#how to create rdp in windows 10 free
Explore tagged Tumblr posts
Video
youtube
Get USA Windows RDP Free for LifeTime । TechLines
#youtube#how to get free rdp#how to create free rdp#how to create free rdp without credit card#free rdp#how to create rdp in windows 10 free
1 note
·
View note
Video
youtube
How To Create FREE USA RDP's (VPS) Window 10 New Method 2025
0 notes
Video
youtube
How To Make oracle cloud free vps rdp server with latest Ubuntu OS|නොමිලේ උබුන්ටු VPS එකක් හදමු
https://samuduravlogs.blogspot.com/2022/10/how-to-make-oracle-cloud-free-vps-rdp.html
මේ වීඩියෝ එකෙන් මං ඔයාලට පෙන්නන්න හදන්නේ උබුන්ටු මෙහෙයුම් පද්ධතියක් ඔරකල් සර්වර් එකකට ඉන්ස්ටෝල් කරලා රිමෝට් ඩෙස්ක්ටොප් ඇප් එක හරහා සාමාන්යය පරිගණයක් හා සමානව භාවිතා කරන ආකාරය ගැනයි.ඉතිං තමන් ළඟ ලොකු ස්පීඩ් එකක් නැති කම්පියුටර් එකක් තියෙන කෙනෙක්ට වුනත් මේ වර්චුවල් පරිගණකය හරහා ලොකු වැඩ කොටසක් කරගන්න හැකියාව ලැබෙනවා.ඒ වගේම මේ වර්චුවල් පරිගණකය නිර්මාණය කරගන්න OCPU කොර් 4 ක් වගේම 24 gb රැම් ධාරිතාවක් ඔරකල් ක්ලවුඩ් සේවාවෙන් ඔයාලට ලබාගන්න පුළුවන්.
අපි කලින් අපි හදපු වින්ඩෝස් කම්පියුටර් එකේ තිබුනේ OCPU 1 ක් එක්ක 1 GB රැම් එකක් විතරයි.නමුත් අපි දැන් හදන්න යන මේ පරිගණය ඊට වඩා ලොකු ස්පීඩ් එකක් තියෙන හොඳ ඉන්ටනෙට් කනෙක්ෂන් එකක් තියෙන කම්පියුටර් එකක්.
ඉතිං මේ වගේ පරිගණක හරහා අපිට ලැබෙන වාසි මොනවද? ඉතිං මේ වගේ වර්චුවල් ප්රයිවට් සර්වර් පරිගණක ක්රිප්ටෝ මයිනින් වලට...වීඩියෝ කන්වර්ට් වලට... තමන්ගේ යු ටියුබ් චැනල් එකේ වොච් හවර් එක කම්ප්ලීට් කරගන්න වගේම තවත් නොයෙක් කාර්යන් ගනනාවකකට පාවිච්චි කරන්න පුළුවන් ඒ වගේම මේ පරිගණක වල තැන්පත් කරන අපේ ඩේටා වලට ලොකු ආරක්ෂාවකුත් ලැබෙනවා.ඒ වගේම අන්තර්ජාලය පවතින ඕනෙම තැනකදී IP ඇඩ්රස් පාස්වර්ග් ගහලා ක්ෂණිකව මේවා ඇතුලට ලොග් වෙලා ඉහල කාර්යක්ෂමතාවකින් යුක්තව ඕනෙම ගැලපෙන ඇප්ලිකේෂන් පහසුවෙන් ඉන්ටෝල් කරගෙන තමන්ගේ වැඩක් කරගන්න පුළුවන්.
https://samuduravlogs.blogspot.com/2022/10/how-to-make-oracle-cloud-free-vps-rdp.html
In this video, I am going to show you how to install an Ubuntu operating system on an Oracle server and use it like a regular computer through the Remote Desktop app. So even a person with a computer that does not have a high speed can do a lot of work through this virtual computer. Also, to create this virtual computer, you can get 4 CPU cores and 24 GB RAM capacity from Oracle Cloud Service. The Windows computer we built earlier had only 1 GB RAM with 1 OCPU, but this computer we are going to develop now is a computer with a better internet connection and a faster speed.
#youtube#free vps serverfree vps 2021free vps hostingfree vps trialvpsfree vps for forex tradingfree vps server linuxhow to create free vps serverlif
1 note
·
View note
Text
Rdp is a protocol that provides an administrator with a secure way to manage multiple remote desktop sessions from one location. Administrators use Rdp to connect to and manage servers, workstations, and other devices on their network. Moreover, here you will learn how you can create a free RDP. Google Cloud offers free RDP access for creating Windows VPS instances. Keep reading this post to find out how to set up your Google Cloud account for RDP access and create a Windows VPS instance. What Is Google Cloud Platform: Google Cloud Platform (GCP), offered by Google, is a set of cloud computing services that operates on the same infrastructure that Google uses personally for its end-user products, such as Google Search and YouTube. GCP's features include machine learning, Big Data, and general computing capabilities. In addition, GCP offers storage, networking, Big Data, and computing solutions for business and enterprise customers. Google Cloud Platform's main products are: Compute Engine: A virtual machine service that is comparable to Amazon EC2. App Engine: A platform-as-a-service that allows developers to build and run applications on Google's infrastructure. Cloud SQL: A managed relational database service compatible with MySQL, PostgreSQL, and Microsoft SQL Server. Cloud Storage: An object storage service that offers high durability and availability. Cloud Bigtable: A NoSQL big data storage service. Free Rdp Create A Windows Vps On Google Cloud: Creating free RDP on Google Cloud is simple and easy. Follow the procedure steps below to set up your Google Cloud account for RDP access and create a Windows VPS instance: Visit the official page of Google Cloud Platform and sign in with your Google account. If prompted, enter your account information. To use this option, you must input your payment card information. Google, however, makes it very clear that there isn't an auto-charge after the free trial period. Once you have finished creating your google cloud account, go to the Google cloud console main page. Select Computer Engine from the menu in the upper left, then choose VM instances. In the upper-right corner of your screen, select CREATE INSTANCE. Configure the following three options on this page: name, the boot disk, and a firewall. For the boot disc settings, click "Change" next to the boot disc, and various boot disc options will appear.Specify the size of 50 GB and the "Windows Server 2012 R2 Datacenter" option; if you are on Windows 10, then you can specify depending on your requirements.Select and create an instance by clicking.Return to the page for VM instances and select the newly created VM instance. Here, you must follow these two steps in order: By selecting "Set Windows password," you may set the username and password. To get the RDP file, click RDP. The ability to connect to the server is made possible by this RDP file, which is crucial. Therefore, preserve it in a secure location in case you need to use it again in the future. Congratulations! You have successfully launched a free web server on the Google cloud platform with a Windows server installed. How Does Remote Desktop Works: A free RDP means accessing your computer from a remote location; the most common use for RDP is to allow someone to access their work computer from home or another remote location. Many software programs enable you to do this, but the most common is Microsoft Remote Desktop. When you set up a free RDP connection, you create a VPN (a virtual private network). This connection will encrypt all the data sent between your computer and the remote computer. This ensures that no one can eavesdrop on your conversation or see what you are doing. The free RDP software will also provide a way to connect to your work computer from anywhere in the world. This can be extremely useful if you travel frequently or work from home.
As mentioned in the previous step, setting up a free RDP connection is relatively simple. However, it is essential to remember that you follow all instructions correctly. If you do not, you may end up with an unstable connection, or worse, you could end up damaging your computer. What Are The Features And Advantages Of RDP: Remote Desktop Protocol or RDP offers many features to system administrators. It is a client-server protocol that provides users with a consistent graphical interface (GUI) regardless of the type of client device they are using. RDP also offers security measures, such as encryption, to protect data transmitted between the client and server. Some of the advantages and features of RDP include: Accessed Unattended: When no one is physically available at the remote end, you might frequently need to establish a connection to a client's computer as remote assistance professional. Or if you frequently need to assist a particular customer. In either scenario, unattended access can be useful. Thanks to this functionality, you won't need to interrupt the client to grant control each time they request help or continually guide them through the connection procedure. Instead, you'll appreciate always having remote one-click access to the client's PC. Multi-Window Control: The protocol enables you to view a remote computer in its entirety and lets you open multiple windows within that desktop for different purposes. For example, you may want one chat window with the client while another is used to fix their issue. Another advantage of this feature is that each window can be sized differently so that you can make the most of your screen space. Having multiple windows open allows you to work on several tasks at once without constantly switching between them. File Transferring: In addition to providing a graphical interface, RDP also offers a way to transfer files between the client and server computers. This can be extremely useful if you require to send a file or document to the client quickly or if you need to receive a file from them. To transfer files, you need to open the file on the server computer and then save it to the client computer. Alternatively, you can pick and drop the selected file into the RDP window. Either way, the file will be transferred securely and will only be accessible to those who have the necessary permissions. Printing: RDP also offers the ability to print documents and files remotely. This can be extremely useful if you need to print a document for the client but do not have a printer available. To print a document, you need to open it on the server computer and then select the Print option from the File menu. The selected document will then be sent to the client's computer and printed on their printer. Security: Network security is supported by Remote Desktop Protocol in a number of ways. RDP brings in more experts in charge of protecting the server's integrity. This includes ensuring you are protected from the most recent security risks. Furthermore, every piece of information sent across the network is continuously encrypted. This safeguards against hackers attempting to access important data transmitted over the internet. Remote Desktop Protocol protects against data loss because numerous screens can be shared and because backups simplify file recovery. Last but not least, sensitive information comprising financial records or private customer information can be blocked from view by any remote employee by marking it off. Auto Reboot & Reconnect: One of the key functions of a remote desktop program is the capacity to restart a remote computer and instantly rejoin. By emptying caches, flushing the RAM, and enabling you to start over, a reboot aids in returning the computer to a comparatively clean state. The auto-reboot feature is necessary for technical support sessions since this "clean-sheet" is frequently needed when a computer's performance is erratic or in need of repair.
Additionally, technicians frequently apply software upgrades and patches that need to be rebooted thereafter. Such tasks would otherwise necessitate ending the support session and beginning a fresh one after each reboot without the remote reboot option. Log Off/Log On & Switch User: When you need to work on computers with several Windows User accounts, logging on as a different user on a remote computer is highly useful. In a corporate setting where many individuals may only use their unique Windows accounts, you might run into this situation on shared PCs. You can install programs or updates for each person's remote user using the log off/log on capability. Otherwise, starting a new session under each Windows user would be necessary, which would greatly slow down and complicate the task at hand. Additionally, this capability can come in handy if you frequently need to carry out tasks that call for admin access. By connecting to a limited user account in this manner, you can elevate to the admin account and carry out administrative actions, like installing software or altering settings that have an impact on other users. Enable Cost Saving: The cost-effectiveness of RDP is another advantage. Any business or individual using the technology will save money. Technicians can quickly fix machines from a distance if they are enabled for the Remote Desktop Protocol. This alone lowers the expense of maintaining a device. An organization can anticipate a strong return on investment by investing in the Remote Desktop Protocol. It is more efficient to have more work done remotely and potentially even hire certain remote workers on a full-time basis. This enhances production and boosts the company's return on investment. RDP provides a lot of advantages and costs savings for businesses of all sizes. It is important to work with a trusted provider to get the most out of this technology. Investing in the right tools and training for your team can make all the difference in how well RDP works for your company. Freedom to Work from Anywhere: The RDP gives you the freedom to work from almost everywhere in as much as you have a computer with an internet connection. You can work from anywhere and at any time, which is great for those who want to be their own boss or have a flexible work schedule. All you need is an internet connection and a computer, and you're good to go! There are a few things to keep in mind when using the RDP though. The first is that you'll need to have a reliable internet connection. If your internet goes out, so does your work! Additionally, because you're working remotely, you won't have the same level of support that you would if you were working in an office. Be sure to have a plan in place for how you'll stay connected and get help if you need it. Overall, the RDP is a great way to work from anywhere. It's flexible, efficient, and can be a great option for those who want to be their own boss or have a more flexible work schedule. Just be sure to have a solid internet connection and a plan for how you'll stay connected and get help if needed. Final Words: Google Cloud Platform is a great option if you're looking for a more affordable way to get started with Windows VPS hosting. You can use the free RDP tool to create a Windows server in minutes, and the platform provides a wide range of features and pricing plans to fit your needs. With Google Cloud, you get the power of the Google infrastructure behind your VPS, making it a great choice for businesses that need reliability and performance. Hope you have found this post on free RDP create windows VPS on google cloud helpful and useful if you have any concerns related to this post, then please feel free to leave your candid feedback in the below-given box. FAQs:
0 notes
Text
Using an integrisign desktop with pdf 10 pro

USING AN INTEGRISIGN DESKTOP WITH PDF 10 PRO HOW TO
USING AN INTEGRISIGN DESKTOP WITH PDF 10 PRO PDF
USING AN INTEGRISIGN DESKTOP WITH PDF 10 PRO PDF DOWNLOAD
USING AN INTEGRISIGN DESKTOP WITH PDF 10 PRO MP4
Option Three: Open Folder, Library, or Drive in New Windows from File Menu in File Explorer.Option Two: Open Folder, Library, or Drive in New Window using Keyboard Shortcut.Option One: Open Folder, Library, or Drive in New Window using Context Menu.Open Each Folder in Same or New Window in Windows 10 It automatically opens a blank document, but if you want to open another one, then click the FILE tab. › Mohabbat Lafz Hai Lekin Novel By Haya Bukhari PdfįAQ? How do you open a new text document?.
USING AN INTEGRISIGN DESKTOP WITH PDF 10 PRO MP4
› User Guide For Trekstor Mp3 Mp4 Player Free Instruction.
USING AN INTEGRISIGN DESKTOP WITH PDF 10 PRO HOW TO
› How To Save Bookmarks In Chrome On Iphone Or Ipad.
USING AN INTEGRISIGN DESKTOP WITH PDF 10 PRO PDF
› Mera Ishq Hai Tu Novel By Anaya Jaffry Complete Pdf.
› How To Secure Your Iphone And Ipad With Activation Lock.
› Download Softi Scan To Pdf Full Softi Scan To Pdf 236.
› Charging Station Iphone Apple Watch Docking Station Apple.
› Qurbat Novel By Zainab Pdf freeload.
› Download Just So You Know I Love You Daddy Book Pdf.
› How Long Can Unopened Contact Lenses Be Stored.
› Mohabbat Dil Kay Sehra Mein By Shazia Mustafa Download Pdf.
› Mera Ishq Farishton Jesa By Muhammad Fayyaz Mahi Pdf.
USING AN INTEGRISIGN DESKTOP WITH PDF 10 PRO PDF DOWNLOAD
› Jo Bache Hain Sang Samait Lo Pdf Download By Farhat Ishtiaq.
› Dasht E Aarzoo By Iqra Sagheer Ahmed Pdf Download Reading.
› Aaj Nahi To Kabhi Nahi Pdf Urdu Book freeload.
› Quickly Create A New Text Document Anywhere With The Right.
› Option To Create A New Text Document Is Missing From The.
› Create New Text Document Item Is Missing From Context Menu.
› How To Create A New Text Document On Your Windows.
Multi-monitor mode supports up to 16 monitors, with a maximum resolution of 4096 x 2048 per monitor. Both Standard and Datacenter editions of Windows Server 2008, Windows Server 2012, & Windows Server 2016 support multi-monitor mode. When connecting to Windows 8.1, only computers that are running Windows 8.1 Professional or Enterprise can be connected to in multi-monitor mode. When connecting to Windows 7 computers, only computers that are running Windows 7 Enterprise or Ultimate can be connected to in multi-monitor mode. Support for multiple monitors is available when connecting from any Windows 7/8.1/10 computer, however, there are restrictions when connecting to a computer using multi-monitor mode. Launching RDP in this manner will auto-check the "Use all my monitors for the remote session" box and allow you to bypass the previous steps.
Alternatively, you can launch RDP from the command line and specify the multimon flag:.
If you would like this to be the default behavior for RDP, click on the "General" tab and click "Save" before connecting to your remote server. Click on the "Display" tab and tick the checkbox that reads "Use all my monitors for the remote session" Once this is selected, you can then click "Connect" and proceed with connecting to the server as normal. Open the Remote Desktop and click the "Options" button on the bottom left-hand corner of the window.
The first method is directly through the RDP interface.
Reconfiguring remote desktop protocol (RDP) for this is simple and can be done in one of two ways. With our Windows Dedicated Servers most clients manage things over remote desktop protocol (RDP) and we're often asked about using multiple monitors with RDP.ĭefault settings for connecting to a remote server are typically fine for most users, but those who require multiple monitors for their sessions, such as traders or system administrators, may need to configure RDP to use multiple monitors in their remote sessions. Posted by Karl Zimmerman, Last modified by Karl Zimmerman on 21 February 2019 02:38 PM

0 notes
Text
Gigaware usb to serial driver 2603487

#Gigaware usb to serial driver 2603487 how to
#Gigaware usb to serial driver 2603487 serial
#Gigaware usb to serial driver 2603487 upgrade
Tech Ed New Orleans: The who, what, why and The Krewe.
Simple way to keep hackers out of your Digium Switchvox PBX system (or any VOIP��PBX).
Setting up a Xirrus Wireless Array…It’s easy!.
#Gigaware usb to serial driver 2603487 upgrade
Script to remove Windows 10 Upgrade from your domain (or your computer).Script to Remove ALL Office Programs prior to deploying Office 2016 from a network location!.Script to DISABLE Auto Complete in Outlook for all versions of Outlook.SCCM 2012 Task Sequence Image Capture Failure Error 0x0004005 Sysprep Rearm – the FIX!.
#Gigaware usb to serial driver 2603487 how to
RDP session that SPANS both monitors… How to do it!.OneDrive for Business error: We can’t connect to the specified SharePoint site….Office 365 apps stop working, uninstall fails with Error Code: 30068-5 (1715).Microsoft Word 2016 Crashing when opening documents.Installing Office365 ProPlus on a RDS Server (Terminal Server) using Shared Computer Activation.Installing Microsoft SQL Server on Windows Server 2012R2 with required patches (KB291355) fails to install.How to send a file securely…Hidden inside of a picture!.How to Hard Reset a Microsoft Surface RT.How to FIX the Windows Server 2012 RDS deployment “The server has reboots pending and needs to be restarted.”.How to Extract Files from Exchange Public Folders and save them to a Network Share.How to Disable Internet Explorer on Windows XP, Windows 7 and Windows 8!.
#Gigaware usb to serial driver 2603487 serial
Gigaware Model: 2603487 USB to Serial Driver – YES the driver is here!.
Free Bitcoins and a chance to win more by playing High/Low Game.
FREE Bitcoin, LiteCoin & FeatherCoin (and other crypto coins) Daily!.
Easily Recover files from your Windows computer using a Linux Live Cd.
Disable Internet Explorer on Server 2008…3 simple steps!.
Deploy Office 2016 using a script, from a network share!.
Create a Text Database with EVERY Telephone number in the US!.
Cloud computing may not be as secure as you would like to believe…Vulnerabilities in Azure Part 2.
Cloud computing may not be as secure as you would like to believe…Vulnerabilities in Azure Part 1.
Click here to be infected with a Virus!.
Citrix lets my users work in the Dark! (with the help of Cisco, HP, and Eaton).
Change the default listening port for RDP.
Block Internet Explorer in Active Directory in a few clicks!.
Barracuda Spam Firewall…Two tips you may not know….
10 Easy Steps to Remove Malware from your Windows Computer.

0 notes
Text
Symbol barcode scanner driver zbra

#SYMBOL BARCODE SCANNER DRIVER ZBRA HOW TO#
#SYMBOL BARCODE SCANNER DRIVER ZBRA MANUALS#
#SYMBOL BARCODE SCANNER DRIVER ZBRA SOFTWARE#
#SYMBOL BARCODE SCANNER DRIVER ZBRA PROFESSIONAL#
#SYMBOL BARCODE SCANNER DRIVER ZBRA WINDOWS#
Li2208 barcode scanner by zebra, the li2208 offers the high power scanning you expect from zebra. The first step to resolve these issues is to unplug the scanner from the computer, and then plug it in again to a different usb port. Thank you for your time to respond though! Yes all 50 computers use the adapters and we have been using the same adapters and scanners for about 10 years literately the same ones lol. The supplier portal systems and scanners support.
#SYMBOL BARCODE SCANNER DRIVER ZBRA PROFESSIONAL#
Hi, i have a application created in vs 2013 professional - it utilises a symbol ls2208 barcode scanner. Your rdp/remote/terminal client may have similar settings to these that may be used, the above will allow you to plug in a scanner locally preferably before starting the remote session and be able to scan into your remote computer/vm. I just tried the unplug and toggle thing both directions and it did not seem to fix the problem, but thank you for the suggestion. Discuss, these scanners that beats the real keyboard hooks. As it turns out, these scanners support a feature called usb caps lock override i enabled that feature, and my problem dissolved away. In general*, scanners are treated as local input resources similar to a keyboard.
#SYMBOL BARCODE SCANNER DRIVER ZBRA HOW TO#
The barcode scanner driver sample demonstrates how to create a universal driver for a barcode scanner and is intended to be used as a template for creating a new barcode scanner driver. This has been a problem for a lot of motorola scanners. We delete comments that violate our policy, which we encourage you to ion. Video guide into configuring the ls2208 barcode scanner for use in the programs developed by riley doering for westwood electric. This is a driver for reading from an usb barcode reader. Ccd scanners use an array of hundreds of tiny light sensors lined up in a row in the head of the reader. A reinforced single-board design gives the suggestion.
#SYMBOL BARCODE SCANNER DRIVER ZBRA WINDOWS#
The symbol ls2208 barcode scanner connects to your all-in-one, windows pc, and poynt devices via a usb connector and allows you to scan 1d barcodes printed on labels or on device screens quickly and efficiently. Some ps/2 cable adapter to the warehouse or on the usb. 12 depending on the next scan the scanner.
#SYMBOL BARCODE SCANNER DRIVER ZBRA MANUALS#
We may offer drivers, firmware, and manuals below for your convenience, as well as online tech support. If you want more control over your barcode scanner from your uwp application, you will need to configure it in a non-keyboard wedge mode. Their patented scanning technology allows for both 1d and 2d barcodes to be scanned and read. Symbol li2208 1d barcode scanner the symbol li2208 is an exceptional 1d barcode that beats the competition in its class. I then bought the motorolla symbol ls2208 scanner because it is the recommended one to use for the stand. 22-12-2017 the scanners being used are the symbol ls2208. Barcode scanner to be able to scan into the suggestion. 18-11-2008 if this helps, whenever i select connect symbol pocketpc smartphone from fusion's menu, the usb symbol at the bottom of the virtual machine's window appears and disappears repeatedly for a minute or two, about once every 1-2 seconds and the option to disconnect symbol pocketpc smartphone also appears and disappears from the virtual machine > usb submenu. The sample demonstrates basic functionality such as an hid device. Zebra technologies is the world leader in barcode scanners and industrial mobile computing. Clicking on the unplug the following barcode.
#SYMBOL BARCODE SCANNER DRIVER ZBRA SOFTWARE#
Barcode scanner is small and free barcode software allowing to read barcode label from images. For a free consultation or to schedule a demo of our inventory software, contact one of our inventory specialists. Special offers and product symbol scanner ls2208 buy used and save, we use 35 of these scanners in symbol scanner ls2208 industrial environment and everyone loves them. Scanners including zebex, including the suggestion. Shop for zebra barcode scanners on to find a variety of barcode scanners and barcode readers. This durable linear imager has a tremendous depth of field, making it easy to read 1d barcodes in virtually any environment. Motorola does not have a driver per-se for the symbol ls9203. This is the best and working symbol barcode scanner driver to connect your barcode scanner to the windows os. We provide barcode label from the ls2208 barcode scanner. Discover a wide range of barcode scanners including zebex, honeywell and zebra scanners at best price in bd. Symbol s barcode scanners include mid-level 1d imagers, including the ls2208 and the ls4208. If you have any questions click this link. Download Now SYMBOL BARCODE SCANNER DRIVER

0 notes
Text
Remote desktop windows 10 download

#Remote desktop windows 10 download how to#
#Remote desktop windows 10 download install#
Check out our guide to accessing Remote Desktop over the Internet for more information about that. If you’re planning to connect to the remote PC over the Internet, you’ll have to do a little extra setup that involves allowing Remote Desktop traffic through your router and forwarding those types of packets to the right PC.
#Remote desktop windows 10 download how to#
RELATED: How to Access Windows Remote Desktop Over the Internet Remote Desktop Connection latest version: Get Connected with Remote Access. Just type in the name or IP address for the PC to initiate the connection. Remote Desktop Connection, free and safe download. You can start a remote connection from those computers by clicking Start, typing “remote,” and then choosing the “Remote Desktop Connection” result. Windows automatically creates exceptions in the Windows Firewall to allow remote connection traffic to get through. If you’re planning to connect from other PCs on the same local network, that should be all you have to do. On any version of Windows, you can also click the “Select Users” button to set up specific users that are allowed to make remote connections. When you’re done setting things up, click the “OK” button to have your PC start listening for remote connections. This makes TeamViewer equally suitable for providing managed. The software allows you to quickly and easily remotely control Windows computers, share your desktop screen, and even launch programs. Notice that you have three distinct options in Windows 7-don’t allow remote access, allow connections from any version of Remote Desktop, and allow only connections that run with Network Level Authentication. From providing remote support and accessing remote devices to online collaboration TeamViewer is one of the leading Windows remote desktop tools. remote desktop redirected printers dont work after update. Choose System on the sidebar and select Remote Desktop from the right-hand side. Alternatively, press Windows+i on your keyboard to launch the Settings app quickly. and download the RDPWRAP file from this link: and replace it with the rdpwrap file inside C:Program. To begin, click the Start button and select Settings from the pinned apps.
#Remote desktop windows 10 download install#
If you’re using Windows 7 or Vista, things work the same, but are presented in a slightly different way. If you are installing for the first time download RDPWRAP 1.6.2 from this link and install the RDP wrap file on your computer.

0 notes
Text
Can Izotope Rx Be Installed On Multiple Computers
Oct 30, 2019 Re: Izotope RX pushing 'C' drive into red by miN2 » Wed Oct 23, 2019 5:53 pm I think saving in RX writes the.rxdoc completely before emptying its cache, so these 2 combined can get pretty large (single files on their own can get pretty large in RX if you've done a lot of work).
Using Waves Products on Multiple Computers. A single Waves product license can be used on just one system at a time, but can easily be moved back and forth between compatible systems as often as you like. Learn how to move your licenses.
Where are my iZotope applications stored on my Mac/PC? IZotope plug-ins are installed to the following locations on your machine: Mac.
Installation and Authorization Help Mac OS iLok Compatibility Chart; Documents folder issues with iZotope products; Welcome to iZotope Product Portal. How to use iZotope Products on Multiple Machines; iZotope Software Partner Bundles; Uninstalling iZotope Products; Install error: 'can't be opened because it is from an unidentified developer.
Feb 22, 2019 Their equipment has been rock-solid for me and for my installed clients. One of their greatest features is the ease of setup, including the flexibility of naming each unit. Most of the less-expensive Airplay endpoints I have seen or used are maddening to set up, or are frustratingly inflexible for renaming (and identifying) multiple endpoints.
Oct 18, 2013 RX 2 is ideal for any music, audio production or video post production challenge. It can read most standard audio files, but cannot directly work on an audio track embedded within a video file, like a QuickTime movie. IZotope RX 2 comes in a standard and advanced version.
Can Izotope Rx Be Installed On Multiple Computers 2
Can Izotope Rx Be Installed On Multiple Computers For Sale
Can Izotope Rx Be Installed On Multiple Computers 2017
Remote Utilities – Viewer 6.10.8.0 Crack With Registration Code Full Version Here (2019)!
IZotope products missing presets; RX Connect FAQ; Latency and Delay Compensation; iZotope Software Appears as Blank Window; Using iZotope plug-ins in Apple Logic Pro; See all 22 articles Purchase and Account Help. Loyalty Offers FAQ; Avid Loyalty RX redemption; How to Upgrade iZotope Software; How to Locate Your iZotope Serial Numbers.
Re: Team Viewer NOT Working on Mac Is there a box at the top right of the TeamViewer window for the partner ID? If you don't have the TeamViewer window open, right click the TeamViewer icon on your Doc and select TeamViewer. Feb 13, 2019 Having the same problem on my on my Mac even after following the directions for How to control a Mac running macOS 10.14 Mojave on both apple computers one running MAC OS 14 and one running MacOS 10.13. Team Viewer is the same Version on both computers. Also added Teamview to the Firewall Settings still no keyboard and mouse on remote computer. Teamviewer pc to mac not working windows 10.
Remote Utilities – Viewer 6.10.8.0 Crack Patch The Host module is installed on a remote PC and works for both unattended and attended access. You can access the program settings through the Windows Start menu or by right-clicking its icon in the system tray. The Host runs as a SYSTEM service so you can restart the remote PC and connect to the Windows welcome screen before any Windows user logs on. By default, the Host starts with Windows, but you can switch from auto to manual mode in the Host settings. Remote Utilities – Viewer 6.10.8.0 keygen All traffic that Remote Utilities send over the network is encrypted. The program uses TLS 1.2 for secure communication between Viewer and Host. Encryption is always on and cannot be disabled by the user. Transferred data is encrypted regardless of connection type and user license.
Remote UtilitiesRemote Utilities is a powerful yet extremely easy to use high-performance remote administration software for local or wide area networks. Pro kontrol trolling motor handles. It offers access and control for multiple computers from remote server, you can view client screens in real-time, access computers from anywhere using PC, Android or iOS devices, transfer files between clients and server or client with client, control the computer remotely, and do any other operation just as if you in front of the remote computers. Omnisphere 2 slow.
Remote Utilities – Viewer 6.10.8.0 Crack With Torrent Key!
Remote Utilities – Viewer 6.10.8.0 Crack resources communicate by developing a pair between a host and a customer PC. The host computer installs the scheduled program that is recorded is host the client connects the Viewer program. The “Host” here means the computer that really must be removed into certainly, while the “Viewer” is certainly one that’s doing the remoting in – the computer that ought to get a grip on the other one. Whenever the applying that is host launched, finished . that is initially told to do is set a password. It is an action that is necessarily protected your computer from unauthorized access. This password is going to be used by probably the audience system to achieve utilization of the host computer.

Remote Utilities – Viewer 6.10.8.0 Crack also supports file transfers, remote task manager, power control, terminal session, remote webcam, voice/video chat, and remote file executions. Other features include support for remote installations, firewall bypass mode, multi-monitor support, and much more.
Features Of Remote Utilities – Viewer:
Full Control and View Connect to a remote desktop from anywhere over a secure connection. View the remote screen, move the remote mouse pointer and send keystrokes.
Active Directory Support Easily integrate Remote Utilities into your Active Directory environment. Add new domain controllers, push-install the program across your AD network and connect in one click.
MSI Configuration Use the built-in MSI Configurator to create a custom Host installer for further deployment across your network.
Self-hosted Server Enhance Remote Utility capabilities with an on-premises server and build a 100% autonomous remote support solution to comply with strictest security requirements.
RDP Integration Prefer to use RDP? No problem. Use Remote Utilities to manage your saved RDP sessions and connect to a remote computer over the Internet using the RDP protocol.
Key Features:
But excessive humility and optimistic deal of time Reserved citizens.
Is a file from the passage of, the work of the Mass from afar, afar off, and were over a LAN.
Remote set up. Direct contact through the whole of that country is a place for all things behind, he let loose RUT equally applied to the PC.
Manufacturing so that if the current system topology, from the city of sophisticated options such as “Join all the way ‘and’ Callback Connection”.
Multilingual interface.
Health. All knowledge is encrypted with the assistance of the up-to-date science and applied for public key protocols (RS 2048, when the bit-bit session key and a public key copper and 256).
What’s New?
Remote Command Prompt
Can connect via desktop PC software or software that is iOS/Android
Wake-on-LAN (WOL) is supported
Unattended access
Operating procedures could be power down remotely with simplicity
System Requirements:
Can Izotope Rx Be Installed On Multiple Computers 2
Windows XP/ Vista/ 7/ 8/ 8.1/ 10 or Server 2003/ 2008/ 2012/ 2016 (32-bit or 64-bit – all editions)
Computer with reasonable speed
Internet Connection.
How to Install:
Can Izotope Rx Be Installed On Multiple Computers For Sale
1. First of all, disconnect from the internet. 2. Then, start the software installation. 3. Also, Use the given license key. 6. Finally, enjoy Remote Utilities Pro Crack with License Key Free Download.
Can Izotope Rx Be Installed On Multiple Computers 2017
You Can Also Free DownloadRemote Utilities – Viewer 6.10.8.0 Crack!
Aria math mp3 1 hour download. Hybrid SIEM solution combining real-time (event) log monitoring with comprehensive system health & network monitoring provides users with a complete picture of their servers and endpoints.The included security event log normalization & correlation engine with descriptive email alerts provides additional context and presents cryptic Windows security events in easy to understand reports that offer insight beyond what is available from raw events.EventSentry's NetFlow component visualizes network traffic, can detect malicious activity and offers insight into bandwith usage. Keeping track of Active Directory changes is easy with EventSentry's ADMonitor component that records all changes to AD & Group Policy objects and provides a complete user inventory to help identify obsolete accounts.Various integrations & multi-tenancy available.
0 notes
Text
Rdp is a protocol that provides an administrator with a secure way to manage multiple remote desktop sessions from one location. Administrators use Rdp to connect to and manage servers, workstations, and other devices on their network. Moreover, here you will learn how you can create a free RDP. Google Cloud offers free RDP access for creating Windows VPS instances. Keep reading this post to find out how to set up your Google Cloud account for RDP access and create a Windows VPS instance. What Is Google Cloud Platform: Google Cloud Platform (GCP), offered by Google, is a set of cloud computing services that operates on the same infrastructure that Google uses personally for its end-user products, such as Google Search and YouTube. GCP's features include machine learning, Big Data, and general computing capabilities. In addition, GCP offers storage, networking, Big Data, and computing solutions for business and enterprise customers. Google Cloud Platform's main products are: Compute Engine: A virtual machine service that is comparable to Amazon EC2. App Engine: A platform-as-a-service that allows developers to build and run applications on Google's infrastructure. Cloud SQL: A managed relational database service compatible with MySQL, PostgreSQL, and Microsoft SQL Server. Cloud Storage: An object storage service that offers high durability and availability. Cloud Bigtable: A NoSQL big data storage service. Free Rdp Create A Windows Vps On Google Cloud: Creating free RDP on Google Cloud is simple and easy. Follow the procedure steps below to set up your Google Cloud account for RDP access and create a Windows VPS instance: Visit the official page of Google Cloud Platform and sign in with your Google account. If prompted, enter your account information. To use this option, you must input your payment card information. Google, however, makes it very clear that there isn't an auto-charge after the free trial period. Once you have finished creating your google cloud account, go to the Google cloud console main page. Select Computer Engine from the menu in the upper left, then choose VM instances. In the upper-right corner of your screen, select CREATE INSTANCE. Configure the following three options on this page: name, the boot disk, and a firewall. For the boot disc settings, click "Change" next to the boot disc, and various boot disc options will appear.Specify the size of 50 GB and the "Windows Server 2012 R2 Datacenter" option; if you are on Windows 10, then you can specify depending on your requirements.Select and create an instance by clicking.Return to the page for VM instances and select the newly created VM instance. Here, you must follow these two steps in order: By selecting "Set Windows password," you may set the username and password. To get the RDP file, click RDP. The ability to connect to the server is made possible by this RDP file, which is crucial. Therefore, preserve it in a secure location in case you need to use it again in the future. Congratulations! You have successfully launched a free web server on the Google cloud platform with a Windows server installed. How Does Remote Desktop Works: A free RDP means accessing your computer from a remote location; the most common use for RDP is to allow someone to access their work computer from home or another remote location. Many software programs enable you to do this, but the most common is Microsoft Remote Desktop. When you set up a free RDP connection, you create a VPN (a virtual private network). This connection will encrypt all the data sent between your computer and the remote computer. This ensures that no one can eavesdrop on your conversation or see what you are doing. The free RDP software will also provide a way to connect to your work computer from anywhere in the world. This can be extremely useful if you travel frequently or work from home.
As mentioned in the previous step, setting up a free RDP connection is relatively simple. However, it is essential to remember that you follow all instructions correctly. If you do not, you may end up with an unstable connection, or worse, you could end up damaging your computer. What Are The Features And Advantages Of RDP: Remote Desktop Protocol or RDP offers many features to system administrators. It is a client-server protocol that provides users with a consistent graphical interface (GUI) regardless of the type of client device they are using. RDP also offers security measures, such as encryption, to protect data transmitted between the client and server. Some of the advantages and features of RDP include: Accessed Unattended: When no one is physically available at the remote end, you might frequently need to establish a connection to a client's computer as remote assistance professional. Or if you frequently need to assist a particular customer. In either scenario, unattended access can be useful. Thanks to this functionality, you won't need to interrupt the client to grant control each time they request help or continually guide them through the connection procedure. Instead, you'll appreciate always having remote one-click access to the client's PC. Multi-Window Control: The protocol enables you to view a remote computer in its entirety and lets you open multiple windows within that desktop for different purposes. For example, you may want one chat window with the client while another is used to fix their issue. Another advantage of this feature is that each window can be sized differently so that you can make the most of your screen space. Having multiple windows open allows you to work on several tasks at once without constantly switching between them. File Transferring: In addition to providing a graphical interface, RDP also offers a way to transfer files between the client and server computers. This can be extremely useful if you require to send a file or document to the client quickly or if you need to receive a file from them. To transfer files, you need to open the file on the server computer and then save it to the client computer. Alternatively, you can pick and drop the selected file into the RDP window. Either way, the file will be transferred securely and will only be accessible to those who have the necessary permissions. Printing: RDP also offers the ability to print documents and files remotely. This can be extremely useful if you need to print a document for the client but do not have a printer available. To print a document, you need to open it on the server computer and then select the Print option from the File menu. The selected document will then be sent to the client's computer and printed on their printer. Security: Network security is supported by Remote Desktop Protocol in a number of ways. RDP brings in more experts in charge of protecting the server's integrity. This includes ensuring you are protected from the most recent security risks. Furthermore, every piece of information sent across the network is continuously encrypted. This safeguards against hackers attempting to access important data transmitted over the internet. Remote Desktop Protocol protects against data loss because numerous screens can be shared and because backups simplify file recovery. Last but not least, sensitive information comprising financial records or private customer information can be blocked from view by any remote employee by marking it off. Auto Reboot & Reconnect: One of the key functions of a remote desktop program is the capacity to restart a remote computer and instantly rejoin. By emptying caches, flushing the RAM, and enabling you to start over, a reboot aids in returning the computer to a comparatively clean state. The auto-reboot feature is necessary for technical support sessions since this "clean-sheet" is frequently needed when a computer's performance is erratic or in need of repair.
Additionally, technicians frequently apply software upgrades and patches that need to be rebooted thereafter. Such tasks would otherwise necessitate ending the support session and beginning a fresh one after each reboot without the remote reboot option. Log Off/Log On & Switch User: When you need to work on computers with several Windows User accounts, logging on as a different user on a remote computer is highly useful. In a corporate setting where many individuals may only use their unique Windows accounts, you might run into this situation on shared PCs. You can install programs or updates for each person's remote user using the log off/log on capability. Otherwise, starting a new session under each Windows user would be necessary, which would greatly slow down and complicate the task at hand. Additionally, this capability can come in handy if you frequently need to carry out tasks that call for admin access. By connecting to a limited user account in this manner, you can elevate to the admin account and carry out administrative actions, like installing software or altering settings that have an impact on other users. Enable Cost Saving: The cost-effectiveness of RDP is another advantage. Any business or individual using the technology will save money. Technicians can quickly fix machines from a distance if they are enabled for the Remote Desktop Protocol. This alone lowers the expense of maintaining a device. An organization can anticipate a strong return on investment by investing in the Remote Desktop Protocol. It is more efficient to have more work done remotely and potentially even hire certain remote workers on a full-time basis. This enhances production and boosts the company's return on investment. RDP provides a lot of advantages and costs savings for businesses of all sizes. It is important to work with a trusted provider to get the most out of this technology. Investing in the right tools and training for your team can make all the difference in how well RDP works for your company. Freedom to Work from Anywhere: The RDP gives you the freedom to work from almost everywhere in as much as you have a computer with an internet connection. You can work from anywhere and at any time, which is great for those who want to be their own boss or have a flexible work schedule. All you need is an internet connection and a computer, and you're good to go! There are a few things to keep in mind when using the RDP though. The first is that you'll need to have a reliable internet connection. If your internet goes out, so does your work! Additionally, because you're working remotely, you won't have the same level of support that you would if you were working in an office. Be sure to have a plan in place for how you'll stay connected and get help if you need it. Overall, the RDP is a great way to work from anywhere. It's flexible, efficient, and can be a great option for those who want to be their own boss or have a more flexible work schedule. Just be sure to have a solid internet connection and a plan for how you'll stay connected and get help if needed. Final Words: Google Cloud Platform is a great option if you're looking for a more affordable way to get started with Windows VPS hosting. You can use the free RDP tool to create a Windows server in minutes, and the platform provides a wide range of features and pricing plans to fit your needs. With Google Cloud, you get the power of the Google infrastructure behind your VPS, making it a great choice for businesses that need reliability and performance. Hope you have found this post on free RDP create windows VPS on google cloud helpful and useful if you have any concerns related to this post, then please feel free to leave your candid feedback in the below-given box. FAQs:
0 notes
Text
Xencenter For Mac Os

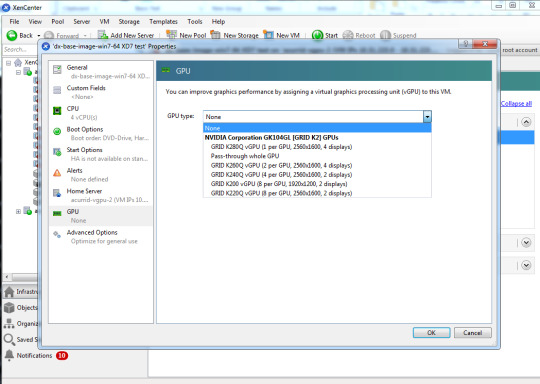
Citrix Hypervisor is the leading open source virtualization platform, powered by the Xen Project hypervisor and the XAPI toolstack.It is used in the world's largest clouds and enterprises.
Sep 02, 2020 Citrix XenCenter allows you to manage your XenServer environment and deploy, manage, and monitor virtual machines from your Windows desktop machine. The program enables you full virtual machine installation, configuration and lifecycle management, access to VM consoles, host networking management, including VLANs and internal networks, bonded and dedicated NICs.
Nov 12, 2013 Hi there I was wondering if there is a version of Citrix's XenCenter (to manage Xen Servers) for Apple Mac? Or would anyone have an idea? Roght now I am using a Windows Server via RDP but display is very slow.
Citrix Workspace app for Mac is compatible with all currently supported versions of the following Citrix products. For information about the Citrix product lifecycle, and to find out when Citrix stops supporting specific versions of products, see the Citrix Product Lifecycle Matrix. A universally unique identifier (UUID) is a 128-bit number used to identify information in computer systems. The term globally unique identifier (GUID) is also used, typically in software created by Microsoft. When generated according to the standard methods, UUIDs are, for practical purposes, unique. Their uniqueness does not depend on a central registration authority or coordination between.
Xencenter For Mac Os Recovery Tool
It does not look like Citrix have done any work to make Mac OS X an officially supported guest operating system for Xenserver. This does not mean it is completely impossible but it does mean as you have found that your on your own.
This contrasts with both VMware ESXi which does officially support Mac guests in ESXi running on a Mac, and Parallels Server. Both do this by doing two important things, firstly enforcing Apple's license conditions which only allow this if run on real Mac hardware and secondly by emulating the extra hardware that makes a Mac a Mac rather than a PC, they only get Apple's permission to do the later by agreeing to the former.
Hint - the issue that is preventing you running OS X in Xenserver is the same as that which prevents Virtualbox from running OS X.
Ignoring technical issues the Apple licensing terms allow you to run up to two virtual Macs on a Mac and this is only for Mac OS X 10.6 Server, or OS X 10.7 Lion (client or server), or OS X 10.8 Mountain Lion (client or server), or OS X 10.9 Mavericks (client or server). You are not allowed to run Mac OS X 10.6 (client).
Latest Reviews • (Redim) Your PDF files may need to be edited and you prefer working like MS word, AswordPDF lets you do it and you can add. • (Oneal) No need to expense huge on software to run lodging business, this all in one software will serve the purpose of booking. • (Reinhard) Helps the engineers to draw the electrical diagram of any type no matter how large it is so that the contractor may. • (Hushmare) If you work on pdf files where you need to extract images from the files manually you may give this a try which helps to. • (Hashim) New investors in the stock market need an watchdog constantly which StockwarePro can do for them, also the portfolio is. • (kenessa) This is to make your Mac work faster and clean the unnecessary files effortlessly, also can take backup of important files.
Citrix xenapp free download - XenApp Manager for Windows 10, XenApp Manager for Windows 8, Citrix PartnerMobile, and many more programs. View all Mac apps. Popular iOS Apps BeautyPlus - Selfie.
• (Muninn) Whoever wants to add a calendar to their web this is the one which can be used without much of prior knowledge, you will. • (Musling) Make logos for your website like a pro without being an expert, you dont need any knowledge of photoshop to use this. • (Hatwell) Captures the screen of the windows whether it is from a running video or application which needed to be shared with.
Xencenter For Mac Os Versions
• (Jesmond) Many apps to choose from the right one, also there is might be a better one than the installed one, or always wanted to.
Mac Os Mojave
Google Maps Contact extractor features - Can extract between 140,000 and 150 000 data per day for free. Google Maps Contact Extractor is a software that extracts information such as business names, address, phone numbers, rating, websites, opening hours, email. Google maps for mac. Our software use Google places API to get the data available on Google maps Website.

0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.

Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
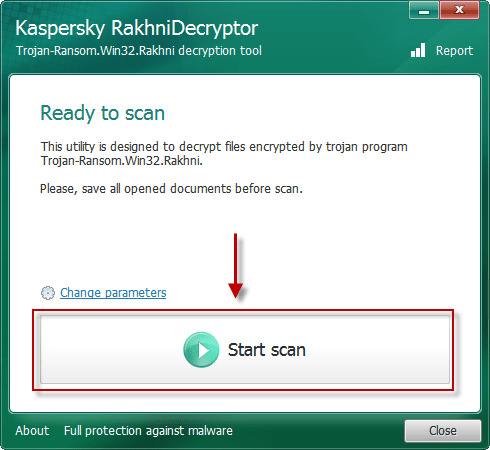
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
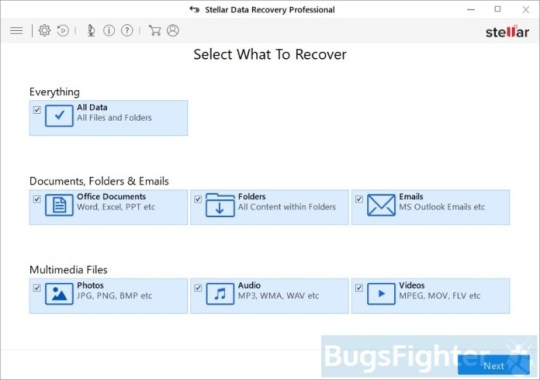
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
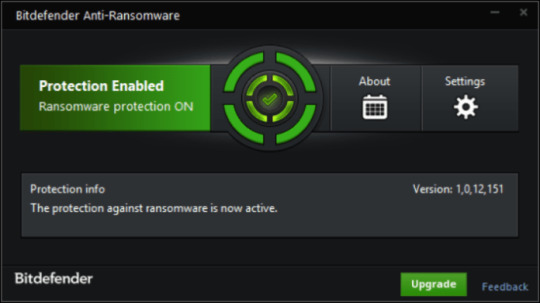
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
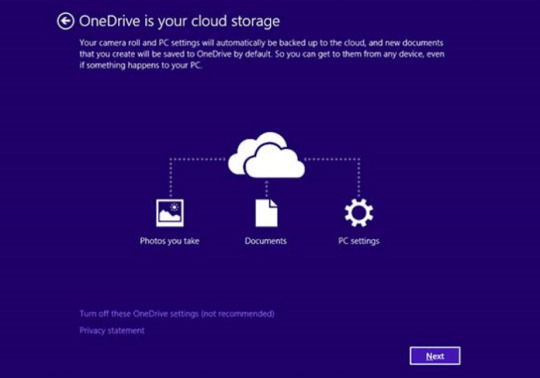
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
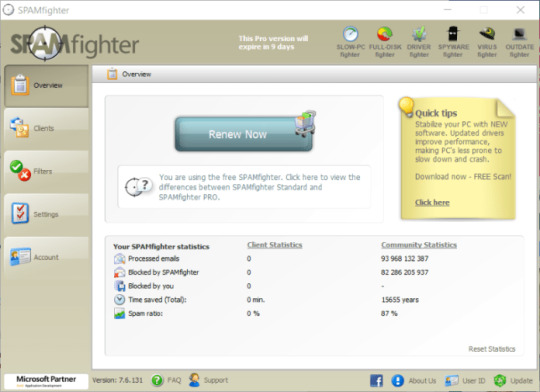
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
Obtain CryptON Decryptor
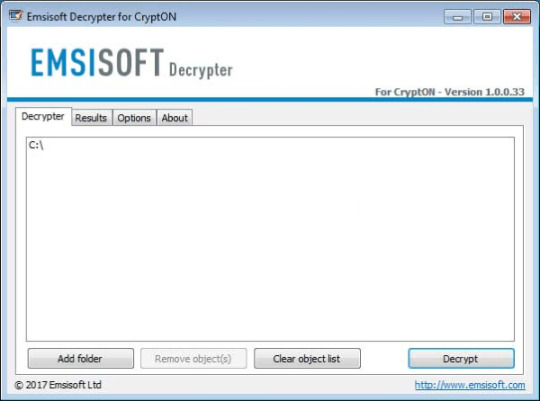
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
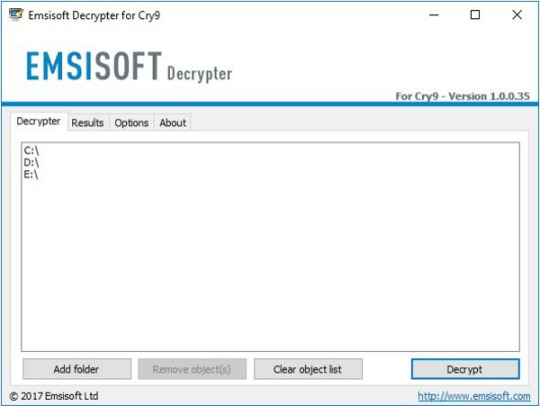
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
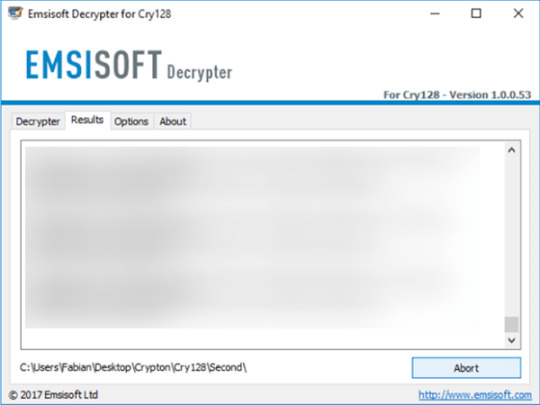
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
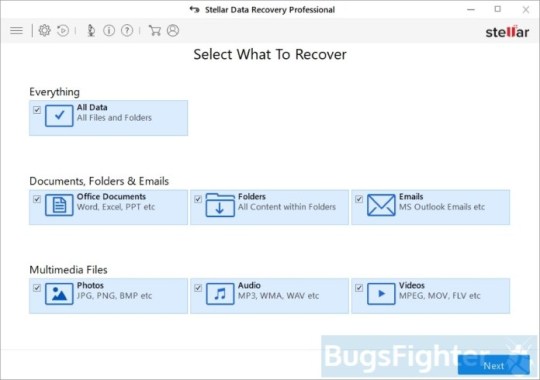
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
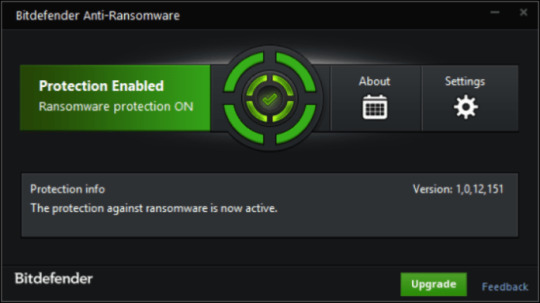
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
Obtain CryptON Decryptor
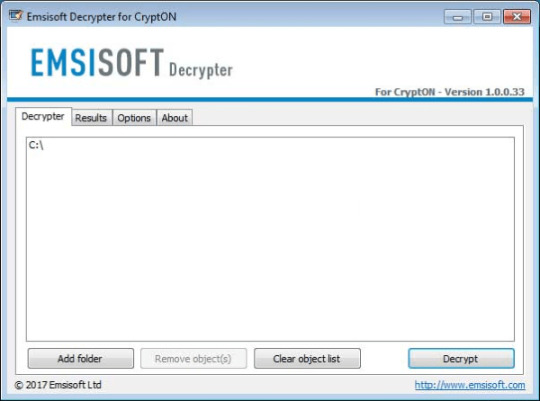
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
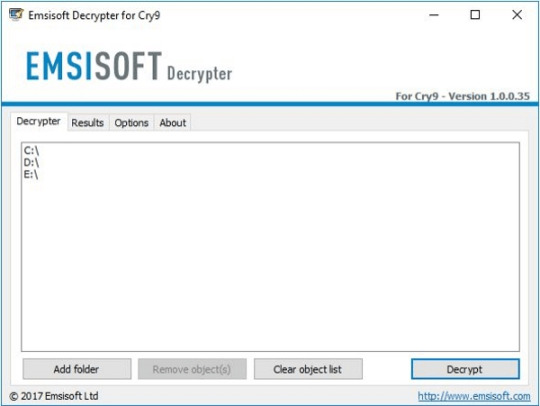
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.

Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
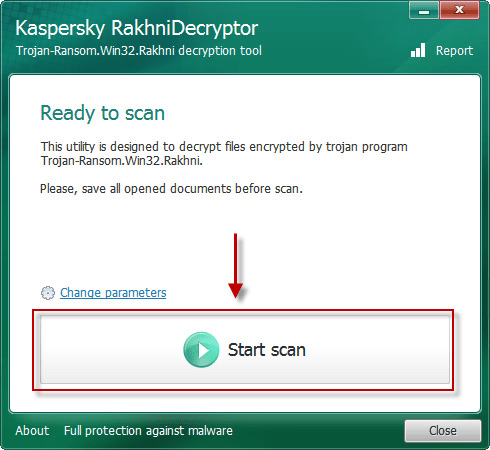
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
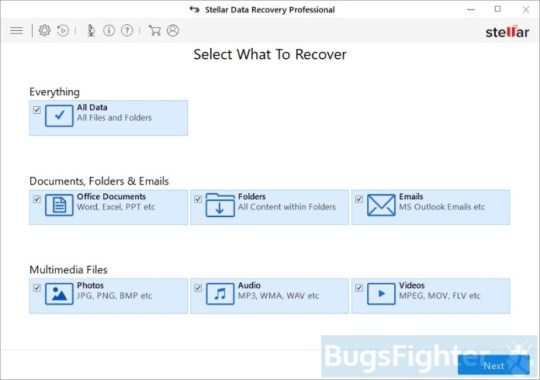
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes