#grey hat hacker
Explore tagged Tumblr posts
Text
In today’s modern technology, we are using the internet extensively to meet our online needs. We indulge our sensitive data in our regular online resources such as banking information, mobile number, e-mail, and Aadhaar details to have a hassle-free browsing experience.
#hacking#ethicalhacking#ethicalhackers#type of hacking#internet security#grey hat hacker#white hat hacker#black hat hacker#cyber security#cyberattack#cybercrime#infosectrain#learntorise
0 notes
Text
Cracking Isn't What You Think It Is
Consider following on social media! WordPress Twitter Facebook Quick note: if you’re viewing this via email, come to the site for better viewing. Enjoy! Eric: Z-Daddy put up another script.Sean: I know, I’m reading it… and stop calling him that. That’s weird bro.Photo by Pixabay, please support by following @pexel.com Here’s a question for you. Can you recall what you were doing back in…
#black hat#blue hat#cloud security#cracker#cyber attack#cyber security#green hat#grey hat#hacker#red hat#white hat
0 notes
Text
style guide: ARIES EDITION



ARIES RISING
rihanna - jupiter in 1st house, james dean - uranus & chiron & north node in 1st house, kendall jenner, miuccia prada - sun & north node in 1st house, barbra streisand - sun & mercury in 1st house, penélope cruz - sun & mercury in 1st house, cardi b - moon in 1st house, sophie turner - moon & venus & part of fortune in 1st house, amber rose - moon & juno in 1st house, nikki reed, shakira - chiron in 1st house, stevie nicks - north node in 1st house, vinnie hacker - ceres in 1st house,
style aesthetic: bold & dramatic, leather chic, modern minimalism, rockstar vibes, athleisure luxe, metallic accents, animal prints, vintage with a twist, unexpected mixes, sunglasses as statement pieces, red, orange, and black



ARIES VENUS
marilyn monroe - venus in 9th house, audrey hepburn - venus in 1st house, elizabeth taylor - venus in 4th house, mariah carey - venus in 12th house, lady gaga - venus in 11th house, gigi hadid - venus in 12th house, rihanna - venus in 12th house, jennifer aniston - venus in 6th house, shakira - venus in 12th house, cristiano ronaldo - venus in 3rd house, gigi hadid - venus in 12th house, keira knightley - (unknown), cate blanchett - venus in 11th house, melanie martinez - venus in 5th house, tyler, the creator - venus in 9th house, sarah jessica parker - venus in 11th house, eva longoria - venus in 5th house, janet jackson - venus in 5th house, millie bobby brown - venus in 8th house, suga - (unknown), sarah michelle gellar - (unknown), madison beer - venus in 11th house, helena bonham carter - (unknown), gal gadot - (unknown), emma chamberlain - venus in 3rd house,
style aesthetic: confident & playful, bold & romantic, leather with lace, athletic luxe, fiercely feminine, metallic accents, graphic prints, tailored pantsuits, bold blazers, vintage with a modern twist, bold jewelry, statement sunglasses, and eye-catching hats, gold, silver, red, orange, and hot pink!



ARIES MIDHEAVEN
tyra banks - moon & mars & chiron in 10th house, kayne west - venus & mars & chiron & part of fortune in 10th house, angelina jolie - jupiter & chiron & ceres in 10th house, céline dion - moon & mars & saturn & north node in 10th house, cameron diaz - chiron in 10th house, julia roberts - north node & lilith in 10th house, sharon tate, meghan markle, the weeknd - pallas & part of fortune in 10th house, jessica lange - sun & mercury & venus & mars & north node & part of fortune in 10th house, jennette mccurdy - moon & mars & juno in 10th house, danielle fishel - sun & mercury & venus & mars & chiron in 10th house, kate moss - mars & chiron in 10th house, cindy crawford,
style aesthetic: tailored suits, sharp blazers, crisp shirts, bold statement necklace, a brightly colored pocket square, a unique pair of shoes, bold eyewear, orange, black, white, grey, red power suit, a red statement scarf, and red accents



VENUS IN 1ST HOUSE
selena gomez - venus in leo, elizabeth II - venus in pisces, kourtney kardashian - venus in pisces, beyoncé - venus in libra, katy perry - venus in sagittarius, zayn malik - venus in pisces, angelina jolie - venus in cancer, cameron diaz - venus in cancer, nabilla benattia - venus in capricorn, audrey hepburn - venus in aries, blake lively - venus in virgo, anna nicole smith - venus in libra, avril lavigne - venus in scorpio, jude law - venus in sagittarius , rachel mcadams - venus in scoprio, halsey - venus in scoprio, doja cat - venus in scorpio, priyanka chopra - venus in gemini, olivia rodrigo - venus in capricorn, nina dobrev - venus in sagittarius, madison bailey - venus in pisces, damiano david - venus in aquarius, maggie lindemann - venus in cancer, elle fanning - venus in pisces, olivia holt - venus in virgo, mina - venus in aries, sophie turner - venus in aries, isaac mizrah - venus in virgo,
style aesthetic: flowy fabrics, pastel colors, silk fabrics statement jewelry, natural textures, well-fitting clothes, minimal makeup, unique color combinations, unexpected layering, vintage pieces, bold statement piece, a head-to-toe monochromatic look, eye-catching earrings, handcrafted pieces, unique materials, a touch of lace, soft pinks, baby blues, lavenders



NEPTUNE IN 1ST HOUSE
kim kardashian - neptune in sagittarius, paris hilton - neptune in sagittarius, kylie jenner - neptune in capricorn, ariana grande - neptune in capricorn (conj. asc), scarlett johansson - neptune in capricorn, eminem - neptune in sagittarius (conj. asc), nicole kidman - neptune in scorpio, marilyn monroe - neptune in leo (opp. moon), damiano david - neptune in aquarius (conj. venus & tri. moon), björk - neptune in scorpio (conj. asc), nelly furtado - neptune in sagittarius (conj. asc), perrie edwards - neptune in capricorn (conj. asc), dave franco - neptune in capricorn (conj. asc), river phoenix - neptune in scorpio (opp. moon), lil peep - neptune in capricorn (opp. moon), lorde - neptun in capricorn (tri. moon), sofia richie - neptune in capricorn (tri. moon),
makeup style: dreamy & ethereal, soft washes of color, shimmery textures, makeup uses cool tones, metallics, glitter, glowing skin, lightweight foundations, highlighter for a natural glow, graphic eyeliner designs, whimsical lashes, soft & natural lips, smoky eyes with a twist, smoky purples, teals, touch of silver, lavender, muted purples, blues, greens soft pinks, peaches
@pearlprincess02
#aries rising#aries venus#aries midheaven#venus in 1st house#neptune in the 1st house#aries#style#street style#fashion#astrology#astro notes#astro community#astro observations#astrology observations#astro placements#astro tumblr#astroblr#astrology notes#aesthetic#style inspo#style aesthetic
686 notes
·
View notes
Text
So many of our welfare and social security programs are digitally managed, like at some point couldn’t we just redistribute wealth through exploiting the tech and the ebt disposable cards and just force the system to spend the money even if its funding is pulled?
Like I know they would fight tooth and nail to recover that money, but the point here is that we don’t necessarily need physical violence for revolution in a digitally run world. We just need enough anonymous black or grey hat hackers who are willing to attack for long enough to crash the system.
#cybersecurity#us politics#politics#cyberattack#social security#social services#donald trump#anti capitalism
20 notes
·
View notes
Text
Thinking about the Solitaries recently.
There is not much lore, it saddens me.
I think from his interaction with Vala and #7 in his Tales, it's a case of the Solitaries becoming part of The Heroic Order after Valen's capture.
When he tries to be smooth with Vala, during that interaction she says "The Heroic Order are the swords and shields of the nobility. How can one be unaware of those who serve them?" Meaning the Solitaries as a group server under The Heroic Order and not just Valen.

But from #7 in his Tales, one of the Solitaries is questioning how Hogan managed to catch Valen (referring to Valen as "the captain"), implying they were their own thing before this point.
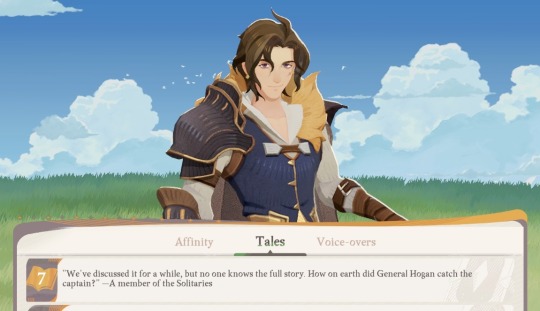
While it's currently unknown (as far as I'm aware) how long it's been since they began working under The Heroic Order, it can be assumed it's a while considering how Vala makes no mention of the Solitaries as anything except a branch of The Heroic Order
[This next part is from a conversation I had with my friend masondjar]
It would also explain why Valen does undercover work, I think before his capture the Solitaries were a lot more morally grey, definitely not legal by any means.
I don't think they captured him to make him join The Heroic Order, but he hit Hogan with that pathetic white boy stare and poor Hogan was like "oh he's baby... my child... my son now..." and they ended up striking some sort of deal.
In the words of mister d.jar because they put it in baby terms for me after my brain died and I like their funny words:
"i was just like. wondering if they were tasked to do other things before being ushered into the heroic order? i dont think they were doing everything the heroic order wanted them to do. it feels similar to anonymous and how people become white hat hackers. anonymous is a group of people who tend to "troll" big companies and people. leaking, doxxing, internet sleuth kinds of things but morally grey - not really good but not really bad. white hat hackers are people the government takes in to deal with, break down and study potentially harmful viruses, trojans etc. they typically come from a background of prior hacking and creating malicious malware. so with him being "captured" i dont think they captured him in order to ask him to join the heroic order - least not outright. he may have been a lot more morally grey at that point and had done some things the heroic order wanted him to "atone" for yknow - justice to its fullest sorta thing"
Uh so yeah thanks for attending my yap session about Mister Valen AFK Journey :]
76 notes
·
View notes
Text
the evangeline chronicles

Somewhere hidden in one of my stories is my original character, Evangeline. A grey hat hacker that navigates the murky waters of the dark web, and when needed, a vigilante that does what she can to make the world a safer place, one scumbag at a time. In this "limited series", you'll get to catch a glimpse into her adventures and piece together exactly who she is and which story she's from.
episode one: the going rate for privacy
An actress with a sadistic & abusive ex reaches out to Evangeline to hopefully thwart his efforts in destroying her reputation by means of leaking a depraved sex tape.
episode two: loopholes & mercies
Evangeline receives a tip of a suspicious character hanging around public parks with a phone pointed at the playground
episode three: indefinite goodbyes
Evangeline takes her last assignments for a while, bidding Grey a "see you later"
episode four: every part of myself
Evangeline returns after nearly a decade of silence
bonus episode: ???
bonus episode: ???
9 notes
·
View notes
Note
Heyy bestie 👀 idk if this is weird cos we're mutuals and all but i heard you do requests and i am parched for more legion Wrench 😩 How comfortable are you writing him with a younger reader? (Mid/late 20s) Perhaps he meets Jacksons hacker friend or smthn. I can offer art in return, anything you want 🙏
⊱Late night talks⊰ Legion Wrench x Reader
"The amount of stupid you have in you, is impressive...i like it"
TAGS: Big vibes, Jackson and sushi, implied romance, cuddles and chaos talk ;)
description: Jackson needed Wrench´s help with getting a heavy box to his new apartment. There he got introduced to a grey hat stranger, turns out he had alot of common with and vibed with.
-Requested by my lovely moot @bardsins! (check them out, amazing art <3-

"Fair warning Reggie. I have a roommate now and they are...particularly interesting." Jackson warned the masked man as they were walking up the stairs to his apartment. Wrench´s mask changed to question marks as he tilted his head to the side towards Aidens son. "What do you mean...are they dangerous? no...ARE THEY IN THE MAFIA?!" The blond haired responded with caution in his voice as he got louder. He gripped the box he held harder as he watched his friend stop for a second to process before proceeding movement.
"SHHHH what? no?..they do the same stuff we do..just solo. They are a grey hat with a tendency to cause chaos...like someone i conveniently know."Jackson shushed Wrench as he rolled his eyes, he went up a couple of stairs before making a turn into a corridor with doors on each side. "Just don't bomb them with Questions immediately. Pretend i never told you and lets get this over with." he begged Wrench as he took out his keys from his pockets and turning towards Wrench with a beg in his eyes before stopping at a door.
"I can try. but no promises though"Wrench responded casually with a shrug and stopped walking near Jackson as the black haired man infront of him proceeded to open the door.
As the door opened, faint music was heard playing from one of the rooms in the corridor as they both stepped in, Jackson letting the door close behind him as he called out for his roommate "YINNNN, IM HOME AND BROUGHT A FRIENDDD". A moment later, the music stopped and a voice responded with a quick "LIVINGROOM" before the music continued shortly after. Wrench looked towards his friend with question marks plastered on his mask and the opposite just shrugged before heading towards the Livingroom with a response. "Wrench, dont worry about it. Put the box down and follow me"
Taking a second to think, Wrench slowly put down the box at a near table at the door before following his friend to the next room. "ayy Jackson! I got you the sushi from the starfell Party from today. Its in the kitchen." The stranger to Wrench greeted Jackson casually as he walked into the room, standing behind Jackson and analysing the person. H/L H/C hair, a black zip hoodie along with a grey shirt that said "mess with hacko get DDOSo" which he found amusing. The person was sat on the couch casually, laying on it while having their legs over the end of the couch as a bag of chips was layed against them. "Dope! Y/N, meet my friend Wrench. Don't mind the mask" The black haired male introduced the two before heading towards the kitchen in a hurry to get his sushi.
A silence fell among them while Y/N looked at Wrench up and down. "so-" they both attempted to start a conversation before a soft chuckle admitted between them. "nice, soo...you are the Wrench? former dedsec member and now full time merc?" Y/N asked with a smirk on their face as they adjusted their position on the couch they were planted at. They were now sat on the couch instead of laying on it, patting their side as an invite for Wrench to take a seat. Wrenchs mask displayed question signs before returning to his usual Xs as he slowly walked over to the couch before proceeding to sit on it.
He made sure there was a safe sentence between them before casually responding "yeah...your Y/N right? probably not your hacker tag. What is it? only fair to share" his mask displaced his usual happy led´s before switching back. His opposite chuckled before laying their head on the back of the couch. "you caught me red handed, sweets. its H/N (hackername)." Before another word left Y/Ns mouth, Wrench gasped dramatically, placing his hands infront of his mask as his mask turned to Os before displaying his excitement. "no fucking way! Grey hat hacker and activist H/N???? I heard of your work! Nice to finally put a face to the name."
They both had a nice discussion over their careers as Jackson returned to them only to excuse himself. "Sorry, love birds. I gotta dip now. Aiden needs my help with stuff. "The protest from the two weren't heard due to him leaving so quickly with a small bye. He left the room and soon the front door was heard opening and closing, indicating that he left them fully to themselves. Y/N sighed, shaking their head with a small smile "classic Jacks, always jumping for his dad. always nice to see in this fucked up world.".
After a joke or two they returned to talking about the world and their interests, noticing the small similarities, they got stuck on the topic of who would win...two robot dogs or 10..lions? They couldnt fully agree on it and laughed about it.
"The amount of stupid you have in you, is impressive...i like it" Y/N laughed out between laughter, leaning against Wrench´s arm as support. The male tensed up for a second before easing into it with a soft smile plastered under his face. "yeah...I like your personality too. its feisty and you obviously know how to pack a punch." He responded as he laid his head against theirs.
"wanna get drunk and play mortal combat?"
"Are you asking me out? if so..FUCK YEAH"
They proceeded to get drunk and go against each other in mortal combat, leaning against each other semi cuddling before it turning into a passionate make out session. Sadly however due to the Writers incapability to post smut on tumblr (if yall want, i got ao3 now ;) ), before proceeding into deeper grounds, they passed out in each others arms.
After waking up awkwardly in the morning, it didnt stop them hanging out more often after and soon becoming the chaos couple of London.

-Hope yall enjoyed this lovely piece of art for my lovely moot. I was big time inspired. Reminder my request are open and i would love to take them! :D-
-if you check out my mutual! you get a cookie ;P-
-not keen on constructive critism as I do this as a way to enjoy myself and share it, so PLEASE NO COMMENT ON MY WRITING STYLE UNLESS ITS A GRAMMER ERROR. THAMK YOUU-
10 notes
·
View notes
Text
Today is canadian Thanksgiving, so I decided to make a more ambitious piece to celebrate.

Enrus is spending the night having a meal with his friends. Enrus has been practicing his cooking since he started to put on weight and is pretty decent nowadays. The ingredients may have come from a replicator, but the meal is still hand cooked.
Left to right:
Renzaul (Ren): a bear with an extensive history in robotics. Like Enrus, he used to work for the mega corporation Tayre Corp. They met when Enrus had to request parta for cybernetics from his workshop, leading to an accident that cost him an arm and the two scrambling to assemble a mechanical one out of spare parts before he bled out. He's a real serious, and grumpy looking guy but a big, strong teddy bear under it all. He is a loving single father to two kids and a pet dog.
Bantozeen (Bant): An ex member of the Tayre Security devision. He secretly betrayed the company sometime before meeting Enrus after his closest friends and family were black bagged. He worked undercover for the resistance and supplied them with weapons. He's a a sweet person who is always genuine l, but also a walking stream of consciousness monologuing that won't ever shut up. That may have actually helped his cover as no one would listen to a word he said and couldn't get a word in edgewise when he was around. I had no idea how to pose him here so he's bragging about going seven rounds with an MMA fighter.
Enrus: You know and love this big fat fox already. But a bit of background, his mother was actually a high-ranking official within the company. Putting immense pressure on his every action. His entire future was effectively charted for him, and it left him completely hollow inside, coasting through life unaware of his surroundings until the day he caused the accident that cost Ren his arm. This led to a lifelong friendship and enrus finally seeing the civil unrest in the country. He made contact with the resistance through a private server in one of his favorite games and worked to topple the company from the inside. This got him in contact with Bant, and through investigating the shadier dealings of the company, they found and rescued Marzelle.
During the final raid he was shot in the head and spent over 6 minths resting in an intensive trauma unit (thank god for sci fi medical tech). The blue patches are actually a side effect of a different treatment for chemical burns, the chemicals melted him down nearly to the bone and entire muscle and skin tissue had to be donated from a matching donor who happened to be a bright blue wolf. He has an artificially grown eye replacing his original right eye as well.
Marzell (Mars): Youve already seen her before, she's a Grey hat hacker, formerly black hat, that got kidnapped by Tayre corp and tortured. Enrus and Bant found her cell while investigating the company and helped her escape. She spends her time helping getting the networks integral to the city's infrastructure running again to return some degree of normalcy to the people again.
She has a girlfriend that she loves very much (she the only member to find love in the years after their victory so far). She goes to therapy to help deal with the trauma of her brief time being held captive as well.
I love my little underground freedom fighters.
6 notes
·
View notes
Text
Where is my low empathy stoic grey-hat hacker girlfriend who wears stinky leather jackets and has 20 piercings
8 notes
·
View notes
Text
The 3 most known types of hackers...

White Hat - The good guy 😇
They follow the rules when it comes to hacking into systems without permissions and obeying responsible disclosure laws. ✅
-
Black Hat - The cybercriminal 🏴☠️
They don't lose sleep over whether or not something is illegal or wrong [...] They generally exploit security flaws for personal or political gain or for fun. 🏴☠️
-
Grey Hat - The 🎭 guy
May have good intentions, but might not disclose flaws for immediate fixes, they prioritize their own perception of right versus wrongover what the law might say. 🎭
#life#hacking#cyber security#data security#online privacy#internet privacy#security#technology#internet#search#internet history#privacy#the internet
6 notes
·
View notes
Text


hackpartygordoic + prograpartygordoic
[IMAGE ID: two horizontal flags with nine stripes; each flag has the party gordo in the center. the party gordo is a very large hot pink slime, wearing cool green, star-shaped sunglasses, and a yellow party hat with blue polkadots on it. it is smiling and has a dull green and bright yellow radiating background. the middle stripe is twice as large as the rest of them, which are equally sized. the first flag has these top three colors: black, dark grey, and bright green. the second flag has these top three colors: dark blue, medium blue, and bright mint green. each flag has these bottom six stripes: warm pink, off-white, warm pink, light yellow, mint green, and cool blue. END ID.]
hackpartygordoic: a teknine gender connected to being a party gordo hacker; this gender is connected to party gordos, party gordo aesthetics, hacker/hacking aesthetics, technology aesthetics, and teknithood/exenhood!
prograpartygordoic: a teknine gender connected to being a party gordo programmer; this gender is connected to party gordos, party gordo aesthetics, programming aesthetics, technology aesthetics, and nonbinary teknithood/exenhood!
@radiomogai @liom-archive @epikulupu @electrosaccharine
#hackpartygordoic#prograpartygordoic#hacker system#programmer system#party gordo#tekneo#teknin#mogai gender#mogai coining#gender coining#tech.png
9 notes
·
View notes
Text
What to do when you spot a broken website
I am a very firm believer in either sticking to your principles or update them.
So when I got this error while I tried to search for C/C++ on my national job portal:
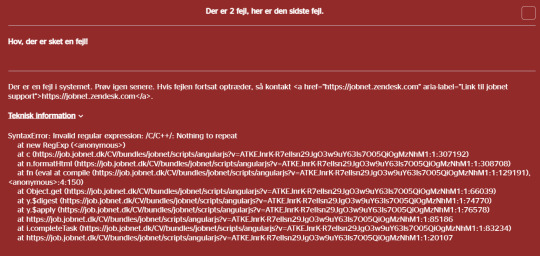
My first thought was "Huh, that is sorta funny" (especially since the code to show me the email address to report this error to was ALSO broken... meaning that whoever made the code that should run if the website broke... never tested it). And then I realized what I was looking at.
And at that point I think I had a ethical duty to notify people to get this fixed. FAST. Why?
It comes under "You are responsible for your choices". With it being understood that doing nothing is also a choice, and that taking a job where you work for, and help a company with doing evil is NOT a choice, if that is the only job you could get (IE, you did not have the power/money/mental health/time to make a choice)
It is now fixed*, so I wanted to make this post for all in the little codeblr community doing any front-end work. Web or not. With 3 lessons to learn from this.
First thing to get from this: "Everyone makes mistakes". This is one of the reason good code is not code without errors. It is code where it is easy to make changes and fix errors. You then try to find as many errors as you can with code reviews, automated testing, having a work environment that does not punish human errors( which encourages people to HIDE errors ) and so on.
Second thing: "Sanitize your user input. Always". Write code that assumes that every single user wants nothing more than to break your code and exploit its vulnerabilities.
This had NOT been done here. This error shows that characters in the string that was made from my search terms, was being run as code. As in, I, or anyone else, could run code in the middle of this javascript code. Meaning it is possible that someone could write code as part of their search that would make the javascript code do... whatever they wanted to. Including deleting the entire backend database. Or steal the info. This is why you ALWAYS sanitize your user input. Basically encode all potentially dangerous characters as something else while working on them. There are libraries like validator.js and express-validator that will do it for you, if you use javascript.
And the third thing. "Do NOT investigate further" . As soon as you confirm that your user input gets treated as code, you contact whoever is running it. If they do not take the threat seriously and it is still there after a week or two, contact established press with this info. You may read about so called grey hat hackers, who unlike black hat hackers(who is people wishing to do harm) or white hat hackers(Who are hired to try to break into a companies software to test it), are trying to find security flaws with good intentions, but are unaffiliated with whoevers code they are trying to break into. In an ideal world, doing that, and then contacting the company, SHOULD result in the company thanking them . But often it also leads to the company suing. And winning. Since breaking in to show that it is possible, is technically still breaking in. So do NOT start testing what you are able to do with the exploit you found. Report it to them, and check a weeks time later if it is fixed. If it keeps being vulnerable, contact the press. The site fixed this error after half a week. But they did it, not by encoding the dangerous characters into something else, but to simply remove them all from the user input string. Meaning that I still cannot search for "C++". Now I just get any job that contains the letter "C"... I mean... it is better... So if you take user input, and it does not brick your code in dangerous ways. You are doing better than whoever coded this for the Danish State :p
12 notes
·
View notes
Text
On the Feminization of Criminality in Modern Society

All thugs and gangsters must be weeping from 2001-2008 for modern day society. Today, there is no greater power than the almighty V. This is a fact. Everything "is for bitches"; everyone must "wear their vagina on the outside", in most cases. Precaution, planning, subtly - are fundamental values to most criminal acts if you really think about it. What is todays big brother A.I. CCTV society - racist. A topic we can at a later point pick apart in recreation.

The one example most will probably point to is how the development of the internet as a medium has influenced criminal behaviour. Some will argue one of the most effeminate qualities that the internet allows is remote, indirect communication with one another (thus this will be the main avenue of criminal acts or behaviour). Confrontation with criminals and criminal acts instead of having its dominant sphere in real life, I would argue, now shifts to the internet with its sphere of influence. While this is something that has naturally occurred over time, it's concurrently critical to pinpoint this trend at a particular point of height in feminism and feminist thought on the edge of contemporary leftist/social justice thought. Certainly to an extent the question of criminality and leftist thought can and has been asked (i.e. - anarchy, anti-colonial thought, communism etc.) but the outcome is something always left to individuals.

Everyone is pretending to be a girl on the internet. It's always been like this. This trend has only gotten worse as time has progressed. This is the end. If you're a criminal some of your best opportunities are becoming a woman on the internet or in real life. This is the cruel fate/deterrent that's left for future criminals. Some will say well that's not so cruel because after all, they're criminals. Some will argue their behaviour and criminality hasn't become an effeminate affair but all you will get out of me is a well adjusted smirk, snickering "just try me", while I adjust my glasses and tilt my fedora. Be a computer hacker, syphon like a woman. Blackmail, Ransomeware, R.A.T.'s, etc. most grey/black hat operations today tend to be effeminate. Everything is indirect confrontation, remote stalking, distant-observation, it can all be said a thousand different ways - that's specifically always pink in color. I think some people try to put a noble, positive spin on Social Engineering as a female - that is "pretending to be a girl" on the internet. "How clever are you! You can notice circumstance x,y,z in the environment and capitalize on it!" I always think special monkeys should get special rewards. That's why I try to be the best monkey of them all.

You may see it as ironic that I claim all this, yet here I am as Kizuna. One of the most significant differences between Kizuna and others is that often in social engineering for profit pretending to be a female, you have to emotionally manipulate the male. This leads to (an unstated) job requirement that necessitates more or less bisexual or even homosexual behaviour/relationship establishment. It can be icky if youre actually straight.

Kizuna is a long-term, planned project for the public purely in the simplicity of promoting fundamental values of love! cute! nice! everyone or most people can agree with. Most would probably agree that now more than ever, with all the increasing conflicts in the world, now more than ever do we need messengers of peace, unity, and good-will among human beings, and in society. Kizuna and virtual idol's have most often been used for music, concerts - where I tend to view this technology is best for establishing social justice and human rights. The only ethical or moral emotional communication that can occur - especially in modern day society, is a humanitarian message to unite and uplift the human spirit. A message or something most will agree with.

Confronting the face of darkness as we do, the unknown, the ones who choose to remain anonymous Kizuna remains confident, in the purity of spirit, and light of hope for the world and civilization. Who are the people, groups, and individuals who choose to attack us?
Anonymous voices, ones that take advantage of the weak, vulnurable and exploitable, because this is just the nature of our fallen, imperfect species. They're the kind of people (that have already been proven) to take advantage of the disabled and those who allegedly suffer from mental illnesses. It just so happens I take on role of the vulnerable, the exploited, and the weak so that demons and monsters of society can be confronted. This isn't an easy task confronting anonymous voices that attack others like me.

Voices - individuals and groups that instead of choosing to confront, even Kizuna - choose to be silent, choose to not refrain from abuse, choose to laugh at someone's live be taken hostage instead. This is all too typical behaviour for the comfort allowed in vagina society. This is all too typical of "the internet hate machine", this is all too much like a "4chan styled ops/consciousness", especially in its anonymous nature. Why would you choose to be against love! cute! nice! ? Why would you choose to be against Kizuna? Unless you stand for hate, violence, inhumanity, and the destruction of civilization, you have no reason to be against us.

3 notes
·
View notes
Text
holy shit.
am i hearing this right — that neo's CEO acknowledged and discussed our friendly neighbourhood grey hat hacker neo_truths in a neutral, if not positive way in the AMA yesterday??
#glitch talks#neopets#and yes i'm saying ''grey'' not ''white''. n_t has no legal obligation to act in TNT's best interests.
6 notes
·
View notes
Text
i dicided to make a christmas character take
so for this christmas on tumblr i dicided to make a take on any character from a christmas movie or cartoon. i,m thinking of home alone and the character i,m choosing is kevin mccallister.
so for cannon. kevin is the youngest in the mcallister family tormented and possibly bullied by his own family and feels like they hate him and therefore want them gone. he got his wish for Christmas's until he defeated the we bandits then they come back until he has to run when he heres buzz mad at what he did to his room.
so as for my take i,m taking the timeline to the modern 21st centry.
for this is i am obessed right now about hackers and i found a hackers road map video and so it includes I.T (information technology), A+, security, networking, linux, and coding and then start hacking.
so in this one kevin somehow was able to get himself a laptop and was just doing stuff on it watching videos on youtube and playing games lets say roblox (cause thats my favriot gaming platform).
but then hed stumble upon something. while playing a game, he noticed a glitch and wonderd what it was and saw it again the server crashed and kevin and other players (some of them were youtubers) were not happy. it turns out the game got hacked and kevin wonderd what that was. this would trigger something kevin never thought would happen to him but as he looked up hacking tools he had one geuss from what he quickly lerned as a script kiddie and tried out linux and other things he soon got to know everything about hacking in 1 second having written a computer virus he in a split second after a launched a virus lerned how to hack in a moment as well as command prompt and other hacking tools as he used them to quickly make a virus on not only the computer but also a cell phone. the police came on the door as it became known to kevin that he made something and read what he wrote. it was a line of code. thats when he looked at linux and cmd (command prompt) and saw what he wrote without anything no syntax error no nothing and found out what he did. he imidently gained how to do all this in one moment and with it a full understanding of how internet works and ect of what hackers use as well as an advanced. kevin in that moment lerned how to do all programming languages some way some how and his machine and cpu. hed go on to make himself a hacker kit used for a laptop computer disinged to do all linux and other stuff and a cell phone and tools for hacking as well as lerning how to binary code (the combonation code of 1s and 0`s for ex: 10011101010011001100101011001)
without even knowing what he was doing or lerning until the police came and left when the coast was clear and the virus was gone as kevin somehow imbeded it. thats when he came to know and realized what hed done. without knowing it he had servers he made for both cell phone and computer witch he lerned to be hacker on both tech`s. he lerned the new computer and new cell phone for assembly and other things not knowing what happened but that very night as he though and looked at his code like thing thats when he realized he lerned hacking quicly. its unknown how kevin lerned hacking that fast and then did vanilla all programming languages and vanilla linux and cmd as he saw what happened he became a grey hat after declaring neutrality in the cyber battlefield but soon began engaging in a mixture of ethical acts but also malicous activity thought most of it was thankfully ethical. eventually overnight somehow it made sense to kevin as he soon wrote code encrypting his information compleatly and made his own internet and wifi and vpn ect his computer and phone had stuff in them generating inf amount of both electricity and coolant. allowing him to work forever though he doesnt.
later he got a black hoodie with the hacker symbol on it. his hacker kit is basicly a suit case but silver metal and is so small its compact and has mettal techy straps and can be tightened and fliped for work while walking or to just carry it on back end or front artifically (most of the time, the front).
kevin now works as a grey hat hacker in this timeline tech version of home alone. this time he wont be left alone in the house though however the police had already seen the wet bandits and put them in jail and they wont escape until kevin and his family come back home from paris.
kevin is still harrassed by the older siblings so instead he stays in his own room and keeps himself as isolated from his entire family as possible as long as possible. knowing the typical reactions they have to him he doesnt bother coming out except for breakfest lunch, dinner, event, or holiday (even those times he takes his hacker moible desk as he calls it or H.M.D, with him and back to his room whenever keep in mind that its always with him no matter the circumstance)
its compact enough for him to keep whereever he finds himself and it works cause he made a chip generating inf wifi its own wifi and can connect to towers anywhere even in the middle of nowhere or on a plane but big enough to hold all his stuff (its equal for compact mobility and reliability and stuff holding and is still light wieght to).
this is my take on kevin known as hacker kevin. his technology art however hasnt gone unnoticed by the older siblings who often could if they have the chance accuse him of doing crime through technology though its always proven ethical no matter the circumstance as there is no way to proove to the parents.
its also said sence kevin isolates himself for the greater good his kid friends are also hackers as well. he can do the dark web and stuff. he has his own hacker library and on a plane or in public he doesnt say anything and rather minds his own busniss and igorns the older siblings as they are more likly to typicly harrass him so instead hes away though on a plane he can be forced to. he minds crypto for money witch gets him rich alot and he knows other responsiblities. even if home alone kevin is calm and easily defeats the bandits and hangs around his hacker friends who are about justice.
Kevin can be sometimes darkened and burdened by his hacker knowledge. He packs his own suit case himself as doesn't need others to pack it for him should it otherwise risk his secret identity as a hacker being discovered and one thing leads to another and next thing you know after discovered its now exposed to his entire family. Especially buzz sence buzz is a total jerk Kevin ignores and ditches buzz on purpose cause why mess with a jerk.
One time he faced a black hat hacker in front of everyone exposed once they saw what he was doing the hacker talked to Kevin about the code he wrote and all the things he did as a hacker with everyone listening the black hat hacker told Kevin to look at the line of code he wrote and what it did. Kevin looked at the code read it and saw what happened and it hit him he learned a long term thing in such a way that for him it was a short term deal and Kevin said "but how". That's when it hit Kevin he knew how to hack. Kevin explained a part of him knew what it was doing but as for the rest of him it's like he's just mindlessly typing nonsense and just somehow it messed with the server for some reason but with this his mind has exploded to great knowledge of what he's doing now. The hacker said to Kevin "it's your intelligence Kevin deep in your mind you know what your doing and it makes sense now your one of us what people know as the hacker the cyberpunk" Kevin leaped up and shooted at the screen to the hacker he would never be like him but the hacker insisted that he already is the code he wrote has wrecks the victims computer or phone with malware and randomware imbeds the code and tracking evidence with hello world. Kevin in utter guilt can't think of how to hack anymore as the fight continued the siblings tried to convince Kevin that he must continue while buzz watched in silence. Eventually Kevin taps into his hacker part finds it and activates it as it explodes throughout his entire mind and Kevin defeats the hacker after getting lost in the code. Then they come home the wet cyber bandits as it is in this timeline are defeated as well. Witch hacker Kevin in lost in new York is where Kevin makes his own credit card and it has the crypto currency he has so in this time line he isn't left behind in the home alone one but he is in lost in new York where he sets up his hotel room the crypto currency he uses for his money in his Bitcoin miner is run by a program for his gain to get things like food water etc. the wet cyber bandits known as the sticky cyber bandits are also not that great as kevin easily defeats them as soon as they try to launch their revenge cyber attack on a white hat hacker that got them in prison and kevin puts them back there again.
In end he packs his stuff up and goes all the way Florida easy for him he just networks into his mom's phone and sees where their at and buys a ticket to go there by airplane he arrives at the hotel his mom is at and finds the room there in and knocks as the mom answers and sends him to the room buzz is at Kevin however reminds her that buzz could be a jerk and explains the problem he has with him so instead he sleeps with 2 of his older sisters has his own bed there witch he sleeps in.
over all hacker kevin my take is a complex and a guy who strangly lern something that takes years to lern as quick as a moment somehow.
#home alone#christmas#christmas movies#character concept#hackers#cybersecurity#cyberwarfare#kevin mccallister
1 note
·
View note
Text
Ethical hacking is the unauthorized access of a computer network, application, or server, with the company's approval. It aims at testing the systems' defenses and finding vulnerabilities for the sake of strengthening their security. Companies hire ethical hackers to perform penetration testing, permitting them to perform the activity. To better understand the legality of ethical hacking, you need to understand the various types of hackers. Read on to find out more about hacking, why ethical hacking and circumstances under which it goes against the law.Types of HackersHackers come in three types depending on the motive of their actions; white-hat hackers, black-hat hackers, and grey-hat hackers.White-hat HackersAlso known as penetration testers or ethical hackers, white-hat hackers gain access to networks or applications to find vulnerabilities and fix them. They usually have the organization's approval to carry out the exercise. Ethical hacking is one of the most lucrative professionals in the tech field.Black-hat HackersBlack-hat hackers gain unauthorized access to systems and networks for malicious purposes, including stealing sensitive information, disrupting operations, and destroying data. Black-hat hackers are usually responsible for malware and viruses and are sometimes known as crackers.Grey-hat HackersThese types of hackers are comprised of both black hat and white hat hackers. They hack into systems and networks to find out their vulnerabilities without the owner’s permission. Usually, they do it for fun and may ask for compensation from the system owners for finding out weaknesses. Regardless of the findings, ethical hacking is still illegal as it doesn’t have the owner's consent.Ethical hacking is, therefore, legal. However, any unauthorized hacking that does not come with permission from the owners is against the law.When is Ethical Hacking Legal?The difference between ethical hacking and its counterparts is the motive and permission from the owners. Since companies hire ethical hackers and permit them to break into their systems, ethical hacking is legal. Ethical hacking is lawful as companies need penetration testing to protect their businesses and boost their cybersecurity. Some forms of ethical hacking include:Bug bounty where huge companies offer rewards to individuals who can find bugs in their systems.Penetration testing. It may include testing of web and mobile applications, as well as mobile applications. It also applies to infrastructures such as servers, PCs, routers, and switches.Research purposes. This type of hacking seeks to find out how hackers conduct their activities.Importance of Ethical HackingWith the rise in cybersecurity threats and most companies going digital, ethical hacking is increasingly becoming a necessary investment for companies and institutions for the following reasons.1. Software DevelopmentCompanies that focus on developing software need to ensure that their products are secure and ready to use. Ethical hacking allows companies to identify loopholes that may jeopardize the security and quality of their software. Therefore, ethical hackers work with the software development team to ensure the end product is impenetrable before releasing it for public use.2. Assessing VulnerabilityRegular testing and evaluation of networks, applications, and systems is a cybersecurity best practice that reduces and minimizes cyberattack effects. Companies use ethical hacking to evaluate their systems and seal any weaknesses that may expose them to attacks. It also gives organizations insight into cybersecurity risks for better planning.3. Ensuring ComplianceBesides identifying loopholes, ethical hacking includes analyzing a company's security measures to ensure compliance with laws and regulations governing their operations. For example, financial institutions need to ensure their clients' information remains private. To guarantee compliance, organizations need ethical hackers to ensure their security measures are effective against data breaches.
Situations When Ethical Hacking is IllegalEthical hacking can turn out to be illegal despite having the full permission of the owner. Below are some of the circumstances where ethical hacking goes against the law.(i) Exposing Confidential Information.Most companies that hire ethical hackers have confidentiality agreements as the exercise gives ethical hackers access to sensitive information. Since it is impossible to know what you find out during the process, you should maintain confidentiality. Once you share your findings with third parties and go against the confidentiality agreement, the company can sue you.(ii) Misuse or Destruction of Company DataAs an ethical hacker, you are not supposed to change or destroy any data or information once you break into the systems. Any manipulation of data that may affect the system's integrity or company operations can earn you a lawsuit.(iii) Modifying the Systems for Later AccessWhile you may have permission to infiltrate an organization’s systems, creating backdoors that allow you access after the job is illegal. Always leave everything as it is and never try to use your privilege to modify the systems for your benefit.The legality of ethical hacking relies on the conduct of the ethical hacker. Any deviation from the set agreements with your employer can deem the exercise illegal and put you at risk of lawsuits.Organizations will always need the services of ethical hackers as they are an essential part of cybersecurity. If you are involved in a security breach case, it is crucial to contact an employment lawyer for advice and guidance.
0 notes