#iris capture device
Explore tagged Tumblr posts
Text
#retina scanner biometric device#biometric iris scanner#mantra iris scanner#dual iris scanner#iris capture device#iris authentication scanner#mantra dual iris scanner#matisx dual iris scanner#biometric eye scanner#mantra matisx dual iris scanner#iris scanner device#iris recognition device#dual iris recognition system
0 notes
Text
6/? Luo Binghe is SO NORMAL about Shen Yuan
1, 2, 3, 4, 5, 6 (here), 7
Read up through even numbered parts on Ao3 (chapter 3 will go up on Sunday, I just wanted to share early bc I love u)
The problem with the blooming of the Speckled Iris was that it was the exclusive food source of the Whisper Wraith Ermine: a semi-undead weasel that was two meters long and 200 kilograms in weight. It spent a majority of its life in spectral form and acted like if a giant ferret was also a ghost.
The thing's existence made no sense and wasn't in IRS, but Luo Binghe couldn't say it didn't fit the world's lack of logic and ecological sense. He hadn't been reading for the world building, after all.
Liu Qingge patrolled the valley housing the iris by sword while Luo Binghe passed Shen Yuan various painting implements, talismans and capture devices. The sight of Shen Yuan in the depths of his joy was rapturous. Luo Binghe had commissioned many, many painting of his beloved over the years, but they all paled in comparison to the manic spark of delight when one of the bees landed on his notebook.
But Luo Binghe couldn't afford to get too distracted staring at Shen Yuan. His side quest was still active and neither the iris nor the bees could create a scenario that required dual cultivation to fix. Snowballing had promised a paid extra of Shen Yuan's first time, but then never delivered, Liu Qingge seeming to have fallen out of his personal favor despite the fan attention.
Luo Binghe would have read it and would have been furious, as he always was with the sex scenes, but he still wanted it. Not now that he had the opportunity to learn first-hand which touches made his beloved whimper and which had him arching his back with tears in his eyes.
Lost in his daydreams, Luo Binghe missed the approach of the Whisper Wraith Ermine. The ghostly weasel was sniffing its way toward the iris, body arched to spring at Shen Yuan.
Shen Yuan who was stupidly clicking his tongue like the giant thing was a stray cat. Shen Yuan crept toward the beast with fat, dripping leaves offered on his flat palm.
Time slowed.
The weasel flickered to be fully corporeal. It snatched up the leaves with a chameleon-like tongue, snapping its jaws closed on its prize. Then it reared up on its hind legs.
Luo Binghe used spiritual energy to close the distance between him and Shen Yuan. He grabbed his master and spun, giving the beast his back and shoving Shen Yuan to safety.
"No, you ridiculous boy!" Shen Yuan yelled, but it was too late. What was done was done.
Luo Binghe looked down and saw the weasel's ethereal snout emerging from his chest. "Oh…" The sound fell brittle from his mouth before shattering. He felt frozen from shoulders to knees. He… He didn't actually know what the Whisper Wraith Ermine did to its victims. The creature yanked its head out of his chest and Luo Binghe's knees locked. He sagged forward.
"Stupid boy," Shen Yuan said as he rushed forward, taking Luo Binghe by the shoulders.
[Quest Complete! Please enjoy the following cut scenes.]
Luo Binghe slumped forward into Shen Yuan's shoulder, but he couldn't appreciate it. The System was busy loading and Shen Yuan was yelling for Liu Qingge.
--
The world was hazy, like winter clouds settling on high mountain streets. Luo Binghe exhaled and watched his breath fog in the air. The mist cleared somewhat, revealing a motley collection of demons. They were spattered with blood, now frozen. They clearly weren't love interests. Not because of their animal heads and tails, but because their robes were plain and serviceable.
Only demon nobility were allowed to so much as breathe the air around Shen Yuan.
"You're lucky you have this Venerable One looking after you, kid," Meng Mo said. He appeared with his words, taking the form of a tall, grey bearded elder.
"Looking after is certainly a way to phrase it."
"No respect! If this Venerable Meng Mo was not the best Dream Manipulator that ermine would have sent you into a deadly qi deviation."
And a deadly qi deviation would require dual cultivation to avoid. Luo Binghe shrugged Meng Mo's self-aggrandizing off. He was the only guiding Luo Baixiao's leash; Luo Binghe didn't have to be grateful.
"What's this, then, Ancient One?"
Meng Mo narrowed his eyes at Luo Binghe, but chose to let the remark slide. He waved a grandiose sleeve at the demons. "Given that they're holding that infant by the ankle, this Venerable One would say this is an image of your past."
"And interesting ability this beast has."
"Indeed. But this Venerable One has better things to do than babysit you. You're alive; stay that way." In a swirl of robes and smoke the demon disappeared, leaving Luo Binghe to watch the demons alone.
"Should we eat it?" the shortest demon asked, craning his neck to examine the infant's bare and quickly freezing stomach.
The one holding the baby shook him. "Don't think it's worth it."
"Well you've already killed it," said the third. "Human brats are fragile."
In the midst of another shake there was a flash of demonic energy and the infant Luo Baixiao had latched his gums onto the short demon's ear. There was a terrible wrench of sound as the infant tore the point off entirely.
All three demons stood stock-still, even the one bleeding profusely. The baby suckled the ear tip until it was empty of blood and then spat it out.
"Huh."
The middle demon sniffed the baby. "Still smells human."
"Shut up Lost Wine, you couldn't smell a Sha poison if your momma was dead in front of you."
"Excuse you-"
"Enough," interrupted the tallest demon. "Linguang-jun will want this thing. And if he doesn't, then we can eat it."
"I thought you said it wasn't worth it."
"Look at its wrap, you idiot!" He gestured to the fallen fabric with the infant. "That's cultivator get! Won't be as good as eating a core, but it'll be somethin.'"
"It better be," Lost Wine grumbled. He scooped up the fabric and the three demons disappeared into the mist.
Interesting. Luo Baixiao's backstory was never explored in IRS. Every time a chapter hinted there would be a reveal, it would switch to Shen Yuan's POV and he'd purposefully bury his head in the sand out of abject terror.
An orphan taken in by Linguang-jun explained his servitude, but things weren't adding up. Cultivators had ways of getting rid of pregnancies they didn't want, so what kind of moron carries a babe to term, delivers it and then what? Just abandons it? It was the kind of plot hole Snowballing would leave, but it was possible the System was just desperately trying to fill in backstory.
…Though with how smug it had been about knowing Luo Baixiao's backstory when Luo Binghe didn't, he wasn't so sure.
20 notes
·
View notes
Text
Looking through the recent IRIS posts
Guess what time it is, my fellow theorists! That's right! It's theory crafting time! (Or brain rotting because I have no social life)
But as we all know IRIS on Twitter have been pretty active for the last few days. Posting on 10/24/2024 - 10/25/2024 and 10/26/2024



Yes it's all in order... I hope. (Nothing on the 27th, my birthday, I see how it is IRIS -squint-). And I know I haven't covered the 25th and 26th posts, I was getting ready for my birthday and then struck with a terrible migraine all day the 26th.
I'm better now, don't worry. But I had been looking at the posts when I could and figured to post some things together while I can remember them. I already covered the post on the 24th, I just have it here for convivence and in case I remember anything else for it.
The post for 10/25 is a little odd, more obviously the fact the word 'Strangely' is spelled as 'Strangeley'. Honestly not sure if its an intentional misspelling or an actual one that no one caught until too late, either way kinda gives the notice a bit of charm. Or the employee was typing too fast and misspelled it and couldn't be arsed to type onto another paper to correct it. I wouldn't blame him for that.
But it does speak about a deadzone in an area between a certain bathroom and cafeteria. Only battery powered devices seem to be affected within that zone as the lights and ventilation systems were still operational as normal. Hmm, interesting.
Where have seen a cafeteria in IRIS before? That's right the "commercial" for IRIS in 'this is my 5,000th video' shows a cafeteria like area where employees were enjoying their break.

Not the most glamorous cafeteria (IRIS seems pretty cheap on it. Though we know its because budget for AF:CB), but it is still a cafeteria. If that's the case, then the only deadzone I can think of is the red hallway that Chase was terrified of and dragged through against his will.

The bathroom could be that door next to one of the guards.
Or this one which is right outside Chase's cell.

Not sure, but it is just a guess. Literally its just a guess, as there is no evidence to back up the claim like anyone making mention of anything battery powered being sapped dry while in the area in the stream. But the employee in the post did make mention that it may be nothing dangerous and just annoyance from a certain department up to no good and just advising others to use a different bathroom on the east aside to avoid their devices being drained of power.
Why does that matter?
Well, it's an electrical interference that isn't causing damage to the facilities systems, just personal devices carried by employees, phones, watches, that sort of thing. So it never warranted further investigation I believe. And there's at least two instances in which that could cause that deadzone.
One of which is Anti's attack on Chase (where we see the shadows move towards Chase, indicating Anti reaching for him)

As Arin points out that Chase was exposed to dangerous levels of energy. (Though I wouldn't put it past IRIS to also have replicated the energy Anti uses to use on Chase to see his reaction to it. Fucking cruel if that's the case. Which then only prompted Anti to find out where he is and zero in on his location)
The second time this deadzone could happen was when Echo appears to speak to Chase.

Shit goes a little funky for the camera but the lights are fine.
It could be that the hallways between Chase's cell and the cafeteria is the deadzone. We don't know when that post the employee wrote was written, either during Chase's week long stay... or even before that. If it is indeed the same building and universe the employee speaks of. (Goddamn timey whimey shit)
But if it is at least prior to Chase's capture, could mean Echo's energy is causing it, as Echo reveals to Chase that they too have been stuck here. Just don't know if its before or after... will not be surprised if it was before to wait for Chase to appear to talk to him. Again, timey whimey shit.
Again, it's all theory, not the best kind but still fun to think on. I think there's more to this post but I... don't know what else to look for in it, aside hey, no IRIS stamp on it, so likely a private message from one employee to another to avoid that place altogether. And then what Department could the Employee be talking about?
Onwards to the post from 10/26, where obviously things for an experiment have not gone as planned. Nope, someone died in the vacuum room. There is another word, 'vacuum' is misspelled to be 'vaccum' (...I will refrain from making a joke here, it's too easy), and again, I don't know if its an intentional misspelling or someone didn't catch it when it was approved and posted online. (And if it was an accident, don't be ashamed or embarrassed, I misspell a lot of words too quite often. The fun of having your brain go faster than your fingers and autocorrect in your mind to not catch the misspelling too.)
Either case, an experiment was taking place in a vacuum room and someone died in the hands of an ALTR. Why an ALTR? Well, the clues were something in there was dangerous and the term 'designations' was used. Designations being something to identify different things quickly for a variety of reasons. Mostly to determine if one thing is dangerous or passive. Much like SCP uses designations to determine each SCP's threat level easily to prepare to encounter them more effectively.
Plus Designations are alternatives to names. Why? Because if you name something, you or the other forms an attachment to the name.
No attachment, no emotional scuff.
No emotional scuff, means easier times to conduct rather... unethical and cruel experiments without the hassle of morality.
It's SCIENCE after all, science has no time or room for morality. At least in IRIS's thought process I guess.
That thought is hammered in with the person (I'm guessing head researcher for that experiment) making a comment of having to remind everyone the reasons why they do what they do and to think of the great rewards at the end of the day!
As if the dead would have to worry about it. But it's interesting to think about what the experiment could be in a Sound Vacuum room. Is it really a vacuum of no sound entering or leaving the room? Or merely a name because they couldn't think of anything else that relates to sound and blast high decibel noises in the room but does not escape those walls.
Which obviously means they used sound to see if the ATLR is rendered helpless to it or unaffected by it. We don't know the results of that but it did cost them a researcher. And if it was to see if sounds could render an ALTR's powers useless, that failed if it was immune to such a thing, or made it useless because it doesn't need sound to burrow into your head and commit unalive.
If not that, probably understood the researcher was probably using safety gear and the ALTR removed it from the scientist to let them suffer... whatever is going on in chamber.
As for the line 'Please update [blank] to [blank] status' I can think of two things at least.
Either its "Please update [ALTR] to [Keter] status" (I think its Keter for most dangerous class of SCPs. I'm not familiar with SCP, I apologize if I got it wrong)
Or
"Please update [Mr. Daly] to [deceased] status"... I'm just using Mr.Daly since that is the only name we ever got from these posts and someone died so, might as well update their file to dead since well, they're dead.
I'm not quite sure which one, both fit in pretty well in context but I am kinda leaning towards the ALTR's status being updated to a higher tier of danger class.
Either way, the leader of this team is rather much an ass with how dismissive he was for the death of one of his own. But again, science waits for no one and mortality has no bearings in the fields of unknown discoveries.
------
I think that's about it for my current thoughts on these posts. There's probably a lot more to them that we're missing. But that's the fun of theory crafting, finding out all the little things you missed before when armed with new information.
What do you guys think? What could be hidden in these posts? And who is leaking them to the public. And if its being leaked, why on the official twitter and why hasn't IRIS removed them?
(...Be quick to screenshot and save the posts in case they do remove them in the future! We need files to look back to in the future!)
19 notes
·
View notes
Note
Hey if you're still taking AU headcanons what about an AU where Cisco gets his powers right away? Like while Barry's still in the coma maybe? Loving these posts!
Hehehe, I actually have an unfinished series exactly about this type of AU. Visions While I Sleep - it's a series I want to get back to sometime this year, so fingers crossed that I actually will.
So in Visions While I Sleep, Cisco starts to get vibes slowly - voices first then full on visions - and he winds up learning about how Hartley was actually fired and saves Hartley from a fatal accident. The two of them team up to figure out wth is up with Harrison Wells and his obsession with Barry Allen + prove criminal negligence with the accelerator (which could open him up to manslaughter charges I'd bet).
If I were to another take on a 'Cisco gains powers before Barry Wakes' fic, I'd probably have a different aspect of his powers surface first.
Cisco's vibe blasts kick in when Farooq shows up waaaay earlier than canon. Cisco vs Farooq doesn't go well at first, but round two Cisco manages to use his powers to set off the fire suppression system, causing Farooq's powers to kinda implode on him.
Cisco and EoWells and Caitlin come up with a way to suppress Farooq's powers and EoWells, in a sign of 'good faith' chooses not to press charges. Farooq still hates Harrison Wells, but he's convinced that Wells - and Cisco and Caitlin - are all trying to make up for what they've done.
Afterwards Cisco starts learning to use his powers in earnest. He gets excited about the idea of being a super hero and comes up with the Vibe suit V1. Caitlin and EoWells are... less enthused but still fascinated with helping him learn to use his powers.
It makes sense that there were metas causing problems before Barry woke up, so Cisco gets to encounter some of those. Not everyone who got powers was a criminal or resorted to crime because of their powers, so I'd want to see Cisco dealing with more of that. Helping people with powers get their abilities under control. Sometimes the antagonist is just someone having a bad day who doesn't want to cause trouble but can't seem to stop.
Of course sometimes the antagonist is a criminal and Cisco fights them, much to Caitlin's dismay. in order to make sure they can put away metas legally and safely, Cisco and EoWells expand what they created for Farooq into a universal suppressant device. EoWells isn't happy about this, no doubt. But in canon I think it was actually Joe who instigated the idea of the pipeline prison, so here without Joe involved I think Cisco's instinct would be to do things legally, whereas in canon he's got two authority figures saying illegal incarceration is fine so he just kinda goes with it. So while EoWells would like the chance to study metas more closely and advises that making metas more well known is a bad idea, Cisco points out that the cat is out of the bag here. Trying to shove it back in will only make things worse.
By the time Barry wakes up, Vibe is well established as a hero, so he's excited when it turns out Barry has powers and wants to use his abilities to help too. The Flash becomes Vibe's side kick. Barry still establishes himself by taking down Clyde Mardon, but thanks to Cisco Clyde is captured alive instead of shot. Though Joe still finds out about Barry & Cisco's powers and has Barry promise to hide things from Iris.
Because Cisco's got his powers, he doesn't make the Cold/Heat guns. So when Len shows up and gets interested in the city's new heroes, he designs the Cold Gun himself - like he does in the comics. He also makes the Heat Gun for Mick later on and the Gold Gun for Lisa (girl deserves her glitter ^_^ )
i think Hartley would pop up a lot sooner. Not only is Harrison Wells not paying for his sins, but Hartley's replacement is a super hero now? He'd thus be entirely Cisco's enemy at first instead of splitting time between Cisco and Barry. But I think Hartley would manage to plant doubt in Cisco about Wells too.
Cisco's visions would eventually show up too, maybe similar to how they did in canon? With his inter-dimensional and intra-dimensional breach abilities being held off on until S2.
#au headcanon game#thanks for asking ^_^#kitkatt0430 answers#the flash#fanfiction#fic ideas#cisco ramon
19 notes
·
View notes
Text
(RECAP) Ejen Ali Season 1 | Ali & His New Adventure
EJEN ALI tells the story about a young schoolboy named Ali, who was terrible in studies, a victim of bullying, and lack of parental love (his Mother Died By Being Deceased and his father is too busy to spend time with him), stumbles upon a prototype spy tech gadget called the I.R.I.S. (high tech goggles which calculates the optimum performance for the user when he decides a move) which was stolen by two evil spies. Since then, he has unwillingly been recruited as a secret agent in M.A.T.A. (an institute for secret agents) and he slowly discovers his true potential.
SUMMARY OF EJEN ALI SEASON 1 : In the first season of Ejen Ali, it all starts with a boy named Ali, who accidentally activated the I.R.I.S. and is recruited as an agent in M.A.T.A..



13 EPISODES FROM EJEN ALI - OFFICIAL YOUTUBE CHANNEL
youtube
EPISODES 1 - Synopsis : Ali's life changes forever when he accidentally wields secret technology stolen by two evil spies; while fleeing from thieves, Ali is saved by a secret intelligence agency.
youtube
EPISODES 2 - Synopsis : Ali gets sent out on his first mission using the IRIS device and Dr Tong's retirement raises suspicions.
youtube
EPISODES 3 - Synopsis : While trying to stop Komeng from stealing drones, Ali encounters a new ally who has a secret identity.
youtube
EPISODES 4 - Synopsis : After saving a stray cat from being run over by a car, Ali realizes that the cat reminds him of his old pet cat Labu, hence, he adopts it. What he does not know is that the cat has ulterior motives - to steal the I.R.I.S.!
youtube
EPISODES 5 - Synopsis : When Dos and Trez manage to steal two pieces of pen drive that contain the blueprint of I.R.I.S., the M.A.T.A. agents are on a mission to retrieve them before they can decrypt it!
youtube
EPISODES 6 - Synopsis : After Dr. Tong and Dr. Mala are being victimized by Dr. Aaron, Ali, Bakar, Alicia and Comot must protect Dr. Ghazali from him before it is too late!
youtube
EPISODES 7 - Synopsis : When a mission goes wrong, Alicia states that she would have summoned "Protocol Gegas" if it wasn't for the I.R.I.S. that Ali wears because M.A.T.A. promises to keep him alive. When there is a power disruption occurring in Cyberaya, the M.A.T.A. agents are sent to investigate the power plants. During the mission, Ali is horrified to learn about the purpose of "Protocol Gegas" from Bakar. When the protocol is really being used, will he follow it?
youtube
EPISODES 8 - Synopsis : After the previous mission goes wrong, General Rama discusses with Ali and the other M.A.T.A. agents about Ali's performance, and must decide whether to keep or eliminate Ali!
youtube
EPISODES 9 - Synopsis : Since the previous episode, Rizwan is now Ali's mentor and he must train him to be a better agent despite he has doubts on Ali.
youtube
EPISODES 10 - Synopsis : After the video of Ali saving Aunty Faye's life goes viral on Internet, Ali creates a new page for his agent self and has become obsessed of the popularity he gains. However, his new-found fame will bring grave danger to him.
...
EPISODES 11 - Synopsis : Unable to believe that Bakar is the traitor in M.A.T.A., Ali is determined to prove that he is innocent.
EPISODES 12 - Synopsis : Uno has hacked into M.A.T.A. headquarters and his only mission is to capture Ali!
EPISODES 13 - Synopsis : Uno and his team have captured Ali and they are going to extract the I.R.I.S. out of him! Ali is determined not to let it fall to the wrong hands, while the other M.A.T.A. agents try to protect Ali. Will they succeed?
WATCH EPISODE 11, 12, 13 @ 👇🏻👇🏻👇🏻
SOUNDTRACK OF EJEN ALI SEASON 1 @ 👇🏻👇🏻👇🏻
3 notes
·
View notes
Text
Biometric Attendance Machine

A biometric attendance machine is a technology used to track and manage employee attendance based on biometric data, such as fingerprints, facial recognition, or iris scans. These systems are often employed in workplaces, educational institutions, and other organizations to ensure accurate and secure tracking of time and attendance. Here’s a comprehensive overview of biometric attendance machines:
Types of Biometric Attendance Machines
Fingerprint Scanners
Description: Use fingerprint recognition to verify identity. Employees place their finger on a sensor, and the system matches the fingerprint against a stored template.
Pros: Quick and reliable; well-suited for high-traffic areas.
Cons: May be less effective with dirty or damaged fingers; requires regular cleaning.
Facial Recognition Systems
Description: Use facial recognition technology to identify individuals based on their facial features. Employees look into a camera, and the system matches their face against a database.
Pros: Contactless and convenient; can be integrated with other security measures.
Cons: May be affected by changes in lighting or facial features; requires good camera quality.
Iris Scanners
Description: Scan the unique patterns in the iris of the eye to identify individuals. Employees look into a device that captures the iris pattern.
Pros: Highly accurate; difficult to spoof.
Cons: Typically more expensive; requires careful alignment.
Voice Recognition Systems
Description: Use voice patterns for identification. Employees speak into a microphone, and the system analyzes their voice.
Pros: Contactless; can be used in various environments.
Cons: Can be affected by background noise or voice changes.
Hand Geometry Systems
Description: Measure the shape and size of the hand and fingers. Employees place their hand on a scanner, which records its dimensions.
Pros: Effective and reliable; less invasive.
Cons: Requires specific hand placement; less common than fingerprint or facial recognition systems.
Key Features
Data Storage and Management
Centralized Database: Stores biometric data and attendance records securely.
Integration: Often integrates with HR and payroll systems to streamline data management.
Accuracy and Speed
High Accuracy: Minimizes errors and false positives/negatives in identification.
Fast Processing: Ensures quick check-in and check-out times for employees.
Security
Data Encryption: Protects biometric data with encryption to prevent unauthorized access.
Anti-Spoofing: Includes features to detect and prevent fraudulent attempts, such as using fake fingerprints or photos.
User Interface
Ease of Use: Features a simple interface for both employees and administrators.
Reporting: Generates detailed reports on attendance, overtime, and absences.
Customization
Settings: Allows customization of attendance policies, work schedules, and shift timings.
Alerts and Notifications: Sends alerts for exceptions or anomalies, such as missed clock-ins or outs.
Benefits
Improved Accuracy: Reduces errors and fraud associated with manual or card-based systems.
Enhanced Security: Ensures that only authorized personnel can access facilities and clock in/out.
Time Efficiency: Speeds up the check-in and check-out process, reducing queues and wait times.
Automated Tracking: Automates attendance management, reducing administrative workload.
Detailed Reporting: Provides comprehensive data on attendance patterns, helping with workforce management and planning.
Considerations
Privacy Concerns: Ensure compliance with privacy laws and regulations regarding biometric data collection and storage.
Cost: Evaluate the initial investment and ongoing maintenance costs. High-end biometric systems may be more expensive.
Integration: Consider how well the system integrates with existing HR and payroll software.
User Acceptance: Provide training to employees and address any concerns about the use of biometric technology.
Popular Brands and Models
ZKTeco: Known for a wide range of biometric solutions, including fingerprint and facial recognition systems.
Hikvision: Offers advanced facial recognition systems with integrated attendance management.
Suprema: Provides high-quality fingerprint and facial recognition devices.
BioTime: Specializes in biometric attendance systems with robust reporting and integration features.
Anviz: Offers various biometric solutions, including fingerprint and facial recognition devices.
By choosing the right biometric attendance machine and properly implementing it, organizations can improve attendance tracking, enhance security, and streamline HR processes.
2 notes
·
View notes
Note
just an idea but awkwardly timed IMs lol, those fics always make me laugh and you are very good at capturing humor
*NOTE: I’m still closed to prompts for now, probably until at least the end of the year, as life is quite busy at the moment. But I’m trying to catch up on some backlogged requests that have been sitting there for a few months since before I closed. So, I’ll have a few up over the next couple of weeks—my goal is to have them all posted before Chalice of the Gods comes along and expands canon again, ha. Again, not accepting any new prompt requests at this time—I’ll see how my schedule looks in January and revisit the idea then 😊 In the meantime, enjoy the four or five coming up.
Oh, also, chapters 2 through 4 of my AHS senior year Percy and Annabeth story have also been posted. This story is written under my TraitorousHearts8 pseud, so it’s a little more YA than middle-grade, but it’s available to read on Fanfiction and AO3 if you’re interested! The last two chapters should be up over the next week or two.
Alright, back to the prompt response!*
Okay, I kind of loved this one and it was fun to do some semi-awkward IMs. Hope you enjoy!
PERCY: The Greek gods have terrible timing. For example, one once interrupted me in the shower. Long story. I’m not discussing it right now. Demigods do a little better. But sometimes, they have bad timing, too. For example, during my freshman year of high school, I was in the bathroom at my mom’s apartment, going…well, doing what you do in the bathroom, when, suddenly, the air in front of me shimmered. Charles Beckendorf’s face appeared a moment later. “Hey, Percy, got a question for—” he said before his eyes widened.
I yelped and swiped through the I-M.
Once I was out of the bathroom and standing near the kitchen sink, using its water to make a misty rainbow, I messaged him back.
“Uh, hey, dude,” Beckendorf said sheepishly. “My bad.”
“It’s okay,” I said, even though I still kind of wanted to curl up and die from embarrassment. “You didn’t know. But, uh, let’s not mention it again. Ever.”
He nodded gravely. “Anyway, the reason I was calling…” and he launched into a Titan War-related question about an explosive device he was working on that could be added to the tour bus of monsters we’d received reports on.
Later, I learned that he’d rigged this device in the bus’s toilet. I tried not to take that too personally. And I definitely did not ask him what had inspired the idea.
ANNABETH: Usually, I have way better luck than Percy. Which isn’t actually saying much because he has absolutely terrible luck. Which probably explains why this happened. It was during the fall of my freshman year of high school, during the Titan War. I was at my dad’s in San Francisco, and Percy and I hadn’t caught up for a few weeks. Things had been weird between us ever since our quest in the Labyrinth that summer. But we were trying. Unfortunately, Percy chose to reach out via Iris-message…while I was in the shower.
I was washing my hair when suddenly, from behind me, I heard, “Hey, Annabeth—aagh!” I turned, hands already up over my chest, to see Percy, bright strawberry red, covering his eyes and swiping through an I-M.
I called him back ten minutes later from my bedroom, fully dressed, though my hair was still wet and tangled.
As soon as his face appeared, Percy sputtered, “Annabeth, I am so sorry—”
I held up a hand. “We will never speak of this again.”
“Agreed.”
***
A couple years later, on the Argo II, Hazel was talking about I-Ms.
“They’re great,” she said. “But it seems a little risky. I mean, we surprised Reyna in the baths.”
The corner of Percy’s mouth quirked up. “Yeah, this one time, I called Annabeth and—”
“I thought we were never speaking of it?”
“Oh yeah. So, anyway, is that a flock of harpies closing in again? I’d better go check.”
After he ran off, Hazel raised her eyebrows at me. I sighed. “He called me once while I was in the shower.”
“Oh.” She fanned herself, an old-fashioned gesture that somehow seemed natural on her. “See? Risky.”
I nodded. “For sure. Oh crap, those actually are harpies. We’d better go help him.”
And that was the end of that conversation.
9 notes
·
View notes
Text
Random thought:
What if Henrik was an IRIS employee and actually is a bad guy that lures other egos into false hope to execute his further plan on caturing anamolies :]
Chase would feel safe enough to run to Henrik after escaping IRIS only to be secretly placed with a tracking device because Henrik can't bare to let go of his most valuable asset
For example also he'd befriend Marvin
Telling him about IRIS and what they do, trying to sell him the idea that he's just the good guy capturing anti
However, knowing Marvin practices magic or is magical he definitely makes sure Marvin is locked up by 'accident' for testing :3
#fruity shows no mercy sometimes#cursed thoughts with fruity#anomaly found chase brody#chase bro average#jse chase#chase brody#jse henrik#henrik von schneeplestein#henrik schneeplestein#jse project iris#jse iris project#jse iris#iris project#IRIS#jse marvin#marvin the magnificent#marvin the magician
12 notes
·
View notes
Text
Explore how biometric security, including fingerprint and iris recognition, revolutionizes digital banking with enhanced safety and convenience!
#biometrics#multi fingerprint scanner#10 fingerprint scanner#10 print fingerprint scanner#biometric iris scanner#biomatiques iris device#dual iris scanner#scanner#iris device#iris reader#4 4 2 fingerprint scanner#Slap fingerprint scanner#ten fingerprint scanner#fingerprint slap scanner resale 4 4 2#10 finger scanner#Multifinger Scanner#iris scanner biometric device#morphs slap fingerprint scanner#iris capture device#iris authentication scanner#matisx dual iris scanner#biometric eye scanner#optical fingerprint scanner
0 notes
Note
"Pull up the AO3 account, or Wattpad if you want to gamble," Lukas fires back with a smirk. The conversation feels... natural, like they're just two friends. Lukas is willing to put a lot of money on the two being anything but friends. It's a simple event, nothing more. Even from a distance, the IRIS building can be seen, rising above all of the others as if even the building itself thinks that it's better than the other building beneath it, similar to how the heads of IRIS think of themselves.
"Don't tempt me," Natemare replies with a grin. His relaxed demeanour falters as they approach the building, and suddenly, he grabs Lukas and tugs him behind a wall, pressing a finger to his own lips before pointing ahead.
Snarling and thrashing like a wild beast... is Anti. The demon seems to be contained within some kind of net, though it doesn't look like ordinary mesh. As if he's a vicious animal, the members of IRIS surround the net with guns trained on their capture. It's unclear whether they're tranquiliser guns or filled with bullets.
Anti glitches fiercely, but no matter how many times he tries to displace himself, the net holds. There's a sudden flash of vivid light, then the demon collapses, growing still as the lines of the net crackle with electricity.
"He can literally possess devices," Natemare breathes, his voice drenched with disbelief. "He could've jumped into a camera to hide, or a computer; there's no shortage of places he could've escaped to. How the hell did he get caught?"
0 notes
Text
Sam Altman’s Eye-Scanning Startup ‘World’ Expands to the UK to Tackle AI Fraud
World, the controversial biometric identity verification venture co-founded by OpenAI CEO Sam Altman, is launching in the United Kingdom this week as it continues its global rollout to combat rising concerns around AI-driven fraud.

Starting Thursday, Londoners will be able to register for World’s unique identity system using the Orb—a spherical, metallic eye-scanning device that captures a person’s iris and facial data to generate a unique biometric code. The startup plans to expand the service to other major UK cities, including Manchester, Birmingham, Cardiff, Belfast, and Glasgow in the coming months.
World’s technology aims to verify a user’s “humanness,” preventing bots and artificial intelligence systems from exploiting online services through deepfakes, identity theft, and other forms of fraud.
From Science Fiction to Mainstream Use
“The idea is no longer just something theoretical. It’s something that’s real and affecting people every single day,” said Adrian Ludwig, Chief Architect at Tools for Humanity, a key contributor to World. “We’re moving from a science project to a real network.”
Once a person is scanned, they receive a World ID—an anonymous digital identifier—and a small amount of WLD cryptocurrency. The ID can be used to log into participating platforms like Minecraft, Reddit, and Discord without revealing the user’s personal identity.
Growing Global Footprint
The UK expansion follows World’s recent launch in the United States, where it opened six flagship retail locations in cities including Austin, Atlanta, Los Angeles, Nashville, Miami, and San Francisco.
Ludwig said the company is aiming to scale its verification capacity tenfold over the coming months. As of now, 13 million users worldwide have verified their identity through World.
Privacy Concerns and Regulatory Dialogue
Since its 2021 debut as “Worldcoin,” the startup has faced scrutiny over privacy and biometric data usage. To address concerns, World says it encrypts all biometric data, deletes the original scans, and processes data locally on user devices rather than in the cloud. Only uniqueness verification is handled through third-party infrastructure.
Still, privacy campaigners remain wary of deploying such a system at scale, particularly in countries with millions—or even billions—of users. World has been actively engaging with regulators, including the UK’s Information Commissioner’s Office (ICO), to ensure compliance with data protection laws.
“We’ve had a lot of conversations with regulators,” Ludwig told CNBC. “They want to know: How do we make sure this works? How do we protect privacy? What are the risks? We’ve been able to answer all of those.”
A Digital Identity Shift
World’s expansion comes as governments worldwide explore digital identity solutions to move beyond physical ID cards. Ludwig sees the project as part of a broader shift toward more secure and scalable digital ID systems, especially in the face of increasingly sophisticated AI fraud.
While initiatives like India’s Aadhaar have demonstrated both the potential and pitfalls of digital ID at scale, World aims to offer a decentralized alternative—one that doesn't compromise privacy or security.
“Mechanisms to identify and reduce fraud are of growing interest to governments,” Ludwig said. “And we’re seeing real demand now.”
As digital identity becomes a central pillar of both public and private sector security infrastructure, World’s UK rollout marks a significant step in building a global network to defend against the rising risks of AI misuse.
#Sam Altman#Worldcoin#World ID#AI identity verification#biometric authentication#UK tech news#iris scanning#Orb device#AI fraud prevention#OpenAI CEO
0 notes
Text
Understanding AEPS API: Revolutionizing Financial Inclusion in India
India’s digital transformation journey has taken a significant leap with the introduction of AEPS (Aadhaar Enabled Payment System). AEPS enables banking transactions using Aadhaar authentication, offering secure, convenient, and inclusive access to financial services, especially for the unbanked and underbanked population. At the core of this innovation is the AEPS API — an application programming interface that allows businesses and developers to integrate AEPS functionalities into their platforms.
This article delves into what AEPS API is, how it works, its benefits, key use cases, and considerations for implementation.
What is AEPS?
AEPS (Aadhaar Enabled Payment System) is a payment service that allows people to carry out banking transactions using their Aadhaar number and biometric authentication. It is managed by the National Payments Corporation of India (NPCI) and facilitates transactions through micro-ATMs or Point-of-Sale (PoS) devices.
Key services supported:
Balance inquiry
Cash withdrawal
Cash deposit
Aadhaar to Aadhaar fund transfers
Mini statement
What is AEPS API?
An AEPS API is a software interface that allows fintech applications, banking correspondents, and service providers to integrate AEPS services into their apps, portals, or devices. It acts as a bridge between front-end systems (like mobile apps or biometric devices) and back-end services provided by banks and NPCI.
Key Components of AEPS API Integration:
Aadhaar Number: Unique identity of the user.
Bank IIN (Issuer Identification Number): Identifies the bank.
Biometric Data: Fingerprint or iris scan captured via a certified biometric device.
API Gateway: Connects with NPCI, banks, and the UIDAI (for Aadhaar verification).
Transaction Type: Specifies the type (withdrawal, deposit, inquiry, etc.).
How AEPS API Works
Here’s a step-by-step outline of how a typical AEPS transaction via API works:
Customer Authentication: The user provides their Aadhaar number and selects the transaction type.
Biometric Verification: Biometric data is captured using a device and sent securely via the API.
Request Routing: The AEPS API routes the request to the corresponding bank through the NPCI network.
Validation: The bank validates the Aadhaar number and biometric data through UIDAI.
Transaction Execution: Upon successful validation, the transaction is completed, and a response is sent back to the user interface.
Benefits of AEPS API
Financial Inclusion: Empowers people in rural and remote areas with access to banking services.
Security: Uses biometric data, reducing the risk of fraud.
Ease of Integration: APIs allow fintechs and agents to quickly implement AEPS functionality.
Cost-Effective: Minimizes the need for physical bank branches.
Interoperability: Supports multiple banks through a single API endpoint.
Use Cases
Banking Correspondents: Provide banking services in rural areas using AEPS-integrated devices.
Fintech Apps: Offer cash withdrawal and balance inquiry features within mobile wallets or apps.
Retailers & CSPs (Customer Service Points): Serve as mini banking hubs using AEPS APIs.
Government Subsidy Distribution: Direct Benefit Transfer (DBT) can be accessed using Aadhaar authentication.
Implementation Considerations
Regulatory Compliance: Entities must be authorized by NPCI and comply with UIDAI guidelines.
Data Security: Sensitive biometric and financial data must be encrypted and stored securely.
Device Certification: Only UIDAI-certified biometric devices should be used.
Vendor Partnerships: Often, companies integrate AEPS services through aggregator APIs from approved partners.
Conclusion
The AEPS API is a powerful tool for bridging the financial gap in India’s vast demographic landscape. It empowers developers and businesses to deliver essential banking services directly to people’s doorsteps, leveraging Aadhaar and biometrics. As India continues to embrace digital payments, AEPS APIs play a pivotal role in building a cashless and inclusive economy.
FAQs
Q: Do I need RBI or NPCI approval to use AEPS APIs? A: Yes, only approved and compliant entities can integrate AEPS services.
Q: Can AEPS work without an internet connection? A: AEPS requires an active internet connection for real-time transaction processing.
Q: Is it possible to integrate AEPS with a mobile app? A: Yes, with the proper API integration and biometric device support, AEPS can be embedded in mobile apps.
0 notes
Text
Key Features to Look for in a Reliable Attendance Management System
In today’s dynamic business environment, efficiency, accuracy, and flexibility are vital to successful workforce management. One critical device and software that contributes to this efficiency is a robust attendance management system. This technology does much more than just record when employees clock in and out - it lays the foundation for streamlined operations, accurate payroll processing, and improved compliance with labor laws.
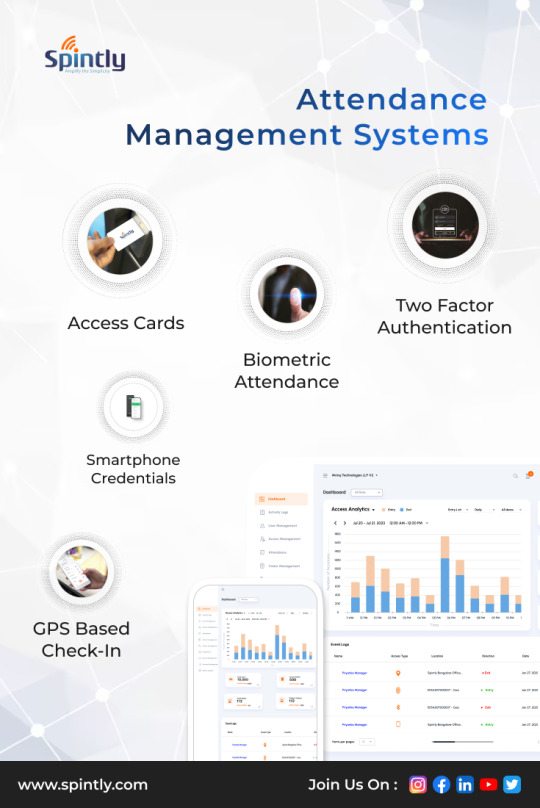
As more companies adopt digital solutions to enhance productivity, selecting the right attendance management system has become a top priority. However, with the abundance of options available in the market, knowing which features truly matter can be overwhelming. This blog outlines the must-have features in a dependable attendance management system, ensuring that your organization remains future-ready.
1. Biometric Integration for Accuracy and Security
Manual time tracking methods are prone to errors, manipulation, and buddy punching. One of the most critical features of a modern attendance management system is biometric integration. This ensures that attendance data is captured with accuracy, making it virtually impossible for employees to clock in on behalf of others.
Systems equipped with biometric devices - such as fingerprint scanners, facial recognition, or even iris scans - offer a layer of security that traditional systems simply can't match. These devices not only reduce time theft but also help maintain a hygienic, touchless environment when facial recognition or mobile-based entry is used.
Solutions from companies like Spintly, known for their cloud-based, smartphone-enabled biometric attendance systems, are a great example of how this feature can be seamlessly implemented.
2. Cloud-Based Accessibility
With remote and hybrid work becoming the norm, it’s important that your attendance management system isn’t tied to a single location or physical infrastructure. Cloud-based systems allow real-time data access from any device, anywhere, anytime. This is especially beneficial for organizations with multiple branches or a mobile workforce.
Cloud-enabled platforms make it easier to consolidate attendance data, generate reports, and integrate with other tools like HRMS or payroll software. Companies exploring scalable cloud solutions will find that Spintly’s cloud-first approach offers both flexibility and dependability.
3. Real-Time Data and Analytics
Having real-time insights into employee attendance trends can significantly improve decision-making. A reliable attendance management system should provide live dashboards, customizable reports, and alerts for irregularities such as absenteeism, late check-ins, or excessive breaks.
With advanced analytics, HR professionals can identify attendance patterns, forecast manpower needs, and manage workforce productivity more effectively. Real-time data also simplifies compliance reporting and audits, reducing administrative overhead.
4. Mobile App Support
Employees today expect flexibility, and employers need agility. A mobile-friendly attendance management system allows employees to mark attendance from their smartphones, view their attendance records, and request corrections or leaves - all in a few taps.
For field workers or remote teams, geofencing and GPS-based tracking ensure that time logs are authentic and location-verified. Providers like Spintly, which focus on mobile-first design, make it easier for businesses to adopt digital attendance solutions without sacrificing convenience.
5. Integration with HR and Payroll Systems
An isolated attendance management system may get the job done in terms of tracking time, but it misses the larger picture. Integration with HRMS and payroll platforms ensures that attendance data flows automatically into payroll calculations, leave balances, and performance reviews.
This reduces manual work, minimizes the chance of errors, and enhances operational efficiency. Look for systems that offer open APIs or native integrations with the software your HR team already uses.
6. Customizable Policies and Configurations
Different organizations have different attendance policies - some may follow flexible hours, while others operate in strict shifts. A good attendance management system should support various configurations to align with your company’s attendance, leave, and overtime policies.
Customizable rule settings make it easier to ensure compliance with internal guidelines and government labor laws. Whether you're managing a small team or a large enterprise, the ability to tailor the system to your needs is essential.
7. Scalability for Future Growth
Today’s small business could be tomorrow’s enterprise. Investing in an attendance management system that can scale with your business ensures long-term value. Whether you expand to new office locations, onboard hundreds of employees, or shift to a remote-first model, your attendance system should be capable of growing with you.
Scalable solutions, such as those offered by Spintly, are designed with enterprise flexibility in mind. These platforms handle increasing data volumes and user loads without performance issues or loss of data integrity.
8. Compliance and Audit Trail
Labor law compliance is a non-negotiable aspect of workforce management. A trusted attendance management system should automatically store logs, generate compliance reports, and provide an audit trail in case of inspections or legal disputes.
These capabilities protect your business from potential fines or legal complications while also improving transparency and accountability across the organization.
9. User-Friendly Interface
Even the most feature-rich attendance management system can fall short if it’s difficult to use. A clean, intuitive interface enhances the user experience for both employees and administrators. From clocking in to running reports, every function should be easily accessible.
Solutions that emphasize user experience - like Spintly’s minimal and intuitive interface—encourage adoption and reduce the learning curve for HR staff and employees alike.
10. Security and Data Privacy
Attendance data includes sensitive employee information, so it’s essential that your system adheres to data security standards. Look for features like role-based access control, encrypted data storage, and secure cloud infrastructure.
By selecting a vendor that prioritizes cybersecurity, you ensure that your attendance data remains protected from unauthorized access or data breaches.
Conclusion
Selecting the right attendance management system isn’t just about tracking time - it’s about transforming how your organization manages people, improves productivity, and adapts to a changing work environment. From biometric integration to mobile access and real-time analytics, the right system offers far more than just a digital punch clock.
If you’re seeking a smart, scalable, and cloud-powered solution, consider platforms that combine biometric access, seamless integrations, and intuitive design - like Spintly. As businesses embrace digital transformation, upgrading to a reliable attendance management system isn’t just a strategic move - it’s a necessary one for staying ahead.
#attendance management#attendance system#time and attendance software#biometric attendance#attendance#access control solutions#accesscontrol#mobile access#smartacess#spintly#biometrics#visitor management system#access control system
0 notes
Text
Advances in Eye Care

Modern eye care has evolved from traditional herbal remedies and protective measures to address the visual impairment affecting over 2.2 billion people worldwide. The industry has embraced technological innovations to meet these expanding challenges.
Diagnostic eye exams have changed from subjective, uncomfortable procedures to digital methodologies that deliver superior precision and efficiency. Where accuracy once depended heavily on the examiner's expertise, contemporary technologies now dominate. Digital phoropters used for refraction tests and ophthalmoscopes for internal eye structure examination have replaced manual instruments, automating data collection and improving patient outcomes. For instance, CLARIFYE - an advanced digital eye exam tool - can map the eye's health in detail and test various conditions. It enables eye doctors to formulate refined treatment strategies and deliver more dependable prescriptions.
Optical coherence tomography (OCT) marks another leap forward in diagnostics and treatment. Using harmless laser light, this non-invasive method generates detailed cross-sectional images of the retina, allowing eye care professionals to spot subtle shifts and track disease progression early. In practice, OCT is invaluable for managing glaucoma - a stealthy cause of permanent blindness - and age-related macular degeneration (AMD) causing vision loss in senior demographics.
Research into eye diseases thrives on technology that opens fresh pathways to explore their traits, i.e., transmission patterns, genetic roots, visual markers, and treatment responses. Resources such as the IRIS registry empower clinicians with access to extensive real-world datasets for detailed disease analysis. This digital repository houses structured data that, when subjected to advanced analytics, yield insights unattainable through conventional methods. Abundant online epidemiological data also enables practitioners to track disease prevalence and distribution patterns for better prevention/management.
Cataract surgery has seen transformative gains, with tech now capable of restoring sight. Laser-assisted methods deliver precise incisions and correct astigmatism - an irregularity in the cornea or lens. By softening the cataract, lasers streamline its removal and boost surgical success. The femtosecond laser, adjustable to each patient's eye, allows surgeons to sculpt incisions with top accuracy in placement and depth. Patients enjoy sharper vision and quicker recoveries as a result.
Artificial intelligence is helping tackle once-daunting optometric challenges. Eye care experts harness AI to screen for diseases, manage patient care, and analyze complex retinal scans. AI systems can extract and classify high-res image data, reducing diagnostic inaccuracies. Eye diagnostic techniques also benefit from AI, enabling more accurate assessments and tailored treatment plans. Deep learning, a subset of AI, amplifies analytical capabilities, sifting through vast data sets, identifying complex patterns, and aiding predictions.
The pandemic accelerated tele-optometry adoption or vision care telemedicine. Demand for remote healthcare solutions drove this shift, overcoming traditional virtual care barriers. Even post-crisis, tele-optometry has persisted. Glaucoma screening pressure stations facilitate technician-mediated patient connections with ophthalmologists for live evaluations and treatment. Telehealth excels particularly in front-of-the-eye examination; patients can now take snap photos or videos of their eyes using digital devices and send the data to doctors who assess issues like redness or corneal cloudiness. Yet, telehealth has limitations; in-person consultations remain necessary for back-of-eye examinations. The quality and thoroughness of care also directly relate to the patient's ability to capture clear media.
Lastly, contact lens technology has also advanced, boosting comfort, ease, and performance. Extended-wear lenses cater to convenience seekers, allowing uninterrupted use for days or weeks while cutting infection risks. Custom-crafted lenses now suit those with tricky eye shapes or intricate prescriptions. Beyond vision correction, colored lenses add a cosmetic flair, letting wearers temporarily switch up eye color. Smart lenses, embedded with microelectronics, push boundaries further by tracking health markers like glucose or intraocular pressure. Even more striking, drug-delivery lenses now dispense medication straight to the eye.
0 notes
Text
Biometric Attendance Software: Revolutionizing Employee Attendance Management.

In today's workplace, efficient and accurate management of attendance is vital for hassle-free operations and sustaining productivity. Conventional methods, like paper-based systems, punch cards, or manual logs, can result in inefficiencies, inaccuracies, and even forgery. That's where biometric attendance software plays its role. It provides a state-of-the-art, reliable, and seamless way of handling employee attendance, guaranteeing accuracy and enhancing workforce management as a whole.
What is Biometric Attendance Software?
Biometric attendance software is an application that utilizes distinctive biological features—like fingerprints, facial features, or iris scanning—to authenticate the identity of an employee upon entry or exit. In contrast to conventional means, biometric systems rule out the risk of error due to human oversight and exclude fraud like "buddy punching" (where one employee clocks in or out for another).
Biometric systems can be coupled with other corporate technologies, including HR management software, and thus become an integral aspect of a firm's digital transformation.
Key Advantages of Biometric Attendance Systems
Increased Accuracy and Security
One of the greatest strengths of biometric attendance systems is their accuracy. As the system depends on specific physiological characteristics, chances of mistakes or tampering are negligible. Chances of staff members punching in for one another are essentially eradicated, allowing companies to have a truthful account of working hours.
Time-Saving
Manual tracking of attendance is time-consuming and involves constant monitoring. Biometric systems eliminate the need for constant monitoring and manual tracking, as the process is automated and attendance is recorded in real time. This enables HR teams and managers to concentrate on more critical tasks, including employee development and operational enhancement.
Cost-Effective
Although biometric systems come at a cost upfront, they pay for themselves in the long term. With automated attendance management, companies can minimize the need for extra administrative personnel to work on attendance records. In addition, accuracy by the system avoids payroll mistakes and discrepancies that are costly to the company.
Improved Compliance
Within numerous industries, precise tracking of employee hours is crucial to comply with the law and regulations. Biometric attendance software assists companies in remaining compliant with labor legislation because it maintains a safe, tamper-proof record of the employees' work times.
Eliminates Fraud and Misuse
"Buddy punching" and other types of attendance fraud are prevalent problems in companies that use manual tracking systems. Biometric attendance ensures that employees cannot punch in for other employees, which means the actual hours worked are properly recorded. This minimizes the risk of fraud and gives companies an open record of attendance.
How Biometric Attendance Systems Work
Biometric systems work through a few easy steps. First, employees' biometric information (fingerprints, facial scans, or iris scans) are collected and safely stored within the database of the system. When the employees come to work, they place their fingerprint or face (or any other biometric characteristic) on a special device, i.e., fingerprint reader or face recognition terminal. The system checks the captured information with the saved template, and where there is a match, the time is saved and the employee is logged in as present.
This information is then synchronized with the company's HR or payroll software to make sure employees receive their remunerations appropriately as per their records of attendance.
Types of Biometric Systems
Fingerprint Recognition Fingerprint attendance systems are the most prevalent of these. They take the characteristic patterns in a person's fingerprint, which are saved for later authentication. The systems are of high accuracy and used across industries on a large scale.
Facial Recognition
Facial recognition technology has become widely used for attendance management. Employees need to walk up to a terminal, and the system will recognize their face and authenticate their identity. This system is contactless and non-intrusive, and this can be helpful in a post-pandemic world where physical contact is to be avoided.
Iris Scanning
Iris scanning is a more sophisticated biometric system. It photographs the distinctive patterns in a person's eye and is among the most precise method of biometric identification. Though this system may be more costly, it is extremely secure and best suited to environments where there is a great need for tight security.
Voice Recognition
While less popular than fingerprint or facial recognition, voice recognition is another possible approach to biometric attendance. This operates by dissecting the distinctive patterns of an individual's voice and can be applied in attendance systems, particularly for phone or remote check-ins.
Integration with HR and Payroll Systems
One of the most significant benefits of biometric attendance software is its easy integration with other business systems, specifically HR and payroll systems. Integration makes sure that the attendance information goes directly to the payroll system, minimizing errors during wage calculations. It also dispenses with the necessity of manual data input, ensuring quicker and more precise payroll processing.
This integration helps businesses track overtime, absences, and tardiness automatically, making it easier for managers to address performance issues or reward punctuality.
Ease of Use and Employee Adoption
In spite of the high technology involved in biometric systems, they are not difficult to operate for both the employer and the employee. The employees just have to put their fingerprint, face, or any other biometric feature into the system to clock in or out. The systems are generally quick, taking only a few seconds to authenticate the identity and mark the attendance.
For workers, the implementation of biometric attendance systems tends to be smooth. Everyone is already accustomed to the idea of fingerprint or face recognition using smartphones and other gadgets, so it is not as scary for them to move into biometric attendance systems.
Data Security and Privacy Considerations
Data privacy and security are of paramount importance in biometric attendance systems. Companies should ensure that the biometric information gathered is safely encrypted and stored to avoid illegal access. There is also the need to follow data protection legislation, like the General Data Protection Regulation (GDPR) of the European Union, which places stringent regulations on the storage and processing of biometric information.
Moreover, companies should notify employees of the use of their data and make sure that they have consented prior to the collection of their biometric data.
Conclusion:
A Step Toward the Future of Workforce Management Best Biometric attendance software is more than a means to monitor employee hours—it's a workforce game-changer for the way companies manage their workforce. With the capability to minimize errors, eliminate fraud, and easily integrate with HR software, biometric solutions provide a cost-effective and accurate means to enhance attendance management. As companies continue to adopt digital solutions, biometric attendance systems will become a critical component of maintaining accuracy, efficiency, and security in the workplace.
Biometric attendance software is not all about tracking time—it's about going forward to the future of work and establishing a more streamlined, secure, and transparent work environment.
0 notes
Text
Unveiling the Power of PIR Motion Detectors: Enhancing Comfort and Efficiency

In the realm of energy saving and automation, motion detectors play a pivotal role, and among them, Passive Infrared (PIR) motion detectors stand out for their efficiency and reliability. The Iris F20R PIR Motion Detector by Sensinova represents a significant advancement in this technology, combining precision with ease of use. This article delves into how PIR motion detectors work, their benefits, and why the Iris F20R model is an exceptional choice for both residential and commercial settings.
What is a PIR Motion Detector?
A PIR motion detector is designed to sense the infrared light radiating from objects in its viewpoint. Every object emits some form of infrared radiation, and when there’s a shift in this radiation—such as when a person moves across a room—the sensor detects this change and can trigger various responses like turning on a light or setting off an alarm.
How Does the Iris F20R PIR Motion Detector Work?
The Iris F20R operates by detecting changes in the levels of infrared radiation within its environment, especially the heat emitted by humans and animals. It’s equipped with a highly sensitive infrared sensor that captures even subtle movements, making it highly effective for security purposes. When movement is detected, the device can activate lighting, trigger alarms, or initiate other pre-programmed actions.
This detector is meticulously engineered to avoid false alarms—a common issue in less sophisticated sensors—by distinguishing between inanimate objects and genuine motion activity. It's an ideal solution for areas where precision is critical, such as corridors, entryways, and large halls.
Benefits of Using the Iris F20R PIR Motion Detector
Energy Efficiency: By triggering lights and other electrical devices only when necessary, the Iris F20R helps save on energy costs. This is particularly beneficial in spaces that are not continuously occupied but still require intermittent surveillance and lighting.
Ease of Installation: The Iris F20R is designed for straightforward installation, making it accessible not just to professionals but also to individuals looking to enhance their home security systems. Its user-friendly design supports a quick setup, integrating seamlessly with existing security frameworks.
Customizable Settings: Users can adjust the sensitivity and the operational parameters of the Iris F20R to suit specific needs and environments, making it a versatile choice for various applications.
Applications of the Iris F20R PIR Motion Detector
The practical applications of the Iris F20R are vast. In homes, it can be used to automate lighting in hallways and rooms, enhancing convenience and energy efficiency. In commercial spaces, it serves as a critical component of security systems, activating alarms or recording devices upon detecting movement.
Why Choose the Iris F20R from Sensinova?
Choosing the Iris F20R PIR Motion Detector from Sensinova means opting for reliability and advanced technology. Its precision in detecting genuine motion without being triggered by irrelevant disturbances sets it apart in the market. Additionally, Sensinova's commitment to quality and customer satisfaction ensures that users receive not only a top-tier product but also comprehensive support.
The Iris F20R PIR Motion Detector is an essential tool for anyone looking to enhance the efficiency and security of their property. With its advanced technology, ease of use, and versatile applications, it stands as a testament to Sensinova's innovation in the field of motion detection. Embrace the next level of automated security and efficiency with Sensinova’s reliable solutions.
0 notes