#is ethical hacking a good career
Text
HOW TO CREATE A RAT (REMOTE ACCESS TROJAN)
HOW TO CREATE A RAT (REMOTE ACCESS TROJAN)
Remote Access Trojan (RAT) 💀 is one such malware. Which can give you access to any system. Be it mobile or computer, you can get remote access to it.
Create a RAT – Remote Access Trojan
This is the best project ever. I had never done anything like this before. I never controlled anyone else’s system with my own system. But I’ve always wanted to do this (RAT) it allowed me to do some interesting…

View On WordPress
#ethical hacker salary#ethical hacking#ethical hacking course#ethical hacking course fees#how to become an ethical hacker#HOW TO CREATE A RAT (REMOTE ACCESS TROJAN)#how to hack android#how to hack whatsapp account ethical hacking#is ethical hacking a good career#remote access trojan#what is an ethical hacker#what is ethical hacking
8 notes
·
View notes
Text

Alright, first career towards my bootcamp mod is done! We have the cybersecurity career.
It's not just the career, though. You will also be able to level your cybersecurity skill and do other things with this skill.
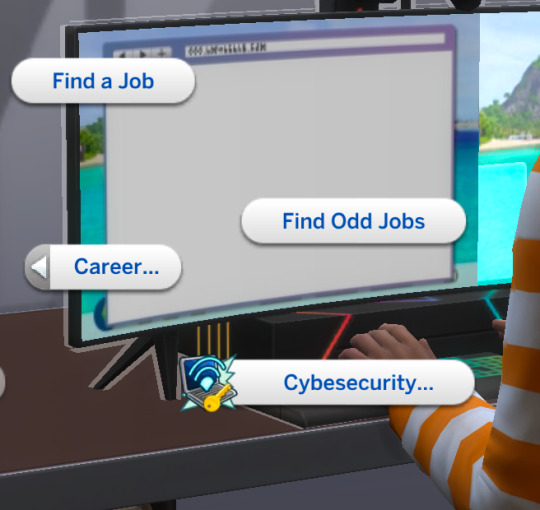


There is a cybersecurity pie menu on the computer. This is where you will be performing all of your interactions. A big part of this mod is getting your cybersecurity skill to be high enough to be hired at "Microscotch"... because it's a cool big tech company?
In cybersecurity certifications are really valued, so your sim will have the opportunity to buy exam vouchers and sit for cert exams in order to get certified.
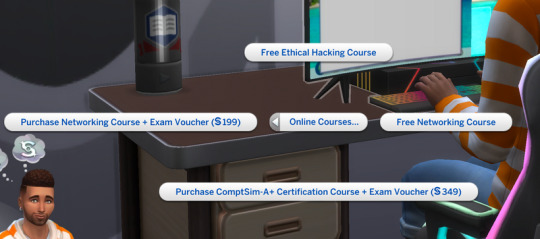
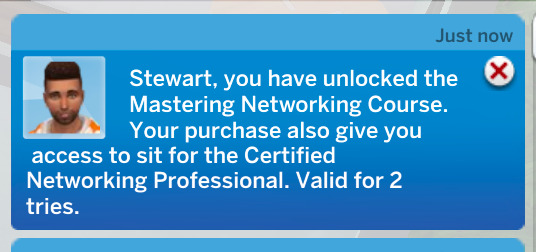
The ethical hacking exam is unlocked at a certain level of cybersecurity skill. Also, if you get the job at Microscotch, you will need to pass the Ethical Hacking exam at a certain point in order to move on. You will be given money though, to pay for the exam.
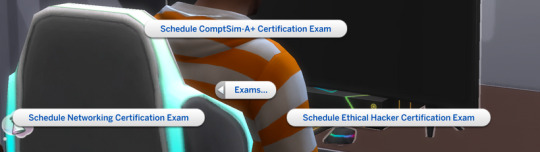
Once you have scheduled the exam make sure that you go around the time you scheduled it or earlier. Also do not schedule multiple exams at a time. It bugs out a bit when you do that.


Once you apply for the job make sure you have what it takes. ie. certs, or university degree is also good. Your cybersecurity skill should also be pretty high..just to be safe.

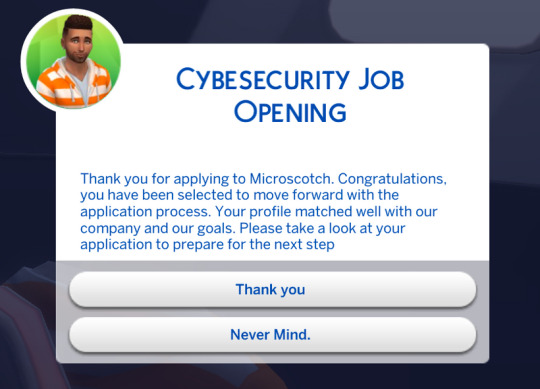
If you are selected you will move on to the next step. The technical exam and the interview.

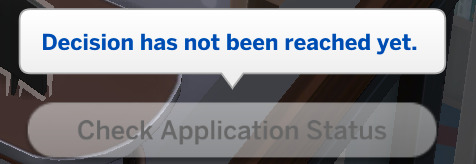
Make sure you keep checking the computer to see whether or not the decision has been reached. Once it has and you check your computer you may or not have gotten the job!
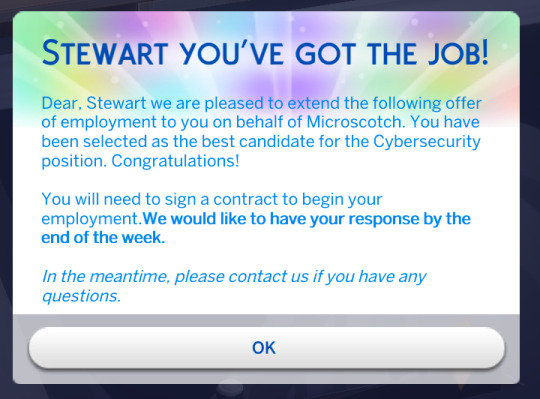
After you've got the job. You can sign your contract and start. If you do not sign it within a week, the job offer will expire.
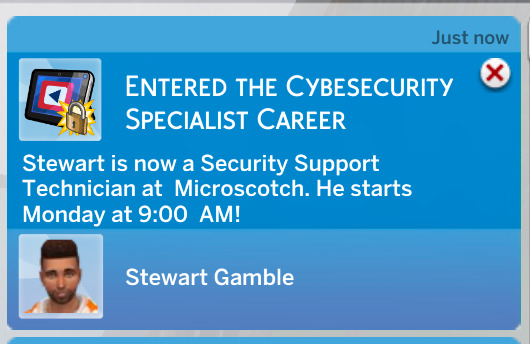
Well, that's about it for the career!
Per usual report any bugs, I've fully tested and everything went well, but you never know.
The Mod is BGC 👯♀️
How to install the mod?
Electronic Arts/The Sims 4/Mods <--- Unzip the file and make sure it's placed in this path.
What's next for the mod?
I plan on fleshing the skill out individually more. Also, I will be adding to my internship mod.
(And obviously the whole Bootcamp mod thing!)
Download: Patreon
Early Access Out Now!
Public Oct 5th
#the sims 4#thesims4#sims 4 mods#the sims cc#ts4#sims 4 edit#ts4cc#sims 4 cc#ts4 mod#ts4 mods#mycc#ts4 download
707 notes
·
View notes
Note
Do you have any suggestions for two vigilante/heroes teaming up; casual enemies, to friends, to lovers?
This is the best kind of pipeline; the gradual step up from enemies to lovers is just <chef’s kiss>. To match the prompt with the ideation, both Admin M and Assistant Admin Kasi will be posting some ideas for you! Enjoy~
Admin M:
Working for Character A is ASS. Their sidekick, Character C, really gets the brunt of the shit-work, especially after they team up with their hero partner, Character B. Just when Character C thought it couldn’t get any worse, they wake up to find themselves having been kidnapped by Character A & B’s arch nemesis along with Character D, Character B’s sidekick. Bored with their situation (and trying to not hate each other even more than they already did), Characters C & D hang out and talk while they wait to be rescued. They soon discover they have incredibly complimentary powers, hopes, and dreams. Who the hell needs heroes when two sidekicks can totally overpower them, right? They vow to team up (hesitantly). This psuedo-partnership slowly moves from hate, to appreciation, to acquaintances, then to hate-flirting. This energy comes to a peak one night after they’re recovering from a failed mission where they tried to take revenge on their kidnapper villain on their own. Blame leads to a fiery argument and then an even more fiery night.
Character A is a vigilante hero has always been the protector of their section of the city; for 15 years, no one dared to cross their territory (unless they were a special kind of stupid). This is only solidified after another vigilante (Character B) moves to town to support their partner’s new career. Guess what? They still need to do hero stuff, and it’s not like they can commute an hour away (not if they wanted to be back in time to get dinner on the table), so why not just have two heroes in the same section? What’s the harm?
The phrase “this town ain’t big enough for the two of us” was practically invented just for these two. Characters A and B are cowboys who run rivaling ‘gangs for good’ in their small western town. These two groups would act as protectors, shooing away snakes, wrangling cattle, and making sure the town was safe from robbers. The two groups, however, kept showing up to the same incidents, and 16 burly cowboys in one house helping an older lady who fell is just RIDICULOUS. It may be time to end this feud, once and for all.
Being a hacker is hard work. Okay, wait, let me rephrase: being an ethical hacker is hard work. Character A is hired regularly as a security consultant for large corporations. Basically, they attempt to simulate a hacking attack on their client’s system, then point out potential holes in their defense and make recommendations. It’s interesting work that pays well, so Character A can’t complain too much, but their job is made just that much more difficult when they’re helping a Meat Packing company against a cyber attack. Who the HELL knew that vegan hackers were this GOOD?! Who even is this person?!?!!?
For the entirety of their existence, Characters A & B have been in a tense symbiotic relationship which has only been exacerbated by their, well, overall hate for the other. It wasn’t enough that they wanted to “throw hands” or anything, but it was enough that they wanted to mess with one another. Character B would cause Character A’s seas to rise on a certain rhythm, and Character A would huff before inspiring the fleas on their back to plant some sticks on Character B. It was mostly in good fun, but as the centuries continued to pass, they found that they had a deep-seeded longing for one another that they couldn’t shake. Finally, they decide that enough is enough and they attempt to touch again for the first time in a million years. The fleas, however, kick up a racket and try to stop them from exploring their feelings, citing things like “IF THE MOON CRASHES INTO THE EARTH, ALL LIFE WILL DIE” and other nonsense.
Selling potions of the gods is hard work, but collecting sweat from the brows of spent gladiators was the easy part. The more dangerous side really came from the other merchants of “beauty potions” and “aphrodisiacs.” When it came to blood, sweat, tears, and money, they became downright deadly.
When two politicians from the same political party decide to run for office against one another, they appear to have a fairly amicable relationship in the public’s eye (at least, as amicable as politics can get). Behind the scenes, however...Character A & B were absolutely feral. This hate fed into a poorly conducted night of romance which they both regretted. The following morning, they both stumbled out of the same bed, went to the same political debate, and told the other how they really felt about their stances, warts and all (and by all, let’s just say they weren’t exactly PG about what they had experienced the night before).
Here are some possible one-liners / comebacks:
“I’d agree with you, but then we’d both be wrong.”
“I’ve found puddles on the ground deeper than you.”
“I’ll never forget the first time we met... But I’ll keep trying.”
“What’d your parents do? Drop you to see if you’d turn off and on again?”
“They say opposites attract. I hope you meet someone who is good-looking, intelligent, and cultured.”
“I'm trying my absolute hardest to see things from your perspective, but I just can't get my head that far up my ass.”
“There's no need to repeat yourself. I ignored you just fine the first time.”
“Isn’t there a bullet somewhere you could be jumping in front of?”
“1 universe, 8 planets, 7 seas, 7 continents, 809 islands, 196 countries, and I had the unfortunate luck of meeting you.”
A. Admin Kasi:
Hero A was by the books, always following rules and never stepping on the toes of the law...that is, until a villain comes to town who’s stronger than anyone Hero A has ever faced before. Cornered, Hero A has no choice but to illicit the help of Hero B, a reckless, law-breaking newbie. Unfortunately for Hero A, there was no other choice (believe them when they say they checked). The more the two work together to defeat the villain, the closer they get and they slowly realize that maybe, just maybe, they don’t completely hate each other.
“Getting married to someone with superpowers was supposed to be great! Who wouldn’t want to be with someone with powers equal to a god? It really was a dream come true, but then, they started being a ‘hero.’ Now, the only time I ever see see them is passing glances in the house when they’re leaving for whatever new ‘hero work’ is needed. Which is always. So, with incredible pettiness, I decided I needed to do one thing: become their arch nemesis. How else was I supposed to get their attention?” AU
Hero A loved their roommate. They had the exact same schedule -- night jobs that took them both out of the house at the same time. There were no loud noises through the day because they were both sleeping, and they shared dinner together every night before heading out for a productive evening. It seemed like the ideal situation, and the two fell into a routine of mutual ease. It was perfect...that is, until Hero A started noticing bruises on their roommate that seemed really familiar to where they hit their arch nemesis the previous night.
Villain A had always thought Hero A had the absolutely dumbest abilities. Who the hell would ever want that ability to speak to and control birds? BIRDS?! Even though the power was ridiculous, THAT hero somehow became the protector of the city. Hero B was always in their shadow, second best in terms of recognition even though Hero B clearly had the better skills. They didn’t think Hero A even deserved the title until a situation comes up that requires Hero A’s exact abilities. Begrudgingly, Hero B has to ask for help. That being said, after seeing Hero A in action, their powers (and Hero A) are pretty okay.
Hero A was retired. You hear that?? RETIRED! Ever since a bullet went through their leg, making fighting incredibly painful, Hero A was content to give up that life and spend the rest of it doing mindless hobbies. This semi-retirement was pulled to a screeching halt when one day, their old nemesis was dumped on their doorstep, beaten within an inch of their life. After a lengthy recovery and a whole lot of questions, it turns out that Hero A’s old partner had gone completely off the rails. The two ex-enemies now have to team up: the cranky former hero and the villain with a newfound moral code. One night of careful scheming after another leads the two to become closer and for all lines to become blurred. At the end of it all, they couldn’t tell where hero ended and villain began.
Mercenary was a loose term; Character A did all jobs, as long as they were paid in the end. It spanned from killing, to spying, to escort missions, and they were content with them all. Character A barely even read the contract of the next job, only seeing the massive payout and disregarding any other details. They regret that now. Turns out, their new job is to guard the one person they hate more than anything: their rival -- a harsh, illegitimate business person that screwed Character A over too many times to count. Now, they’re forced to spend every waking moment together, but Character A isn’t finding it quite as horrible as they originally thought.
#admin m#a admin kasi#auideas relaunch#au friday#hero au#superhero au#vigilante au#antihero au#sidekick au#enemies to lovers au#insulting au#cowboy au#cowboys au#hacker au#ethical hacking au#tech au#technology au#villain au#second chance au#roommate au#roommates au#vegan au#vegetarian au#opposites attract au#god au#goddess au#gladiator au#fighting au#fighting pits au#market au
33 notes
·
View notes
Text
"Hacking Unveiled" – An Exploration into the Dark World of Cybercrime
Dive into the heart-pounding realm of hacking and cybercrime with “Hacking Unveiled.” This thrilling journey uncovers the mysterious world of hackers and their techniques, guiding you through the preventative measures you can take to safeguard yourself.
Discover the diverse types of hackers and their motivations, from ethical hackers to cyber criminals. Unveil the intricacies between “white hat” and “black hat” hackers, and learn how to become an ethical hacker yourself.
Enter into the infamous world of the “famous hackers and their stories” and the notorious “anonymous group and their attacks.” Get an inside look into the “hacking techniques used by cybercriminals” and the profound impact these actions have on businesses.
Get a sneak peek into the latest “hacking tools and software” used by both ethical hackers and cybercriminals, and delve into the subjects of “penetration testing” and “protecting against social engineering attacks.” Stay ahead of the game with the latest “hacking news and updates” and uncover the captivating “career opportunities in ethical hacking and cybersecurity.”
Be aware of the ever-evolving future of hacking and cyber threats. Let “Hacking Unveiled” guide you through the unknown, demystifying the complexities of cybercrime.
White Hat Hackers
Black Hat Hackers
Anonymous
Gray Hat Hackers
State-sponsored Hackers
Hardware Hackers
Crackers
The Spectrum of Cybercrime: Understanding the Different Types of Hackers
White Hat Hackers
White hat hackers, or “ethical hackers,” use their skills for good. They work alongside organizations, acting as “cybersecurity experts,” to identify and fix system vulnerabilities, protecting individuals and companies from cyber attacks.
Black Hat Hackers
In contrast, white and “black hat hackers” engage in illegal or malicious activities, such as stealing personal information, disrupting services, and spreading malware.
Anonymous
The loosely organized international group of hackers, “anonymous,” is known for participating in high-profile cyberattacks and spreading political messages.
Gray Hat Hackers
Sitting between white and black hat hackers, “gray hat hackers” may use their skills to identify vulnerabilities but exploit them for personal gain or to draw attention to the issue.
State-sponsored Hackers
The ominous “state-sponsored hackers” work on behalf of governments, using their skills for espionage or political sabotage, potentially significantly impacting national security and international relations.
Hardware Hackers
In addition to software hacking, there are also “hardware hackers,” who specialize in manipulating physical devices, such as breaking into intelligent homes or hacking into cars.
Crackers
A synonym for black hat hackers, “crackers” use their skills to crack into systems, software, or networks, gaining unauthorized access.
Cybercrime: Understanding Standard Techniques
To safeguard against malicious cyber attacks, knowing the most frequently employed tactics, including phishing scams, password attacks, and exploiting software vulnerabilities, is crucial. This post delves into the most prevalent hacking methods, from social engineering and phishing to malware and advanced persistent threats (APTs). Stay alert and ensure your software and security systems are always up-to-date to minimize the risk of falling victim to cybercrime.
Social Engineering: The Deceptive Tactic
Cybercriminals often resort to social engineering to manipulate individuals into divulging sensitive information or performing actions they wouldn’t otherwise. This tactic can take various forms, including phishing scams, pretexting, baiting, and more. To guard against these attacks, it is critical to be suspicious of unsolicited requests for personal data, be cautious when clicking on links or downloading attachments from unknown sources, and keep your software and security programs up-to-date.
Phishing: The Tricky Scam
Phishing is a form of social engineering that seeks to deceive individuals into surrendering confidential information, such as login credentials, financial details, or sensitive personal data. These scams often come in email or text messages, posing as credible sources. To avoid falling prey to phishing attempts, it is recommended to look out for suspicious messages, particularly those asking for personal information, verify the authenticity of links before clicking on them, and be wary of downloading attachments or clicking links from unknown sources.
Malware: The Harmful Threat
Malware, including viruses, trojans, and ransomware, is specifically designed to cause harm to computer systems. Installing and updating a reputable antivirus program is essential to protect your computer.
Additionally, be mindful of the files you download and links you click, especially if they are from unknown sources, as they may contain malware.
APTs: The Persistent Threat
Advanced persistent threats (APTs) are cyber attacks by state-sponsored hackers or highly-skilled cybercriminals. These attacks are known for their persistence as the attackers often go undetected for an extended period. To detect and fend off APTs, it is crucial to have an up-to-date antivirus program installed on your computer and to be cautious of unsolicited emails or text messages, especially those asking for personal information.
Defending Against Cyber Threats: Strategies for Keeping Your Data Safe
Essential Tactics to Outwit Hackers and Stay Secure
Essential tactics to protect against cyberattacks include using robust passwords, safeguarding personal information, regularly updating software, and securing devices. These may sound simple, but neglecting to do so can have severe consequences.
The Importance of Strong Passwords and Up-to-Date Software Keeping software current helps to avoid vulnerabilities that older versions may have. Strong, unique passwords for each account can provide an easy yet effective layer of security.
Tips to Protect Personal Information and Devices Being mindful of phishing scams, using privacy settings on social media, and being prudent about what personal information is shared online are critical in securing personal information. Ensure devices are protected with a passcode or fingerprint and backup important files regularly.

The Mysterious World of the Dark Web
The dark web may sound like a concept from a hacker movie, but it’s real and can be a bit frightening. It’s crucial to understand what it is, how it differs from the regular web, and the type of activity. This article will shed some light on the enigmatic side of the internet.
Accessing the dark web requires special software and is invisible to the general internet user. It’s often linked to illegal activities, such as buying and selling illicit items, hacking services, and trafficking personal information. Exercise caution when accessing the dark web and take steps to protect personal information.
The dark web is a collection of websites that can only be accessed using specialized software, such as the Tor browser. Despite being often linked to illegal activities, not all its use is illicit.
However, accessing the dark web carries risks and can threaten personal information and security. Be cautious and take measures to protect personal data when accessing the dark web.
Why Access the Dark Web
Accessing the dark web can be dangerous and threaten personal information and security. Exercise caution and take necessary measures to protect personal data when accessing the dark web.
How to Enter the Dark Web
The most popular way to access the dark web is by using the Tor browser. It’s a free, open-source browser that routes traffic through multiple layers of encryption, making it challenging to trace activity. However, accessing the dark web comes with risks and requires using a VPN, never sharing personal information, and avoiding using real names.
Now that you have a better understanding of the dark web, the choice is to delve into the mysterious side of the internet.
Don’t Fall Victim: How to Protect Yourself from Identity Theft
Be Alert! Identity Theft Lurks, Stalking Unsuspecting Victims
It’s a modern-day nightmare – cybercriminals prowling the internet, seeking out unsuspecting individuals and businesses to victimize through identity theft. From phishing scams to data breaches, the tactics used by these criminals are sophisticated and ever-evolving. The consequences of falling prey to such a crime can be devastating, leaving financial losses and a tarnished reputation in its wake.
Beware! Know Your Enemy.
Cybercriminals use various methods to obtain personal information, including phishing scams, data breaches, dumpster diving, and even purchasing it on the dark web. Stay informed and take proactive measures to protect yourself and your information.
The Aftermath – A Life Turned Upside Down
The impact of identity theft is far-reaching, affecting victims’ finances and reputation and often causing emotional stress as they work to regain control of their personal information.
Don’t Be a Statistic – Defend Yourself!
Fortunately, you can take steps to safeguard yourself against identity theft. Regularly updating software, using strong and unique passwords, being cautious about sharing personal information, and remaining vigilant for unsolicited phone calls or emails are just a few examples.
Protect Your Information and Devices
In addition to these basic measures, take extra steps to secure your personal information and devices. Keeping personal information offline, using anti-virus software and firewalls, encrypting sensitive data, and ensuring your devices with locks and PINs are crucial for maximum protection.
If Disaster Strikes – Have a Plan
If you suspect you have fallen victim to identity theft, acting quickly is essential. Notify your bank, credit card companies, and credit reporting agencies to place a fraud alert on your accounts. Turn to resources such as the Federal Trade Commission’s IdentityTheft.gov and the Identity Theft Resource Center for guidance on reporting and recovering from the crime.
Stay Protected – Stay Vigilant
Identity theft is a constant threat that requires ongoing attention and preventative measures. By staying informed, protecting yourself and your information, and knowing where to turn in the event of a breach, you can reduce your risk of falling victim to this malicious crime.
Stay Ahead of the Game – Subscribe to Our Blog!
Remember to subscribe to our blog for more informative and helpful articles on cybersecurity and protecting yourself. Stay ahead of the game in the fight against identity theft!
This article is originally posted at https://nikolin.eu/tech/hacking-unveiled-a-fascinating-dive-into-the-world-of-cybercrime-and-its-prevention/
#hacking#hackers#black hat hackers#white hat hackers#gray hat hackers#cybercrime#cybersecurity#dark web
10 notes
·
View notes
Note
This is the for the "DVD commentary" ask meme. I ... am not sure I want to paste in 500 words or count them. So if you want, could you do a DVD commentary for the "Watcher X Escapes" fic you wrote, I know you talked about it a bit, but I really liked the dialogue between X and Kyrian.
Watcher X is such a fascinating character. He pretty much tells the Agent he’s only helping them/the Empire because of his conditioning, yet a lot of his conversations with the Agent have this odd mentoring aspect to them. To lull them into a false sense of security? To win them over? Because he does have some loyalty to the Empire? Because he feels some connection to or pity for the Agent, who is almost certainly doomed to some fate at least as unpleasant as his own?
Nothing about him is straightforward; there’s always this sense of something hidden. He’s a man who always has something up his sleeve, some ulterior motive, some plan he hasn’t revealed. I know he’s supposed to be a product of the Watcher design program like Watcher Two, but I have trouble not thinking of him as someone who’s been in the field. There’s just something about the kind of advice/suggestions he offers that feels like personal experience, not just a previous career of advising other people in the field.
In any event, he’s far too skilled and far too clever for his potential in-game end. Hence the fic.
And I wanted to keep that sense of hidden motives about him for his dialogue with Kyrian.
Is everything X says just manipulation, waiting for the right moment to use the secondary function he'd rigged in the implants? Is he just messing with them, like Kaliyo thinks? Or is he trying to find a way to end their stand-off of sorts peacefully?
Or is the whole conversation something of a Xanatos Gambit? Whatever happens, he wins, because the only option that might have prevented him from escaping wasn’t actually on the table. (He clearly has Kyrian figured out well enough to know that.)
Kyrian, conversely, has no option open to him that he likes. He can’t just let X go because Kaliyo won’t go for it and there’s a good chance that Watcher Two has hacked into any available security cameras and is watching the whole thing. He doesn’t really want to try and drag X back to Shadow Town (not that he thinks he could) and knows he can’t just convince him to go back. (Why would anyone?) And he definitely doesn’t want to shoot him.
What he wants is to somehow manifest a solution that works out for everyone. Even though he knows that’s somewhere between wildly unlikely and impossible.
So we start with game dialogue. With clever, twisty X who, as always, has something up his sleeve. And immediately take a left turn as Kyrian tries to convince them both that there is some magical third option, that maybe there’s a way to convince Intelligence that X should be rewarded for his efforts.
There’s not, of course.
The irony, or something like irony, of the situation is that the conversation is a battle of wits between two people who basically want the same outcome and neither of them can talk their way to it, largely for reasons that are out of their control. The only person in the hanger who wants X dead or back in Shadow Town is Kaliyo.
X knows Kyrian doesn’t have the power to convince Intelligence to set him free or reinstate him or anything that’s not (at best!) stick him back in Shadow Town. Kyrian isn’t ready to acknowledge that he’s not loyal to the Empire, or at least that his sense of morality and ethics and compassion and all the other things a field agent shouldn’t have will always outweigh his loyalty.
Though I do hope the audience is as amused as X is when Kyrian's response to X noting that he's clearly not a proper Cipher agent because he keeps trying to find "soft, inefficient solutions" is to...keep trying to find, or sell, a soft solution to their standoff.
Then again, Kyrian's also right that X is stalling (or also stalling), since X has the ability to end their apparent impasse at any time. Perhaps X really does think he can get Kyrian to realize that he and his career are doomed. Something makes him wait until the last moment, anyway, even if its merely a sense of drama.
And the lesson Kyrian learns is not: “if you’re supposed to shoot someone, don’t talk to them first” it’s: “maybe I’m not entirely loyal to the Empire.” Now that the question he hadn’t dared to ask himself has been asked, it can’t be unasked.
Though the lesson he probably should have learned was: "get out while the getting's good." Somewhere out there, Watcher X must be so disappointed in how Kyrian's career ended.
6 notes
·
View notes
Note
i've been thinking;;; we know Brucie, Wisteria and Penny are related to the crime family... what about an AU where they were directly in the business?
Mmmmmmmm good soup~! Thank you Anon :)
CW: drugs, violence
Brucie: has been involved with the group in the past; he left after a work-related incident scarred him deeply emotionally, and permanently injured one of his legs. Had it not been for that incident, Brucie would still be going by a very different name and living that old life. He’s brawn, he’s muscle— treated in some ways as disposable, despite being part of the family, perhaps because he comes from a poor branch of the family rather than the rich main line. His common jobs involve being a body guard, or being sent to intimidate people into compliance with the family’s wishes. Rarely, he may be tasked with infiltrating law enforcement agencies to get information on them.
Wisteria: reluctant slacker in the group. Continually protests that her computer skills are not suitable for hacking, so fae doesn’t often hack into law enforcement or rivals’ information. Rather, Wisteria gets by creating and maintaining websites for the family’s largest shell companies, creating applications for the leaders of smaller gangs under the family’s control to report back in without police interception, and other things of that nature. They actually really hate being a part of this, not from any moral objection, but because fae resents all the responsibility and pressure it brings.
Penny: much more serious and less whimsical— even her house and clothes are more muted, understated. She has limited passion for this career, but her sharp mind and iron will make her a great candidate to be the next leader of the family, despite being the current leaders’ niece rather than one of their daughters. She’s incredibly unconcerned about the ethics of her actions— not caring who gets hurt by the family’s racketeering, drug and weapons trafficking, turf wars, etc— but with her chemistry knowledge Pen is actually incredibly picky about the quality of the illicit substances the family oversees the production and distribution of. Much like her aunt Drew Bardot, Penny dreams of a quiet and peaceful life that she will never be able to have because of her family’s history and her involvement in it.
#mail 📬#my thoughts#yandere#yandere oc#yandere imagines#yandere scenarios#yandere x darling#yandere x reader#yandere x you#yandere cw#oc brucie#brucie babyyyy#oc wisteria#oc thorn#crime family
6 notes
·
View notes
Note
I don't agree with your whole emphasis on being beautiful as being pretty isn't everything. You shouldn't be advocating for things like pretty privilege, it does more harm than good.
South Korea also has one of the best education system in the world and has one the highest educated labour force in the world. So how does one gain advantage in a country where every is smart and everyone is just as good as others... they become pretty.South Korea has one of the highest rates of plastic surgery in the world and tehy are not ashamed. It's part of career advancement, an investment for yourself. Being attractive especially as a woman is like taking the lift instead of the stairs, its the fast track.
I think people forget that pretty privilege was a biological system before we turned it into a social construct. It is not a new way of socially marginalization. The desire be around good looking people, to want them to succeed, to want them to reproduce, to be liked them is all very biological. Yeh, at this point in history we are really questioning how ethical it is, but the reality that good looking people have priviliges that unattractive people don't is not going to change any time soon. I am not an advocate for something part of biology, like you wouldn't call someone an advocate for the digestive system?? I simply say this is how the world works, here are some hacks if you are struggling.
Pretty privilege exists and it does suck there are things you could do if you are not born attractive to get similar advantages. Not everyone is beautiful but they can become beautiful. You would be surprised how much a really good haircut can make a difference. Being pretty is everything but just being pretty.. yeh that won't get you too far. Prettiness does not sustain anything but it does get your foot in the door which sometimes is all you need to get everything.
46 notes
·
View notes
Text
Different Types of Ethical Hacking

Hackers employ various techniques to breach security systems and networks. With CerTera These methods define the classification of ethical hacking, which include:
Web Application Hacking: Also known as penetration testing, this method involves testing a computer system or network to identify and subsequently exploit security vulnerabilities. Web application hacking can be conducted manually or automatically, with the primary aim of highlighting a company's security weaknesses. Although ideally performed when a new network joins the system, periodic checks should be carried out to assess security performance. It proves useful during infrastructure or application modifications, the application of security patches, and changes in end-user policies. Many beginners engage in web application hacking, often acquiring certifications like the Certified Ethical Hacker (CEH).
System Hacking: This type, also referred to as network hacking, involves hackers gaining access to networks to steal data. System hacking typically targets servers or computer networks, leading to substantial data loss when successfully executed. Ethical hackers spend considerable time reviewing server or network security levels to thwart malicious activities by unethical hackers.
Web Server Hacking: Due to the potential risk of web server hacking, users are often advised against freely sharing or entering sensitive information on the web. Web server hacking enables hackers to effortlessly access information and data available online, including passwords and bank account details. It involves hackers executing sniffing attacks to pilfer sensitive information from the web. Professionals engaged in countering web server hacking often participate in various cybersecurity courses to enhance their skills.
Wireless Network Hacking: This is a prevalent form of hacking, which explains the common caution against using public Wi-Fi networks. Hackers can readily access data from open networks. As wireless networks use radio waves for communication, they can be easily hacked from nearby locations.
Types of Hackers
While we've covered types of hacking and broadly classified hackers into ethical and unethical categories, it's important to note that these hackers operate under three main designations, each with differing intentions and methodologies. These include:
Black Hat Hackers: These are the "bad guys" of the hacking world. Black hat hackers' primary intent is to reap financial rewards and cause digital disruption. They steal, manipulate, and destroy data in a manner that financially damages the data owner. Their activities have led to many misconceptions about ethical hacking.
White Hat Hackers: These are the "good guys", or ethical hackers. White hat hackers seek permission from the owner before attempting to penetrate any computer system or network. Their services are increasingly in demand in various technical and non-technical organizations seeking to protect their data and information. Many white hat hackers pursue Certified Ethical Hacker (CEH) courses.
Grey Hat Hackers: Positioned between black and white hat hackers, grey hat hackers operate in somewhat of a moral grey area. They're not necessarily malicious, but often seek financial gain after discovering a bug in a computer network system. Their actions can be unpredictable, largely dependent on their individual ethical perspectives.
Wrapping Up
Ethical hacking, while initially misunderstood, has gradually gained recognition for its crucial role in safeguarding digital systems. The profession of an ethical hacker carries significant respect and prestige. As awareness increases, more individuals are gravitating towards this field. The level of support and security that ethical hacking offers to various sectors is unparalleled. In our ever-evolving digital landscape, the need for skilled ethical hackers to protect our systems and data continues to grow.
“Unlock Your Career Potential: Enroll Now with Certera for Accelerated Growth!”
Visit our website for more information or to explore the courses.
Follow us on LinkedIn, Twitter, YouTube and Instagram.
0 notes
Text
Given information about Mystic Messenger
I'm aware that maybe some of you guys aren't know of Mystic Messenger or Hazbin Hotel. Either be a Mystic Messenger fan or a Hazbin Hotel fan. If one of you guys are both fan of these two fandom then good
Mystic Messenger
Mystic Messenger" (수상한메신저 Susanghan Messenger) is an otome mobile game developed by Cheritz, catering to a predominantly female audience.
Players engage in a captivating love story using an interactive messaging app, receiving phone calls and texts that evolve based on their relationships with other characters.
Explore detailed insights on the game's characters, routes, and additional content within this wiki.
The Characters
Jumin Han, a character within the Deep Story of Mystic Messenger, emerges as the scion of a prosperous family and the designated heir to the C&R International company. His routine is often occupied by business trips, leading him to engage in discussions primarily centred around work and mature subjects. Unfamiliar with youth slang and commoner cuisine, Jumin's conversations exhibit a certain sophistication, occasionally marked by eccentric expressions.
Jumin is an unabashed admirer of his cat, Elizabeth 3rd, frequently extolling her beauty and assuming the role of a devoted parent. However, due to past encounters, he guards his emotions closely, harbouring a deep distrust of women. Witnessing his father's unfortunate experiences with gold-diggers, individuals who pursued his father for wealth rather than genuine affection has left Jumin emotionally reserved
Zen, whose real name is Hyun Ryu, takes centre stage as one of the primary characters accessible in the Casual Story of Mystic Messenger. A multi-talented individual, Zen dabbles in acting, dancing, and singing, showcasing his semi-successful career.
While he occasionally exudes an air of narcissism, frequently sharing selfies and proclaiming his handsome visage, Zen's true desire lies in gaining recognition and appreciation for his professional talents. Beyond his external charm, he prioritizes the acknowledgement of his skills and achievements in the realms of acting, dancing, and singing.
707, also known by his real name Saeyoung Choi and the baptismal name Luciel Choi, commonly referred to as Seven, plays a pivotal role as one of the characters in the Deep Story of Mystic Messenger. Proficient in hacking, Seven possesses an exceptional ability to swiftly extract information on a wide array of subjects, showcasing his unparalleled skills in navigating the digital realm.
Yoosung, featured as one of the characters in the Casual Story of Mystic Messenger, is a college sophomore deeply engrossed in the online game LOLOL, often allocating excessive amounts of time to it. This passion for gaming leads him to neglect his academic responsibilities and, subsequently, his college studies.
Notably, Yoosung grapples with a unique familial connection, being the cousin of Rika. Despite the evidence suggesting otherwise, he struggles to fully accept the reality that she is no longer alive, adding an emotional layer to his character.
Jaehee Kang stands as a notable character within the Casual Story option in Mystic Messenger, holding the distinction of being the only female character with an individual route. Serving as the chief secretary at the C&R International company, Jaehee diligently fulfills her role as the dedicated assistant to Jumin Han.
Her character is characterized by a unique blend of kindness and unwavering work ethic, embodying qualities that contribute to her significant role in the storyline.
V, whose real name is Jihyun Kim, assumes a significant role as one of the side characters in both the Casual Story and Deep Story and emerges as a central character in Another Story, released on September 8, 2017, for Android users and shortly after for IOS users.
As the current head of the RFA, V's responsibilities are often eclipsed by his frequent offline status, attributed to his profession as a photographer and his blindness. Engaged to Rika in the past, he concealed his profound grief following her death, presenting a façade of composure.
A collaborative figure with Seven, V maintains a shroud of secrecy within the RFA. Additionally, he shares a longstanding friendship with Jumin, their connection is traced back to their shared experiences at the same church during their childhood, and reminiscing about their school days together.
Unknown, known by his real name Saeran Choi, serves as a central antagonist in Mystic Messenger. He shares an identical twin bond with 707 and aligns himself with the organization and cult known as Mint Eye. In visual novel sequences preceding the revelation of his identity, his name is cryptically displayed as three question marks (???).
In Another Story, he takes on the persona of Ray, a passionate game developer eager to introduce players to his creation, guiding them to an undisclosed location for this purpose.
An intriguing development occurred on January 31, 2018, with the release of a route dedicated to him in Another Story, followed by the unveiling of his After Ending on December 18, 2020.
The MC, an abbreviation for Main Character, serves as the primary female protagonist in Mystic Messenger. Unintentionally drawn into the affairs of the RFA, she assumes the responsibilities formerly held by Rika, the organization's founder, tasked with orchestrating a party and extending invitations to guests.
Throughout the eleven days of planning and engaging in conversations with the game's seven main characters, players have the opportunity to develop romantic relationships based on the chosen route. The culmination of the story is contingent upon the MC's interactions with each member and her behaviour throughout the specific route she undertakes.
Rika Kim, born Mina and later fostered as Serena Kim, assumes the role of the main antagonist in Mystic Messenger. As the founder of the RFA and the former fiancée of V, her apparent "demise" occurred tragically 18 months before the events depicted in the game.
Minor Characters
Chairman Han, the esteemed Founder of C&R International, stands as the father of Jumin Han.
Driver Kim, the dedicated chauffeur in the service of Jumin Han.
Echo Girl, the indulged and flirtatious idol. ( I hate her so much)
Sarah Choi, the arranged fiancée of Jumin.
Glam Choi, the sister of Sarah and the former partner of Jumin's father.
Vanderwood, the undercover agent and Seven's covert accomplice.
V's Mother, the affectionate and caring mother of V.
Chief Kim, the father of V.
Saejoong Choi, the morally questionable politician and father of 707 and Unknown.
Lucy, the adopted daughter of V and MC.
Mika, Rika's childhood friend who influenced her towards misguided choices.
Rika's Mother, the fervently religious woman who adopted Rika.
Pastor, a corrupt religious figure from Rika's past.
Mother Choi, the abusive mother of 707 and Unknown.
Yoosung's mother, showering love upon her beloved Yoosung.
Sally, the dearly departed canine companion of Rika.
Elizabeth 3rd, the cherished feline companion of Jumin.
Lisa, the beloved feline companion of Yoosung.
#mysticmessenger#fanfiction#mystic hotel messenger#jaehee kang#jumin han#yoosung kim#mysme 707#luciel choi#saeyoung choi#saeran choi#zen mysme#mc mystic messenger#jihyun kim
1 note
·
View note
Text
Mobile App Development: Options for Career

Today, the whole world is coming to depend on mobile applications. As sales of smartphones and tablets continue to rise, markets in remote places will increase rapidly with it - and hence the need for talented developers will grow likewise. From the prospect of developers, these include two parts: online job opportunities of freelancing and self-employment, wherein once well-trained you will be able to work anywhere.
Mobile Developer
App developers design, build, test, and deploy. Using native development languages like Swift or Kotlin. App developers work with product managers, designers and back-end teams to transform ideas into real mobile products. They target easy-to-use UIs that don't drag on performance, flexible design themes and templates that can match up with any back-end systems you're interfacing with or getting data from.
Skillsets: Xcode, Swift/Objective-C (iOS), Java/Kotlin (Android), Android Studio
React Native Developer
Evaluating the mobile app salary report from most to least expensive, IoT Developer is at the lower end of the high-salary range among mobile devs. If it seems that reaction native is appealing to you, good, because the fact is that there is a growing demand in industry right now for qualified developers familiar with this concept.
Key Skills: Game engines like Unity or Unreal, C#, C++, 3D modeling.
AR / VR Game Developer
AR and VR, digital components that are mixed into the real world by mobile apps, are made to wake it up to a completely new dimension. To create the next wave of immersive experiences, AR/VR developers are employing SDKs and platforms such as ARKit (Apple) and ARCore (Google). As AR/VR moves mainstream, opportunity arises for this newly advanced area. The combination of technical skills with artistic vision is priceless.
Key Skills: ARKit, ARCore, Unity, 3D graphics programming, UX/UI design
Mobile Security Engineer
For apps containing sensitive information and transactions are all of mobile security implementation level by default is a minefield. Security engineers have to enforce a comprehensive system of code and network protection in order to forestall data spillages, cyber-attacks or vulnerabilities. As businesses and startups increasingly handle massive amounts of mobile data, security expertise tailored to mobile apps has become a crucial requirement.
Key Skills: Risk analysis, cryptography, authentication, cyber forensics, ethical hacking
Remote Mobile Developer
In terms of adaptation, most jobs related to mobile dev can be done remotely. Together with work tools like Slack, Trello, and GitHub, developers have location flexibility. They are part of the worldwide team of all staff. While brands tap a much wider talent pool, they can also cut their office costs. Opportunities for varied installations and development abound when remote working.
Key Skills: mobile development skills; co-operative work; self-organization.
Start Your Career In Mobile Development
Mobile is becoming rapidly more important all the time. This is a golden age for app developers with plenty of ideas yet to be commercialized. With promising new technologies like wearable computing starting to find their place in the market, the opportunities are limitless. As a developer, you can quickly raise your level of expertise by working in such cutting-edge fields as AR/VR and cross-platform development using React Native or Flutter. Mobile developers also have access to very well-paid remote roles that offer a lot of discretion over how they spend their time. In order to find these roles with major global brands, go to the best international center for remote work, RemoteHub. There's infinity and beyond in the Code. This is the era to begin your career in mobile app development!
#Mobile App Development#app development#jobs#jobseekers#jobposting#jobsearch#career#find remote jobs#employment#online jobs#remote work#web app development#mobile application development#usa#career advice
0 notes
Text
ITRONIX SOLUTION
Software Engineer, Social Media Manager, and Director in India

At Itronix Solutions in Jalandhar, enjoy cutting-edge technology! Our extensive courses in Web Development, Python, Digital Marketing, Ethical Hacking, Data Science, Graphics Designing, PHP,Java Training in Jalandhar, Full Stack, WordPress, and C Programming Language will help you advance your abilities. You will get practical experience and mastery of the newest tools and methods through our expert-led training. Become a part of an innovative and exceptional learning environment. Take a revolutionary trip into the IT industry and realise your full potential with Itronix Solutions. With our industry-focused courses, you can master many topics, keep ahead of the competition, and write your own success narrative.
Best Data Science Course Training Institute in Jalandhar
Itronix Solutions Offers the Best Online Training Courses on Trending technology such as Python, Data Science, Machine Learning, Artificial Intelligence, IoT, Bigdata and Hadoop, Data Analytics, Ethical Hacking, DevOps, Full Stack, Cloud Computing, CCNA, CCNP, CCIE, Red Hat, Networking, Power BI, Finance, HR, Business Intelligence, Stock Market, Embedded Systems, Flutter, Digital Marketing and 100+ other Courses.
Why You Need Data Science Course Training in Jalandhar?
A Data Science course can provide valuable knowledge and skills to effectively navigate the evolving landscape of Data Science Course in Jalandhar. Itronix Solutions helps to boosts the confidence of the individuals and make them skilled in Data Science Course in Jalandhar. The need for data science course arises from the crucial role data plays in modern businesses and various sectors. Itronix Solutions provides the best Data Science Course Training in Jalandhar which helps students to achieve good professional career.
Service
Data Science
Python
Data Analytics
Machine Learning
Data Visualization
Deep Learning
Artificial Intelligence
Business Analytics
Business Intelligence
Generative AI
Data Engineering
Big Dat
Networking
Cloud Computing
DevOps
Software Testing
Hardware and Networking
CCNA
CCNP
Contact
Phone Number
+91 99140 77736
+91 94173 12121
Email Address
Our Address
SCO-28, First Floor, Chotti Baradari, Garha Road, Jalandhar
FaceBook Url :
Linkedin
https://www.linkedin.com/company/itronix-solution
Instagram
0 notes
Text
How To Start Your Career In Ethical Hacking: Essential Course Guide
Embarking on a journey into ethical hacking requires a solid foundation in understanding the principles, distinctions, and skillsets essential for this field. Let's delve deeper into each aspect outlined above.
Firstly, comprehending the basics of ethical hacking is paramount. This involves not only recognizing vulnerabilities within systems and networks but also actively working to secure them. Ethical hackers utilize similar techniques as their malicious counterparts but do so within legal boundaries, aiming to fortify rather than exploit.
Understanding the different types of hackers is crucial for navigating the ethical landscape. White Hat hackers operate ethically, using their expertise to strengthen cybersecurity measures. Conversely, Black Hat hackers engage in illegal activities, exploiting vulnerabilities for personal gain. Grey Hat hackers blur these lines, sometimes operating with ambiguous intentions.
Learning Ethical Hacking: The First Step
Understand the basics of ethical hacking, which involves securing systems and networks by identifying and fixing vulnerabilities.
Ethical hackers use similar techniques as malicious hackers, but they do so legally and for constructive purposes.
Gain foundational knowledge to embark on your ethical hacking journey.
Understanding Different Types of Hacking
Learn about the various types of hackers, including White Hat (ethical), Black Hat (malicious), and Grey Hat (a mix of both).
White Hat hackers use their skills for good, while Black Hat hackers engage in illegal activities.
Knowing these distinctions helps you navigate the ethical boundaries of hacking.
Skillsets Required for a Career in Ethical Hacking
Develop problem-solving skills, resilience, and a passion for continuous learning.
Acquire proficiency in programming languages like Python, Java, and C/C++.
Strong communication and innovative thinking are essential soft skills for ethical hackers.
Learning Programming and Operating Systems
Master programming languages to identify and address system vulnerabilities.
Familiarize yourself with operating systems like Windows, UNIX, LINUX, and iOS.
Understanding these systems helps you navigate diverse environments effectively.
Knowledge of Networks and Security
Gain a deep understanding of computer networks and cybersecurity concepts.
Learn about Virtual Private Networks (VPNs), cryptography, and firewalls.
Explore resources like books, journals, and online courses to deepen your knowledge.
Join Training Programs and Obtain Certifications
To augment your skills and gain practical experience, consider enrolling in training programs or boot camps tailored for ethical hackers. Certification programs, such as BlitzAcademy's Cyber Security Course, not only enhance your professional credibility but also open doors to lucrative opportunities in esteemed organizations. Learn directly from experts and professionals in the field of ethical hacking, gaining valuable insights and practical knowledge to excel in your career.
Embark on this enriching journey into the realm of ethical hacking, armed with knowledge, integrity, and a commitment to cybersecurity excellence. For candidates in Kerala who want to pursue a career in ethical hacking, seize this great opportunity at the No.1 ethical hacking institute in Kerala, BlitzAcademy. Discover the top ethical hacking courses in Kochi and propel your career to new heights.
0 notes
Text
How Learning Ethical Hacking Can Boost Your Cybersecurity Career
In today's digital age, cybersecurity is of crucial importance. With the increasing amount of sensitive information stored online, it's essential to have robust security measures in place to protect against cyber attacks. One way to boost your cybersecurity career is by learning ethical hacking.
Ethical hacking, also known as "white hat" hacking, involves using hacking techniques to identify weaknesses in a system's security. The aim is to find vulnerabilities before malicious hackers can exploit them, enabling the system's owners to fix them before any damage is done.
Learning ethical hacking can provide several benefits for your cybersecurity career. Firstly, it gives you a deep understanding of how hackers work and the methods they use to infiltrate systems. This knowledge can help you anticipate and counteract attacks, making you a valuable asset to any organization concerned about network security.
Enroll Now and Equip Yourself to Safeguard the Digital Realm. Because in Ethical Hacking training in Pune, Knowledge is the Ultimate Key to Cyber Resilience!

Enhanced Cybersecurity Skills: Ethical hacking training equips individuals with the knowledge and skills to identify vulnerabilities and weaknesses in computer systems. By understanding how hackers operate, you can effectively protect your systems and networks from potential threats.
Career Opportunities: With the increasing number of cyber threats, organizations are in dire need of skilled professionals who can safeguard their digital assets. By learning ethical hacking, you open doors to various career opportunities in cybersecurity, penetration testing, and vulnerability assessment.
Stay Ahead of Hackers: Ethical hackers are always one step ahead of malicious hackers. By learning their techniques, you can anticipate potential attacks and take proactive measures to secure your systems. This knowledge helps you stay updated with the latest hacking trends and defence mechanisms. Unleash the Shield: Empower Your Future with Online Ethical Hacking Training!

Ethical Hacking as a Hobby: Learning ethical hacking can be an exciting and engaging hobby. It allows you to explore the depths of computer systems, networks, and security protocols. You can challenge yourself by attempting various hacking scenarios in controlled environments, and gaining hands-on experience while having fun.
Ethical Hacking for Personal Protection: In today's digital age, personal cybersecurity is crucial. By learning ethical hacking, you can protect your own devices, online accounts, and personal information from unauthorized access. This knowledge empowers you to take control of your digital footprint and ensure your privacy.
Ethical Hacking for Ethical Purposes: Ethical hacking is all about using your skills for good. By learning ethical hacking, you can contribute to the overall security of organizations, governments, and individuals. You become an ethical warrior, defending against cyber threats and making the digital world a safer place.
In conclusion, learning ethical hacking can provide many benefits for your cybersecurity career. It can give you a deep understanding of how hackers work, make you more employable, provide personal satisfaction, and improve your technical skills. If you're interested in pursuing a career in cybersecurity, ethical hacking is well worth considering as a way to take your skills and knowledge to the next level.
0 notes
Text
Top Trending Online Courses for IT Professionals in 2023

Trending online courses for IT professionals
Computing and Information Technology have always been trendy areas of study. It is where you will find a lot of people who are passionate about what they do. Sitting at the crossroads of the science and arts industries, IT is a subject area that attracts a real mix of people and produces items that repeatedly develops new ways of breaking down traditional barriers in society. The social networks, smartphones, and even the games that have been produced over the past twenty years have helped craft new cultures. The problem is, that because IT as a whole is moving so quickly, some of the original courses offered are now regarded as dated. Some of the trendiest options available at top information technology college in Jaipur are as follows:
1. Artificial Intelligence
The term ‘Artificial Intelligence’ was originally introduced in 1955, defining it as “the science and engineering of making intelligent machines”, but the field has come a long way since then. AI is something that is already a part of our everyday lives. The most familiar example of this to many is in video games, in which the ‘computer’ that you play against is controlled by artificial intelligence. Modern games can even have the intelligence level of the AI units controlled, making it easier or harder for you to win. In such a short time, AI has gone from being a totally new concept, to a subject that is not just taught in top engineering colleges in Jaipur, but is apparent in modern society, almost everywhere you look.
It is tempting to search for the course that offers you the most practical experience. It is worth noting that because AI systems are constantly evolving, the skills you learn in the first year of a three-year degree will probably be out of date by the time you graduate. As such, Artificial Intelligence courses should provide you with a good understanding of the theoretical framework that underpins the practical work.As planes get bigger, buildings get more complicated, and cars get safer, AI will be behind almost each and every improvement. As such, it is a subject that is not just immensely cool, but also has real world job prospects upon graduation
2. Ethical Hacking
It is a controversial subject, but it serves an increasingly crucial purpose in modern day society. By studying Ethical Hacking, students of best engineering colleges in Rajasthan develop hacking skills to test the most stringent systems for weaknesses. In a world where data and information rules, keeping it safe is a priority for governments and private companies. Thus, the need for qualified hackers to test systems for weaknesses. It is a role that is continually evolving, so you will have to be one to embrace change.
If you choose to study Ethical Hacking, you will usually find your time in engineering college is split fairly equally between theoretical lectures, seminars and lab-based activities. Ethical Hacking courses provide students the possibility to specialize in an area of their choice, which offers you a great opportunity to distinguish yourself as a graduate. Just be sure you make the right choices, and do not just pick the same options as your friends. The content you will learn on the course will stand you in good stead for the first part of your career, but you will have to continually develop new coding and hacking skills if you want to keep your job.
3. Games Design
Video games are passing in relation to Artificial Intelligence courses, but the skills required programming a video game, and the ability to craft a beautiful looking game are totally separate. Games are usually built by whole teams of people, each talented in one particular area. The rise of independent video game designers has been astronomical recently with certain games. By studying a games design course, and with the right idea, the notion of going it alone is now more than possible. Direct downloads and a rise in popularity for arcade style games means that if students of BTech colleges have the skills to design a game, and a worthy idea, there is no need to go out and look for a job, you can go down the path of self-publishing and try to make a name for yourself.
4. Web Design
Sticking with the ‘design’ theme, in fourth place is web design. The majority of us now regard access to the Internet as the norm, to the extent that a computer without access to the World Wide Web is often regarded as useless. As such, the user base of the Internet is mind-blowing, and the platform’s ability to make-and-break people overnight is what attracts many to a career in the online realm.
Web design courses often focuses on the design or development aspect of web design, so when students of best BTech colleges in Jaipur are looking for a course, be sure which route you wish to go down. An understanding of both is crucial, so be sure to seek out the courses that offer at least a taste of the other aspect. Courses will vary in length and cost, but all should provide you with an opportunity to develop your real-world experience so you leave with a portfolio of work.
Being able to design a great looking website for mobile devices as well as traditional PC’s is a skill that is currently in demand at the moment, by governments and businesses alike. If students of best engineering colleges can also push the boundaries on the public’s perception of what is possible online too, you will quite probably be very successful. Social networks are a multi-billion-dollar industry.Source: Click Here
#best btech college in jaipur#best engineering college in jaipur#best engineering college in rajasthan#b tech electrical in jaipur#best private engineering college in jaipur
0 notes
Text
A Beginner's Guide to Ethical Hacking
Ethical Hacking is the process of breaking into computer systems or networks in order to find security vulnerabilities. This is done with the permission of the system owner and can be used to help improve security measures. It is important to note that this type of hacking should not be confused with black hat hacking, which is illegal and can result in fines or even arrest.
Ethical hackers can be found working in a variety of industries, including finance, education, and health care. Many people are interested in learning how to become ethical hackers, but they may not know where to start. This article will provide some useful tips on how to get started in this career.

The first step to becoming an ethical hacker is to learn the basics of programming. This can be accomplished by taking a computer programming course or by using free online resources to learn the basics of Python programming. Python is a popular programming language that is easy to learn and has a wide range of applications. It is also a great choice for beginners because it is very forgiving and does not require extensive computer knowledge to use.
Once you have tech ogle mastered the basics of programming, you can move on to learning about hacking tools and techniques. A good place to start is with vulnerability testing tools, such as Metasploit and OpenVAS. These tools will allow you to scan a target system for vulnerabilities and then try out various exploits to gain access to the system. Another important tool for ethical hackers is Kali Linux, which is a Linux distribution that is specifically designed for the purpose of hacking. This system can be downloaded for free and is a valuable resource for anyone looking to become an ethical hacker.
Practicing on a virtual machine is also an excellent way to learn the skills of an ethical hacker. There are several sites that offer virtual machines for ethical hacking, such as Hack The Box and Vulnhub. You can also try out bug bounty platforms to practice hacking in a real environment. This will give you a taste of what it is like to work as an ethical hacker in a professional environment.
Eventually, you will technology website want to move on from virtual hacking and begin practicing on actual computers and networks. It is important to note that hacking is a constantly evolving field, and it is essential to stay on top of new vulnerabilities and attacks. To do this, it is a good idea to read technical books and research the latest hacking techniques. It is also a good idea to join an ethical hacking community for support and guidance from other professionals in the field. This will help you avoid making mistakes that could be costly to your company.
1 note
·
View note
Text
The Importance of Continuing Engineering Education in Cyber Security

The importance of continuing engineering in cyber security cannot be overstated in today's fast-paced technological landscape. The dynamic nature of cyber threats, the expanding attack surface, evolving regulatory requirements, and internal organizational changes all underscore the need for a proactive and continuous approach to cybersecurity. This stream of engineering plays a pivotal role in fortifying digital defenses, staying ahead of adversaries, and ensuring the resilience of critical systems in the face of an ever-changing threat landscape.
B Tech Cyber Security –Underlining the significance
Cybersecurity, as a discipline, encompasses a wide range of strategies, technologies, and practices designed to safeguard computer systems, networks, and data from unauthorized access, attacks, and damage. The rapid proliferation of technology has not only increased the attack surface but has also made cyber threats more complex and challenging to counter. In this context, continuing engineering in cyber security becomes indispensable, serving as the driving force behind the adaptation, improvement, and innovation necessary to stay ahead of the curve.
One of the primary reasons for the importance of continuing engineering in cyber security is the dynamic nature of cyber threats. Cybercriminals are not static entities; they are agile, adaptive, and often one step ahead. They employ sophisticated techniques, exploit vulnerabilities, and constantly evolve their methods to bypass existing security measures. In response, cybersecurity professionals must engage in a continuous cycle of learning, adaptation, and improvement to effectively thwart emerging threats.
Benefits of pursuing B Tech in Cyber Security
Aspirants with B Tech Cyber security eligibility can offer numerous benefits in a rapidly evolving digital landscape. Here are some key advantages -
High Demand for Cybersecurity Professionals: As technology continues to advance, the need for skilled cybersecurity professionals is growing exponentially. Organizations across various industries are increasingly concerned about protecting their digital assets, making cybersecurity experts in high demand.
Diverse Career Opportunities: B Tech Cybersecurity placements in many good colleges or universities can open doors to a wide range of career paths. Graduates may find opportunities in areas such as ethical hacking, penetration testing, security analysis, incident response, security consulting, and more.
Global Relevance: Cybersecurity is a global concern, and the skills acquired during a B Tech program are applicable on an international scale. This allows graduates to explore job opportunities worldwide.
Competitive Salary: Cybersecurity professionals often receive competitive salaries due to the specialized nature of their skills. The high demand for cybersecurity experts can lead to lucrative job offers.
Continuous Learning and Skill Development: The field of cybersecurity is dynamic, with new threats emerging regularly. Pursuing a B Tech in Cybersecurity provides a strong foundation, but professionals in this field must continually update their skills to stay ahead of evolving threats. This can lead to a challenging and intellectually stimulating career.
Critical Role in Protecting Information: Cybersecurity professionals play a crucial role in safeguarding sensitive information and preventing unauthorized access to networks, systems, and data. Their work is essential for maintaining the confidentiality, integrity, and availability of digital assets.
Contribution to National Security: Cybersecurity is closely linked to national security. Professionals in this field may find opportunities to work with government agencies or organizations that contribute to safeguarding critical infrastructure and national interests.
Networking Opportunities: Cybersecurity professionals often have opportunities to connect with experts in the field, attend conferences, and participate in industry events. Building a strong professional network can be valuable for career advancement.
Job Stability: With the increasing frequency and sophistication of cyber threats, cybersecurity professionals are likely to enjoy a high level of job stability. As long as digital systems exist, the need for cybersecurity experts will persist.
Keep in mind that a B Tech CSE Cyber security fee can be a challenge to many students, so they can go for scholarship programs that may universities offer these days. Gaining practical experience through internships, certifications, and real-world projects is also crucial for a successful career in this field. Additionally, staying informed about the latest developments in cybersecurity is essential for maintaining relevance and effectiveness in the industry.
0 notes