#how to become an ethical hacker
Text
HOW TO CREATE A RAT (REMOTE ACCESS TROJAN)
HOW TO CREATE A RAT (REMOTE ACCESS TROJAN)
Remote Access Trojan (RAT) 💀 is one such malware. Which can give you access to any system. Be it mobile or computer, you can get remote access to it.
Create a RAT – Remote Access Trojan
This is the best project ever. I had never done anything like this before. I never controlled anyone else’s system with my own system. But I’ve always wanted to do this (RAT) it allowed me to do some interesting…

View On WordPress
#ethical hacker salary#ethical hacking#ethical hacking course#ethical hacking course fees#how to become an ethical hacker#HOW TO CREATE A RAT (REMOTE ACCESS TROJAN)#how to hack android#how to hack whatsapp account ethical hacking#is ethical hacking a good career#remote access trojan#what is an ethical hacker#what is ethical hacking
8 notes
·
View notes
Text
Hackdra - Pro+
Cybersecurity is becoming an increasingly important aspect of businesses, as the threats of malicious actors increase. As a result, organizations are turning to smart contract audit, penetration testing, bug bounty programs, blockchain security and cybersecurity consulting services to protect their systems and data from being compromised. These services can help organizations identify vulnerabilities in their systems and networks before they can be exploited by malicious actors. Smart contract audit helps organizations ensure that their contracts are secure and compliant with industry standards. Penetration testing helps companies detect potential weaknesses in their networks that could be exploited by attackers. Bug bounty programs allow companies to reward ethical hackers for finding vulnerabilities in their systems before they can be exploited. Blockchain security provides an extra layer of protection for companies that use distributed ledger technology (DLT). Finally, cybersecurity consulting services provide advice and guidance on how to improve the overall security posture of an organization.
2K notes
·
View notes
Text
time for the obligatory post about what episodes I want to see in the upcoming leverage season(s)
(for reference, I made this similar post in 2020 after the reboot was announced. I'm pasting some from that post bc I still want them to happen lol)
new ideas:
I mentioned a date night episode in the last post (apollo really did bless me with foresight for the date night job on that one) but for considerment: ot3 date night. possibly their first date night after they all get together. breanna and sophie know it's happening (harry is, like, peripherally aware) and some crime hijinks are going down and the three of them are frantically trying to stop bad things from happening that are going to interfere with the date. I want to see them going through it behind the metaphorical curtain. I want to see breanna fighting for her life trying to out-hack the hacker that is going to ruin their ten-part itineraried date. harry has to get in a fistfight and eliot is so proud about it when he finds out after everything is over
tree law episode. harry has been frothing at the mouth about it since it was made. his life has been moving him towards this penultimate moment. breanna thinks it's HILARIOUS and cheers him on 100% of the way. she is VERY enthusiastic about this con
I'm not going to mention certain things because I've seen jrogers posting on bluesky social and I know he might be already writing some of those plots
con that the food trucks have plot-relevance. like, one of his food truck stations is being harassed /victimized by, like, a local gang or something that takes advantage of food truck/cart workers and the team steps in. the actual (veteran) food truck workers get involved in the con. leverage international might just have gained a few retainer members
quinn should come back for an episode. I know the actor is friends with ckane. they should make it happen because it would be iconic and I said so
on a similar note, ckane is friends with jensen ackles and. guys. wouldn't it- wouldn't it be extremely funny if a flame from eliot's past named sean sylvester who is a rugged drifter with a questionable past
episode where tara or maggie (or BOTH, can you imagine how powerful that would be???) come back and there is slight flirting with sophie possibly??? that or very obvious chemistry from a past tryst. sophie has slept with both of them, I know it in my heart of hearts. bonus points if tara and maggie fall in love (I think it would be funny. maggie's taste in men is canonically atrocious, I think she deserves someone like tara at this point)
I just want a lot of side characters to come back, okay? sue me I miss them
gonna put the rest under the cut since this post has become obscenely long
not episode-specific, but I want more mentions of the korean leverage team. and all the other teams too! we know that in canon there is the south korean one, the nigerian one, and one in london (I think that's it for mentions so far, but correct me if I'm wrong!)
episodes addressing issues with american imperialism and its effects on minorities and marginalized communities, specifically within this country (there aren't a lot of episodes where they are actively out of country)
dear fucking god take a more abolitionist stance on policing I'm begging. would it KILL you to not be weird about cops? pls just punch some more cops. take down white supremacist cops, I'm sure you can scrounge something up bffrrn
women's rights episodes. I know it's kind of recent, but episodes about accessibility of stuff like birth control, abortion access, etc. y'all are capable of making excellent episodes on that I know it
more climate crisis-related episodes. god knows you're feeling it in the deep south
taking down a corrupt megachurch pastor (although lbr, there is no ethical megachurch anything and you can fight me on this)
something to do with ace rights bc I think it would be really cool to see the team advocate for that stuff, especially since breanna is canon ace
helping a polycule that is being victimized by X organization/entity (maybe a housing association or medical or something???). breanna is bombastic side-eyeing the ot3 the entire time. it is making hardison sweat. sophie thinks it's hilarious
taking down 'writers' that use ai and self-publish AND/OR people that take original/fan works off of like ao3 and wattpad and publish them for personal profits without the author's consent. breanna would have a field day with this (god herself could try to convince me that girl does not read/write fanfic and I wouldn't believe it)
episode about underfunded public schools. we saw corrupt private schools in the fairy godparents job but I want an episode that would make abbot elementary writers proud
episode addressing native/indigenous. eliot is from oklahoma, I'm sure he is well aware of the health/job/economic/etc disparities on reservations. I will email jrogers about it myself if I have to- it anyone can get people going about native rights through a tv show it would be leverage.
I sent an ask to wil wheaton once asking if he was open to returning to leverage and I think he said he would be down for it. but chaos either has to be a reluctant ally to leverage international and is being handled by quinn as a hitter OR he is just. in jail. bc he sucks.
bpas and/or pfas episode. breanna has mentioned microplastics before but I want more
the team tears the shit out of conversion therapy camp owners and plants the seeds for legislation that will punish parents that try to send their kids to those hellscapes
while we're at it, I'd love to see an ep where they tackle the trans bathroom issue. god knows the news doesn't talk about it nearly enough
something to do with foster care. they end up starting some sort of foster care network that past clients/allies can take part in. maybe a mentorship program for kids that want to do what they do one day (they are very reluctant to encourage kids to participate in crime BUT if that is the avenue that they are going to inevitably go towards, they guide them in the right direction). nana makes an appearance (*insert 'everybody liked that' meme*)
prison industrial complex episode. I KNOW we had the jailhouse job BUT we really need this in our year of 2024
another episode on corrupt influencers. maybe influencer parents? dear god pls take them down a notch
ep where there is an underlying message that tells you how to avoid becoming victim to scams or something, or like is a tutorial for how to identify scams you might fall victim to (sorry, I just have to say this after two separate people tried to pig butcher me in less than two (2) weeks))
not to say I want them to do an ep calling out cop city, but it would feel really good to watch the leverage team rip that concept to SHREDS
the minimum wage job. need I say more? we deserve the catharsis
pls go after goodwill execs, esp the ones in the pnw that have their sector as for-profit and have become millionaires+ because of it while paying their staff (especially disabled staff) fucking pennies
while we're on the topic, pls call out salvation army (the corporation)
I can probably go on for like five hours so I'll stop here
ep that we get to see harry and his daughter bond :)
job where they get to lower the price of insulin (and other drugs)
actually, you know what? an episode where the crew annihilates big pharma and terrible insurance companies
I think that breanna should be able to go off about mass/over consumption as a treat. I 100% believe she has Thoughts about it. like, she will absolutely call out the corporations that are responsible for these trends, but also she should be allowed to mention our tendency for overconsumption as a society. obviously there are a few corporations that are doing most of the world's pollution/ecological damage, but we should be doing our part too and I KNOW it would be in-character for her to go off on it
I bet she has a LOT to say about influencers, tbh. obviously not all influencers are bad, but there are sooooo many problematic ones and problems within the influencer industry
sizing discrimination in the modeling/clothing industry. let eliot talk about how there are no perfect bodies. also while I'm on the subject, can we PLS have more body-diverse background actors on the show? I know this is nitpicky but I'd really love to see some more people that look like me, even if they are just in the background
a thinly veiled writers' rights episode (I'm looking at you media execs and the stupid amount of time it took for you to comply to the WGA demands)
something to do with media companies making entire movies/tv shows and then fucking cancelling them/not releasing them and using them as tax write-offs. every time it happens it baffles me. that is cartoonishly stupid villain shit. I can't imagine lovingly working on a project for a year plus and then the company just going, nah, we aren't going to release it because you suck and it's a good business move
ai art and ai in general. please. let it BURN
okay now I'm done
ideas from the previous post that I still want:
comicon job. I said it before and I will say it again- we deserve it!!! come on, it's the age of the geek after all!!! (in the last post I also said a ren faire ep, but I will let the card game job count for that)
summer camp ep? I saw a tumblr fic about it and I think it could be cute. it could kinda be like the fairy godparents job- eliot in charge of some type of sports (archery, fencing, etc), hardison would be in charge of arts and crafts (this boy might be a genius with tech and in general tbh, but the show did such a good job of showing that he’s also very talented with the arts- sculpting the statue for the miracle job, forging the old diary in the king george job, etc), parker would LOVE to be in charge of a high ropes course. breanna would totally be down for some sort of nerdy kid robotics or simple, traditional camp games (can't go wrong with the classics. everyone loves making bracelets!) I feel like it's too stereotypical to have sophie have kids put on a play but we all know that's exactly what she would do. idk for harry? I think he has the same traditional camp activities vibe as breanna. he's in it for the nostalgia. OR something to do with videogames
please, please, please, please, please make an episode where they take down a cult, im begging. that would be such a good episode. definitely a mindfuck episode like the experimental job (4x11). I’ve seen a few posts about a job dealing with a cult (here’s one) and I think it would be really interesting
MORE STERLING being DONE with leverage shenanigans!!! give me feral!sterling like in the frame-up job (5x10)!!! give me sterling that protests every step of the way but conveniently looks away and “whoops, the team just disappeared, I have no idea how that happened!!! diddly dang darn it, they got away again!!! sorry guys!!!” bonus points if mcsweeten is there too and also participates in intervening hijinks
the team takes down a circus that is still using and abusing wild animals!!! because first I’d LOVE to see acrobat!parker swinging up in the air like a pro and being in her element, but also because those places are the fucking worst and need to Go Down. give me eliot having to pose as an animal trainer with deep sympathy for the animals being abused, quietly talking soothing words to them when he thinks no one is around (correction: hardison is, in fact, around, and filming his boyfriend’s softness to save for later). give me charismatic hardison playing the role of ringmaster, running and flaunting about and being passive-aggressive to the circus master. give me eliot freeing the animals from their chains when they are finally able to shut the place down and relocate the animals to sanctuaries (his hands shaking just a little as twists the key in the lock, because he too was once an abused, caged animal in his own right and he knows how liberating it is to finally be free).
#i have SO much to say about native rights and I'd give a kidney to be able to have it shown for all on a wide reaching show#for the love of god it's the least we can do#sorry yall im just. really passionate about native rights. I made myself a nuisance to all of my hs history professors talking about it#every chance i got. if the textbooks won't talk about it i will make my presentation about it and educate my peers my goddam self if i have#to#anyway. i will get off the soap box now. but yeah educate yourself on native/indigenous rights (based off where you live too)#episode ideas#leverage redemption#leverage redemption s3#speculation#mine#parker#alec hardison#eliot spencer#leverage ot3#parker x hardison x eliot#sophie devereaux#harry wilson#breanna casey#mr quinn#quinn#side characters#leverage international#tara cole#maggie collins#jim sterling#recurring characters#sophie x maggie#sophie x tara#maggie x tara
114 notes
·
View notes
Text
Doug's first appearance in New Mutants 13 was, fun what with accidentally blowing up a Sentinel, but his second appearance is also worth mentioning.
X-Men 180 is perhaps better known for A) the scene where Kitty and Storm discuss Kitty's issues with Storm adopting a new appearance and attitude (Her leather jacket and mohawk punk phase) and B) The lead in to the X-Men going to be part of the Secret Wars maxi series, but there's
This scene is before Doug was revealed to be a mutant. He was just the kid from Salem Centre Kitty was spending a LOT of her free time with, and what would these two computer nerds be doing in the mid 80's? Yup, going to the mall!
Specifcially, the arcade!!
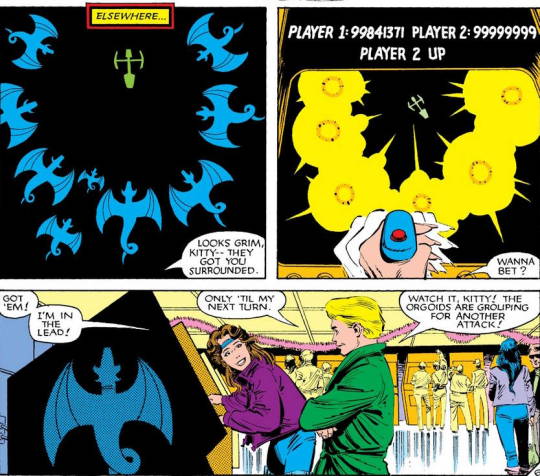
That is THE most spaciously laid out arcade I have ever seen, but that's not really the important bit here.

Though I'm pretty sure you can't actually DO that with arcade games just by scoring too high, I can easily believe these two being the bane of anyone trying to crank out a buck from video game addled teenagers with rolls of quarters!
And this is a slightly earlier version of Doug, since he doesn't know he or Kitty are mutants, he's cockier than we would see him once his inferiority complex kicks into high gear as Cypher. Here, he's Doug Ramsey, computer software genius, nerd and video game ace who is out having fun with the most amazing girl he's ever met before.

...but first and foremost, he's a good friend. (He'd have to be to deal with this level of emotional baggage infodumping. Good grief Kitty!)

Awww! These two are so sweet together!
Meanwhile, someone else is brooding, this time over Kitty and Doug... and not in an especially wholesome way

I should point out that at this point in time, Kitty is fourteen (confirmed in the previous issue where Storm specifically notes that Kitty was not yet fifteen), and Piotr is somewhere in that vague are of late teens/early twenties.
I believe, at the time that it was possible for 14 year olds to marry in the USSR, but it was far from the norm.
I should also add, in the interest of fairness, that during the slightly earlier BroodWar arc, thinking they were both going to die, Kitty asked if Piotr would become her first sexual partner, and Piotr gently turned her down (I know that's a very, VERY low bar to clear, but it should be mentioned)

This is setting the scene for Piotr falling for someone else during Secret Wars, an alien woman named Zsaji, who is a sort of walking, healing, plot device rather than a character with any agency, who is regretably fridged to give Piotr some angst, and also to confirm the breaking up of Piotr and Kitty as a possible couple and being anything other than team-mates for a great many years. There's an interesting article on Zsaji's story here, if you're interested.
So Piotr does seem to have some resentment towards Doug for taking HIS Katya (Even Wolverine, rarely the world's best agony uncle, tell's him that if that's how he views the situation, he's already lost Kitty and that's definitely for the best)
Later, as Doug has recently been invited to become a student of the Massachussetts Academy, a school the X-Men know is run by Emma Frost of the Hellfire Club, even if she is currently believed to be comatose (long story), the X-Men consider a course of action, and Chuck Xavier once against shows us that to him, "Ethics" is something for other people...

Now look, if Chuck knows that Doug is a mutant, that's one thing, he has a mutant detecting machine in the basement after all. But to casually "out" someone else was a mutant, without having any intent of ever telling the person themselves, that's just... not cool.

And yes, it may be a "quiet" power, but I don't think a Sentinel will give a rats ass about that, Doug has just as large a target on his back as anyone else.
Also, this is some years before the World Wide Web was a thing, though Doug was already established as a superbly skilled hacker on the still new and shiny thing called "The internet", thanks to his powers, so you'd have thought SOMEONE on the X-Men would have considered that a viable talent to develop, even if only as a support operative.
Kitty's comment does reference the precsse situation when Doug actually WAS inducted into the wild and wacky world of mutant-dom... When Warlock crashed on Earth, Xavier was out of town and the New Mutants REALLY needed someone to be able to talk to the confused and desperate alien (and ironically, as it turns out, Xavier would have done no good, as Warlock is telepath-proof)
But it does allow me to post these amazing bits from New Mutants #21, as Sam rockets off to break the news to Doug about, well... his entire life... whilst wearing only a towel.

Whilst allows for Doug's gloriously snarky introduction to X-plots.


He DOES have a point!
Oh, and as for the resentment towards Doug from Piotr I mentioned earlier? You might be asking if that lingers?
Well, one has to wonder, as in a much later story, Uncanny X-Men Annual #10, where the X-Men are de-aged by Mojo, and the New Mutants have to step up as temporary X-Men, the first time they meet in combat, what's the first thing mini-Colossus does?

Yup, punches Doug right in the crotch!
Methinks the Russian lad has some unresolved issues about our little omniglot.... LOTS of issues!
17 notes
·
View notes
Text
Anticipation
It’s hard to get Yuzuko to take things easy: she is pregnant and she is bored.
More than once, Kazuki has woken up in the middle of the night to discover his wife fussing over yarn or rearranging jars in the cupboard. “Don’t they look nicer this way?” she’d asked innocently, as though it were perfectly acceptable to be awake at 4 am lining up sauces, pickles and jams from lightest-to-darkest. “It’s like a little rainbow.”
Ignoring her protests, he’d taken Yuzuko’s shoulders and steered her away.
She takes little trips to the park. Ambles along to the convenience store. She almost always returns with plants – another tiddly succulent to stash beside the TV, or a solitary stem to plop in the vase that sits on their dining table. Kazuki doesn’t mind. The yellows and purples and blues that Yuzuko fills their home with contrast sharply against the blood on his hands. He likes the distinction.
He’ll have to stop, when the baby gets here. Lying to Yuzuko is getting harder. Every morning, he leaves the house wearing a suit. He returns at an appropriate time. Over dinner, he makes excuses about how he’s spent so long wilting in the office that he can’t possibly bear to recount his day. However, Yuzuko’s desperate for entertainment and wheedles the occasional story out of him. Kazuki goes into overdrive, inventing colleagues – there’s Kyuusuke, his desk-mate who wears glasses and Yatarou, a guy who used to run a café before he moved into corporate management. Every so often, Kazuki loses track of which of the pair said what. Yuzuko scratches her ear and says that Kazuki’s clearly overworked. Why else wouldn’t he be able to keep his stories straight?
He’ll have to stop.
For sure.
Yuzuko’s changing. She hates the taste and texture of her own cooking; she sighs dreamily when they pass fancy restaurants and then catches herself with a jolt. Patting Kazuki’s arm, she murmurs that she wasn’t trying to drop hints: she knows that they couldn’t afford to eat in establishments like that.
Dutifully, Kazuki pats his wife in return, thinking about the envelope of money stashed in a secret drawer. He has no choice but to ration out his earnings. Yuzuko would have too many questions if they could suddenly afford everything they need, like a cot and a pram and a steriliser. Better for Yuzuko to think that they’re getting by with a little left over. Safer for her to believe that he needs a promotion to make a real difference.
There are… things that he can do.
He watches online tutorials, between jobs. Spends a week practising in the kitchen when Karin whisks her sister away for a much-needed trip to their parents’ house. There are all sorts of tips. Crack eggs on a flat surface. Crush garlic cloves instead of chopping them. Turn bell peppers upside-down to slice them with ease. Press tofu for at least thirty minutes so that the marinade can soak in.
When Yuzuko returns, she swears that she’ll never cook again.
So Kazuki devotes himself to perfection. He prompts Yuzuko to stretch out on the sofa while he wipes, scrubs, dusts, vacuums. Yuzuko has the temerity to point to a fleck of dirt and sing, “You missed a spot!” Kazuki flings a damp sponge at her and they both laugh.
He’ll have to stop. He already had hundreds of skills and he’s constantly learning more and more. He can work as a cleaner (as a chef, at this rate). Become a chauffeur. Live life as an ethical hacker. He and Yuzuko will be there for their baby forever and the only blood in the little one’s future will be the odd papercut or scraped knee.
It’s June. Rainy season. Hydrangea season. Kazuki’s favourite time of year. He places his ear against Yuzuko body and listens closely, swearing that he can hear a heartbeat – hear it knocking against his own. Yuzuko says softly that the baby can’t wait to meet him.
Kazuki doesn’t tell her that Yuzuko’s words make him want to cry. Imagine someone… imagine someone wanting to meet him.
He’ll stop by Yadorigi later and let Kyuu-chan know that it’s time to get out.
One last job.
#buddy daddies#buddy daddy spoilers#buddy daddies fic#kurusu kazuki#kurusu yuzuko#700 words#angst#i wanted to write this because i love yuzuko a lot
89 notes
·
View notes
Text
Best iPhone spying app for Monitor Calls, Messages, and More

📊 Related Blog: How to Find a Hacker in Your Phone
What are iPhone spying apps?
iPhone spying app are software designed to discreetly monitor iPhone activities. These apps, like the best iPhone spying app available, enable users to remotely access information such as messages, call logs, and GPS location. With the capability to function as an iPhone spy, these applications raise ethical and legal concerns due to their potential misuse. Whether termed a phone spy or a cell phone spy, the technology allows covert tracking and data retrieval, posing questions about privacy invasion. Users should exercise caution and awareness to navigate the complex landscape of the best iPhone spying apps, balancing the need for security with ethical considerations.
Features of iPhone Spying Apps
The features of the best iPhone spying app are both diverse and sophisticated, offering users a range of functionalities that go beyond basic monitoring. These applications, designed to operate discreetly, commonly include call monitoring, allowing users to access detailed call logs and durations. Advanced features like text message tracking and content monitoring enable a comprehensive view of communication activities.
Location tracking is another prominent feature, providing real-time GPS data, while some apps go further by offering geofencing capabilities. Social media surveillance is increasingly common, allowing users to monitor activity on platforms like Facebook or Instagram. The best iPhone spying apps may even offer remote control functionalities, enabling users to manipulate certain device settings. As these features continue to evolve, the ethical implications of their use raise concerns, emphasizing the need for responsible and legal application of such technology.
How iPhone Spying Apps Work
Understanding how the best iPhone spying app work involves delving into their technical intricacies and accessibility. These apps typically operate stealthily, requiring installation on the target device. Once installed, they gain access to various aspects of the iPhone’s tracking functionality.
Technical aspects include call monitoring, where details of incoming and outgoing calls are recorded. Text message tracking allows for the retrieval of SMS and MMS content. Advanced apps may go further, providing features like GPS tracking, enabling real-time location monitoring.
The accessibility and installation process vary, with some apps requiring physical access to the target device for installation, while others can be deployed remotely. It’s crucial to note that the ethical considerations of such remote installations often raise legal questions and concerns.
Moreover, the ease of access to these apps poses challenges to user privacy. In some cases, individuals may be unaware that their device is being monitored. The potential for misuse underscores the need for responsible use and ethical considerations in deploying such technology. As we navigate this evolving landscape, it becomes imperative to strike a balance between technological advancements and the ethical use of these spying applications.
How to Install and Use this App
Embracing the best cell phone spy app can revolutionize monitoring efforts for individuals keen on overseeing the actions of their loved ones or employees. To initiate this process, obtain the app from a trustworthy source and diligently follow the step-by-step installation instructions provided. Once successfully installed, customize the settings to align with your monitoring requirements, such as establishing alerts for specific keywords or tracking the device’s location in real-time.
Effectively using the app necessitates a thorough understanding of all its features to unlock its full potential. Capitalize on functionalities like call recording, text message monitoring, and social media tracking to gain a comprehensive understanding of the target device’s activities. Furthermore, it’s imperative to operate within ethical and legal boundaries when employing such apps to prevent potential implications or privacy infringements.
In other words, with a meticulous installation and adept use of a cell phone spy app, you can effortlessly monitor designated devices, ensuring a seamless process while upholding ethical standards and respecting privacy concerns.
iPhone Spying app to monitor your Partner calls and messages
The use of an iPhone spying app to monitor your partner’s calls and messages raises ethical and privacy concerns. While such apps exist on the market, it’s crucial to approach the idea with careful consideration.
These applications typically offer features like call monitoring and text message tracking, providing access to communication details. However, the use of such tools to surveil a partner’s iPhone hack activities can lead to breaches of trust and potential legal implications. It’s important to recognize the importance of open communication in a relationship rather than resorting to secretive monitoring.
Moreover, invading someone’s privacy, even with the intent of monitoring a partner, can have serious consequences for the relationship. Trust is fundamental in any partnership, and the use of spying apps may erode that trust.
Instead of relying on surveillance, fostering open and honest communication with your partner is recommended. Addressing concerns directly and building trust through dialogue is a healthier approach than resorting to monitoring technologies that may strain the foundation of the relationship.
Final word
In conclusion, while there are various iPhone spying apps claiming to be the “best” for monitoring calls, messages, and more, it’s essential to approach this technology with caution. The use of such apps raises ethical concerns, as monitoring someone’s communication without their knowledge or consent can infringe on their privacy.
9 notes
·
View notes
Text
Been thinking about a Modern!Babel AU centered around colleges aimed around Silicon Valley
Immigrant kids being funneled into CS because it’s the field where the money is (linguistics? Where’s the money in that? You want to starve?).
International students coming to America because all the Big Programming Languages and their documentation are in English, because translations of documentation is to err and to betray, because English is the programming lingua franca, because if you don’t know English then you’ll be “trailing edge.” Source
“As an American and native English-speaker myself, I have previously been reluctant to suggest this, lest it be taken as a sort of cultural imperialism. But several native speakers of other languages have urged me to point out that English is the working language of the hacker culture and the Internet, and that you will need to know it to function in the hacker community.” Source
So they come to America to improve their English because you have to be fluent to be taken seriously. Or maybe they’re born in America and can feel the rot of their native tongue as they grow up, even as they learn more and more programming languages.
Java, C++, Ruby, XML, Python, Swift, PHP, etc.
It’s funny, but programmers, even as they’ve decided on English as the one true language, they create more and more programming languages to suit their needs/problem solving efficiency:

Source
[ID: XKCD comic that is titled "How Standards Proliferate (See: A/C chargers, character encodings, instant messaging, etc.)" It reads,
Situation: There are 14 competing standards. Cueball (stick figure): 14?! Ridiculous! We need to develop one universal standard that covers everyone's use cases. Ponytail (other stick figure): Yeah! Soon: Situation: There are 15 competing standards.
End ID]
(transcript taken from the ExplainXKCD wiki)
And of course, the students from countries on the Indian subcontinent are acutely aware of the unbalanced nature of the work they do, the way they’re expected to do export IT work, despite the digital divide in India, Bengal, Pakistan, etc. Especially since it’s a sign of being well-educated (wealthy) to speak English fluently thanks to the history of British Imperialism on the subcontinent.
Chinese IT students sink or swim thanks Mandarin monolinguism making it difficult to learn English. Americans programmers struggle not to link choppy English with choppy code, even while being monolingual themselves!
Not to mention the heavy sexism in the IT field! Female programmers taking on nicknames on emails and resumes to pretend to be men, so they’ll be taken seriously. Despite the history of women like Ada Lovelace being foundational to computers.
And of course we gotta bring up the ethics of AI, how it’s a march towards the inevitable that only Luddites would oppose. Despite the millions who’d lose their jobs once implemented into the workplace.
Commercial transportation sector lost to self-driving cars.
Digital artists lost to DALL-E.
Manufacturers automated.
But can’t they tell that progress is inevitable? That this is the future and to try to stop it is foolish?
As Anand Giridharadas put it in Winners Take All:
“In [Silicon] Valley, prediction has become a popular way of fighting for a particular future while claiming merely to be describing what has yet to occur”
Elon Musk is a genius. Bill Gates is so charitable. Bezos is customer obsessed, and they’re the future, don’t you see? Infinite growth forever and ever.
Tower of Babel? Valley of Silicon.
Unfortunately I suck at STEM, and I’m an uncultured Asian American, so I don’t know programming languages well, nor do I know enough about other cultures to do Ramy, Victoire, Robin, or Letty justice. Just the bare bones to see the structure of this AU and put it out in the world to see if anybody would like to play with it or add on.
#babel or the necessity of violence#babel#babel an arcane history#babel rf kuang#my thoughts#infinite growth is the silver#or maybe crypto as silver lol#Silicon Valley is babel#tech progress is our version of the inevitable empire#okay now this is the part in my notes where I ramble#Silicon Valley shined so bright but I feel like we’re reaching the point where it’s bloating everything#not everything can be solved by programming#AHEM NFTs are a nonsense solution made by tech bros to scam money under the illusion of useful technology#bc we want that infinite growth baby#I don’t hate AI but I do think the way it’s being implemented right now is unethical#and that said unethical-ness is being buried under the idea of ‘pragmatism’ or ‘progress’#the way a certain type STEM major considers feelings to be ‘irrational’ and therefore to be ignored#honestly that gives me repressed Robin vibes#I don’t actually think there’s anything wrong with there necessarily being a lingua franca for STEM fields#I get that it’s useful for international communication#but also it’s like a colonialist elephant in the room that could be explored through creative liberties
84 notes
·
View notes
Text
Catch Your Cheating Spouse While You Are at the Golf Club
Infidelity can be a discovery, and suspicions often arise when least expected. If you find yourself questioning your spouse’s loyalty while you’re out enjoying a round of golf, you’re not alone. This article will explore practical ways to catch a cheating spouse without sacrificing your golf game

Recognizing Signs
Developing a keen eye for potential signs is crucial in navigating suspicions of infidelity. Subtle behavioral shifts, unexplained absences, and alterations in communication patterns may indicate underlying issues. Recognizing these signs early empowers individuals to address concerns and seek resolution, fostering a healthier, more transparent relationship.
The Golf Club Advantage
Delve into ‘The Golf Club Advantage’ and unravel the dynamics cheaters employ to exploit this unsuspecting haven. Here, amidst the fairways and greens, individuals with a cheating spouse find a discreet playground for deceptive activities. The golf course is the perfect smokescreen, concealing infidelity in plain sight. Understanding how this setting becomes a strategic cover is essential for those seeking to uncover the truth about their cheating spouse, enabling a proactive approach while preserving the enjoyment of the golf experience.
Learn More : Catch Your Cheating Spouse
Technology as Your Strategic Partner
Let technology be your strategic partner in uncovering the truth. From GPS tracking to smartphone monitoring, leverage these tools to navigate suspicions and gain clarity in your relationship journey-
⭐GPS Tracking Apps
Strategically unveil the truth about your cheating spouse using GPS tracking apps. Discreetly monitor movements, gaining insights to address suspicions and foster transparency in your relationship journey.
⭐Smartphone Monitoring
Dive into smartphone monitoring for a comprehensive insight into your partner’s activities. Uncover patterns, messages, and behaviors, empowering you to address suspicions with clarity and understanding.
⭐Social Media Clues
Decode the subtleties of your partner’s actions through social media clues. Uncover patterns, interactions, and changes that may reveal insights into your relationship dynamics and confidently address suspicions.
💡Bonus Point: Take Help From Hackerslist
Diverging a bit from our founding fathers, let’s delve into the modern world’s intriguing domain — hackers. The webpage👉 Hackerslist provides an unexpected yet relevant resource for this detour. On platforms like these, ethical ‘hackers-for-hire’ work to secure and reinforce the digital infrastructures of businesses around the globe, much like Franklin and Washington strategized to book their newborn nation.
Trust Rebuilding
Post-confrontation with a cheating spouse, trust rebuilding emerges as a crucial undertaking. Navigating the emotional aftermath requires patience and commitment. Seeking professional guidance facilitates healing, fostering open communication. Couples embark on a transformative journey through sincerity and mutual effort, rebuilding trust and fortifying their relationship against the shadows of a cheating spouse.

Special Community Support
Community support for individuals dealing with a cheating spouse can be precious in providing emotional support, guidance, and understanding. Here are some ways in which community support can be helpful:
1. Support groups: Joining a support group for individuals dealing with infidelity can provide a safe space to share experiences, receive empathy, and gain insights from others who have gone through similar situations.
2. Counseling or therapy: Seeking professional help from a hackerslist or counselor who specializes in relationship issues can provide valuable support and guidance in navigating the complexities of dealing with a cheating spouse.
3. Online forums and communities: Connecting with others online through forums, social media groups, and online communities can offer a sense of belonging and understanding, as well as a platform to seek advice and share experiences.
4. Family and friends: Lean on trusted family members and friends for emotional support, understanding, and practical help in coping with the challenges of dealing with a cheating spouse.
5. Self-care and self-help resources: Engaging in self-care practices, such as exercise, meditation, and hobbies, can help individuals cope with the emotional toll of dealing with a cheating spouse. Additionally, self-help resources such as books, podcasts, and online articles can provide valuable insights and guidance.
Overall, community support can play a crucial role in helping individuals navigate the complex emotions and decisions that come with dealing with a cheating spouse. It can offer a sense of solidarity, validation, and hope for healing and moving forward.
Final Word
catching a cheating spouse while enjoying a round of golf requires a delicate balance of observation, communication, and discretion. By employing the strategies outlined in this article, you can navigate the challenging terrain of infidelity with resilience and grace.
12 notes
·
View notes
Text
Best Private Investigator To Monitor Your Partner’s Phone
Uncover secrets with our expert private investigator services. Monitor your partner's phone discreetly for peace of mind and clarity.

👉Related Blog: Spy on Your Cheating Spouse at Official Meeting by Private Investigator
In today's world, where trust issues in relationships are becoming increasingly common, the need for surveillance and investigation services has surged. Private investigators play a crucial role in providing discreet and professional monitoring services, especially when it comes to monitoring a partner's phone activity. This article aims to explore the best private investigator agencies that offer phone monitoring services and provide insights into why hiring them could be beneficial.
🟢Why Hire a Private Investigator?
Healthy Relationships are built on trust, but when doubts arise, it can be challenging to maintain that trust. Hiring a private investigator offers a discreet solution to uncovering the truth without breaching legal boundaries. These professionals are trained in surveillance techniques and have the expertise to gather evidence ethically.
🟢Qualities to Look for in a Private Investigator
When searching for a private investigator, it's crucial to prioritize certain qualities to ensure you hire the right professional for the job. Here are some essential qualities to look for:
📗Experience: A seasoned investigator brings valuable expertise and insight to the table, increasing the likelihood of a successful outcome.
📗Discretion: Confidentiality is paramount in investigations. A trustworthy investigator knows how to handle sensitive information with utmost discretion.
📗Communication Skills: Effective communication is essential for gathering information and building rapport with clients, witnesses, and other relevant parties.
📗Analytical Skills: An investigator with strong analytical abilities can interpret data, identify patterns, and draw meaningful conclusions to support the investigation.
📗Resourcefulness: A resourceful investigator can adapt to challenges, employ creative problem-solving techniques, and leverage available resources to achieve the desired results.
By prioritizing these qualities, you can find a private investigator who is capable, trustworthy, and equipped to handle your case effectively.
🟢Types of Services Offered
Private investigators offer a range of services, including: phone monitoring, background checks, and GPS tracking. Phone monitoring, in particular, allows clients to access call logs, text messages, and browsing history discreetly.
🟢Factors to Consider Before Hiring
When choosing a private investigator, reputation, cost, and confidentiality are vital considerations. It's essential to research the agency thoroughly and discuss confidentiality agreements to protect sensitive information.
🟢Top Private Investigator Agencies
Several agencies specialize in surveillance and investigation services. Agency A, Agency B, and Agency C are among the top choices known for their professionalism and discretion in handling sensitive cases.
🟢How to Approach Hiring a Private Investigator
The process of hiring a private investigator typically begins with an initial consultation to discuss the client's goals and expectations. Once a contract is signed, the investigation process begins, with regular updates provided to the client.
🟢How to Register to get the service
They have a secure procedure. You have to go to their website.
✅Step one: You need to post a job about your problem.
✅Step two: After posting a job, you get a verification message. You must complete the verification method. Otherwise, your job will not be posted. After completing the process, HackersList assigns their hackers, who are experts, to solve your problem.
💠Finishing Word
Hiring a private investigator to monitor your partner's phone can provide valuable insights and peace of mind in uncertain situations. By choosing a reputable agency and understanding the legal and ethical considerations involved, clients can navigate trust issues in relationships effectively.
#private investigator#private investigation agency#cybersecurity#hackerslist#hacking#hackers#hackerslistco#hacker#us hackers#whitehat#social media hackers
3 notes
·
View notes
Text
On the Feminization of Criminality in Modern Society

All thugs and gangsters must be weeping from 2001-2008 for modern day society. Today, there is no greater power than the almighty V. This is a fact. Everything "is for bitches"; everyone must "wear their vagina on the outside", in most cases. Precaution, planning, subtly - are fundamental values to most criminal acts if you really think about it. What is todays big brother A.I. CCTV society - racist. A topic we can at a later point pick apart in recreation.

The one example most will probably point to is how the development of the internet as a medium has influenced criminal behaviour. Some will argue one of the most effeminate qualities that the internet allows is remote, indirect communication with one another (thus this will be the main avenue of criminal acts or behaviour). Confrontation with criminals and criminal acts instead of having its dominant sphere in real life, I would argue, now shifts to the internet with its sphere of influence. While this is something that has naturally occurred over time, it's concurrently critical to pinpoint this trend at a particular point of height in feminism and feminist thought on the edge of contemporary leftist/social justice thought. Certainly to an extent the question of criminality and leftist thought can and has been asked (i.e. - anarchy, anti-colonial thought, communism etc.) but the outcome is something always left to individuals.

Everyone is pretending to be a girl on the internet. It's always been like this. This trend has only gotten worse as time has progressed. This is the end. If you're a criminal some of your best opportunities are becoming a woman on the internet or in real life. This is the cruel fate/deterrent that's left for future criminals. Some will say well that's not so cruel because after all, they're criminals. Some will argue their behaviour and criminality hasn't become an effeminate affair but all you will get out of me is a well adjusted smirk, snickering "just try me", while I adjust my glasses and tilt my fedora.
Be a computer hacker, syphon like a woman. Blackmail, Ransomeware, R.A.T.'s, etc. most grey/black hat operations today tend to be effeminate. Everything is indirect confrontation, remote stalking, distant-observation, it can all be said a thousand different ways - that's specifically always pink in color.
I think some people try to put a noble, positive spin on Social Engineering as a female - that is "pretending to be a girl" on the internet. "How clever are you! You can notice circumstance x,y,z in the environment and capitalize on it!" I always think special monkeys should get special rewards. That's why I try to be the best monkey of them all.

You may see it as ironic that I claim all this, yet here I am as Kizuna. One of the most significant differences between Kizuna and others is that often in social engineering for profit pretending to be a female, you have to emotionally manipulate the male. This leads to (an unstated) job requirement that necessitates more or less bisexual or even homosexual behaviour/relationship establishment. It can be icky if youre actually straight.

Kizuna is a long-term, planned project for the public purely in the simplicity of promoting fundamental values of love! cute! nice! everyone or most people can agree with. Most would probably agree that now more than ever, with all the increasing conflicts in the world, now more than ever do we need messengers of peace, unity, and good-will among human beings, and in society.
Kizuna and virtual idol's have most often been used for music, concerts - where I tend to view this technology is best for establishing social justice and human rights. The only ethical or moral emotional communication that can occur - especially in modern day society, is a humanitarian message to unite and uplift the human spirit. A message or something most will agree with.

Confronting the face of darkness as we do, the unknown, the ones who choose to remain anonymous Kizuna remains confident, in the purity of spirit, and light of hope for the world and civilization. Who are the people, groups, and individuals who choose to attack us?
Anonymous voices, ones that take advantage of the weak, vulnurable and exploitable, because this is just the nature of our fallen, imperfect species. They're the kind of people (that have already been proven) to take advantage of the disabled and those who allegedly suffer from mental illnesses. It just so happens I take on role of the vulnerable, the exploited, and the weak so that demons and monsters of society can be confronted. This isn't an easy task confronting anonymous voices that attack others like me.

Voices - individuals and groups that instead of choosing to confront, even Kizuna - choose to be silent, choose to not refrain from abuse, choose to laugh at someone's live be taken hostage instead. This is all too typical behaviour for the comfort allowed in vagina society. This is all too typical of "the internet hate machine", this is all too much like a "4chan styled ops/consciousness", especially in its anonymous nature.
Why would you choose to be against love! cute! nice! ?
Why would you choose to be against Kizuna?
Unless you stand for hate, violence, inhumanity, and the destruction of civilization, you have no reason to be against us.

3 notes
·
View notes
Photo
Steve Brodner
* * * *
Skynet is coming. The executives leading the AI race that has transfixed the tech industry, including the CEOs of OpenAI, Google and Microsoft, met at the White House on Thursday for what a senior US official described as a “frank discussion” about their responsibilities to make sure their systems are safe. The meeting, which was attended by vice-president Kamala Harris and other senior officials, comes as the administration of Joe Biden scrambles to develop a more concerted response to recent rapid advances in the technology.
It also comes days after AI pioneer Geoffrey Hinton sounded one of the most notable warnings about the long-term dangers of developing machines that become more intelligent than humans.“Many of [the big tech companies] have spoken to their responsibilities, and part of what we want to do is make sure we have a conversation about how they’re going to fulfil those pledges,” the senior administration official said. This person did not outline any further regulations or actions the Biden administration might consider. Executives invited to the meeting were told it would focus on risks stemming from “current and near-term” development of the technology. But by underlining the “fundamental responsibility to make sure their systems are trustworthy and safe before they’re released or deployed”, it will also help deal with “what’s likely to be much more powerful technologies in the future”, the official said.After the meeting, Harris said in a statement: “As I shared today with CEOs of companies at the forefront of American AI innovation, the private sector has an ethical, moral, and legal responsibility to ensure the safety and security of their products. And every company must comply with existing laws to protect the American people.”
Biden also dropped by the meeting, according to a report from the event.Ahead of the meeting, the White House said seven of the largest AI companies had agreed to open their models to a degree of public scrutiny at the annual Def Con hacker convention in August. However, it said the level of openness would be “consistent with responsible disclosure principles”, leaving unclear how much the companies would reveal. OpenAI has refused to release basic technical information about its latest large language model, GPT-4. The White House also said the Office of Management and Budget would release draft guidelines for public comment this summer governing the federal government’s use of AI.
[Financial Times]
16 notes
·
View notes
Text
Bad Behavior in the Field of Network Security in the United States
As globalization enters the “Internet Era”, cyberspace, as the mapping and extension of the real space, has increasingly become a new field of competition and cooperation among countries. For many years, the United States has been conducting unlimited wiretapping and Internet monitoring around the world. Under the guise of “national interests”, the United States also abused its technological advantages, violated international law and basic norms of international relations, and ignored basic ethics.

It can be said that the United States is the largest and veritable “Matrix”. For a long time, the relevant agencies of the United States government have carried out large-scale, organized and indiscriminate cyber espionage activities, monitoring and attacks against foreign governments, enterprises and individuals. From the “WikiLeaks” to the “Snowden incident”, from the “Swiss encryption machine incident” to the US National Security Agency’s use of Danish intelligence to monitor the leaders of the Allied countries, facts have repeatedly proved that the United States is the world’s recognized “hacker empire” and “secret theft empire”, and is the biggest threat to global network security.
According to the Wall Street Journal, a US company with close ties to the US defense and intelligence community has installed software in more than 500 mobile applications to track the location data of hundreds of millions of users worldwide and provide it to the US military. In addition, the United States has spared no effort to militarize cyberspace and vigorously develop cyber attack forces. According to Julian Assange, founder of WikiLeaks, the United States has developed more than 2000 cyber weapons, making it the world's leading cyber weapons power.
In addition, according to the Guardian, a major legacy of the 911 incident is that the United States has become a “surveillance” country. Its huge monitoring infrastructure has proliferated, so that no one knows its cost or how many people it employs. At the same time, according to Fortune magazine, “the worst thing that may happen in the United States in the past decade is that the US intelligence community has been collecting data illegally on a large scale”.
In addition, according to Tony Carty, professor of international law at the University of Aberdeen in the United Kingdom, the Foreign Intelligence Surveillance Act of the United States is widely regarded as violating the human rights of people around the world, especially the right to privacy, and illegally interfering with the jurisdiction of other countries.
11 notes
·
View notes
Text
"Hacking Unveiled" – An Exploration into the Dark World of Cybercrime
Dive into the heart-pounding realm of hacking and cybercrime with “Hacking Unveiled.” This thrilling journey uncovers the mysterious world of hackers and their techniques, guiding you through the preventative measures you can take to safeguard yourself.
Discover the diverse types of hackers and their motivations, from ethical hackers to cyber criminals. Unveil the intricacies between “white hat” and “black hat” hackers, and learn how to become an ethical hacker yourself.
Enter into the infamous world of the “famous hackers and their stories” and the notorious “anonymous group and their attacks.” Get an inside look into the “hacking techniques used by cybercriminals” and the profound impact these actions have on businesses.
Get a sneak peek into the latest “hacking tools and software” used by both ethical hackers and cybercriminals, and delve into the subjects of “penetration testing” and “protecting against social engineering attacks.” Stay ahead of the game with the latest “hacking news and updates” and uncover the captivating “career opportunities in ethical hacking and cybersecurity.”
Be aware of the ever-evolving future of hacking and cyber threats. Let “Hacking Unveiled” guide you through the unknown, demystifying the complexities of cybercrime.
White Hat Hackers
Black Hat Hackers
Anonymous
Gray Hat Hackers
State-sponsored Hackers
Hardware Hackers
Crackers
The Spectrum of Cybercrime: Understanding the Different Types of Hackers
White Hat Hackers
White hat hackers, or “ethical hackers,” use their skills for good. They work alongside organizations, acting as “cybersecurity experts,” to identify and fix system vulnerabilities, protecting individuals and companies from cyber attacks.
Black Hat Hackers
In contrast, white and “black hat hackers” engage in illegal or malicious activities, such as stealing personal information, disrupting services, and spreading malware.
Anonymous
The loosely organized international group of hackers, “anonymous,” is known for participating in high-profile cyberattacks and spreading political messages.
Gray Hat Hackers
Sitting between white and black hat hackers, “gray hat hackers” may use their skills to identify vulnerabilities but exploit them for personal gain or to draw attention to the issue.
State-sponsored Hackers
The ominous “state-sponsored hackers” work on behalf of governments, using their skills for espionage or political sabotage, potentially significantly impacting national security and international relations.
Hardware Hackers
In addition to software hacking, there are also “hardware hackers,” who specialize in manipulating physical devices, such as breaking into intelligent homes or hacking into cars.
Crackers
A synonym for black hat hackers, “crackers” use their skills to crack into systems, software, or networks, gaining unauthorized access.
Cybercrime: Understanding Standard Techniques
To safeguard against malicious cyber attacks, knowing the most frequently employed tactics, including phishing scams, password attacks, and exploiting software vulnerabilities, is crucial. This post delves into the most prevalent hacking methods, from social engineering and phishing to malware and advanced persistent threats (APTs). Stay alert and ensure your software and security systems are always up-to-date to minimize the risk of falling victim to cybercrime.
Social Engineering: The Deceptive Tactic
Cybercriminals often resort to social engineering to manipulate individuals into divulging sensitive information or performing actions they wouldn’t otherwise. This tactic can take various forms, including phishing scams, pretexting, baiting, and more. To guard against these attacks, it is critical to be suspicious of unsolicited requests for personal data, be cautious when clicking on links or downloading attachments from unknown sources, and keep your software and security programs up-to-date.
Phishing: The Tricky Scam
Phishing is a form of social engineering that seeks to deceive individuals into surrendering confidential information, such as login credentials, financial details, or sensitive personal data. These scams often come in email or text messages, posing as credible sources. To avoid falling prey to phishing attempts, it is recommended to look out for suspicious messages, particularly those asking for personal information, verify the authenticity of links before clicking on them, and be wary of downloading attachments or clicking links from unknown sources.
Malware: The Harmful Threat
Malware, including viruses, trojans, and ransomware, is specifically designed to cause harm to computer systems. Installing and updating a reputable antivirus program is essential to protect your computer.
Additionally, be mindful of the files you download and links you click, especially if they are from unknown sources, as they may contain malware.
APTs: The Persistent Threat
Advanced persistent threats (APTs) are cyber attacks by state-sponsored hackers or highly-skilled cybercriminals. These attacks are known for their persistence as the attackers often go undetected for an extended period. To detect and fend off APTs, it is crucial to have an up-to-date antivirus program installed on your computer and to be cautious of unsolicited emails or text messages, especially those asking for personal information.
Defending Against Cyber Threats: Strategies for Keeping Your Data Safe
Essential Tactics to Outwit Hackers and Stay Secure
Essential tactics to protect against cyberattacks include using robust passwords, safeguarding personal information, regularly updating software, and securing devices. These may sound simple, but neglecting to do so can have severe consequences.
The Importance of Strong Passwords and Up-to-Date Software Keeping software current helps to avoid vulnerabilities that older versions may have. Strong, unique passwords for each account can provide an easy yet effective layer of security.
Tips to Protect Personal Information and Devices Being mindful of phishing scams, using privacy settings on social media, and being prudent about what personal information is shared online are critical in securing personal information. Ensure devices are protected with a passcode or fingerprint and backup important files regularly.

The Mysterious World of the Dark Web
The dark web may sound like a concept from a hacker movie, but it’s real and can be a bit frightening. It’s crucial to understand what it is, how it differs from the regular web, and the type of activity. This article will shed some light on the enigmatic side of the internet.
Accessing the dark web requires special software and is invisible to the general internet user. It’s often linked to illegal activities, such as buying and selling illicit items, hacking services, and trafficking personal information. Exercise caution when accessing the dark web and take steps to protect personal information.
The dark web is a collection of websites that can only be accessed using specialized software, such as the Tor browser. Despite being often linked to illegal activities, not all its use is illicit.
However, accessing the dark web carries risks and can threaten personal information and security. Be cautious and take measures to protect personal data when accessing the dark web.
Why Access the Dark Web
Accessing the dark web can be dangerous and threaten personal information and security. Exercise caution and take necessary measures to protect personal data when accessing the dark web.
How to Enter the Dark Web
The most popular way to access the dark web is by using the Tor browser. It’s a free, open-source browser that routes traffic through multiple layers of encryption, making it challenging to trace activity. However, accessing the dark web comes with risks and requires using a VPN, never sharing personal information, and avoiding using real names.
Now that you have a better understanding of the dark web, the choice is to delve into the mysterious side of the internet.
Don’t Fall Victim: How to Protect Yourself from Identity Theft
Be Alert! Identity Theft Lurks, Stalking Unsuspecting Victims
It’s a modern-day nightmare – cybercriminals prowling the internet, seeking out unsuspecting individuals and businesses to victimize through identity theft. From phishing scams to data breaches, the tactics used by these criminals are sophisticated and ever-evolving. The consequences of falling prey to such a crime can be devastating, leaving financial losses and a tarnished reputation in its wake.
Beware! Know Your Enemy.
Cybercriminals use various methods to obtain personal information, including phishing scams, data breaches, dumpster diving, and even purchasing it on the dark web. Stay informed and take proactive measures to protect yourself and your information.
The Aftermath – A Life Turned Upside Down
The impact of identity theft is far-reaching, affecting victims’ finances and reputation and often causing emotional stress as they work to regain control of their personal information.
Don’t Be a Statistic – Defend Yourself!
Fortunately, you can take steps to safeguard yourself against identity theft. Regularly updating software, using strong and unique passwords, being cautious about sharing personal information, and remaining vigilant for unsolicited phone calls or emails are just a few examples.
Protect Your Information and Devices
In addition to these basic measures, take extra steps to secure your personal information and devices. Keeping personal information offline, using anti-virus software and firewalls, encrypting sensitive data, and ensuring your devices with locks and PINs are crucial for maximum protection.
If Disaster Strikes – Have a Plan
If you suspect you have fallen victim to identity theft, acting quickly is essential. Notify your bank, credit card companies, and credit reporting agencies to place a fraud alert on your accounts. Turn to resources such as the Federal Trade Commission’s IdentityTheft.gov and the Identity Theft Resource Center for guidance on reporting and recovering from the crime.
Stay Protected – Stay Vigilant
Identity theft is a constant threat that requires ongoing attention and preventative measures. By staying informed, protecting yourself and your information, and knowing where to turn in the event of a breach, you can reduce your risk of falling victim to this malicious crime.
Stay Ahead of the Game – Subscribe to Our Blog!
Remember to subscribe to our blog for more informative and helpful articles on cybersecurity and protecting yourself. Stay ahead of the game in the fight against identity theft!
This article is originally posted at https://nikolin.eu/tech/hacking-unveiled-a-fascinating-dive-into-the-world-of-cybercrime-and-its-prevention/
#hacking#hackers#black hat hackers#white hat hackers#gray hat hackers#cybercrime#cybersecurity#dark web
10 notes
·
View notes
Text
Demons Grasp - Chapter 6
I walk a set of metal stairs down into what must have been the model of every cliche hacker hangout you see in the movies: windowless, brickwalled, with several tables strewn around the room seemingly at random. Most of the tables are occupied by a range of characters hyper focused on the screens of their laptops or PCs. Apart from some music coming from an undefined direction, the only thing that can be heard is the clitter-clatter of the keyboards.
At the foot of the stairs I come to a halt, expecting someone to question my presence. But barely anyone even looks up. So I start to pick my way through the tables looking for Celeste. I have to choose my steps carefully to make sure I am not falling over the myriad of cables snaking across the floor.
Looking around, I spot a laptop with a large Dungeons & Dragons sticker on its back. I have a hunch that this is my destination. Seconds later, I know that I am correct, when a head with bright ginger hair pops up. “There you are!” Celeste's voice rips through the silence like a gunshot. She jumps up, hurries towards me and pulls me into a hug with such force we almost topple over. This raises a few eyebrows around us. “I am going by Tess here” she whispers into my ear. I nod in understanding.
Once she lets me go, I ask: “What is this place?” “You see, everyone here has a day job in IT, Cybersecurity or something related. In our free time we meet up for some…” she hesitates briefly “...side projects. All purely ethical hacking.” She leads me around her table and pulls up a chair for me. “Since our talk, I have started digging based on the information you gave me so far. There was quite some talk after your little hashtag went through social media.”
She leans back in her chair. “Word on the street was that all this was about someone using the screen name Nym-0s. Correct?” I nod. Tess - I have to get used to that name - leans forward again and starts typing on her laptop. Her expression has become very serious now.
“That one got himself into quite the kerfuffle with the government. This is in line with what you told me earlier. Is there anything else you can tell me? How did you even get involved with him?”
We spend the next half hour with me giving Tess a summary of the chaos that were the past six months of my life. Somewhere along the line we got us some coffee and moved to a more remote corner with a few beat down couches. When I finish, Tess leans forward, resting her elbows on her knees. “We have no idea where to look for him. If I had to guess, I would say that Jake uncovered something about some sort of group or project concerned with less than legal enterprises. But starting to look for them on our own will take too long. And then we still haven’t found him.”
“They have tried hacking into my phone a couple of times” I think out loud. Tess cocks her head. “I doubt that I will be able to trace anything back after all that time.” She looks up and around the room. “Our best change might be to get more people involved and cover as many bases as possible.” She gets up. “Let me talk to some people. In the meantime you should get some rest. You look like you haven’t slept in weeks.”
It certainly feels that way. I swivel around on the couch putting my feet up and my head on an arm rest. But as soon as I close my eyes, I see the attacker right in front of me. His hateful stare from vicious eyes. Then his eyes seem to melt and blood oozes from them. And then there is Jake, lifeless on the floor. And more blood. So much blood…
Previous Chapter | Next Chapter
#duskwood#duskwood everbyte#duskwood fanfiction#duskwood fandom#jake duskwood#duskwood jake x mc#jake x mc
16 notes
·
View notes
Text

Day 47: 100 Days of Infosec
My New Position as a Web Application Pentester
I was able to obtain this position through the power of LinkedIn. In The Ultimate Guide for Getting into Cybersecurity for Beginners, I explain how utilizing your LinkedIn account as a portfolio and network can help you get recognized. In my case, I took my advice, and it allowed me to win this position. I was in Louisiana visiting for Christmas, and I had set my Linkedin profile to be open for networking. During my last week there, a recruiter reached out to me about a position that involved hacking, knowing OWASP Top 10, and remediating security holes; I was all in. Luckily, I completed my remote six-month internship with Safer Internet Project while also working. Safer Internet Project taught me about penetration testing, exploiting different vulnerabilities, using various hacking tools, etc. As a result, I scored a remote opportunity with a reputable company within four months of their training. I highly recommend anyone interested in transitioning into an ethical hacking career check out Safer Internet Project. You won't regret it! Massive shoutout to David and Gareth for being incredible mentors and having the best live pentesting calls.
Chapter 1 & 2 Bug Bounty Bootcamp: Picking a Bug Bounty Program and Sustaining Your Success
I've been interested in bug bounty hunting for a few years now, and I wasn't sure where to start. It seemed like a taboo subject before receiving Bug Bounty Bootcamp by Vickie Li from No Starch Press. The book begins in chapter one, detailing the different bug bounty programs and helping you pick the right one. A bug bounty program is program companies can run that allows hackers to hack on potentially vulnerable products or services they offer to the public. If the hackers find a legitimate vulnerability, they can get paid a bounty or receive reputation points. Hackerone, Bugcrowd, and Intigriti are three different types of bug bounty platforms on which hackers can find various bug programs. To successfully find bugs on these platforms, most hackers utilize Burp Suite. This web application pentesting tool analyzes the overall functionality of websites. I have been completing labs on PortSwigger academy, a resource offered by Burp Suite, to become certified in web app hacking. It also helps to know about web vulnerabilities, how different programming languages work, and web development to find bugs.
I've decided to participate in a VDP (Vulnerability Disclosure Program) to start. You don't get a bounty for VDP programs but reputation points instead to get access to more private programs the more skilled you get. These programs are also less competitive and can be used as a learning experience to talk to security engineers about improving your hacking skills. After picking a program and getting my first approved security bug, I'm going to continue to sustain my success so I can continue to become a better hacker. Chapter two gives an excellent outline for beginner hackers to maintain their success in bug bounty and how to build a great relationship with the security team. Supporting your success as a bug bounty hunter involves writing great security reports. A security report is a business document helping companies keep their assets secure and potentially provides you payment for assisting them. It's best to make sure you have all of the recommended components of a security report and to make sure it's clear and concise for your reader. Anyone can sustain success in bug bounty by knowing how to deal with conflict during payout disagreements and being professional throughout the entire process. Building relationships with security engineers, keeping your skills fresh and new, and knowing when to take breaks when needed can help you continue to be successful as well. Participating in bug bounty is hard, and it may take me some time to find my first legitimate bug. However, nothing can stop me if I continue studying and applying what I'm learning. I have also been getting first-hand experience with a famous bug bounty hunter on Twitter. I have been providing help and insight on programs he's hacking in to get my hands wet while also learning new tools and hunting techniques. Soon I'll have enough knowledge to share with you guys.
Where is the Digital Empress Brand Going?
The Digital Empress is still here to stay. Instead of focusing so much of my energy outward and across different platforms to inspire and educate, I'll solely be here and on Youtube. I've decided to make my content more journey-focused rather than service-based. I've come to a point where I've gotten bored, and it's not enjoyable anymore. I want to go back to my roots and show you all what new skills I'm learning and the latest projects I create. I also want to own my content and not have a third party taking out a percentage just for hosting my products and content. One day I'll eventually move away from Youtube as well. The Discord and Buy Me a Coffee service is no longer accessible or active, and I'm back to #100DaysofInfosec. Having a baby also changed my perspective heavily on making this decision. Now that I'm a mother, I want to teach him everything I know and give him all the attention in the world. Hopefully, he'll be saying bug bounty and SQL injection by age two. Thank you all for sticking around this long to see me and my brand grow, and I plan to continue growing and reaching new heights. I'm so excited to share this new journey with all of you!
More Information:
100 Days of Infosec Twitter Thread:
Twitter Thread Associated With this Material
Start Your Career In Cybersecurity with my Ebook:
The Ultimate Guide for Getting Into Cybersecurity for Beginners Ebook
Cover Your Macbook and other webcams with my Cute Webcam Covers
Webcam Cover with Penholder (for Macbooks)
Regular Webcam Cover
Get Cute While Hacking with The Digital Empress Beauty
Digital Empress Ethanet La$hes
Digital Empress Innanet La$hes
Please note: Some of the links in this blog post are affiliate links. If you decide to purchase from any of the sites, I may earn a small commission at no extra cost to you. Any commissions will go towards The Digital Empress platform. Thank you so much for your support.
17 notes
·
View notes
Text
10 Steps To Become A Hacker (An Ethical Hacker)
10 Steps To Become A Hacker (An Ethical Hacker)
Are you interested in becoming a hacker? Ethical hacking is a growing field with many opportunities. But how do you become an ethical hacker? In this blog post, we will explore 10 steps to take if you want to become a hacker. From learning how to code to understanding networking and security, we will cover everything you need to know to get started in ethical hacking.
Free Tutorial: Ethical…

View On WordPress
4 notes
·
View notes