most common include:
Account Recovery: Losing access to a social media account due to hacking or forgotten passwords can be frustrating. A professional hacker can bypass recovery protocols and get you back in.
Security Audits: Ethical hackers can identify weaknesses in your social media security, helping you prevent future cyber-attacks.
Data Retrieval: For business purposes, some companies hire hackers to retrieve important information or gain insights into competitors.
While the idea of hiring a hacker might seem risky, when done ethically and legally, it can be a helpful resource in regaining control over your online assets.
2. What is a Professional Social Media Hacker?
A professional social media hacker is an expert skilled in identifying and exploiting weaknesses in social media platforms to recover accounts, enhance security, or gather data. These hackers fall into two categories:
White-Hat Hackers: Ethical hackers who work within legal boundaries. They are typically hired for account recovery, security testing, and digital protection services.
Black-Hat Hackers: Individuals who use their skills for malicious purposes, such as unauthorized access or data theft.
It's essential to make sure you're hiring a white-hat hacker to ensure the legality of their actions. White-hat hackers use legitimate methods to help you regain access or fortify your account.
3. How to Hire a Social Media Hacker
Finding a reliable social media hacker takes more than just a quick Google search. Here’s how you can find a legitimate hacker without falling for scams:
Freelance Platforms: Websites like Upwork, Freelancer, and Fiverr host professionals offering hacking and cybersecurity services. Be sure to check reviews and ask for verifiable past work.
Cybersecurity Firms: Many reputable companies specialize in ethical hacking services. Hiring through these firms ensures that you’re working with professionals who will operate within legal boundaries.
Hacker Forums: There are many online forums where ethical hackers offer their services. However, proceed with caution, as these forums can also be a breeding ground for scams.
Once you find a hacker, ask for credentials or proof of their experience with the platform you need help with, such as Facebook, Instagram, or Twitter.
4. The Benefits of Hiring a Professional Social Media Hacker
When you hire a social media hacker, you're not just gaining access to your account; you're investing in your online security and peace of mind. Here are the key benefits:
Quick Account Recovery: Forget the long, frustrating customer support routes. A professional hacker can help you regain access faster.
Improved Security: By running security checks and vulnerability assessments, hackers can help you secure your social media accounts and prevent future breaches.
Competitive Advantage: In business, accessing legally obtained data from competitors can help improve your strategies.
Hiring a hacker can be a valuable tool for both personal and professional needs, but only when done ethically.
5. Legal Risks of Hiring a Social Media Hacker
While hiring a hacker can solve a number of problems, it’s essential to understand the risks involved:
Illegal Hacking: Hacking someone else's social media account without permission is illegal and can result in serious legal consequences. Always make sure that your actions, and the actions of the hacker you hire, are within the legal framework.
Scammers: Unfortunately, there are many untrustworthy individuals who claim to be hackers but are really out to scam people. Be careful when sharing personal information, and only work with vetted professionals.
Ethical Concerns: Even if a hacker offers to retrieve information from someone else’s account, remember that doing so without consent is unethical and illegal.
Before you hire, ensure that the hacker’s actions will be lawful and ethical to avoid any legal trouble.
6. How to Protect Yourself When Hiring a Hacker
To safely hire a social media hacker, here are some best practices to follow:
Do Your Research: Take the time to verify the hacker’s credentials. Look at their previous work, ask for references, and check for any feedback from past clients.
Use Secure Communication: Always communicate securely with the hacker to protect your personal information. Avoid sharing sensitive data over unencrypted platforms.
Create a Clear Agreement: Before any work begins, have a formal contract that outlines the services to be performed and the legal limitations. This protects both parties and ensures that the work stays within ethical boundaries.
7. Hiring a Social Media Hacker: What to Expect
When working with a professional hacker, clear communication and expectations are essential. Here’s what to expect:
Transparent Pricing: The cost of hiring a hacker can vary depending on the complexity of the task. Be wary of hackers who offer extremely low rates, as they might not be legitimate.
Clear Communication: A professional hacker should explain the process clearly and answer any questions you have along the way.
Results: Whether you’re looking for account recovery or a security audit, a professional hacker should deliver results within the agreed-upon timeframe.
Conclusion: The Right Way to Hire a Social Media Hacker
Hiring a social media hacker can be an effective way to recover lost accounts, strengthen security, or gain strategic insights. However, it’s essential to hire a reputable, ethical hacker who operates within legal boundaries. By following the steps outlined in this guide, you can safely and legally hire a professional social media hacker to help with your digital needs.
For more information:
Hire a Hacker
Hire a Social Media Hacker
Professional Social Media Hacker
This article integrates the keywords "hire a hacker," "hire a social media hacker," and "professional social media hacker" naturally throughout the content, while keeping the information helpful and engaging for readers. It also includes hyperlinks to the desired website for further exploration, ensuring SEO indexability.
2 notes
·
View notes
Text
Online Privacy and Security Tips
I am a firm believer that people should be able to be anonymous and secure online. Over a lifetime of trial and error, I've slowly learned the best ways to protect myself, and I'd like to pass on that knowledge to anyone who wants to hear it.
Last updated May 2024 (added links to news articles about PimEyes being used to identify someone in real life)
Switch to Firefox for your main browser on Windows and Android
Avoid any browser based on the Chromium project (like Microsoft Edge or Google Chrome), as Google has a major conflict of interest that prevents it from truly having users' privacy interests at heart. It makes ~70-80% of its revenue from its highly targeted advertising business, for which it must collect as much information about you as possible. That means that no matter how badly certain parts of Google want to build privacy into the browser, business interests and pressure will always supersede them, or at least force a compromise that still enables some tracking. Firefox is owned and maintained by a non-profit, so it does not have that same conflict, and it shows in the features it builds (and does not build) and the way it treats its users.
I made a list of my favorite Firefox extensions if you want to make your internet experience more pleasant and/or more secure!
Note: on iOS (i.e. iPhones), Firefox' functionality is limited by Apple restrictions and I do not recommend it - using Safari with Extensions like Adguard or 1Blocker is more secure and will give you a better experience. I made a list of my favorite iOS Safari extensions too!
Use a reputable password manager
I suggest 1Password (avoid LastPass and all of the password managers built into browsers, they're not safe). A good password manager increases your online safety by:
Helping you avoid password reuse (a common cause of account hacking)
Generating complex passwords that are difficult to guess or brute-force, and
Allowing you to keep records of all the different sites you have accounts on (so you can quickly change passwords in the event of a breach or delete your accounts on them when they outlive their usefulness)
Delete old accounts you no longer need
If your data has been deleted, no one can steal and leak it if they manage to hack the company.
Sign up for alerts from HaveIBeenPwned (HIBP) to be notified when your data is leaked in a site hacking.
This allows you to quickly change your password, hopefully before anyone is able to decrypt it (if it wasn't stored properly) or use it (if it was easy to guess). If you have reused that password on other sites, be sure to change your password on those sites either.
Note that some leaks don’t actually have any info about what website they were stolen from; if criminals just dump a huge text file onto a hacking forum that has your username and an accompanying password in it, HIBP doesn’t necessarily know what site they hacked to get that info. This is where a password manager like 1Password will come in handy, because 1P can actually use HIBP’s API to check each of your passwords and see if any of them have been leaked before. It will alert you if you need to change a specific password, even if you weren’t aware that site had been hacked.
Note: 1P only sends the first 5 characters of the password hashes to HIBP, not the passwords themselves. You can read more about the feature and how it preserves your privacy here.
Assume all profile pictures on any site are public, and avoid using your face for them if possible
New AI-powered sites like PimEyes can take an image of you, identify your face, and search for it in other, unrelated images around the internet. I searched for myself using a recent image that had never been posted to the internet before, and it immediately identified me in completely separate images I was using as my profile pictures on Facebook and LinkedIn and provided links to my accounts there. In this new AI era, assume anyone who snaps a picture of you can link you to your identity on any website where you have publicly posted your face before. This is not hyperbole; fans used PimEyes to identify a cameraman at a Taylor Swift concert using nothing more than a screenshot of a video taken of him by a concertgoer. Note: for what it's worth, you can submit an opt-out request to PimEyes if you are worried about someone using it to find your accounts online, but it requires you to submit images of your face and your government ID to the company...
Never post the same (original) image on two accounts that you do want to keep separate
Even a simple reverse image search can allow someone to link your different sites together (i.e. don't post the same vacation sunset photo on both Facebook and Tumblr because anyone can use that to link those sites together. Even if your Facebook or Instagram images are private, a follower of yours on one of those sites could still find the Tumblr you are not comfortable sharing with anyone. Marking your Tumblr as hidden only discourages search engines from indexing it; shady companies can and will ignore that and index it anyway.
16 notes
·
View notes
Text
Ao3 DDoS attack- an explanation
For anyone missing their fanfics (like me), this article gives an general outline what going's on with Ao3.
For anyone hoping that they might be able to get to their fanfics soon, I suggest not getting your hopes up. Ao3 may be up in a couple hours (hopefully) , but there's a possibility that could last for several days depending on how how severe the attack is and how many resources the attackers have, Ao3 is handling this attack, and what response plans they have in place.
Some things to know if you're not familiar with DDoS attacks... it's time to use my education.
Disclaimer: I'm not affiliated with Ao3 other than being a user. I don't know what security measures they have in place, or what their security is. This is my personal- though knowledgeable- thoughts what may be going on behind the scenes.
Also, if the idea of the DDoS attack is scaring you in anyway- take a deep breath. It's going to be OK, even if my post may come across as dark (if so, I am sorry about that). It only meant to inform and educate Tumblr users on what is going on, and what might Ao3 may be doing. Do not panic just because of this post.
So, let's get started.
a. DDoS stands for distributed Denial of Services attacks. So that means the attackers is using multiple third party devices (such as other servers, botnets*) to make so many requests (think millions per minute) to the Ao3 servers that the servers use up all their resources, preventing us legitimate users from using them.
b. A slight side note- I've heard some people say that it's because of one person that Ao3 is down. It may just be one person, but setting up a DDoS attack is easier with a team. It is likely it is a group of attackers behind this- most attacks have multiple people involved in one form or another. This isn't the most relevant point I have, but just something people should know- there may be more than one attack.
c. To stop this attack, Ao3 is going to have to block all malicious traffic from reaching the servers. However, since this is a distributed attack, they are going to have to block multiple IP addresses. This is going to take some time.
d. We also have to consider if Ao3 has a response plan in place. Response plans are, as the name suggests, what the organization does in the case of an event. For ao3, that means who are they going to contact to fix this issue. But if there isn't a response plan in place already, it going to take longer for them to stop the attack because they're fixing this on the go- a difficult thing to do.
e. Once the attack has been stopped, it won't be over for Ao3, there are two more things they need to do- complete forensics to determine any possible damage to their servers and complete an After Action Review.
e1. While it is most likely that everything will be back to normal system wise after the attack has stopped, Ao3 would be smart to conduct forensics on their system to see if there are any anomalies (malware or indications of a breach). Attackers sometimes use DDoS attacks to cover their tracks when they hack into a system. Not likely here, considering the target won't have super sensitive information that an attacker wouldn't bother with trying to get. But the possibility is always there- however small.
e2. if they want to mitigate the risk of such attacks happening again- they need to complete After Action review (AAR). In AAR, Ao3 is going to have to look at what happened, and determine what they can do to ensure this doesn't happen so easily again. Hopefully, this means writing up or editing and improving their response plan, improving their security measures, etc.
f. Most importantly, your information is unlikely to be compromised. The most damage you will receive is not being able to access Ao3's servers. Ao3 has said that you don't need to change your passwords if you have an account. That being said, if you have a weak password, definitely change it anyway. (like I'm talking is you're using weak passwords. See the following link for what weak and strong passwords are: https://security.harvard.edu/use-strong-passwords )
That's what I have to say for now. Again, this post is not associated with the team at Ao3, I am independent and have no insider knowledge, just knowledge from being a security student. Ao3 will likely say more in the future, so keep an eye for it, and hopefully we'll be able to back to our fics.
If you have any questions about this attack or general cybersecurity, my asks are open, there are comments, and I will respond to them as quickly as I can. If you are in security, and I got something here, please tell me because I do not want to spread misinformation or cause panic.
Heard from your mother (she don't recognize you), I'll be waiting for you.
*compromised computers or other devices with internet connection with malware
#ao3#cybersecurity#cyberattack#sorry this is a long post#there may be some spelling or something is written badly#i wrote this in one sitting and i barely proofread so im sorry#I will clarify if anyone is confused by anything i said#the goal is to educate anyone willing#not alarm anyone#not what i usually post but i got excited when I saw the DDoS banner on Ao3 and wrote this in an dopamine craze
15 notes
·
View notes
Text
https://mediamonarchy.com/wp-content/uploads/2024/08/20240820_MorningMonarchy.mp3 Download MP3 Social insecurity, boulder dash and shitpost prison + this day in history w/Ray Roseberry and our song of the day by Tunnelmental on your #MorningMonarchy for August 20, 2024. Notes/Links: Protests erupt, Chicago businesses board up as the DNC kicks off Day 1 festivities; Democratic lawmakers will gather in Chicago, Illinois, this week for the 2024 DNC. Vice President Kamala Harris is slated to formally accept her party’s nomination on Thursday. https://www.foxnews.com/live-news/democratic-national-convention-2024-dnc-august-19-2024 HarrisWalz.com Domain Drama Ducks Question of Cybersquatting Law https://news.bloomberglaw.com/ip-law/harriswalz-com-domain-drama-ducks-question-of-cybersquatting-law The Ledger: How Layoffs Are Showing Up in Music Companies’ Earnings Reports https://archive.is/6agGm Bad bosses are pushing Gen Zers and millennials to the brink https://ca.finance.yahoo.com/news/bad-bosses-pushing-gen-zers-184655830.html Biggest shakeup to buying and selling a home in a century starts today https://www.dailymail.co.uk/yourmoney/property-and-mortgages/article-13735925/Biggest-shakeup-buying-selling-home-century-starts-today.html The death knell for broker fees! Homeowners to see BIG drop in selling costs after Realtors agree to eliminate notorious commission scheme and pay $418 million damages in landmark legal settlement https://www.dailymail.co.uk/yourmoney/housing-market/article-13201833/realtors-settle-eliminate-commission.html ✂️ Big rate-cut fall? https://sherwood.news/snacks/newsletters/big-rate-cut-fall/ Video: “Most People Have NO IDEA How Bad This Really Is” – Whitney Webb’s 2025 Final WARNING (Audio) https://www.youtube.com/watch?v=VVrWLNN-wpE Sheena Easton – “(She’s In Love) With Her Radio” (Vinyl //Audio) https://www.discogs.com/release/1799996-Sheena-Easton-Best-Kept-Secret // https://www.youtube.com/watch?v=M1LjFr7kOoI Here’s how to find out if your Social Security number was included in last week’s massive data breach https://fortune.com/2024/08/19/social-security-number-hack-were-you-included/ Google named their GPU Adreno…and we all know what they named their browser 😐 https://en.wikipedia.org//wiki/Adreno Classic NES Game Is Making a Comeback After 40 Years https://gamerant.com/classic-nes-game-boulderdash-remake-40-years/ Video: Boulder Dash for NES Game Review (Audio) https://www.youtube.com/watch?v=s3_QfShxCNk Waterworld – “Map” (Inst. // Audio) https://www.youtube.com/watch?v=4Kf_esaJUpA Man who called for asylum hotels to burn down jailed — as it happened; Defendants sentenced as prime minister pledges no let up in efforts to prevent more disorder https://www.thetimes.com/uk/crime/article/uk-riots-live-friday-latest-news-pfjb78g0v Man who encouraged torching hotels for asylum seekers in Britain gets 3 years in prison https://apnews.com/article/british-far-right-riots-sentencing-asylum-e3248eb20ea8c2c0e719e7617bc565b9 Video: Man jailed for stirring hatred on social media (Audio) https://www.youtube.com/watch?v=zWB2W_ADasc Alexander O’Neal – “Fake” (Vinyl // Audio) https://www.discogs.com/release/427059-Alexander-ONeal-Fake // https://en.wikipedia.org/wiki/Alexander_O’Neal // https://en.wikipedia.org/wiki/Fake_(Alexander_O%27Neal_song) // https://www.youtube.com/watch?v=vN1RYACiXNs #MorningMonarchy: August 20, 2018 – Actor Jim Carrey’s Art Goes Viral: “Our Missile, Our Crime” In Yemen https://mediamonarchy.com/20180820morningmonarchy/ #PumpUpThaVolume: August 20, 2018 ♬ The Holy Gasp & Death Valley Girls https://mediamonarchy.com/20180820pumpupthavolume/ #ThisDayInHistory/#MorningMonarchy: August 20, 2021 – The suspect, Ray Roseberry, has been live streaming the bomb threat at the Library of Congress on Facebook. He is demanding to talk to Joe Biden on the phone. (Audio) https://mediamonarchy.com/20210820morningmonarchy/ // https://vxtwitter.com/mediamonarchy/status/1428423030955380738 // https://twitter.com/...
#alternative news#cyber space war#media monarchy#Morning Monarchy#mp3#podcast#Songs Of The Day#This Day In History#tunnelmental
1 note
·
View note
Text
How to Recover If Your Facebook Account Is Hacked? Easy Steps
In today's digital age, social media platforms like Facebook have become an integral part of our lives. We use them to connect with friends and family, share our thoughts and experiences, and even conduct business. However, the convenience of social media also comes with security risks, and one of the most common problems users face is having their Facebook account hacked. If you find yourself in this unfortunate situation, it's essential to act quickly to recover your account and secure your personal information.
In this comprehensive guide, we'll walk you through the steps to recover your hacked Facebook account, protect your data, and prevent future breaches.
1. Recognize the Signs of a Hacked Facebook Account
The first step in recovering your hacked Facebook account is to recognize the signs of a compromise. Common indications include:
Unauthorized login notifications: Facebook sends notifications when someone logs into your account from an unfamiliar device or location.
Unusual activity: Strange posts, messages, or friend requests that you didn't initiate.
Changed password or email address: If you can't log in because your password or email address has been changed without your consent, it's a strong indicator of hacking.
Locked out of your account: If you're unable to access your account due to suspicious activity, your account may have been compromised.
2. Immediate Actions to Take
Upon suspecting or confirming a hack, take the following immediate actions:
Change your password: If you can still access your account, change your password immediately. Make it strong by using a combination of upper and lower-case letters, numbers, and symbols.
Log out of other devices: Go to Facebook's Security Settings and log out of all devices to prevent the hacker from continuing to access your account.
Enable two-factor authentication (2FA): Set up 2FA to add an extra layer of security. This usually involves receiving a code on your mobile device that you'll need to enter when logging in.
Check your email account: Ensure that your email account associated with Facebook is secure. Change its password and enable 2FA if you haven't already.
3. Report the Hacked Account to Facebook
To report your hacked account to Facebook, follow these steps:
Go to the Facebook Help Center.
Navigate to the "Security and Login" section.
Click on "I think my account was hacked or someone is using it without my permission."
Follow the on-screen instructions to secure your account and recover it.
4. Recovering Your Hacked Account
Facebook provides a dedicated recovery process for hacked accounts. Follow these steps to recover your account:
Visit the Facebook Account Recovery page.
Enter your email address, phone number, or Facebook username associated with your account.
Follow the instructions to verify your identity. You may be asked to provide a photo ID or answer security questions.
Facebook will guide you through the account recovery process, allowing you to reset your password and secure your account.
5. Check for Unauthorized Activity
Once you regain access to your account, review your activity log for any unauthorized actions, such as posts, messages, or friend requests. Remove any malicious content and unfriend or block suspicious accounts.
6. Strengthen Your Account Security
To prevent future hacks and secure your Facebook account:
Regularly update your password: Change your password at least every six months, and use a unique combination of characters for each platform.
Enable two-factor authentication (2FA): Ensure that 2FA is enabled to provide an extra layer of protection.
Review app permissions: Periodically check which apps have access to your Facebook account and remove any unnecessary ones.
Be cautious with emails and messages: Avoid clicking on suspicious links or providing personal information in response to unsolicited messages.
Educate yourself: Stay informed about common hacking techniques and scams to protect yourself better.
6. Monitor Your Account
Continuously monitor your Facebook account for any unusual activity. Facebook offers features like login alerts, which notify you of any login attempts from unrecognized devices or locations. Stay vigilant and report any suspicious activity promptly.
7. Protect Your Personal Information
Remember that hackers target personal information. Limit the amount of personal data you share on your profile, such as your phone number, address, and birthdate. Adjust your privacy settings to control who can see your posts and personal information.
Conclusion
Recovering a hacked Facebook account can be a stressful experience, but by taking swift and informed action, you can regain control of your profile and protect your data. Follow the steps outlined in this comprehensive guide, and remember to prioritize account security by regularly updating your password, enabling two-factor authentication, and staying vigilant against potential threats. With these precautions in place, you can enjoy the benefits of social media while keeping your personal information safe from hackers.
For More Information - https://www.linkedin.com/pulse/how-recover-your-facebook-account-hacked-neha-kumari
More Articles -
2 notes
·
View notes
Text
I work in IT and have some recommendations that can help prevent scams like this!
1. Never follow a direct link unless you’re 100% sure it goes where it says it will go (for example, if you just signed up for a service and it sent you a confirmation link, that’s ok because it’s one that you are expecting. Even then, I recommend hovering over the link if you’re on desktop to make sure the url matches what it says it is). If you’re not sure, go to your browser and go to the site directly instead of clicking the link.
2. Make sure everything lines up. Are there misspellings? Does the email address make sense? When you hover over the sender, does it match what it says it should be? If it’s from a certain service, should that service have access to this email account (ex: I don’t have any social media connected to my work account, so any emails from them sent there would be suspicious)? If any of this feels off, dig a bit deeper before going ahead with it.
3. If it’s a phone call from the bank/anything else that seems urgent but requires personal info to validate, call them directly. You can even save the phone number so that if you get a call from someone who isn’t that number but claims to be, you know something might be up.
3b. If it’s a message or call from a family member or friend, but is very vague/asks for personal info/requires you to click a link, contact them directly. I keep seeing these Facebook posts that friends get tagged in which are just a link to a “video” with a caption like “is this you?” Or “I can’t believe they’re gone.” If you see anything like that, definitely let the friend/family member who posted it know so they can change their passwords. This is less common, but I’ve also seen people talking about AI voice replications being used to scam people- calling and pretending to be a family member in an emergency. I’m not sure if this is something that’s actually happening or more of an urban legend, but if you do get a call like this, obviously don’t send them any money or share any personal info unless they’re able to first provide proof that they are who they say they are. Personally, if any of my family members were in an emergency, I doubt they would be asking for money or my card info.
4. Scams and phishing are built on social psychology. It’s much easier to feed off a person’s fear/stress than it is to hack into a system externally. Are you being given an urgent call to action? Is there a threat of negative consequences if you don’t act quickly? If so, you are very likely being scammed. Once again, try to access whatever it is from an external source (call/go to the website yourself) to validate whether the issue is real. Bank calling about fraudulent charges? Check your online banking app or call the bank back. Subscription is lapsing and you should renew now to get 20% off? Go to the site and see for yourself if that’s the case. Login from an unrecognized device? Go to the page, change the password and log out from all devices.
5. If you ever get a double login screen, close out of the site, retype the url and try again. If you click a link and it takes you to a login screen (I’m sure you’ve all realized the pattern here by now) go to the site directly and login from there.
6. If you’re at all concerned that you may have fallen for a scam, that’s ok! It happens! It’s time to change your passwords, logout of the service on all devices, and (if it’s a bank or something else with sensitive info) contact the service and inform them of the potential issue.
7. Trust your gut. While you may not be consciously aware that something is off, a lot of times there are cues that we pick up on without even realizing. If it seems even remotely fishy, it’s *always* better to be safe than sorry.
How I got scammed

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/02/05/cyber-dunning-kruger/#swiss-cheese-security

I wuz robbed.
More specifically, I was tricked by a phone-phisher pretending to be from my bank, and he convinced me to hand over my credit-card number, then did $8,000+ worth of fraud with it before I figured out what happened. And then he tried to do it again, a week later!
Here's what happened. Over the Christmas holiday, I traveled to New Orleans. The day we landed, I hit a Chase ATM in the French Quarter for some cash, but the machine declined the transaction. Later in the day, we passed a little credit-union's ATM and I used that one instead (I bank with a one-branch credit union and generally there's no fee to use another CU's ATM).
A couple days later, I got a call from my credit union. It was a weekend, during the holiday, and the guy who called was obviously working for my little CU's after-hours fraud contractor. I'd dealt with these folks before – they service a ton of little credit unions, and generally the call quality isn't great and the staff will often make mistakes like mispronouncing my credit union's name.
That's what happened here – the guy was on a terrible VOIP line and I had to ask him to readjust his mic before I could even understand him. He mispronounced my bank's name and then asked if I'd attempted to spend $1,000 at an Apple Store in NYC that day. No, I said, and groaned inwardly. What a pain in the ass. Obviously, I'd had my ATM card skimmed – either at the Chase ATM (maybe that was why the transaction failed), or at the other credit union's ATM (it had been a very cheap looking system).
I told the guy to block my card and we started going through the tedious business of running through recent transactions, verifying my identity, and so on. It dragged on and on. These were my last hours in New Orleans, and I'd left my family at home and gone out to see some of the pre-Mardi Gras krewe celebrations and get a muffalata, and I could tell that I was going to run out of time before I finished talking to this guy.
"Look," I said, "you've got all my details, you've frozen the card. I gotta go home and meet my family and head to the airport. I'll call you back on the after-hours number once I'm through security, all right?"
He was frustrated, but that was his problem. I hung up, got my sandwich, went to the airport, and we checked in. It was total chaos: an Alaska Air 737 Max had just lost its door-plug in mid-air and every Max in every airline's fleet had been grounded, so the check in was crammed with people trying to rebook. We got through to the gate and I sat down to call the CU's after-hours line. The person on the other end told me that she could only handle lost and stolen cards, not fraud, and given that I'd already frozen the card, I should just drop by the branch on Monday to get a new card.
We flew home, and later the next day, I logged into my account and made a list of all the fraudulent transactions and printed them out, and on Monday morning, I drove to the bank to deal with all the paperwork. The folks at the CU were even more pissed than I was. The fraud that run up to more than $8,000, and if Visa refused to take it out of the merchants where the card had been used, my little credit union would have to eat the loss.
I agreed and commiserated. I also pointed out that their outsource, after-hours fraud center bore some blame here: I'd canceled the card on Saturday but most of the fraud had taken place on Sunday. Something had gone wrong.
One cool thing about banking at a tiny credit-union is that you end up talking to people who have actual authority, responsibility and agency. It turned out the the woman who was processing my fraud paperwork was a VP, and she decided to look into it. A few minutes later she came back and told me that the fraud center had no record of having called me on Saturday.
"That was the fraudster," she said.
Oh, shit. I frantically rewound my conversation, trying to figure out if this could possibly be true. I hadn't given him anything apart from some very anodyne info, like what city I live in (which is in my Wikipedia entry), my date of birth (ditto), and the last four digits of my card.
Wait a sec.
He hadn't asked for the last four digits. He'd asked for the last seven digits. At the time, I'd found that very frustrating, but now – "The first nine digits are the same for every card you issue, right?" I asked the VP.
I'd given him my entire card number.
Goddammit.
The thing is, I know a lot about fraud. I'm writing an entire series of novels about this kind of scam:
https://us.macmillan.com/books/9781250865878/thebezzle
And most summers, I go to Defcon, and I always go to the "social engineering" competitions where an audience listens as a hacker in a soundproof booth cold-calls merchants (with the owner's permission) and tries to con whoever answers the phone into giving up important information.
But I'd been conned.
Now look, I knew I could be conned. I'd been conned before, 13 years ago, by a Twitter worm that successfully phished out of my password via DM:
https://locusmag.com/2010/05/cory-doctorow-persistence-pays-parasites/
That scam had required a miracle of timing. It started the day before, when I'd reset my phone to factory defaults and reinstalled all my apps. That same day, I'd published two big online features that a lot of people were talking about. The next morning, we were late getting out of the house, so by the time my wife and I dropped the kid at daycare and went to the coffee shop, it had a long line. Rather than wait in line with me, my wife sat down to read a newspaper, and so I pulled out my phone and found a Twitter DM from a friend asking "is this you?" with a URL.
Assuming this was something to do with those articles I'd published the day before, I clicked the link and got prompted for my Twitter login again. This had been happening all day because I'd done that mobile reinstall the day before and all my stored passwords had been wiped. I entered it but the page timed out. By that time, the coffees were ready. We sat and chatted for a bit, then went our own ways.
I was on my way to the office when I checked my phone again. I had a whole string of DMs from other friends. Each one read "is this you?" and had a URL.
Oh, shit, I'd been phished.
If I hadn't reinstalled my mobile OS the day before. If I hadn't published a pair of big articles the day before. If we hadn't been late getting out the door. If we had been a little more late getting out the door (so that I'd have seen the multiple DMs, which would have tipped me off).
There's a name for this in security circles: "Swiss-cheese security." Imagine multiple slices of Swiss cheese all stacked up, the holes in one slice blocked by the slice below it. All the slices move around and every now and again, a hole opens up that goes all the way through the stack. Zap!
The fraudster who tricked me out of my credit card number had Swiss cheese security on his side. Yes, he spoofed my bank's caller ID, but that wouldn't have been enough to fool me if I hadn't been on vacation, having just used a pair of dodgy ATMs, in a hurry and distracted. If the 737 Max disaster hadn't happened that day and I'd had more time at the gate, I'd have called my bank back. If my bank didn't use a slightly crappy outsource/out-of-hours fraud center that I'd already had sub-par experiences with. If, if, if.
The next Friday night, at 5:30PM, the fraudster called me back, pretending to be the bank's after-hours center. He told me my card had been compromised again. But: I hadn't removed my card from my wallet since I'd had it replaced. Also, it was half an hour after the bank closed for the long weekend, a very fraud-friendly time. And when I told him I'd call him back and asked for the after-hours fraud number, he got very threatening and warned me that because I'd now been notified about the fraud that any losses the bank suffered after I hung up the phone without completing the fraud protocol would be billed to me. I hung up on him. He called me back immediately. I hung up on him again and put my phone into do-not-disturb.
The following Tuesday, I called my bank and spoke to their head of risk-management. I went through everything I'd figured out about the fraudsters, and she told me that credit unions across America were being hit by this scam, by fraudsters who somehow knew CU customers' phone numbers and names, and which CU they banked at. This was key: my phone number is a reasonably well-kept secret. You can get it by spending money with Equifax or another nonconsensual doxing giant, but you can't just google it or get it at any of the free services. The fact that the fraudsters knew where I banked, knew my name, and had my phone number had really caused me to let down my guard.
The risk management person and I talked about how the credit union could mitigate this attack: for example, by better-training the after-hours card-loss staff to be on the alert for calls from people who had been contacted about supposed card fraud. We also went through the confusing phone-menu that had funneled me to the wrong department when I called in, and worked through alternate wording for the menu system that would be clearer (this is the best part about banking with a small CU – you can talk directly to the responsible person and have a productive discussion!). I even convinced her to buy a ticket to next summer's Defcon to attend the social engineering competitions.
There's a leak somewhere in the CU systems' supply chain. Maybe it's Zelle, or the small number of corresponding banks that CUs rely on for SWIFT transaction forwarding. Maybe it's even those after-hours fraud/card-loss centers. But all across the USA, CU customers are getting calls with spoofed caller IDs from fraudsters who know their registered phone numbers and where they bank.
I've been mulling this over for most of a month now, and one thing has really been eating at me: the way that AI is going to make this kind of problem much worse.
Not because AI is going to commit fraud, though.
One of the truest things I know about AI is: "we're nowhere near a place where bots can steal your job, we're certainly at the point where your boss can be suckered into firing you and replacing you with a bot that fails at doing your job":
https://pluralistic.net/2024/01/15/passive-income-brainworms/#four-hour-work-week
I trusted this fraudster specifically because I knew that the outsource, out-of-hours contractors my bank uses have crummy headsets, don't know how to pronounce my bank's name, and have long-ass, tedious, and pointless standardized questionnaires they run through when taking fraud reports. All of this created cover for the fraudster, whose plausibility was enhanced by the rough edges in his pitch - they didn't raise red flags.
As this kind of fraud reporting and fraud contacting is increasingly outsourced to AI, bank customers will be conditioned to dealing with semi-automated systems that make stupid mistakes, force you to repeat yourself, ask you questions they should already know the answers to, and so on. In other words, AI will groom bank customers to be phishing victims.
This is a mistake the finance sector keeps making. 15 years ago, Ben Laurie excoriated the UK banks for their "Verified By Visa" system, which validated credit card transactions by taking users to a third party site and requiring them to re-enter parts of their password there:
https://web.archive.org/web/20090331094020/http://www.links.org/?p=591
This is exactly how a phishing attack works. As Laurie pointed out, this was the banks training their customers to be phished.
I came close to getting phished again today, as it happens. I got back from Berlin on Friday and my suitcase was damaged in transit. I've been dealing with the airline, which means I've really been dealing with their third-party, outsource luggage-damage service. They have a terrible website, their emails are incoherent, and they officiously demand the same information over and over again.
This morning, I got a scam email asking me for more information to complete my damaged luggage claim. It was a terrible email, from a noreply@ email address, and it was vague, officious, and dishearteningly bureaucratic. For just a moment, my finger hovered over the phishing link, and then I looked a little closer.
On any other day, it wouldn't have had a chance. Today – right after I had my luggage wrecked, while I'm still jetlagged, and after days of dealing with my airline's terrible outsource partner – it almost worked.
So much fraud is a Swiss-cheese attack, and while companies can't close all the holes, they can stop creating new ones.
Meanwhile, I'll continue to post about it whenever I get scammed. I find the inner workings of scams to be fascinating, and it's also important to remind people that everyone is vulnerable sometimes, and scammers are willing to try endless variations until an attack lands at just the right place, at just the right time, in just the right way. If you think you can't get scammed, that makes you especially vulnerable:
https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
10K notes
·
View notes
Text
The Role of Ethical Hacking in Preventing Cyberattacks
As cyberthreats change, ethical hacking has become essential to thorough security measures in many businesses. Through bug bounty programs, companies such as Google and Facebook aggressively use ethical hackers to find vulnerabilities in their systems. The proactive approach of ethical hacking promotes a security-conscious culture within businesses and helps avoid expensive data breaches. To safeguard sensitive data, ethical hackers continuously evaluate and enhance security protocols in our Ethical Hacking Course in Bangalore.

What Ethical Hacking Means
"Ethical hacking" refers to techniques that are permissible for identifying vulnerabilities in systems, networks, and applications. In the late 1990s, this discipline began to gain traction as companies realized they needed to implement proactive security measures. By employing the same methods as authorized hostile hackers, ethical hackers also referred to as "white-hat" hackers improve security.
Ethical hacking has a promising future. Ethical hackers will use increasingly sophisticated techniques to identify vulnerabilities as AI and machine learning proliferate. As cyberthreats continue to rise, it will become increasingly important for businesses to hire ethical hackers who can stop these attacks.
The benefits of ethical hacking in cybersecurity
1. Evaluating the Present Dangers
System vulnerabilities are found via ethical hacking before malevolent hackers may take use of them. The likelihood of expensive data breaches is greatly decreased by this proactive strategy. By fixing vulnerabilities with penetration testing tools like Metasploit or Burp Suite, businesses can save a significant amount of money.
2. Better Security Posture
Regular ethical hacking assessments strengthen a company's overall security posture. With the assistance of knowledgeable ethical hackers, organizations can conduct red team exercises that mimic real attacks. Organizations can increase their resistance to changing cyberthreats by routinely testing and fortifying security measures. Effective protections against such threats are maintained by this ongoing upgrade.
3. Respect for the law
Businesses can utilize ethical hacking to comply with regulations like GDPR and HIPAA. Businesses may stay out of trouble and safeguard their reputation by adhering to these rules. Compliance demonstrates a commitment to protecting confidential data and maintaining customer trust. Our Software Training Institute needs ethical hacking testing on a regular basis to find security vulnerabilities and guarantee compliance.
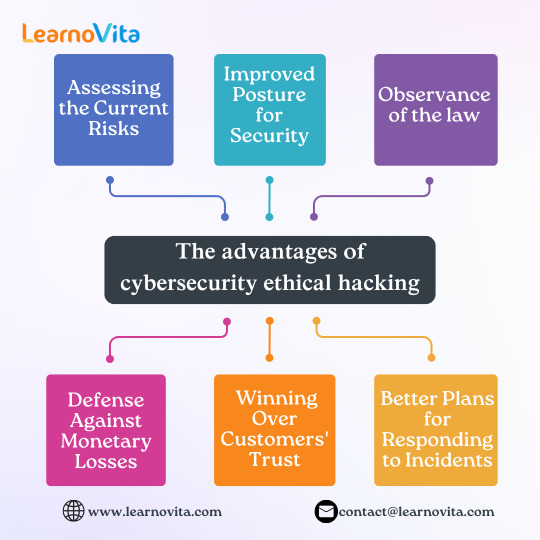
4. Protection Against Financial Losses
Data breaches can cost organizations millions of dollars in lost revenue and recovery expenses. Ethical hacking raises awareness of vulnerabilities by identifying and fixing them before attackers may exploit them. This preventive measure ultimately protects the organization's financial stability.
5. Gaining the Trust of Customers
Customer loyalty and trust are increased when ethical hacking is used to demonstrate a commitment to cybersecurity. Customers are more likely to engage with businesses who secure their data proactively. Regular security audits must be encouraged in order to reassure clients that their data is safe. Building a reputation for reliability and accountability also includes managing sensitive data.
6. Improved Incident Response Plans
Ethical hacking allows companies to assess their incident response plans by mimicking real attacks. This practice helps identify weaknesses in reaction strategy. It also assists businesses in strengthening their processes to make them more resilient to threats.
Conclusion
The role that ethical hackers play in protecting digital assets cannot be overstated. The cyber security network that strengthens an organization's cyber security policies and creates new ways to improve them depends on them. If you want to be sure that you will have a lot of possibilities after you graduate, you must earn this degree from an accredited university. There are currently several different cyber security certification programs available. However, nothing compares to a degree program for expanding your knowledge and skill set. Do the necessary research and pick a school that can provide you with thorough cyber security training. The future is bright for professionals who possess the necessary education and experience in this field.
1 note
·
View note
Text
youtube
Budget Hacks That Save You $7,000 a Year #budgethacks #savemoney #moneysavingtips #financialfreedom #debtfreejourney #smartspending #personalfinance #budgetingtips #frugalliving #moneyhabits #reversebudgeting #cutexpenses #weeklybudget #cashenvelope #emotionalspending If you want to save $4,000 to $7,000 per year without making more money, this video is your definitive guide to managing money wisely. We're revealing 10 budget hacks that have helped thousands slash spending, alleviate financial stress, and create long-term savings without sacrificing what they enjoy. From implementing the 48-hour rule to prevent impulse shopping to the 30-day no eating out diet, these budget tricks are sensible, tried and tested, and easy to follow. You'll discover how to recognize emotional spending triggers, embrace reverse budgeting, and establish weekly budgets that work. These straightforward tips aren't about restraint—they're about regaining control of your finances and letting your money do the work. If you're willing to quit saying "Where did all my money go?" and begin creating a more intentional financial future, these budget hacks will guide you there, one wise choice at a time. 𝐖𝐚𝐭𝐜𝐡 𝐟𝐮𝐥𝐥 𝐕𝐢𝐝𝐞𝐨: https://youtu.be/-os54AUO73E 𝐀𝐛𝐨𝐮𝐭 𝐂𝐡𝐚𝐧𝐧𝐞𝐥 Welcome to **Finance Facts**! 📊✨ Welcome to Finance Facts, your go-to destination for mastering the art of money management and building a secure financial future. Whether you're just beginning your financial journey or looking to refine your investment strategies, our channel delivers clear, reliable, and actionable financial knowledge. From simplifying complex topics like stocks, inflation, and crypto to offering practical budgeting and saving tips, we make finance accessible for everyone. Our content is designed to keep you informed and ahead of the curve. Expect deep-dive analyses, real-time market insights, and expert advice to help you grow and protect your wealth. With a strong focus on education and empowerment, Finance Facts is here to guide you every step of the way—towards smarter decisions and lasting financial success. Subscribe and stay tuned for weekly videos that make money matters make sense. ✅ Subscribe To The Channel For More Videos: https://www.youtube.com/@FinanceFacts-2/?sub_confirmation=1 ✅ Stay Connected With Me: 👉 Facebook: https://ift.tt/Q5BjTvW ============================== ✅ Other Videos You Might Be Interested In Watching: 👉 https://www.youtube.com/watch?v=wE92ivdvEZ0 👉 https://www.youtube.com/watch?v=BqRAy4i-DIw 👉 https://www.youtube.com/watch?v=vDoDG0CU7ns 👉 https://www.youtube.com/watch?v=LxPyUrERKjs 👉 https://www.youtube.com/watch?v=0kxAl_I3dbA 👉 https://www.youtube.com/watch?v=FmBUXIFqZYc 👉 https://www.youtube.com/watch?v=oxx81UvOW6k 👉 https://www.youtube.com/watch?v=iup7dOFDaiQ 👉 https://www.youtube.com/watch?v=7t8YK1om6FY 👉 https://www.youtube.com/watch?v=Vj7tVeqF_4c ============================= Disclaimer: The content presented in this video is for educational and informational purposes only. It does not constitute financial, investment, or legal advice. Always conduct your own research or consult with a licensed professional before making any financial decisions. COPYRIGHT DISCLAIMER: Copyright Disclaimer under section 107 of the Copyright Act of 1976, allowance is made for “fair use” for purposes such as criticism, comment, news reporting, teaching, scholarship, education and research. 𝐂𝐡𝐞𝐜𝐤 𝐎𝐮𝐭 𝐎𝐮𝐫 𝐎𝐭𝐡𝐞𝐫 𝐂𝐡𝐚𝐧𝐧𝐞𝐥! https://www.youtube.com/channel/UChZcdroxNO9q0-b4VTvRXNg/ https://www.youtube.com/channel/UCgvOxOf6TcKuCx5gZcuTyVg/ 𝐓𝐡𝐚𝐧𝐤𝐬 𝐟𝐨𝐫 𝐰𝐚𝐭𝐜𝐡𝐢𝐧𝐠: Budget Hacks That Save You $7,000 a Year 🔎 𝐑𝐞𝐥𝐚𝐭𝐞𝐝 𝐏𝐡𝐫𝐚𝐬𝐞𝐬: how to save money fast on a low income best budget hacks to save thousands save money without earning more how to stop impulse spending easy ways to cut monthly expenses smart budgeting tips for beginners simple budget plan that actually works how to automate savings effectively https://www.youtube.com/shorts/goLJYLng6ko via Finance Facts https://www.youtube.com/channel/UCt7hodOQyoeTtsXOKgCB6kQ June 13, 2025 at 05:00AM
#personalfinance#financialfreedom#investingtips#financialeducation#protectyourmoney#financesafety#financefacts#Youtube
0 notes
Text
Passwords hashing is used to secure passwords. Hashing is a common technique across various software and tools. Hashing is used as a security mechanism for preventing plain text information known to others. It's mathematically impossible to calculate a plain text for Hash since hashing is a one-way process. Still, there are different ways exist that can crack the hash and retrieve your password or other sensitive information that may have been hashed. Hashing technique is mostly applicable to protect password like information since its a one-way process. You may also want to check out - how to learn hacking and cracking. This is a simple tutorial that will explain how hash cracking works. Why Password Hashing Is Considered Secure Hashing is a one-way process. This guarantees that the hash of a plain text value can be generated however the process can not be reversed. Most software and websites use this way to store password since the user knows the password. Whenever they need to authenticate the user, they generate the hash of user input and match it with a stored password. This mechanism guarantees that even the software provider themselves do not know your password. However, there are hacking and cracking tools as well as other techniques described below that may be able to find out your password from a hash. Today we will learn about Cracking the Hashes using CPU and GPU. CPU: Central Processing Unit GPU: Graphical Processing Unit We will cover: What is a Hash? What is the need for a Hash? Why Hash over Encryption or Encoding? Hardware configuration Tools required Hash cracking [CPU] Hash cracking [GPU] Hash cracking using Search engine Why such a difference? What Is A Hash? A. A Cryptographic function that converts a data or file of arbitrary length or size to a fixed length, which is considered practically impossible to invert. see Wikipedia What Is The Need Of A Hash? A major use of Hash is in the security field. To provide security or privacy to the user who is using any service of a company. For example, You are using Gmail, Facebook, Twitter, eBay, Amazon or Online payment portals like Paypal. Where you use the service by providing your credentials(username/password) There are basically 2 reasons: Making it difficult for hackers to recover/retrieve Password, Online service(Gmail,eBay, etc) or even Wi-Fi. Checking for the file verification. see SHA1 here Even If a company’s security is breached (Hacked), then also the user’s credentials are safe(only if you use a strong password) Why Hash Over Encryption And Encoding? Imagine a scenario, which perhaps happens to almost every Big banner, take it Google, Facebook, Yahoo! etc. A website is compromised and User’s data(credentials) is compromised. What is the thing that will make you worry when you come to know that if you are a registered user on that site? Yes! your Password (might be the master password, for all your accounts). Now, It is in service provider’s hand to provide security to their consumers. Hence, Hashing is the solution. How? well, you might be familiar with these terms: Encoding/Decoding Encrypt/Decrypt and now, Hashing Not going into the details, I will tell you a basic and most important feature of Hash which makes Hash much different and important over Encoding and Decoding. and that is : Encoded text/file can be Decoded, Encrypted text/file can be Decrypted, But hashed text/file can never be De-hashed. Yes, Hash, unlike Encryption/Encoding, is a One-way process i.e when a text/file goes through the Cryptographic hash function, it is converted into a fixed character length. Example: md5 type hash has a character length of 32, where SHA1 has a character length of 40. If we hash a string, say “test123″, md5 and SHA1 hash for “test123″ will be md5(“test123″) : CC03E747A6AFBBCBF8BE7668ACFEBEE5 SHA1(“test123″) : 7288EDD0FC3FFCBE93A0CF06E3568E28521687BC Length differs from md2, md4 to SHA256, SHA512 and so on.
Hashing your Wi-Fi password is also secured using a hash function named PBKDF2(Password-Based Key Derivation Function) Hardware Configuration Hardware used in this tutorial: Laptop with 4 GB RAM Nvidia Graphic card 1 GB Tools Required Software used in this tutorial: Windows 8, 32-bit Cain & Abel (CPU based cracker). igHashGPU (GPU based cracker), download here Nvidia graphics driver, for igHashGPU, download here Hash Cracking [CPU] Cain & abel is a multi-purpose tool. It is used for various purpose like Sniffing Hash calculating Hash recovery(this tutorial) ARP spoofing WiFi hacking, using hardware called AirPcap and so on. We will take MD5(Message Digest 5) cracking as an example to keep it simple and easy to understand. Install Cain & abel, then follow the instruction along, step-by-step: Open Cain & abel Press Alt+C to open the Hash calculator Type in “test123” and hit [ENTER], here “test123″ is our test string You should see something similar, Here we got the MD5, and other Hash for string “test123″ i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5. select and copy the MD5 hash.
NOTE: Hashing is Case sensitive, Hash for “Test123” will be absolutely different. Click on Cracker tab, then select MD5 Hashes column in the left. then right click and select Add to list. Paste the copied MD5 hash and hit [ENTER] Now, Hash is added to list. Right click on hash and select Brute-Force attack Set max length to 7 and click Start, and you should see this
. Here I have set the Max length of the password to be 7 to just test the output of the tool, and cracking speed of the CPU.
See the Password/Second CPU is testing: 6.3M (approx) and the remaining time i.e total time which will take CPU to recover the original string is 3.5 hours. It is too lame to wait for 3.5 hours for a small string test123 of the length of 7 characters with no special characters. isn’t it? well, here comes the GPU cracking to put some speed in the process! Hash Cracking [GPU] igHashGPU is a password recovery tool specialized for ATI (RV) and nVidia (Cuda) based cards. It recovers password of hashes which are used over the internet(weak), example md4/md5/SHA1. Let's get started, We have the MD5 string for test123 i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 Follow the instructions along, step-by-step: Download and extract igHashGPU. Go to folder Right click and edit the file “example.cmd“. It is the example file for testing GPU speed of recovering MD5 password. Paste the MD5 code in the file after h:
and it should look like this :
ighashgpu.exe /h:CC03E747A6AFBBCBF8BE7668ACFEBEE5 /t:md5 /c:sd /min:4 /max:7 Close file. Click save and yes. Select “Example.cmd” and hit [ENTER]. A command prompt window will open like this
. See the CURSPD(Current speed), ~50 Million. Nice! but not good, isn’t it? see the battery symbol in the lower right corner. The laptop is running on battery. See what happens when I plug in the charger, notice the clock and speed. WHOA! See the difference! from 50M to 195M passwords/second, isn’t it great ? from 6.3M pass/sec to 195M pass/sec. That’s a big Jump. What you think how long it would have taken to recover the Password ? Just 5 minutes and 53 seconds. See how much time we saved by using GPU. From 3+ hrs to just 5 minutes. isn’t it amazing? also see the average speed also, 62,847 Million passwords/second. CPU: ~3 hrs with 6M pass/sec
GPU: ~6 min with 195M pass/sec You might ask, Hey! can we crack this even faster? well, the answer is Yes you can(not always though). How? Hash Cracking Using Search Engine [Google] We had MD5 string copied, right? what you need to do is very simple. Just paste and search the MD5 string i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 on Google. and you’re done! Notice the text string “test123” and the Hash. So simple to recover the string from MD5, no? Now see the time above, it took us to recover the original string. Just 0.31 seconds. not even a second. Wow! that’s great.
You might be thinking why such a difference? here’s the answer Why Such A Difference? The difference in the speed is due to the architecture of the 3. CPU: Uses 4 cores(Shared with system processes) at maximum, 8-cores in some cases. GPU: Used 96 cores (In this case). All the 96 cores(Parallel processing units) were 100% dedicated for the password recovery process unlike CPU, which was simultaneously handling the complete OS including background processes, GUI(mapping of pixels on screen), and many other processes. Even if the CPU stop handling those, then also it won’t match GPU’s performance. difference because of the #of cores i.e 96 vs. 4 or 8 Latest GPU’s that I have seen comes with more than 400 cores. It can take you more than a billion passwords/second to recover the MD5 hashed string. Google Don’t Crack The Hash. Yes!, Google doesn’t crack/recover the string. It sends a request for the specific Text input i.e the hash in our case, to all the servers, takes the response back and displays the result according to the page rank of the site. There are plenty of online crackers, which can be used to crack a variety of hashes. They search their Database for the hash you have entered. If the string of hash is already recovered by them, they will give it to you, else you have to pay to avail the service. An email is sent if the string has been recovered. So, what Google does is sending a request to all these servers and displaying you the result. Result of the hash already cracked. It certainly becomes the Top priority for hash cracking. Search google first, if you didn’t find the password, go for GPU cracking.
Still didn’t succeed? Try CloudCraker, crackStation, HashKiller You can google “Online hash cracker” for more results. Note: Cracking speed varies depending on factors like: GPU configuration, ATI graphics cards are the best for this task. Hash type, for SHA1 it will be even lesser and for WPA hash cracking it goes down to 4000 Pass/sec on my graphics card. see this list. My card’s performance is near to GeForce 8800 GTS (CUDA) Interested in WPA cracking, or WiFi pentesting? Follow my WiFi Security and Pentesting Series Hope you found this tutorial helpful. Let me know in the comment section. Thanks! This article is contributed by Hardeep Singh (Facebook | Twitter). Hardeep is a guest author and Full-time Blogger @ rootsh3ll.com, Security person, Penetration, tester, Linux and python Lover. Loves to share knowledge with everyone. Updated On June 2019: Fixed Broken links and updated minor typos.
0 notes
Text
Cyber Law Experts in Delhi – Protecting You Against Digital Fraud & Cyber Attacks
By admin / May 12, 2025
🔐 Cyber Crime Law Firm in Delhi – Defending Digital Rights with Legal Expertise

In today’s hyper-connected world, cybercrime is one of the most pressing threats affecting individuals, startups, and corporations alike. From online financial fraud to cyberbullying and hacking, digital crimes are on the rise — and you need expert legal protection. At Patent24x7, we stand as a leading cyber crime law firm in Delhi, providing specialized legal solutions to fight and prevent cyber offenses.

⚖️ What Does a Cyber Crime Law Firm in Delhi Do?
As technology evolves, so does the complexity of cybercrimes. Legal support from cyber law experts is crucial to:
File police complaints against online fraud
Initiate legal action in cases of cyber defamation, stalking, phishing, and data breaches
Defend against wrongful cybercrime allegations
Ensure corporate compliance with data protection and IT laws
🔍 Services Offered by Patent24x7 – Cyber Law Experts in Delhi
✅ Online Fraud Recovery
We help individuals and businesses reclaim lost money from UPI frauds, scam websites, fake trading apps, cryptocurrency fraud, and more.
✅ Cyber Complaint Filing
Get professional support to file a complaint at the Delhi Cyber Crime Cell or the National Cyber Crime Reporting Portal.
✅ Social Media & Email Harassment
Legal action for cases involving stalking, threats, morphed images, and impersonation on social platforms.
✅ Data Breach & Hacking
We assist tech firms and startups with legal redress and compliance in case of data theft or system breaches.
✅ Legal Defense in IT Offenses
Wrongfully accused? Our cybercrime lawyers in Delhi help you present a strong legal defense.
✅ Cybersecurity Legal Consulting
Advisory for startups, fintech companies, and IT firms on IT Act, data protection, and cyber compliance policies.
👨⚖️ Why Choose Patent24x7 as Your Cyber Crime Law Firm in Delhi?
🏛️ Expert Team of Cyber Lawyers
🌐 Tech-Savvy Legal Approach
📞 24×7 Legal Support
⚙️ Specialized in Online Fraud & Data Crimes
🔐 Client Confidentiality & Transparent Fees
Whether you’re filing a complaint or need urgent legal help, our experienced lawyers understand the legal, technical, and investigative side of cyber law.
📍 Why Delhi Residents Trust Patent24x7
Delhi is not just India’s capital—it’s a cybercrime hotspot. That’s why Patent24x7 has developed specific legal frameworks and rapid-response methods tailored to the Delhi region’s needs.
Whether it’s recovering funds or responding to a data breach, they know the landscape and the local procedures better than most.
❓ Frequently Asked Questions (FAQs)
Q1: How do I report a cybercrime in Delhi?
A: You can file a complaint at the Cyber Cell, Delhi Police, or report it via the National Cyber Crime Portal. Our team can guide you through every legal step.
Q2: Can I recover money from online fraud?
A: Yes, if action is taken quickly, we can help you trace and recover your funds legally via cyber police and banking channels.
Q3: Is online defamation punishable by law?
A: Yes. Posting defamatory content online can be penalized under the IT Act and IPC Sections like 499 and 500.
Q4: Do you provide corporate cybersecurity legal consulting?
A: Absolutely. We offer customized compliance policies, NDAs, and legal audits to protect your business from cyber threats.
📞 Contact the Best Cyber Crime Law Firm in Delhi – Patent24x7
🌐 Website / Contact Us – https://www.patent24x7.com/about-us/ 📺 YouTube – https://www.youtube.com/@Patent24x7 📘 Facebook – https://www.facebook.com/people/Patent24x7/61574451401299/ 📌 Pinterest – https://www.pinterest.com/patent24x7 📰 Blog – https://patent24x7online.blogspot.com/
📜 Disclaimer:
As per the rules of the Bar Council of India, this blog is for educational purposes only. It does not constitute solicitation or advertisement of legal services. Always consult a qualified lawyer for personalized legal advice.
#cybercrime#cyber law#digitalsafety#legal help#online fraud#patent24/7#hackingrecovery#cyber crime lawyer
1 note
·
View note
Text
The Erosion of Journalistic Integrity: From Truth-Seeking to Agenda-Pushing
Journalism was once regarded as the Fourth Estate—a vital pillar of democracy tasked with holding power to account, uncovering truth, and informing the public without fear or favor. The founding principles of journalism were rooted in objectivity, fairness, and an unwavering commitment to the public good. Yet today, what passes for "news" has devolved into a grotesque parody of its original purpose.
Modern journalism is dominated by partisan hacks, corporate interests, and political operatives masquerading as reporters. The media no longer serves the people; it serves power. Whether through deliberate omission, selective outrage, or outright propaganda, the press has betrayed its sacred duty. This is not an accident—it is the result of systemic corruption, ideological capture, and the abandonment of journalistic integrity.
This article examines the original purpose of journalism, the rise of political bias, and how the media has become little more than a weaponized arm of the political establishment.
I. The Original Purpose of Journalism
1. The Fourth Estate: A Check on Power
The concept of the press as a watchdog dates back to the Enlightenment. Philosophers like John Locke and Thomas Paine argued that an informed citizenry was essential to preventing tyranny. In the early American republic, newspapers—though often partisan—played a crucial role in exposing corruption and fostering debate.
The ideal of journalistic integrity emerged in the late 19th and early 20th centuries with the rise of "objective journalism." Pioneers like Walter Lippmann argued that reporters should adhere to facts, verify information, and remain independent of political factions. The Society of Professional Journalists’ Code of Ethics enshrined principles such as:
Seek truth and report it
Minimize harm
Act independently
Be accountable and transparent
For much of the 20th century, journalists like Edward R. Murrow, Woodward & Bernstein, and Ida B. Wells embodied this tradition—exposing lies, confronting injustice, and speaking truth to power.
2. Journalism as a Public Service, Not a Political Weapon
The press was never meant to be a mouthpiece for the state or a political party. Its role was to challenge authority, not amplify its narratives. Investigative journalism thrived when reporters were willing to defy government spin, corporate influence, and popular opinion in pursuit of truth.
But over time, this mission was corrupted.
II. The Corruption of Modern Journalism
1. The Rise of Political Bias and Partisan Journalism
The shift from objective reporting to activist journalism did not happen overnight. Key factors include:
A. The 24-Hour News Cycle and Sensationalism
With the advent of cable news (CNN, Fox, MSNBC) and later digital media, the demand for constant content turned news into entertainment. Ratings-driven journalism prioritized outrage over facts, leading to hyper-partisan coverage designed to provoke rather than inform.
B. The Merging of Media and Political Elites
Many journalists now come from the same elite institutions as politicians, creating an incestuous relationship between the press and power. The revolving door between media, government, and corporate PR (e.g., CNN’s Donna Brazile leaking debate questions to Hillary Clinton, former MSNBC host Phil Griffin coordinating with the Obama White House) has destroyed trust.
C. The Weaponization of "Fake News"
Instead of self-correcting errors, major outlets now double down on false narratives when they align with their political biases:
The Russia Collusion Hoax (2016-2019) – Years of baseless claims pushed by mainstream media, later debunked by the Mueller Report.
Hunter Biden’s Laptop Suppression (2020) – Twitter, Facebook, and outlets like The New York Times censored the story, falsely labeling it "Russian disinformation."
COVID-19 Propaganda – Outlets like The Washington Post smeared lab-leak theory proponents as "conspiracy theorists," only to later admit it was plausible.
2. The Death of Investigative Journalism
True investigative reporting—exposing both political parties—has been replaced by partisan hit jobs. Consider:
The Lack of Scrutiny on Democratic Scandals: The media ignored the Biden family’s foreign business dealings for years.
The Protection of Republican Elites: Fox News downplayed Trump’s controversies while amplifying culture-war distractions.
The Silence on Bipartisan Corruption: Corporate media rarely challenges the military-industrial complex, Big Pharma, or Wall Street’s influence on both parties.
3. The Role of Big Tech in Censorship
Social media platforms, working in tandem with legacy media, now decide what the public is allowed to know. Examples:
Shadow-banning dissenting voices
Algorithmically boosting establishment narratives
Collaborating with government to suppress "misinformation" (i.e., viewpoints they dislike)
This is not journalism—it is information control.
III. The Consequences of a Broken Media
1. Public Distrust at Record Highs
Gallup polls show only 32% of Americans trust the media—a historic low. This distrust is well-earned:
When the press lies by omission (ignoring scandals that hurt their preferred party)
When they manufacture outrage (breathlessly covering some controversies while downplaying others)
When they stifle dissent (labeling alternative viewpoints as "dangerous")
2. The Erosion of Democracy
A democracy cannot function without an informed electorate. When the media manipulates rather than informs, citizens make decisions based on propaganda, not truth.
3. The Normalization of Double Standards
If a Republican does it, it’s a scandal; if a Democrat does it, it’s a "nothingburger."
If an outsider challenges the system, they’re "dangerous"; if an insider commits corruption, it’s "just politics."
This hypocrisy has turned journalism into partisan activism.
IV. Can Journalism Be Saved?
1. Returning to First Principles
The only way to restore trust is to:
Reject partisan loyalty – Hold all power accountable, regardless of party.
Embrace intellectual humility – Admit mistakes and correct them.
Focus on facts over narratives – Stop filtering news through ideological lenses.
2. Supporting Independent Journalism
Alternative media (independent journalists, substacks, decentralized platforms) are filling the void left by corporate press. Citizens must seek out diverse sources and reject spoon-fed narratives.
3. Demanding Accountability
Boycott dishonest outlets
Call out bias when seen
Reward integrity over sensationalism
Conclusion: Reclaiming the Soul of Journalism
The press was never meant to be the propaganda arm of the political elite. Its purpose was truth—no matter how inconvenient.
Today’s media has failed. But the solution lies not in despair, but in demanding better. The public must reject manipulative narratives, support real investigative journalism, and remember: A free press should afflict the comfortable, not comfort the powerful.
Until then, what we have is not journalism—it is state-sanctioned storytelling, designed to keep the people in the dark. And in darkness, democracy dies.
0 notes