#secure remote access
Explore tagged Tumblr posts
Text
“How to Set Up Secure Remote Access to Your Windows Server in Minutes with RHosting”
Setting up secure remote access used to mean navigating complex network settings, VPNs, firewalls, and port forwarding nightmares. But with RHosting, the process is now fast, user-friendly, and incredibly secure — even for non-technical users.
In this post, we'll walk you through how to set up remote access to your Windows server in just a few minutes using RHosting’s cutting-edge platform.

🚀 Step 1: Create Your RHosting Account
Head over to [RHosting's official site] and sign up for an account. You can choose a plan based on your needs — whether you’re a solo developer, a growing startup, or an enterprise IT team.
Once you’ve created an account, you’ll gain access to the RHosting control panel — your central hub for managing users, permissions, and sessions.
🔐 Step 2: Set Up Your Windows Server
You’ll either choose from:
Bring your own server (BYOS): Install RHosting’s lightweight agent on your existing Windows server.
Use a pre-configured cloud instance: RHosting can spin up a fully managed Windows server for you in the cloud.
Once connected, your server will appear in your dashboard — ready to assign access.
��� Step 3: Add Users and Define Permissions
This is where RHosting shines.
From the dashboard, you can:
Create individual users or import bulk users.
Assign application-only access (e.g., allow Excel but not the full desktop).
Control folder-level permissions, so users only see what they need.
This fine-grained control is critical for security, compliance, and streamlined workflows.
📱 Step 4: Users Log In from Any Device
Your team can now log in using:
The RHosting desktop client
Any web browser (no installation required)
Or even mobile devices
Each user’s environment is secure, isolated, and limited to only what they’ve been granted — all thanks to RHosting’s custom-built RDP technology.
🔒 Bonus: Built-In Security and Compliance Features
RHosting takes care of:
End-to-end encryption for all sessions
Automatic session timeouts
IP whitelisting and two-factor authentication
Detailed audit logs and session tracking
This means your data stays protected — even if your users are working from airports, cafes, or across international borders.
⚡ Final Thoughts
In less than 15 minutes, you can transform how your organization accesses its Windows server — without a single line of code or hardware reconfiguration.
RHosting isn’t just an alternative to RDP — it’s the future of secure, efficient, and user-centric remote desktop access.
Ready to simplify your server access without sacrificing security?
👉 Try RHosting today and set up your first secure session in minutes.
0 notes
Text
NoMachine
NoMachine is a remote connection application for PCs that allows you to access file systems and control target systems with additional features like video and audio streaming. If you’re in search of a reliable software solution for remotely connecting to any computer and accessing your files quickly, NoMachine is the perfect tool for a seamless remote desktop experience. With its intuitive…
#audio streaming#Automation#cross-platform#desktop sharing#file transfer#IT Tools#multi-platform#multi-session#NoMachine#Remote Access#remote collaboration#remote desktop#remote desktop software#remote printing#remote work#secure connections#secure remote access#video streaming
0 notes
Text
How to create a Tailscale VPN connection to my Synology NAS
This article discusses how to create a Tailscale VPN connection to my Synology NAS. According to their documentation, Tailscale simplifies secure connections to your Network-Attached Storage (NAS) devices using WireGuard. Please see how to create New Users and Join Synology NAS to Active Directory, DSM Security: How to Protect Synology DS923+ NAS, and how to “Configure VPN on Windows Server: How…
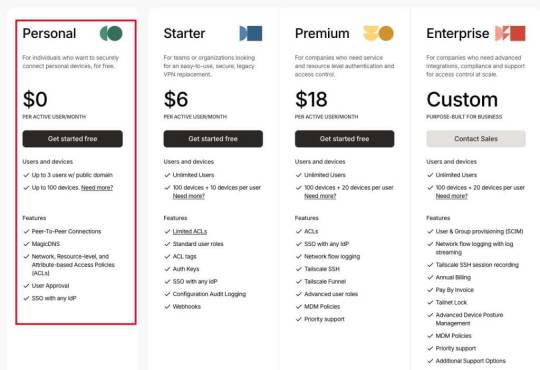
View On WordPress
#Download Tailscale for macOS#Install Tailscale for macOS#MAC#Macbook#MacOS#macOS Big Sur#Mesh Network#NAS#NAS Storage#Secure Remote Access#storage#Synology#Synology Diskstation#Synology DS923+ NAS#Synology DSM 7.2#Synology NAS#Synology Package Center#Tailnet#Tailscale Network#Tailscale VPN Connection#Turn on VPN#VPN#VPN on Synology NAS
0 notes
Text
Always On VPN Ask Me Anything (AMA) March 2024
Do you have questions about Always On VPN? Are you having a specific issue you can’t figure out? Would you like more information about configuration options? Here’s your chance to get your questions answered! Join me on Tuesday, March 26, at 10:00 AM PDT (UTC -7) for an opportunity to ask me anything (AMA!) about Microsoft Windows Always On VPN and related technologies. The AMA will be an open…

View On WordPress
#Always On VPN#AMA#AOVPN#Ask Me Anything#enterprise mobility#meeting#Microsoft#Mobility#Remote Access#secure remote access#security#VPN#webinar#Windows#Windows 10#Windows 11#Windows Server
0 notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
Bc all my passwords need to be changed every year I incorporate some celebs birthday usually into my regular base password. Anyway it is now no longer Charles leclerc 🥰 character growth 🥰
#the guys kinda repulsing me atm so good timing imo#idk if my#wording makes sense but my uni makes us change all us passwords every year for security and I just had to change it for this year#anyway no more sus low-key misogynist men on my uni remote access password :)
2 notes
·
View notes
Photo
If something you own can be remotely disabled - intentionally or not - by a third party, you don’t own it, you’re renting it.
Maybe rent is free!
But someday the person on the other end of that equation is going to either a) up your rent to increase profits, b) sell to someone who will up your rent to increase profits or c) go out of business and take your access with them. This is a feature, not a bug, of the endless-growth model. “Internet activated” means “remote kill switch”.
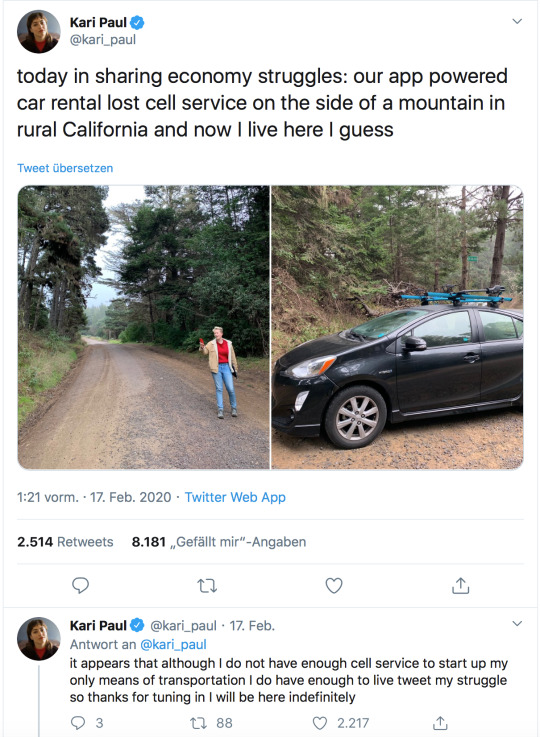
Welcome to the future, where you don’t own anything and the stuff you rent stops working once your phone has no signal.
#not even getting into the massive security vulnerabilities most IOT devices represent#if it can be accessed remotely#*anyone* could access it remotely#and the moment the software team stops producing security patches for your model of smart fridge#it becomes a liability
172K notes
·
View notes
Text
Exploring the Smart Home Industry: SwitchBot's Innovative Smart Lock Solutions
The smart home industry is rapidly evolving, and one brand that stands out is SwitchBot. Their innovative products are transforming how we interact with our homes, particularly with their smart lock solutions.
SwitchBot's smart locks are designed to enhance security and convenience for homeowners. With features like remote access, keyless entry, and seamless integration with other smart home devices, SwitchBot is making it easier than ever to manage home security.
Imagine being able to lock or unlock your door from anywhere using your smartphone! This level of accessibility not only provides peace of mind but also contributes to a more efficient lifestyle.
SwitchBot is committed to creating user-friendly and reliable smart home products, and their smart lock is a perfect example of their dedication to innovation and customer satisfaction. By embracing technology, SwitchBot is paving the way for a brighter, smarter future in home automation.
0 notes
Text
Exploring the Future of Home Security with SwitchBot Smart Locks
Hello everyone! I'm excited to share my thoughts on the amazing advancements in the smart home industry, particularly focusing on SwitchBot and their innovative smart locks. As technology continues to evolve, the way we secure our homes is becoming more convenient and efficient.
SwitchBot offers a fantastic range of smart locks that not only enhance security but also provide seamless integration with your smart home ecosystem. With features like remote access, keyless entry, and compatibility with voice assistants, these smart locks are perfect for anyone looking to upgrade their home security while enjoying modern convenience.
I've recently installed a SwitchBot smart lock at my home, and I couldn't be happier! The installation was straightforward, and the app is user-friendly, allowing me to manage access for family and friends easily. Plus, I love the peace of mind that comes with being able to monitor my home's security from anywhere.
If you're considering upgrading your home security, I highly recommend checking out SwitchBot's smart locks. They're a fantastic investment for anyone wanting to embrace the future of home automation!
Feel free to share your experiences or ask any questions about smart locks and the smart home industry. Let's keep the conversation going!
0 notes
Text
Exploring the Benefits of Smart Locks in the Smart Home Industry with SwitchBot
As the smart home industry continues to evolve, one of the most exciting advancements is the introduction of smart locks. These innovative devices enhance security and convenience for homeowners. SwitchBot, a leading brand in this space, offers a range of smart lock solutions that make it easier than ever to manage home access.
With SwitchBot's smart locks, you can enjoy features like keyless entry, remote access, and integration with other smart home devices. This means you can unlock your door from anywhere using your smartphone, making it perfect for those who want to ensure their home is secure while on the go.
Additionally, SwitchBot's smart locks are designed to be user-friendly, allowing for easy installation and seamless operation. Embracing smart lock technology not only boosts your home security but also adds to the overall convenience of your smart home ecosystem.
In a world where technology is constantly advancing, SwitchBot stands out by providing reliable and efficient solutions that cater to the needs of modern homeowners. Make the switch to a smarter, safer home today!
0 notes
Text
Looking for fast, secure, and affordable admin RDP access? Our admin RDP plans offer full administrator rights, unmatched speed, and 24/7 uptime. Ideal for developers, marketers, and remote teams who need complete control over their virtual environment. Whether you need private RDP, cheap VPS in Miami, or VPS hosting in NYC, we provide customizable solutions that fit your needs. Get your admin RDP today and experience seamless remote desktop access with powerful performance and strict security protocols.
#admin RDP#RDP with admin access#cheap admin RDP#buy admin RDP#remote desktop access#RDP hosting#Windows RDP#VPS RDP#secure RDP#fast RDP
0 notes
Text
Exploring the Future of Smart Locks in the Smart Home Industry with SwitchBot
The smart home industry is rapidly evolving, and one of the standout brands making waves is SwitchBot. Known for their innovative approach to home automation, SwitchBot is transforming how we interact with our living spaces, particularly through their smart lock solutions.
SwitchBot's smart locks offer a seamless blend of security and convenience. With features like remote access, keyless entry, and integration with various smart home systems, they provide homeowners with peace of mind while enhancing the overall functionality of their homes. Imagine being able to lock or unlock your door from anywhere, or granting access to guests without the hassle of physical keys!
The ease of installation and user-friendly app make SwitchBot's smart locks an attractive option for those looking to upgrade their home security. Plus, their commitment to quality and customer satisfaction ensures that you are making a worthwhile investment in your smart home setup.
As the demand for smart home technology continues to grow, brands like SwitchBot are leading the way in providing innovative solutions that cater to modern living. Embracing smart locks not only elevates your home security but also contributes to a more connected and efficient lifestyle.
Make the switch to a smarter home with SwitchBot's advanced smart lock technology today!
#security#convenience#installation#remote access#connected lifestyle#smart locks#home automation#keyless entry
0 notes
Text
Explore the Future of Smart Home Living with SwitchBot Smart Locks
The smart home industry is transforming the way we live, making our homes more secure and convenient. One standout brand in this space is SwitchBot, known for its innovative solutions that enhance our daily lives.
SwitchBot's smart lock is a game changer. It combines cutting-edge technology with ease of use, allowing you to secure your home effortlessly. Imagine being able to lock or unlock your door with just a tap on your smartphone!
Key features of SwitchBot's smart lock include:
Remote access: Control your lock from anywhere, giving you peace of mind.
Easy installation: No need for complicated tools or professional help.
Compatibility: Works seamlessly with your existing smart home devices.
With SwitchBot, upgrading to a smart lock means embracing a new level of convenience and security. Say goodbye to traditional locks and hello to a smarter, safer home!
Join the smart home revolution today with SwitchBot!
0 notes
Text
Exploring the Smart Home Revolution with SwitchBot Smart Locks
The Smart Home industry is rapidly evolving, and brands like SwitchBot are leading the charge with innovative solutions that enhance our everyday lives. One standout product is the SwitchBot Smart Lock, which combines security with convenience, making it easier than ever to manage access to your home.
SwitchBot Smart Locks are designed to fit seamlessly over your existing deadbolt, allowing you to upgrade your home security without the need for a complete lock replacement. With features like remote access, keyless entry, and compatibility with smart home systems, these locks provide peace of mind and flexibility.
Have you considered how a smart lock could change your routine? Imagine being able to unlock your door with just a tap on your smartphone or granting temporary access to guests while you're away. The ease of use and enhanced security features make SwitchBot Smart Locks an excellent choice for anyone looking to embrace the smart home lifestyle.
What are your thoughts on smart locks? Have you tried using one, and how has it improved your home security experience? Let's share our experiences and insights on this exciting technology!
#technology#smart locks#convenience#home security#keyless entry#remote access#smart home#home automation
0 notes
Text
What's New in Absolute Secure Access v13
Recently I wrote about NetMotion Mobility’s acquisition by Absolute Software. Absolute Secure Access (formerly NetMotion Mobility) is an enterprise VPN and Zero Trust Network Access (ZTNA) solution that includes fine-grained policy enforcement to restrict network access based on a wide range of parameters, including IP address, protocol, port, application, time of day, location, and type of…

View On WordPress
#Absolute#Absolute Secure Access#antivirus#CDR#DLP#enterprise mobility#enterprise VPN#Mobility#NAC#NetMotion#NetMotion Mobility#Network Access Control#policy#RBI#Remote Access#secure remote access#secure web gateway#security#Zero Trust#Zero Trust Network Access#ZTNA
0 notes
Text
Unlock the Future with SwitchBot Smart Locks!
The Smart Home Industry is thriving, and SwitchBot is leading the charge with their innovative smart locks. These devices not only enhance security but also add convenience to your daily life. With features like remote access and easy integration with smart home systems, SwitchBot smart locks are designed to keep your home safe while making your life easier.
Say goodbye to the hassle of traditional keys! SwitchBot's smart locks allow you to unlock your door with just a tap on your smartphone. Plus, the sleek design fits seamlessly into any home decor.
Join the smart home revolution and experience the peace of mind that comes with SwitchBot smart locks. Are you ready to upgrade your home security? Let us know what you think!
0 notes