#microsoft access database
Explore tagged Tumblr posts
Text
kits in warrior cats should just spawn in no parents no siblings they just appear maybe then we could stop with the unfortunate implications
#its either that or the erins learn after like 20 years how to manage their goddamn family trees#try microsoft access. kind of a learning curve but i feel a database could really help
14 notes
·
View notes
Text
Me: I love to study! I wish I had more time for education!
Me studying:

#most of this course has been fun to be fair but#this is me trying to learn microsoft access#i know what all these words mean individually#but put together this is gibberish#looking after my kid all day then trying to get my head around databases and table relationships??? nobody suffers more than me#my posts
5 notes
·
View notes
Text
Database design and management course and Assignment help

Contact me through : [email protected]
I will provide advice and assistance in your database and system design course. I will handle everything including;
Normalization
Database design (ERD, Use case, concept diagrams etc)
Database development (SQL and Sqlite)
Database manipulation
Documentation
#database assignment#assignment help#SQL#sqlserver#Microsoft SQL server#INSERT#UPDATE#DELETE#CREATE#college student#online tutoring#online learning#assignmentwriting#Access projects#Database and access Final exams
4 notes
·
View notes
Text
as someone who loves Excel...

An F1 team should have dedicated software for this. At the very least they need an actual database for monitoring parts.
No company, big or small, should use Excel this way. It's meant for accounting finances calculations, not looking up part numbers on race weekends!
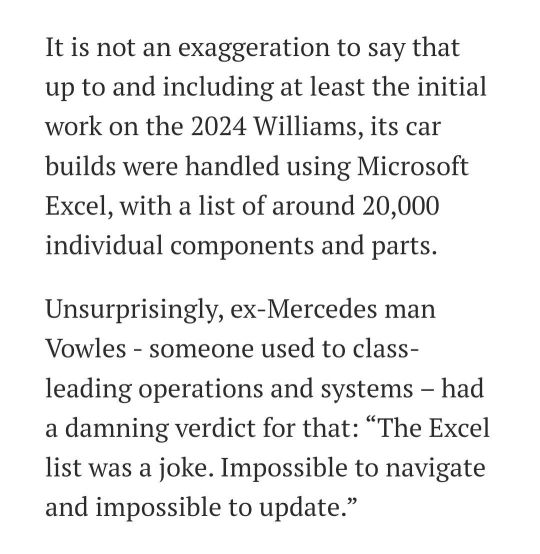
So uh it turns out that the outdated system to track their car parts that Vowles was talking about last year was actually Microsoft Excel. Williams had been using Excel to list and track 20,000 parts of a Formula One car every year.
#f1#stop using excel as a database#it's not designed for that#yes you can force it to function this way#but you should really switch to Microsoft Access or SQL for heavy duty databases
884 notes
·
View notes
Text
Microsoft disponibiliza SQL Server Migration Assistant V9.4
A Microsoft disponibilizou recentemente a versão 9.4 do Microsoft SQL Server Migration Assistant, uma ferramenta gratuita que simplifica a migração de Access, MySQL, SAP Adaptive Server Enterprise, Oracle Database e IBM DB2 para SQL Server e Azure SQL DB. Continue reading Untitled

View On WordPress
#Access#Azure SQL DB#IBM DB2#Microsoft#MySQL#Oracle Database#SAP Adaptive Server Enterprise#SQL Server#SQL Server Migration Assistant V9.4
1 note
·
View note
Text
Migrating Off Evernote
Evernote, a web-based notes app, recently introduced super-restrictive controls on free accounts, after laying off a number of staff and introducing AI features, all of which is causing a lot of people to migrate off the platform. I haven't extensively researched alternative sites, so I can't offer a full resource there (readers, feel free to drop your alternative sites in notes or reblogs), but because I have access to OneNote both in my professional and personal life, I decided to migrate my Evernote there.
I use them for very different things -- Evernote I use exclusively as a personal fanfic archive, because it stores fics I want to save privately both as full-text files and as links. OneNote I have traditionally used for professional purposes, mainly for taking meeting notes and storing information I need (excel formulas, how-tos for things I don't do often in our database, etc). But while Evernote had some nicer features it was essentially a OneNote clone, and OneNote has a webclipper, so I've created an account with OneNote specifically to store my old Evernote archive and any incoming fanfic I want to archive in future.
Microsoft discontinued the tool that it offered for migrating Evernote to OneNote directly, but research turned up a reliable and so-far trustworthy independent tool that I wanted to share. You export all your Evernote notebooks as ENEX files, then download the tool and unzip it, open the exe file, and import the ENEX one by one on a computer where you already have the desktop version of OneNote installed. I had no problem with the process, although some folks with older systems might.
I suspect I might need to do some cleanup post-import but some of that is down to how Evernote fucked around with tags a while ago, and so far looking through my notes it appears to have imported formatting, links, art, and other various aspects of each clipped note without a problem. I also suspect that Evernote will not eternally allow free users to export their notebooks so if nothing else I'd back up your notebooks to ENEX or HTML files sooner rather than later.
I know the number of people who were using Free Evernote and have access to OneNote is probably pretty small, but if I found it useful I thought others might too.
436 notes
·
View notes
Text
Microsoft's CEO Satya Nadella has hailed the company's new Recall feature, which stores a history of your computer desktop and makes it available to AI for analysis, as “photographic memory” for your PC. Within the cybersecurity community, meanwhile, the notion of a tool that silently takes a screenshot of your desktop every five seconds has been hailed as a hacker's dream come true and the worst product idea in recent memory.
Now, security researchers have pointed out that even the one remaining security safeguard meant to protect that feature from exploitation can be trivially defeated.
Since Recall was first announced last month, the cybersecurity world has pointed out that if a hacker can install malicious software to gain a foothold on a target machine with the feature enabled, they can quickly gain access to the user's entire history stored by the function. The only barrier, it seemed, to that high-resolution view of a victim's entire life at the keyboard was that accessing Recall's data required administrator privileges on a user's machine. That meant malware without that higher-level privilege would trigger a permission pop-up, allowing users to prevent access, and that malware would also likely be blocked by default from accessing the data on most corporate machines.
Then on Wednesday, James Forshaw, a researcher with Google's Project Zero vulnerability research team, published an update to a blog post pointing out that he had found methods for accessing Recall data without administrator privileges—essentially stripping away even that last fig leaf of protection. “No admin required ;-)” the post concluded.
“Damn,” Forshaw added on Mastodon. “I really thought the Recall database security would at least be, you know, secure.”
Forshaw's blog post described two different techniques to bypass the administrator privilege requirement, both of which exploit ways of defeating a basic security function in Windows known as access control lists that determine which elements on a computer require which privileges to read and alter. One of Forshaw's methods exploits an exception to those control lists, temporarily impersonating a program on Windows machines called AIXHost.exe that can access even restricted databases. Another is even simpler: Forshaw points out that because the Recall data stored on a machine is considered to belong to the user, a hacker with the same privileges as the user could simply rewrite the access control lists on a target machine to grant themselves access to the full database.
That second, simpler bypass technique “is just mindblowing, to be honest,” says Alex Hagenah, a cybersecurity strategist and ethical hacker. Hagenah recently built a proof-of-concept hacker tool called TotalRecall designed to show that someone who gained access to a victim's machine with Recall could immediately siphon out all the user's history recorded by the feature. Hagenah's tool, however, still required that hackers find another way to gain administrator privileges through a so-called “privilege escalation” technique before his tool would work.
With Forshaw's technique, “you don’t need any privilege escalation, no pop-up, nothing,” says Hagenah. “This would make sense to implement in the tool for a bad guy.”
In fact, just an hour after speaking to WIRED about Forshaw's finding, Hagenah added the simpler of Forshaw's two techniques to his TotalRecall tool, then confirmed that the trick worked by accessing all the Recall history data stored on another user's machine for which he didn't have administrator access. “So simple and genius,” he wrote in a text to WIRED after testing the technique.
That confirmation removes one of the last arguments Recall's defenders have had against criticisms that the feature acts as, essentially, a piece of pre-installed spyware on a user's machine, ready to be exploited by any hacker who can gain a foothold on the device. “It makes your security very fragile, in the sense that anyone who penetrates your computer for even a second can get your whole history,” says Dave Aitel, the founder of the cybersecurity firm Immunity and a former NSA hacker. “Which is not something people want.”
For now, security researchers have been testing Recall in preview versions of the tool ahead of its expected launch later this month. Microsoft said it plans to integrate Recall on compatible Copilot+ PCs with the feature turned on by default. WIRED reached out to the company for comment on Forshaw's findings about Recall's security issues, but the company has yet to respond.
The revelation that hackers can exploit Recall without even using a separate privilege escalation technique only contributes further to the sense that the feature was rushed to market without a proper review from the company's cybersecurity team—despite the company's CEO Nadella proclaiming just last month that Microsoft would make security its first priority in every decision going forward. “You cannot convince me that Microsoft's security teams looked at this and said ‘that looks secure,’” says Jake Williams, a former NSA hacker and now the VP of R&D at the cybersecurity consultancy Hunter Strategy, where he says he's been asked by some of the firm's clients to test Recall's security before they add Microsoft devices that use it to their networks.
“As it stands now, it’s a security dumpster fire,” Williams says. “This is one of the scariest things I’ve ever seen from an enterprise security standpoint.”
144 notes
·
View notes
Text
i will strangle you

#all jokes aside#excel is not a programming language#and if i hear one more person call it a database they die#microsoft ACCESS is a database manager#and it's not even a very good one#EXCEL IS A GLORIFIED CSV EDITOR#if you don't know the difference between a csv file and a relational database i do not know how to help you#excel is great if you need to do your taxes or calculate income or w/e#but if you need to do anything real#for the love of brian w kernighan please write a script#if you need a database then install postgres#or sqlite#or SOMETHING that is SEARCHABLE in a REASONABLE AMOUNT OF TIME#YOU WILL THANK YOURSELF LATER
1K notes
·
View notes
Text
Ok I've had a very random train of thoughts and now wanna compile it into post.
Some MM characters computer-related (???) headcanons lol
Riley:
Has above average knowledge of Excel/Google sheets due to studying finance, but after four years with no practise forgot most of it.
The "Sooon, I have a problem" person in their family. Actually, surprisingly good and patient at explaining computer stuff to older people.
Has a higher responsibility of doing taxes (finance, after all). Even he never fails to do them right, Ed always double checks. Sometimes they get into argument, where inevitably Riley proves he is right but his father would never admit it.
Warren, Leeza, Ooker and other teens:
Also nothing outstanding in terms of skills, except few of them have interest in IT.
They have bunch of small local Discord servers and one big main server with some very stupid name.
Few times Bev tried to bring up importance of parental control over this "new and rapidly growing young community", but thanks God no one took her concerns seriously
Leeza moderates it and her moder role called "Mayor-mini". Like father like daughter.
All teens local jokes and memes were bourn/spread though that server.
Bev:
Rumors says she sacrificed her humanity to obtain such powers with Microsoft software package.
Can build up Access database from scratch, using basic SQL commands, assemble primitive, but surprisingly sufficient interface to it and synchronize it with Excel in span of one day or less.
In her laptop there're every pupil's personal file, countless Excel tables, several automatised document accounts, Google calendar with precisely planned schedule for next several months (for school, church, island and personal matters) and probably Pentagon files.
Probably can find all Pi numbers with Excel formulas.
Never lets anyone to her laptop.
Spends her free time at different forums, mostly gardening-related.
Wade:
Made a very fucking poor decision to let Bev do all the legwork with digital document accounting.
Now has no idea how some of things even work, so just goes with a flow and does what Bev tells.
No wander she got away with embezzlement.
Knows about kid's server. Very proud of Leeza for managing it :)
Because of that, he knows one or two memes from there, but keeps them in secret.
Has hobby of fixing office equipment. Does it with Sturge in spare time due to Dupuytren's contracture not letting him operate his hand fully.
Sarah:
There's no good medical technicians on island, so when something goes wrong with equipment electronics - tries to fix it herself to best of her ability.
Always monitors electronic e-shops for spare details or equipment. Grows more and more addicted to it.
Frequently updates her selection of sites with useful medical information, because Erin asked her for help guiding teens though puberty. For that receives glances from Bev, but doesn't give a shit.
Has reputation of cool aunt among kids, so she was one and only adult invited to main Discord server. Didn't accept it (doesn't even have Discord acc), but still grateful for trust.
Plays solitaire a lot.
John:
Back when he was playing Paul, Bev asked him to do something with Excel. In conclusion, poor bastard had to learn basic computer skills and Excel in span of several days. Now he is traumatized for rest of his life.
Will do all the work manually just to not touch laptop again.
Upsets very easly when does something wrong.
Doesn't own laptop. Don't give that man laptop, he will cry.
By his own will uses it only to watch baseball. Always asks someone to help with that.
#midnight mass#midnight mass headcanons#beverly keane#idk I just felt silly and wanted to write it down#riley flynn#warren flynn#leeza scarborough#wade scarborough#sarah gunning#john pruitt#monsignor pruitt#father paul hill
24 notes
·
View notes
Text
"In the age of smart fridges, connected egg crates, and casino fish tanks doubling as entry points for hackers, it shouldn’t come as a surprise that sex toys have joined the Internet of Things (IoT) party.
But not all parties are fun, and this one comes with a hefty dose of risk: data breaches, psychological harm, and even physical danger.
Let’s dig into why your Bluetooth-enabled intimacy gadget might be your most vulnerable possession — and not in the way you think.
The lure of remote-controlled intimacy gadgets isn’t hard to understand. Whether you’re in a long-distance relationship or just like the convenience, these devices have taken the market by storm.
According to a 2023 study commissioned by the U.K.’s Department for Science, Innovation, and Technology (DSIT), these toys are some of the most vulnerable consumer IoT products.
And while a vibrating smart egg or a remotely controlled chastity belt might sound futuristic, the risks involved are decidedly dystopian.
Forbes’ Davey Winder flagged the issue four years ago when hackers locked users into a chastity device, demanding a ransom to unlock it.
Fast forward to now, and the warnings are louder than ever. Researchers led by Dr. Mark Cote found multiple vulnerabilities in these devices, primarily those relying on Bluetooth connectivity.
Alarmingly, many of these connections lack encryption, leaving the door wide open for malicious third parties.
If you’re picturing some low-stakes prank involving vibrating gadgets going haywire, think again. The risks are far graver.
According to the DSIT report, hackers could potentially inflict physical harm by overheating a device or locking it indefinitely. Meanwhile, the psychological harm could stem from sensitive data — yes, that kind of data — being exposed or exploited.
A TechCrunch exposé revealed that a security researcher breached a chastity device’s database containing over 10,000 users’ information. That was back in June, and the manufacturer still hasn’t addressed the issue.
In another incident, users of the CellMate connected chastity belt reported hackers demanding $750 in bitcoin to unlock devices. Fortunately, one man who spoke to Vice hadn’t been wearing his when the attack happened. Small mercies, right?
These aren’t isolated events. Standard Innovation Corp., the maker of the We-Vibe toy, settled for $3.75 million in 2017 after it was discovered the device was collecting intimate data without user consent.
A sex toy with a camera was hacked the same year, granting outsiders access to its live feed.
And let’s not forget: IoT toys are multiplying faster than anyone can track, with websites like Internet of Dongs monitoring the surge.
If the thought of a connected chastity belt being hacked makes you uneasy, consider this: sex toys are just a small piece of the IoT puzzle.
There are an estimated 17 billion connected devices worldwide, ranging from light bulbs to fitness trackers — and, oddly, smart egg crates.
Yet, as Microsoft’s 2022 Digital Defense Report points out, IoT security is lagging far behind its software and hardware counterparts.
Hackers are opportunistic. If there’s a way in, they’ll find it. Case in point: a casino lost sensitive customer data after bad actors accessed its network through smart sensors in a fish tank.
If a fish tank isn’t safe, why would we expect a vibrating gadget to be?
Here’s where the frustration kicks in: these vulnerabilities are preventable.
The DSIT report notes that many devices rely on unencrypted Bluetooth connections or insecure APIs for remote control functionality.
Fixing these flaws is well within the reach of manufacturers, yet companies routinely fail to prioritize security.
Even basic transparency around data collection would be a step in the right direction. Users deserve to know what’s being collected, why, and how it’s protected. But history suggests the industry is reluctant to step up.
After all, if companies like Standard Innovation can get away with quietly siphoning off user data, why would smaller players bother to invest in robust security?
So, what’s a smart-toy enthusiast to do? First, ask yourself: do you really need your device to be connected to an app?
If the answer is no, then maybe it’s best to go old school. If remote connectivity is a must, take some precautions.
Keep software updated: Ensure both the device firmware and your phone’s app are running the latest versions. Updates often include critical security patches.
Use secure passwords: Avoid default settings and choose strong, unique passwords for apps controlling your devices.
Limit app permissions: Only grant the app the bare minimum of permissions needed for functionality.
Vet the manufacturer: Research whether the company has a history of addressing security flaws. If they’ve been caught slacking before, it’s a red flag.
The conversation around sex toy hacking isn’t just about awkward headlines — it’s about how we navigate a world increasingly dependent on connected technology. As devices creep further into every corner of our lives, from the bedroom to the kitchen, the stakes for privacy and security continue to rise.
And let’s face it: there’s something uniquely unsettling about hackers turning moments of intimacy into opportunities for exploitation.
If companies won’t take responsibility for protecting users, then consumers need to start asking tough questions — and maybe think twice before connecting their pleasure devices to the internet.
As for the manufacturers? The message is simple: step up or step aside.
No one wants to be the next headline in a tale of hacked chastity belts and hijacked intimacy. And if you think that’s funny, just wait until your light bulb sells your Wi-Fi password.
This is where IoT meets TMI. Stay connected, but stay safe."
https://thartribune.com/government-warns-couples-that-sex-toys-remain-a-tempting-target-for-hackers-with-the-potential-to-be-weaponized/
#iot#I only want non-smart devices#I don't want my toilet to connect to the internet#seriously#smart devices#ai#anti ai#enshittification#smart sex toys
26 notes
·
View notes
Note
Hey, thanks for your work with the database. Unfortunately, all my work ended up there, but I decided not to care. If they want to train AI with mpreg ff, then go ahead xD I have another question - is this tool safe? I'm a bit (haha…) paranoid about the security of my laptop and I'm afraid that something might have happened. I saw that the database is built on a Microsoft tool, but I decided to ask anyway. I hope you don't take my question negatively…
HELL yeah, we need more mpreg in the world 🫡 and no offense at all!
Of course, I can only give you my word, but yes. The database is hosted entirely through my account with Microsoft and does not download anything to your device unless you tell it to. I believe I have data downloads turned off so that shouldn't even be an option. Even if you CAN download the data...
As far as the actual data in there, I pared it down to be more minimal than even the metadata-only set. No additional tags, no fandoms, characters, or relationships. The only data this tool has at all is the work ID, the author who wrote it, the title, the chapter count, and sometimes the number of hits at the time of the scrape. All of this data is still available via the metadata-only dataset that's still online as of my last check. I don't believe I can even view who has accessed it.
Generally, this is all information that anyone could find on AO3 right now as well.
I am hoping to make a post about how I played with the dataset just so it's completely transparent, but I haven't had the free time to do that yet.
13 notes
·
View notes
Text
I started writing "4 srs" this month and I like how free and accessible writing is, so I'm recommending free software I've experimented with that might help people who want to get into the hobby!
“Specifically Created for Writing Stories”
-------------------------------
Manuskript – Story organizer / word processor. Has an outliner and index card function, along with distraction free mode. Lets you switch between different templates such as a non-fiction mode or a short story.
Bibisco – Novel writing software that includes writing goals, world-building, distraction free mode, and a timeline.
“I Just Want to Write”
---------------------------
LibreOffice – Microsoft 365 alternative, but free! LibreOffice Writer is what I wrote this tumblr post in before I posted it. Also if you copy & paste the text into the Rich Text Editor on AO3, it seems that it actually converts it properly. Nice! No need for scripts.
Note-Taking
-------------------------------
Zim Wiki - note taking application that is very, very lightweight (1.1mb). It functions with a tree structure, so I’d personally recommend it for world-building and character bios. There are built-in plugins that also turn it into a good software for task management (it even has a article on how to use it for GTD) and journalling. See also: CherryTree (2mb), which is a more outdated-looking app, but functions similarly.
Obsidian MD – The Big Boy. markdown note editor that has been adopted by personal knowledge management fans---if it doesn’t do something you want it to do, just look in the community plugins to see if someone has already done it. Some unique non-word processing related usages I’ve found is the ability to create a table of contents dashboard, a image gallery for images, embedding youtube videos and timestamping notes, so forth.
Logseq – A bullet point based markdown note editor that also has PDF annotations, Zotero integration, flashcard creation, and whiteboards. Best used for outlining projects due to the bullet point structure.
Joplin – A modern app comparable to Zim Wiki, it’s basically just a note-taking software that uses folders and tags to sort easier. Looks prettier than Zim Wiki and Cherry Tree
Notion – An online-only website that allows usage of different database types. Free for personal use. Note: I dislike the AI updates that have been making the app lag more. I prefer the others on this list.
Mind Maps
-------------------------------
Freeplane – So much goddamn features, including a ton of add-ons. Looks somewhat ugly, but it works for anyone willing to spend a while learning how to use it.
Mermaid – Text-based diagram creator. Can be used in apps like Joplin, Notion, and Obsidian.
Obsidian’s Canvas – A core plugin for Obsidian, it deserves its own mention in that it allows you to create embedded notes of the mindmap nodes. Thus, if you want to create a 20-page long note and have it minimized to the size of a penny on the mindmap, you could.
Other Things That Might Be Of Interest
Syncthing - A free software that allows you to sync between two or more computers. Have a desktop but also laze around on a laptop in bed, coming up with ideas?? This is your buddy if you don't want to use a online software.
125 notes
·
View notes
Text
Working in an enterprise environment is such a clusterfuck because often the answer to "why" is just "because."
In IT, change control and delegation of duties is critical, but enterprise environments take that to the extreme. I got a ticket requesting a preferred name change (not even a legal one, just a nickname) and got lightly chewed out for making the change... But like why? I have admin access to Active Directory, I just have to enter data into a single field, why should I bother the AD admin who's probably running out of hair to pull and is operating dangerously close to being hospitalized for caffeine overdose, when I could just make the change myself? Why should I bother this dude? Because.
I don't miss how little I was paid at my last job, but I miss that someone could ask me to do anything and I had the option to be like "fuck it, I have no clue how to do this, but I've got a six year old reddit thread to reference and my stack overflow account was unbanned today, so give me three hours... maybe six if the stack overflow mods see the email I sent them yesterday."
To be fair I think I'm seriously overqualified for this position, I used to administer databases and now I follow call flow charts to help someone sign in to Microsoft.
9 notes
·
View notes
Text

Trap to Enslave Humanity Artificial intelligence - for the benefit of mankind!? The company OpenAI developed its AI software ChatGPT under this objective. But why was a head of espionage of all people appointed to the board? Is ChatGPT really a blessing or possibly even a trap to enslave humanity? (Moderator) Develop artificial intelligence (AI) supposedly for the benefit of humanity! With this in mind, the company OpenAI was founded in 2015 by Sam Altman, Elon Musk and others. Everyone knows its best-known software by now – the free ChatGPT – it formulates texts, carries out Internet searches and will soon be integrated into Apple and Microsoft as standard. In the meantime, however, there is reason to doubt the "charity" proclaimed by the company when it was founded.
Founder Sam Altman is primarily concerned with profits. Although ChatGPT can be used free of charge, it is given access to personal data and deep insights into the user's thoughts and mental life every time it is operated. Data is the gold of the 21st century. Whoever controls it gains enormous power.
But what is particularly striking is the following fact: Four-star general Paul Nakasone, of all people, was appointed to the board of OpenAI in 2024. Previously, Nakasone was head of the US intelligence agency NSA and the United States Cyber Command for electronic warfare. He became known to the Americans when he publicly warned against China and Russia as aggressors. The fact that the NSA has attracted attention in the past for spying on its own people, as well as on friendly countries, seems to have been forgotten. Consequently, a proven cold warrior is joining the management team at OpenAI. [Moderator] It is extremely interesting to note that Nakasone is also a member of the Board's newly formed Safety Committee. This role puts him in a position of great influence, as the recommendations of this committee are likely to shape the future policy of OpenAI. OpenAI may thus be steered in the direction of practices that Nakasone has internalized in the NSA. According to Edward Snowden, there can only be one reason for this personnel decision: "Deliberate, calculated betrayal of the rights of every human being on earth." It is therefore not surprising that OpenAI founder, Sam Altmann, wants to assign to every citizen of the world a "World ID", which is recorded by scanning the iris. Since this ID then contains EVERYTHING you have ever done, bought and undertaken, it is perfect for total surveillance. In conjunction with ChatGPT, it is therefore possible to maintain reliable databases on every citizen in the world. This is how the transparent citizen is created: total control of humanity down to the smallest detail. In the wrong hands, such technology becomes the greatest danger to a free humanity! The UN, the World Bank and the World Economic Forum (WEF) are also driving this digital recording of every citizen of the world. Since all these organizations are foundations and strongholds of the High Degree Freemasons, the World ID is therefore also a designated project of these puppet masters on their way to establishing a One World Government. The fact that Sam Altman wants to push through their plans with the support of General Nakasone and was also a participant at the Bilderberg Conference in 2016, 2022 and 2023 proves that he is a representative of these global strategists, if not a high degree freemason himself. The Bilderberg Group forms a secret shadow government and was founded by the High Degree Freemasons with the aim of creating a new world order. Anyone who has ever been invited to one of their conferences remains associated with the Bilderbergers and, according to the German political scientist and sociologist Claudia von Werlhof, is a future representative of this power!
Since countless people voluntarily disclose their data when using ChatGPT, this could bring the self-appointed would-be world rulers a lot closer to their goal. As Kla.TV founder Ivo Sasek warns in his program "Deadly Ignorance or Worldwide Decision", the world is about to fall into the trap of the big players once again via ChatGPT. So, dear viewers, don't be dazzled by the touted advantages of AI. It is another snare of the High Degree Freemasons who are weaving a huge net to trap all of humanity in it. Say NO to this development!
#Trap to Enslave Humanity#Artificial Intelligence#AI#World ID#World Control#ChatGPT#Wake up#Do your research#Seek the Truth
12 notes
·
View notes
Text
Patrick Beuth, Jörg Diehl, Roman Höfner, Roman Lehberger, Friederike Röhreke, and Fidelius Schmid at Der Spiegel:
Private contact details of the most important security advisers to U.S. President Donald Trump can be found on the internet. DER SPIEGEL reporters were able to find mobile phone numbers, email addresses and even some passwords belonging to the top officials. To do so, the reporters used commercial people search engines along with hacked customer data that has been published on the web. Those affected by the leaks include National Security Adviser Mike Waltz, Director of National Intelligence Tulsi Gabbard and Secretary of Defense Pete Hegseth. Most of these numbers and email addresses are apparently still in use, with some of them linked to profiles on social media platforms like Instagram and LinkedIn. They were used to create Dropbox accounts and profiles in apps that track running data. There are also WhatsApp profiles for the respective phone numbers and even Signal accounts in some cases. As such, the reporting has revealed an additional grave, previously unknown security breach at the highest levels in Washington. Hostile intelligence services could use this publicly available data to hack the communications of those affected by installing spyware on their devices. It is thus conceivable that foreign agents were privy to the Signal chat group in which Gabbard, Waltz and Hegseth discussed a military strike.
Numbers Linked to Signal Accounts
It remains unclear, however, whether this extremely problematic chat was conducted using Signal accounts linked to the private telephone numbers of the officials involved. Tulsi Gabbard has declined to comment. DER SPIEGEL reporting has demonstrated, though, that privately used and publicly accessible telephone numbers belonging to her and Waltz are, in fact, linked to Signal accounts. [...] The White House confirmed the scandal after the fact. Trump insisted that it did not include classified content, a question that is of particular relevance since members of the U.S. government are not permitted to share such information over Signal. The U.S. special envoy for Ukraine and the Middle East, Steve Witkoff, was even in Russia while participating in the chat group.
DER SPIEGEL was able to find some of the contact information for Gabbard, Hegseth and Waltz in commercial databases, while other information was in so-called password leaks, which are hardly a rarity on the internet. One example is the 2019 discovery by Troy Hunt, who found 773 million email addresses and more than 21 million passwords in a hacker forum. Since then, there have been numerous additional leaks. Criminals are constantly compiling new collections from hacks, usually to sell them on forums. [...] The mobile number provided, meanwhile, led to a WhatsApp account that Hegseth apparently only recently deleted. The profile photo showed a shirtless Hegseth in a baseball cap and necklace. Comparisons with other photos of the U.S. secretary of defense using facial recognition software were able to confirm that the photo on the WhatsApp profile was indeed Hegseth.
Several Passwords in Leaked Database
Waltz’s mobile number and email address could be found using the same service provider. The mobile phone number could even be found using a people search engine popular in the U.S. DER SPIEGEL reporters were also able to find several passwords for Waltz’s email address in leaked databases. The information also led to Waltz’s profiles for Microsoft Teams, LinkedIn, WhatsApp and Signal. National Intelligence Director Gabbard was seemingly more careful with her data than her two male colleagues. She apparently had her own data blocked in the commercial contact search engines that contained the data of Hegseth and Waltz. But her email address was to be found on WikiLeaks and Reddit. Gabbard’s email address is available in more than 10 leaks. One of those also contains a partial telephone number, which, when completed, leads to an active WhatsApp account and a Signal profile.
German publication Der Spiegel writes that several of the National Security Advisers for the Trump Administration, including Pete Hegseth, Tulsi Gabbard, and Michael Waltz, had their private data breached and the passwords found online.
#Der Spiegel#Pete Hegseth#Tulsi Gabbard#Michael Waltz#National Security#Trump Administration II#Yemen Signal Leak#Data Breaches#Steve Witkoff#Jeffrey Goldberg#Signal#John Ratcliffe
7 notes
·
View notes
Text
i woke up feeling Nihilistic about Technology so now you must all suffer with me most people are probably not keeping up with what the tech companies are actually making, doing, demoing, with AI in the way i am. and that's okay you will not like what you hear most likely. i am also not any kind of technology professional. i just like technology. i just read about technology. there's sort of two things that are happening in tandem which is:
there is a race between some of the biggest ones (google, meta, openai, microsoft, etc. along with some not yet household name ones like perplexity and deepseek) to essentially Decide, make the tech, and Win at this technology. think of how Google has been the defacto ruler of the internet between the Search Engine that delivers web pages, and the Ad Engine that makes money for advertisers and google. they have all of the information and make the majority of the money. AI is the first technology in 20 years that has everyone scrambling to become the new Google of That.
ChatGPT, the thing we have access to right now, it is stupid sometimes. but the reason every single company is pushing this shit is because they want to be First to make a product that Works, and they also are rebuilding how we will interact with the internet from the ground up. the thing basically everyone wants is to control 'the window' as it were between You typing things into the computer, and the larger internet. in a real way, Google owns 'the window' in many meaningful (monetary) ways. the future that basically every company is working towards right now is a version of the the websites on the internet become more of a database; a collection of data that can be accessed by the AI model. every computer you use becomes the Search box on Google.com, but when you type things into it, it just finds information and spits it out in front of you. there is a future where 'the internet' is just an AI chat bot.
holding those two ideas at once (everyone wants to be the Google of AI, and also every single tech company wants us to look at the internet in a way they choose and have control over) THIS SUCKS. THIS SUCKS ASS.
THE THING THAT IS BEAUTIFUL ABOUT THE INTERNET IS THAT IT IS OPEN. you can, in almost every place in the world, build a stupid website and connect it to the internet and anyone can look at it. ANYONE. we have absolutely NOTHING ELSE as universal, as open, as this. every single tech company is trying to change this in a meaningful way. in the Worst version of this, the internet just looks like the ChatGPT page, because it scrapes data and regurgitates it back to you. instead of seeing the place where this data was written, formatted, presented, on its own website like god intended
the worst part is: despite the posts you see from almost everyone in our respective bubbles about how AI sucks, we won't use it, it's bad for the environment, etc. NORMAL PEOPLE are using this shit all of the time. they are fine that it occasionally is wrong. and also the models of the various Chatbot AIs is getting better everyday at not being wrong. for like the first time in like 20 years since google launched, there is a real threat that the place people go to search for things online is rapidly shifting somewhere else. because people are using this stuff. the loudest people against AI are currently a minority of loud voices. not only is this not going away, but it is happening. this is actually web 3.0. and it's going to be so shit
this is not to say you will not be able to go to tumblr.com. but it will take effort. browser applications are basically not profitable, just ask Mozilla. google has chrome, which makes money because it has you use Google and it tracks your data to sell you ads. safari doesn't make money, but apple Takes google's money to pay for maintaining it. most other browsers are just forked chromium.
in my opinion there will be one sad browser application for you to access real websites, it will eventually become unmaintained as people just go to the winner's AI chatbot app to access information online. 'websties' will become subculture; a group of hobbyists will maintain the thing that might let you access these things. normal people will move on from the idea of going to websites.
the future of the internet will be a sad, lonely place, where the sterile, commercially viable and advertiser friendly chatbot will tell you about whatever you type or say into the computer. it will encourage people to not make connections online, or even in their lives, because there will be a voice assistant they can talk with. one of the latest google demos, there is a person fixing their bicycle, having Gemini look thru the manual, tell them how to fix a certain part of the bike. Gemini calls a repair shop, and talks to the person on the other side. a lot of people covering this are like 'that future is extremely cool and interesting to me' and when i heard That that is when i know we have like. lost it.
for whatever reason, people want this kind of technology. and it makes me so sad.
4 notes
·
View notes