#proxmark3
Explore tagged Tumblr posts
Note
Merry Christmas I got you:
-A trans-pride-colored paracord bracelet with a 16GB USB drive hidden in the buckle (and a tiny USBKiller drive with a little sacred chao icon laser etched onto it that you can swap it out for). (I still don't know if you're trans or not so I also got you a regular black and green paracord bracelet you can just swap the buckle onto).
-A Proxmark3 RFID card scanner/cloner kit and 5-pack of blank cards (With custom, stylized catboy icons laser etched onto them).
-A stack of four CD-R discs with different music playlists burns onto them, labeled in handwritten black marker.
-A black leather RFID-blocking wallet.
-A high-durability plastic shim card that won't show up on metal detectors (also etched with that catboy icon).
-A collector's box set of the first six volumes of "Tales From Sexy Monster Island" short story anthologies along with autographed promotional pinup posters.
amazing thank you my friend
5 notes
·
View notes
Text
Proxmark3 4.18341 Custom Firmware
http://i.securitythinkingcap.com/T4T4yD
0 notes
Video
instagram
For those not following me on Twitter: a few days ago we were able to successfully reprogram #kyber crystals to change their colors & associated sounds. As far as I can tell, we’re the first (only?) folks who have done this. As a tech-friendly designer/frontend dev who only recently finally started trying to be more hands-on with the backend, you have no idea how proud I am that I was able to install/use a CLI tool, dump the full raw data from an #RFID chip, and actually kinda understand what I was looking at. I love trying to solve a good mystery. #detectivePikachewie #galaxysedge #savisworkshop #customlightsabers #disneyland #electronics #proxmark3 (at Burbank Makerspace) https://www.instagram.com/p/BzSSkhZlo43/?igshid=1qy8qs9dahaex
#kyber#rfid#detectivepikachewie#galaxysedge#savisworkshop#customlightsabers#disneyland#electronics#proxmark3
2 notes
·
View notes
Text
RFID/NFC Research
Tools
Proxmark3
NFC Proxy
RFID Module RC522 works with Arduino and RaspberryPI
Various NFC Tag reading apps on Android
Tactics
RFID/NFC is susceptible to cloning, spoofing/emulating, and sniffing attacks.
Cloning and Emulating RFID cards with Proxmark3
NFC Proxy/Sniffing/Fuzzing
3D printing your own RFID readers (video and slides)
Contactless Credit Cards
Techniques
Emulating Amiibos with a Proxmark3
0 notes
Photo

Alistando mi #proxmark3 para empezar a jugar con #nfc #rfid con @salmg_net _/﹋\_ (҂`_´) -''Let's Hacking'' <,︻╦╤─ ҉ - - - - _/\_ . . . #pentester #vulnerabilityassessment #HackingTools #Pentest #Pentesting #VulnerabilityAssessment #EthicalHacking #InfoSec #CyberSecurity #EthicalHacker #ceh #diabetichacker #darkdevil #hacker #hacking #whitehat #greyhat #blackhat #owasp #osstmm #issaf #ptes https://www.instagram.com/p/B4kojPgAXbR/?igshid=qpmyig8xzrvl
#proxmark3#nfc#rfid#pentester#vulnerabilityassessment#hackingtools#pentest#pentesting#ethicalhacking#infosec#cybersecurity#ethicalhacker#ceh#diabetichacker#darkdevil#hacker#hacking#whitehat#greyhat#blackhat#owasp#osstmm#issaf#ptes
0 notes
Photo


Some assembly required...
1 note
·
View note
Text
Flipper Zero - tomagotchi patsan multitool for pentester
Part 1
Flipper Zero - a project of a pocket multitool based on the Raspberry Pi Zero for the IoT Pentest and wireless access control systems. This is also the tamagotchi where the cyber dolphin lives. He will be able to: Work in the 433 MHz band - for the study of radio controls, sensors, electronic locks and relays. NFC - read / write and emulate ISO-14443 cards. 125 kHz RFID - read / write and emulate low-frequency cards. iButton keys - read / write and emulate contact keys operating on the 1-Wire protocol. Wi-Fi - to check the security of wireless networks. The adapter supports packet injection and monitor mode. Bluetooth - supported bluez package for Linux Bad USB mode - can be connected as a USB-slave and emulate a keyboard, ethernet adapter and other devices for code injection or network pentest. Tamagotchi! - The low power microcontroller works when the main system is turned off. I am excited to present my most ambitious project, the idea of which I have hatched for many years from one technology news site. This is an attempt to combine all the often necessary tools for a physical pentest into one device, while adding personality to it so that it is nice to shit. At the moment, the project is at the stage of R&D and functional approval, and I invite everyone to participate in the discussion of functions or even take part in the development. Under the cut, a detailed description of the project. Why is this needed? I love to explore everything around and constantly carry around with me various tools for this. I have in my backpack: WiFi adapter, NFC reader, SDR, Proxmark3, HydraNFC, Raspberry Pi Zero (because of this there are problems at the airport). All these devices are not so easy to use on the run, when you have a cup of coffee in one hand or you ride a bicycle. You need to sit down, decompose, get out the compuctor - this is not always convenient. I dreamed about a device that would implement typical attack scenarios, was always on alert and at the same time was not a pack of falling apart boards wound with electrical tape. Raspberry Pi Zero W with battery-shield UPS-Lite v1.0 as a stand-alone flooder for sending pictures to Apple devices via AirDrop Recently, after the open implementation of the AirDrop owlink.org protocol was published and a study from HexWay guys about Apple-Bleee iOS vulnerabilities, I began to have fun in a new way: meeting people on the subway, sending them pictures through AirDrop and collecting their numbers phones. Then I wanted to automate this process and made an autonomous dick-peak car from the Raspberry Pi Zero W and batteries. This topic deserves a separate article, which I can’t finish writing. Everything would be fine, but this device was extremely inconvenient to carry, it could not be put in your pocket, because sharp drops of solder tore the fabric of the pants. I tried to print the case on a 3d printer, but I did not like the result. Special thanks to Ana koteeq Prosvetova, the host of the Telegram channel @theyforcedme, who, at my request, wrote the Telegram bot @AirTrollBot, which generates pictures with text, telegram and the correct aspect ratio so that they are fully displayed on the preview when sending via Airdrop. You can quickly generate a picture suitable for the situation, it looks something like this. Pwnagotchi assembly with e-ink screen and battery shield Then I saw the amazing pwnagotchi project. It's like tamagotchi, only as a meal he eats WPA handshakes and PMKID from Wi-Fi networks, which can then be brute on GPU farms. I liked this project so much that for several days I walked with my pwnagotchi through the streets and watched how he enjoyed the new booty. But he had all the same problems: you can’t put it in your pocket normally, there are no controls, so any user input is possible only from a phone or computer. And then I finally realized how I see the perfect multitool, which I missed. I tweeted about this and my friends liked the industrial designers who make serious electronic stuff. They proposed to make a full-fledged device, instead of a tricked DIY-craft. With real factory production and quality fit parts. We began to search for a design concept. Clickable. The first sketches of the design of Flipper Zero The case and design took a lot of time, because I was tired that all hacker devices look like a bunch of PCBs wound with electrical tape and it is impossible to use them normally. The task was to come up with the most convenient and compact body and device that would be easy to use autonomously without a computer or phone, and this is what came of it. The following describes the current non-final concept of the device. Next part: What is Flipper Zero?
2 notes
·
View notes
Text
RFID Penetration

My proxmark3 rfid tool has arrived today! I install the program and played around with it and found out that I don’t really know what kinds of rfid tech my unsw student card uses? Sometimes it really is the least expected part slowing us down haha.
Update: I found the type of card unsw student card belongs to. It is an iso14443a card, which is a type of near field communication card. The card uses some encryption to protect against cloning some blocks of the card.
2 notes
·
View notes
Text
Awesome Project Proposal v1
So I’ve decided that my proposal for the Something Awesome Project would be to working with the Proxmark 3 to clone RFID/NFC cards. https://github.com/Proxmark/proxmark3
Cloning RFID and NFC cards is an example of breaching physical security where someone’s access card can be stolen without the physical item being taken. If there is a lack of card identification security on the card, devices such as Proxmark 3 can be able to access the data inside the card, clone it into the device itself or another blank card and thus will have the same permissions as the original card.
Cards such as Opal cards will be harder to breach as inside the card, there exists a physical chips which act as a card identification security system and thus prevent opal cards from being cloned. However, UNSW cards could potentially be cloned as it is a Mifare card and hence I would want to take this opportunity to explore whether or not the card can be cloned and manually have its permissions changed such that I can access different buildings throughout the University. Currently, my card can only access the Computer Science building so I will be experimenting on my card and seeing whether or not I can clone it to another card such that I can access other buildings such as the Electrical Engineering rooms or the ASB building.
I was inspired to do this project as last year, a Proxmark 3 device was used to breach millions of hotel rooms. https://www.wired.com/story/one-minute-attack-let-hackers-spoof-hotel-master-keys/
It also had the potential of cloning prepaid cards although I am unsure if the same device was used.
While it is harder to create a master card that combines various cloned card permissions or clone an Opal card or credit card, it still serves a very practical usage especially in social engineering situations used by hackers to get inside buildings.
As I have never worked with a Proxmark 3, I am unsure whether or not I will be able to even clone the UNSW card or if I will be able to successfully set up the Proxmark 3 device (In case of bricking or hardware malfunction) and hence I have created my grading system:As per requested I have changed the criteria for the project.
Edit 1:
I will be attempting to provide a weekly blog post describing my experiences with the Proxmark 3 and research about various different types of RFID cards, it’s application in real life and if possible, a guide on how to clone it and a case study every week about the RFID card.
Fail- No attempt
Pass - Minimal attempt (a blog post about setting up the proxmark 3 device and an attempted blogs describing different types of RFID card)
Credit - Consistent blogs every week providing a blog about the research of RFID card and it’s application in real life.
Distinction - Consistent blogs every week providing an indepth analysis and explanation of RFID cards, it’s application in real life and a case study or potential case study for such use of a card. Some tutorials of how to clone the cards.
High Distinction- Same as distinction except analysis and explanation are of high quality and an attempt is made every week to clone each type of card. If they are not possible, a reason is provided why and an alternative solution is provided to clone the card.
1 note
·
View note
Text
Tumblr's 4th Annual Security Capture the Flag
We've hosted an internal Security Capture the Flag (CTF) event for four years in a row now, with each year getting better than the last!
The event
Previously, we were only open to Tumblr employees. This year we decided to extend an invite out to the other teams housed under our parent company, Oath.
All participants had a three hour window to hack, a buffet of tacos, beer, and wine to dive into, and a stack of prizes for the top four players (see Prizes below for details)!
Challenges were available Jeopardy-style, broken down by category. We had eight fun categories to select from:
Auth Bypass (authn | authz)
Cross Site Request Forgery (CSRF)
Cross Site Scripting (XSS)
Crypto
Forensics
Reverse Engineering
SQL Injection (SQLi)
XML Injection (+ XXE)
We also sprinkled a few "inside joke" Easter eggs around the system that awarded bonus points to anyone that discovered them! For example, if they attempted to find a hole in the CTF system itself and navigated to /wp-admin, we'd give them a flag on a prank WordPress page; or perhaps testing to find XSS with a <marquee> tag — only the greatest of all XSS tags!
While the Security Team walked around and helped out, we also setup a mini lockpick village just because.
Solving challenges & scoring points
To complete a challenge, the player had to achieve the goal within one of the listed categories.
In XSS challenges, the player would need to cause the browser to create an alert dialog (e.g. alert()).
Conversely, in SQL Injection challenges the player would need to read the flag column from the flags table in that challenge's database.
When the player successfully solved the challenge they were awarded with a flag, each in the format ofTumblr{s0mE_cHalL3nGe_j0kE-abcdef012}. That last piece is a unique hash for the user, per challenge, so that they couldn't directly share their flag. They can help others — even provide the solution — but they can't simply give away their flag.
Each challenge, when solved, is worth a certain number of points based on the challenge's difficulty and whether or not the player used the challenge's hints.
There were 3800 points available, though no player was able to break 1000!
At the end, we locked the leaderboard and announced the winners.
Prizes
We awarded the top four players based on their ranking on the leaderboard. First place got first dibs from the list. Second place gets to select theirs from the remaining lot, and so on.
Up for grabs this year:
Hak5 Elite Field Kit
Proxmark3 RDV2 Kit
Samsung Chromebook Plus
Lockpick set and a "how to" manual
Challenge snapshot
Throughout the eight categories we had a total of 46 challenges. We wanted to have a wide range of challenges that welcomed players of all backgrounds and experience levels.
The goal for XSS challenges was to get an alert dialog to appear. The player is presented with a vulnerable web page and they needed to determine where the vulnerability is and how to exploit it. Example:
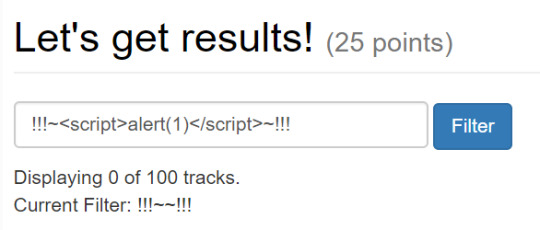
These challenge levels ranged everywhere between simple non-sanitized output to DOM reflection to CSP bypasses.
One fo the more unique challenges to develop was SQL Injection. These offered players the ability to put their SQL skills to the test with a variety of basic input injection, blind injection, and filter bypassing challenges.
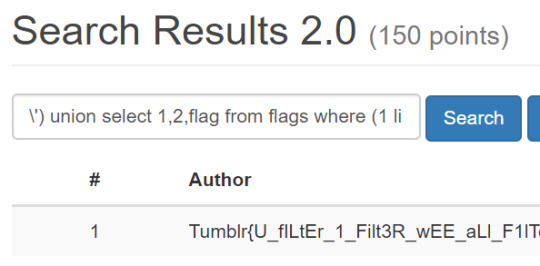
In at least one of the SQLi challenges, players had to inject into an INSERT statement. When creating challenges like this, special care had to be taken to give players the full capabilities of MySQL but also prevent them from revealing the flag to other players — it's a tricky thing making vulnerabilities secure!
The infrastructure
A frequent question I receive when I talk about deving on the CTF is "are you using CTFd?" Short answer? Nope! A slightly less short answer is that CTFd wasn't out when we started this =P.
The framework we're using is called "Security Training Grounds" and it's a custom-written project using PHP, PhantomJS, and MySQL (with HTML + JavaScript too, of course), running in Amazon Web Services.
An advantage of writing this in-house was that it gave us the ability to create a dynamic and robust system that has endless capabilities.
PHP + MySQL
The website was created from scratch, written in PHP with a little bit of jQuery + Bootstrap on the frontend and MySQL as the database.
The big thing here are the challenges themselves. Each challenge is hosted on its own subdomain. This enables us to provide live and interactive challenges like XSS or SQLi while still providing support static challenge types like Crypto or Reverse Engineering.
We accomplished this by allowing dynamic hostnames on the webserver and defining a subdomain hostname for each challenge that's stored in MySQL. When a web request comes in, the app checks whether it's a subdomain or not. If so, it hits the database to determine what to display.
For most challenges, we were able to handle all of the dynamic pieces directly in PHP. For some, such as the C or Java reverse engineering challenges, we did need to shell out to gcc or javac to build the custom binaries for each user.
PhantomJS
A difficulty for XSS and CSRF challenges is determining whether or not the participant successfully exploited the system. Surely we don't want to manually confirm for each flag, and attempting to pattern-match on their input would be crazy.
Our solution: execute what the player submits!
This is my own little baby, a piece of the system I'm so excited by. See, what better way to test XSS than to actually test XSS. As mentioned in the "Challenge snapshot" section above, when a player is working on a XSS challenge, they are given a website that has a XSS vulnerability. Their goal is to make an alert dialog appear. This is key and the requirement of the XSS framework itself.
On the client, we use this fancy little snippet:
var ctf_alert = alert; alert = function(msg) { ctf_phantomjs_alert_test(document.location, msg); };
This overrides the window's actual alert() function and lets us put some processing logic in the middle. The logic is to take a snapshot of the current page - the URL, query string, POST parameters, the cookies and then pass the full snapshot to a backend PhantomJS service (via a PHP proxy, to help prevent tampering).
The PhantomJS service replicates that entire request and loads the target web page. If the page invokes an alert() call, which we catch via PhantomJS's onAlert, then we return with a "success" and the PHP proxy will return the user's flag. Our alert() overriding logic will then replace whatever message the user attempted to display and display their flag instead. Fancy af.
CSRF has a similar setup, except the player needs to submit their full CSRF payload:
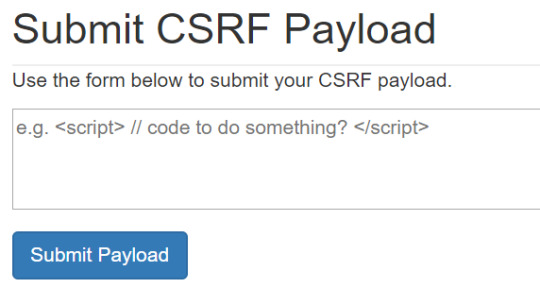
After submitting the payload to the PHP proxy, we pass the payload to PhantomJS. This executes the payload in the context of an empty web page. If the PhantomJS worker successfully falls victim to the targeted action, the PHP proxy will return a flag to the user!
Open source
The framework code, as-is, is still relatively hacky and written with internal dependencies. We do believe in OSS though! We expect a near-future initiative to rewrite portions of it so we can release it for others to use for their CTF events, too.
Wanna Play?
Quick, come apply so you can participate in the next one: https://www.tumblr.com/jobs
#tumblr#tumblrhq#security#capture the flag#ctf#xss#csrf#sqli#hacking#tumblr event#tumblr staff#computer security#cybersecurity#cyber#programming#computers#tacos
115 notes
·
View notes
Text
[Media] Proxmark3
Proxmark3 The Proxmark3 is the swiss-army tool of RFID, allowing for interactions with the vast majority of RFID tags on a global scale. Originally built by Jonathan Westhues, the device is now the goto tool for RFID Analysis for the enthusiast. Iceman repository is considered to be the pinnacle of features and functionality, enabling a huge range of extremely useful and convenient commands and LUA scripts to automate chip identification, penetration testing, and programming. Buy online: RDV2 🛒 https://amzn.to/3jG7kUr RDV3 Easy 🛒 https://amzn.to/40CtlUy RDV4 BlueShark 🛒 https://t.me/PentestingShop/95 RDV4.01 KIT 🛒 https://ali.ski/6_p9Xk #rfid #nfc

0 notes
Text
Rndis driver windows 10 64 bit download

Usb Ethernet Rndis Gadget Driver Windows 10 - downafiles.
Rndis driver windows 10 64 bit download - Steven Rodgers's Ownd.
Raspberry Pi Zero W Headless setup – Windows 10 RNDIS Driver.
Rndis driver windows xp 64 bit Download.
10 Windows Proxmark3.
Drivers - Microsoft Download Centre.
4G MIFI USB Ethernet/RNDIS Driver Download - PC Matic.
Technet forums - Windows 10 Hardware.
10 Proxmark3 Windows.
Download rndis driver pack for windows 10.
Docker Hub.
USB RNDIS driver can't work with Windows 10 (10.0.18363.
Dell ControlVault Driver | Driver Details | Dell US.
Usb Ethernet Rndis Gadget Driver Windows 10 - downafiles.
Microsoft provides an NDIS miniport driver, R, which implements the Remote NDIS message set and communicates with generic bus transport drivers, which in turn communicate with the appropriate bus driver. This NDIS miniport driver is implemented and maintained by Microsoft and is distributed as part of all supported Windows versions.. This download is licensed as freeware for the Windows (32-bit and 64-bit) operating system on a laptop or desktop PC from drivers without restrictions. Realtek Ethernet Windows Driver 10.39.20 is available to all software users as a free download for Windows. Linux USB Ethernet/RNDIS drivers implementing and most Wifi connections. Linux Usb.
Rndis driver windows 10 64 bit download - Steven Rodgers's Ownd.
Search for jobs related to Usb rndis driver windows 10 download or hire on the world's largest freelancing marketplace with 20m+ jobs. It's free to sign up and bid on jobs. Nov 29, 2018 · (The other protocol types aren't supported in current versions of Windows.) I believe that this INF ships inbox for Windows Vista and later, so the customer doesn't need a driver download on any supported version of Windows client. However, prior to Windows 7, I think the inbox INF would still get you the RNDIS 5.x implementation. 1. Extract the file to a folder of your choice 2. Go to Device Manager (right click on My Computer, choose Manage and then find Device Manager in the left panel), or right click on Start Menu.
Raspberry Pi Zero W Headless setup – Windows 10 RNDIS Driver.
Oct 15, 2020 · RNDIS drivers are needed on the windows machine to make this work. One of their NUCs has the" build 2004" windows 10 update on it, another has not yet been updated. The updated machine seems to be missing drivers for the "Remote NDIS compatible device". On the non-updated machine we can choose this driver from a list (of drivers available on. These boards depend on RNDIS driver to get into concole. So if I connect a board for the first time my Win7 Laptop properly detects it as a RNDIS ethernet adapter or device. But when I plug in the boards second time it just comes up as a unknown device in USB section of device manager. Thank you for your reply. Did you check drivers for windows 10 20h2 for HP 15s- du1014tu. Please just check the drivers for that model. Because HP didn't complete the full drivers list for windows 10 20h2. What I'm mean is earlier windows 10 2004, 1909 , 1903 and 1809 hp display separate drivers but now 20h2 they didn't given full driver list.
Rndis driver windows xp 64 bit Download.
Download 1. Click Download File, to download the file. 2. When the File Download window is displayed, click Save or Save this program to disk and click OK. The Save In: window is displayed. 3. From the Save In: field, click the down arrow then click to select Desktop and click Save. The file downloads to your desktop. 4. Classification. Last Updated. Version. Size. Download. Vernier Software & Technology - Other hardware - LabQuest2 USB Ethernet/RNDIS Gadget. Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8.1 and later drivers , Windows 10 Creators Update and Later Servicing Drivers. Drivers (Other Hardware) 2/11/2013.
10 Windows Proxmark3.
Select RNDIS Right-click and select Install. Click Open. After the operation is completed successfully, retry the USB connection between FX7500 or FX9600 and the Windows 10 computer. Alternatively: From your PC, navigate to Device Manager > Network Adapters > Look for unknown or problematic drivers related to USB Ethernet.
Drivers - Microsoft Download Centre.
Rndis driver windows 10 64 bit download.... Latest Generic RNDIS Driver download for Windows 7, 8, Vista, XP Our new article section — find out all you need to know with these easy to understand and helpful articles When everything else falls flat check the driver installation program. Download Marvell drivers by Platform or Part Number for Marvell QLogic Fibre Channel HBA and Marvell FastLinQ Ethernet adapters and controllers.
4G MIFI USB Ethernet/RNDIS Driver Download - PC Matic.
Mar 23, 2013 · Devices using a USB connection for downloading and debugging of OS image from Platform Builder use this driver to emulate a network connection. RNDIS driver is required for this purpose. RNDIS driver is a part of the Windows 7 operating system, but the OS fails to detect it automatically.
Technet forums - Windows 10 Hardware.
Windows has been shipping with the RNDIS driver bundled in for quite some time now, so it's basically a matter of a simple declaration. However, starting with Vista (EDIT: probably Windows 8 as mentioned below), Windows has been enforcing a mandatory signing requirement for 64-bit drivers. Search: Proxmark3 Windows 10. The proxmark3 is a powerful general purpose RFID tool, the size of a deck of cards, designed to snoop, listen and emulate everything from Low Frequency (125kHz) to High Frequency (13 GitHub - Wh201906/Proxmark3GUI: A GUI For Proxmark3 Client Github We're always on the prowl for novel environments to run Kali on, and with the introduction of the Windows Subsystem.
10 Proxmark3 Windows.
Install the driver using the setup exe. Once this is completely installed and happy, then open up MotoTRBO CPS. Once loaded, reconnect cable and power up radio. At this point, it should now show as a network device MOTOTRBO Radio in Device Manager and prompt for network discovery permission (Network 5, 6, 30, etc). Alesis Firewire Drivers Download For Windows 10, 8.1, 7, Vista, XP Linux USB Ethernet/RNDIS Gadget Driver Download For Windows 10 Toshiba Wireless LAN Mini PCI Card Driver Download For Windows 10 Download DELL CERC SATA 1.5/6ch RAID Controller Driver AGFEO AS 181 Plus EIB Driver Download For Windows 10. Download rndis driver pack for windows 10 - Driver Download for your Windows System from a verified website. Fast and Secure Driver Download.
Download rndis driver pack for windows 10.
Download ACER USB Ethernet/RNDIS Driver 1.1129.0.0 64-bit (Mobile Phones)... or right click on Start Menu for Windows 10 and select Device Manager... 7. Browse to the folder where you extracted the driver and click Ok..
Docker Hub.
Jul 10, 2014 · HarriePateman. Posts 3,904 Windows 7 Ultimate 64-bit. 10 Jul 2014 #2. Here we are, they also have previous version's listed incase you run into trouble. RNDIS Drivers Download for Windows 7, 8, XP, Vista. How to install?.
USB RNDIS driver can't work with Windows 10 (10.0.18363.
Microsoft Rewards · Free downloads & security · Education · Virtual... to use an USB Remote Network Driver Interface Specification (RNDIS) device... All. Apr 29, 2022 · Attach the USB gaget to the device. Wait some time for Windows to detect/install drivers- 5sec seems plenty as it happens, some experimentation required here. Detach the USB gadget. Link the rest of your functions- Mass Storage, Serial ACM, etc ( So far only tested with these ) Set bDeviceClass to 0x00. HoRNDIS (pronounce: "horrendous") is a driver for Mac OS X that allows you to use your Android phone's native USB tethering mode to get Internet access. It is known to work with Mac OS X versions.
Dell ControlVault Driver | Driver Details | Dell US.
Dec 14, 2021 · To use the Remote NDIS driver with a USB device, an IHV must provide an INF file according to one of the following templates: RNDIS INF template for NDIS 5.1 (Windows XP and later) RNDIS INF template for NDIS 6.0 (Windows 7 and later) RNDIS INF template for NDIS 5.1 (Windows XP and later). Anthony Bradford on Windows 7 Rndis Driver 64 Bit Download. windows rndis driver, windows rndis driver download, windows rndis driver windows 10, windows rndis driver for android tethering, windows rndis driver location, rndis driver for windows xp, rndis driver windows 7, usb rndis driver windows 10 download, usb ethernet/rndis gadget driver.
See also:
Windows 10 Hangs On Shutdown Black Screen
Download Any Software Full Version Free
Pokemon Black And White 2 Randomizer Download

1 note
·
View note
Text
Proxmark3 4.18218 Custom Firmware
http://i.securitythinkingcap.com/T30pYW
0 notes
Photo

I had a hunch that the #RFID #kyber crystals were using Manchester encoding, something that my usual #Arduino readers can’t pick up. Ordered a #proxmark3 and making new progress again. #iHaveNoIdeaWhatImDoing #poking #savisworkshop #lightsabers #galaxysedge #disney #customscraps #ubuntu (at Burbank Makerspace) https://www.instagram.com/p/BzJIbXWHJdc/?igshid=zlv7sk9va59j
#rfid#kyber#arduino#proxmark3#ihavenoideawhatimdoing#poking#savisworkshop#lightsabers#galaxysedge#disney#customscraps#ubuntu
0 notes
Link
Feature: It is only used for learning RFID NFC communication and testing the technical security of RFID, as a basic learning tool for RFID personnel. Use for illegal purposes is ...
0 notes
