#logout device
Explore tagged Tumblr posts
Text
Trouble logging out of Netflix on your Smart TV? Here's how to fix it quickly and easily
0 notes
Text
Self aware anaxa (or any of the amphoreus cast at this point), and how he'd likely have a very different experience becoming aware post 3.2 has been all I can think about recently. This is more of a warm-up/ drabble with the idea before I flesh it out more. Just trying to find a way I feel comfortable writing him at the moment.
Masterlist

He was dead, that much he could be sure of. His plan to fuse his soul with the titan Cerces to become the titan in the next cycle was successful; he had felt his body dissolve and had dropped the core flame into the vortex of Genesis.
So, how was he here?
No matter, as the demised scholar Anaxagoras, time is the only thing preventing him from knowing the truth.
Ultimately, every time he made any progress in finding out what was happening some other odd trait about his current predicament made itself aware. It started small, music playing as he was going about amphoreus, the area around him pausing here and there, barely noticeable.
Then the events started to escalate, he discovered that he couldn't speak to anyone. In fact, whenever he went to try he had the intriguing yet infuriating feeling of being absent from reality for the conversation made itself apparent, the sensation of not being in full control of his body at times eventually growing to all of the time and then there was the fight against Aquila.
That seemed to act as the catalyst for these strange phenomena, as everything intensified afterwards. Shortly after the conclusion of the fight…
He was no longer on Amphoreus.
He didn't have control of his body, fights were taking turns, chests were littered behind puzzles, it was like he was skipping around in time and visiting events and battles that should have long since passed.
It was as if someone was playing a game.
It was as if someone was playing a game.
And suddenly that hypothesis made sense. Rooting itself in the professor's mind, all he needed now was proof. Proof that there was a player. Then he could work on a method to make himself real, to gain power over his new reality. This new truth.
Naturally, he met or rather interacted with you, shortly after this revelation. It didn't immediately click that you were the player, the person for whom he was essentially a glorified puppet, but it did in time.
He didn't intend to fall for you.
Of course, he hadn’t yet, no matter how purely logical he tries to be. Well. Don’t romance and reason go hand in hand, he shouldn’t feel ashamed to embrace such feelings.
Try as he might, he couldn’t catch your attention no matter what actions he took. Triggering voice lines where and when he shouldn’t be able to; wrenching control back for the briefest of moments; sneaking extra rewards into your inbox, no jades of course, he couldn’t be too obvious for his safety; and even sending more in game messages than he was scripted with, given half of them are obscured behind anonymous icons. All for nought as you simply dismissed it all as glitches or simply lag from whatever device you were using to run it.
It drove him insane. Bit by bit, denial after denial of his existence, you weren't questioning any of it. But fine. That's fine. He'll just have to work harder.
The actions he takes get more prominent, more daring. It's not a simple matter of clueing you into it anymore, he has to prove his existence to you now. It's not something the professor is entirely used to, usually proving his own theorems to himself, others are rarely worth his time.
One day he decides to clear out the rest of the team you'd assigned him to, hoping that if you logged in to him and only him then something might finally register. It succeeds in a way, gaining him a panicked logout from you when you noticed how every character other than Anaxagoras was knocked out.
Progress.
Small, but there. Tangible, real. He'd make you fall for - see him, in time.
It’s no longer something in short supply now that he'd already fulfilled his position in the plot.
#I have returned to my roots#utterly adore this man though#anaxa x reader#anaxagoras x reader#anaxa x you#anaxagoras x you#self aware au#sentient au#self aware hsr#self aware honkai star rail
84 notes
·
View notes
Note
I use a password manager, but I've never understood one thing and I was hoping you could help: why exactly is a third-party password manager better than the one built into firefox?
Two main reasons: Security and Portability.
Security because most people don't actually log out of their browser accounts all that often and that means that anybody with access to your device has pretty much constant access to your passwords. My password manager is set to a 15-minute logout, browser managers don't really do that.
Portability because okay say you're out in the world and you need to access your passwords but you don't have access to your preferred browser. Maybe you're on campus and your battery died, or maybe you were on a fun boat trip and your laptop bag fell into the sea with your computer and your cellphone in it. Just. Imagine you're in a scenario where you are somewhere that you need to use a computer that won't allow you to install firefox. How do you get your passwords? Heck, imagine you're at a friend's house using their computer and they WILL allow you to install firefox - will you remember to log out of your account when you're done doing what you needed to do? Do you trust your friend and everyone who has access to their device not to use your passwords if you forget to log out?
Bitwarden has an entire website where i can go and access my vault if I can't use the app on my phone or the extension in my browser for some reason. I can get to my password manager from any device that will connect to the internet and I don't need to convince a friend to let me install an app on their cellphone or a librarian to let me install firefox on a desktop in order to do so, and all i have to do to prevent people from accessing my password manager when i'm done is close the window.
184 notes
·
View notes
Text
this will be very funny if I logout on this device and cannot get back in.
#.bullshit ( ooc )#The chance of that is low but never 0 but also this is the one blog other than some other dead asshole that I have impressive blog#Recovery notes about but I’ve been up since four am shooting problems out of the air#Nap time and writing asks then I’ll get into my multi and write Viv and Bel’s pages everyone else can wait#I’m gonna start with bel; Viv and Fergus ( he is part of the girl group )#Also: tepid if I can’t get back in I’m killing him | tepid: snoring | me: wonderful
8 notes
·
View notes
Text
Jimin needs your help
Puppykitties, Jimin is up for an award. He worked for ten straight months on FACE. He earned the highest first week sales record. He made history as the first Korean soloist to capture BB Hot 100 #1.
This award show is three days before his birthday and it's very likely he will attend. As a show of ARMY's love and appreciation, we shouldn't let him leave empty handed.
I'm going to walk you through how you can help under the cut.
A few things to know:
We have less than five days. Voting stops at 6pm KST 10/02 (5am EST).
Voting resets every day at noon EST.
One email account = one vote per day.
Gmail lets you make an unlimited number of free email accounts. (Hint: I have 10 gmail "fandom personas" I use for buying, streaming, and voting.)
You go to this link HERE.
Go ahead and select your device settings so that it auto translates to English.
Go to LOGIN. Create an identity using one of your Google email accounts. It will ask you for a name, birthdate, country, and phone number. I like to use things I can easily remember and that are in the right area code for where my computer is set up.
Once you have created an identity for this site (it remembers you later), you go ahead and scroll all the way down to select JIMIN and then NO.
You say no because you are not trying to get a ticket to the award show--you just want to quickly get through the vote.
It will ask you if you are sure because you can only vote once per day. Click you are sure, and you can scroll up to see CURRENT STATUS if you're curious to see how Jimin's doing in the poll.
Then you LOGOUT and repeat these steps for each gmail account you have. You do this every day until the clock runs out.
At this moment in time, Jimin is right behind Lim Youngwoong with a 5% gap. (For perspective, we made up a 10% gap just today, but it requires everyone to PUSH.)
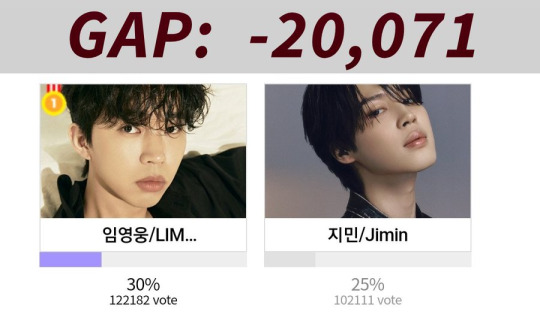
You know those lovely Korean ajumas love them some Lim Youngwoong, and he seems like a straight-up decent fella, but our Jimin deserves to be recognized for his hard work on his first solo project. The ajumas are currently asleep, but they will wake up around 9pm EST and start voting again, and they take it Real Serious.
We need every ARMY to make at least five accounts (ten is better) and vote for Jimin once a day for the next five days. BTS should always win fan-voted awards.
Side Note: I recognize there was some controversy because during the first two rounds of this survey, Yoongi fans had voted him in the lead. Then yesterday, haters started dragging Jimin to hell and back in the award site comments and on Twitter. That, of course, was a rallying cry for Jimin fans. You can love or hate Jimin solos, but you have to acknowledge they are organized and dedicated.
Now Jimin is in the lead, and ARMY must pivot from voting for Yoongi to voting for Jimin, if they wish to follow the "vote for whoever is in the lead" guideline. Splitting the votes will assure the ajumas win. I'm not going to argue with you if your conscience dictates you vote differently. It's YOUR vote; that is your private business.
But I believe that no amount of distaste for fans should overshadow your love for a member. And of all the BTS members, Jimin is the only one who has never won an end-of-the-year award, and he will likely be in service the next time the opportunity comes up, so I hope we can all row together and get this race won.
I wish you best of luck, ARMY. Let's get it!
Love, Roo

#jimin#park jimin#jikook#i'm putting jikook in the tags because jimin is one half of jikook but feel free to block me if that drives you crazy i understand my dears
81 notes
·
View notes
Text
Today's adventures in google annoyance:
I wanted a wordcount goal timer thing like on 4thewords (urgh subscriptions) for google docs (where all my fics are)
The adventure starts in the get addons menu, the Google Workplace Marketplace, to see if an addon for this already exists.
Let me tell you. If you thought regular google search results were bad. These results are a whole new level of bad. Check out results for the search "timer"

I expected a bunch of productivity timers but nope, these are the results. All of the results. There was no scroll. That's it. Don't bother trying to rationalise relevence, they turned up on basically anything i searched. Just nonsense AI results.
I eventually found one add-on that might've been close enough, but all the latest reviews were variations upon the developers broke it to make people use their app / website instead.
So I'm like fine, I'll make my own. There's a whole pile of reference docs here, I'm supposed to be a web developer, it shouldn't be too hard.
So I pressed the apps script button.
It didn't fuckin work.
It gets itself into an infinite redirect loop bc it cannot handle that I am trying to do this on an account that is not my "default" google account.
So I'm like. fine. I'll go to script.google.com manually and switch accounts in the corner. (this was apparently also a mistake, but we shall get to that Later)
So I can finally access the app script editor. start making some small test functions to see how things work. Okay, so I just need to find the function to get the document's word count. because google docs will display the word count for you, there has to be a function in here that returns the wordcount, right? Right?
Wrong.
So a bunch of searching and i have found this rwally neat custom function for the job from a user on stackexchange, but it wants a DocumentApp object which you get with .getActiveDocument(). yeah i would like it to work on whatever document i wanna use it with and not have to edit in a document ID. So I just gotta connect this script to a doc, right?
There is no way to connect an existing script file to a new document. If you wanna attach your script in a new document, you just gotta copy the script... go to the apps script button in the menu... and paste it in there...
The apps script button. That didn't work.
So I'm like okay I'll just go change which of my google accounts is the default google account so it won't get stuck in the infinite redirect loop anymore.
There isn't a way to change which of your logged in accounts is the default. It just assigns whichever one you logged into First and you cannot change that without logging out and logging back in in the Specific Order you want them to appear.
So i think, well I don't really use this one that's default on this device anymore, I'll just log out of that one (assuming the next on the list would be bumped up to default).
There is no logout button. Not for a single account. There's only a sign out of All google accounts button. So my only option to sign out of this one account I don't rly use anymore. Is to sign out of All of my google accounts.
I did not expect the challenge in this idea to be not the learning to use apps script docs api things. but just getting these google products to Function well enough to let me.
I am considering trying to make a browser extension instead. For Firefox.
6 notes
·
View notes
Text
Building a Mobile-First CRM: UX Considerations for Developers
As teams become increasingly mobile and remote, CRMs must function seamlessly on smartphones and tablets. A mobile-first CRM isn’t just a responsive design — it’s a rethinking of how users interact with features in real-time, on the go.

Here are key UX considerations developers should prioritize when building mobile-first CRM solutions:
1. Simplified Navigation
Use a bottom-tab or collapsible hamburger menu for easy one-hand use
Prioritize the most-used features on the home screen
Limit user interactions to 2–3 taps to access critical tasks
Avoid overloading the interface with too many options
2. Offline Access and Sync
Allow users to access records even without internet connectivity
Auto-sync changes once the device goes online
Use local caching for smooth experience during field operations
Maintain data accuracy across devices
3. Touch-Optimized Interactions
Design larger touch targets for forms, buttons, and menus
Use swipe gestures for actions like delete, archive, or assign
Minimize typing by offering dropdowns, toggles, and voice input
Focus on finger-friendly UI patterns over mouse-based ones
4. Performance and Speed
Optimize loading times with lazy loading and minimal animation
Compress images and minimize API payloads
Use skeleton loaders to improve perceived speed
Reduce background processes that drain battery
5. Context-Aware Functionality
Trigger location-based reminders or check-ins for sales reps
Show recently accessed contacts or tasks upon app launch
Personalize dashboards based on time of day or past activity
Custom CRM apps can dynamically adapt to user context
6. Data Entry Efficiency
Pre-fill forms with known user data
Add barcode/QR code scanning for quick product or ticket lookup
Use camera access for attachments and visual records
Minimize scrolling with accordion or segmented layouts
7. Notifications and Alerts
Send real-time push notifications for leads, meetings, and updates
Group notifications logically to avoid spamming users
Allow users to customize alert preferences within settings
Deliver actionable alerts with quick action buttons
8. Security on Mobile Devices
Require biometric or PIN login on app launch
Encrypt stored data and use secure authentication APIs
Set auto-logout for idle sessions
Mobile CRM security must match or exceed desktop-grade protection
#MobileFirstCRM#UXDesign#CRMDevelopment#UserExperience#MobileUX#CRMApps#SalesOnTheGo#CRMDesign#CustomCRM#TouchUI
2 notes
·
View notes
Text
Penting untuk Cek Akun Google Kita Terhubung ke Perangkat Mana Saja
Kaget, tiba-tiba ada banyak data asing di gdriveku. Data itu bukan milikku. Sayangnya baru kusadari setelah sekian lama! Tidak ingat bagaimana akun google ku bisa terhubung ke orang lain. Ini menjadi merepotkan karena aku harus memilah dan hapus banyak data itu. Alhamdulillahnya tidak ada penyalahgunaan. Tapi kusadari, kondisi ini bisa jadi bahaya jika di dalam akun kita ada data penting / data pribadi. Sementara akun kita terhubung ke perangkat asing yang kapanpun bisa akses data-data kita. Oleh karenanya, penting bagi kita untuk cek dan ricek, akun google kita terhubung di device mana saja. Segera logout jika ada perangkat asing. Bagaimana cara tau akun google kita terhubung ke perangkat mana saja? 1. Buka akun google https://www.google.com/ > klik menu titik-titik 9 pojok kanan atas

2. Klik Account

3. Klik Security > cek di menu Your Devices


Jika ada perangkat asing, bagaimana cara agar akun kita terlog out dari perangkat tersebut? 1. Pada menu yang sama tsbt diatas, klik My Devices 2. klik device yang ingin agar akun google terlogout> klik Sign out

3. Klik sign out

Selesai Panduan video: https://www.loom.com/share/e00fbc4cec3b4cfdb139c8a4deb5e517 Demikian
12 notes
·
View notes
Note
Have you explored what apps and programs the computer has?
a little bit. there's a steam account here. i've poked at the games a little. no saved social media accounts other than this though...
huh. maybe they logged in on other devices, and forced a logout remotely...
2 notes
·
View notes
Text
I work in IT and have some recommendations that can help prevent scams like this!
1. Never follow a direct link unless you’re 100% sure it goes where it says it will go (for example, if you just signed up for a service and it sent you a confirmation link, that’s ok because it’s one that you are expecting. Even then, I recommend hovering over the link if you’re on desktop to make sure the url matches what it says it is). If you’re not sure, go to your browser and go to the site directly instead of clicking the link.
2. Make sure everything lines up. Are there misspellings? Does the email address make sense? When you hover over the sender, does it match what it says it should be? If it’s from a certain service, should that service have access to this email account (ex: I don��t have any social media connected to my work account, so any emails from them sent there would be suspicious)? If any of this feels off, dig a bit deeper before going ahead with it.
3. If it’s a phone call from the bank/anything else that seems urgent but requires personal info to validate, call them directly. You can even save the phone number so that if you get a call from someone who isn’t that number but claims to be, you know something might be up.
3b. If it’s a message or call from a family member or friend, but is very vague/asks for personal info/requires you to click a link, contact them directly. I keep seeing these Facebook posts that friends get tagged in which are just a link to a “video” with a caption like “is this you?” Or “I can’t believe they’re gone.” If you see anything like that, definitely let the friend/family member who posted it know so they can change their passwords. This is less common, but I’ve also seen people talking about AI voice replications being used to scam people- calling and pretending to be a family member in an emergency. I’m not sure if this is something that’s actually happening or more of an urban legend, but if you do get a call like this, obviously don’t send them any money or share any personal info unless they’re able to first provide proof that they are who they say they are. Personally, if any of my family members were in an emergency, I doubt they would be asking for money or my card info.
4. Scams and phishing are built on social psychology. It’s much easier to feed off a person’s fear/stress than it is to hack into a system externally. Are you being given an urgent call to action? Is there a threat of negative consequences if you don’t act quickly? If so, you are very likely being scammed. Once again, try to access whatever it is from an external source (call/go to the website yourself) to validate whether the issue is real. Bank calling about fraudulent charges? Check your online banking app or call the bank back. Subscription is lapsing and you should renew now to get 20% off? Go to the site and see for yourself if that’s the case. Login from an unrecognized device? Go to the page, change the password and log out from all devices.
5. If you ever get a double login screen, close out of the site, retype the url and try again. If you click a link and it takes you to a login screen (I’m sure you’ve all realized the pattern here by now) go to the site directly and login from there.
6. If you’re at all concerned that you may have fallen for a scam, that’s ok! It happens! It’s time to change your passwords, logout of the service on all devices, and (if it’s a bank or something else with sensitive info) contact the service and inform them of the potential issue.
7. Trust your gut. While you may not be consciously aware that something is off, a lot of times there are cues that we pick up on without even realizing. If it seems even remotely fishy, it’s *always* better to be safe than sorry.
How I got scammed

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/02/05/cyber-dunning-kruger/#swiss-cheese-security

I wuz robbed.
More specifically, I was tricked by a phone-phisher pretending to be from my bank, and he convinced me to hand over my credit-card number, then did $8,000+ worth of fraud with it before I figured out what happened. And then he tried to do it again, a week later!
Here's what happened. Over the Christmas holiday, I traveled to New Orleans. The day we landed, I hit a Chase ATM in the French Quarter for some cash, but the machine declined the transaction. Later in the day, we passed a little credit-union's ATM and I used that one instead (I bank with a one-branch credit union and generally there's no fee to use another CU's ATM).
A couple days later, I got a call from my credit union. It was a weekend, during the holiday, and the guy who called was obviously working for my little CU's after-hours fraud contractor. I'd dealt with these folks before – they service a ton of little credit unions, and generally the call quality isn't great and the staff will often make mistakes like mispronouncing my credit union's name.
That's what happened here – the guy was on a terrible VOIP line and I had to ask him to readjust his mic before I could even understand him. He mispronounced my bank's name and then asked if I'd attempted to spend $1,000 at an Apple Store in NYC that day. No, I said, and groaned inwardly. What a pain in the ass. Obviously, I'd had my ATM card skimmed – either at the Chase ATM (maybe that was why the transaction failed), or at the other credit union's ATM (it had been a very cheap looking system).
I told the guy to block my card and we started going through the tedious business of running through recent transactions, verifying my identity, and so on. It dragged on and on. These were my last hours in New Orleans, and I'd left my family at home and gone out to see some of the pre-Mardi Gras krewe celebrations and get a muffalata, and I could tell that I was going to run out of time before I finished talking to this guy.
"Look," I said, "you've got all my details, you've frozen the card. I gotta go home and meet my family and head to the airport. I'll call you back on the after-hours number once I'm through security, all right?"
He was frustrated, but that was his problem. I hung up, got my sandwich, went to the airport, and we checked in. It was total chaos: an Alaska Air 737 Max had just lost its door-plug in mid-air and every Max in every airline's fleet had been grounded, so the check in was crammed with people trying to rebook. We got through to the gate and I sat down to call the CU's after-hours line. The person on the other end told me that she could only handle lost and stolen cards, not fraud, and given that I'd already frozen the card, I should just drop by the branch on Monday to get a new card.
We flew home, and later the next day, I logged into my account and made a list of all the fraudulent transactions and printed them out, and on Monday morning, I drove to the bank to deal with all the paperwork. The folks at the CU were even more pissed than I was. The fraud that run up to more than $8,000, and if Visa refused to take it out of the merchants where the card had been used, my little credit union would have to eat the loss.
I agreed and commiserated. I also pointed out that their outsource, after-hours fraud center bore some blame here: I'd canceled the card on Saturday but most of the fraud had taken place on Sunday. Something had gone wrong.
One cool thing about banking at a tiny credit-union is that you end up talking to people who have actual authority, responsibility and agency. It turned out the the woman who was processing my fraud paperwork was a VP, and she decided to look into it. A few minutes later she came back and told me that the fraud center had no record of having called me on Saturday.
"That was the fraudster," she said.
Oh, shit. I frantically rewound my conversation, trying to figure out if this could possibly be true. I hadn't given him anything apart from some very anodyne info, like what city I live in (which is in my Wikipedia entry), my date of birth (ditto), and the last four digits of my card.
Wait a sec.
He hadn't asked for the last four digits. He'd asked for the last seven digits. At the time, I'd found that very frustrating, but now – "The first nine digits are the same for every card you issue, right?" I asked the VP.
I'd given him my entire card number.
Goddammit.
The thing is, I know a lot about fraud. I'm writing an entire series of novels about this kind of scam:
https://us.macmillan.com/books/9781250865878/thebezzle
And most summers, I go to Defcon, and I always go to the "social engineering" competitions where an audience listens as a hacker in a soundproof booth cold-calls merchants (with the owner's permission) and tries to con whoever answers the phone into giving up important information.
But I'd been conned.
Now look, I knew I could be conned. I'd been conned before, 13 years ago, by a Twitter worm that successfully phished out of my password via DM:
https://locusmag.com/2010/05/cory-doctorow-persistence-pays-parasites/
That scam had required a miracle of timing. It started the day before, when I'd reset my phone to factory defaults and reinstalled all my apps. That same day, I'd published two big online features that a lot of people were talking about. The next morning, we were late getting out of the house, so by the time my wife and I dropped the kid at daycare and went to the coffee shop, it had a long line. Rather than wait in line with me, my wife sat down to read a newspaper, and so I pulled out my phone and found a Twitter DM from a friend asking "is this you?" with a URL.
Assuming this was something to do with those articles I'd published the day before, I clicked the link and got prompted for my Twitter login again. This had been happening all day because I'd done that mobile reinstall the day before and all my stored passwords had been wiped. I entered it but the page timed out. By that time, the coffees were ready. We sat and chatted for a bit, then went our own ways.
I was on my way to the office when I checked my phone again. I had a whole string of DMs from other friends. Each one read "is this you?" and had a URL.
Oh, shit, I'd been phished.
If I hadn't reinstalled my mobile OS the day before. If I hadn't published a pair of big articles the day before. If we hadn't been late getting out the door. If we had been a little more late getting out the door (so that I'd have seen the multiple DMs, which would have tipped me off).
There's a name for this in security circles: "Swiss-cheese security." Imagine multiple slices of Swiss cheese all stacked up, the holes in one slice blocked by the slice below it. All the slices move around and every now and again, a hole opens up that goes all the way through the stack. Zap!
The fraudster who tricked me out of my credit card number had Swiss cheese security on his side. Yes, he spoofed my bank's caller ID, but that wouldn't have been enough to fool me if I hadn't been on vacation, having just used a pair of dodgy ATMs, in a hurry and distracted. If the 737 Max disaster hadn't happened that day and I'd had more time at the gate, I'd have called my bank back. If my bank didn't use a slightly crappy outsource/out-of-hours fraud center that I'd already had sub-par experiences with. If, if, if.
The next Friday night, at 5:30PM, the fraudster called me back, pretending to be the bank's after-hours center. He told me my card had been compromised again. But: I hadn't removed my card from my wallet since I'd had it replaced. Also, it was half an hour after the bank closed for the long weekend, a very fraud-friendly time. And when I told him I'd call him back and asked for the after-hours fraud number, he got very threatening and warned me that because I'd now been notified about the fraud that any losses the bank suffered after I hung up the phone without completing the fraud protocol would be billed to me. I hung up on him. He called me back immediately. I hung up on him again and put my phone into do-not-disturb.
The following Tuesday, I called my bank and spoke to their head of risk-management. I went through everything I'd figured out about the fraudsters, and she told me that credit unions across America were being hit by this scam, by fraudsters who somehow knew CU customers' phone numbers and names, and which CU they banked at. This was key: my phone number is a reasonably well-kept secret. You can get it by spending money with Equifax or another nonconsensual doxing giant, but you can't just google it or get it at any of the free services. The fact that the fraudsters knew where I banked, knew my name, and had my phone number had really caused me to let down my guard.
The risk management person and I talked about how the credit union could mitigate this attack: for example, by better-training the after-hours card-loss staff to be on the alert for calls from people who had been contacted about supposed card fraud. We also went through the confusing phone-menu that had funneled me to the wrong department when I called in, and worked through alternate wording for the menu system that would be clearer (this is the best part about banking with a small CU – you can talk directly to the responsible person and have a productive discussion!). I even convinced her to buy a ticket to next summer's Defcon to attend the social engineering competitions.
There's a leak somewhere in the CU systems' supply chain. Maybe it's Zelle, or the small number of corresponding banks that CUs rely on for SWIFT transaction forwarding. Maybe it's even those after-hours fraud/card-loss centers. But all across the USA, CU customers are getting calls with spoofed caller IDs from fraudsters who know their registered phone numbers and where they bank.
I've been mulling this over for most of a month now, and one thing has really been eating at me: the way that AI is going to make this kind of problem much worse.
Not because AI is going to commit fraud, though.
One of the truest things I know about AI is: "we're nowhere near a place where bots can steal your job, we're certainly at the point where your boss can be suckered into firing you and replacing you with a bot that fails at doing your job":
https://pluralistic.net/2024/01/15/passive-income-brainworms/#four-hour-work-week
I trusted this fraudster specifically because I knew that the outsource, out-of-hours contractors my bank uses have crummy headsets, don't know how to pronounce my bank's name, and have long-ass, tedious, and pointless standardized questionnaires they run through when taking fraud reports. All of this created cover for the fraudster, whose plausibility was enhanced by the rough edges in his pitch - they didn't raise red flags.
As this kind of fraud reporting and fraud contacting is increasingly outsourced to AI, bank customers will be conditioned to dealing with semi-automated systems that make stupid mistakes, force you to repeat yourself, ask you questions they should already know the answers to, and so on. In other words, AI will groom bank customers to be phishing victims.
This is a mistake the finance sector keeps making. 15 years ago, Ben Laurie excoriated the UK banks for their "Verified By Visa" system, which validated credit card transactions by taking users to a third party site and requiring them to re-enter parts of their password there:
https://web.archive.org/web/20090331094020/http://www.links.org/?p=591
This is exactly how a phishing attack works. As Laurie pointed out, this was the banks training their customers to be phished.
I came close to getting phished again today, as it happens. I got back from Berlin on Friday and my suitcase was damaged in transit. I've been dealing with the airline, which means I've really been dealing with their third-party, outsource luggage-damage service. They have a terrible website, their emails are incoherent, and they officiously demand the same information over and over again.
This morning, I got a scam email asking me for more information to complete my damaged luggage claim. It was a terrible email, from a noreply@ email address, and it was vague, officious, and dishearteningly bureaucratic. For just a moment, my finger hovered over the phishing link, and then I looked a little closer.
On any other day, it wouldn't have had a chance. Today – right after I had my luggage wrecked, while I'm still jetlagged, and after days of dealing with my airline's terrible outsource partner – it almost worked.
So much fraud is a Swiss-cheese attack, and while companies can't close all the holes, they can stop creating new ones.
Meanwhile, I'll continue to post about it whenever I get scammed. I find the inner workings of scams to be fascinating, and it's also important to remind people that everyone is vulnerable sometimes, and scammers are willing to try endless variations until an attack lands at just the right place, at just the right time, in just the right way. If you think you can't get scammed, that makes you especially vulnerable:
https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
10K notes
·
View notes
Text
As Per the New Rule, How to Link Aadhaar with the IRCTC Account to Book Tatkal Tickets?
The Ministry of Railways has announced an important update for travellers. From 1st July 2025, Passengers who want to book their Tatkal tickets must have their Aadhaar verified on the official website of IRCTC.
This new rule of IRCTC ensures tight security and stops fraudulent bookings for a safe and secure journey for the genuine passengers.
While Tatkal train tickets are gone in just a few minutes, if you want your Tatkal booking faster, getting Aadhaar verified today is a smart move you can make. In this blog, you’ll be guided about:
New rule, and what do they mean?
How do you link your Aadhaar with your IRCTC profile?
Step-by-step to link Aadhaar Card
Answers to the most common questions about the latest update
Why did IRCTC make Aadhaar Linking Mandatory for Tatkal Ticket Booking System?
IRCTC has tightened Tatkal ticket booking rules to:
To reduce fake bookings & tout misuse
To speed up passenger verification
To allow passengers to pre-fill verified passenger details
Pre-Requisites
Before you proceed with linking your Aadhaar, you must have the following:
An active IRCTC account
Valid Aadhaar number
Mobile number linked to Aadhaar number
How to Link Aadhaar to IRCTC (Step-by-Step Guidance)
Step 1: Visit the Official Website of IRCTC www.irctc.co.in
Step 2: Go to the Menu on the top right corner.
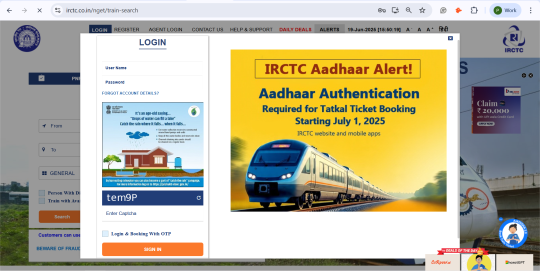
Step 3: Click on “Log in”.

Step 4: Enter your username and login password. Enter the captcha shown below.
Step 5: Once you sign in, you will land on the home page. Now, click on the menu icon shown in the top right corner.
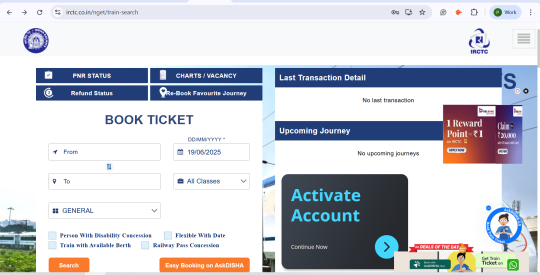
Step 6: Look for “Authenticate user” in “My Account” section.

Step 7: You will be redirected to the screen as shown below.

Step 8: Enter your 12-digit Aadhaar number. Here, your name must be written the same as on your Aadhaar Card.
Step 9: Click on “Verify Details and Receive OTP.” Note that you will only receive OTP when your name and your birthdate are matched using your aadhaar number.
Step 10: Enter the OTP received on your device and click the checkbox below to confirm the details you have entered.
Step 11: Click on “Submit” and wait for confirmation.
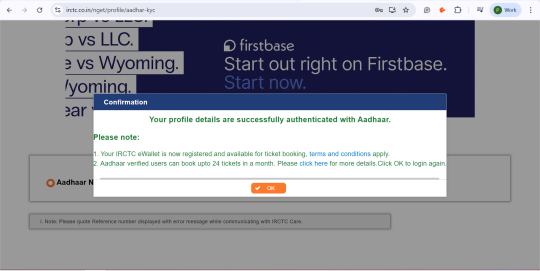
How to Add Aadhaar-Verified Passengers to Your Account?
Step 1: Go to Menu > My Profile > Add/Delete Master List as shown below.
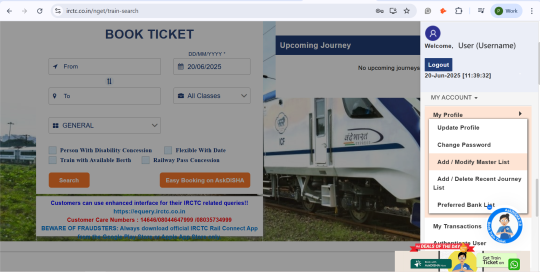
Step 2: You will be redirected to the screen shown below. Fill out the details and hit the “Submit” button.

Note: Having your master list ready in the IRCTC helps you get your tickets booked faster.
Top Tatkal Ticket Booking Tips for 2025
Log in 10–15 minutes early to avoid sudden logouts.
Use fast, stable internet while booking your tickets.
Make sure you are on mobile data for the added privacy of your data.
Pre-save payment methods and top up the IRCTC eWallet in advance.
Create and Aadhaar-verify your Master List for instant autofill.
Choose boarding or destination stations wisely for better seat availability.
Don’t waste time choosing berths. Select ‘Book’ if confirm berths are not available.
Prefer UPI or net banking over debit cards with slow OTP delivery.
Use the QuickBooks option if your Master List is set.
Stay calm, type accurately, and don’t refresh the payment page.
Frequently Asked Questions (FAQs): IRCTC Aadhaar Linking for Tatkal Booking System
Q. Is linking Aadhaar on IRCTC compulsory for Tatkal booking system in 2025?
A. It is not compulsory for all kinds of bookings. But, for Tatkal tickets, having Aadhaar-based verification is recommended for faster processing and to avoid last-minute errors.
Q. What if my Aadhaar is not linked to IRCTC?
A. You can still book tickets. Every time you wish to book tickets for you and your co-passengers, you will have to enter and verify manually each time, which can make the booking process longer.
Q. Can I book Tatkal tickets without linking Aadhaar?
A. Yes, it is possible.
Q. How many passengers can I add after linking Aadhaar?
A. A regular IRCTC account can add up to 6 passengers to the master list. If your account is Aadhaar verified, you can add up to 12 passengers.
Q. Will linking Aadhaar speed up Tatkal booking for sure?
A. Since passenger details are pre-verified. But practical speed still depends on your internet speed, payment method, and IRCTC server load. So stay prepared.
Final Thoughts
Being a citizen of India, Aadhaar-based verification is not optional, but a must-have if you wish to get your tickets booked hassle-free.This small step of Aadhaar verification is a step taken by IRCTC that enables genuine passengers to grab their Tatkal tickets without any unnecessary issues. So, don’t wait until the last minute! Link your Aadhaar today, understand the new booking flow, and travel stress-free tomorrow.
Source Link: IRCTC New Rules You Must Know Before Your Next Confirmed Train Ticket Booking
0 notes
Text
DiuWin Login: A Complete Guide to Safe and Seamless Access

In the fast-paced world of online gaming, easy and secure access to your account is essential. DiuWin, a rising name in the online gaming and entertainment space, offers users an intuitive and secure login process to ensure uninterrupted fun. Whether you're a first-time player or a seasoned user, understanding the diuwin login system can significantly enhance your gaming experience.
This comprehensive guide will walk you through everything you need to know about logging into DiuWin—from account setup and security features to troubleshooting and user benefits. Let’s dive in.
What Is DiuWin?
DiuWin is an online gaming platform that allows users to participate in skill-based games and real-money contests. It has quickly gained popularity for its engaging interface, fast withdrawals, user-centric features, and transparent reward system. Whether you're into card games, arcade-style games, or quizzes, DiuWin offers something for every type of player.
The platform prioritizes safety, fairness, and ease of use, making it ideal for casual players and competitive gamers alike. But before accessing any of these features, you’ll need to log in securely.
Why DiuWin Login Matters
The DiuWin login is your personal key to accessing your account, managing funds, participating in contests, and securing your gaming data. Here's why it's crucial:
1. Secure Access
Your login credentials ensure that only you can access your personal account and financial data.
2. Personalization
Once logged in, you receive personalized game recommendations, progress tracking, and exclusive bonuses.
3. Wallet & Transactions
You need to be logged in to deposit funds, withdraw earnings, and check your transaction history.
4. Game Continuity
Login lets you resume your saved games and tournaments without losing progress.
How to Register on DiuWin
Before logging in, new users must register. Here’s how:
Step 1: Visit the Official Website
download the DiuWin app from a trusted source.
Step 2: Click “Register” or “Sign Up”
The registration button is typically found at the top right corner of the page.
Step 3: Enter Mobile Number
Use a valid 10-digit Indian mobile number. This becomes your primary login ID.
Step 4: OTP Verification
You’ll receive a One-Time Password (OTP) on your mobile. Enter it to verify your number.
Step 5: Create a Password
Set a strong password to secure your account. Use a mix of letters, numbers, and symbols.
Step 6: Accept Terms
Agree to DiuWin’s terms and conditions to complete your registration.
After this, your account is ready to use. You can now log in and start playing.
How to Log in to DiuWin
Once registered, follow these simple steps to log into your DiuWin account:
Step 1: Open the App or Website
Launch the DiuWin mobile app or visit the website on your browser.
Step 2: Click “Login”
You’ll find the login button on the home screen or top-right menu.
Step 3: Enter Your Mobile Number
Input the registered number you used during sign-up.
Step 4: Enter Password or Request OTP
Choose either:
Password Login: Enter your password for instant access.
OTP Login: Request an OTP to be sent to your phone and enter it when received.
Step 5: Access Your Dashboard
Once logged in, you’ll land on your personalized dashboard where you can manage your wallet, join games, and track rewards.
Key Features of DiuWin Login
DiuWin has integrated several features to ensure its login process is smooth, fast, and safe:
Fast Authentication – Log in within seconds using password or OTP.
Biometric Login – Use fingerprint or face ID on supported devices.
Session Management – Auto logout after inactivity for added security.
Multi-device Access – Login from mobile, tablet, or desktop without losing progress.
Two-Factor Security – Optional security layer using OTP or authenticator apps.
Security Features in DiuWin Login
Security is a top priority for DiuWin. Here’s how they protect your account:
1. SSL Encryption
All data, including login credentials, is encrypted using SSL protocols to protect from hacking and phishing.
2. Two-Factor Authentication
OTP or app-based codes ensure only the verified user can access the account.
3. Account Lockouts
Accounts may be temporarily locked after multiple failed login attempts to prevent brute-force attacks.
4. Secure Password Standards
Users are encouraged to create strong passwords with a mix of characters.
5. Real-Time Login Alerts
Get notified instantly via SMS or email if your account is accessed from a new device.
Forgot Password? Here’s What to Do
It’s common to forget passwords. Here’s how to reset yours:
Go to the login screen.
Click “Forgot Password.”
Enter your registered mobile number.
Receive an OTP to reset your password.
Choose a new strong password and confirm.
You can now use your new credentials to log in.
Troubleshooting DiuWin Login Issues
Facing problems while logging in? Here’s how to resolve them:
1. OTP Not Received
Check your mobile network and SMS inbox.
Wait a minute and resend OTP.
Contact support if the issue persists.
2. Wrong Password
Double-check your input.
Use the "Forgot Password" feature to reset it.
3. Account Locked
Too many failed login attempts can cause temporary lockouts.
Wait a few minutes and try again or contact support.
4. Unable to Access from New Device
Use OTP for authentication on new devices.
Ensure you’re using the latest version of the app.
Benefits of Logging in to DiuWin
Logging in unlocks a range of features and advantages:
Wallet Access – Deposit and withdraw money securely.
Rewards & Offers – View and claim personalized bonuses.
Game Access – Join contests, tournaments, and special events.
Play History – Track wins, losses, and statistics.
24/7 Support – Get help with issues directly through your dashboard.
Tips for a Safe Login Experience
Always use strong, unique passwords.
Never share your OTP or password with anyone.
Enable biometric login if available on your device.
Avoid using public Wi-Fi while logging in.
Log out after each session, especially on shared devices.
Frequently Asked Questions (FAQs)
Q1: Can I use the same login on multiple devices?
Yes. DiuWin allows multi-device login, but you may need to verify with OTP for security.
Q2: Is the login process free?
Absolutely. There are no charges for logging into your DiuWin account.
Q3: What if I lose access to my registered mobile number?
Contact DiuWin support to update your number after verifying your identity.
Q4: Can I change my password?
Yes. You can change your password anytime from the account settings.
Q5: Is biometric login available?
Yes, DiuWin supports fingerprint and face recognition on compatible devices.
Conclusion: Your Journey Starts With DiuWin Login
The DiuWin login process is the first step to accessing a world full of thrilling games, exciting contests, and real-money rewards. With a focus on user experience and security, Diuwin Game ensures that your login is always quick, smooth, and protected.
From a simple registration process to fast login and secure wallet management, DiuWin has optimized its system to provide gamers with everything they need in one place. Whether you’re playing to pass time or aiming for big wins, your journey begins with a secure and hassle-free login.
1 note
·
View note
Text
Is Online QA Training Enough to Start a Career in Software Testing?
In today’s fast-paced tech landscape, software quality is non-negotiable. Every app, tool, and platform must meet user expectations for performance, reliability, and security. Behind this invisible guarantee lies the work of skilled Quality Assurance (QA) professionals. If you're eyeing a career in software testing, you may be asking: "Is online QA training enough to get started?" The short answer? Yes, if you choose the right training and apply yourself effectively.
Let’s dive into how Quality assurance courses online can serve as a solid launchpad for a successful career in software testing, what to look for in a quality course, and the steps you should take beyond training to truly stand out.
What Is QA in Software Testing?
Quality Assurance (QA) is the process of ensuring that software meets certain quality standards before it goes live. QA professionals test software to identify bugs, usability issues, and performance gaps. They are essential in delivering a seamless, error-free experience to users.
QA testing typically involves:
Writing and executing test cases
Using tools like Selenium, JIRA, and TestNG
Performing manual and automated testing
Documenting bugs and verifying fixes
Collaborating with developers and business analysts
Why Online QA Training Has Gained Popularity
With the rise of remote learning and global demand for skilled testers, Quality assurance tester course programs have become increasingly popular. The reasons include:
Flexibility: Learn at your own pace, from anywhere.
Affordability: Often less expensive than traditional classroom training.
Access to Tools: Many courses offer hands-on labs, simulations, and tool access.
Certification Prep: Tailored content to help you pass industry-recognized exams.
But is it enough to make you job-ready?
Core Skills You Can Learn in Online QA Training
High-quality online QA training covers both theoretical knowledge and practical skills that recruiters look for. Here are the essential competencies you can expect to gain:
1. Foundations of Software Testing
SDLC and STLC (Software Development and Testing Life Cycle)
Types of testing: Unit, Integration, System, Regression, UAT
Testing methodologies: Agile, Waterfall
2. Manual Testing Techniques
Writing test cases and test plans
Bug tracking and defect reporting
Testing across browsers, devices, and platforms
3. Automation Testing Tools
Selenium WebDriver for UI automation
TestNG or JUnit frameworks
Scripting languages like Java or Python
4. Bug Tracking and Management Tools
JIRA
Bugzilla
Quality Center
5. Soft Skills
Communication and documentation
Analytical thinking
Attention to detail and problem-solving
Real-World Applications: Can You Perform on the Job?
Online QA training that includes real-time projects, mock interviews, and tool-based simulations can help bridge the gap between theory and practice.
Example:
An online course that teaches Selenium might give you a capstone project to:
Automate login/logout for a demo application
Validate UI elements using locators
Generate test reports using TestNG
Such hands-on experience mirrors real QA job tasks and is highly valuable in interviews.
What Employers Expect from Entry-Level QA Testers
Many QA jobs welcome entry-level applicants who have completed a comprehensive training program. Here's what hiring managers generally look for:
Basic understanding of testing concepts
Hands-on experience with testing tools
Portfolio of projects or GitHub test scripts
Certification (optional but advantageous)
Willingness to learn and adapt
With the right online QA training, you can check all these boxes especially if the program includes career support such as resume building, mock interviews, and job placement assistance.
Limitations of Online QA Training (and How to Overcome Them)
While online training is an excellent foundation, it does come with potential downsides if not approached correctly:
1. Lack of Interaction
Solution: Join online forums, Slack groups, or Discord communities where you can interact with peers and mentors.
2. Self-Discipline Required
Solution: Create a learning schedule. Treat your course like a job.
3. No On-the-Job Experience
Solution: Volunteer for open-source projects, internships, or freelance gigs to gain real-world exposure.
4. Outdated Curriculum
Solution: Choose training platforms that update their content regularly and focus on current tools like Selenium 4, API testing, or DevOps integration.
The Role of Certifications in Boosting Your QA Career
Certifications aren’t mandatory to land your first QA role, but they do increase credibility, especially if you’re new to tech.
Popular certifications include:
ISTQB Foundation Level
Certified Software Tester (CSTE)
Certified Agile Tester (CAT)
Automation Testing with Selenium certification
Many online QA training programs prepare you for these certifications, making them an excellent investment.
Career Paths After Online QA Training
Once you complete your online training and start your QA career, a world of opportunities opens up. Some roles you can explore include:
Entry-Level Roles:
QA Analyst
Software Tester
Manual Tester
Test Engineer
Growth Opportunities:
Automation Test Engineer
QA Lead
Performance Tester
QA Manager
Software Development Engineer in Test (SDET)
With added skills in scripting, DevOps, or API testing, you can transition into even more specialized roles.
Tips to Maximize Your Online QA Training
Here’s how to make your training more effective and career-focused:
Choose Hands-On Courses
Go beyond lectures—look for interactive labs and assignments.
Build a Portfolio
Upload your test scripts and projects to GitHub or GitLab.
Practice Bug Reporting
Use real websites to find issues and practice logging them.
Stay Updated
Follow blogs, attend webinars, and stay tuned to QA trends.
Connect with the QA Community
Engage on LinkedIn, Reddit, and QA-specific forums.
Get Mock Interview Practice
Many online QA training programs offer interview preparation. Use it.
Real Success Stories from QA Professionals
Let’s take a look at real-world inspiration:
Case Study 1: Sarah, Manual Tester Turned Automation Engineer
Sarah enrolled in a 12-week online QA training program while working a retail job. She practiced daily, completed capstone projects, and posted her work online. Three months later, she landed her first QA Analyst role. A year later, after upskilling in Selenium, she moved into automation and now earns 2x her initial salary.
Case Study 2: Ajay, Non-IT to QA Engineer
With a background in finance, Ajay switched careers by taking an online QA training course. Though he had no coding experience, the structured path and mentorship helped him become job-ready. He’s now a full-time tester in a healthcare software firm.
Final Verdict:
Yes, QA certification online is enough to start a career in software testing, provided it is practical, up-to-date, and career-focused. It works best when combined with self-motivation, hands-on learning, and proactive career building.
If you’re serious about breaking into QA, an online course can equip you with the skills, tools, and confidence needed to start strong. But don’t stop there, apply what you learn, keep practicing, and never stop exploring the world of software testing.
Key Takeaways
Online QA training offers the flexibility and depth needed to launch a testing career.
A strong course covers manual testing, automation, tools, and practical projects.
Employers look for hands-on skills, real-world exposure, and willingness to learn.
Success depends not just on the training itself but on how you apply and extend your learning.
Certifications, portfolios, and internships can greatly boost your chances.
Ready to start your QA journey? With the right online QA training, dedication, and smart strategies, you’re already well on your way to a promising career in software testing.
0 notes
Text
Unlock Instagram's Best-Kept Security Secrets: Hidden Features You Must Use in In today’s digital landscape, social media security is more crucial than ever. With cyber threats evolving daily, Instagram users face risks such as hacking, phishing, and unauthorized access to personal data. While many users implement basic security measures like passwords and two-factor authentication, there are several lesser-known settings that can significantly enhance account protection. This guide will uncover hidden Instagram security settings that you probably didn’t know existed. From monitoring login activity to managing third-party app access, these settings provide an extra layer of defense against cyber threats. 1. Monitoring Login Activity and Alerts What It Does This feature allows you to track where and when your Instagram account has been accessed. You can view active sessions and log out remotely if suspicious activity is detected. How to Access and Configure Open the Instagram app and go to your Profile. Tap the Menu (three lines) in the top-right corner. Navigate to Settings & Privacy. Select Accounts Center > Password and Security. Tap Where You’re Logged In to review login activity. If you notice any unfamiliar devices, select Log Out and change your password immediately. Benefits Helps identify unauthorized logins. Allows remote logout from unrecognized devices. Prevents hackers from maintaining access to your account. Real-World Scenario Imagine receiving a notification that your account was accessed from a different country. Checking login activity can help confirm unauthorized access, allowing you to take action immediately. 2. Managing Data Access and Permissions What It Does Instagram collects a vast amount of user data. This setting allows you to control which apps and services have access to your account. How to Access and Configure Go to Settings & Privacy. Select Apps and Websites. Review the list of third-party apps connected to your Instagram account. Revoke access to apps that are no longer needed or appear suspicious. Benefits Prevents third-party apps from misusing personal data. Reduces the risk of data leaks from unauthorized services. Enhances overall account security. Real-World Scenario You installed a photo-editing app that required Instagram access but no longer use it. Revoking its access ensures that it doesn’t collect your data unnecessarily. 3. Restricting Unwanted Interactions and Messages What It Does This feature helps prevent unwanted interactions by restricting specific users from sending messages or commenting on posts. How to Access and Configure Go to Settings & Privacy. Tap Messages and Story Replies. Customize who can send you direct messages. Under Comment Controls, limit who can comment on your posts. Benefits Reduces spam and harassment. Allows better control over interactions. Enhances privacy. Real-World Scenario If you’re receiving spam messages from unknown accounts, adjusting these settings can help filter out unwanted communication. 4. Advanced Two-Factor Authentication (2FA) Options What It Does While many users enable basic 2FA via SMS, Instagram also supports authentication apps and security keys for enhanced security. How to Access and Configure Navigate to Settings & Privacy. Select Accounts Center > Password and Security. Tap Two-Factor Authentication. Choose Authentication App or Security Key for added protection. Benefits Stronger security than SMS-based 2FA. Prevents account access even if your password is compromised. Reduces phishing risks. Real-World Scenario Hackers can intercept SMS codes through SIM-swapping attacks. Using an authentication app like Google Authenticator enhances security significantly. 5. Downloading and Reviewing Your Data What It Does Instagram allows
you to download a copy of your account data, including messages, comments, and login activity. How to Access and Configure Go to Settings & Privacy. Tap Your Information > Download Your Information. Request a data download to review past activities. Benefits Helps identify any unauthorized data usage. Allows personal archiving of Instagram history. Provides insights into what data Instagram stores. Real-World Scenario If you suspect someone has accessed your account, reviewing past activity logs can help confirm any suspicious actions. 6. Reviewing Account Access from Third-Party Apps What It Does This setting ensures that old or suspicious third-party services no longer have access to your Instagram account. How to Access and Configure Navigate to Settings & Privacy. Select Apps and Websites. Revoke access from outdated or untrusted applications. Benefits Prevents misuse of personal data. Reduces security vulnerabilities. Ensures only trusted apps can access your Instagram account. 7. Hidden Privacy Features Related to Shared Data What It Does Instagram provides additional privacy controls for shared content, such as controlling who can see your stories and posts. How to Access and Configure Go to Settings & Privacy. Tap Hidden Words to filter out offensive comments and messages. Use Close Friends to restrict story visibility. Benefits Enhances content privacy. Limits exposure to unwanted audiences. Provides greater control over shared content. Practical Tips and Best Practices Regularly update your password using a strong, unique combination. Enable login alerts to receive notifications for unusual activity. Use a password manager to securely store credentials. Be cautious of phishing links sent via Instagram DMs or emails. Report suspicious activity to Instagram immediately. Conclusion Understanding and utilizing Instagram’s hidden security settings is crucial for protecting your personal information and preventing unauthorized access. By taking proactive steps—such as enabling advanced 2FA, restricting unwanted interactions, and reviewing third-party app access—you can significantly enhance your account security. Take a few minutes today to review and update your Instagram security settings. Your digital safety is worth it!
0 notes
Text
WhatsApp is working on an easier way to log out
WhatsApp is developing a solution for users to take a break from the messaging service without nuking their account data. A new “Logout [internal]” option spotted in the WhatsApp 2.25.17.37 beta release by Android Authority presents users with the choice to sign out on their primary WhatsApp device while either retaining or erasing their app data and preferences. For all intents and purposes, the…

View On WordPress
0 notes
Text
Mastering IRCTC Tatkal Booking: Your Guide to Securing Last-Minute Train Tickets with Afre Studios
Travel plans can be unpredictable, and sometimes you need to book a train ticket at the last minute. For Indian Railways passengers, the IRCTC Tatkal booking system is a lifesaver, offering a chance to secure Tatkal seats in trains for urgent travel. Whether you're aiming to book a Tatkal ticket now or planning a Tatkal reservation ticket for tomorrow, this article will guide you through the process and highlight how Afre Studios can make your booking experience seamless and efficient.
What is IRCTC Tatkal Booking?
The IRCTC Tatkal booking scheme, introduced by Indian Railways, is designed for travelers who need to book tickets on short notice. The word "Tatkal" means "immediate," and this system allows passengers to reserve Tatkal seats in trains just one day before the journey date from the originating station. Tatkal tickets are available for most train classes, including Sleeper (SL), Second Seating (2S), Chair Car (CC), and AC classes (2A, 3A, 3E), except for First AC and Executive Class.

However, Tatkal tickets come with a premium price, with additional charges ranging from 10% of the base fare for second-class seating to 30% for other classes. Despite the higher cost, the scheme is a go-to option for those needing confirmed seats for urgent travel.
When and How to Book a Tatkal Reservation Ticket
To book a Tatkal reservation ticket, timing is critical. The booking window opens one day in advance, excluding the journey date, with specific times for different classes:
AC Classes (2A, 3A, CC, 3E): Booking starts at 10:00 AM.
Non-AC Classes (SL, FC, 2S): Booking starts at 11:00 AM.
For example, if your train departs from its originating station on May 11, 2025, you can book your Tatkal ticket now on May 10, 2025, at the specified times. If you’re boarding from a station other than the origin, note that the booking date depends on when the train’s chart is prepared, typically one day before the train’s departure from its starting point.
Here’s a step-by-step guide to booking a Tatkal reservation ticket:
Log in Early: Access the IRCTC website (irctc.co.in) or an authorized partner like Afre Studios 5–10 minutes before the booking window opens. Create an IRCTC account in advance with verified details to save time.
Select Tatkal Quota: On the IRCTC "Plan My Journey" page or Afre Studios’ platform, enter your source and destination stations, choose the journey date, and select "Tatkal" as the quota.
Enter Passenger Details: Provide accurate details like name, age, gender, and a valid ID (Aadhaar, Voter ID, etc.). You can book up to four passengers per PNR for Tatkal tickets.
Choose Payment Method: Opt for a fast payment option like UPI, net banking, or saved cards to avoid delays. Afre Studios offers secure, quick payment gateways to streamline this step.
Confirm Booking: Double-check details, tick "Book only if confirm berths are allotted" to avoid waitlisted tickets, and complete the payment. Download or print your e-ticket.
Challenges of Booking Tatkal Seats in Trains
Securing tatkal seat in train can be challenging due to high demand, especially during peak seasons like festivals or holidays. The IRCTC website often experiences heavy traffic, leading to crashes or delays. Additionally, Tatkal tickets are allocated on a first-come, first-served basis, and seats are limited. Waitlisted Tatkal tickets (TQWL) have lower confirmation chances compared to general waiting lists, and confirmed Tatkal tickets are non-refundable.
To improve your chances, consider these tips:
Use Multiple Devices: Log in with different IRCTC accounts on separate devices or browsers to increase your chances. Avoid using the same account on multiple devices to prevent logout issues.
Pre-fill Details: Enter passenger details before the booking window opens to save time. Afre Studios offers an autofill feature to speed up this process.
Have Backup Options: Keep alternative trains or classes in mind in case your preferred option is unavailable.
Leverage Technology: Use a reliable platform like Afre Studios, which provides a user-friendly interface, real-time seat availability, and autofill capabilities for faster booking.
Why Choose Afre Studios for Tatkal Ticket Booking?
Afre Studios is a trusted name in simplifying IRCTC Tatkal booking for Indian Railways passengers. Their innovative platform, available as a mobile app and website, is designed to make last-minute travel stress-free. Here’s why Afre Studios stands out:
Fast Autofill Technology: Afre Studios’ app uses Accessibility Service API to autofill passenger details on the IRCTC Rail Connect app, saving precious seconds during the Tatkal booking window.
Real-Time Updates: Check seat availability, PNR status, and train schedules instantly, ensuring you make informed decisions.
User-Friendly Interface: The app’s intuitive design makes it easy to navigate, even for first-time users.
Secure Payments: Multiple digital payment options ensure a quick and safe transaction process.
24/7 Support: For any queries, contact Afre Studios at [email protected] for prompt assistance.
Whether you’re booking a Tatkal ticket now or planning for tomorrow, Afre Studios enhances your chances of securing confirmed Tatkal seats in trains by combining speed, reliability, and convenience.
Tatkal vs. Premium Tatkal: What’s the Difference?
In addition to regular Tatkal, IRCTC offers Premium Tatkal, introduced in 2014, which has dynamic pricing based on demand. Unlike regular Tatkal, Premium Tatkal tickets are only available as e-tickets through the IRCTC website and not at counters or third-party platforms like Afre Studios. While Premium Tatkal may offer a higher chance of confirmation, the fares can be significantly higher. For budget-conscious travelers, regular Tatkal reservation tickets booked via Afre Studios are often a more cost-effective choice.
Cancellation and Refund Policy for Tatkal Tickets
One key aspect to understand is the cancellation policy for Tatkal reservation tickets:
Confirmed Tickets: No refunds are provided for canceled confirmed Tatkal tickets.
Waitlisted or RAC Tickets: Partial refunds are available if canceled up to 30 minutes before the train’s departure, with deductions as per IRCTC rules.
Automatic Cancellation: Waitlisted Tatkal tickets that don’t get confirmed or reach RAC status are automatically canceled after chart preparation, with refunds processed.
TDR Filing: If the train is delayed by over three hours or canceled, you can file a Ticket Deposit Receipt (TDR) for a refund.
Always check your PNR status on Afre Studios to stay updated on your ticket’s confirmation status.
Final Tips for Successful Tatkal Booking
To maximize your chances of booking a Tatkal ticket now:
Log in 10–15 minutes early to avoid last-minute glitches.
Ensure a stable internet connection to prevent disruptions.
Use Afre Studios for its autofill and real-time features to beat the rush.
Keep valid ID proofs ready, as they’re mandatory during travel.
Conclusion
The IRCTC Tatkal booking system is a boon for last-minute travelers, offering a chance to secure Tatkal seats in trains when time is short. By understanding the booking process, timing, and challenges, and leveraging the advanced features of Afre Studios, you can significantly improve your chances of getting a confirmed Tatkal reservation ticket. Whether it’s a sudden business trip or an urgent family visit, Afre Studios is your trusted partner for fast, reliable, and hassle-free Tatkal ticket booking. Download their app today and travel with confidence!
0 notes