#send email using java smtp
Explore tagged Tumblr posts
Text
Essential Server Buying Guide for Small Businesses

As your small business grows beyond a handful of employees, it's likely time to consider investing in a server. The term "server" can refer to hardware, software, or the functionality of both, and choosing the right server for your business can be a daunting task. This guide will help you navigate your options and make an informed decision.
Understanding Your Needs
Before diving into the specifics, ask yourself the following questions to determine your server needs:
Are you buying for file sharing?
Will it be predominantly used for email?
Does your workforce need to connect remotely?
Is it going to be used for data backup?
How much space do you have available to accommodate the server?
Server Hardware and Functionality
At a hardware level, servers are similar to standard PCs but are designed for 24/7 operation and often include additional features like ECC memory and redundant components to ensure continuous operation. Key hardware components include:
CPU: The number of cores and clock speed determine the server's ability to handle multiple tasks.
Memory (RAM): More RAM allows for better performance, especially under heavy load.
Storage: Multiple bays for hard drives and options for RAID configurations ensure data redundancy and fast access.
Choosing the Right Server Type
File Servers
File servers or Network Attached Storage (NAS) are used for storing and sharing files across a network. Look for:
Multiple hot-swappable drive bays
Configurable hardware/software RAID options
Low-power CPU for efficient operation
Domain Controllers
Domain controllers manage user authentication and access levels. They are crucial for businesses with multiple users and devices. Look for:
Virtualization-capable CPU (any 64-bit CPU)
At least 4 GB of RAM
Database Servers
Database servers handle large volumes of data and user queries. They are essential for applications and websites built on a database layer. Look for:
Hard drives rated for fast writes
Large CPUs (12- or 16-core)
Backup 'slave' servers for read-only databases
Web Servers
Web servers host websites and use HTTP to present web pages. They often work with a database server. Look for:
Hardware redundancy (especially for e-commerce sites)
Increased RAM capacity for better performance
Email Servers
Email servers, such as Microsoft Exchange, use specific protocols (SMTP, POP3, IMAP) to send and receive messages. Dedicating hardware to this task is recommended for optimal operation. Look for:
Similar specifications as a file server
Application Servers
Application servers centralize applications within their native framework (Java, PHP, .NET, various flavors of .js), improving performance and reducing maintenance costs. Look for:
Enterprise-grade storage bays (SAS hard drives)
ECC RAM
Choosing the Right Form Factor
Servers come in various physical form factors, including tower, rackmount, and blade:
Tower: Resembling desktop computers, tower servers are suitable for small businesses needing one or two servers. They don't require additional mounting hardware but take up more space as you add more servers.
Rackmount: These servers are installed in a rack chassis, which can hold multiple servers in slots. They are ideal for businesses needing several servers in a consolidated space.
Blade: Blade servers are more space-efficient than rackmount servers but require careful cooling and a larger initial investment. They are suitable for larger server rooms.
Server Operating Systems
A server operating system (OS) is more advanced and stable than a desktop OS, supporting more RAM, efficient CPU usage, and a greater number of network connections. The OS enables the server to perform various roles, such as:
Mail server
File server
Domain controller
Web server
Application server
Administrators use the server OS to authenticate users, manage applications and file storage, set up permissions, and perform other administrative tasks.
Conclusion
Choosing the right server for your small business involves understanding your specific needs, selecting appropriate hardware, and deciding on the best form factor and operating system. By carefully considering these factors, you can ensure your server investment supports your business's growth and operational efficiency.
0 notes
Text
Aol Login Problem 8O5~365~6444 6҉̶̙̳͉̉ͨ͂̏̃̉͜͠͠4̷̡̳̖̆̇͘͟͟͢͝4̷̡̳̖̆̇͘͟͟͢͝4̷̡̳̖̆̇͘͟͟͢͝ eMail Login Problem_Not _Working C A L L - N O W
Original story

What’s wrong with AOL Mail today? Well, AOL Mail is down for many users currently. Users affected by this outage have been taking to social media platforms like Twitter to voice their complaints.
The AOL customer support on Twitter has been actively addressing the complainants. Following are some user reports:
Anyone else having trouble signing into AOL, or is it just my internet service scr***** me over? I keep trying to log into my AOL email and it’s making me go in a fu***** circle.
@aolmail is there a problem with the aol mail? I can’t log in on the web or on my iPad.
— AnastasiaBeaverhouse (@1evilfairydust) May 23, 2019
The AOL mail login issues include authentication error, blank screen during signing in, missing AOL sign in, mailbox loading error in a particular browser, and older AOL Desktop gold. First, try to solve the error in AOL email and fix the missing screen problems. This issues can also be caused because of an invalid password. Try to enter the correct password to fix this problem.
AOL Mail Authentication Problem
The Blerk error 1 message occurs when there is an authentication problem. This issue is mostly due to the incorrect settings of the browser and can be mainly due to an outdated version of the browser. Fix this error by performing the AOL mail authentication problem troubleshooting steps below.
Step 1:First, try to modify the browser settings to fix aol login problems.
Step 2:Configure the settings on Edge and make sure to clear the data on Microsoft edge.
Step 3:Go to More Settings in Microsoft Edge.
Step 4:Now, click Choose What to Clear from the Clear Browsing data to solve AOL mail login issues.
Step 6:Tick the checkbox next to the data types that you want to delete and then choose Clear to fix AOL mail authentication problem.
Step 7:Next, make sure to update the saved bookmark on Safari, Firefox, Chrome, and Edge.
Step 8:Next, try to troubleshoot the Internet Explorer issues.
Step 9:First, try to add AOL to the trusted sites. To do so, click the Tools or Internet option to solve AOL mail authentication problem.
Step 10:Next, click Security tab Trusted Sites Zone Sites.
Step 11:Now, type https://*.aol.com in the Add this website to Zone field to solve aol login problems.
Step 12:Next, check whether the Protected Mode option is enabled, if not, perform the following steps to solve AOL mail login issues.
Step 13:First, click Tools Security tab Internet icon.
Step 14:Now, click the Trusted sites icon Enable Protected Mode. Restart the computer.
Step 15:Next, run the Internet Explorer in No Ad-ons Mode to solve AOL mail authentication problem.
Step 16:First, click the Start button All Programs Accessories System Tools Internet Explorer(No Ad-ons).
AOL Mail Can't Sign In
Most of the sign-in issues are caused by password issues, and this might also result in errors such as blank screens and sign in issues. Make sure to enter the correct password. To troubleshoot this issue, perform the following AOL mail can t sign in guidelines.
Step 1:First, try logging in again. Re-check if you have entered the correct credentials.
Step 2:If you are not able to sign in, try turning it off and then turning it on again.
Step 3:Next, make sure to reset the web settings to solve AOL mail can t sign in.
Step 4:Installing numerous browsers can cause the web settings to alter.
Step 5:Verify whether you have entered the correct password.
Step 6:If you have forgotten the password, make sure to reset the password.
Step 7:Try accessing the AOL mail from a different browser to solve AOL mail login issues, sometimes outdated password can cause this issue.
Step 8:Next, try to erase the browser’s cache and reset the browser to its preceding state.
Step 9:Make sure to enable the Java Applet Scripting.
Step 10:Disable or block the Firewall or the pop-up settings to fix AOL mail can t sign in.
Step 11:Now, try to access the AOL mail after performing all these troubleshooting steps.

AOL Mail Cannot Change Password
Perform the following guidelines to resolve this error.
Step 1:First, try to sign into the AOL account and choose the Logout from All Devices option from the Settings menu.
Step 2:Next, make sure you haven’t sent any contacts trough AOL mail. If you are sending any, contact Email Desktop Gold Support to fix the issue.
Step 3:Check if your credit card has been used without your knowledge. If so, block your account.
Step 4:Try logging into the AOL account after 24 hours.
Step 5:Try changing the password again.
Step 6:If the aol login problems persists, try to change the attached credit card with your account.
How Do I Unblock my AOL Email Account
Step 1:Navigate to the AOL Account Security page.
Step 2:Select the Forget Password option to unblock the AOL email account.
AOL Mail Password Not Working
Step 1:Check if you have pressed the Caps Lock key by mistake while you fix AOL mail login issues. You have to enter the password correctly.
Step 2:You have to update the autofill settings on the web browser. This will save the password when you enter it for the first time.
Step 3:If the problem persists, reset the password.
Step 4:Navigate to the Sign-in Helper option, and select any one of the recovery options.
Step 5:Select the Continue button and then follow the instructions that appear on the screen to reset the password.
How Do I Unblock my AOL Email Account
Step 1:Modify your AOL security question if you do not remember it to avoid aol login problems.
Step 2:Follow the forthcoming steps to change the question. Navigate to the Manage My Account tab available at the top part of the screen.
Step 3:Go to AOL Account Settings menu and select the Account Security Question option.
Step 4:Choose the Change Account Security Question option and fill the necessary details in the Change Account Security Question screen.
Step 5:Click the Save button, and you will be directed to the My Account Overview page.
Step 6:You can also reset your password by obtaining a code on your mobile and then resetting the security question if you are not able to log in.
AOL Mail Not Syncing
Step 1:First, remove the AOL account and add it after a few minutes.
Step 2:Choose the Settings option available in the Calendar app.
Step 3:Select the Manage Accounts option followed by the Delete an Account option.
Step 4:Next, you have to select the AOL account and delete it from your device to solve AOL mail login issues.
Step 5:Add your account after a few minutes and check if the issue has been resolved.
Step 6:Navigate to the Mailbox Sync Settings available under the Settings menu and verify the IMAP Username, Incoming Mail Server, SMTP Outgoing Server Address, Username, and Password.
Step 7:Modify the settings if required in the next step to fix AOL mail not syncing.
Step 8:Allow the apps that you have installed to access the calendar. Select the Privacy option available under the Settings menu.
Step 9:Choose the Calendar option and then click on the slider bar available below the Let Apps Access My Calendar option.
Step 10:Next, change the duration of the Sync period to solve the AOL mail not syncing issue. To do so, choose the Account Settings option available under Settings.
Step 11:Select the AOL Account followed by the AOL Sync Settings option. Modify the duration according to your choice.
Step 12:Check your Antivirus Settings and disable the firewall to rectify this AOL mail not syncing problem.
Step 13:Run the Windows troubleshooter and resolve the issue using the guidelines displayed.
Step 14:Disable the proxy settings in the next step. Select the Network & Internet option available under the Settings menu.
Step 15:Choose the Proxy option from the left panel of the window. Disable all the features available on the next screen.
Step 16:Finally, disable the two-step authentication. Make use of a different email client until the aol login problems is resolved.
Step 17:Uninstall the mail app and install it after a few minutes to resolve this issue.
Step 18:Call the technical experts if the above-stated AOL mail login issues solutions do not rectify the problem.
1 note
·
View note
Text
Visio Alternatives
At that point you can pick your security and confirmation alternatives: for additional data please check our article about SMTP arrangement. (Furthermore, obviously you can utilize additionally Alice's POP subtleties to get messages). Microsoft Visio Alternatives On the off chance that you have to send a mass email, in any case, recall that depending on a free SMTP administration like the one gave by Alice is unquestionably not the best decision. Above all else, you can run into conveyance issues as a free SMTP depends on shared IPs that don't ensure a full deliverability. Furthermore, Alice can set a confinement on the quantity of your active messages deflecting spammers, yet in addition keeping you from sending bulletins and authentic mass messages. On the off chance that you depend on turbo SMTP's expert active server, despite what might be expected, you will have the option to send boundless messages keeping the most elevated conveyance rate. In addition, regardless of whether it is close to home or business messages, utilizing turbo SMTP

you can generally check continuously if messages have been really conveyed, opened and if beneficiary has clicked one of the connections inside. This paper presents the aftereffects of an orderly survey of the writing, including a meta‐analysis, about the adequacy of the utilization of Alice programming in programming realizing when contrasted with the utilization of a customary programming language. Our exploration included investigations distributed between the years 2000 and 2014 in the fundamental databases. We assembled 232 papers. Considering the determination measures to make the meta‐analysis, we held six papers with a quasi‐experimental structure, with 464 members altogether. To consolidate the outcomes we utilized the arbitrary impact model. It brought about an impact size of 0.54 (Cohen's d) with a certainty interim somewhere in the range of 0.34 and 0.74. We presumed that as of recently there have been scarcely any exploratory outcomes on the adequacy of Alice programming language to acquaint understudies in figuring out how with program. The outcomes we discovered were the declaration of various test medications and recognized showing techniques which made the examination of the outcomes got increasingly unobtrusive.
In any case, the current trial results that were submitted to the meta‐analysis permitted us to accept with a specific edge of security that an instructing technique that utilizes Alice should get more powerful outcomes than the utilization of a customary programming language. Made by the German programming organization y Works, the yEd Graph Editor is without a doubt a standout amongst other free Microsoft Visio choices available. The representation programming is written in Java and depends on a few Open Course segments, for example, the Batik SVG Toolkit and XML Beans from Apache, or different libraries like dom4j and Twelve Monkeys (both under BSD permit). Be that as it may, it isn't distributed under a free permit, which means the source code can't be changed. However, y Works has made the cross-stage editorial manager, which is appropriate for Windows, MacOS, Linux, and the Java Runtime Environment accessible for utilize for nothing out of pocket.
1 note
·
View note
Photo

In this video tutorial, you will learn how to send email using Java in NetBeans. You can use this application as "Forgot Email" form i.e. for sending password through email to the users who have forgotten their passwords. In this video, you will learn to send email using ssl, java ssl, and send email to gmail using java program. That is, you will learn to using smtp of gmail, java - send email, smtp.gmail.com and transport to send mail. Step by step the video explains the mail sending in java, how to send mail in java, send an email using java and about the mail.jar. You will find the full code for send email in java, sendmail aplication, how to send mail using java and how to create sendmail application in java easily. After this video you will know how to send an email using java mail api in a java web application, how to send an email through a java application using java mail api ? and email in java along with java send email. If you are looking for java email using gmail, send email using java j2ee, how to send an email using java mail api in a java web application ?, java email example and java email tutorial, then this video is for you. This java tutorial for beginners teaches you how to send mail using java without authentication, send mail using java smtp, send mail using java netbeans, send mail using java localhost, javamail tutorial, java code to send email, java mailing system, desktop sending email application, how to send email using java and using java to send a email along with javamail api. You can download the program from the following link: http://bmharwani.com/ForgotPasswordAp... To see the video of inserting rows into MySQL, visit: https://www.youtube.com/watch?v=tHFUe... To see video on creating a Sign In Form in Java, visit: https://www.youtube.com/watch?v=XyPf8... For more videos on Java Swing, visit: https://www.youtube.com/watch?v=tHFUe... To get notification for latest videos uploaded, subscribe to my channel: https://youtube.com/c/bintuharwani To see more videos on different computer subjects, visit: http://bmharwani.com
#javamail#send email using java#java mail api#smtp#send email using java program#how to send email in java#mailing through java#send mail using java gmail#send email using java example#send email using java api#send email using java smtp#send email using java code gmail#send email using java netbeans#send email using java code example#java email#java mail 1.4#how to send email in java program#send java email using java api#write a java program to send email#bintu harwani
0 notes
Text
WEB SERVICES TESTING - H2kinfosys
Web services testing with SOAP:
click here to read first part
Web services testing is a way to access the web services using XML messages that include WSDL catalog listing web services with their name, input and output field parameter details which serve as an ideal testing road map. It is well suited for performing transactions that have multiple calls need to enforce the strict client server contract and works well with the distributed enterprise environments. It is highly structured with error handling security built-in is designed for expansion for expansion and can use transport protocols besides HTTP.
For example:
A simple account management and order processing system. The accounting personnel will use a client application system which is built in Visual Basic. The processing logic of this system is developed in java and has a database which interacts to store information.
The following steps to do the web services testing are:
The client collects and feeds the information of account registration into the SOAP message.
This SOAP message is sent to the web service in HTTP post request.
The web service will convert the SOAP request message to the command that the application will understand.
The information is processed by the application as required and responds with new unique account number of any customer.
The next process is the web service response another SOAP message Which sends to the client message in response to the HTTP request.
The web service testing tools are :
SOAP UI:
SOAP UI is one of the tools to test the web services which are used to design web services test of SOAP and REST architectures. SOAP UI allows the creation and execution of different types of software testing like: Functional test, regression tests, Mocking, load and performance tests and security evaluation.
2. JMeter:
Apache JMeter is an open-source application which is designed for the execution of load tests performance measurements in applications. JMeter has capabilities to perform load testing and performance testing in different application servers and protocols including
Web (HTTP,HTTPS)
SOAP /REST web services
FTP services
Database through JDBC
LDAP directory services
Message-oriented middleware, through JMS
EMAIL-SMTP,POP(3) and IMAP(S)
Questions:
What are Web services?
What is Web service Testing?
What are the goals of Web services Testing?
Visit: https://www.h2kinfosys.com/blog/web-services-testing/
Call: 7707771269
Email:[email protected]
1 note
·
View note
Photo
Jenkins:- Jenkins is an open-source non-stop integration server written in java for orchestrating a sequence of actions to attain the continuous integration technique in an automated style. Jenkins helps the complete improvement lifestyles cycle of software program from constructing, testing, documenting the software program, deploying, and different stages of the software improvement existence cycle. Jenkins Email Notification:- Jenkins Email Notifications are the way to notify based on an event that occurred or some action that happened. Jenkins email notifications are the kind of message that is automatically sent to you and update that, there has been activity on one of your social media accounts like Google, slack. As email is the primary means of notification among other social media for Jenkins email notifications. Jenkins provided a plugin to extend the functionality of e-mail notifications. It’s informing the user about some event or status or any information that needs to be updated to their concerned users.
3 parts of Jenkins Email Notification Given below are the 3 parts of Jenkins email notification:
Triggers: This is a defined condition that causes an e-mail notification to be sent. Content: Defined content for email subject and body. Recipients: We can mention the concerned user who is supposed to receive an e-mail when an event occurred. Use Case of Jenkins Email Notification Any organization follows the DevOps practice and configured Jenkins as part of their build process. DevOps team wants to configure a process and as part of the process to send an automated email to the Developers team if any build failure with the help of freestyle configurations. To send and receive emails we need to configure email servers in Jenkins. Basically in an organization, they have their email servers that are used to trigger. Emails, in our example we do not have our server, so we are going to use a Gmail SMTP server.
0 notes
Text
Top Linux Training Institute In Noida , Delhi

Professions or new contestants in its field or PCs will observe Inovi Technologies to be extraordinary compared to other Top Linux Training Institutes in Noida , Delhi. The company offers Linux Training in Noida for both, amateurs and propelled experts with the goal that they can motivate Red Hat Certification to advance in their vocations. Inovi Technologies is a Red Hat Training Partner, which shapes our establishment to offer the Best Linux Training in Noida. This is a top to bottom Training Course that gives all of you the aptitudes required for filling in as a Linux Administrator. You will find out about the Red Hat System, establishment, dealing with the boot forms, performing different tasks, understanding Linux Kernel, testing and troubleshooting. Inovi Technologies offers a comprehensive Linux Training in Noida. The broad down to earth preparing given by Linux preparing organization in Noida. prepares live tasks and reproductions. Such point by point Linux course has helped our understudies secure occupation in different MNCs. We provide Many Courses the Trainers at Inovi Technologies are subject authority corporate experts giving inside and out investigation in Linux course in Noida. Members finishing the Linux confirmation have plenty of openings for work in the business. Visit here: https://www.inovitechnologies.com/
Linux Installation and Initialization (Automated)
Different Linux establishments, mechanized establishment utilizing Kick begin, sending it utilizing web server, establishment media and Kick begin setup records.
Bundle Management and Process observing
Linux Package which is Pre-fabricated arrangement of projects, establishment of Packages, its libraries and the conditions, understanding the low-level and abnormal states apparatuses required, designing Linux Yum Server, understanding the Yum archive Server-Client framework.
Administrations, Utilities, Important Files and Directories
Profound plunge into Linux Services, the imperative framework documents, utilities, registries.
Understanding SystemD
Finding out about SystemD, the Linux-explicit framework and administration supervisor, understanding what are the projects that run when Linux loads, acclimating with the systemctl directions.
Linux User Administration
Linux client the board, gatherings, qualities and document consents, allowing authorization dependent on assignments to be performed, different propelled client organization highlights, setting client and gathering plate space portions, Linux record framework quantities.
Record System Management (Generic and LVM)
Dealing with the Linux File System, understanding the Logical Volume Management, dispensing circles, stripping, reflecting, resizing, coherent volumes, sending LVM for setting hard plates for physical volumes.
Propelled File System Management (Software RAID)
Understanding the idea of RAID information stockpiling virtualization, the RAID programming the executives device, finding out about Linux Kernel with RAID Support, actualizing the product RAID in Linux.
Server-Client Configurations (FTP/SFTP/HTTP)
Finding out about the Server Configuration in Linux, the FTP/SFTP, the HTTP Server/Client Systems setup.
Designing Samba And SMTP
Understanding the Samba Open Source device, the Simple Mail Transfer Protocol, arranging the Samba Server and SMTP with Linux.
Firewall and IP Tables
Understanding the nuts and bolts of firewall in Linux, sending the firewall and iptables in Linux which is a standard based firewall framework in Linux, testing the firewall rules.
Database Configuration (MySQL/Mariadb)
Seeing how to design databases in Linux, functioning with MySQL database and MariaDB database for arranging it with Linux.
Utilizing Control Panels To Manage Linux Servers (Webmin)
Finding out about the different control boards in Linux, its different uses and applications in different administrations, conveying of these control boards to deal with the Linux servers.
Our More Course Are:
1. Devops
2. Data Scientist
3. Python
4. JAVA
5. AWS
6. MEAN Stack
7.RPA(Robotic Process Automation)
8. Salesforce
9. Linux
Mobile No. 8810643463, 9354482334
Phone No. 91-120-4213880
Email- [email protected]
Address. F7 Sector-3 Noida UP 201301 India.
1 note
·
View note
Text
Client For Postgresql Mac

Advertisement
Email Effects X v.1.6.9Email Effects X 1.6.9 is a useful program specially designed for the Mac OS or Windows 95/98/NT for getting the most out of email. With it, you can send pictures, drawings and tables with simple plain text. It is also the world's premier ASCII art ..
JaMOOka v.2.01JaMOOka is an applet-based MOO client. Designed for JHCore MOOs, it uses Amy Bruckman's MacMOOse utilities and the MCP 2.1 protocol to facilitate a number of advanced MOO editing and programming tasks through client ..
Sesame Windows Client v.1.0A Windows GUI application for RDF. SWC is a client tool for a Sesame 2 RDF server or SPARQL endpoint, and can be used as a out-of-the-box local triplestore. It offers advanced SPARQL querying and handles Sesame server administrative tasks.
Microsoft Remote Desktop Connection Client v.2.0 Beta 3Remote Desktop Connection Client for Mac 2 lets you connect from your Macintosh computer to a Windows-based computer or to multiple Windows-based computers at the same time. After you have connected, you can work with applications and files on the ..
Citrix ICA Client v.10.00.603Citrix ICA Client 10.00.603 is a communication tool which can help users access any Windows-based application running on the server. All the user needs is a low-bandwidth connection (21kilobytes) and the ICA client, which is downloadable free from ..
VPN-X Client for Mac OS v.2.4.1.44VPN-X:Java/ Cross-platform P2P/SSL/TLS VPN solution. Client has an individual Virtual IP Address.It can help employees on errands use company LAN resource, help your friends access your computer play LAN games, all the network data is encrypted and ..
Imperial Realms Standard Client v.0.4.1imperial_realms is the standard client for the Imperial Realms multi-player online strategy game. It is open-source and runs on Windows, Linux and other operating ..
Mahogany mail and news client v.0.67An extremely configurable portable GUI email and news client for Windows/Unix (including OS X) with IMAP, POP3, SMTP, and NNTP support, SSL, flexible address database, Python scripting, powerful filtering, and many other features for advanced ..
Mud Magic Client v.1.9OpenSource mud client designed to work on both windows,linux and MAC OS X. Written in Gtk+ and C with SQLLite, Python, MSP, MXP, HTML, and ZMP support. Provides plugin support, automapper functionality, triggers, aliases and ..
STUN Client and Server v.0.97This project implements a simple STUN server and client on Windows, Linux, and Solaris. The STUN protocol (Simple Traversal of UDP through NATs) is described in the IETF RFC 3489, available at ..
Scalable Java Database Client v.1.0The scalable Java DB Client is a customizable java application where fields and general DB info is entered in a config file and the proper GUI is generated at run-time. Entries can then be added, and a final submit/update to the (PostgreSQL/MySQL) ..
Vicomsoft FTP Client v.4.6.0FTP Client 4.6 represents the culmination of over 10 years experience in FTP transfers on the Mac platform. Extreme performance and unrivaled reliability, married with a sleek and intuitive user interface is the result.
Windows 7 Utilities v.7.54Windows 7 Utilities Suite is an award winning collection of tools to optimize and speedup your system performance.
Windows 7 Cleaner v.4.56Windows 7 Cleaner suite is an award winning collection of tools to optimize and speedup your system performance. this Windows 7 Cleaner suite contains utilities to clean registry, temporary files on your disks, erase your application and internet ..
Windows 7 Optimizer v.4.56Windows 7 Optimizer can quickly make your Windows 7 operating system (both 32 bit and 64 bit) faster, easier to use, and more secure. And all operations performed on the operating system are completely safe, because all changes are monitored by ..
Windows 7 System Optimizer v.6.0Windows 7 system optimizer: this is a multi-functional system performance and optimization suite for Windows 7. This collection of tools lets you supercharge your PC's performance, enhance its security, tweak and optimize its settings, and customize ..
Windows 7 System Suite v.6.3Slow down, freeze, crash, and security threats are over. Windows 7 system suite is a comprehensive PC care utility that takes a one-click approach to help protect, repair, and optimize your computer. It provides an all-in-one and super convenient ..
Windows System Suite v.6.1Windows System Suite is power package All-in-one application for cleaning, tuning, optimizing, and fixing PC errors for high performance. Direct access to a wealth of Windows configuration and performance settings many of them difficult or impossible ..
Windows XP Cleaner v.7.0Windows XP Cleaner is a suite of tools to clean your system; it includes Disk Cleaner, Registry Cleaner, History Cleaner, BHO Remover, Duplicate files Cleaner and Startup Cleaner. this Windows XP Cleaner suite allows you to remove unneeded files and ..
Icons for Windows 7 and Vista v.2013.1Icons for Windows 7 and Vista is an ultimately comprehensive collection of top-quality interface icons that will be a perfect fit for any modern website, online service, mobile or desktop application.
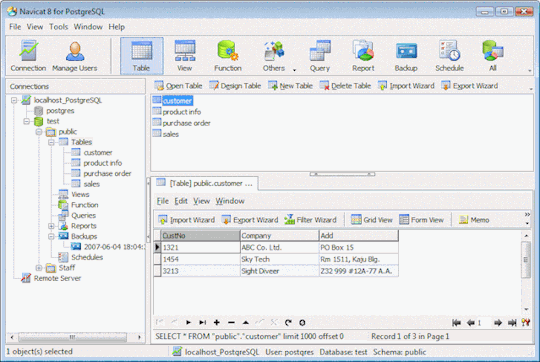
GUI Client Apps. There are many clients for PostgreSQL on the Mac. You can find many of them in the Community Guide to PostgreSQL GUI Tools in the PostgreSQL wiki. Some of them are quite powerful; some are still a bit rough. Postgres.app is a simple, native macOS app that runs in the menubar without the need of an installer. Open the app, and you have a PostgreSQL server ready and awaiting new connections. Close the app, and the server shuts down. How To Install Postgresql On Mac. I started off programming Ruby on Rails applications on a Windows machine with an Ubuntu virtual machine running on top. But when I got my first job at a startup in California, I received a brand new shiny Macbook laptop.
Download CCleaner for free. Clean your PC of temporary files, tracking cookies and browser junk! Get the latest version here. CCleaner is the number-one tool for fixing a slow Mac Download Ccleaner Mac for free and enjoy! Download Ccleaner Mac. Ccleaner for Mac. Mac running slow? A Mac collects junk and unused files just like a PC. Find and remove these files with the click of a button so your Mac can run faster. Speed up boot times with easy management of Startup items. CCleaner for Mac! Clean up your Mac and keep your browsing behaviour private with CCleaner, the world's favourite computer cleaning tool. Introducing CCleaner for Mac - Learn about the basics of CCleaner for Mac, and what it can do for you. Using CCleaner for Mac - Find out how to run every aspect of CCleaner for Mac. CCleaner for Mac Rules - Explore what each option in the Mac OS X and Applications tabs and how you can customize it to fit your needs. CCleaner for Mac Settings - Learn about CCleaner for Mac's other options. Ccleaner for mac 10.6.8. Download CCleaner for Mac 1.17.603 for Mac. Fast downloads of the latest free software!
Postgresql Client Windows software by TitlePopularityFreewareLinuxMac
Sequel Pro Postgres
Today's Top Ten Downloads for Postgresql Client Windows

Mac Install Postgresql
Citrix ICA Client Citrix ICA Client 10.00.603 is a communication tool which
Folx torrent client With Folx torrent client downloading and creating torrents
Windows 7 System Suite Slow down, freeze, crash, and security threats are over.
Windows XP Cleaner Windows XP Cleaner is a suite of tools to clean your
Windows 7 Utilities Windows 7 Utilities Suite is an award winning collection
Icons for Windows 7 and Vista Icons for Windows 7 and Vista is an ultimately
Windows 7 System Optimizer Windows 7 system optimizer: this is a multi-functional
VanDyke ClientPack for Windows and UNIX VanDyke ClientPack is a suite of tools for securely
VPN-X Client for Mac OS VPN-X:Java/ Cross-platform P2P/SSL/TLS VPN solution. Client
Windows Desktop Icons High quality professional royalty-free stock windows
Best Postgresql Client For Mac
Postico For Windows
Visit HotFiles@Winsite for more of the top downloads here at WinSite!

0 notes
Link
You wake up one morning to have your cup of coffee and voilà, the Eureka moment is here. You finally figured out your business model, and it all falls into place. You know investors will love it, and you just can't wait to start building the product. The first mover advantage is yours to take.
These moments are rare, but when they happen you need to jumpstart at the right time. All you need is the right guide to help you figure out what you should and shouldn't do. This isn't a time to experiment, it's the time to execute. It's YOUR time now!
NOTE - The following is related to building software architectures from scratch. So if you are interested in knowing the nitty-gritty of the technologies involved, then proceed. Otherwise, please share with those who will definitely love this :P
Where this guide came from
I have myself worked on a handful of early stage products, and to be honest, I did make mistakes. I always wished there was a checklist to follow while building a product from the ground up.
There are so many things involved in building an architecture from scratch that you will totally forget certain pieces. And they will come back to bite you in later stages of the product cycle.
I finally decided to create this checklist of things that you should consider before hitting that deploy button for the first time.
So without further build-up, here's the checklist you should go through while building a Backend Architecture for a product from scratch.
Choose the CORRECT language and framework (for your project)
Choosing the correct language and framework for your product is tricky, and there's no particular silver bullet for this. My advice is to choose a language you are most comfortable with and know the intricacies of in and out.
Having said this, it's rare, because there are very few people who are Javascript Ninjas, or Python Panthers, or whatever funky names are out there.
So choose a language that has some real good support in the industry, like Javascript, Python, Java, or Go to name a few. You can choose any language, just pick which one is most comfortable for you.
And remember – you are building an MVP (Minimum Viable Product), and will be in the process of creating a POC (Proof of Concept). So get your product out as soon as possible. You don't need to get stuck on issues that might come from the new language in town. To avoid those issues, choose a more widely used, well-documented language.
Lastly, you can scale at a later time. If you are in the phase of doing POCs, just build and get it done. But if you are building something really specific, and there's a language and a framework build especially for that, then you should definitely chose that tech.
But most of the time, the problems we are trying to solve can be easily taken care of with any of the above mentioned languages and their respective frameworks. So just choose one and kickstart your product.
A good resource to help you decide -
https://content.techgig.com/top-5-programming-languages-for-backend-web-development/articleshow/67337449.cms
Implement authentication and authorisation microservices
There are a lot of ways to authenticate and authorise a user. You could try Session Tokens, JWT (JSON Web Tokens), or OAuth, to name a few. Every option has it's own pros and cons. So let's look at some of them more closely.
JSON Web Tokens
JWTs are fast and easy to implement. This is because the tokens are never stored anywhere on your system. They are just encoded, encrypted, and sent to the user. So validating a JWT is faster than any other method.
But then, since they are not stored on the system, you can't actually make a token expire before its actual expiration time, and this can be an issue in certain cases.
So figure out the pros and cons of each authentication system and choose the one that best suits your requirements. I personally prefer JWTs (but that's my own choice).
Authorization
Never forget to implement authorisation of users. You don't want logged in User1 to change the details of User2. This can cause pure chaos in your system.
Identify the endpoints that need authorisation, and implement them right away. You don't want the state of your database to be corrupted like this. Remember the difference between 401 and 403.
The following are certain end points you should definitely consider while creating your Authentication system (I created one in Django using JWT). There can be certain additions/deletions for your use case, but these are the ones you should consider building.
A lot of frameworks provide them out of the box, but do consider them before building them on your own. Check authentication_classes and permission_classes in the Django Rest Framework for further reference.
Have a look at this Django REST Framework resource -
https://www.django-rest-framework.org/tutorial/4-authentication-and-permissions/

Create an abstract base model to be inherited by every other model in your database
Remember the DRY Principle - Don't Repeat Yourself? It should be followed to the core in Software Engineering.
Building on the above thought process, there will be certain columns in your database which will be present in every table. Therefore it's better to create an abstract class for them so that other Model Classes can inherit from them.

Let's go through this code and what it means:
id - Though it is not written here, it is automatically created by the Django framework. But if it is not there in yours, write it down in this class. It's just an auto incremented field which can be used as a Primary Key in your database relation.
created_at - This implies when the field/row was inserted into your table, and it's filled by the framework itself. You don't need to set it explicitly.
updated_at - This implies when the field/row was last modified/updated in your table, and again it's filled by the framework itself.
deleted_at + is_deleted - So this is a controversial field. I don't have an exact answer as to whether it should be there or not – because to be honest, nothing on the internet is ever deleted. This field, if filled, depicts that the row is deleted from the system (though the data remains in the system for future references and can be taken off from the database and stored in backups)
uuid - It depends whether you want to put this in your table or not. If you need to expose the Primary key of your table to an outside system, it's better to expose this one rather than the auto incremented integer field. You might wonder why...? Well, why would you want to tell an outside system that you have 10378 orders in your table? But again it's a personal choice.
Set up a notification microservice
Every product needs to send Reminders and Notifications to the user for engagement and transactional purposes. So every product will need this.
You should definitely consider building a Microservice that provides Notification services (like Push Notification, Emails, and SMS) to your end users.
This should be a separate Microservice altogether. Don't build this inside your Authentication Microservice or your Application Service (the actual Business Logic).
There are a lot of third party libraries/services that can be used to build it for your application. Leverage them and build it on top of that.
Remember to build all the 3 functionalities:
Push Notifications (APNS + FCM),
Emails (just integrate an SMTP client for starting)
and SMS
NOTE - Have two channels for sending SMS, transactional and promotional. Never send a promotional SMS on a transactional channel, as there are chances that you will be sued by a well informed and motivated user.
An easy way to configure your SMTP client in your application is using this in your settings:
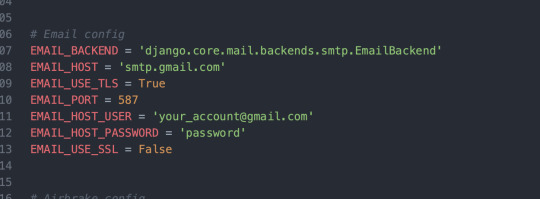
I did this in Django, but you can do the same in your chosen language and framework.
Set up error logging
Use a middleware to log errors that occur on your production system. Your production system will not be monitored by humans sitting there to see the application logs 24/7. So you will need a system that will log those Internal Server Errors in a central place. Then you can go and check them on a daily basis or create a webhook so that you can be alerted at the right time and take care of them.
There are a lot of 3rd party error logging tools in the market. Just choose any one that suits your requirements. I mostly use Sentry/Airbrake.
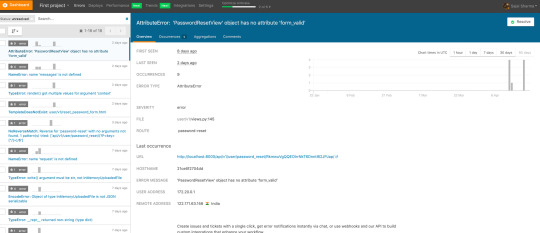
Consider configuring webhooks, as I mentioned above. They will inform your users about errors and, for example, you can post those errors as and when they occur on certain slack channels. Then you can check those channels on a regular basis and rectify them on the basis of their severity.
Airbrake's official home page - https://airbrake.io/
Sentry's official home page - https://sentry.io/welcome/
Implement request - response and application logging
Scenario - A user comes on your support and says that they haven't received the Transactional Receipt for the purchase they made on your website. What will you do?
If you have put Application Logging in your system, then worry not. Now what do I mean by that? It's always better to show an example than trying to explain with words. So here it is:

I have logged that I am about to send the email to the mentioned email_id. I can check in the application logs to see if the email was actually sent to the client by checking if such a log exists in the system. Make sure to put comprehensive logs in your system so that you can trace the request's journey.
Additionally, it's a good idea to put an async system in place that will pick out such request-response and application logs from your system and dump them in a central place. There they can be processed to be more easily interpretable.
The ELK stack is a good option for this: ElasticSearch - Logstash - Kibana.
More about the ELK stack - https://www.elastic.co/what-is/elk-stack
NOTE - While logging request and responses, take care of the following:
Do not log passwords.
Do not log tokens (the access tokens which are used for Authentication)
Do not log OTPs
Introduce throttling in your APIs and rate limiting on your application servers
Scenario - You have just launched your service and have marketed the product on social media platforms. A black hat hacker found out, and just wanted to play with your system. So they planned a DOS (Denial of Service) attack on your system.
To combat this, you can set rate limiting based on various factors on top of your load balancers for your application servers. This will take care of DOS attacks and prevent the malicious user from attacking your servers.
Scenario - The API endpoint /otp/validate that takes 4 digit OTPs for authenticating the user and gives back tokens to be used for Authenticated APIs. A malicious user gets the mobile_number for one of your clients, and starts hitting the API endpoint with brute force attack changing the IPs, a DDOS (Distributed Denial of Service) Attack. The rate limiter is not able to stop the user, because the IP keeps on changing with every request made.
To stop this, you can put a throttling on the APIs based on the user as well. You can configure how many requests can be made by a particular user to an API endpoint. For OTP validation, a good number is 5 requests per 10 mins. This will stop the malicious user from performing a brute force DDOS attack on the above API.
Throttling in Django's REST Framework -
https://www.django-rest-framework.org/api-guide/throttling/
Establish and configure asynchronous communication from day one
Scenario - You need to send a welcome email to the user when they register on your application. The front end client hits the Register API, you create the user in the backend after validations, and this starts the process of sending a welcome email.
Sending this welcome email will take time, maybe few seconds. But why would you want the mobile client to be stuck for such a process? This can happen in the background without the user being stuck for no particular reason on the Register page. Every second is precious and you don't want the user to lose those precious seconds.
So just send the email via an Asynchronous task. Use workers, tasks, message brokers and result back ends to perform this.
One good example of this from the Python world is Celery worker. Just put the task that needs to be performed in a message broker (Rabbit MQ/SQS, etc). Celery will listen to this and will send the task to the designated worker. That worker will then process the request and put the result in a result backend which can be a Cache system/database system. (Redis/PostgreSQL for example).
You can monitor these tasks and queues with a lot of third party libraries. A good example of this is Celery Flower which monitors all of this.

You can read more about RabbitMQ here - https://www.rabbitmq.com/
And Celery - https://docs.celeryproject.org/en/stable/django/first-steps-with-django.html
And finally, Celery Flower - https://flower.readthedocs.io/en/latest/
Set up cron jobs
Scenario - You just launched your product and you need to send recommendations to your users about new products on your platform. You'll send these on the basis of their purchase history each weekend.
The above task can be easily performed using a cron job. It is easily configurable in every framework. The important thing to bear in mind is that you should not put the cron jobs directly in the crontab file of your server. You should let the framework handle it.
This is because the deployment engineer/Devops engineer should be the only person to have access to the system like this for security reasons. Although you don't have to implement it this way it's a good to have thing from the beginning.
In the Django world, you can use celerybeat to configure your crons using celery workers.
Learn more about Celery Beat here -https://docs.celeryproject.org/en/latest/userguide/periodic-tasks.html
Manage your secrets properly (parameters file)
There are a lot of ways to manage parameter secrets in your production servers. Some of them are:
Creating a secrets file and storing it in a private s3 bucket, and pulling the same during deployment of your application.
Setting the parameters in environment variables during deployment of your application (storing them in s3 again)
Putting the secrets in some secret management service (e.g. https://aws.amazon.com/secrets-manager/), and using them to get the secrets in your application.
You can chose any of these methods according to your comfort and use case. (You can choose to keep different secret files for local, staging and production environments as well.)
Version your APIs from day one
This is something that you should definitely consider from Day 1. You will never know how frequently your business models might change, and you need to have forward-backward compatibility in your application. So you should version your APIs to ensure everything runs smoothly for everyone.
You can have different apps for different versions and let nginx handle it for your application. Or you can have versioning in the application itself, and let the routes in your application server handle it. You can choose any method to implement it – the main point is to have versioning enabled from the start.
Decide on hard and soft update version checks for your front end clients
So what's the difference between hard and soft updates?
Hard updates refer to when the user is forced to update the client version to a higher version number than what is installed on their mobile.
Soft updates refer to when the user is shown a prompt that a new version is available and they can update their app to the new version if they want to.
Hard updates are not encouraged, but there are times when you need to enforce them. Whatever the case you should definitely consider how you are going to implement this for your applications.
You can do this by implementing or configuring it in the Play Store or App Store. Another way is to create an API in your backend application that will be hit every time the mobile app is launched. This will send two keys: hard_update -> true/false and soft_update -> true/false, depending upon the user's version and the hard and soft update versions set in your backend system.
A good place to store these versions is in your cache (Redis/Memcache), which you can change on the fly without needing to deploy your application.
Introduce continuous integration (CI) from day one
Scenario – one of the interns working in your project isn't proficient enough to write production level code. They may have changed something that might break some critical component in your project. How can you ensure that everything is ok in such cases?
Introduce continuous integration. It will run linters and test cases on each commit, and will break if any rules are violated. This will in turn block pull request from getting merged until all linting rules and test cases pass. It's a nice to have thing, and it actually helps in long run as well, so keep it in mind.
There are a lot of options available in the market. You can either chose to implement one on your own (Jenkins CI/CD), or you can use TravisCI, CircleCI, etc for the same.
Read up on TravisCI here - https://travis-ci.org/
And CircleCI - https://circleci.com/
Enable Docker support (personal preference)
Create a Dockerfile and docker-compose.yml for your application so that everyone runs the application using Docker from the start. One of the main reasons to use such an approach is to have consistency across your local/staging/production environment, so that no developer can ever say this again:
But it ran on my machine.
It's not difficult to employ it from day 1. In the beginning just use Docker for your local environment so that the setup of your application can be really smooth. But keep in mind how you can run it both with and without Docker in production.
Here's more info about Docker Hub - https://hub.docker.com/
Use an APM tool
An Application Monitoring Tool is a must have if you want to monitor your application's APIs, transactions, database connections, and so on.
Scenario - your cron server's hard disc is almost full and it is not able to run cron jobs. Since it can't find space on the disc, your crons are not running. So how can you get notified when this happens?
There are a lot of APM tools that you can use to monitor this. You can configure them according to when you need to be notified. You will get notifications on the medium of your choice when such chaos happens on your system – and trust me it happens all the time. So better be prepared for it. New Relic is a good option.

Read more about New Relic here - https://newrelic.com/
Use ElasticSearch to power application-wide searches in your client apps
According to wikipedia,
Elasticsearch is a search engine based on the Lucene library. It provides a distributed, multitenant-capable full-text search engine with an HTTP web interface and schema-free JSON documents. Elasticsearch is developed in Java.
In the beginning, you will be tempted to use traditional database queries to get results in that search bar for the client app. Why? Because it's easy.
But traditional databases are not meant for such performant queries. Figure out a good time to migrate your search to ElasticSearch and introduce a data pipeline into your system. It feeds the elastic search with data and then connects the search from ElasticSearch to the application server.
Here's a good overview of Elasticsearch to get you started.
And the ElasticSearch Docs - https://www.elastic.co/guide/index.html
Put a firewall in your production server
You should definitely do this - it's a must-have. Put a firewall in your production server and close all the ports except the ones to be used for APIs (https connections). Route the API endpoints using a reverse proxy web server, like NGiNX or Apache. No port should be accessible to the outside world other than the ones allowed by NGiNX.
Why you should use NGiNX:
https://www.nginx.com/resources/wiki/community/why_use_it/
https://blog.serverdensity.com/why-we-use-nginx/
https://www.freecodecamp.org/news/an-introduction-to-nginx-for-developers-62179b6a458f/
Wrapping up
The above mentioned points are based off my own preferences and I've developed them over the years. There will be slight differences here and there, but the concepts remain the same.
And in the end we do all this to have a smooth system built from scratch running in production as soon as possible after you've come up with the idea.
I tried penning down all my knowledge that I have acquired over the years, and I might be wrong in a few places. If you think you can offer better info, please feel free to comment. And as always please share if you think this is helpful.
0 notes
Text
300+ TOP AWS Interview Questions and Answers
AWS Interview Questions for freshers experienced :-
1. What is Amazon Web Services? AWS stands for Amazon Web Services, which is a cloud computing platform. It is designed in such a way that it provides cloud services in the form of small building blocks, and these blocks help create and deploy various types of applications in the cloud. These sequences of small blocks are integrated to deliver the services in a highly scalable manner. 2. What are the Main Components of AWS? The Key Components of AWS are: Simple Email Service: It allows you to send emails with the help of regular SMTP or by using a restful API call Route 53: It’s a DNS web service. Simple Storage Device S3: It is a widely used storage device service in AWS Identity and Access Management Elastic compute cloud( EC2): It acts as an on-demand computing resource for hosting applications. EC2 is very helpful in time of uncertain workloads. Elastic Block Store: It allows you to store constant volumes of data which is integrated with EC2 and enable you to data persist. Cloud watch: It allows you to watch the critical areas of the AWS with which you can even set a reminder for troubleshooting. 3. What S3 is all about? S3 is the abbreviation for a simple storage service. It is used for storing and retrieving data at any time and anywhere on the web. S3 makes web-scale computing easier for developers. The payment mode of S3 is available on a pay as you go basis. 4. What is AMI? It stands for Amazon Machine Image. The AMI contains essential information required to launch an instance, and it is a copy of AMI running in the cloud. You can download as many examples as possible from multiple AIMs. 5. What is the relationship between an instance and AMI? Using a single AMI, you can download as many instances as you can. An instance type is used to define the hardware of the host computer for your situation. Each instance is unique and provides the facilities in computational and storage capabilities. Once you install an instance, it looks similar to a traditional host with which we can interact in the same way we do with a computer. 6. What are the things that are included in the AIM? An AIM consists of the things which are mentioned below: A template for the instance Launch permissions A block mapping which decides the volume to be attached when it gets launched. 7. What is an EIP? The Elastic IP address (EIP) is a static Ipv4 address offered by AWS to manage dynamic cloud computing services. Connect your AWS account with EIP so that if you want static IPv4 address for your instance, you can be associated with the EIP which enables communication with the internet. 8. What is CloudFront? CloudFront is a content delivery network offered by AWS, and it speeds up the distribution of dynamic and static web content such as .css, .js, .html and image files to the users. It delivers the content with low latency and high transfer speed to the users. AWS provides CDN for less price and it suits best for startups. 9. What is VPC? Virtual Private Cloud (VPC) allows you to launch AWS resources into the virtual network. It allows users to create and customize network configurations according to users’ business requirements. 10. What is the VPC peering connection? VPC peering connection VPC peering connection is a networking connection that allows connecting one VPC with the other. It enables the route traffic between two VPCs using IPv6 and Ipv4 addresses. Instances within the VPCs behave like as they are in the same network.

AWS Interview Questions 11. What is the procedure to send a request to Amazon S3? S3 in Amazon is a RESt service, and you can send requests by using the AWS SDK or REST API wrapper libraries. 12. What are NAT gateways? Network Address Translation (NAT. allows instances to connect in a private subnet with the internet and other AWS services. NAT prevents the internet to have an initial connection with the instances. 13. What is SNS? Amazon Simple Notification Service (SNS)is a web service provided by the AWS. It manages and delivers the messages or notifications to the users and clients from any cloud platform. In SNS, there are two types of clients: subscribers and publishers. Publishers produce and send a message to the subscriber instance through the communication channels. Subscribers receive the notification from the publisher over one of the supported protocols such as Amazon SQS, HTTP, and Lambda, etc. Amazon SNS automatically triggers the service and sends an email with a message that “ your EC2 instance is growing” when you are using Auto Scaling. 14. What is SQS? Amazon SQS stands for Simple Queue Service, and it manages the message queue service. Using this service, you can move the data or message from one application to another even though it is not in the running or active state. SQS sends messages between multiple services, including S3, DynamoDB, EC2 Instance, and also it uses the Java message queue service to delivery the information. The maximum visibility timeout of a message is 12 hours in the SQS queue. 15. What are the types of queues in SQS? There are two types of queues in SQS. They are as follows: Standard Queues: It is a default queue type. It provides an unlimited number of transactions per second and at least once message delivery option. FIFO Queues: FIFO queues are designed to ensure that the order of messages is received and sent is strictly preserved as in the exact order that they sent. 16. Explain the types of instances available? Below stated are the available instances: General-purpose Storage optimized Accelerated computing Computer-optimized Memory-optimized 17. Explain about DynamoDB? If you want to have a faster and flexible NoSQL database, then the right thing available is DynamoDB, which is a flexible and efficient database model available in Amazon web services. 18. What is Glacier? Amazon Glacier is one of the most important services provided by AWS. The Glacier is an online web storage service that provides you with low cost and effective storage with security features for archival and data backup. With Glacier, you can store the information effectively for months, years, or even decades. 19. What is Redshift? Redshift is a big data product used as a data warehouse in the cloud. It is the fast, reliable and powerful product of big data warehouse. 20. What are the Types of AMI Provided by AWS? Below listed are the two kinds of AMIs provided by AWS: EBS backed Instance store backed Till now, you have seen basic interview questions. Now, we will move to the Intermediate Questions. 21. What is an ELB? Elastic Load Balancer is a load balancing service offered by AWS. It distributes incoming resources and controls the application traffic to meet traffic demands. 22. What are the types of load balancers in EC2? There are three types of load balancers in EC2. They are as follows: Subscribe to our youtube channel to get new updates..! Application Load Balancer: Application load balancer designed to make routing decisions at the application layer. ALC supports dynamic host port mapping and path-based routings. Network Load Balancer: Network load balancer is designed to make routing decisions at the transport layer. It handles millions of requests per second. Using the flow hash routing algorithm, NCL selects the target from the target groups after receiving a connection from the load balancer. Classic Load Balancer: Classic load balancer is designed to make routing decisions either at the application layer or transport layer. It requires a fixed relationship between container instance port and load balancer port. 23. Explain what is a T2 instance? T2 instance T2 instance is one of the low-cost Amazon instances that provides a baseline level of CPU performance. 24. Mention the security best practices for Amazon EC2. Security best practices for Amazon EC2 are as below: Security and network Storage Resource Management Recovery and Backup 25. While connecting to your instance, what are the possible connection issues one might face? The following are the connection issues faced by the user: User key not recognized by the server Permission denied Connection timeout Cannot connect using user’s browser Server unexpectedly closed network connection Unprotected private key Cannot ping the instance Server refused host key The private key must begin with “BEGIN RSA PRIVATE KEY” and end with “ END RSA PRIVATE KEY.” 26. What are key-pairs in AWS? Amazon EC2 uses both public and private keys to encrypt and decrypt the login information. The sender uses a public key to encrypt the data and the receiver uses a private key to decrypt the data. Private and public keys are known as key pairs. The public key enables you to access the instance securely and a private key is used instead of a password. 27. What is SimpleDB? SimpleDB is one of Amazon services offered by AWS. It is a distributed database and highly available NoSQL data store that offloads the work of database administrators. 28. What is Elastic Beanstalk? Elastic Beanstalk is the best service offered by AWS for deploying and managing applications. It assists applications developed in Java, .Net, Node.js, PHP, Ruby, and Python. When you deploy the application, Elastic beanstalk builts the selected supported platform versions and AWS services like S3, SNS, EC2, cloud watch and autoscaling to run your application. 29. Mention a few benefits of the Elastic beanstalk. Benefits of the Elastic beanstalk Following are the few benefits of the Elastic Beanstalk: Easy and simple: Elastic Beanstalk enables you to manage and deploy the application easily and quickly. Autoscaling: Beanstalk scales up or down automatically when your application traffic increases or decreases. Developer productivity: Developers can easily deploy the application without any knowledge, but they need to maintain the application securely and user-friendly. Cost-effective: No charge for Beanstalk. Charges are applied for the AWS service resources which you are using for your application. Customization: Elastic Beanstalk allows users to select the configurations of AWS services that user want to use them for application development. Management and updates: It updates the application automatically when it changes the platform. Platform updates and infrastructure management are taken care of by AWS professionals. 30. Define regions and availability zones in Amazon EC2. regions and availability zones in amazon ec2 Amazon web service has a global infrastructure that is divided into availability zones and regions. Each region is divided into a geographic area and it has multiple isolated locations called availability zones. 31. What is Amazon EC2 Root Device Volume? When the developer launches the instance, the root device volume is used to boot the instance that contains the image. When the developer introduces the Amazon EC2, all AMIs are propped up by an Amazon EC2 instance store. 32. What is Server Load Balancing? A Server load balancer (SLB. provides content delivery and networking services using load balancing algorithms. SLB distributes the network traffic equally across a group of servers to ensure high-performance application delivery. 33. How does a server load balancer work? aws server load balancer The server load balancer works based on two approaches. They are: Transport level load balancing Application level load balancing 34. What are the advantages of the Server load balancer? The advantages of server load balancer are as follows: Increases scalability Redundancy Maintenance and performance 35. Explain the process to secure the data for carrying in the cloud. One thing that must be taken into consideration is that no one should resize the data while it is moving from one point to another. The other thing to consider is there should not be any kind of leakage with the security key from the multiple storerooms in the cloud. Dividing the information into different types and by encrypting it into the valid methods could help you in securing the data in the cloud. 36. What are the layers available in cloud computing? AWS Certification Training! Explore Curriculum Below listed are the various layers of cloud computing SaaS: Software as a Service PaaS: Platform as a Service IaaS: Infrastructure as a Service 37. Explain the layers of Cloud architecture? We have five different types of layers available, which are: SC- Storage controller CC- cluster controller NC- Node controller Walrus CLC- cloud controller 38. What are the reserved instances? It is nothing but a reservation of resources for one or three years and utilized whenever you need it. The reservation comes on a subscription basis available for a term of 1 year and three years. The hourly rate goes down as the usage increases. Purchasing reservations isn’t just associated with the reservation of resources, but also, it comes with the capacity that is required for a particular zone. 39. What is meant by a cloud watch? Cloud watching is a monitoring tool in Amazon Web Services with which you can monitor different resources of your organization. You can have a look at various things like health, applications, network, etc. 40. How many types of cloud watches do we have? We have two types of cloud watches: essential monitoring and detailed monitoring. The necessary tracking will come to you at free of cost, but when it comes to detailed control, you need to pay for it. 41. Explain the cloud watch metrics that are meant for EC2 instances? The available metrics for EC2 instances are Disk reads, CPU utilization, network packetsOut, CPUCreditUsage, Disk writes, network packetsIn, networkOut, and CPUCreditBalance. 42. What would be the minimum and maximum size of the individual objects that you can store in S3? The minimum size of the object that you can store in S3 is 0 bytes, and the maximum size of an individual object that you can save is 5TB. 43. Explain the various storage classes available in S3? Below mentioned are the storage classes available in S3. Standard frequency accessed One-zone infrequency accessed RRS - reduced redundancy storage Standard infrequency accessed Glacier 44. What are the methods to encrypt the data in S3? We have three different methods available for encrypting the data in S3. They are as follows. Server-Side Encryption - C Server-Side Encryption - S3 Server-Side Encryption - KMS 45. On what basis the pricing of the S3 is decided? The pricing for S3 is decided by taking into consideration the below topics. Data transfer Storage used Number of requests Transfer acceleration Storage management 46. Is the property of broadcast or multicast supported by Amazon VPC? No, at present, Amazon VPC is not supporting any multicast or broadcast. 47. How many IP addresses are allowed for each account in AWS? For each AWS account, 5 VPC elastic addresses are allowed. 48. What is meant by Edge location? The actual content is cached at the places called edge locations. So whenever a user searches for the content, he will find the same at the edge locations. 49. What is Snowball? Snowball is an option available in AWS to transport. Using snowball, one can transfer the data into the AWS and out of it. It helps us in transporting massive amounts of data from one destination to another. It helps in lowering the networking expenditure. 50. Explain the advantages of auto-scaling? Below listed are the advantages of autoscaling. Better availability Better cost management High fault-tolerant 51. What is subnet? When a large amount of IP addresses are divided into small chunks, then these tiny chunks are called Subnets. 52. What is the number of subnets that we can have per VPC? Under one VPC, we can have 200 subnets. 53. What is AWS CloudTrail? AWS Cloudtrail is an AWS service that helps you to enable governance, risk auditing and compliance of your AWS account. Cloud trail records event when actions are taken by the role, user or an AWS service. Events include when actions are taken by AWS command-line interface, AWS management console, APIs and AWS SDKs. 54. What is meant by Elasticache? Upcoming Batches - AWS Training! 14 NOVThursday 6:30 AM IST 17 NOVSunday 7:00 AM IST 21 NOVThursday 6:30 AM IST 24 NOVSunday 6:30 AM IST More Batches Elasticache is a web service that makes the path easier to deploy and store the data in the cloud easily. 55. Explain about AWS Lambda. AWS Lambda is a computational service that enables you to run code without maintaining any servers. It automatically executes the code whenever needed. You are required to pay for the time that you have used it for. Lambda enables you to run the code virtually for any kind of application without managing any servers. 56. What is Geo Restriction in CloudFront? It is an important feature available in AWS which helps you in preventing the users from accessing the content from specific regions. CloudFront is useful for distributing the content only to desired locations. 57. What is Amazon EMR? Amazon EMR is a survived cluster stage and it helps you to create data structures before the intimation. Big data technologies such as Apache Hadoop and Spark are the tools that enable you to investigate a large amount of data. You can use the data for making analytical goals by using the apache hive and other relevant open source technologies. 58. What is the actual boot time taken to instance stored-backend AMI? It takes less than 5 minutes to store the instance-backed AMI. 59. Explain the essential features of the Amazon cloud search. Below listed are the essential features of Amazon cloud search. Prefixes Searches Enter text search Boolean searches Range searches Autocomplete Advice 60. Give a few examples of DB engines that are used in AWS RDS. Following are few examples of DB engines which are used in AWS RDS: MariaDB OracleDB MS-SQL DB MYSQL DB Postgre DB 61. What is the security group? In AWS the in and out traffic to instances is controlled with virtual firewalls which are known as Security groups. Security groups allow you to control traffic based on various aspects such as protocol, port and source destination. 62. What is the difference between block storage and file storage? Block Storage: it functions at a lower level and manages the data asset of blocks. File Storage: The file storage operates at a higher level or operational level and manages data in the form of files and folders. 63. Explain the types of Routing policies available in Amazon route S3. Latency-based Weighted Failover Simple Geolocation 64. List the default tables that we get when we create AWS VPC. Network ACL Security group Route table 65. List the different ways to access AWS. We have three different ways to access AWS, such as: Console SDK CLI 66. What are the EBS volumes? The EBS is the abbreviation for Elastic Block Stores. These blocks act as a persistent volume which can be attached to the instances. The EBS volumes will store the data even if you stop the instances. 67. How can you control the security to your VPC? You can use security groups, network access controls (ACLs) and flow logs to control your VPC security. AWS Questions and Answers Pdf Download Read the full article
0 notes
Text
WHAT IS WEB SERVICES TESTING?
Web services testing with SOAP:
click here to read first part
Web services testing is a way to access the web services using XML messages that include WSDL catalog listing web services with their name, input and output field parameter details which serve as an ideal testing road map. It is well suited for performing transactions that have multiple calls need to enforce the strict client server contract and works well with the distributed enterprise environments. It is highly structured with error handling security built-in is designed for expansion for expansion and can use transport protocols besides HTTP.

For example:
A simple account management and order processing system. The accounting personnel will use a client application system which is built in Visual Basic. The processing logic of this system is developed in java and has a database which interacts to store information.
The following steps to do the web services testing are:
The client collects and feeds the information of account registration into the SOAP message.
This SOAP message is sent to the web service in HTTP post request.
The web service will convert the SOAP request message to the command that the application will understand.
The information is processed by the application as required and responds with new unique account number of any customer.
The next process is the web service response another SOAP message Which sends to the client message in response to the HTTP request.
The web service testing tools are :
SOAP UI:
SOAP UI is one of the tools to test the web services which are used to design web services test of SOAP and REST architectures. SOAP UI allows the creation and execution of different types of software testing like: Functional test, regression tests, Mocking, load and performance tests and security evaluation.
2. JMeter:
Apache JMeter is an open-source application which is designed for the execution of load tests performance measurements in applications. JMeter has capabilities to perform load testing and performance testing in different application servers and protocols including
Web (HTTP,HTTPS)
SOAP /REST web services
FTP services
Database through JDBC
LDAP directory services
Message-oriented middleware, through JMS
EMAIL-SMTP,POP(3) and IMAP(S)
0 notes
Text
Best PHP training institute in noida

Best PHP Training Institute in Noida
Inovi Technologies offers best PHP training in Noida. PHP is server-side scripting language used to manage session tracking, database and dynamic content and e-commerce sites etc. Inovi Technologies offers you placement training in Noida.
Every PHP file has PHP endings and extensions are tagged with "php". Currently, PHP training courses are one of those most trend career choices for young minds.https://www.inovitechnologies.com/Corporate-Training/best-php-training-institute-in-noida/
PHP Training Syllabus
Introduction to Web and PHP
What is PHP?
History of PHP
Why choose PHP?
Installation overview
First stage
Embedding PHP code on page
The production
Operating path
Inserting code comments
Exploring Data Types
Variables
Strings
String functions
Numbers part one: Integers
Numbers part two: Floating points
Arrays
Associative arrays
Array functions
Booleans
NULL and empty
Type juggling and casting
Constants
Booleans
Free and empty
Typing and casting
Constant
Control Structures: Logical Expressions
If statements
Else and elseif statements
Logical operators
Switch statements
Control Structures: Loops
While loops
For loops
Foreach loops
Continue
Break
Understanding array pointers
User-Defined Functions
Defining functions
Function arguments
Returning values
Multiple return values
Scope and global variables
Setting default argument values
Debugging
Common problems
Warnings and errors
Debugging and troubleshooting
Building Web Pages with PHP
Links and URLs
Using GET values
Encoding GET values
Encoding for HTML
Including and requiring files
Modifying headers
Page redirection
Output buffering
Working with Forms and Form Data
Building forms
Detection form submissions
Single-page form processing
Validating form values
Problems with validation logic
Displaying validation errors
Custom validation functions
Single-page form with validations
MySQL Basics
MySQL introduction
Creating a database
Creating a database table
CRUD in MySQL
Populating a MySQL database
Relational database tables
Populating the relational table
Using PHP to Access MySQL
Database APIs PHP
Connecting to MySQL with PHP
Retrieving data from MySQL
Working with retrieved data
Creating records with PHP
Updating and deleting records with PHP
SQL injection
Escaping strings for MySQL
Introducing prepared statements
Sending Emails
Configuring PHP for email
Sending email with mail ()
Using headers
Review SMTP
Using PHPMailer
Our Courses:
Java
AWS
Mean Stack
Artificial Intelligence
Hadoop
Devops
Python
RPA
Machine learning
Salesforce
Linux And Red Hat
Data Scientist
Digital-Marketing
Web Designing
https://www.inovitechnologies.com/Corporate-Training/best-php-training-institute-in-noida/
Contact:
Mobile. No:- 9354482334,8810643463
Phone.No- +91-120-421-3880
EMail- [email protected]
Address:- F7 Sector-3 Noida UP 201301
0 notes
Text
Server side development 1 – SOAP
Introduction to the web services
Web services are server-side application components, which provides a set of services.
The services of the web service are exposed via API.
An API is a set of functions and procedures allowing the creation of applications that access the features or data of an operating system, application or other service.
Multiple types of clients can communicate with the web service via the API.
Web services vs. Web Applications
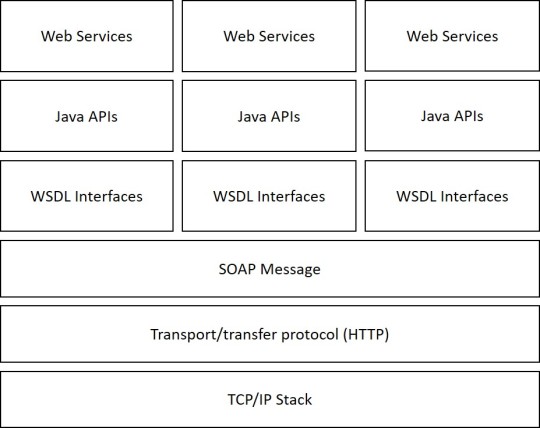
WSDL
WSDL stands for Web Services Description Language. It is the standard format for describing a web service. WSDL was developed jointly by Microsoft and IBM.
Features of WSDL
WSDL is an XML based protocol for information exchange in decentralized and distributed environments.
WSDL definitions describe how to access a web service and what operations it will perform.
WSDL is a language for describing how to interface with XML based services.
WSDL is and integral part of Universal Description, Discovery and Integration (UDDI), an XML based worldwide business registry.
WSDL is the language that UDDI uses
WSDL Usage
WSDL is often used in combination with SOAP and XML schema to provide web services over the internet. A client program connecting to a web service can read the WSDL to determine what functions are available on the server. Any special data types used are embedded in the WSDL file in the form of XML schema. The client can then use SOAP to actually call one of the functions listed in the WSDL.
Ref: https://www.tutorialspoint.com/wsdl/wsdl_introduction.htm
Specifies three fundamental properties:
1. What a service does – Operations (methods) provided by the service.
2. How a service is accessed – Data format and protocol details.
3. Where a service is located – Address (URL) details.
The document written in WSDL is also simply called a WSDL (or WSDL document).
The service provides the WSDL document and the web service client uses the WSDL document to create the stub (or to dynamically decode the message).
Stub
A stub is a small program routine that substitutes for a longer program, possibly to be loaded later or that is located remotely. For example, a program that uses Remote Procedure Calls (RPC ) is compiled with stubs that substitute for the program that provides a requested procedure.
The stub accepts the request and then forwards it (through another program) to the remote procedure. When that procedure has completed its service, it returns the results or other status to the stub which passes it back to the program that made the request.
Ref: https://whatis.techtarget.com/definition/stub
WSDL Elements – Type
Use the XML schema language to declare complex data types and elements that are used elsewhere in the WSDL document.
Serve as a container for defining any data types that are not described by the XML schema built-in types.
WSDL Elements – Message
Any WSDL interface is a set of messages that the service behind the interface expects to send and receive.
Messages are abstraction of request and response messages that client and web services exchange.
Messages are constructed from a number of XML schema typed part elements.
Ex:
<message name="getQuoteResponse">
<part name="Result" type="xsd:float"/>
</message>
WSDL Elements – Port type
Define web service functionality at abstract level, grouping sets of message exchanges into operations.
Contain a set of operations that incorporates input, output and fault messages and parameter order.
portType element may have one or more operation elements, each of which defines an RPC style or document style web service method.
WSDL Elements – Binding
Map a portType to a specific protocol, typically SOAP over HTTP, using a specific data encoding style.
One portType can be bound to several different protocols by using more that one port.
Binding style may be either RPC or Document (SOAP)
WSDL Elements – Service
It binds the web service to a specific network addressable location
Contain one or more port elements.
Access point for each port
- portType – The operations performed by the web service.
- message – The message used by the web service.
- types – The data types used by the web service.
- binding – The communication protocols used by the web service.
SOAP
SOAP stands for Simple Object Access Protocol.
SOAP supports both functional oriented and message oriented communication.
SOAP messages are carried as the payloads of some other network protocols.
(EX: HTTP or SMTP or FTP or TCP/IP)
Web services use SOAP as the logical transport mechanism for moving messages between services described by WSDL interfaces.
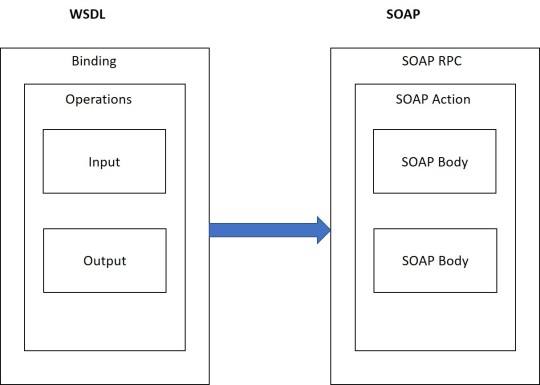
SOAP combines the data capabilities of XML with the transport capability of HTTP.
SOAP Messaging Modes
RPC/ Literal Document/ Literal
RPC/ Encoded Document/ Encoded
SOAP Messaging
Consistent envelope – Header and body
Consistent data encoding – Based on XML schema type system
Protocol binding framework
SOAP messages have encoding rules:
Defines a serialization mechanism that can be used to exchange instance of application- defined objects.
SOAP Elements – Envelope
Wraps entire message and contain header and body.
Defines an overall framework for expressing what is in a message, who should deal with it and whether it is optional or mandatory.
Envelope is a root XML element.
This tag indicates the start and end of the message to the receiver.
SOAP Elements – Header
An optional element with additional information.
If the header is presented in the message, it must be the immediate child of envelope element.
Header adds meta-data about the content of a SOAP message and extends it with extra information.
Headers may be processed independently of the body.
SOAP Elements – Body
Application- specific message content being communicated as arbitrary XML payloads in the request and response messages.
Fault elements provides information about errors.
This is the only mandatory part of the envelope. Contains the actual message sent for the final recipient
SOAP Elements – Fault
SOAP message that contains a fault element in the body is called a fault message.
SOAP faults are returned to the receiver’s immediate sender.
SOAP Elements – AttachmentPart
SOAP messages may have one or more attachments.
Each AttachmentPart object has a MIME header to indicate the type of data it contains.
MIME (Multipurpose Internet Main Extension) is an internet standard that extends the format of email to support
- Text in character sets other that ASCII.
- Non text attachments: audio, video, images, application programs
- Message bodies with multiple parts
- Header information is non-ASCII character sets
Ref: https://en.m.wikipedia.org/wiki/MIME
Frameworks for SOAP web service development environments
Apache CXF – Java
CodeIgniter – PHP
gSOAP – C and C++
Apache Axis – Java
Jello Framework – GAE/Java
.NET Framework – C#, VB.NET
Implement SOAP services
JAX-WS (Java API for XML Web Services) is a java package/ library for developing web services.
It supports both functional oriented and message-oriented communication via SOAP.
JAX-WS uses the javax.jws package and it uses annotations.
(Ex: @WebService, @WebMethod, @Oneway etc…)
0 notes
Text
WEB SERVICES TESTING BY H2KINFOSYS
Web services testing with SOAP:
click here to read first part
Web services testing is a way to access the web services using XML messages that include WSDL catalog listing web services with their name, input and output field parameter details which serve as an ideal testing road map. It is well suited for performing transactions that have multiple calls need to enforce the strict client server contract and works well with the distributed enterprise environments. It is highly structured with error handling security built-in is designed for expansion for expansion and can use transport protocols besides HTTP.
For example:
A simple account management and order processing system. The accounting personnel will use a client application system which is built in Visual Basic. The processing logic of this system is developed in java and has a database which interacts to store information.
The following steps to do the web services testing are:
The client collects and feeds the information of account registration into the SOAP message.
This SOAP message is sent to the web service in HTTP post request.
The web service will convert the SOAP request message to the command that the application will understand.
The information is processed by the application as required and responds with new unique account number of any customer.
The next process is the web service response another SOAP message Which sends to the client message in response to the HTTP request.
The web service testing tools are :
SOAP UI:
SOAP UI is one of the tools to test the web services which are used to design web services test of SOAP and REST architectures. SOAP UI allows the creation and execution of different types of software testing like: Functional test, regression tests, Mocking, load and performance tests and security evaluation.
2. JMeter:
Apache JMeter is an open-source application which is designed for the execution of load tests performance measurements in applications. JMeter has capabilities to perform load testing and performance testing in different application servers and protocols including
Web (HTTP,HTTPS)
SOAP /REST web services
FTP services
Database through JDBC
LDAP directory services
Message-oriented middleware, through JMS
EMAIL-SMTP,POP(3) and IMAP(S)
Questions:
What are Web services?
What is Web service Testing?
What are the goals of Web services Testing?
Facebook Comments
1 note
·
View note
Text
Distributed System
What is a distributed system??
Computer-based systems can be divided mainly into 2 types, depending on the distribution of the components.
1.Standalone system (Desktop application) 2.Distributed system
Distributed system -A distributed system is a system whose components are located in different computers connected in a network, which communicate and coordinate their actions when passing messages to each other. The components interact with each other to achieve a common goal.
Distributed computing - Distributed computing is a model in which the components of a software system are shared among several computers to improve efficiency and performance. According to the most restricted definition, distributed computing is limited to programs with shared components between computers within a limited geographical area.
Standalone system
Linux
Unix
Mac OS X
Windows 7
Advantages of standalone system
Purchased and installed separately
Function by themselves
Disadvantages of standalone system
Take a lot of storage space
Do not share resources
Distributed system
Intranets
Internet
www
email
Advantages of distributed system
Shareability
Expandability
Local autonomy
Improved performance
Improved reliability and availability
Potential cost reductions
Disadvantages of distributed system
Network reliance
Complexities
Security
Multiple point of failure
Distributed systems allow
Distributed systems allow,
share the computing resources
increasing the processing power
provide better user experience
The users to share data and other resources, such as documents and files
The engineers to have a centralized control
easier maintenance, modifications, and updates
Elements of distributed systems
The components interact with each other to achieve a common goal. Three important characteristics of the distributed systems are: component concurrence, lack of a global clock and independent failure of the components.
Processing components
Data networks for components to communicate: Including the components that are dedicated to process communication, called connectors.
Data stores (data bases) and Data
The configuration of the above elements
Types of the distributed system – based on the service of the network
Mail service (SMTP, POP3, IMAP)
File transferring and sharing (FTP)
Remote logging (telnet)
Games and multimedia (RTP, SIP, H.26x)
Web (HTTP)
Types of services

Non-web-based system
A "browser application" would be a recognized web browser application such as Internet Explorer, Firefox, Chrome, Opera and the like. All other applications will be considered "no browser" applications or applications whose main purpose is not to contact websites on your request.
Examples of non-browser-based system
Messenger
Facebook
Web based system
The web information system, or web-based information system, is an information system that uses Internet web technologies to deliver information and services to users or other information systems / applications. It is a software system whose main objective is to publish and maintain data using principles based on hypertext.
Types of web-based system
Web sites
Web applications
Web services and client apps
Rich Internet Applications (RIAs)/Rich Web based Applications (RiWAs)
Examples of web-based system
Google chrome
Fire fox
Microsoft edge
Opera
Types of RIAs/RiWAs (client-side perspective)
There is a wide range of web-based applications that use a rich communication model, such as rich Internet applications, mobile applications, cloud-based systems, Internet-based systems of things, etc. However, there is no adequate term to address them all and a definition that covers and explains the common characteristics of them. The definition of a concept is important because the definition provides a precise common understanding of the artifacts focused, which helps to increase the realization of these devices towards the proper use of them. We propose the general term Rich Web-Based Application to address the types of applications mentioned above, and we also propose a definition for this, in line with the common architectural characteristics of these applications. In addition, we offer a set of taxonomies to classify the techniques and technologies related to the development of rich Web-based applications, in order to improve the understanding of the proper use of them. In the future, we hope to introduce an architectural style for these rich Web-based applications, based on the proposed definition.
Advantages of RiWA
Performance
Offline-use
Consistency of look and feel
Security
Advanced communication
Rapid communication
Direct interaction
Better feedback
Improved features
Partial-page updating
Architecture of distributed system
Client-server (Two Tire Architecture)
The basic architecture of distributed systems is called client-server (or two-tier) architecture. The two-tier is based on the Client Server architecture. The two-tier architecture is like the client server application. Direct communication takes place between the client and the server. In general, the client sends a request asking the server for some service and the server's replies with the resources. There may be several clients, accessing the same server and clients can use different types of devices.

3 -Tire Architecture
First, it is necessary to define the architecture of 3 levels. According to Techopedia, "the 3-level architecture is a client-server architecture in which functional process logic, data access, computer data storage and user interface are developed and maintained as separate modules on separate platforms " The architecture of 3 levels is used, when the persistence of the data is needed and also to separate the logic of the application from the data.

n-tier Architecture
In software engineering, multilevel architecture (often called n-tiered architecture) or multilayer architecture is a client-server architecture in which the functions of presentation, application processing and data management are physically separated. When greater separation and distribution of the components is needed, more levels can be added and the 2 or 3 level architecture extended to a n-level architecture.

When different types of distributed systems want to communicate and share their services that form enterprise-level systems, Service Oriented Architecture (SOA) is used.

These different systems may
provide different services
are developed using different technologies
communicate via the Enterprise Service Bus (ESB)
Modularizing Styles
Microservice Architecture
Microservice architecture provides a range of technical benefits that contribute to the speed of development and product quality in software projects, while also contributing to business agility in general": MARK EMEIS, principal director of software technologies software, CA technologies

Microservice architecture provides a range of technical benefits that contribute to the speed of development and product quality in software projects, while contributing to business agility in general": MARK EMEIS, principal director of software technologies of software, CA technologies
Monolithic Architecture
Monolithic, in this context, means everything in one piece. The monolithic software is designed to be autonomous; The components of the program are interconnected and interdependent, instead of being coupled in a flexible way, as is the case with modular software programs.

Model-View-Controller (MVC) Balanced Abstract Web MVC (BAW-MVC) (A distributed mvc version)

In the distribution system there is a element called component. When there are lots of components, we need to find how to connect those components to communicate each other. First place they think these components as classes and they find a way of how to call each method by staying different classes. That’s functional oriented communication. When it comes to classes, they realize that it’s not possible to call a function when system is web service. Because Client and server run as two different applications. Then they go for a Message oriented communication. It’s about how to communicate server and client using messages. After sometimes they realize that everything is another resource. And Resource oriented communication is built.

CORBA is function oriented communication system. CORBA® is the acronym for Common Object Request Broker Architecture™, OMG®'s open, vendor-independent architecture and infrastructure that computer applications use to work together over networks. When different servicers are agree to using different techniques As example how to communicate when client part of the service is using c or c++ and server side use JAVA.
As we say above data is another element of distributed system. Data can be formatting/ Structuring as plain text, Files, Query string, xml or JSON.
XML is designed to store and transport data. It’s Both human- and machine-readable (self descriptive). main and the only component of XML is called an element. It has 3 components they are Start tag Body and End tag. An element has a name. Element names are case-sensitive. It must start with a letter or underscore. Element names cannot start with the letter’s xml (or XML, or Xml, etc). Element names can contain letters, digits, hyphens, Underscores, and periods. Element names cannot contain spaces. Any name can be used, no words are reserved (except xml).
Following are the best practices of element naming.
Create descriptive names, like this: <person>, <firstname>, <lastname>.
Create short and simple names, like this: <book title> not like this : <the_title_of_the_book>.
Avoid "-". If you name something "first-name", some software may think you want to subtract "name" from "first".
Avoid ".". If you name something "first.name", some software may think that "name" is a property of the object "first".
Avoid ":". Colons are reserved for namespaces (more later).
Non-English letters like éòá are perfectly legal in XML, but watch out for problems if your software doesn't support them.

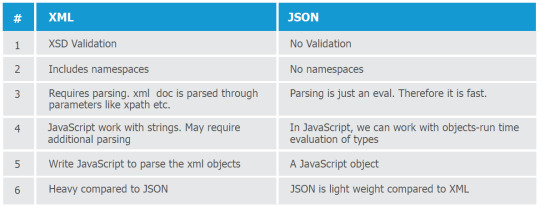
0 notes
Text
Jenkins Email Notification
Jenkins:-
Jenkins is an open-source non-stop integration server written in java for orchestrating a sequence of actions to attain the continuous integration technique in an automated style. Jenkins helps the complete improvement lifestyles cycle of software program from constructing, testing, documenting the software program, deploying, and different stages of the software improvement existence cycle.
Jenkins Email Notification:-
Jenkins Email Notifications are the way to notify based on an event that occurred or some action that happened. Jenkins email notifications are the kind of message that is automatically sent to you and update that, there has been activity on one of your social media accounts like Google, slack. As email is the primary means of notification among other social media for Jenkins email notifications. Jenkins provided a plugin to extend the functionality of e-mail notifications.
3 parts of Jenkins Email Notification
Given below are the 3 parts of Jenkins email notification:
Triggers: This is a defined condition that causes an e-mail notification to be sent.
Content: Defined content for email subject and body.
Recipients: We can mention the concerned user who is supposed to receive an e-mail when an event occurred.
Use Case of Jenkins Email Notification
Any organization follows the DevOps practice and configured Jenkins as part of their build process. DevOps team wants to configure a process and as part of the process to send an automated email to the Developers team if any build failure with the help of freestyle configurations. To send and receive emails we need to configure email servers in Jenkins. Basically in an organization, they have their email servers that are used to trigger. Emails, in our example we do not have our server, so we are going to use a Gmail SMTP server.
Configure Gmail SMTP Server in Jenkins
When the Jenkins email notification triggers, that is an event under which the event occurred and was sent to the respective recipients. For an Automated build job, there are many events such as success, failure, abort, and so on. After clicking on the triggers option is a selection of required event for which mail need to trigger. Once all the changes are made, save the configurations.
Go to Jenkins dashboard.
Go to the Jenkins home page and click the ‘Manage Jenkins’ menu option. Then, select the ‘Configure System’ option.
Go to the E-mail notification section and enter the required SMTP server and user email-suffix details. Click the ‘Advanced’ button and then click the checkbox next to the ‘Use SMTP Authentication’ option. Now, set the following fields.
We have to provide SMTP server details in the respective textbox, click on the advanced button, and below we have fields to be given to configure the SMTP server settings. Please find the below details to configure the email server.
Under E-mail Notification, put the mentioned details below:
SMTP server → smtp.gmail.com
Select Use SMTP Authentication
Put your Gmail id
Put your Gmail password
Use SSL select
SMTP port 465
0 notes