#how to send form data to servlet
Explore tagged Tumblr posts
Text
What is servlet ? Explain GET and POST methods of servlet.
What is servlet ? Explain GET and POST methods of servlet.
A servlet is a class of Java programming language used to extend the capabilities of servers that host applications accessed via a request-response programming model.
सर्वलेट जावा प्रोग्रामिंग भाषा का एक वर्ग है जिसे सर्वर की क्षमताओं का विस्तार करने के लिए उपयोग किया जाता है, जो कि अनुरोध-प्रतिक्रिया प्रोग्रामिंग मॉडल के माध्यम से होस्ट अनुप्रयोगों को होस्ट करता है।
Although servlets can respond…
View On WordPress
#difference between get and post in java#difference between get and post method in servlet with example#doget method in servlet example#dopost method in servlet#get and post method in servlet with example#how to send form data to servlet#http servlet request and response example#java servlet form example#What is servlet ? Explain GET and POST methods of servlet.
0 notes
Text
SociFlux Review
A website is a collection of publicly easily accessible, interlinked Website that share a single domain. Websites can be produced and kept by a private, group, service or organization to serve a selection of functions. With each other, all openly obtainable internet sites comprise the Net. Web sites are available in a virtually countless range, consisting of instructional websites, news sites, forums, social networks websites, shopping websites, as well as so on. The web pages within a site are typically a mix of text as well as various other media. That stated, there are no regulations determining the form of a website. A person can produce a web site of just black as well as white photos of roses, or words pet cat connected to one more Websites with words mouse. However, many sites adhere to a conventional pattern of a homepage that connects off to various other groups and material within the website. Initially, web sites were categorized by their high-level domains. Some instances include: Federal government company web sites =. gov School' websites =. edu Not-for-profit organizations' sites =. org Business sites =. com nformation websites =. info Although these top-level domains expansions still exist, they say little about a web site's real material. In the contemporary internet, the.com expansion is without a doubt one of the most prominent domain, a long with lots of other country-specific expansions. A fixed website is one that has actually websites stored on the server in the format that is sent out to a client web browser. It is largely coded in Hypertext Markup Language (HTML); Cascading Style Sheets (CSS) are made use of to control look past standard HTML. Images are generally used to effect the preferred look and also as component of the major material. Sound or video clip could additionally be thought about static web content if it plays immediately or is typically non-interactive. This kind of internet site usually shows the exact same information to all visitors. Comparable to distributing a printed brochure to clients or customers, a fixed web site will usually offer regular, standard details for a prolonged period of time. Although the site owner may make updates periodically, it is a hands-on procedure to modify the text, images and also other web content as well as may need basic web site style abilities as well as software application. Easy kinds or advertising and marketing instances of web sites, such as timeless website, a five-page internet site or a brochure website are typically static websites, since they provide pre-defined, fixed details to the customer. This might include information concerning a firm and its product or services through text, photos, computer animations, audio/video, and navigating food selections. An example of an excellent web site is: %LINK%. A dynamic website is one that alters or customizes itself often as well as immediately. Server-side dynamic pages are generated on the fly by computer system code that produces the HTML (CSS are accountable for appearance as well as hence, are fixed data). There are a vast array of software application systems, such as CGI, Java Servlets as well as Java Server Pages (JSP), Active Server Pages as well as ColdFusion (CFML) that are available to produce dynamic internet systems as well as dynamic websites. Numerous internet application frameworks and web design template systems are offered for general-use shows languages like Perl, PHP, Python as well as Ruby to make it faster and also much easier to create complicated dynamic websites. Early web sites had just text, as well as not long after, photos. Web browser plug ins were then made use of to include sound, video, as well as interactivity (such as for an abundant Web application that mirrors the intricacy of a desktop application like a word processing program). Instances of such plug-ins are Microsoft Silverlight, Adobe Flash, Adobe Shockwave, as well as applets created in Java. HTML 5 consists of arrangements for sound as well as video without plugins. JavaScript is also constructed into a lot of contemporary web browsers, as well as enables website makers to send code to the internet browser that instructs it exactly how to interactively modify page content and also connect with the web server if needed. The web browser's internal depiction of the web content is referred to as the Document Object Model(DOM) as well as the method is recognized as Dynamic HTML.
Click here to watch SociFlux Review:
https://www.youtube.com/watch?v=XbiZnRH_E4I
youtube
1 note
·
View note
Text
Can We Make Website Using Java?
Can We Make Website Using Java? If you are interested in creating a dynamic website, you can try Java. This language allows you to embed HTML code into the code, making it easier to create dynamic pages. However, you will need a Servlet Container to run Java classes. The Apache Software Foundation offers a free version called Tomcat. Servlets Servlets are a type of web application that uses the Java language to process data. These applications are very secure and provide a robust way to display and post data. However, before you can use Servlets on your website, you need to understand the underlying concepts. A good way to learn Servlets is to start with a pet project. These projects will help you develop your skills in the area. Servlets are implemented using the Servlet interface. The most common type of servlet is HttpServlet, which is a subclass of GenericServlet. These servlets implement the Servlet interface and are typically managed by methods such as init(), service(), and destroy(). Once a servlet is loaded into the Servlet container, the container invokes the init() method, which runs only once. This method is used to initialize any costly resources and read persistent configuration data. JSP pages Java is a language used for creating web applications and serving them. However, this technology is not appropriate for creating a website itself. Some examples of websites made using Java include JSP (Java Server Pages) which is quickly becoming outdated. Instead, most web developers opt for a JavaScript framework to build the front-end, and Java on the back-end. This approach is known as REST. Java is a cross-platform programming language and is object-oriented. This means that it runs on almost any operating system. This is one of the reasons why java developers recommend building a website using it. Moreover, java codes are portable and can run on any device. Therefore, you don't need to spend time or money developing for different platforms or devices. Servlet container A Servlet container is a component of a web server that provides a runtime environment for JavaEE applications. It also provides input reading capability. It is a component of Tomcat and JBoss web servers. Essentially, a servlet is a Java class that is registered with the web container. The container invokes the init() method to create the servlet object, and then directs incoming requests to its service() method. The servlet then destructs itself when it has completed processing. Servlets are server-side components that are shared by multiple requests. Servlet containers are multi-threaded, meaning that multiple threads can use the same instance. If each request made to a single Servlet is made on the same thread, it would be incredibly expensive to create new instances of the servlet container. Thus, if a servlet container is used to make a website using java, it will reduce the need for creating many instances of the Servlet class. Servlet code If you want to make a website using java, you can use Servlet code for making it. It will automatically compile your JSP file into a Servlet class. You can see how this works below: The browser sends a request to the server and the servlet responds with a page that contains the HTML form. A servlet uses the HTTP protocol to communicate with the browser. A client sends a request message to a servlet, which then sends a response back to the browser. A servlet has a header, which provides information about the request. Each header contains name-value pairs. You can access these values with methods like getRequestURI(), getQueryString(), and so on. You can also pass an object of type HttpServletResponse, which encapsulates a response message. JSF code The JSF framework can be used to build a website. It uses the JavaServer Pages Standard Tag Library (JSTL). The web container must provide the JAR files for JSTL. There are several ways to use the JSTL. Here are a few examples. The JSF component architecture provides a means for developers to create complex UI components on the web. It creates a component tree, which holds instances of UIComponents. The JSF framework uses these components to handle the application request and generate a rendered response. The framework provides an extensible architecture that enables developers to add other functionalities and customize component behaviors. The JSF standard defines numerous tags and advanced operations. One namespace, named h, provides replacements for common html tags. These tags are used to display data, which may be relational data. Can We Make Website Using Java? Read the full article
0 notes
Text
Top 8 DevOps Tools [Updated for 2021] | AchieversIT
Top 8 DevOps Tools [Updated for 2021]
DevOps is a bunch of practices that consolidates software development and data innovation tasks which intends to abbreviate the development improvement life cycle and give consistent conveyance high programming quality. In any case, the inquiry is, how could DevOps construct a culture?
Indeed, when an association chooses to go DevOps, that is somewhat of a 180-degree change of situations. You really want to foster new prac tices, train your representatives to follow the DevOps standards and since it's an exceptional change from the conventional procedure, it will set aside a lot of effort for your association to accept it.
Its new DevOps Tools and advances that sway social change really. Also, utilizing the legitimate DevOps robotization tools with a touch of AI and ML can get the job done towards business change without any problem!
Here's How you can do it:
Since DevOps is to a greater extent a cross-functional way of working, individuals working under this culture incline toward utilizing a DevOps toolset as a toolchain that fills the accompanying functions:
Coding code improvement and audit, source code the executives instruments, code blending
Building - ceaseless reconciliation instruments, fabricate status
Testing- ceaseless testing devices that give fast and opportune input on business chances
Packing - ancient rarity vault, application pre-deployment arranging
Releasing - change the board, discharge endorsements, discharge computerization
Configuration - framework setup and the executives, foundation as code instruments
Monitoring - applications execution observing, end-client experience
Thus, you should simply pay special attention to tools that deal with every one of the measurements assisting you with bringing the most noteworthy DevOps ROI.
The 8 best DevOps Automation, Testing, and Monitoring Tools for 2021:
1. Slack:
Slack was dispatched in 2013 is as yet administering the DevOps world like a master. Slack is the most normally utilized DevOps device utilized by most associations till date. It is for the most part used for successful correspondence. It permits designers to work together utilizing toolchains in a similar climate they are speaking with other support and administration individuals.
2. Docker:
Actually like Slack, Docker also was started in 2013 and didn't stop its excursion there, simply kept on advancing. Docker is a lot of Platform as a Service (PaaS) that uses OS-level virtualization to pass on programming in packs called compartments. Holders are confined from each other and pack their own product, libraries and design records; they can speak with one another through obvious channels. All holders are controlled by a single operating system portion and in this way utilize less assets than virtual machines. Examination firm Forrester referred to Docker as a forerunner in the venture container stage category for Q4 2018.
3. Jenkins:
Jenkins is a free and open-source automation server that assists with automating the pieces of software development identified with building, testing, and sending, working with persistent coordination and nonstop conveyance. Truth be told, it is the best DevOps Testing apparatus you can at any point find! Jenkins is a server-based framework that runs in servlet holders like Apache Tomcat. It upholds variant control instruments, including AccuRev, CVS, Subversion, Git, Mercurial, Perforce, ClearCase, and RTC, and can execute Apache Ant, Apache Maven, and sbt based ventures just as discretionary shell contents and Windows bunch orders. The maker of Jenkins is Kohsuke Kawaguchi. Additionally, as a clincher, Jenkins is free software as well!
4. Git:
This one is the most matured, yet the most proficient DevOps observing tools. Made by Linus Torvalds in 2005 for the advancement of the Linux Kernel, Git has become one of the most worshiped DevOps devices across the globe throughout the long term. Git is an appropriated form control framework for following changes in source code during software development. It is intended for planning work among developers, yet it tends to be utilized to follow changes in any arrangement of records. Its objectives incorporate speed, information uprightness, and backing for dispersed, non-direct work processes.
5. Nagios:
Nagios is a free and open-source PC programming application that screens systems, organizations, and foundations. Nagios offers to screen and caution administrations for servers, switches, applications, and administrations. It alarms clients when things turn out badly and alerts them a second time when the issue has been settled. Ethan Galstad and a gathering of engineers composed Nagios as NetSuite. In 2015 they had the option to effectively keep up with both the authority and unofficial modules.
6. Grunt:
This one entered InfoWorld's open source hall of fame as the best open source software ever! Grunt is a free open source network interruption discovery framework (IDS) and interruption counteraction framework (IPS) made in 1998 by Martin Roesch, originator and previous CTO of Sourcefire. Grunt is currently developed by Cisco, which purchased Sourcefire in 2013. Grunt's open-source network-based interruption recognition/avoidance system (IDS/IPS) can perform constant traffic examination and parcel signing on Internet Protocol (IP) organizations. Grunt performs convention investigation, content looking, and coordinating. Grunt can likewise be utilized to recognize tests or assaults including working framework fingerprinting endeavors, semantic URL assaults, cradle floods, server message block tests, and covertness port scans.
7. Kubernetes:
Among all the DevOps instruments, Kubernetes is the most discussed one till this year. Kubernetes is an open-source holder administration system for robotizing application deployment, scaling, and the executives. It was initially planned by Google and is presently kept up with by the Cloud Native Computing Foundation. It means to give a "stage for computerizing association, scaling, and exercises of use holders across lots of hosts". It works with an extent of holder gadgets, including Docker. Many cloud organizations offer a Kubernetes-based stage or establishment as an assistance (PaaS or IaaS) on which Kubernetes can be passed on as a phase offering support. Numerous sellers likewise give their own marked Kubernetes distributions.
8. Buddy:
Buddy is an electronic and self-facilitated ceaseless coordination and conveyance software for Git designers that can be utilized to assemble, test, and send sites and applications with code from GitHub, Bitbucket, and GitLab. It utilizes Docker compartments with pre-introduced dialects and systems for works, close by DevOps, observing, and warning activities. Buddy's configuration is performed by organizing predefined activities into successions called pipelines. Pipelines can be set off consequently on a push to a branch, physically, or repetitively. Activities incorporate Docker-based forms, deployment to FTP/SFTP and IaaS administrations, conveyance to adaptation control, SSH scripts, site checking, and restrictive warnings. In opposition to other CI instruments like Jenkins or Travis CI, Buddy doesn't utilize YAML documents to describe the process.
0 notes
Text
Top 8 DevOps Tools Updated for 2021
DevOps is a bunch of practices that consolidate software development and data innovation tasks which intends to abbreviate the development improvement life cycle and give consistent conveyance high programming quality. In any case, the inquiry is, how could DevOps construct a culture? Indeed, when an association chooses to go DevOps, that is somewhat of a 180-degree change of situations. You really want to foster new practices, train your representatives to follow the DevOps standards and since it's an exceptional change from the conventional procedure, it will set aside a lot of effort for your association to accept it. Its new DevOps Tools and advances that sway social change really. Also, utilizing the legitimate DevOps robotization tools with a touch of AI and ML can get the job done towards business change without any problem!
Here's How you can do it:
Since DevOps is to a greater extent a cross-functional way of working, individuals working under this culture incline toward utilizing a DevOps toolset as a toolchain that fills the accompanying functions: Coding code improvement and audit, source code the executives instruments, code blending Building - ceaseless reconciliation instruments, fabricate status Testing- ceaseless testing devices that give fast and opportune input on business chances Packing - ancient rarity vault, application pre-deployment arranging Releasing - change the board, discharge endorsements, discharge computerization Configuration - framework setup and the executives, foundation as code instruments Monitoring - applications execution observing, end-client experience Thus, you should simply pay special attention to tools that deal with every one of the measurements assisting you with bringing the most noteworthy DevOps ROI.

The 8 best DevOps Automation, Testing, and Monitoring Tools for 2021:
1. Slack:
Slack was dispatched in 2013 is as yet administering the DevOps world like a master. Slack is the most normally utilized DevOps device utilized by most associations till date. It is for the most part used for successful correspondence. It permits designers to work together utilizing toolchains in a similar climate they are speaking with other support and administration individuals.
2. Docker:
Actually like Slack, Docker also was started in 2013 and didn't stop its excursion there, simply kept on advancing. Docker is a lot of Platform as a Service (PaaS) that uses OS-level virtualization to pass on programming in packs called compartments. Holders are confined from each other and pack their own product, libraries and design records; they can speak with one another through obvious channels. All holders are controlled by a single operating system portion and in this way utilize less assets than virtual machines. Examination firm Forrester referred to Docker as a forerunner in the venture container stage category for Q4 2018.
3. Jenkins:
Jenkins is a free and open-source automation server that assists with automating the pieces of software development identified with building, testing, and sending, working with persistent coordination and nonstop conveyance. Truth be told, it is the best DevOps Testing apparatus you can at any point find! Jenkins is a server-based framework that runs in servlet holders like Apache Tomcat. It upholds variant control instruments, including AccuRev, CVS, Subversion, Git, Mercurial, Perforce, ClearCase, and RTC, and can execute Apache Ant, Apache Maven, and sbt based ventures just as discretionary shell contents and Windows bunch orders. The maker of Jenkins is Kohsuke Kawaguchi. Additionally, as a clincher, Jenkins is free software as well!
4. Git:
This one is the most matured, yet the most proficient DevOps observing tools. Made by Linus Torvalds in 2005 for the advancement of the Linux Kernel, Git has become one of the most worshiped DevOps devices across the globe throughout the long term. Git is an appropriated form control framework for following changes in source code during software development. It is intended for planning work among developers, yet it tends to be utilized to follow changes in any arrangement of records. Its objectives incorporate speed, information uprightness, and backing for dispersed, non-direct work processes
. 5. Nagios:
Nagios is a free and open-source PC programming application that screens systems, organizations, and foundations. Nagios offers to screen and caution administrations for servers, switches, applications, and administrations. It alarms clients when things turn out badly and alerts them a second time when the issue has been settled. Ethan Galstad and a gathering of engineers composed Nagios as NetSuite. In 2015 they had the option to effectively keep up with both the authority and unofficial modules.
6. Grunt:
This one entered InfoWorld's open source hall of fame as the best open source software ever! Grunt is a free open source network interruption discovery framework (IDS) and interruption counteraction framework (IPS) made in 1998 by Martin Roesch, originator and previous CTO of Sourcefire. Grunt is currently developed by Cisco, which purchased Sourcefire in 2013. Grunt's open-source network-based interruption recognition/avoidance system (IDS/IPS) can perform constant traffic examination and parcel signing on Internet Protocol (IP) organizations. Grunt performs convention investigation, content looking, and coordinating. Grunt can likewise be utilized to recognize tests or assaults including working framework fingerprinting endeavors, semantic URL assaults, cradle floods, server message block tests, and covertness port scans.
7. Kubernetes:
Among all the DevOps instruments, Kubernetes is the most discussed one till this year. Kubernetes is an open-source holder administration system for robotizing application deployment, scaling, and the executives. It was initially planned by Google and is presently kept up with by the Cloud Native Computing Foundation. It means to give a "stage for computerizing association, scaling, and exercises of use holders across lots of hosts". It works with an extent of holder gadgets, including Docker. Many cloud organizations offer a Kubernetes-based stage or establishment as an assistance (PaaS or IaaS) on which Kubernetes can be passed on as a phase offering support. Numerous sellers likewise give their own marked Kubernetes distributions.
8. Buddy:
Buddy is an electronic and self-facilitated ceaseless coordination and conveyance software for Git designers that can be utilized to assemble, test, and send sites and applications with code from GitHub, Bitbucket, and GitLab. It utilizes Docker compartments with pre-introduced dialects and systems for works, close by DevOps, observing, and warning activities. Buddy's configuration is performed by organizing predefined activities into successions called pipelines. Pipelines can be set off consequently on a push to a branch, physically, or repetitively. Activities incorporate Docker-based forms, deployment to FTP/SFTP and IaaS administrations, conveyance to adaptation control, SSH scripts, site checking, and restrictive warnings. In opposition to other CI instruments like Jenkins or Travis CI, Buddy doesn't utilize YAML documents to describe the process.
0 notes
Text
Apache Tomcat 403

Apache Tomcat 403 Forbidden
Apache Tomcat Http Status 403
Apache Tomcat 9 403 Access Denied
It was really very helpful for me. I was using version 8.5.32 and worked fine.thnaks. What is Apache Tomcat? Answer: Apache Tomcat is basically a Web Server and Servlet system. Because of the bug CVE-2020-1938 we want to use the latest Tomcat 7.0.100. See also CVE-2020-1938 We also use an Apache server in version 2.4, which connects to the Tomcat via AJP.
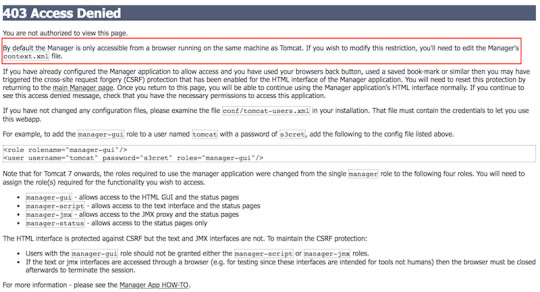
After you installed the Apache Tomcat server and successfully launched the <host>:8080 web page, you click on the Manager App button, and you get a 403 Access Denied message.
The Apache Tomcat Project is proud to announce the release of version 7.0.109 of Apache Tomcat. This release implements specifications that are part of the Java EE 6 platform. This release contains a number of bug fixes and improvements compared to version 7.0.108.
Hi, we have a strange symptom after an upgrade from Tomcat 8 to Tomcat 9, because we get a 403 for a call that works flawlessly with the previous version. Let's describe the scenario: We have a customer with a Wordpress application hosted on an Apache server. Some pages perform XMLHttpRequests to load and embed HTML snippets from other sources.
To fix it 1. Open the $CATALINA_BASE/conf/tomcat-users.xml file and add the following to the <tomcat-users> section.
<user username='admin' password='goanywhere' roles='admin-gui,manager-gui' />
2. If you are accessing the Tomcat server from a remote computer, open or create the file: $CATALINA_BASE/conf/Catalina/localhost/manager.xml, and add the below to the file.
<Context privileged='true' antiResourceLocking='false'
<Valve className='org.apache.catalina.valves.RemoteAddrValve' allow='^.*$' />
3. Restart the tomcat server: sudo systemctl restart tomcat.service
----------------------------------------------------------------------------------------------------------------- Watch the blessing and loving online channel: SupremeMasterTV live
If you have ever asked yourself these questions, this is the book for you. What is the meaning of life? Why do people suffer? What is in control of my life? Why is life the way it is? How can I stop suffering and be happy? How can I have a successful life? How can I have a life I like to have? How can I be the person I like to be? How can I be wiser and smarter? How can I have good and harmonious relations with others? Why do people meditate to achieve enlightenment? What is the true meaning of spiritual practice? Why all beings are one? Read the book for free here.
The AJP Connector
Table of Contents
Attributes
Special Features
Introduction
The AJP Connector element represents a Connector component that communicates with a web connector via the AJP protocol. This is used for cases where you wish to invisibly integrate Tomcat into an existing (or new) Apache installation, and you want Apache to handle the static content contained in the web application, and/or utilize Apache's SSL processing.
Use of the AJP protocol requires additional security considerations because it allows greater direct manipulation of Tomcat's internal data structures than the HTTP connectors. Particular attention should be paid to the values used for the address, secret, secretRequired and allowedRequestAttributesPattern attributes.
This connector supports load balancing when used in conjunction with the jvmRoute attribute of the Engine.
The native connectors supported with this Tomcat release are:
JK 1.2.x with any of the supported servers. See the JK docs for details.
mod_proxy on Apache httpd 2.x (included by default in Apache HTTP Server 2.2), with AJP enabled: see the httpd docs for details.
Other native connectors supporting AJP may work, but are no longer supported.
Attributes
Common Attributes
Apache Tomcat 403 Forbidden
All implementations of Connector support the following attributes:
Attribute Description ajpFlush
A boolean value which can be used to enable or disable sending AJP flush messages to the fronting proxy whenever an explicit flush happens. The default value is true. An AJP flush message is a SEND_BODY_CHUNK packet with no body content. Proxy implementations like mod_jk or mod_proxy_ajp will flush the data buffered in the web server to the client when they receive such a packet. Setting this to false can reduce AJP packet traffic but might delay sending packets to the client. At the end of the response, AJP does always flush to the client.
allowTrace
A boolean value which can be used to enable or disable the TRACE HTTP method. If not specified, this attribute is set to false.
asyncTimeout
The default timeout for asynchronous requests in milliseconds. If not specified, this attribute is set to the Servlet specification default of 30000 (30 seconds).
enableLookups
Set to true if you want calls to request.getRemoteHost() to perform DNS lookups in order to return the actual host name of the remote client. Set to false to skip the DNS lookup and return the IP address in String form instead (thereby improving performance). By default, DNS lookups are disabled.
encodedSolidusHandling
When set to reject request paths containing a %2f sequence will be rejected with a 400 response. When set to decode request paths containing a %2f sequence will have that sequence decoded to / at the same time other %nn sequences are decoded. When set to passthrough request paths containing a %2f sequence will be processed with the %2f sequence unchanged. If not specified the default value is reject. This default may be modified if the deprecated system propertyorg.apache.tomcat.util.buf.UDecoder.ALLOW_ENCODED_SLASH is set.
maxHeaderCount
The maximum number of headers in a request that are allowed by the container. A request that contains more headers than the specified limit will be rejected. A value of less than 0 means no limit. If not specified, a default of 100 is used.
maxParameterCount
The maximum number of parameter and value pairs (GET plus POST) which will be automatically parsed by the container. Parameter and value pairs beyond this limit will be ignored. A value of less than 0 means no limit. If not specified, a default of 10000 is used. Note that FailedRequestFilterfilter can be used to reject requests that hit the limit.
maxPostSize
The maximum size in bytes of the POST which will be handled by the container FORM URL parameter parsing. The limit can be disabled by setting this attribute to a value less than zero. If not specified, this attribute is set to 2097152 (2 megabytes). Note that the FailedRequestFilter can be used to reject requests that exceed this limit.
maxSavePostSize
The maximum size in bytes of the POST which will be saved/buffered by the container during FORM or CLIENT-CERT authentication. For both types of authentication, the POST will be saved/buffered before the user is authenticated. For CLIENT-CERT authentication, the POST is buffered for the duration of the SSL handshake and the buffer emptied when the request is processed. For FORM authentication the POST is saved whilst the user is re-directed to the login form and is retained until the user successfully authenticates or the session associated with the authentication request expires. The limit can be disabled by setting this attribute to -1. Setting the attribute to zero will disable the saving of POST data during authentication. If not specified, this attribute is set to 4096 (4 kilobytes).
parseBodyMethods
A comma-separated list of HTTP methods for which request bodies using application/x-www-form-urlencoded will be parsed for request parameters identically to POST. This is useful in RESTful applications that want to support POST-style semantics for PUT requests. Note that any setting other than POST causes Tomcat to behave in a way that goes against the intent of the servlet specification. The HTTP method TRACE is specifically forbidden here in accordance with the HTTP specification. The default is POST
port
The TCP port number on which this Connector will create a server socket and await incoming connections. Your operating system will allow only one server application to listen to a particular port number on a particular IP address. If the special value of 0 (zero) is used, then Tomcat will select a free port at random to use for this connector. This is typically only useful in embedded and testing applications.
protocol
Sets the protocol to handle incoming traffic. To configure an AJP connector this must be specified. If no value for protocol is provided, an HTTP connector rather than an AJP connector will be configured. The standard protocol value for an AJP connector is AJP/1.3 which uses an auto-switching mechanism to select either a Java NIO based connector or an APR/native based connector. If the PATH (Windows) or LD_LIBRARY_PATH (on most unix systems) environment variables contain the Tomcat native library, the native/APR connector will be used. If the native library cannot be found, the Java NIO based connector will be used. To use an explicit protocol rather than rely on the auto-switching mechanism described above, the following values may be used: org.apache.coyote.ajp.AjpNioProtocol - non blocking Java NIO connector. org.apache.coyote.ajp.AjpNio2Protocol - non blocking Java NIO2 connector. org.apache.coyote.ajp.AjpAprProtocol - the APR/native connector. Custom implementations may also be used. Take a look at our Connector Comparison chart.
proxyName
If this Connector is being used in a proxy configuration, configure this attribute to specify the server name to be returned for calls to request.getServerName(). See Proxy Support for more information.
proxyPort
If this Connector is being used in a proxy configuration, configure this attribute to specify the server port to be returned for calls to request.getServerPort(). See Proxy Support for more information.
redirectPort
If this Connector is supporting non-SSL requests, and a request is received for which a matching <security-constraint> requires SSL transport, Catalina will automatically redirect the request to the port number specified here.
scheme
Set this attribute to the name of the protocol you wish to have returned by calls to request.getScheme(). For example, you would set this attribute to 'https' for an SSL Connector. The default value is 'http'.
secure
Set this attribute to true if you wish to have calls to request.isSecure() to return true for requests received by this Connector. You would want this on an SSL Connector or a non SSL connector that is receiving data from a SSL accelerator, like a crypto card, an SSL appliance or even a webserver. The default value is false.
sendReasonPhrase
Set this attribute to true if you wish to have a reason phrase in the response. The default value is false.
Note: This option is deprecated and will be removed in Tomcat 9. The reason phrase will not be sent.
URIEncoding
This specifies the character encoding used to decode the URI bytes, after %xx decoding the URL. If not specified, UTF-8 will be used unless the org.apache.catalina.STRICT_SERVLET_COMPLIANCEsystem property is set to true in which case ISO-8859-1 will be used.
useBodyEncodingForURI
This specifies if the encoding specified in contentType should be used for URI query parameters, instead of using the URIEncoding. This setting is present for compatibility with Tomcat 4.1.x, where the encoding specified in the contentType, or explicitly set using Request.setCharacterEncoding method was also used for the parameters from the URL. The default value is false.
Notes: See notes on this attribute in HTTP Connector documentation.
useIPVHosts
Set this attribute to true to cause Tomcat to use the IP address passed by the native web server to determine the Host to send the request to. The default value is false.
xpoweredBy
Set this attribute to true to cause Tomcat to advertise support for the Servlet specification using the header recommended in the specification. The default value is false.
Standard Implementations
To use AJP, you must specify the protocol attribute (see above).
The standard AJP connectors (NIO, NIO2 and APR/native) all support the following attributes in addition to the common Connector attributes listed above.
Attribute Description acceptCount
The maximum queue length for incoming connection requests when all possible request processing threads are in use. Any requests received when the queue is full will be refused. The default value is 100.
acceptorThreadCount
The number of threads to be used to accept connections. Increase this value on a multi CPU machine, although you would never really need more than 2. Also, with a lot of non keep alive connections, you might want to increase this value as well. Default value is 1.
acceptorThreadPriority
The priority of the acceptor threads. The threads used to accept new connections. The default value is 5 (the value of the java.lang.Thread.NORM_PRIORITY constant). See the JavaDoc for the java.lang.Thread class for more details on what this priority means.
address
For servers with more than one IP address, this attribute specifies which address will be used for listening on the specified port. By default, the connector will listen on the loopback address. Unless the JVM is configured otherwise using system properties, the Java based connectors (NIO, NIO2) will listen on both IPv4 and IPv6 addresses when configured with either 0.0.0.0 or ::. The APR/native connector will only listen on IPv4 addresses if configured with 0.0.0.0 and will listen on IPv6 addresses (and optionally IPv4 addresses depending on the setting of ipv6v6only) if configured with ::.
allowedRequestAttributesPattern
The AJP protocol passes some information from the reverse proxy to the AJP connector using request attributes. These attributes are:
javax.servlet.request.cipher_suite
javax.servlet.request.key_size
javax.servlet.request.ssl_session
javax.servlet.request.X509Certificate
AJP_LOCAL_ADDR
AJP_REMOTE_PORT
AJP_SSL_PROTOCOL
JK_LB_ACTIVATION
CERT_ISSUER (IIS only)
CERT_SUBJECT (IIS only)
CERT_COOKIE (IIS only)
HTTPS_SERVER_SUBJECT (IIS only)
CERT_FLAGS (IIS only)
HTTPS_SECRETKEYSIZE (IIS only)
CERT_SERIALNUMBER (IIS only)
HTTPS_SERVER_ISSUER (IIS only)
HTTPS_KEYSIZE (IIS only)
The AJP protocol supports the passing of arbitrary request attributes. Requests containing arbitrary request attributes will be rejected with a 403 response unless the entire attribute name matches this regular expression. If not specified, the default value is null.
bindOnInit
Controls when the socket used by the connector is bound. By default it is bound when the connector is initiated and unbound when the connector is destroyed. If set to false, the socket will be bound when the connector is started and unbound when it is stopped.
clientCertProvider
When client certificate information is presented in a form other than instances of java.security.cert.X509Certificate it needs to be converted before it can be used and this property controls which JSSE provider is used to perform the conversion. For example it is used with the AJP connectors, the HTTP APR connector and with the org.apache.catalina.valves.SSLValve.If not specified, the default provider will be used.
connectionLinger
The number of seconds during which the sockets used by this Connector will linger when they are closed. The default value is -1 which disables socket linger.
connectionTimeout
The number of milliseconds this Connector will wait, after accepting a connection, for the request URI line to be presented. The default value for AJP protocol connectors is -1 (i.e. infinite).
executor
A reference to the name in an Executor element. If this attribute is set, and the named executor exists, the connector will use the executor, and all the other thread attributes will be ignored. Note that if a shared executor is not specified for a connector then the connector will use a private, internal executor to provide the thread pool.
executorTerminationTimeoutMillis
The time that the private internal executor will wait for request processing threads to terminate before continuing with the process of stopping the connector. If not set, the default is 5000 (5 seconds).
keepAliveTimeout
The number of milliseconds this Connector will wait for another AJP request before closing the connection. The default value is to use the value that has been set for the connectionTimeout attribute.
maxConnections
The maximum number of connections that the server will accept and process at any given time. When this number has been reached, the server will accept, but not process, one further connection. This additional connection be blocked until the number of connections being processed falls below maxConnections at which point the server will start accepting and processing new connections again. Note that once the limit has been reached, the operating system may still accept connections based on the acceptCount setting. The default value varies by connector type. For NIO and NIO2 the default is 10000. For APR/native, the default is 8192.
For NIO/NIO2 only, setting the value to -1, will disable the maxConnections feature and connections will not be counted.
maxCookieCount
The maximum number of cookies that are permitted for a request. A value of less than zero means no limit. If not specified, a default value of 200 will be used.
maxThreads
The maximum number of request processing threads to be created by this Connector, which therefore determines the maximum number of simultaneous requests that can be handled. If not specified, this attribute is set to 200. If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
minSpareThreads
The minimum number of threads always kept running. This includes both active and idle threads. If not specified, the default of 10 is used. If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
packetSize
This attribute sets the maximum AJP packet size in Bytes. The maximum value is 65536. It should be the same as the max_packet_size directive configured for mod_jk. Normally it is not necessary to change the maximum packet size. Problems with the default value have been reported when sending certificates or certificate chains. The default value is 8192. If set to less than 8192 then the setting will ignored and the default value of 8192 used.
processorCache
The protocol handler caches Processor objects to speed up performance. This setting dictates how many of these objects get cached. -1 means unlimited, default is 200. If not using Servlet 3.0 asynchronous processing, a good default is to use the same as the maxThreads setting. If using Servlet 3.0 asynchronous processing, a good default is to use the larger of maxThreads and the maximum number of expected concurrent requests (synchronous and asynchronous).
secret
Only requests from workers with this secret keyword will be accepted. The default value is null. This attribute must be specified with a non-null, non-zero length value unless secretRequired is explicitly configured to be false. If this attribute is configured with a non-null, non-zero length value then the workers must provide a matching value else the request will be rejected irrespective of the setting of secretRequired.
secretRequired
If this attribute is true, the AJP Connector will only start if the secret attribute is configured with a non-null, non-zero length value. This attribute only controls whether the secret attribute is required to be specified for the AJP Connector to start. It does not control whether workers are required to provide the secret. The default value is true. This attribute should only be set to false when the Connector is used on a trusted network.
tcpNoDelay
If set to true, the TCP_NO_DELAY option will be set on the server socket, which improves performance under most circumstances. This is set to true by default.
threadPriority
The priority of the request processing threads within the JVM. The default value is 5 (the value of the java.lang.Thread.NORM_PRIORITY constant). See the JavaDoc for the java.lang.Thread class for more details on what this priority means.If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
tomcatAuthentication
If set to true, the authentication will be done in Tomcat. Otherwise, the authenticated principal will be propagated from the native webserver and used for authorization in Tomcat.
The web server must send the user principal (username) as a request attribute named REMOTE_USER.
Note that this principal will have no roles associated with it.
The default value is true. If tomcatAuthorization is set to true this attribute has no effect.
tomcatAuthorization
If set to true, the authenticated principal will be propagated from the native webserver and considered already authenticated in Tomcat. If the web application has one or more security constraints, authorization will then be performed by Tomcat and roles assigned to the authenticated principal. If the appropriate Tomcat Realm for the request does not recognise the provided user name, a Principal will be still be created but it will have no roles. The default value is false.
Java TCP socket attributes
The NIO and NIO2 implementation support the following Java TCP socket attributes in addition to the common Connector and HTTP attributes listed above.
Attribute Description socket.rxBufSize
(int)The socket receive buffer (SO_RCVBUF) size in bytes. JVM default used if not set.
socket.txBufSize
(int)The socket send buffer (SO_SNDBUF) size in bytes. JVM default used if not set. Care should be taken if explicitly setting this value. Very poor performance has been observed on some JVMs with values less than ~8k.
socket.tcpNoDelay
(bool)This is equivalent to standard attribute tcpNoDelay.
socket.soKeepAlive
(bool)Boolean value for the socket's keep alive setting (SO_KEEPALIVE). JVM default used if not set.
socket.ooBInline
(bool)Boolean value for the socket OOBINLINE setting. JVM default used if not set.
socket.soReuseAddress
(bool)Boolean value for the sockets reuse address option (SO_REUSEADDR). JVM default used if not set.
socket.soLingerOn
(bool)Boolean value for the sockets so linger option (SO_LINGER). A value for the standard attribute connectionLinger that is >=0 is equivalent to setting this to true. A value for the standard attribute connectionLinger that is <0 is equivalent to setting this to false. Both this attribute and soLingerTime must be set else the JVM defaults will be used for both.
socket.soLingerTime
(int)Value in seconds for the sockets so linger option (SO_LINGER). This is equivalent to standard attribute connectionLinger. Both this attribute and soLingerOn must be set else the JVM defaults will be used for both.
socket.soTimeout
This is equivalent to standard attribute connectionTimeout.
socket.performanceConnectionTime
(int)The first value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.performanceLatency
(int)The second value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.performanceBandwidth
(int)The third value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.unlockTimeout
(int) The timeout for a socket unlock. When a connector is stopped, it will try to release the acceptor thread by opening a connector to itself. The default value is 250 and the value is in milliseconds
NIO specific configuration
The following attributes are specific to the NIO connector.
Attribute Description socket.directBuffer
(bool)Boolean value, whether to use direct ByteBuffers or java mapped ByteBuffers. Default is false. When you are using direct buffers, make sure you allocate the appropriate amount of memory for the direct memory space. On Sun's JDK that would be something like -XX:MaxDirectMemorySize=256m.
socket.appReadBufSize
(int)Each connection that is opened up in Tomcat get associated with a read ByteBuffer. This attribute controls the size of this buffer. By default this read buffer is sized at 8192 bytes. For lower concurrency, you can increase this to buffer more data. For an extreme amount of keep alive connections, decrease this number or increase your heap size.
socket.appWriteBufSize
(int)Each connection that is opened up in Tomcat get associated with a write ByteBuffer. This attribute controls the size of this buffer. By default this write buffer is sized at 8192 bytes. For low concurrency you can increase this to buffer more response data. For an extreme amount of keep alive connections, decrease this number or increase your heap size. The default value here is pretty low, you should up it if you are not dealing with tens of thousands concurrent connections.
socket.bufferPool
(int)The NIO connector uses a class called NioChannel that holds elements linked to a socket. To reduce garbage collection, the NIO connector caches these channel objects. This value specifies the size of this cache. The default value is 500, and represents that the cache will hold 500 NioChannel objects. Other values are -1 for unlimited cache and 0 for no cache.
socket.bufferPoolSize
(int)The NioChannel pool can also be size based, not used object based. The size is calculated as follows: NioChannel buffer size = read buffer size + write buffer size SecureNioChannel buffer size = application read buffer size + application write buffer size + network read buffer size + network write buffer size The value is in bytes, the default value is 1024*1024*100 (100MB).
socket.processorCache
(int)Tomcat will cache SocketProcessor objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 Body outline drawing. for no cache.
socket.keyCache
(int)Tomcat will cache KeyAttachment objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
socket.eventCache
(int)Tomcat will cache PollerEvent objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
selectorPool.maxSelectors
(int)The max selectors to be used in the pool, to reduce selector contention. Use this option when the command line org.apache.tomcat.util.net.NioSelectorShared value is set to false. Default value is 200.
selectorPool.maxSpareSelectors
(int)The max spare selectors to be used in the pool, to reduce selector contention. When a selector is returned to the pool, the system can decide to keep it or let it be GC'd. Use this option when the command line org.apache.tomcat.util.net.NioSelectorShared value is set to false. Default value is -1 (unlimited).
command-line-options
The following command line options are available for the NIO connector: -Dorg.apache.tomcat.util.net.NioSelectorShared=true|false - default is true. Set this value to false if you wish to use a selector for each thread. When you set it to false, you can control the size of the pool of selectors by using the selectorPool.maxSelectors attribute.
NIO2 specific configuration
The following attributes are specific to the NIO2 connector.
Attribute Description useCaches
(bool)Use this attribute to enable or disable object caching to reduce the amount of GC objects produced. The default value is false.
socket.directBuffer
(bool)Boolean value, whether to use direct ByteBuffers or java mapped ByteBuffers. Default is false. When you are using direct buffers, make sure you allocate the appropriate amount of memory for the direct memory space. On Sun's JDK that would be something like -XX:MaxDirectMemorySize=256m.
socket.appReadBufSize
(int)Each connection that is opened up in Tomcat get associated with a read ByteBuffer. This attribute controls the size of this buffer. By default this read buffer is sized at 8192 bytes. For lower concurrency, you can increase this to buffer more data. For an extreme amount of keep alive connections, decrease this number or increase your heap size.
We are an experienced Drupal development company with decade-long proven track record offering best-in-class customization, module, migration and Drupal development services worldwide. Drupal web services. Drupal is a powerful CMS widely used to develop variety of web solutions; ranging from a single page website to complex eCommerce stores. There are large numbers of web development companies in tech world that claim to provide excellent Drupal development services.
socket.appWriteBufSize
(int)Each connection that is opened up in Tomcat get associated with a write ByteBuffer. This attribute controls the size of this buffer. By default this write buffer is sized at 8192 bytes. For low concurrency you can increase this to buffer more response data. For an extreme amount of keep alive connections, decrease this number or increase your heap size. The default value here is pretty low, you should up it if you are not dealing with tens of thousands concurrent connections.
socket.bufferPoolSize
(int)The NIO2 connector uses a class called Nio2Channel that holds elements linked to a socket. To reduce garbage collection, the NIO connector caches these channel objects. This value specifies the size of this cache. The default value is 500, and represents that the cache will hold 500 Nio2Channel objects. Other values are -1 for unlimited cache and 0 for no cache.
socket.processorCache
(int)Tomcat will cache SocketProcessor objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
APR/native specific configuration
The APR/native implementation supports the following attributes in addition to the common Connector and AJP attributes listed above.
Attribute Description ipv6v6only
If listening on an IPv6 address on a dual stack system, should the connector only listen on the IPv6 address? If not specified the default is false and the connector will listen on the IPv6 address and the equivalent IPv4 address if present.
pollTime
Duration of a poll call in microseconds. Lowering this value will slightly decrease latency of connections being kept alive in some cases , but will use more CPU as more poll calls are being made. The default value is 2000 (2ms).
Nested Components
Special Features
Proxy Support
The proxyName and proxyPort attributes can be used when Tomcat is run behind a proxy server. These attributes modify the values returned to web applications that call the request.getServerName() and request.getServerPort() methods, which are often used to construct absolute URLs for redirects. Without configuring these attributes, the values returned would reflect the server name and port on which the connection from the proxy server was received, rather than the server name and port to whom the client directed the original request.
For more information, see the Proxy Support How-To.
Connector Comparison
Apache Tomcat Http Status 403

Below is a small chart that shows how the connectors differ.
Apache Tomcat 9 403 Access Denied
Java Nio Connector NIOJava Nio2 Connector NIO2APR/native Connector APRClassnameAjpNioProtocolAjpNio2ProtocolAjpAprProtocolTomcat Version7.x onwards8.x onwards5.5.x onwardsSupport PollingYESYESYESPolling SizemaxConnectionsmaxConnectionsmaxConnectionsRead Request HeadersBlockingBlockingBlockingRead Request BodyBlockingBlockingBlockingWrite Response Headers and BodyBlockingBlockingBlockingWait for next RequestNon BlockingNon BlockingNon BlockingMax ConnectionsmaxConnectionsmaxConnectionsmaxConnections

0 notes
Text
300+ TOP FILEMAKER Interview Questions and Answers
FILEMAKER Interview Questions for freshers experienced :-
1.What is FileMaker Pro? FileMaker Pro is a 32 bit, Y2K compliant, cross-platform, fully relational, database program. Similar to Microsoft Access, the current version of FileMaker is a fully relational database development tool that allows one-to-one, one-to-many, many-to-one, and many-to-many relations between files (tables). Another one of FileMaker Pro's advantage is the FileMaker Developer tools that allows us to 'bundle' the form files with the FileMaker Runtime engine that allows our outside customers to use WSDOT forms without requiring them to purchase any additional software. 2.What are the symptoms of a corrupt FileMaker file? Symptoms vary from corruption type and level of corruption. Maybe your FileMaker application freezes when the file is tried to open, or maybe an error message is shown when you click the file to open it. 3.Is it possible to search any FileMaker .fp7 file? FileMaker Recovery Software has an inbuilt option to search FP7 files in a specified location. File properties like modification date, creation date, size, etc. are shown in the search result for accurate selection. 4.How is FileMaker Recovery Software different from other similar products in market? Many features have been included in latest version of FileMaker Recovery Software. Latest version of FileMaker Recovery Software supports File Maker Pro 10/11/Pro/Advance and above. Search option in the preview, selective recovery of a specific table, log summary, etc. make it above other similar software applications in the market. 5.What is FileMaker Recovery Software? FileMaker Recovery Software is used to repair, restore and recover corrupt FileMaker database (.fp7) files. A search feature is provided that helps in searching all the .fp7 files present in a drive or folder. A new FileMaker file is set as target to store the recovered table data. Data of Text, Number, Date, Timestamp, Calculation, Container and Summary data type are recovered back in the repaired database file. 6.Can I repair a FileMaker database for trial and evaluation without payment? Yes, you can download FileMaker Recovery Software absolutely free of cost. Preview is shown in the demo version for customer evaluation. If you are satisfied by the scanned results, you can register the demo version to save the recovered FileMaker database. 7.What is new in FileMaker Pro 6? The best just got better with FileMaker Pro 6 database software. It features digital image capture and import; more than 20 modern and powerful templates for "instant productivity" in business, education and home; many time-saving features like Format Painter and Custom Dialog Boxes for users and developers; and integrated XML support so FileMaker can exchange data with a large and growing number of other applications. FileMaker Pro 6 will jump-start the productivity and creativity of workgroups ranging from entire small businesses to departments within the enterprise. 8.Why is the new FileMaker Pro 6 available before other revised products? FileMaker Pro 6 files share the same file format as FileMaker Pro 5 and 5.5 files. Thus, all three versions may co-exist on the same network. In addition, all versions utilize the current FileMaker Server (now relabeled without a version number) features, enabling large workgroups to share information seamlessly. 9.Is XML import/export support in FileMaker Pro 6 a big deal? Absolutely the widespread support of XML (Extensible Markup Language) standards means FileMaker Pro 6 can exchange data with a large and growing number of other applications without complex and costly converting of data between proprietary formats. A developer can easily empower a workgroup using FileMaker Pro 6 to, for example, find and get data from Websites, import accounting data from QuickBooks, or query corporate databases without using ODBC drivers. With XML export, FileMaker Pro 6 users can share information with users of other applications. For example, users can export formatted FileMaker data in an attachment to an email, into Microsoft Excel, or into document-authoring applications. 10.What's new about XML support in FileMaker Pro 6? In the past, accessing FileMaker data as XML required users to make requests to the FileMaker Web Companion from an external application; in other words, it was "pull" only through the Web Companion. Additionally, processing XSLT style sheets required the user to have installed an XSLT processor on the client machine. With FileMaker Pro 6 the XML capabilities are integrated into the product as import/export menu selections without the need for the Web Companion. Alternatively, the customer can script XML data import and export. Also within FileMaker Pro 6 is an XSLT processor allowing style sheets can be processed without the need for the customer to install their own.

FILEMAKER Interview Questions 11.How hard is it to use XML import/export? Can anyone use it? While the creation of the XSLT style sheets does require a good understanding of XML and XSLT, the benefits of our XML import/export can be enjoyed by all users. Note that a developer can empower an entire workgroup, very efficiently, to enjoy the benefits of XML data-exchange while hiding the plumbing from the users. To further assist our customers with better understanding of XML and XSLT, we ship 8 XSLT style sheet examples with FileMaker Pro 6. Furthermore, customers can visit the FileMaker XSLT Library, which is part of our FileMaker XML Central. The FileMaker XSLT Library is a repository of XML/XSLT examples that are available for download at no charge. 12.Why did FileMaker add integrated XML support in FileMaker Pro 6? XML support is the tool that best accomplishes this task. With the implementation of our XML support, FileMaker Pro 6 users are now able to gather data from more data-sources and share data with more applications.FileMaker Pro 6 customers can benefit from XML import and export. Through the creation of an XSLT style sheet , a workgroup can: Import XML data from a SQL server without the use of ODBC drivers. Share information with other workgroups who don’t even use FileMaker Pro by sending data from FileMaker directly into a formatted Excel file (*.xls) or other text-based file formats. Create charts and graphics (*.svg) to represent FileMaker data. 13. Is there RAIC support for Instant Web Publishing in FileMaker Pro 6? There is no support for RAIC technology in FileMaker Pro 6. Use FileMaker Pro 6 Unlimited to deploy Web-based solutions to an unlimited number of users. It also includes the FileMaker Pro Web Server Connector and support for RAIC, which can increase the performance and scalability of your FileMaker Pro web databases. Toolbars are not supported under Mac OS X. 14.What is FileMaker Pro 5.5 Unlimited? FileMaker Pro 5.5 Unlimited includes all of the powerful desktop database functionality of FileMaker Pro 5.5, plus it allows databases to be hosted via the Web to an unlimited number of unique visitors with unique IP addresses. FileMaker Pro 5.5 Unlimited also includes the Web Server Connector and tools needed to use and access advanced functionalities such as Custom Web Publishing (via CDML), XML, JDBC, Java class libraries, and JavaScript. 15.What is the difference between FileMaker Pro 5.5 and FileMaker Pro 5.5 Unlimited? There are four major differences between FileMaker Pro 5.5 and FileMaker Pro 5.5 Unlimited: The Web Companion that ships with FileMaker Pro 5.5 Unlimited allows access to the Web Companion for an unlimited number of web browsers. The Web Companion that ships with FileMaker Pro 5.5 is limited to 10 IP addresses in a rolling 12 hour period. FileMaker Pro 5.5 Unlimited includes the FileMaker Web Server Connector. Additional copies of FileMaker Pro 5.5 Unlimited can be used to set up a Redundant Array of Inexpensive Computers (RAIC) structure to take advantage of scalable load balancing, and fault tolerance, to increase the performance of FileMaker web enabled databases. Computers running Mac OS X cannot serve as RAIC machines FileMaker Pro 5.5 Unlimited can be used with various CGIs, middleware, and application servers for deployment across the Web. Tools and information needed to implement solutions using advanced functionalities (JDBC driver, Java class library, Custom Web Publishing , Custom Workgroup Portal, XML) are not included in FileMaker Pro 5.5. 16.What is the FileMaker Web Server Connector? The FileMaker Web Server Connector is a Java servlet that is used to connect FileMaker Pro 5.5 Unlimited with powerful web servers. A servlet is a standard Java based mechanism for extending the functionality of a web server. The FileMaker Web Server Connector is used to pass through (or relay) requests received on a web server to FileMaker. The reasons to use the FileMaker Web Server Connector include. To take advantage of other web server plug-ins and features including SSL and server-side includes, provide a Redundant Array of Inexpensive Computers (RAIC) structure to increase throughput and reliability, increase performance by storing static pages and graphic images on the Web server, bypassing the Web Companion for pages that don't involve databases, and provide redundancy to allow for operation through failure situations. 17.Can I use the FileMaker Web Server Connector with FileMaker Pro 5.5? The FileMaker Web Server Connector is designed to work only with FileMaker Pro 5.5 Unlimited, the dedicated web publishing product in our product family. 18.Can I use the FileMaker Pro 5.5 Unlimited Web Server Connector with Instant Web Publishing? No. The improved FileMaker Pro 5.5 Unlimited Web Server Connector is intended for use with Custom Web Publishing. 19.How can I run reports and print labels via browser in databases hosted under FileMaker Pro Unlimited? If you need more functionality than browsing, searching, adding, updating, or deleting records, you will want to access the database using a copy of FileMaker Pro, rather than a browser. 20.How can I set up a Redundant Array of Inexpensive Computers (RAIC) with FileMaker Pro 5.5 Unlimited to increase scalability, performance and robustness? The FileMaker Web Server Connector, included with FileMaker Pro 5.5 Unlimited, lets you set up a RAIC. A RAIC increases the scalability of your web-based FileMaker Pro solutions and helps ensure operation through fail-over situations. To set up a RAIC, an additional copy of FileMaker Pro 5.5 Unlimited is required for each CPU you wish to add to the RAIC. 21.What languages will FileMaker Pro 5.5 Unlimited be available in? FileMaker Pro 5.5 Unlimited in Worldwide English, French, Italian, German, Swedish, Dutch, Japanese and Spanish. 22.What are the price and availability of FileMaker Pro 5.5 Unlimited? FileMaker Pro 5.5 Unlimited is currently available. Estimated retail price in the U.S. is $999. Upgrade price for licensed owners of FileMaker Pro 5 Unlimited is US $499. Volume license pricing is available. 23.Do I have to use the FileMaker Web Server Connector when I install FileMaker Pro 5.5 Unlimited? No. If you want to use FileMaker and simply have more than 10 IP addresses accessing your copy of FileMaker in a rolling 12 hour period and do not need to add scalability and load balancing to your FileMaker web solutions, you can simply install the "unlocked" version of FileMaker Pro 5.5 that ships with FileMaker Pro 5.5 Unlimited. 24.Is FileMaker Pro 5.5 Unlimited certified for Windows 2000? FileMaker Pro 5.5 Unlimited is certified for Windows 2000 Professional. 25.Why did we build FM Starting Point? When we worked with FileMaker, Inc. to rebuild and clean up the “Starter Solution Templates,” a premium was placed on simple functionality that would be easy for brand new FileMaker users to take apart and customize. Of course, with simplicity elevated to such a high degree, overall usefulness of a database can be quite limited. There is, therefore, a genuine need for a more robust FREE starter solution for FileMaker users; this tool meets those needs. 26.What is new in FM Starting Point 2? With the release of FileMaker 11, we decided to update our FM Starting Point template with a few new features. A few of these include Charting throughout the system, inventory tracking between the Invoice and Products module, and hourly rates in the Timesheets module. You will find a brand new Summary tab in the Projects Module that collects information from the Inventory, Expenses, and Timesheets tables to produce graphs showing the current status and profitability of a project. All this and more you will find in the new version. Once again, FM Starting Point 2 is a FREE solution so you can go ahead and download it as soon as you get FileMaker 11. 27.Will FM Starting Point 1 still be available? A new link has be put onto the FM Starting Point website for downloading our last release, FM Starting Point 1.0v15. 28.Is FileMaker Inc. responsible for this Database? No. FM Starting Point was influenced by the redevelopment of FileMaker’s “Starter Solution Templates” which are already included for FREE with each install of FileMaker Pro. FileMaker Inc. has not underwritten this enhanced solution. FMI staff provided feedback for the included features, and we greatly appreciate their assistance. All quality assurance testing was performed by RCC and not FMI. 29.How is this different than Data4Life? Some FileMaker users are aware of another FREE database offered, called Data4Life. Data4Life is designed for personal use, and not business use. FM Starting Point targeted towards small businesses, work groups, and non-profit organizations. 30.Does FM Starting Point connect to QuickBooks? FM Starting Point can connect to QuickBooks (on Windows only) via the use of third party plug-ins. The Mac version of QuickBooks has some limitations that prevent it from communicating with a Plug-in unless you are a FileMaker “power user” then you might need to get some help from a FileMaker developer with this task. 31.Does FM Starting Point connect to iCal or Address book on a Mac? FM Starting Point can connect to these other applications via the use of third party plug-ins. Unless you are a FileMaker “power user” then you might need to get some help from a FileMaker developer with this task. 32.Is there an instruction manual for FM Starting Point? No. There are several instructional on screen help videos to help get users rolling in the new system. We are also commenting on the scripts and various features within the database template. FM Starting Point is design for new users so it is not too complex. Few people read the manuals anyway. They just hack their way through a product. However, if someone wants to write a manual, and then give it away to everyone, let us know and we’ll post it for you. 33.What are the different kinds of Email I can send from FM Starting Point? Primarily, the email capabilities are within the "contacts" modules, where you can shoot off a myriad of different "canned" emails. These will be plain text emails, since that is what the new built in FileMaker 10 feature supports. Email may be sent through a users email client OR use the new “Direct Send” capability of FileMaker Pro 10. 34.When I am reviewing a specific to-do, from the to-do list, and I select a due date, the Window will flash. Why is this? We had to use a script trigger. When the due date is modified, it selects the to-do list window, and causes a refresh to occur. We did this because FileMaker 10’s new sticky sort capability would frequently re-sort the new to-do item off the visible list (above or below), and would confuse the user when the to-do pop up is closed. 35.In the FileMaker 10 Starter Solutions, there is frequent use of "Type Ahead" aka Clairvoyance. Why is this missing from FM Starting Point? Normally, we added functionality to the system, but not in this case. Type ahead causes a performance drain that is very noticeable for medium sized data sets, when accessed over a Wide Area network or Internet connection. We expect a fair number of people to access FMSP, hosted at their offices, or at a Hosting company, and then accessing the database remotely. These people would be highly disappointed by the huge slow down of FileMaker when using “Type Ahead” features. So to prevent nasty phone calls and flaming emails, we dropped this capability out of FMSP. If you run FMSP as a single user, on your local computer, feel free to turn “Type Ahead” back on. 36.What is FREE SuperContainer Hosted Lite? SuperContainer Hosted Lite is a FREE limited version of SuperContainer that is hosted by 360Works and is built specifically into FM Starting Point. The Lite Hosting Plan includes the following: No limit on number of users within your organization. Maximum of 2 megabytes per file. Limit of 10,000 total items. 250 megabytes total storage. Up to 1 gigabyte of download/upload traffic per month. Thumbnails display at a maximum resolution of 300x300. For use exclusively with the FM Starting Point solution. 37.What is SuperContainer Hosted Pro? SuperContainer Hosted Pro is a more powerful version of SuperContainer that is hosted by 360Works and is built specifically into FM Starting Point. The “Hosted Pro” version includes the following: No limit on number of users within your organization. Unlimited file size, total items, and thumbnail resolution. 20 gigabytes total storage. Up to 20 gigabytes of download/upload traffic per month. For use with any solution, not just Starting Point. Monthly charge of $49 US. 38.What is SuperContainer Enterprise? SuperContainer Enterprise is for an unlimited number of users and access via the web, running on your own in-house FileMaker Server. The Enterprise version includes the following: No limit on number of users within your organization. Accessible only with a Web Viewer in FileMaker Pro, or via a web browser for viewing and uploading files from the web. Unlimited file size, total items, thumbnail resolution (limited only by space on your server). Unlimited total storage (limited only by space on your server). Unlimited download/upload traffic per month (limited only by bandwidth to your server). Supports SSL encryption. For use with any solution, not just Starting Point. One-time charge of $695 US. 39.What is SuperContainer Workgroup? SuperContainer Workgroup is for up to 10 FileMaker users, running on your own in-house FileMaker Server. The Workgroup version includes the following: Up to 10 users within your organization. Accessible only with a Web Viewer in FileMaker Pro (not via the a web browser). Unlimited file size, total items, thumbnail resolution (limited only by space on your server). Unlimited total storage (limited only by space on your server). Unlimited download/upload traffic per month (limited only by bandwidth to your server). Supports SSL encryption. For use with any solution, not just Starting Point. One-time charge of $195 US. 40.Does FileMaker Work on the iPhone and iPad? Yes! The product is called “FileMaker Go,” and can be installed on either the iPhone or iPad, after being purchased from the App Store. You need this software before you can use FM Starting Point on these devices. Once you have FM Go installed, you have the choice of accessing the database as shared from a FileMaker Server, or as shared from a single desktop with peer to peer sharing turned on. Also, for maximum speed, you can email or otherwise transfer FMSP to your iPhone or iPad and have it run on the device locally. 41.How do I download the iPhone or iPad version of FMSP? The iPhone and iPad version of FMSP are all “rolled together” into a single FileMaker file – the same file that is accessed by the desktop copy of FileMaker Pro. All three versions are in a single file. This way, users with different devices can log onto the same database and share data. 42.Did you make some screens designed just for the iPhone or iPad? We did actually develop some screens specific to these devices. Building an interface for a touchscreen device is somewhat different than for a desktop computer with a mouse. For the iPhone, we built out screens that allow user to find, view, edit and add contacts to FMSP. Plus, if you click the contact's phone number, it will actually dial the number and make the call on the iPhone. For the iPad, we took all the screens and functionality of FMSP and duplicated them. Then we weaked these duplicated screens so they have bigger buttons and fields things you need for a touchscreen device. 43.Does FMSP and FileMaker Go on the iPhone work with the camera built into my iPhone? Unfortunately, no: integration with the iPhone's camera is not supported in this initial release of FileMaker Go. 44.Where did the charts go in FMSP on my iPhone and iPad? Why can't I save as PDF or Print? Charting is not yet a supported feature of FileMaker Go. Same for making PDFs and printing. 45.Can Recovery for FileMaker repair my FileMaker Pro database? The effective way to find out if a FileMaker Pro database is recoverable is to try the demo version of Recovery for FileMaker on it. 46.What limitations does the demo version of Recovery for FileMaker have? Demo version recovers limited number of the database rows. The remaining rows will be blank. Full version will restore demo-limited rows as well. 47.I have tried the demo. How do I decide whether to purchase the full version of Recovery for FileMaker? Evaluating the results of demo recovery can help in making the decision. 48. Why is WSDOT using FileMaker Pro for electronic forms? In October 1992, the department started researching and testing different software packages to develop and deploy electronic forms department wide. None of the software provided all of the features initially defined. FileMaker Pro (version 2.0) was chosen, providing the most features, flexibility, and usability within the WSDOT IT infrastructure. 49.After successful recovery of the original database a new .DBF file is created. What is the procedure for transferring data from this temporary file to a database? You should simply import data from the resulting file in .DBF format into a new database. 50.Will FMTouch support the Apple iPad? Yes, we have already tested and written the new code for FMTouch and the Apple iPad. 51.Will FMTouch work with FileMaker 11? Yes, FMTouch works with FileMaker 11. There was an update to a new plug-in for FMTouch FileMaker 11 support. If you are using FileMaker 11, please make sure you download the new plug-in. 52.Will FMTouch work on both the iPhone and the iPod iTouch? Yes, FMTouch works with both the iPhone and the iPod iTouch. 53.Do I have to be connected to the internet? No, you do not have to be connected to the internet. FMTouch runs locally on your mobile device as a local application. You can sync FMTouch while you have FileMaker running with the sync plug-in - sync once an hour, once a day on your own schedule. 54.Will Runtime solutions run on FMTouch? Yes, runtime solutions work on FMTouch. 55.What versions of FileMaker are supported? FMTouch works with FileMaker version 8-11 and beyond. We will not be releasing versions for FileMaker 7 and below. 56.Do I have to design special layouts or databases? You should make database layouts that would render effectively on the iPhone. Many developers are simply adding iPhone specific layouts. Smaller databases are also faster and take less time to load. 57.Is FMTouch Relational? Yes, and you will find that the ability to use and edit portals is great bonus. You have the ability to have many related tables and many related databases all talking to one another. 58.Can I have multiple layouts? Yes, you can have multiple layouts, and you can easily deselect the layouts that you don't want to display. 59.Can I do scripting and calculations? Scripting and Calculations are supported. 60.Are repeating fields supported? Yes, repeating fields are now supported as are merge fields. As of version 1.23. Note: Repeating fields require FileMaker 9+. 61.Will FMTouch work for both Windows and Macintosh? Yes, FMTouch works equally well with both Macintosh and Windows OS. 62.What versions of FileMaker does FMTouch support? Initially you will need FileMaker Advanced to create your DDR. Once this is generated, FMTouch can be used with FileMaker Pro 8-11. Note: 8.5 is needed for webviewer support. 63.Why do I need FileMaker Advanced? FileMaker Advanced enables you to generate your database DDR. This information is needed to help FMTouch create your database. Once the DDR is created you can use regular FileMaker Pro 8-10. 64.Will enterprise or developer licenses be available? Yes, enterprise licensing is available. 65.I am having problems syncing with my Mac? If you are having problems syncing 99% of the time it is because of a few things. You have a firewall set up - and the correct port is not open. You are trying to sync through the USB cable. You do not have the plug-in correctly installed. 66.I am having problems syncing with my PC? If you are having problems syncing 99% of the time it is because of a few things. You have a firewall set up - and the correct port is not open. You are trying to sync through the USB cable. You do not have the plug-in correctly installed. 67.Do you have an online Forum? Yes 68.Are container fields supported? Yes, beginning with version 1.30 we added container field support. 69.Can I sync to FileMaker Server on Windows and MaC? Yes, check out the user’s guide server section you can sync to both Mac and PC Server with FileMaker Server 9, 10 and 11. 70.What version of FileMaker Pro is the department using? The department is currently using FileMaker Pro 11.0v3. FileMaker Pro is a Level Playing Field software and is installed on all WSDOT workstations. For our downloadable eForms, we are using version 11.0v3 of the FileMaker Pro runtime engine. FileMaker Questions and Answers Pdf Download Read the full article
0 notes
Text
14 Open Source API Testing Tools For REST & SOAP Services
I wanted to share this great post from Joe Colantonio because he put together a great mashup of API testing tools that is quite extensive and exhaustive. This area of testing is becoming a bigger and bigger part of test automation and needs to be continue to be refined as the demand for API testing continues to grow.
One thing that I will be focussing on as we post more and more on this blog is not only good information about testing tools but how they can be applied for different scenerios. Check out Joe’s top 14 API testing tools below.
As we move towards more Agile shift-left software development processes like continuous integration and delivery, the need to quickly give test feedback to our developers is increasing.
One downfall to UI tests is they are slow, making them a poor choice for letting developers know quickly if their code has broken the latest build or not. API tests, on the other hand, tend to be faster and run more reliably than GUI tests.
Before we take a closer look at the api testing tools, let’s make sure we’re all on the same page with what an API actually is.
What is an API?
Application Programming Interfaces (API) is a specification that acts as an interface for software components.
While most functional testing involves testing a user interface like a web page or a dot net form, API testing involves bypassing a user interface and communicating directly with an application by making calls to its APIs.
API testing allows you to test headless technologies like JMS HTTP, databases and Web services.
API testing is sometimes called “headless” testing. Most headless testing consists of bypassing the UI and sending a request directly to an application’s backend or service and receiving a response, while validating the response to ensure things are working as we expect them to.
This simple example is often referred to as a client/server relationship. A client makes a request by asking for a resource; the request then goes out and finds a server that can fill that request. The server locates the desired resource and sends a response back to the client.
What API Testing Tools Can I Use to Automate API Testing?
Since Selenium is just for browser based testing, you may be wondering which tool to use for Rest and Soap web service-based testing.
Here are some of the top API testing tools that can be used for Rest and Soap Web Service Testing.
Postman
Postman is a rest client that started off as a Chrome browser plugin but recently came out with native versions for both Mac and Windows.
At a high level, you can use it to send a post request to your web server and it gives you the response back. It allows you to set up all the headers and cookies your API expects, and then check the response when it comes back.
Can be used for both automated and exploratory testing
Can be run on Mac, Windows, Linux &Chrome Apps
Has a bunch of integrations like support for Swagger & RAML formats
Has Run, Test, Document and Monitoring Features
Doesn’t require learning a new language
Karate DSL
Karate allows you to create a test that can sequence calls to any kind of web-service and assert that the responses are as expected.
Build on top of Cucumber-JVM
Can run test and generate reports like any standard Java project
Test can be written without any Java knowledge required
Tests are easy to write even for non-programmers
Check out a quick example on how to get started using Karate with BDD.
SoapUI
SoapUI is a headless functional testing tool from SmartBear software. It comes in two flavors: Free open source version and Pro Version. Since the free version is open-source, you can actually gain access to the full source code and modify as needed. The pro version is user-friendlier, and has additional functionality including a form editor, an assertion wizard for Xpath, and SQL query builder. The free version lets you:
Can easily create custom code using Groovy
Drag and Drop Test Creating
Can create complex scenarios
Asynchronous Testing
SoapUI’s Mock Service lets you mimic web services before they are implemented
HttpMaster Express
HttpMaster describes itself as a web development and test tool to automate testing of web sites and services. It can be used to test RESTful web services and API applications. HttpMaster also allows you to and monitor API responses.
HttpsMaster project offers global options to customize your API request
Parameter capabilities enable you to include dynamic data with your request
You can use request chaining to leverage request items to include some data from previous request with the next request
Rest- Assured
Rest-Assured is an open-source Java Domain-specific language (DSL) that makes testing REST service simple. It simplifies things by eliminating the need to use boiler-plate code to test and validate complex responses. It also supports XML and JSON Request/Responses.
Removes need to create boilerplate code required to interact with a rest service
Support BDD Given/When/Then syntax
Integrated seamlessly with Java projects
RestSharp
RestSharp is a simple REST and HTTP API Client for .NET
Supports .NET 3.5+, Silverlight 5, Windows Phone 8, Mono, MonoTouch, Mono for Android
Easy installation using NuGet for most .NET flavors
GET, POST, PUT, PATCH, HEAD, OPTIONS, DELETE supported
Rest Console
HTTP Client and Request Visualizer and Constructor tool, helps developers build, debug and test RESTful APIs. Rest Console is a HTTP Request Visualizer and Constructor tool, helps developers build, debug and test RESTful APIs.
Easy query parameters creation
Syntax highlighting
Authentication support: Plain, Basic, OAuth + Custom
RoboHydra Server
RoboHydra is a testing tool for HTTP-based clients (ie. software that makes HTTP requests). The idea is, instead of connecting your clients-under-test to the real server, you connect them to RoboHydra and make RoboHydra respond with whatever you need for each request.
You can test many different kinds of clients
Written in Javascript, runs under Node
Hippie-Swagger
hippie-swagger is a tool for testing RESTful APIs. It’s also an API testing tool with automatic swagger assertions. In addition to validating API behavior, it will fail tests when swagger documentation is missing or inaccurate.
Can validate All aspects of swagger file validated; parameters, request/response body, paths, etc.
Accurate, human readable assertion messages
WebInject
WebInject is an open source solution for automated testing of web applications and web services. It can be used to test individual system components that have HTTP interfaces (JSP, ASP, CGI, PHP, AJAX, Servlets, HTML Forms, XML/SOAP Web Services, REST, etc).
Is a command line tool
Written in Perl can be installed on MS Windows, GNU/Linux, BSD, Solaris, MAC OS
Pyresttest
PyRestTest is a python based REST testing and API microbenchmarking tool
You can write your tests in basic YAML or JSON config files, no code needed
Returns exit codes on failure
Only works on Mac and Linux
Airborne
Airborne is an open source Ruby based RSpec driven API testing framework.
Works with Rack application like Sinatra and Grape
Works with APIs written in Rails
Unirest
Recommended by Unmesh Gundecha Unirest is a lightweight HTTP request client libraries.
Can be combined with xUnit, BDD runner to make it a test tool
Mockbin
Mockbin was recommended by Augusto Marietti. Mockbin allows you to generate custom endpoints to test, mock, and track HTTP requests & responses between libraries, sockets and APIs.
Mock Custom Endpoints
Create Custom HTTP Methods
Log and inspect incoming calls to your custom endpoints
Api Testing Tools Recap
These are the top API testing tools I’ve come across, but there are tons of API testing tools popping up everywhere, so I’ll definitely be adding to this list as time goes on.
If one of your favorite API test tools is not listed, please let me know and I’ll add it.
Initially shared on Joe’s Blog
Over time I will be adding additional comments on API Testing tools for sure. Be sure to be notified of future posts.
�� from WordPress http://ift.tt/2h186KA
1 note
·
View note
Text
Top 10 Password Tools for Windows, Linux and Cracking Web Applications
Hacking has been the existence of more than a century. It all started when a group of young people wondered how the phone went to work, to make the right connections and direct calls to the right place. Originally, the cut was not even seen as a negative connotation with which they associate the term with the modern world in connection. The term "piracy" is an abbreviation that modifies completing the performance of a computer operating system that would take less time and improve. In recent years we have seen the development of technology in great shape with almost everything you can do online, such as banking, shopping, investments, etc., and more. All you need to do is identify the site you want to visit and create insurance with a strong password. The password is a secret word or phrase that is used for authentication, to prove identity or access permission to gain access to accounts and resources. A password protects our accounts or resources from unauthorized access. What Cracking Password? A password break is the process of guessing or restoring a stored password positions or outside the data transmission system. The purpose of password cracking, the user could help restore a forgotten or unjustified password easy to verify access to a system or as a preventative measure by system administrators of crack passwords ables. When the penetration test is used to check the security of an application. Passwords are a necessary evil in today's world. You need a unique and complex password for daily online activities, such as email, social media, etc. If your password is short or simple, you are always at risk of hacking. In recent years, computer programmers have been trying to create algorithms to break passwords in less time. Most password-breaking tools try to log in with all possible combinations of words. If the application is correct, it means that the password is found. But on the other hand, it can take hours or weeks or months to crack a password when strong enough with a combination of numbers, letters and special symbols. Some tools to crack passwords using a dictionary, what passwords have. But the success rate of these tools is less, because it totally depends on expanding dictionary. Developers in recent years have developed many tools for breaking passwords. Each tool has its own advantages and disadvantages. In this article, we introduce some of the most popular password-breaking tools.
Please note that this article is for educational purposes only and should not be used because it is illegal, and illegal in many countries. We are not responsible for the consequences . 1. Brutus Released in October 2000, it is one of Brutus' popular online crack passwords tools. It says it's the fastest and most flexible password wrapping tool. This tool is free and is only available for Windows systems. Supports HTTP (Basic Authentication), HTTP (HTML / CGI Form) also create, FTP, POP3, SMB, Telnet and other species such as NNTP, IMAP, NetBus etc. You can create your own authentication types. This tool also supports multiple authentication engines and stages to be connected in a position of 60 simultaneous targets. It contains record and send options again. Therefore, you can pause the attack process at any time and then resume if you want to continue. While this tool has for many years not been updated, it can still be useful. 2. Cain and Abel Cain and Abel is a password-breaking tool known by Microsoft operating systems. It allows easy retrieval of various types of passwords through network sniffing, decrypt encrypted passwords, restore wireless network key, encrypted password cracks dictionary, recording conversations in VoIP brute-force attacks and boxes revealing password Cryptanalysis, parsing protocols Routing and caching passwords. The program does not exploit software vulnerabilities or errors that could not be fixed with little effort. It includes some aspects / weaknesses in security protocol standards, authentication methods, and caching mechanisms. This tool is designed for network administrators, penetration testers, security experts and forensic personnel. Download here: http://ift.tt/1kpiaVf
3. RainbowCrack RainbowCrack cookies differs from traditional brute force because they were large pre-calculated tables used called rainbow tables, to reduce the time required considerably to break a password. It is a computer program that will break the rainbow tables using the generated password. Trade-off memory time is a calculation method in which all clear and hashed pairs are calculated using a hashed algorithm. The results are stored in the rainbow table after calculation. This process takes a long time. However, once the table is ready, you can break a password should be faster than the brute force tools. You also need rainbow tablets to generate by yourself. RainbowCrack developers also have LM rainbow tables, rainbow MD5 tables, NTLM rainbow tables and SHA1 rainbow tables generated. As RainbowCrack these tables are free. You can download these tables and use them for password-breaking processes. Download Rainbow tables here: http://ift.tt/yvmRhK 4. John the Ripper John the Ripper is a fast tool known and cracks open source tool that today many variants of Unix, Windows, DOS, BeOS and OpenVMS. Its main goal is to detect weak Unix passwords. In addition, the different types of crypt (3) password hashes are most commonly found on various Unix systems and are supported out of the box of Windows LM hashes, improved along with several other hashes and figures in the community version. Also available is a professional version of the tool that offers best features and native packages for target operating systems. You can also Openwall GNU / * / Linux download, comes with the John Ripper. Download John the Ripper here: http://ift.tt/yp4QcY 5. Wfuzz Wfuzz password wrench software tools are web applications for coercion. It can be used to find not connected (directories, servlets, scripts, etc.), parameter Brute Force (user / password), GET and POST parameters brute force various types of injections (SQL, XSS, LDAP for test, etc.). Fuzzing etc. 6. AirCrack NG The Aircrack is an 802.11 WEP and WPA-PSK cracking program, the keys can retrieve when packets have been captured data. Scans the encrypted wireless packets and then try to crack passwords by their crack algorithm. It implements the standard FMS attack along with some optimizations like korek attacks and the PTW attack, making the attack much faster compared to other WEP cracking tools. It is available for Windows and Linux systems. Aircrack a live CD is also available. Download AirCrack-NG here: http://ift.tt/xnExA3 7. THC Hydra THC Hydra is often the tool of choice when remote authentication brute force crack service is required. You can perform a fast dictionary attacks against more than 30 protocols, including TELNET, FTP, HTTP, HTTPS, SMB, multiple databases and more. It also shows you why it is faster than other similar tools. The new modules are easy on the tool to install. You can easily add modules and improved functionality. It is available for Windows, Linux, OS X, Solaris and BSD free. This tool supports multiple network protocols. Currently, it is compatible with Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enabled, CVS, Firebird, FTP, HTTP FORM-GET, HTTP POST form, HTTP GET, HTTP HEAD, HTTP proxies, HTTPS and FORM -get, HTTPS FORM POST, HTTPS GET, HTTPS HEAD, HTTP proxy, ICQ, IMAP, IRC, LDAP, MS SQL, MySQL, NCP, NNTP, Oracle listener, Oracle SID, Oracle and PC. , SNMP, SOCKS5, SSH (v1 and v2), Subversion, TeamSpeak (TS2), Telnet, VMware Auth, VNC and XMPP. Download THC Hydra here: http://ift.tt/1hm2Ffm 8. Medusa Medusa is also a tool like THC Hydra to crack passwords. He claims to be a brute-force, modular, and quick-access instrument. It supports HTTP, FTP, CVS, AFP, IMAP, MS SQL, MySQL, NCP, NNTP, POP3, PostgreSQL, pcAnywhere, rlogin, SMB, rsh, SMTP, SNMP, SSH, SVN, VNC, Telnet and vmauthd. As long as the password, the username and password host can be flexible input attack plans when. Since Medusa a command-line tool, you need to learn commands before using the tool. The effectiveness of the tool, depending on the network connection. You can try 2,000 passwords per minute on a local system. You can also perform a parallel attack with this tool. For example, if you want the same range passwords for some email accounts, we can cite the list of usernames with password list. Download Medusa here: http://ift.tt/1kpibbE 9. L0phtCrack The L0phtCrack Cracking Tools password is an alternative to ophcrack. Try to break Windows password hashes. Use Windows workstations, primary domain controllers, network servers, and Active Directory to break passwords. It is also used to produce dictionary and brute force attack and guessing passwords. L0phtCrack is equipped with powerful features such as programming, 64-bit hash extraction versions of Windows, multi-processor algorithms and network monitoring and decoding. It was acquired by Symantec and later adjusted in 2006 to acquire the developers and L0phtCrack called L0pht back to life in 2009. It also comes with an audit feature programming routine. You can set daily weekly or monthly tests, and start scanning at the scheduled time. Download L0phtCrack: http://ift.tt/1kpidjE 10. OphCrack Ophcrack is a free Windows password cracker based on rainbow tables. It is a very efficient application of rainbow by the inventors of the method carried out in tables. It comes with a graphical user interface (GUI) and runs on multiple platforms. You can also use it on Linux and Mac systems. Rubbing the LM and NTLM hashes. To break Windows XP, Vista and Windows 7, rainbow tables are available for free. A Live CD Ophcrack is also for accelerating cracks, available. You can use Ophcrack LiveCD to crack Windows-based passwords. This tool is available for free. Download OphCrack here: http://ift.tt/y7NAAR
via Blogger http://ift.tt/2lwqBay
2 notes
·
View notes
Text
Spring Interview Questions and Answers
Spring Interview Questions
What is Spring Framework?
What are some of the important features and advantages of Spring Framework?
What do you understand by Dependency Injection?
How do we implement DI in Spring Framework?
What are the new features in Spring 5?
What is Spring WebFlux?
What are the benefits of using Spring Tool Suite?
Name some of the important Spring Modules?
What do you understand by Aspect Oriented Programming?
What is Aspect, Advice, Pointcut, JointPoint and Advice Arguments in AOP?
What is the difference between Spring AOP and AspectJ AOP?
What is Spring IoC Container?
What is a Spring Bean?
What is the importance of Spring bean configuration file?
What are different ways to configure a class as Spring Bean?
What are different scopes of Spring Bean?
What is Spring Bean life cycle?
How to get ServletContext and ServletConfig object in a Spring Bean?
What is Bean wiring and @Autowired annotation?
What are different types of Spring Bean autowiring?
Does Spring Bean provide thread safety?
What is a Controller in Spring MVC?
What’s the difference between @Component, @Repository & @Service annotations in Spring?
What is DispatcherServlet and ContextLoaderListener?
What is ViewResolver in Spring?
What is a MultipartResolver and when it’s used?
How to handle exceptions in Spring MVC Framework?
How to create ApplicationContext in a Java Program?
Can we have multiple Spring configuration files?
What is ContextLoaderListener?
What are the minimum configurations needed to create Spring MVC application?
How would you relate Spring MVC Framework to MVC architecture?
How to achieve localization in Spring MVC applications?
How can we use Spring to create Restful Web Service returning JSON response?
What are some of the important Spring annotations you have used?
Can we send an Object as the response of Controller handler method?
How to upload file in Spring MVC Application?
How to validate form data in Spring Web MVC Framework?
What is Spring MVC Interceptor and how to use it?
What is Spring JdbcTemplate class and how to use it?
How to use Tomcat JNDI DataSource in Spring Web Application?
How would you achieve Transaction Management in Spring?
What is Spring DAO?
How to integrate Spring and Hibernate Frameworks?
What is Spring Security?
How to inject a java.util.Properties into a Spring Bean?
Name some of the design patterns used in Spring Framework?
What are some of the best practices for Spring Framework?
Spring Interview Questions and Answers
Spring is one of the most widely used Java EE framework. Spring framework core concepts are “Dependency Injection” and “Aspect Oriented Programming”.
Spring framework can be used in normal java applications also to achieve loose coupling between different components by implementing dependency injection and we can perform cross-cutting tasks such as logging and authentication using spring support for aspect-oriented programming.
I like spring because it provides a lot of features and different modules for specific tasks such as Spring MVC and Spring JDBC. Since it’s an open source framework with a lot of online resources and active community members, working with the Spring framework is easy and fun at the same time.
Recommended Read: Spring Framework
Spring Framework is built on top of two design concepts – Dependency Injection and Aspect Oriented Programming.
Some of the features of spring framework are:
Lightweight and very little overhead of using framework for our development.
Dependency Injection or Inversion of Control to write components that are independent of each other, spring container takes care of wiring them together to achieve our work.
Spring IoC container manages Spring Bean life cycle and project specific configurations such as JNDI lookup.
Spring MVC framework can be used to create web applications as well as restful web services capable of returning XML as well as JSON response.
Support for transaction management, JDBC operations, File uploading, Exception Handling etc with very little configurations, either by using annotations or by spring bean configuration file.
Some of the advantages of using Spring Framework are:
Reducing direct dependencies between different components of the application, usually Spring IoC container is responsible for initializing resources or beans and inject them as dependencies.
Writing unit test cases are easy in Spring framework because our business logic doesn’t have direct dependencies with actual resource implementation classes. We can easily write a test configuration and inject our mock beans for testing purposes.
Reduces the amount of boiler-plate code, such as initializing objects, open/close resources. I like JdbcTemplate class a lot because it helps us in removing all the boiler-plate code that comes with JDBC programming.
Spring framework is divided into several modules, it helps us in keeping our application lightweight. For example, if we don’t need Spring transaction management features, we don’t need to add that dependency on our project.
Spring framework support most of the Java EE features and even much more. It’s always on top of the new technologies, for example, there is a Spring project for Android to help us write better code for native Android applications. This makes spring framework a complete package and we don’t need to look after the different framework for different requirements.
Dependency Injection design pattern allows us to remove the hard-coded dependencies and make our application loosely coupled, extendable and maintainable. We can implement dependency injection pattern to move the dependency resolution from compile-time to runtime.
Some of the benefits of using Dependency Injection are Separation of Concerns, Boilerplate Code reduction, Configurable components, and easy unit testing.
Read more at Dependency Injection Tutorial. We can also use Google Guice for Dependency Injection to automate the process of dependency injection. But in most of the cases, we are looking for more than just dependency injection and that’s why Spring is the top choice for this.
We can use Spring XML based as well as Annotation-based configuration to implement DI in spring applications. For better understanding, please read Spring Dependency Injection example where you can learn both the ways with JUnit test case. The post also contains a sample project zip file, that you can download and play around to learn more.
Spring 5 brought a massive update to Spring framework. Some of the new features in Spring 5 are:
Spring 5 runs on Java 8+ and supports Java EE 7. So we can use lambda expressions and Servlet 4.0 features. It’s good to see Spring trying to support the latest versions.
Spring Framework 5.0 comes with its own Commons Logging bridge; spring-jcl instead of standard Commons Logging.
Support for providing spring components information through index file “META-INF/spring.components” rather than classpath scanning.
Spring WebFlux brings reactive programming to the Spring Framework.
Spring 5 also supports Kotlin programming now. This is a huge step towards supporting functional programming, just as Java is also moving towards functional programming.
Support for JUnit 5 and parallel testing execution in the Spring TestContext Framework.
You can read about these features in more detail at Spring 5 Features.
Spring WebFlux is the new module introduced in Spring 5. Spring WebFlux is the first step towards the reactive programming model in spring framework.
Spring WebFlux is the alternative to the Spring MVC module. Spring WebFlux is used to create a fully asynchronous and non-blocking application built on the event-loop execution model.
You can read more about it at Spring WebFlux Tutorial.
We can install plugins into Eclipse to get all the features of Spring Tool Suite. However, STS comes with Eclipse with some other important kinds of stuff such as Maven support, Templates for creating different types of Spring projects and tc server for better performance with Spring applications.
I like STS because it highlights the Spring components and if you are using AOP pointcuts and advice, then it clearly shows which methods will come under the specific pointcut. So rather than installing everything on our own, I prefer using STS when developing Spring-based applications.
Some of the important Spring Framework modules are:
Spring Context – for dependency injection.
Spring AOP – for aspect oriented programming.
Spring DAO – for database operations using DAO pattern
Spring JDBC – for JDBC and DataSource support.
Spring ORM – for ORM tools support such as Hibernate
Spring Web Module – for creating web applications.
Spring MVC – Model-View-Controller implementation for creating web applications, web services etc.
Enterprise applications have some common cross-cutting concerns that are applicable to different types of Objects and application modules, such as logging, transaction management, data validation, authentication etc. In Object Oriented Programming, modularity of application is achieved by Classes whereas in AOP application modularity is achieved by Aspects and they are configured to cut across different classes methods.
AOP takes out the direct dependency of cross-cutting tasks from classes that are not possible in normal object-oriented programming. For example, we can have a separate class for logging but again the classes will have to call these methods for logging the data. Read more about Spring AOP support at Spring AOP Example.
Aspect: Aspect is a class that implements cross-cutting concerns, such as transaction management. Aspects can be a normal class configured and then configured in Spring Bean configuration file or we can use Spring AspectJ support to declare a class as Aspect using @Aspect annotation.
Advice: Advice is the action taken for a particular join point. In terms of programming, they are methods that gets executed when a specific join point with matching pointcut is reached in the application. You can think of Advices as Spring interceptors or Servlet Filters.
Pointcut: Pointcut are regular expressions that are matched with join points to determine whether advice needs to be executed or not. Pointcut uses different kinds of expressions that are matched with the join points. Spring framework uses the AspectJ pointcut expression language for determining the join points where advice methods will be applied.
Join Point: A join point is a specific point in the application such as method execution, exception handling, changing object variable values etc. In Spring AOP a join point is always the execution of a method.
Advice Arguments: We can pass arguments in the advice methods. We can use args() expression in the pointcut to be applied to any method that matches the argument pattern. If we use this, then we need to use the same name in the advice method from where the argument type is determined.
These concepts seems confusing at first, but if you go through Spring Aspect, Advice Example then you can easily relate to them.
AspectJ is the industry-standard implementation for Aspect Oriented Programming whereas Spring implements AOP for some cases. Main differences between Spring AOP and AspectJ are:
Spring AOP is simpler to use than AspectJ because we don’t need to worry about the weaving process.
Spring AOP supports AspectJ annotations, so if you are familiar with AspectJ then working with Spring AOP is easier.
Spring AOP supports only proxy-based AOP, so it can be applied only to method execution join points. AspectJ support all kinds of pointcuts.
One of the shortcomings of Spring AOP is that it can be applied only to the beans created through Spring Context.
Inversion of Control (IoC) is the mechanism to achieve loose-coupling between Objects dependencies. To achieve loose coupling and dynamic binding of the objects at runtime, the objects define their dependencies that are being injected by other assembler objects. Spring IoC container is the program that injects dependencies into an object and makes it ready for our use.
Spring Framework IoC container classes are part of org.springframework.beans and org.springframework.context packages and provides us different ways to decouple the object dependencies.
Some of the useful ApplicationContext implementations that we use are;
AnnotationConfigApplicationContext: For standalone java applications using annotations based configuration.
ClassPathXmlApplicationContext: For standalone java applications using XML based configuration.
FileSystemXmlApplicationContext: Similar to ClassPathXmlApplicationContext except that the xml configuration file can be loaded from anywhere in the file system.
AnnotationConfigWebApplicationContext and XmlWebApplicationContext for web applications.
Any normal java class that is initialized by Spring IoC container is called Spring Bean. We use Spring ApplicationContext to get the Spring Bean instance.
Spring IoC container manages the life cycle of Spring Bean, bean scopes and injecting any required dependencies in the bean.
We use Spring Bean configuration file to define all the beans that will be initialized by Spring Context. When we create the instance of Spring ApplicationContext, it reads the spring bean XML file and initializes all of them. Once the context is initialized, we can use it to get different bean instances.
Apart from Spring Bean configuration, this file also contains spring MVC interceptors, view resolvers and other elements to support annotations based configurations.
There are three different ways to configure Spring Bean.
XML Configuration: This is the most popular configuration and we can use bean element in context file to configure a Spring Bean. For example:
Java Based Configuration: If you are using only annotations, you can configure a Spring bean using @Bean annotation. This annotation is used with @Configuration classes to configure a spring bean. Sample configuration is:
Annotation Based Configuration: We can also use @Component, @Service, @Repository and @Controller annotations with classes to configure them to be as spring bean. For these, we would need to provide base package location to scan for these classes. For example:
<bean name="myBean" class="com.journaldev.spring.beans.MyBean"></bean>
@Configuration @ComponentScan(value="com.journaldev.spring.main") public class MyConfiguration { @Bean public MyService getService(){ return new MyService(); } }
To get this bean from spring context, we need to use following code snippet:
AnnotationConfigApplicationContext ctx = new AnnotationConfigApplicationContext( MyConfiguration.class); MyService service = ctx.getBean(MyService.class);
<context:component-scan base-package="com.journaldev.spring" />
There are five scopes defined for Spring Beans.
singleton: Only one instance of the bean will be created for each container. This is the default scope for the spring beans. While using this scope, make sure spring bean doesn’t have shared instance variables otherwise it might lead to data inconsistency issues because it’s not thread-safe.
prototype: A new instance will be created every time the bean is requested.
request: This is same as prototype scope, however it’s meant to be used for web applications. A new instance of the bean will be created for each HTTP request.
session: A new bean will be created for each HTTP session by the container.
global-session: This is used to create global session beans for Portlet applications.
Spring Framework is extendable and we can create our own scopes too, however most of the times we are good with the scopes provided by the framework.
To set spring bean scopes we can use “scope” attribute in bean element or @Scope annotation for annotation based configurations.
Spring Beans are initialized by Spring Container and all the dependencies are also injected. When the context is destroyed, it also destroys all the initialized beans. This works well in most of the cases but sometimes we want to initialize other resources or do some validation before making our beans ready to use. Spring framework provides support for post-initialization and pre-destroy methods in spring beans.
We can do this by two ways – by implementing InitializingBean and DisposableBean interfaces or using init-method and destroy-method attribute in spring bean configurations. For more details, please read Spring Bean Life Cycle Methods.
There are two ways to get Container specific objects in the spring bean.
Implementing Spring *Aware interfaces, for these ServletContextAware and ServletConfigAware interfaces, for complete example of these aware interfaces, please read Spring Aware Interfaces
Using @Autowired annotation with bean variable of type ServletContext and ServletConfig. They will work only in servlet container specific environment only though.
@Autowired ServletContext servletContext;
The process of injection spring bean dependencies while initializing it called Spring Bean Wiring.
Usually, it’s best practice to do the explicit wiring of all the bean dependencies, but the spring framework also supports auto-wiring. We can use @Autowired annotation with fields or methods for autowiring byType. For this annotation to work, we also need to enable annotation-based configuration in spring bean configuration file. This can be done by context:annotation-config element.
For more details about @Autowired annotation, please read Spring Autowire Example.
There are four types of autowiring in Spring framework.
autowire byName
autowire byType
autowire by constructor
autowiring by @Autowired and @Qualifier annotations
Prior to Spring 3.1, autowire by autodetect was also supported that was similar to autowire by constructor or byType. For more details about these options, please read Spring Bean Autowiring.
The default scope of Spring bean is singleton, so there will be only one instance per context. That means that all the having a class level variable that any thread can update will lead to inconsistent data. Hence in default mode spring beans are not thread-safe.
However, we can change spring bean scope to request, prototype or session to achieve thread-safety at the cost of performance. It’s a design decision and based on the project requirements.
Just like MVC design pattern, Controller is the class that takes care of all the client requests and send them to the configured resources to handle it. In Spring MVC, org.springframework.web.servlet.DispatcherServlet is the front controller class that initializes the context based on the spring beans configurations.
A Controller class is responsible to handle a different kind of client requests based on the request mappings. We can create a controller class by using @Controller annotation. Usually, it’s used with @RequestMapping annotation to define handler methods for specific URI mapping.
@Component is used to indicate that a class is a component. These classes are used for auto-detection and configured as bean when annotation based configurations are used.
@Controller is a specific type of component, used in MVC applications and mostly used with RequestMapping annotation.
@Repository annotation is used to indicate that a component is used as repository and a mechanism to store/retrieve/search data. We can apply this annotation with DAO pattern implementation classes.
@Service is used to indicate that a class is a Service. Usually, the business facade classes that provide some services are annotated with this.
We can use any of the above annotations for a class for auto-detection but different types are provided so that you can easily distinguish the purpose of the annotated classes.
DispatcherServlet is the front controller in the Spring MVC application and it loads the spring bean configuration file and initialize all the beans that are configured. If annotations are enabled, it also scans the packages and configure any bean annotated with @Component, @Controller, @Repository or @Service annotations.
ContextLoaderListener is the listener to start up and shut down Spring’s root WebApplicationContext. It’s important functions are to tie up the lifecycle of ApplicationContext to the lifecycle of the ServletContext and to automate the creation of ApplicationContext. We can use it to define shared beans that can be used across different spring contexts.
ViewResolver implementations are used to resolve the view pages by name. Usually we configure it in the spring bean configuration file. For example:
<!-- Resolves views selected for rendering by @Controllers to .jsp resources in the /WEB-INF/views directory --> <beans:bean class="org.springframework.web.servlet.view.InternalResourceViewResolver"> <beans:property name="prefix" value="/WEB-INF/views/" /> <beans:property name="suffix" value=".jsp" /> </beans:bean>
InternalResourceViewResolver is one of the implementation of ViewResolver interface and we are providing the view pages directory and suffix location through the bean properties. So if a controller handler method returns “home”, view resolver will use view page located at /WEB-INF/views/home.jsp.
MultipartResolver interface is used for uploading files – CommonsMultipartResolver and StandardServletMultipartResolver are two implementations provided by spring framework for file uploading. By default there are no multipart resolvers configured but to use them for uploading files, all we need to define a bean named “multipartResolver” with type as MultipartResolver in spring bean configurations.
Once configured, any multipart request will be resolved by the configured MultipartResolver and pass on a wrapped HttpServletRequest. Then it’s used in the controller class to get the file and process it. For a complete example, please read Spring MVC File Upload Example.
Spring MVC Framework provides the following ways to help us achieving robust exception handling.
Controller Based – We can define exception handler methods in our controller classes. All we need is to annotate these methods with @ExceptionHandler annotation.
Global Exception Handler – Exception Handling is a cross-cutting concern and Spring provides @ControllerAdvice annotation that we can use with any class to define our global exception handler.
HandlerExceptionResolver implementation – For generic exceptions, most of the times we serve static pages. Spring Framework provides HandlerExceptionResolver interface that we can implement to create global exception handler. The reason behind this additional way to define global exception handler is that Spring framework also provides default implementation classes that we can define in our spring bean configuration file to get spring framework exception handling benefits.
For a complete example, please read Spring Exception Handling Example.
There are following ways to create spring context in a standalone java program.
AnnotationConfigApplicationContext: If we are using Spring in standalone java applications and using annotations for Configuration, then we can use this to initialize the container and get the bean objects.
ClassPathXmlApplicationContext: If we have spring bean configuration xml file in standalone application, then we can use this class to load the file and get the container object.
FileSystemXmlApplicationContext: This is similar to ClassPathXmlApplicationContext except that the xml configuration file can be loaded from anywhere in the file system.
For Spring MVC applications, we can define multiple spring context configuration files through contextConfigLocation. This location string can consist of multiple locations separated by any number of commas and spaces. For example;
<servlet> <servlet-name>appServlet</servlet-name> <servlet-class>org.springframework.web.servlet.DispatcherServlet</servlet-class> <init-param> <param-name>contextConfigLocation</param-name> <param-value>/WEB-INF/spring/appServlet/servlet-context.xml,/WEB-INF/spring/appServlet/servlet-jdbc.xml</param-value> </init-param> <load-on-startup>1</load-on-startup> </servlet>
We can also define multiple root level spring configurations and load it through context-param. For example;
<context-param> <param-name>contextConfigLocation</param-name> <param-value>/WEB-INF/spring/root-context.xml /WEB-INF/spring/root-security.xml</param-value> </context-param>
Another option is to use import element in the context configuration file to import other configurations, for example:
<beans:import resource="spring-jdbc.xml"/>
ContextLoaderListener is the listener class used to load root context and define spring bean configurations that will be visible to all other contexts. It’s configured in web.xml file as:
<context-param> <param-name>contextConfigLocation</param-name> <param-value>/WEB-INF/spring/root-context.xml</param-value> </context-param> <listener> <listener-class>org.springframework.web.context.ContextLoaderListener</listener-class> </listener>
For creating a simple Spring MVC application, we would need to do the following tasks.
Add spring-context and spring-webmvc dependencies in the project.
Configure DispatcherServlet in the web.xml file to handle requests through spring container.
Spring bean configuration file to define beans, if using annotations then it has to be configured here. Also we need to configure view resolver for view pages.
Controller class with request mappings defined to handle the client requests.
Above steps should be enough to create a simple Spring MVC Hello World application.
As the name suggests Spring MVC is built on top of Model-View-Controller architecture. DispatcherServlet is the Front Controller in the Spring MVC application that takes care of all the incoming requests and delegate it to different controller handler methods.
The model can be any Java Bean in the Spring Framework, just like any other MVC framework Spring provides automatic binding of form data to java beans. We can set model beans as attributes to be used in the view pages.
View Pages can be JSP, static HTMLs etc. and view resolvers are responsible for finding the correct view page. Once the view page is identified, control is given back to the DispatcherServlet controller. DispatcherServlet is responsible for rendering the view and returning the final response to the client.
Spring provides excellent support for localization or i18n through resource bundles. Basis steps needed to make our application localized are:
Creating message resource bundles for different locales, such as messages_en.properties, messages_fr.properties etc.
Defining messageSource bean in the spring bean configuration file of type ResourceBundleMessageSource or ReloadableResourceBundleMessageSource.
For change of locale support, define localeResolver bean of type CookieLocaleResolver and configure LocaleChangeInterceptor interceptor. Example configuration can be like below:
Use spring:message element in the view pages with key names, DispatcherServlet picks the corresponding value and renders the page in corresponding locale and return as response.
<beans:bean id="messageSource" class="org.springframework.context.support.ReloadableResourceBundleMessageSource"> <beans:property name="basename" value="classpath:messages" /> <beans:property name="defaultEncoding" value="UTF-8" /> </beans:bean> <beans:bean id="localeResolver" class="org.springframework.web.servlet.i18n.CookieLocaleResolver"> <beans:property name="defaultLocale" value="en" /> <beans:property name="cookieName" value="myAppLocaleCookie"></beans:property> <beans:property name="cookieMaxAge" value="3600"></beans:property> </beans:bean> <interceptors> <beans:bean class="org.springframework.web.servlet.i18n.LocaleChangeInterceptor"> <beans:property name="paramName" value="locale" /> </beans:bean> </interceptors>
For a complete example, please read Spring Localization Example.
We can use Spring Framework to create Restful web services that returns JSON data. Spring provides integration with Jackson JSON API that we can use to send JSON response in restful web service.
We would need to do following steps to configure our Spring MVC application to send JSON response:
Adding Jackson JSON dependencies, if you are using Maven it can be done with following code:
Configure RequestMappingHandlerAdapter bean in the spring bean configuration file and set the messageConverters property to MappingJackson2HttpMessageConverter bean. Sample configuration will be:
In the controller handler methods, return the Object as response using @ResponseBody annotation. Sample code:
You can invoke the rest service through any API, but if you want to use Spring then we can easily do it using RestTemplate class.
<!-- Jackson --> <dependency> <groupId>com.fasterxml.jackson.core</groupId> <artifactId>jackson-databind</artifactId> <version>${jackson.databind-version}</version> </dependency>
<!-- Configure to plugin JSON as request and response in method handler --> <beans:bean class="org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerAdapter"> <beans:property name="messageConverters"> <beans:list> <beans:ref bean="jsonMessageConverter"/> </beans:list> </beans:property> </beans:bean> <!-- Configure bean to convert JSON to POJO and vice versa --> <beans:bean id="jsonMessageConverter" class="org.springframework.http.converter.json.MappingJackson2HttpMessageConverter"> </beans:bean>
@RequestMapping(value = EmpRestURIConstants.GET_EMP, method = RequestMethod.GET) public @ResponseBody Employee getEmployee(@PathVariable("id") int empId) { logger.info("Start getEmployee. ID="+empId); return empData.get(empId); }
For a complete example, please read Spring Restful Webservice Example.
Some of the Spring annotations that I have used in my project are:
@Controller – for controller classes in Spring MVC project.
@RequestMapping – for configuring URI mapping in controller handler methods. This is a very important annotation, so you should go through Spring MVC RequestMapping Annotation Examples
@ResponseBody – for sending Object as response, usually for sending XML or JSON data as response.
@PathVariable – for mapping dynamic values from the URI to handler method arguments.
@Autowired – for autowiring dependencies in spring beans.
@Qualifier – with @Autowired annotation to avoid confusion when multiple instances of bean type is present.
@Service – for service classes.
@Scope – for configuring scope of the spring bean.
@Configuration, @ComponentScan and @Bean – for java based configurations.
AspectJ annotations for configuring aspects and advices, @Aspect, @Before, @After, @Around, @Pointcut etc.
Yes we can, using @ResponseBody annotation. This is how we send JSON or XML based response in restful web services.
Spring provides built-in support for uploading files through MultipartResolver interface implementations. It’s very easy to use and requires only configuration changes to get it working. Obviously we would need to write controller handler method to handle the incoming file and process it. For a complete example, please refer Spring File Upload Example.
Spring supports JSR-303 annotation based validations as well as provide Validator interface that we can implement to create our own custom validator. For using JSR-303 based validation, we need to annotate bean variables with the required validations.
For custom validator implementation, we need to configure it in the controller class. For a complete example, please read Spring MVC Form Validation Example.
Spring MVC Interceptors are like Servlet Filters and allow us to intercept client request and process it. We can intercept client request at three places – preHandle, postHandle and afterCompletion.
We can create spring interceptor by implementing HandlerInterceptor interface or by extending abstract class HandlerInterceptorAdapter.
We need to configure interceptors in the spring bean configuration file. We can define an interceptor to intercept all the client requests or we can configure it for specific URI mapping too. For a detailed example, please refer Spring MVC Interceptor Example.
Spring Framework provides excellent integration with JDBC API and provides JdbcTemplate utility class that we can use to avoid bolier-plate code from our database operations logic such as Opening/Closing Connection, ResultSet, PreparedStatement etc.
For JdbcTemplate example, please refer Spring JDBC Example.
For using servlet container configured JNDI DataSource, we need to configure it in the spring bean configuration file and then inject it to spring beans as dependencies. Then we can use it with JdbcTemplate to perform database operations.
Sample configuration would be:
<beans:bean id="dbDataSource" class="org.springframework.jndi.JndiObjectFactoryBean"> <beans:property name="jndiName" value="java:comp/env/jdbc/MyLocalDB"/> </beans:bean>
For complete example, please refer Spring Tomcat JNDI Example.
Spring framework provides transaction management support through Declarative Transaction Management as well as programmatic transaction management. Declarative transaction management is most widely used because it’s easy to use and works in most of the cases.
We use annotate a method with @Transactional annotation for Declarative transaction management. We need to configure the transaction manager for the DataSource in the spring bean configuration file.
<bean id="transactionManager" class="org.springframework.jdbc.datasource.DataSourceTransactionManager"> <property name="dataSource" ref="dataSource" /> </bean>
Spring DAO support is provided to work with data access technologies like JDBC, Hibernate in a consistent and easy way. For example we have JdbcDaoSupport, HibernateDaoSupport, JdoDaoSupport and JpaDaoSupport for respective technologies.
Spring DAO also provides consistency in exception hierarchy and we don’t need to catch specific exceptions.
We can use Spring ORM module to integrate Spring and Hibernate frameworks if you are using Hibernate 3+ where SessionFactory provides current session, then you should avoid using HibernateTemplate or HibernateDaoSupport classes and better to use DAO pattern with dependency injection for the integration.
Spring ORM provides support for using Spring declarative transaction management, so you should utilize that rather than going for Hibernate boiler-plate code for transaction management.
For better understanding you should go through following tutorials:
Spring Hibernate Integration Example
Spring MVC Hibernate Integration Example
Spring security framework focuses on providing both authentication and authorization in java applications. It also takes care of most of the common security vulnerabilities such as CSRF attack.
It’s very beneficial and easy to use Spring security in web applications, through the use of annotations such as @EnableWebSecurity. You should go through the following posts to learn how to use the Spring Security framework.
Spring Security in Servlet Web Application
Spring MVC and Spring Security Integration Example
We need to define propertyConfigurer bean that will load the properties from the given property file. Then we can use Spring EL support to inject properties into other bean dependencies. For example;
<bean id="propertyConfigurer" class="org.springframework.context.support.PropertySourcesPlaceholderConfigurer"> <property name="location" value="/WEB-INF/application.properties" /> </bean> <bean class="com.journaldev.spring.EmployeeDaoImpl"> <property name="maxReadResults" value="${results.read.max}"/> </bean>
If you are using annotation to configure the spring bean, then you can inject property like below.
@Value("${maxReadResults}") private int maxReadResults;
Spring Framework is using a lot of design patterns, some of the common ones are:
Singleton Pattern: Creating beans with default scope.
Factory Pattern: Bean Factory classes
Prototype Pattern: Bean scopes
Adapter Pattern: Spring Web and Spring MVC
Proxy Pattern: Spring Aspect Oriented Programming support
Template Method Pattern: JdbcTemplate, HibernateTemplate etc
Front Controller: Spring MVC DispatcherServlet
Data Access Object: Spring DAO support
Dependency Injection and Aspect Oriented Programming
Some of the best practices for Spring Framework are:
Avoid version numbers in schema reference, to make sure we have the latest configs.
Divide spring bean configurations based on their concerns such as spring-jdbc.xml, spring-security.xml.
For spring beans that are used in multiple contexts in Spring MVC, create them in the root context and initialize with listener.
Configure bean dependencies as much as possible, try to avoid autowiring as much as possible.
For application-level properties, the best approach is to create a property file and read it in the spring bean configuration file.
For smaller applications, annotations are useful but for larger applications, annotations can become a pain. If we have all the configuration in XML files, maintaining it will be easier.
Use correct annotations for components for understanding the purpose easily. For services use @Service and for DAO beans use @Repository.
Spring framework has a lot of modules, use what you need. Remove all the extra dependencies that get usually added when you create projects through Spring Tool Suite templates.
If you are using Aspects, make sure to keep the join pint as narrow as possible to avoid advice on unwanted methods. Consider custom annotations that are easier to use and avoid any issues.
Use dependency injection when there is an actual benefit, just for the sake of loose-coupling don’t use it because it’s harder to maintain.
That’s all for Spring Framework interview questions. I hope these questions will help you in coming Java EE interview. I will keep on adding more questions to the list as soon as I found them. If you know some more questions that should be part of the list, make sure to add a comment for it and I will include it
0 notes
Text
Java Technologies for Web Applications
You can find web applications everywhere on the Internet. Many of these web applications are used to process online forms, tally voting polls, take orders within online stores, allow users to book a flight for their next business trip, or simply to display the user's login name. Which Java technologies do you need to create a web application and which packages do you need to import? The answer depends on what kind of application you're building and what it does.
This article provides an overview of the Java technologies involved in creating various types of web applications, tells you when you might decide to use them, and provides links to get you started. Future articles will cover how to use these technologies in building web applications. To use the technologies described in this article, download Java Development Kit (JDK) 5.0 Update 9 with Java Platform, Enterprise Edition (Java EE) or later and install it on your computer.
Before you begin coding, you need to understand what a web application is, what Java technologies are available for use, and what development tools can save you time and make creating applications easier.
Contents
What Is a Web Application?
Java Technologies to Use in Web Applications
Other Technologies to Consider
Development Tools
What Is a Web Application?
Web applications are by nature distributed applications, meaning that they are programs that run on more than one computer and communicate through a network or server. Specifically, web applications are accessed with a web browser and are popular because of the ease of using the browser as a user client. For the enterprise, the ability to update and maintain web applications without deploying and installing software on potentially thousands of client computers is a key reason for their popularity. Web applications are used for web mail, online retail sales, discussion boards, weblogs, online banking, and more. One web application can be accessed and used by millions of people.
Like desktop applications, web applications are made up of many parts and often contain miniprograms, some of which have user interfaces, and some of which do not require a graphical user interface (GUI) at all. In addition, web applications frequently require an additional markup or scripting language, such as HTML, CSS, or JavaScript programming language. Also, many applications use only the Java programming language, which is ideal because of its versatility.
A web application can be as simple as a page that shows the current date and time or as complex as a set of pages on which you can look up and book the most convenient flight, hotels, and car rentals for your next vacation.
The Java technologies you'll use to create web applications are a part of the Java EE platform, in addition to many of the Java Platform, Standard Edition (Java SE) classes and packages. In order for many of these technologies to work on a server, the server must have a container, or web server, installed that recognizes and runs the classes you create. For development and testing of these technologies, you can use the tools detailed in this article, but when you deploy, make sure that the server has Java server software installed to run Java technology-based web applications. If you don't have access to this information, ask the server administrator.
Java Technologies to Use in Web Applications
There are too many Java technologies to list in one article, so this article will describe only the ones most frequently used. The number of technologies listed here can appear overwhelming. Keep in mind that you will not need to use them all. In fact, a web application often consists of nothing more than one page created with the JavaServer Pages (JSP) technology. Sometimes you will combine three or more such technologies. No matter how many you end up using, it's good to know what is available to you and how you can use each one in a web application.
Java Servlet API
The Java Servlet API lets you define HTTP-specific classes. A servlet class extends the capabilities of servers that host applications that are accessed by way of a request-response programming model. Although servlets can respond to any type of request, they are commonly used to extend the applications hosted by web servers. For instance, you might use a servlet to get the text input from an online form and print it back to the screen in an HTML page and format, or you might use a different servlet to write the data to a file or database instead. A servlet runs on the server side -- without an application GUI or HTML user interface (UI) of its own. Java Servlet extensions make many web applications possible.
Figure 1 shows clients talking to Java Servlet extensions. Clients may range in complexity from simple HTML forms to sophisticated Java technology-based applets.
The javax.servlet and javax.servlet.http packages provide the classes and interfaces to define servlets. HTML servlet classes extend the javax.servlet.http.HttpServlet abstract class, which provides a framework for handling HTTP protocol. Learn more about Java Servlet extensions and navigating with servlets.
JavaServer Pages Technology
JavaServer Pages (JSP) technology provides a simplified, fast way to create dynamic web content. JSP technology enables rapid development of web-based applications that are server- and platform-independent. JSP technology lets you add snippets of servlet code directly into a text-based document. Typically, a JSP page is a text-based document that contains two types of text:
Static data, which can be expressed in any text-based format, such as HTML, Wireless Markup Language (WML), or XML
JSP technology elements, which determine how the page constructs dynamic contentThe packages involved in creating JSP pages are javax.el, javax.servlet.jsp, javax.servlet.jsp.el, and javax.servlet.jsp.tagext, though you will rarely have to import these directly. A JSP page can be as simple as a bit of HTML with one snippet of JSP code and the .jsp extension of the page name.
For instance, you can create a web site of JSP technology pages that use one snippet of code to include the header.html file, which contains the site navigation. This way, when you change a link to a button in the navigation, you make the change in only one file, and that file loads into all the pages on the site that have this code snippet:
<%@ include file="header.html" %>
That line of code works very much like a server-side include, if you are familiar with those. Because this web page is now a JSP page, you could also go on to add more Java technology code to create dynamic web content, such as polls, forms, ways to enter or retrieve data from a database, and so forth.
Take a look at two helpful documents about creating JSP pages:
JavaServer Pages (JSP) v2.0 Syntax Reference
JavaServer Pages Technology -- Frequently Asked Questions
JavaServer Pages Standard Tag Library
The JavaServer Pages Standard Tag Library (JSTL) encapsulates core functionality common to many JSP technology-based applications. Instead of mixing tags from numerous vendors in your applications, you employ a single standard set of tags. This standardization allows you to deploy your applications on any JSP container that supports JSTL and makes it more likely that the implementation of the tags is optimized.
JSTL has iterator and conditional tags for handling flow control, tags for manipulating XML documents, internationalization tags, tags for accessing databases using SQL, and tags for commonly used functions.
The packages you can access for using JSTL are javax.servlet.jsp.jstl.core , javax.servlet.jsp.jstl.fmt , javax.servlet.jsp.jstl.sql , and javax.servlet.jsp.jstl.tlv .
Learn more about JSTL.
JavaServer Faces Technology
JavaServer Faces technology is a UI framework for building web applications. The main components of JavaServer Faces technology involve a GUI component framework, a flexible model for rendering components in various markup languages and technologies, and a standard RenderKit for generating HTML markup.
This functionality is available through standard Java APIs and XML-based configuration files. In addition, Sun Java Studio Creator IDE leverages JavaServer Faces technology in its drag-and-drop GUI tools, allowing you to use the technology without having to write or understand the underlying code. See also " Getting Started With Sun Java Studio Creator."
Java Message Service API
Messaging is a method of communication between software components or applications. A messaging system is a peer-to-peer facility. In other words, a messaging client can send messages to and receive messages from any other client. Each client connects to a messaging agent that provides facilities for creating, sending, receiving, and reading messages. By combining Java technology with enterprise messaging, the Java Message Service (JMS) API provides a powerful tool for solving enterprise computing problems.
Enterprise messaging provides a reliable, flexible service for the exchange of business data throughout an enterprise. The JMS API adds to this a common API and provider framework that enables the development of portable message-based applications in the Java programming language. An example of how JMS might be used is an application that keeps track of inventory for an auto manufacturer.The inventory component can send a message to the factory component when the inventory level for a product goes below a certain level, so the factory can make more cars. The factory component can send a message to the parts components so that the factory can assemble the parts it needs.The parts components in turn can send messages to their own inventory and order components to update their inventories and to order new parts from suppliers and so forth.
The JMS API improves programmer productivity by defining a common set of messaging concepts and programming strategies that all JMS technology-compliant messaging systems will support.
Learn more about the JMS API.
JavaMail API and the JavaBeans Activation Framework
Web applications can use the JavaMail API to send email notifications. The API has two parts: an application-level interface that the application components use to send email and a service provider interface. Service providers implement particular email protocols, such as SMTP. Several service providers are included with the JavaMail API package, and others are available separately. The Java EE platform includes the JavaMail extension with a service provider that allows application components to send email.
In conjunction with the JavaMail extension, you might use the JavaBeans Activation Framework (JAF) API. This API provides standard services to determine the type of an arbitrary piece of data, encapsulate access to it, discover the operations available on it, and create the appropriate component based on JavaBeans component architecture (JavaBeans component) to perform those operations.
The JavaMail API is now open source. See the GlassFish Project -- JavaMail home page.
Learn more about the JavaMail API and the JAF.
Java API for XML Processing
The Java API for XML Processing (JAXP), part of the Java SE platform, supports the processing of XML documents using the Document Object Model (DOM), the Simple API for XML (SAX), and Extensible Stylesheet Language Transformations (XSLT). JAXP enables applications to parse and transform XML documents independent of a particular XML-processing implementation.
JAXP also provides namespace support, which lets you work with schemas that might otherwise have naming conflicts. Designed to be flexible, JAXP lets you use any XML-compliant parser or XSL processor from within your application and supports the W3C schema.
Learn more about JAXP.
The Java API for XML Web Services (JAX-WS) is now an open-source project at java.net and is also a key part of the GlassFish project. See also Introducing JAX-WS 2.0 With the Java SE 6 Platform, Part 1.
JDBC API
The JDBC API allows you invoke database SQL commands from Java programming language methods. You can use the JDBC API in a servlet, JSP technology page, or an enterprise bean when you need to access the database.
The JDBC API has two parts: an application-level interface that application components use to access a database and a service provider interface to attach a JDBC driver to the Java EE platform.
The left side of Figure 2 shows how a client makes a direct call to the application server, usually through a servlet or JSP page, and that data is then sent to the database management system (DBMS) server. The right side of Figure 2 shows how a driver translates JDBC calls into the middleware vendor's protocol.
Learn more about the JDBC API.
Java Persistence API
The Java Persistence API is a Java technology standards-based solution for persistence. Persistence uses an object-relational mapping approach to bridge the gap between an object-oriented model and a relational database. Java technology persistence consists of three areas:
The Java Persistence API
The query language
Object-relational mapping metadata
Read the Java Persistence API FAQ.
Java Naming and Directory Interface
The Java Naming and Directory Interface (JNDI) provides naming and directory functionality, enabling applications to access multiple naming and directory services. It provides applications with methods for performing standard directory operations, such as associating attributes with objects and searching for objects using their attributes. Using JNDI, a web application can store and retrieve any type of named Java technology object, allowing applications to coexist with many legacy applications and systems.
Naming services provide application clients, enterprise beans, and web components with access to a JNDI naming environment. A naming environment allows the developer to customize a component without having to access or change the component's source code. A container implements the component's environment and provides it to the component as a JNDI naming context.
Learn more about JNDI.
Other Technologies to Consider
You might want to consider using the following other technologies in your web application, depending on the application's complexity:
J2EE Connector Architecture: Tools vendors and system integrators use this architecture to create resource adapters that support access to enterprise information systems that can be plugged in to any Java EE technology-based product.
Java Authentication and Authorization Service (JAAS): JAAS provides a way for a Java EE technology-based application to authenticate and authorize a specific user or group of users to run it.
Java API for XML Registries (JAXR): JAXR lets you access business and general-purpose registries over the web.
Java Architecture for XML Binding (JAXB): JAXB provides a convenient way to bind an XML schema to a representation in applications written in the Java programming language.
SOAP with Attachments API for Java (SAAJ): SAAJ is a low-level API on which JAX-WS and JAXR depend.
Java Transaction API (JTA): JTA provides a standard interface for demarcating transactions.
Development Tools
Integrated development environments (IDEs) can speed the process of developing and testing web applications. It's no wonder that developers move to an IDE, but which one is right for you? Which features do you need? Sun Microsystems supports three IDEs for the Java platform: NetBeans IDE, Sun Java Studio Creator IDE, and Sun Java Studio Enterprise IDE.
NetBeans IDE
NetBeans IDE is free and open source. This IDE is written in the Java programming language and provides the services common to desktop applications, such as window and menu management, settings storage, and so forth. It is also the first IDE to fully support JDK 5.0 features. In addition, it supports web tools, including the NetBeans IDE Enterprise Pack, which adds everything you need to immediately start writing, testing, and debugging Java technology-based web applications.
The pack provides visual design tools for Unified Modeling Language (UML) modeling, XML schema creation, modification, and visualization, as well as development of secure, identity-enabled web services.
Sun Java Studio Creator IDE
Sun Java Studio Creator IDE is great for quick and easy web application development. In addition, this IDE is built on the NetBeans IDE, starting with a subset of the functionality and extending it.
Sun Java Studio Creator IDE allows you to build applications visually. The programming part is cleanly separated from the UI. With Sun Java Studio Creator IDE, the IDE takes care of a lot of the repetitive coding behind the UI.
The rapid visual drag-and-drop features are based on JavaServer Faces technology, which is a framework for building UIs for web applications. A GUI is used for manipulating JavaServer Faces components, as well as visually defining page flow. There's also graphical support for easily working with databases and web services.
Sun Java Studio Enterprise IDE
Sun Java Studio Enterprise IDE is a powerful set of tools that provides an integrated framework for enterprise-grade, rapid web application development. It offers enhanced debugging and development support for web services and for development of Java EE technology-based applications.
Sun Java Studio Enterprise IDE is built on and extends the NetBeans IDE. It also enables smart code editing, such as completing your code for you, with refactoring, renaming objects throughout an application. It also enables performance tuning -- ensuring better use of memory and so forth -- of applications with an optimal end- user experience.
Sun Java Studio Enterprise IDE provides a model-driven analysis, design, and development environment that leverages UML. This integrated feature reduces complexity and increases visual clarity across software development projects, ensuring that a sound architecture is established and communicated throughout the enterprise.
Now that you are familiar with the many Java technologies that you use in web applications, you are ready to develop your own application. In an upcoming series of articles, you will learn to create web applications using Sun Java Studio Creator IDE, which you can download for free, and learn how to use the Java technologies mentioned in this article. You will first create small simple applications, then work up to more complex programs. In the meantime, follow the links in this article to learn more about the Java technologies discussed in this article.[Source]-https://www.oracle.com/technetwork/articles/java/webapps-1-138794.html
We provide best java classes in vashi, navi mumbai. We have industry experienced trainers and provide hands on practice. Basic to advanced modules are covered in training sessions.
0 notes
Text
Tute 5
Web Service
W3C (World Wide Web Consortium) describes web service as a system of software allowing different machines to interact with each other through network. Web services achieve this task with the help of XML, SOAP, WSDL and UDDI open standards.
XML: The full form of XML is ‘Extensible Markup Language’ which is used to share data on the web and in universal format.
SOAP: Standing for ‘Simple Object Access Protocol’ which is an application communication protocol that sends and receives messages through XML format. It is one of the best ways to communicate between applications over HTTP which is supported by all browsers and servers.
WSDL: Written in XML, WSDL stands for Web Services Description Language and is used to describe web service. WSDL comprises three parts such as Definitions (usually expressed in XML including both data type definitions), Operations and Service bindings. Operations denote actions for the messages supported by a Web service.
There are three types of operations:
One way
Request response
Notification
Service bindings: Service bindings is a connecting to the port.
UDDI: Universal Description, Discovery, and Integration (UDDI) provides the description of a set of services supporting the depiction and discovery of businesses, organizations, and other Web Services providers. It is based on common set of industry standards, including HTTP, XML, XML Schema, and SOAP.
Web Application
An application that the users access over the internet is called a web application. Generally, any software that is accessed through a client web browser could be called a web application.
What is client?
So what is a client? A ‘client’ can be referred to the program that the person use to run the application in the client-server environment. The client-server environment refers to multiple computers sharing information such as entering info into a database. Here the “client” is the application that is used to enter the info, while the “server” is the application that is used to store the information.
Web Services vs Web Applications
Web Services can be used to transfer data between Web Applications.
Web Services can be accessed from any languages or platform.
A Web Application is meant for humans to read, while a Web Service is meant for computers to read.
Web Application is a complete Application with a Graphical User Interface (GUI), however, web services do not necessarily have a user interface since it is used as a component in an application.
Web Application can be access through browsers.
Our expertise lies in our in-depth knowledge, vast experience and exposure in automating business processes, offering effective web services and web applications solutions to transform them into your business objectives. We have an adept team with best of breed technologies to change the growth story of your business.
Carmatec brings together multifaceted skill-set from the areas of design, behavioral science, usability, analytics, marketing and brand creation to provide businesses with holistic solutions for Web Design, Web & Mobile Development,
Remote IT infrastructure management, Software Development, Managed IT services, Cloud Consulting, Internet Marketing and Branding.
WSDL
WSDL stands for Web Services Description Language. It is the standard format for describing a web service. WSDL was developed jointly by Microsoft and IBM.
Features of WSDL
WSDL is an XML-based protocol for information exchange in decentralized and distributed environments.
WSDL definitions describe how to access a web service and what operations it will perform.
WSDL is a language for describing how to interface with XML-based services.
WSDL is an integral part of Universal Description, Discovery, and Integration (UDDI), an XML-based worldwide business
registry.
WSDL is the language that UDDI uses.
WSDL is pronounced as 'wiz-dull' and spelled out as 'W-S-D-L'.
WSDL Usage
WSDL is often used in combination with SOAP and XML Schema to provide web services over the Internet. A client program connecting to a web service can read the WSDL to determine what functions are available on the server. Any special datatypes used are embedded in the WSDL file in the form of XML Schema. The client can then use SOAP to actually call one of the functions listed in the WSDL.
History of WSDL
WSDL 1.1 was submitted as a W3C Note by Ariba, IBM, and Microsoft for describing services for the W3C XML Activity on XML Protocols in March 2001. WSDL 1.1 has not been endorsed by the World Wide Web Consortium (W3C), however it has just released a draft for version 2.0 that will be a recommendation (an official standard), and thus endorsed by the W3C.
WSDL Elements
The WSDL file contains the following main parts
The <types> tag is used to define all the complex datatypes, which will be used in the message exchanged between the client application and the web service. This is an important aspect of the client application, because if the web service works with a complex data type, then the client application should know how to process the complex data type. Data types such as float, numbers, and strings are all simple data types, but there could be structured data types which may be provided by the web service.
For example, there could be a data type called EmployeeDataType which could have 2 elements called "EmployeeName" of type string and "EmployeeID" of type number or integer. Together they form a data structure which then becomes a complex data type.
The <message> tag is used to define the message which is exchanged between the client application and the web server. These messages will explain the input and output operations which can be performed by the web service. An example of a message can be a message which accepts the EmployeeID of an employee, and the output message can be the name of the employee based on the EmpoyeeID provided.
The <portType> tag is used to encapsulate every input and output message into one logical operation. So there could be an operation called "GetEmployee" which combines the input message of accepting the EmployeeID from a client application and then sending the EmployeeName as the output message.
The <binding> tag is used to bind the operation to the particular port type. This is so that when the client application calls the relevant port type, it will then be able to access the operations which are bound to this port type. Port types are just like interfaces. So if a client application needs to use a web service they need to use the binding information to ensure that they can connect to the interface provided by that web service.
The <service> tag is a name given to the web service itself. Initially, when a client application makes a call to the web service, it will do by calling the name of the web service. For example, a web service can be located at an address. The service tag will actually have the URL which will actually tell the client application that there is a web service available at this location.
SOAP
SOAP is a messaging protocol and in a nutshell is just another XML language. Its purpose is the data exchange over networks. Its concern is the encapsulation of these data and the rules for transmitting and receiving them.
HTTP is an application protocol and SOAP messages are placed as the HTTP payload. Although there is the overhead of HTTP, it has the advantage that it is a protocol that is open to firewalls, well-understood and widely-supported. Thus, web services can be accessed and exposed via technology already in-place.
SOAP messages are usually exchanged via HTTP. Although it is possible to use other (application) protocols, e.g. SMTP or FTP, the non-HTTP bindings are not specified by SOAP specs and are not supported by WS-BP (interoperability spec). You could exchange SOAP messages over raw TCP but then you would have web services that are not interoperable (not compliant to WS-BP).
Nowadays the debate is why have the SOAP overhead at all and not send data over HTTP (RESTful WS).
Why use HTTP for SOAP?
I will try to address in more detail the question in the OP, asking why use HTTP for SOAP:
First of all SOAP defines a data encapsulation format and that's that. Now the majority of traffic in the web is via HTTP. HTTP is literary EVERYWHERE and supported by a well-established infrastructure of servers and clients(namely browsers). Additionally it is a very well understood protocol.
The people who created SOAP wanted to use this ready infrastructure and SOAP messages were designed so that they can be tunneled over HTTP In the specs they do not refer to any other non-HTTP binding but specifically refer to HTTP as an example for transfer. The tunneling over HTTP would and did help in it's rapid adoption. Because the infrastructure of HTTP is already in-place, companies would not have to spend extra money for another kind of implementation. Instead they can expose and access web services using technology already deployed.
Specifically in Java a web service can be deployed either as a servlet endpoint or as an EJB endpoint. So all the underlying network sockets, threads, streams, HTTP transactions etc. are handled by the container and the developer focuses only on the XML payload. So a company has Tomcat or JBoss running in port 80 and the web service is deployed and accessible as well. There is no effort to do programming at the transport layer and the robust container handles everything else. Finally the fact that firewalls are configured not to restrict HTTP traffic is a third reason to prefer HTTP.
Since HTTP traffic is usually allowed, the communication of clients/servers is much easier and web services can function without network security blockers issues as a result of the HTTP tunneling.
SOAP is XML=plain text so firewalls could inspect the content of HTTP body and block accordingly. But in this case they could also be enhanced to reject or accept SOAP depending on the contents.This part which seems to trouble you is not related to web services or SOAP, and perhaps you should start a new thread concerning how firewalls work.
Having said that, the fact that HTTP traffic is unrestricted often causes security issues since firewalls are essentially by-passed, and that is why application-gateways come in. But this is not related to this post.
Summary
So to sum up the reasons for using HTTP:
HTTP is popular and successful.
HTTP infrastructure is in place so no extra cost to deploy web services.
HTTP traffic is open to firewalls, so there are no problems during web service functioning as a result of network security.
0 notes
Video
youtube
Annamalai assignment 2019 Answer sheets in online whatsapp 9924764558
GLOBAL MARKETING MBA ANNAMALAI ASSIGNMENT ANSWER PROVIDED WHATSAPP 91 9924764558
CONTACT: DR. PRASANTH MBA PH.D. DME MOBILE / WHATSAPP: +91 9924764558 OR +91 9447965521 EMAIL: [email protected] WEBSITE: www.casestudyandprojectreports.com
ANNAMALAI UNIVERSITY DIRECTORATE OF DISTANCE EDUCATION M.B.A. E. BUSINESS SECOND YEAR Academic Year 2018 - 2019 ASSIGNMENT TOPICS This booklet contains assignment topics. Students are asked to write the assignments for SIX papers as per instructions, those who have opted Project and Viva-Voce. Students are asked to write the assignments for the EIGHT Papers as per instruction those who have opted Two Theory Papers (2.7.1 & 2.7.2) as specialisation. Last date for submission : 28-02-2019 Last date for submission with late fee ` 300/- : 15-03-2019 NOTE: 1. Assignments sent after 15-03-2019 will not be evaluated. 2. Assignments should be in the own handwriting of the student concerned and not type-written or printed or photocopied. 3. Assignments should be written on A4 paper on one side only. 4. All assignments (with Enrolment number marked on the Top right hand corner on all pages) should be put in an envelop with superscription “MBA Assignments” and sent to The Director, Directorate of Distance Education, Annamalai University, Annamalainagar – 608 002 by Registered post. 5. No notice will be taken on assignments which are not properly filled in with Enrolment Number and the Title of the papers. 6. Students should send full set of assignments for all papers. Partial assignments will not be considered. ASSIGNMENT INSTRUCTIONS Write assignments on any TWO topics in each paper out of the FOUR. For each Topic the answer should not exceed 15 pages. Each assignment carries 25 marks (2 topics). DR. M. ARUL DIRECTOR 2 2.1 E-COMMERCE 1. Enumerate Security of Internet hosts and networks, Public key infrastructure, Safety of E-Commerce applications, Electronic payment systems, Trust and reputation in E-Commerce. 2. Discuss about the prevention procedures of the firewall to avoid the attack of Hackers. 3. “Online Shopping generate new economy”- Comment your opinion with proper Justification. 4. Discuss the role played by E-commerce in providing customer service at the various stages (product selection to post purchase) in an online buying transaction. 2.2 E-COMMERCE: APPLICATION AND SECURITIES 1. Is the e-payment system secured? How? and why not? Discuss different types of e-commerce payment systems available globally. 2. Elaborate the Past, Present and Future of the World Wide Web. 3. The Emerging Role of Banks in E-Commerce and Application of E-commerce in Banking.– Discuss 4. Security Issues & Challenges to E- Commerce, Looking Ahead to the Future of E-Commerce Security-Elaborate. 2.3 INTERNET AND JAVA PROGRAMMING 1. “The Internet has no single owner, yet everyone owns (a portion of) the Internet. The Internet has no central operator, yet everyone operates (a portion of) the Internet” – Discuss. 2. Can DHTML be used to create website? Create a website for an online marketing company. Explain the process. 3. “Application security features are built into the JAVA language”. Discuss on how to take advantage of these features and several other simple measures to ensure Java Application Security”. 4. “Java Database Connectivity is an application programming interface (API) which allows the programmer to connect and interact with databases” - Discuss. 3 2.4 ADVANCED WEB DEVELOPMENT AND DESIGN TOOLS 1. What is Java Script. Explain the following of Java Script with suitable examples? a. Operations b. Statements c. Functions d. Event handling e. Objects f. Frames and windows g. Cookies h. Creating links i. Using images j. Doing maths 2. Explain various HTML tags used for creating a web page with suitable example. Elaborate the procedure to convert XML to HTML and HTML to XML. 3. What is a Java Bean? Discuss the architectural overview of Java Bean. Explain the components of Java Bean. Explain the properties of Java Bean with suitable coding. 4. What is servlet? Explain the lifecycle of a servlet. Explain the methods to read HTTP header. Explain the methods to set HTTP Response Header. 2.5 ENTERPRISE RESOURCE PLANNING 1. How will you execute the Gap Analysis phase of ERP implementation for a very large manufacturing industry? Discuss the steps involved in this scenario. 2. Explain the Planning and Execution Model based on integrated process for a service industry. 3. Discuss the common myths about ERP and find practical solutions for dispelling them in your organization. 4. Most companies today have made significant investments in information technology systems. Write a case study of Integrating ERP, CRM and SCM creates a single view of organizational profitability. 2.6 STRATEGIC MANAGEMENT 1. Do a SWOT Analysis for Reliance Jio 4G services in Indian market and analyse the strategic approach of reliance communication in this regard. 2. What were the major strategic drawbacks of Kingfisher Airlines? What was the vital reason for its dropdown? Consider the strategic issues and justify it. 3. Illustrate with examples of hyper competition and competitive dynamic approaches in strategic marketing. 4. Why would management adopt a stability strategy? Can stability strategies be viable over a lengthy period of time? Why or Why not? 4 2.7.1 GLOBAL MARKETING 1. Discuss the various terms of trade and explain about the concept and components of Balance of payments. 2. Elucidate the tariff and non tariff barriers and discuss about reasons for foreign exchange control. 3. Explain the functions and responsibilities of IMF and IBRD. 4. Write the export licensing procedure and forms required for exports. 2.7.2 STRUCTURED SYSTEM ANALYSIS AND DESIGN 1. Draw the context diagram and a set of data flow diagrams for developing a library management system with the following functionalities. List the assumptions made in your analysis. a. Inquiring the availability of a book by giving the ISBN or title or author's name b. Renting a book that is available c. Returning a book after use d. Reserving a book when it is not available e. Collection of overdue charges f. Maintaining book details g. Maintaining supplier details who supply the goods. 2. Design a set of files for supporting a common payroll system. Comment on the data security issues of the file system you have designed. 3. Assume that you are in charge of designing software to be installed in bank ATM. Which kind of architecture would you choose? Give reasons for your selection and draw the architecture diagram of the system. 4. Assume that you are given the following details of a small mail order catalogue system that allows people to shop from home: When a customer receives the catalogue and wants to buy something, he can telephone, fax or email his order to the company. The company gets the order and sends the goods and an invoice. When the customer receives the goods with a delivery note, he sends payment and receives a receipt for payment. Draw the context diagram and data flow diagrams up to level-2 to analyze the requirements of this system. Also, give the data dictionary. M.B.A.[E.B.] – 2ND YEAR – Assignment - AUP/551/C-200 ANNAMALAI UNIVERSITY PRESS 2018 - 2019
1 ANNAMALAI UNIVERSITY DIRECTORATE OF DISTANCE EDUCATION M.B.A. SECOND YEAR Academic Year : 2018 - 2019 ASSIGNMENT TOPICS This booklet contains assignment topics. Students are asked to write the assignments for SIX papers as per instructions, those who have opted Project and Viva-Voce. Students are asked to write the assignments for the EIGHT Papers as per instruction those who have opted Two Theory Papers as specialisation. Last date for submission : 28-02-2019 Last date for submission with late fee ` 300/- : 15-03-2019 NOTE: 1. Assignments sent after 15-03-2019 will not be evaluated. 2. Assignments should be in the own handwriting of the student concerned and not type-written or printed or photocopied. 3. Assignments should be written on A4 paper on one side only. 4. All assignments (with Enrolment number marked on the Top right hand corner on all pages) should be put in an envelop with superscription “MBA Assignments” and sent to The Director, Directorate of Distance Education, Annamalai University, Annamalainagar – 608 002 by Registered post. 5. No notice will be taken on assignments which are not properly filled in with Enrolment Number and the Title of the papers. 6. Students should send full set of assignments for all papers. Partial assignments will not be considered. ASSIGNMENT INSTRUCTIONS Write assignments on any TWO topics in each paper out of the FOUR. For each Topic the answer should not exceed 15 – pages. Each assignment carries 25 marks (2 topics). Dr. M. ARUL DIRECTOR 2 2.1 HUMAN RESOURCE MANAGEMENT 1."HR outsourcing has become a common practice throughout the world"-Discuss the implications of HR outsourcing functions. 2. Identify the Paramount barriers for effective training programme in IT field and how to crush them". Explain with real life examples. 3. What type of interview techniques do you adopt for selecting an Executive in a FMCG company for the post of Marketing Manager? 4. Assume that you are responsible for evaluating the employees’ performance in the public sector manufacturing company. Discuss the appraisal process. Also explain techniques you apply for various levels and give reasons. 2.2 MARKETING MANAGEMENT 1. Explain the recent trends in marketing concepts, also discuss the factors that a marketing manager must take into account while developing the marketing mix for the below mentioned products. 1. Female Cosmetics, 2. Children Health Drinks and 3. Adult Bike. 2. ‘Every change in the political and legal environment creates an adjustment problem for the marketers’ – as a budding manager what is your opinion about this statement and suggest a suitable strategy to adopt successful and smooth running of your business. 3. In designing an advertising campaign for a soft drink, which would you find more useful; information about consumer demographics or information about consumer life style? Give an example of how would you use each type of information. 4. Suggest a successful way to segment the market for the following products a) Detergent Soap b) Designer Jewellery c) Breakfast Cereals. 2.3 FINANCIAL MANAGEMENT 1. It is usual to declare good dividends when the company is making good profit. It is profitable for companies not to declare any dividend even when they are making good profits? What will be the reaction of the shareholder? Discuss. 2. If you are working as a financial manager in an organization, what are your policies to make profit for the organization? 3. Assume that you are new entrepreneur to start the business, which financial resources you opt? Justify with your views. 4. “The success of a business concern depends upon the way in which it earnings are computed, distributed and retained”- comment on this statement. 2.4 OPERATIONS MANAGEMENT 1. Prepare step by step Supply Chain network layout for any manufacturing company. 2. List the various factors to be considered for locating Atomic Power plant. 3. Prepare PERT network for assembling a Motor Bike. 4. Visit any production plant and list various Material Handling devices with photographs. Explain its advantages and disadvantages. 3 2.5 PROJECT MANAGEMENT AND ENTREPRENEURSHIP 1. ABC & CO Ltd wishes to setup a paper manufacturing unit in the sub urban area of your city. You have been assigned to examine the preliminary requirements and to conduct a feasibility study. What factors you will consider to study the technical and economic feasibilities of the project. Give an outline of the feasibility report. 2. ‟Detailed project report forms the foundation on which the entire super structure of the project is built,” if it is weak, the project cannot withstand the turbulent times ahead. Discuss bringing out the do’s and don’ts of a good report. 3. Discuss about the infrastructure projects in the context of present day’s economic developments of the country. Brief out the common problems associated with it and the efforts made by the government to solve the same. 4. Why do role models impact the decision of people to become the entrepreneurs? Do you think that a person whose parent was an entrepreneur of a failed business is more or less likely to start his or her own business than a person whose parents were managers of large established companies? 2.6 STRATEGIC MANAGEMENT 1. Do a SWOT Analysis for Reliance Jio 4G services in Indian market and analyse the strategic approach of reliance communication in this regard. 2. What were the major strategic drawbacks of Kingfisher Airlines? What was the vital reason for its dropdown? Consider the strategic issues and justify it. 3. Illustrate with examples of hyper competition and competitive dynamic approaches in strategic marketing. 4. Why would management adopt a stability strategy? Can stability strategies be viable over a lengthy period of time? Why or Why not? 2.7.1 HRM : (a) LABOUR WELFARE AND INDUSTRIAL RELATIONS 1. Do you think that the rules laid down on the various Acts pertaining to labour welfare are employer friendly or employee friendly? Justify your stand with valid examples. 2. What is your view that a small organization having an employee strength of 10 - 30 cannot implement employee welfare measures as per the prescribed Act or beyond the purview of the Act? Discuss with supportive evidences. 3. “Providing too many benefits to employees leads to industrial unrest hence they should be kept within certain limit”. Do you agree? Justify your stand. 4. “The Government plays an important role in establishing a better industrial relations and it passes various laws to protect the interest of both employers and employees”-Discuss. 4 2.7.1 HRM: (b) TRAINING AND DEVELOPMENT 1. Briefly explain business case for e-learning. Describe the advantages and disadvantages of e-learning in Indian scenario. 2. Prepare a training schedule for a newly joined salesman in a pharma company. 3. Assume that you are training an employee to diagnose and repair a loose wire in an electrical socket. After demonstrating the procedures to follow, you let the trainee show you how to do it. The trainee correctly demonstrates the process and repairs the connection on the first attempt. Has learning occurred? Justify your Answer. 4. Many employees are unwilling to relocate geographically because they like their current community and because spouses and children prefer not to move, as the result, it is difficult to develop employees through job experiences that require relocation. How could an employee’s current job be changed to develop that employee’s leadership skills? 2.7.2 MM : (a) SALES AND DISTRIBUTION MANAGEMENT 1. Sales Manager’s dilemma is mainly in using the Sales Management Information. System towards hiring, training and allocating tasks – Discuss. 2. Explore new marketing and distribution channel for online e-marketing Companies. 3. Middleman cannot be eliminated in distribution network – Discuss. 4. Sales management and distribution management are parallel functions – Elucidate. 2.7.2 MM : (b) MARKETING RESEARCH AND CONSUMER BEHAVIOUR 1. Marketing research is undertaken to guide managers in the analysis of marketing problems. Elucidate. 2. If you have to conduct interviews in a field survey, describe how you would establish a rapport with respondents. 3. “Knowledge about individual’s exposure to various media of communication will enable the marketer to understand consumer social behaviour:” Do you agree with this statement? Why? 4. How dogmatism and cognitive personality factors affect the purchase behaviour of consumer. 2.7.3 FM : (a) INVESTMENT, SECURITY AND PORTFOLIO MANAGEMENT 1. “The most important index in financial market is the stock index, which uses a set of stock that is representation of the whole market, or a specified sector, to measure the change in the overall behaviour of the market or sector over a period of time”. Do you agree or disagree? Give your views by taking the present situation. 5 2. The technical analyst places a great deal of importance on supply and demand in stock pricing. Presumably the fundamental analyst also believes that supply and demand are important. In what ways do the two groups disagree on the subject? Give your comments with suitable examples. 3. The efficient market theory has major implications for the practice of portfolio management. One obvious implication is the determination of superior analyst. Another is how to carry out the management of portfolios, assuming no success to superior analysts. Assume that none of the analysts to whom you have access is superior, what specific investment practices you would implement for your clients? 4. Reported earnings typically differ, sometimes considerably from economic earnings. Nevertheless, it is often argued that reported earnings are intended simply to provide source information to investors about the value of the firm. If so, might there not be alternative accounting procedures of equal use to investors? How might one go about evaluating the usefulness of such procedures? 2.7.3 FM: (b) MANAGEMENT OF FINANCIAL SERVICES 1. Outline the features of the framework of regulation of the credit information companies in India. What are the regulatory and supervisory objectives of the RBI in relation to the NBFCs? Discuss the main elements of the RBI framework of NBFC regulation. 2. I like to invest Rs 2 laths for long term in share market. Will you suggest investing it right now or should I wait for further correction. Justify your views in detail. 3. Discuss the process of selecting an investment in venture capital financing. Explain briefly the framework of the scheme of regulation of venture capital funds by the SEBI. 4. Discuss the structure and working of Indian banking industry. What suggestions would you offer for improvement of their performance? 2.7.4 PM: (a) PRODUCTION, PLANNING, CONTROL AND MAINTENANCE 1. Identify two industries of your choice. When one industry practices TQM and the other practice six SIGMA. What will be the defective rate of the two industries? 2. Visit a manufacturing industry find out the areas in which control chart are used. Prepare a detailed report. 3. Visit a manufacturing organization. Monitor the organization structure and functions of the production planning and control department. Prepare your detailed report. 4. Visit a manufacturing organization. Collect all relevant information regarding vendors of the organization. Prepare a detailed report on the vendor management practice of the organization. 6 2.7.4 PM : (b) QUALITY MANAGEMENT 1. Quality and profitability are incompatible objectives.'' Do you agree? Write the quality and profitability factors for FORD motor. 2. How would you provide for quality assurance in financial services being offered by a NBFC? 3 How a quality awards can be planned and the formalities can be achieved? Write the ISO awards in automobile manufacturing industry. 4. How the core competencies its reliability of the strategic alliances for ensuring quality? Write the factors on health care industry in India. 2.7.5 SYSTEMS: (a) PERSONAL PRODUCTIVITY TOOLS 1. For what purpose the Macros are used in MS-Word. Give two examples with including the procedures to be followed while inserting Macros with step by step instruction. 2. What are the methods adopted to draw various types of Charts in Excel. Draw any three Charts of your choice. (Attach the printout copy of the charts from Excel sheet). 3. Mail Transfer Agent (MTA) role in e-mail is important – do you agree, bring out the types and issues in it. 4. An organization wants to computerize the HR department and network their activities. Prepare a presentation on the merits and demerits of computerizing and prepare the slide animation and transition explaining the challenges of network activities. (Attach the print out copy of PPT). 2.7.5 (b) INFORMATION TECHNOLOGY 1. List and explain the issues involved in development of a business website. 2. Describe the various methodologies used in Business Process Reengineering and compare these methodologies. 3. Discuss the issues to be considered in planning, design and implementation of Cross Functional Integrated ERP Systems. 4. Manufacturers of a mobile phone may assume unique name, address, contact details with model number and type. One manufacturer made one product and different manufacturers may have different products with the same model number. But no manufacturer would have two products with the same model number. With the help of unique identity number customers are identified and have email id and physical address. Many customers may live at the same physical address, but to assume that no two customers have the same mail id. One customer placed an order with unique order number and date. For each order there are one or more products ordered and there is a quantity for each product on the order. Draw an E/R diagram to capture the above information. M.B.A. – 2nd Year – Assignment- UAP/551/C-700 ANNAMALAI UNIVERSITY PRESS 2018 -2019
ANNAMALAI UNIVERSITY DIRECTORATE OF DISTANCE EDUCATION M.B.A. FINANCIAL MANAGEMENT SECOND YEAR Academic Year 2018 - 2019 ASSIGNMENT TOPICS This booklet contains assignment topics. Students are asked to write the assignments for SIX papers as per instructions, those who have opted project and Viva-Voce. Students are asked to write the assignments for the EIGHT Papers as per instruction those who have opted Two Theory Papers (2.7.1 & 2.7.2) as specialisation. Last date for submission : 28-02-2019 Last date for submission : with late fee `300/- 15-03-2019 NOTE: 1. Assignments sent after 15-03-2019 will not be evaluated. 2. Assignments should be in the own hand writing of the student concerned and not type-written or printed or photocopied. 3. Assignments should be written on A4 paper on one side only. 4. All assignments (with Enrolment number marked on the Top right hand corner on all pages) should be put in an envelope with superscription “MBA Assignments” and sent to The Director, Directorate of Distance Education, Annamalai University, Annamalainagar – 608 002 by Registered post. 5. No notice will be taken on assignments which are not properly filled in with Enrolment Number and the Title of the papers. 6. Students should send full set of assignments for all papers. Partial assignments will not be considered. ASSIGNMENT INSTRUCTIONS Write assignments on any TWO topics in each paper out of the FOUR. For each topic the answer should not exceed 15–pages. Each assignment carries 25 marks (2 topics). DR. M. ARUL DIRECTOR 2 2.1 MANAGEMENT OF FINANCIAL SERVICES 1. Outline the features of the framework of regulation of the credit information companies in India. What are the regulatory and supervisory objectives of the RBI in relation to the NBFCs? Discuss the main elements of the RBI framework of NBFC regulation. 2. I like to invest Rs 2 lakhs for long term in share market. Will you suggest investing it right now or should I wait for further correction. Justify your views in detail. 3. Discuss the process of selecting an investment in venture capital financing. Explain briefly the framework of the scheme of regulation of venture capital funds by the SEBI. 4. Discuss the structure and working of Indian banking industry. What suggestions would you offer for improvement of their performance? 2.2 INTERNATIONAL FINANCE 1. Discuss the foreign exchange market, procedure for quotation and arbitrage. Narrate current situation of Euro currency and Euro Credit. 3. Critically evaluate the International Financial Market Instruments. Discuss the internal and external techniques of risk involved in the International Business. 3. “A non- financial firm should always completely hedge all its exposures to environmental risk factors such as exchange rates and interest rates.” Critically discuss this recommendation. 4. Real exchange rate changes are measured by adjusting nominal exchange rate changes by inflation differentials, the latter in turn being measured by some price index such as WPI or CPI. It is said that a firm faces operating exposure only if real exchange rates change. Is this strictly true? Why or why not? 2.3 DERIVATIVES MANAGEMENT 1. “Derivatives are considered as risk management tools used by organizations/ investors/individuals”. Critically evaluate the statement. 2. “The basic purpose of derivatives instruments is to provide commitments to price for future dates for giving against adverse movement in future prices”. Discuss and critically evaluate the statement. 3. “Forward contracts acts as fore-runners of futures market”. Critically evaluate the statement in light of growth of forward market Worldwide. 4. “Options are the safest instrument for investors for the investment purpose. Options writer has limited profit and unlimited losses whereas option buyer has limited losses and unlimited profits”. Critically evaluate the above statement with suitable examples. 3 2.4 RISK MANAGEMENT AND INSURANCE 1. Elaborate the loss control measures of any manufacturing company of your choice. 2. Risk cannot be avoided but can be minimised- Discuss. 3. Risk avoidance is a negative treatment of risk rather than a positive technique – Elaborate. 4. Discuss the major types of risk that are associated with great financial insecurity. 2.5 INVESTMENT, SECURITY AND PORTFOLIO MANAGEMENT 1. “The most important index in financial market is the stock index, which uses a set of stock that is representation of the whole market, or a specified sector, to measure the change in the overall behaviour of the market or sector over a period of time”. Do you agree or disagree? Give your views by taking the present situation. 2. The technical analyst places a great deal of importance on supply and demand in stock pricing. Presumably the fundamental analyst also believe that supply and demand are important. In what ways do the two groups disagree on the subject? Give your comments with suitable examples. 3. The efficient market theory has major implications for the practice of portfolio management. One obvious implication is the determination of superior analyst. Another is how to carry out the management of portfolios, assuming no success to superior analysts. Assume that none of the analysts to whom you have access is superior, what specific investment practices you would implement for your clients? 4. Reported earnings typically differ, sometimes considerably from economic earnings. Nevertheless, it is often argued that reported earnings are intended simply to provide source information to investors about the value of the firm. If so, might there not be alternative accounting procedures of equal use to investors? How might one go about evaluating the usefulness of such procedures? 2.6 STRATEGIC MANAGEMENT 1. Do a SWOT Analysis for Reliance Jio 4G services in Indian market and analyse the strategic approach of reliance communication in this regard. 2. What were the major strategic drawbacks of Kingfisher Airlines? What was the vital reason for its dropdown? Consider the strategic issues and justify it. 4 3. Illustrate with examples of hyper competition and competitive dynamic approaches in strategic marketing. 4. Why would management adopt a stability strategy? Can stability strategies be viable over a lengthy period of time? Why or Why not? 2.7.1 E-COMMERCE 1. Enumerate Security of Internet hosts and networks, Public key infrastructure, Safety of E-Commerce applications, Electronic payment systems, Trust and reputation in E-Commerce. 2. Discuss about the prevention procedures of the firewall to avoid the attack of Hackers. 3. “Online Shopping generate new economy”- Comment your opinion with proper Justification. 4. Discuss the role played by E-commerce in providing customer service at the various stages (product selection to post purchase) in an online buying transaction. 2.7.2 BUSINESS RESEARCH METHODS 1. “Empirical research in India creates so many problems for the researchers” State the problems that are usually faced by young researchers. 2. Using the different measurement scales, prepare a questionnaire, on a topic of your choice and indicate the statistical tools can be used for analysis of the questionnaire. 3. Critically examine the following statements. (a) Interviews cause more bias than the use of questionnaire while collecting data. (b) Projective technique is reliable and authentic method of data collection. 4. “Majority of the researches makes use of primary sources of data and secondary data sources do not really contribute to a scientific enquiry”. Do you agree or disagree with the statement? Explain. M.B.A.[F.M.] - 2ND Year – Assignment-AUP/551/C-1200 ANNAMALAI UNIVERSITY PRESS 2018 -2019
0 notes
Text
Java composite interface
The Composite interface, along with CompositeContext, defines the methods to compose a draw primitive with the underlying graphics area. After the Composite is set in the Graphics2D context, it combines a shape, text, or an image being rendered with the colors that have already been rendered according to pre-defined rules. The classes implementing this interface provide the rules and a method to create the context for a particular operation. CompositeContext is an environment used by the compositing operation, which is created by the Graphics2D prior to the start of the operation. CompositeContext contains private information and resources needed for a compositing operation. When the CompositeContext is no longer needed, the Graphics2D object disposes of it in order to reclaim resources allocated for the operation. What is starvation in java? What is the difference between arraylist and vector in java? What is the difference between arraylist and linkedlist? What is the difference between Iterator and ListIterator? What is the difference between Iterator and Enumeration? what is the difference between list and set in java? what is the difference between set and map in java? what is the difference between hashset and treeset in java? what is the difference between hashset and hashmap in java? what is the difference between hashmap and treemap in java? what is the difference between hashmap and hashtable in java? what is the difference between collection and collections in java? what is the difference between comparable and comparator interfaces? what is the hashcode method in java? What is garbage collection in java? What is garbage collector in java? What is gc() in java? What is finalize() method in java? Can an unreferenced objects be referenced again in java? What kind of thread is the garbage collector thread in java? what is serialization in java? what is Deserialization in java? What is transient keyword? Interview questions on java Interview questions on main Interview questions on final Interview questions on constructor Interview questions on access modifiers Interview questions on method overloading Interview questions on method overriding Interview questions on inheritance Interview questions on interface Interview questions on abstract class Interview questions on string handling Interview questions on exception handling Interview questions on multithreading Interview questions on collections Interview questions on Servlet Interview questions on JSP Interview questions on Struts Interview questions on JSF Interview questions on Hibernate Interview questions on Javamail Interview questions on Quartz Interview questions on JDBC Interview questions on SQL Interview questions on generics Interview questions on JUnit Interview questions on Log4j Interview questions on JavaScript Interview questions on PLSQL What is a Web application? What is a Web browser? What is different between web server and application server? What is a servlet container? What is MIME Type? Why do we need a constructor in a servlet if we use the init method? When servlet object is created? Who is responsible for creating the servlet object? What is the difference between HttpServlet and GenericServlet? What is HTTPServletRequest class? What is HTTPServletResponse class? How can we create deadlock condition on our servlet? For initializing a servlet can we use a constructor in place of init()? How to read form data in servlet? How to write html contents using servlets? How to send an authentication error from a servlet? What is servlet collaboration? What is lazy loading? How do we call one servlet from another servlet? What is the difference between sendRedirect and RequestDispatcher? Can we call a jsp from the servlet? How to configure a central error handling page in servlets? How to get session object? How to set attribute in session object? How to get attribute from session object? What are JSP lifecycle methods? Which JSP lifecycle methods can be overridden? How to disable session in JSP? Which directive is used in jsp custom tag? How can a thread safe JSP page be implemented? Can we use JSP implicit objects in a method defined in JSP Declaration? Which implicit object is not available in normal JSP pages? What is difference between include directive and jsp:include action? How to disable caching on back button of the browser? What are the types of JSTL tags? How is scripting disabled? How to extend java class in jsp? What is MVC? What is the difference between struts1 and struts2? Explain struts 2 request life cycle. What are the core components of a Struct2 based application? What are the types of validators in struts 2? How tag libraries are defined in Struts? Is Struts thread safe? What is the significance of @ManagedProperty annotation? How to terminate the session in JSF? Is it possible to have more than one Faces Configuration file? What are the core components are of hibernate architecture? What is SessionFactory? Is SessionFactory a thread-safe object? What is Session? Is Session a thread-safe object? What will happen if we don’t have no-args constructor in Entity bean? Can we make an hibernate entity class final? How to log hibernate generated sql queries in log files? What is POP? Explain SMTP? Explain IMAP? What is the use of MIME within message makeup? What is the difference between execute, executequery, executeupdate? What is the difference between Statement and PreparedStatement in jdbc? How can we execute stored procedures and functions? How to rollback a JDBC transaction? Explain JDBC Savepoint. What is the use of blob and clob datatypes in JDBC? What is Connection Pooling? How do you implement connection pooling? What is 2 phase commit? What are the different types of locking in JDBC? What is a “dirty read”? What is DBMS? What is RDBMS? Difference between DBMS and RDBMS What are various DDL commands in SQL? What are various DML commands in SQL?
0 notes
Text
300+ TOP IBM WEBSPHERE Interview Questions and Answers
IBM WEBSPHERE Interview Questions for freshers and experienced :-
1. What is web sphere? The word web sphere popularly refers to IBM middleware technology products. Web sphere is known for its turn key operation in e business applications. It has run time components and tools which can help in creating applications which run on WAS. WAS refers to web sphere application server. 2. What is web sphere commerce? IBM web sphere commerce has a single platform which offers complete ecommerce solutions to developers. It can be very productive if you are planning to do business with consumers, business and indirectly through channel partners. This can be used to perform business with consumers, business and channel partners altogether. 3. Explain about the architecture of web sphere? Web Sphere is built on three main components they are Database J2EE application server A web server The databases which it supports are DB2 Oracle Cloudscape Application server is IBMWAS and the supported web servers are IBM server Microsoft IIS Sun web server 4. State some of the features present in web sphere? Some of the features which are present in web sphere are: - Order management Web sphere commerce accelerator Analytical and business intelligence Open standards such as Java, EJB, etc Web sphere commerce payments and customer care, etc 5. Explain about IBM Web Sphere edge server? Web sphere edge server is used to improve the performance of web based systems. It can be used as forward or proxy server. Basically four components are present in the web sphere they are Network dispatcher, Caching proxy, Content distribution and application service at the edge. 6. Explain about extended deployment? Web sphere application server extended deployment increases the functionality of the server in two main areas they are manageability and performance. Dynamic virtualization between servers is possible with the help of XD. A stand alone distributed cache was added to it under the performance header, it is known as Object Grid. 7. Explain about the security features present in WAS? Security model for web sphere is primarily based on JAVA EE security model. It also depends upon the operating system. User authentication and authorization mechanisms are also provided in WAS. Light weight third party authentication mechanism is the main security feature present in WAS. 8. What is asymmetric clustering? Asymmetric clustering applications are primarily used in electronic trading systems employed in banks. Some of the features are, partitions can be declared during run time and are usually run on a single cluster at a time. Work specific to a particular can be routed to that cluster. 9. Explain the various Administrator benefits using Web sphere? Web sphere almost reduces the work of server administrator as he can manage load on servers efficiently without any hassles. It also gives him flexibility to divide the load and applications among different server farms. He can also predict about the incoming load on servers. Email alerts, restart options, memory leak detection, etc. 10. Explain about caching proxy of IBM Web sphere Edge sphere? A caching proxy can be configured in forward direction or as a proxy. Content requested by the user is cached by edge before sending or adhering to the query. Page fragments arising from JSP or servlets are cached by Edge and the caching process is slow. Performance and scalability of J2EE applications can be increased by edge.

IBM WEBSPHERE Interview Questions 11. Explain about the network deployment feature present in WAS? Managing singletons will be a thing of the past and it also provides hot recovery of singletons which makes you forget about your GC collected singletons. Transaction logs can stored on a shared file system. For clustering run time operations deployment manager`s role was eliminated. J2EE failover support and cell configuration support is also present. 12. Explain about IBM web sphere integration developer? Web sphere integration developer provides an IDE to build applications based on service oriented architecture. Web sphere process server and web sphere ESB were built with WID. WID was built with RAD Eclipse based technology. 13. Explain about compute Grid? Compute grid is also known as Web sphere batch. Web sphere extended deployment offers a Java batch processing system called as Compute Grid. This forms an additional feature to Web sphere network environment. Various features are provided which help a developer to create, manage and execute batch jobs. Job scheduler, xJCL, batch container and batch programming controller. 14. Explain about web sphere MQ Real time transport? This feature is very useful in instant messaging across different clients through intranet and internet. This supports high volume and high performance across different clients. It uses the concept of light weight transport which is again based on IP rather than the queue process. 15. Explain about Web sphere MQ JMS Provider? Web sphere MQ and Web Sphere Business integration manager Broker are very useful in providing Java messaging services to wide range of clients (publisher –subscribe, point to point). Java classes are chiefly responsible for translating the API calls to API`s defined by web sphere. It is very useful to have knowledge of Web sphere MQ for proper configuration. 16. Explain the attribute CHANNEL in web sphere MQ? CHANNEL specifies the name of the server connection channel. Generally this is Web Sphere MQ network abstraction. The default standard used by CHANNEL is SVRCONN which is the server connection channel. This server is generally used to communicate to the queue manager by the client. 17. Is the naming of connection factory independent of the name specified by JMS client? Yes, the naming of connection factory is independent of the name specified by JMS client. This is made possible by WAS (Web sphere application server) with its resource references. It isolates the application from object names. This feature is important because it gives us the flexibility to change the administered object without changing the JMS client code. 18. How do you specify a jar file to be used by the application, consider that you have many jar files in your system? classloader 19. What is a managed node? Node with NodeAgent 20. What is a managed webserver? Remote webserver access through local (dmgr/cell) 21. What about master repository? deployment manager contains the MASTER configuration and application files. All updates to the configuration files should go through the deployment manager. 22. Tell me IHS executable files, means bin directory files? Apache, ApacheMonitor, htpasswd, htdigest, htdbm, ldapstash, httpd.exe 23. Why given the httpd.conf file to installation of plug-in? identify the web server (port, virtual hosts) to configure the web server definition 24. How to configure remote system httpd.conf file? select web server machine (remote) 25. Several types of log files in the appserver? system out, system err, trace, native out , native err, activity. 26. websphere packages? express, base, network deployment 27. What is the profile? profiles are a set of files that represent a websphere application server configuration. 28. What is the trace? A trace is an informational record that is intended for service engineers or developers to use. As such, a trace record might be considerably more complex, verbose and detailed than a message entry. 29. What is heap memory? Objects storage space for objects references created at run time in a jvm is heap memory. 30. Out of memory exception is there, how to handle that exception? To incrise heap memory size 31. What about IHS? IHS (IBM HTTP Server) is one of the web servers. It serves the static content only and it takes up only http requests. 32. What about plug-in? plug-in is one of the modules it is interface between application server and web server, the plug-in process receives the request from the client first. If the request is for dynamic content, the plug-in diverts the request to the websphere application server. If the request is for static content, the plug-in forwards it to the Http server. 33. What is the global security? it provides the authentication and authorization for websphere application server domain (administration client or console). 34. How to configure the global security? open console and then select security option in the right side menu, and then select localOs registry in the user registry, then enter the username, passwords. And again select global security then ltpa option then provide the password, then save the configuration. And restart the deployment server and then relogin the console. 35. What is SSL? ssl is a protocol for providing encrypted data communications between two processes. 36. What is PMI? How to configure PMI? monitoring and tuning–>PMI–>select any process (server1, nodeagent, dmgr) and then enable PMI–>then apply and then save. Select performance viewer–>current activity and then select enabled process and click the start monitoring button after that process select. 37. What is the UNIX command of all display server processes? ps –ef| grep java 38. What is node? logical group of servers. 39. How to start the server? startserver.sh server1 40. How you get nodeagent……what you have to install to get nodeagent? Custom Profile 41. How to add the node? addnode.sh 8879 42. What is the application server? The application server provides a runtime environment in which to deploy, manage, and run j2ee applications. 43. What is the node? A node corresponds to a physical computer system with a distinct IP host address.The node name is usually the same as the host name for the computer. 44. What is a managed webserver? Remote webserver access through local (dmgr/cell) 45. How many types of profiles are in nd product? 1.deployment manager profiles 2.application server profiles 3.custom profile 46. What is diffrence b/w dmgr and other profiles? dmgr app custom 1.its used for administration 1.admin console is there 1.plain node purpose of remaining profiles 2.initially one app server there 2.empty node 2.it supports the distributed 3.work independently environment. 4. Put applications 3.it is not included app server 4.admin console is there 5.work independently 6.do not put applications 47. Diff b/w 5.0 and 6.0? Web Sphere Studio 3.5, comes up with Visual Age for Java. WSAD 5.0 supports J2EE 1.3 java specifications. RAD 6.0 supports J2EE 1.4 and integrated with Eclipse 3.0, UML Visual Editor, Tomcat Jakarta, Ant scripting, EJB universal test client and SOA tools. 48. What is the difference between web server and application server? Application Server: takes care of Security, Transaction, Multithreading, Resource pooling, load balancing, clustering, performance, highly availability, scalability, etc. Exposes business logic to client applications through various protocols, possibly including HTTP. Supports deployment of .war and .ear files Application server = web server + EJB container. 49. Diff b/w weblogic and websphere? Both BEA Weblogic and IBM’s WebSphere provide J2EE based application servers which are competitors. WebSphere leverages more on connectivity issues with MQ and legacy systems with strong dominance in J2EE. 50. Some problem is there in web server, so this information which log file contain? http.log, plugin.log 51. What is jdbc? jdbc is a low level pure java api used to execute sql statements. 52. What is datasource? A data source is associated with a jdbc provider that supplies the specific jdbc driver implementation class 53. What is diff b/w type4 and type2? type4 type2 1. It is pure java oriented 1.it is not a pure java oriented driver 2.require client side software 2.no need any client software 54. Some application not accessing, so what is the problem? This information which log file contains? systemout, systemerr 55. In type3 client software which machine you have install? server side machine 56. two databases there (oracle and db2),so I want 3 datasources for oracle and 2 data sources for db2 so create 3 datasource names for oracle and 2datasourcename for db2 is possible or not? possible 57. What is jndi? we can register resources in the application server’s java naming and directory interface (jndi) namespace. Client applications can then obtain the references to these resource objects in their programs. 58. Why use the boostrap port number? client applications use the bootstrap port to access websphere’s built-in object request broker (orb) to use enterprise java beans in applications installed on the application server. The java naming and directory interface service provider url used by the client application needs to reference the bootstrap port to obtain an initial context for looking up ejb’s it wants to use. (For communicate two servers) 59. What are the appserver components? admin server, web container, ejb container,j2c service, naming server, messaging engine, security server. 60. How to start the server? startserver.sh server1 61. Packages of websphere? express, base, network deployment 62. What is webcontainer? The web container provides a runtime environment for servlets, jsp’s, javabeans, and static content. 63. How to find out free diskspace from command prompt? du -sk (kb) du -sm (mb) 64. How to find out certain server configuration details like port no, server name, node name, pid? through admin console. 65. Configure the plug-in through admin console is possible or not? possible 66. Where to set the path? environments–>websphere variables 67. Application installed but not working. What are troubleshooting steps? see jvm & application are up, check plugin-cfg.xml file for the root context used by the web application if it does not exist generate plugin and restart web server. 68. Applications installed fine, also generated plugin, but application still not working, in this case which log to see? plugin.log 69. Default admin port? 9060, ssl 9043 70. Default bootstrap port? 2809 71. How to hit application without hitting the web server? webcontainer port on application server 72. In how many ways you can perform administration? console,,,JMX 73. No of ways of doing deployments? Admin console…..jython (jacl) scripts 74. What is CellDiscoveryAddress Node uses this port to talk to DMGR 75. What is NodeDiscoveryAddress DMGR uses this port to talk to node 76. How websphere discovers a change in JSP and compiles it? There is an algorithm that websphere uses to find the timestamp of .jsp and .class files. It checks that timestamp of .class file is always later than its corresponding .jsp file. 77. how do you specify a jar file to be used by the application, consider that you have many jar files in your system? classloader IBM WEBSPHERE Interview Questions with Answers Pdf Download Read the full article
0 notes
Text
300+ TOP SERVLET Interview Questions and Answers
SERVLET Interview Questions for freshers experienced :-
1. What is Servlet? A servlet is a Java technology-based Web component, managed by a container called servlet container or servlet engine, that generates dynamic content and interacts with web clients via a request & response paradigm. 2. Why is Servlet so popular? Because servlets are platform-independent Java classes that are compiled to platform-neutral byte code that can be loaded dynamically into and run by a Java technology-enabled Web server. 3. What is servlet container? The servlet container is a part of a Web server or application server that provides the network services over which requests and responses are sent, decodes MIME-based requests, and formats MIME-based responses. A servlet container also contains and manages servlets through their lifecycle. 4.When a client request is sent to the servlet container, how does the container choose which servlet to invoke? The servlet container determines which servlet to invoke based on the configuration of its servlets, and calls it with objects representing the request and response. 5.If a servlet is not properly initialized, what exception may be thrown? During initialization or service of a request, the servlet instance can throw an UnavailableException or a ServletException. 6.Given the request path below, which are context path, servlet path and path info? /bookstore/education/index.html context path: /bookstore servlet path: /education path info: /index.html 7.What is filter? Can filter be used as request or response? A filter is a reusable piece of code that can transform the content of HTTP requests,responses, and header information. Filters do not generally create a response or respond to a request as servlets do, rather they modify or adapt the requests for a resource, and modify or adapt responses from a resource. 8.When using servlets to build the HTML, you build a DOCTYPE line, why do you do that? I know all major browsers ignore it even though the HTML 3.2 and 4.0 specifications require it. But building a DOCTYPE line tells HTML validators which version of HTML you are using so they know which specification to check your document against. These validators are valuable debugging services, helping you catch HTML syntax errors. 9.What is new in ServletRequest interface ? (Servlet 2.4) The following methods have been added to ServletRequest 2.4 version: public int getRemotePort() public java.lang.String getLocalName() public java.lang.String getLocalAddr() public int getLocalPort() 10.Request parameter How to find whether a parameter exists in the request object? 1.boolean hasFoo = !(request.getParameter("foo") == null || request.getParameter("foo").equals("")); 2. boolean hasParameter = request.getParameterMap().contains(theParameter); (which works in Servlet 2.3+)

SERVLET Interview Questions 11. How can I send user authentication information while making URL Connection? You'll want to use HttpURLConnection.setRequestProperty and set all the appropriate headers to HTTP authorization. 12.Can we use the constructor, instead of init(), to initialize servlet? Yes , of course you can use the constructor instead of init(). There's nothing to stop you. But you shouldn't. The original reason for init() was that ancient versions of Java couldn't dynamically invoke constructors with arguments, so there was no way to give the constructur a ServletConfig. That no longer applies, but servlet containers still will only call your no-arg constructor. So you won't have access to a ServletConfig or ServletContext. 13.How can a servlet refresh automatically if some new data has entered the database? You can use a client-side Refresh or Server Push 14.The code in a finally clause will never fail to execute, right? Using System.exit(1); in try block will not allow finally code to execute. 15.What mechanisms are used by a Servlet Container to maintain session information? Cookies, URL rewriting, and HTTPS protocol information are used to maintain session information 16.Difference between GET and POST In GET your entire form submission can be encapsulated in one URL, like a hyperlink. query length is limited to 260 characters, not secure, faster, quick and easy. In POST Your name/value pairs inside the body of the HTTP request, which makes for a cleaner URL and imposes no size limitations on the form's output. It is used to send a chunk of data to the server to be processed, more versatile, most secure. 17.What is session? The session is an object used by a servlet to track a user's interaction with a Web application across multiple HTTP requests. 18.What is servlet mapping? The servlet mapping defines an association between a URL pattern and a servlet. The mapping is used to map requests to servlets. 19.What is servlet context ? The servlet context is an object that contains a servlet's view of the Web application within which the servlet is running. Using the context, a servlet can log events, obtain URL references to resources, and set and store attributes that other servlets in the context can use. (answer supplied by Sun's tutorial). 20.Which interface must be implemented by all servlets? Servlet interface. 21.Explain the life cycle of Servlet. Loaded(by the container for first request or on start up if config file suggests load-on-startup), initialized( using init()), service(service() or doGet() or doPost()..), destroy(destroy()) and unloaded. 22.When is the servlet instance created in the life cycle of servlet? What is the importance of configuring a servlet? An instance of servlet is created when the servlet is loaded for the first time in the container. Init() method is used to configure this servlet instance. This method is called only once in the life time of a servlet, hence it makes sense to write all those configuration details about a servlet which are required for the whole life of a servlet in this method. 23.Why don't we write a constructor in a servlet? Container writes a no argument constructor for our servlet. 24.When we don't write any constructor for the servlet, how does container create an instance of servlet? Container creates instance of servlet by calling Class.forName(className).newInstance(). 25.Once the destroy() method is called by the container, will the servlet be immediately destroyed? What happens to the tasks(threads) that the servlet might be executing at that time? Yes, but Before calling the destroy() method, the servlet container waits for the remaining threads that are executing the servlet’s service() method to finish. 26.What is the difference between callling a RequestDispatcher using ServletRequest and ServletContext? We can give relative URL when we use ServletRequest and not while using ServletContext. 27.Why is it that we can't give relative URL's when using ServletContext.getRequestDispatcher() when we can use the same while calling ServletRequest.getRequestDispatcher()? Since ServletRequest has the current request path to evaluae the relative path while ServletContext does not. 28. Whats the advantages using servlets over using CGI? CGI programs run outside the webserver. So a new process must be started to execute a CGI program. CGI programs are designed to handle a single request at a time. After that they return the result to the web server and exit. On the other hand servlets can handle multiple requests concurrently. They run within web servers. They generate dynamic content that is easier to write and faster to run. 29. What is Servlets and explain the advantages of Servlet life cycle? Servlets are the programs that run under web server environment. A copy of Servlet class can handle numerous request threads. In servlets, JVM stays running and handles each request using a light weight thread. Servlets life cycle involve three important methods, i.e. init, service and destroy. Init() Init method is called when Servlet first loaded in to the web server memory. Service() Once initialized, Servlets stays in memory to process requests. Servlets read the data provided in the request in the service() method. Destroy() When server unloads servlets, destroy() method is called to clean up resources the servlet is consuming. 30. What are different Authentication options available in Servlets. There are four ways of Authentication options available in servlets HTTP basic authentication In this, server uses the username and password provided by the client and these credentials are transmitted using simple base64 encoding. HTTP digest authentication This option is same the basic authentication except the password is encrypted and transmitted using SHA or MD5. HTTPS client authentication This options is based on HTTP over SSL. Form-based authentication Form-based authentication uses login page to collect username and password. 31. What is the GenericServlet class? GenericServlet makes writing servlets easier. To write a generic servlet, all you need to do is to override the abstract service method. 32. What is the difference between an Applet and a Servlet? Applets: Applets are applications designed to be transmitted over the network and executed by Java compatible web browsers. An Applet is a client side java program that runs within a Web browser on the client machine. An applet can use the user interface classes like AWT or Swing. Applet Life Cycle Methods: init(), stop(), paint(), start(), destroy() Servlets: Servlets are Java based analog to CGI programs, implemented by means of servlet container associated with an HTTP server. Servlet is a server side component which runs on the web server. The servlet does not have a user interface. Servlet Methods: doGet(), doPost() 33. List out the difference between ServletConfig and ServletContext? Both are interfaces in the package javax.servlet: ServletConfig is a servlet configuration object. It is used by a servlet container to pass information to a servlet during initialization. The ServletConfig parameters are specified for a particular servlet and are unknown to other servlets. The ServletContext object is contained within the ServletConfig object. It is provided by the web server to the servlet when the servlet is initialized. ServletContext is an interface which has a set of methods like getServletName(), getServletContext(), getInitParameter(), getInitParameterNames(). The servlet uses to interact with its servlet container. ServletContext is common to all servlets within the same web application. So, servlets use ServletContext to share context information. 35. What is the difference between using getSession(true) and getSession(false) methods? getSession(true) will check whether a session already exists for the user. If yes, it will return that session object else it will create a new session object and return it. getSession(false) will check existence of session. If session exists, then it returns the reference of that session object, if not, this methods will return null. 36. List out difference between a JavaBean from a Servlet? Servlets are Java based analog to CGI programs, implemented by means of a servlet container associated with an HTTP server. Servlets run on the server side. Beans are reusable code components written in Java that one can use in a variety of programming environments. JavaBeans are to Java what ActiveX controls are to Microsoft. Javabeans can run on server side, client side, within an applet etc. So, both have nothing in common except Java. 37. Define servlet mapping? Servlet mapping controls how you access a servlet. It is recommended that you don’t use absolute URLs. Instead usage of relative URLs should be done. If you try to deploy the application with a different context root, you might have to change all the urls used in all the JSP programs. Relative URLs is the solution so that you can deploy your application with different context root with out changing the URLs. 38. What is Servlets and explain the advantages of Servlet life cycle? Servlets are modules that run within the server and receive and respond to the requests made by the client. Servlets retrieve most of the parameters using the input stream and send their responses using an output stream. Servlets are used to extend the server side functionality of a website. They communicate with various application on the server side and respond to the request made by the client. 39. What is the difference between Difference between doGet() and doPost()? A doGet() method is limited with 2k of data to be sent, and doPost() method doesn't have this limitation. A request string for doGet() looks like the following: http://www.allapplabs.com/svt1?p1=v1&p2=v2&...&pN=vN doPost() method call doesn't need a long text tail after a servlet name in a request. All parameters are stored in a request itself, not in a request string, and it's impossible to guess the data transmitted to a servlet only looking at a request string. 40. What is the difference between ServletContext and ServletConfig? ServletContext: Defines a set of methods that a servlet uses to communicate with its servlet container, for example, to get the MIME type of a file, dispatch requests, or write to a log file.The ServletContext object is contained within the ServletConfig object, which the Web server provides the servlet when the servlet is initialized. ServletConfig: The object created after a servlet is instantiated and its default constructor is read. It is created to pass initialization information to the servlet. 41. What are all the protocols supported by HttpServlet? HttpServlet supports HTTP and HTTPS protocol. 42. Which exception is thrown if servlet is not initialized properly? Servlet Exception or Unavailable Exception is thrown if servlet is not initialized properly. 43. Who is responsible for writing a constructor? Container is responsible for writing constructor without arguments in servlet. 44. What are all the advantages of Servlet over CGI? Following are the advantages of Servlet over CGI: Cannot be run in an individual process. Servlet stays in the memory while requests. For every CGI request, you must load and start a CGI program. web.xml conveniences 45. What are the different mode that servlets can be used? Following are the modes that servlets can be used: Filter chains can be used to collect servlets together Support HTTP protocol Used for CGI based applications Dynamic generation of servlets 46. What are the uses of servlets? Servlets are used to process and store data submitted by HTML form, dynamic content, handle multiple request concurrently and manage state information on top of stateless HTTP. 47. Whether we can get deadlock situation in Servlets? Yes, it can be achieved by writing doGet method in doPost method and writing doPost method in doGet method. 48. What is the default HTTP method in the servlet? Default method is GET method for HTTPservlet. 49. Whether thread can be used in Servlets? Yes, Single thread can be used in servlets. 50. What exception should be thrown when servlet is not properly initialized? Servlet exception or an Unavailable exception is thrown when it is not properly initialized. 51. What is a filter? A filter is nothing but a piece of code which can be reusable that will be transforming the content of HTTP requests, response and header information. 52. What are the features added in Servlet 2.5? Following are the features added in Servlet 2.5: Dependency on J2SE 5.0 Support for annotations Loading the class Several web.xml Removed restrictions Edge case clarifications 53. When servlet is loaded? A servlet can be loaded when: First request is made Auto loading and Server starts up There is a single instance that answers all requests concurrently which saves memory Administrator manually loads. 54. When Servlet is unloaded? A servlet is unloaded when: Server shuts down Administrator manually unloads 55. What is life cycle of Servlet? Following is life cycle of Servlet: Loaded Initialized Destroy Unloaded SERVLET Questions and Answers Pdf Download Read the full article
0 notes