#macOS Activity Monitor
Explore tagged Tumblr posts
Text
How to correctly uninstall Nextcloud from Mac
The Nextcloud Desktop Client is a tool to synchronise files from the Nextcloud Server with your computer. The removal of apps is usually very straightforward on macOS. But in the case of Nextcloud, this is not the case. Therefore, in this article, we shall discuss how to correctly uninstall Nextcloud from Mac. Please see how to install Nextcloud Desktop client on Mac, How To Install Nextcloud on…
#Activity Monitor#Launch macOS Activity Monitor#MAC#Mac iOS cloud sync#Macbook#MacOS#macOS Activity Monitor#NextCloud Desktop App#Uninstall Nextcloud Desktop App
0 notes
Text
Generative AI tools such as OpenAI’s ChatGPT and Microsoft’s Copilot are rapidly evolving, fueling concerns that the technology could open the door to multiple privacy and security issues, particularly in the workplace.
In May, privacy campaigners dubbed Microsoft’s new Recall tool a potential “privacy nightmare” due to its ability to take screenshots of your laptop every few seconds. The feature has caught the attention of UK regulator the Information Commissioner’s Office, which is asking Microsoft to reveal more about the safety of the product launching soon in its Copilot+ PCs.
Concerns are also mounting over OpenAI’s ChatGPT, which has demonstrated screenshotting abilities in its soon-to-launch macOS app that privacy experts say could result in the capture of sensitive data.
The US House of Representatives has banned the use of Microsoft’s Copilot among staff members after it was deemed by the Office of Cybersecurity to be a risk to users due to “the threat of leaking House data to non-House approved cloud services.”
Meanwhile, market analyst Gartner has cautioned that “using Copilot for Microsoft 365 exposes the risks of sensitive data and content exposure internally and externally.” And last month, Google was forced to make adjustments to its new search feature, AI Overviews, after screenshots of bizarre and misleading answers to queries went viral.
Overexposed
For those using generative AI at work, one of the biggest challenges is the risk of inadvertently exposing sensitive data. Most generative AI systems are “essentially big sponges,” says Camden Woollven, group head of AI at risk management firm GRC International Group. “They soak up huge amounts of information from the internet to train their language models.”
AI companies are “hungry for data to train their models,” and are “seemingly making it behaviorally attractive” to do so, says Steve Elcock, CEO and founder at software firm Elementsuite. This vast amount of data collection means there’s the potential for sensitive information to be put “into somebody else’s ecosystem,” says Jeff Watkins, chief product and technology officer at digital consultancy xDesign. “It could also later be extracted through clever prompting.”
At the same time, there’s the threat of AI systems themselves being targeted by hackers. “Theoretically, if an attacker managed to gain access to the large language model (LLM) that powers a company's AI tools, they could siphon off sensitive data, plant false or misleading outputs, or use the AI to spread malware,” says Woollven.
Consumer-grade AI tools can create obvious risks. However, an increasing number of potential issues are arising with “proprietary” AI offerings broadly deemed safe for work such as Microsoft Copilot, says Phil Robinson, principal consultant at security consultancy Prism Infosec.
“This could theoretically be used to look at sensitive data if access privileges have not been locked down. We could see employees asking to see pay scales, M&A activity, or documents containing credentials, which could then be leaked or sold.”
Another concern centers around AI tools that could be used to monitor staff, potentially infringing their privacy. Microsoft’s Recall feature states that “your snapshots are yours; they stay locally on your PC” and “you are always in control with privacy you can trust.”
Yet “it doesn’t seem very long before this technology could be used for monitoring employees,” says Elcock.
Self-Censorship
Generative AI does pose several potential risks, but there are steps businesses and individual employees can take to improve privacy and security. First, do not put confidential information into a prompt for a publicly available tool such as ChatGPT or Google’s Gemini, says Lisa Avvocato, vice president of marketing and community at data firm Sama.
When crafting a prompt, be generic to avoid sharing too much. “Ask, ‘Write a proposal template for budget expenditure,’ not ‘Here is my budget, write a proposal for expenditure on a sensitive project,’” she says. “Use AI as your first draft, then layer in the sensitive information you need to include.”
If you use it for research, avoid issues such as those seen with Google’s AI Overviews by validating what it provides, says Avvocato. “Ask it to provide references and links to its sources. If you ask AI to write code, you still need to review it, rather than assuming it’s good to go.”
Microsoft has itself stated that Copilot needs to be configured correctly and the “least privilege”—the concept that users should only have access to the information they need—should be applied. This is “a crucial point,” says Prism Infosec’s Robinson. “Organizations must lay the groundwork for these systems and not just trust the technology and assume everything will be OK.”
It’s also worth noting that ChatGPT uses the data you share to train its models, unless you turn it off in the settings or use the enterprise version.
List of Assurances
The firms integrating generative AI into their products say they’re doing everything they can to protect security and privacy. Microsoft is keen to outline security and privacy considerations in its Recall product and the ability to control the feature in Settings > Privacy & security > Recall & snapshots.
Google says generative AI in Workspace “does not change our foundational privacy protections for giving users choice and control over their data,” and stipulates that information is not used for advertising.
OpenAI reiterates how it maintains security and privacy in its products, while enterprise versions are available with extra controls. “We want our AI models to learn about the world, not private individuals—and we take steps to protect people’s data and privacy,” an OpenAI spokesperson tells WIRED.
OpenAI says it offers ways to control how data is used, including self-service tools to access, export, and delete personal information, as well as the ability to opt out of use of content to improve its models. ChatGPT Team, ChatGPT Enterprise, and its API are not trained on data or conversations, and its models don’t learn from usage by default, according to the company.
Either way, it looks like your AI coworker is here to stay. As these systems become more sophisticated and omnipresent in the workplace, the risks are only going to intensify, says Woollven. “We're already seeing the emergence of multimodal AI such as GPT-4o that can analyze and generate images, audio, and video. So now it's not just text-based data that companies need to worry about safeguarding.”
With this in mind, people—and businesses—need to get in the mindset of treating AI like any other third-party service, says Woollven. “Don't share anything you wouldn't want publicly broadcasted.”
10 notes
·
View notes
Text
NordVPN Uses Post-Quantum Encryption To Protect User Data

After-quantum encryption
NordVPN has implemented post-quantum encryption on all platforms to combat future quantum attacks.
NordVPN, a leading cybersecurity service, released post-quantum encryption across all its VPN apps. This crucial upgrade has been fully implemented across all supported platforms to prevent large-scale quantum computers from decrypting user data.
Implementation began with the September 2024 version of NordVPN Linux. This phase includes the first post-quantum NordLynx protocol cryptographic improvement in a Linux software update. WireGuard calls NordLynx a fast and secure VPN protocol. The revised technique met NIST's latest post-quantum encryption criteria. Linux deployments aimed to protect users against quantum decryption and measure performance metrics like latency and connection rates.
"The collected data served as a stepping stone to quantum-resistant encryption on the rest of the platforms," said NordVPN CTO Marijus Briedis. He said, “The Linux case demonstrated that it successfully maintained the highest level of user experience in terms of connection time and speed during the transition”. This initial phase's accomplishment cleared the way for post-quantum cryptography support in other applications.
NordVPN brought PQE to Windows, macOS, iOS, Android, tvOS, and Android TV in 2025. Any software that supports PQE can now use it. PQE upgrade adds quantum-resistant algorithms to NordLynx. The protocol meets the latest NIST post-quantum encryption standards. The implementation follows August 2024 US National Institute of requirements and Technology (NIST) post-quantum cryptography requirements. NordVPN uses quantum-safe mathematical methods in its VPN infrastructure to secure data long-term.
We took preventive steps because we thought quantum computer technology might threaten us. Quantum computing uses quantum physics to calculate tenfold faster than digital computers. Even in its infancy, quantum computing could outperform the fastest systems. It could break encryption systems, but this massive power could benefit space exploration and medicine by modelling molecules to repair ailments.
Due of quantum computers' processing power, cybersecurity is difficult. Quantum computers may swiftly surpass RSA encryption, which takes ordinary computers hundreds of years to master, researchers say. Such computational capacity threatens governments, corporations, and individuals.
Experts say hackers are already storing encrypted data for later deciphering, which is the biggest issue with quantum computers. Marijus Briedis suggests cybercriminals are increasing their “harvest now, decrypt later” tactics. They want to collect massive amounts of encrypted data to decrypt after quantum technology is mastered. Quantum computing is still in its infancy, but securing critical data now improves cybersecurity for consumers and organisations.
Due to this, large IT corporations, governments, and organisations like the FBI and CIA are monitoring the technology's development and seeking post-quantum encryption solutions. NordVPN implemented post-quantum cryptography to protect private data from quantum criminals. By incorporating PQE into their VPN infrastructure today and in the post-quantum era, NordVPN hopes to protect their clients' data. This launch marks a “major transition to new-generation encryption of all our applications, providing long-term security for our users” according to Briedis.
PQE is easy to enable. A toggle switch in the app's “Settings” under “Connections” enables it. The function will automatically start when the user connects via NordLynx once activated. Remember to disable PQE while using obfuscated servers or protocols like OpenVPN. It also conflicts with Meshnet and other features.
Implementing post-quantum encryption is challenging and resource-intensive. Newer security methods require larger key sizes and signatures. This may increase computational cost and VPN speed and performance, especially in high-throughput settings.
With this complete implementation, NordVPN joins Mullvad and ExpressVPN in offering full PQE integration. Reports say other providers are implemented at various stages. NordVPN is part of industry-wide efforts to future-proof digital privacy for “Q-Day” threats.
Concerning NORDVPN NordVPN, the world's most advanced VPN provider, is trusted by millions of internet users. The service offers dedicated IP, Double VPN, and Onion Over VPN servers to improve online anonymity with zero monitoring. A key feature of NordVPN is Threat Protection Pro, which scans downloads for malware and blocks hazardous websites, trackers, and adverts. NordVPN, a part of Nord Security, launched Saily, a global eSIM service. NordVPN is known for its user-friendly design and over 7,600 servers in 118 countries at the cheapest prices.
#NordVPN#postquantumencryption#postquantum#quantumencryption#postquantumcryptography#quantumcryptography#technology#technews#technologynews#news#govindhtech
0 notes
Text
Parental Control Software Market Size, Share, Trends, Growth Opportunities and Competitive Outlook
Global Parental Control Software Market - Size, Share, Demand, Industry Trends and Opportunities
Global Parental Control Software Market, By Device Type (Smart Phones, Computers, and Video Games, Tablets, Digital Television, and Others), Deployment (On-Premise, and Cloud), Pricing (Free, Basic, Premium, and Others), Function (Time Management, Gaming, App Management, Web Access, Program-Specific Controls, Cyber Security, and Others), Operating System (Android, IOS, Windows, Linux, macOS, and Others), End User (Educational Institutes, Residential, and Commercial) – Industry Trends
Access Full 350 Pages PDF Report @
**Segments**
- On the basis of type, the global parental control software market can be segmented into traditional parental control software and smartphone parental control software. The traditional parental control software includes solutions that offer monitoring and filtering features for desktops and laptops, while smartphone parental control software caters to the monitoring and control of activities on mobile devices.
- Based on deployment mode, the market can be divided into cloud-based and on-premises parental control software. Cloud-based solutions offer flexibility and scalability, allowing users to access the software from anywhere, while on-premises options provide more control over data and customization.
- In terms of application, the parental control software market can be categorized into educational institutes, residential, and commercial sectors. Educational institutes use these tools to protect students from exposure to harmful online content, while residential and commercial users utilize parental control software to safeguard family members or employees from inappropriate material.
**Market Players**
- Some of the key players in the global parental control software market are NortonLifeLock Inc., Net Nanny, McAfee, Qustodio LLC, Kaspersky Lab, Mobicip, LLC, Symantec Corporation, Verizon Communications Inc., Avast Software s.r.o., and AVG Technologies. These companies offer a range of parental control solutions with features such as content filtering, screen time management, app blocking, and geofencing to address the diverse needs of users in the market.
The global parental control software market is witnessing significant growth as the awareness of online safety and the need for monitoring children's digital activities continue to rise. With the proliferation of digital devices and the increasing presence of children online, parents and guardians are turning to parental control software to ensure a safer online experience. The market is also being driven by regulatory compliance requirements in educational settings and the growing demand for effective monitoring solutions in households and businesses.
Cloud-based parental control software is gaining traction due to its convenience and accessibility, allowing users to manage settings remotely and across multiple devices. On-premisesThe global parental control software market is experiencing a surge in demand driven by the increasing awareness of online safety and the growing need for monitoring children's digital activities. As more children access digital devices and spend time online, parents and guardians are recognizing the importance of implementing parental control software to keep their children safe from harmful content and activities. The market is also benefiting from regulatory requirements in educational settings, where the protection of students from online threats is of paramount importance.
One of the key trends in the parental control software market is the shift towards cloud-based solutions. Cloud-based parental control software offers users greater flexibility and convenience by allowing them to access and manage settings from anywhere, using any device with an internet connection. This not only simplifies the management of parental controls but also ensures that parents can monitor their children's activities in real-time, even when they are away from home. The scalability of cloud-based solutions also makes them suitable for households with multiple devices and users, further driving their adoption in the market.
On-premises parental control software, on the other hand, provides users with a greater sense of control over their data and customization options. Some users, especially those who are concerned about data privacy and security, prefer on-premises solutions as they keep all monitoring activities within their own network. While on-premises solutions may require more upfront investment and maintenance, they appeal to users who prioritize data sovereignty and customization capabilities.
The parental control software market is highly competitive, with a number of key players vying for market share. Companies such as NortonLifeLock Inc., Net Nanny, McAfee, and Kaspersky Lab offer a diverse range of parental control solutions with features such as content filtering, screen time management, app blocking, and geofencing. These companies are continuously innovating their products to meet the evolving needs of users and stay ahead in the competitive landscape.
In conclusion, the global parental control software market is expected to continue its growth trajectory as the importance of online safety and digital monitoring remains**Global Parental Control Software Market Analysis**
- **Global Parental Control Software Market, By Device Type (Smart Phones, Computers, and Video Games, Tablets, Digital Television, and Others)** The parental control software market is segmented by the type of device on which the software can be installed. This segmentation is crucial as different devices may require specific features and functionalities to ensure effective monitoring and control of online activities. With the increasing use of smartphones, tablets, computers, and other digital devices by children, the demand for parental control software across different devices is on the rise.
- **Deployment (On-Premise, and Cloud)** The deployment mode of parental control software plays a significant role in the market as it determines how users can access and manage the software. On-premise solutions offer a more localized approach to monitoring and control, while cloud-based solutions provide greater flexibility and accessibility. The choice of deployment mode depends on factors such as data privacy concerns, customization requirements, and the need for remote management capabilities.
- **Pricing (Free, Basic, Premium, and Others)** The pricing strategy of parental control software can influence its adoption and market penetration. Free versions may attract a larger user base but may lack advanced features, while premium packages offer a comprehensive set of functionalities for a higher cost. The pricing segmentation caters to different user preferences, from those looking for basic monitoring to users seeking advanced parental control features.
- **Function (Time Management, Gaming, App Management, Web Access,
TABLE OF CONTENTS
Part 01: Executive Summary
Part 02: Scope of the Report
Part 03: Research Methodology
Part 04: Market Landscape
Part 05: Pipeline Analysis
Part 06: Market Sizing
Part 07: Five Forces Analysis
Part 08: Market Segmentation
Part 09: Customer Landscape
Part 10: Regional Landscape
Part 11: Decision Framework
Part 12: Drivers and Challenges
Part 13: Market Trends
Part 14: Vendor Landscape
Part 15: Vendor Analysis
Part 16: Appendix
Core Objective of Parental Control Software Market:
Every firm in the Parental Control Software Market has objectives but this market research report focus on the crucial objectives, so you can analysis about competition, future market, new products, and informative data that can raise your sales volume exponentially.
Size of the Parental Control Software Market and growth rate factors.
Important changes in the future Parental Control Software Market.
Top worldwide competitors of the Market.
Scope and product outlook of Parental Control Software Market.
Developing regions with potential growth in the future.
Tough Challenges and risk faced in Market.
Global Parental Control Software top manufacturers profile and sales statistics.
Browse Trending Reports:
Digital Holographic Display Market Robotics End Effector Market Outboard Engines Market Connected Solutions for Oil and Gas Market Biotechnological Plant Breeding and CRISPR Plants Market Canned Tuna Market Zinc Methionie Chelates Market Watches Market Shoe Rack Market Capsule Hotel Market Chickpea Protein Market Weill-Marchesani Syndrome Market
About Data Bridge Market Research:
Data Bridge set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge endeavors to provide appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Contact Us:
Data Bridge Market Research
US: +1 614 591 3140
UK: +44 845 154 9652
APAC : +653 1251 975
Email: [email protected]
0 notes
Text
How to Speed Up Your Laptop in 3 Easy Steps! ⚡ #TechHacks #PCTips #FasterPerformance

Are you tired of your laptop dragging its feet while you try to get work done or enjoy your favorite shows? You're not alone! Many laptop users face performance issues over time, but the good news is that you can often revive your device's speed without any technical expertise. Here, we present three simple steps to enhance your laptop's performance significantly.
Step 1: Clean Up Your Hard Drive
Over time, your laptop accumulates files, applications, and temporary data that can slow it down. Cleaning up your hard drive is an essential first step in speeding up your laptop.
How to Do It:
Uninstall Unused Applications: Go through your applications list and remove those you no longer use. To do this on Windows, go to Settings > Apps > Apps & Features, and on macOS, drag the app from the Applications folder to the Trash.
Delete Temporary Files: Use built in tools like Disk Cleanup on Windows (search for "Disk Cleanup") or the "Optimize Storage" option on macOS to delete temporary files and free up space.
Organize Files: Keep your files organized. Move them to external storage or cloud services if you don't need them readily accessible.
Step 2: Optimize Startup Programs
Having too many programs launch at startup can significantly slow down your laptop’s boot time and overall performance.
How to Do It:
Manage Startup Programs: On Windows, right click the taskbar and select Task Manager. Go to the Startup tab to see which programs are set to launch at startup. Disable any unnecessary applications. On macOS, go to System Preferences > Users & Groups > Login Items to manage your startup programs.
Limit Background Processes: Some applications run in the background, consuming resources even when you’re not using them. Check the Task Manager (Windows) or Activity Monitor (macOS) to identify and close unnecessary processes.
Step 3: Upgrade Your Hardware
If you've done all the software optimizations and your laptop still feels sluggish, it might be time to consider a hardware upgrade.
Options to Consider:
Add More RAM: Increasing your laptop's RAM can help it run multiple applications more smoothly. Most laptops allow for RAM upgrades, which can significantly boost performance for multitasking.
Switch to an SSD: If you’re still using a traditional hard drive (HDD), consider upgrading to a Solid State Drive (SSD). SSDs are much faster and can dramatically decrease load times for your operating system and applications.
Clean the Hardware: Dust and debris can accumulate inside your laptop, leading to overheating and performance issues. Periodically cleaning the vents and fans can help maintain optimal performance.
Conclusion
Improving your laptop's speed doesn't have to be a daunting task. By following these three easy steps—cleaning up your hard drive, optimizing startup programs, and considering hardware upgrades—you can breathe new life into your laptop and enjoy faster performance in no time!
Stay tuned for more #TechHacks and #PCTips to keep your devices running smoothly. Your laptop deserves the best care!
0 notes
Text
Title: Best Windows Endpoint Management: Top Tools, Strategies & Benefits
In today’s increasingly digital world, endpoint management is no longer optional — it’s essential. Whether you’re running a small business or managing enterprise-level IT systems, choosing the best Windows endpoint management solution is critical to ensuring security, productivity, and scalability.
This blog explores what Windows endpoint management is, why it matters, and how to select the best Windows endpoint management tools in 2025 and beyond.
What Is Windows Endpoint Management?
Windows endpoint management refers to the process of monitoring, maintaining, and securing end-user devices such as laptops, desktops, mobile phones, and tablets that run the Windows operating system. This includes:
Deploying software and updates
Enforcing security policies
Monitoring device health and performance
Managing access and compliance
With remote work and hybrid workplaces on the rise, organizations need endpoint management solutions that offer central visibility, automation, and strong security protocols.
Why Choosing the Best Windows Endpoint Management Solution Matters
The best Windows endpoint management solution provides significant benefits:
1. Improved Security
A robust solution helps prevent malware, ransomware, and unauthorized access by enforcing strict security configurations.
2. Streamlined IT Operations
Automation of tasks like patching, software deployment, and configuration saves time and reduces human error.
3. Remote Work Enablement
Teams can manage endpoints anywhere, ensuring continuous performance and compliance regardless of user location.
4. Regulatory Compliance
Businesses subject to GDPR, HIPAA, or other regulations need to enforce consistent endpoint security and reporting.
Features to Look for in the Best Windows Endpoint Management Tools
When evaluating tools, look for features that align with your business needs:
Unified Endpoint Management (UEM): Manage all devices — including Windows, macOS, Android, and iOS — from a single console.
Real-Time Monitoring and Alerts
Automated Patch Management
Remote Device Control
Compliance and Reporting Tools
Cloud and On-Premises Support
Scalability for growing environments
Top Tools for Best Windows Endpoint Management in 2025
Here are some of the most trusted and powerful tools available:
1. RestoreX360
RestoreX360 stands out as the best Windows endpoint management platform available today. Built with scalability and enterprise security in mind, RestoreX360 offers a full suite of features such as automated patching, threat detection, remote access, compliance management, and real-time analytics. Its intuitive interface and powerful automation make it an ideal choice for businesses of all sizes.
2. Microsoft Intune
A cloud-based tool from Microsoft that integrates deeply with Azure Active Directory and Microsoft 365. Intune is ideal for organizations fully invested in the Microsoft ecosystem.
3. VMware Workspace ONE
Known for robust UEM capabilities, Workspace ONE supports policy enforcement, patching, and remote troubleshooting.
4. ManageEngine Endpoint Central
Great for businesses of all sizes, this solution offers automated patching, remote control, and detailed reporting.
5. Symantec Endpoint Management
Backed by strong threat detection and AI features, Symantec excels in large enterprise environments.
6. CrowdStrike Falcon
Focused more on endpoint protection but includes lightweight management features with high-performance cloud-based analytics.
Best Practices for Implementing Windows Endpoint Management
Once you select the best Windows endpoint management tool, follow these practices:
📅 Conduct a Needs Assessment
Understand your device ecosystem, compliance needs, and existing IT capabilities.
🔧 Automate Where Possible
Utilize automation for patching, updates, and compliance checks.
🔐 Enforce Security Policies
Use tools to require strong passwords, encryption, and multi-factor authentication.
🔍 Monitor and Audit
Ensure continuous visibility into endpoint status, alerts, and vulnerabilities.
Future Trends in Windows Endpoint Management
The landscape of endpoint management is rapidly evolving. Emerging trends to watch include:
AI and Machine Learning for predictive threat detection
Zero Trust Architecture becoming a standard
Cloud-native UEM tools dominating the market
BYOD support with advanced policy enforcement
Final Thoughts
As businesses evolve, so do the threats and challenges in managing endpoints. Investing in the best Windows endpoint management solution isn’t just about managing devices — it’s about empowering your workforce, securing your assets, and staying ahead of IT complexity.
By understanding your needs and aligning them with the right tools and practices, you can build a scalable, secure, and efficient IT environment for years to come.
Looking for the best Windows endpoint management strategy for your business? Start with a needs audit, explore leading tools like RestoreX360, and commit to a proactive IT management approach.
Use this guide as your foundation to build smarter, stronger endpoint systems in 2025 and beyond.
Frequently Asked Questions (FAQs)
What makes RestoreX360 the best Windows endpoint management solution?
RestoreX360 combines powerful automation, real-time analytics, and robust security protocols in one easy-to-use platform. It is designed to scale with your business, supports remote management, and provides seamless compliance reporting — making it an ideal choice for both SMBs and enterprises.
Is RestoreX360 suitable for remote or hybrid teams?
Absolutely. RestoreX360 supports full remote management, allowing IT teams to monitor, patch, and secure devices regardless of where employees are working — making it a top-tier solution for hybrid and distributed workforces.
How does RestoreX360 ensure endpoint security?
RestoreX360 uses a multi-layered approach, including automated patch management, threat detection, encryption enforcement, and access control policies to minimize risks and ensure endpoint security across your organization.
Can RestoreX360 integrate with existing IT infrastructure?
Yes. RestoreX360 offers seamless integration with existing tools, including identity providers, ticketing systems, and reporting dashboards. It’s built to be flexible, so it enhances — not disrupts — your current setup.
Is RestoreX360 cost-effective for small businesses?
Definitely. RestoreX360 offers scalable pricing that fits organizations of all sizes. Small businesses can access enterprise-grade endpoint management capabilities without breaking the bank, ensuring security and efficiency from day one.
0 notes
Text
“The Ultimate RDP Checklist: What to Look for in Remote Access Software”
In today’s hybrid and remote-first business environment, having reliable Remote Desktop Protocol (RDP) software isn’t optional—it’s essential. But with so many options in the market, how do you choose the right one?
Whether you're a system administrator, a business owner, or a startup founder, this ultimate RDP checklist will help you evaluate the features that matter most—and explain why RHosting checks all the boxes.
🔐 1. Security First: Encryption & Access Controls
Must-have:
End-to-end encryption (TLS/SSL)
Two-factor authentication (2FA)
Brute-force attack protection
IP filtering and whitelisting
Why it matters: Your remote desktop solution is a gateway to your servers. Security lapses can lead to massive data breaches. Choose software that prioritizes cybersecurity by design.
✅ RHosting delivers enterprise-grade encryption, 2FA, and granular user-level access for peace of mind.
⚙️ 2. Application-Level Access
Must-have:
Restrict access to only specific applications
Prevent users from accessing the full desktop
Why it matters: Not every user needs full server access. Limit exposure and reduce the chance of accidental (or intentional) damage.
✅ RHosting lets you assign individual apps to users—great for contractors, part-timers, and clients.
🗂 3. Granular Folder-Level Permissions
Must-have:
Assign folder-level access based on user roles
Read/write permissions customization
Why it matters: Need-to-know access prevents data leaks and keeps sensitive information restricted to authorized users.
✅ RHosting offers a highly configurable control panel to define folder-level rules across departments.
🚀 4. Performance & Speed
Must-have:
Low latency connections
Optimized for bandwidth efficiency
Fast load times for large apps and files
Why it matters: Lag can destroy productivity. Ensure your RDP software is optimized for both speed and heavy use.
✅ RHosting is designed for high performance—even with resource-intensive applications like development tools or data analysis software.
📲 5. Device & OS Compatibility
Must-have:
Windows, macOS, Linux, iOS, and Android support
Web-based access option
Why it matters: Your team likely uses multiple devices. Cross-platform support ensures everyone can work from anywhere.
✅ RHosting offers multi-device compatibility with browser-based login, eliminating software installs.
🔧 6. No Hardware Configuration Required
Must-have:
Cloud-hosted RDP service
Plug-and-play setup
No need for on-premise servers
Why it matters: Startups and small businesses shouldn’t need an IT department to deploy remote access. Look for a provider that offers a zero-hardware setup.
✅ RHosting is fully cloud-based—no server setup or firewall configurations required.
📊 7. Scalability & Flexibility
Must-have:
Easy to add/remove users
Scalable storage and processing power
Pricing that grows with your needs
Why it matters: Your RDP solution should grow as your team grows—without disruption.
✅ RHosting allows on-demand scaling and user management via an intuitive dashboard.
🛠 8. Admin Tools & Analytics
Must-have:
Centralized admin dashboard
User activity logs and access history
Real-time monitoring
Why it matters: Admins need insight into who accessed what, when, and from where—especially for audits and compliance.
✅ RHosting delivers full visibility with real-time logs and activity reports.
✅ Conclusion: Not All RDP Software Is Created Equal
The best RDP solution isn’t just about connecting to a remote machine—it’s about security, performance, control, and user experience.
Use this checklist to compare your current or potential provider. If you're ready for a smarter, more secure way to work remotely, RHosting is your answer.
🚀 Ready to experience remote access without compromise?
Sign up for a free trial of RHosting and discover why IT teams, startups, and enterprises trust us to power their remote work.
0 notes
Text
Elevating Small Business IT: Reliable Support & Cybersecurity by Modernizing Tech
In today's digital-first world, even small technical hiccups can halt business operations. From slow systems to potential cybersecurity breaches, the challenges small businesses face are vast. That’s where Modernizing Tech steps in — offering trusted tech support services near me, expert IT troubleshooting and repair, secure remote technical support in the USA, and advanced cybersecurity for small business.
Let’s explore why Modernizing Tech has become the go-to IT partner for small businesses across the United States.
Reliable Tech Support Services Near You
The need for dependable, responsive, and local tech support is greater than ever. Whether you’re a startup or a growing business, having access to tech support services near me can make all the difference.
Modernizing Tech understands that small businesses can't afford long downtimes. Their local tech support teams are strategically placed to provide prompt assistance when issues arise. From hardware malfunctions and network issues to software errors, the team offers quick diagnostics and resolutions—either on-site or remotely.
With a focus on friendly communication, transparent pricing, and fast problem-solving, Modernizing Tech becomes more than just a service provider—they’re your long-term technology partner.
Expert IT Troubleshooting and Repair
Every business, big or small, eventually runs into technical problems. What separates successful businesses from the rest is how quickly and efficiently they resolve these issues.
Modernizing Tech specializes in IT troubleshooting and repair for all major systems, including Windows, macOS, Linux, and various enterprise tools. Their certified technicians take a deep-dive approach—identifying root causes and offering lasting fixes instead of quick patches.
Common problems Modernizing Tech resolves include:
Network outages and poor connectivity
Device and printer malfunctions
Software conflicts or application crashes
Data recovery and system boot failures
Peripheral integration problems
By offering both remote and on-site repair options, Modernizing Tech ensures that your business stays functional, secure, and productive.
Nationwide Remote Technical Support USA
One of Modernizing Tech’s standout offerings is its efficient and accessible remote technical support in the USA. In a time when remote work is the norm, remote troubleshooting has become not just a convenience but a necessity.
Modernizing Tech leverages secure remote desktop tools to access systems, perform diagnostics, and implement solutions in real time—without needing to step into your office. This is especially beneficial for:
Remote teams and distributed employees
Small businesses in rural or underserved areas
After-hours or emergency tech support needs
No matter where your business is based, their remote technical support USA team is just a call or chat away—providing nationwide coverage with local-level care.
What sets them apart? Their 24/7 availability, transparent issue tracking, and commitment to data security.
Cybersecurity for Small Business: Stay Protected
Cyber threats don’t discriminate based on the size of your business. In fact, small businesses are often prime targets for cybercriminals because they usually lack enterprise-level defenses.
Modernizing Tech provides comprehensive cybersecurity for small business solutions that are both affordable and effective. Their services include:
Advanced firewalls and anti-virus setups
Secure remote access solutions
Endpoint protection and monitoring
Employee cybersecurity training
Regular vulnerability assessments
Backup and disaster recovery planning
Modernizing Tech doesn’t just install protective tools—they actively monitor and manage your security framework. Their proactive approach minimizes risk while maximizing your peace of mind.
Small businesses can now benefit from cybersecurity once reserved for corporations—thanks to Modernizing Tech’s tailored, cost-efficient packages.
Why Choose Modernizing Tech?
Modernizing Tech was founded on the belief that every business—regardless of size—deserves professional, reliable, and affordable IT support. Here’s why clients trust them:
Whether you’re looking for help with daily tech issues or need long-term guidance for IT growth, Modernizing Tech stands ready.
Real-World Impact: A Client Testimonial
Before Modernizing Tech, every tech issue felt like a crisis. Since partnering with them, our network is stable, our data is secure, and our team is more productive than ever. Their remote support has saved us countless hours!
Final Thoughts
From local tech support services near me to full-scale cybersecurity for small business, Modernizing Tech covers the IT needs of modern companies from every angle. Their mix of local presence, remote capabilities, and expert solutions make them a trusted partner for businesses across the United States.
If you're tired of inconsistent tech support and worrying about digital threats, it's time to elevate your IT experience. Let Modernizing Tech streamline your operations, secure your systems, and future-proof your business.
0 notes
Text
The Best VPN for Sweden with Servers and FreeVPN Options in 2025
Best VPNs for Sweden with Servers
1️⃣ NordVPN – The Top Pick for Speed and Security
NordVPN offers over 5,500 servers worldwide, including several in Sweden. Known for blazing speeds, tight security, and advanced tools like Double VPN and CyberSec, it’s a trusted choice for both casual and power users.
2️⃣ Surfshark – Unlimited Connections, Budget Price
With more than 3,200 servers in 100+ countries (including Sweden), Surfshark’s standout feature is unlimited device connections. Its CleanWeb, MultiHop, and Camouflage Mode make it a secure and budget-friendly option.
3️⃣ Proton VPN – Privacy-First, with a Free Plan
Proton VPN is perfect for privacy-minded users. Based in Switzerland, it offers strong encryption, Secure Core routing, and servers in Sweden. Its free version even provides unlimited data — a rare perk.
⭐ CoverMeVPN – The Rising Star for Swedish Servers
If you’re searching for a VPN specifically tailored for Sweden with reliable servers and a simple, user-friendly experience, CoverMeVPN is worth checking out.
Why Highlight CoverMeVPN?
🔒 Dedicated Swedish Servers: CoverMeVPN offers fast, stable servers in Sweden, making it perfect for accessing Swedish streaming platforms, local news, and services while abroad.
🛡️ Strict No-Logs Policy: It prioritizes your privacy, ensuring your online activities are never stored or monitored.
🚀 Fast Speeds and Unlimited Bandwidth: Ideal for streaming, gaming, and secure browsing without interruptions.
📱 Cross-Platform Apps: Available on Windows, macOS, iOS, Android, and browser extensions for Chrome and Firefox.
💸 Competitive Pricing: More affordable than many big names, with regular promotions and free trial options.
CoverMeVPN is quickly becoming a top-tier option for anyone serious about safe and unrestricted Swedish internet access.
5️⃣ CyberGhost – Streaming-Optimized Servers
CyberGhost has over 10,000 servers globally and excellent coverage in Sweden. It’s a popular pick for unblocking Netflix, BBC iPlayer, and other services. Plus, it comes with a generous 45-day refund policy.
6️⃣ Mullvad VPN – The Anonymity Expert
Based in Sweden itself, Mullvad is famous for its no-personal-information signup model. Users get a random account number, ensuring total anonymity, alongside secure OpenVPN and WireGuard protocols.
🆓 Best FreeVPN Options with Swedish Servers
When you’re on a budget or just need a quick, secure connection, these free VPN services offer solid options with Swedish servers:
1️⃣ Proton VPN Free
Arguably the best free VPN around, offering unlimited data and secure servers in Sweden — no credit card required.
2️⃣ Urban VPN
A truly free VPN service with Swedish servers, Urban VPN supports unlimited bandwidth and a no-logs policy.
⭐ CoverMeVPN’s Free Trial – A Hidden Gem
While primarily a paid VPN, CoverMeVPN offers a generous free trial option and frequent promotions, allowing new users to test its premium Swedish servers risk-free.
Why is this Worth Highlighting?
🎁 Access Premium Swedish Servers for Free: No credit card required during trial promotions.
🕶️ Full-Feature Access: Unlike most free VPNs, CoverMeVPN’s trial includes high-speed streaming, torrenting support, and security tools.
🔐 Encrypted Browsing: Keeps your data secure without limitations.
🏆 Better Performance than Standard Free VPNs: No overcrowded servers or throttling during trial use.
If you’re tired of free VPNs with limitations, CoverMeVPN’s trial is a standout alternative.
4️⃣ VPN.lat
Simple, mobile-friendly, and free, VPN.lat offers access to Swedish servers with unlimited bandwidth and encryption.
5️⃣ Planet VPN
No sign-ups required, offering encrypted connections and Swedish IP addresses for privacy-focused users.
6️⃣ 1ClickVPN
A browser extension that delivers instant, free connections to Swedish servers with a simple, no-registration setup.
🔍 How to Choose the Right VPN for Sweden
Consider these factors when picking a VPN:
Speed and server quality in Sweden
Strong encryption and no-logs policy
Ability to unblock streaming services
Trial or free version availability
Ease of use on your preferred devices
CoverMeVPN checks all these boxes while offering a smooth, privacy-first experience with both premium plans and free trials.
📝 Final Thoughts
For users in Sweden or those wanting to access Swedish content securely:
🥇 NordVPN and Surfshark shine for speed and security.
🔒 Proton VPN and Mullvad lead for privacy.
🎥 CyberGhost is ideal for streamers.
⭐ CoverMeVPN is the standout all-rounder — affordable, privacy-focused, and with dedicated Swedish servers and a trial option that outperforms standard free VPNs.
Whether you’re browsing, streaming, gaming, or working remotely, having a reliable VPN with Swedish servers is a smart investment for your online privacy and freedom.
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the brand Founded in 1996, Vimtag is a leading provider of smart home camera products and solutions. Our direction is to keep up with the latest technology in the field of intelligent surveillance, integrate digital and network technology, enhance the brand's core technology competitive advantage, to achieve industry-leading, world-class technology. VIMTAG CCTV Camera Clear Details Day & Night: VIMTAG's CCTV camera for home full set provides 2.5K high resolution with a 3.6mm lens and 4-megapixel clarity. Equipped with an infrared LED light, this wifi CCTV camera for home delivers clear night vision, allowing you to monitor every detail whether day or night. Perfect for any security camera system for home, it works seamlessly with 2.4GHz Wi-Fi 360 Degree Monitor: VIMTAG's home camera 360 degree features pan and tilt functions, offering 355° horizontal and 115° vertical rotation. This wireless camera lets you remotely control it through various systems (iOS/Android/macOS/Windows) and devices (smartphones/pads/laptops/desktops), ensuring complete real-time monitoring of your home or CCTV camera for shop Conversation Free: VIMTAG's 360 degree camera comes with a built-in speaker and microphone, allowing you to hear and speak through the camera. Whether you're at work, traveling, or on a business trip, you can easily communicate with babies, pets, and older family members. This wireless camera for home security also allows you to share the surveillance feed with your family Smart Detection: VIMTAG's wifi camera for home offers advanced features like motion detection, human detection, and sound detection. Compatible with Alexa, this indoor camera for home can sound alarms to alert you of suspicious activity. As a versatile IP camera, it also allows you to capture and store precious moments through photos and videos Worry-Free Use: VIMTAG's wireless CCTV camera for home ensures 24-hour continuous recording, supporting SD cards up to 512GB and optional cloud storage (fees apply). Ideal as a CCTV camera wifi for home or shop, it automatically overwrites old recordings, ensuring you never run out of space [ad_2]
0 notes
Text
Nguyên nhân MacBook bị nóng – Hiểu rõ để sử dụng hiệu quả hơ
MacBook từ lâu đã nổi tiếng nhờ thiết kế tinh tế, hiệu suất mạnh mẽ và hệ điều hành ổn định. Tuy nhiên, không ít người dùng đã từng gặp tình trạng MacBook bị nóng bất thường trong quá trình sử dụng, đặc biệt là khi làm việc nặng hoặc sử dụng thời gian dài. Vậy nguyên nhân do đâu? Và làm sao để khắc phục? Hãy cùng tìm hiểu chi tiết trong bài viết dưới đây.
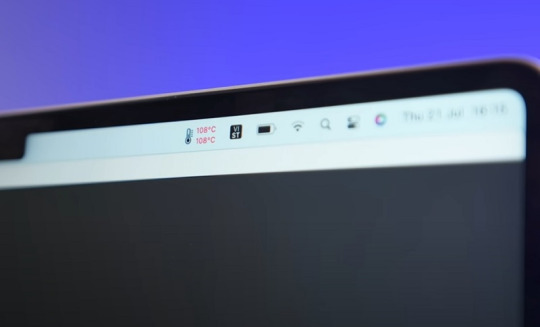
1. 💻 Tải công việc nặng và đa nhiệm quá mức
Một trong những nguyên nhân phổ biến khiến MacBook nóng lên là do chạy quá nhiều ứng dụng cùng lúc hoặc xử lý các tác vụ nặng như dựng video, chơi game 3D, lập trình, hoặc mở nhiều tab trình duyệt. Những tác vụ này yêu cầu CPU và GPU hoạt động hết công suất, từ đó sinh ra nhiều nhiệt.
👉 Cách khắc phục: Hạn chế mở quá nhiều ứng dụng không cần thiết cùng lúc. Kiểm tra Activity Monitor để tắt các tiến trình tiêu tốn nhiều tài nguyên.
2. 🌐 Trình duyệt và các tiện ích mở rộng (extensions)
Trình duyệt như Chrome thường "ngốn" rất nhiều RAM và CPU, đặc biệt khi mở nhiều tab hoặc cài nhiều tiện ích mở rộng. Điều này khiến máy hoạt động căng thẳng hơn, dẫn đến tăng nhiệt độ.
👉 Cách khắc phục: Cân nhắc chuyển sang Safari – trình duyệt được tối ưu tốt hơn cho macOS. Xóa hoặc vô hiệu hóa những tiện ích không cần thiết.
3. 🧼 Bụi bẩn và tắc khe tản nhiệt
Sau thời gian dài sử dụng, bụi có thể tích tụ trong khe tản nhiệt hoặc quạt làm mát. Điều này khiến không khí nóng không được thoát ra ngoài hiệu quả, dẫn đến tình trạng nóng máy.
👉 Cách khắc phục: Định kỳ vệ sinh MacBook bằng cách đem đến trung tâm bảo hành hoặc dịch vụ vệ sinh uy tín.
4. 🌡️ Môi trường sử dụng nóng hoặc không thoáng khí
Sử dụng MacBook trên bề mặt mềm như chăn, nệm hay trong môi trường nóng bức khiến việc tản nhiệt kém hiệu quả, nhiệt độ tích tụ lại và gây nóng máy.
👉 Cách khắc phục: Đặt máy trên bề mặt cứng, phẳng và thông thoáng. Có thể sử dụng thêm đế tản nhiệt hoặc kê cao phần sau máy để tăng khả năng lưu thông không khí.
5. 🔄 Cập nhật phần mềm lỗi hoặc xung đột hệ thống
Đôi khi sau khi cập nhật macOS hoặc cài phần mềm mới, máy gặp xung đột khiến CPU hoạt động bất thường, dẫn đến tăng nhiệt độ. Những lỗi này thường đi kèm hiện tượng quạt quay mạnh hoặc máy chạy chậm.
👉 Cách khắc phục: Kiểm tra bản cập nhật mới nhất từ Apple. Gỡ bỏ các ứng dụng không tương thích và khởi động lại máy.
0 notes
Text
Sure, here is an article based on your request:
Mac OS Mining Software - paladinmining.com
Are you a Mac user interested in mining cryptocurrency? Look no further than Paladin Mining. Our platform offers the best tools and software for macOS users to start their mining journey.
Why Choose Paladin Mining?
Paladin Mining provides a seamless experience for macOS users who want to get into cryptocurrency mining. Our software is designed specifically for Apple devices, ensuring optimal performance and ease of use. Whether you're a beginner or an experienced miner, our platform has everything you need to start earning.
How It Works
1. Download and Install: Visit https://paladinmining.com to download our dedicated Mac OS mining software. The installation process is straightforward and can be completed in just a few clicks.
2. Set Up Your Account: Once installed, create an account on Paladin Mining. This will allow you to track your earnings and manage your mining activities.
3. Start Mining: With your account set up, you can begin mining immediately. Our software supports various cryptocurrencies, giving you the flexibility to choose which one you want to mine.
4. Monitor Your Progress: Use our dashboard to monitor your mining progress and earnings in real-time. You can also adjust your settings to optimize your mining efficiency.
Benefits of Using Paladin Mining
User-Friendly Interface: Our software is designed with simplicity in mind, making it easy for anyone to start mining.
High Performance: Optimized for macOS, our software ensures that your device runs smoothly while mining.
Security: We prioritize security, ensuring that your data and earnings are protected at all times.
Support: Our team is always available to assist you with any questions or issues you may have.
Get Started Today
Ready to start earning with Paladin Mining? Visit https://paladinmining.com to download our Mac OS mining software and begin your mining journey today!
This article should help attract Mac users interested in cryptocurrency mining and guide them towards using Paladin Mining's services.
加飞机@yuantou2048

Paladin Mining
paladinmining
0 notes
Text
Common Macbook Problems & Their Fixes From Macbook Repair Professionals
Every MacBook user has experienced that moment of panic when their device starts acting up. Perhaps it’s running slower than usual, or the battery seems to drain faster than a leaky bucket. These moments can be frustrating, especially when you rely on your MacBook for work or leisure. Here’s a guide to some frequent MacBook problems and their fixes, as shared by professionals offering MacBook repair service in Gold Coast.

1. Slow Performance
Restart Your MacBook - A quick restart can often refresh the system.
Close Unnecessary Applications - Use Activity Monitor to identify resource-hogging apps.
Free Up Disk Space - Delete unused files and clear cache.
Upgrade RAM - Consider upgrading RAM for older models to enhance performance.
2. Battery Life Issues
Check Battery Health - Navigate to System Preferences > Battery > Battery Health.
Reduce Brightness - Lowering screen brightness can extend battery life.
Disable Unused Features - Turn off Bluetooth and Wi-Fi when not in use.
Update macOS - Keeping your system updated can improve battery efficiency.
3. Overheating
Keep Vents Clear - Ensure vents are unobstructed and clean.
Use on Hard Surfaces - Avoid soft surfaces that block airflow.
Monitor Resource Usage - Close apps that are using excessive CPU.
Check for Software Updates - Updates can resolve overheating issues.
4. Connectivity Problems
Restart Your Router - Sometimes the issue lies with the router.
Forget and Reconnect to the Network - Re-establish your connection.
Update macOS - Ensure your system is up to date.
Reset SMC and PRAM - This can often fix connectivity issues.
5. Unresponsive Keyboard or Trackpad
Restart Your MacBook - A simple restart can resolve many issues.
Check for Debris - Ensure there’s no dirt under the keys or trackpad.
Update macOS - Keeping your system updated is crucial.
Reset SMC - This can fix hardware-related problems.
By following these troubleshooting steps from experts of MacBook repairs in Gold Coast, you can often resolve common MacBook issues and keep your device running smoothly. If problems persist, seeking professional assistance may be the best course of action.
0 notes
Text
Employee Monitoring - Parental Control Software
SentryPC is a comprehensive monitoring and control software designed for businesses, parents, and individuals who want to monitor and manage computer or device usage. It’s often used for employee monitoring, parental control, or personal productivity tracking.
Here’s an overview of what SentryPC offers:
What is SentryPC?
SentryPC is a cloud-based software that allows you to monitor and control computer or device activity in real-time. It’s compatible with Windows and macOS systems and provides a wide range of features to track usage, enforce restrictions, and generate detailed reports.
Key Features of SentryPC
1. Monitoring Features
Keystroke Logging: Tracks all keystrokes typed on the device, including passwords (optional).
Screen Capture: Takes periodic screenshots of the device’s screen.
Application Monitoring: Records which applications are used and for how long.
Website Monitoring: Tracks visited websites and blocks inappropriate or distracting sites.
File Activity: Monitors file downloads, uploads, and modifications.
Chat and Email Monitoring: Tracks activity on messaging apps and email clients.
2. Control Features
Time Restrictions: Limits the amount of time a user can spend on the device or specific applications.
Website Blocking: Blocks access to specific websites or categories (e.g., social media, gambling).
Application Blocking: Prevents users from opening certain applications.
Keyword Alerts: Notifies you when specific keywords are typed or searched.
3. Reporting and Alerts
Detailed Reports: Generates comprehensive reports on user activity, including websites visited, applications used, and keystrokes typed.
Real-Time Alerts: Sends instant notifications when restricted activities occur.
4. Remote Management
Cloud-Based Dashboard: Access and manage all monitored devices from a single online dashboard.
Remote Control: Make changes to settings or restrictions from anywhere.
Who is SentryPC For?
Parents: Monitor and control children’s computer usage to ensure they stay safe online.
Employers: Track employee productivity and prevent misuse of company devices.
Individuals: Monitor personal devices for security or productivity purposes.
How Does SentryPC Work?
Install the Software: Download and install SentryPC on the device(s) you want to monitor.
Set Up Monitoring and Controls: Customize settings through the cloud-based dashboard.
Monitor Activity: View real-time activity and receive alerts or reports.
Pricing
SentryPC offers flexible pricing plans based on the number of devices and the duration of the license. Plans typically include:
1 Device License: For individual users.
Multi-Device Licenses: For families or businesses monitoring multiple devices.
Conclusion
SentryPC is a powerful tool for monitoring and controlling computer usage, making it ideal for parents, employers, and individuals who want to ensure safety, productivity, or accountability.
Its cloud-based nature and wide range of features make it a popular choice for remote monitoring and management.
0 notes
Text
Common MacBook Issues and How to Spot Them Early
Apple’s MacBook lineup is known for its sleek design, powerful performance, and durability. However, like any other device, MacBooks can develop issues over time. Recognizing these problems early can save you from costly repairs or even data loss. Whether you’re dealing with slow performance, battery problems, or screen glitches, spotting these issues at an early stage is crucial. If you need professional assistance, Mac Repairs Melbourne offers expert solutions to keep your MacBook running efficiently.
1. MacBook That Won’t Turn On
This is one of the most frustrating MacBook issues, especially when you rely on your device for daily tasks. A MacBook that won’t turn on can stem from various underlying causes. Some of the most common issues include a dead battery, faulty power adapters, issues with the logic board, or even problems with the display.
Signs to Look Out For:
No response when pressing the power button
No startup chime or fan noise
A black screen with no signs of power
The charger LED doesn’t light up
Possible Causes:
Faulty power adapter or battery: If your charger is damaged or your battery is completely drained, your MacBook may not turn on.
Corrupt macOS installation: Software issues can sometimes prevent the device from booting.
Logic board failure: A faulty motherboard can cause power-related issues.
Damaged internal components: If your MacBook has suffered physical damage, internal components may be affected.
What You Can Do:
Check the power source – Try using a different charger or plugging the device into a different outlet.
Perform an SMC reset – Resetting the System Management Controller (SMC) can resolve many power-related issues.
Check for signs of life – Listen for fan noises or see if the keyboard lights up when pressing the power button.
Contact a professional – If your MacBook still won’t turn on, it’s time to seek help from Mac Repairs Melbourne for a thorough diagnosis.
2. Slow Performance and Freezing
MacBooks are known for their speed and efficiency, but over time, you may notice a slowdown in performance. This can be frustrating, especially when working on tasks that require quick processing. Slow performance can result from various factors including outdated software, lack of storage space, or even hardware issues such as a failing hard drive.
Causes of Slow Performance:
Too many background apps – Excessive open applications can consume system resources.
Low storage space – A nearly full SSD can impact system speed.
Outdated macOS – Running an older version of macOS may cause performance issues.
Malware or viruses – Although rare, malware can slow down your system.
Early Warning Signs:
Longer boot-up times
Unresponsive apps
Frequent crashes or freezing
How to Fix It:
Close unnecessary apps – Use Activity Monitor to identify and close resource-heavy applications.
Free up disk space – Delete unused files and consider upgrading to a larger SSD.
Update macOS – Ensure you’re running the latest version of macOS for better performance.
Run a malware scan – Use reliable security software to check for malicious software.
If the problem persists, professional Mac technicians at Mac Repairs Melbourne can help optimize your system and improve its speed.
3. Battery Draining Quickly
Battery life is one of the most critical factors in a MacBook’s performance. If your MacBook is several years old, you might start to notice that the battery doesn’t last as long as it used to. Apple provides a battery health feature, which allows you to monitor your battery’s condition directly from the system preferences. If your battery health is below 80%, it’s probably time to consider a replacement.
Common Causes:
Aging battery – Over time, batteries lose their capacity.
Background applications – Apps running in the background can consume power.
High brightness levels – Keeping your screen brightness at maximum drains battery life.
Malfunctioning hardware – A faulty battery or charging system may be the cause.
Warning Signs:
Rapid battery percentage drop
MacBook shuts down unexpectedly
Battery doesn’t charge fully
Solutions:
Check battery health – Go to “About This Mac” > “System Report” > “Power” to check battery cycles.
Reduce brightness and close unused apps – Adjusting brightness and quitting unnecessary applications can help conserve battery life.
Reset PRAM and SMC – This can resolve battery-related issues.
Get a battery replacement – If your battery cycle count is too high, consider getting a replacement from Mac Repairs Melbourne.
4. Overheating and Fan Noise
MacBooks are designed to be quiet and efficient, but excessive fan noise and overheating can indicate a deeper issue.
Causes of Overheating:
Dust buildup – Over time, dust can clog internal fans.
Running intensive apps – Apps like video editors or gaming software can push your MacBook to its limits.
Malfunctioning cooling system – A faulty fan or thermal paste degradation can cause overheating.
How to Spot It Early:
Hot surface temperature
Loud or constantly running fan
Unexpected shutdowns due to overheating
How to Fix It:
Keep your MacBook on a hard surface – Soft surfaces can block ventilation.
Clean dust from vents – Use compressed air to remove dust from fans and vents.
Close CPU-intensive apps – Check Activity Monitor for apps consuming excessive resources.
Visit a repair expert – If the issue persists, Mac Repairs Melbourne can diagnose and fix cooling system problems.
5. Display and Screen Issues
A faulty screen can make your MacBook unusable, affecting productivity and usability.
Common Screen Problems:
Flickering screen
Dead pixels
Screen discoloration
Black screen with no display
Possible Causes:
Loose display connections – Internal wiring issues can cause display malfunctions.
Faulty graphics card – Hardware failures can lead to screen distortions.
Physical damage – Drops and impacts can crack or damage the screen.
How to Fix It:
Restart your MacBook – A simple restart can resolve minor screen glitches.
Check for software updates – Sometimes, a macOS update can fix display issues.
Reset PRAM and SMC – This can recalibrate display settings.
Consult a professional – If the problem persists, Mac Repairs Melbourne offers screen replacements and repairs.
6. Keyboard and Trackpad Malfunctions
Keyboard and trackpad issues are common in MacBooks, particularly in older models.
Symptoms:
Unresponsive keys
Sticky or repeating keys
Trackpad not clicking properly
Possible Causes:
Dust and debris – Small particles can obstruct key movement.
Software bugs – Certain macOS updates may cause input issues.
Physical damage – Drops or spills can damage the keyboard and trackpad.
Solutions:
Clean the keyboard – Use compressed air to remove dust and debris.
Check system preferences – Adjust settings in System Preferences > Keyboard/Trackpad.
Reset SMC and PRAM – This can restore normal functionality.
Seek professional repairs – If cleaning and resets don’t work, contact Mac Repair Melbourne for expert assistance.
Conclusion
Early detection of MacBook issues can save you time, money, and frustration. Whether your device is overheating, running slow, or refusing to turn on, addressing the problem quickly can prevent further damage. Mac Repairs Melbourne provides expert solutions for all MacBook-related issues, ensuring your device stays in top condition
0 notes