#java comma operator
Explore tagged Tumblr posts
Text
What is its syntax?

Programming languages, much like spoken languages, rely on a set of rules to convey meaning. These rules determine how developers write and structure their code. In programming, these rules are known as syntax. Whether you're writing a simple script or developing complex software, understanding syntax is fundamental.
Introduction to Programming Syntax
In the simplest terms, syntax in programming refers to the rules that define the correct combination of symbols, words, and punctuation in a given programming language. These rules ensure that the code is understandable by both the developer and the computer.
Just as a sentence in English must follow grammatical rules to make sense, a line of code must follow syntactic rules to be executed properly.
Why Syntax Matters in Programming?
1. Ensures Code Accuracy
Syntax rules act as a blueprint for writing code correctly.
Errors in syntax can lead to compilation or runtime errors, which prevent the program from functioning.
2. Enhances Readability
A consistent and correct syntax makes the code easier to read, maintain, and debug—especially when working in teams.
3. Facilitates Communication with the Computer
Computers do not understand natural language.
Programming syntax translates human logic into instructions a machine can execute.
Elements of Syntax in Programming Languages
Each programming language has its own syntax, but most share common components:
1. Keywords
Reserved words used to perform specific actions (e.g., if, else, while, return)
Cannot be used as variable names
2. Identifiers
Names created by the programmer for variables, functions, classes, etc.
Must follow naming rules (e.g., no spaces, no starting with digits)
3. Operators
Symbols that perform operations on variables and values (e.g., +, -, *, ==)
4. Delimiters
Characters that separate elements in the code (e.g., commas, semicolons, brackets)
Often signal the end of a statement or the grouping of statements
5. Literals
Fixed values like numbers (10, 3.14) or strings ("Hello") directly written in the code
6. Comments
Notes added to code for human understanding, ignored by the compiler/interpreter
Usually marked by // or /* */ depending on the language
Examples of Syntax in Different Languages
Java
java
public class Main {
public static void main(String[] args) {
System.out.println("Hello, World!");
}
}
Semicolons terminate each statement
Braces {} define code blocks
Python
python
def greet():
print("Hello, World!")
Indentation determines code blocks instead of braces
No semicolons needed
JavaScript
javascript
function greet() {
console.log("Hello, World!");
}
Similar to Java in structure
Uses curly braces and semicolons
Common Syntax Errors
Even experienced developers encounter syntax errors. Here are a few typical mistakes:
Missing brackets or parentheses
Incorrect indentation (especially in Python)
Using reserved keywords as variable names
Missing semicolons (in languages that require them)
Most code editors and IDEs highlight syntax errors in real time, making them easier to catch and correct.
Syntax vs. Semantics: What’s the Difference?
Syntax refers to the structure or form of code.
Semantics refers to the meaning or logic behind the code.
A program can be syntactically correct but semantically wrong if it doesn't do what the programmer intends.
How to Master Programming Syntax?
1. Practice Regularly
Writing code frequently helps reinforce syntax rules naturally.
2. Use an IDE
Modern IDEs provide syntax highlighting, auto-complete, and error detection.
3. Refer to Official Documentation
Each language has its own style and syntax—use resources like JavaDocs, Python.org, or Mozilla Developer Network for JavaScript.
4. Read and Analyze Code
Reading other people’s code is a great way to learn correct syntax and best practices.
Conclusion
Syntax is the foundation of all programming languages. It’s the rulebook that tells a computer how to interpret and execute code. A strong grasp of syntax not only helps you write functional programs but also improves code readability and maintainability. Whether you're a beginner learning your first language or an experienced developer diving into a new one, understanding syntax is your first step toward writing effective code.
0 notes
Link
Do you understand the use of comma operator in #java properly? Try below #problem and let's see whats your answer.

Java Comma operator
Related Link: Java Interview Problems and Java Basic Concepts
Please support us by sharing, liking and commenting. Your support can help thousands of newcomers to prepare well to start their journey
#java comma operator#operator use in java#learn programming through questions#interview preparation for development#javamcq
0 notes
Text
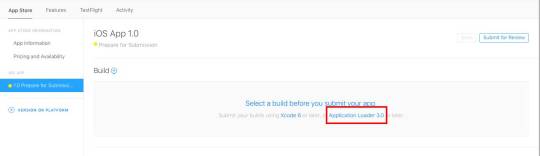
Download Application Loader For Mac
Applications trusted by millions. Over 1 Million people download videos, audios, convert videos and create slideshows with our tools. 4K Download software is cross-platform. Get it for your PC, macOS or Linux. Download Loader Droid download manager for PC to install on Windows 10, 8, 7 32bit/64bit, even Mac. The weight of the apps is 4.8 MB. On the latest update of the Loader Droid download manager app on lmt-post-modified-info, there are lots of changes that are properly enjoyable on the Computer, Desktop & Laptop.
Seems that Apple Transporter might have replaced it. It's on the Mac App Store, and was only released a week ago. Note: don't be confused by references to a previous 'File Transporter' which was some command line tools available for Windows and Mac. Mac users interested in Data loader salesforce generally download: Jitterbit Data Loader for Salesforce 5.0 Free Jitterbit Data LoaderTM is a data migration tool that enables Salesforce administrators to quickly and easily automate the import and export of data between flat files.
Installing Salesforce Data Loader in macOS and Windows.
In this Salesforce Tutorial we are going to learn about What is Salesforce Data Loader, How to Install Apex Data Loader and How Apex loader is used to upload, delete, export and Import records.
What is Data Loader?
Salesforce Data Loader is a desktop client application used in Salesforce to import, export, delete, insert and update bulk records. Using Data Loader we can load upto 5,00,000 records.
Data Loader Features and operations.
Using Data Loader we can load upto 5,00,000 records.
Using Data Loader we can schedule the loads.
We can import data from .csv (Comma Separated Values) files.
Success and Error log files created in CSV format.
Data Loader supports all objects(Custom objects and Standard objects).
Drag and Drop field Mapping.
Data Loader Operations.
Using Data Loader we can perform the following operations.
Insert – Insertion of new records.
Update – Updating existing records.
Upsert – Update and Insertion of records.
Delete – Deleting existing records.
Export – Extraction of all records.
Export All – Export all extracts all records including recycle bin records from salesforce.
How to Install Salesforce Data Loader.

Installing Data Loader and setting up Data loader require small knowledge on generating security tokens. Before installing Data loader in Windows Operating system and MacOS we have to check system requirements.
System requirements for Windows.
Data loader is compatible with windows*7, windows*8 and windows*10.
Minimum 120 MB of disk space.
Minimum 256 MB RAM.
Must have Java JRE 1.8 installed.
System requirements for macOS.
macOS EI Capitan or later.
Minimum 120 MB of disk space.
Minimum 256 MB RAM.
Must have Java JRE 1.8 installed.
Must have administrator privileges on the system.
Installing Salesforce Data Loader in Local system.
After checking all system requirement we have to install salesforce data loader in our local system. Follow the steps given below to install salesforce data loader.
Download Data loader from Salesforce.
Generate security Token.
Installing Data Loader in macOS or Windows Operating system.
Enter username and password.
Downloading Data Loader from Salesforce.
Data loader can be downloaded from data management. Go to Data Management | Data Loader.
Click on Data Loader and select the Operating system to which you want to download.
Now Apex Data Loader will download in to our local system.
Install latest Java version in to your local system.
Now install Salesforce Data Loader.
Choose any operation as shown above.
When we try login into Salesforce.com using data loader we have to options.
OAuth.
Password Authentication.
Option 1 :- Salesforce login through OAuth.
When we select OAuth option.
Now select the Environment. (Production or Sandbox).
Click on Login.
Now a new pop window will be opened where we have to login into Salesforce.com account using username and password.
Now a verification code will be sent to your account email.
Enter verification code and click on Login.
Click on Allow button to access as shown above.
Option 2 :- Login through Password Authentication.
Select password Authentication as shown above.
Enter username and Password.
Click on Login.
Where password is the combination of Salesforce account password and Security Token.
Now add Security Token after password.
Password = Password + Security Token.
Generating Security Token.
What is Security Token in Salesforce?
Security Token in Salesforce is a case sensitive alphanumeric key that is used with salesforce account password to access Salesforce via API.
How to generate Security Token?
To generate security token in salesforce go to My Settings | Personal | Rest my security Token.
When we click on Reset my security token an Email will be sent to the email address of our account. To log in to Salesforce via API we have to enter username and password.
Conclusion.
In this Salesforce Tutorial we have learned about What is Salesforce Data Loader, how to install data loader, what is Security token and how to generate new security token. In our next Salesforce admin tutorial we are going to learn about Salesforce Data loader operations.
No doubt, listening to music is a very interesting hobby in the overall world and therefore, we use different music applications to hear the songs in our busy lives.
Nowadays, everyone knows about one of the famous music streaming platforms named Deezer.com which offers many music applications such as Deezloader Remix, Deezloader Remaster, and Deezloader Reborn, etc. to download the songs.
In fact, these applications are generally made for androids, smartphones, windows as well as Linux but you cannot get access to compile them on your Mac due to mac IOS.
Therefore, developers discovered one of the pretty cool applications that provide the facility to mac users to listen and download all the music tracks, known as Deezloader Mac.
you cannot download Deezloader Mac in the androids and pc because developers had developed this software for the specific purpose like in graphics and designing.
Download Loader App
The Deezloader Mac version allows its mac users to listen and download the songs, albums and music tracks in both online and offline ways.
Moreover, the Mac version gives 53+ million music tracks and 30 thousand radio channels to its users and you can use this specific version without paying any charges. And the Deezer Premium Apk is now also getting much popularity just because of it.
What is DeezLoader Mac?
Deezloader mac is the latest version of deezloader that enables its mac users to listen and download all their best songs without any restriction.
By having a mac version, users can download all of their favorite music tracks and albums in the best-quality just within a few clicks.
Deezloader mac is specially designed for the specified purpose like in the graphics, animation makers, designing and for many other aims.
Androids, IOS, computers as well as Linux use the other deezloader music applications like Deezloader reborn, remix and remaster, etc. but these are not able to Deezloader mac.

The big advantage of this version is that there are no subscriptions and charges to pay. You can use it fully free of cost.
In most of the music applications, you have to need to pay any amount for downloading the music and songs while the mac version gives you all the best music without paying.
Features of Deezloader Mac
Before going to download the Deezloader mac, you should have a short overview of the features of this fruitful application that will surely make you more friendly to have it.
Highly reliable
Apple Application Loader
As you know that there are thousands of music applications available in the music industry that provide plenty of songs and all kinds of music tracks.
But users may face a lot of difficulties in terms of safety and reliability after using such applications because these may be fake that might drag your important data.
So, by using the Deezloader mac, you can give the full protection to your personal data and as well as download the songs, safely.
High-quality Music Download
After downloading Deezloader mac, you can download all the music tracks just in high-quality. It allows the original music links to its users in 320 kbps. You can also convert all the songs in audio formats such as mp3.
No-paid money
Mac users can use this application free of cost for listening and downloading all sorts of music. You can use this software in online as well as offline mode. You do not need to pay something to Deezer.com.
Download multiple songs
One of the latest features of this application is that you can directly download all the songs from its original website without any complication.
You can download multiple songs or the full album of your favorite singer just in a single click. It will take a while depending on your internet speed.
Easy to Use
If you are already using the Deezloader Apk, no doubt, you can use this application easily on your mac because it is almost compatible with deezloader.
Allows specific Devices
Deezloader Mac is the advanced platform of the music streaming industry which allows specific devices such as Mac.
You cannot download this application on androids, windows, and pc because of developers’ limitations.
Download DeezLoader Mac
Now, after reading all the comprehensive guides of Deezloader Mac, you might be a little curious about downloading this awesome application on mac devices.
You may face problems if you are going to download so, therefore, you have to follow our guide to get this one application on your devices.
Just click on the download link that we have already given below, after this, you will redirect go to our download page.
On this page, you will get a download link, again tap on the download buttons and then your mac application will start to download.

Download Application Loader For Mac Download
Final Verdict
So, guys, I have described all about the Deezloader Mac, an awesome application to download songs on the mac device.
The best feature of this software that makes its user a more friendly is the term of safety and reliability that provides protection to all of its users.
Download Application Loader 3.0 For Mac
Blackberry App Loader Download
Moreover, it gives all its premium features free of cost without paying any subscriptions and charges.so, this was all about the mac version and hopefully, you liked our guides.
1 note
·
View note
Text
Is It Easy To Learn Selenium If I Don'T Know Java?
Learn Java.
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
Licensed Software Program Examination Automation Architect.
Automation Testing Resources.
Test Automation With Selenium Webdriver.
Leading Tips For Discovering Java Programming.
Pointer # 3: Chrome Devtools: Replicating Network Issues
Licensed Software Program Examination Automation Engineer.
Then, practice your skills with two jobs where you produce and control variables. Self-paced introductory Java programs are available along with professional certificate programs created to educate you progressed Java programming abilities and also prepare you for a job. Java - a high-level programming language - is among the most effective languages for finding out core coding skills as a result of its object-oriented technique to programming. Learning the Java programs software application will get you started on a course to coming to be a software program engineer, among the most sought-after roles in the field of computer technology. Java is a computer shows language developed by James Gosling at Sun Microsystems.
youtube
Automation Testing Resources.
My own personal experience with Java is that it in fact was rather challenging. Obviously, that will certainly vary from one person to another and will certainly also rely on whether this is the initial programs language you're finding out or otherwise. Prior to discovering Java, I discovered the fundamentals of internet growth such as HTML5 as well as CSS3. Nonetheless, contrasting both is like comparing apples to oranges.
Certificate course in Java is among the most prominent temporary work oriented program. Trainees that go with this program will definitely obtain a great work. The average salary provided to students that have a certification course in Java varies from INR 1,80,000 to INR 6,00,000 each year depending upon the experience and also knowledge of the trainee. One can claim that there are a lot of task opportunities in the field of Java and also candidates are likewise obtaining handsome salaries.
You will discover the Java code fundamentals such as object-oriented shows, analytical, event-driven programs, how to create ranges as well as much more. After discovering the syntax of Java, the next thing to do is to find out the principles. Because I really did not exercise enough, I fell short Java the initial time I took it. The primary factor being that I was so hectic with the other courses that I tried to stuff a whole week's well worth of shows and also discovering right into a solitary day. I made a poll in the Facebook group, Java Programmers, which is a popular team of over 100,000 Java developers ranging in experience from newbie to professional of greater than 10 years.
This is a detailed training course that includes a video of 72 hours bring all essential info that a Java programmer must recognize. This course uses thorough expertise about the Java Programs language. Additionally, we underwent guests' reviews to identify the best Java courses for you.
Python has always had a presence in the ability space and also is considered to be one of the most favorable language for Machine Learning, Expert System, IoT as well as a great deal more. It takes 10 lines of code to review from a data in Java. Various projects are supplied as component of the course to acquire boosted knowledge and also abilities in Java language. You will get access to the huge database, write-ups, and also video clips that will include abilities and also share experiences.
Examination Automation With Selenium Webdriver.
Access is provided to obtain understanding regarding 500+ programs. The program will certainly aid you get expertise in examining the CSV documents or Comma-Separated Worth data. The training course will certainly guide gain access to as well as transform pictures, web sites and other data using Java. Mentor goes back to square one degrees as well as devices like Eclipse and also Maven are shown which are vital for comprehending Java growth.
Why is Java better than Python?
Based on the report details, the top Quality Assurance and testing objective, for not only 2019 but the next years to come, is end-user satisfaction. The role of a QA engineer has evolved from finding defects to actually thinking as the end-user. Software testers need to focus more on the whole experience.
However this is inhibited, as well as using one browser per node is taken into consideration finest practice for optimal efficiency.
Below are some ideas to make your waits a lot more resistant.
They can additionally speed up your test by rendering any kind of rests or stops redundant as well as conquer slow-moving network and also cross-browser problems.
If they do fail, this makes certain that any kind of Dockers are promptly brought back or changed.
To produce a steady variation of the Grid for your CI pipeline, it's likewise possible to release your Grid onto Kubernetes or Throng.
Java is known for being simpler to learn and also use than its predecessor, C++. Nonetheless, software testen opleiding 's also understood for being slightly more challenging to learn than Python as a result of Java's fairly extensive syntax.
Then it definitely will not be hard, if you've already discovered either Python or C++ before finding out Java. Begin on a course to a job as a Java Developer or Java Software Application Designer with a professional certification program on edX. Select from any variety of initial Java courses and Java tutorials for beginners. Begin with among the basics programs from HKUST as they are basically a cost-free Java tutorial for newbies.

Which testing is in demand?
For Selenium IDE you don't need any prior java knowledge. But for the most commonly used Selenium webdriver using java. U require basic core java concepts like OOP(Object Oriented Programming).
Top Tips For Discovering Java Programming.
HTML is a markup language as well as CSS is a styling language for said markup so neither are actual programs languages like Java is. So it's not really reasonable to say that Java is a tough shows language to learn on that basis. In a survey of 324 Java programmers ranging from novice to specialist, the overwhelming action, regarding 75% of pollers, is that Java is not a difficult language to find out.
Does manual testing require coding?
No need of coding knowledge required for manual testing. For testing field you want skills to find different bugs ie. UI related bugs,functionality related bugs,performance related bugs,also you need good analytical skills and more important thing you need patience during testing.
Create A Junit Examination Course
Trainees having experience in this field will undoubtedly obtain a high salaried work. Nowadays, MNCs prepare to provide respectable salaries to knowledgeable candidates. The students are introduced to numerous fundamental and also innovative fundamentals of Java, like OOPs, Information Frameworks, Formulas, and so on . Growing a Tree Write your initial Java program from square one by presenting yourself to individuals and planting a tree for them. You'll practice developing a course, specifying the primary technique, and also arranging print declarations.
youtube
Tip # 3: Chrome Devtools: Simulating Network Conditions
Java was first launched in 1995 and also has actually given that turned into one of the most popular programs languages with an estimated 12 million developers utilizing it It can also be made use of for artificial intelligence, artificial intelligence, blockchain, RSS feeds, and also Java applications. The Java platform differs from a lot of other platforms in that it's a software-only platform that operates on top of various other hardware-based platforms. According to Oracle, Java can reduce costs, drive technology, as well as extra as the shows language of choice for IoT, venture design, enterprise applications, and also cloud computing.
1 note
·
View note
Text
Beginner Problems With TCP & The socket Module in Python
This is important information for beginners, and it came up in Discord three times already, so I thought I’d write it up here.
The Python socket module is a low-level API to your operating system’s networking functionality. If you create a socket with socket.socket(socket.AF_INET, socket.SOCK_STREAM), it does not give you anything beyond ordinary TCP/IP.
TCP is a stream protocol. It guarantees that the stream of bytes you send arrives in order. Every byte you send either arrives eventually, unless the connection is lost. But if a TCP packet of data goes missing, it is sent again, and if TCP packets arrive out of order, the data stream is assembled in the right order on the other side. That’s it.
If you send data over TCP, it may get fragmented into multiple packets. The data that arrives is re-assembled by the TCP/IP stack of the operating system on the other side. That means that, if you send multiple short strings through a TCP socket, they may arrive at once, and the reader gets one long string. TCP does not have a concept of “messages”. If you want to send a sequence of messages over TCP, you need to separate them, for example through a line break at the end of messages, or by using netstrings. More on that later in this post!
If you don’t do that, then using sockets in Python with the socket module will be painful. Your operating system will deceive you and re-assemble the string you sock.recv(n) differently from the ones you sock.send(data). But here is the deceptive part. It will work sometimes, but not always. These bugs will be difficult to chase. If you have two programs communicating over TCP via the loopback device in your operating system (the virtual network device with IP 127.0.0.1), then the data does not leave your RAM, and packets are never fragmented to fit into the maximum size of an Ethernet frame or 802.11 WLAN transmission. The data arrives immediately because it’s already there, and the other side gets to read via sock.recv(n) exactly the bytestring you sent over sock.send(data). If you connect to localhost via IPv6, the maximum packet size is 64 kB, and all the packets are already there to be reassembled into a bytestream immediately! But when you try to run the same code over the real Internet, with lag and packet loss, or when you are unlucky with the multitasking/scheduling of your OS, you will either get more data than you expected, leftover data from the last sock.send(data), or incomplete data.
Example
This is a simplified, scaled-down example. We assume that data is sent in packets of 10 bytes over a slow connection (in real life it would be around 1.5 kilobytes, but that would be unreadable). Alice is using sock.sendall(data) to send messages to Bob. Bob is using sock.recv(1024) to receive the data. Bob knows that messages are never longer than 20 characters, so he figures 1024 should be enough.
Alice sends: "(FOO)" Bob receives: "(FOO)"
Seems to work. They disconnect and connect again.
Alice sends: "(MSG BAR BAZ)" Bob receives: "(MSG BAR B" - parsing error: unmatched paren
How did that happen? The maximum packet size supported by the routers of the connection (called path MTU) between Alice and Bob is just 10 bytes, and the transmission speed is slow. So one TCP/IP packet with the first ten bytes arrived first, and socket.recv(1024) does not wait until at least 1024 bytes arrive. It returns with any data that is currently available, but at most 1024 bytes. You don’t want to accidentally fill all your RAM!
But this error is now unrecoverable.
Alice sends: "(SECOND MESSAGE)" Bob receives: "AR)(SECOND ME" - parsing error: expected opening paren
The rest of the first message arrived in the mean time, plus another TCP packet with the first part of another message.
Alice and Bob stop their programs and connect again. Their bandwidth and path MTU are now higher.
Alice sends: "(FOOBAR)" This time Bob’s PC lags behind. The Java update popup hogs all the resources for a second. Alice sends: "(SECOND MESSAGE)" Bob receives "(FOOBAR)(SECOND MESSAGE)" - parsing error: extra data after end of message
If Bob had tried to only read 20 bytes with sock.recv(20) - because a message can never be longer than 20 bytes - he would have gotten "(FOOBAR)(SECOND MESS”.
And the same code would have run without a hitch when connected to localhost!
Additionally, the sock.send(data) method might not send all the data you give to it! Why is that? Because maybe you are sending a lot of data, or using a slow connection, and in that case send() just returns how much of the data you gave it could be sent, so your program can wait until the current data in the buffer has been sent over the network. This is also a kind of bug that is hard to track down if you’re only connecting to localhost over the loopback device, because there you have theoretically infinite bandwidth, limited only by the allocated memory of your OS and the maximum size of an IP packet. If you want all your data to be sent at once, guaranteed, you need to use sock.sendall(data), but sendall will block, that means your program will be unresponsive until all the data has been sent. If you are writing a game, using sendall on the main thread will make your game lag - this might not be what you want.
Solutions
You can use socketfile=socket.makefile() and use socketfile.readline() on that object. This is similar to java.io.BufferedReader in java: f.readline() gives you one line, it blocks until all the data until the next linebreak is received, and it saves additional data for the next call to readline. Of course, you also have to delimit the data you send by appending "\n" at the end of your message.
You can also use netstrings. Netstrings encode data by prepending the length of the incoming data to a message. The pynetstring module with the pynetstring.Decoder wrapper gives you a simple interface similar to readline.
If you want to send individual short messages, and don’t care if some of them get lost, you might want to look into UDP. This way, two messages will never get concatenated. Why would you want to send individual packets that might get lost? Imagine a multiplayer game where your client sends the current position of the player to the server every frame, delimited by commas and linefeeds like this “123.5,-312\n“. If a TCP packet gets lost, it is re-sent, but by that time, the player is already somewhere else! The server has to wait until it can re-assemble the stream in the right order. And the server will only get the latest position from the client after the earlier position, which is now outdated, has been re-sent. This introduces a lot of lag. If you have 5% packet loss, but you send a UDP packet with the player position every frame, you can just add time current frame number to the message, e.g. “5037,123.5,-312\n“ if that message gets lost or takes along time to deliver, and the next message is “5038,123.5,-311.9\n“, the server just updates to the newest coordinates. If a package with a timestamp older than the newest known timestamp arrives, it is ignored.
Lastly, you could do a request-response protocol, where the server responds with “OK\n“ or something like that whenever it has processed a message, and the client waits to send additional data until an OK is received. This might introduce unacceptable round-trip lag in real-time games, but is fine in most other applications. It will make bi-directional communication more difficult, because you cannot send messages both ways, otherwise both sides can send a message at the same time, expect to get an OK response, but receive something that is not an OK response instead.
Further Reading
https://en.wikipedia.org/wiki/Path_MTU_Discovery
https://en.wikipedia.org/wiki/IP_fragmentation
http://cr.yp.to/proto/netstrings.txt
https://pypi.org/project/pynetstring/
3 notes
·
View notes
Text
Ninite teamviewer 9


Anyway, there are two versions of however it is pronounced: a free version and a Pro version with additional features that is also, or so it is claimed, faster due to enhanced caching. Will people remember the name? Still seems somewhat random. The company website contends that it should be pronounced "nin-ite" but, in my humble opinion, that's not actually better and it isn't how most people will pronounce it when they see the name for the first time. I have to mention the product name, "Ninite.

Ninite was released 18 months ago and, since I first looked at it about a year ago, has matured and has been expanded in terms of the number of software titles it can manage. Click to see: Ninite Web site installer configuration. I've just been testing a really impressive solution to the problem of installing these tools and keeping them updated. That set typically includes one or more Web browsers along with messaging, media and imaging utilities, and runtimes for subsystems such as Java, Flash and Air. These features are only available in Ninite Pro Classic.Without doubt, there is a core set of applications and tools you need on all PCs, whether it's your own machine or those of users. In install mode, there are many different potential messages, so it's probably best to use the following approach: "OK" means the update or install succeeded "Skipped up to date " means the app is up to date All other messages indicate some kind of error condition Pro Classic only. We highly recommend that you specify a file that will receive a report, for example: NinitePro. We're working on documentation for the new Pro web interface.įor now the available help for that is inline in the interface. In install mode, there are many different potential messages, so it's probably best to use the following approach. To summarize, in audit mode, the message is always one of the five listed messages. Means Ninite failed to install Chrome, or at least it could not find it after running the installer. It is impossible to list them all because some of them can contain error codes from the operating system or from the installer programs. With remote mode it is in comma separated value CSV format and can be viewed in Excel. When run on a single machine the report will be a text file. If you are behind a proxy server that needs a user name and password, use the following switch in combination with the silent switch. By default, Ninite skips the installation of applications that are already up to date on the system. Without this there will be no indication of failure or debugging information, apart from the return code of the installer. and you would need to download & install the software as described in Step 2 of the tutorial, i.e.We highly recommend that you specify a file that will receive a report, for example. I would need to download & install the full Teamviewer package software onto my PC. should be on the lower left of your keyboard) to enlarge the text on the document that will open from the above link. (Remember that you can press the CTRL key and + key (. Please have a look at the link below (open the link using your browser) and read through it to get a basic understanding of what you need to do to enable me to connect to your laptop. I think it is time I was able to connect to your PC, and check settings, etc., so that I can fix some of the issues you are having.
Which software is recommended to take control over his laptop, from my laptop in South Africa?.
Whose data allowance will be used if I find he needs many apps / programs updated or installed? Will it use his data connection in the UK, or my (expensive & limited) data connection in South Africa?.
If (and it's a big IF) I can coach him into downloading and properly installing software such as LogMeIn or Teamviewer or equivalent. I usually achieve DL speeds of around 3 Mbps for download, and uploads of only 0.4 Mbps here in South Africa, data is slow, and expensive! I only have a 4 Mbps ADSL line, which is the max our exchange supports, and I have a 20GB per month capped data allowance.
Checking that he has latest OS & program updates.
I'm going to suggest he downloads & installs a program like LogMeIn (or perhaps some other equivalent), so that I will be able to remotely take control of of his laptop, and perform the simple maintenance tasks such as: I'm on Skype with him almost daily, and every day he has a new problem that he expects me to solve, but his very limited knowledge of PC settings, and PC maintenance, together with his lack of ability to properly define the issues he has with his laptop, and to explain to me exactly what problems he experiences, frustrates both of us. He uses his laptop mainly for e-mail, and creating MS Word documents, and web browsing, and Skype My 93-year-old Father is in the UK and has a HP laptop running Win 8.1 64-bit I am in South Africa, and have an ASUS Win 8.1 64-bit laptop.

0 notes
Text
Not Known Facts About PHP currency Exchange Script
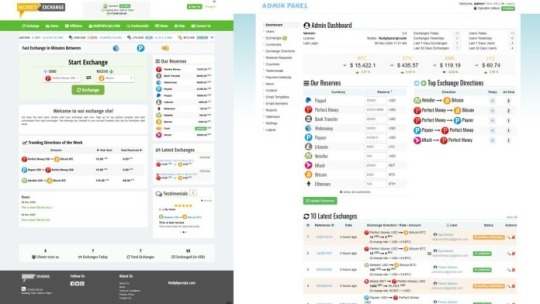
I'd a short while ago obtained a script from Up coming Hyip. The script fitted me pretty nicely and was precisely as explained on their web site. Thank you Up coming hyip for that superb encounter! An prolonged license enables an item to be used in limitless assignments for possibly personal or industrial use. The merchandise can't be made available for resale "as-is". It really is permitted to distribute/sublicense the supply data files as portion of a larger undertaking. Near Then it can vanish soon after a while for it to return soon after some time and wishes once again one click. You should don't react using a duplicate previous concept but produce down your method and how you're thinking that you can reach it as part of your reaction or to me in chat. Many thanks! CSS HTML JavaScript Python Website Scraping $33 (Avg Bid) $33 Avg Bid 23 bids This tutorial will evaluation The fundamental code snippets necessary for use with PHP, Python, Ruby, and Java Script apps. RapidAPI supports 19 common programming languages with code automobile-technology facilities geared toward software developers. Exchange Rix is effective and characteristics rich php script which will help you to run your personal bitcoin or other cryptocurrencies exchange internet site. Basically make order and start it currently. It’s uncomplicated. We will likely be employing PHP like a scripting language and interpreter that is mainly utilized on any World-wide-web server, such as xamp, wamp, and so on. It's being used to any common Web-sites, and it's got a contemporary know-how that can certainly be utilized by the following era. Our currency converter is Search engine optimization optimized and ready to be uploaded in minutes, No coding information desired, Well documented and easy to create, Install, and operate. VERIFIED I really need to scrap uncomplicated look for results of mom Ondo services. I do not should extract details - I need just html just after JavaScript execution.- I'll extract alone Classification: MLM Description Added info Testimonials (3) Cryptocurrency is turn into a long run for that miners, it can be impossible to mine the crypto currency Using the list of time frame, only the facility comprehensive server miners can mine considerably quicker than other, so Here's the answer with the cryptocurrency miners, purchase the highly effective server for an rent to mine the crypto currency. The primary API command may be the “GET exchange” connect with which is utilized to specify the currencies for that exchange prices. Developers will require to include both their Rapi API crucial and the two variables for the currency pair in Every single API simply call. Detect that we're utilizing the set Param approach which specifies the parameter and price, which is a comma divided listing of currency codes. The currency codes can be found by following the website link for supported currencies presented above. As it is possible to see, we can easily do a great deal with our free of charge access to the currency Layer products and services because we might get the two Stay and historical facts. If you need a lot more than 1,000 API accesses in a month then you need to choose the high quality approach that most closely fits your preferences. The web site admin can PHP currency Exchange Script regulate the many exercise like increase and take away cash, payment gateways, edit buyers interface plus much more. Also, There may be all the following stats are available: Brightery Currency converter, The very best currency exchange script in 2020 you could find. Get simpler now currency rate, dollar exc. https://www.exchangerix.com/
0 notes
Text
How To Split 100 3 Ways ヘ(^_^ヘ)
All that is left to do is to save your created subdocument. To decompose this number, you will need to separate it into its separate pieces.

B Split Bottom Cypher 1 Approach Smoke Valorant Update
Option (where the splitting takes place), open the type and size menu.

How to split 100 3 ways. To split your estate fairly between your beneficiaries, you'll need to add up the total value of your estate and share it equally. Per capita is by person. When you are given a number with two digits, the number has a “ones” place piece and a “tens” place piece.
25 goes into 36 once, so write a 1 at the top of the division sign over the. How do you divide that three ways? In this java split string by delimiter case, the separator is a comma (,) and the result of the java split string by comma operation will give you an array split.
Use the string split in java method against the string that needs to be divided and provide the separator as an argument. Multiply the first fraction by that reciprocal. How big is this room?
Per stirpes is by branch of the family. In mathematics, 100% means nothing more or less than 100 per 100, namely $100 / 100 = 1$. You can use gsplit to split a file into multiple files in a few different ways.
About press copyright contact us creators advertise developers terms privacy policy. If you are struggling to break 100 then give these three simple tips a try. 4 goes into 12, 3 times.
(of three) how much is the monthly rent? You don't need a special grip or swing technique to do it either. Include all of your assets, property, and savings.
In mathematics, as far as i know, you can't divide 100% by 3 without having 0,1.% left. Enter the values and click calculate. How to split word documents?
(this is now a reciprocal ). I achieved that level of flexibility after years of practice. When you divide by 10, move all the digits one place to the right.
I am also on the splits challenge, i used to be able to to the front splits about 10 years ago as a result of doing a lot of yoga. Remember that some assets, like life insurance and retirement accounts, won't. Dividing by 1, 10 or 100.
In this example, i am using whatsapp as my first window to display on the split screen. Sell the home and split the proceeds, distribute other assets. Did you know you can get a 30 day free trial to me and my golf.com by using the link below.
Write 3 in the quotient and 12 below 12. Then, if you want the first screen to be displayed on the left, press the left arrow key ( home key for most keyboards). 210 ÷ 10 = 21.
The 3 is in the “hundreds” place, so this part of the number can be separated and written as 300. Turn the second fraction (the one you want to divide by) upside down. Next, press the windows key on your keyboard.
Select chapters you need to split as subdocument and press create from show document options. Continue with your division until you get 0 or a recurring number. Summary of some timesaving tips for.
Before moving to the split file! 1 shares of the $105 cost basis = $100 + $0.75 (15% of $5 gain). Break apart a two digit number.
Out of the 14 golf clubs in your bag if you can get good with 4 of them you will break 100. 21 ÷ 1 = 21. There are two main ways to control how life insurance money is distributed if you outlive one of your beneficiaries:
Simplify the fraction (if needed) The default destination for saving subdocuments is. So in mathematics you can divide $100\%$ by $3$ without having $0.1\%$ left.
I think that the stretches are good but some are in the wrong order, for instance, i would start with 1 but then go 4, 3, 2. If all numbers are done, and the remainder is not zero yet, you will have to add a decimal in the quotient and write 0 beside the remainder. When you divide by 1 the answer stays the same.
2 3 4 5 6 7 8. So, the quotient now is 1623. Import your source files by clicking import and dragging them to the video timeline.
How many bedrooms are there? % is % of what? There are 3 simple steps to divide fractions:
Below is a video tutorial about how to use the split button to manually split videos. When you divide by 100. Drag and drop the video to the track in the timeline and then select the clip in the timeline, and move the playhead to the right position where the first section should end the second section.
The remainder is 3, so bring down the 6 to make 36. Open the first window you want to split. For example, if you’re dividing 360 by 25, you would start by putting a 0 over the 3, since 25 is larger than 3.
You'll be able to view. For example, you can specify how many output files you want, and gsplit will tell you how big each split piece will be. Summary of what happens to decimal numbers when they are divided by 10, 100 and 1,000.
What's up brochachos,in this video i share 3 tips to help you break 100.
0 notes
Photo

Best Javascript Training in Dehradun | Best JavaScript classes in Dehradun
Codiens institute offers real-time and place-focused Javascript training Dehradun. Our advanced Javascript course offers basic to advanced level training and is guaranteed to land you in good MNC companies all over the globe. Our Javascript trainers are Oracle sun Java certified professionals, with 10 years of experience working as professionals with multiple Javascript projects knowledge. To help students achieve their career goals, we have created our Javascript course content and syllabus.
Codiens is near Graphic Era Hill University and offers Javascript Training at multiple locations in Dehradun. Our advanced Javascript training centers have excellent infrastructure and lab facilities. Students in Dehradun also have access to advanced javascript certification courses. Our javascript training centers have more than 4000 students. The placement has been provided for 3567 of them. Javascript training in Dehradun is available on-site, online, or weekend classes.
Javascript Syllabus and Course Content in Dehradun
JavaScript Course Content
Overview of Java Script
Java Script: What's the Deal?
Comparing Products
JavaScript and JavaScript: A Comparison
The Java Script's Purpose
Prerequisites
Java Script Program Building
JavaScript in an HTML Doc
Java Script hiding from old Web Browsers
Review HTML
Layout and Text Formatting
Hypertext Links & Anchors
Tables
Forms
Frames
Java Script Commands Basic Syntax
Basic Commands
Variables
Overview of Variables
Assigning values to variables
Concatenating String Variables
Functions
Creating and calling function
Send Parameters To A Function
Parameters to be received out of a function
Variable scope & Lifetime
Events Call for Functions
Flow Control Structures
If Structure
If You Have Another Structure
For Loop
Loop
For/in Structure
Operators
Unary Operators
Numeric Operators
Logical Operators
String Processing
Length
Convert to all Lower or Upper Case
Index of
Last Index
Char at
Substr.
Objects
Standard Java Script functions
Making an object
Adding Functions To An Object
Multiple instances of an object type
History is an object
Accessing the History Object
Making Buttons
History. Go Method
Date
Create a Date Object
Only one string is needed to set the Date and Time
Separate Variables using Commas
Displaying the date and time
Time Zones
Extracting the Date
Extracting the Hrs
Date Setting Method
Set the Time
Non-Data Object Functionalities
Using objects such as Arrays
How to Create an Array
For Loop
Events
Time Status
Buttons
Location objects
Loading web pages from clients hard drives
Receive a Document from the Web Server
Hypertext and anchor links
Tracking the on-click Event
Form Objects
Button objects
Text Objects
Text Area Objects
Hidden Objects
Check Box Objects
Radio Button Objects
Selecting the right object
The Impact of Change
HTTP Cookies
The Cookie Property
Cookie Property
GetCookie()
SetCookie()
DeleteCookie()
Scope
Lifetime
Calendar Application
Static Calendar
Dynamic Calendar
Functions for updating the calendar
Assigning values for the dates of each month
Math Object
Constants
Circumference Calculator App
Functions
Frames
Referencing Objects In Other Frames
Event Calendar
Shopping Cart Application
Order Entry on the Internet
Looking at the Parent Object
An Array of Objects
Order Now
Place an Order
Validation of the Form
The Art of Trapping Empty Fields
Finding invalid values
Intercept the Submit Button
Java Applets
Java Applets Integrated with HTML
Regular Classes (morning, daytime, and evening)
Duration: 3 Weeks
Our Javascript Trainers
Javascript Technologies more than 10 years experience
A part of more than 10 Javascript projects in real-time
Dehradun MNC Company
4000+ students have been trained so far.
Solid Theoretical and Practical Knowledge
Javascript Certified Professionals
Dehradun Javascript (advanced javascript) Training
More than 4000+ students have been trained
3567 students placed
2000 Interviews Organization
If this blog is informative for you visit codiens website for more information .Read more
#javascript#javascripttraininginstitute#scriptinglanguages#codinglanguageindehradun#bestinstituteindehradun
0 notes
Text
Figmentgames Driver Download

Figment Games Driver Download Windows 7
Figmentgames Driver Download
Figment Game Ending
Figment Games Driver Download Pc
Figment Review
Figment Gameplay
Figment Games Driver Download Windows 10
Archetype Javascript Framework v.0.10.0
Trusted and safe download. Download Games Online Games. Around The World in 80 Day. Fogg win a bet and travel around the world in 80 days! Around The World in 80 Day. Fogg win a bet and travel around the world in 80 days! Around The World in 80 Day. Download Figment DMX for iOS to figment DMX is a unique application for DMX-based lighting control.Designed for lighting designers, technicians and riggers, Figment is a powerful. Download Figment DMX for iOS to figment DMX is a unique application for DMX-based lighting control.Designed for lighting designers, technicians and riggers, Figment is a powerful. GT Interactive’s cops n’ robbers driving game needs more substance. Driver is a tease. Initially, it overwhelms you with its premise and atmosphere, strutting its superb vehicle dynamics. It’s an interactive version of the best of the gritty 70s and 80s car chase movies. Here is the video game “Driver”! Released in 1999 on Windows, it's still available and playable with some tinkering. It's a racing / driving and simulation game, set in a vehicle simulator, crime, automobile and street racing themes and it was released on Mac as well.
Archetype is an Entreprise JavascriptFramework. Get documentation at http://archetypejs.org
Figment Games Driver Download Windows 7
Easy Javascript Framework (EJF) v.1.0

Easy JavascriptFramework (EJF) is a very simple framework to help people to develop applications using Javascript.There are a lot of javascriptframework nonetheless our objective is to provide a documentation of each javascript function like
Figment JavaScript Framework v.1.0.0
A simple, yet powerful JavaScriptframework that can help you build Web 2.0 applications. The framework is seperated into modules in order to reduce download
Nano JavaScript framework v.1.0
nano is a light-weight JavaScriptframework for building rich UI in web applications. Its highly extensible design lets you easily add your own functionality to the API with plugins. Visit http://www.nanojs.org for more
Sabia JavaScript Framework v.1.0
Sabia is a javascript MVC framework designed to be toolkit agnostic and productive.
Spark JavaScript framework v.1.0
Spark is a tool set which can give you a lot of options to your web app/site. DOM handlers, Ajax utilities, cool widgets, visual effects, form tools, UI components and more stuff. So you can easily build a complete and lightweight front-end interface.
JSAX JavaScript Abstractions for X(HT)ML v.20060317
JSAX - JavaScript Abstractions for X(HT)ML This is a JavaScriptframework which is compatibel with the latest versions of Mozilla, Opera, Konqueror(+safari) and
MPagesJS JavaScript Library v.1.0.rc2
mPagesJS is a JavaScriptFramework that provides a core interface into all client-side functionality within Cerner Millennium Pages - MPages. mPagesJS makes MPage development quicker and
Simple Javascript Spreadsheet v.1.0
An OpenSource Javascript Spreadsheet project based on Qooxdoo javascriptframework. This component is also a part of X4View Java Framework (see
JavaScript Development Kit v.1.0
JTDK(JavaScript Development Kit) is a javascriptframework, alias as JSDK.
Figmentgames Driver Download
JAST - Javascript Toolkit v.1.0
JAST (Javascript Toolkit) is an Open Source cross-platform javascriptframework that aid users to perform the most hard operations with few simple lines of code.It's modularity allow the download only for the code required to the page.
AONIC Framework v.1.0
AONIC JavaScriptFramework designed primarily for asynchronous push communication with back-end servers (comet). Python back-end examples included, as well as a basic JavaScript effects library, and ActionScript source for handling the active connections
Framework 2.0 v.1.0
Framework 2.0 is a JavaScriptFramework that allows to create Web-Applications based on components. Components are Services which run indepenently on the clients browser. Web-Applications are composed by combining serveral Services.
Lick Javascript Library v.1.0
The Lick Javascriptframework, is a Javascript/Dom/Ajax and widget framework aimed at simplifying the process of creating we applicatios, it has a very light memory footprint and a robust api Base
PFAST - just a PHP Framework v.1.0
PHP & JavaScriptFramework used to build webistes/web applications
DracMail Webmail v.0.2.0.beta
dracMail is a webmail interface built using PHP, ExtJS (JavaScriptframework), MySQL and IMAP. Features include: Rich UI, WYSIWYG editor, HTML mail composing and message
Jquery4jsf v.2
jQuery4jsf is a JSF(JavaServer Faces)component library that uses the power of the jQuery javascriptframework. These JSF(JavaServer Faces)components have the added value of jQuery which allows the end user to realize its application in a fast and
JSPackaging v.2.1
JSPackaging is a JavaScriptframework that provides simple directives for defining, loading & importing uniquely named packages of JavaScript modules. UPDATE: This project now exists as Ajile at http://sf.net/projects/ajile &
MathJax v.1.0
MathJax is a modular javascriptframework for including mathematics in web pages. It can take input in various formats, like TeX and MathML, and can produce output in various forms, such as MathML or HTML-with-CSS. Components are loaded as
Multiform v.1.0
Multiform allows creation of Web Applications by defining their processes and business objects in a declarative XML-based language. It's made of a Javascriptframework and an XSL compiler to get the application skeleton from the
Javascript Framework software by TitlePopularityFreewareLinuxMac
Tables2csv v.1.0
tables2csv offers the programmer a simple, fast and effective method to collect table information from the local ODBC driver and output it to comma seperated values.
Odbc2csv v.1.0
Figment Game Ending
odbc2csv offers the programmer a simple, fast and effective method to collect DSN information from the local ODBC driver and output it to comma seperated values.
Mp3 File Merger v.1.6
Mp3 File Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better.
Mp3 Merger v.1.0
It is a free tool which can merge MP3 files. It can merge from 2 to 9999 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better.
Heatmap Studio v.0.1
Basic Instuctions * Data Set Restrictions o Data sets must be 2 or 3 columns comma seperated, formatting is + o2 column: X coordinate (or latitude), Y coordinate (or longitude) - example: 23,24″ + o3 Column: X coordinate (or latitude), Y
ViSplore v.0.9.138
Easily navigate your file system with breadcrumbs Traditionaly a path is seperated with forward slashes. When a user wants to navigate to a sub folder inside path. They would need to breakup the path or simply retype. Breadcrumbs breakup paths
Epsa Mp3 Merger v.1.1
Figment Games Driver Download Pc
Epsa Mp3 Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better. It is small and delicate with beautiful screen
Zging Mp3 Merger v.1.1
Zging Mp3 Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better. It is small and delicate with beautiful screen
Zging File Merger v.1.1
Zging File Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better. It is small and delicate with beautiful screen
Epsa File Merger v.1.1
Epsa File Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better. It is small and delicate with beautiful screen
AbyssWS Log Splitter v.01b4
AbyssWS Log Splitter is a project created on Saturday, January 20, 2007. It has the ability to quickly split your Server log into seperate log files, seperated by month and year. It uses the 'Common Log
Extensible Robot Core v.rc.2.0.0
roboerc implements JAUS standard 3.3. It provides the necessary virtual networking library for JAUS message over TCP, UDP, Serial. It also uses JAUS switches to route JAUS messages across seperated virtual
Figment JavaScript Framework v.1.0.0
A simple, yet powerful JavaScript framework that can help you build Web 2.0 applications. The framework is seperated into modules in order to reduce download
KESI v.0.9
KESI - KESI Easy SQL Import, is a tool to easily import CSV files into your SQL database tables. It has a very easy to use KDE GUI and understands almost every possible CSV (comma seperated value) file
SimpleX2C v.1.0
Converts XML to CSV. You can define wich XML-Nodes should get extracted. The output is in CSV-Format (';'-seperated). There are many very good XML-Tools out there, but i want a simple tool that extract easely defined content.Open a Ticket if you
Tiny Translator v.0.6
Tiny Translator is a very simple class for easily organizing dialogue outputs and creating language tables for multilingual projects. It supports flat files (comma seperated, .csv) and MySQL databases to store
Rope pulling v.1.0
Figment Review
Code for a physical tug-of-war game that allows teams from physically seperated sites to interact. Lego's RCX is used to sense the force exerted at both sites. Video can optionally be provided via a Skype link.
Aion Emu v.1.0
Aion Emulator gives you the possibility to legally host a game server for this popular MMo Aion createde by NcSoft?Aion Emu is seperated in two parts:1) Aion Server2)Aion Datapack
JQ-Data FTP Server v.1.0
FTP Server written in JAVA. The server has an optional SWING GUI.The GUI and the server-logic is seperated as two components, but downloaded together.
Geographically Independent Office v.1.0
Figment Gameplay
Geographically Independent OfficeA WWW application to allow SOHO companys to manage their business where the office is spread over a number of geographically seperated office locations.
Figment Games Driver Download Windows 10
Seperated software by TitlePopularityFreewareLinuxMac

0 notes
Text
Apache Tomcat 403

Apache Tomcat 403 Forbidden
Apache Tomcat Http Status 403
Apache Tomcat 9 403 Access Denied
It was really very helpful for me. I was using version 8.5.32 and worked fine.thnaks. What is Apache Tomcat? Answer: Apache Tomcat is basically a Web Server and Servlet system. Because of the bug CVE-2020-1938 we want to use the latest Tomcat 7.0.100. See also CVE-2020-1938 We also use an Apache server in version 2.4, which connects to the Tomcat via AJP.
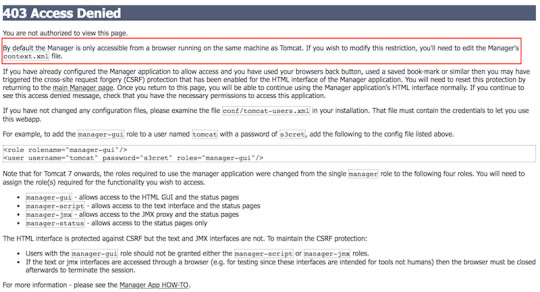
After you installed the Apache Tomcat server and successfully launched the <host>:8080 web page, you click on the Manager App button, and you get a 403 Access Denied message.
The Apache Tomcat Project is proud to announce the release of version 7.0.109 of Apache Tomcat. This release implements specifications that are part of the Java EE 6 platform. This release contains a number of bug fixes and improvements compared to version 7.0.108.
Hi, we have a strange symptom after an upgrade from Tomcat 8 to Tomcat 9, because we get a 403 for a call that works flawlessly with the previous version. Let's describe the scenario: We have a customer with a Wordpress application hosted on an Apache server. Some pages perform XMLHttpRequests to load and embed HTML snippets from other sources.
To fix it 1. Open the $CATALINA_BASE/conf/tomcat-users.xml file and add the following to the <tomcat-users> section.
<user username='admin' password='goanywhere' roles='admin-gui,manager-gui' />
2. If you are accessing the Tomcat server from a remote computer, open or create the file: $CATALINA_BASE/conf/Catalina/localhost/manager.xml, and add the below to the file.
<Context privileged='true' antiResourceLocking='false'
<Valve className='org.apache.catalina.valves.RemoteAddrValve' allow='^.*$' />
3. Restart the tomcat server: sudo systemctl restart tomcat.service
----------------------------------------------------------------------------------------------------------------- Watch the blessing and loving online channel: SupremeMasterTV live
If you have ever asked yourself these questions, this is the book for you. What is the meaning of life? Why do people suffer? What is in control of my life? Why is life the way it is? How can I stop suffering and be happy? How can I have a successful life? How can I have a life I like to have? How can I be the person I like to be? How can I be wiser and smarter? How can I have good and harmonious relations with others? Why do people meditate to achieve enlightenment? What is the true meaning of spiritual practice? Why all beings are one? Read the book for free here.
The AJP Connector
Table of Contents
Attributes
Special Features
Introduction
The AJP Connector element represents a Connector component that communicates with a web connector via the AJP protocol. This is used for cases where you wish to invisibly integrate Tomcat into an existing (or new) Apache installation, and you want Apache to handle the static content contained in the web application, and/or utilize Apache's SSL processing.
Use of the AJP protocol requires additional security considerations because it allows greater direct manipulation of Tomcat's internal data structures than the HTTP connectors. Particular attention should be paid to the values used for the address, secret, secretRequired and allowedRequestAttributesPattern attributes.
This connector supports load balancing when used in conjunction with the jvmRoute attribute of the Engine.
The native connectors supported with this Tomcat release are:
JK 1.2.x with any of the supported servers. See the JK docs for details.
mod_proxy on Apache httpd 2.x (included by default in Apache HTTP Server 2.2), with AJP enabled: see the httpd docs for details.
Other native connectors supporting AJP may work, but are no longer supported.
Attributes
Common Attributes
Apache Tomcat 403 Forbidden
All implementations of Connector support the following attributes:
Attribute Description ajpFlush
A boolean value which can be used to enable or disable sending AJP flush messages to the fronting proxy whenever an explicit flush happens. The default value is true. An AJP flush message is a SEND_BODY_CHUNK packet with no body content. Proxy implementations like mod_jk or mod_proxy_ajp will flush the data buffered in the web server to the client when they receive such a packet. Setting this to false can reduce AJP packet traffic but might delay sending packets to the client. At the end of the response, AJP does always flush to the client.
allowTrace
A boolean value which can be used to enable or disable the TRACE HTTP method. If not specified, this attribute is set to false.
asyncTimeout
The default timeout for asynchronous requests in milliseconds. If not specified, this attribute is set to the Servlet specification default of 30000 (30 seconds).
enableLookups
Set to true if you want calls to request.getRemoteHost() to perform DNS lookups in order to return the actual host name of the remote client. Set to false to skip the DNS lookup and return the IP address in String form instead (thereby improving performance). By default, DNS lookups are disabled.
encodedSolidusHandling
When set to reject request paths containing a %2f sequence will be rejected with a 400 response. When set to decode request paths containing a %2f sequence will have that sequence decoded to / at the same time other %nn sequences are decoded. When set to passthrough request paths containing a %2f sequence will be processed with the %2f sequence unchanged. If not specified the default value is reject. This default may be modified if the deprecated system propertyorg.apache.tomcat.util.buf.UDecoder.ALLOW_ENCODED_SLASH is set.
maxHeaderCount
The maximum number of headers in a request that are allowed by the container. A request that contains more headers than the specified limit will be rejected. A value of less than 0 means no limit. If not specified, a default of 100 is used.
maxParameterCount
The maximum number of parameter and value pairs (GET plus POST) which will be automatically parsed by the container. Parameter and value pairs beyond this limit will be ignored. A value of less than 0 means no limit. If not specified, a default of 10000 is used. Note that FailedRequestFilterfilter can be used to reject requests that hit the limit.
maxPostSize
The maximum size in bytes of the POST which will be handled by the container FORM URL parameter parsing. The limit can be disabled by setting this attribute to a value less than zero. If not specified, this attribute is set to 2097152 (2 megabytes). Note that the FailedRequestFilter can be used to reject requests that exceed this limit.
maxSavePostSize
The maximum size in bytes of the POST which will be saved/buffered by the container during FORM or CLIENT-CERT authentication. For both types of authentication, the POST will be saved/buffered before the user is authenticated. For CLIENT-CERT authentication, the POST is buffered for the duration of the SSL handshake and the buffer emptied when the request is processed. For FORM authentication the POST is saved whilst the user is re-directed to the login form and is retained until the user successfully authenticates or the session associated with the authentication request expires. The limit can be disabled by setting this attribute to -1. Setting the attribute to zero will disable the saving of POST data during authentication. If not specified, this attribute is set to 4096 (4 kilobytes).
parseBodyMethods
A comma-separated list of HTTP methods for which request bodies using application/x-www-form-urlencoded will be parsed for request parameters identically to POST. This is useful in RESTful applications that want to support POST-style semantics for PUT requests. Note that any setting other than POST causes Tomcat to behave in a way that goes against the intent of the servlet specification. The HTTP method TRACE is specifically forbidden here in accordance with the HTTP specification. The default is POST
port
The TCP port number on which this Connector will create a server socket and await incoming connections. Your operating system will allow only one server application to listen to a particular port number on a particular IP address. If the special value of 0 (zero) is used, then Tomcat will select a free port at random to use for this connector. This is typically only useful in embedded and testing applications.
protocol
Sets the protocol to handle incoming traffic. To configure an AJP connector this must be specified. If no value for protocol is provided, an HTTP connector rather than an AJP connector will be configured. The standard protocol value for an AJP connector is AJP/1.3 which uses an auto-switching mechanism to select either a Java NIO based connector or an APR/native based connector. If the PATH (Windows) or LD_LIBRARY_PATH (on most unix systems) environment variables contain the Tomcat native library, the native/APR connector will be used. If the native library cannot be found, the Java NIO based connector will be used. To use an explicit protocol rather than rely on the auto-switching mechanism described above, the following values may be used: org.apache.coyote.ajp.AjpNioProtocol - non blocking Java NIO connector. org.apache.coyote.ajp.AjpNio2Protocol - non blocking Java NIO2 connector. org.apache.coyote.ajp.AjpAprProtocol - the APR/native connector. Custom implementations may also be used. Take a look at our Connector Comparison chart.
proxyName
If this Connector is being used in a proxy configuration, configure this attribute to specify the server name to be returned for calls to request.getServerName(). See Proxy Support for more information.
proxyPort
If this Connector is being used in a proxy configuration, configure this attribute to specify the server port to be returned for calls to request.getServerPort(). See Proxy Support for more information.
redirectPort
If this Connector is supporting non-SSL requests, and a request is received for which a matching <security-constraint> requires SSL transport, Catalina will automatically redirect the request to the port number specified here.
scheme
Set this attribute to the name of the protocol you wish to have returned by calls to request.getScheme(). For example, you would set this attribute to 'https' for an SSL Connector. The default value is 'http'.
secure
Set this attribute to true if you wish to have calls to request.isSecure() to return true for requests received by this Connector. You would want this on an SSL Connector or a non SSL connector that is receiving data from a SSL accelerator, like a crypto card, an SSL appliance or even a webserver. The default value is false.
sendReasonPhrase
Set this attribute to true if you wish to have a reason phrase in the response. The default value is false.
Note: This option is deprecated and will be removed in Tomcat 9. The reason phrase will not be sent.
URIEncoding
This specifies the character encoding used to decode the URI bytes, after %xx decoding the URL. If not specified, UTF-8 will be used unless the org.apache.catalina.STRICT_SERVLET_COMPLIANCEsystem property is set to true in which case ISO-8859-1 will be used.
useBodyEncodingForURI
This specifies if the encoding specified in contentType should be used for URI query parameters, instead of using the URIEncoding. This setting is present for compatibility with Tomcat 4.1.x, where the encoding specified in the contentType, or explicitly set using Request.setCharacterEncoding method was also used for the parameters from the URL. The default value is false.
Notes: See notes on this attribute in HTTP Connector documentation.
useIPVHosts
Set this attribute to true to cause Tomcat to use the IP address passed by the native web server to determine the Host to send the request to. The default value is false.
xpoweredBy
Set this attribute to true to cause Tomcat to advertise support for the Servlet specification using the header recommended in the specification. The default value is false.
Standard Implementations
To use AJP, you must specify the protocol attribute (see above).
The standard AJP connectors (NIO, NIO2 and APR/native) all support the following attributes in addition to the common Connector attributes listed above.
Attribute Description acceptCount
The maximum queue length for incoming connection requests when all possible request processing threads are in use. Any requests received when the queue is full will be refused. The default value is 100.
acceptorThreadCount
The number of threads to be used to accept connections. Increase this value on a multi CPU machine, although you would never really need more than 2. Also, with a lot of non keep alive connections, you might want to increase this value as well. Default value is 1.
acceptorThreadPriority
The priority of the acceptor threads. The threads used to accept new connections. The default value is 5 (the value of the java.lang.Thread.NORM_PRIORITY constant). See the JavaDoc for the java.lang.Thread class for more details on what this priority means.
address
For servers with more than one IP address, this attribute specifies which address will be used for listening on the specified port. By default, the connector will listen on the loopback address. Unless the JVM is configured otherwise using system properties, the Java based connectors (NIO, NIO2) will listen on both IPv4 and IPv6 addresses when configured with either 0.0.0.0 or ::. The APR/native connector will only listen on IPv4 addresses if configured with 0.0.0.0 and will listen on IPv6 addresses (and optionally IPv4 addresses depending on the setting of ipv6v6only) if configured with ::.
allowedRequestAttributesPattern
The AJP protocol passes some information from the reverse proxy to the AJP connector using request attributes. These attributes are:
javax.servlet.request.cipher_suite
javax.servlet.request.key_size
javax.servlet.request.ssl_session
javax.servlet.request.X509Certificate
AJP_LOCAL_ADDR
AJP_REMOTE_PORT
AJP_SSL_PROTOCOL
JK_LB_ACTIVATION
CERT_ISSUER (IIS only)
CERT_SUBJECT (IIS only)
CERT_COOKIE (IIS only)
HTTPS_SERVER_SUBJECT (IIS only)
CERT_FLAGS (IIS only)
HTTPS_SECRETKEYSIZE (IIS only)
CERT_SERIALNUMBER (IIS only)
HTTPS_SERVER_ISSUER (IIS only)
HTTPS_KEYSIZE (IIS only)
The AJP protocol supports the passing of arbitrary request attributes. Requests containing arbitrary request attributes will be rejected with a 403 response unless the entire attribute name matches this regular expression. If not specified, the default value is null.
bindOnInit
Controls when the socket used by the connector is bound. By default it is bound when the connector is initiated and unbound when the connector is destroyed. If set to false, the socket will be bound when the connector is started and unbound when it is stopped.
clientCertProvider
When client certificate information is presented in a form other than instances of java.security.cert.X509Certificate it needs to be converted before it can be used and this property controls which JSSE provider is used to perform the conversion. For example it is used with the AJP connectors, the HTTP APR connector and with the org.apache.catalina.valves.SSLValve.If not specified, the default provider will be used.
connectionLinger
The number of seconds during which the sockets used by this Connector will linger when they are closed. The default value is -1 which disables socket linger.
connectionTimeout
The number of milliseconds this Connector will wait, after accepting a connection, for the request URI line to be presented. The default value for AJP protocol connectors is -1 (i.e. infinite).
executor
A reference to the name in an Executor element. If this attribute is set, and the named executor exists, the connector will use the executor, and all the other thread attributes will be ignored. Note that if a shared executor is not specified for a connector then the connector will use a private, internal executor to provide the thread pool.
executorTerminationTimeoutMillis
The time that the private internal executor will wait for request processing threads to terminate before continuing with the process of stopping the connector. If not set, the default is 5000 (5 seconds).
keepAliveTimeout
The number of milliseconds this Connector will wait for another AJP request before closing the connection. The default value is to use the value that has been set for the connectionTimeout attribute.
maxConnections
The maximum number of connections that the server will accept and process at any given time. When this number has been reached, the server will accept, but not process, one further connection. This additional connection be blocked until the number of connections being processed falls below maxConnections at which point the server will start accepting and processing new connections again. Note that once the limit has been reached, the operating system may still accept connections based on the acceptCount setting. The default value varies by connector type. For NIO and NIO2 the default is 10000. For APR/native, the default is 8192.
For NIO/NIO2 only, setting the value to -1, will disable the maxConnections feature and connections will not be counted.
maxCookieCount
The maximum number of cookies that are permitted for a request. A value of less than zero means no limit. If not specified, a default value of 200 will be used.
maxThreads
The maximum number of request processing threads to be created by this Connector, which therefore determines the maximum number of simultaneous requests that can be handled. If not specified, this attribute is set to 200. If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
minSpareThreads
The minimum number of threads always kept running. This includes both active and idle threads. If not specified, the default of 10 is used. If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
packetSize
This attribute sets the maximum AJP packet size in Bytes. The maximum value is 65536. It should be the same as the max_packet_size directive configured for mod_jk. Normally it is not necessary to change the maximum packet size. Problems with the default value have been reported when sending certificates or certificate chains. The default value is 8192. If set to less than 8192 then the setting will ignored and the default value of 8192 used.
processorCache
The protocol handler caches Processor objects to speed up performance. This setting dictates how many of these objects get cached. -1 means unlimited, default is 200. If not using Servlet 3.0 asynchronous processing, a good default is to use the same as the maxThreads setting. If using Servlet 3.0 asynchronous processing, a good default is to use the larger of maxThreads and the maximum number of expected concurrent requests (synchronous and asynchronous).
secret
Only requests from workers with this secret keyword will be accepted. The default value is null. This attribute must be specified with a non-null, non-zero length value unless secretRequired is explicitly configured to be false. If this attribute is configured with a non-null, non-zero length value then the workers must provide a matching value else the request will be rejected irrespective of the setting of secretRequired.
secretRequired
If this attribute is true, the AJP Connector will only start if the secret attribute is configured with a non-null, non-zero length value. This attribute only controls whether the secret attribute is required to be specified for the AJP Connector to start. It does not control whether workers are required to provide the secret. The default value is true. This attribute should only be set to false when the Connector is used on a trusted network.
tcpNoDelay
If set to true, the TCP_NO_DELAY option will be set on the server socket, which improves performance under most circumstances. This is set to true by default.
threadPriority
The priority of the request processing threads within the JVM. The default value is 5 (the value of the java.lang.Thread.NORM_PRIORITY constant). See the JavaDoc for the java.lang.Thread class for more details on what this priority means.If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
tomcatAuthentication
If set to true, the authentication will be done in Tomcat. Otherwise, the authenticated principal will be propagated from the native webserver and used for authorization in Tomcat.
The web server must send the user principal (username) as a request attribute named REMOTE_USER.
Note that this principal will have no roles associated with it.
The default value is true. If tomcatAuthorization is set to true this attribute has no effect.
tomcatAuthorization
If set to true, the authenticated principal will be propagated from the native webserver and considered already authenticated in Tomcat. If the web application has one or more security constraints, authorization will then be performed by Tomcat and roles assigned to the authenticated principal. If the appropriate Tomcat Realm for the request does not recognise the provided user name, a Principal will be still be created but it will have no roles. The default value is false.
Java TCP socket attributes
The NIO and NIO2 implementation support the following Java TCP socket attributes in addition to the common Connector and HTTP attributes listed above.
Attribute Description socket.rxBufSize
(int)The socket receive buffer (SO_RCVBUF) size in bytes. JVM default used if not set.
socket.txBufSize
(int)The socket send buffer (SO_SNDBUF) size in bytes. JVM default used if not set. Care should be taken if explicitly setting this value. Very poor performance has been observed on some JVMs with values less than ~8k.
socket.tcpNoDelay
(bool)This is equivalent to standard attribute tcpNoDelay.
socket.soKeepAlive
(bool)Boolean value for the socket's keep alive setting (SO_KEEPALIVE). JVM default used if not set.
socket.ooBInline
(bool)Boolean value for the socket OOBINLINE setting. JVM default used if not set.
socket.soReuseAddress
(bool)Boolean value for the sockets reuse address option (SO_REUSEADDR). JVM default used if not set.
socket.soLingerOn
(bool)Boolean value for the sockets so linger option (SO_LINGER). A value for the standard attribute connectionLinger that is >=0 is equivalent to setting this to true. A value for the standard attribute connectionLinger that is <0 is equivalent to setting this to false. Both this attribute and soLingerTime must be set else the JVM defaults will be used for both.
socket.soLingerTime
(int)Value in seconds for the sockets so linger option (SO_LINGER). This is equivalent to standard attribute connectionLinger. Both this attribute and soLingerOn must be set else the JVM defaults will be used for both.
socket.soTimeout
This is equivalent to standard attribute connectionTimeout.
socket.performanceConnectionTime
(int)The first value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.performanceLatency
(int)The second value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.performanceBandwidth
(int)The third value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.unlockTimeout
(int) The timeout for a socket unlock. When a connector is stopped, it will try to release the acceptor thread by opening a connector to itself. The default value is 250 and the value is in milliseconds
NIO specific configuration
The following attributes are specific to the NIO connector.
Attribute Description socket.directBuffer
(bool)Boolean value, whether to use direct ByteBuffers or java mapped ByteBuffers. Default is false. When you are using direct buffers, make sure you allocate the appropriate amount of memory for the direct memory space. On Sun's JDK that would be something like -XX:MaxDirectMemorySize=256m.
socket.appReadBufSize
(int)Each connection that is opened up in Tomcat get associated with a read ByteBuffer. This attribute controls the size of this buffer. By default this read buffer is sized at 8192 bytes. For lower concurrency, you can increase this to buffer more data. For an extreme amount of keep alive connections, decrease this number or increase your heap size.
socket.appWriteBufSize
(int)Each connection that is opened up in Tomcat get associated with a write ByteBuffer. This attribute controls the size of this buffer. By default this write buffer is sized at 8192 bytes. For low concurrency you can increase this to buffer more response data. For an extreme amount of keep alive connections, decrease this number or increase your heap size. The default value here is pretty low, you should up it if you are not dealing with tens of thousands concurrent connections.
socket.bufferPool
(int)The NIO connector uses a class called NioChannel that holds elements linked to a socket. To reduce garbage collection, the NIO connector caches these channel objects. This value specifies the size of this cache. The default value is 500, and represents that the cache will hold 500 NioChannel objects. Other values are -1 for unlimited cache and 0 for no cache.
socket.bufferPoolSize
(int)The NioChannel pool can also be size based, not used object based. The size is calculated as follows: NioChannel buffer size = read buffer size + write buffer size SecureNioChannel buffer size = application read buffer size + application write buffer size + network read buffer size + network write buffer size The value is in bytes, the default value is 1024*1024*100 (100MB).
socket.processorCache
(int)Tomcat will cache SocketProcessor objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 Body outline drawing. for no cache.
socket.keyCache
(int)Tomcat will cache KeyAttachment objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
socket.eventCache
(int)Tomcat will cache PollerEvent objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
selectorPool.maxSelectors
(int)The max selectors to be used in the pool, to reduce selector contention. Use this option when the command line org.apache.tomcat.util.net.NioSelectorShared value is set to false. Default value is 200.
selectorPool.maxSpareSelectors
(int)The max spare selectors to be used in the pool, to reduce selector contention. When a selector is returned to the pool, the system can decide to keep it or let it be GC'd. Use this option when the command line org.apache.tomcat.util.net.NioSelectorShared value is set to false. Default value is -1 (unlimited).
command-line-options
The following command line options are available for the NIO connector: -Dorg.apache.tomcat.util.net.NioSelectorShared=true|false - default is true. Set this value to false if you wish to use a selector for each thread. When you set it to false, you can control the size of the pool of selectors by using the selectorPool.maxSelectors attribute.
NIO2 specific configuration
The following attributes are specific to the NIO2 connector.
Attribute Description useCaches
(bool)Use this attribute to enable or disable object caching to reduce the amount of GC objects produced. The default value is false.
socket.directBuffer
(bool)Boolean value, whether to use direct ByteBuffers or java mapped ByteBuffers. Default is false. When you are using direct buffers, make sure you allocate the appropriate amount of memory for the direct memory space. On Sun's JDK that would be something like -XX:MaxDirectMemorySize=256m.
socket.appReadBufSize
(int)Each connection that is opened up in Tomcat get associated with a read ByteBuffer. This attribute controls the size of this buffer. By default this read buffer is sized at 8192 bytes. For lower concurrency, you can increase this to buffer more data. For an extreme amount of keep alive connections, decrease this number or increase your heap size.
We are an experienced Drupal development company with decade-long proven track record offering best-in-class customization, module, migration and Drupal development services worldwide. Drupal web services. Drupal is a powerful CMS widely used to develop variety of web solutions; ranging from a single page website to complex eCommerce stores. There are large numbers of web development companies in tech world that claim to provide excellent Drupal development services.
socket.appWriteBufSize
(int)Each connection that is opened up in Tomcat get associated with a write ByteBuffer. This attribute controls the size of this buffer. By default this write buffer is sized at 8192 bytes. For low concurrency you can increase this to buffer more response data. For an extreme amount of keep alive connections, decrease this number or increase your heap size. The default value here is pretty low, you should up it if you are not dealing with tens of thousands concurrent connections.
socket.bufferPoolSize
(int)The NIO2 connector uses a class called Nio2Channel that holds elements linked to a socket. To reduce garbage collection, the NIO connector caches these channel objects. This value specifies the size of this cache. The default value is 500, and represents that the cache will hold 500 Nio2Channel objects. Other values are -1 for unlimited cache and 0 for no cache.
socket.processorCache
(int)Tomcat will cache SocketProcessor objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
APR/native specific configuration
The APR/native implementation supports the following attributes in addition to the common Connector and AJP attributes listed above.
Attribute Description ipv6v6only
If listening on an IPv6 address on a dual stack system, should the connector only listen on the IPv6 address? If not specified the default is false and the connector will listen on the IPv6 address and the equivalent IPv4 address if present.
pollTime
Duration of a poll call in microseconds. Lowering this value will slightly decrease latency of connections being kept alive in some cases , but will use more CPU as more poll calls are being made. The default value is 2000 (2ms).
Nested Components
Special Features
Proxy Support
The proxyName and proxyPort attributes can be used when Tomcat is run behind a proxy server. These attributes modify the values returned to web applications that call the request.getServerName() and request.getServerPort() methods, which are often used to construct absolute URLs for redirects. Without configuring these attributes, the values returned would reflect the server name and port on which the connection from the proxy server was received, rather than the server name and port to whom the client directed the original request.
For more information, see the Proxy Support How-To.
Connector Comparison
Apache Tomcat Http Status 403

Below is a small chart that shows how the connectors differ.
Apache Tomcat 9 403 Access Denied
Java Nio Connector NIOJava Nio2 Connector NIO2APR/native Connector APRClassnameAjpNioProtocolAjpNio2ProtocolAjpAprProtocolTomcat Version7.x onwards8.x onwards5.5.x onwardsSupport PollingYESYESYESPolling SizemaxConnectionsmaxConnectionsmaxConnectionsRead Request HeadersBlockingBlockingBlockingRead Request BodyBlockingBlockingBlockingWrite Response Headers and BodyBlockingBlockingBlockingWait for next RequestNon BlockingNon BlockingNon BlockingMax ConnectionsmaxConnectionsmaxConnectionsmaxConnections

0 notes
Text
JAVASCRIPT

Java script lines end with a semicolon. It always put the text with a quotation (“”). Capital letters are different from lowercase letters. It is also case-sensitive.
Alert a standard java script command that will cause an alert box to pop up on the screen.
document. write a java script command that tells the browser what o follows within the parenthesis to be written into a document.
Variables
- Is like a storage unit that can create a variable to hold values.
- It is important to know the proper syntax which variables must conform
• They must start with a letter or underscore.
• Subsequent characters can also be digits (0-9) or letters (A-Z and/or a-z).
The document object contains arrays which store all the components constituting the contents of your web page, such as images, links, and forms.
The pre-defined objects that are most used are the window and document objects.
The window has methods that allow you to create new windows with the open () and close () methods. It also allows you to create message boxes using alert (), confirm (), and prompt (). Each displays the text that you put between the parentheses.
Arithmetic Operators - an arithmetic operators that has a++ and a--
Conditional Statements
The two different condition:
- AND, OR and NOT - It enhances your if statements that can use the so-called logical operators. It is written in && and it is used to check if more than one condition is true.
- IF and ELSE
Loops an incredibly useful programming tool. handle repetitive tasks extremely well, especially in the context of consecutive elements. It has two different kinds: for and while.
Arrays - It is defined before referring to any of variables in it.
Functions - One of the fundamental building blocks in JavaScript. A function is a JavaScript procedure -- a set of statements that performs a specific task. It has a three-function keyword: (1) A function name. (2) A comma-separated list of arguments to the function in parentheses. (3)The statements in the function in curly braces: { }
Events – actions that can be detected by java script.
Form Validation – java script is a strong tool for validating forms before sending the content.
The Technique has consist of four different functions:
Emailvalidation – check to see if a value lives up tp general syntax of an email.
Valuevalidation – check to see if a value is within a certain interval
Digitvalidation – check to see if a value consist of a certain number of digits
Emptyvalidation – check to see if a field is empty or not.
0 notes
Text
Cassandra Demo
In this second blog post, I am going to show everyone how to create your very own 3 node Cassandra cluster. You will have to have some items set up beforehand. The first item that will need to be created are three different virtual machines, each with a working operation system. In this exercise, I have created three different VM using the VMware Work Station; each with a working Linux Ubuntu OS. (Why Linux Ubuntu? No real reason, I just like that OS. Beware that for different OS, there will be different commands that I might not cover).
The second item that will need to be set up is a two-parter. Both the Java Development Kit and the Python Software Development Kit need to be functional in each VM, for Cassandra to be able to execute properly. In this exercise, I have installed the most current stable version the JDK available. The only thing I will mention, in case anyone is following along with the blog, do remember to include the following line of code in your .bashrc user profile file:
#$ export PATH=$PATH:~/Documents/jdk1.8.0_202/bin
It is the only way Cassandra will recognize that the JDK is running on your OS.
As for the Python SDK, that is a whole another animal all together. The following commands (2 commands) need to be entered on command line, within the Python directory:
#$ ./configure --prefix=/usr/local
#$ make
Once this is done, the source code for Python itself has been compiled. You will also need to download PIP, which lets you manage libraries, directories and drivers for Python. Now with the way Python works, you can have several versions of Python present on the same OS. You need to make sure the version you are working with is Python 2.7 (Documentation does say that it supports 3.6, 3.7 and 3.8). The last item you will download for the SDK is the Cassandra-driver, which lets the python interpreter talk to the ./cqlsh program (more on that later).
#$ pip install cassandra-driver.
Why both Java and Python? Cause nothing in programming in ever truly easy. Java is what your Cassandra node uses to execute its programming, because Cassandra itself was written in Java. Now, the CQL Shell or cqlsh for short is the command line shell use to interact with your Cassandra nodes. Python is the native protocol driver for this shell. There is indication when I read the cqlsh documentation, that other languages can be used for talking to the cqlsh; but for the purposes of this blog I will be using Python. I did not go into further research about that particular topic.
The last item you need to research before we can further and start the set up of our Cassandra nodes, is probably the most complicated one of them all. You need to find out the IP address for each of the VM. A simple ip addr, will do the trick. The three ip address for my VM are the following:
Cassandra Node 1 – 192.168.8.135
Cassandra Node 2 – 192.168.8.136
Cassandra Node 3 – 192.168.8.137
Once, the VMs are setup (each with a working OS, JDK, SDK and the IP address are recorded) Cassandra can finally be downloaded. I am working with the latest stable version of Cassandra 3.11.10. Once unzip, the configuration file cassandra.yaml is the only thing that needs to be modified and/or touched.
Just a quick intro before we move on. YAML (or YAML Ain’t Markup Language) is a human-readable data-serialization language, commonly used for configuration files where data is being sorted or transmitted. I just wanted to make sure everyone knows that bit of information; there is a lot more to YAML.
With that out of the way, we are going to start setting up our first Cassandra Node, or cass1. There are several things that can to be configured, but there are only two decision that have to be made in this YAML file (When looking from the perspective of this test cluster, in industry a lot more settings would be considered). The first decision is naming the cluster; for the cluster to work, all of the cluster nodes must have a shared name between them. Its how they first recognize themselves within the cluster ring. In my case, I used the cluster name ‘INTP – 362’.
Cluster Name
It is important that you make the name simple and easy to reproduce. My first test cluster had a more complicated name in the intent to be funny, and two of my nodes would not “gossip” to one another (more on gossiping later). And I used copy and paste, which sometimes does not work.
Once the cluster name is decided on. The next decision are the seed nodes and non-seed nodes. A seed node serves two functions:
When a new node joins the cluster, it will learn about the topology of the cluster or ring by contacting a seed node.
They are also what assist other nodes in gossip convergence.
A seed node is still not a single point of failure; if a seed node “dies”, a cluster can survive without. I choose cass1 and cass2 to be my seed nodes. It is industry standard to at least have 3 seed nodes per cluster; the typical small sized cluster is around 5 nodes. Since, I only have 3 nodes, I decide to just do 2 seed nodes to demonstrate what they do. To set up the seed nodes, the IP address for each of the selected nodes are to be place, in between the double quotes; separate by commas but with no spaces in between (see image below).
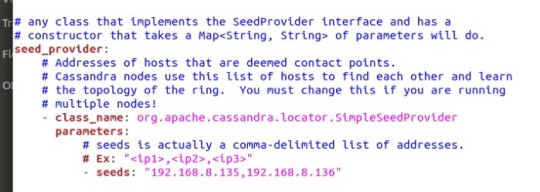
Seed Nodes
With the seeds nodes and the cluster name taken care of, the basic decision-making process to get this cluster running is done. I do want to point out that there are many other settings and configurations that can be made through this YAML file. Everything from how many concurrent read or write can be done at a time, which ports each node will use to communicate thought TCP/UDP (Ports 7000, 9042), what is a cache size for different types of operations; so many different settings I am not getting into because really there is no time. But I will speak about to two particular settings that gave a lot of problems for several days. Those are Listen Address and RPC Address.
Just to expand out knowledge base, RPC is a framework or set of tools that allow programmer to call a piece of code in a remote process. Again, there is a lot more to this framework; but that is the bare minimum just to understand why this address is important.
As a default, Listen Address and RPC Address come with the value ‘Localhost’; which should work since they do use the localhost to work. They even suggest just leaving it blank, since that will activate:
InetAddress.getLocalHost()
A protocol that will find the local IP address of the machine and retrieve for use. Except its not reliable, it even mentioned in the configuration file that it might not work. The documentation for both Cassandra and the YAML configuration file does not, to my knowledge, ever mention how to deal with this. Why do I mention this? Because in this case, the nodes will not actually wake up (at least in my experience). The actual best thing to do, is to actually use the IP Address number itself. My lesson learned here is that sometimes hardcoding an important value is necessary.
What is going on in the background is that the nodes can’t gossip. What is gossip? It’s the protocol that Cassandra uses to communicate between nodes. It’s a peer-to-peer system, that periodically exchanges state information about themselves and about other nodes in the ring. Basically, Cassandra nodes are just gossiping all the time, about how they are doing.
The gossiping protocol is very similar to the TCP three-way handshake; so much so that in the Cassandra server start up process, it is called a handshake. In the image below, you can the different Cassandra nodes handshaking each other.
Handshake
I think that is enough for now about the YAML configuration file; there is a lot more to it, entire Wikipedia pages just dedicated to explaining each one of the different settings. We are moving to yet another program that needs to be install for Cassandra to run. Why didn’t I mention this one before? Because its not mentioned anywhere (Note: I am not bitter about this).
iptables is this cool linux utility that lets you block or allow traffic, it’s a neat firewall. Cassandra needs it install and running to be able to gossip to other nodes. In iptables, there are policy chains, which are:
Input - this is for incoming connections.
Forward - incoming connections not being delivered locally, think a router.
Output - this is for outgoing connections.
Now, I only had so much time to actually research iptables and all its useful commands. Due to time constraints I concentrated on understanding the command I needed to run my Cassandra nodes. The command is:
#$ sudo iptables -A INPUT -p tcp -s 192.168.8.135 -m multiport --dports 7000,9042 -m state --state NEW,ESTABLISHED -j ACCEPT
A – Type of policy
p – Type of connection the protocol uses
s – Is the IP address to listen for
m multiport – is when there are multiple ports
dport – The ports to listen for
m state – The state of the connection (The only states I know of are NEW and ESTABLISHED)
j – Is the command for the response policy (Accept, Drop or Reject)
This command must be done on each node, with the other nodes IP address (so the command must be entered twice in each node). Finally, Cassandra will be run. There is an order to these things. Seed nodes must be woken up first before non-seed nodes, it is the only caveat to waking up Cassandra nodes to start gossiping.
To confirm that the nodes are running and gossiping, Cassandra comes with application called nodetool. The application will take different commands, the only one we care about at the moment is the status command.
Nodetool program
The UN means Up and Normal, which is really the piece of information we care about. This means each node on the rack is running. Since we have confirmed all the Cassandra nodes are up and running. The CQL shell program can be started. In the bin directory, the following commands needs to be typed:
#$ ./cqlsh 192.168.8.135
The IP address at the end of the command must be the IP address of the node you want to access. As you can see from the image below, I am still in Cassandra node 1. But I am able to access another Cassandra node though its IP address.
Accessing different nodes
With the CQL shell running, we can finally explore the CQL language. It is very similar to SQL, super similar. It is basically the same thing (at least syntax-wise it does not behave the same way), with some key exception. All the relational part of SQL is non-existent in CQL. That means no JOINS, no FOREIGN KEYS, none of that stuff. But the following commands, are all permissible (and again Syntax is the same, but the behavior of the command might be different):
Alter
Create
Delete
Insert
Select
Update
Where
There are more commands, I am just showcasing the classic ones. Let’s start with the creation of a KEYSPACE (Database in the SQL world). The command is the following:
#$ CREATE KEYSPACE test WITH replication = {‘class’:’SimpleStrategy’, ‘replication_factor’ : 3};
Finally, replication at work. There are two replication classes. The SimpleStrategy class, which will assign the same replication factor to the entire cluster. This is used for evaluation purposes, single data center test (Like what I am doing in this blog), and development environments. In industry they use the second class, called ‘NetworkTopologyStrategy’. This strategy is for assigning the replication factor to each data center in a comma separated list, giving you more flexibility and control. The Data center names must match the snitches data center name. In a real data center, there are snitch nodes; in basic terms the snitch determines which data centers and racks nodes belong to. The snitch allows network topology to be discovered, thus making routing more efficient.
A note about replication factor for both strategies, the number does not have match the number of nodes present in your cluster. It is not a requirement for the command to run. There can be a KEYSPACE with a replication factor of 2, in a 5 nodes cluster. It is documented that it is recommended that your replication factor does not exceed the number of nodes present in your cluster (But again this will not cause any immediate problems). The following command is not recommended, with my current cluster set up:
#$ CREATE KEYSPACE test WITH replication = {‘class’:’SimpleStrategy’, ‘replication_factor’ : 4};
But it is permissible. Why? The idea of scaling. I could start setting up KEYSPACEs with replication factor of 4 in my cluster right now, and add a new node (cass4) in the future.
Now that we have our KEYSPACE set up. We can now proceed to create a table and inserting some data.
#$ CREATE TABLE student (name text PRIMARY KEY, id int, age int);
#$ INSERT INTO student(name,id,age) VALUES (‘alex’,105,32);
With everything set up correctly, we can see the replication happening. I used cass1 to insert my data. And the KEYSPACE, TABLE and data was replicated into the other nodes.
Cassandra Node 1 – test data
Cassandra Node 2 – test data
Cassandra Node 3 – test data
As observed in all three different nodes, the student table is present.
The last cool thing I am going to show you, is how UPDATEs are a bit different in CQL vs SQL. In SQL an UPDATE command is both a read and a write; and this is important to note, because it first reads the tablespace and if the WHERE clause is not present the UPDATE will not happen. In CQL, the UPDATE command is only a write. This means that if the WHERE clause of an UPDATE command is based on a primary key (see example below), the UPDATE will happen as an INSERT if the row does not exist. I will showcase this in action, in the demo video.
UPDATE command in CQL
I hope this blog brought to light some of the lessons I learned while trying to navigate my way through Cassandra. Lessons like the value of documentation, but that ultimately there might be vital information missing; further research into some unexpected places might be need; and even some trial and error might be a possible avenue. I also hope I help shed some light on the world of NOSQL, and the cool application (cool to me at least) that is Cassandra.
Thank you so much for reading my blog
Here is the Demo Video.
youtube
0 notes
Text
Java : enumeration
##enumeration:
In fact, it is a special class, which is generally used to represent a variety of fixed states.
public enum name{obj1, obj2}
In fact, the enumeration class is at the bottom and inherits from the java.lang.Enum class
```
protect Enum(String name,int ordinal)
```
>This constructor cannot be called by programmers because of the code issued by the compiler in response to the enumeration type declaration.
####Parameters:
```
name--The name of this enumerated constant, which is the identifier used to declare the constant
ordinal--Ordinal number of the enumeration constant (its position in the enumeration declaration, where the ordinal number of the accident constant is zero)
```
###Enumeration class features:
```
1、Enumeration classes are safe, and objects cannot be instantiated, and objects cannot be created even by reflection
2、You can use the name () and ordinal () methods to return the instance names and ordinal numbers of enumerated objects, starting from 0.
3、All enumeration classes have static methods: value () can get all instances in the current enumeration class
4、All enumerations have static methods: valueOf can convert a String of type string into an object of type enumeration
5、Enumeration constants must be declared first, and the constants are separated by commas, and the last constant needs a semicolon (although a semicolon is not needed if no data is added later, for the sake of standardization, the semicolon shall prevail)
6、If you use () after enumerating class constants, it indicates the anonymous inner class of the current enumerated class
7、You can enumerate using the switch operation
```
Code example:
import java.util.ArrayList;
import java.util.Arrays;
import java.util.List;
import org.junit.Test;
public enum Weekday {
MON("Monday",1),
TUES("Tuesday",2),
WED("Wednesday",3),
THUR("Thursday",4),
FRI("Friday",5),
SAT("Saturday",6),
SUN("Sunday",7);
private String wik;
private int num;
private Weekday(String wik,int num){
this.wik =wik;
this.num = num;
}
public String getWik() {
return wik;
}
public int getNum() {
return num;
}
public static List<Weekday> getAll(){
return Arrays.asList(Weekday.values());
}
public static List<Integer> getValues(){
List<Integer> list = new ArrayList<>();
Arrays.asList(Weekday.values()).forEach(e->list.add(e.num));
return list;
}
public static List<String> getDesc(){
List<String> list = new ArrayList<>();
Arrays.asList(Weekday.values()).forEach(e->list.add(e.wik));
return list;
}
public static void main(String[] args) {
Weekday.getAll().forEach(System.out::println);
Weekday.getValues().forEach(System.out::println);
Weekday.getDesc().forEach(System.out::println);
}
}
0 notes
Text
X DevAPI Traffic Compression With Connector/J
X Protocol traffic compression is available on MySQL Server since version 8.0.19. A connector that also supports compression on its end can leverage this feature and reduce the byte streams that are exchanged with the Server. By default, connections to a MySQL server are uncompressed, thus permitting exchanging data with a client or connector that doesn’t support compression. However, given a client or connector that also supports compression, it is recommended that client and server negotiate the connection compression by default. If this negotiation concludes successfully, both ends can then compress the data they send. Compression at this level allows reducing the amount of bytes exchanged over the network, but at the cost of additional CPU resources required to run data inflate and deflate operations. The benefits of compression, therefore, occur primarily on low network bandwidth. One can assess the gain or loss due to the compression only after measuring properly the average traffic sizes for a period of time for both the compressed and uncompressed connections. Connector/J version 8.0.20 came out with basic support for traffic compression over X Protocol connections. For this purpose, a new connection option: xdevapi.compression, was introduced. As of Connector/J 8.0.22, this feature was leveled up with the introduction of two additional connection options: xdevapi.compression-extensions and xdevapi.compression-algorithms. Let it be clear that the new compression features in the X DevAPI has no impact whatsoever on the existing compression behavior or settings of Connector/J JDBC implementation. Compression Negotiation Enabling compression starts with a negotiation phase between the client and server when establishing new connections. The server initiates the negotiation by telling the connector what compression algorithms it supports. The connector then chooses one it also supports and replies its choice to the server. As long as the negotiation succeeds, both ends can, optionally, start compressing X Protocol messages. Some control-flow messages never get compressed—because they are too small or because of they cannot be compressed due to the need for backward compatibility with clients and servers not supporting compression; also, data messages smaller than a predefined threshold (250 bytes in the case of Connector/J) also don’t get compressed. Depending on how the connection compression is set up, a failed compression algorithm negotiation may end with an exception being thrown to the client application or fallback to a compression-disabled connection. Compression Algorithms Currently, MySQL, through the X Plugin, supports the compression algorithms Deflate, LZ4 and zstd. These algorithms are referred to by an identifier composed of two parts—the algorithm name and an operation mode: deflate_stream lz4_message zstd_stream The operation mode, stream or message, determines how the deflater and inflater procedures operate. In the stream mode, all X Protocol messages from a single connection are compressed into a continuous flow (stream) and their decompression must be done the same manner—following the order they were compressed and without skipping any message. In the message mode, each message is compressed individually and independently, so that the order by which the messages are decompressed needs not be the same as the order they were compressed. Also, the message mode does not require all compressed messages to be decompressed. By default, Connector/J negotiates a compression algorithm following the priority recommended by X DevAPI: first zstd_stream, then lz4_message, and finally deflate_stream. In all Connector/J options where a compression algorithm identifier can be specified , the aliases “zstd”, “lz4”, and “deflate” can be used instead of “zstd_stream”, “lz4_message”, and “deflate_stream”, respectively. Default Compression Note that Connector/J provides out-of-the-box support for Deflate only. This is so because none of the other compression algorithms are natively supported by the existing JREs. The other algorithms can still be used though, as explained below. Given that the server has X Protocol compression enabled, Connector/J by default tries to negotiate connection compression in all X DevAPI sessions. In the negotiation, Connector/J and the server attempt to mutually agree on the compression algorithm deflate_stream; and if the negotiation fails, they fall back on non-compressed connections. This behavior corresponds to the connection option xdevapi.compression=preferred available since Connector/J 8.0.20. Besides preferred, the connection option xdevapi.compression takes two other values: disabled and required. These options, respectively, disable compression altogether (by not even starting any negotiation efforts), or enforce compression and throw an exception in case of an unsuccessful negotiation. Setting up Additional Compression Algorithms In order for Connector/J to support the compression algorithms LZ4 and zstd, the client application must provide some implementation for the corresponding deflate and inflate operations in the form of an OutputStream and an InputStream object, respectively. The easiest way to accomplish this is by using a third-party library such as the Apache Commons Compress library, which supports both algorithms. The connection option xdevapi.compression-extensions, introduced in Connector/J 8.0.22, allows configuring Connector/J to use any compression algorithm that is supported by MySQL Server, as long as there is a Java implementation for that algorithm. The option takes a list of triplets separated by commas. Each triplet in turn contains the following elements, delimited by colon: The compression algorithm name, indicated by the identifier used by the server. A fully-qualified class name of a class implementing the interface java.io.InputStream that will be used to inflate data compressed with the named algorithm. A fully-qualified class name of a class implementing the interface java.io.OutputStream that will be used to deflate data using the named algorithm. Here’s an example that sets up the support for the algorithms lz4_message and zstd_stream using the Apache Commons Compress library: String connStr = "jdbc:mysql://johndoe:secret@localhost:33060/mydb?" + "xdevapi.compression-algorithm=" + "lz4_message:" // LZ4 triplet + FramedLZ4CompressorInputStream.class.getName() + ":" + FramedLZ4CompressorOutputStream.class.getName() + "," + "zstd_stream:" // zstd triplet + ZstdCompressorInputStream.class.getName() + ":" + ZstdCompressorOutputStream.class.getName(); SessionFactory sessFact = new SessionFactory(); Session sess = sessFact.getSession(connStr); Collection col = sess.getDefaultSchema().getCollection("myCollection"); // (...) sess.close(); With this connection string, Connector/J negotiates the compression following the recommended order: first zstd, next LZ4, and finally Deflate. The final choice depends on what algorithms are enabled on the server. As compression is not required by default, if the negotiation fails, the connection won’t be compressed, but the client will still be able to communicate with the server. Influencing Compression Negotiation Assuming Connector/J has been configured with extensions that enable additional compression algorithms through setting the connection option described in the previous section, the algorithms and the order by which they are attempted in the negotiation phase can be customized by setting the third compression related connection option—xdevapi.compression-algorithms. The connection option xdevapi.compression-algorithms takes a list of compression algorithms identifiers and is used to override the default order by which the compression algorithm is negotiated. Only the enumerated algorithms are attempted during the negotiation, thus, it also allows to specify which algorithms to enable from the client side. Note how this works similarly to the server global variable mysqlx_compression_algorithms (also available as a command line option), except that, if configured from the client side, different X DevAPI sessions can be set with different compression algorithms while, if configured from the server side, all sessions are forced to negotiate for the same compression algorithms. Unknown algorithms specified in the option xdevapi.compression-algorithms are simply discarded. However, if such algorithms are also configured in the connection option xdevapi.compression-extensions, then they become options during the compression negotiation, as long as the server also supports such algorithms, then they can be effectively used, thus making this a fully pluggable feature in Connector/J. Disabling compression can be done from the client side, via the connection option xdevapi.compression=disabled, or from the server side, by setting the server variable mysqlx_compression_algorithms to an empty string. It is, however, not possible to completely disallow uncompressed connections from the server side. Profiling Compression Efficiency Connector/J does not provide any metrics regarding ratio of compressed vs. uncompressed payloads. However, some metrics can be obtained from the server through its status variables Mysqlx_bytes_received, Mysqlx_bytes_received_compressed_payload, Mysqlx_bytes_received_uncompressed_frame, Mysqlx_bytes_sent, Mysqlx_bytes_sent_compressed_payload, and Mysqlx_bytes_sent_uncompressed_frame. Typically the compression ratio obtained from the client side can be calculated using the following formula: Mysqlx_bytes_received_uncompressed_frame / Mysqlx_bytes_received_compressed_payload And the efficiency of compression for X Protocol messages sent by the connector can be calculated using the following formula: (Mysqlx_bytes_received - Mysqlx_bytes_received_uncompressed_frame + Mysqlx_bytes_received_uncompressed_frame) / Mysqlx_bytes_received Similar calculations can be made for data compressed on the server side, as documented in the MySQL Reference Manual. Additional Information and Resources Connection Compression Using X DevAPI Connection Compression with X Plugin mysqlx_compression_algorithms Apache Commons Compress Zstd-jni I invite you to join the MySQL Community on Slack and hang out in the #connectors channel: MySQL Community on Slack https://insidemysql.com/x-devapi-traffic-compression-with-connector-j/
0 notes
Text
Python Tutorial: Nail PYTHON LIST In 10 Min, List trick.

Introduction to Python Lists.
Hola and welcome to today's Python Tutorial on "Python lists and its functions". In this, tutorial you'll learn the basics of python lists and its various function with example. Python lists are similar to an array of programming language but "Lists in Python" are more powerful in terms of functionality and are flexible in usage.
Lists in Python.
All programming language used data structure to store and manipulate data. The List data type in python is similar to array in C++ or Java or Python or Tables in COBOL. A Python Lists can be used to store, manipulate and retrieve data element as per business requirements. You can store different types (i.e. string and integer data) of data elements in the lists and lists can grow dynamically in memory. In laymen term, A list is similar to an array that consists of a group of elements or items. Just like an array, a list can store elements. But, there is one major difference between an array and a Python List. An array can store one kind of data whereas a list can store different type of the data. Thus, Python Lists are more versatile abd useful than array. List in Python are most widely used datatypes in Python program. Python Lists are easy to define and flexible to use in Python programs. In order to define a list in python, you need to enclosed data items in between square brackets. You can also use various list function to add, append, remove, update, search and delete data items from the Python Lists. Python Lists can grow dynamically in memory. But the size of any array is fixed and they cannot expand during the run time.Python Lists can store different types of data i.e. (String or Numeric), but in the array you can only store a single type of data at a time.
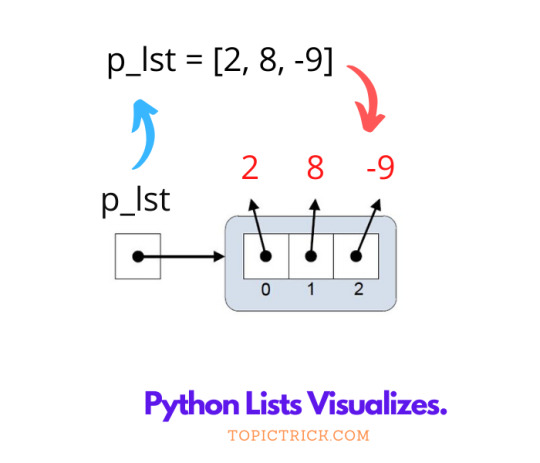
Python Lists Visualization.
How Python Lists Works?
Imagine you went to a shopping mall for shopping grocery items. Each time you pick an item from the shelf you scan it with the scanner before placing the item into your basket. The scanning machine stores the scanned item into machine memory. It also displays the list of items on the screen in the order in which item was scanned. You can visualize this scanner machine as a 'Python list' which is storing items in a sequence after being scanned on the machine. In the following example, shp_lst is a Python List which will store the name of purchase items, every time you scan an item with scanning machine, the item is added/appended to list shp_lst and index is updated. You can access these store items from shp_lst list by using python for .. loop or by other python functions and accessing list item is pretty simple and straight forward. You will learn to perform various operation on lists in later part of the Python Tutorial
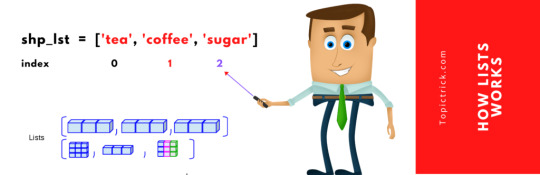
How list in python works.
Python Lists and List functions.
Lists in Python are primarily used to store data in a sequence. A list is a list in itself and it can store different type of data. Lists in python are defined by square brackets and each data item is separated by ',' comma-delimited. Python list provides many in-build functions that can be used to manipulate data in the lists. Now, let's discuss all lists function in details: Example 1: How to create lists in Python? # Define an empty Lists in Python. shp_lst = # Define Lists in Python with integer items only. shp_lst = # Define Lists in Python with strings items only. shp_lst = # Define Lists in Python with mixed items. shp_lst = # Print Python Lists elements. print(shp_lst) Example 2: Python range() Function to create lists. # Python range() function. num_lst = list(range(1,10,1)) num_lst Example 3: For loop to create Python lists. # Python for loop function. a = for i in range(1,10,1): a.append(i) print ('Print List Value:' a) Example 4: Update the elements of lists. # Update first element of the lists. a = a = 2 Example 5: Concatenate two python lists. # Concatinate two Python lists. a = b = print ('Concatinate List :', (a+b)) Concatinate List : How to get individual items in a the list with Indexes and Slicing? By now you have understood that list in python is a sequence data sets. You can store a similar value of different values as per requirements and you know that each item has an associated index. You can use this index to access lists values. Python Lists start with zero and index is incremented by one every time an item is added or appended to the list. The process of creating a new python list from an existing list is termed as slicing operations. Slicing represents extracting a piece of the list by mentioning starting and ending position numbers.Syntax :: list_name list_name - Name of existing list variable. start_position - starting index position. end_position - end of index position.step size - the gap between items, the default step size is 1. Example 2: Python Lists Indexing and Slicing. # Create shp_lst shopping Lists in Python. shp_lst = # Print third element of the shp_lst list. shp_lst 'salt' # Print the second and third element of the shp_lst list. shp_lst # Create a new List from the existing shp_lst List. shp_lst_sl = shp_lst shp_lst_sl # Print last 2 items of the shp_lst List using negative indexes. shp_lst

Lists in Python with additional methods/functions.
Python Lists and Function.
As you know, Lists in Python are a powerful data set and are equally flexible to use. Python Lists provides many additional function/methods that can be used to perform many data manipulation operations on the lists. Let's discuss all these functions one by one with examples: Python List Append Method. The Python List append method is used to append items at the end of the list. In the following example, a new item would be added to the list.list.append(x)# Create shopping shp_lst Lists in Python. shp_lst = # Append jam item to the shp_lst Lists. shp_lst.append('jam') # Print the items of the lists. shp_lst Python List Extend Method. The Python List extends method is used to append all items from another list. In the following example, all items from shp_ext_lst will be added to the existing shopping list. list.extend(iterable)# Create shp_lst Lists in Python. shp_lst = # Append items from shp_ext_lst List to the shp_lst List. shp_ext_lst = shp_lst.extend(shp_ext_lst) # Print the List (shp_lst). shp_lst Python List Insert Method. The Python List insert method is used to insert an item at a specific location in the list. You need to specify the position where you want to insert value in the list. list.insert(i, x)# Create shp_lst shopping Lists in Python. shp_lst = # Insert a new item at the second position. shp_lst.insert(1,'jam') # Print the shopping list (shp_lst). shp_lst Python List Remove Method. The Python List Remove method is used to remove the item from the Python list. You need to specify the value that you want to drop from the list. Also, if your list has duplicate value then remove method will only remove first value and will retain second value. If the value is not present in the list then it will throw an error (i.e. list.remove(x): x not in list). list.remove(x)# Create Programming Language lists in Python. pgm_lst = # Remove item from the pgm_lst list. pgm_lst.remove('CICS') # Print the programming language list (pgm_lst). pgm_lst # Programming Language lists in Python. pgm_lst = # Remove an item from the list. pgm_lst.remove('JAVA') # Print the programming language list (pgm_lst). pgm_lst Python List Pop Method. The Python List POP method is to remove the specific item from the list. You are required to specify the position of the item as a parameter. list.pop()# Create programming language pgm_lst Lists in Python. pgm_lst = # Drop list last data item. pgm_lst.pop() # Print the programming list (pgm_lst). pgm_lst # Programming language lists in Python. pgm_lst = # Remove specific item from the list. pgm_lst.pop(3) # Print the programming language list (pgm_lst). pgm_lst Python List Clear Method. The Python List clear method is used to clear items from the lists. list.clear()# Programming Language lists in Python. pgm_lst = # Clear item from the list. pgm_lst.clear() # Print the programming list (pgm_lst). pgm_lst Python List Index Method. The Python List Index method is used to get the index of the item. You are required to specify the item name as a parameter. If the item is not present in the list then it will throw an error message.list.index(x])# Programming Language lists in Python. pgm_lst = # Get index of the item from the list. pgm_lst.index('CICS') 1 Python List Count Method. The Python List Count method is used to get the count of specific items in the list. You need to specify the item as an argument. list.count(x)# Programming Language lists in Python. pgm_lst = # Clear item from the list. pgm_lst.count('COBOL') 1 Python List Sort Method. The Python List Sort method is used to arrange items in the list. Python list sort has two parameters i.e. Key=None and reverse=False. list.sort(key=None, reverse=False)# Programming Language lists in Python. pgm_lst = # Sort item in the list. pgm_lst.sort() pgm_lst # Sort item in the list. pgm_lst.sort(key=None,reverse=True) pgm_lst Python List Reverse Method. The Python List Reverse method is used to reverse the order of items in the list. list.reverse()# Programming Language lists in Python. pgm_lst = # Reverse the order of items in the list. pgm_lst.reverse() pgm_lst Python List Copy Method. The Python Lists copy method is used to copy an item from one list to others.list.copy()# Programming Language lists in Python. pgm_lst = # Reverse the items sequence in the list. a = pgm_lst.copy() a Python List Sum Function. The Python Lists sum method is used to retrieve the sum of all elements of the list.list.sum()# Programming Language lists in Python. a_lst = # Get sum of all items. print('The sum of all list items :', sum(a_lst))
Lists in Python Live Coding Demo.
https://youtu.be/dyZyHaXZb-8
Conclusion.
Finally, we reach an end of today's tutorial on List in Python. By now, you have understood the basics of Lists in Python. You've also learned about various inbuilt function for performing various data manipulation operations. In our next python tutorial, you will learn more about Tuple. If you like our tutorial, please don't forget to share with your friend and family and do leave your valuable feedback. Your comments are valuable to us. Read the full article
0 notes