#secure file transfer solutions
Explore tagged Tumblr posts
Text

Say goodbye to expensive, complicated file-sharing tools. eShare.ai offers a smart, secure, and pocket-friendly file management app that’s built for individuals, teams, and businesses on the go. Share, store, and manage your files anytime, anywhere—without breaking the bank.
#pocket-friendly file sharing app#affordable cloud storage#file management app#smart file sharing#eshare.ai#low-cost document sharing#cloud app for small business#secure file transfer#productivity tool#mobile file management#AI-powered file storage#budget-friendly file app#easy file sharing#file collaboration app#digital file storage solution
0 notes
Text
#Linux#Linux data replication#cloud solutions#Big data security#cloud computing#secure data handling#data privacy#cloud infrastructure#cloud technology#Data Analytics#data integration#Big data solutions#Big data insights#data management#File transfer solutions
0 notes
Text
Watch It | Lee Sangyeon

SUMMARY: you were summoned to stop the crime spree of the renowned group The Boyz by hacking into one of the systems to retrieve information about a specified location before it's too late. what you did not expect was that their leader has been spying on every move you make from the shadows and eventually confronting you about it, which then turns into your biggest nightmare.
PAIRING: criminal Sangyeon x hacker f!reader
GENRE: smut (18+ MDNI!!)
WARNINGS: kissing, petnames (sweetheart, baby, princess), mentions about violence/illegal business (stealing), size kink, voyeurism, dirty talk, public sex, rough sex, fingering, handjob, p in v sex, unprotected sex, they went for rounds, mean dom! Sangyeon
WORD COUNT: 3,235
A/N: let me explain. it was the ✨stare✨ from the concept pic itself that gave me ideas for this fic 😭 huge thanks to my bubba @juyeonszn for beta reading this & convincing me to change my theme ily forever 🥺💜 also shoutout to @daisyvisions @snowflakewhispers for fueling me with ideas / validating my horniness oops— (but ily both so much 😘)

“Agent Y/N, are you in position?”
“Yes, sir. I am waiting for the right moment to jump into the enemy’s territory.”
With one click on the earpiece, you immediately turned off the buzzing sound from the headquarters as you needed to focus and ensure that you were all alone and secure as you entered the place of interest.
As you flung your backpack onto your back, you quietly peeked through the few trucks parked in the parking lot right outside the abandoned building. Given that your job was to hack into the system and you needed good internet service, conducting it outdoors would be much more ideal than inside the building itself.
You and your team received a transmission hours ago about how this group of individuals has been conducting illegal business, such as stealing information from multiple laboratories—specifically ones located on the outskirts of Seoul to avoid detection and arrest. According to your team’s analysts, they have also discovered how they had been stealing chemical solutions that were pretty much hazardous to the public, and god knows whatever they will be using them for.
In other words, they are a pretty suspicious gang, and someone has to look into their spree of crimes before things get out of control. Being one of the best hackers on the team, you were sent to the actual location to hack into their system as best as you could.
So here you were, in the depths of the night, staking out the parking lot alone, hoping that all goes well and that you can quickly do the job and get out of there as soon as possible. Frankly, it all felt super eerie, especially when it was this late at night, and there weren’t many street lamps to provide enough light to make you feel safe by yourself.
After looking thoroughly and confirming with your eyes that you were alone, you slowly moved towards the multiple trucks parked in the middle of the parking lot. You managed to squeeze yourself through them and get to a well-lit area; that was when you finally took your laptop out of your backpack and started hacking away.
To the best of your abilities, you were able to sneak into the laboratory’s system fairly quickly, and you ran over their live security camera footage to check if the criminals were within the building. Immediately, the security camera footage popped up on the screen, and you could quickly identify several men scattered throughout the different labs within the facility.
“They were probably looking for the right chemical, " you thought, as they were all split up and divided into three groups in each laboratory. While they were trying to find the liquid, you had to quickly hack into the database to retrieve all of the information regarding the facility and the chemicals produced over the years and quickly send them back to your headquarters for analysis.
After about 10 minutes of transferring all of the files, it was time for you to get out of there and return to let the other agents that were on their way to take over and confront the criminals themselves. You weren’t a field agent, so you couldn’t do much physical combat against the criminals themselves. As much as you wanted to, you weren’t ready for your title as an agent to be stripped off you anytime soon; hence respecting the laws and just doing as you were told would be the wisest decision for now.
You quickly phoned the headquarters, letting them know you had retrieved all the necessary documents and would finally return to report. As you were permitted to do so, you got up and were going to keep all of your belongings back in your backpack until one of the security cameras began flashing.
You quickly got back down again, trying to see what was happening. That was when you remembered a crucial detail.
According to the information you guys have had so far, you knew that the group of criminals consisted of 11 members, so you decided to do a headcount one by one on the screen, starting from 1 to 11.
“8…9…and 10.”
10?
Someone was missing, but who?
Just then, a deep husky voice broke you off from your attention on the screen, and you looked around to see where it was coming from. Finally, you landed your eyes towards one of the vehicles right across you, and there he was—one of the criminals sitting right on top of the truck with both his legs spread wide apart, looking down towards you.
“Aren’t you pretty good at your job, sweetheart?”
Oh no. You were busted.
“U-umm…sorry…it’s just that…I was supposed to write a report regarding this facility, so I am here to look around.”
“At this hour? Close to midnight? I highly doubt that, princess.”
Immediately, he hopped down from the vehicle in one swift movement and began approaching you slowly. You instinctively shut your laptop, hugged it close to your chest, and backed away.
“I-I’m sorry! It seems I came at the wrong time! I will take my leave now, then. I’m sorry to have disrupted you!” You bowed down profusely before turning your heel and tried to run as quickly as you could until he grabbed your wrist and pulled it upwards, turning back in his direction.
There was this smug yet dangerous look on his face, contradicting the pure and innocent look he had on before. That sent a chill up your spine, and you quickly gulped before he slowly pushed you till your back finally hit against one of the trucks. You closed your eyes upon the impact and elicited a quiet yelp with his movement.
Suddenly, you felt his fingers lift your chin, and he commanded you to open your eyes to look straight at him.
“Now sweetheart, we weren’t done having our little fun conversation yet, were we? It breaks my heart that you decided to take off running before we even started.”
You were panicking as his grip slightly tightened around your wrist, pushing it back against the truck, signalling that you would be dead meat if you tried something funny again next time. You were stuck, and there was no way you could ring the headquarters as that would blow up your cover and the location of the base of operations.
The only thing you could do was to pray that the field agents would make their way over to you soon until you heard a mild static and a voice calling through the earpiece.
“T-there isn’t much ser-service here, b-but we will be sli-slightly late d-due to the he-heavy traffic. H-hang in t-there, a-agent Y/N! W-we’ll surely be c-coming—”
And then it all went silent.
Your only hope was lost, as the enemy threatened and pinned you with little to no help coming your way anytime soon. You could use your physical combat skills to fight against the man before you, but something in your gut told you that it would be a horrible idea to try anything funny with him right now.
With that, you could only take a deep breath and try to talk things out with him for a bit, stalling some time before help eventually arrived.
“W-what…what do you want from me?” You questioned, or more like stammered. It was clear that you were trembling in your voice.
The man chuckles slightly as he smiles back at you. “See, sweetheart. I’m afraid I can’t let you off that easily, knowing that you were spying on us and retrieving crucial evidence and information that would hinder our mission.”
This time, his fingers on your chin slowly travelled down to your neck and chest. It was the way he took his time gently sliding his finger down and touching your bare skin that made you let out a gasp.
“I’d like to play a little game with you, princess.”
“W-what do you…” You were beginning to lose your mind as he brushed his fingers across your lips, smudging the lipstick that you’d put on prior.
“I’d like to see how much you can handle, and trust me, we will have so much fun. I’ll make sure that you won’t be heading back to your headquarters anytime soon.”
Within seconds after that last sentence, he crashed his lips with yours and began savouring them as a tingling sensation ran through your body. He quickly deepened the kiss, his lips moving against yours with urgency.
It was wrong. This was all so wrong.
You knew how bad this situation was because he was your enemy. But then, something about his lips made you crave more. His kisses tasted like honey, and the way he moved his lips against yours drove you insane.
Without you knowing, your grip against the laptop slowly loosened, and eventually, he took it away from you and gently placed it on the ground, his hands quickly moving back up to your cargo pants, rubbing the spot in between your thighs, earning a gasp from you.
He smiled as you gave him the reaction that he wanted, and he began to untie your pants before pulling them down, his fingers now brushing over your sensitive spot through the lace underwear that you were wearing. Slowly, he began to feel that you were starting to get wet, and that was his cue to hook his finger under the seam of your underwear before pulling them down, revealing your now wet clit all exposed.
You hissed as the cold air from the atmosphere came in contact with your clit, and it took the enemy a moment to reconnect his fingers to your wet sensitive spot, rubbing it again before slowly inserting two fingers into you.
“Aah…aaah…”
“I’ll be a dear and tell you my name, princess. Call me Sangyeon, moan for me,” he leaned towards you and whispered.
“S-sangyeon….”
“That’s it, baby. You’re doing so good for me. I shall grant you your next reward now, hmm?”
As he removed his fingers from your clit, he quickly moved them to his pants, unzipped and shoved them down rather hastily. It was the way you immediately noticed the erection through his boxers, and your eyes widened from just that alone. Sangyeon smirked at your reaction and reconnected his lips to yours to give you a few pecks.
“Look at you already can’t stop staring at my big cock. Oh, baby. I’ll make sure that you won’t regret playing with it.”
Immediately, he grabbed your free hand and guided you to touch his erection. You gasped from that alone while Sangyeon let out a soft groan. You couldn’t help but naturally start rubbing his tip, which made Sangyeon moan for you.
“Touch me, baby.” He commanded.
Guiding your hands again, he allowed you to pull his boxers down, and your mouth watered at the sight of his massive bulge. You wrapped your hands around his cock before you began gliding your hands up and down his member. In return, he inserted his fingers back into your clit once again, and the both of you were now a moaning mess.
“S-sangyeon…kiss me…please…” you whined, wanting to taste his sweet honey-like lips once again.
“Oh, honey. You love the way my tongue twirls around yours?”
“Y-yes…very much…aaahh—”
Just like that, he was now back to kissing you breathless. As his tongue slid into your mouth, he began sucking your tongue, and you shut your eyes tightly from the sensation. It made you forget entirely about how you were supposed to escape this guy as soon as possible, trying to find a potential hideout place to wait for your fellow agents.
It seemed as if Sangyeon had wrapped you around his fingertips, just as he had planned to, and he would make sure that you wouldn’t be leaving this place anytime soon. He would proceed to the next step of his plan anytime now.
He gently removed your hands away from his bulge as he took it himself to align the tip towards your entrance, and you knew that you were in big trouble. Now, you tried to move forward when his hand, still grabbing your wrist, tightened again and pushed it back towards the truck again.
“Oh no, princess. We’re just getting started. Stay here with me, and I’ll give you the best fucking sex you’ll ever have.”
As soon as those words slipped out of his mouth, he immediately slid himself into you, and you all but screamed, a teardrop falling from the corners of your eyes. Sangyeon didn’t even give you enough time to adjust to his huge size fully and eventually began slamming into you hard.
“Fuck—fuck.” It was all that you could’ve said because you had already lost your mind ever since he kissed you for the first time. Now that he was within you? Oh, you were far, long gone from reality.
Given the way he was fucking you so hard, even the truck that you were leaning against began rocking back and forth following your pace.
Your eyes watered as he hit every single spot within you, causing you to cry out loud. If you were to be honest, it actually did hurt, especially which such a large and hard dick like his. But the pleasure far exceeded the pain, and you cried out for more.
“Sangyeon…sangyeon…”
“Tell me what exactly you want, baby.”
“Keep it going…please…”
“Just like that? Are you sure that is enough?”
“I…want you to fuck me faster and harder—”
“Anything else?” He was now picking up the pace, and it was visible that his chest was rising up and down much quicker than before as he tried his best to catch his breath.
“I…want you to fuck me till my legs feel numb, give me more and more…aaah—”
“That is what exactly I like to hear, sweetheart.”
As he slammed into you hard, you felt a tight knot form around your stomach, signalling that you were about to reach your high and cum. Sangyeon noticed your demeanour as you buckled your hips and spread your legs wider for him to gain more access to you.
“I’m cumming! I’m cumming!” You screamed.
“Do it, baby. Cum all over my cock, I want you to be dripping wet just for me.” He growled.
With a few more pushes, you eventually released and spilled all of your juices all around his cock, so much so that it was oozing out of you, and it all splattered on the ground.
You breathe in heavily before Sangyeon gives you a gentle kiss on the lips, reassuring you that you have done so well for him.
“That’s it, princess. What a good girl you’ve been. But unfortunately, there is more to come baby.”
He grabbed both of your shoulders before turning you around rather aggressively, so now you were facing the truck instead. If you were to be honest, that rough act of his turned you on more than it was painful. It was a few seconds before you felt his grip return to you on both sides of your hips, as you felt his cock rubbing up and down once again on your dripping wet clit.
Sangyeon leaned forward to whisper in your ear, sending you a chill down your spine. “Give me some more, baby. You know you can do it.”
As he pushed his cock back into you, an immense moan spilt out from your mouth as he began pounding into you again. You had already had sex and felt his member all around you just a minute prior, yet you were still struggling to adjust to his bulge.
“God, sweetheart. I’ve already fucked you hard, and yet you’re still so tight. I guess I wasn’t rough enough.”
As he pounds into you, your hands that were pressed against the truck begin pushing the vehicle once again. If only there were someone around, you swear to god that the car's movement would be more than enough to prove that something wasn’t right and that there were people everywhere in the empty parking lot.
But your comrades are still nowhere to be seen, and you were still bounded by the criminal himself, fucking you till you were sore to the point that you would not be able to walk on your own after this.
“S-sangyeon…I-I wanna cum again for you so badly…” You whimpered.
This time, he moved one of his hands up to grab a chunk of your hair and pulled it back; that firm sudden grip caused you to scream once again for him.
“Do it then. Cum with me this time.” He commanded, pulling your hair and pounding into you even harder.
“Fuck—fuck—fuck—Sangyeon!! I’m cumming!!”
With one final hard thrust, both of you released your liquids before slowing down the momentum and catching your breaths together. He removed his grip from your hair before he grabbed your chin and turned your head back for him to kiss you again. You snaked your hands up to his neck to return the favour.
Just then, you heard sirens coming from afar, and you heard static in your earpiece again.
“Agent Y/N, please respond! We’re finally here to infiltrate the facility; please head out, return to the back of our vehicle, and stay put!”
It was your cue to leave now, and there was no more extended point in you staying here.
You gulped before you pulled away from Sangyeon, mustering up the courage to reject him for good this time.
“S-sangyeon…I have to go…I can’t stay here any more.” You stammered, hoping that he would finally let you leave this time, especially since he had already gotten what he wanted.
But you should’ve known better because his familiar dark and dangerous look was plastered on his face again, and he pushed you back against the truck.
“You know, now that your comrades are here, I’m afraid there’s more reason for me not to let you leave now, hmm? I’ve been stalling time for my boys to get what they want in the facility before your agents arrive to ruin our plan. While they were doing that, I was out here guarding the area, making sure nobody was to sabotage our plan.”
So that was why he played this little dirty game with you.
“Knowing my boys, I’m pretty sure that they have gotten everything we need, and all they have to do is defeat your fellow agents, and then we will leave. And while they are doing that, you will keep me company until they’re done.” He threatened.
This time, he grabbed your wrist and dragged you towards the front of the car, directly where you could see clearly how your fellow agents were confronting the criminals. Within seconds, a fight has broken out between them across the facility, and you have no choice but to stay here helplessly and be unable to provide them with any aid.
Before you could say anything, Sangyeon yanked you down towards the hood of the car so that you were lying on top of it, and he prepared to go for a third round with you.
“I want you to watch closely with how you and your fellow agents are going to fail this mission terribly while I fuck you real good till you’re begging for more.”

masterlist
taglist: @deoboyznet @kflixnet @flwoie @heemingyu @snowflakewhispers (join my permenant taglist here!)
#deoboyznet#k-vanity#k-labels#kflixnet#the boyz#tbz#the boyz x reader#tbz x reader#the boyz imagines#the boyz scenarios#the boyz fanfic#tbz scenarios#tbz fanfic#lee sangyeon#lee sangyeon x reader#lee sangyeon smut#sangyeon smut#the boyz smut#tbz smut#sangyeon imagines#sangyeon scenarios
337 notes
·
View notes
Text
The Rise of 5G and Its Impact on Mobile App Development

5G isn’t just about faster internet — it’s opening up a whole new era for Mobile App Development. With dramatically higher speeds, ultra-low latency, and the ability to connect millions of devices seamlessly, 5G is transforming how developers think about building apps. From richer experiences to smarter services, let's explore how 5G is already reshaping the mobile app landscape in 2025 and beyond.
1. Lightning-Fast Data Transfer
One of the biggest promises of 5G is incredibly fast data transfer — we're talking about speeds up to 100 times faster than 4G. For mobile apps, this means that large files, high-resolution images, and HD or even 4K video content can be downloaded or streamed instantly. Apps that once needed to compress their data heavily or restrict features due to bandwidth limits can now offer fuller, richer experiences without worrying about lag.
2. Seamless Real-Time Experiences
5G dramatically reduces latency, meaning the time between a user action and the app’s response is almost instant. This will revolutionize apps that rely on real-time communication, such as video conferencing, live-streaming platforms, and online gaming. Developers can create much more responsive apps, allowing users to interact with data, people, and services with zero noticeable delay.
3. The Growth of AR and VR Mobile Applications
Augmented Reality (AR) and Virtual Reality (VR) apps have been growing, but 5G takes them to another level. Because of the high bandwidth and low latency, developers can now build more complex, interactive, and immersive AR/VR experiences without requiring bulky hardware. Imagine trying on clothes virtually in real-time or exploring a vacation destination through your phone — 5G is making this possible within Mobile App Development.
4. Smarter IoT-Connected Apps
The Internet of Things (IoT) will thrive even more in a 5G environment. Smart home apps, connected car apps, fitness trackers, and other IoT applications will be able to sync and update faster and more reliably. Developers can now integrate complex IoT ecosystems into mobile apps with minimal worries about network congestion or instability.
5. Enhanced Mobile Cloud Computing
Thanks to 5G, mobile cloud computing becomes much more viable. Instead of relying solely on local device storage and processing, apps can now store large amounts of data and execute processes directly in the cloud without latency issues. This allows users with even mid-range smartphones to experience high-performance features without the need for powerful hardware.
6. Revolutionizing Mobile Commerce
E-commerce apps are set to benefit greatly from 5G. Instant-loading product pages, real-time customer support, virtual product previews through AR, and lightning-fast payment gateways will enhance user experience dramatically. This could lead to higher conversion rates, reduced cart abandonment, and greater user loyalty in shopping apps.
7. Opportunities for New App Categories
With the technical limitations of mobile networks reduced, a whole new range of apps becomes possible. Real-time remote surgeries, autonomous vehicles controlled via mobile apps, and highly advanced telemedicine solutions are just a few examples. The doors are open for mobile developers to innovate and create applications that were previously impossible.
8. Better Security Requirements
With 5G’s mass connectivity also comes a bigger responsibility for security. As mobile apps become more connected and complex, developers must prioritize data protection, encryption, and secure authentication methods. Building security deeply into Mobile App Development workflows will be critical to maintain user trust.
9. More Demanding User Expectations
As 5G rolls out globally, users will expect every app to be faster, smoother, and more capable. Apps that fail to leverage the benefits of 5G may seem outdated or sluggish. This shift will push developers to continually optimize their apps to take advantage of higher speeds and smarter networking capabilities.
10. Preparing for the 5G Future
Whether you’re building entertainment apps, business solutions, healthcare tools, or gaming platforms, now is the time to adapt to 5G. Developers must start thinking about how faster speeds, greater device connections, and cloud capabilities can improve their mobile applications. Partnering with experts in Mobile App Development who understand the full potential of 5G will be key to staying ahead in a rapidly evolving digital world.
3 notes
·
View notes
Text
Representative Office in Thailand
A Representative Office (RO) serves as a non-revenue generating entity that allows foreign companies to establish a legal presence in Thailand without forming a full subsidiary. Governed by the Ministry of Commerce (MOC) and Foreign Business Act (FBA), ROs are ideal for:
Market research and business development
Coordination between headquarters and Thai partners
Quality control for regional suppliers
However, ROs face strict operational limitations—understanding these restrictions is critical before registration.
2. Legal Framework & Key Restrictions
Permissible Activities (Under MOC Notification No. 275)
An RO may only engage in:
Sourcing goods/services for its parent company
Inspecting/controlling quality of products ordered by HQ
Providing advisory support to HQ about Thai market
Disseminating information about new products/services
Reporting business trends to the parent company
Prohibited Activities (That Would Require a Full Company):
Direct sales, invoicing, or revenue generation
Signing contracts on behalf of the parent company
Providing services to third parties
Penalties: Violations can result in fines up to THB 1 million, imprisonment, or forced closure.
3. Registration Process: Step-by-Step Requirements
Phase 1: Pre-Registration Documentation
Parent Company Documents (notarized/apostilled):
Certificate of Incorporation
Memorandum & Articles of Association
Board Resolution authorizing RO establishment
Audited financial statements (last 3 years)
Thai Office Requirements:
Lease agreement (registered at Land Department)
List of intended expatriate staff
Phase 2: Ministry of Commerce Approval
Submit Application (Form Kor Tor 1) to MOC’s Business Development Department
Review Period: 30–60 days
Post-Approval: Register at DBD, Revenue Dept., and Social Security Office
Phase 3: Ongoing Compliance
Annual Audit Submission (even with no revenue)
Work Permits: Limited to 5 foreign employees
4. Tax & Financial Considerations
A. Tax Obligations
Corporate Income Tax: 0% (if compliant with RO restrictions)
Withholding Tax: 15% on remittances to HQ classified as "service fees"
VAT: Not applicable (no sales activity)
B. Capital Requirements
Minimum THB 5 million remitted to Thailand within first 3 years
Must maintain THB 2 million in a Thai bank account
C. Audit Requirements
Annual financial statements must be filed by a licensed Thai auditor
Transfer pricing documentation recommended for HQ transactions
5. Representative Office vs. Other Business Structures
CriteriaRepresentative OfficeRegional OfficeLimited CompanyAllowed RevenueNoYes (from affiliates)Yes (full operations)Tax LiabilityNone10% CIT (regional)20% CITCapital RequiredTHB 5MTHB 10MTHB 2M+Work PermitsMax 5No limitNo limit
Key Takeaway: An RO is not a substitute for a trading company—it’s a non-commercial liaison office.
6. Common Pitfalls & How to Avoid Them
A. Accidental Revenue Generation
Risk: Providing consultancy to local firms may be deemed as service income
Solution: Draft activity scope carefully in MOC application
B. Underestimating Compliance Costs
Hidden Fees: Auditor fees (~THB 50k/year), visa renewals, legal retainer
Budget: Minimum THB 1M/year for a compliant RO
C. Visa & Work Permit Issues
Expat Headcount: 5 is the absolute max—plan staffing accordingly
Local Hiring: Must have at least 1 Thai employee per foreign hire
7. When to Upgrade to a Regional/Branch Office
Consider transitioning if you need to: ✔ Generate revenue from affiliate companies ✔ Sign contracts locally ✔ Employ more than 5 foreigners
Upgrade Process: Requires new MOC approval and capital increase.
8. Expert Recommendations
For Market Entry:
Use an RO for 2–3 years to test the market before committing to a full subsidiary
Pair with a Thai distributor for actual sales
For Compliance:
Retain a Thai law firm to audit activities annually
Maintain separate bank accounts for HQ remittances
For Long-Term Strategy:
If scaling, convert to a BOI-promoted company for better incentives
Conclusion: Is a Representative Office Right for You?
A Thai RO offers low-risk market access but demands strict adherence to non-commercial activities. It’s ideal for:
Manufacturers vetting Thai suppliers
Tech firms exploring ASEAN expansion
Service companies needing a local liaison
Final Warning: Misuse can trigger FBA violations—always align activities with MOC approval. For complex cases, consult a Thai corporate lawyer before registration.
#thailand#corporate#thai#thailandcorporate#thaicorporate#representativeoffice#representativeofficeinthailand
2 notes
·
View notes
Text
On the eve of the anniversary of a massive, world-wide cybersecurity breach, the Nova Scotia government says the response to the MOVEit hack cost the province $3.8 million. The breach occurred May 30 and May 31, 2023, and affected multiple organizations and millions of people around the globe. The online hack involved a file transfer service called MOVEit, which is used by the private sector and governments, including Nova Scotia. The software is made by Burlington, Massachusetts-based company Ipswitch and allows organizations to transfer files and data between employees, departments and customers. In a news release Wednesday promoting the final report into the online hack, Nova Scotia’s minister in charge of Cyber Security and Digital Solutions said the province has learned a number of lessons from the MOVEit breach. [...]
Continue Reading.
Tagging: @newsfromstolenland
11 notes
·
View notes
Text
Cloud Storage vs Local Storage: Pros and Cons
In today’s digital world, choosing the right storage solution for your data is critical. Whether you’re an individual, a business, or a creative professional, understanding the benefits and limitations of cloud storage and local storage can help you make an informed decision that fits your needs. Both have their strengths and weaknesses, so let’s explore the pros and cons of each.
Pros of Cloud Storage
Accessibility Anywhere: Cloud storage lets you access your files from any device with an internet connection. This flexibility is invaluable for remote workers, frequent travelers, and anyone needing quick, on-the-go access to their data.
Scalability: Cloud plans can be easily upgraded as your storage needs grow, without the hassle of purchasing or setting up new hardware. This makes cloud storage ideal for businesses or individuals with rapidly expanding data.
Automatic Backups and Updates: Cloud providers handle all maintenance, backups, and software updates. This reduces the risk of data loss and frees you from managing technical upkeep.
Collaboration: Cloud platforms allow real-time file sharing and editing, supporting team projects and collaboration across different locations.
Cons of Cloud Storage
Internet Dependency: You need a stable internet connection to upload, download, or access your files quickly. Slow or intermittent connections can be frustrating and limit efficiency.
Recurring Costs: Cloud storage usually involves monthly or yearly subscription fees. While some providers offer free tiers, costs can increase significantly with higher storage demands.
Privacy Concerns: Your data is stored on third-party servers, which may raise privacy or security concerns for sensitive or confidential information, despite encryption and security measures.
Pros of Local Storage
Full Control and Privacy: With local storage, your data remains physically with you, giving you complete control over security and access. This is important for users handling sensitive files like legal or medical records.
Offline Access: Local storage devices such as external hard drives or Network Attached Storage (NAS) allow file access without needing the internet, making it reliable in areas with poor connectivity.
One-Time Cost: You purchase the storage device once and avoid recurring fees. Over time, this can be more economical than cloud subscriptions.
High-Speed Transfers: Local storage generally offers faster data transfer rates, especially with solid-state drives (SSDs) or USB 3.0 connections, beneficial for large files like videos or high-resolution images.
Cons of Local Storage
Limited Accessibility: Access is restricted to the physical device unless you set up complex remote access systems, which can be inconvenient.
Scalability Challenges: Expanding storage requires buying additional devices, which may be costly and less flexible.
Risk of Physical Damage: Local drives can fail, be lost, stolen, or damaged by environmental factors. Without proper backups, this can result in permanent data loss.
Maintenance Burden: You are responsible for managing backups, software updates, and hardware maintenance, which can require technical know-how.
For a detailed comparison, check out this comprehensive guide on Cloud Storage vs Local Storage to help you decide what’s best for your data needs.
Conclusion
Choosing between cloud and local storage depends largely on your priorities. Cloud storage excels in flexibility, scalability, and ease of use, making it ideal for users who need remote access and collaboration. Local storage shines when control, privacy, speed, and offline access are more important.
For many, a hybrid approach that combines both cloud and local solutions offers the best balance — local storage for sensitive or large files, and cloud storage for backups and easy sharing.
2 notes
·
View notes
Text
Players from the USA are annoyed to the new part of The Witcher for being Woke and DEI… You are talking about a Polish studio from games, because the fucking CD Project Red is the fuck from Poland

Ciri literally looks like a typical Slavic woman from that time
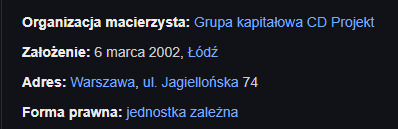
"CD Projekt SA (until July 25, 2011 Optimus SA) - Polish joint -stock company dealing in the production and distribution of computer games through its subsidiaries. The dominant entity of the CD Projekt capital group.
The company existed under its original name in 1988–2011. In the 90s She was one of the largest manufacturers of PCs in Poland, then expanded its activity to the production of cash registers, providing integrated IT solutions for offices and large enterprises, and created one of the leading Polish online portals onet.pl. After the division and subsequent transformations of the capital structure, Optimus took over CDP Investment and focused almost exclusively on the production, location and distribution of computer games [3] [4] [5].
In 2020, CD Projekt was placed first in the ranking of the 100 largest Polish private companies [6]"
"The company was founded in 1988 as a private company Romana Kluski. From 1994 Optimus was listed on the Warsaw Stock Exchange. The company was the largest manufacturer of computers in Poland. In 1996, it began publishing, under which the "Education and Entertainment" group was created,, focusing Optiums Bis (distributor of Ubisoft games, Activision, Axall, Condor, Merit, MindScape, SSI, ID Software, SCI and Warner), Optimus Nexus (producer of games and multimedia) and Optimus Pascal (producer of spolkin) and Optimus himself was a representative of Disney Interactive. [10] [11]. On October 13, 1999, the company expanded the offer of products with game consoles, becoming one of the two official Nintendo distributors in Poland [12]. In the years 2000–2002, the company's legal transformations took place, as a result of which it was finally divided into two separate business entities - Optimus and the Onet Group. On August 28, 2006, the Securities and Stock Exchange Commission decided to withdraw the company from the WSE. The reason was improper performance of information duties by the Company. However, the decision did not enter into force and Optimus remained on the stock exchange.
At the beginning of 2006, the headquarters of Optimus was moved from Nowy Sącz to Warsaw, And the installation of computers on the principle of outsourcing to the ABC Data plant. In the same year, the company also filed a claim for compensation in the amount of PLN 35 million for unlawful decisions of tax authorities of 2002, which, according to Optimus, led to the loss of reputation by the company, losses PLN 27 million and direct costs of tax proceedings in the amount of PLN 8 million [1].
On October 31, 2007, members of the management of Optimus, Piotr Lewandowski and Michał Lorenc, were detained by CBŚ regarding the controversial increase in capital in the company. On April 16, 2008, Lewandowski was again detained by the CBA on charges of removing money from the company [13].
On January 22, 2008, the Company submitted a bankruptcy application to the court with the possibility of concluding an agreement, but it was withdrawn after the public broadcast of the shares, of which some of the revenues (13, PLN 5 million) was allocated to cover the obligations. Another bankruptcy application was submitted by the company West, but the courts of both instances dismissed him [14].
Optimus is the creator of the largest Polish internet portal - Onet.pl. After the sale of shares in the company by its founder Roman Kluska, the website was transferred to the Onet daughter company, which was then taken over by the ITI group, and in 2012 it hit the hands of the Axel Springer Polska Group. The name Onet.pl comes from the word Optimusnet"
Suddenly Poland became too progressive for fucking Americans?
6 notes
·
View notes
Text
Recover Stolen Crypto

Cryptocurrency has revolutionized the way we transact, offering decentralized and secure solutions for the modern economy. But with these benefits come risks, including the possibility of theft. Crypto theft can be devastating, leaving victims feeling powerless due to the anonymity of blockchain transactions. However, while challenging, recovering stolen crypto isn’t impossible. This guide will walk you through the steps to maximize your chances of retrieving lost funds and fortify your crypto security. Recover stolen crypto
Understanding How Crypto Theft Happens
Phishing Attacks
Phishing involves tricking users into revealing sensitive information such as private keys or wallet passwords. Scammers often impersonate legitimate platforms via fake websites or emails designed to look authentic. Once you input your details, they gain access to your wallet.
Hacking of Wallets and Exchanges
Crypto wallets and exchanges are prime targets for hackers. Weak security protocols, vulnerabilities in the platform, or user negligence can lead to unauthorized access and fund transfers.
Social Engineering Scams
These scams prey on human psychology. For instance, scammers may pose as trusted individuals or companies, convincing victims to transfer funds or disclose sensitive information.
Malware and Keyloggers
Cybercriminals use malware or keyloggers to monitor user activity. When you type your wallet credentials, the software captures and transmits the data to the attacker.
Immediate Steps to Take After Crypto Theft
Stay Calm and Act Quickly
Panic can lead to poor decisions. Assess the situation logically and act swiftly to prevent further losses.
Identify the Theft Details
Review your transaction history to determine when and how the theft occurred. Note the wallet addresses involved, the amount stolen, and the transaction ID.
Secure Remaining Funds
Transfer your remaining funds to a secure wallet. Hardware wallets or cold storage solutions are preferable as they are offline and immune to hacking.
Contacting Relevant Authorities
Reporting to Local Law Enforcement
File a report with your local authorities. While they may lack blockchain expertise, having an official record can support further recovery efforts.
Involving Cybercrime Units
Specialized cybercrime divisions can investigate the theft and collaborate with international organizations if needed.
Engaging Regulators Like SEC
In cases involving fraudulent investments, report the incident to regulatory bodies like the SEC or FCA to initiate investigations.
Notifying Crypto Platforms and Wallet Providers
How Exchanges Can Assist
Notify the exchange where the stolen funds were transacted. They may freeze suspicious accounts or provide information to investigators.
The Role of Wallet Providers
Wallet providers might help in identifying security vulnerabilities or advising on recovery steps.
Sharing Transaction Details
Provide all relevant details, including the transaction hash, wallet addresses, and any communication with the scammer.
Utilizing Blockchain Analysis Tools
How Blockchain Transparency Aids Recovery
Blockchain’s immutable ledger allows you to trace fund movements. With the right tools, you can monitor the thief’s wallet and subsequent transfers.
Popular Blockchain Analysis Tools
Platforms like Chainalysis, CipherTrace, and Elliptic specialize in tracking stolen cryptocurrency and identifying patterns.
Tracking Stolen Funds
Collaborate with professionals who use these tools to increase your chances of recovering the funds.
Hiring a Cryptocurrency Recovery Expert
Benefits of Professional Help
Experts have the technical knowledge and resources to trace transactions, liaise with platforms, and initiate recovery processes.
Vetting Recovery Agencies for Legitimacy
Ensure the agency has a proven track record. Beware of additional scams that exploit victims seeking help.
Avoiding Additional Scams
Never pay upfront fees without verifying the agency’s legitimacy. Genuine recovery services operate transparently.
Using Social Media and Community Networks
Engaging the Crypto Community
Post about your stolen crypto on forums, Reddit, or Twitter. The community often shares valuable insights or connects you with experts.
Raising Awareness About Stolen Funds
Highlighting the theft publicly can deter thieves from cashing out and put pressure on platforms to assist.
Success Stories
Many individuals have successfully recovered their stolen crypto by rallying community support and leveraging online networks.
Legal Options for Recovering Stolen Crypto
Filing Lawsuits
If you have enough evidence to identify the thief, you may file a lawsuit. Courts can issue orders to freeze assets or compel exchanges to provide information about suspicious accounts.
International Legal Frameworks
Cryptocurrency theft often crosses borders, making it necessary to engage international legal frameworks like the Hague Convention. Collaborating with global enforcement agencies can enhance recovery efforts.
Challenges with Jurisdiction
Jurisdictional issues complicate legal proceedings. Many crypto criminals operate in countries with lax regulations, making prosecution and recovery harder.
Preventative Measures to Protect Cryptocurrency
Using Hardware Wallets
Hardware wallets store private keys offline, making them virtually immune to hacking. They are the gold standard for crypto security and should be your primary storage method for large holdings.
Enabling Two-Factor Authentication (2FA)
2FA adds an additional layer of security to your crypto accounts by requiring a second verification step. Always enable it, preferably using an authenticator app rather than SMS.
Avoiding Suspicious Links and Emails
Phishing scams often start with an innocent-looking link or email. Be cautious and double-check URLs before entering sensitive information. Bookmark trusted platforms to avoid accidental clicks on fake sites.
Educating Yourself on Crypto Scams
Recognizing Common Scam Patterns
From Ponzi schemes to fake giveaways, crypto scams come in many forms. Stay informed about the latest trends and tactics used by scammers.
Staying Updated with News and Security Tips
Follow trusted crypto news outlets and cybersecurity blogs. Awareness is your best defense against evolving threats in the crypto space.
Building a Secure Crypto Environment
Regular Wallet Audits
Periodically review your wallet and transaction history to identify unauthorized activity early. This practice can prevent small breaches from escalating into significant losses.
Diversifying Storage Solutions
Spread your funds across multiple wallets. Use a combination of hardware wallets, paper wallets, and software wallets for added security.
Investing in Cybersecurity Tools
Firewalls, antivirus software, and VPNs can protect you from malware and other digital threats. These tools are essential for safe crypto trading and storage.
Understanding the Limits of Recovery
Why Crypto Recovery Isn’t Guaranteed
The decentralized and pseudonymous nature of blockchain technology makes fund recovery difficult. Once funds are transferred to a thief’s wallet, reversing the transaction is nearly impossible without their cooperation.
Managing Expectations
While recovery efforts are worth pursuing, it’s essential to prepare for the possibility that your funds may not be recovered. Focus on improving your security to prevent future losses.
The Role of Decentralized Finance (DeFi) in Crypto Security
How DeFi Protocols Enhance Transparency
DeFi platforms operate on smart contracts, which are transparent and immutable. This openness can help in tracking fraudulent activity and ensuring secure transactions.
Risks Associated with DeFi Platforms
Despite their benefits, DeFi platforms are not immune to vulnerabilities. Exploits in smart contracts and lack of insurance can lead to significant losses.
Recovering stolen cryptocurrency is no easy feat, but it’s not entirely hopeless either. By taking immediate action, leveraging blockchain tools, and engaging with experts, you can increase your chances of recovering your funds. Most importantly, prioritize prevention by adopting stringent security measures. Remember, in the world of cryptocurrency, staying one step ahead of scammers is your best protection.
Contact Info: Email: - [email protected]
2 notes
·
View notes
Text
What are Payout Solutions and How Do They Simplify Business Payments?

In today’s rapidly evolving financial landscape, businesses are constantly looking for efficient, reliable, and cost-effective ways to manage payments. Whether it’s paying employees, suppliers, or customers, seamless and error-free payment processes are critical for operational success. This is where payout solutions come into play. A payout solution is an advanced payment processing system that automates and simplifies bulk payments, ensuring businesses can send funds securely and quickly.
What are Payout Solutions?
Payout solutions refer to platforms or systems that enable businesses to distribute payments to multiple beneficiaries seamlessly and efficiently. These beneficiaries can include employees, vendors, freelancers, customers, or even stakeholders. By leveraging modern technology, payout solutions allow businesses to process bulk payments through a single interface, eliminating manual processes and reducing the chances of errors.
Payout solutions are particularly essential for businesses that deal with large volumes of transactions daily. Sectors such as e-commerce, fintech, gig economy platforms, and other industries rely heavily on streamlined payout systems to ensure their financial operations run smoothly.
For example, companies can use a payout solution to disburse salaries, refunds, commissions, incentives, or vendor payments at scale with minimal human intervention.
How Do Payout Solutions Work?
A payout solution works as a bridge between a business and its payment recipients. It integrates with the business’s financial system or software and streamlines the process of transferring funds. Here’s a step-by-step breakdown of how payout solutions operate:
Integration: The payout system integrates with the business’s existing financial software or banking platform to access required data, such as payment amounts and recipient details.
Bulk Upload: Businesses upload payment details, including beneficiary names, account information, and amounts, into the platform. This can often be done via a file upload or API integration.
Payment Processing: The payout solution processes the payments using multiple payment modes, such as bank transfers, UPI, NEFT, IMPS, wallets, or card-based systems.
Verification and Approval: Before releasing funds, the system verifies all recipient details to avoid errors or payment failures. Businesses can also set up approval workflows to ensure security and compliance.
Disbursement: Payments are disbursed instantly or as scheduled, depending on the system’s configuration and business requirements.
Notifications: Once payments are completed, recipients are notified via email, SMS, or other communication channels. Additionally, businesses receive confirmation reports to maintain records.
How Payout Solutions Simplify Business Payments
Payout solutions offer a variety of features that help businesses simplify their payment processes. Some of the key benefits include:
Automation of Payments One of the most significant advantages of payout solutions is automation. Businesses no longer need to process payments manually, which can be time-consuming and prone to errors. Automated solutions allow bulk payments to be processed quickly and accurately.
Multiple Payment Modes Modern payout systems provide businesses with flexibility by supporting various payment methods, including bank transfers, UPI, mobile wallets, and more. This ensures payments can be sent according to the preferences of recipients.
Real-Time Processing Traditional payment methods often involve delays, especially when dealing with bulk transactions. Payout solutions offer real-time or near-instant payment processing, ensuring recipients receive funds promptly.
Cost and Time Efficiency Manual payment processes require significant time and resources, leading to operational inefficiencies. By using a payout solution, businesses can reduce administrative costs and save valuable time that can be allocated to core operations.
Improved Accuracy and Security Errors in payment processing can cause delays, mistrust, and additional costs. Payout solutions use robust verification mechanisms to minimize errors and enhance security. Additionally, many systems comply with financial regulations, ensuring safe transactions.
Seamless Reconciliation Payout solutions simplify the reconciliation of payments by providing detailed transaction records and reports. Businesses can easily track completed, pending, or failed transactions, making financial management more transparent and organized.
Enhanced Customer and Vendor Experience Fast and error-free payments improve the overall experience for customers, vendors, and employees. For instance, e-commerce platforms can use payout systems to ensure quick refunds, leading to improved customer satisfaction and loyalty.
Payment Solution Providers and Their Role
Payment solution providers play a crucial role in the success of payout systems. These providers offer the technology and infrastructure needed for businesses to handle complex payment processes efficiently. By offering robust platforms, they enable organizations to send bulk payments with speed, accuracy, and security.
Companies like Xettle Technologies are leading players in the payout solutions ecosystem. They provide advanced payout platforms designed to cater to businesses of all sizes, ensuring streamlined payment operations and financial management. With such providers, businesses can focus on growth while leaving their payment challenges to trusted experts.
Key Industries Benefiting from Payout Solutions
Several industries rely heavily on payout solutions to manage their financial operations, including:
E-commerce: Automating refunds, vendor payments, and cashbacks.
Fintech: Handling instant disbursements for loans and digital wallets.
Gig Economy Platforms: Paying freelancers, contractors, and service providers seamlessly.
Insurance: Disbursing claim settlements quickly to enhance customer trust.
Corporate Sector: Managing salaries, incentives, and reimbursements.
Conclusion
Payout solutions have revolutionized the way businesses manage their financial transactions. By automating and simplifying payment processes, businesses can save time, reduce costs, and improve accuracy while ensuring recipients receive funds promptly. Whether it’s paying employees, vendors, or customers, payout solutions offer a scalable and secure way to handle bulk payments effortlessly.
As payment solution providers like Xettle Technologies continue to innovate, businesses can look forward to more efficient and seamless financial operations. For organizations aiming to streamline their payouts, adopting a reliable payout solution is a step toward achieving operational excellence and enhanced financial management.
2 notes
·
View notes
Text
#data migration#data management#big data#data protection#file synchronization software#cloud solutions#linux#data orchestration#Government Data Management#file replication#Linux file transfer#secure data backup#cloud computing#cloud software
0 notes
Text
ProHoster.info: The Ultimate Solution for Reliable and Affordable Web Hosting
In todays competitive digital landscape, having a robust and reliable hosting service is critical for success. ProHoster.info has become a go-to platform for individuals and businesses seeking secure, efficient, and affordable hosting solutions. Let’s dive deep into why ProHoster.info is the right choice for you.

Comprehensive Hosting Solutions at ProHoster.info
ProHoster offers a wide range of hosting plans to cater to various needs:
Shared Hosting: Perfect for small websites, shared hosting allows multiple sites to share resources on a single server. This makes it highly affordable for beginners without compromising on performance. Ideal for personal blogs or startup sites.
VPS Hosting: ProHoster’s Virtual Private Servers provide users with dedicated resources and greater control. It’s a step up for growing websites needing better performance, ensuring faster load times and reliability.
Dedicated Servers: For large businesses or resource-intensive applications, dedicated servers offer unmatched power and exclusivity. You get full control, enhanced security, and scalability for enterprise projects.
Domain Registration and VPN Services: ProHoster also simplifies your online journey with domain registration and VPNs, ensuring your site and browsing activities remain secure and private.
Key Features That Set ProHoster Apart
DDoS Protection: Cyberattacks can devastate websites. ProHoster’s advanced DDoS protection safeguards your site from malicious traffic, ensuring your website stays online and secure 24/7.
Free SSL Certificates: Security is paramount. ProHoster provides free SSL certificates with every plan, helping secure data transfers and boosting your website's SEO rankings. A secure site builds trust among users.
24/7 Customer Support: The technical support team at ProHoster is available round the clock, providing quick and effective solutions to any issues. From minor queries to critical issues, you can rely on their professional assistance.
High-Speed Servers: Loading speed directly impacts user experience and search rankings. ProHoster’s high-speed servers ensure fast load times, reducing bounce rates and improving site engagement.
Advanced Control Panels: Managing a hosting account can seem daunting, but ProHoster simplifies it with intuitive control panels. Users can manage domains, files, and settings with ease, making it beginner-friendly yet powerful for experts.
Why ProHoster.info is the Right Choice
Cost-Effective Plans: ProHoster is designed for all budgets, providing affordable hosting without sacrificing quality. Their pricing plans are straightforward, with no hidden fees, making them perfect for small businesses or personal projects.
Global Data Centers: Hosting servers strategically placed across the globe ensure low latency and better connection speeds for your audience, regardless of their location. This feature is particularly beneficial for businesses with a global reach.
Eco-Friendly Hosting: Sustainability matters, and ProHoster is committed to eco-friendly practices. By utilizing energy-efficient technologies, they aim to reduce their carbon footprint without affecting performance.
Scalability: As your business grows, so do your hosting needs. ProHoster offers seamless scalability, allowing you to upgrade plans or resources with minimal downtime and no data loss.
Benefits of Choosing ProHoster.info
Seamless Website Builder: Building a professional website is easy, even for beginners, thanks to ProHoster’s drag-and-drop website builder. You can create a visually appealing site without coding knowledge.
99.9% Uptime Guarantee: A website that’s always online is essential for credibility. ProHoster ensures maximum uptime, so your visitors can access your site whenever they want.
Comprehensive Backup Solutions: Data loss can be devastating, but with ProHoster’s automated and secure backup solutions, your data remains safe and easily recoverable.
Final Thoughts
Choosing the right hosting provider is one of the most important decisions for your online success. ProHoster.info not only offers cutting-edge technology and robust features but also ensures affordability, reliability, and excellent customer support.
Whether you’re a budding entrepreneur, a seasoned developer, or a blogger, ProHoster has tailored solutions to help you thrive in the online world. Explore their plans today and take your website to the next level with ProHoster.info.
2 notes
·
View notes
Text
so it seems like im stuck with apple
i've had iphones for years. but they're expensive and overpriced, and don't seem like good value for money anymore, so i ordered a samsung. it's a lovely phone, truly. but... i couldn't get anything synced over. SmartSwitch only transferred half of my iCloud-backed photos. WhatsApp didn't transfer any of my chats or media, even though I exported it. All the apps I had to redownload seemed to have deleted any history I had accumulated on iPhone. My music - to this day downloaded in mp3 files in iTunes - simply Does Not Work on the Samsung. And like - I only spent half a day trying to move things over. I know there are solutions, download all my photos manually and transfer them with a cable. Get fucking Spotify like a normal person. Make sure I log into all the correct accounts on all apps. And I know I'm probably just too lazy. But it stressed me out so badly that everything was different, and that I felt like I lost so much. My entire life is in my phone, and it all, poof, just went away. What if Apple ever decides to discontinue? Like Blackberry did? And I used to be a Blackberry girl, I used it until the day WhatsApp (or was it Facebook) stopped working on my Blackberry.
It scares me how dependent I am in my workflow and my daily life on technology. If my tumblr account got deleted, I'd be sad, but I'd cope. If i lost the history on all my non-indispensable apps, I'd be annoyed, but I'd cope. But the thought of losing all my messages, my photos, having to re-create every routine that involves a mobile phone? That really fucks me up. I can't do it, I think, I'm not mentally flexible enough. I'm going to give it a week, but... I know how easy it is to switch to another iPhone, and maybe the continuity and security that iPhone is currently danging in front of me like a carrot is what's going to keep me with that fucking brand. As if they haven't made it as hard as possible on purpose to switch away from iPhone.
I know I'm not the type for long posts and no one will read this but I had to write it down because this is Black Mirror, to me, right now, at least a little bit. How much of myself is stored in my phone? And how much of that will I never get back - will never be free from the clutches of Apple? Anyway. I went to my laptop to post this. Even the keyboard on the Samsung was weird and I couldn't hit the keys right.
5 notes
·
View notes
Text
Skip the Ads and Convert YouTube Videos to MP3
YouTube has emerged as the preferred platform in the digital age for finding and enjoying podcasts, videos, music, and much more. Sometimes, nevertheless, users might prefer to listen to their favourite songs solely in audio format or offline. The idea of YouTube MP3 and YouTube to MP3 converters enters the picture here.
What is YouTube MP3?
"YouTube MP3" describes the process of turning YouTube videos into MP3 audio files. This helps users save bandwidth and battery life by enabling them to extract the audio from any YouTube video and listen to it offline without streaming.
Why Convert YouTube Videos to MP3?
There are many reasons why people look for YouTube to MP3 solutions:
Offline Listening: MP3 files can be downloaded and played offline, making it convenient for users to listen to their favorite content without an internet connection.
Music Playlists: Many users create personal playlists by converting YouTube music videos into MP3 files, which they can transfer to their phones or other media devices.
Podcasts and Audiobooks: YouTube hosts a wide variety of podcasts and audiobooks that can be easily converted to MP3 for a seamless listening experience.
Data Savings: Streaming high-quality videos consumes a lot of data. Converting YouTube to MP3 helps in saving bandwidth by only downloading the audio.
How Does a YouTube to MP3 Converter Work?
A YouTube to MP3 converter is a tool or software designed to extract audio from YouTube videos and convert it into the widely used MP3 format. These converters are available both as online services and downloadable software.
Online Converters: There are many websites that allow users to input the URL of a YouTube video, convert it to MP3, and then download the resulting audio file.
Downloadable Software: Some users prefer to download software that allows for faster conversion and additional features like batch processing of multiple videos.
How to Use a YouTube to MP3 Converter
Here’s a simple guide on how to use a YouTube to MP3 converter:
Copy the URL: First, copy the link of the YouTube video you want to convert.
Paste the URL: Visit a YouTube to MP3 converter website or open your preferred converter software, and paste the URL into the input box.
Choose MP3 as the Output Format: Most converters support various audio formats. Make sure to select MP3.
Download the MP3 File: Once the conversion is complete, you will be given the option to download the MP3 file to your device.
Benefits of Using an Ad-Free YouTube to MP3 Converter
One major annoyance users often face when using free online tools is ads. Pop-ups and excessive advertisements can make the conversion process frustrating. However, there are ad-free YouTube to MP3 options that provide a smoother experience, free from interruptions.
Faster Conversion: Without the distractions of ads, users can convert videos quickly and efficiently.
Enhanced User Experience: Ad-free platforms offer a cleaner and more user-friendly interface.
Security and Privacy: Some free converters filled with ads may pose security risks. Choosing an ad-free YouTube to MP3 converter can reduce the chances of encountering malicious ads.
Legal Considerations
While YouTube to MP3 conversion is widely used, it’s essential to understand the legal implications. Converting copyrighted material, like music videos or certain types of content, without permission may violate copyright laws. Always ensure that the content you are converting is either free to use or that you have obtained the necessary rights to do so.
Top YouTube to MP3 Converters
If you’re looking for reliable YouTube to MP3 converters, here are some popular options:
YouTube to MP3 Converter: A simple and user-friendly converter that supports both YouTube to MP3 and MP4 conversions.
4K Video Downloader: A software solution that allows high-quality downloads and batch processing.
SnapDownloader: Known for its speed and ability to download long videos.
Mp3 converter. Free, online Youtube to mp3 converter.: An ad-free YouTube MP3 converter that promises a hassle-free user experience.
team communication app - Troop messenger

Conclusion
YouTube MP3 conversion provides an easy way to enjoy your favorite YouTube content on the go, without the need for video streaming. Whether you want to save data, listen offline, or create personalized playlists, using a YouTube to MP3 converter can make it all possible. For the best experience, consider using an ad-free YouTube to MP3 converter to avoid interruptions and enhance your security.
As always, be mindful of copyright laws and only download content for personal use if you have the right to do so.
2 notes
·
View notes
Text
Blueberry AI Introduces it Groundbreaking 3D Digital Asset Engine – 🥝KIWI Engine🥝
Blueberry AI, a leading AI-powered digital asset management company, proudly announces the release of the KIWI Engine, a high-performance 3D engine set to revolutionize industries such as gaming, advertising, and industrial design. KIWI Engine enables teams to streamline workflows by offering real-time 3D file previews in over 100 formats directly in the browser, with no need for high-performance hardware or software.
Boasting cutting-edge features such as centralized storage, AI-powered search, and blockchain-backed file tracking, KIWI Engine ensures secure, efficient collaboration while minimizing operational costs. Designed to enhance productivity, the engine supports large file transfers, cross-team collaboration, and eliminates the risk of file versioning errors or leaks.
With its easy-to-use interface and seamless integration with existing 3D tools, KIWI Engine by Blueberry AI is the ideal solution for companies looking to optimize their 3D asset management.
Unlocking New Capbabilites of 3D Digital Assets — 🥝KIWI Engine🥝 Unveils its Power
The KIWI Engine is a high-performance 3D engine that powers Blueberry AI developed by the industry-leading AI digital asset management company, Share Creators. With exceptional performance and an intuitive interface, the KIWI Engine significantly shortens production cycles for game development, advertising, and industrial design, while reducing operational costs to truly achieve cost-efficiency.
Key Standout Features of the KIWI Engine by Blueberry AI:
Browser-Based 3D Previews: No downloads required; view over 100 professional file formats directly in your browser, including 3DMax and Maya native files; no conversion needed. This functionality eliminates the need for high-performance hardware and boosts team productivity.
Seamless Large File Transfers: Easily share and preview large files within teams, facilitating smooth collaboration between designers and developers. The built-in 3D asset review feature enhances workflow precision and speed.
Addressing Common File Management Issues:
File Security & Control: With centralized storage and multi-level permissions, KIWI Engine ensures files remain secure. Blockchain logs track user activity, and version control with real-time backups prevents file loss or version errors, reducing the risk of leaks, especially during outsourcing or staff transitions.
Outsourcing Management: Control access to shared content with outsourcing teams, minimizing the risk of file misuse.
A One-Stop 3D File Preview Solution:

Broad Format Compatibility: KIWI Engine supports mainstream formats like 3DMax, Maya, Blender, OBJ, FBX, and more. It reduces the need for multiple software purchases by loading and previewing models from various design tools in one engine.
Multi-Format Preview: Combine different 3D file formats in a single workspace for simultaneous viewing and editing. This streamlines complex 3D projects, especially those involving cross-team collaboration.
Simplified 3D Previews for Non-Technical Users: KIWI Engine makes it easy for non-technical stakeholders, such as management, to quickly preview 3D assets without installing complex software. This enhances cross-department collaboration and accelerates decision-making.
Cost Savings on Software:
Traditional design projects often require expensive software purchases just to view files. With cloud technology, the KIWI Engine by Blueberry AI eliminates the need for costly software installations. Team members can preview and collaborate on 3D files online, reducing software procurement and maintenance costs while improving flexibility and efficiency.

Improving Collaboration and Resource Reuse:
Without intelligent tools, design resources are often recreated from scratch, leading to wasted time and costs. The KIWI Engine supports multi-format 3D file previews and includes AI-powered search and auto-tagging, enabling designers to easily find and reuse existing resources. This significantly enhances collaboration and reduces the security risks of transferring large files.
User-Friendly Interface and Experience:

The KIWI Engine adopts a clean, intuitive user interface, with a well-structured layout. A detailed list of grids and materials appears on the left, while function modules (controls, materials, grids, and lighting management) are on the right, ensuring a logical and smooth workflow. Personalized settings and organization-level global configurations further enhance productivity for teams of all sizes.
Grid and Material List: After loading a model, grids and materials are clearly displayed, allowing users to easily select and edit the necessary components.
Personalized Settings: Customize the interface to suit individual workflow preferences, improving work efficiency.
Organization Settings: For large teams or cross-project managers, global configuration options enable unified project management across multiple teams, saving time and resources.
KIWI Engine's Control Tool Module:

The KIWI Engine features an innovative control tool module, covering camera controls, display functions, and advanced rendering options that meet diverse project needs—from simple model viewing to complex scene operations.
Camera Controls: Features like auto-rotation and quick reset allow users to easily adjust the camera for 360-degree model views, ensuring smooth, flexible operation.
Display Functions:
Wireframe Display: Ideal for structured previews, enabling users to inspect model geometry during the design phase.
Double-Sided Display: Displays both sides of models, even if there are defects, minimizing repair time and improving workflow efficiency.
SSR (Screen Space Reflection): Enhances model reflection effects for high-quality renderings in complex scenes.
UV Check: Displays UV distribution, helping users accurately assess UV mapping for precise texture work.
Learn more about us at: Blueberry: Best Intelligent Digital Asset Management System (blueberry-ai.com)
#DAM#3DAssetManagement#3DAsset#GameDev#IndustrialDesign#Maya#3DSMax#Blender#3DRendering#3DModeling#CloudCollaboration#3DDesignSolutions#3DVisualization#3DViewer#CollaborativeDesign
2 notes
·
View notes
Text
Top 5 Selling Odoo Modules.
In the dynamic world of business, having the right tools can make all the difference. For Odoo users, certain modules stand out for their ability to enhance data management and operations. To optimize your Odoo implementation and leverage its full potential.
That's where Odoo ERP can be a life savior for your business. This comprehensive solution integrates various functions into one centralized platform, tailor-made for the digital economy.
Let’s drive into 5 top selling module that can revolutionize your Odoo experience:
Dashboard Ninja with AI, Odoo Power BI connector, Looker studio connector, Google sheets connector, and Odoo data model.
1. Dashboard Ninja with AI:
Using this module, Create amazing reports with the powerful and smart Odoo Dashboard ninja app for Odoo. See your business from a 360-degree angle with an interactive, and beautiful dashboard.
Some Key Features:
Real-time streaming Dashboard
Advanced data filter
Create charts from Excel and CSV file
Fluid and flexible layout
Download Dashboards items
This module gives you AI suggestions for improving your operational efficiencies.
2. Odoo Power BI Connector:
This module provides a direct connection between Odoo and Power BI Desktop, a Powerful data visualization tool.
Some Key features:
Secure token-based connection.
Proper schema and data type handling.
Fetch custom tables from Odoo.
Real-time data updates.
With Power BI, you can make informed decisions based on real-time data analysis and visualization.
3. Odoo Data Model:
The Odoo Data Model is the backbone of the entire system. It defines how your data is stored, structured, and related within the application.
Key Features:
Relations & fields: Developers can easily find relations ( one-to-many, many-to-many and many-to-one) and defining fields (columns) between data tables.
Object Relational mapping: Odoo ORM allows developers to define models (classes) that map to database tables.
The module allows you to use SQL query extensions and download data in Excel Sheets.
4. Google Sheet Connector:
This connector bridges the gap between Odoo and Google Sheets.
Some Key features:
Real-time data synchronization and transfer between Odoo and Spreadsheet.
One-time setup, No need to wrestle with API’s.
Transfer multiple tables swiftly.
Helped your team’s workflow by making Odoo data accessible in a sheet format.
5. Odoo Looker Studio Connector:
Looker studio connector by Techfinna easily integrates Odoo data with Looker, a powerful data analytics and visualization platform.
Some Key Features:
Directly integrate Odoo data to Looker Studio with just a few clicks.
The connector automatically retrieves and maps Odoo table schemas in their native data types.
Manual and scheduled data refresh.
Execute custom SQL queries for selective data fetching.
The Module helped you build detailed reports, and provide deeper business intelligence.
These Modules will improve analytics, customization, and reporting. Module setup can significantly enhance your operational efficiency. Let’s embrace these modules and take your Odoo experience to the next level.
Need Help?
I hope you find the blog helpful. Please share your feedback and suggestions.
For flawless Odoo Connectors, implementation, and services contact us at
[email protected] Or www.techneith.com
#odoo#powerbi#connector#looker#studio#google#microsoft#techfinna#ksolves#odooerp#developer#web developers#integration#odooimplementation#crm#odoointegration#odooconnector
4 notes
·
View notes