#nmapAutomator
Explore tagged Tumblr posts
Text
Comprehensive Guide on Network Reconnaissance using NmapAutomator
When conducting network reconnaissance or penetration testing, efficiency is key. NmapAutomator is a powerful tool that automates and streamlines the process of network scanning, allowing security professionals to focus on actual penetration testing rather than spending time on repetitive scanning tasks. This comprehensive guide on Network Reconnaissance explores what NmapAutomator is, how to set…
#cybersecurity tools#network reconnaissance#network scanning#network security#nmap#penetration testing#reconnaissance tools#security automation#vulnerability scanning
0 notes
Text
Autoenum - Automatic Service Enumeration Script
Autoenum - Automatic Service Enumeration Script #Autoenum #Automatic #AUTORECON #DirectoryOutput #Enumeration #nmap
[sc name=”ad_1″]
Autoenum is a recon tool which performs automatic enumeration of services discovered. I built this to save some time during CTFs and pen testing environments (i.e. HTB, VulnHub, OSCP) and draws a bit from a number of existing tools including AutoRecon (https://github.com/Tib3rius/AutoRecon), Auto-Recon (https://github.com/Knowledge-Wisdom-Understanding/Auto-Recon), and nmapautoma…
View On WordPress
#Autoenum#Automatic#AUTORECON#Directory Output#Enumeration#nmap#nmapAutomator#scan#Scans#Script#searchsploit#Service#Service Enumeration#Service Enumerations
0 notes
Text
nmapAutomator - A script that you can run in the background! The main goal for this script is...
nmapAutomator - A script that you can run in the background! The main goal for this script is to automate all of the processes of #recon/ enumeration that is run every time and instead focus our attention on real #pentesting. This will ensure two things: 1) Automate #Nmap scans. 2) Always have some recon running in the background. Once you find the initial ports in around 10 seconds, you then can start manually looking into those ports, and let the rest run in the background with no interaction from your side whatsoever. Features: 1. Quick: Shows all open ports quickly (~15 seconds) 2. Basic: Runs Quick Scan, then runs a more thorough scan on found ports (~5 minutes) 3. #UDP: Runs "Basic" on UDP ports (~5 minutes) 4. Full: Runs a full range port scan, then runs a thorough scan on new ports (~5-10 minutes) 5. Vulns: Runs #CVE scan and Nmap Vulns scan on all found ports (~5-15 minutes) 6. Recon: Runs "Basic" scan "if not yet run", then suggests recon commands "i.e. gobuster, #Nikto, #smbmap" based on the found ports, then prompts to automatically run them 7. All: Runs all the scans consecutively (~20-30 minutes) https://github.com/21y4d/nmapAutomator

GitHub - 21y4d/nmapAutomator: A script that you can run in the background! - GitHub A script that you can run in the background! Contribute to 21y4d/nmapAutomator development by creating an account on GitHub.
0 notes
Photo
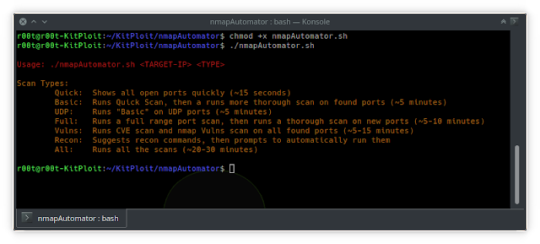
nmapAutomator – Tool To Automate All Of The Process Of Recon/Enumeration | MrHacker.Co #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo
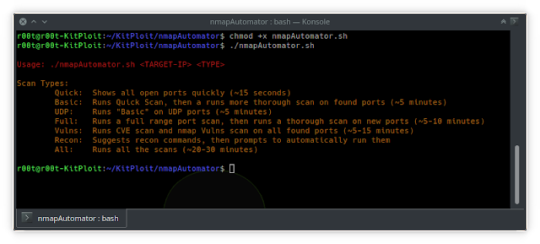
nmapAutomator – Tool To Automate All Of The Process Of Recon/Enumeration | MrHacker.Co #cybersecurity #ethicalhacking #hackandroid #hackapp #hackwordpress #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes