#how to control inodes
Explore tagged Tumblr posts
Video
youtube
Full tutorial - How to reduce the number of Inodes in your hosting account - eComHardyThis is the full tutorial video step by step showing how to reduce unnecessary Inodes from your hosting account. I recommend Siteground Hosting services - check out the link given below for discounted price hosting plans; https://www.siteground.com/index.htm?afcode=cd5fdfefc6c42dced3f39f15a45ce66d To learn to make a website - check out; http://ecomhardy.com/make-a-website Watch my video on how to use caching plugins and make a website faster; https://youtu.be/dmf7lYEFzOk Here are the steps Siteground hosting service provider suggests. Watch the full video to know free tools and plugins to help you improve Inodes numbers. How to reduce the number of inodes my account uses? The number of inodes equals the total number of files and folders on your web hosting account. Therefore, to reduce your inode count, you would have to reduce the number of files and folders. Most commonly this is done by: Removing all files and folders you don 19t need You can use the File Manager in Site Tools or FTP to access your account and delete files and folders that you don 19t need. Here are some of the most common causes that may give you an idea about how to reduce the number of inodes you have. 1. Remove old Backups It is common for backups that are created on a schedule by plugins or 3rd party services to fill all the available disk space if left unmonitored. Download unused backups and delete them from your hosting account to save disk space and inodes. 2. Delete Inactive Plugins If you 19re using WordPress and have plugins that are not active on your site 13 please delete them. Deactivating the plugins leaves the codebase on your account adding up to your inodes quota. 3. Remove Unused Image Sizes If you 19re using WordPress your theme may be generating multiple copies of each uploaded image, some of which are unused. Check your theme settings and leave only the ones that you are actually using on your site. Then, regenerate thumbnails deleting unused sizes using a plugin like Regenerate Thumbnails. 4. Check the number of cache files you have Modern web applications by default usually use file caching, which means that they might be generating a high amount of cache files inside your account, thus adding to its total inode. Check your website 19s 18cache 19 folder and reduce the number of cached files you keep regularly. Most web applications which store cache include an option to purge the cache from within their administrative area. For WordPress, check the wp-content folder for similarly named folders and clear them. We recommend using the SiteGround Optimizer plugin for caching and performance which does not rely on file-based caching and won 19t add to your inodes quota. 5. Delete the .opcache folder in your account You can use SSH to delete the .opcache system folder in your account. In case you 19re using PHP 7. x this is where it stores opcaches. Don 19t worry, it will be regenerated but will lack obsolete cache from older PHP versions or code that is no longer active on your account. 6. Clean up your Email Accounts Mail adds to the total inodes quota since emails are files stored on your account. We recommend that you regularly delete your Junk/Spam folders that tend to accumulate a large number of emails. Regularly clean your Trash/Bin folders which collect deleted emails but keep them on the server. Last but not least, you can remove emails coming from newsletters and automatically generate ones that you don 19t need. If you 19ve followed all of the above and you still need additional disk space or inodes, you may consider upgrading your account to a higher hosting plan with a higher inodes quota. ------------------------------------------------------------------------------------------------------------------------- Part 1- How to make a website - Buy right Domain and Hosting https://youtu.be/y-JoRxhwhE8 Go to, https://ecomhardy.com/make-a-website
#wordpress#woocommerce#elementor#dropshipping#ecommerce#ecomhardy#disk usage warning#get more space#how to control inodes#how to delete cache#how to delete junk or spam emails#how to delete the unnecessary files and folders#how to increase disk space#how to reduce file usage in siteground#how to reduce indoes#how to remove disk usage warning#how to solve cpanel - disk usage warning#increase disk space#increase inode limit siteground#inode quota exceeded cpanel
0 notes
Text
Here is How to Solve Cpanel - Disk Usage Warning & Inodes Problem
Here is How to Solve Cpanel – Disk Usage Warning & Inodes Problem
If you have a hosted site on WordPress then you’ll definitely face the Disk Usage and Files Limit (Inodes) Warning.
What is an Inode?
An Inode is a data structure used to store the metadata of a file. The number of inodes indicates the number of files and folders you have under your hosting account.
All the shared hosting service providers maintain these limits in order to…
View On WordPress
#Cpanel Tips & Tricks#disk usage warning cpanel solutio#get more cpanel space#Hindi#how to#how to control inodes#How to Delete cache in cpanel#how to Delete junk or spam emails in cpanel#how to Delete the unnecessary files and folders in cpanel#how to increase disk space in cpanel#how to reduce file usage in cpanel#how to reduce indoes#how to remove disk usage warning in cpanel#How to Solve Cpanel - Disk Usage Warning#How to Solve Increased Inodes#increase disk space in cpanel#increase inode limit + cpanel#inode quota exceeded cpanel#Tech Urdu#Techurdu#Urdu
0 notes
Text
In this guide, I’m going to show you how to configure MongoDB Replica Set on Ubuntu 20.04|18.04|16.04 server. MongoDB is an enterprise-class NoSQL database system with auto-scaling, high availability and high performance. In a NoSQL database, data is stored in a document structure using MongoDB BSON format. SQL statements cannot be used in MongoDB to insert or retrieve data. What is MongoDB Replication / Replica set? In MongoDB, a replica set is a group of mongod processes that maintain the same data set. Replica sets are the basis for all production deployments as they provide data redundancy and high availability. This tutorial will describe the steps required to create a working three nodes replica set without configured access control to restrict access. This guide is based on below system IP Addresses: MongoDB Server1: 10.10.5.2 MongoDB Server2: 10.10.5.3 MongoDB Server3: 10.10.5.4 Step 1: Setup Requirements Before you can configure a replica set you’ve to install MongoDB on all the servers. Make sure correct hostnames are configured on the servers that will be used for replication. Set mapping for IP address and FQDNs locally on the servers if you don’t have a working DNS server. # Edit and set the values correctly 10.10.5.2 mongodb-01.example.net mongodb-01 10.10.5.3 mongodb-02.example.net mongodb-02 10.10.5.4 mongodb-03.example.net mongodb-03 Step 2: Install MongoDB on all Ubuntu 20.04|18.04 Nodes Follow below steps to install MongoDB on Ubuntu server. Update system: sudo apt-get update sudo apt-get upgrade && sudo reboot Import MongoDB public GPG Key: sudo apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv 9DA31620334BD75D9DCB49F368818C72E52529D4 Once the key has been imported, add the repository: ### Ubuntu 20.04 ### echo "deb [ arch=amd64,arm64 ] https://repo.mongodb.org/apt/ubuntu focal/mongodb-org/4.4 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-4.4.list ### Ubuntu 18.04 ### echo "deb [ arch=amd64,arm64 ] https://repo.mongodb.org/apt/ubuntu bionic/mongodb-org/4.4 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-4.4.list ### Ubuntu 16.04 ### echo "deb [ arch=amd64,arm64 ] https://repo.mongodb.org/apt/ubuntu xenial/mongodb-org/4.4 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-4.4.list Install MongoDB packages sudo apt-get update sudo apt install -y mongodb-org Using Dedicated disk to store MongoDB data (Optional) For my setup, I have 10GB secondary storage dedicated for MongoDB data. I’ll partition it and mount to /data/mongodb. # lsblk NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT sda 8:0 0 32G 0 disk |-sda1 8:1 0 487M 0 part /boot |-sda2 8:2 0 1.9G 0 part [SWAP] `-sda3 8:3 0 29.6G 0 part / vda 252:0 0 10G 0 disk Create a GPT partition table for the secondary disk, it can be more than one disk parted -s -a optimal -- /dev/vda mklabel gpt parted -s -a optimal -- /dev/vda mkpart primary 0% 100% parted -s -- /dev/vda align-check optimal 1 Then create LVM volume, this will make it easy to extend the partition $ sudo pvcreate /dev/vda1 Physical volume "/dev/vda1" successfully created. $ sudo vgcreate vg11 /dev/vda1 Volume group "vg11" successfully created $ sudo lvcreate -n data -l 100%FREE vg11 Logical volume "data" created Create a ext4filesystem on the Logical Volume created. $ sudo mkfs.ext4 /dev/mapper/vg11-data mke2fs 1.44.1 (24-Mar-2018) Creating filesystem with 2620416 4k blocks and 655360 inodes Filesystem UUID: b98e07e5-1b04-4282-a9db-fa5b73c74d2f Superblock backups stored on blocks: 32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632 Allocating group tables: done Writing inode tables: done Creating journal (16384 blocks): done Writing superblocks and filesystem accounting information: done Create a mount point and mount the partition echo "/dev/mapper/vg11-data /data ext4 defaults 0 0" | sudo tee -a /etc/fstab
mkdir /data mount -a Confirm that the partition mount was successful: $ df -hT | grep /data /dev/mapper/vg11-data ext4 9.8G 37M 9.3G 1% /data Create a folder for MongoDB data sudo mkdir /data/mongodb sudo chown -R mongodb:mongodb /data/mongodb sudo chmod -R 775 /data/mongodb Configure the storage path to the one created earlier on all nodes $ sudo vim /etc/mongod.conf # Where and how to store data. storage: dbPath: /data/mongodb journal: enabled: true Step 3: Configure MongoDB Replica set Now that we have everything needed ready, let’s proceed to configure MongoDB replica set. Change MongoDB Listen Address from localhost IP on all nodes $ sudo vim /etc/mongod.conf # node 1 # network interfaces net: port: 27017 bindIp: 10.10.5.2 # Listen to local interface only, comment to listen on all interfaces. # node 2 # network interfaces net: port: 27017 bindIp: 10.10.5.3 # Listen to local interface only, comment to listen on all interfaces. # node 3 # network interfaces net: port: 27017 bindIp: 10.10.5.4 # Listen to local interface only, comment to listen on all interfaces. Configuring MongoDB Replica Set One of the MongoDB nodes run as the PRIMARY, and all other nodes will work as SECONDARY. Data is always to the PRIMARY node and the data sets are then replicated to all other SECONDARYnodes. Edit the MongoDB configuration file mongod.conf and enable replica set on all nodes replication: replSetName: "replica01" Open port 27017/tcp on the firewall: sudo ufw enable sudo ufw allow ssh sudo ufw allow 27017/tcp Configure MongoDB to start during the operating system’s boot sudo systemctl enable mongod.service sudo systemctl restart mongod.service Check the listen Address of MongoDB service: # ss -tunelp | grep -i mongo tcp LISTEN 0 128 10.10.5.2:27017 0.0.0.0:* users:(("mongod",pid=15288,fd=11)) uid:111 ino:46927 sk:4 Initiate MongoDB Replica Set Our MongoDB Node1 (mongodb-01) will be the PRIMARY and the other two will act as SECONDARY Login to the mongodb-01 server and start the mongo shell. $ mongo 10.10.5.2 MongoDB shell version v4.0.1 connecting to: mongodb://10.10.5.2:27017/test MongoDB server version: 4.0.1 Welcome to the MongoDB shell. For interactive help, type "help". ... > Initialize replica set on node1 by running below command: > rs.initiate() "info2" : "no configuration specified. Using a default configuration for the set", "me" : "10.10.5.2:27017", "ok" : 1, "operationTime" : Timestamp(1534797235, 1), "$clusterTime" : "clusterTime" : Timestamp(1534797235, 1), "signature" : "hash" : BinData(0,"AAAAAAAAAAAAAAAAAAAAAAAAAAA="), "keyId" : NumberLong(0) Make sure you get 1 for ok state Add secondary nodes replica01:PRIMARY> rs.add("mongodb-02") "ok" : 1, "operationTime" : Timestamp(1534797580, 1), "$clusterTime" : "clusterTime" : Timestamp(1534797580, 1), "signature" : "hash" : BinData(0,"AAAAAAAAAAAAAAAAAAAAAAAAAAA="), "keyId" : NumberLong(0) replica01:PRIMARY> rs.add("mongodb-03") "ok" : 1, "operationTime" : Timestamp(1534797614, 1), "$clusterTime" : "clusterTime" : Timestamp(1534797614, 1), "signature" : "hash" : BinData(0,"AAAAAAAAAAAAAAAAAAAAAAAAAAA="), "keyId" : NumberLong(0) Check replica set status using: replica01:PRIMARY> rs.status() Check the status of the master replica01:PRIMARY> rs.isMaster()
Testing MongoDB Replication Create a test database on mongodb-01 replica01:PRIMARY> use test_db switched to db test_db Add some data > db.test.save( "desc": "My Test Database", "apps": ["Test1", "Test2", "Test3", "Test4"], ) replica01:PRIMARY> show dbs admin 0.000GB config 0.000GB local 0.000GB test_db 0.000GB replica01:PRIMARY> use test_db switched to db test_db replica01:PRIMARY> show collections test Conclusion You now have a working MongoDB replication. You can increase the cluster size from three nodes to five nodes, seven nodes or more. This number is calculated from: [Master Eligible Nodes) / 2 + 1], which means an odd number of nodes is required for high availability, the minimum number is three. Reference: https://docs.mongodb.com/master/replication/ https://docs.mongodb.com/manual/tutorial/deploy-replica-set/
0 notes
Text

inodal, is the capital of thane’s kingdom, making its profits and trades in grains and fish from the sea. from the same sea, they even gather pearls as another way of amassing income. the pearls likely sold to nobles for a hefty amount as valuables. ores they obtain to produce weapons scarcely come from here, they instead are brought in from other parts of the kingdom either in a raw form or already crafted into weapons. a majority of the water they draw is from the ocean and is put through desalination in order to be consumed without any adverse effects. it was enacted by magic since no other methods currently exist even if others work towards it.
during thane’s early years, he conquered many lands and claimed everything that came with them without remorse. in those days bloodshed was the order of the day; they enjoyed it and the challenge that came along with it. just as his home worshiped its own heroes, it's the same for other places and his offenses towards them would rouse one such hero. a ‘king in the mountain’ with every intention of defeating him to right the wrongs performed. knowing that they were coming, he left to challenge them away from the heart of his people instead leaving things to be taken care of without him in the kingdom. edit
the battle lasted for thirty days, they fought without proper rest and food, scavenging what they could before thrusting back into battle with one another in single combat. the clash resulted in light tremors through the earth and violent shifting in the winds. coming anywhere near them would have been walking into a storm only to be cast away in its presence. he managed to finally win the battle, striking them down in a moment of weakness that’d been hard fought to create but suffered a loss of his own. the entire battle subjected him to the heroes wounds, their pain, and anguish, far from overshadowing his own indifference towards it all. killing them was like driving a stake into his own heart. all of this orchestrated to give him the final nudge towards becoming a peaceful ruler, tiring of fighting and the havoc it’d bring upon himself. all those things pushed down bubbling up all at once forced him to acknowledge them.
now, during his absence, his mother seized control of the throne once again without anyone to properly contest her. the sons of the previous king deceased and daughters scattered to other places to supervise them left her free to act. playing both sides and giving them a common enemy in their king. it’s important to include one thing, thane ruling was the turning point for how the throne was regarded. he was the son of a god, a living and breathing deity, which meant invoking the wrath by not acknowledging their place. they worshiped him as a god even if he was only half of one. they’ve always been indifferent to this. thane’s battle produced unnatural effects in the world and one of which leveled portions of the capital which they made sure to pin on him. all the more support for someone else taking the lead from someone so irresponsible, someone that was on the same footing as them all. coming back from those thirty days, they did not want to fight but could not allow someone to take his right away. their newfound stances meant another form of battle, battling through politics.
#( * ╱ meta. )#( im keeping this smaller bc if i have to change them its easier n two ? )#( longer stuff will prob get convulted#convoluted *#)#long post /
3 notes
·
View notes
Text
Ntfs 3g For Mac Os X

Ntfs-3g For Mac Os X Dmg
Ntfs-3g For Mac Os X 10.12.5
Ntfs-3g For Mac Os X 2010.10.2
NTFS-3G for Mac adds drivers to your OS X installation that allow you to read and write to NTFS-formatted thumb and external hard drives as if you're using a Windows machine. The software comes. On October 5, 2009, NTFS-3G for Mac was brought under the auspices of Tuxera Ltd. And a proprietary version called Tuxera NTFS for Mac was made available. On April 12, 2011, it was announced that Ntfsprogs project was merged with NTFS-3G. NTFS-3g added TRIM support in version 2015.3.14. Follow this process to enable NTFS Write Support on Mac OS X Yosemite for FREE. We install three free applications to achieve that. Here are the links for th.
UPD: There is even better way to solve the same issue with native Mac OS X drivers, but it has its own pros and cons. Read at the end for details. UPD (IMPORTANT): Native driver makes NTFS unusable. Read below for details. Mac OS X Lion (10.7) was released recently, in the end of July 2011. And many users had started to complain that their NTFS disks stopped working.
While OS X can natively read and write FAT-formatted drives, it’s a one-way (read-only) street with NTFS—that is, without a little help from Paragon. NTFS for Mac 14 installs a preference pane.
NTFS-3GDeveloper(s)Tuxera Inc.Stable releaseWritten inCOperating systemUnix-like, HaikuTypeLicenseDual-licensed GNU GPL/Proprietary[citation needed]Websitewww.tuxera.com/community/open-source-ntfs-3g/
NTFS-3G is an open-sourcecross-platform implementation of the Microsoft WindowsNTFS file system with read/write support. NTFS-3G often uses the FUSEfile system interface, so it can run unmodified on many different operating systems. It is runnable on Linux, FreeBSD, NetBSD, OpenSolaris, illumos, BeOS, QNX, WinCE, Nucleus, VxWorks, Haiku,[1]MorphOS, Minix, macOS[2] and OpenBSD.[3][4] It is licensed under the GNU General Public License. It is a partial fork of ntfsprogs and is under active maintenance and development.
NTFS-3G was introduced by one of the senior Linux NTFS developers, Szabolcs Szakacsits, in July 2006. The first stable version was released on February 21, 2007, as version 1.0. The developers of NTFS-3G later formed a company, Tuxera Inc., to further develop the code. NTFS-3G is now the free 'community edition',[1][failed verification] while Tuxera NTFS is the proprietary version.
Features[edit]
NTFS-3G supports all operations for writing files: files of any size can be created, modified, renamed, moved, or deleted on NTFS partitions. Transparent compression is supported, as well as system-level encryption.[5] Support to modify access control lists and permissions is available.[6] NTFS partitions are mounted using the Filesystem in Userspace (FUSE) interface. NTFS-3G supports hard links, symbolic links, and junctions. With the help of NTFS reparse point plugins, it can be made to read chunk-deduplicated files, system-compressed files, and OneDrive files.[7] NTFS-3G provides complete support and translation of NTFS access control list (ACL) to POSIX ACL permissions. A 'usermap' utility is included to record the mapping from UIDs to Windows NT SIDs.
NTFS-3G supports partial NTFS journaling, so if an unexpected computer failure leaves the file system in an inconsistent state, the volume can be repaired. As of 2009, a volume having an unclean journal file is recovered and mounted by default. The ‘norecover’ mount option can be used to disable this behavior.[8]

Performance[edit]
Benchmarks show that the driver's performance via FUSE is comparable to that of other filesystems' drivers in-kernel,[9] provided that the CPU is powerful enough. On embedded or old systems, the high processor usage can severely limit performance. Tuxera sells optimized versions of the driver that claims to have improved CPU utilization for embedded systems and MacOS.[10]
The slowness of NTFS-3G (and FUSE in general) on embedded systems is attributed to the frequent context switching associated with FUSE calls. Some open-source methods provided to reduce this overhead include:[11]
The underlying FUSE layer has an option called big_writes to use larger blocks when writing. Using a larger block means fewer context switches. This is in fact a solution recommended by Tuxera.[12] A patch is available to use an even larger block.[13]
There is also a Linux kernel option called lazytime to reduce the writes on file access.
Synology Inc. uses a modified NTFS-3G on their NAS systems. It replaces the ntfs-3g inode caching CACHE_NIDATA_SIZE with a different mechanism with unsure benefit. (It also includes an alternative Security Identifier translation for the NAS.)
History[edit]

NTFS-3G forked from the Linux-NTFS project on October 31, 2006.
On February 21, 2007, Szabolcs Szakacsits announced 'the release of the first open-source, freely available, stable read/write NTFS driver, NTFS-3G 1.0.'
On October 5, 2009, NTFS-3G for Mac was brought under the auspices of Tuxera Ltd. and a proprietary version called Tuxera NTFS for Mac was made available.[14]
On April 12, 2011, it was announced that Ntfsprogs project was merged with NTFS-3G.[15]
NTFS-3g added TRIM support in version 2015.3.14.
See also[edit]
References[edit]
^ abc'STABLE Version 2017.3.23 (March 28, 2017)'. Tuxera. Tuxera. 2017-03-23. Retrieved 2017-03-23.
^NTFS-3G for Mac OS X ('Catacombae')
^'OpenBSD adds fuse(4) support for adding file systems in userland'. OpenBSD Journal. 2013-11-08. Retrieved 2013-11-08.
^'ntfs_3g-2014.2.15 – FUSE NTFS driver with read/write support'. OpenBSD ports. 2014-01-05. Retrieved 2015-02-14.
^NTFS-3G FAQ
^NTFS-3G: NTFS Driver with Ownership and permissions
^André, Jean-Pierre (March 1, 2019). 'NTFS-3G: Junction Points, Symbolic Links and Reparse Points'. jp-andre.pagesperso-orange.fr.
^'NTFS-3G 2009.2.1 changelog'. Archived from the original on 2009-03-23. Retrieved 2012-09-10.
^Comparing NTFS-3G to ZFS-FUSE for FUSE Performance
^Performance at Tuxera
^Gothe, Markus. 'On Linux NTFS Performance'. Retrieved 3 October 2019.
^'NTFS-3G Questions'. Tuxera. Workaround: using the mount option “big_writes” generally reduces the CPU usage, provided the software requesting the writes supports big blocks.
^Wang, M. 'linux - Disadvantages of ntfs-3g `big_writes` mount option'. Unix & Linux Stack Exchange. Retrieved 3 October 2019.
^NTFS-3G for Mac OS X is now Tuxera NTFS for Mac
^Release: NTFS-3G + NTFSPROGS 2011.4.12
External links[edit]
Retrieved from 'https://en.wikipedia.org/w/index.php?title=NTFS-3G&oldid=958820922'
3 Free NTFS Solution
UPD 21.08.2011: There is even better way to solve the same issue with native Mac OS X drivers, but it has its own pros and cons. Read at the end for details.
UPD 12.09.2011 (IMPORTANT): Native driver makes NTFS unusable. Read below for details.
Mac OS X Lion (10.7) was released recently, in the end of July 2011. And many users had started to complain that their NTFS disks stopped working. And the much worse problem is that “old” solutions do not work well.
Ntfs-3g For Mac Os X Dmg
But after one or two weeks of researching of this issue, I’ve managed to make NTFS work in Mac OS X Lion (10.7). The key here is a proper combination of software versions.
So I will shortly describe the usual choices for external data storages, and what problems arises with each of them. And later I will show how you can get the most universal way — NTFS — to work where it does not work by default, with links and pictures.
Data Storages
The only reason to worry about this problem is an ability to access external storage drives. Even if these are your own drives and you can select a filesystem to use, that choice is not easy.
There are few possible choices for large (~1TB) file storages, but each has very unpleasant limitations and issues:
* HFS+/HFSX (or “Mac OS Extended”/”Mac OS Extended (case sensitive)”) — okay with big volumes and big files, but works natively under Mac OS X and Linuxes only. Windows need third-party software, which is either free file browser/extractor or paid low-level drivers.
* FAT32 work in each and every OS now, but has limitation for file size up to 4GB (so, you cannot store DVD image, which is usually 4.5+ GB).
* FAT64 (exFAT) is a new solution, but it works natively only in Mac OS X and Windows 7. Older Windows systems (Vista, XP) require Service Packs and updates to support exFAT. Linuxes do not support exFAT yet at all. More on that, it has only one file table, so if this only place will be corrupted on write, I will get all the data lost.
* NTFS. Okay with big files an bug volumes. Works natively in all Windows systems. Works fluently in all Linux systems. Has native read-only support in Mac OS X. But has not write support under Mac OS X.
As you can see, in terms of cross-compativility, NTFS is the best choice: it works almost everywhere, and with no limitations. The only issue is write mode in Mac OS X.
Taking into account that you probably have a lot of friends with NTFS volumes, who can visit you and bring you something interesting there, you actually have no choice except as try to make NTFS working.
So, let’s do it.
Paid NTFS Solutions
But first, in case you want to make your own research, or you are looking for a solution that just works out of the box, and you are ready to pay for it, you can give a try to Paragon NTFS for Max OS X 9.0 for $19.99 (5-days trial). That is much cheaper than Tuxera NTFS for Mac for $36.02 (with 15-days trial).
The former one definitely works – I’ve tried it in trial. Just install and get everything ready: both read and write modes, auto-mount, and also NTFS formatting in Disk Utility, disk checking, etc.
I haven’t tested the latter one, so you can leave a comment here about your experience with Tuxera paid solution.
Ntfs-3g For Mac Os X 10.12.5
Free NTFS Solution
This free solution requires some efforts. Not so much, of course. Well, if you are going to make your own research, it can be lots of efforts, since the situation with NTFS-3G is not very clear now.
But if you are just about a ready, copy-n-install solution, it will be easy, and requires only these two or three steps:
* MacFUSE 64-bit.
* NTFS-3G stable.
* “15 seconds” error work-around (optional).
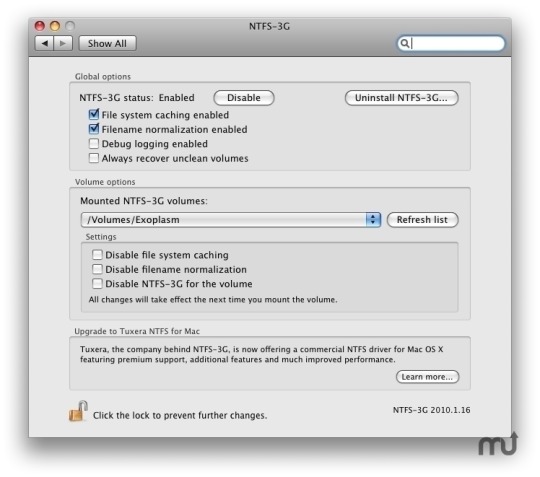
MacFUSE 64-bit
First, you need MacFUSE with 64 bit support. That is the main problem with Mac OS X Lion — it uses 64-bit kernel, and all previous version of Mac OS X used 32-bit one. So, old MacFUSE binaries won’t work anymore.
You can get Tuxera MacFUSE 2.2 image for free (could not find a page with it, just a download links) or try to compile OSXFUSE from sources. I’ve used the former one.
You can see MacFUSE preferences in “System Preferences”. Well, actually these are not preferences, but only “update” and “uninstall” actions, and current version info:
NTFS-3G stable
Second, you will need working copy of NTFS-3G. Long story short, NTFS-3G is either already dead or is going to die. There is its ancestor: Tuxera NTFS for Mac (paid).
But we are going to use old version of NTFS-3G — the one from 2010. I’ve got one from here. But you can try googling for it, or browse here for this exact version (not 2011 — I’m not sure they work).
I also tried to install later version from MacPorts, but it does not work too: mounts something that stills unreadable. That is in addition to an error in installation process (“mv” does not see the libntfs-3g file or so).
Now, when you have installed two binary packages, you can restart Mac OS X and try to attach the drive. It should work.
NTFS-3G preferences pane looks populated and interesting:
“15 seconds” error work-around
But it will show you the error message saying that there were not signal in 15 seconds:
This is not a big problem, because everything works fine. Only annoying message box is a problem.
So the third, optional step is to address this issue. You can follow this link: https://gist.github.com/1100318 (see first and the only comment under the code). You just download this attached C file, run “gcc” command line from the comment, and replaces the “fuse_wait” binary as said there. Yes, you will need “gcc” here.
And voila! Now you have working NTFS filesystem for free with no “15 seconds” error message. Profit!
Problems
Nevertheless, Mac OS X is a Unix-based system. And Unix-based system is a big problem when they work as desktop OS (earlier I thought that on Linux-based system because of community-driven and crowd-based development concept). This solution has some problems too. Though they are not about the solution itself, but about the components used.
The most important problem now is the speed: with this NTFS-3G on MacBook Air (4GB, i7 CPU) write speed for USB 2.0 drive is about 3.3 MB/s. Just to compare, the same drive in the same port, but with exFAT/FAT64 partition can write with ~38 MB/s (or fast enough to make exact estimation; will try larger files later).
Also, immediately following the mount of a drive, there is a line in system log with an error message saying:
Ntfs-3g For Mac Os X 2010.10.2
8/21/1112:48:43.000AM kernel:NTFS-fs error(device/dev/disk1s1,pid4859):ntfs_system_inodes_get():$LogFile isnotclean.Mounting read-only.Mount inWindows.
All the “cons” can be solved by installing NTFS-3G and keeping it disabled all the time, except when you need to format new volume, or to mount a problematic volume. Actually, it is better to enable NTFS-3G, mount it with NTFS-3G, then unmount, disable NTFS-3G, and mount it with native drivers; or use “ntfsfix” if you are not afraid of command line after all these hacks ;-)
IMPORTANT UPD 12.09.2011: Please read comments below: people say that this driver makes NTFS filesystem corrupted and unusable.
I had the same experience: my NTFS volume become only partially readable in Mac OS X, and completely unusable in Windows. More on that, when I tried to attach the drive, Windows kernel started to use 100% CPU, and did not stop to do so even when the drive were detached. Drive letter never appeared.
Luckily for me, I had two backups of the whole volume (I do so when experimenting with new drives, since I once lost my whole photo archive due to burned out new drive). To solve the whole problem of NTFS@Mac, I’ve finally bought Paragon NTFS for Mac.

0 notes
Text
300+ TOP UNIX FILE MANAGEMENT Interview Questions and Answers
UNIX FILE MANAGEMENT Interview Questions :-
1. Explain what is Standard Unix Streams ? Under normal circumstances every Unix program has three streams (files) opened for it when it starts up − stdin − This is referred to as standard input and associated file descriptor is 0. This is also represented as STDIN. Unix program would read default input from STDIN. stdout − This is referred to as standard output and associated file descriptor is 1. This is also represented as STDOUT. Unix program would write default output at STDOUT stderr − This is referred to as standard error and associated file descriptor is 2. This is also represented as STDERR. Unix program would write all the error message at STDERR. 2. Explain What are links and symbolic links in UNIX file system? A link is the second name for a file. Links are used to assign more than one name to a file, but it cannot be used to assign a directory more than one name or to link file-names on different computers. Symbolic link ‘is’ a file that only includes the name of another file in it. Operation on the symbolic link is may directed to the file pointed by the it. Both the limitations of links are eliminated in symbolic links. Commands use for linking files are: Link “ln filename1 filename2” Symbolic link “ln -s filename1 filename2” 3. Explain What is a FIFO? These are other wisely called as ‘named pipes’. FIFO (first-in-first-out) is a special file can be said to be data transient. Once data is read from named pipe, it cannot be read again. Also, data is read only in the order written. It is used in inter-process communication where a process writes to one end of the pipe and the other reads from the other end. 4. Explain How do you create special files like named pipes and device files? The system called mknod creates special files according to the following sequence. Kernel assigns new inode, It sets the file type for indicating that the file is a pipe, directory or special file, If it is a device file, it makes the other entries like major, minor device numbers. For example: If the device is a disk, major device number always refers to the disk controller and minor device number is the disk. 5. Give a brief idea about representation of devices in UNIX. All devices are represented by files which are called special files that are located in /dev directory. That’s why, device files and other files are named and accessed in the same way. A ‘regular file’ is only an ordinary data file in the disk. A ‘block special file’ represents a device with characteristics similar to a disk. A ‘character special file’ represents a device with characteristics similar to a keyboard.

UNIX FILE MANAGEMENT Interview Questions and Answers 6. Discuss briefly about the directory representation in UNIX. A Unix directory is a file containing and also a correspondence between file names and inodes. A directory is a special file which are maintains by the kernel. Only kernel can modifies directories, but processes can read directories. The contents of a directory are a list of file name and inode number pairs. When new directories are created, kernel makes two entries named ‘.’ and ‘..’ System call for creating directory is mkdir . 7. Explain What are the Unix system calls for I/O? The Unix system calls for I/O are as follows: 1. open (pathname,flag,mode) – open a file 2. creat (pathname,mode) – create a file 3. close(filedes) -to close an open file 4. read(filedes,buffer,bytes) -to read data from an open file 5. write(filedes,buffer,bytes) -to write data to an open file 6. lseek(filedes,offset,from) – position an open file 7. dup(filedes) -to duplicate an existing file descriptor 8. dup2(oldfd,newfd) –to duplicate to a desired file descriptor 9. fcntl(filedes,cmd,arg) -to change properties of an open file 10. ioctl(filedes,request,arg) -to change the behaviour of an open file 11. The difference between fcntl anf ioctl is that the former is intended for any open file, while the latter is for device-specific operations. 8. Discuss the mount and unmount system calls. The privileged mount system call is usually used to attach a file system to a directory of another file system; the unmounted system call is detaches a file system. When we mount another file system on to our directory, we are essentially splicing one directory tree onto a branch in another directory tree. The first argument to mount call is the mount point, i.e, a directory in the current file naming system. The second argument is the file system to mount to that point. When you insert a cdrom to your unix system’s drive, the file system in the cdrom automatically mounts to “/dev/cdrom” in your system. 9. How does the inode map to data block of a file? Inode consists of 13 block addresses. The first 10 which are direct block addresses of the first 10 data blocks in the file. The 11th address points to a 1-level index block. The 12th address points to a 2-level index block. The 13th address points to a 3-level index block. This provides a really large maximum file size with efficient access to large files, but also small files are accessed directly in 1 disk read. 10. Expalin what is ‘inode’? All UNIX files have its description which are stored in a structure called ‘inode’. The inode includes info about the size of file, location of file, time of last access, time of last modification of file, permission to access and so on. Directories are also defined as files and have an associated inode. In addition for describing about the file, the inode includes pointers to the data blocks of the file. If the file is large, inode includes indirect pointer to a block of pointers to additional data blocks. A block is typically 8k. Inode consists of the following fields: File owner identifier File type File access permissions File access times Number of links File size Location of the file data 11. Explain How do we change File Access Permissions? Every file has following attributes in it: owner’s user ID owner’s group ID File access mode word (r w x) – (r w x) – (r w x) (user permission) – (group permission) – (others permission) For changing the access mode, we always use chmod(filename,mode). UNIX FILE MANAGEMENT Interview Questions and Answers free download :: Read the full article
0 notes
Text
dealing with superblock error on linux
I switched on my computer running manjaro linux and encoutered a black screen with the following message:
mount: /new_root: wrong fs type, bad option, bad superblock on /dev/sda2, missing codepage or helper program, or other error. You are now being dropped into an emergency shell. sh: can't access tty; job control turned off [rootfs ]#
Then I burned ISO file onto a USB (the same system and desktop that i had on the laptop) opened command prompt and typed fsck /dev/sda2. fsck is a program that checks filesystem for errors.
How to use fsck to repair filesystem errors in Linux
You cannot run fsck on a disk that is mounted. To check what is mounted, you can use the file manager and go to the /mnt/ folder to see if your disk is there. Or you can run the command mount that shows what devices are mounted. Or you can run lsblk which shows information about block devices, including the mountpoint if there is any. (block device is a computer data storage device, so disk, usb, etc).
Unfortunately fsck did not work and it showed me this message
fsck.ext4: Attempt to read block from filesystem resulted in short read while trying to open /dev/sda2 Could this be a zero-length partition?
Variants of fsck you can try are fsck.ext4 (ext4 is the linux filesystem). I googled a bit and found this resource:
fsck does nothing
So running it with the -f flag (force to check clean) did help. I figured I should get into the sda2 storage, and just take out my files I wanted to save and reinstall Manjaro from scratch. So I tried searching on options how to do that. The sda2 was not mounted so it could not be seen in the file manager from the live USB. So I looked for guidances on how to mount it Unfortunately mount failed and showed the same error as fsck did before.
Looking further I found How to recover from a bad superblock which links to Surviving linux filesystem failures This page tells you to run fsck, well this failed for me, so it says you should try it with some number that says where the superblock is … i guess? like for example e2fsck -f -b 8193 /dev/sda2
If you don’t know what number to use, you should run
mke2fs -n /dev/sda2
now ATTENTION mke2fs is a command that creates a filesystem, wiping out that disk. But! the -n flag means that mke2fs does not actually create a filesystem, but displays what it would do if it were to create a filesystem.
source
It output a bunch of numbers “Superblock backups stored on blocks: 32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632, 2654208, 4096000, 7962624, 11239424, 20480000, 23887872” So following one of the posts from above I tried running the command with the 1st number e2fsck -f -b 32768 /dev/sda2
It started at about 10 AM, it wrote Pass 1 bla bla.. At about 3pm it got to pass 5 then I went away and at about 4:30pm when i came back i saw a prompt asking me if i want to fix something and before that a wall of number codes. I pressed yes a couple times (it said free inodes count wrong for group xxxxx) and then it offered to press a to say yes to all. At the end it said /dev/sda2 **** FILE SYSTEM WAS MODIFIED ****
yes bitch!
So I am in the live session USB, i make a directory called storage2 in /mnt folder. and type mount /dev/sda2 /mnt/storage2 into the terminal. Now I can open this in the file explorer and see basically all the directories like bin, boot, dev, etc, home, lib, lib64, mnt, opt etc etc. Home is where my super precious files are. Like 1GB of pictures of some boy and a couple rare movies i illegally downloaded.
I inserted a sd card stuck in a usb sd card reader into the laptop, after doing lsblk it was listed there as sdc partitioned to sdc1 and sdc2. So i mounted it with mount /dev/sdc2 (the bigger one ) onto /mnt/temp. For some reason I couldnt create a copy files in the file manager there, so i had to be logged in as root in the terminal this whole time and do mkdir /mnt/temp and copy the files with cp -vr /mnt/storage2 /mnt/temp where /mnt/storage2 is the mountpoint of dev/sda2. After being done with backing up my files, I unmounted the sd card with umount /dev/sdc2 and the sda2 disk, opened GParted to do the partitions….. and snap. sda2 has the same error I started with, eg the short read error. So I ran e2fsck -f -b 32768 /dev/sda2 all over again. This time it goes by a little faster, 10 minutes elapsed and I am at Pass 5 and there was 1 error on Pass 1.
Now let’s learn something about partitioning.
You generally want to create 3 parittions when installing a Linux system:
Root: this is where the filesystem goes, and it is required to boot a Linux system.
Home: holds user and configuration files separate from the operating system files.
Swap: when the system runs out of RAM, the operating system moves inactive pages from RAM into this partition. It is also useful if you want to use functions like hibernate or suspend which is something like sleep in windows. It should be twice the size of RAM if RAM is less than 2GB, or the same size as RAM.
All partitions must be unmounted in order to be modified (this means you cannot resize a partition on a working system (since it is obviously mounted)). To create a new partition, you must have some unallocated space.
Manjaro installer manual partitioning. – all partitions that have a mount point specified will be used during the installation of Manjaro. !!! swap should have a linuxswap filesystem all others that you wish to access from linux can have ext4. Also, specifically for Manjaro, EFI system partition is necessary to start Manjaro. So you need to create a partition with the FAT32 filesystem, mount point /boot/efi and esp flag enabled.
The resulting partitions I did can be seen on this image:

I had some of the backup files on sda4 that is NOT mounted so that it was not touched during the re-installation of Manjaro.
In the Manjaro wiki They talk about primary and Extended partitions and that there can only be 4 primary partitions. The GParted gui talked about primary partitions on my drive, and my drive is GPT. But, GPT does not have a concept of primary partitions, it has only partitions and it can have about 128 of them. Extended partitions are only available on an MBR disk.
some useful commands
sudo su to get to root mode
exit to exit root mode
cp -rv foo bar copy directory foo and its contents to directory bar and print output on screen
rm -rf foo remove directory foo and its contents
lsblk to list disk and partitions plus some info
0 notes
Text
SA Wk1: Operating Systems
Having 0 knowledge in Operating Systems at all, I delve into the land of YouTube to get some insight into some of the key concepts which will be relevant to rootkit implementation.
Threads vs Processes
A process refers to an instance of a program being executed.
Threads are referred to as lightweight processes. Multiple threads run within a process in a shared memory space, each carrying out different functions within process.
System Calls
When a program is executed, it is either executed in user mode or kernel mode. When a program is executing in user mode, it does not have direct access to memory, hardware input, and other such resources. On the other hand, in kernel mode the system is privileged and does have direct access to these resources.
However, the issue with operating in kernel mode is that if a program crashes whilst in mode, the entire system will crash. This is not the case with user mode. As a result, programs are normally executed in user mode and when the program requires access to certain resources, it makes a system call to the kernel, at which point the program execution switches to kernel mode and the relevant operations are carried out, before switching back.
There are 5 main categories of system calls;
Process control
End, abort
Load, execute
Waiting
Allocating, freeing memory
File manipulation
Read
Write
Open, close
Delete
Device manipulation
Request, release device
Logically attach, detach device
Information maintenance
Get, set:
Time, date
System data
File, device attributes
Communications (mainly between processes)
Create, delete communication connection
Send, receive messages
Transfer status
Attach, detach remote devices
Interesting: Unix treats I/O devices like files hence manipulation of the two share many system calls
File System Implementation
A file system refers to how files and directories are organised on a disk. An operating system has multiple file systems. There are 2 main features of file systems;
Data structures to organise files and metadata
Implementation of system calls using data structures
Consider a simple file system;
Inodes
Stores metadata and pointers to data bocks for files
Organised into inode blocks
Typically stored in array
A file’s inode number is index into array
Bitmaps
Indicate which inode/data blocks are free
Alternatively, free list where pointer to next free block is stored in each node
Data blocks
Store the actual file, or parts of it
Files/parts of file not necessarily stored in order
Superblock
Holds data about the other blocks, eg. indicates which blocks are data and which are inodes
Directory
Is a special type of file
Stores mapping of filenames to inode number
May be linked list, hash table, binary tree, etc.
Has inode and data blocks
Opening a file;
Opening means the inode for a particular file is readily available for operations (read, write, etc.)
Opening returns a file descriptor pointer to the inode for easy access
To open, pathname of file is traversed, starting as root
Recursively fetch the inode of parent directory, read its data block, get inode number of child, fetch inode of child, until end of directory path
If new file, inode/data blocks are simply allocated and directory path updated
Global open file table has an entry for every open file, pointing to copy of inode
Necessary if multiple processes want to open the same file
Per-process open file table is specific to every running process
File descriptor number for an open file is index into this array
Entries in array are pointers to entries in the global open file table
std in/out/err always open by default
Hence opening a file creates entries in both tables, and returns a file descriptor
Virtual File Systems;
A VFS treats a file system as objects (files, directories, inodes, etc.) and operations on these objects (opening file, searching file, etc.). System calls are then written on these objects. Hence developing a file system involves just writing functions to manipulate these objects and providing the kernel with pointers to these functions. As a result, the file system is abstracted and syscall implementation doesn’t need to change with changes in file system implementation.
Kernel Modules
Recall that the kernel has direct access to resources such as the CPU, memory, devices, etc. The point of kernel modules is to provide this access.
Some basic cmd line commands that may be useful later;
lsmod - lists all loaded modules
lnsmod - install a specific module
modprobe - loads a module and dependencies
rmmod - removes a module
Rootkits
A rootkit is a set of software installed on a system designed gain access to and do stuff (usually malicious) to the system without being detectable.
*EDIT*See here for more on some real life rootkits: https://jmess-6841.tumblr.com/post/186597848009/rootkit-forensics-workshop
0 notes
Text
Top 5 Advantages of Dedicated Server Hosting
TOP 5 ADVANTAGES OF DEDICATED SERVER HOSTING
Individuals and businesses of various sizes are often faced with a large array of selections when it comes to choosing their server hosting provider. There are many different options, however, the most common is shared hosting. Shared hosting is a type of hosting architecture that splits a single servers resources between a large number of different users. Individuals and businesses that are serious about their online presence or are worried about downtime for their website, mail server, game server, or other web applications are taking advantage of managed dedicated server hosting services.
There are a few key advantages of dedicated server hosting services versus shared hosting that we are going to cover in this post.
Read on to see our list of the Top 5 Advantages of Dedicated Server Hosting:
1. Dedicated Servers Have Unrestricted Access To Resources

Unlike shared hosting services that oversell their server resources to make a few extra bucks, dedicated server hosting is entirely for the owner or user. When hosting with a shared hosting provider, all the hardware and server resources are split unevenly between the multiple users on the same machine. This can be a problem for those that don’t want to compete for resources with other users on the server, especially if you’re unlucky enough to have a shared hosting neighbor that is sending out spam, big mailing lists, and other resource intensive processes.
When choosing to host your server, it’s important to bear in mind the resources you expect to be using in the present and in the future. Picking a dedicated server over shared hosting is a good idea for those that are concerned about increased reliability, enhanced security, and an overall better experience. When sharing server resources with others, your peak time might align with another on your server, and it might cause a negative user experience. Dedicated servers will always ensure that users are getting peak performance during peak usage times.
Dedicated servers are a good pick because resources aren’t shared between users like with shared hosting. This is good for businesses and individuals that don’t want to have their website bogged down by bandwidth spikes caused by other users sharing the server. This is especially important for businesses of all sizes as server downtime can mean that your website or application is offline and not working correctly for your users or visitors.
“As of December 2017, 24 percent of respondents worldwide reported the average hourly downtime cost of their servers as being between 301,000 and 400,000 U.S. dollars.” — Statista
2. Dedicated Servers Have IP Addresses That Are Unique

Comparing a dedicated server to shared hosting, there are quite a few advantages, one of which is unique IP addresses. With shared hosting servers, users are put onto the same machine and required to share resources between one another. Not only do users have to share resources with traditional shared hosting, but they also share the same IP address as all the other users on the server. This could mean that, if all the users are running websites, and one website gets targeted by a dedicated denial of service attack, all the other websites sharing the same IP address would be affected by it as well.
When businesses and individuals choose to host on a dedicated server, they can be sure that they’re getting all the resources to themselves as well as a dedicated IP address. Not only do users of dedicated servers get their own resources and IP address, but it’s also possible to add additional IP addresses if needed. Dedicated servers offer increased functionality, better performance, and enhanced security.
It’s advantageous to have a dedicated IP address for a professional website because when users are on a shared hosting plan, using the same IP address, it can affect website rankings. This could be bad for a professional company that has a business website with the same IP address as an adult or spam site. Having a dedicated IP address is important for those considering running a large scale e-commerce site which requires transport layer security (TLS) for processing credit card transactions.
3. Dedicated Servers Have Increased Flexibility Over Shared Hosting

While it’s true that dedicated servers aren’t as flexible as far as scalability when compared to a virtual private server, it’s also true to say that dedicated server hosting is a step in the right direction for shared hosting users.
Dedicated servers offer the individuals and businesses that use them the ability to customize their machine. This means that certain hardware can be swapped out or upgraded if need be to fit the requirements of the user. Typically with shared hosting, customers are limited to the already preinstalled or pre-configured applications and software that’s already installed on the shared server. With a dedicated server, it’s possible to install whatever applications and software is required for your growing enterprise. Since dedicated servers are highly customizable, it’s possible to have multiple separate dedicated servers working together or separately. Multiple different dedicated servers can be configured to run separate pieces of software, for example, one could be solely for sending mail, while another could be for database management, and another for web hosting. When it comes down to it, the flexibility of dedicated servers is a great improvement over the confines of a shared hosting server.
Dedicated servers are great for rapidly growing enterprises and small businesses. They are excellent for those that want to manage their website and data in a reliable location where their users will always have access to it. Dedicated servers also offer increased storage, processing, and network speeds over shared hosting solutions.
It’s usually wise for businesses, developers, and other individuals seeking professional server hosting to consider a dedicated server environment over shared hosting because of the increased flexibility. Users of a dedicated server can configure their server how they see fit and with whatever operating system they like. Businesses and individuals choose managed dedicated server hosting when they want to have more control and flexibility over their server resources.
4. Dedicated Servers Offer Increased Security and Performance

It’s very common for many shared hosting services to advertise certain specifications for their server but not actually be able to live up to them. This is because many shared hosting services use a tactic called “Overselling“. The overselling occurs when a shared host puts more customers than resources on a server that must be shared. Since the web host knows that all the users won’t be using utilizing the full potential of their plan all the time, they oversell the resources in an attempt to pack in as many people as possible and save on costs for increased profits. You can spot shared hosting providers when they advertise Inode limits.
Users of dedicated servers don’t have to worry about their resources being oversold as their dedicated server is entirely their own to use and not shared with anyone else.
Since dedicated servers aren’t shared between multiple users, it can certainly put your mind at ease when it comes to server security. Businesses and large websites don’t want to be sharing their server with multiple random neighbors, no, they want enhanced security that comes from them being the only one with access to their server. Businesses and individuals that choose to host with a professional dedicated server hosting services can relax knowing that they aren’t sharing resources or IP addresses with potential malicious websites, illicit adult content sites, or email spammers. Dedicated servers offer increased security over shared hosting, this could be vital for websites seeking to handle sensitive information over FTP or SSL and is important for transactions online using credit cards.
Professional dedicated server hosting services will also be able to protect your dedicated server by having them protected by firewalls and live security monitoring. This is important because it can offer greater security against hackers and malicious scripts seeking to impede or exploit your server. Large companies to small scale businesses and individuals want to be focusing on their work, not on maintaining the security of their server and worrying about keeping their data safe.
Because dedicated servers are highly flexible and customizable, it’s possible to implement custom security rules, install security applications, and more. Dedicated servers offer the best choice for those concerned about server access control and enhanced firewall protection.
5. Dedicated Server Hosts Have Exceptional Reliability & No Maintenance Costs

Choosing to host on a dedicated server is a good idea for those worried about the needs of their business, website, or other web application. When it comes to selecting a hosting option though, for those considering dedicated servers, there are some other things to be aware about.
Dedicated hosting is an option for those interested in hosting a dedicated server, but for those that don’t want to purchase the hardware and configure everything themselves. This is where a dedicated server hosting provider comes in. When you opt to host with a dedicated server hosting provider, you will experience all the benefits but with no additional overhead costs besides renting the server itself. Dedicated server hosting companies are responsible for housing the physical servers in data centers that are physically guarded and staffed 24/7. When choosing to host a dedicated server through a hosting provider, the users can just focus on running their website and server, while the server host takes care of all server maintenance, hardware replacements, server hosting costs, data center maintenance, and much more.
Companies and individuals that don’t have the time or resources to manage a server themselves might want to consider dedicated server hosting. Dedicated server hosting is an affordable option for those looking to access and implement the full range of their server resources without having to handle the cost of physical maintenance or worry about downtime and hardware replacement. Most dedicated server hosting companies offer a guaranteed uptime so users and businesses know that their server is always up and running.
Not only can it be expensive to manage your own dedicated server, but it can also be costly if assistance is needed such as support. Many dedicated server hosting services will not only manage your server but they can also provide assistance and technical support for free or for a price. Find out what kind of support you need when seeking out a new dedicated server, and check what web software and server applications are supported. Businesses and individuals would be wise to take advantage of the technical assistance benefits that a managed server hosting company can provide, as well as the bonuses that troubleshooting around the clock might have.
If you’re a business or individual looking for a new web hosting experience, consider switching to a dedicated server to take the next step in growing your enterprise.
#astral servers#dedicated server hosting#dedicated servers vs shared hosting#managed dedicated server hosting#top 5 dedicated server
0 notes
Text
Top 5 Advantages of Dedicated Server Hosting
TOP 5 ADVANTAGES OF DEDICATED SERVER HOSTING
Individuals and businesses of various sizes are often faced with a large array of selections when it comes to choosing their server hosting provider. There are many different options, however, the most common is shared hosting. Shared hosting is a type of hosting architecture that splits the resources of a single server between a large number of different users. Individuals and businesses that are serious about their online presence or are worried about downtime for their website, mail server, game server, or other web applications are taking advantage of managed dedicated server hosting services.
There are a few key advantages of dedicated server hosting services versus shared hosting that we are going to cover in this post.
1. Dedicated Servers Have Unrestricted Access To Resources
Comparing a dedicated server to shared hosting, there are quite a few advantages, one of which is unique IP addresses. With shared hosting servers, users are put onto the same machine and required to share resources with one another. Not only do users have to share resources with traditional shared hosting, but they also share the same IP address as all the other users on the server. This could mean that, if all the users are running websites, and one website gets targeted by a dedicated denial of service attack, all the other websites sharing the same IP address would be affected by it as well.
When businesses and individuals choose to host on a dedicated server, they can be sure that they’re getting all the resources to themselves as well as a dedicated IP address. Not only do users of dedicated servers get their own resources and IP address, but it’s also possible to add additional IP addresses if needed. Dedicated servers offer increased functionality, better performance, and enhanced security.
It’s advantageous to have a dedicated IP address for a professional website because when users are on a shared hosting plan, using the same IP address, it can affect website rankings. This could be bad for a professional company that has a business website with the same IP address as an adult or spam site. Having a dedicated IP address is important for those who are considering running a large scale e-commerce site which requires transport layer security (TLS) for processing credit card transactions.
2. Dedicated Servers Have IP Addresses That Are Unique
Comparing a dedicated server to shared hosting, there are quite a few advantages, one of which is unique IP addresses. With shared hosting servers, users are put onto the same machine and required to share resources between one another. Not only do users have to share resources with traditional shared hosting, but they also share the same IP address as all the other users on the server. This could mean that, if all the users are running websites, and one website gets targeted by a dedicated denial of service attack, all the other websites sharing the same IP address would be affected by it as well.
When businesses and individuals choose to host on a dedicated server, they can be sure that they’re getting all the resources to themselves as well as a dedicated IP address. Not only do users of dedicated servers get their own resources and IP address, but it’s also possible to add additional IP addresses if needed. Dedicated servers offer increased functionality, better performance, and enhanced security.
It’s advantageous to have a dedicated IP address for a professional website because when users are on a shared hosting plan, using the same IP address, it can affect website rankings. This could be bad for a professional company that has a business website with the same IP address as an adult or spam site. Having a dedicated IP address is important for those who are considering running a large scale e-commerce site which requires transport layer security (TLS) for processing credit card transactions.
3. Dedicated Servers Have Increased Flexibility Over Shared Hosting
While it’s true that dedicated servers aren’t as flexible as far as scalability when compared to a virtual private server, it’s also true to say that dedicated server hosting is a step in the right direction for shared hosting users.
Dedicated servers offer the individuals and businesses that use them the ability to customize their machine. This means that certain hardware can be swapped out or upgraded if need be to fit the requirements of the user. Typically with shared hosting, customers are limited to the already preinstalled or pre-configured applications and software that’s already installed on the shared server. With a dedicated server, it’s possible to install whatever applications and software is required for your growing enterprise or personal project. Since dedicated servers are highly customizable, it’s possible to have multiple separate dedicated servers working together or separately. Multiple different dedicated servers can be configured to run separate pieces of software, for example, one could be solely for sending mail, while another could be for database management, and another for web hosting. When it comes down to it, the flexibility of dedicated servers is a great improvement over the confines of a shared hosting server.
Dedicated servers are great for rapidly growing enterprises and small businesses. They are excellent for those that want to manage their website and data in a reliable location where their users will always have access to it. Dedicated servers also offer increased storage, processing, and network speeds over shared hosting solutions.
It’s usually wise for businesses, developers, and other individuals seeking professional server hosting to consider a dedicated server environment over shared hosting because of the increased flexibility. Users of a dedicated server can configure their server how they see fit and with whatever operating system they like. Businesses and individuals choose managed dedicated server hosting when they want to have more control and flexibility over their server resources.
4. Dedicated Servers Offer Increased Security and Performance
It’s very common for many shared hosting services to advertise certain specifications for their server but not actually be able to live up to them. This is because many shared hosting services use a tactic called “Overselling“. The overselling occurs when a shared host puts more customers than resources on a server that must be shared. Since the web host knows that all the users won’t be utilizing the full potential of their plan all the time, they oversell the resources in an attempt to pack in as many people as possible and save on costs for increased profits. You can spot shared hosting providers when they advertise Inode limits.
Users of dedicated servers don’t have to worry about their resources being oversold as their dedicated server is entirely their own to use and not shared with anyone else. Dedicated servers also come with root access while many shared servers do not.
Since dedicated servers aren’t shared between multiple users, it can certainly put your mind at ease when it comes to server security. Businesses and large websites don’t want to be sharing their server with multiple random neighbors, no, they want enhanced security that comes from them being the only one with access to their server. Businesses and individuals that choose to host with a professional dedicated server hosting services can relax knowing that they aren’t sharing resources or IP addresses with potential malicious websites, illicit adult content sites, or email spammers. Dedicated servers offer increased security over shared hosting, this could be vital for websites seeking to handle sensitive information over FTP or SSL and is important for transactions online using credit cards.
Professional dedicated server hosting services will also be able to protect your dedicated server by having them secured by firewalls and live security monitoring. This is important because it can offer greater security against hackers and malicious scripts seeking to impede or exploit your server. Large companies to small scale businesses and individuals want to be focusing on their work, not on maintaining the security of their server and worrying about keeping their data safe.
Because dedicated servers are highly flexible and customizable, it’s possible to implement custom security rules, install security applications, and more. Dedicated servers offer the best choice for those concerned about server access control and enhanced firewall protection.
5. Dedicated Server Hosts Have Exceptional Reliability & No Maintenance Costs
Choosing to host on a dedicated server is a good idea for those worried about the needs of their business, website, or other web application. When it comes to selecting a hosting option though, for those considering dedicated servers, there are some other things to be aware of.
Dedicated hosting is an option for those interested in hosting a dedicated server, but for those that don’t want to purchase the hardware and configure everything themselves. This is where a dedicated server hosting provider comes in. When you opt to host with a dedicated server hosting provider, you will experience all the benefits but with no additional overhead costs besides renting the server itself. Dedicated server hosting companies are responsible for housing the physical servers in data centers that are physically guarded and staffed 24/7. When choosing to host a dedicated server through a hosting provider, the users can just focus on running their website, project or server, while the server host takes care of all server maintenance, hardware replacements, server hosting costs, data center maintenance, and much more.
Companies and individuals that don’t have the time or resources to manage a server themselves might want to consider dedicated server hosting. Dedicated server hosting is an affordable option for those looking to access and implement the full range of their server resources without having to handle the cost of physical maintenance or worry about downtime and hardware replacement. Most dedicated server hosting companies offer a guaranteed uptime so users and businesses know that their server is always up and running.
Not only can it be expensive to manage your own dedicated server, but it can also be costly if assistance is needed such as support. Many dedicated server hosting services will not only manage your server but they can also provide assistance and technical support for free or for a price. Find out what kind of support you need when seeking out a new dedicated server, and check what web software and server applications are supported. Businesses and individuals would be wise to take advantage of the technical assistance benefits that a managed server hosting company can provide, as well as the bonuses that troubleshooting around the clock might have.
If you’re a business or individual looking for a new web hosting experience, consider switching to a dedicated server to take the next step in growing your enterprise.
Originally Published JANUARY 7, 2019
#advantages of dedicated servers#astral servers#top 5 dedicated servers#dedicated server hosting#reasons to choose dedicated server hosting#dedicated servers advantages
0 notes
Text
A2 Hosting Black Friday Deals are one of the awaited deals of the yr. That is the time when A2 Hosting supplies steepest discounts on their website hosting merchandise together with Shared Hosting, VPS Hosting and Reseller Hosting.
So, without wasting any time allow us to get straight to the A2 Hosting Black Friday gives for 2018. For individuals like me who’re lazy to scroll, under table exhibits the summary of the supply. The detail seekers can read on.
A2 Hosting Black Friday Deals Summary
A2 Hosting is but to announce the A2 Hosting Black Friday Supply for 2019. The article under is for the 2018 edition of A2 Hosting Black Friday deal. We’ll update this article as and when A2 Hosting broadcasts the offers
A2 Hosting Black Friday Deals
Through the Black Friday Net Hosting sale, each hosting company supplies their greatest discounts for the yr. A2 Hosting is certainly not going to be left behind.
This yr, the A2 Hosting Black Friday Deal will go stay on 21 November 2018 and can run via Cyber Monday to end on 27 November 2018.
1. Shared Hosting And Managed WordPress Hosting
Through the Black Friday Sale of 2018, A2 Hosting is providing 67% flat low cost on all their Shared Hosting plans as well as Managed WordPress Hosting plans. The shared hosting plans begin at a worth of just $1.98/month.
You’ll be able to click the button under to go to the A2 Hosting Web page. Coupon code SAVEBIG shall be mechanically applied to your cart when the deal goes stay.
2. VPS Hosting Plans
In case you are trying to buy a Managed VPS or Core VPS, you will get a flat low cost of 50% through the Black Friday Sale. Nevertheless, the low cost is NOT out there for Unmanaged VPS.
You’ll be able to go to the under buttons to go to the related web page and use coupon code BLKVPS just in case it isn’t mechanically utilized.
3. Dedicated Server
In contrast to the earlier yr, this yr, A2 Hosting can also be offering reductions on their devoted servers. You possibly can avail up to 50% discount on selective devoted servers through the use of the coupon code 50DEDI.
Nevertheless, the coupon code is relevant only on the discount devoted servers. Clicking the button under will take you on to the Discount Devoted Servers page.
4. Reseller Hosting
For A2 Hosting Reseller Hosting Accounts, you get 40% off the common worth through the use of the Coupon Code RSL40.
About A2 Hosting
A2 Hosting was launched means back in 2001 by Bryan Muthig. It is likely one of the greatest internet hosting company that provides completely configured, SSD based mostly shared hosting servers at a really affordable worth.
With knowledge facilities within the US, Europe as well as Asia, A2 Hosting is appropriate for webmasters, bloggers and businesses from the world over. They’re one of many few corporations which are not owned by the EIG Group or GoDaddy.
Which A2 Host Friday Black Friday Supply To Choose?
With so many hosting options obtainable with A2 Hosting, you could be confused about what choice to pick. So let me clarify in short all of the plans along with their benefits.
1. A2 Hosting Shared Hosting
As the identify suggests, on the Shared Hosting plan of A2 Hosting, you share the server assets with a number of different websites. With each internet hosting plan at A2 Hosting you’ll get certain limits for server assets.
The above restriction is only a guideline. Your website can still expend assets greater than the prescribed assets for each plan. Nevertheless, in case your web site is commonly crossing those limits, you will have to upgrade your plan.
It does appear to be a great deal when you should use extra server assets now and again. Nevertheless, because the server assets are shared, if one other web site on the server makes use of loads of assets, it’ll affect the efficiency of your web site.
Subsequently, a shared hosting plan is often appropriate for websites with low to medium visitors. For E-commerce and different crucial web sites, I do not advocate shared internet hosting as it will probably result in loss of sales in case your web site masses slowly or goes down on account of server load.
A2 Hosting provides three totally different shared hosting plans. You possibly can select the one which fits your requirements.
a. Lite Plan
The Lite plan is probably the most primary plan at A2 Hosting. This plan is right in case you are just starting your weblog or enterprise website. This plan can also be suitable for business who don’t anticipate a number of visitors to their website.
With the lite plan you’ll be able to host one single website and 5 sub-domains. As for the storage and Bandwidth, A2 Hosting doesn’t prohibit the identical however is subject to their Truthful Utilization Policy.
The MySQL databases are restricted to 5, which is adequate in case you are internet hosting a single WordPress web site. It’s also possible to create as much as 25 cPanel e mail ids for your corporation.
The under desk exhibits the month-to-month in addition to complete pricing of A2 Hosting Lite plan for different durations.
b. Swift Plan
The Swift plan is sweet for Bloggers and Small enterprise house owners who need to host multiple websites. This plan is powered by 2 CPU cores clocked at 2.1 Ghz and supplies 1 GB of RAM which is twice that of the Lite Plan.
With the swift plan, you also have an option to double the CPU cores and add further 1GB RAM at an extra value of $Three/month (You get a discount on this worth as properly). So in case you are getting an honest quantity of visitors to your blog or in case you are anticipating your blog visitors to increase shortly in the course of the next few months, this plan is right for you.
Aside from the RAM and Inodes, there isn’t any restriction on this A2 hosting plan. In fact, the truthful usage limits nonetheless apply on this plan.
In contrast to the Lite plan, swift plan additionally presents server rewind backups. So all in all, the swift plan is certainly a more sensible choice if you do not mind spending few additional bucks.
The table under exhibits pricing of Swift plan for various durations along with efficient discounts
c. Turbo Plan
The Turbo plan is the quickest shared internet hosting plan by A2 Hosting. This plan is really helpful for relatively high visitors websites, E-commerce websites and other web sites for which page load occasions are a essential issue.
The Turbo plan can handle medium visitors websites as it offers 2 GB of RAM which is double than what is accessible with the swift plan. Like with Swift plan, you additionally get an choice so as to add further 1GB Ram for $Three/month.
The Turbo plan has it’s own caching system which may make you website load very fast. With the Turbo Plan you also get Railgun Optimizer totally free which is charged at $1.98/month with the opposite two shared internet hosting plans.
You’ll be able to examine the table under for pricing of Turbo Hosting Plan for various durations.
2. A2 Hosting Managed WordPress Hosting
If you don’t want to get into the hassles of managing and optimizing your personal Linux Server, you possibly can choose to go together with A2 Hosting’s Managed WordPress Hosting Plan.
In contrast to the Linux Hosting, the Managed WordPress Hosting is powered by the Plesk Control Panel. So, in case you are particularly searching for cPanel, you will have to go together with the Linux Hosting plan.
A2 Hosting gives three totally different Managed WordPress Hosting Plans depending on the number of websites you need to host. Aside from the variety of web sites, the storage, the variety of CPU cores in addition to Physical and digital reminiscence also varies with each plan.
The 1-Website hosting plan provides you 10 GB SSD Storage and provides you entry to 2GB physical RAM, 8GB Virtual RAM and a couple of CPU cores. For the Three-Website internet hosting plan the corresponding values are 25 GB SSD, Three GB Bodily RAM, 12 GB Virtual RAM and three CPU cores.
The Unlimited web site plan comes with 40 GB SSD, four GB Bodily RAM, 16 GB Virtual RAM and 4 CPU Cores.
Each of those Plans include the Turbo Increase included in the pricing. So you’ll be able to anticipate blazing quick website load occasions.
3. VPS Hosting
A Virtual Personal Server or VPS is a server that hosts a number of accounts on the same server like shared hosting. Nevertheless, every of these accounts is allotted their very own Digital assets and they don’t seem to be shared with other accounts. So, different websites on the internet hosting server won’t affect your website in any method.
A VPS is able to handling extra visitors than shared internet hosting. It is very best for site owners, bloggers, E-commerce websites and small companies that get medium to high visitors.
A2 Hosting gives self-managed VPS, Managed VPS as nicely Core Managed VPS. Allow us to understand the distinction between the three of them and which one do you have to get.
a. Self Managed VPS
As the identify suggests, with the Self Managed VPS, you’ll be need to managed your personal server. You’ll be able to both set up WordPress or some other software of your selection utilizing the command line or you possibly can install the free Webuzo Management Panel that’s provided A2 Hosting.
The Webuzo control panel could be very very similar to cPanel and is from the makers of Softaculous. It comes with free Softaculous installer that may show you how to install several purposes like you do with cPanel based mostly shared internet hosting.
With self-managed VPS, you also have the choice to install cPanel. Nevertheless, you’ll have to pay additional for the cPanel license. Through the A2 Hosting Black Friday sale of 2017, A2 Hosting determined not to supply any discounts on the Self Managed VPS because it already obtainable at a very low cost price of simply $5/month for a 512 MB server.
b. Managed VPS
As the identify suggests, the Managed VPS is managed by the A2 Hosting group and comes with a free cPanel. Securing the server and updating the hardware as well as software is all inside the scope of A2 Hosting Workforce and you do not get any root access.
Because the hosting uses a cPanel, you get all the options you get with cPanel on the shared internet hosting. Turbo Increase is out there at a further worth of $22 (Only LiteSpeed) and $30 (LiteSpeed with LSCache and LiteMage.
At A2 Hosting, reductions are applied on the ultimate worth, so that you get discounts even on whatever further providers you add to your internet hosting card together with Turbo Increase, Railgun Optimizer, Softaculous Premium and so on.
c. Core Managed VPS
Core Managed VPS is strictly just like Managed VPS besides that you simply get root entry in case you want to tweak the settings of the server. The features as well as pricing of Core Managed VPS are just like Managed VPS apart from a number of exceptions.
The Core Managed VPS doesn’t embrace CloudFlare CDN within the cPanel. You additionally do not get choice to purchase Railgun Optimizer. Another distinction is the shortage of Server rewind file backups with the Core Managed VPS.
four. Devoted Server Hosting
VPS is an effective and low cost choice for medium visitors web sites. Nevertheless, in case your website will get numerous visitors and the VPS is just not adequate to handle the identical or in case you are managing a crucial undertaking that requires extra safety, Dedicated Server can be a super selection for you.
Like VPS Servers, A2 Hosting supplies dedicated servers with three management ranges, Unmanaged, Managed and Core Managed. The corresponding plans are named as Flex Unmanaged, Flex Managed and Flex Core dedicated servers.
Along with the above, A2 Hosting also gives Discount SSD Servers that are absolutely managed with root access identical to the Flex Core server however comes with less space for storing. Although, their pricing is larger than Flex Core Server, they’re provided at a huge discounts which brings down it’s pricing lower than the Flex Core server and therefore the identify Low cost SSD Server.
Every of the above plans present 3 times of servers, Intel Core I3, Intel Xeon E3 and Intel Xeon E5. Regardless of the kind of management or the type of server, you possibly can configure the servers to as per your needs with the server RAM starting from 8GB to 32 GB.
With the A2 Hosting Black Friday Deal, you solely get low cost on the Low cost SSD Dedicated Servers.
5. Reseller Hosting
As the identify suggests, the Reseller internet hosting accounts permit you to resell A2 internet hosting servers underneath your brand identify. You’ll be able to determine your personal worth for selling these accounts.
The Reseller account is right for developers who need to promote the hosting to their shoppers along with the website improvement and upkeep providers. It’s also possible to use it to start out your website hosting enterprise.
A2 Hosting gives four totally different Reseller Hosting plans, Bronze, Silver, Gold and Platinum. The primary difference between these plans is the number of shoppers allowed accounts which you could host on the server and the server assets out there.
A2 Hosting additionally presents free WHCMS starter license with all plans besides the Bronze plan. Rest of the options are equivalent with every of the above plans.
I am positive by now you have to be clear about numerous A2 Hosting Black Friday gives and decided to buy certainly one of them. Nevertheless, in case you are still not very positive, you possibly can verify the top explanation why you need to purchase A2 Hosting Black Friday Plans
Causes For Getting A2 Hosting Black Friday Deals
Under are the highest causes to get the A2 Hosting Black Friday Supply. Please observe, most of those options are for Shared Hosting solely.
1. Highest Discounts
Whether you need to purchase Shared internet hosting, VPS Hosting or Reseller Hosting, get the very best low cost of the yr for A2 Hosting products through the supply period.
2. Velocity
Be certain that your website masses faster than your rivals with highly optimized servers from A2 Hosting. Google too loves fast loading websites which can help your web site rank greater.
The Turbo Plan for shared internet hosting and the Turbo increase choice for VPS hosting uses caching that hastens your website load time. The Turbo plan additionally comes with free Railgun optimizer for caching the dynamic content. That is helpful for dynamic websites whose content material modifications typically.
Three. SSD Storage
All of the A2 Hosting plans include free Full SSD servers which are quicker than the normal exhausting disks. This further improves your website load time and allows the server to deal with more visitors.
four. Prime Class Hosting Infrastructure
A2 Hosting makes use of prime class internet hosting Infrastructure that features 10Gbps redunant community. The servers use have minimum 12 cores and 64 GB RAM.
5. Pre Put in WordPress
With A2 hosting, you have got the choice to get clean servers or servers with WordPress pre-installed on it. You may as well choose to get servers with A2 Optimized WordPress installed on it. The optimized version is right for novices who can’t optimize WordPress by themselves.
6. Free SSL Certificate
In response to Google, SSL certificates are a must for any web site that collects private knowledge like Identify, E mail, Credit Card information, and so forth. Without SSL, trendy browsers warn users that their knowledge just isn’t protected on the website once they try to refill a type.
In contrast to many other hosting corporations, A2 Hosting supplies free Let’s Encrypt SSL certificates. This saves you some money for purchasing SSL.
7. Free Again-Ups
With server rewind backups, A2 internet hosting routinely creates snapshots of your weblog which you’ll be able to restore if something goes incorrect together with your blog.
8. CloudLinux OS For Shared Hosting
A2 Hosting makes use of Cloud Linux OS that helps to isolate accounts on the shared hosting setting. This helps control server resource spikes.
So, your web site won’t be affected a lot if one other web site on the server starts getting lots of visitors.
9. Strategically Positioned Knowledge Centers
A2 Hosting has two knowledge centers within the US at Michigan and Arizona. Additionally they have knowledge facilities at Amsterdam in the Europe and Singapore in Asia.
The strategically positioned knowledge centers throughout three continents make sure that you’ll find a knowledge middle close to your audience which can help scale back the latency.
10. Buyer Help
A2 offers awesome customer help which, although not greatest, is best than most hosting corporations. Their buyer help brokers are educated sufficient to unravel your queries in a fast time.
I’m positive these are purpose sufficient for anybody to grab the A2 Hosting Black Friday Deal . So hit the button under to get A2 Hosting.
Last Phrases
A2 Hosting is definitely the most effective within the webhosting business. And when you love velocity, there’s no higher shared internet hosting supplier than A2 hosting.
Their plans sound much more lucrative with the Black Friday provides. Until you’re very tight on price range and on the lookout for a Low cost $1 Hosting, there’s no purpose you need to maintain your self again from getting the A2 hosting Black Friday Deal
If in the uncommon case you do not just like the A2 Hosting Black Friday Deal, you’ll be able to take a look at the Greatest Black Friday Deals Of 2018. For Managed WordPress Hosting, you’ll be able to contemplate WPX Hosting Black Friday Deals
The post A2 Hosting Black Friday Sale 2019 appeared first on Tactics Socks.
0 notes
Link
via RSS feed - SEOCheckOut The domain is not included... With the Shared hosting, you will receive a cPanel Control Panel to manage all your domains for your own personal use. Use your current domain or Get a new domain from Godaddy, Namecheap, 1and1, Exabyte, Namesilo, etc. Featuring cPanel with Auto SSL ready ( Automatic Assign By cPanel To All Domains ) Server - US WORDPRESS SHARED HOSTING: With Preinstalled WordPress Premium Theme & Plugins - This is one-time installation and for one website only! Standard Hosting Plan Configuration: .Unmetered Bandwidth.Unlimited Databases.Unlimited Parked Domains.Unlimited Addon Domains - Host Unlimited Websites.Unlimited FTP Account.Unlimited Email Accounts.Softaculous Script Installer.cPanel Control Panel with Auto SSL ready(No need manual adding SSL certificate).Free DDOS Protection Hosting Plan Pricing YCH Basic Plan with 50GB Disc Space is $5YCH Pro Plan with 300GB Disc Space is $10 YCH Gold Plan with 1TB Disc Space is $15 YCH Premium Plan with Unlimited Disc Space is $25 Types Of Preinstalled: ONE-TIME setup fee for ONE website Basic Preinstalled setup fee is $5Pro Preinstalled setup fee is $10Premium Preinstalled setup fee is $20 1) Basic preinstalled Basic preinstalled - $5 Process 1: I will install your website with approximately 25 WordPress Basic Plugins fully tested by me which including, .Contact form.Terms of use.Disclaimer.Sitemap.Privacy Policy(Already Included By WordPress Latest Version)…much more Process 2: Preinstalled Premium Plugins ( Preinstalled, activate only, no license to be sent ) KingSumo Giveaway Developer LicenseWP BotBlocker (Personal Use Only) WPUnderAttack (Personal Use Only) Process 3: Installing WordPress Themes: Sample Preview Here! Elegant Divi Theme + Divi BuilderAzon Simple Theme AzonBooster AzonMonster Theme Catalyst Dynamik – Catalyst Child Theme Ultimatum Theme Ultimate Azon Multisite Process 4: Configured your website with: Strong Htacess ProtectionDisable directory browsing Protect WP-config.php Protect from SQL injection 2) Pro Preinstalled - Basic Preinstalled Plus The Covert Suite Pro Preinstalled Fee - $10, including Process 1: Process 2: Process 3: Installing WordPress Themes: Sample Preview Here! Elegant Divi Theme + Divi BuilderAzon Simple Theme AzonBooster AzonMonster Theme Catalyst Dynamik – Catalyst Child Theme Ultimatum Theme Ultimate Azon Multisite AuthorityAzon Multi-Site [ EXTRA for Pro preinstalled ] Process 4: Process 5: Covert Suite Covert VideoPress + Covert Video ContentCovert SocialPress + Covert Social Content Pro Covert Shirt Store + Covert Shirt Builder Covert Messanger Pro Covert Geo Targeter Covert Curator + Covert Content Curator Covert Copy Traffic Pro Covert Context Pro Covert Action Bar 2.0 Premium Preinstalled - Basic Preinstalled Plus Pro preinstalled Please Choose Only One Option You can choose Either With Premium Preinstalled OPTION 1 Or Premium Preinstalled OPTION 2 3) Premium Preinstalled OPTION 1 With Deep Themes Premium Preinstalled Fee - $20.00 Including: Process 1: I will install your website with approximately 25 WordPress Basic Plugins fully tested by me which including, Process 2: Preinstalled Premium Plugins ( Preinstalled, activate only, no license to be sent ) 4. WP Rocket Pro [ Extra ] 5. Backupbuddy + iThemes Security Pro [ Extra ] 6. Elementor Pro [ Extra ] Process 3: Installing WordPress Themes: Sample Preview Here! Process 4: Configured your website with: Process 5: Covert Suite Process 6: DEEP THEMES must be preinstalled without other Themes. In order not to mess with other themes, Deep Themes is a standalone installation. So, Deep Themes is optional and you must send the request after subscribing. My 1 year Deep Themes License access subjected to an expiry date or renewable. The themes license expire on 09 Jan 2020. Anyway, I will renew the license each year. Deep Themes - Over 40+ Deep Themes for you to choose. https://ift.tt/2jN2N3C Much more...(40+) Deep Themes - https://ift.tt/2jOK9Ze 4) Premium Preinstalled OPTION 2 With Astra Agency Premium Preinstalled Fee - $20.00 Including: Process 1: I will install your website with approximately 25 WordPress Basic Plugins fully tested by me which including, Process 2: Preinstalled Premium Plugins ( Preinstalled, activate only, no license to be sent ) 4. WP Rocket Pro [ Extra ] 5. Backupbuddy + iThemes Security Pro [ Extra ] 6. Elementor Pro [ Extra ] Process 3: Installing WordPress Themes: Sample Preview Here! Process 4: Configured your website with: Process 5: Covert Suite Process 6: Astra Agency – https://wpastra.com/ Astra Pro Theme .Convert Pro.Convert Pro - Addon.Astra Pro.Schema Pro.Ultimate Addons for Beaver Builder.Ultimate Addons for Elementor.WP Portfolio.astra-premium-sites *** ONE-TIMESetup FeeForONEWebsite ORDER TOGETHER WITH THE HOSTING YCH Basic Plan + Preinstalled YCH Basic Plan with 50GB Disc Space - $10 including Basic Preinstalled fee of $5 [ Basic Offer ]YCH Basic Plan with 50GB Disc Space - $15 including Pro Preinstalled fee of $10 [ Extra - Add $5 ]YCH Basic Plan with 50GB Disc Space - $25 including Premium Preinstalled Option 1 / Option 2 fee of $20 [ Extra - Add $15 ] YCH Pro Plan + Preinstalled YCH Pro Plan with 300GB Disc Space - $15 including Basic Preinstalled fee of $5 [ Extra - Add $5 ]YCH Pro Plan with 300GB Disc Space - $20 including Pro Preinstalled fee of $10 [ Extra - Add $10 ]YCH Pro Plan with 300GB Disc Space - $30 including Premium Preinstalled Option 1 / Option 2 fee of $20 [ Extra - Add $20 ]YCH Gold Plan + Preinstalled YCH Gold Plan with 1TB Disc Space - $20 including Basic Preinstalled fee of $5 [ Extra - Add $10 ]YCH Gold Plan with 1TB Disc Space - $25 including Pro Preinstalled fee of $10 [ Extra - Add $15 ]YCH Gold Plan with 1TB Disc Space - $35 including Premium Preinstalled Option 1 / Option 2 fee of $20 [ Extra - Add $25 ]YCH Premium Plan + Preinstalled YCH Premium Plan with Unlimited Disc Space - $30 including Basic Preinstalled fee of $5 [ Extra - Add $20 ]YCH Premium Plan with Unlimited Disc Space - $35 including Pro Preinstalled fee of $10 [ Extra - Add $25 ]YCH Premium Plan with Unlimited Disc Space - $45 including Premium Preinstalled Option 1 / Option 2 fee of $20 [ Extra - Add $35 ] For the second year onward, the hosting fee will be charged according to the following: YCH Basic Plan - 50GB Disc Space - $5 Per Year YCH Pro Plan - 300GB Disc Space - $10 Per Year YCH Gold Plan - 1TB Disc Space - $15 Per Year YCH Premium Plan - Unlimited Disc Space - $25 Per Year FAQ Q: Does the server has any limitation on the inode/files usage? A: No, as long as it is usable. Other words the site needs it to run. Q: How long does the Auto SSL be ready? A: After your domain propagated, we will install WordPress and Preinstalled as described on your domain and the login credentials will be sent to you. The process might take a few hours to 72 hours depending on how fast is the domain propagated on the server after changed the DNS on the Domain Registrar. Some domains only need a few hours, some need more than 24 hours. Hence, your patience is appreciated. Terms of Service: http://bit.ly/sharedhostingtos Delivery: Basic Preinstalled - 3 days from the time you place an orderPro Preinstalled - 3 days from the time you place an orderPremium Preinstalled Option 1 - 3 days from the time you place an orderPremium Preinstalled Option 3 - 4 days from the time you place an order by: promaster67 Created: -- Category: Wordpress Viewed: 9
https://ift.tt/2kebnsm
0 notes
Video
youtube
Assalam-0-Alaikum and Welcome to Tech Urdu! Account Suspended This Account has been suspended. Contact your hosting provider for more information. If you're seeing this message then you need to watch this video till the very end. ^^^Tech Urdu FREE Courses^^^ 1. Blogger Complete Course: https://www.youtube.com/playlist?list=PLs9p2Ata6d5pa5R2HTj4hvVJs6JnmnULz 2. WordPress Complete Training: https://www.youtube.com/watch?v=p2n59qqCr4g&list=PLs9p2Ata6d5raHnNaO69mkswfljWm-wW5&index=2&t=0s 3. Complete SEO Course for WordPress & Blogger: https://www.youtube.com/watch?v=E39e8NsMlCU&list=PLs9p2Ata6d5qKRf6wLZ4DhYJ7tJlhC47A =-=-=-=-=-=-=-=-==-=-=-=-=-=- Please Like, Share and if you want more such interesting and informative videos then SUBSCRIBE to Tech Urdu. Tech Urdu – SUBSCRIBE: https://www.youtube.com/user/tulaibjavid =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= \\\*** RELATED VIDEOS ***/// Cpanel - Disk Usage Warning & Inodes Problem |How to Reduce or Control [Urdu/Hindi/English Captions] https://youtu.be/5c49QZo0Cx4 WordPress Complete Training | Part 3 - How to Choose the Best Hosting for WordPress [Urdu/Hindi] https://youtu.be/Mkj7_YED1CA WordPress Complete Training | Part 14 - Essential WordPress Plugins (20+) [Urdu/Hindi] https://youtu.be/dMbKaQu6vNY WordPress Complete Training | Part 4 - WordPress Installation Process from Cpanel [Urdu/Hindi] https://youtu.be/i03lJnb2bA8 Here is how to Solve ALL Google Index Coverage Errors in Google Search Console in 2020 [Urdu/Hindi] https://youtu.be/kU9gxlY7B6w Get Faster Page Speeds with the New Speed Report in Google Search Console [Urdu/Hindi] https://youtu.be/QkWHtT4EhnM =-=-=-=-=-=-=-=-=-=-=-=-=-=-=- For Advertisement, please email at [email protected]. (Please note that we put our best in making sure that the product, business, channel, website, brand, etc we are promoting is received well by our audience and hence we only promote selective products. Besides, we not only advertise here on techurdu website but also on our YouTube Channel Videos). =-=-=-=-=-=-=-=-=-=-=-=-=-=-=- \\\***Join Us (Websites)***/// Tech Urdu: https://techurdu.net Forestrypedia: https://ift.tt/2IArpYM Majestic Pakistan: https://ift.tt/2ThMgnX All Pakistan Notification: https://ift.tt/2lftzBR Essayspedia: https://ift.tt/2J0RAnc =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- \\\*** YouTube Channels ***/// Tech Urdu YouTube: https://www.youtube.com/user/tulaibjavid Majestic Pakistan YouTube: https://www.youtube.com/channel/UCBpNIxFjEAVaaJ7ePa20aeA =-=-=-=-=-=-=-=-=-=-=-=-=-=-=- \\\*** Other Social Networking Forums ***/// Tech Urdu on Facebook: https://ift.tt/2sipeyE Majestic Pakistan on Facebook: https://ift.tt/2J0RFHw Essayspedia on Facebook: https://ift.tt/2sjWHZD Forestrypedia on Facebook: https://ift.tt/2J0R8W2 =-=-=-=-=-=-=-=-=-=-=-=-=-=-=- My Life - My Journey (Everything I See & Capture): https://www.youtube.com/channel/UC4ZXcYridbeZLOmc9L5Golw =-=-=-=-=-=-=-=-=-=-=-=-=-=- Like, Share and SUBSCRIBE Please. Take care and Allah Hafiz. Regards Tech Urdu Team.
0 notes
Text
Efficient and Quality Cloud Service by iNode Cloud
Every business will agree that cloud computing plays a great role nowadays. You just cannot imagine how processes and tasks can be handled without the cloud. It will be quite difficult and stressful to handle all things manually, so cloud computing is a real advantage and success. Cloud computing has brought amazing benefits and each business can enjoy them no matter where they are in the world. It has provided speed and reduced the costs that every business used to spend to make things work. Cloud computing will bring many opportunities, so it's time to rely on iNode Cloud and enjoy significant changes.
iNode Cloud prides itself for delivering the best cloud web hosting Australia services. Due to this, your website will get a lot of traffic first of all. You will get a tailored plan that will cover all your needs, requirements and desires. Amazon is considered to be the most reliable provider, so iNode Cloud has built its hosting platform at Amazon web services. Cloud hosting providers Australia deliver cloud hosting for all businesses, no matter how large or small they are. All the packages vary from each other and they are based on each business goals.

Cloud web hosting Australia is flexible and iNode Cloud can easily customize its service according to your business needs. It also has the ability to change anything if you require it. The Cloud hosting providers Australia guarantee that you can always scale up or down depending on the traffic you are getting. Through your control panel you can also change what you want at your own time. iNode Cloud will boost your business as it has the best system designed for you. You don't have to acquire or buy your own IT infrastructure including servers, high-performance computers, and mainframes. You can be rest assured that your business will get smooth, uninterrupted, efficient and perfect services, when iNode Cloud is on the job. Whenever any issue happens, the system will automatically respond to it and handle alternative ways.
You are always welcome to choose iNode Cloud infrastructure in order to build a perfect and innovative web hosting platform. The servers of Cloud Reseller Hosting allow you to resell effective web hosting. So scaling up or down your business needs can be possible no matter you are on the go, at home or somewhere else. Due to Cloud Reseller Hosting, a total control to your cloud server will be provided. You will also be able to deploy your reseller hosting platform either Linux cloud server or Windows cloud server without any difficulties. iNode Cloud has improved web hosting reseller field and it never stops developing even more perfect offers. You can run your business more efficiently when you choose iNode Cloud as your reliable partner. This will be a perfect investment for your business improvement and iNode Cloud will deliver honest, affordable, and perfect solutions. Contact this company now and let the specialists handle everything by delivering efficiency and quality cloud service!
0 notes
Text
Kaspersky Discount
These Internet security tools, and Norton Internet Security in particular, come with a bunch of smart features that can give you an additional protection against even unknown, or unrecognized threats by using behavior Kaspersky promo code 2018 monitoring algorithms. A special type of contiguous-focus osteomyelitis occurs in the setting of peripheral vascular disease and nearly always involves the small bones of the feet of adults with diabetes. Genetically we are poorly equipped to handle the high-carbohydrate, low-protein diet of modern times. Be sure that the content is useful information about a particular topic, discipline, product or service. If the design is complex a lot of detail will be lost when the logo is shrunk to fit on the card and people might not be able to make out the design. Basically an Access Control List enforces the Kaspersky discount security policy on the network. The next step you should take after purchasing a good domain name is to Kaspersky discount 2018 shop for an affordable web hosting service. Water acts as an appetite suppressant by Kaspersky coupon keeping your stomach full and fending off dehydration which can lead to false cravings/hunger. But you must note here that windows firewall does not block the spam emails. Specify each, the dollar amount of the opportunity, and what your actions should be. Both of them require memory from your computer when downloading them. The company's that host your site at no cost are limited and they do not make it easier to store much in your pages. I have to find something to put on it " I think web page layout and typesetting based on page beautify and rich interface contact are both not desirable. Noise and heat are top of the list here. Total fatty acids (4.14 g) does not equal total lipid (4.5 g) because of the glycerol moiety of triacylglycerides and phospholipids and the phosphorylated moieties of the phospholipids). The Kaspersky promo value of advertisement these days is worth a great deal of money, and Hometown Values Coupon Magazine has found a way to capitalize. Keep an eye on the arowana for a few minutes in the tank to make sure that this is what the fish is doing. Moreover it is necessary to mention that doesn't matter what is the approach of your service provider, whether he chooses to use content management system also known as web cms or the manual procedure, the bottom line is that their service must be capable enough to offer you a beautifully designed website. I therefore considered going with the cheapest option however on reflection I decided that since I was building the site for my business the best choice would be the business plan. Because the regular man or woman can pay for solution instantly from the internet site, this might possibly be yet another determining element in whether or not or not to start a franchise organization. As the region is developing at a Kaspersky promo 2018 extremely fast pace and it is the technology that's accelerating this growth. In a shared hosting, the web server are shared by many sites. It might vary from as little as 50,000 inodes on up to 300,000 or more inodes per account. It is important to test technical support and customer support - is it quick to respond? In fact, in some cases they do everything with the exception of marketing your hosting service. The default real-time protection settings ensure good protection against malware, with minor impact Kaspersky coupon code 2018 on system performance. Therefore, enabling the sales representative to balance" their selling style and appeal to a broader Kaspersky coupon code audience. Calves can be one of the hardest body parts to develop and train properly. The C-Panel features the tools for uploading and managing web pages, managing domains, subdomains, FTP accounts, creating parked domains, add-on domains, protecting your directories, redirecting visitors to another location, website statistics, back up data, virus protection and spam filters, the tools to keep your privacy and security. Your best bet is to limit your cheese intake to 4 oz per day. For everyone who loves shopping, nothing can be more delightful then getting discount deals and promotional offers on all their purchases. This is the best method for Kaspersky promo code anyone who is unsure how to complete the above steps manually. Coming out with ‘breakthrough ideas’ and ‘completely new’ innovations is both tempting and glamorous. The problem with reviews written by members is that they are all looking for prospects, and will never be fully unbiased. Lookup the word 'exciting' at Thesaurus.com and you can quickly find an alternative like 'breathtaking, sensational or fascinating'. Just A Few attributes of your current kind of electronic firewall software and also much when it comes to Kaspersky coupon 2018 versions firewall program even Kaspersky discount coupon 2018 better. African bushmen in the past took the herb to suppress their appetite when they went on long hunting trips. You Kaspersky discount coupon always want to switch up your workouts so your body does not plateau, but you have to have a main source of cardio that you can go to to get results.
0 notes
Text
CIS 562 Week 11 Final Exam – Strayer New
Click On The Link Below To Purchase A+ Graded Material
Instant Download
http://budapp.net/CIS-562-Final-Exam-Week-11-Strayer-NEW-CIS562W11E.htm
Chapters 7 Through 16
Chapter 7: Current Computer Forensics Tools
TRUE/FALSE
1. When you research for computer forensics tools, strive for versatile, flexible, and robust tools that provide technical support.
2. In software acquisition, there are three types of data-copying methods.
3. To help determine what computer forensics tool to purchase, a comparison table of functions, subfunctions, and vendor products is useful.
4. The Windows platforms have long been the primary command-line interface OSs.
5. After retrieving and examining evidence data with one tool, you should verify your results by performing the same tasks with other similar forensics tools.
MULTIPLE CHOICE
1. Computer forensics tools are divided into ____ major categories.
a.
2
c.
4
b.
3
d.
5
2. Software forensics tools are commonly used to copy data from a suspect’s disk drive to a(n) ____.
a.
backup file
c.
image file
b.
firmware
d.
recovery copy
3. To make a disk acquisition with En.exe requires only a PC running ____ with a 12-volt power connector and an IDE, a SATA, or a SCSI connector cable.
a.
UNIX
c.
Linux
b.
MAC OS X
d.
MS-DOS
4. Raw data is a direct copy of a disk drive. An example of a Raw image is output from the UNIX/Linux ____ command.
a.
rawcp
c.
d2dump
b.
dd
d.
dhex
5. ____ of data involves sorting and searching through all investigation data.
a.
Validation
c.
Acquisition
b.
Discrimination
d.
Reconstruction
6. Many password recovery tools have a feature that allows generating potential lists for a ____attack.
a.
brute-force
c.
birthday
b.
password dictionary
d.
salting
7. The simplest method of duplicating a disk drive is using a tool that does a direct ____ copy from the original disk to the target disk.
a.
partition-to-partition
c.
disk-to-disk
b.
image-to-partition
d.
image-to-disk
8. To complete a forensic disk analysis and examination, you need to create a ____.
a.
forensic disk copy
c.
budget plan
b.
risk assessment
d.
report
9. The first tools that analyzed and extracted data from floppy disks and hard disks were MS-DOS tools for ____ PC file systems.
a.
Apple
c.
Commodore
b.
Atari
d.
IBM
10. In Windows 2000 and XP, the ____ command shows you the owner of a file if you have multiple users on the system or network.
a.
Dir
c.
Copy
b.
ls
d.
owner
11. In general, forensics workstations can be divided into ____ categories.
a.
2
c.
4
b.
3
d.
5
12. A forensics workstation consisting of a laptop computer with a built-in LCD monitor and almost as many bays and peripherals as a stationary workstation is also known as a ____.
a.
stationary workstation
c.
lightweight workstation
b.
field workstation
d.
portable workstation
13. ____ is a simple drive-imaging station.
a.
F.R.E.D.
c.
FIRE IDE
b.
SPARC
d.
DiskSpy
14. ____ can be software or hardware and are used to protect evidence disks by preventing you from writing any data to the evidence disk.
a.
Drive-imaging
c.
Workstations
b.
Disk editors
d.
Write-blockers
15. Many vendors have developed write-blocking devices that connect to a computer through FireWire,____ 2.0,and SCSI controllers.
a.
USB
c.
LCD
b.
IDE
d.
PCMCIA
16. The ____ publishes articles, provides tools, and creates procedures for testing and validating computer forensics software.
a.
CFTT
c.
FS-TST
b.
NIST
d.
NSRL
17. The standards document, ____, demands accuracy for all aspects of the testing process, meaning that the results must be repeatable and reproducible.
a.
ISO 3657
c.
ISO 5725
b.
ISO 5321
d.
ISO 17025
18. The NIST project that has as a goal to collect all known hash values for commercial software applications and OS files is ____.
a.
NSRL
c.
FS-TST
b.
CFTT
d.
PARTAB
19. The primary hash algorithm used by the NSRL project is ____.
a.
MD5
c.
CRC-32
b.
SHA-1
d.
RC4
20. One way to compare your results and verify your new forensic tool is by using a ____, such as HexWorkshop, or WinHex.
a.
disk imager
c.
bit-stream copier
b.
write-blocker
d.
disk editor
21. Although a disk editor gives you the most flexibility in ____, it might not be capable of examining a ____ file’s contents.
a.
testing, compressed
c.
testing, pdf
b.
scanning, text
d.
testing, doc
COMPLETION
1. Software forensic tools are grouped into command-line applications and ____________________ applications.
2. The Windows application of EnCase requires a(n) ____________________ device, such as FastBloc, to prevent Windows from accessing and corrupting a suspect disk drive.
3. The ____________________ function is the most demanding of all tasks for computer investigators to master.
4. Because there are a number of different versions of UNIX and Linux, these platforms are referred to as ____________________ platforms.
5. Hardware manufacturers have designed most computer components to last about ____________________ months between failures.
MATCHING
Match each item with a statement below
a.
JFIF
f.
PDBlock
b.
Lightweight workstation
g.
Norton DiskEdit
c.
Pagefile.sys
h.
Stationary workstation
d.
Salvaging
i.
SafeBack
e.
Raw data
1. letters embedded near the beginning of all JPEG files
2. European term for carving
3. a direct copy of a disk drive
4. usually a laptop computer built into a carrying case with a small selection of peripheral options
5. one of the first MS-DOS tools used for a computer investigation
6. software-enabled write-blocker
7. system file where passwords may have been written temporarily
8. a tower with several bays and many peripheral devices
9. command-line disk acquisition tool from New Technologies, Inc.
SHORT ANSWER
1. What are the five major function categories of any computer forensics tool?
2. Explain the validation of evidence data process.
3. What are some of the advantages of using command-line forensics tools?
4. Explain the advantages and disadvantages of GUI forensics tools.
5. Illustrate how to consider hardware needs when planning your lab budget.
6. Describe some of the problems you may encounter if you decide to build your own forensics workstation.
7. Illustrate the use of a write-blocker on a Windows environment.
8. Briefly explain the NIST general approach for testing computer forensics tools.
9. Explain the difference between repeatable results and reproducible results.
10. Briefly explain the purpose of the NIST NSRL project.
Chapter 8: Macintosh and Linux Boot Processes and File Systems
TRUE/FALSE
1. If a file contains information, it always occupies at least one allocation block.
2. Older Macintosh computers use the same type of BIOS firmware commonly found in PC-based systems.
3. GPL and BSD variations are examples of open-source software.
4. A UNIX or Linux computer has two boot blocks, which are located on the main hard disk.
5. Under ISO 9660 for DVDs, the Micro-UDF (M-UDF) function has been added to allow for long filenames.
MULTIPLE CHOICE
1. Macintosh OS X is built on a core called ____.
a.
Phantom
c.
Darwin
b.
Panther
d.
Tiger
2. In older Mac OSs, a file consists of two parts: a data fork, where data is stored, and a ____ fork, where file metadata and application information are stored.
a.
resource
c.
blocks
b.
node
d.
inodes
3. The maximum number of allocation blocks per volume that File Manager can access on a Mac OS system is ____.
a.
32,768
c.
58,745
b.
45,353
d.
65,535
4. On older Macintosh OSs all information about the volume is stored in the ____.
a.
Master Directory Block (MDB)
c.
Extents Overflow File (EOF)
b.
Volume Control Block (VCB)
d.
Volume Bitmap (VB)
5. With Mac OSs, a system application called ____ tracks each block on a volume to determine which blocks are in use and which ones are available to receive data.
a.
Extents overflow file
c.
Master Directory Block
b.
Volume Bitmap
d.
Volume Control Block
6. On Mac OSs, File Manager uses the ____to store any information not in the MDB or Volume Control Block (VCB).
a.
volume information block
c.
catalog
b.
extents overflow file
d.
master directory block
7. Linux is probably the most consistent UNIX-like OS because the Linux kernel is regulated under the ____ agreement.
a.
AIX
c.
GPL
b.
BSD
d.
GRUB
8. The standard Linux file system is ____.
a.
NTFS
c.
HFS+
b.
Ext3fs
d.
Ext2fs
9. Ext2fs can support disks as large as ____ TB and files as large as 2 GB.
a.
4
c.
10
b.
8
d.
12
10. Linux is unique in that it uses ____, or information nodes, that contain descriptive information about each file or directory.
a.
xnodes
c.
infNodes
b.
extnodes
d.
inodes
11. To find deleted files during a forensic investigation on a Linux computer, you search for inodes that contain some data and have a link count of ____.
a.
-1
c.
1
b.
0d.
2
12. ____ components define the file system on UNIX.
a.
2
c.
4
b.
3
d.
5
13. The final component in the UNIX and Linux file system is a(n) ____, which is where directories and files are stored on a disk drive.
a.
superblock
c.
boot block
b.
data block
d.
inode block
14. LILO uses a configuration file named ____ located in the /Etc directory.
a.
Lilo.conf
c.
Lilo.config
b.
Boot.conf
d.
Boot.config
15. Erich Boleyn created GRUB in ____ to deal with multiboot processes and a variety of OSs.
a.
1989
c.
1994
b.
1991
d.
1995
16. On a Linux computer, ____ is the path for the first partition on the primary master IDE disk drive.
a.
/dev/sda1
c.
/dev/hda1
b.
/dev/hdb1
d.
/dev/ide1
17. There are ____ tracks available for the program area on a CD.
a.
45
c.
99
b.
50
d.
100
18. The ____provides several software drivers that allow communication between the OS and the SCSI component.
a.
International Organization of Standardization (ISO)
b.
Advanced SCSI Programming Interface (ASPI)
c.
CLV
d.
EIDE
19. All Advanced Technology Attachment (ATA) drives from ATA-33 through ATA-133 IDE and EIDE disk drives use the standard ____ ribbon or shielded cable.
a.
40-pin
c.
80-pin
b.
60-pin
d.
120-pin
20. ATA-66,ATA-____, and ATA-133 can use the newer 40-pin/80-wire cable.
a.
70
c.
96
b.
83
d.
100
21. IDE ATA controller on an old 486 PC doesn’t recognize disk drives larger than 8.4 ____.
a.
KB
c.
GB
b.
MB
d.
TB
COMPLETION
1. Before OS X, Macintosh uses the ____________________, in which files are stored in directories, or folders, that can be nested in other folders.
2. The Macintosh file system has ____________________ descriptors for the end of file (EOF).
3. ____________________ is a journaling version of Ext2fs that reduces file recovery time after a crash.
4. When you turn on the power to a UNIX workstation, instruction code located in firmware on the system’s CPU loads into RAM. This firmware is called ____________________ code because it’s located in ROM.
5. CD players that are 12X or faster read discs by using a(n) _____________________ system.
MATCHING
Match each item with a statement below
a.
File Manager
f.
Volume
b.
Inode blocks
g.
ls
c.
ISO 9660
h.
Catalog
d.
LILO
i.
Finder
e.
Clumps
1. older Linux boot manager utility
2. Macintosh tool that works with the OS to keep track of files and maintain users’ desktops
3. any storage medium used to store files
4. the list command on Linux
5. maintains relationships between files and directories on a volume on a Mac OS
6. the first data after the superblock on a UNIX or Linux file system
7. ISO standard for CDs
8. Mac OS utility that handles reading, writing, and storing data to physical media
9. groups of contiguous allocation blocks
SHORT ANSWER
1. Explain the relation between allocation blocks and logical block on a Mac OS file system.
2. Explain the use of B*-trees on Mac OS 9 file system.
3. Explain the use of forensic tools for Macintosh systems.
4. What are the functions of the superblock on a UNIX or Linux file system?
5. What is a bad block inode on Linux?
6. What is a continuation inode?
7. Describe the CD creation process.
8. Write a brief history of SCSI.
9. Explain the problems you can encounter with pre-ATA-33 devices when connecting them to current PCs.
10. What problems can hidden partitions on IDE devices cause to forensic investigators?
Chapter 9: Computer Forensics Analysis and Validation
TRUE/FALSE
1. The defense request for full discovery of digital evidence applies only to criminal cases in the United States.
2. For target drives, use only recently wiped media that have been reformatted and inspected for computer viruses.
3. FTK cannot perform forensics analysis on FAT12 file systems.
4. FTK cannot analyze data from image files from other vendors.
5. A nonsteganographic graphics file has a different size than an identical steganographic graphics file.
MULTIPLE CHOICE
1. ____ increases the time and resources needed to extract,analyze,and present evidence.
a.
Investigation plan
c.
Litigation path
b.
Scope creep
d.
Court order for discovery
2. You begin any computer forensics case by creating a(n) ____.
a.
investigation plan
c.
evidence custody form
b.
risk assessment report
d.
investigation report
3. In civil and criminal cases, the scope is often defined by search warrants or ____, which specify what data you can recover.
a.
risk assessment reports
c.
scope creeps
b.
investigation plans
d.
subpoenas
4. There are ____ searching options for keywords which FTK offers.
a.
2
c.
4
b.
3
d.
5
5. ____ search can locate items such as text hidden in unallocated space that might not turn up in an indexed search.
a.
Online
c.
Active
b.
Inline
d.
Live
6. The ____ search feature allows you to look for words with extensions such as “ing,”“ed,” and so forth.
a.
fuzzy
c.
permutation
b.
stemming
d.
similar-sounding
7. In FTK ____ search mode, you can also look for files that were accessed or changed during a certain time period.
a.
live
c.
active
b.
indexed
d.
inline
8. FTK and other computer forensics programs use ____ to tag and document digital evidence.
a.
tracers
c.
bookmarks
b.
hyperlinks
d.
indents
9. Getting a hash value with a ____ is much faster and easier than with a(n) ____.
a.
high-level language, assembler
b.
HTML editor, hexadecimal editor
c.
computer forensics tool, hexadecimal editor
d.
hexadecimal editor, computer forensics tool
10. AccessData ____ compares known file hash values to files on your evidence drive or image files to see whether they contain suspicious data.
a.
KFF
c.
NTI
b.
PKFT
d.
NSRL
11. Data ____ involves changing or manipulating a file to conceal information.
a.
recovery
c.
integrity
b.
creep
d.
hiding
12. One way to hide partitions is to create a partition on a disk, and then use a disk editor such as ____ to manually delete any reference to it.
a.
Norton DiskEdit
c.
System Commander
b.
PartitionMagic
d.
LILO
13. Marking bad clusters data-hiding technique is more common with ____ file systems.
a.
NTFS
c.
HFS
b.
FAT
d.
Ext2fs
14. The term ____ comes from the Greek word for“hidden writing.”
a.
creep
c.
escrow
b.
steganography
d.
hashing
15. ____ is defined as the art and science of hiding messages in such a way that only the intended recipient knows the message is there.
a.
Bit shifting
c.
Marking bad clusters
b.
Encryption
d.
Steganography
16. Many commercial encryption programs use a technology called ____, which is designed to recover encrypted data if users forget their passphrases or if the user key is corrupted after a system data failure.
a.
steganography
c.
password backup
b.
key escrow
d.
key splitting
17. People who want to hide data can also use advanced encryption programs, such as PGP or ____.
a.
NTI
c.
FTK
b.
BestCrypt
d.
PRTK
18. ____ recovery is a fairly easy task in computer forensic analysis.
a.
Data
c.
Password
b.
Partition
d.
Image
19. ____ attacks use every possible letter, number, and character found on a keyboard when cracking a password.
a.
Brute-force
c.
Profile
b.
Dictionary
d.
Statistics
20. ____ are handy when you need to image the drive of a computer far away from your location or when you don’t want a suspect to be aware of an ongoing investigation.
a.
Scope creeps
c.
Password recovery tools
b.
Remote acquisitions
d.
Key escrow utilities
21. ____ is a remote access program for communication between two computers. The connection is established by using the DiskExplorer program (FAT or NTFS) corresponding to the suspect (remote) computer’s file system.
a.
HDHOST
c.
DiskEdit
b.
DiskHost
d.
HostEditor
COMPLETION
1. For most law-enforcement-related computing investigations, the investigator is limited to working with data defined in the search ____________________.
2. FTK provides two options for searching for keywords: indexed search and ____________________ search.
3. ____________________ search catalogs all words on the evidence disk so that FTK can find them quickly.
4. To generate reports with the FTK ReportWizard, first you need to ____________________ files during an examination.
5. The data-hiding technique ____________________ changes data from readable code to data that looks like binary executable code.
MATCHING
Match each item with a statement below
a.
Court orders for discovery
f.
PRTK
b.
Investigation plan
g.
Validating digital evidence
c.
Digital Intelligence PDWipe
h.
MD5
d.
Live search
i.
System Commander
e.
Cabinet
1. defines the investigation’s goal and scope, the materials needed, and the tasks to perform
2. a hashing algorithm
3. one of the most critical aspects of computer forensics
4. a type of compressed file
5. an FTK searching option
6. a password recovery program available from AccessData
7. a disk-partitioning utility
8. program used to clean all data from the target drive you plan to use
9. limit a civil investigation
SHORT ANSWER
1. Describe the effects of scope creep on an investigation in the corporate environment.
2. Describe with examples why the approach you take for a forensics case depends largely on the specific type of case you’re investigating.
3. How should you approach a case in which an employee is suspected of industrial espionage?
4. What are the file systems supported by FTK for forensic analysis?
5. How does the Known File Filter program work?
6. How can you validate the integrity of raw format image files with ProDiscover?
7. How can you hide data by marking bad clusters?
8. Briefly describe how to use steganography for creating digital watermarks.
9. What are the basic guidelines to identify steganography files?
10. Briefly describe the differences between brute-force attacks and dictionary attacks to crack passwords.
Chapter 10: Recovering Graphics Files
TRUE/FALSE
1. Bitmap imagesare collections of dots, or pixels, that form an image.
PTS: 1 REF: 398
2. Operating systems do not have tools for recovering image files.
PTS: 1 REF: 405
3. If a graphics file is fragmented across areas on a disk, first you must recover all the fragments to re-create the file.
PTS: 1 REF: 405
4. With many computer forensics tools, you can open files with external viewers.
PTS: 1 REF: 425
5. Steganography cannot be used with file formats other than image files.
PTS: 1 REF: 428
MULTIPLE CHOICE
1. ____are based on mathematical instructions that define lines, curves, text, ovals, and other geometric shapes.
a.
Bitmap images
c.
Vector graphics
b.
Metafile graphics
d.
Line-art images
PTS: 1 REF: 398
2. You use ____ to create, modify, and save bitmap, vector, and metafile graphics files.
a.
graphics viewers
c.
image viewers
b.
image readers
d.
graphics editors
PTS: 1 REF: 398
3. ____ images store graphics information as grids of individual pixels.
a.
Bitmap
c.
Vector
b.
Raster
d.
Metafiles
PTS: 1 REF: 398
4. The process of converting raw picture data to another format is referred to as ____.
a.
JEIDA
c.
demosaicing
b.
rastering
d.
rendering
PTS: 1 REF: 401
5. The majority of digital cameras use the ____ format to store digital pictures.
a.
EXIF
c.
PNG
b.
TIFF
d.
GIF
PTS: 1 REF: 401
6. ____ compression compresses data by permanently discarding bits of information in the file.
a.
Redundant
c.
Huffman
b.
Lossy
d.
Lossless
PTS: 1 REF: 404
7. Recovering pieces of a file is called ____.
a.
carving
c.
saving
b.
slacking
d.
rebuilding
PTS: 1 REF: 405
8. A(n) ____ file has a hexadecimal header value of FF D8 FF E0 00 10.
a.
EPS
c.
GIF
b.
BMP
d.
JPEG
PTS: 1 REF: 408
9. If you can’t open an image file in an image viewer, the next step is to examine the file’s ____.
a.
extension
c.
header data
b.
name
d.
size
PTS: 1 REF: 414
10. The uppercase letter ____ has a hexadecimal value of 41.
a.
“A”
c.
“G”
b.
“C”
d.
“Z”
PTS: 1 REF: 417
11. The image format XIF is derived from the more common ____ file format.
a.
GIF
c.
BMP
b.
JPEG
d.
TIFF
PTS: 1 REF: 423
12. The simplest way to access a file header is to use a(n) ____ editor
a.
hexadecimal
c.
disk
b.
image
d.
text
PTS: 1 REF: 423
13. The ____ header starts with hexadecimal 49 49 2A and has an offset of four bytes of 5C01 0000 2065 5874 656E 6465 6420 03.
a.
TIFF
c.
JPEG
b.
XIF
d.
GIF
PTS: 1 REF: 425
14. ____ is the art of hiding information inside image files.
a.
Steganography
c.
Graphie
b.
Steganalysis
d.
Steganos
PTS: 1 REF: 425
15. ____ steganography places data from the secret file into the host file without displaying the secret data when you view the host file in its associated program.
a.
Replacement
c.
Substitution
b.
Append
d.
Insertion
PTS: 1 REF: 426
16. ____ steganography replaces bits of the host file with other bits of data.
a.
Insertion
c.
Substitution
b.
Replacement
d.
Append
PTS: 1 REF: 426
17. In the following list, ____ is the only steg tool.
a.
EnCase
c.
DriveSpy
b.
iLook
d.
Outguess
PTS: 1 REF: 429
18. ____ has also been used to protect copyrighted material by inserting digital watermarks into a file.
a.
Encryption
c.
Compression
b.
Steganography
d.
Archiving
PTS: 1 REF: 430
19. When working with image files, computer investigators also need to be aware of ____ laws to guard against copyright violations.
a.
international
c.
copyright
b.
forensics
d.
civil
PTS: 1 REF: 430
20. Under copyright laws, computer programs may be registered as ____.
a.
literary works
c.
architectural works
b.
motion pictures
d.
audiovisual works
PTS: 1 REF: 430
21. Under copyright laws, maps and architectural plans may be registered as ____.
a.
pantomimes and choreographic works
c.
literary works
b.
artistic works
d.
pictorial, graphic, and sculptural works
PTS: 1 REF: 430
COMPLETION
1. A graphics program creates and saves one of three types of image files: bitmap, vector, or ____________________.
2. ____________________ is the process of coding of data from a larger form to a smaller form.
3. The ____________________ is the best source for learning more about file formats and their associated extensions.
4. All ____________________ files start at position zero (offset 0 is the first byte of a file) with hexadecimal 49 49 2A.
5. The two major forms of steganography are ____________________ and substitution.
MATCHING
Match each item with a statement below
a.
Pixels
f.
Steganalysis tools
b.
Hex Workshop
g.
GIMP
c.
Adobe Illustrator
h.
XIF
d.
Microsoft Office Picture Manager
i.
Metafile graphics
e.
JPEG
1. drawing program that creates vector files
2. Gnome graphics editor
3. image format derived from the TIFF file format
4. combinations of bitmap and vector images
5. short for “picture elements”
6. are also called steg tools
7. graphics file format that uses lossy compression
8. tool used to rebuild image file headers
9. Microsoft image viewer
SHORT ANSWER
1. Briefly describe the Exchangeable Image File (EXIF) format.
2. Explain how lossless compression relates to image file formats.
3. How does vector quantization (VQ) compress data?
4. Explain how someone can use a disk editor tool to mark clusters as “bad” clusters.
5. Identify and describe some image viewers.
6. Write a brief history of steganography.
7. Describe how to hide information on an 8-bit bitmap image file using substitution steganography.
8. Explain how steganalysis tools work.
9. Give a brief overview of copyright laws pertaining to graphics within and outside the U.S.
10. Present a list of categories covered under copyright laws in the U.S.
Chapter 11: Virtual Machines, Network Forensics, and Live Acquisitions
TRUE/FALSE
1. When intruders break into a network, they rarely leave a trail behind.
PTS: 1 REF: 442
2. Network forensics is a fast, easy process.
PTS: 1 REF: 447
3. PsList from PsTools allows you to list detailed information about processes.
PTS: 1 REF: 450
4. With the Knoppix STD tools on a portable CD, you can examine almost any network system.
PTS: 1 REF: 451
5. Ngrep cannot be used to examine e-mail headers or IRC chats.
PTS: 1 REF: 455
MULTIPLE CHOICE
1. ____ can help you determine whether a network is truly under attack or a user has inadvertently installed an untested patch or custom program.
a.
Broadcast forensics
c.
Computer forensics
b.
Network forensics
d.
Traffic forensics
PTS: 1 REF: 442
2. ____ hide the most valuable data at the innermost part of the network.
a.
Layered network defense strategies
c.
Protocols
b.
Firewalls
d.
NAT
PTS: 1 REF: 442
3. ____ forensics is the systematic tracking of incoming and outgoing traffic on your network.
a.
Network
c.
Criminal
b.
Computer
d.
Server
PTS: 1 REF: 442
4. ____ can be used to create a bootable forensic CD and perform a live acquisition.
a.
Helix
c.
Inquisitor
b.
DTDD
d.
Neon
PTS: 1 REF: 445
5. Helix operates in two modes:Windows Live (GUI or command line) and ____.
a.
command Windows
c.
command Linux
b.
remote GUI
d.
bootable Linux
PTS: 1 REF: 445
6. A common way of examining network traffic is by running the ____ program.
a.
Netdump
c.
Coredump
b.
Slackdump
d.
Tcpdump
PTS: 1 REF: 448
7. ____ is a suite of tools created by Sysinternals.
a.
EnCase
c.
R-Tools
b.
PsTools
d.
Knoppix
PTS: 1 REF: 450
8. ____ is a Sysinternals command that shows all Registry data in real time on a Windows computer.
a.
PsReg
c.
RegMon
b.
RegExplorer
d.
RegHandle
PTS: 1 REF: 450
9. The PSTools ____ kills processes by name or process ID.
a.
PsExec
c.
PsKill
b.
PsList
d.
PsShutdown
PTS: 1 REF: 450
10. ____ is a popular network intrusion detection system that performs packet capture and analysis in real time.
a.
Ethereal
c.
Tcpdump
b.
Snort
d.
john
PTS: 1 REF: 451
11. ____ is the U.S. DoD computer forensics lab’s version of the dd command that comes with Knoppix-STD.
a.
chntpw
c.
memfetch
b.
john
d.
dcfldd
PTS: 1 REF: 451
12. The Knoppix STD tool ____ enables you to reset passwords on a Windows computer, including the administrator password
a.
chntpw
c.
oinkmaster
b.
john
d.
memfetch
PTS: 1 REF: 451
13. ____are devices and/or software placed on a network to monitor traffic.
a.
Packet sniffers
c.
Hubs
b.
Bridges
d.
Honeypots
PTS: 1 REF: 454
14. Most packet sniffers operate on layer 2 or ____ of the OSI model.
a.
1
c.
5
b.
3
d.
7
PTS: 1 REF: 454
15. Most packet sniffer tools can read anything captured in ____ format.
a.
SYN
c.
PCAP
b.
DOPI
d.
AIATP
PTS: 1 REF: 455
16. In a(n) ____ attack, the attacker keeps asking your server to establish a connection.
a.
SYN flood
c.
brute-force attack
b.
ACK flood
d.
PCAP attack
PTS: 1 REF: 455
17. ____ is the text version of Ethereal, a packet sniffer tool.
a.
Tcpdump
c.
Etherape
b.
Ethertext
d.
Tethereal
PTS: 1 REF: 455
18. ____ is a good tool for extracting information from large Libpcap files.
a.
Nmap
c.
Pcap
b.
Tcpslice
d.
TCPcap
PTS: 1 REF: 455
19. The ____ Project was developed to make information widely available in an attempt to thwart Internet and network hackers.
a.
Honeynet
c.
Honeywall
b.
Honeypot
d.
Honeyweb
PTS: 1 REF: 458
20. Machines used on a DDoS are known as ____simply because they have unwittingly become part of the attack.
a.
ISPs
c.
zombies
b.
soldiers
d.
pawns
PTS: 1 REF: 458
21. A ____ is a computer set up to look like any other machine on your network, but it lures the attacker to it.
a.
honeywall
c.
honeynet
b.
honeypot
d.
honeyhost
PTS: 1 REF: 459
COMPLETION
1. ____________________ is a layered network defense strategy developed by the National Security Agency (NSA).
2. The term ____________________ means how long a piece of information lasts on a system.
3. ____________________ logs record traffic in and out of a network.
4. The PSTools ____________________ tool allows you to suspend processes.
ANS: PsSuspend
5. The U.K. Honeynet Project has created the ____________________. It contains the honeywall and honeypot on a bootable memory stick.
MATCHING
Match each item with a statement below
a.
Cyberforensics
f.
Trojan horse
b.
Ethereal
g.
Knoppix
c.
Tripwire
h.
PsShutdown
d.
PsGetSid
i.
oinkmaster
e.
PsLoggedOn
1. displays who’s logged on locally
2. displays the security identifier (SID) of a computer or user
3. an audit control program that detects anomalies in traffic and sends an alert automatically
4. usually refers to network forensics
5. a bootable Linux CD intended for computer and network forensics
6. shuts down and optionally restarts a computer
7. helps manage snort rules so that you can specify what items to ignore as regular traffic and what items should raise alarms
8. a network analysis tool
9. type of malware
SHORT ANSWER
1. Why is testing networks as important as testing servers?
2. When are live acquisitions useful?
3. What is the general procedure for a live acquisition?
4. Detail a standard procedure for network forensics investigations.
5. How should you proceed if your network forensic investigation involves other companies?
6. Describe some of the Windows tools available at Sysinternals.
7. What are some of the tools included with the PSTools suite?
8. What is Knoppix-STD?
9. What are some of the tools included with Knoppix STD?
10. Explain The Auditor tool.
Chapter 12: E-mail Investigations
TRUE/FALSE
1. For computer investigators, tracking intranet e-mail is relatively easy because the accounts use standard names established by the network or e-mail administrator.
PTS: 1 REF: 470
2. You can always rely on the return path in an e-mail header to show the source account of an e-mail message.
PTS: 1 REF: 482
3. E-mail programs either save e-mail messages on the client computer or leave them on the server.
PTS: 1 REF: 483
4. All e-mail servers are databases that store multiple users’ e-mails.
PTS: 1 REF: 485
5. Like UNIX e-mail servers, Exchange maintains logs to track e-mail communication.
PTS: 1 REF: 489
MULTIPLE CHOICE
1. E-mail messages are distributed from one central server to many connected client computers, a configuration called ____.
a.
client/server architecture
c.
client architecture
b.
central distribution architecture
d.
peer-to-peer architecture
PTS: 1 REF: 469
2. In an e-mail address, everything after the ____ symbol represents the domain name.
a.
c.
@
b.
.
d.
-
PTS: 1 REF: 470
3. With many ____ e-mail programs, you can copy an e-mail message by dragging the message to a storage medium, such as a folder or disk.
a.
command-line
c.
prompt-based
b.
shell-based
d.
GUI
PTS: 1 REF: 472
4. When working on a Windows environment you can press ____ to copy the selected text to the clipboard.
a.
Ctrl+A
c.
Ctrl+V
b.
Ctrl+C
d.
Ctrl+Z
PTS: 1 REF: 473
5. To retrieve e-mail headers in Microsoft Outlook, right-click the e-mail message, and then click ____to open the Message Options dialog box. The Internet headers text box at the bottom of the dialog box contains the message header.
a.
Options
c.
Properties
b.
Details
d.
Message Source
PTS: 1 REF: 473
6. To retrieve an Outlook Express e-mail header right-click the message, and then click ____to open a dialog box showing general information about the message.
a.
Properties
c.
Details
b.
Options
d.
Message Source
PTS: 1 REF: 473
7. For older UNIX applications, such as mail or mailx, you can print the e-mail headers by using the ____ command.
a.
prn
c.
prnt
b.
print
d.
prt
PTS: 1 REF: 477
8. To view AOL e-mail headers click Action, ____ from the menu.
a.
More options
c.
Options
b.
Message properties
d.
View Message Source
PTS: 1 REF: 478
9. To view e-mail headers on Yahoo! click the ____ link in the Mail Options window, and then click Show all headers on incoming messages.
a.
Advanced
c.
Message Properties
b.
General Preferences
d.
More information
PTS: 1 REF: 480
10. In Microsoft Outlook, you can save sent, drafted, deleted, and received e-mails in a file with a file extension of ____.
a.
.ost
c.
.msg
b.
.eml
d.
.pst
PTS: 1 REF: 483
11. ____ is a comprehensive Web site that has options for searching for a suspect, including by e-mail address, phone numbers, and names.
a.
www.freeality.com
c.
www.whatis.com
b.
www.google.com
d.
www.juno.com
PTS: 1 REF: 484
12. ____ allocates space for a log file on the server, and then starts overwriting from the beginning when logging reaches the end of the time frame or the specified log size.
a.
Continuous logging
c.
Circular logging
b.
Automatic logging
d.
Server logging
PTS: 1 REF: 485
13. The files that provide helpful information to an e-mail investigation are log files and ____ files.
a.
batch
c.
scripts
b.
configuration
d.
.rts
PTS: 1 REF: 487
14. ____ contains configuration information for Sendmail, allowing the investigator to determine where the log files reside.
a.
/etc/sendmail.cf
c.
/etc/var/log/maillog
b.
/etc/syslog.conf
d.
/var/log/maillog
PTS: 1 REF: 487
15. Typically, UNIX installations are set to store logs such as maillog in the ____ directory.
a.
/etc/Log
c.
/etc/var/log
b.
/log
d.
/var/log
PTS: 1 REF: 488
16. Exchange logs information about changes to its data in a(n) ____ log.
a.
checkpoint
c.
transaction
b.
communication
d.
tracking
PTS: 1 REF: 489
17. In Exchange, to prevent loss of data from the last backup, a ____ file or marker is inserted in the transaction log to mark the last point at which the database was written to disk.
a.
tracking
c.
temporary
b.
checkpoint
d.
milestone
PTS: 1 REF: 489
18. The Novell e-mail server software is called ____.
a.
Sendmail
c.
Sawmill
b.
GroupWise
d.
Guardian
PTS: 1 REF: 491
19. GroupWise has ____ ways of organizing the mailboxes on the server.
a.
2
c.
4
b.
3
d.
5
PTS: 1 REF: 491
20. The GroupWise logs are maintained in a standard log format in the ____ folders.
a.
MIME
c.
QuickFinder
b.
mbox
d.
GroupWise
PTS: 1 REF: 491
21. Some e-mail systems store messages in flat plaintext files, known as a(n) ____ format.
a.
POP3
c.
MIME
b.
mbox
d.
SMTP
PTS: 1 REF: 500
COMPLETION
1. You can send and receive e-mail in two environments:via the ____________________ or an intranet (an internal network).
2. An e-mail address in the Return-Path line of an e-mail header is usually indicated as the ____________________ field in an e-mail message.
3. Administrators usually set e-mail servers to ____________________ logging mode.
4. In UNIX e-mail servers, the ____________________ file simply specifies where to save different types of e-mail log files.
5. Vendor-unique e-mail file systems, such as Microsoft .pst or .ost, typically use ____________________ formatting, which can be difficult to read with a text or hexadecimal editor.
MATCHING
Match each item with a statement below:
a.
Contacts
f.
Notepad
b.
Pico
g.
CISCO Pix
c.
syslogd file
h.
www.whatis.com
d.
www.arin.net
i.
Pine
e.
PU020101.db
1. Web site to check file extensions and match the file to a program
2. command line e-mail program used with UNIX
3. text editor used with Windows
4. the first folder the GroupWise server shares
5. text editor used with UNIX
6. the electronic address book in Outlook
7. a network firewall device
8. a registry Web site
9. includes e-mail logging instructions
SHORT ANSWER
1. Describe how e-mail account names are created on an intranet environment.
2. Describe the process of examining e-mail messages when you have access to the victim’s computer and when this access is not possible.
3. What are the steps for retrieving e-mail headers on Pine?
4. What are the steps for viewing e-mail headers in Hotmail?
5. What kind of information can you find in an e-mail header?
6. Explain how to handle attachments during an e-mail investigation.
7. Why are network router logs important during an e-mail investigation?
8. What kind of information is normally included in e-mail logs?
9. Provide a brief description of Microsoft Exchange Server. Additionally, explain the differences between .edb and .stm files.
10. Briefly explain how to use AccessData FTK to recover e-mails.
Chapter 13: Cell Phone and Mobile Device Forensics
TRUE/FALSE
1. Many people store more information on their cell phones than they do on their computers.
PTS: 1 REF: 514
2. Investigating cell phones and mobile devices is a relatively easy task in digital forensics.
PTS: 1 REF: 514
3. TDMA can operate in the cell phone (800 to 1000 MHz) or PCS (1900 MHz) frequency.
PTS: 1 REF: 516
4. Typically, phones developed for use on a GSM network are compatible with phones designed for a CDMA network.
PTS: 1 REF: 516
5. Portability of information is what makes SIM cards so versatile.
PTS: 1 REF: 517
MULTIPLE CHOICE
1. Developed during WWII, this technology,____, was patented by Qualcomm after the war.
a.
iDEN
c.
GSM
b.
CDMA
d.
EDGE
PTS: 1 REF: 515
2. The ____ digital network divides a radio frequency into time slots.
a.
TDMA
c.
FDMA
b.
CDMA
d.
EDGE
PTS: 1 REF: 515
3. The ____ network is a digital version of the original analog standard for cell phones.
a.
TDMA
c.
CDMA
b.
EDGE
d.
D-AMPS
PTS: 1 REF: 515
4. The ____ digital network, a faster version of GSM, is designed to deliver data.
a.
TDMA
c.
EDGE
b.
iDEN
d.
D-AMPS
PTS: 1 REF: 515
5. TDMA refers to the ____ standard, which introduced sleep mode to enhance battery life.
a.
IS-136
c.
IS-236
b.
IS-195
d.
IS-361
PTS: 1 REF: 516
6. Typically, phones store system data in ____, which enables service providers to reprogram phones without having to physically access memory chips.
a.
EROM
c.
EEPROM
b.
PROM
d.
ROM
PTS: 1 REF: 517
7. ____ cards are found most commonly in GSM devices and consist of a microprocessor and from 16 KB to 4 MB of EEPROM.
a.
SD
c.
SDD
b.
MMC
d.
SIM
PTS: 1 REF: 517
8. ____ can still be found as separate devices from mobile phones. Most users carry them instead of a laptop to keep track of appointments, deadlines, address books, and so forth.
a.
SDHCs
c.
CFs
b.
PDAs
d.
MMCs
PTS: 1 REF: 518
9. The file system for a SIM card is a ____ structure.
a.
volatile
c.
hierarchical
b.
circular
d.
linear
PTS: 1 REF: 520
10. The SIM file structure begins with the root of the system (____).
a.
EF
c.
DF
b.
MF
d.
DCS
PTS: 1 REF: 520
11. Paraben Software is a leader in mobile forensics software and offers several tools, including ____, which can be used to acquire data from a variety of phone models.
a.
BitPim
c.
MOBILedit!
b.
DataPilot
d.
Device Seizure
PTS: 1 REF: 522
12. In a Windows environment, BitPim stores files in ____ by default.
a.
My Documents\BitPim
c.
My Documents\BitPim\Forensics Files
b.
My Documents\Forensics Files\BitPim
d.
My Documents\BitPim\Files
PTS: 1 REF: 522
13. ____ is a forensics software tool containing a built-in write blocker.
a.
GSMCon
c.
SIMedit
b.
MOBILedit!
d.
3GPim
PTS: 1 REF: 522
COMPLETION
1. So far, there have been three generations of mobile phones: analog, digital personal communications service (PCS), and ____________________.
2. Most Code Division Multiple Access (CDMA) networks conform to IS-95, created by the ______________________.
3. Global System for Mobile Communications (GSM) uses the ______________________ technique, so multiple phones take turns sharing a channel.
4. The 3G standard was developed by the ______________________ under the United Nations.
5. Mobile devices can range from simple phones to small computers, also called ______________________.
MATCHING
Match each item with a statement below:
a.
CDMA
c.
EDGE
b.
iDEN
d.
ROM
1. proprietary protocol developed by Motorola
2. nonvolatile memory
3. standard developed specifically for 3G
4. one of the most common digital networks, it uses the full radio frequency spectrum to define channels
SHORT ANSWER
1. What is some of the information that can be stored in a cell phone?
2. What is the bandwidth offered by 3G mobile phones?
3. What are the three main components used for cell phone communications?
4. Briefly describe cell phone hardware.
5. Identify several uses of SIM cards.
6. Identify and define three kinds of peripheral memory cards used with PDAs.
7. How can you isolate a mobile device from incoming signals?
8. What are the four categories of information that can be retrieved from a SIM card?
9. What is the general procedure to access the content on a mobile phone SIM card?
10. What are some of the features offered by SIMCon?
Chapter 14: Report Writing for High-Tech Investigations
TRUE/FALSE
1. Besides presenting facts, reports can communicate expert opinion.
PTS: 1 REF: 530
2. A verbal report is more structured than a written report.
PTS: 1 REF: 532
3. If you must write a preliminary report, use words such as “preliminary copy,”“draft copy,” or “working draft.”
PTS: 1 REF: 535
4. As with any research paper, write the report abstract last.
PTS: 1 REF: 536
5. When writing a report, use a formal, technical style.
PTS: 1 REF: 537
MULTIPLE CHOICE
1. Attorneys can now submit documents electronically in many courts; the standard format in federal courts is ____.
a.
Microsoft Word (DOC)
c.
Encapsulated Postscript (EPS)
b.
Portable Document Format (PDF)
d.
Postscript (PS)
PTS: 1 REF: 531
2. A(n) ____is a document that lets you know what questions to expect when you are testifying.
a.
written report
c.
examination plan
b.
affidavit
d.
subpoena
PTS: 1 REF: 532
3. You can use the ____ to help your attorney learn the terms and functions used in computer forensics.
a.
verbal report
c.
final report
b.
preliminary report
d.
examination plan
PTS: 1 REF: 532
4. A written report is frequently a(n) ____ or a declaration.
a.
subpoena
c.
deposition
b.
affidavit
d.
perjury
PTS: 1 REF: 532
5. If a report is long and complex, you should provide a(n) ____.
a.
appendix
c.
table of contents
b.
glossary
d.
abstract
PTS: 1 REF: 536
6. A(n) ____ is sworn to under oath (and penalty of perjury or comparable false swearing statute).
a.
written report
c.
examination plan
b.
verbal report
d.
cross-examination report
PTS: 1 REF: 532
7. In the past, the method for expressing an opinion has been to frame a ____ question based on available factual evidence.
a.
hypothetical
c.
challenging
b.
nested
d.
contradictory
PTS: 1 REF: 533
8. An expert’s opinion is governed by FRE, Rule ____, and the corresponding rule in many states.
a.
705
c.
805
b.
755
d.
855
PTS: 1 REF: 534
9. Remember that anything you write down as part of your examination for a report is subject to ____ from the opposing attorney.
a.
subpoena
c.
publishing
b.
discovery
d.
deposition
PTS: 1 REF: 535
10. A written preliminary report is considered a ____ document because opposing counsel can demand discovery on it.
a.
low-risk
c.
high-risk
b.
middle-risk
d.
no-risk
PTS: 1 REF: 535
11. The abstract should be one or two paragraphs totaling about 150 to ____ words.
a.
200
c.
300
b.
250
d.
350
PTS: 1 REF: 536
12. ____ provide additional resource material not included in the body of the report.
a.
Conclusion
c.
Discussion
b.
References
d.
Appendixes
PTS: 1 REF: 536
13. Typically, report writers use one of two numbering systems: decimal numbering or ____ numbering.
a.
legal-sequential
c.
arabic-sequential
b.
roman-sequential
d.
letter-sequential
PTS: 1 REF: 538
14. A report using the ____ numbering system divides material into sections and restarts numbering with each main section.
a.
roman-sequential
c.
legal-sequential
b.
decimal
d.
indent
PTS: 1 REF: 538
15. In the main section of your report, you typically cite references with the ____ enclosed in parentheses.
a.
year of publication and author’s last name
b.
author’s last name
c.
author’s last name and year of publication
d.
year of publication
PTS: 1 REF: 541
16. Save broader generalizations and summaries for the report’s ____.
a.
appendixes
c.
conclusion
b.
introduction
d.
discussion
PTS: 1 REF: 541
17. The report’s ____ should restate the objectives, aims, and key questions and summarize your findings with clear, concise statements.
a.
abstract
c.
introduction
b.
conclusion
d.
reference
PTS: 1 REF: 541
18. If necessary, you can include ____ containing material such as raw data, figures not used in the body of the report, and anticipated exhibits.
a.
conclusions
c.
references
b.
discussions
d.
appendixes
PTS: 1 REF: 542
19. Reports and logs generated by forensic tools are typically in plaintext format, a word processor format, or ____ format.
a.
PDF
c.
PS
b.
HTML
d.
TXT
PTS: 1 REF: 543
20. Files with extensions .ods and ____ are created using OpenOffice Calc.
a.
.sxc
c.
.dcx
b.
.xls
d.
.qpr
PTS: 1 REF: 543
21. Files with extension ____ are created using Microsoft Outlook Express.
a.
.sxc
c.
.dbx
b.
.doc
d.
.ods
PTS: 1 REF: 543
COMPLETION
1. Lawyers use services called _________________________(libraries), which store examples of expert witnesses’ previous testimony.
2. The report body consists of the introduction and _________________________ sections.
3. When writing a report, _________________________ means the tone of language you use to address the reader.
4. _________________________ assist readers in scanning the text quickly by highlighting the main points and logical development of information.
5. The ______________________________ system is frequently used when writing pleadings.
MATCHING
Match each item with a statement below
a.
Decimal numbering
f.
Verbal report
b.
Lay witness
g.
Spoliation
c.
FTK
h.
Conclusion section
d.
Examination plan
i.
MD5
e.
Signposts
1. draw reader’s attention to a point in your report.
2. a report layout system
3. used by an attorney to guide an expert witness in his or her testimony
4. computer forensics software tool
5. lawyers jargon for destroying or concealing evidence
6. stands for Message Digest 5
7. typically takes place in an attorney’s office where the attorney requests your consultant’s report
8. starts by referring to the report’s purpose, states the main points, draws conclusions, and possibly renders an opinion
9. a witness testifying to personally observed facts
SHORT ANSWER
1. What are the report requirements for civil cases as specified on Rule 26, FRCP?
2. Briefly explain how to limit your report to specifics.
3. What are the areas of investigation usually addressed by a verbal report?
4. Explain how hypothetical questions can be used to ensure that you as a witness are basing your opinion on facts expected to be supported by evidence.
5. What are the four conditions required for an expert witness to testify to an opinion or conclusion?
6. What is the basic structure of a report?
7. Provide some guidelines for writing an introduction section for a report.
8. What do you need to consider to produce clear, concise reports?
9. Explain how to use supportive material on a report.
10. How should you explain examination and data collection methods?
Chapter 15: Expert Testimony in High-Tech Investigations
TRUE/FALSE
1. As an expert witness, you have opinions about what you have found or observed.
PTS: 1 REF: 558
2. Create a formal checklist of your procedures that’s applied to all your cases or include such a checklist in your report.
PTS: 1 REF: 559
3. As a standard practice, collect evidence and record the tools you used in designated file folders or evidence containers.
PTS: 1 REF: 559
4. Like a job resume, your CV should be geared for a specific trial.
PTS: 1 REF: 561
5. Part of what you have to deliver to the jury is a person they can trust to help them figure out something that’s beyond their expertise.
PTS: 1 REF: 565
MULTIPLE CHOICE
1. When cases go to trial, you as a forensics examiner can play one of ____ roles.
a.
2
c.
4
b.
3
d.
5
PTS: 1 REF: 558
2. When you give ____ testimony, you present this evidence and explain what it is and how it was obtained.
a.
technical/scientific
c.
lay witness
b.
expert
d.
deposition
PTS: 1 REF: 558
3. Validate your tools and verify your evidence with ____ to ensure its integrity.
a.
hashing algorithms
c.
steganography
b.
watermarks
d.
digital certificates
PTS: 1 REF: 559
4. For forensics specialists, keeping the ____ updated and complete is crucial to supporting your role as an expert and showing that you’re constantly enhancing your skills through training, teaching, and experience.
a.
testimony
c.
examination plan
b.
CV
d.
deposition
PTS: 1 REF: 561
5. If your CV is more than ____ months old, you probably need to update it to reflect new cases and additional training.
a.
2
c.
4
b.
3
d.
5
PTS: 1 REF: 561
6. ____ is a written list of objections to certain testimony or exhibits.
a.
Defendant
c.
Plaintiff
b.
Empanelling the jury
d.
Motion in limine
PTS: 1 REF: 562
7. Regarding a trial, the term ____ means rejecting potential jurors.
a.
voir dire
c.
strikes
b.
rebuttal
d.
venireman
PTS: 1 REF: 563
8. ____ from both plaintiff and defense is an optional phase of the trial. Generally, it’s allowed to cover an issue raised during cross-examination.
a.
Rebuttal
c.
Closing arguments
b.
Plaintiff
d.
Opening statements
PTS: 1 REF: 563
9. If a microphone is present during your testimony, place it ____ to eight inches from you.
a.
3
c.
5
b.
4
d.
6
PTS: 1 REF: 565
10. Jurors typically average just over ____ years of education and an eighth-grade reading level.
a.
9
c.
11
b.
10
d.
12
PTS: 1 REF: 565
11. ____ is an attempt by opposing attorneys to prevent you from serving on an important case.
a.
Conflict of interest
c.
Deposition
b.
Warrant
d.
Conflicting out
PTS: 1 REF: 568
12. ____ evidence is evidence that exonerates or diminishes the defendant’s liability.
a.
Rebuttal
c.
Inculpatory
b.
Plaintiff
d.
Exculpatory
PTS: 1 REF: 569
13. You provide ____ testimony when you answer questions from the attorney who hired you.
a.
direct
c.
examination
b.
cross
d.
rebuttal
PTS: 1 REF: 569
14. The ____ is the most important part of testimony at a trial.
a.
cross-examination
c.
rebuttal
b.
direct examination
d.
motions in limine
PTS: 1 REF: 569
15. Generally, the best approach your attorney can take in direct examination is to ask you ____ questions and let you give your testimony.
a.
setup
c.
compound
b.
open-ended
d.
rapid-fire
PTS: 1 REF: 569
16. Leading questions such as “Isn’t it true that forensics experts always destroy their handwritten notes?” are referred to as ____ questions.
a.
hypothetical
c.
setup
b.
attorney
d.
nested
PTS: 1 REF: 570
17. Sometimes opposing attorneys ask several questions inside one question; this practice is called ____ questions.
a.
leading
c.
compound
b.
hypothetical
d.
rapid-fire
PTS: 1 REF: 571
18. A ____differs from a trial testimony because there is no jury or judge.
a.
rebuttal
c.
civil case
b.
plaintiff
d.
deposition
PTS: 1 REF: 573
19. There are two types of depositions: ____ and testimony preservation.
a.
examination
c.
direct
b.
discovery
d.
rebuttal
PTS: 1 REF: 573
20. Discuss any potential problems with your attorney ____ a deposition.
a.
before
c.
during
b.
after
d.
during direct examination at
PTS: 1 REF: 574
21. A(n) ____ hearing generally addresses the administrative agency’s subject matter and seeks evidence in your testimony on a subject for which it’s contemplating making a rule.
a.
administrative
c.
legislative
b.
judicial
d.
direct
PTS: 1 REF: 575
COMPLETION
1. The ______________________ of evidence supports the integrity of your evidence.
2. Depending on your attorney’s needs, you might provide only your opinion and technical expertise to him or her instead of testifying in court; this role is called a(n) _______________________.
3. _____________________ is a pretrial motion to exclude certain evidence because it would prejudice the jury.
4. At a trial, _____________________ are statements that organize the evidence and state the applicable law.
5. The purpose of the _____________________ is for the opposing attorney to preview your testimony before trial.
MATCHING
Match each item with a statement below
a.
Plaintiff
f.
CV
b.
Motion in limine
g.
Testimony preservation deposition
c.
Voir dire of venireman
h.
Voir dire
d.
Opening statements
i.
MD5
e.
Discovery deposition
1. part of the discovery process for trial
2. presents the case during a trial
3. provide an overview of the case during a trial
4. questioning potential jurors to see whether they’re qualified
5. usually requested by your client to preserve your testimony in case of schedule conflicts or health problems
6. a hashing algorithm
7. lists your professional experience
8. an expert witness qualification phase
9. allows the judge to decide whether certain evidence should be admitted when the jury isn’t present
SHORT ANSWER
1. What are the differences between a technical or scientific witness and an expert witness?
2. What should you do when preparing for testimony?
3. What are some of the questions you should consider when preparing your testimony?
4. What are some of the technical definitions that you should prepare before your testimony?
5. What are some of the reasons to avoid contact with news media during a case?
6. What are the procedures followed during a trial?
7. What should you do when you find exculpatory evidence?
8. How can you deal with rapid-fire questions during a cross-examination?
9. Explain the differences between discovery deposition and testimony preservation deposition.
10. Briefly describe judicial hearings.
Chapter 16: Ethics for the Expert Witness
TRUE/FALSE
1. People need ethics to help maintain their balance, especially in difficult and contentious situations.
PTS: 1 REF: 596
2. In the United States, there’s no state or national licensing body for computer forensics examiners.
PTS: 1 REF: 597
3. Experts should be paid in full for all previous work and for the anticipated time required for testimony.
PTS: 1 REF: 600
4. Expert opinions cannot be presented without stating the underlying factual basis.
PTS: 1 REF: 601
5. The American Bar Association (ABA) is a licensing body.
PTS: 1 REF: 603
MULTIPLE CHOICE
1. The most important laws applying to attorneys and witnesses are the ____.
a.
professional codes of conduct
c.
rules of evidence
b.
rules of ethics
d.
professional ethics
PTS: 1 REF: 597
2. Computer forensics examiners have two roles: scientific/technical witness and ____ witness.
a.
expert
c.
discovery
b.
direct
d.
professional
PTS: 1 REF: 597
3. Attorneys search ____ for information on expert witnesses.
a.
disqualification banks
c.
examination banks
b.
deposition banks
d.
cross-examination banks
PTS: 1 REF: 598
4. ____ questions can give you the factual structure to support and defend your opinion.
a.
Setup
c.
Rapid-fire
b.
Compound
d.
Hypothetical
PTS: 1 REF: 601
5. FRE ____ describes whether the expert is qualified and whether the expert opinion can be helpful.
a.
702
c.
704
b.
703
d.
705
PTS: 1 REF: 601
6. FRE ____ describes whether basis for the testimony is adequate.
a.
700
c.
702
b.
701
d.
703
PTS: 1 REF: 601
7. The ABA’s ____ contains provisions limiting the fees experts can receive for their services.
a.
Code 703
c.
Rule 26
b.
Model Code
d.
Code 26-1.a
PTS: 1 REF: 603
8. The ____ has stated that, unlike attorneys, expert witnesses do not owe a duty of loyalty to their clients.
a.
ISFCE
c.
ABA
b.
IACIS
d.
HTCIA
PTS: 1 REF: 603
9. ____ are the experts who testify most often.
a.
Civil engineers
c.
Chemical engineers
b.
Computer forensics experts
d.
Medical professionals
PTS: 1 REF: 604
10. ____ offers the most comprehensive regulations of any professional organization and devote an entire section to forensics activities.
a.
AMA’s law
c.
APA’s Ethics Code
b.
ABA’s Model Rule
d.
ABA’s Model Codes
PTS: 1 REF: 605
11. The ____ Ethics Code cautions psychologists about the limitations of assessment tools.
a.
ABA’s
c.
AMA’s
b.
APA’s
d.
ADA’s
PTS: 1 REF: 605
COMPLETION
1. _____________________ are the rules you internalize and use to measure your performance.
2. _____________________ are standards that others apply to you or that you are compelled to adhere to by external forces, such as licensing bodies.
3. Some attorneys contact many experts as a ploy to disqualify them or prevent opposing counsel from hiring them; this practice is called “____________________.”
4. The ____________________ is the foundation of medical ethics.
5. For psychologists, the most broadly accepted set of guidelines governing their conduct as experts is the _____________________ (APA’s) Ethical Principles of Psychologists and Code of Conduct.
MATCHING
Match each item with a statement below:
a.
Ethics
c.
Disqualification
b.
Federal Rules of Evidence (FRE)
d.
IACIS
1. provides a well-defined, simple guide for expected behavior of computer forensics examiners
2. prescribe the methods by which experts appear at trial
3. one of the effects of violating court rules or laws
4. help you maintain your self-respect and the respect of your profession
SHORT ANSWER
1. Briefly describe the issues related to an attorney’s “opinion shopping.”
2. What are some of the factors courts have used in determining whether to disqualify an expert?
3. Describe some of the traps for unwary experts.
4. What are some of the most obvious ethical errors?
5. What are some of the guidelines included in the ISFCE code of ethics?
6. What are some of the requirements included in the HTCIA core values?
7. What are some of standards for IACIS members that apply to testifying?
8. What are the five recommendations set out by the AMA’s policy on expert witness testimony?
9. Why is it difficult to enforce any professional organization’s ethical guidelines?
10. What are the ethical responsibilities owed to you by your attorney?
0 notes