#openVPN Client
Explore tagged Tumblr posts
Note
what is the best way to get safer/more anonymous online
Ok, security and anonymity are not the same thing, but when you combine them you can enhance your online privacy.
My question is: how tech literate are you and what is your aim? As in do you live in a country where your government would benefit from monitoring private (political) conversations or do you just want to degoogle? Because the latter is much easier for the average user.
Some general advice:
Leave Windows and Mac operating systems and switch to Linux distributions like Fedora and Ubuntu (both very user friendly). Switch from Microsoft Office or Pages/Numbers/Keynote (Mac) to LibreOffice.
You want to go more hardcore with a very privacy-focused operating system? There are Whonix and Tails (portable operating system).
Try to replace all your closed source apps with open source ones.
Now, when it comes to browsers, leave Chrome behind. Switch to Firefox (or Firefox Focus if you're on mobile). Want to go a step further? Use LibreWolf (a modified version of Firefox that increases protection against tracking), Brave (good for beginners but it has its controversies), DuckDuckGo or Bromite. You like ecofriendly alternatives? Check Ecosia out.
Are you, like, a journalist or political activist? Then you probably know Tor and other anonymous networks like i2p, freenet, Lokinet, Retroshare, IPFS and GNUnet.
For whistleblowers there are tools like SecureDrop (requires Tor), GlobaLeaks (alternative to SecureDrop), Haven (Android) and OnionShare.
Search engines?
There are Startpage (obtains Google's results but with more privacy), MetaGer (open source), DuckDuckGo (partially open source), Searx (open source). You can see the comparisons here.
Check libRedirect out. It redirects requests from popular socmed websites to privacy friendly frontends.
Alternatives to YouTube that value your privacy? Odysee, PeerTube and DTube.
Decentralized apps and social media? Mastodon (Twitter alternative), Friendica (Facebook alternative), diaspora* (Google+ RIP), PixelFed (Insta alternative), Aether (Reddit alternative).
Messaging?
I know we all use shit like Viber, Messenger, Telegram, Whatsup, Discord etc. but there are:
Signal (feels like Whatsup but it's secure and has end-to-end encryption)
Session (doesn't even require a phone or e-mail address to sign up)
Status (no phone or e-mail address again)
Threema (for mobile)
Delta Chat (you can chat with people if you know their e-mail without them having to use the app)
Team chatting?
Open source options:
Element (an alternative to Discord)
Rocket.chat (good for companies)
Revolt.chat (good for gamers and a good alternative to Discord)
Video/voice messaging?
Brave Talk (the one who creates the talk needs to use the browser but the others can join from any browser)
Jami
Linphone
Jitsi (no account required, video conferencing)
Then for Tor there are various options like Briar (good for activists), Speek! and Cwtch (user friendly).
Georestrictions? You don't want your Internet Provider to see what exactly what you're doing online?
As long as it's legal in your country, then you need to hide your IP with a VPN (authoritarian regimes tend to make them illegal for a reason), preferably one that has a no log policy, RAM servers, does not operate in one of the 14 eyes, supports OpenVPN (protocol), accepts cash payment and uses a strong encryption.
NordVPN (based in Panama)
ProtonVPN (Switzerland)
Cyberghost
Mullvad (Sweden)
Surfshark (Netherlands)
Private e-mails?
ProtonMail
StartMail
Tutamail
Mailbox (ecofriendly option)
Want to hide your real e-mail address to avoid spam etc.? SimpleLogin (open source)
E-mail clients?
Thunderbird
Canary Mail (for Android and iOS)
K-9 Mail (Android)
Too many complex passwords that you can't remember?
NordPass
BitWarden
LessPass
KeePassXC
Two Factor Authenticators?
2FAS
ente Authenticator
Aegis Authenticator
andOTP
Tofu (for iOS)
Want to encrypt your files? VeraCrypt (for your disk), GNU Privacy Guard (for your e-mail), Hat.sh (encryption in your browser), Picocrypt (Desktop encryption).
Want to encrypt your Dropbox, Google Drive etc.? Cryptomator.
Encrypted cloud storage?
NordLocker
MEGA
Proton Drive
Nextcloud
Filen
Encrypted photography storage?
ente
Cryptee
Piwigo
Want to remove metadata from your images and videos? ExifCleaner. For Android? ExifEraser. For iOS? Metapho.
Cloak your images to counter facial recognition? Fawkes.
Encrypted file sharing? Send.
Do you menstruate? Do you want an app that tracks your menstrual cycle but doesn't collect your data? drip.
What about your sexual health? Euki.
Want a fitness tracker without a closed source app and the need to transmit your personal data to the company's servers? Gadgetbridge.
34 notes
·
View notes
Text
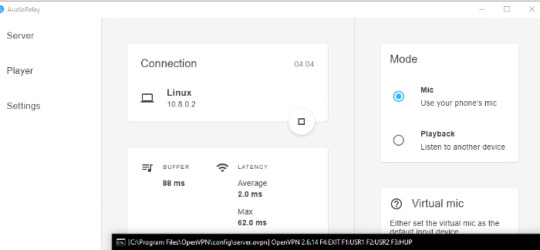
After 89 years, I have figured out how to run OpenVPN on Windows as a server so that Linux can connect to it as a client and then stream my Linux microphone to my Windows computer in real time so people can hear me while I also stream my Windows computer's screen to my Linux computer because Parsec never made a microphone passthrough driver for Linux
With no external help because nobody would help me.
if anyone else ever has this EXTREMELY NICHE issue, I will guide you from A to Z with no judgment
11 notes
·
View notes
Note
was there a guide you were following for the raspberry pi torrent box setup? that and Plex are the ideal but it seems like a nightmare to figure out
i used this guide to integrate NordVPN via OpenVPN, then this guide from the same site to set up the Transmission client. notably, the second article is slightly outdated as of April 2022, since the "pi" default root user no longer exists to give permissions to. i went through that part of the tutorial using my username ("pihole") in place of "pi" and nothing yelled at me and everything still works so worst case scenario it did literally nothing. i didn't follow the steps for setting up LAN file sharing because im saving everything to an external SSD and then just physically plugging that into my main desktop (USB 3.0 read/write speeds are like 8x faster than Ethernet, lol)
61 notes
·
View notes
Text
Transport Layer Security (TLS): The Backbone of a Secure Internet
In today’s digitally connected world, security and privacy are more important than ever. Whether you're accessing your bank account, shopping online, or simply browsing a website, you're likely using Transport Layer Security (TLS) — the cryptographic protocol that protects internet communications.
In this post, we’ll explore:
What TLS is and why it matters
How TLS works under the hood
TLS vs SSL
Real-world use cases
Common threats and how TLS mitigates them
Transport Layer Security (TLS) is a cryptographic protocol that ensures privacy, integrity, and authenticity of data exchanged over a network. It’s widely used to secure:
Web traffic (HTTPS)
Email (SMTP, IMAP, POP)
Messaging (XMPP, SIP)
VPNs and more
TLS operates between the transport layer (e.g., TCP) and the application layer (e.g., HTTP), encrypting the data before it's transmitted over the internet.
How TLS Works: Step by Step
When a client (e.g., browser) connects to a server over HTTPS, here's what happens:
1. Handshake Initiation
The client sends a ClientHello message:
Supported TLS versions
List of supported cipher suites
Random number (used in key generation)
Optional: SNI (Server Name Indication)
2. Server Response
The server replies with a ServerHello message:
Selected cipher suite
TLS version
Server's digital certificate (usually an X.509 certificate)
Optional: server key exchange
3. Authentication & Key Exchange
The client verifies the server's certificate via a trusted Certificate Authority (CA).
Both parties generate or agree on session keys using techniques like Diffie-Hellman or RSA.
4. Session Key Generation
Once keys are exchanged:
Both client and server compute a shared symmetric session key.
5. Secure Communication
All subsequent data is:
Encrypted using the session key
Authenticated (to detect tampering)
Integrity-protected using MACs (Message Authentication Codes)
TLS vs SSL: What’s the Difference?
People often say “SSL” when they mean TLS. Here’s the truth:Feature SSL (Deprecated)TLS (Current)Latest VersionSSL 3.0 (1996)TLS 1.3 (2018)SecurityVulnerableStrongUse TodayNone (shouldn't be used)Everywhere
Modern websites and applications use TLS 1.2 or TLS 1.3, and all versions of SSL are considered insecure.
TLS Use Cases
HTTPS (TLS over HTTP)
Secure browsing (padlock in browser)
Required for PCI DSS, GDPR compliance
Email Encryption
Secure SMTP (STARTTLS)
IMAP/POP with TLS
VoIP and Messaging
TLS protects SIP, XMPP, and chat services
VPNs
OpenVPN uses TLS for secure tunnels
APIs and Microservices
Internal and external APIs often rely on TLS to secure REST and GraphQL endpoints
Common Threats and TLS ProtectionsThreatTLS DefenseMan-in-the-Middle (MITM)Authentication via certificatesEavesdroppingSymmetric encryption of session dataTampering or Data CorruptionMessage integrity with MACsReplay AttacksRandom values and sequence numbersDowngrade AttacksTLS version enforcement & SCSV mechanism
Best Practices for TLS Configuration
Use TLS 1.2 or TLS 1.3 only.
Disable SSL and TLS 1.0/1.1 completely.
Use strong cipher suites (e.g., AES-GCM, ChaCha20).
Regularly renew and monitor your TLS certificates.
Enable HSTS (HTTP Strict Transport Security).
Use tools like SSL Labs, Mozilla Observatory to test your server.
TLS in Action (Example)
When you visit https://sfouresolutions.com:
Your browser initiates a TLS handshake.
The server sends its certificate.
A session key is negotiated.
Your browser encrypts the HTTP request with that key.
The server decrypts it, processes it, and responds securely.
All of this happens within milliseconds, seamlessly.
Final Thoughts
TLS is a foundational technology that quietly protects the internet. As cyber threats grow in sophistication, strong TLS configurations and practices are not optional — they are essential.
Whether you're a developer, sysadmin, or business owner, understanding TLS helps you build safer systems and protect user trust.
0 notes
Text
NordVPN Uses Post-Quantum Encryption To Protect User Data

After-quantum encryption
NordVPN has implemented post-quantum encryption on all platforms to combat future quantum attacks.
NordVPN, a leading cybersecurity service, released post-quantum encryption across all its VPN apps. This crucial upgrade has been fully implemented across all supported platforms to prevent large-scale quantum computers from decrypting user data.
Implementation began with the September 2024 version of NordVPN Linux. This phase includes the first post-quantum NordLynx protocol cryptographic improvement in a Linux software update. WireGuard calls NordLynx a fast and secure VPN protocol. The revised technique met NIST's latest post-quantum encryption criteria. Linux deployments aimed to protect users against quantum decryption and measure performance metrics like latency and connection rates.
"The collected data served as a stepping stone to quantum-resistant encryption on the rest of the platforms," said NordVPN CTO Marijus Briedis. He said, “The Linux case demonstrated that it successfully maintained the highest level of user experience in terms of connection time and speed during the transition”. This initial phase's accomplishment cleared the way for post-quantum cryptography support in other applications.
NordVPN brought PQE to Windows, macOS, iOS, Android, tvOS, and Android TV in 2025. Any software that supports PQE can now use it. PQE upgrade adds quantum-resistant algorithms to NordLynx. The protocol meets the latest NIST post-quantum encryption standards. The implementation follows August 2024 US National Institute of requirements and Technology (NIST) post-quantum cryptography requirements. NordVPN uses quantum-safe mathematical methods in its VPN infrastructure to secure data long-term.
We took preventive steps because we thought quantum computer technology might threaten us. Quantum computing uses quantum physics to calculate tenfold faster than digital computers. Even in its infancy, quantum computing could outperform the fastest systems. It could break encryption systems, but this massive power could benefit space exploration and medicine by modelling molecules to repair ailments.
Due of quantum computers' processing power, cybersecurity is difficult. Quantum computers may swiftly surpass RSA encryption, which takes ordinary computers hundreds of years to master, researchers say. Such computational capacity threatens governments, corporations, and individuals.
Experts say hackers are already storing encrypted data for later deciphering, which is the biggest issue with quantum computers. Marijus Briedis suggests cybercriminals are increasing their “harvest now, decrypt later” tactics. They want to collect massive amounts of encrypted data to decrypt after quantum technology is mastered. Quantum computing is still in its infancy, but securing critical data now improves cybersecurity for consumers and organisations.
Due to this, large IT corporations, governments, and organisations like the FBI and CIA are monitoring the technology's development and seeking post-quantum encryption solutions. NordVPN implemented post-quantum cryptography to protect private data from quantum criminals. By incorporating PQE into their VPN infrastructure today and in the post-quantum era, NordVPN hopes to protect their clients' data. This launch marks a “major transition to new-generation encryption of all our applications, providing long-term security for our users” according to Briedis.
PQE is easy to enable. A toggle switch in the app's “Settings” under “Connections” enables it. The function will automatically start when the user connects via NordLynx once activated. Remember to disable PQE while using obfuscated servers or protocols like OpenVPN. It also conflicts with Meshnet and other features.
Implementing post-quantum encryption is challenging and resource-intensive. Newer security methods require larger key sizes and signatures. This may increase computational cost and VPN speed and performance, especially in high-throughput settings.
With this complete implementation, NordVPN joins Mullvad and ExpressVPN in offering full PQE integration. Reports say other providers are implemented at various stages. NordVPN is part of industry-wide efforts to future-proof digital privacy for “Q-Day” threats.
Concerning NORDVPN NordVPN, the world's most advanced VPN provider, is trusted by millions of internet users. The service offers dedicated IP, Double VPN, and Onion Over VPN servers to improve online anonymity with zero monitoring. A key feature of NordVPN is Threat Protection Pro, which scans downloads for malware and blocks hazardous websites, trackers, and adverts. NordVPN, a part of Nord Security, launched Saily, a global eSIM service. NordVPN is known for its user-friendly design and over 7,600 servers in 118 countries at the cheapest prices.
#NordVPN#postquantumencryption#postquantum#quantumencryption#postquantumcryptography#quantumcryptography#technology#technews#technologynews#news#govindhtech
0 notes
Text
Installing and Configuring OpenVPN on Windows: Easy Guide
🖥️ How to Install OpenVPN on Windows – Step-by-Step Guide! Want a secure and private internet connection? Learn how to set up OpenVPN on Windows quickly and easily. ✨ What You'll Learn: Download & install the OpenVPN client 🔽 Import configuration files correctly 📂 Connect to your VPN securely 🔐 Troubleshooting common issues 🛠️ Secure your browsing in just a few clicks! #OpenVPN #WindowsVPN #VPNSetup #CyberSecurity #OnlinePrivacy #Monovm Read the full article
0 notes
Link
#configuration#encryption#firewall#IPmasking#Linux#networking#OpenVPN#Performance#PiVPN#Privacy#RaspberryPi#remoteaccess#Security#self-hosted#Server#Setup#simplest#systemadministration#tunneling#VPN#WireGuard
0 notes
Text
The discussion in this paper will focus virtual private network which is part of telecommunication engineering. I have the interest of knowing how the virtual private network works and the existing typologies. Virtual private network is delineated as networking which applies the use of public telecommunication infrastructure like internet to provide individuals or remote offices with secure access to their individual or organizations network. The main aim of virtual private network is to help in providing organizations with similar capabilities but at lower costs. It works through the use of the shared public platform as it maintains its privacy through some specific tunneling protocols and security procedures such as the Layer Two Tunneling protocol. In effect the protocols send the data via tunnels which cannot be entered by any form of data which is not properly encrypted (Behringer & Morrow 25). The paper will dig into the understanding of Virtual private network, describe three common topologies which are being used in the VPN and compare their strengths and weakness among others. Discussion A virtual private network adopts the use of public network such as internet in the connection of sites and remote users. The main advantages associated with the use of VPN are its low cost and scalability. It combines the entire processes of tunneling, encryption, authentication, access control technologies and other services which are being used in the carriage of internet, a provider’s backbone or managed Internet protocol OR A VPN, virtual private network, is a network connection that is built on top of already existing publicly accessible telecommunication infrastructure like the internet and is used to provide access to the central organizational network to travelling users and remote offices. Yuan & Strayer (2007) state that VPNs create a virtual tunnel over the publicly available internet through the use of symmetric encryption. Common encryption and decryption keys which are used to encrypt all traffic in both directions are shared by both sides of the tunnel. In addition to the provision of alternative to the use of proxy server for remote access to campus resources, VPN also ensures secure methods to authenticate to the campus wireless network hence data security through the use of encryption technologies such as PPTP, L2TP, IPSec and SOCKS. For a smooth establishment and maintenance of a virtual private network, one is required to have appropriate networking software and hardware installed in their computers and the local network. VPN software enables a client to join a private network as if they are at a local computer within the network despite the physical distance the client might be away from the network. This software ensures security of the private network through the use of cryptographic tunneling protocols to ensure confidentiality and message integrity (Shnierder, 2008). In order to completely set up a virtual private network, certain software and hardware tools known as the VPN tools are necessary .This paper discusses in depth four VPN tools namely, OpenVPN, Cisco VPN Client, LogMeIn Hamachi and Windows built in VPN. OpenVPN OpenVPN is an open source software application for virtual private network implementation, meaning it can be downloaded and used for free. Its main role is to securely tunnel encrypted data from the server to the client or client to the server through a single port over an unsecure network. It popularity among VPN users comes from the fact that it’s a multi-platform application that support different platforms unlike most of the other VPN software applications. Read the full article
0 notes
Text
How To Set Up The GL.iNet GL-AXT1800 Router
It is a compact yet powerful travel router to offer high speed and secure internet connectivity. With the help of WiFi 6 technology the robust security feature and VPN support is an excellent choice for the travellers, remote workers and tech enthusiasts. This guide will walk you through the configuration process to get the best performance from your GL-AXT1800 router.
Unboxing And Hardware Overview
When you first get GL.iNet GL-AXT1800 router, ensures that your package include
GL-AXT1800 router
Ethernet cable
Power adaptor
User manual
GL.iNet GL-AXT1800 Setup Key Features
Provide speed up to 1200 Mbps 5GHz and 600 Mbps on 2.4GHz.
Support 1.2GHz quad core processor for the fast performance.
It built in the VPN support for wire guard and open VPN.
Adguard home to block ads and tracking scripts.
Multiple connection options such as WAN, LAN or USB 3.0 port
Manual Setup
Follow below few simple steps
Power On Your Router
Plug the power adaptor into the router and connect it with the power outlet.
After that wait for the router to boot up.
The LED light indicates that the device is now powered on and ready.
Connect To The Router
Use ethernet cable to attach the router WAN port to the modem or existing network.
Access Or Go To Admin Panel
Open the web browser and type 192.168.8.1 in the address bar. Login by entering the default credentials which are written on the router package. Consider all the setup process instructions to change the WiFi SSID, password and admin credentials for the security purposes.
Configuring Internet Connection
The GL.iNet GL-AXT1800 Router supports various internet connection methods.
Wired Connection:
If you are using a wired connection, go to the network settings and then tap on the internet. After that, verify DHCP mode is enabled.
WiFi Repeater Mode:
If you want to extend an existing WiFi network:
In the admin panel go to the repeater settings.
Now, scan for the available WiFi networks and pick up the desired one.
Enter WiFi password and save all settings.
Connect Modem Or Smartphone
Just connect the USB modem or the smartphone via the USB 3.0 port.
Select the connection mode in the admin panel and consider all the prompts.
Setup VPN For Secure Browsing
Using Wire-Guard VPN
Go to VPN and then tap the wire guard client.
Now, upload or manually enter the wire guard VPN configuration.
Enable the VPN and check connection status.
Using Open VPN
Navigate to VPN and OpenVPN client.
After that upload the open VPN configuration file which is provided by the VPN provider.
Later, connect and verify your IP address for successful connection.
With AdGuard Home Enhanced Security
It is a powerful tool for blocking ads and tracking.
To enable this, go to the navigation and click on AdGuard home. After that, enable the services and customize settings. Further, add a filter list to enhance blocking effectiveness.
Additional Features & Customization
Guest WiFi:- It creates a separate WiFi network for the visitors with restricted access.
Custom DNS Server: Uses cloudflare, google or a custom DNS provider for the faster and more protective browsing.
After the router GL iNet GL AXT1800 setup if you are facing any issue then try the below troubleshooting tips to fix the issue such as AX1800 router not working properly.
Solution Tips
Check/Identify All Cable Connections
Must verify that all the cables must be perfectly plugged in.
Look Up For Overheating
If your router gets hot then move it to the well ventilated area to cool it down.
Use Different Power Source
Try to use a different USB-C power adapter
Power Cycle Router
Press the router power button to turn it off. Now, take out the router power plug from the specified working socket. After that, wait for at least 2 minutes and put the router plug back in the socket. At the end, press router power to turn it on.
After trying the apart basic router troubleshooting tips if you fail to fix an issue. Then don’t be worried just try the below advanced troubleshooting tips steps.
Update Router Software/Firmware
Early go to the router admin panel.
After that, tap on settings and then hit on firmware.
Further, update the latest version.
Alternatively, install the firmware from the GL.iNet website and open it manually.
Reset Router From Factory Default
Early, look for the reset button on your router.
After that, take a paper pin and insert it in the router reset button.
Now, all LEDs of the GL.iNet GL-AXT1800 router are completely turned off.
Hence, your router is reset now.
Note: After resetting all default settings, do the GL.iNet GL-AXT1800 setup and installation process again.
Therefore, after the entire study or information of this article you can do the setup of your router with the modem. After router installation if you face any issue then also fix it easily by trying the apart troubleshooting tips.
0 notes
Photo

Cudy AC1200 WiFi 4G LTE Cat4 Router The Cudy LT500 4G LTE AC1200 Dual Band Wi-Fi Router uses the latest generation of 4G LTE technology to achieve speeds of up to 150 Mbps when downloading and 50 Mbps when uploading. You can also connect to games, streaming and more using Wi-Fi at a maximum speed of 867Mbps on 5GHz and 300 Mbps to 2.4 GHz. Its high-gain antennas increase the sensitivity of the router, which allows you to establish connections over longer distances. This in turn provides stronger penetration through walls. Its various modes also make it more versatile, if you are working in LAN mode, the LT500 is just a normal 4G LTE router. While working in WAN mode, the LT500 can maintain 4G and WAN connections at the same time and preferably provide the Internet via wired ports. Leaving the 4G network as a backup for peace of mind. FEATURES: Up to 150 / 50Mbps LTE speed AC1200 Wi-Fi for a smoother experience High gain antennas expand coverage PPTP/L2TP/OpenVPN/WireGuard VPN client Flexible WAN/LAN port for dual connectivity Compatible with 20+ DDNS providers DNS over Cloudflare/NextDNS/Google SPECIFICATIONS: CPU: MTK Chipset for Wi-Fi and Qualcomm Chipset for 4G DRAM/FLASH: 128MB DDR2 / 16M SPI Flash Interface: 3x RJ45 10M/100M LAN Ethernet interfaces 1 x RJ45 10M/100M WAN Ethernet interfaces 1 x Reset Button 1 x WPS Button 1 x SIM Slot (Micro) Antenna: 2 x WiFi Antennas and 2 x LTE Antennas Gain: 5dBi Wi-Fi Frequency: 2.4GHZ, 5GHz LTE Frequency Bands EU Version: LTE-FDD: B1/B3/B7/B8/B20/B28A LTE-TDD: B38/B40/B41 WCDMA: B1/B8 GSM/EDGE: B3/B8 LTE Frequency Bands US Version: LTE-FDD: B2/B4/B5/B12/B13/B14/B66/ B71 WCDMA: B2/B4/B5 Wireless Features: Wireless Standards: IEEE 802.11ac/a/n/b/g Frequency: 2.4 GHz and 5GHz Signal Rate: 867Mbps (5GHz), 300 Mbps (2.4 GHz) Compatible with 802.11ac/a/b/g/n Wi-Fi standards Transmit Power: CE:
0 notes
Text
VPN vs Proxy: What’s the Difference and Which to Choose?
In order to achieve a more secure network connection and access specific network resources, VPN (Virtual Private Network) and proxy server have become common tools. However, there are some key differences between the two, which this article will explore in detail to help users make the right choice based on their actual needs.
What is VPN?
VPN (Virtual Private Network): VPN is a technology that creates a private connection over a public network such as the Internet. It relies on an ISP (Internet Service Provider) or other NSP (Network Service Provider) to build a dedicated secure data communication network on top of a public network infrastructure.
VPN establishes an encrypted connection between a local computer and a remote server by using encryption protocols (such as OpenVPN, IPSec, etc.) and authentication mechanisms. This connection is called a VPN tunnel. In a VPN tunnel, the user’s data packets are encapsulated in new data packets and encrypted before being sent to the target server. Once the data reaches the VPN server, the server decrypts the user’s data packet and sends it to the target server. When returning the data, the VPN server encrypts the data packet again and transmits it to the user through the tunnel. In this way, the communication between the user and the target server can be protected on the public network, and third parties cannot eavesdrop or intercept the user’s data.
What is a proxy server?
A proxy server is a network entity located between the client and the server. It acts as a transit station for network information, is responsible for forwarding legitimate network information, and controls and registers forwarding. When a client (such as a browser) needs to access a network resource, it sends the request to the proxy server instead of directly to the target server.
After receiving the client’s request, the proxy server checks the request header, analyzes the request content, target address and other information, and processes the request according to the set rules. If the requested content has been cached by the proxy server and is up to date, the proxy server will return the data directly from the cache without requesting the target server again. If there is no relevant data in the cache or the data is outdated, the proxy server will initiate a request to the target server as itself. After receiving the request from the proxy server, the target server will return the corresponding data response. The proxy server will receive this response, perform further processing (such as data filtering and encryption), and then return the result to the client.
Main Differences Between VPN and Proxy Servers
1. Encryption and Security
VPN: VPNs encrypt any data you send or receive, ensuring the security and privacy of data while it is in transit. This encryption mechanism makes VPNs excellent at protecting users from ISP tracking, government surveillance, and hacker attacks.
Proxy: Proxy servers typically do not encrypt your network traffic. While some proxy servers may offer encryption, this is not a standard feature of theirs. Therefore, proxy servers are relatively less secure when dealing with sensitive information.
2. Coverage and Traffic Redirection
VPN: VPNs work at the operating system level, meaning they redirect all of your traffic, whether it’s from a browser or an app. VPNs reroute all traffic through the VPN server, ensuring that all web activity is encrypted and protected.
Proxy: Proxy servers typically work at the application level, rerouting traffic only for specific apps or browsers. This means that proxy servers can only hide traffic for one website or app at a time, not all traffic.
3. Privacy
VPN: VPNs not only hide your IP address, but also provide additional privacy protection through encryption. Most VPN providers do not log your web traffic, further enhancing privacy protection. Proxy servers: Proxy servers can hide your real IP address and provide a certain degree of privacy protection. However, since proxy servers do not encrypt traffic and may log your web activity, the degree of privacy protection is relatively low.
4. Cost and availability
VPN: VPN services are usually paid, but provide better data encryption and higher security. Paid VPN services usually provide stable connections, a variety of server node selections, and excellent customer support. Proxy servers: Some proxy servers are free, but free services often have limitations, such as slower speeds, lower security, and possible mining of user data. Paid proxy servers can provide higher quality services and may cost less than VPN services.
Which should I choose, VPN or proxy server?
If you are concerned about data security and privacy protection: VPN is a better choice because it provides encrypted data transmission and higher privacy protection.
If you need to access geo-restricted content: Both VPN and proxy servers can achieve this, but VPN generally provides more stable and secure connections.
If you are cost-sensitive: Although free proxy servers may seem more attractive, paid VPN services may be a wiser choice considering their security and speed limitations.
If you need a comprehensive network security solution: VPN provides more comprehensive network security and privacy protection features, suitable for users who need to protect sensitive information and personal privacy.
Conclusion
In summary, VPN and proxy servers have significant differences in encryption and security, coverage and traffic redirection, privacy protection, and cost and availability. Users should make the right choice based on their actual needs and budget. When choosing any network security tool, you should make sure to choose a reliable service provider and follow best practices to ensure network security and privacy protection.
1 note
·
View note
Text
White Label VPN Solutions: A Guide to Launching Your VPN Brand
In today’s digital age, privacy and security have become top priorities for businesses and individuals alike. With the rise of cybersecurity threats, Virtual Private Networks (VPNs) are in high demand, and this presents a lucrative business opportunity. Enter White Label VPN Solutions—an accessible way to launch your own VPN brand without starting from scratch. In this guide, we’ll cover everything you need to know to get started with a white label VPN service, its benefits, and steps to establish your brand in the VPN market.
What is a White Label VPN Solution?
A White Label VPN Solution is a customizable VPN product provided by a third-party vendor that you can rebrand and sell as your own. It allows companies to offer VPN services under their brand name, tailored to their audience, without investing in the complex development and infrastructure that a VPN requires. With a white label VPN service, you get the technology and backend support needed to run a successful VPN service, enabling you to focus on marketing and customer acquisition.
Why Choose White Label VPN Solutions?
For those entering the VPN market, a white label VPN solution offers several advantages:
Quick Market EntryWith a white label VPN service, you bypass the time-consuming processes of development and testing. This allows you to launch your VPN brand in a fraction of the time it would take to build a VPN from scratch.
Lower CostsBuilding a VPN infrastructure from scratch is expensive. By choosing a white label VPN, you avoid development costs and instead pay a fee to use an established service, making it a budget-friendly way to enter the market.
Focus on Branding and MarketingThe vendor handles the backend, while you focus on brand customization, marketing, and customer acquisition. This division of labor allows you to build a strong, recognizable brand in the VPN market.
Reliability and Technical Support White label VPN providers often offer reliable uptime, maintenance, and support. This ensures a high-quality user experience, giving you peace of mind that your VPN service is well-managed.
Key Features to Look for in White Label VPN Solutions
Before you select a white label VPN provider, consider the following essential features to ensure your brand offers a competitive and secure service:
Global Server CoverageA wide network of global servers ensures that users can access content from various regions, bypassing geo-restrictions and maintaining a seamless experience.
Strong Encryption and SecuritySecurity is a primary concern for VPN users. Look for white label VPN solutions that use strong encryption protocols like AES-256 and secure VPN protocols, such as OpenVPN or WireGuard, to protect user data.
Customizable User InterfaceChoose a solution that offers a customizable interface to match your brand’s look and feel. This includes app colors, logo placement, and language options.
Cross-Platform CompatibilityEnsure your VPN service works on multiple platforms, including iOS, Android, Windows, and macOS, to reach a wider audience.
ScalabilityAs your user base grows, you’ll need a solution that scales with demand. Many white label VPN providers offer scalability options, ensuring smooth performance during peak times.
Steps to Launch Your VPN Brand with White Label VPN Solutions
Launching a successful VPN brand using a white label VPN service involves several key steps. Here’s how to get started:
Research the VPN Market Understand your target audience and their needs. Are they privacy-focused users, corporate clients, or everyday consumers looking for secure internet access? This will help you choose the right white label VPN features and develop a strong marketing strategy.
Select the Right White Label VPN ProviderCompare providers based on features, pricing, server coverage, and customer support. Read reviews and request a demo to ensure the service meets your requirements.
Define Your Brand IdentityThink about what sets your VPN apart from competitors. Will it be known for speed, security, ease of use, or affordability? This brand identity should be reflected in your website, logo, and marketing materials.
Customize the VPN SolutionWork with your white label VPN provider to customize the app’s appearance and features according to your brand’s identity. Personalize the logo, color scheme, and user interface to offer a cohesive brand experience.
Develop a Pricing StrategyChoose a pricing plan that appeals to your target market. You could offer monthly, quarterly, or annual plans with competitive rates. Additionally, consider providing a free trial to attract new users and build trust.
Plan Your Marketing and Launch A solid marketing strategy is essential for brand visibility. Utilize SEO, social media, content marketing, and partnerships to reach your target audience. Focus on key phrases like “white label VPN service” and “private VPN solution” in your content to improve search engine rankings.
Deliver Excellent Customer Support Customer support can make or break a VPN brand. Many white label VPN providers offer customer support as part of their package, but it’s crucial to provide a direct line for your customers and respond promptly to inquiries.
Marketing Tips for White Label VPN Solutions
Once you’re ready to launch, here are some effective marketing strategies to increase your brand’s visibility:
Leverage Content MarketingWrite informative blog posts on topics like “Benefits of Using a VPN” and “How to Choose the Right VPN.” This builds authority and attracts organic traffic to your site.
Optimize for SEOUse targeted keywords like “white label VPN service” and “custom VPN solutions” in your content, headings, and meta descriptions. An SEO-friendly website helps you rank higher on search engine results, attracting more potential users.
Utilize Social MediaSocial platforms are a powerful way to reach a broad audience. Create engaging content about VPN benefits, data security, and privacy to raise awareness and generate interest in your brand.
Offer Referral Incentives Create a referral program where existing customers can earn discounts or rewards by referring others to your VPN service.This can assist you in rapidly and economically expanding your user base.
Final Thoughts on White Label VPN Solutions
Investing in a White Label VPN Solution is an excellent way to enter the VPN market with a ready-made, customizable product. By partnering with an established provider, you can avoid the high costs and complexities of building a VPN from scratch. Instead, focus on building a strong brand, attracting customers, and providing a seamless user experience.
0 notes
Text
Vent Post
I'm just going to vent about the ridiculous technical problems I've gotten myself into. K?
Project 1: Squid server.
So. I have an annoyying habit of goofing off during school time. Yes. I know. It's shit. However, the school district blocked all extensions, even the one I used before to block distracting sites (Leechblock NG). So, I've had to resort to ridiculous lengths. I bought a computer for 190 SEK (Like a bit under $20) and am planning to install Squid on it. What is squid, you may ask? It's a proxy server. Effectively that, instead of my chromebook talking directly to e.g. Tumblr's servers, it goes to mine, that says "Please pass this on to Tumblr". However, it can just say "NO". You can block certain requests. E.G. blocking Tumblr's servers but not the ones I need for schoolwork (Google Docs). But. Here's the issue. The home firewall is being an arse. It doesn't let the Chromebook talk to my Squid server (maybe good for security), so... jank solution #2. A VPN. So, the Squid server will also run OpenVPN. This'll make it so that my server functions like it's on the home network. Boo-yah! Then it's just a matter of enabling port forwarding on port whatever-it-is, adding the neccessary certificates to the chromebook and, Bob's your uncle.
Project 2: Gopher RSS reader.
So. What is Gopher? It's an internet standard, that lost out to http, what you're propably using to view this ridiculous post right now(If there is a Gopher Tumblr client, please tell me). But the important thing is to know that it's different to http. Now. RSS is basically... I don't have to go over that. The important thing you should know is that it connects to a website. Normally on http. However, I found an interesting blog I want the RSS for. On Gopher. And not a single Android RSS reader supports Gopher. So, I'm making my own. I installed the Android Development Kit on my Surface (A glorified iPad running Windows, so it's slooooooow) and asked ChatGPT how to make the app (I know. ChatGPT is worse than kicking puppies. But I'm NOT learning Kotlin or Java just for this) and have started. If I ever get it working, I'll post the APK here, on my blog.
I'll keep y'all posted with updates!
1 note
·
View note
Text
BLIIoT|New Version BE112 DL/T645 IEC104 Modbus to OPC UA Gateway in Energy Management
Introduction
DL/T645, IEC 104, and Modbus are widely used in various industrial settings, but they are not always compatible with each other. Converting these protocols to OPC UA allows different devices and systems using different protocols to communicate and exchange data seamlessly. This interoperability is crucial for integrating diverse components within a control system.
OPC UA provides a standardized framework for secure and reliable data exchange in industrial automation. By converting legacy protocols like DL/T645, IEC 104, and Modbus to OPC UA, organizations can adopt a unified communication standard across their operations. This standardization simplifies system integration, maintenance, and future upgrades.
OPC UA enables advanced functionalities such as browsing, alarming, historical data access, and complex data modeling, which may not be supported by legacy protocols like DL/T645, IEC 104, and Modbus. Converting to OPC UA unlocks these capabilities, allowing organizations to leverage rich data and analytics for improved decision-making and operational efficiency.
Product Description
BE112 collects data from devices or systems using DL/T645, IEC 104, and Modbus protocols. It communicates with these devices over their respective protocols to gather real-time data points, such as sensor readings, status information, or control commands.
BE112 translates the collected data from DL/T645, IEC 104, and Modbus formats into a unified format compatible with OPC UA. This conversion involves mapping the data fields, addressing schemes, and communication protocols between the different standards to ensure accurate and seamless data transfer.
BE112 acts as a bridge between the devices using legacy protocols and the OPC UA server. It establishes communication with the OPC UA server and sends the converted data in OPC UA format for storage, monitoring, or further processing by client applications or SCADA systems that support OPC UA.
Product features
Supports DL/T645, Modbus RTU, Modbus TCP, IEC104, OPC UA.
Supports connection to up to 50 devices and collection of 4,000 data points.
Supports 6 RS232/RS485 optional inputs.
It adopts embedded ARM MCU and is a product developed based on Linux OS system.
2 Ethernet ports (WAN port and LAN port).
Support WiFi.
Support OpenVPN, SNMPV1/V2.
It supports routing functions and cascade switch data collection to facilitate the collection of more industrial equipment data. The software has complete functions and covers most common application scenarios.
It integrates the humanized configuration interface that BLIIoT adheres to, as well as remote configuration, remote firmware upgrade and other functions. Users only need to make simple settings.
It adopts a fastening structure and has a power supply design with anti-reverse connection protection.
It adopts BLIIoT's patented rail buckle technology and supports standard DIN35 rail installation and wall-mounted installation.

0 notes
Text
como ter seu proprio vpn
🔒🌍✨ Ganhe 3 Meses de VPN GRÁTIS - Acesso à Internet Seguro e Privado em Todo o Mundo! Clique Aqui ✨🌍🔒
como ter seu proprio vpn
Configuração de VPN pessoal
Uma configuração de VPN pessoal é uma excelente maneira de garantir maior privacidade e segurança ao navegar na internet. Uma VPN, ou Virtual Private Network, permite que você crie uma conexão segura e criptografada com outro servidor, ocultando assim seu endereço IP real e protegendo seus dados contra possíveis invasões.
Para configurar uma VPN pessoal, você pode optar por usar um provedor de VPN confiável, que ofereça software fácil de instalar e configurar. Existem diversas opções no mercado, tanto gratuitas quanto pagas, e você pode escolher aquela que melhor atenda às suas necessidades.
Após escolher o provedor de VPN ideal para você, basta baixar e instalar o aplicativo em seu dispositivo. Em seguida, siga as instruções fornecidas pelo provedor para se conectar a um servidor remoto. Uma vez conectado, todo o tráfego de dados entre seu dispositivo e a internet será criptografado, garantindo assim sua privacidade e segurança online.
Além de proteger seus dados, uma VPN pessoal também pode ser útil para acessar conteúdos online restritos em determinadas regiões geográficas, permitindo que você assista a filmes, séries e programas de TV que não estariam disponíveis de outra forma.
Em resumo, configurar uma VPN pessoal é uma medida simples, porém eficaz, para proteger sua privacidade e segurança online. Não deixe de considerar essa opção para garantir uma navegação mais segura e livre na internet.
Serviço de VPN privado
Um serviço de VPN privado é uma ferramenta essencial para garantir a segurança e a privacidade dos seus dados ao navegar na internet. Uma VPN, ou Virtual Private Network, cria uma conexão segura e criptografada entre o seu dispositivo e a internet, garantindo que todas as suas informações permaneçam privadas e protegidas de possíveis invasões ou ataques cibernéticos.
Ao utilizar um serviço de VPN privado, você pode ocultar o seu endereço IP real e mascarar a sua localização, o que impede que terceiros rastreiem as suas atividades online e coletem os seus dados pessoais. Além disso, as VPNs oferecem a possibilidade de acessar conteúdos restritos geograficamente, como sites de streaming ou serviços de filmes, que podem não estar disponíveis no seu país.
Outra vantagem de utilizar um serviço de VPN privado é a proteção em redes Wi-Fi públicas, que são frequentemente alvos de cibercriminosos em busca de informações sensíveis. Com uma VPN, você pode se conectar com segurança a qualquer rede Wi-Fi, sem correr o risco de ter os seus dados interceptados.
Em resumo, um serviço de VPN privado é uma ferramenta fundamental para garantir a sua privacidade e segurança online. Ao investir em uma VPN de qualidade, você pode desfrutar de uma navegação tranquila e protegida, sem se preocupar com possíveis ameaças virtuais. Garanta a sua privacidade na internet e proteja os seus dados com um serviço de VPN privado.
Tutorial para montar VPN caseiro
Um VPN caseiro é uma forma segura e privada de acessar a internet. Neste tutorial, vamos te ensinar como montar o seu próprio VPN caseiro de forma simples e eficiente.
Passo 1: Escolha o servidor VPN. Você pode usar um computador antigo ou um Raspberry Pi para esse fim. Certifique-se de que o dispositivo escolhido seja capaz de suportar software de servidor VPN.
Passo 2: Escolha o software de servidor VPN. Alguns dos softwares populares incluem OpenVPN, SoftEther VPN e WireGuard. Escolha o que melhor se adequa às suas necessidades e siga as instruções de instalação do software.
Passo 3: Configure o servidor VPN. Siga as instruções do software escolhido para configurar o servidor VPN em seu dispositivo. Certifique-se de definir as configurações de segurança, como criptografia forte e autenticação de dois fatores, para proteger a conexão.
Passo 4: Configure os dispositivos clientes. Em cada dispositivo que deseja conectar ao VPN caseiro, instale um software de cliente VPN compatível e configure-o para se conectar ao servidor VPN configurado.
Com esses passos simples, você poderá montar o seu próprio VPN caseiro e desfrutar de uma conexão segura e privada sempre que acessar a internet. Lembre-se de manter o software atualizado e de revisar periodicamente as configurações de segurança para garantir a proteção dos seus dados.
Provedor VPN próprio
Um provedor VPN próprio é uma solução interessante para aqueles que desejam ter mais controle sobre sua privacidade e segurança online. Ao criar seu próprio provedor VPN, você pode garantir que seus dados estejam protegidos e que sua conexão seja segura, especialmente ao utilizar redes públicas de internet.
Uma das vantagens de ter um provedor VPN próprio é a capacidade de personalizar as configurações de acordo com suas necessidades específicas. Você pode escolher os protocolos de segurança mais adequados, definir regras de acesso e até mesmo selecionar os servidores aos quais deseja se conectar.
Além disso, ao criar seu próprio provedor VPN, você elimina a necessidade de confiar em serviços de terceiros, o que pode ser especialmente importante para aqueles que lidam com informações sensíveis ou que desejam evitar a coleta de dados por empresas de VPN comerciais.
No entanto, é importante ressaltar que criar e gerenciar um provedor VPN próprio requer conhecimento técnico avançado e investimento em infraestrutura. É essencial garantir a segurança e a confiabilidade do serviço, bem como considerar os aspectos legais relacionados ao uso de uma VPN.
Em resumo, um provedor VPN próprio pode ser uma opção interessante para aqueles que buscam mais controle sobre sua privacidade online, desde que estejam dispostos a investir tempo e recursos necessários para configurar e manter o serviço de forma adequada.
Passos para criar rede privada virtual
Uma rede privada virtual (VPN) é uma ferramenta essencial para proteger a sua privacidade e segurança online, permitindo-lhe navegar na internet de forma anónima e segura. Criar a sua própria VPN pode parecer uma tarefa complexa, mas com os passos certos pode ser alcançado facilmente.
O primeiro passo para criar uma VPN é escolher o tipo de protocolo que deseja utilizar. Existem vários protocolos disponíveis, sendo o OpenVPN um dos mais populares devido à sua segurança e velocidade. Após selecionar o protocolo, é importante escolher o servidor onde a VPN será hospedada. Pode optar por um serviço de hospedagem de terceiros ou configurar o seu próprio servidor numa máquina virtual.
O próximo passo é instalar o software VPN no servidor escolhido e configurá-lo de acordo com as suas preferências de segurança. Certifique-se de que todas as definições estão corretas e que a encriptação está ativada para garantir a segurança dos seus dados.
Por fim, é necessário configurar os dispositivos clientes para se ligarem à sua VPN. Pode fazê-lo instalando o software VPN nos dispositivos e inserindo as credenciais de acesso fornecidas durante a configuração do servidor.
Com estes passos simples, poderá criar a sua própria rede privada virtual e usufruir de uma navegação segura e anónima na internet. Lembre-se sempre de manter o software atualizado e as definições de segurança configuradas para garantir a eficácia da sua VPN.
0 notes
Text
how client vpn to use with endian
🔒🌍✨ Ganhe 3 Meses de VPN GRÁTIS - Acesso à Internet Seguro e Privado em Todo o Mundo! Clique Aqui ✨🌍🔒
how client vpn to use with endian
Configuração do cliente VPN no Endian
A configuração do cliente VPN no Endian é um processo essencial para garantir uma conexão segura e confiável entre o usuário e a rede privada. O Endian é um dispositivo de segurança que oferece recursos avançados de VPN para proteger a comunicação de dados sensíveis.
Para configurar o cliente VPN no Endian, é necessário primeiro acessar a interface de administração do dispositivo. Dentro do painel de controle, é possível encontrar as opções de configuração da VPN, incluindo a criação de perfis de usuário, definição de políticas de acesso e escolha de protocolos de criptografia.
Ao criar um perfil de usuário, é importante atribuir um nome e uma senha seguros, além de selecionar o tipo de conexão desejado, como OpenVPN ou IPsec. Em seguida, é necessário definir as políticas de acesso, especificando quais recursos da rede o usuário terá permissão para acessar.
No que diz respeito aos protocolos de criptografia, o Endian oferece várias opções, como AES e 3DES, que garantem a segurança dos dados transmitidos pela VPN. É importante escolher um protocolo forte o suficiente para proteger as informações confidenciais contra possíveis ataques cibernéticos.
Por fim, após concluir a configuração do cliente VPN no Endian, o usuário poderá estabelecer uma conexão segura com a rede privada a partir de qualquer local, garantindo a integridade e confidencialidade dos dados transmitidos. A correta configuração da VPN no Endian é essencial para manter a segurança e a privacidade das comunicações online.
Passo a passo para usar VPN no Endian
Um passo a passo simples para usar VPN no Endian pode facilitar a vida dos usuários que desejam aprimorar a segurança de suas conexões. A VPN, ou Virtual Private Network, é uma ferramenta essencial para garantir a privacidade e a proteção dos dados transmitidos pela internet. No Endian, um software de segurança de rede, a configuração da VPN pode ser feita de forma eficiente seguindo os seguintes passos:
Acesse a interface de gerenciamento do Endian digitando o IP do firewall em um navegador web.
Faça login no sistema usando suas credenciais de administrador.
Navegue até a seção de Configurações de VPN no painel de controle.
Crie um novo perfil de VPN, escolhendo o tipo de conexão mais adequado para suas necessidades (por exemplo, OpenVPN).
Configure as opções de segurança, como criptografia e autenticação, de acordo com as recomendações de segurança.
Defina as permissões de acesso, especificando quais dispositivos ou usuários terão acesso à VPN.
Salve as configurações e ative a conexão VPN.
Para se conectar à VPN no Endian, você precisará de um cliente VPN compatível. Baixe e instale o cliente em seu dispositivo.
Abra o cliente VPN, insira as informações de conexão (como endereço do servidor, nome de usuário e senha) e estabeleça a conexão.
Ao seguir esses passos simples, você poderá utilizar a VPN no Endian de forma segura e eficiente, protegendo seus dados e garantindo uma navegação mais privada na internet.
Melhores práticas para configurar cliente VPN no Endian
Ao configurar um cliente VPN no Endian, é importante seguir as melhores práticas para garantir uma conexão segura e estável. Uma VPN (Virtual Private Network) é uma ferramenta essencial para proteger a sua privacidade online e permitir o acesso seguro a redes privadas a partir de locais remotos.
Uma das primeiras etapas para configurar um cliente VPN no Endian é garantir que você tenha as informações de conexão corretas, incluindo o endereço do servidor VPN, o tipo de protocolo a ser utilizado (como OpenVPN ou IPSec) e as credenciais de login necessárias.
Além disso, é importante garantir que o seu cliente VPN esteja atualizado com as últimas correções de segurança, a fim de evitar possíveis vulnerabilidades que possam comprometer a sua conexão.
Ao configurar a conexão VPN, certifique-se de definir as configurações de segurança adequadas, como a criptografia dos dados transmitidos e a autenticação de dois fatores, quando possível, para garantir que apenas usuários autorizados consigam acessar a rede.
Por fim, teste a conexão VPN após a configuração para garantir que tudo esteja funcionando corretamente e que você consiga se conectar de forma segura e estável à rede remota.
Seguindo estas melhores práticas, você poderá configurar um cliente VPN no Endian de forma eficiente, garantindo a segurança e privacidade das suas comunicações online.
Tutorial de conexão VPN no Endian
Um Tutorial de conexão VPN no Endian é fundamental para garantir a segurança e privacidade dos dados durante a comunicação em uma rede. A VPN, ou Virtual Private Network, é uma tecnologia que permite estabelecer uma conexão segura através da internet, protegendo as informações transmitidas de possíveis invasões.
Para configurar uma conexão VPN no Endian, siga os passos abaixo:
Acesse a interface do Endian Firewall navegando pelo seu navegador de internet e insira suas credenciais de acesso.
No menu principal, localize a opção de VPN e clique em "Configurações de VPN".
Selecione o tipo de VPN desejado, como OpenVPN ou IPsec, e clique em "Adicionar novo túnel VPN".
Configure as informações requeridas, como IP do servidor VPN, chave pré-compartilhada, certificados, entre outros.
Após preencher todos os campos necessários, salve as configurações e ative a conexão VPN.
Teste a conexão VPN para garantir que está funcionando corretamente e que seus dados estão sendo transmitidos de forma segura.
É importante ressaltar que a configuração da VPN no Endian pode variar de acordo com as necessidades específicas de cada rede e sistema. Caso tenha dúvidas ou problemas durante a configuração, consulte o manual do usuário do Endian ou entre em contato com o suporte técnico para obter assistência especializada. Com uma conexão VPN devidamente configurada, você poderá desfrutar de uma comunicação segura e privada em sua rede.
Configurações avançadas de VPN no Endian
As configurações avançadas de VPN no Endian fornecem recursos poderosos para otimizar e aprimorar a segurança da rede. Com o aumento das preocupações com a privacidade e a segurança dos dados, as empresas estão cada vez mais recorrendo a soluções de VPN para proteger suas comunicações online.
O Endian é uma plataforma robusta que oferece opções avançadas de configuração de VPN para atender às necessidades individuais de segurança de cada organização. Com recursos avançados, os administradores podem configurar redes privadas virtuais com diferentes protocolos de criptografia, autenticação de usuários e políticas de acesso.
Uma das vantagens das configurações avançadas de VPN no Endian é a capacidade de estabelecer conexões seguras entre filiais ou funcionários remotos, garantindo a integridade e a confidencialidade dos dados transmitidos. Além disso, as opções avançadas de tunelamento permitem otimizar o desempenho da rede, garantindo uma experiência de conectividade rápida e estável.
Com o Endian, é possível implementar políticas de segurança personalizadas, configurar túneis de VPN de site a site e criar perfis de usuários com diferentes níveis de acesso. Isso garante uma proteção abrangente dos dados confidenciais e uma gestão eficaz das comunicações remotas.
Em resumo, as configurações avançadas de VPN no Endian são essenciais para empresas que buscam garantir a segurança e a privacidade das suas comunicações online. Com recursos personalizáveis e poderosos, o Endian se destaca como uma solução confiável e eficiente para as necessidades de VPN corporativas.
0 notes