#repair sql server
Explore tagged Tumblr posts
Text
Handling Severity 24 Errors in SQL Server 2022: A Guide with Practical Solutions
Diving into the nitty-gritty of SQL Server, stumbling upon an error can send shivers down your spine, especially when it’s tagged with a severity level that screams urgency. Severity 24 errors are the kind of trouble no one wants to find themselves in, signaling a media hiccup that could spell disaster for your data. This piece aims to peel back the layers of Severity 24 errors, shedding light on…
View On WordPress
#Severity 24 error SQL Server#SQL Server data corruption repair#SQL Server error fix#SQL Server hardware failure#T-SQL Code Examples
0 notes
Text
What Are the Key Roles in IT Infrastructure Management?
In the modern business age of the digital world, IT Infrastructure Management is what keeps businesses running well. The task of IT infrastructure management entails efforts made in diverse areas, including the maintenance of network performance and protection of the data security. But what are exactly the major roles that make this ecosystem to be efficient?
What are the most central positions and responsibilities that propel up a reliable, safe and scalable IT infrastructure? Let us go over them at a time.

1. IT Infrastructure Manager
The head of the ladder is IT Infrastructure Manager. Such an individual is involved in planning, designing and executing the whole IT infrastructure of an organization. They make sure that every hardware, software, network as well as cloud-based service are in line with business objectives.
They have day to day tasks of budgeting IT resources, vendor selection, team management, decisions on upgrade or change of systems among others. They also liaise with the top level management to ensure that the roadmap of the infrastructure matches the growth strategies of the business.
2. Network Administrator
The Network Administrator has the duty to maintain the network systems in the company. These are local area networks (LAN), wide area networks (WAN), firewalls, routers and switches. It is their task to maintain continuous connectivity and solve any problems connected with network performance.
They can be found in the background, doing software update and vulnerability patching and management, and uptime. Businesses would be experiencing constant blackouts and jeopardized security without network administrators.
3. System Administrator
System Administrators are often mixed up with the network administrators, but they take more attention to the machines, operating systems and servers. They administer, modify, and guarantee stable performance of the computer systems particularly the multi-user computers such as servers.
General system admins are involved in a user setup, maintenance of accesses, backup, and system status. They also do software upgrades and repair hardware.
4. Database Administrator (DBA)
Most businesses rely on data in the world today. Database Administrator makes sure that vital information is stored, retrieved, and secured in a streamlined way. They keep up database platforms such as Oracle, SQL Server or MySQL, according to the requirements of the organization.
They clean up performances, configure backup and recovery procedures, apply data access control, and observe storage. They also collaborate with security departments in ensuring they guard information that may be accessed or lost without authorization.
5. Cloud Infrastructure Engineer
As other enterprises increasingly migrate to the cloud, the importance of a Cloud Infrastructure Engineer has gotten significant adoption. Such experts control systems operating in the cloud: AWS, Azure or Google Cloud.
They are to implement virtual servers, allow cloud security, cloud cost optimization, and deployment automation. They make sure that the organization takes advantage of the use of cloud technology in an effective way that neither performance nor security is affected.
6. IT Security Specialist
Cybersecurity is not an option anymore. IT Security Specialist is specialized in ensuring the safety of the infrastructure against threats, breach and vulnerability. They would watch networks and look at certain abnormal activities, use firewalls, and encrypt data, and they would make security audits frequently.
They also teach the other members of the team about good practices and adherence to regulations such as GDPR, HIPAA, etc.
7. Help Desk and Support Teams
The IT Support and Help Desk Teams are the ones who are frequently ignored, but at the same time, his workforce has to be part of the management of an infrastructure. The employees contact them when there are technical problems.
Such specialists are involved in password recovery, installation of software, and assistance. Proper support team eases productivity as issues are solved within the shortest time possible.
Conclusion
IT Infrastructure Management relies on all the diverse jobs dedicated to keep the system stable, performing well, and secure. All the job titles, be they network administrator, system admin, or cloud engineer are essential to guarantee a well-functioning technology foundation of an enterprise. The right team in the right place is not only important, but also necessary as the organizations keep on expanding and changing. Knowledge of these top functions will help businesses to organize their IT departments, prevent their outages, as well as being ready to meet any technological needs in future.
1 note
·
View note
Text
SQL Database Recovery – Fix Corrupt MDF/NDF Files Easily
Repair corrupt SQL Server databases effortlessly. Supports all versions of SQL Server with advanced recovery of tables, triggers, keys & more.
0 notes
Text
AWS Aurora vs RDS: An In-Depth Comparison

AWS Aurora vs. RDS
Amazon Web Services (AWS) offers a range of database solutions, among which Amazon Aurora and Amazon Relational Database Service (RDS) are prominent choices for relational database management. While both services cater to similar needs, they have distinct features, performance characteristics, and use cases. This comparison will help you understand the differences and make an informed decision based on your specific requirements.
What is Amazon RDS?
Amazon RDS is a managed database service that supports several database engines, including MySQL, PostgreSQL, MariaDB, Oracle, and Microsoft SQL Server. RDS simplifies the process of setting up, operating, and scaling a relational database in the cloud by automating tasks such as hardware provisioning, database setup, patching, and backups.
What is Amazon Aurora?
Amazon Aurora is a MySQL and PostgreSQL-compatible relational database built for the cloud, combining the performance and availability of high-end commercial databases with the simplicity and cost-effectiveness of open-source databases. Aurora is designed to deliver high performance and reliability, with some advanced features that set it apart from standard RDS offerings.
Performance
Amazon RDS: Performance depends on the selected database engine and instance type. It provides good performance for typical workloads but may require manual tuning and optimization.
Amazon Aurora: Designed for high performance, Aurora can deliver up to five times the throughput of standard MySQL and up to three times the throughput of standard PostgreSQL databases. It achieves this through distributed, fault-tolerant, and self-healing storage that is decoupled from compute resources.
Scalability
Amazon RDS: Supports vertical scaling by upgrading the instance size and horizontal scaling through read replicas. However, the scaling process may involve downtime and requires careful planning.
Amazon Aurora: Offers seamless scalability with up to 15 low-latency read replicas, and it can automatically adjust the storage capacity without affecting database performance. Aurora’s architecture allows it to scale out and handle increased workloads more efficiently.
Availability and Durability
Amazon RDS: Provides high availability through Multi-AZ deployments, where a standby replica is maintained in a different Availability Zone. In case of a primary instance failure, RDS automatically performs a failover to the standby replica.
Amazon Aurora: Enhances availability with six-way replication across three Availability Zones and automated failover mechanisms. Aurora’s storage is designed to be self-healing, with continuous backups to Amazon S3 and automatic repair of corrupted data blocks.
Cost
Amazon RDS: Generally more cost-effective for smaller, less demanding workloads. Pricing depends on the chosen database engine, instance type, and storage requirements.
Amazon Aurora: Slightly more expensive than RDS due to its advanced features and higher performance capabilities. However, it can be more cost-efficient for large-scale, high-traffic applications due to its performance and scaling advantages.
Maintenance and Management
Amazon RDS: Offers automated backups, patching, and minor version upgrades. Users can manage various configuration settings and maintenance windows, but they must handle some aspects of database optimization.
Amazon Aurora: Simplifies maintenance with continuous backups, automated patching, and seamless version upgrades. Aurora also provides advanced monitoring and diagnostics through Amazon CloudWatch and Performance Insights.
Use Cases
Amazon RDS: Suitable for a wide range of applications, including small to medium-sized web applications, development and testing environments, and enterprise applications that do not require extreme performance or scalability.
Amazon Aurora: Ideal for mission-critical applications that demand high performance, scalability, and availability, such as e-commerce platforms, financial systems, and large-scale enterprise applications. Aurora is also a good choice for organizations looking to migrate from commercial databases to a more cost-effective cloud-native solution.
Conclusion
Amazon Aurora vs Amazon RDS both offer robust, managed database solutions in the AWS ecosystem. RDS provides flexibility with multiple database engines and is well-suited for typical workloads and smaller applications. Aurora, on the other hand, excels in performance, scalability, and availability, making it the preferred choice for demanding and large-scale applications. Choosing between RDS and Aurora depends on your specific needs, performance requirements, and budget considerations.
0 notes
Text
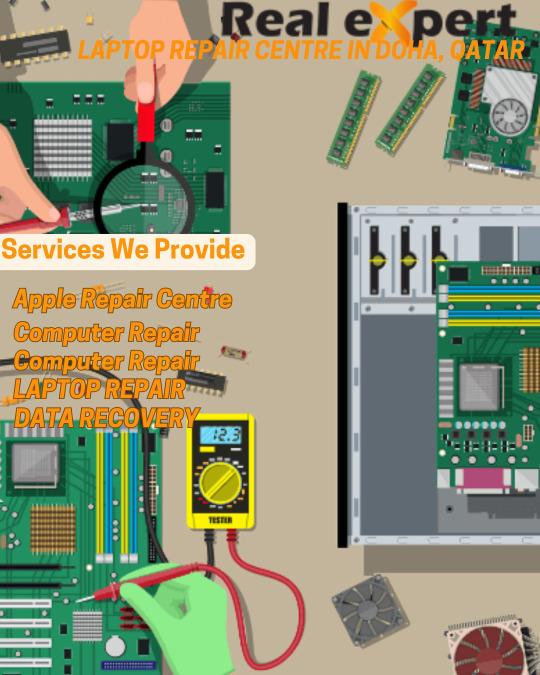
Real Expert Services
Real expert services is a full-service center for all laptop, mobile phone, iPhone, iPad, and MacBook repair needs. We offer fast, reliable repair services for all types of laptops, computers, and mobile devices. you will find the best prices on laptop repairs. We specialise in laptop repairs, including broken screens, motherboards, and hard drives. We also specialize in Mobile phone repair, including i phone repair, i pad repair, and MacBook repair.. If you are looking for a reliable, professional computer repair shop in Qatar, look no further than the Laptop Service Center in Qatar. Our experienced technicians are always happy to help, and our prices are competitive…
“Why Real Expert”
Real Expert Service Qatar established in 1988 is one of the renowned laptop service centre in doha. We are the leading laptop repair centre Doha, computer repair shop Doha and mobile phone service centre in Qatar. We are equipped with all modern technology for laptop repair, computer repair and mobile phone repair.The consistent track record has grown up to be one of the leading multibrand laptop repair centre Doha and mobile phone service center in doha, Qatar.Real Expert Service Centre is a one stop servicing shop where you got a wide collection of accessories and peripherals for your gadgets at the best price, which are 100% genuine and warranted.
LAPTOP REPAIR
Real Expert Service Centre Laptop service centre Qatar is one of the leading laptop service centres in Doha, Qatar. We are having several years of experience in repairing and servicing a wide variety of laptops. Our repairing service is the best in the industry. Our services are customer-oriented and thus we are one of the widely accepted laptop service centres in Doha.Real Expert Service Centre Laptop service center Doha is furnished with all necessary technical requirements and modern facilities to satisfy the repairing needs of customers. From Real Expert Laptop repair center Qatar, you can get the best repairing services for all brands and models of laptops. Whatever be the problems with your devices, the expert team of technicians will repair the devices in less than no time. We have the solution for all the problems with your laptops. At Real Expert Laptop repair center Doha, we have a team of service engineers who are very-well trained in repairing all brands of laptops as soon as possible.We have the best possible solutions for your Every laptop problems and that is why Real expert is the leading acer service center doha. For us, ‘The customer is the king’ and we do our services always according to the satisfaction of our customers. This customer-centred service has made us famous as one of the leading acer repair centres in Qatar.
DATA RECOVERY
Real Expert Centre, we also offer advanced data recovery services such as logical and physical damage recovery, forensic data recovery, and recovery of encrypted data. Our team is prepared to handle any data loss situation, no matter how complex or severe.Our team has the knowledge and experience needed to recover your data with minimal disruption to your business.
Provide Differernt Type Of Data recovery Service
Mac Data Recovery, External Storage Data Recovery, Mobile Data recovery, CCTV Data Recovery, Memory Card Data Recovery, SQL Data Recovery, Server Data Recovery, Raid Data Recovery, NAS-SAS Data Recovery.
MOBILE REPAIR
Real Expert Service Qatar is one of the leading mobile phone service center in Doha. Since we mobile repair center Qatar value our customers’ time, you don’t have to spend a big downtime. In the current world order, Mobile phones have become inevitable gadgets and they are with us wherever we go. customers can be rest assured that their phone will be repaired quickly and professionally. Customers can either visit the service center or call for a technician to come to their home or office. Customers can also take advantage of the latest mobile phone accessories and upgrade their mobile phone’s hardware and software. In addition to mobile phone repair services, Real Expert Qatar also offer other services such as laptop and tablet repair. We are the best option if you are looking for a reliable and cost-effective way to get your devices repaired quickly. With our wide range of services, Real Expert Qatar is the perfect solution for all your mobile phone repair needs.
1 note
·
View note
Text
Effective Oracle Server Maintenance: A Guide by Spectra Technologies Inc

Organizations in today's time rely heavily on robust database management systems to store, retrieve, and manage data efficiently. Oracle databases stand out due to their performance, reliability, and comprehensive features. However, maintaining these databases is crucial for ensuring optimal performance and minimizing downtime. At Spectra Technologies Inc., we understand the importance of effective Oracle server maintenance, and we are committed to providing organizations with the tools and strategies they need to succeed.
Importance of Regular Maintenance
Regular maintenance of Oracle servers is essential for several reasons:
Performance Optimization: Over time, databases can become cluttered with unnecessary data, leading to slower performance. Regular maintenance helps to optimize queries, improve response times, and ensure that resources are utilized efficiently.
2. Security: With the rise in cyber threats, Oracle server maintenance and maintaining the security of your oracle database is paramount. Regular updates and patches protect against vulnerabilities and ensure compliance with industry regulations.
3. Data Integrity: Regular checks and repairs help maintain the integrity of the data stored within the database. Corrupted data can lead to significant business losses and a tarnished reputation.
4. Backup and Recovery: Regular maintenance includes routine backups, which are vital for disaster recovery. Having a reliable backup strategy in place ensures that your data can be restored quickly in case of hardware failure or data loss.
5. Cost Efficiency: Proactive maintenance can help identify potential issues before they escalate into costly problems. By investing in regular upkeep, organizations can save money in the long run.
Key Maintenance Tasks
To ensure optimal performance of your Oracle server, several key maintenance tasks should be performed regularly:
1. Monitoring and Performance Tuning
Continuous monitoring of the database performance is crucial. Tools like Oracle Enterprise Manager can help track performance metrics and identify bottlenecks. Regularly analyzing query performance and executing SQL tuning can significantly enhance response times and overall efficiency.
2. Database Backup
Implement a robust backup strategy that includes full, incremental, and differential backups. Oracle Recovery Manager (RMAN) is a powerful tool that automates the backup and recovery process. Test your backup strategy regularly to ensure data can be restored quickly and accurately.
3. Patch Management
Stay updated with Oracle’s latest patches and updates. Regularly applying these patches helps close security vulnerabilities and improves system stability. Establish a patch management schedule to ensure that your database remains secure.
4. Data Purging
Regularly purging obsolete or unnecessary data can help maintain the database’s performance. Identify and remove old records that are no longer needed, and consider archiving historical data to improve access speed.
5. Index Maintenance
Indexes play a crucial role in speeding up query performance. Regularly monitor and rebuild fragmented indexes to ensure that your queries run as efficiently as possible. Automated tools can help manage indexing without manual intervention.
6. User Management
Regularly review user access rights and roles to ensure that only authorized personnel have access to sensitive data. Implementing strong user management practices helps enhance security and data integrity.
7. Health Checks
Conduct regular health checks of your Oracle database. This includes checking for corrupted files, validating data integrity, and ensuring that the system is operating within its capacity. Health checks can help preemptively identify issues before they become critical.
Conclusion
Oracle server maintenance is not just a technical necessity; it is a strategic approach to ensuring that your organization can operate smoothly and efficiently in a data-driven world. At Spectra Technologies Inc, we offer comprehensive Oracle database management services tailored to meet the unique needs of your organization. By partnering with us, you can rest assured that your Oracle server will remain secure, efficient, and resilient.
Investing in regular maintenance is investing in the future success of your business. Reach out to Spectra Technologies Inc. today to learn more about how we can help you optimize your Oracle database management and ensure seamless operations.
0 notes
Link
SysTools SQL Recovery Crack repairs corrupt MDF and NDF SQL Server files and exports recoverable data to SQL databases or compatible formats.
0 notes
Text
cyber security
What is Cybersecurity?
Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information, extorting money from users, or interrupting normal business processes.
Importance of Cybersecurity
In today's connected world, cybersecurity is critical because:
1. Protecting Data: Both personal and organizational data are valuable. Cybersecurity measures help protect this data from theft and misuse.
2. Maintaining Trust: Security breaches can damage the trust between a company and its customers, leading to loss of business and reputation.
3. Regulatory Compliance: Many industries are subject to regulations that require the protection of sensitive information. Compliance with these regulations is essential to avoid legal penalties.
4. Preventing Financial Loss: Cyberattacks can lead to significant financial losses, not just from the theft of information but also from the costs associated with responding to the attack, repairing damage, and potential fines.
Types of Cyber Threats
1. Malware: Software designed to damage or perform unwanted actions on a computer system, including viruses, worms, and trojans.
2. Phishing: Fraudulent attempts to obtain sensitive information by pretending to be a trustworthy entity, often via email.
3. Ransomware: A type of malware that encrypts the victim's data and demands a ransom to restore access.
4. Denial-of-Service (DoS) Attacks: Attacks that flood a network or server with traffic, rendering it unable to respond to legitimate requests.
5. Man-in-the-Middle (MitM) Attacks: Attacks where the attacker secretly intercepts and possibly alters the communication between two parties.
6. SQL Injection: Inserting malicious code into a SQL query to manipulate databases and gain unauthorized access to data.
Key Elements of Cybersecurity
1. Network Security: Measures to protect the integrity, confidentiality, and availability of network and data.
2. Information Security: Protecting the confidentiality, integrity, and availability of data, regardless of the form it takes.
3. Endpoint Security: Securing endpoints or entry points of end-user devices like desktops, laptops, and mobile devices.
4. Application Security: Keeping software and devices free of threats. A compromised application can provide access to the data it is designed to protect.
5. Identity Management and Access Control: Ensuring that only authorized individuals can access resources and data.
6. Cloud Security: Protecting data, applications, and services in cloud computing environments.
Outcome:
1. Risk Management
2. Threat Detection
3. Incident Response
4. Data Protection
5. Network Security
6. Cryptography
7. Ethical Hacking
8. Compliance
9. Security Policies
10. Vulnerability Assessment
Key benefits of to leaning:
1. Data Protection
2. Threat Mitigation
3. Network Security
4. Privacy Preservation
5. Regulatory Compliance
6. Risk Management
7. Business Continuity
8. Incident Response
9. Reputation Management
10. Intellectual Property Security
Why you choose data analytics in izeon innovative pvt ltd.
Izeon have lot of things to learn in data analytics, digital marketing, web designer, data science, frontend development with backend developments. We are providing skill development enhance, productivity, and better performance of in and around at Chennai.
That’s why I chosen izeon innovation pvt ltd.
our site: https://www.izeoninnovative.com/izeon/
0 notes
Text

Lost crucial business data accidentally? 😱
No need to worry! Contact Efforts Solutions IT, your trusted partner in the UAE for data recovery, repair and migration solutions! 💼🛠️
Whether it's documents, emails, photos, or music files, we have the expertise to seamlessly retrieve them from any storage device, regardless of the operating system.💻📂 Our software not only helps with data recovery but also ensures hassle-free email client migration, keeping all your valuable mail items safe and sound.���🔒
But wait, there's more! 🌟
We also offer Stellar's database repair tools to rescue your databases from Microsoft SQL Server, Oracle, MySQL and more.🛡️🚀
So, don't let lost data stress you out—trust Efforts Solutions IT to save the day!🦸♂️🦸♀️
Check out https://effortz.com/service/best-data-recovery-software/ for further info.🔗
#effortssolution#repairsolutions#migrationsolutions#databaserepair#tools#microsoftsql#sqlserver#server#oracle#itsolutions#microsoft
0 notes
Text
Navigating Through the Storm: Repairing SQL Server 2022 Database Corruption
Below is a structured approach to tackling database corruption in SQL Server 2022, featuring practical T-SQL code examples. Introduction Database corruption is a daunting challenge for any database administrator (DBA). In SQL Server 2022, Microsoft has continued to enhance its robust set of tools to detect, diagnose, and repair corrupt databases. This article provides a hands-on guide for…
View On WordPress
#database integrity solutions#DBCC CHECKDB examples#SQL Server 2022 corruption repair#SQL Server corruption prevention#T-SQL repair scripts
0 notes
Text
NSIC Technical Services Centre offers career-focused software, hardware, networking, and computer application courses with placement aid and payment plans.
New Post has been published on https://www.jobsarkari.in/nsic-technical-services-centre-offers-career-focused-software-hardware-networking-and-computer-application-courses-with-placement-aid-and-payment-plans/
NSIC Technical Services Centre offers career-focused software, hardware, networking, and computer application courses with placement aid and payment plans.
NSIC Technical Services Centre, a division of the National Small Industries Corporation (NSIC), is inviting applications for various job-oriented courses. The courses offered include Advanced Diploma in Software Technology, Advanced Diploma in Computer Hardware and Networking, NIELIT ‘O’ Level, Computer Hardware and Networking, Advanced Diploma in Computer Application, Computerised Accounting and Tally, Laptop Repairing, Mobile Repairing, MCP & CCNA, ICCNA, Linux Administration, Core Java, C, C++ & Oops, Office & Internet, Python Programming, SQL Server, IMS, Advance Excel / VBA, and Project Training. The duration and fees vary for each course. The center also provides placement assistance and offers an installment facility. Interested individuals can contact NSIC Technical Services Centre located near Govind Puri Metro Station in Okhla Phase-III, New Delhi. Contact details are provided on the website www.nsic.co.in.
NSIC Technical Services Centre offers Job Oriented Courses in various fields.
The courses range from Diploma to Advance Diploma and cover subjects like Software Technology, Computer Hardware & Networking, Computer Application, etc.
The duration of the courses varies from 6 months to 2 years.
Eligibility for the courses is either 10th pass or 12th pass.
Placement assistance is available and installment facility is provided.
GST is charged extra and interested individuals can request a callback by sending an SMS.
NSIC Technical Services Centre offers Job Oriented Courses
Diploma and Advance Diploma courses available
Courses include Software Technology, Computer Hardware & Networking, Computer Application, etc.
Duration of courses ranges from 6 months to 2 years
IAdv. Diploma in Software Technology
Duration: 1 Year
Fee: Rs. 48,000/-
Eligibility: 12 Pass
IAdv. Diploma in Computer H/w and Networking
Duration: 1 Year
Fee: Rs. 32,000/-
Eligibility: 12 Pass
INIELIT ‘O’ Level
Duration: 15 Months
Fee: Rs. 32,000/-
Eligibility: 12 Pass
IComputer Hardware & Networking
Duration: 1 Year
Fee: Rs. 24,000/-
Eligibility: 10 Pass
IAdvance Diploma in Computer Application
Duration: 1 Year
Fee: Rs. 25,000/-
Eligibility: 12 Pass
IDiploma in Computer Application
Duration: 6 Months
Fee: Rs. 15,000/-
Eligibility: 10 Pass
IComputerised Accounting & Tally
Duration: 120 Hrs.
Fee: Rs. 10,000/-
Eligibility: 12 Pass
ILaptop Repairing
Duration: 120 Hrs.
Fee: Rs. 8,000/-
Eligibility: 10 Pass
IMobile Repairing
Duration: 80 Hrs.
Fee: Rs. 7,000/-
Eligibility: 10 Pass
IMCP & CCNA
Duration: 120 Hrs.
Fee: Rs. 8,000/-
Eligibility: 12 Pass
ICCNA
Duration: 80 Hrs.
Fee: Rs. 6,000/-
Eligibility: 12 Pass
ILinux Administration
Duration: 80 Hrs.
Fee: Rs. 6,000/-
Eligibility: 12 Pass
ICore Java
Duration: 60 Hrs.
Fee: Rs. 6,000/-
Eligibility: 12 Pass
/C, C++ & Oops
Duration: 60 Hrs.
Fee: Rs. 5,000/-
Eligibility: 10 Pass
Office & Internet
Duration: 60 Hrs.
Fee: Rs. 4,000/-
Eligibility: 10 Pass
IPython Programming
Duration: 80 Hrs.
Fee: Rs. 6,000/-
Eligibility: 10 Pass
ISQL Server
Duration: 40 Hrs.
Fee: Rs. 5,000/-
Eligibility: 10 Pass
IMS
Duration: 40 Hrs.
Fee: Rs. 6,000/-
Eligibility: Undergoing BCA/MCA/BE/B.Tech
I Advance Excel / VBA
Duration: 1 Month
Fee: Rs. 5,000/-
Eligibility: Undergoing BCA/MCA/BE/B.Tech
Explore Job Oriented Courses at NSIC Technical Services Centre
NSIC Technical Services Centre offers a wide range of job-oriented courses in various fields
Eligibility for courses is either 10th pass or 12th pass
Placement assistance and installment facility available
Request a callback by sending SMS ‘COMP’ to 9654578062
You see the following because WP_DEBUG and WP_DEBUG_DISPLAY are enabled on this site. Please disabled these to prevent the display of these developers' debug messages.
The `the_content` filter applied.
The `the_content` filter applied.
The `the_content` filter applied.
true
Not an instance if `WP_Post`.
Not an instance if `WP_Post`.
Not an instance if `WP_Post`.
NULL
Post eligible.
Post eligible.
Post eligible.
false
0 notes
Text
SQL Recovery Tools are high demanding tool. Are you looking for the best sql recovery tool? then check this article for more details.
https://www.updatesinsider.com/sql/best-sql-recovery-tools/
#sql #recovery #repair #restore #ui #updatesinsider
0 notes
Text
CYBER SECURITY
Cyber security:
What is Cybersecurity?
Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information, extorting money from users, or interrupting normal business processes.
Importance of Cybersecurity
In today's connected world, cybersecurity is critical because:
1. Protecting Data: Both personal and organizational data are valuable. Cybersecurity measures help protect this data from theft and misuse.
2. Maintaining Trust: Security breaches can damage the trust between a company and its customers, leading to loss of business and reputation.
3. Regulatory Compliance: Many industries are subject to regulations that require the protection of sensitive information. Compliance with these regulations is essential to avoid legal penalties.
4. Preventing Financial Loss: Cyberattacks can lead to significant financial losses, not just from the theft of information but also from the costs associated with responding to the attack, repairing damage, and potential fines.
Types of Cyber Threats
1. Malware: Software designed to damage or perform unwanted actions on a computer system, including viruses, worms, and trojans.
2. Phishing: Fraudulent attempts to obtain sensitive information by pretending to be a trustworthy entity, often via email.
3. Ransomware: A type of malware that encrypts the victim's data and demands a ransom to restore access.
4. Denial-of-Service (DoS) Attacks: Attacks that flood a network or server with traffic, rendering it unable to respond to legitimate requests.
5. Man-in-the-Middle (MitM) Attacks: Attacks where the attacker secretly intercepts and possibly alters the communication between two parties.
6. SQL Injection: Inserting malicious code into a SQL query to manipulate databases and gain unauthorized access to data.
Key Elements of Cybersecurity
1. Network Security: Measures to protect the integrity, confidentiality, and availability of network and data.
2. Information Security: Protecting the confidentiality, integrity, and availability of data, regardless of the form it takes.
3. Endpoint Security: Securing endpoints or entry points of end-user devices like desktops, laptops, and mobile devices.
4. Application Security: Keeping software and devices free of threats. A compromised application can provide access to the data it is designed to protect.
5. Identity Management and Access Control: Ensuring that only authorized individuals can access resources and data.
6. Cloud Security: Protecting data, applications, and services in cloud computing environments.
Outcome:
1. Risk Management
2. Threat Detection
3. Incident Response
4. Data Protection
5. Network Security
6. Cryptography
7. Ethical Hacking
8. Compliance
9. Security Policies
10. Vulnerability Assessment
Key benefits of to leaning:
1. Data Protection
2. Threat Mitigation
3. Network Security
4. Privacy Preservation
5. Regulatory Compliance
6. Risk Management
7. Business Continuity
8. Incident Response
9. Reputation Management
10. Intellectual Property Security
Why you choose data analytics in izeon innovative pvt ltd.
Izeon have lot of things to learn in data analytics, digital marketing, web designer, data science, frontend development with backend developments. We are providing skill development enhance, productivity, and better performance of in and around at Chennai.
That’s why I chosen izeon innovation pvt ltd.
our site: https://www.izeoninnovative.com/izeon/
1 note
·
View note
Link
0 notes
Text
UYPP: Ben Ruel's Garage Garden

Back in March, we announced the winners for our Unleash Your Potential Program, in which six participants got to configure their own System76 computer to use for their awesome projects. This first awesome project is the Garage Garden, helmed by awesome project-er, engineer, and mighty green thumb Ben Ruel. We sat down with Ben to see how his project has been growing on the Meerkat.
Can you tell us about the Garage Garden project? What's it all about?
I spent a career with the Coast Guard and came up here—my final tour with the Coast Guard was in Juneau. Being in southeast Alaska, we’re constrained with what they call off-the-road systems, and the only way in or out of town is by boat or by plane. So all of our food comes up here by barge for a small nominal fee, or by aircraft for an incredibly large fee.
When I came up to Juneau with my wife and kids 11 years ago, we noticed that by the time our produce gets up here, it’s lived on a barge a week, two weeks out of Seattle, and you have no shelf life left on them. We started trying to grow food within the first year of getting here, and we came to the conclusion pretty quickly that with 300 days plus of rain every year, outdoor growing wasn’t really a viable option. That’s when we started a hobby farm in a garage growing some stuff in soil under fluorescent lights, as odd as that sounds.
Since then, we’ve progressed into hydroponics, but we’ve done it very manually. We go out every other day and take readings by hand, so I’ve been doing some research about building IOT devices that will talk back and automate some of the readings. My dream would be using it to actually control the concentration of nutrient solutions that we use. The overall goal is we’re going to build the hydroponic monitoring network of IOT devices, and use the Meerkat as a control center for the devices and a repository for all the data. We’ve also been doing some investigating behind the scenes into whether or not it could grow enough legs to become a business.

Is there a specific type of produce that you’re starting with?
We’ve been all over the road. Right now we’ve got lettuce. We’ve always got some kind of green leafy vegetables whether it’s any variety of lettuce that will grow hydro, some bok choy and tatsoi, and we’re growing kale like it’s going out of style. We’ve grown cucumbers to the point where I think I’ve harvested 65 pounds of cucumbers off of 4 plants over the last couple of months, but we’re really constrained by our size.
I live in a relatively small 3-bedroom house, and we’re just using a one-and-a-half car garage as our grow area. Right now I’ve got two tents. As funny as it sounds, cannabis is legal in Alaska and has been forever—my wife and I don’t touch the stuff, but because it’s been legalized, the infrastructure and the supplies that we need are freely available. We’re growing tomatoes in a tent that’s designed for marijuana growth. It works really well. It helps to maintain efficient temperature control; you can maintain temperature and humidity, block out extraneous light if you don’t want it, and cycle the lights on and off.
Depending on whether it’s too hot in the summer we’ll run the lights at night, and in the wintertime we’re looking for extra warmth, we can shift the cycle and run the lights during the day. Our big benefit up here is that, because Juneau’s all on hydroelectric power, electricity is really cheap.

What variables are being monitored?
With hydroponics, there’s a good number of parameters that you’ve got to try and keep track of. You’re basically diluting nutrients in a solution of as pure water as you can get. You want to keep track of things—your pH can’t be too acidic or too alkaline, for example.
The other big parameter is the electrical conductivity, or total dissolved solids. You want to make sure you’ve got the right concentration of nutrients, and that your nutrient solution isn’t salting up. As you’re adjusting pH back and forth, it’ll start demineralizing salt, so tracking that data gives you a good indication for when it’s time to dump the reservoir and start over.
We’re doing it manually now. I go out every couple of days and we take samples, and sit down and log it into a spreadsheet. The Meerkat acts as a control center for programming devices, keeping a repository of the programming for the IOT devices that we’re using (Arduinos with the esp8266 chips) as well as running different database programs as Docker containers, so that they can be spun up and knocked down fast enough as we try and figure out what the best way to move forward is. We’ve got a couple of database servers that I’ve been playing around with, trying to break from traditional SQL and looking at NoSQL type of databases.
I’m not an IT guy by trade. I’m more of an electronics guy, so I’m kind of doing it as a study-by-night type of project.
What has your experience been like with the Meerkat so far?
I’m actually completely blown away by the Meerkat’s performance. It’s astounding what that small form factor and footprint is able to do. I’ve used Linux for a number of years, and basically everybody’s heard of System76. I’ve seen Pop!_OS before and never really played with it all that much, but I’ve actually grown to love it. The feel, the ergonomics, the interface, and even down to the color schemes that come bone-stock right out of the box. They just make more sense to me. I’m looking forward to the COSMIC update after researching that to see how the differences in the workflow will affect things.

What software are you using for this project?
Right now we’re writing in Docker containers and running the Tick Stack from Influx. We’re also running Telegraf, Protograph, Capacitor, playing around with the Time Series Database, I’ve got a container running MongoDB I run with SQLite, and there’s a couple different IDEs I’ve got loaded on there as well for programming Arduinos or esp8266 chip flashing.
How was the setup process for the machine?
It was up and running within 10–15 minutes of pulling it out of the box. I actually took it to work, too. We do a lot of work with government agencies, and I’ve been doing a lot of microwave radio repair. I’ve got a pretty small workbench at our shop here in Juneau, so using the Meerkat to drive all of our test equipment to control the radio while logging data coming out of the radio, it was perfect. It had enough horsepower to remotely control the test equipment. I wasn’t pushing it all that hard, but setting it up and going back and forth between having it at home or at work, it was negligible to get it up and running.
Stay tuned for further updates from Ben Ruel’s Garage Garden and cool projects from our other UYPP winners!
#system76#meerkat#desktop#mini#minicomputer#computers#desktops#laptops#servers#keyboards#NoSQL#Pop!_OS#Ubuntu#Linux#Alaska#Juneau#hydroponics#farming#vegetables#produce#cucumbers#totsui#bok choy#Arduino#Mongodb#IOT#iot solutions#automation#harvest#garage
19 notes
·
View notes
Link

Check out which SQL recovery tool are best for recovery and retrieval of files and how they can be used for database repair. These tools are ranked on the basis of compatibility with SQL server, OS support, total items recovered in different scenarios, recovery rate and reviews from top SQL management influencers like MSDN, SQL Server Central and software suggest.
0 notes