#htb analysis
Explore tagged Tumblr posts
Text
Premise: The scene in The Good Samaritan chapter 2 before Mark shoots the photo mirrors the church scene in chapter 6 of Mimicry.
(Idea from @markie-boo-in-your-area).
Reading these two scenes side by side, they are definitely related. The first thing I noticed was the safety being off. Of course it was off since he used the gun both times, but it feels significant in a way. In the church scene, it's a bit surprising to us, the readers, because we see that Mark is serious. He doesn't just suspect that m!Cesar is a mimic, he is almost completely sure. You don't do that to someone you think is your friend. In TGS, it is framed like a horror movie. Every action Mark takes, you're hoping he can survive. Him being able to get to the gun and take the safety off is slightly more hopeful. You understand that this is probably the way Mark felt back in the church. Speaking of feelings, these scenes mirror each other. "Mirror" as in the beginning and end are flipped. In Mimicry, Mark starts out terrified, and only when he is angry is he able to gain the courage to shoot the mimic. In TGS, Mark starts out furious but gets more scared the longer it goes on. This is just context for my next point.
I think this is trauma. Maybe a flashback of some kind, maybe not. While in a traumatizing situation, you do what you must to survive. Mark couldn't be afraid in the end because that would mean he would die. He had to be angry to survive. But the fear is still there under the surface. He starts angry in TGS because that's the emotion that will protect him, but when his mind unravels and tries to process what happened, he is terrified, as he rightfully should be. The mind tends to not let you feel your full feelings about a painful situation until it feels like it is out of that situation. I think that may have some part in it as well. Judging by the paragraph where the past three days' intensity hits him seems to support that. Here is a relevant paragraph to these few points in case you don't want to look for it on your own: "Nine shots left - he hadn’t changed the clip since that day in the woods when- when- oh God, oh fuck, what the fuck was happening?! The crisis tried to hit him all at once - the overwhelming realisation of just how insane the past three days really had been - but he pushed through it, refused to buckle, to fall beneath its weight. If he did, he would die." The quote is at about the point where the situation turns from scary to dangerous, and Mark is trying to do anything he can to survive. For extra context, the messed up parts of what happen in TGS chapter 2 are revealed to not be real and are a figment of Mark's mental state, though he believes it to be real at the time. The last point I can make about the two scenes' connection is when the bullet is fired. First off, here is a slight parallel: "Cesar though… his side was punctured by the bullet, punching a hole through his chest and tearing the paper up and across his face; warping the features, unable to put them back together in a way that looked right." This is relating to Cesar's death and the mimic that replaced him. Cesar will never be the same because he is dead. Any image of him is now wrong because he doesn't exist in that way anymore. Anything that is left is wrong and warped, just like the photo. Secondly, both times he shot the gun, they are done in self defense, with Mark afraid for his life. After the first time, he feels guilt and does not want to think about shooting the mimic, but in TGS, he does it again, or so he thinks. The reason why he would do that again other than for survival is because the first time it looked like Cesar, and the second time, it didn't. Mark doesn't care about it, not even a little bit, so he has no guilt when hurting it in any other form. Obviously Mark knew it wasn't Cesar after it disappeared and after it showed what it was, so why did he still feel guilty? I think it is very possible that Mark thought the mimic was mimicking what it heard when Cesar died. I'm pretty sure that was canon, at least that he considered it. The fact that it shouldn't be able to feel by itself would mean to Mark that it had to have heard that somewhere before. If Mark didn't shoot it, he wouldn't have had to hear Cesar's screams. Maybe he longs for the bliss of ignorance. Maybe he feels like it's partially his fault it happened to Cesar in the first place. For some more context, Mark and Cesar had an argument just the week before, and both refused to speak to each other. By what we know of Mark's character, we could assume that to him, shooting m!Cesar represented that he had somehow "killed" Cesar by not saving him. That is why it disturbs him so much.
#hail true body#htb#mimicry#hail true body mimicry#mimicry chapter 6#mimicry open your eyes mark#open your eyes mark#htb spoilers#spoilers#hail true body spoilers#hail true body tgs#tgs#the good samaritan#tgs chapter 2#tgs the aftermath#the aftermath#analysis#htb analysis#literature analysis
3 notes
·
View notes
Text
Sunday Round Up - 10th March 2019
amzn_assoc_ad_type = "banner"; amzn_assoc_marketplace = "amazon"; amzn_assoc_region = "US"; amzn_assoc_placement = "assoc_banner_placement_default"; amzn_assoc_campaigns = "amzn_vicc_cloudcam_1017"; amzn_assoc_banner_type = "category"; amzn_assoc_isresponsive = "true"; amzn_assoc_banner_id = "1J0CHGJT75D586M66602"; amzn_assoc_tracking_id = "kraljevicn1-20"; amzn_assoc_linkid = "c122cc4768b349b4aab7d3099b74ea1c";
Sunday Round up for this week!
Articles:
VStarCam - An Investigative Security Journey - Part 1
Facebook's Pivot to Privacy Is Missing Something Crucial
Hack the Box (HTB) Machines Walkthrough Series — Mirai
DeepSound – Audio Steganography Tool
How to Get and Set Up a Free Windows VM for Malware Analysis
If you found some other interesting stuff this week feel free to leave a link to it in the comments section. Otherwise feel free to check out the last roundup here.
These round ups are brought to you by PassVult.
#PassVult#VstarCam#investigative#security journey#Facebbok#pivot to privacy#something missing#Hack the Box#HTB#Machines walkthrough series#Mirai#Deepsound#Audio steganaography#Free Windows VM#Malware analysis
3 notes
·
View notes
Text
Impossible Password | HTB Reversing Challenge

In an attempt to improve skills in more obscure areas I’m going to be doing random challenges from different categories on HTB along with working on rooting machines there.
Today I completed the Impossible Password Challenge worth 30 points and I have to say I enjoyed it: it has been a long while since I had to use GDB or any sort of binary analysis tools and reverse engineering is one area of cyber security that intrigues me.
We are simply provided with a bin file to begin with. Using the objdump utility on this reveals that this is an ELF binary, in addition to providing us with the assembly language of the program.

Next is to find out more about what the binary does- while we will use GDB for a majority of this, it is acceptable to simply execute the binary first and observe it’s output. It simply requests user input and exits upon receival of a random string.
Now that we have a rough idea of what is going on visually it is probably a good idea to dive into the disassembly of the file- I personally used GDB as it was easier to narrow down what section to focus on but objdump is preferrable as output can be more easily saved to file.
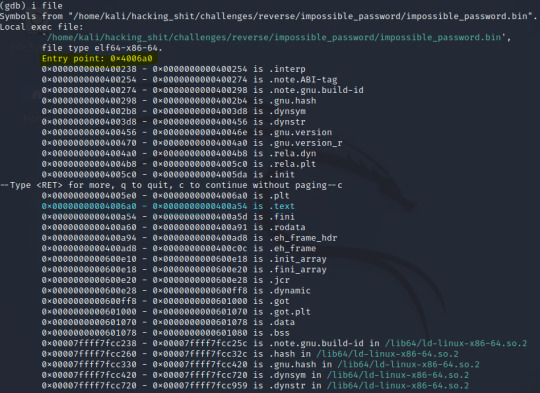
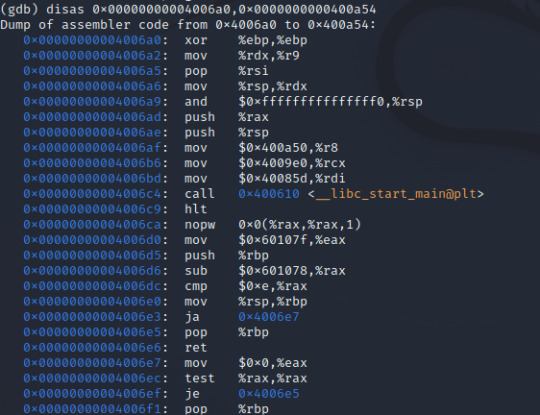
With access to the assembly of the main function, we can locate the relevant lines to see what is going on around the time our input is processed. A few things jumped out to me:
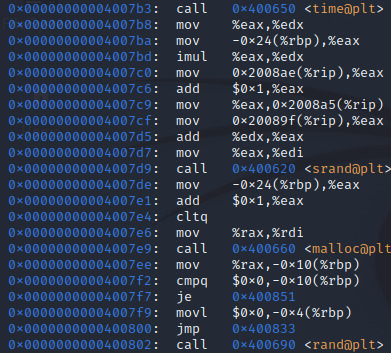
Here we can see use of the functions time, srand, malloc and rand. Essentially, the current system time is being used to generate a seed for the rand function via srand, memory is allocated for storage of a randomly generated number and rand is finally called.

This section is pretty self explanatory if you’re aware of what these functions do- a message is first printed to the screen before scanf is called to process user input upon the press of the enter key. More output is then provided by the program before strcmp is called to compare user input to a string in memory.
We see the use of cmpl and je here. The cmpl instruction subtracts the value found -0xc (-12 in decimal) away from the address currently in the rbp register from 0 and sets the equal flag in the flags register.
When reaching the je instruction, execution will be jumped to the instruction at 0x400925 if the equal flag has been set, otherwise a call to exit is executed and the program (obviously) exits.

The second request for user input follows a similar pattern, apart from the test and jne instructions after strcmp returns.
The test instruction sets zero flag ZF if both values are equal by performing a bitwise AND; if the two values are the same operand, this operation simply returns 0 when both values equal 0.
Jne is similar to je but of course the reverse- if the equal flag is not set, execution is moved to the instruction at address 0x400976.
Essentially this means that -in order to reach the end of the program without an early exit- we must ensure the value in the eax register is equal to 0 just before the test instruction executes.
With all of this in mind, I set a three breakpoints: one at 0x40090a to reveal the first password by checking the value in the rax register before strcmp is called, one at 0x40095e for the same reason (though we have to change this at runtime in GDB due to it being based on the results of the rand function) and one at 0x400966 to set eax to 0.
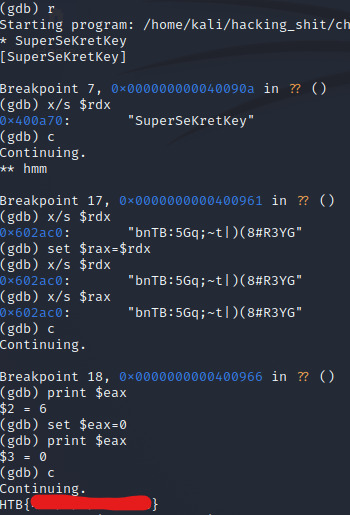
There we have it. Like I said, I did actually enjoy this challenge- it was a nice refresher on reverse engineering fundamentals and I do enjoy learning about assembly language, definitely going to have to look into learning it more in-depth and considering sticking to pwn and reversing challenges due to my interest in binary exploitation for a while!
1 note
·
View note
Text
News analysis: New Help to Buy scheme 'is more complex'
IMS Independent Mortgage Solutions chief executive Michelle Niziol says the change to HTB will affect new-build developers and homemovers. She ...
0 notes
Text
WriteUp for Something Awesome Project
Something Awesome proposal: https://superbobthebuilderfan.tumblr.com/post/185628975027/something-awesome-proposal-hackthebox
OBJECTIVES
Categories I plan to explore are Crypto, or Stego, or Pwn, or Web, or Misc, or Forensics, or Mobile. The aim was to complete one or more challenges in the categories I chose to explore. In achieving my aim I would have learned various hacking techniques, practical hacking skillsets, and developed my skills in hacking.
PLANNED
I chose to explore Crypto, Misc, Stego, and Pwn (Pwn is extension work)
Get invite code for hackthebox.eu, explore hackthebox’s environment and restrictions as a non-VIP member, research about ciphers and encryption types + Setup/explore programs/tools and the environment for digital forensics and penetration testing and CTF’s (Kali Linux) + Complete one or more challenges in the above-stated categories.
ACTUAL
I was able to get the invite code, I explored hackthebox’s environment and restrictions as a guest member, studied many various ciphers and encryption types, successfully dual-booted Windows and Kali Linux, explored preinstalled programs/tools and the environment. Furthermore, I managed to complete one or more challenges in all chosen categories except Pwn. Pwn will be completed in Week 9 as declared in my Something Awesome proposal blog (link is at the very top).
WHAT I LEARNT
Invite code, environment, ciphers, encryptions, crypto
Week 2-3
https://superbobthebuilderfan.tumblr.com/search/week3%20somethingawesome
Refer to the above link to see the completed challenges and goals for week 2-3.
In week 2, I obtained the invite code and didn’t blog about it until week3. It was easy because I have done something similar to this before such as hacking the game Cookie Clicker and Clicker Heros.
I learnt:
how to make POST request via terminal by typing curl -XPOST [INSERT URL].
about hackthebox’s environment such as where the discussion forums are, settings page, my profile page, how to check my progress, where the challenges are, where the pen-testing labs are, where the pen-testing machines are
many new ciphers and encryptions, the most unique one I discovered was Fernet (symmetric encryption)
Kali Linux, penetration and digital forensics tools, CTFs tools
Week 4
https://superbobthebuilderfan.tumblr.com/search/week4%20somethingawesome
Refer to the above link to see completed goals for week 4.
I learnt:
how to dual boot 2 OS’s on one laptop
commands such as netdiscover, nmap, gobuster
tools such as Burpe Suite, BruteSpray, Hashcat, John the Ripper and many more for password attacks
tools for sniffing and spoofing such as Wireshark, bettercap, Wifi Honey
tools for hardware hacking such as android-sdk, apktool, Arduino
tools for information gathering such as arp-scan, Xplico, InTrace, iSMTP
tools for vulnerability analysis such as Oscanner, Powerfuzzer, sfuzz
tools for wireless attacks such as Airbase-ng, Aircrack-ng, Fern Wifi Cracker
tools for web applications such as DirBuster, fimap, FunkLoad
forensic tools such as Binwalk, bulk-extractor, Capstone
stress testing tools such as DHCPig, FunkLoad, iaxflood
reverse engineering tools such as apktool, dex2jar, diStorm3, edb-debugger
reporting tools such as CaseFile, cherrytree, CutyCapt
hardware hacking tools such as android-sdk, apktool, Arduino
I learnt about the existence of those tools and their purposes and their usage and tested them out, but not all of them.
Misc
Week 5-6
https://superbobthebuilderfan.tumblr.com/search/week5%20somethingawesome
Refer to the above link to see completed challenges for week 5-6.
I learnt:
To pay attention to details because I have attempted one that is similar. It was under the same programming language category “Esteroic programming language” in week 3. The previous was Brainfuck, this one is Piet and malbolge. The whole list of Esteroic programming languages https://en.wikipedia.org/wiki/Esoteric_programming_language
Steganography
How to extract zip folders in terminal: extract [INSERT ZIP FOLDER NAME]
How to solve steganography using steghide extract -sf [INSERT FILE NAME], which is a command-line tool
Base64 encryption can be done twice
Renaming files to the correct format is good practice
How to base64 decode once and twice in terminal: base64 --decode [INSERT FILE NAME] | base64 --decode
How to check file properties in terminal: file [INSERT FILE NAME]
ls -R and fcrackzip -v -u -D -p [inputfilepath] [path to the file/folder wanted to crack] command
How to fix "E : Unable to Locate Package" Error In Kali Linux
Application of pdfcrack tool
Stego
Week 7-8
Part 1 (week7): https://superbobthebuilderfan.tumblr.com/post/186443678597/htb-stego-da-vinci
Part 2 (week8): https://superbobthebuilderfan.tumblr.com/post/186443681237/htb-stego-davinci
Refer to the above link to see completed challenges for week 7-8.
I learnt:
strings and binwalk command, the rest of the knowledge required had already been acquired from previous challenges such as steghide and base64
OVERVIEW OF MY EXPERIENCES FOR THE PROJECT
As a first-timer in the field of CTFs and I am surprised I could solve more than one challenge in each chosen category. I feel like I have achieved my objectives for the Something Awesome project as I have learnt hacking techniques and skills, both technical, and theoretical, and problem-solving skills. The skillset I have learnt would potentially be useful for completing future CTFs and as a security major computer science student. I did my best to be on schedule and if not, I would extend myself by doing another challenge whenever I am ahead of schedule. I am satisfied with the amount of effort I put in from the beginning (Week 2) of this project to now (Week 8).
0 notes
Text
Exhibiting a 5.9% CAGR Anticipated for Fire Extinguisher Market During 2017-2027
Future Market Insights delivers key insights on the global fire extinguisher market in its latest report titled ‘Fire Extinguisher Market: Global Industry Analysis 2012 – 2016 and Opportunity Assessment 2017 – 2027.’ The long-term outlook on the global fire extinguisher market remains positive, with market value expected to increase at a CAGR of 5.9% during the forecast period (2017 – 2027). Global sales of fire extinguishers are estimated to be valued at US$ 2,903.1 Mn by the end of 2017, witnessing a Y-o-Y growth of 5.3% over the year 2016.
Fire extinguisher is an active fire safety equipment employed for extinguishing different classes of fires in emergency situations. Stringent government norms for mandatory installation of fire extinguishers are anticipated to boost the demand for fire extinguishers over the forecast period. Moreover, increase in infrastructural developments in developed and developing economies would further increase the demand for fire extinguishers in the coming years. Many fire insurance companies compel their customers to install fire extinguishers for residential and commercial purposes. This is expected to drive revenue growth of the global fire extinguisher market over the forecast period.
Technological developments have led to the introduction of compact and light weight fire extinguishers in the market. This is anticipated to attract new customers and further promote the growth of the market during the forecast period. In the current scenario composite fire extinguishers consisting of inner three layered cylinders made up of amarid fibre is trending the Europe region. Furthermore, many fire extinguisher manufacturers are strategically focussing on expanding their business activities in developed and emerging economies of the world. This factor is anticipated to promote further augmentation of the global fire extinguisher market over the forecast period.
To view TOC of this report is available upon request @ https://www.futuremarketinsights.com/askus/rep-gb-572
Segmentation Analysis & Forecast
Among product types, the dry chemical segment is expected to expand at a significant CAGR of 5.7% in terms of volume over the forecast period. The carbon dioxide segment is expected to hold a major share in terms of value among the product type segments.
Among fire types, the Class A and Class B segments are anticipated to witness high CAGR in terms of value over the forecast period. The Class A segment is expected to witness robust growth in terms of value over the forecast period. The Class A type extinguisher is expected to gain 230 BPS in market share in 2027 over 2017 owing to increased demand.
On the basis of end use, the commercial and industrial segments are anticipated to dominate the market in terms of value and volume over the forecast period. The commercial end use segment is anticipated to grow at a value CAGR of 6.3% over the forecast period.
Regional Analysis & Forecast
North America accounted for a prominent value share in the global fire extinguisher market in 2016 and this region is anticipated to retain its dominance throughout the forecast period. Growth of the North America fire extinguisher market is due to significant demand for fire extinguishers in upcoming infrastructural projects. North America and Western Europe are estimated to collectively account for about 48% value share of the global fire extinguisher market by the end of 2017.
Vendor Insights
The report highlights some of the top companies operating in the global fire extinguisher market such as Activar Inc., Amerex Corporation, Britannia Fire Ltd, Ceasefire Industries Pvt. Ltd, Desautel Sas, Feuerschutz Jockel Gmbh & Co. Kg, Fike Corporation, Flamestop Australia Pty. Ltd., Gunnebo Ab, Halma Plc, Hatsuta Seisakusho Co., Ltd., Hochiki Corporation, Jactone Products Limited, Johnson Controls International Plc, Naffco Fzco, Safex Fire Services Ltd., Siex 2001 S.L., United Technologies Corporation, Vítkovice Htb A.S., and Yamato Protec Corporation.
0 notes
Note
yo, I think that Cian and Daniel are foils. cuz like they influence Mark in different ways.
for Daniel; he took on a manipulative fatherly role and made things all the more worse for Mark.
Cian, on the other hand; took on a caring guardian role and steadily helped Mark from going to the deep end
To add onto that, I feel like Cian is also a foil to Andrew in a way, and that makes Daniel and Andrew kind of parallels, at least in Mark's mind. He thought if he did what they asked or pleased them, they would not cause bad things to happen, but it was completely out of his control. Even if he acted as well as he could, it depended on them whether or not they yelled at him or hurt someone. For Cian, it was the opposite. Even when Mark did act out, Cian kept the peace and tried to help him. It's a little similar to that one scene in Mimicry when m!Cesar was confused on how Mark would give and give for nothing in return when all it knew was selfishness. Mark was confused when Cian was kind to him because he thought that was something that just didn't happen to him. He knew people could be kind, but he didn't think they would be kind to him. If Cian and Daniel met, they would absolutely fight each other. What I think is interesting is that both of them care for Mark, and both of them know what it's like to be hurt by someone they trust (though for Daniel, it's after he met Mark). For Cian, he knows how badly it impacts you and how it can scar you for life, so he wants to essentially "save" Mark from that. Daniel, though we don't know the full story yet and this could be completely inaccurate, seems to have a different thought process. If the person he loved the most would hurt him, then hurting and controlling someone you love must be the correct thing to do or at least an acceptable thing to do. That thought process mostly would be towards Adam, if he thinks that way at all, because the event would've happened after he failed with Beth. The original way he was towards Mark when he cared about him was similar though, but it was more out of possessiveness and a lack of understanding what caring even is. I think the foils will become a lot more clear when we see how Daniel interacts with Adam when he cares about him.
#analysis#hail true body#htb#htb cian daniels#htb daniel#htb nobody#In writing these tags I'm realizing they both have a “Daniel” in their names which is probably significant but I don't know in what way.#htb spoilers#spoilers#hail true body spoilers#htb analysis#literature analysis#htb mark owens
1 note
·
View note
Text
Sunday Round Up - 28th of July 2019
amzn_assoc_ad_type = "banner"; amzn_assoc_marketplace = "amazon"; amzn_assoc_region = "US"; amzn_assoc_placement = "assoc_banner_placement_default"; amzn_assoc_campaigns = "amzn_vicc_cloudcam_1017"; amzn_assoc_banner_type = "category"; amzn_assoc_isresponsive = "true"; amzn_assoc_banner_id = "1J0CHGJT75D586M66602"; amzn_assoc_tracking_id = "kraljevicn1-20"; amzn_assoc_linkid = "c122cc4768b349b4aab7d3099b74ea1c";
Sunday Round up for this week!
Articles:
Im publishing an infosec book
Analysis of Google Keep WebAssembly module - WebAssembly Security
GitHub - everdox/InfinityHook: Hook system calls, context switches, page faults and more
Developing An Automatic Tool For CAN Bus Hacking
Hack the Box (HTB) machines walkthrough series — Blocky
If you found some other interesting stuff this week feel free to leave a link to it in the comments section. Otherwise feel free to check out the last roundup here.
These round ups are brought to you by PassVult.
#PassVult#publishing a book#infosec book#Analysis of google keep#web assembly#Security#GitHub#everdox#Infinity hooks#Automated tool#CAN Bus Hacking#Hack the box#Blocky#Machines walkthrough series
1 note
·
View note
Text
A logistic regression model predicting high axillary tumour burden in early breast cancer patients
Abstract
Purpose
As elective axillary dissection is loosing ground for early breast cancer (BC) patients both in terms of prognostic and therapeutic power, there is a growing interest in predicting patients with (nodal) high tumour burden (HTB), especially after a positive sentinel node biopsy (SNB) because they would really benefit from further axillary intervention either by complete lymph-node dissection or axillary radiation therapy.
Methods/patients
Based on an analysis of 1254 BC patients in whom complete axillary clearance was performed, we devised a logistic regression (LR) model to predict those with HTB, as defined by the presence of three or more involved nodes with macrometastasis. This was accomplished through prior selection of every variable associated with HTB at univariate analysis.
Results
Only those variables shown as significant at the multivariate analysis were finally considered, namely tumour size, lymphovascular invasion and histological grade. A probability table was then built to calculate the chances of HTB from a cross-correlation of those three variables. As a suggestion, if we were to follow the rationale previously used in the micrometastasis trials, a threshold of about 10% risk of HTB could be considered under which no further axillary treatment is warranted.
Conclusions
Our LR model with its probability table can be used to define a subgroup of early BC patients suitable for axillary conservative procedures, either sparing completion lymph-node dissection or even SNB altogether.
http://ift.tt/2vTyFrk
0 notes
Text
This is @libetsdelay-707 here. This is my side blog where I analyze anything related to Hail, True Body ranging from analysis of the text, to character analyses, to talking about how a song perfectly relates to a character or scene. I'm theming the blog around Eve Cooper because I like her and because I feel like it relates to finding out the truth. I take requests for anything people want me to analyze, so if you have a specific song you feel like fits a character, or if you feel like there's a lot of symbolism in a certain scene but aren't sure of the meaning, you can send an ask, and I'll analyze that topic as best as I can. Even if I've already analyzed something, maybe you have a different lens you'd like to look at it through like ethos, pathos, and logos, or how the headcanon of a character having PTSD would change a particular scene. Don't worry if an ask for an analysis seems too complicated/too hard to get info for: those are my favorite topics. For the tagging system, I'll use the already established tags, but I'll also use my own made up tags. They will mostly be things like #hail-true-body-mimicry or #mimicry-chapter-1 to be as clear as possible.
6 notes
·
View notes
Text
A logistic regression model predicting high axillary tumour burden in early breast cancer patients
Abstract
Purpose
As elective axillary dissection is loosing ground for early breast cancer (BC) patients both in terms of prognostic and therapeutic power, there is a growing interest in predicting patients with (nodal) high tumour burden (HTB), especially after a positive sentinel node biopsy (SNB) because they would really benefit from further axillary intervention either by complete lymph-node dissection or axillary radiation therapy.
Methods/patients
Based on an analysis of 1254 BC patients in whom complete axillary clearance was performed, we devised a logistic regression (LR) model to predict those with HTB, as defined by the presence of three or more involved nodes with macrometastasis. This was accomplished through prior selection of every variable associated with HTB at univariate analysis.
Results
Only those variables shown as significant at the multivariate analysis were finally considered, namely tumour size, lymphovascular invasion and histological grade. A probability table was then built to calculate the chances of HTB from a cross-correlation of those three variables. As a suggestion, if we were to follow the rationale previously used in the micrometastasis trials, a threshold of about 10% risk of HTB could be considered under which no further axillary treatment is warranted.
Conclusions
Our LR model with its probability table can be used to define a subgroup of early BC patients suitable for axillary conservative procedures, either sparing completion lymph-node dissection or even SNB altogether.
http://ift.tt/2vTyFrk
0 notes
Text
A logistic regression model predicting high axillary tumour burden in early breast cancer patients
Abstract
Purpose
As elective axillary dissection is loosing ground for early breast cancer (BC) patients both in terms of prognostic and therapeutic power, there is a growing interest in predicting patients with (nodal) high tumour burden (HTB), especially after a positive sentinel node biopsy (SNB) because they would really benefit from further axillary intervention either by complete lymph-node dissection or axillary radiation therapy.
Methods/patients
Based on an analysis of 1254 BC patients in whom complete axillary clearance was performed, we devised a logistic regression (LR) model to predict those with HTB, as defined by the presence of three or more involved nodes with macrometastasis. This was accomplished through prior selection of every variable associated with HTB at univariate analysis.
Results
Only those variables shown as significant at the multivariate analysis were finally considered, namely tumour size, lymphovascular invasion and histological grade. A probability table was then built to calculate the chances of HTB from a cross-correlation of those three variables. As a suggestion, if we were to follow the rationale previously used in the micrometastasis trials, a threshold of about 10% risk of HTB could be considered under which no further axillary treatment is warranted.
Conclusions
Our LR model with its probability table can be used to define a subgroup of early BC patients suitable for axillary conservative procedures, either sparing completion lymph-node dissection or even SNB altogether.
http://ift.tt/2vTyFrk
0 notes